IP Address Handoff in the MANET
ip helper-address用法

ip helper-address用法IP helper-address是一种在网络设备中用来转发DHCP和BOOTP协议请求的命令,它的主要作用是帮助将这些请求从一个网络段转发到另一个网络段中的DHCP服务器。
在实际网络配置中,IP helper-address是一个非常常见且重要的命令,下面将详细介绍它的用法。
1. IP helper-address的基本概念IP helper-address命令是一种在网络设备上配置的命令,用于指定一个或多个DHCP服务器的IP地址。
它的原理是将接收到的DHCP和BOOTP协议请求封装在UDP数据包中,然后转发到配置的DHCP服务器上。
通过使用IP helper-address命令,网络管理员可以将DHCP服务器放置在不同的网络段,并确保客户端设备能够从任意网络段上获取IP地址。
2. IP helper-address的使用场景IP helper-address主要用于以下几种场景:- 跨网段的DHCP分发:当网络中的客户端设备和DHCP服务器处于不同的网络段时,IP helper-address命令可以将DHCP和BOOTP请求从客户端所在的网络段转发到DHCP服务器所在的网络段。
- 多个DHCP服务器:在大型网络中,可能会部署多个DHCP服务器来负载均衡或实现冗余。
通过配置多个IP helper-address命令,可以将DHCP请求转发到多个DHCP服务器上,并实现高可用性。
- IPv4和IPv6的互通:IP helper-address命令不仅适用于IPv4网络,也适用于IPv6网络。
通过配置IP helper-address命令,可以将IPv6的DHCPv6请求转发到DHCPv6服务器上,实现IPv6网络的自动配置。
3. IP helper-address的配置步骤下面是配置IP helper-address的基本步骤:3.1 进入网络设备的配置模式:首先,需要通过Telnet、SSH或控制台等方式登录到网络设备,并进入其配置模式。
IP Addressing IP地址举例(英文)

• • •
When subnetting is used, one generally speaks of a “subnetmask” (instead of a netmask) and a “subnet” (instead of a network) Use of subnetting or length of the subnetmask is decided by the network administrator Consistency of subnetmasks is responsibility of administrator
128.143.137.144
Example
• Example: 128.143 137.144
• Network address is: 128.143.0.0 • Host number is: 137.144 • Netmask is: 255.255.0.0
•
Convention (but not a reserved address)
Default gateway has host number set to ‘1’, e.g., e.g., 192.0.1.1
Subnetting
• Problem: Organizations have multiple networks which are independently managed
– all addresses 127.0.0.1-127.0.0.255 are reserved for loopback interfaces – Most systems use 127.0.0.1 as loopback address – loopback interface is associated with name “localhost”
ipaddress什么意思

ip address什么意思
小编整理了IP地址是什么意思,大家可以参考一下。
互联网协议地址(英语:Internet Protocol Address,又译为网际协议地址),缩写为IP地址(IP Address)。
IP地址,每个电脑都有一个固定上网IP,IP就是你现在上网用的电脑在网络中的地址,就像你收快递要留的地址差不多的意思!
P address
[英][ˌaɪˈpi: ədres]
n.
IP地址;
复数:IP addresses
1
Every connection that you make to the network is stamped with your IP address.
你每次连接到网络都会留下你的IP地址。
2
The hypervisor itself requires another IP address so that it can be managed remotely.
虚拟机管理程序本身需要另一个IP地址以便进行远程管理。
查看本机IP的方法如下:
方法1:在百度上输入“本机IP查询”,可以找到查找本机IP的网页。
方法2:借助软件查询,不如windows优化大师就有这个功能。
方法3:用命令查询,打开命令提示符,输入“ipconfig/all”即可查询本机IP。
网络基础地址解析协议

网络基础地址解析协议地址解析协议(Address Resolution Protocol,缩写为ARP)是TCP/IP协议栈中的一个协议,用于将一个32位的IPv4地址转换为对应的48位MAC地址。
在网络中,每一个网络接口都有对应的MAC地址和IP 地址,ARP协议就是用于获取这两个地址之间的映射关系的。
ARP协议工作在网络层(第3层)和数据链路层(第2层)之间。
在一个局域网络中,当一个主机需要发送一个数据包到另一个主机时,会先检查目标主机的IP地址是否存在于自己的ARP缓存中。
如果存在,就直接使用对应的MAC地址发送数据包。
如果不存在,就需要使用ARP协议进行地址解析。
ARP协议的工作原理如下:1.发送ARP请求:当一个主机需要找到另一个主机的MAC地址时,它会在本地网络广播一个ARP请求包,包含自己的MAC地址和IP地址,以及目标主机的IP地址。
2.接收ARP请求:网络中所有的主机都会接收到这个广播包,但只有目标主机会响应。
3.ARP响应:目标主机接收到ARP广播包后,会直接向发送主机发送一个ARP响应包,包含自己的MAC地址和IP地址。
4.更新ARP缓存:发送主机收到ARP响应包后,会将目标主机的MAC 地址与IP地址的映射关系存储到自己的ARP缓存中,以便下次发送数据包时直接使用。
ARP协议的优点是实现简单且适用于大多数网络环境。
它通过在局域网内广播ARP请求,可以快速获取到目标主机的MAC地址,从而实现数据包的传递。
但是,由于ARP协议是通过广播方式查询MAC地址,可能存在网络拥塞和安全性问题。
在实际网络中,为了减少广播带来的网络负载,主机会将最近的ARP查询结果保存在本地的ARP缓存中。
这样,在发送数据包时,不再需要进行ARP请求,直接使用缓存中的映射关系即可。
但是,由于网络中主机的MAC地址和IP地址是可能动态变化的,故ARP缓存中的映射关系也需要定期更新。
此外,为了防止ARP欺骗(ARP Spoofing)攻击,可以通过静态ARP 表、交换机的ARP防火墙等方式提高网络的安全性。
ip helper-address

