DSL implementation in MetaOCaml, Template Haskell, and C
华为DSLAM架构与业务原理基础知识

华为DSLAM架构与业务原理基础知识华为DSLAM(Digital Subscriber Line Access Multiplexer)是用于数字用户线路接入的设备,主要用于将来自多个用户的DSL(Digital Subscriber Line)信号进行集中处理和转发,以提供高性能的宽带接入服务。
DSLAM的架构华为DSLAM的架构主要分为物理层和逻辑层。
物理层:物理层包括用户接口,线路接口、交换接口、传输接口等。
用户接口用于与用户设备(如ADSL调制解调器)进行连接,线路接口用于与传输线路连接,交换接口用于与核心网络设备连接,传输接口用于与运营商传输设备连接。
逻辑层:逻辑层包括系统管理和业务处理。
系统管理层负责设备的配置管理、性能管理和故障管理等;业务处理层负责接收用户的请求,分析用户需求并进行相应的业务处理。
华为DSLAM的逻辑层采用分布式架构,可以实现高扩展性和可靠性。
DSLAM的业务原理DSLAM的主要功能是将来自用户设备的DSL信号进行集中处理,并将数据转发到核心网络。
DSL信号传输主要有ADSL (Asymmetric Digital Subscriber Line)、VDSL(Very-high-speed Digital Subscriber Line)等多种方式。
DSLAM通过用户接口与用户设备通信,接收用户设备发送的DSL信号。
对于ADSL信号,DSLAM将用户设备发送的上行信号和下行信号进行分离,并按照不同的业务要求进行处理,然后将数据转发至核心网络。
对于VDSL信号,DSLAM可以提供更高的传输速率和更长的传输距离,可以满足用户对高速宽带的需求。
华为DSLAM支持多种业务类型,包括宽带接入、IP电话、视频监控等。
通过业务处理模块,DSLAM可以根据用户需求进行不同的业务处理。
例如,在宽带接入业务中,DSLAM可以根据用户的带宽需求,对数据进行分配和计量,并提供相应的服务质量保证。
KT0913_datasheet_V1.2
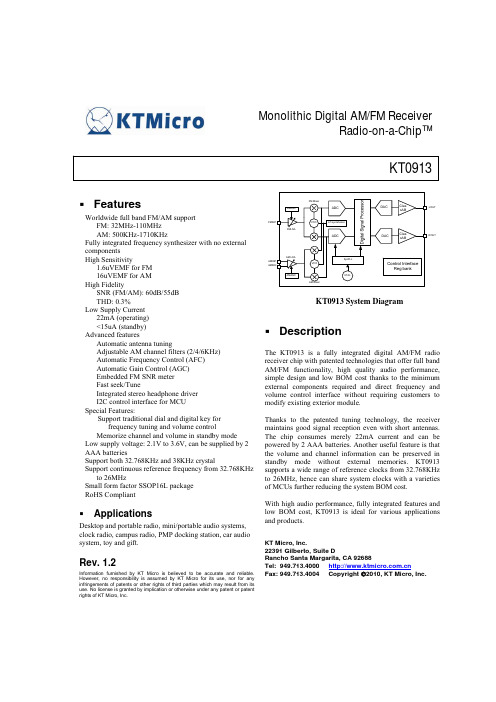
Monolithic Digital AM/FM Receiver Radio-on-a-Chip™KT0913FeaturesWorldwide full band FM/AM support FM: 32MHz-110MHz AM: 500KHz-1710KHz Fully integrated frequency synthesizer with no external components High Sensitivity 1.6uVEMF for FM 16uVEMF for AM High Fidelity SNR (FM/AM): 60dB/55dB THD: 0.3% Low Supply Current 22mA (operating) <15uA (standby) Advanced features Automatic antenna tuning Adjustable AM channel filters (2/4/6KHz) Automatic Frequency Control (AFC) Automatic Gain Control (AGC) Embedded FM SNR meter Fast seek/Tune Integrated stereo headphone driver I2C control interface for MCU Special Features: Support traditional dial and digital key for frequency tuning and volume control Memorize channel and volume in standby mode Low supply voltage: 2.1V to 3.6V, can be supplied by 2 AAA batteries Support both 32.768KHz and 38KHz crystal Support continuous reference frequency from 32.768KHz to 26MHz Small form factor SSOP16L package RoHS CompliantFMINP FMLNA FM Mixer FMAGCADCDACClas sABLOUTVCOLO syntehsizerADCDACClas sABROUTAM LNA AMINP AMINN VCOSysPLLControl Interface Reg bankAMAGC AM MixerXTALKT0913 System DiagramDescriptionThe KT0913 is a fully integrated digital AM/FM radio receiver chip with patented technologies that offer full band AM/FM functionality, high quality audio performance, simple design and low BOM cost thanks to the minimum external components required and direct frequency and volume control interface without requiring customers to modify existing exterior module. Thanks to the patented tuning technology, the receiver maintains good signal reception even with short antennas. The chip consumes merely 22mA current and can be powered by 2 AAA batteries. Another useful feature is that the volume and channel information can be preserved in standby mode without external memories. KT0913 supports a wide range of reference clocks from 32.768KHz to 26MHz, hence can share system clocks with a varieties of MCUs further reducing the system BOM cost. With high audio performance, fully integrated features and low BOM cost, KT0913 is ideal for various applications and products.KT Micro, Inc. 22391 Gilberto, Suite D Rancho Santa Margarita, CA 92688 Tel: 949.713.4000 Fax: 949.713.4004 Copyright ©2010, KT Micro, Inc.ApplicationsDesktop and portable radio, mini/portable audio systems, clock radio, campus radio, PMP docking station, car audio system, toy and gift.Rev. 1.2Information furnished by KT Micro is believed to be accurate and reliable. However, no responsibility is assumed by KT Micro for its use, nor for any infringements of patents or other rights of third parties which may result from its use. No license is granted by implication or otherwise under any patent or patent rights of KT Micro, Inc.Table of Content1. Electrical Specification............................................................................................................................ 4 2. Pin List .................................................................................................................................................... 6 3. Function Description ............................................................................................................................... 7 3.1. Overview ............................................................................................................................................. 7 3.2. FM Receiver........................................................................................................................................ 7 3.3. AM Receiver ....................................................................................................................................... 7 3.4. Operation Bands................................................................................................................................. 7 3.5. Standby ............................................................................................................................................... 7 3.6. Crystal and reference clock............................................................................................................... 8 3.7. Digital Signal Processing ................................................................................................................... 8 3.7.1. FM Stereo Decoder ........................................................................................................................ 8 3.7.2. Mute / Softmute.............................................................................................................................. 8 3.7.3. Stereo / Mono Blending ................................................................................................................. 9 3.7.4. Bass ................................................................................................................................................ 9 3.7.5. Stereo DAC, Audio Filter and Driver............................................................................................. 9 3.7.6. AM Bandwidth............................................................................................................................... 9 3.7.7. TUNE ............................................................................................................................................. 9 3.7.8. SEEK.............................................................................................................................................10 3.8. User-Machine Interface ....................................................................................................................10 3.8.1. Programmable band.......................................................................................................................10 3.8.2. Key Mode......................................................................................................................................10 3.8.3. Dial Mode......................................................................................................................................11 3.9. I2C Control Interface .......................................................................................................................13 3.10. Register Bank ....................................................................................................................................15 3.10.1. CHIP ID (Address 0x01)...............................................................................................................16 3.10.2. SEEK (Address 0x02) ...................................................................................................................16 3.10.3. TUNE (Address 0x03)...................................................................................................................16 3.10.4. VOLUME (Address 0x04) ............................................................................................................16 3.10.5. DSPCFGA (Address 0x05) ...........................................................................................................17 3.10.6. LOCFGA (Address 0x0A) ............................................................................................................18 3.10.7. LOCFGC (Address 0x0C).............................................................................................................18 3.10.8. RXCFG (Address 0x0F)................................................................................................................18 3.10.9. STATUSA (Address 0x12) ...........................................................................................................19 3.10.10. STATUSB (Address 0x13) ...........................................................................................................19 3.10.11. STATUSC (Address 0x14) ...........................................................................................................19 3.10.12. AMSYSCFG (Address 0x16)........................................................................................................20 3.10.13. AMCHAN (Address 0x17) ...........................................................................................................21 3.10.14. AMCALI (Address 0x18) .............................................................................................................21 3.10.15. GPIOCFG (Address 0x1D) ...........................................................................................................21 3.10.16. AMDSP (Address 0x22) ...............................................................................................................21 3.10.17. AMSTATUSA (Address 0x24).....................................................................................................22 3.10.18. AMSTATUSB (Address 0x25) .....................................................................................................22 3.10.19. SOFTMUTE (Address 0x2Eh)......................................................................................................22 3.10.20. USERSTARTCH (Address 0x2F).................................................................................................23 3.10.21. USERGUARD (Address 0x30).....................................................................................................23 3.10.22. USERCHANNUM (Address 0x31) ..............................................................................................23 3.10.23. AMCFG (Address 0x33) ...............................................................................................................24 3.10.24. AMCFG2 (Address 0x34h) ...........................................................................................................24 3.10.25. VOLGUARD (Address 0x3Ah) ....................................................................................................24 3.10.26. AFC (Address 0x3Ch)...................................................................................................................25 4. Typical Application Circuit ....................................................................................................................26 5. Package Outline......................................................................................................................................27 6. Revision History.....................................................................................................................................28Copyright ©2010, KT Micro, Inc.27.Contact Information................................................................................................................................28Copyright ©2010, KT Micro, Inc.31. Electrical SpecificationParameter Power Supply Ambient Temperature Symbol AVDD Ta Table 1: Operation Condition Operating Condition Min Relative to AVss 2.1 -30 Table 2: DC Characteristics Symbol Test/Operating Min Condition IFM IAM IAPD Typ 3.3 25 Max 3.6 70 Units V ℃Parameter Current Consumption Standby Current FM Mode AM ModeTyp 21.3 22 14.5Max -Units mA mA μATable 3: FM Receiver Characteristics (Unless otherwise noted Ta = -30~70℃, AVDD= 2.1V to 3.6V) Parameter Symbol Test/Operating Min Typ Max Condition FM Frequency Range Frx 110 32 Sensitivity1,2,3 Sen (S+N)/N=26dB 1.6 2 Input referred 3rd Order IIP3 85 Intermodulation Production4,5 Adjacent Channel Selectivity 35 51 ±200KHz Alternate Channel Selectivity 50 70 ±400KHz Image Rejection Radio 35 AM suppression 50 RCLK frequency 32.768 32.768 26000 RCLK frequency Range8 -100 100 Audio Output Voltage1,2,3,4 32ohm load 90 100 110 Audio Band Limits1,2,4 30 15k ±3dB 1,4,6 Audio Stereo Separation 35 Audio Mono S/N1,2,3,4 55 60 Audio Stereo S/N1,4,6,7 DBLND=1 64 Audio THD1,2,4,6 0.3 De-emphasis Time Constant DE=0 75 DE=1 50 Audio Common Mode Voltage 0.85 Audio Output Load Resistance RL Single-ended 32 Seek/Tune Time 50 Power-up Time 600 Notes: 1. FMOD=1KHz, 75us de-emphasis 2. MONO=1 3. △F=22.5KHz 4. VEMF=1mV, Frequency=32MHz~110MHz 5. AGCD=1 6. △F=75KHz 7. VOLUME<4:0>=11111 8. The supported RCLK frequency is not continuous. Please refer to application notes.Units MHz uVemf dBuVE MF dB dB dB dB KHz ppm mVRMS Hz dB dB dB % μs μs V Ω ms msCopyright ©2010, KT Micro, Inc.4Table 4: AM Receiver Characteristics (Unless otherwise noted Ta = -30~70℃, AVDD= 2.1V to 3.6V) Parameter Symbol Test/Operating Min Typ Condition AM Frequency Range Frx 500 Sensitivity1,2 Sen (S+N)/N=26dB 15 Audio Output Voltage1,2,3,4 32ohm load 60 Audio Mono S/N1,2,3,4 55 Audio THD1,2,4,6 0.3 Antenna inductance L 280 350 Notes: 1. FMOD=1KHz 2. Modulation index is 30% 3. VEMF=1mV, Frequency=500KHz~1710KHz 4. VOLUME<4:0>=11111Max 1710Units KHz uVemf mVRMS dB % uH0.6 420Copyright ©2010, KT Micro, Inc.52. Pin ListTable 5: Pin listPin Num 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16Pin Name CH DVSS ROUT LOUT AVSS AVDD XI/RCLK XO ENABLE AMINN AMINP RFINP RFGND SCL SDA VOLDescription Channel adjustment. Digital ground. Right channel audio output. Left channel audio output. Analog ground. Power supply. Crystal input/Reference clock input. Crystal output. Chip enable. Tied to an internal 600kohm pull down resistor. AM RF negative input. AM RF positive input. FM RF input. RF ground. SCL of I2C interface. Tied to an internal 47kohm pull-up resistor. SDA of I2C interface. Tied to an internal 47kohm pull-up resistor. Volume adjustment.Figure 1: KT0913 Pin assignment (Top view)Copyright ©2010, KT Micro, Inc.63. Function Description3.1. OverviewKT0913 offers a true single-chip, full-band FM/AM and versatile radio solution by minimizing the external components and offering a variety of configurations.3.2. FM ReceiverKT0913 enters FM mode by setting register AM_FM to 0. The FM receiver is based on the architecture of KT Micro’s latest generation FM receiver chips in mass production. There are no external filters or frequency-tuning devices thanks to a proprietary digital low-IF architecture consisting of a fully-integrated LNA, an automatic gain control (AGC), a set of high-performance ADCs, high-quality analog and digital filters, and an on-chip low-noise self-tuning VCO. The on-chip high-fidelity Class-AB driver further eliminates the need for external audio amplifiers and can drive stereo headphones directly.3.3. AM ReceiverKT0913 enters AM mode by setting register AM_FM to 1. The AM Receiver employs a similar digital low IF architecture and share many circuits with the FM receiver. The AM receiver supports a wide band from 500KHz to 1710KHz also known as the popular AM bands. The AM channel spacing can be set to 1KHz, 9KHz or 10KHz to address different applications. The bandwidth of the channel filter can be set to 2KHz, 4KHz or 6KHz to suit various requirements. The AM receiver in KT0913 can provide accurate and automatic AM tuning without manual alignment. It supports 350uH ferrite loop antenna with +/- 25% tolerance.3.4. Operation BandsKT0913 supports wide FM band and AM bands. The FM receiver covers frequencies from 32MHz to 110MHz. The 32MHz to 64MHz is defined as Campus Band in KT0913 and can be enabled by setting CAMPUSBAND_EN register to 1. The AM band is from 500KHz to 1710KHz.3.5. StandbyKT0913 supports both Software Standby mode and Hardware Standby mode. To enter Software Standby, the STANDBT register shall be set to 1 through I2C interface. To enter Hardware Standby, the ENABLE pin is pulled down to ground. In the standby modes, the internal state (channel, volume) is preserved and can be recovered when the chip wakes up from the standby.Copyright ©2010, KT Micro, Inc.73.6. Crystal and reference clockKT0913 integrates a low frequency crystal oscillator that supports 32.768KHz and 38KHz crystals. Alternatively a CMOS level external reference clock may be used by setting the RCLK_EN register to 1 and setting REFCLK<3:0> according to the frequency of the reference clock.3.7. Digital Signal Processing3.7.1. FM Stereo DecoderThe digitized IF signal is fed to the FM demodulator which demodulates the signal and outputs a digital multiplexed (MPX) signal consisting of L+R audio, L-R audio, 19KHz pilot tone and RDS signal. The left channel signal and the right channel signal can be extracted from the MPX signal by simply adding and subtracting the L+R signal and L-R signal. The spectrum diagram is shown in Figure 2.Figure 2: Spectrum diagram of the MPX signal3.7.2. Mute / SoftmuteKT0913 can be hard muted by setting DMUTE to 0 and the output of the audio signal is set to the common mode voltage. There is also a Soft Mute feature that is enabled by setting FMDSMUTE to 0 in FM mode and AMDSMUTE to 0 in AM mode. In this mode, the audio volume is gradually attenuated when the signal reception is bad (i.e. when the RSSI is below a certain level as defined by FM_SMTH<2:0> and AM_SMTH<2:0>, respectively.) The attenuation attack rate and depth can be configured through SMUTER<1:0> and SMUTEA<1:0>, Copyright ©2010, KT Micro, Inc. 8respectively. The target volume can be configured through VOLUMET<4:0>. SNR value can also be used as the judgment threshold in FM mode by setting SMMD to 1.3.7.3. Stereo / Mono BlendingIn order to provide a comfortable listening experience, KT0913 blends the stereo signal with mono signal gradually when in weak reception in FM mode. The signal level range over which the blending occurs is set by BLNDADJ<1:0>. The blending is disabled when DBLND is set to 1. MONO playback mode can be forced by setting the MONO to 1. If the MONO bit and the INV_LEFT_AUDIO bit are both set to 1, then a fully differential signal will be output at the LOUT and ROUT.3.7.4. BassKT0913 provides bass boost feature for audio enhancement. The gain of the bass boost can be programmed through BASS<1:0>. With BASS<1:0>=00, this feature is disabled.3.7.5. Stereo DAC, Audio Filter and DriverTwo high-quality single-bit ΔΣ audio digital-to-analog converters (DAC) are integrated along with high-fidelity analog audio filters and class AB drivers. Headphones with impedance as low as 16ohms can be directly driven without adding external audio drivers. An integrated anti-pop circuit suppresses the click-and-pop sound during power up and power down. For different load capacitor, user can set different anti-pop configuration through POP<1:0>.3.7.6. AM BandwidthKT0913 provide programmable AM channel bandwidth through AM_BW<1:0>.3.7.7. TUNEThe fully integrated LO synthesizer supports wide band operation. Channel tuning is started when the register AMTUNE/FMTUNE is set to 1. In FM mode, the channel frequency is set by FMCHAN<11:0> and is defined as Freq(MHz) = 50KHz × FMCHAN<11:0> In AM mode, the channel frequency is set by AMCHAN<10:0> and is defined as Freq(KHz) = 1KHz × AMCHAN<10:0>Copyright ©2010, KT Micro, Inc.93.7.8. SEEKKT0913 offers an effective software based seek algorithm. Refer to application notes for more information.3.8. User-Machine InterfaceChannel and volume can be adjusted not only by setting corresponding FMCHAN, AMCHAN and VOLUME registers, but also by using built-in user-machine interface. Two types of user-machine interface, Key Mode and Dial Mode, are provided by KT0913. In these modes, the channel and volume are controlled by KT0913 itself.3.8.1. Programmable bandKT0913 supports programmable arbitrary frequency range of the operation band by setting register USERBAND to 1. Information of the current band, such as AM/FM mode, upper and lower edge of the band, channel step and the number of guard channel used in Dial Mode, should be written to KT0913 once the band is chosen, which is sensed by MCU. The number of channels and start channel are defined in register USER_CHAN_NUM<11:0> and USER_START_CHAN<14:0>. In FM mode, where register AM_FM is set to 0, the lower and upper bound of the current band can be express as: f bot = USER _ START _ CHAN < 14 : 0 > ×50 KHzf top = f bot + USER _ CHAN _ NUM < 11 : 0 > × f step Where f step is the channel step, which can be configured by register FMSPACE<1:0>. In AM mode, where register AM_FM is set to 1, the corresponding lower and upper bound of the band are: f bot = USER _ START _ CHAN < 14 : 0 > ×1KHzf top = f bot + USER _ CHAN _ NUM < 11 : 0 > × f stepWhere f step is the channel step, which can be configured by register AMSPACE<1:0>.3.8.2. Key ModeKT0913 allows user to control the channel and volume by using keys/buttons to send digital control signals to CH and VOL pins. Please refer to Section 4 for a typical application circuit. The key mode is enabled by setting GPIO1<1:0> and GPIO2<1:0> to 01.Copyright ©2010, KT Micro, Inc.10Each time VOLP/VOLM key is pressed, the volume increases/decreases by 2dB. If the VOLP/VOLM key is pressed and held, the volume will continue to increase/decrease at 2dB steps until the key is released. When configured in Key Mode, KT0913’s channel selection has two working modes. Mode A: If KEY_MODE<1:0> is set to 00, Mode A is selected. In this mode, each time the CHP (CHM) is pressed, the channel frequency increases (decreases) by one step. The step sizes are defined by FMSPACE<1:0> and AMSPACE<1:0>. If the CHP (CHM) key is pressed for and held for a certain time (defined by TIME1<1:0>), the channel frequency will continue to increase (decrease) automatically at a certain pace (as defined by TIME2<2:0>) until the key is released. Mode B: If KEY_MODE<1:0> is set to 01, Mode B is selected. In this mode, each time the CHP (CHM) is pressed, the channel increases (decreases) by one step. The step sizes are defined by FMSPACE<1:0> and AMSPACE<1:0>. If the CHP (CHM) key is pressed and held for a specific time (TIME1<1:0>), the channel will continue to increase (decrease) automatically at a certain pace (TIME2<2:0>) even if the key is released. The movement is stopped when the key is pressed again.3.8.3. Dial ModeKT0913 supports a unique Dial Mode whose application circuit is shown in Figure 3. The dial is implemented by a variable resistor with the center tap connected to the chip. KT0913 measures the divider ratio of two parts of the variable resistor and maps the result to the real control parameters, such as channel frequency, volume, etc. The channel controller enters dial mode by setting register GPIO1<1:0> to 10. The illustration circuit is shown in Figure 3 错误!未找到引用源。
DCS常见英文缩写

DCS系统常见英文缩写HMI —Human Machine Interface (人机界面)HTML —Hyper Text Markup Language (超文本链接标示语言)CM —— Control Module控制模块SCM ----- Sequential Control Module 顺序控制模块CPM ----- Control Processing Module (控制处理模块)CEE ----- C ontrol Execution Environment 控制执行环境CNI ------ C ontrol Net Interface 控制网络接口C200 ----- Control processor 控制处理器RM ------ R edundancy Module 冗余模块lOMs ---- input/output Modules 输入/输出模块SCE ------ Simulation Control Module 模拟控制模块ACE ----- Application Control Module |应用控制模块IOLIM ------ IO Link Interface Module 接口模块FIM ------ F ieldbus Inerface Module 现场总线模块PMIO —Process Manager Input/Output 流程管理器输入/输出FTA-Field Termination AssembliesIOP ------ I nput/Output Processor (card)■输入/输出处理器(卡)ERDBEngineering Repository Database 工程数据库EMDB —Enterprise model database 企业模型数据库RTDB —Real Time Database 实时数据库ODBC —Open Database Connectivity 开放式数据库连接SQL —Structured Query Language 结构化查询语言PV —Process Value 工艺价值SCADA —Supervisory control and data acquisition监督控制和数据采集FTE-fault tolerant Ethernet 容错以太网CP-control processor 控制处理器CNI-control net interface 控制网接口FTEB-fault tolerant Ethernet bridge 容错以太网桥RM-redundancy module 冗余模块FIM-fieldbus interface module 现场总线接口模块OPC-OLE for process control 用于过程控制ACE-application control environment (应用控制环境) DSA-distributed system architecture 分布式系统架构CEE-control execute environment 控制执行环境ES-CE --Console Extension Station 控制扩展控制站ES-F --Experion Flex Station ES-C --Experion Console StationFTA--Field Termination Assembly (for Serial Interface) CDAserver : Contorl Data Access Server 控制数据接入服务器OPC :OLE for process controlDSA :disbuted system Architecture 分布式系统结构FTE :fault tolerant Ethernet 容错以太网RTD :热电阻T/C :热电偶PIM :pulse Input Module 脉冲输入模块SIM :Serial Interface Module 串口接口模块DCS 画面常用常用缩写词语1ST1 级FRQ 频率A 报警FSH 末级过热器ADS 自动调度系统FSSS 炉膛安全监测系统AGC 自动发电机控制FW 给水AH 空气预热器FWP 给水泵AS 轴向位移GC 高压调门控制ATC 汽轮机自动控制GEN 发电机AUTO 自动GV (高压)调节汽门AUX 辅助的I 11 iHH 高高BASE 基本HAV 暖通BCP 炉水循环泵HDR 联箱,集箱BD 排污HP 高压缸BF 锅炉跟随HTR 加热器BFP 锅炉给水泵IC 中压调门控制BMCR 锅炉最大连续出力ID 标志,标识BMP 燃烧器管理系统IDF 引风机BOP 轴承油泵IMP 冲动式(级)BP 旁路INCR 提高,增加BRG 轴承INTERM 定期,间断BTG 锅炉-汽机-发电机IV 中压调门C 切换LL 低低CAF 冷却风机LDC 负荷指令计算机CAMP 控制+报警+监测+保护LOP 顶轴油泵CCCW 闭式循环冷却水Lp 低压CCS 协调控制系统LSH 低温过热器CDSR 凝汽器LUB 润滑油COND 凝结MANU 手动(方式)CON 连续的MCR 最大连续出力COOR 连续的MCS 模拟量控制系统CORR 校正,修正MEH 小型汽轮机电液调节CRT 显示器MFT 主燃料失去保护CRH 低温再热器MIN 最小CSH 包覆过热器MS 主蒸汽CW 循环水MW 兆瓦D NO 编号,第。
Synopsys OptoDesigner 2020.09安装指南说明书

3. Troubleshooting scanning issues........................................................25
Accidental full scan proliferation by folder paths which include build or commit ID............................ 25 Solution......................................................................................................................................25
Contents
Contents
Preface....................................................................................................5
1. Scanning best practices......................................................................... 8
DIgSILENT Simulation Language DSL Workshop presentatio教程
DIgSILENT GmbH
Overview
• DIgSILENT Simulation Language (DSL)
• DSL can describe:
– every linear or nonlinear system of differential equations. – dead times (e.g. ideal wave equations) – every arithmetic or logic expression (e.g. digital controllers). – every event (e.g. open breaker if x>y).