ip helper-address2009-09-22 20:01路由器是不转达发广播的,帮助地址通过将这些广播数据包直接转发到目标服务器而帮助客户机和服务器建立联系。
帮助地址命令将广播性目的地地址改变为单点传达室送地址(或一个定向的广播-在某个子网内的本广播),使该广播消息可以被路由到一个具体的目的地而不是所有地方使用"ip helper-address address"接口配置命令配置一个可能会接收到广播的接口。
在该命令中"ADDRESS"是指在转发用户数据报协议(UDP)广播时所使用的目的地地址。
该指定地址可以是远程服务器的单点传送地址或定向广播地址。
如果定义了"ip helper-address address"命令,为8个缺省UDP端口进行转发的功能就被自动启用,它们是:TFTP(69)、DNS(53)、时间(37)、NETBIOS 服务(137)、N ETBIOS数据报服务(138)、BOOTP服务器(67)、BOOTP客户机(68)和终端访问控制器访问控制系统TACACS(49)。
1. 在客户端设备和DHCP服务器不再同一广播域内的时候,中间设备即路有器(路有功能的设备)必须要能够转发这种广播包,具体到cisco的设备上,则启用ip helper-address命令,来实现这种中继。
2. DHCP服务器要给终端设备分配地址则需要掌握两个重要的信息,第一,该客户端设备所在网络的子网掩码,DHCP服务器依据子网掩码的信息来判断,服务器该分配哪个IP地址,以使得该ip地址在那个子网内,第二,DHCP服务器必须知道客户端的MAC地址,以维护DHCP服务器的ip 地址和MAC之间的映射关系,由此保证同样一台客户机,每次启动后能获得和前一次相同的ip地址。
3 .配置了ip helper-address命令之后的路由器在中继DHCP请求时的工作过程如下:(1)DHCP客户端发送请求,由于没有ip地址,所以自己的源IP地址为0.0.0.0,而且也不知道目的DHCP服务器的地址,所以为广播255.255.255.255。
飞塔防火墙IP_MAC地址绑定方法简介
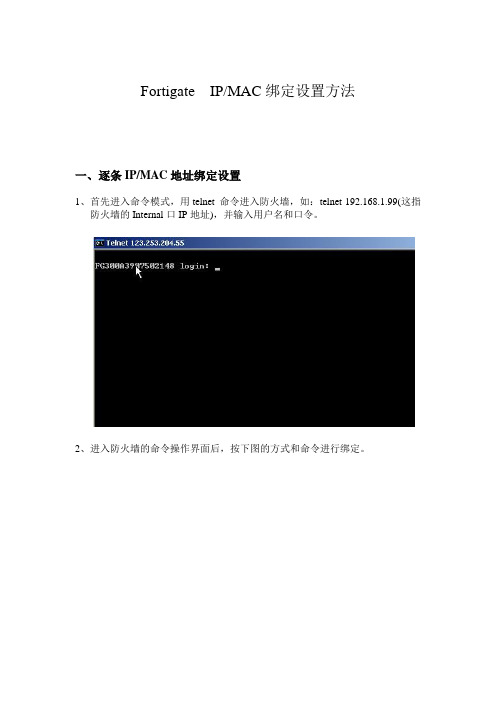
Fortigate IP/MAC绑定设置方法一、逐条IP/MAC地址绑定设置1、首先进入命令模式,用telnet 命令进入防火墙,如:telnet 192.168.1.99(这指防火墙的Internal口IP地址),并输入用户名和口令。
2、进入防火墙的命令操作界面后,按下图的方式和命令进行绑定。
第一个红框中命令解释如下:Config firewall ipmacbinding setting 进入MAC地址功能开启界面Set bindthroughfw enable 允许绑定的IP穿透防火墙Set bindtofw enable 充许绑定IP到达防火墙Set undefinedhost block或allow 没有绑定的全部阻止End 退出保存的意思第二个红框中的意思在接口上启用绑定功能:Config system interface 进入接口配置界面Edit internal(这里填具体端口)进入接口Set ipmac enable 开启IP/MAC地址绑定功能End 退出保存3、具体绑定操作:上图各个命令解释:Config firewall ipmacbinding table 进入绑定界面Edit 1 输入编辑行号(每一个行代表一个IP/MAC地址的绑定)Set ip 192.168.1.5 指定IP地址Set mac 00:0c:29:34:95:60 指定MAC地址(需要用‘:’隔开)Set name ‘test’指定名称Set status enable 开启状态End 退出保存Show firewall ipmacbinding table 1 查看编号为1的IP/MAC绑定情况到此,一个IP/MAC绑定就完成了。
注:当有多个绑定的时候,每编辑完一个,都要“end”,然后“edit 2、edit 3……edit N”一直到全部写完为此;输入edit 1命令进行创建表1并进入到表1的命令行界面(表此数字是依次增加的,一个表只能绑定一个IP、MAC,继续绑定第二个IP时需要输入edit 2)二、FG防火墙批量绑定方法:1、前两步功能开启和穿透设定,同逐条IP/MAC地址绑定一样,请参照1-2步操作。
ipv4route destination address is loopback -回复

ipv4route destination address is loopback -回复IPv4(Internet Protocol version 4)是互联网中最广泛使用的网络协议之一,负责将数据包从一个网络节点传输到另一个网络节点。
在IPv4中,每个网络设备都被分配一个唯一的IP地址,这些地址由32位的二进制数字组成。
IPv4路由表则用于确定应该将数据包发送到哪个网络设备。
在IPv4路由表中,可以定义多种类型的目的地地址,包括广播地址、多播地址和环回地址。
环回地址是一种特殊类型的地址,用于将数据包发送给同一个设备,而不需要通过网络传输。
这个地址被称为"127.0.0.1",也被称为"localhost"。
环回地址常用于测试和诊断网络设备,它提供了一种简单的方式来验证设备的网络连接性和功能。
当设备接收到一个发送到环回地址的数据包时,它将立即将其传递给自己的网络堆栈,而无需通过任何物理网络接口。
这使得网络管理员能够轻松地测试设备的网络功能,而无需依赖于其他设备或网络。
在IPv4路由表中,环回地址通常被定义为一个特殊的目的地地址,以确保设备能够正确地处理发送到自己的数据包。
这些路由表条目包含了目的地地址、子网掩码和下一跳信息。
对于环回地址,目的地地址通常被设定为"127.0.0.1",而子网掩码被设定为"255.0.0.0",以确保它与任何IPv4地址匹配。
然而,对于环回地址,下一跳信息通常被设定为"本地"或"直接连接"。
这意味着数据包将被直接发送到设备自己的网络堆栈,而不需要通过任何物理网络接口。
这进一步确保设备能够正确地处理发送到自己的数据包,并避免了不必要的网络延迟和资源消耗。
总而言之,IPv4路由表中的环回地址条目被用于确保设备能够正确地处理发送到自己的数据包。
这些条目允许将数据包直接发送到设备自己的网络堆栈,而无需通过任何物理网络接口。
ipaddress用法(二)

ipaddress用法(二)ipaddress用法ipaddress是Python的一个标准库,用于处理IP地址和网络操作。
它提供了一组丰富的功能,用于验证、解析和操作IP地址。
下面是一些ipaddress的常见用法及详细讲解:创建和解析IP地址•使用和类可以分别创建IPv4和IPv6的地址对象。
import ipaddressip_v4 = ('')ip_v6 = ('2001:0db8:85a3:0000:0000:8a2e:0370:7334')•使用IP地址对象的属性可以获取与之相关的信息,如版本、压缩形式和正常形式的地址等。
print(ip_) # 输出:4print(ip_) # 输出:2001:db8:85a3::8a2e:370:7334print(ip_) # 输出:2001:0db8:85a3:0000:0000:8a2e:0370:7 334•使用和类可以解析IP地址和子网掩码,创建网络对象。
network_v4 = ('/24')network_v6 = ('2001:0db8:85a3::/64')地址计算和操作•ipaddress模块提供了一些方法来比较和操作IP地址,如获取网络地址、广播地址以及判断IP地址是否在指定网络中。
print(network__address) # 输出:print(network__address) # 输出:print(ip_v4 in network_v4) # 输出:Trueprint(network__address) # 输出:2001:db8:85a3::print(network__address) # 输出:2001:db8:85a3:ffff:ffff: ffff:ffff:ffffprint(ip_v6 in network_v6) # 输出:False•使用IP地址对象的is_private方法可以判断IP地址是否是私有地址。
RFC2865中文文档