dx1 dt
=
x1
+
x2
+
dx2 dt
=
x1
− x2
+
yi
• General, Explicit System of Differential Equations:
xyrr&o==frgr((xrxr,,yryri i))
DSL Workshop, Dynamic Modeling
6
Example of a system / process: Steam Turbine
• A DSL model can be represented graphically.
• Macros are used to define: algebraic equations, basic control elements like PID, PTn or even complete physical subsystems like valve groups or excitation systems.
01-ATM和DSL接口命令

目录1 ATM和DSL接口配置命令...................................................................................................................1-21.1 ATM和DSL接口公共命令..................................................................................................................1-21.1.1 display interface atm..............................................................................................................1-21.1.2 interface atm...........................................................................................................................1-31.1.3 reset atm interface..................................................................................................................1-41.2 IMA-E1/T1接口配置命令..................................................................................................................1-41.2.1 cable.......................................................................................................................................1-41.2.2 clock.......................................................................................................................................1-51.2.3 code........................................................................................................................................1-61.2.4 differential-delay.....................................................................................................................1-61.2.5 display interface ima-group....................................................................................................1-71.2.6 frame-format...........................................................................................................................1-81.2.7 frame-length...........................................................................................................................1-91.2.8 ima ima-group.......................................................................................................................1-101.2.9 ima-clock..............................................................................................................................1-111.2.10 ima-standard.......................................................................................................................1-111.2.11 ima-test...............................................................................................................................1-121.2.12 interface ima-group............................................................................................................1-131.2.13 loopback.............................................................................................................................1-131.2.14 min-active-links...................................................................................................................1-141.2.15 scramble.............................................................................................................................1-151.2.16 reset counters interface......................................................................................................1-151.3 ATM E3/T3接口配置命令...............................................................................................................1-161.3.1 cable.....................................................................................................................................1-161.3.2 clock.....................................................................................................................................1-171.3.3 frame-format.........................................................................................................................1-171.3.4 loopback...............................................................................................................................1-181.3.5 scramble...............................................................................................................................1-191.4 ATM OC-3c/STM-1接口配置命令...................................................................................................1-191.4.1 clock.....................................................................................................................................1-191.4.2 frame-format.........................................................................................................................1-201.4.3 loopback...............................................................................................................................1-201.4.4 scramble...............................................................................................................................1-211.4.5 threshold...............................................................................................................................1-221.5 ADSL接口配置命令.........................................................................................................................1-231.5.1 activate.................................................................................................................................1-231.5.2 adsl standard........................................................................................................................1-231.5.3 adsl tx-attenuation................................................................................................................1-241.5.4 bootrom update file...............................................................................................................1-251.5.5 display dsl configuration.......................................................................................................1-261.5.6 display dsl status..................................................................................................................1-271.5.7 display dsl version................................................................................................................1-281.6 G.SHDSL接口配置命令...................................................................................................................1-301.6.1 activate.................................................................................................................................1-301.6.2 display dsl configuration.......................................................................................................1-311.6.3 display dsl status..................................................................................................................1-32 1.6.4 display dsl version................................................................................................................1-36 1.6.5 shdsl annex..........................................................................................................................1-37 1.6.6 shdsl mode...........................................................................................................................1-37 1.6.7 shdsl pbo..............................................................................................................................1-38 1.6.8 shdsl psd..............................................................................................................................1-39 1.6.9 shdsl rate..............................................................................................................................1-39 1.6.10 shdsl snr-margin.................................................................................................................1-40 1.6.11 shdsl wire............................................................................................................................1-41本文中标有“请以实际情况为准”的特性描述,表示各型号对于此特性的支持情况可能不同,本节将对此进行说明。
TCG_Storage-Opal_SSC_v2.01_rev1.00

TCG StorageSecurity Subsystem Class: OpalSpecification Version 2.01Revision 1.00August 5, 2015Contact: admin@ PUBLISHEDCopyright © TCG 2015Copyright © 2015 Trusted Computing Group, Incorporated.Disclaimers, Notices, and License TermsTHIS SPECIFICATION IS PROVIDED “AS IS” WITH NO WARRANTIES WHATSOEVER, INCLUDING ANY WARRANTY OF MERCHANTABILITY, NONINFRINGEMENT, FITNESS FOR ANY PARTICULAR PURPOSE, OR ANY WARRANTY OTHERWISE ARISING OUT OF ANY PROPOSAL, SPECIFICATION OR SAMPLE.Without limitation, TCG disclaims all liability, including liability for infringement of any proprietary rights, relating to use of information in this specification and to the implementation of this specification, and TCG disclaims all liability for cost of procurement of substitute goods or services, lost profits, loss of use, loss of data or any incidental, consequential, direct, indirect, or special damages, whether under contract, tort, warranty or otherwise, arising in any way out of use or reliance upon this specification or any information herein.This document is copyrighted by Trusted Computing Group (TCG), and no license, express or implied, is granted herein other than as follows: You may not copy or reproduce the document or distribute it to others without written permission from TCG, except that you may freely do so for the purposes of (a) examining or implementing TCG specifications or (b) developing, testing, or promoting information technology standards and best practices, so long as you distribute the document with these disclaimers, notices, and license terms.Contact the Trusted Computing Group at for information on specification licensing through membership agreements.Any marks and brands contained herein are the property of their respective owners.Change HistoryVersion / Revision Date DescriptionVersion 1.00 Rev 1.00 27 January 2009 First publicationVersion 1.00 Rev 2.00 20 April 2009 Changed TCG Storage Architecture Core Specificationreference and Opal SSC specification numbering Version 1.00 Rev 3.00 18 December 2009 Corrected the definition of LockingEnabled bitClarified Revert when Manufactured-InactiveVersion 2.00 Rev 1.00 27 February 2012 Added LBA range alignment restriction informationmechanismAdded SecretProtect table as Mandatory in the LockingSP media encryption keysAdded Sector Table access granularity reportingmechanismAdded support for SEDs with SID values not equal toMSIDAdded support for Admin authorities in the Admin SPProvided an optional ability to disable the SID authorityin the Admin SPAdded a programmatic TPer reset mechanismMade Additional DataStore Feature Set mandatory forSEDs compliant with Opal v2.00Added a mechanism for disallowing User authorities tochange their C_PIN valuesAllowed modification of CommonName columns inLocking and Authority tables of the Locking SPMade Authenticate method of the Base templatemandatoryMade Random method of the Crypto templatemandatoryVersion / Revision Date DescriptionVersion 2.01 Rev 1.00 5 August 2015 Fixed Table column values in Table 33 “Locking SP -SecretProtect Table Preconfiguration”.Updated reference [4] to latest version 1.04.Moved SP life cycle and ATA Security Feature Setinteractions in Appendix 5.3.2.4 to [4].Moved list of aborted ATA/SCSI commands from section4.3.7 to [4].Added PSID Feature Set as mandatory.Removed Interface Control Template.Moved interactions between Activate and ATA Securityin section 5.1.1 to [4].TABLE OF CONTENTS1INTRODUCTION (1)1.1D OCUMENT P URPOSE (1)1.2S COPE AND I NTENDED A UDIENCE (1)1.3K EY W ORDS (1)1.4D OCUMENT R EFERENCES (1)1.5D OCUMENT P RECEDENCE (1)1.6SSC T ERMINOLOGY (2)1.7L EGEND (2)2OPAL SSC OVERVIEW (4)2.1O PAL SSC U SE C ASES AND T HREATS (4)2.2S ECURITY P ROVIDERS (SP S) (4)2.3I NTERFACE C OMMUNICATION P ROTOCOL (4)2.4C RYPTOGRAPHIC F EATURES (4)2.5A UTHENTICATION (4)2.6T ABLE M ANAGEMENT (5)2.7A CCESS C ONTROL &P ERSONALIZATION (5)2.8I SSUANCE (5)2.9SSC D ISCOVERY (5)2.10M ANDATORY F EATURE S ETS (5)3OPAL SSC FEATURES (6)3.1S ECURITY P ROTOCOL 1S UPPORT (6)3.1.1Level 0 Discovery (M) (6)3.1.1.1Level 0 Discovery Header (6)3.1.1.2TPer Feature (Feature Code = 0x0001) (7)3.1.1.3Locking Feature (Feature Code = 0x0002) (7)3.1.1.3.1LockingEnabled Definition (8)3.1.1.4Geometry Reporting Feature (Feature Code = 0x0003) (8)3.1.1.4.1Overview (8)3.1.1.4.2Align (9)3.1.1.4.3LogicalBlockSize (9)3.1.1.4.4AlignmentGranularity (9)3.1.1.4.5LowestAlignedLBA (9)3.1.1.5Opal SSC V2.00 Feature (Feature Code = 0x0203) (9)3.2S ECURITY P ROTOCOL 2S UPPORT (10)3.2.1ComID Management (10)3.2.2Stack Protocol Reset (M) (10)3.2.3TPER_RESET command (M) (10)3.3C OMMUNICATIONS (11)3.3.1Communication Properties (11)3.3.2Supported Security Protocols (11)3.3.3ComIDs (11)3.3.4Synchronous Protocol (12)3.3.4.1Payload Encoding (12)3.3.4.1.1Stream Encoding Modifications (12)3.3.4.1.2TCG Packets (13)3.3.4.1.3Payload Error Response (13)3.3.5Storage Device Resets (13)3.3.5.1Interface Resets (13)3.3.5.2TCG Reset Events (13)3.3.6Protocol Stack Reset Commands (M) (14)4OPAL SSC-COMPLIANT FUNCTIONS AND SPS (15)4.1S ESSION M ANAGER (15)4.1.1Methods (15)4.1.1.1Properties (M) (15)4.1.1.2StartSession (M) (16)4.1.1.3SyncSession (M) (16)4.1.1.4CloseSession (O) (16)4.2A DMIN SP (16)4.2.1Base Template Tables (16)4.2.1.1SPInfo (M) (16)4.2.1.2SPTemplates (M) (16)4.2.1.3Table (M) (17)4.2.1.4MethodID (M) (18)4.2.1.5AccessControl (M) (18)4.2.1.6ACE (M) (24)4.2.1.7Authority (M) (25)4.2.1.8C_PIN (M) (26)4.2.2Base Template Methods (26)4.2.3Admin Template Tables (27)4.2.3.1TPerInfo (M) (27)4.2.3.2Template (M) (27)4.2.3.3SP (M) (27)4.2.4Admin Template Methods (28)4.2.5Crypto Template Tables (28)4.2.6Crypto Template Methods (28)4.2.6.1Random (28)4.3L OCKING SP (28)4.3.1Base Template Tables (28)4.3.1.1SPInfo (M) (28)4.3.1.2SPTemplates (M) (29)4.3.1.3Table (M) (29)4.3.1.4Type (N) (30)4.3.1.5MethodID (M) (30)4.3.1.6AccessControl (M) (31)4.3.1.7ACE (M) (53)4.3.1.8Authority (M) (56)4.3.1.9C_PIN (M) (57)4.3.1.10SecretProtect (M) (58)4.3.2Base Template Methods (58)4.3.3Crypto Template Tables (58)4.3.4Crypto Template Methods (58)4.3.4.1Random (58)4.3.5Locking Template Tables (58)4.3.5.1LockingInfo (M) (58)4.3.5.2Locking (M) (59)4.3.5.2.1Geometry Reporting Feature Behavior (60)4.3.5.2.2LockOnReset Restrictions (61)4.3.5.3MBRControl (M) (61)4.3.5.3.1DoneOnReset Restrictions (62)4.3.5.4MBR (M) (62)4.3.5.5K_AES_128 or K_AES_256 (M) (62)4.3.6Locking Template Methods (62)4.3.7SD Read/Write Data Command Locking Behavior (63)4.3.8Non Template Tables (63)4.3.8.1DataStore (M) (63)5APPENDIX – SSC SPECIFIC FEATURES (64)5.1O PAL SSC-S PECIFIC M ETHODS (64)5.1.1Activate – Admin Template SP Object Method (64)5.1.1.1Activate Support (64)5.1.1.2Side effects of Activate (64)5.1.2Revert – Admin Template SP Object Method (64)5.1.2.1Revert Support (65)5.1.2.2Side effects of Revert (65)5.1.2.2.1Effects of Revert on the PIN Column Value of C_PIN_SID (65)5.1.3RevertSP – Base Template SP Method (66)5.1.3.1RevertSP Support (66)5.1.3.2KeepGlobalRangeKey parameter (Locking Template-specific) (66)5.1.3.3Side effects of RevertSP (67)5.2L IFE C YCLE (67)5.2.1Issued vs. Manufactured SPs (67)5.2.1.1Issued SPs (67)5.2.1.2Manufactured SPs (67)5.2.2Manufactured SP Life Cycle States (67)5.2.2.1State definitions for Manufactured SPs (68)5.2.2.2State transitions for Manufactured SPs (68)5.2.2.2.1Manufactured-Inactive to Manufactured (68)5.2.2.2.2ANY STATE to ORIGINAL FACTORY STATE (69)5.2.2.3State behaviors for Manufactured SPs (69)5.2.2.3.1Manufactured-Inactive (69)5.2.2.3.2Manufactured (69)5.2.3Type Table Modification (69)5.3B YTE T ABLE A CCESS G RANULARITY (69)5.3.1Table Table Modification (70)5.3.1.1MandatoryWriteGranularity (70)5.3.1.1.1Object Tables (70)5.3.1.1.2Byte Tables (70)5.3.1.2RecommendedAccessGranularity (70)5.3.1.2.1Object Tables (71)5.3.1.2.2Byte Tables (71)5.4E XAMPLES OF A LIGNMENT G EOMETRY R EPORTING (72)TABLESTable 1 Opal SSC Terminology (2)Table 2 SP Table Legend (2)Table 3 Level 0 Discovery Header (6)Table 4 Level 0 Discovery - TPer Feature Descriptor (7)Table 5 Level 0 Discovery - Locking Feature Descriptor (7)Table 6 Level 0 Discovery - Geometry Reporting Feature Descriptor (8)Table 7 Level 0 Discovery - Opal SSC V2.00 Feature Descriptor (9)Table 8 TPER_RESET Command (11)Table 9 ComID Assignments (12)Table 10 Supported Tokens (12)Table 11 reset_types (13)Table 12 Properties Requirements (15)Table 13 Admin SP - SPInfo Table Preconfiguration (16)Table 14 Admin SP - SPTemplates Table Preconfiguration (16)Table 15 Admin SP - Table Table Preconfiguration (17)Table 16 Admin SP - MethodID Table Preconfiguration (18)Table 17 Admin SP - AccessControl Table Preconfiguration (19)Table 18 Admin SP - ACE Table Preconfiguration (24)Table 19 Admin SP - Authority Table Preconfiguration (25)Table 20 Admin SP - C_PIN Table Preconfiguration (26)Table 21 Admin SP – TPerInfo Columns (27)Table 22 Admin SP - TPerInfo Table Preconfiguration (27)Table 23 Admin SP - Template Table Preconfiguration (27)Table 24 Admin SP - SP Table Preconfiguration (28)Table 25 Locking SP - SPInfo Table Preconfiguration (28)Table 26 Locking SP - SPTemplates Table Preconfiguration (29)Table 27 Locking SP - Table Table Preconfiguration (29)Table 28 Locking SP - MethodID Table Preconfiguration (30)Table 29 Locking SP - AccessControl Table Preconfiguration (31)Table 30 Locking SP - ACE Table Preconfiguration (53)Table 31 Locking SP - Authority Table Preconfiguration (56)Table 32 Locking SP - C_PIN Table Preconfiguration (57)Table 33 Locking SP - SecretProtect Table Preconfiguration (58)Table 34 Locking SP – LockingInfo Columns (58)Table 35 Locking SP - LockingInfo Table Preconfiguration (59)Table 36 Locking SP - Locking Table Preconfiguration (59)Table 37 Locking SP - MBRControl Table Preconfiguration (61)Table 38 Locking SP - K_AES_128 Table Preconfiguration (62)Table 39 Locking SP - K_AES_256 Table Preconfiguration (62)Table 40 LifeCycle Type Table Modification (69)Table 41 Table Table Additional Columns (70)1 Introduction1.1 Document PurposeThe Storage Workgroup specifications provide a comprehensive architecture for putting Storage Devices under policy control as determined by the trusted platform host, the capabilities of the Storage Device to conform tothe policies of the trusted platform, and the lifecycle state of the Storage Device as a Trusted Peripheral.1.2 Scope and Intended AudienceThis specification defines the Opal Security Subsystem Class (SSC). Any SD that claims OPAL SSC compatibility SHALL conform to this specification.The intended audience for this specification is both trusted Storage Device manufacturers and developers that want to use these Storage Devices in their systems.1.3 Key WordsKey words are used to signify SSC requirements.The Key Words “SHALL”, “SHALL NOT”, “SHOULD,” and “MAY” are used in this document. These words are a subset of the RFC 2119 key words used by TCG, and have been chosen since they map to key words used in T10/T13 specifications. These key words are to be interpreted as described in [1].In addition to the above key words, the following are also used in this document to describe the requirements of particular features, including tables, methods, and usages thereof.•Mandatory (M): When a feature is Mandatory, the feature SHALL be implemented. A Compliance test SHALL validate that the feature is operational.•Optional (O): When a feature is Optional, the feature MAY be implemented. If implemented, a Compliance test SHALL validate that the feature is operational.•Excluded (X): When a feature is Excluded, the feature SHALL NOT be implemented. A Compliance test SHALL validate that the feature is not operational.•Not Required (N) When a feature is Not Required, the feature MAY be implemented. No Compliance test is required.1.4 Document References[1]. IETF RFC 2119, 1997, “Key words for use in RFCs to Indicate Requirement Levels”[2]. Trusted Computing Group (TCG), “TCG Storage Architecture Core Specification”, Version 2.01[3]. NIST, FIPS-197, 2001, “Advanced Encryption Standard (AES)”[4]. Trusted Computing Group (TCG), “TCG Storage Interface Interactions Specification“, Version 1.04[5]. Trusted Computing Group (TCG), “TCG Storage Security Subsystem Class: Opal”, Versions 1.00, 2.00[6]. Trusted Computing Group (TCG), “TCG Storage Opal SSC Feature Set: Additional DataStore Tables”,Version 1.00[7]. Trusted Computing Group (TCG), “TCG Storage Opal SSC Feature Set: PSID”, Version 1.001.5 Document PrecedenceIn the event of conflicting information in this specification and other documents, the precedence for requirements is:1. This specification2. Storage Interface Interactions Specification [4]3. TCG Storage Architecture Core Specification [2]1.6 SSC TerminologyThis section provides special definitions that are not defined in [2].Table 1 Opal SSC Terminology Term DefinitionManufactured SP A Manufactured SP is an SP that was created and preconfigured during the SD manufacturing processN/A Not Applicable.Original Factory State (OFS) The original state of an SP when it was created in manufacturing, including its table data, access control settings, and life cycle state. Each Manufactured SP has its own Original Factory State. Original Factory State applies to Manufactured SPs only.Vendor Unique (VU) These values are unique to each SD manufacturer. Typically VU is used in table cells.MM MM The LSBs of a User Authority object’s UID (hexadecimal) as well as the corresponding C_PIN credential object’s UID (hexadecimal)NN NN The LSBs of a Locking object’s UID (hexadecimal) as well as the corresponding K_AES_128/K_AES_256 object’s UID (hexadecimal)XX XX The LSBs of an Admin Authority object’s UID (hexadecimal) as well as the corresponding C_PIN credential object’s UID (hexadecimal)1.7 LegendThe following legend defines SP table cell coloring coding. This color coding is informative only. The table cell content is normative.Table 2 SP Table LegendTableCellLegend R-W Value Access Control CommentArial-Narrow Read-only Opal SSC specified Fixed •Cell content is Read-Only. •Access control is fixed. •Value is specified by the Opal SSCArial Narrow bold-under Read-only VU Fixed•Cell content is Read-Only.