RFC 2865 RADIUS 中文翻译收藏Network Working Group C. Rigney Request for Comments: 2865 S. Willens Obsoletes: 2138 LivingstonCategory: Standards Track A. RubensMeritW. SimpsonDaydreamerJune 2000远程认证拨号用户服务(RADIUS)备忘录状态本文档描述了一种Internet社区的Internet标准跟踪协议,它需要进一步进行讨论和建议以得到改进。
请参考最新版的“Internet正式协议标准” (STD1)来获得本协议的标准化程度和状态。
本备忘录可以不受限制地传播。
版权说明Copyright (C) The Internet Society (2000). All Rights Reserved.IESG说明:本协议已经被广泛实现和使用,经验表明当本协议在一个大范围的系统中使用会降低性能和丢失数据。
部分原因是协议中没有提供拥塞控制的机制。
读者可以发现阅读本文对跟踪IETF组织的AAA工作组的工作进程有很大的帮助,AAA工作组可能会开发一个能够更好的解决扩展性和拥塞控制问题的成功的协议。
摘要本文描述了一个传输认证、授权和配置信息的协议。
这些信息在想要认证链路的网络接入服务器(Network Access Server)和共享的认证服务器务器之间传递。
实现说明本备忘录记录了RADIUS协议,RADIUS协议的早期版本使用的UDP端口是16 45,由于和"datametrics"服务冲突,官方为RADIUS协议分配了一个新的端口号1812。
Rigney, et al. Standards Track [Page 1]RFC 2865 RADIUS June 2000目录1. 简介 (3)1.1 描述文档的约定 (4)1.2 术语 (5)2. 操作 (5)2.1 挑战/回应 (7)2.2 使用PAP和CHAP互操作 (8)2.3 代理 (8)2.4 为什么使用UDP (11)2.5 重发提醒 (12)2.6 被证明是有害的心跳 (13)3. 报文格式 (13)4. 报文类型 (17)4.1 接入请求报文 (17)4.2 接入成功回应报文 (18)4.3 接入拒绝回应报文 (20)4.4 接入挑战报文 (21)5. 属性 (22)5.1 User-Name (26)5.2 User-Password (27)5.3 CHAP-Password (28)5.4 NAS-IP-Address (29)5.5 NAS-Port (30)5.6 Service-Type (31)5.7 Framed-Protocol (33)5.8 Framed-IP-Address (34)5.9 Framed-IP-Netmask (34)5.10 Framed-Routing (35)5.11 Filter-Id (36)5.12 Framed-MTU (37)5.13 Framed-Compression (37)5.14 Login-IP-Host (38)5.15 Login-Service (39)5.16 Login-TCP-Port (40)5.17 (unassigned) (41)5.18 Reply-Message (41)5.19 Callback-Number (42)5.20 Callback-Id (42)5.21 (unassigned) (43)5.22 Framed-Route (43)5.23 Framed-IPX-Network (44)5.24 State (45)5.25 Class (46)5.26 Vendor-Specific (47)5.27 Session-Timeout (48)5.28 Idle-Timeout (49)5.29 Termination-Action (49)Rigney, et al. Standards Track [Page 2] RFC 2865 RADIUS June 20005.30 Called-Station-Id (50)5.31 Calling-Station-Id (51)5.32 NAS-Identifier (52)5.33 Proxy-State (53)5.34 Login-LAT-Service (54)5.35 Login-LAT-Node (55)5.36 Login-LAT-Group (56)5.37 Framed-AppleTalk-Link (57)5.38 Framed-AppleTalk-Network (58)5.39 Framed-AppleTalk-Zone (58)5.40 CHAP-Challenge (59)5.41 NAS-Port-Type (60)5.42 Port-Limit (61)5.43 Login-LAT-Port (62)5.44 Table of Attributes (63)6. IANA注意事项 (64)6.1 术语定义 (64)6.2 推荐的注册策略 (65)7. 举例 (66)7.1 用户Telnet到指定主机上 (66)7.2 用户使用CHAP认证方式认证 (67)7.3 用户使用挑战-回应卡 (68)8. 安全事项 (71)9. 更新记录 (71)10. 参考文献 (73)11. 致谢 (74)12. AAA工作组主席地址 (74)13. 作者地址 (75)14. 版权声明 (76)1. 简介本文档废弃了RFC 2138 [1]。
Addressfinder 用户指南说明书

Getting StartedStep1Sign up for a FREE Addressfinder account at either https://addressfi.au or https://addressfi.This will provide you with an account key(Step3)and allow you to approve your website’s domain/s for use via this account and key(Step4).Step2Log into your Magento Admin and navigate to the Addressfinder configuration menu under: Stores>Settings>Configuration>Services>AddressfinderStep3Configure the settings1.Uncheck the'Use system value'checkbox2.Set‘Enabled’to Yes3.Paste your Addressfinder licence key into the field4.Paste any address params into the‘Widget Options’area(optional,see WidgetOptions below)5.Save ConfigStep4Skip this step if you already added your domain when signing up for your accountLogin to the Addressfinder Portal(https://portal.addressfi/portal/)and add your domain/s to the list of domains approved on your account.Select the‘Domains’button on the Dashboard page or in the side navigation and add them one at a time.Step5Once your Addressfinder licence key has been set in Magento Admin and you have added your domain in the Addressfinder Portal,the extension is ready to test.Testing Steps:1)check that either Australia or New Zealand is selected in the countryfield.2)type thefirst few characters of an address in the Street Addressfield.A dropdown containing addresses that closely match what you have typed should appear below the Street Addressfield.3)select an address from the dropdown and check that each part of that address populates the correctfield(eg,suburb into the Suburbfield).Repeat the Testing Steps above on the following pages:Checkout-Shipping addressfieldsCheckout-Billing addressfieldsNew Account-AddressfieldsEdit Account-Add new addressAdmin>Order-Shipping addressfields(only on Magento version2.2,2.3&2.4)Admin>Order-Billing addressfields(only on Magento version2.2,2.3&2.4) Checkout>Ship to multiple addresses(the service is not yet configured to work on this page)Step6-Configuration of Widget Options(optional)By default,the service will return Australian addresses from the GNAF address database.If this does not align perfectly with your business needs please configure the widget options box(part4of Step3above)with an appropriate code below.The common configurations are:Australia:●To search all verified Australian addresses(including PO Box address types):{"address_params":{"source":"gnaf,paf"}}●To search only Australia Post delivered addresses(including PO Box address types):{"address_params":{"source":"paf"}}●To search only Australia Post delivered addresses(excluding PO Box address types):{"address_params":{"source":“paf","post_box":"0"}}New Zealand:●To search all verified New Zealand addresses(including PO Box address types):{"address_params":{}}●To search all verified New Zealand addresses(excluding PO Box address types):{"address_params":{"post_box":"0"}}For a full list of possible options visithttps://addressfi.au/docs/javascript_widget_reference_au/or contact us if you have any different needs.Disabling the service on specific formsBy default,the service will work in the Checkout,New Account,Edit Account and Admin Order pages(excluding Magento Version2.1).If you do not wish the service to work on all of these forms,disable the appropriate ones via the‘Enable Specific Forms’area found in:Stores> Settings>Configuration>Services>Addressfinder page.。
inetaddress类的方法 -回复

inetaddress类的方法-回复InetAddress类是Java中的一个重要类,它提供了一系列方法来处理IP 地址和主机名。
本文将深入探讨InetAddress类的不同方法,包括获取本地主机信息、获取远程主机信息、解析主机名和IP地址等。
我们将逐步解释每个方法的功能和用法。
首先,让我们来了解一下InetAddress类的概念。
InetAddress代表了一个IP地址,它可以是IPV4或IPV6的地址。
在网络通信中,我们通常使用域名来标识网络上的主机。
但是计算机在网络中通信时,需要使用IP 地址。
InetAddress类提供了方法来处理域名和IP地址之间的转换。
一、获取本地主机信息InetAddress类的getLocalHost()方法用于获取本地主机的信息。
它返回一个InetAddress对象,表示本地主机的IP地址和主机名。
javaInetAddress localHost = InetAddress.getLocalHost();使用上述代码,我们可以获取本地主机的IP地址和主机名。
可以调用InetAddress类的以下方法来获取这些信息:1. getHostName():获取本地主机的主机名。
2. getHostAddress():获取本地主机的IP地址。
javaSystem.out.println(localHost.getHostName());System.out.println(localHost.getHostAddress());二、获取远程主机信息除了本地主机信息,InetAddress类还提供了方法来获取远程主机的信息。
我们可以使用getByName()方法来获取指定主机名的IP地址。
javaString hostname = "InetAddress remoteHost = InetAddress.getByName(hostname);在上面的示例中,我们使用getByName()方法获取了主机名为"javaSystem.out.println(remoteHost.getHostName());System.out.println(remoteHost.getHostAddress());三、解析主机名和IP地址有时候,我们需要将主机名转换为IP地址或者将IP地址转换为主机名。
is a loopback address -回复