•Access Control is fixed.•Values are Vendor Unique (VU).A minimum or maximum valuemay be specified.Arial-NarrowNotDefined(N) Not Defined•Cell content is (N).•Access control is not defined.•Any text in table cell is informativeonly.• A Get MAY omit this column fromthe method response.Arial Narrow bold-under WritePreconfigured,user personalizablePreconfigured,user personalizable•Cell content is writable.•Access control is personalizable•Get Access Control is notdescribed by this color codingTableCellLegend R-W Value Access Control CommentArial-Narrow WritePreconfigured,user personalizableFixed•Cell content is writable.•Access control is fixed.•Get Access Control is notdescribed by this color coding2 Opal SSC Overview2.1 Opal SSC Use Cases and ThreatsBegin Informative ContentThe Opal SSC is an implementation profile for Storage Devices built to:•Protect the confidentiality of stored user data against unauthorized access once it leaves the owner’s control (involving a power cycle and subsequent deauthentication)•Enable interoperability between multiple SD vendorsAn Opal SSC compliant SD:•Facilitates feature discoverability•Provides some user definable features (e.g. access control, locking ranges, user passwords, etc.) •Supports Opal SSC unique behaviors (e.g. communication, table management)This specification addresses a limited set of use cases. They are:•Deploy Storage Device & Take Ownership: the Storage Device is integrated into its target system and ownership transferred by setting or changing the Storage Device’s owner credential.•Activate or Enroll Storage Device: LBA ranges are configured and data encryption and access control credentials (re)generated and/or set on the Storage Device. Access control is configured for LBA range unlocking.•Lock & Unlock Storage Device: unlocking of one or more LBA ranges by the host and locking of those ranges under host control via either an explicit lock or implicit lock triggered by a reset event. MBR shadowing provides a mechanism to boot into a secure pre-boot authentication environment to handle device unlocking.•Repurpose & End-of-Life: erasure of data within one or more LBA ranges and reset of locking credential(s) for Storage Device repurposing or decommissioning.End Informative Content2.2 Security Providers (SPs)An Opal SSC compliant SD SHALL support at least two Security Providers (SPs):1) Admin SP2) Locking SPThe Locking SP MAY be created by the SD manufacturer.2.3 Interface Communication ProtocolAn Opal SSC compliant SD SHALL implement the synchronous communications protocol as defined in Section 3.3.4.This communication protocol operates based upon configuration information defined by:1) The values reported via Level 0 Discovery (Section 3.1.1);2) The combination of the host's communication properties and the TPer's communication properties (seeProperties Method Section 4.1.1.1).2.4 Cryptographic FeaturesAn Opal SSC compliant SD SHALL implement Full Disk Encryption for all host accessible user data stored on media. AES-128 or AES-256 SHALL be supported (see [3]).2.5 AuthenticationAn Opal SSC compliant SD SHALL support password authorities and authentication.2.6 Table ManagementThis specification defines the mandatory tables and mandatory/optional table rows delivered by the SD manufacturer. The creation or deletion of tables after manufacturing is outside the scope of this specification. The creation or deletion of table rows post-manufacturing is outside the scope of this specification.2.7 Access Control & PersonalizationInitial access control policies are preconfigured at SD manufacturing time on manufacturer created SPs. An Opal SSC compliant SD SHALL support personalization of certain Access Control Elements of the Locking SP.2.8 IssuanceThe Locking SP MAY be present in the SD when the SD leaves the manufacturer. The issuance of SPs is outside the scope of this specification.2.9 SSC DiscoveryRefer to [2] for details (see section 3.1.1).2.10 Mandatory Feature SetsAn Opal SSC compliant SD SHALL support the following TCG Storage Feature Sets:1) Additional DataStore Tables, Opal SSC Feature Set (refer to [6]);2) PSID, Opal SSC Feature Set (refer to [7]).3 Opal SSC Features3.1 Security Protocol 1 Support3.1.1 Level 0 Discovery (M)Refer to [2] for more details.An Opal SSC compliant SD SHALL return the following Level 0 response:• Level 0 Discovery Header • TPer Feature Descriptor • Locking Feature Descriptor •Opal SSC Feature Descriptor3.1.1.1 Level 0 Discovery HeaderTable 3 Level 0 Discovery HeaderBit Byte 7 6543210 0 (MSB) Length of Parameter Data1 2 3(LSB) 4 (MSB) Data structure revision 5 6 7 (LSB) 8 (MSB) Reserved ... 15 (LSB) 16 (MSB) Vendor Specific (47)(LSB)• Length of parameter data = VU • Data structure revision = 0x00000001 orany version that supports the defined features in this SSC • Vendor Specific = VU3.1.1.2 TPer Feature (Feature Code = 0x0001)Table 4 Level 0 Discovery - TPer Feature DescriptorBitByte7 6 5 4 3 2 1 00 (MSB)Feature Code (0x0001)1 (LSB)2 Version Reserved3 Length4 Reserved ComID MgmtSupported Reserved StreamingSupportedBuffer MgmtSupportedACK/NAKSupportedAsyncSupportedSyncSupported5 - 15 Reserved•Feature Code = 0x0001•Version = 0x1 or any version that supports the defined features in this SSC •Length = 0x0C•ComID Mgmt Supported = VU•Streaming Supported = 1•Buffer Mgmt Supported = VU•ACK/NACK Supported = VU•Async Supported = VU•Sync Supported = 13.1.1.3 Locking Feature (Feature Code = 0x0002)** = the present current state of the respective featureTable 5 Level 0 Discovery - Locking Feature DescriptorBitByte7 6 5 4 3 2 1 00 (MSB)Feature Code (0x0002)1 (LSB)2 Version Reserved3 Length4 Reserved MBR Done MBREnabledMediaEncryptionLocked LockingEnabledLockingSupported5 - 15 Reserved•Feature Code = 0x0002•Version = 0x1 or any version that supports the defined features in this SSC •Length = 0x0C•MBR Done = **•MBR Enabled = **•Media Encryption = 1•Locked = **•Locking Enabled = See 3.1.1.3.1•Locking Supported = 13.1.1.3.1LockingEnabled DefinitionThe definition of the LockingEnabled bit is changed from [2] as follows:The LockingEnabled bit SHALL be set to one if an SP that incorporates the Locking template is any state other than Nonexistent or Manufactured-Inactive; otherwise the LockingEnabled bit SHALL be set to zero. 3.1.1.4 Geometry Reporting Feature (Feature Code = 0x0003)3.1.1.4.1OverviewThis information indicates support for logical block and physical block geometry. This feature MAY be returned in the Level 0 Discovery response. See [2] for additional information.Table 6 Level 0 Discovery - Geometry Reporting Feature DescriptorBit Byte 7 6543210 0 (MSB) Feature Code (0x0003)1(LSB)2 VersionReserved3 Length4 ReservedALIGN 5 Reserved6 7 8 9 10 1112 (MSB) LogicalBlockSize13 1415(LSB) 16 (MSB) AlignmentGranularity17 18 19 20 21 2223(LSB) 24 (MSB) LowestAlignedLBA25 26 27 28 29 3031(LSB)• The Feature Code field SHALL be set to 0x0003. • The Version field SHALL be set to 0x01. •The Length field SHALL be set to 0x1C.3.1.1.4.2 AlignIf the value of the AlignmentRequired column of the LockingInfo table is TRUE, then the ALIGN bit shall be set to one. If the value of the AlignmentRequired column of the LockingInfo table is FALSE, then the ALIGN bit shall be cleared to zero.3.1.1.4.3 LogicalBlockSizeLogicalBlockSize SHALL be set to the value of the LogicalBlockSize column in the LockingInfo table.3.1.1.4.4 AlignmentGranularityAlignmentGranularity SHALL be set to the value of the AlignmentGranularity column in the LockingInfo table.3.1.1.4.5 LowestAlignedLBALowestAlignedLBA SHALL be set to the value of the LowestAlignedLBA column in the LockingInfo table.3.1.1.5 Opal SSC V2.00 Feature (Feature Code = 0x0203)Table 7 Level 0 Discovery - Opal SSC V2.00 Feature DescriptorBitByte7 6 5 4 3 2 1 00 (MSB)Feature Code (0x0203)1 (LSB)2 Version Reserved3 Length4 (MSB)Base ComID5 (LSB)6 (MSB)Number of ComIDs7 (LSB)8 Reserved for future common SSC parametersRange Crossing Behavior9 (MSB)Number of Locking SP Admin Authorities Supported10 (LSB)11 (MSB)Number of Locking SP User Authorities Supported12 (LSB)13 Initial C_PIN_SID PIN Indicator14 Behavior of C_PIN_SID PIN upon TPer Revert15-19 Reserved for future common SSC parameters•Feature Code = 0x0203•Version = 0x1 or any version that supports the defined features in this SSC •Length = 0x10•Base ComID = VU•Number of ComIDs = 0x0001 (minimum value)•Range Crossing Behavior = VUo0 = The SD supports commands addressing consecutive LBAs in more than one LBA range if all the LBA ranges addressed are unlocked. See Section 4.3.7o 1 = The SD terminates commands addressing consecutive LBAs in more than one LBA range.See Section 4.3.7•Number of Locking SP Admin Authorities = 4 (minimum value)•Number of Locking SP User Authorities = 8 (minimum value)•Initial C_PIN_SID PIN Indicator = VUo0x00 = The initial C_PIN_SID PIN value is equal to the C_PIN_MSID PIN valueo0xFF = The initial C_PIN_SID PIN value is VU, and MAY not be equal to the C_PIN_MSID PIN valueo0x02 – 0x0F = Reserved•Behavior of C_PIN_SID PIN upon TPer Revert = VUo0x00 = The C_PIN_SID PIN value becomes the value of the C_PIN_MSID PIN column after successful invocation of Revert on the Admin SP’s object in the SP tableo0xFF = The C_PIN_SID PIN value changes to a VU value after successful invocation of Revert on the Admin SP’s object in the SP table, and MAY not be equal to the C_PIN_MSID PIN value If an Opal v2.00 SSC implementation is backward compatible with Opal v1.00, the SD SHALL also report the Opal SSC Feature Descriptor as defined in [5].Begin Informative ContentAn Opal v2.00 implementation is backward compatible to Opal v1.00 only if the geometry reported by the Geometry Reporting Feature does not specify any alignment restrictions (i.e. Align = FALSE, see 3.1.1.4.2) , and if the TPer does not specify any granularity restrictions for byte tables (i.e. MandatoryWriteGranularity = 1 for all byte tables, see 5.3.1.1), and if the “Initial C_PIN_SID PIN Indicator” and “Behavior of C_PIN_SID PIN upon TPer Revert” fields are both 0x00.End Informative Content3.2 Security Protocol 2 Support3.2.1 ComID ManagementComID management support is reported in Level 0 Discovery. Statically allocated ComIDs are also discoverable via the Level 0 Discovery response.3.2.2 Stack Protocol Reset (M)An Opal SSC compliant SD SHALL support the Stack Protocol Reset command. Refer to [2] for details.3.2.3 TPER_RESET command (M)If the TPER_RESET command is enabled, it SHALL cause the following before the TPer accepts the next IF-SEND or IF-RECV command:a) all dynamically allocated ComIDs SHALL return to the Inactive state;b) all open sessions SHALL be aborted on all ComIDs;c) all uncommitted transactions SHALL be aborted on all ComIDs;d) the synchronous protocol stack for all ComIDs SHALL be reset to its initial statee) all TCG command and response buffers SHALL be invalidated for all ComIDs;f) all related method processing occurring on all ComIDs SHALL be aborted;g) TPer’s knowledge of the host’s communications capabilities, on all ComIDs, SHALL be reset to theinitial minimum assumptions defined in [2] or the TPer’s SSC definition;h) the values of the ReadLocked and WriteLocked columns SHALL be set to True for all Locking SP’sLocking objects that contain the Programmatic enumeration value in the LockedOnReset column;i) the value of the Done column of the Locking SP’s MBRControl table SHALL be set to False, if theDoneOnReset column contains the Programmatic enumeration value.The TPER_RESET command is delivered by the transport IF-SEND command. If the TPER_RESET command is enabled, the TPer SHALL accept and acknowledge it at the interface level. If the TPER_RESET command is disabled, the TPer SHALL abort it at the interface level with the “Other Invalid Command Parameter” status (see [4]). There is no IF-RECV response to the TPER_RESET command.The TPER_RESET command is defined in Table 8.The Transfer Length SHALL be non-zero. All data transferred SHALL be ignored.Table 8 TPER_RESET CommandFIELD VALUECommand IF-SENDProtocol ID 0x02Transfer Length Non-zeroComID 0x00043.3 Communications3.3.1 Communication PropertiesThe TPer SHALL support the minimum communication buffer size as defined in Section 4.1.1.1. For each ComID, the physical buffer size SHALL be reported to the host via the Properties method.The TPer SHALL terminate any IF-SEND command whose transfer length is greater than the reported MaxComPacketSize size for the corresponding ComID. For details, reference “Invalid Transfer Length parameter on IF-SEND” in [4].Data generated in response to methods contained within an IF-SEND command payload subpacket (including the required ComPacket / Packet / Subpacket overhead data) SHALL fit entirely within the response buffer. If the method response and its associated protocol overhead do not fit completely within the response buffer, the TPer1) SHALL terminate processing of the IF-SEND command payload,2) SHALL NOT return any part of the method response if the Sync Protocol is being used, and3) SHALL return an empty response list with a TCG status code of RESPONSE_OVERFLOW in thatmethod’s response status list.3.3.2 Supported Security ProtocolsThe TPer SHALL support:•IF-RECV commands with a Security Protocol values of 0x00, 0x01, 0x02.•IF-SEND commands with a Security Protocol values of 0x01, 0x02.3.3.3 ComIDsFor the purpose of communication using Security Protocol 0x01, the TPer SHALL:•support at least one statically allocated ComID for Synchronous Protocol communication.•have the ComID Extension values = 0x0000 for all statically allocated ComIDs.•keep all statically allocated ComIDs in the Active state.。
dsl if语法-概述说明以及解释

dsl if语法-概述说明以及解释1.引言1.1 概述在软件开发领域中,DSL(领域特定语言)是一种针对特定领域的编程语言,用于解决该领域特定问题的语言。
DSL与通用编程语言(如Java、Python)不同,它更专注于解决特定领域的问题,使得代码更易于理解和维护。
if语法是DSL中常用的语法之一,用于控制程序流程中的条件分支。
通过if语法,程序员可以根据条件的满足与否执行不同的代码块,实现灵活的程序控制逻辑。
本文将重点讨论DSL中的if语法,探讨其在DSL中的应用以及对软件开发的重要性。
通过深入了解DSL if语法的特点和用途,我们可以更好地理解和使用DSL,提高程序的可读性和可维护性。
1.2文章结构1.2 文章结构本文将按照以下结构展开讨论DSL if语法的相关内容:- 第一部分将介绍什么是DSL,解释DSL的概念和特点,为读者提供DSL的基本知识背景。
- 第二部分将重点讨论DSL中的if语法,详细解释if语法在DSL中的作用和用法。
- 第三部分将探讨DSL if语法的应用场景,结合具体示例说明if语法在实际开发中的重要性和灵活性。
1.3 目的DSL if语法是一种在领域特定语言(DSL)中使用的条件语句结构,其目的是为了提供一种简洁而灵活的方式来描述特定领域的逻辑条件和决策流程。
通过DSL if语法,用户可以更直观地表达业务逻辑并更容易地将其转化为可执行的代码。
在本文中,我们将深入探讨DSL if语法的概念、特点和应用场景,探讨其在实际开发中的重要性和价值。
通过对DSL if语法的研究和讨论,我们旨在帮助读者更好地理解和应用DSL if语法,提高软件开发效率和代码可读性。
同时,我们也将探讨DSL if语法的未来发展方向,展望其在领域特定语言领域的潜在应用和价值。
2.正文2.1 什么是DSLDSL是领域特定语言(Domain-Specific Language)的缩写,是一种针对特定领域或问题领域而设计的计算机编程语言。
ADS教程第6章

实验六、滤波器:设计指导、瞬态和矩量法仿真概述这节将说明在ADS中创建滤波器和使用瞬态仿真器的基本操作。
设计指导是用来构建一个集总元件滤波器,矩量法(Momentum)是用来测试微带滤波器。
任务●运用设计指导构建一个200MHz中频低通集总参数滤波器●构建一个1.9GHz射频带通微带滤波器●在微带滤波器中完成瞬态分析●用矩量法(Momentum)仿真微带滤波器●选学——DAC(数据通路元件)练习目录1.改变项目,开始运行设计指导 (96)2.放入一个LPF(低通滤波器)Smart元件并设计滤波器 (97)3. 1.9GHz微带带通滤波器 (99)4.在微带滤波器中的瞬态分析 (101)5.在电路版图(layout)中进行矩量法(Momentum)仿真 (104)6.选作:数据通路元件(Data Access Component)的阻抗响应 (110)步骤1.改变项目开始运行设计指导。
以下步骤将说明一个设计指导怎样既快速又准确地生产一个滤波器。
其方法与E-syn类似,但对期望的响应和拓扑结构有更多的选择和更强的控制。
a.进入ADS主窗口,然后点击File>open Project。
b.如果你被提示保存所有你当前的文档,选择Y es to All,然后打开你先前的任务system_prj。
c.新建一名为filter_lpf的原理图。
d.确认该原理图是当前你的屏幕上唯一打开的原理图。
现在我们将通过以下三个步骤开始该过程。
●点击命令DesignGuide >Filter。
●出现对话框后,选择Filter Control Window并点击OK。
然后找到新窗口Filter DesignGuide。
在下一步,你从面板放入一个smart元件之后该窗口将被激活。
在滤波器设计指导控制窗口中点击Component Palette —All图标(如xia下图所示)。
在你的原理图窗口中会立即出现元件面板。
现在你就可以放入smart元件了。
cic梳状滤波器 c语言实现

cic梳状滤波器 c语言实现
CIC梳状滤波器是一种适合于高速采样信号预处理的线性相位滤波器,其频率响应像一把梳子,因此被称为梳状滤波器。
CIC滤波器的C语言实现可以参考以下步骤:
1. 定义输入输出变量:使用数组或指针来表示滤波器的输入输出信号。
2. 实现积分器和累加器:使用循环和条件语句来实现积分器和累加器的功能。
3. 计算滤波器的输出:根据CIC滤波器的公式计算输出信号。
请注意,这只是一个简单的实现示例,实际的CIC滤波器可能需要考虑更多的细节和优化。
如需了解更多关于CIC滤波器的信息,请补充相关背景后再次向我提问。
双频激电及其数据处理

甘肃某金银矿点 金银矿受断裂带产于绿泥石角闪片岩、绢云母石英片岩内的挤压带中,金、银与铅、锌、黄铁矿化共生,且有正相关关系。黄铁矿化较强处可呈稠密浸染至半块状。图为该矿体IV号剖面综合图。Fs 与 ηs 相似性也是一目了然。
时间域与频率域的差异
频率域电法的主要优点 a.轻便; b.抗干扰能力强。 传统频率域电法的主要缺点 任何一种频率域电法都是要在不同的频率进行测量,传统的主动源电法勘探(包括激发极化法和电磁法)的工作方式都是“变频法”,变频法是一个频率、一个频率地逐个改变频率进行测量,以致带来了它两大致命弱点. a.变频法的工作效率低(“扫面”的速度更低); b.变频法的相对精度低。 (1)在激电法中区分矿异常性质能力低, (2)在电磁法(CSAMT)中发现深部异常能力低。 (3)不能(像TEM那样)进行近区的频率域电磁测深。
电流脉冲宽度 T(即充电时间长度) 对极化强度的影响
ΔV0
电位差ΔV
ΔV0
时间 (t)
T大,二次电位大
电位差ΔV
ΔV0
ΔV0
T小,二次电位小
T
T
二次电位差 ΔVIP
频率域与时间域的等效性
脉冲宽度 (T)
电位差 ΔV
二次电位差 ΔVIP
ΔVIP
时间域
时间域
频率域
二次电位差 ΔVIP
频率域IP与时间域IP的物理实质是一样的,对于寻找金属矿来说它们的能力是等效的。
01
对于线性时不变系统,在理论上二者是可以相互转换的。
02
在实际条件下,一般电流密度都非常小(小于0.01μA/cm2),实际上可以看作线性系统,如果能测量到相当完整的时间响应和频率响应,则它们在一定精度内也是可以相互转换的。
Oracle Order Capture 实施指南 Release 11i说明书

Copyright 2000, Oracle Corporation. All Rights Reserved.Oracle is a registered trademark, and Order Capture is a trademark of Oracle Corporation. Other names may be trademarks of their respective owners.Oracle Order CaptureImplementation GuideRelease 11iAugust 2000Part No. A86137-01This topic group provides general descriptions of the set up andconfiguration tasks required to implement the application successfully.DependenciesOracle Order Capture requires the following related products andcomponents be installed and implemented:s Oracle Accounts Receivable – for support of Taxes and Customerdefinitionss Oracle Inventory – for Items and Reservationss Oracle Bill of Materials – for the bills of materials associated with Itemss Oracle Configurator – for the configurator URL, if Oracle Configuratoris useds Oracle Order Management – for support of booking an orders Oracle iPayments Oracle Advanced Pricing – for support of prices and discountss Oracle Service Contractss Oracle Contracts Core – for support of templatesRelated Documentation and ResourcesYou may also wish to consult the following documentation:s Oracle Applications, Product Update Notes, Release 11is Installing Oracle Applications, Release 11isImplementing CRM ApplicationssOracle CRM Foundation Components Concepts and Procedures sOracle CRM Foundation T echnical Reference ManualThese documents range from the general to the specific, in the order listed in the following table.Related CoursewareThe following Net Class is available on demand through Oracle University.s11i Overview of CRM Foundation, Course Description ID 8831.Setting Up Oracle Order CaptureStepsGuidelinesMandatory profile options are marked with an asterisk on the table of Oracle Order Capture System Profile Options on page 7.Related Documentation DocumentPurposeOracle Applications, Product Update Notes, Release 11i Contains information about new product features and functions for the various Oracle applicationsInstalling Oracle Applications, Release 11iDocuments the Rapid Install installation processImplementing CRM Applications Contains post-installation information onvarious CRM modules Oracle CRM Foundation Components, Concepts and ProceduresA printed compilation of the Oracle Foundation online help systemOracle CRM Foundation, Technical Reference ManualContains table and view descriptions for all the Foundation componentsStep Number Required?Oracle Order Capture Setup Step DescriptionWindow Name(s)1Yes Set up Quote Status Transitions Quote Status Setup 2Yes S et up Lookup Codes Quick Codes 3YesSetup Profile OptionsPersonal ProfileMandatory lookup codes are marked with an asterisk on the table of Oracle Order Capture Lookup Codes on page5.The ASO: Configurator URL profile option is mandatory only if you want the Configurator feature.The ASO: Quote Conversion Type profile option is mandatory if you use multiple currencies.Setting Up Quote Status and Quote Status TransitionsUse this procedure to perform the following tasks:s Add new quote statusess Set up quote versionings Enable or disable existing quote statusess Set up the allowable status changes, or transitions, for each status Quote status identifies how close a quote is to an order and determines whether a user can modify a quote and whether or not the application creates a new version if changes are made.Oracle Order Capture is delivered with predefined quote statuses. You can define new quote statuses or modify the pre-defined statuses. Users need Quote Statuses to create quotes.See the online help for an explanation of Quote Status.PrerequisitesTo perform these tasks, you must be logged in under the Order