is a loopback address -回复什么是环回地址?网络中,每个设备都有一个唯一的IP地址用于标识和定位。
而环回地址(loopback address)是一种特殊的IP地址,用于将数据包从一个设备回送到同一设备。
也就是说,环回地址的数据不会离开设备,而是在设备内部进行处理和使用。
环回地址最常用的IP地址是IPv4中的127.0.0.1和IPv6中的::1。
环回地址主要用于网络和系统的自我测试、诊断、开发和调试等目的。
在开发和测试网络应用程序时,环回地址可以模拟发送和接收网络数据,以便进行功能测试和故障排除。
此外,在某些情况下,环回地址还可以用于绕过网络连接问题或执行本地网络活动,而无需实际连接到外部网络。
环回地址的用途:1. 网络应用程序的测试和调试:通过将数据包从一个设备回送到同一设备,可以测试网络应用程序的功能和性能,并进行故障排除。
例如,一个Web 开发人员可以使用环回地址测试一个本地运行的网站是否正常工作。
2. 测试网络连接问题:有时,网络连接问题可能导致无法访问外部网络。
使用环回地址可以绕过这些问题,确保设备本身以及设备上的网络服务正常工作。
这有助于确定是否是网络连接导致的问题,还是设备本身出现故障。
3. 系统的自我测试和诊断:操作系统和网络设备可以使用环回地址来自我测试和诊断自身的各个功能和组件。
这使得操作系统可以检测和解决一些潜在的问题,以确保设备正常运行。
4. 维护和管理:环回地址还可用于管理和维护网络设备。
例如,管理员可以使用环回地址进行设备的远程访问和管理,而无需使用真实的外部网络地址。
如何使用环回地址?使用环回地址非常简单。
在大多数操作系统中,只需将环回地址作为目标地址指定,数据包就会在设备内部回送。
以下是使用环回地址的基本步骤:1. 确认设备支持环回地址:大多数现代操作系统和网络设备都支持环回地址。
但是,在使用之前,最好确认设备或操作系统是否支持环回地址。
2. 指定环回地址作为目标地址:将环回地址(例如IPv4中的127.0.0.1或IPv6中的::1)指定为数据包的目标地址。
无线移动网络简介_的讲座

14
网络交换子系统(NSS--Network Switch Subsystem):网络交换子系统主要完成交换 功能和客户数据与移动性管理、安全性管理 所需的数据库功能。
低传输能量 1mw
802.15和Bluetooth标准
29
802.11和Bluetooth将溶合
802.11
Bluetooth
Cordless headset
LAN AP
802.11和Bluetooth共同接入 优势互补
30
无线移动自组网络
Mobile Ad Hoc Networks(MANET)
手持机 (MS)
手持机(MS)
车载台 (MS)
13
蜂窝移动通信系统
蜂 窝 移 动 通 信 系 统 主 要 是 由移 动 台 ( MS ) 、 无 线 基 站 子 系 统 ( BSS ) 和 网 络 交 换 子 系 统 (NSS)三大部分组成.
移动台(MS-Mobile Station):由移动终端 (MS)和客户识别卡(SIM)组成。
3G的主要特点:
✓ 支持移动多媒体业务 ✓ 宽带CDMA技术 ✓ 高频谱效率 ✓ FDMA/TDMA/CDMA ✓ 从电路交换到分组交换 ✓ 从媒体(media) 到多媒体(Multi-media) ✓ 高保密性 ✓ 全球范围无缝漫游系统 ✓ 微蜂窝结构
9
第四代数字蜂窝移动通信—正在研究
How to Check a Computer IP Address

How to Check a Computer IP AddressWhen it comes to using a computer connected to the internet, one of the most important pieces of information you need is the IP address. IP or Internet Protocol addresses are used to identify devices on a network. From accessing websites to remote desktop connections, software licensing, and more, your computer's IP address plays a crucial role in many online activities. So, knowing how to find your computer IP address is essential. In this article, we will discuss different ways to check your computer IP address.What is an IP address?In simple terms, an IP address is a unique identifier that allows computers to communicate with each other over the internet. It consists of a series of numbers and dots separated by periods, such as192.168.1.1. A typical IP address is composed of two parts: network identifier (prefix) and host identifier (suffix). The network identifier helps identify the network, while the host identifier identifies the individual device on that network.How to check IP address on WindowsWindows operating system provides several ways to check your computer IP address. Here are some methods:1. Using Command PromptCommand Prompt is a powerful tool that can be used to perform various tasks, including checking your computer's IP address. Here's how to do it:- Press Windows + R keys together to open the Run dialog box.- Type 'cmd' and press Enter to open the Command Prompt.- Type 'ipconfig' and press Enter.- You should see a list of network adapters connected to your computer. Find the adapter whose IP address you want to check and look for the 'IPv4 Address' field. The number shown under IPv4 address is your computer IP address.2. Using SettingsYou can also check your IP address through the settings app on Windows. Here's how:- Click on the Start menu and select the Settings (cogwheel icon).- Click on Network & Internet.- Select the Wi-Fi or Ethernet option depending on the type of connection you are using.- Under the connection status, you'll see the IPv4 address entry. The number shown is your computer IP address.How to check IP address on MacMac users can also check their computer's IP address using different methods. Here are some:1. Using Network PreferencesNetwork Preferences is the default utility on macOS that allows you to check the IP address of your computer. Follow these steps:- Click on the Apple menu and select System Preferences.- Click on Network.- Select the network connection you want to check (Wi-Fi or Ethernet).- You should see your IP address displayed under the Status section.2. Using TerminalThe Terminal app on macOS allows you to run various commands, including the one to check the IP address of your computer. Here's how you can do it:- Open the Terminal app from Finder > Applications > Utilities.- Type 'ifconfig' and press Enter.- You should see a list of network adapters connected to your computer. Look for the adapter whose IP address you want to check and find the 'inet' field. The number shown in this field is your computer IP address.How to check IP address on mobile devicesChecking the IP address on mobile devices like smartphones or tablets is equally important. Here's how to check it on iOS and Android:1. iOS Devices- Go to Settings > Wi-Fi.- Tap the connected Wi-Fi network.- You should see your IP address displayed below the DHCP or BootP field.2. Android Devices- Open Settings > Network & internet.- Tap Wi-Fi if you're connected to a Wi-Fi network.- Tap the connected network.- You should see your IP address displayed at the bottom of the screen.ConclusionKnowing how to check your computer IP address is essential for various reasons. Whether you're troubleshooting network issues orconfiguring network-related settings, having access to your machine's IP address helps. With the methods mentioned in this article, you can quickly and easily find your computer's IP address on Windows, macOS, and mobile devices.。
Anybus X-gateway - EtherNet IP Scanner 接口网络安装指南说明书

Anybus X-gateway - EtherNet/IP™ Scanner InterfaceNetwork Installation SheetSP1763, rev. 2.20, Sep 2016Product OverviewThe EtherNet/IP Scanner interface can only be mounted in the top slot of the Anybus X-gateway.Top viewON12345678IP Address Configuration SwitchesPower Connector (X3)EtherNet/IP Connector (X1)Front viewGW StatusLA MS NSUSB Connector (X4)Status LED:sIP Address Con fi guration SwitchesSets the binary value of the last byte of the IP address within subnet 192.168.0.1–254 (netmask 255.255.255.0). To use a different subnet, set all switches to OFF and con fi gure with Anybus IPcon fi g.1286432168421Binary valueOFF OFF OFF OFF OFF OFF OFF OFF IP address set with IPcon fi g OFF OFF OFF OFF OFF OFF OFF ON 192.168.0.1OFF OFF OFF OFF OFF OFF ON OFF 192.168.0.2ON ON ON ON ON ON ON OFF 192.168.0.254ON ON ON ON ON ON ON ON (Not valid)12345678Switch number= 192.168.0.1ODVA™ and EtherNet/IP™ are trademarks of ODVA, Inc.Technical SupportTechnical support, documentation and software downloads are available at .Technical questions regarding the EtherNet/IP fi eldbus system should be addressed to ODVA at .Accessories ChecklistThe following items are required for installation:• EtherNet/IP con fi guration tool (optional, not included)• USB cable (included)• EDS fi le for EtherNet/IP (see )• LAN cable (not included)Installation and Startup Summary(Depending on your setup, some steps may not be required.)1. Connect the gateway to the EtherNet/IP network 2. Set a valid IP address for the EtherNet/IP interface(contact your network administrator for information)3. Connect a PC to the gateway via USB 4. Power up and con fi gure the gateway 5.Install the EDS fi le in the EtherNet/IP con fi guration toolEtherNet/IP (RJ45) ConnectorPin Signal 1TD+2TD-3RD+4, 5, 7, 8Termination to PE 6RD-LED IndicatorsLED Indication Meaning GW Status See Gateway Installation SheetLAGreen Link establishedGreen (fl ashing)Receiving/transmitting data OffLink not detected MS Green Normal operation Green (fl ashing)Standby, not yet con fi gured Red Major fault, unrecoverable Red (fl ashing)Minor fault, recoverable Red/green (alternating)Hardware self test OffNo powerNS Green EtherNet/IP connection(s) OK Green (fl ashing)No EtherNet/IP connections Red Duplicate IP address Red (fl ashing)Connection timeout Red/green (alternating)Hardware self testOffNo power or no IP address set。
multicast address例子 -回复