Capture Sales Manager responsibility.Steps1.Navigate to the Quote Status Setup window.2.If you want to add a new quote status, then:a.In the Quote Statuses region, select a blank entry line or a linebelow which you wish to insert the new entry.Alternatively, click the Add icon on the toolbar. The Add icon is thebutton with a green plus (+) sign.b.Enter the status code. This is the internal name and is not be seenby the user.c.Enter the status name and status description. These are displayedin the list of values for users.d.If you want the new status to create a version when the user saves aquote, then check the Auto Versioning check box.e.If you wish to enable a user to make changes to the quote, to addnew quote lines or to modify prices, for instance, then check theUpdate Allowed check box.f.If you wish to set time limits when this new status is available, thenenter dates in the Effective From and Effective To fields.g.Click Save on the toolbar.3.If you wish to set up the rules that determine the permitted statuses auser can select for a particular status, then:a.In the Quote Statuses region, select the status you wish to set up.b.In the Allowed Transition to Status region, use the Code list ofvalues to select an allowable transition status.c.Repeat the previous step for each permitted transition status.d.If you wish to disable an existing status, then uncheck the Enabledbox.e.Click Save on the toolbar.Setting Up Lookup CodesUse the following list to identify the lookup codes (QuickCodes) that you need to define for your specific implementation. You can enter them in any order.To set lookup codes, use the standard procedure outlined in the Oracle Applications Users GuideOracle Order Capture Lookup CodesLookup Code DescriptionASO_CONTACT_PROFILE_TYPE Types of customers. The two seeded valuesare: Consumer and Business.*ASO_DEFAULT_ORDER_STATE The default state of an order when the quoteis passed to Oracle Order Management. Theseeded values are: entered and booked. Eachtriggers different Oracle Order Managementvalidation.*ASO_HEADER_RELATIONSHIP_ TYPE Type of header relationships between quote headers. There is one seeded value: Copy. This lookup is used by an Order Capture API for validation of RELATIONSHIP_TYPE in ASO_QUOTE_HEADER_ RELATIONSHIPS.*ASO_ITEM_TYPE Item types for items which are added to thecart.*ASO_LINE_ATTRIBUTE_STATUS Status of an order line attribute. This lookupis used by an Order Capture API forvalidation of STATUS in ASO_LINE_ATTRIBS_EXT.*ASO_LINE_ATTRIBUTE_TYPE Type of line attribute. This lookup is used byan Order Capture API for validation inASO_LINE_ATTRIBS_EXT.*ASO_LINE_RELATIONSHIP_ TYPE Type of line relationship. This lookup is used by an Order Capture API for validation of RELATIONSHIP_TYPE in ASO_QUOTE_ LINE_RELATIONSHIPS.*ASO_OBJECT_RELATIONSHIP_ TYPE Type of object relationship. This lookup is used by an Order Capture API for validation of RELATIONSHIP_TYPE in ASO_QUOTE_ OBJECT_RELATIONSHIPS.ASO_ORDER_FEEDBACK_CRM_ APPS CRM applications registered for order feedback. All applications listed here are informed of any changes to an order in Oracle Order Management.ASO_ORDER_LINE_STATUSES Status of the order line.ASO_ORDER_STATUSES Order status.ASO_PARTY_RELATIONSHIP_TYPENot in use in the current release.*ASO_PAYMENT_OPTION Payment options available to users. *ASO_PAYMENT_TYPE Payment types available to users. * Lookup codes marked with an asterisk (*) are mandatorySetting System Profile OptionsUse the following list to identify the profile options that you need to set for your specific implementation. You can set these profile options in any order you like.To change profile options, use the standard procedure outlined in the Oracle Applications Users Guide .*ASO_QUOTE_OBJECT_TYPEType of quote objects. This lookup is used for validating OBJECT_TYPE in ASO_QUOTE_OBJECT_RELATIONSHIPS.*ASO_QUOTE_SOURCE The source of the quote.*ASO_RELATED_OBJECT_TYPEType of object related to the quote. This lookup is used for validating RELATED_OBJECT in ASO_QUOTE_OBJECT_RELATIONSHIPS.ASO_RESERVATION_TYPEOptions the user can use to decide at what level the application reserves an item in inventory.*ASO_RETURN_FOR Reasons for returns.*ASO_SERVICE_TYPEService reference type code. A service must always be linked to an item or an item in the customer installed base. This list of values specifies where the item is. Seeded values include: Quote, Order, and Customer Product.ASO_UNIVERSAL_SEARCHTypes of universal search. Not used in Release 11i .Oracle Order Capture Lookup Codes Lookup CodeDescription* Lookup codes marked with an asterisk (*) are mandatoryOracle Order Capture System Profile OptionsProfile Option DescriptionASO: Advanced Inbound Installation Determines if Oracle Advanced Inbound isinstalled. Not applicable in Release 11i.ASO: Advanced Outbound Installation Determines if Oracle Advanced Outbound is installed. Not applicable in Release 11i.ASO: Automatic ATP Check Determines whether ATP check isperformed automatically for an item in theItem View tab.ASO: Automatic ATP check for Number of Items Specifies the number of items in the Related Items window that triggers an automatic ATP check. Users can use this profile to limit the amount of time the application spends performing ATP checks. If the number of related items is less than or equal to the specified number, then the application performs an ATP check.If the number of related items is equal to the specified number, then the application does not perform the check.ASO: Automatic Numbering Determines if the application automaticallygenerates a quote number. If this profileoption is set to null, then the automaticnumbering is turned off and the user has toenter the quote number.By default, this option is set to Yes andcannot be changed in the current release. ASO: Configurator URL Enter the URL for the Oracle Configuratorwindow.ASO: Credit Card Authorization A flag determining whether the applicationperforms a credit card authorization.*ASO: Default Currency Code One of the two profile options thatdetermine the currency of the transactionsin the application.The currency defined in ASO: DefaultOrder Type takes precedence over thisprofile option.*ASO: Default Order Category Determines whether all items in an orderare orders or returns. By default, thisprofile is set to orders and cannot bechanged in the current release.*ASO: Default Order State The default state of the order when thequote is booked. Determines whether ornot quote can be booked or entered.* Profile options marked with an asterisk (*) are mandatory.*ASO: Default Order Type Determines how the order is to beprocessed in Oracle Order Management.The order types are set up in Oracle OrderManagement. This profile determines whatprice list and currency code appears bydefault in the main Order Capture form. ASO: Default Ordered Qty in OC UI The default quantity which appears in theQTY field of the Order Capture window. ASO: Default Payment Option Defaults the payment option. Choices are:single, installment, and split.*ASO: Default Person ID The default sales representative who isallocated the sales credits for booked orderswhen the user is not entered as a salesrepresentative.ASO: Default QTY for ATP Check This profile option is not in use.*ASO: Default Quote Status Default status of a new quote. When thisoption is not defined, the default value isDraft.ASO: Enable Configure Model Item Enables configuration of model items. Thisprofile option is not being used in Release11i. In this release, the configurator isenabled by setting the Configurator URL. ASO: Enable Line Payments Not used in this release.ASO: Enable Split Payment Not used in this release.ASO: Order Feedback Queue Retention Time Amount of time that messages are retained in the order feedback queue.ASO: PAYMENT_TERM Not used in this release.*ASO: Product Organization The organization that Order Capture usesto validate inventory items.ASO: Quote Conversion Type Conversion type for getting dailyconversion rate. Not used in this release. *ASO: Quote Duration The length of time a quote remains valid. ASO: Quote Order Entered State The state of orders when they are createdfrom quotes. Not used in this release. ASO: Quote Order Type This profile option is not in use.* Profile options marked with an asterisk (*) are mandatory.Workflows in Oracle Order CaptureOracle Order Capture does not use workflows.ASO: Receipt MethodDetermines the receipt method for credit card authorization. This profile option is required when ASO: Credit Card Authorization is set to Yes.ASO: Reservation LevelDetermines the level at which itemreservation is done. Items can be reserved either when they are added to the cart or when the order is booked. Manualreservation is not supported in Release 11i .ASO: Scripting Installation Determines if Oracle Scripting is installed. Not used in Release 11i .ASO: Transaction Source TypeThe source type used for reserving items. There must be at least one Transaction Source Type. The source type is set up by Manufacturing & Distribution Manager responsibilityin Inventory > Setup > Transaction Source Type.Attach this Transaction Source Type to the profile option ASO: Transaction Source TypeASO: Use Installation Details Turns on the Installation Details UI. Not used in Release 11i .ASO: Use Product Configurator Not used in Release 11i .*ASO: Validate SalesrepIf this profile is set to Yes, then it checks to see the user is set up as a valid sales representative.If it is set to No, then the application uses the default sales representative entered in ASO: Default Person ID.* Profile options marked with an asterisk (*) are mandatory.。
Maxim Micro SDK (MaximSDK) Installation and Mainte