multicast address例子-回复什么是multicast地址?Multicast地址是用于在网络上进行组播(multicast)通信的特殊IP地址。
它允许发送方将数据一次性发送给多个接收方,节省了网络资源并提高了通信的效率。
与单播(unicast)和广播(broadcast)不同,单播只能发送给一个特定的接收方,而广播则是发送给所有的主机。
而组播则是在互联网上的一组特定接口的集合上发送数据。
Multicast地址通常用于各种多媒体应用和实时通信,例如视频直播、在线游戏、实时会议等。
它提供一种高效、可扩展的方式来传输数据, 能够同时满足一组接收方的需求。
Multicast地址的使用严格遵循一定的规范,这些规范是由Internet工程任务组(IETF)制定的。
Multicast地址是从IPv4地址空间中的特定范围中分配的,而在IPv6中有更多的地址可用于组播。
下面将一步一步地讨论Multicast地址的结构以及如何在网络中使用。
第一步:理解Multicast地址的结构Multicast地址由IP地址和一个扩展的标识符组成。
IP地址用于标识主机或路由器的网络接口,而扩展标识符用于标识特定的组播组。
Multicast 地址是一个32位的二进制数字,在IPv4中,它由四个8位字段组成(例如,224.0.0.1)。
在IPv6中,Multicast地址由128位的二进制数字组成。
在IPv4中,Multicast地址的前8位被保留为1110,以便它们与单播和广播地址区分开。
剩下的24位用于标识特定的组播组。
这有助于将不同的组播组与单播和广播地址区分开来。
其中,特定的范围用于特定的用途,例如224.0.0.0用于本地网络控制消息,239.0.0.0用于全局范围内的组播。
在IPv6中,Multicast地址的前8位被保留为ff00::/8,以便与单播和任播地址区分开。
剩下的120位用于标识特定的组播组。
gateway address 缩写

gateway address 缩写全文共四篇示例,供读者参考第一篇示例:Gateway address 缩写是GA,用于在计算机网络中确定数据包的下一个目的地。
每台计算机连接到互联网或局域网时,都会被分配一个独特的IP地址,这个地址就是用来标识计算机在网络上的位置的。
而网关地址则是指用来连接不同网络的设备,用来转发数据包的位置。
在一个网络中,网关地址将连接两个或多个子网,它起到了扮演"大门"的作用,所有要传输到其他网络的数据包都需要先经过网关。
网关地址通常是网络中的一台路由器或交换机,它负责将数据包从源地址发送到目的地址,确保数据包能够准确快速地到达目的地。
在一个局域网中,网关地址通常是路由器的地址,它会将数据包发送到互联网上。
当一个计算机要连接到互联网时,它会将数据包发送到网关地址,网关地址就会负责将数据包转发给下一个目的地。
网关地址不仅仅是用来连接不同网络的设备,还可以作为转换器来连接不同的网络协议,帮助数据包在不同网络之间进行通信。
Gateway address 缩写为GA,在计算机网络中扮演着十分重要的角色。
它扮演着数据包传输的关键角色,确保数据包能够准确快速地到达目的地,无论是连接到局域网还是互联网。
没有网关地址,计算机之间的通信将变得困难,数据包无法正确地在不同网络之间传输。
网关地址在计算机网络中具有不可替代的作用。
通过网关地址,计算机可以连接到任何一个网络,实现全球范围内的互联。
网关地址的作用不仅仅局限于传输数据包,它还可以实现远程访问、VPN连接、DHCP分配等功能。
网关地址的设置对于计算机网络的正常运行十分重要,只有通过正确设置网关地址,计算机才能正确地连接到网络,实现数据包的传输。
第二篇示例:Gateway address是什么呢?在网络通信中,gateway address是指网关地址,也可以称为网关IP。
网关地址是一个在网络通信中非常关键的概念,它充当着网络中不同子网间数据传输的中转站,是信息传递的关键媒介,可以连接不同网络或子网之间进行数据传输和通信。
出口ip 翻译

出口ip 翻译【原创实用版】目录1.出口 IP 的定义和作用2.出口 IP 的翻译方法3.出口 IP 的实际应用案例正文【出口 IP 的定义和作用】出口 IP,是指在网络中,数据包从本地网络传输到目标网络时,所经过的最后一个路由器(即出口路由器)所具有的 IP 地址。
出口 IP 地址通常是由网络服务提供商(ISP)分配的,用于标识用户所在的网络,并在互联网中进行数据传输。
在网络通信中,出口 IP 地址扮演着至关重要的角色。
首先,出口 IP 地址是数据包在互联网中的标识,它能确保数据包正确地发送到目标网络。
其次,出口 IP 地址还是网络服务提供商(ISP)进行流量控制和计费的重要依据。
此外,通过对出口 IP 地址进行分析,可以了解网络的拓扑结构,为网络优化和故障排查提供参考。
【出口 IP 的翻译方法】在实际应用中,出口 IP 地址通常需要进行翻译,以便在不同的网络环境中进行通信。
出口 IP 的翻译方法主要包括以下两种:1.静态翻译:静态翻译是指出口 IP 地址与目标 IP 地址之间的映射关系由网络管理员手动配置。
这种方法适用于网络规模较小、出口 IP 地址数量有限的场景。
静态翻译的优点是配置简单、易于管理,缺点是需要大量的人工操作,不适应大规模网络环境。
2.动态翻译:动态翻译是指出口 IP 地址与目标 IP 地址之间的映射关系由网络设备自动学习和更新。
这种方法适用于网络规模较大、出口 IP 地址数量较多的场景。
动态翻译的优点是减轻了网络管理员的工作负担,适应大规模网络环境,缺点是网络设备需要具备较高的计算能力。
【出口 IP 的实际应用案例】以某企业网络为例,假设该企业拥有多个分支机构,分别位于不同的城市。
为了实现各分支机构之间的高效通信,企业需要为每个分支机构分配一个出口 IP 地址。
在这个过程中,需要对出口 IP 地址进行翻译,以确保数据包能够正确地发送到目标网络。
具体来说,企业可以采用静态翻译或动态翻译方法,将出口 IP 地址与目标 IP 地址进行映射。
怎么利用IP静态绑定实现冲突IP电脑的隔离

怎么利用IP静态绑定实现冲突IP电脑的隔离
局域网IP冲突将直接导致无法正常访问互联网。
可以借助IP静态绑定实现冲突IP电脑的隔离操作,下面是店铺给大家整理的一些有关IP静态绑定实现冲突IP电脑的隔离的方法,希望对大家有帮助!
IP静态绑定实现冲突IP电脑的隔离的方法
对此我们首先需要获取局域网中所有电脑的MAC地址,并通过路由器实现静态IP分配,从而避免局域网IP地址冲突。
打开“运行”窗口,输入“CMD”进入MSDOS界面。
从打开的“MSDOS”界面中,输入命令“getmac”并按回车键,即可获取当前电脑所有无线网卡或有线网卡的MAC地址。
如图所示:接着进入路由器后台WEb管理界面,在此以华为无线路由器为例,切换到“家庭网络”-“LAN口设置”选项卡,展开“DHCP静态地址”栏目,点击“创建新的静态地址”按钮。
此时将列出当前局域网中所有计算机的MAC地址信息,根据特定的计算机MAC地址,勾选“启用”项以开启静态地址分配功能,同时设置与MAC绑定的IP地址,点击“确定”完成静态地址的添加操作。
利用同样的方法,可以添加多个静态IP地址。
通过以上方法,就可以有效解决局域网IP地址冲突的问题。
同时对于新加入的电脑,也需要在路由器中添加一种静态IP地址信息。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
IP Address Handoff in the MANETHongbo Zhou and Matt W. Mutka Dept. of Computer Science & Engineering Michigan State UniversityEast Lansing, Michigan, USA{zhouhon1, mutka}@Lionel M. NiDept. of Computer ScienceHong Kong University of Science & Technology Hong Kong SAR, Chinani@t.hkAbstract—When compared with a fixed host that is connected to a hardwired network, a mobile node in the MANET may change its IP address more frequently due to the deployment of autoconfiguration, global connectivity, and hierarchical addressing schemes. When an IP address changes, the performance of unicast routing protocols and real-time communications may degrade, and privacy may be compromised within the MANET. Although there have been some autoconfiguration algorithms proposed for the assignment of unique IP addresses to mobile nodes, the overhead resulting from address changes has not been carefully examined. Based on studies of the overhead caused by address change, an IP address handoff solution, which extends the unicast routing protocol and Network Address Translation (NAT) scheme, is proposed in the paper. The proposed approach is able to offset the overhead of broken routing fabrics and on-going communications, which is supported by our analysis and a prototype implementation.Keywords-handoff; IP address allocation; MANET; securityI.I NTRODUCTIONA Mobile Ad-hoc Network (MANET) is a temporary wireless network composed of mobile nodes without an infrastructure. A MANET may be suitable for networks within airports, meeting rooms, and open spaces due to both economical and technological feasibilities. Because the MANET is based upon IP protocol suites, a node in the MANET cannot take part in unicast communications until it is configured with a free IP address.Although it is simple to set IP addresses of mobile nodes in a small scale MANET, it becomes desirable for the procedure to be automatic for a large scale open MANET where mobile nodes are free to join and leave, which has motivated research efforts into the study of autoconfiguration in MANETs [1]-[8].Another problem associated with IP address assignment of a mobile node is that the IP address may change during its session in the MANET. IP address change is not a serious problem in hardwired networks because the IP address of a host is either statically configured or dynamically allocated by a DHCP server. It usually does not change its IP address during a session unless it reboots. However, because the nodes in the MANET are free to move arbitrarily, IP address change happens more frequently when applied with autoconfiguration, global connectivity, and hierarchical addressing schemes.There are several scenarios in which a mobile node will change its IP address:(1) Merger of two partitions of a networkIf some mobile nodes in the MANET move out of the transmission range of the other nodes, the network becomes partitioned as illustrated in Fig. 1(a). Because these nodes may not be aware of the partition, they may still use the previous allocated addresses. If the IP address of a node (say node A) in one partition is allocated to the new node (say node B) in the other partition, address conflict occurs when these two partitions become connected, as illustrated in Fig.1 (b). One example is when some attendants leave a meeting room for a short period and then return during a presentation session. The prophet address allocation is insensitive to this scenario [6] [7], while the nodes in one partition may need to change their addresses with DDHCP [5].Figure 1. A network is partitioned and then merged later(2) Merger of two independent MANETsThe second scenario is that two independently configured MANETs merge. Because these two networks are autoconfigured separately, there may be some duplicate addresses in both networks, such as node A in MANET 1 and node B in MANET 2 in Fig. 2. Thus, one needs to change its address due to the merger.Figure 2. Merger of two independent MANETs(3) Merger of a MANET with a LANThe work was supported in part by NSF Grants No. 0334035, 0098017, 9911074, NIH Grant No. EB002238-01, Hong Kong RGC Grants HKUST6161/03E and DAG02/03.EG02, and a grant from Microsoft Research.(b) (a)The third scenario is that a MANET merges with a LAN that has an “ad-hoc” mode Access Point (AP)1. The mobile nodes (such as node R in Fig. 3) that are within transmission range of the AP of the LAN may want to use the configuration information (e.g., a free IP address in the LAN and the default router) broadcast by the AP to configure itself and function as a relay node. As a result, the MANET becomes connected to the Internet [9] [10]. Furthermore, if the MANET and the LAN use the same private address range, there may be duplicate addresses in both the MANET and LAN, such as node A and node B in Fig. 3. Because the hardwired host in the LAN may not be willing to release its address, the node in the MANET will have to change its address.Figure 4. A MANET with hierarchical addressing schemeAlthough many autoconfiguration algorithms for MANETs have been proposed to allocate a mobile node a free IP address on its arrival in the MANET without an address conflict, few consider the issue of IP address change. To the best of our knowledge, this paper is the first effort to present a systematic solution for IP address handoff in the MANET.The paper is structured as follows. Section 2 discusses the overhead caused by IP address change of a mobile node during1For example, the AP from Ericsson is able to support both ad hoc and infrastructure modes simultaneously.its session in the MANET. Some related work on handoff schemes is introduced in Section 2 as well. However, none of these solutions can solve the problem systematically and satisfactorily. The solutions to remedy the overhead due to broken routing fabrics and on-going communications are presented in Section 3 and Section 4, respectively. Section 5 gives analytical evaluation of the performance and discusses its limitations, other scenarios and challenges to key management in MANETs. A prototype implementation and test are introduced in Section 6. Section 7 concludes the paper.II.I SSUES AND RELATED WORKThis section discusses the motivation for IP address handoff otherwise, they will send a Route Error (RERR) packet back to nodes A and E respectively, which triggers flooding of route rediscovery packets.In a more complicated topology, node C will have many neighbors and will be on many active paths. Thus, much overhead will incur for route maintenance.2) Broken on-going communicationsWhile referring to Fig. 5, suppose that node A is communicating with node E. If node E changes its address2The routing protocols that support multiple paths, such as DSR, are insensitive to the IP address change of a node along the path.)from u to v, the on-going communications between A and E will be broken, which does not meet the requirement of real-time multimedia applications.Because the address of u will not exist any longer (if the address change is not caused by address conflict), the local repair mechanism of AODV will fail eventually. As a result, the overhead of route rediscovery is inevitable. Even if node A initiates route rediscovery, it will not find the destination, unless the DNS scheme proposed in [13] is combined with the reactive routing protocol.An ad-hoc approach is that node E resumes the connection actively. However, because node E may be a server of an application (e.g., the user of node E is running a FTP server so that other participants of the meeting can download documents from him), it is not responsible for the initiation of communication. Furthermore, the application may run in the background or the user of node E may not be aware of the broken communication. Thus, we need a better solution.IP address change may compromise privacy as well. One example is the case of the merger of two MANETs. Suppose that node C is running a VoIP application with node B in MANET 2, as illustrated in Fig. 2. Because node B has the same address as node A in MANET 1, node B will change its address after the merger (for example, MANET 2 has a smaller NID [6] [7]). If node A keeps its address, the route maintenance procedure will rebuild the path between node C and node A. Thus, the voice data packets destined for node B will be redirected to node A. Suppose that node A is also running the VoIP application simultaneously, and that they use the same UDP ports. If the voice data packets are not encrypted, node C will talk with node A for a while until it realizes that it is speaking with a wrong party in the middle of the communication.B.Related workSeveral schemes have been proposed for IP address handoff in hardwired networks and MANETs. However, none of these approaches can solve the issue in the four aforementioned scenarios systematically and satisfactorily.1)Mobile IPMobile IP intends to provide basic support for mobile hosts in a LAN [14]. According to the scheme, a mobile host is assigned a permanent home address that is bound with its home agent. When it becomes connected to a foreign network, it receives a temporary care-of address and other information (e.g., the subnet mask and default router) from the foreign agent. The mobile host registers its current care-of address at its home agent, which then builds a tunnel between itself and the foreign agent. When another host initiates communication with the mobile host, it usually gets the mobile host’s home address from DNS query and sends the packets to the home address. The packets will be then forwarded to the mobile host’s care-of address by the home agent through the IP tunnel.Mobile IP is efficient for IP address handoff in a LAN that has an infrastructure. However, because the nodes in the MANET are mobile and instable, none of them can be designated as the home agent or foreign agent for another node. Thus, it cannot be applied in the MANET.2)Tunneling mechanismIn addition to autoconfiguration in the MANET, the scheme in [8] proposed a solution for the maintenance of communication states after address changes. The node (say node A) that changes its IP address notifies the other end (say node B) with a special Address Error (AERR) message. From then on, they communicate with each other through an IP-in-IP tunnel: the outer IP header contains the A’s new address, while the inner IP header contains A’s old address. Unlike the IP tunneling in Mobile IP, the communicating nodes A and B are also the end points of the tunnel: the source encapsulates the packet that is decapsulated at the destination.This approach is able to preserve communication states at both ends, but neglects the overhead caused by broken routing fabrics. Furthermore, it brings a “DoS” problem that will be discussed in Section 4.III.S OLUTIONS TO BROKEN ROUTING FABRICS Unlike the link breakage caused by node movement, the overhead of broken routing fabrics is due to IP address change of a node. Because the node may still be within the transmission range of its neighbors, and it is aware of the address change, a simple solution can be implemented to remedy this kind of overhead3.We assume AODV as the routing protocol. Suppose that node C changes its address from x to y, as illustrated in Fig. 5. Node C can notify all its neighbors (such as nodes B and E) of the address change. A new routing control packet, namely Route Shift packet, can be introduced into AODV scheme. The packet is a one-hop broadcast packet that contains the source’s old address and new address. On receipt of the packet, the neighbors change the next hop from x to y in all the routing entries with node C as the next hop.However, this solution is vulnerable to IP spoofing attacks, which are difficult to detect and prevent in MANETs that have no infrastructure. With the introduction of the Route Shift packet, a malicious node can impersonate another node and broadcast the packet to undermine the routing fabrics. We need a way to identify the source of the packet.One solution is to use a cryptographic method such as a digital signature, in which node C signs the Route Shift packet with its private key. All its neighbors contact the Certificate Authority (CA) to get the certificate for node C’s public key and validate the Route Shift packet. Although this method can defeat IP spoofing attacks, it brings delay and communication overhead.Our solution is that node C chooses a random number for its current address x, and puts the hash value of the number in the Route Request packet and Route Reply packet4 in transit, and periodical HELLO messages. All its neighbors store the3If the address change happens with link breakage simultaneously, the broken routing fabrics will be repaired with route maintenance.4 These routing control packets are not destined for node C itself.hash value in either their neighbor tables or routing tables. When node A changes its address, it puts the random number in the Route Shift packet. Because the packet is a one-hop broadcast packet, which will be received by its neighbors simultaneously, it is not vulnerable to the “man-in-the-middle” attack. If the hash value of the number contained in the Route Shift packet is equal to the stored hash value, the neighbors will be sure of the source of the packet. This method depends on the complexity of the hash function. MD5 [15] is such a good candidate that it is very difficult to determine the number from its hash value.IV.S OLUTIONS TO BROKEN COMMUNICATIONS The second type of overhead due to IP address change is the broken communications between the source and destination. We first provide the reasonable assumptions, and then describe the schemes for route rebuilding and communication states preservation.A.AssumptionsWe assume that the IP layer of the mobile node supports more than one IP address. Because we can bind at least two IP addresses with a NIC in most mainstream operating systems (e.g., Unix and Windows), we can assume that it is the same for mobile devices.With two IP addresses bound to the same interface, we specify that the new address as primary address and the old address as secondary address, and designate that the node use the primary address in the outgoing IP packets. Therefore, the node can still receive the packets destined for the old address for a short period, but the old address will not be used in the following new connections.In order not to trigger RERR packets sent from the neighbors of the changing node, we also need to extend the HELLO message to contain both the primary and secondary addresses for several intervals. However, to prevent the data packets destined for another node whose primary address is the same as its secondary address to be forwarded to it, the node must not reply to the Route Request (RREQ) packet for its old address.The second assumption is that the underlying links are bi-directional. Because most MAC layers deployed in MANETs confirm to 802.11 standard, our assumption can be easily satisfied.B.Route rebuildingSuppose that node A is communicating with node B and node A changes its address (say, from x to y) during the communication. Although node A can still receive the packets destined for its old address of x for a short period with the mechanism proposed above, we expect that the following communications be based upon the new address of y. However, because the new address has not been seen before, a broadcast of RREQ5from the other end is necessary to build the path towards it.5 The RREQ may be combined with a name query message.To save the overhead of route rediscovery, we resort to a gratuitous Route Reply (RREP) packet. Because the path to node B may be still valid, node A can send a RREP packet with its new address to node B, which generates valid routing entries backwards to A in the routing tables in the nodes along the path because underlying links are bi-directional (our assumption). The routing entries towards the old address of x will expire eventually.munication preservationThe most important problem in handoff processing is the preservation of communication states at end points. This is because the checksum in the transport layer is computed based upon the source and destination IP addresses and the transport layer will check the corresponding header in the IP packet against the communication states before delivering the data to the upper layer.Suppose that node A is communicating with node B, and that node A changes its address from x to y. We adopt an NAT mechanism running on both nodes to preserve the communication states:(1) At node A, the new destination address of y in the incoming packets is modified to the old address of x prior to delivering it to the transport layer, and the old source address in outgoing packets is modified to the new address before sending it to the link layer;(2) At node B, the new source address of y in the incoming packets is modified to the old address of x prior to delivering it to the transport layer, and the old destination address in the outgoing packets is modified to the new address before sending it to the link layer.Although the packets from node A to node B can contain A’s old source address of x, which does not affect forwarding policy and the routing fabrics, we still perform NAT on it for purpose of correct reporting of Route Error packets if the path from A to B becomes invalid due to node mobility.Compared with the tunneling mechanism proposed in [8], our approach has the following advantages:(1) The overhead of a second IP header is saved. Although the length of the IP header is only 20 bytes in IPv4 or 40 bytes in IPv6 (without any options), it may lead to fragmentation/defragmentation that is time-consuming;(2) Because only one address in the IP header is modified in NAT, it will be faster when applied with the improved computation of IP checksum [16];(3) The tunneling scheme brings a “DoS” problem as illustrated in Fig. 6. Suppose that node A has been communicating with node B before node A changes its address from x to y due to the address conflict with node C. An IP tunnel is built between B and A to redirect packets destined for A’s old address of x to its new address of y. If node C begins to communicate with B, the packets from B to C will also be forwarded to A through the tunnel, which means node C will never get any replies. Moreover, suppose that node B runs a TCP server application and listens at a well-known port. When node C initiates a connection from the same client port as nodeA, the connection between node A and node B will be reset due to the incorrect sequence number and TCP flags. Although the IP-in-IP tunnel scheme is simple, it cannot solve these problems.Figure 6. A “DoS” problem caused by IP tunnelingTo overcome these problems, our scheme extends NAT to utilize both port numbers and sequence numbers 6 to distinguish different connections at node B, which can be explained with an example below. Suppose that node B is a web server, and that node A is fetching web pages from B when it changes its address from x to y . An NAT table, such as Table 1, is built at node B to store the required information.TABLE I. NAT TABLE AT NODE B1 2 3 4 5 6Old remote address New remote address Local port Remote port Remote sequence number Next remotesequence numberx y 80 2030 228743 22884312… … … … … …The procedure at node B works as the following:(1) When node B receives a packet, before it delivers the packet to the transport layer, it checks the columns 2, 3, and 4 in the NAT table with the corresponding fields in the packet. If there is a match, there are three possibilities: a) the sequence number in the TCP header is equal to field 5 in the entry, which means the packet is either a retransmitted packet from node A or the first packet from node A since the entry was inserted into the NAT table. The new source address is modified to be the old address in field 1, and the next remote sequence number column is the sum of the remote sequence number and thepayload length; b) if the sequence number in the packet is equalto field 6 in the entry, which means the packet is a new packetfrom node A, the new address in the packet is modified to be the old address, the value in field 6 is copied to filed 5, and field 6 is increased by the payload length; c) if the sequence number is not equal to either, which means the packet comes from node C that has x as its primary address, the packet is discarded silently. In all the other cases, the packet is delivered to the upper layer intact.6Only a TCP header has a sequence number. For a UDP header, the sequence number can be regarded as 0, which is meaningless.(2) When node B has a packet for the destination address of x , before the packet is sent to the link layer, node B compares columns 1, 3, 4 and 6 in the NAT table and the corresponding fields in the packet to find a match 7. If there is such an entry, as the one in Table 1, the old destination address of x is changed to the new address of y , together with re-computation of the IP checksum; otherwise, the packet is sent intact.For UDP communications, because there is no sequence number in the UDP header, only the first four fields in the NAT table are used.Compared with node B, the processing at node A is simpler. Another NAT table, such as Table 2 is used. If the local port number in the packet is equal to one in the table, the old address is modified to the new address in the outgoing packets, and vice versa for incoming packets.TABLE II.NAT TABLE AT NODE A Old addressNew addressPort numberx y 2030 x y …Because node A changes its own address, it is trivial for it to insert the entry when it has a packet to send. The problem remains that how the entry is inserted at node B’s NAT table. A special message, Address Change Message (ACM), can be sent from node A to B indicating the creation of the NAT entry,which includes the old address, new address, protocol (UDP or TCP), local port, remote port, and sequence number (TCP only). The next remote sequence number in B’s NAT table is initialized as zero, and will be filled by the following TCP data packets. To save communication overhead further, the messagecan be combined with the gratuitous RREP packet mentionedin route rebuilding.The ACM packet must be sent before any data packets fornode B. If node A is going to send a packet immediately after the address change, the data packet can be buffered before sending of the ACM packet. If node A has nothing to send immediately after address change, it waits for data packets from node B. Although node B has not been informed of A’s address change, according to our assumption, the route from node B to node A with the old address will be valid for a short period. Thus, the data packet can still arrive at node A, which triggers an ACM packet sent to B. To remove the entry, the TCP flag of FIN can be examined. For UDP entries, an expiration time can be associated with each of them. The entry is refreshed with UDP data packets and removed when it expires. The timeout method could also be utilized for TCP entries in case that the FIN packet is lost on transit or the other end shuts down abruptly. To prevent IP spoofing attacks, the ACM packet must be signed with node A’s private key. Therefore, the contents can be validated with A’s public key at node B.7The acknowledge number in the packet is compared with the next remotesequence number in the NAT table.MANETA (x →y )BC (x )V.P ERFORMANCE EVALUATION AND DISCUSSION This section analyzes the performance, limitations, otherscenarios, and challenges of the handoff scheme.A.Performance analysisSuppose that there are n nodes in the MANET with l links. The average degree of a node is d (=l/n). Node A, which changes its IP address, has k connections with m nodes and on p active paths. The average length of the path is q. In a MANET where the mobile nodes are distributed evenly, we can assume that l >> n >> q, n >>d, and n > m;As analyzed before, there are two kinds of overheads:1)Overhead of broken routing fabricsWithout the handoff scheme, the active paths going through node A will become invalid. As a result, at least one end of each path will initiate route rediscovery if the local repair mechanism is not utilized, which means there will be at least p times of flooding throughout the MANET. If no flooding optimization is adopted, the same packet will be forwarded by all the nodes once. Thus, there will be 2l packets for one flooding. As a result, there will be at least 2pl packets caused by broken routing fabrics.With the introduction of the Route Shift packet, which is a one-hop broadcast packet, only d packets are generated.2)Overhead of broken communicationsWithout the handoff scheme, the m nodes that communicate with node A will perform route rediscovery. Therefore, 2ml packets will be generated to find the path towards node A.With the introduction of a gratuitous RREP packet and the ACM packet, only (m+k)q unicast packets are necessary to rebuild the route and insert NAT table entries. If RREP and ACM are combined, the number of packets is decreased to kq.B.LimitationsIf node A wants to communicate with node C as in Fig. 6, because C’s primary address of x has been bound with A’s NIC as the secondary address, all the packets from A to C will be regarded as local packets. Thus, they cannot communicate with each other until node A does not use the secondary address any longer.As discussed in the section above, to distinguish TCP connections from node A (that changes its address) and node C (that has the same primary address), node B utilizes both port numbers and sequence number in the TCP header. If node C connects to node B’s well-known port from the same port number after node A changes its address, the connection will be rejected. If the client port is dynamically allocated, as most application programs do, node A and node C may have different local ports.On the contrary, node B may connect to C’s well-known port after it has connected with A’s same port (for example, node B is browsing A and Cs’ homepages at the same time) and A has changed its address. If the client port is dynamically allocated, B will have different local port numbers, which will not be affected by our scheme. If node B binds the local port in the program, because the acknowledgement number in the connection with node A is usually different from the one in the connection with node C, the communication will not be affected either. However, if the acknowledgement number is the same, its NAT module will redirect the connection.With regard to UDP communication, because there is no sequence number in the UDP header, if nodes A and C use the same local client port number, the packets for C will be redirected to A. Furthermore, because there are no connection flags, UDP communication between nodes A and B will be forced to break if there has not been any data exchange for a long period after creation of the NAT entry.Another limitation is that if there is no data exchange between node A and B for a while immediately after A changes its address, the path from B to A will be invalid due to node mobility. Thus, a route rediscovery combined with name query from node B is inevitable. However, this problem can be solved if node A actively sends an ACM packet for each pre-existing connection.C.Multiple address changesOur scheme can be applied to multiple address changes without any significant modifications.Suppose that the source node changes its IP address twice during the session, without loss of generality. After the first address change, the NAT tables have been built at both the source and destination to change the secondary address in the data packets to primary address and back forth. When the second address change happens, because the IP layer supports more than one IP address, the old primary address can be “pushed back” to be the second secondary address.The solution for broken routing fabrics can be utilized as usual. As to broken on-going communications, if the communication was initiated with the second secondary address (between the first and the second address change), new NAT entries will be created. However, for the communications initiated with the first secondary address (before the first address change), it must be associated with the up-to-date primary address. To solve this problem, noting that the primary address is mainly used for purpose of routing, we just need to modify the new address field of corresponding entries at both the source and destination.Thus, for all the existing NAT entries at the source node, when a second address change happens, a special flag can be set for each entry in addition to modification of new address field (Table 2). When an outgoing data packet has a matching local port number, an ACM message is sent to the destination, and the flag can be cleared. On receipt of this second ACM message, the destination modifies its NAT table to reflect the change.D.Address changes at both source and destinationIf both of the source and destination change their IP addresses simultaneously, because their old addresses are bound with them as secondary addresses, the ACM messages or data packets from either node with the old destination。