Maxim Micro SDK (MaximSDK) Installation and Maintenance User GuideAbstractThis installation user guide contains detailed information about the installation of the MaximSDK environment for Maxim® Microcontroller ICs.Table of ContentsIntroduction (4)Installation (6)Prerequisites (6)Setup (7)Maintenance Tool (12)Package Manager (13)Update Components (13)Uninstallation (14)Revision History (15)List of FiguresFigure 1. Design resource tab of the MAX32520 web page. (7)Figure 2. Selecting the installation folder. (7)Figure 3. Selecting all the desired components. (8)Figure 4. Selecting a Start Menu for the program shortcuts. (9)Figure 5. Ready to Install window and required disk space. (10)Figure 6. Run Eclipse Maxim Integrated. (11)Figure 7. Maintenance tool window. (12)Figure 8. Maintenance tool window. (13)Figure 9. Uninstall warning message. (14)IntroductionThe Maxim Micro SDK Installer provides a simple interface to install the necessary tools to develop the firmware for Maxim Integrated’s Microcontroller ICs. The Maxim Micros Software Development Kit (MaximSDK) installer provides a compact software package to install the necessary tools containing Maxim® proprietary source codes, libraries, and examples dedicated to:•Board support packages (BSPs)•Validated Hardware Abstraction Layer (HAL) source codes•Librarieso Integrated into the installer:▪MAXUSB: CDC-ACM and HID▪FCL: Free Crypto Library▪FreeRTOS▪lwIP: Lightweight TCP/IP stack▪SDHC: SD Card Libraryo Installed separately (NDA or SLA required):▪EMV L1 Contact-Smart Card: Install as a plugin▪NFC: Install as a plugin▪UCL: Install as a plugin•Documentation•Wide range of examples ready to run on evaluation kits (EV kits)This installer is fully integrated with Eclipse™ and MaximSDK. It also bundles setups for all the required programs. The list of programs bundled in the setup is:•GNU Tools for ARM Embedded Processors•Eclipse CDT IDE for C/C++ Developers (Maxim Integrated version)•Maxim Integrated Bitmap Converter•Maxim Integrated Secure Tools•Minimalist GNU for Windows (MinGW)•Open On-Chip Debugger(OpenOCD)•Olimex ARM-USB-TINY-H DriversEclipse is a trademark of Eclipse Foundation, Inc.MinGW is a Registered Trademark of Software in the Public Interest, Inc. in the United States. The MinGW trademark is managed by the MinGW project.Maxim is a registered trademark of Maxim Integrated Products, Inc.This document describes all the installation, update, and uninstallation processes for the MaximSDK environment. It also explains how to maintain and troubleshoot the tool chain. The screenshots might be different from the MaximSDK installer version, but the steps are identical. The installer is also capable of installing firmare, software, and documentation to run with Maxim Integrated Arm Cortex products. The supported products are:•MAX32520: ChipDNA Secure Arm Cortex M4 Microcontroller•MAX32570: Low-Power Arm Cortex-M4 Microcontroller with Contactless Radio for Secure Applications•MAX32670: High Reliability, Ultra-Low Power Microcontroller Powered by Arm Cortex M4 Processor with FPU for Industrial and IoT•MAX32655: Low-Power, Arm Cortex-M4 Processor with FPU-Based Microcontroller and Bluetooth 5.2•MAX78000: Ultra-Low-Power Arm Cortex-M4 Processor with FPU-Based Microcontroller with Convolutional Neural Network AcceleratorArm and Cortex are registered trademarks of Arm Limited.InstallationPrerequisitesThe MaximSDK online installer can be downloaded from the Maxim Integrated website. The supported operating systems are Win10, MacOS, and Linux distros.The Maxim Micros SDK comes with its own version of Eclipse. Uninstall the previous version of the MaximSDK before installing the new version.The Maxim Micros SDK is updated using the Maintenance Tool integrated in the MaximSDK. Also, the Maintenance Tool can add new libraries and solutions.Setup1. Download MaximMicrosSDK.exe from the Maxim web page. This package is found inthe Design Resources tab of the supported parts web page. Run the installer exe after downloading.Figure 1. Design resource tab of the MAX32520 web page.2. Click Next to proceed from the Welcome screen.3. Choose the installation directory path and name. Click Next. Install in the C:\MaximSDKfolder.Figure 2. Selecting the installation folder.4. Select the components to install into the environment.Figure 3. Selecting all the desired components.5. Read and accept the License Agreements.6. Select the Start Menu Shortcut. Click Next.Figure 4. Selecting a Start Menu for the program shortcuts.7. Check the free and required disk spaces. The required disk space is about 1.6GB.Figure 5. Ready to Install window and required disk space.8. Click Install to download and install. This installation lasts about 20 minutes dependingon the selected components.9. The Eclipse Maxim Integrated is available in the Start Menu after installation.Figure 6. Run Eclipse Maxim Integrated.Maintenance ToolThe MaintenanceTool.exe, the uninstaller and maintenance application, is found at the top of the Maxim Integrated installation directory (e.g. C:\MaximSDK). This application installs, updates, or uninstalls packages for an existing installation. Double click the application and choose from the three options: Package manager, Update components, or Remove all components. Click Next.Figure 7. Maintenance tool window.Package ManagerSelecting this component adds or removes certain packages from the installation. Check or uncheck the corresponding checkboxes to add or remove components. Click Next.Close all applications before removing or adding components.Update ComponentsRun the maintenance tool often to update the tool chain. Selecting this component updates certain packages for an existing installation.Close all applications before removing or adding components.Uninstallation1. Close all active Eclipse applications before uninstallation.2. Select Remove all components. Click Next.3. Click Uninstall. The uninstallation lasts about five minutes.Figure 9. Uninstall warning message.4. The MaximSDK folder is removed from the C:\ directory completely. Ensure the uninstallis complete.©2020 by Maxim Integrated Products, Inc. All rights reserved. Information in this publication concerning the devices, applications, or technology described is intended to suggest possible uses and may be superseded. MAXIM INTEGRATED PRODUCTS, INC. DOES NOT ASSUME LIABILITY FOR OR PROVIDE A REPRESENTATION OF ACCURACY OF THE INFORMATION, DEVICES, OR TECHNOLOGY DESCRIBED IN THIS DOCUMENT. MAXIM ALSO DOES NOT ASSUME LIABILITY FOR INTELLECTUAL PROPERTY INFRINGEMENT RELATED IN ANY MANNER TO USE OF INFORMATION, DEVICES, OR TECHNOLOGY DESCRIBED HEREIN OR OTHERWISE. The information contained within this document has been verified according to the general principles of electrical and mechanical engineering or registered trademarks of Maxim Integrated Products, Inc. All other product or service names are the property of their respective owners.。
dsl 组合条件-概述说明以及解释

dsl 组合条件-概述说明以及解释1.引言1.1 概述概述在软件开发领域,领域特定语言(Domain Specific Language,简称DSL)是一种用于解决特定问题领域的编程语言。
DSL与通用编程语言相比,更加专注于解决特定问题,具有更高的表达能力和灵活性。
DSL组合条件是DSL中一种重要的特性,它允许我们根据特定的需求将多个条件组合起来使用。
通过使用组合条件,我们可以更加方便地构建复杂的逻辑表达式,满足更加复杂的业务要求。
本文将探讨DSL组合条件的意义以及其在实际应用中的用途。
我们将首先介绍DSL的基本概念,然后重点讨论组合条件的概念和意义。
接着,我们将通过一些实际的应用场景,展示DSL组合条件的实际应用效果和优势。
通过深入了解DSL组合条件,我们可以更好地掌握DSL的使用技巧,并在实际开发中更高效地应用DSL来解决问题。
本文旨在为读者提供对DSL组合条件的全面理解,并展望DSL组合条件在未来的发展趋势。
在接下来的章节中,我们将进一步探讨DSL组合条件的相关概念和实际应用,并为读者提供更多有关DSL组合条件的详细信息。
文章结构部分的内容可以如下所写:1.2 文章结构本文共分为三个主要部分:引言、正文和结论。
在引言部分,将对整篇文章进行概述,包括给出对DSL组合条件的简要定义和介绍。
随后,将阐述文章的结构和目的,为读者提供整个文章的框架和目标。
正文部分将详细探讨DSL组合条件的相关内容。
首先,通过解释什么是DSL,读者将了解到DSL在编程中的作用和意义。
接下来,将详细探讨组合条件的意义,解释为什么在实际应用中需要使用多个条件的组合。
最后,将通过一些实例来展示DSL组合条件在实际场景中的应用和优势。
结论部分将对全文进行总结和归纳,概括主要观点和在DSL组合条件方面的展望。
首先,将总结文章中所介绍的关键观点和结论。
接着,将展望DSL组合条件在未来的发展和应用前景。
最后,通过对整篇文章的回顾和总结,给出最终的结论。
uno platform的xaml语法

一、什么是Uno Platform?Uno Platform是一个开源跨评台应用程序框架,让开发者可以用统一的XAML和C#代码来创建跨评台应用。
这意味着开发者可以使用Uno Platform来构建适用于Windows、iOS、Android和Web的应用程序,极大地提高了开发效率和代码重用性。
二、什么是XAML语法?XAML是一种可扩展的应用程序标记语言,用于定义用户界面的布局和外观。
它与C#代码相结合,用于创建跨评台应用程序的用户界面。
Uno Platform的XAML语法与传统XAML语法相似,但又有一些特定的差异和扩展。
三、Uno Platform的XAML语法特点1. 支持多个评台Uno Platform的XAML语法支持多个评台,包括Windows、iOS、Android和Web。
开发者可以使用相同的XAML语法和C#代码来创建适用于不同评台的用户界面,而无需进行大量的重复工作。
2. 支持数据绑定Uno Platform的XAML语法支持数据绑定,开发者可以将界面元素与数据模型进行绑定,实现界面和数据的实时同步。
这使得开发者可以更轻松地管理用户界面和数据之间的交互。
3. 支持动画和转换Uno Platform的XAML语法支持动画和转换效果,开发者可以通过简单的XAML语法来实现界面元素的动画效果和转换效果,提升用户体验。
4. 支持自定义控件Uno Platform的XAML语法支持自定义控件,开发者可以通过XAML语法和C#代码来创建自定义的用户界面控件,满足特定的需求和设计要求。
5. 支持样式和模板Uno Platform的XAML语法支持样式和模板,开发者可以通过XAML语法来定义界面元素的外观和布局样式,实现界面的统一风格和可重用性。
6. 支持响应式设计Uno Platform的XAML语法支持响应式设计,开发者可以使用XAML语法和C#代码来创建适配不同设备屏幕大小和分辨率的用户界面,提升应用程序的适用性和用户体验。
TR-062 ADSL自动配置

Technical ReportDSL ForumTR-062Auto-Configuration for the Connection Between the DSL Broadband Network Termination (B-NT) and theNetwork using ATM(TR-037 update)November 2003Produced by:Auto-Configuration Working GroupEditor: Sven Ooghe, AlcatelWorking Group Co-Chair: Greg Bathrick, Samsung Working Group Co-Chair: Tony Stankus, SamsungNotice:The DSL Forum is a non-profit corporation organized to create guidelines for DSL network system development and deployment. This Technical Report has been approved by members of the Forum. This document is not binding on the DSL Forum, any of its members, or any developer or service provider involved in DSL. This document is subject to change, but only with approval of members of the Forum. ©2003 Digital Subscriber Line Forum. All Rights Reserved.DSL Forum technical reports may be copied, downloaded, stored on a server or otherwise re-distributed in their entirety only.Notwithstanding anything to the contrary, the DSL Forum makes no representation or warranty, expressed or implied, concerning this publication, its contents or the completeness, accuracy, or applicability of any information contained in this publication. No liability of any kind shall be assumed by the DSL Forum as a result of reliance upon any information contained in this publication. The DSL Forum does not assume any responsibility to update or correct any information in this publication.Table of Contents1 Introduction (4)2 Scope (4)3 Definitions (5)3.1 Access Protocol (5)3.2 Connection (5)3.3 Service (5)4 Auto-Configuration Requirements (6)5 Configuration Parameter Categories (7)6 ILMI-based B-NT Auto-Configuration (8)7 Use of ILMI Layer 2 and Layer 3 Protocol Id Objects (10)7.1 Usage of LLC (11)7.2 Access Protocol (11)7.3 Encapsulation Specification Encodings (12)8 Required ILMI Objects (15)8.1 ATM Service Category and Traffic Conformance Definition Objects (15)9 References (17)1 IntroductionThis recommendation specifies a set of configurable parameters for DSL B-NT thatwill be used to access a variety of broadband services. The B-NT is the functionalelement that exists between the U and S interfaces at the customer premises (see TR-017 [15] for the DSL Forum reference model). The B-NT configurable parameters are derived from specific protocol-related parameters, as well as parameters necessary for enabling certain types of business models for DSL service deployment. Theseparameters configure a B-NT to use an ATM virtual channel connection from the B-NT through the Network Access Provider (NAP). It thus allows the B-NT to utilizeprovisioned ATM communications with the Network Service Provider (NSP) and lays the groundwork for further configuration of services supported by the connections.An important goal of parameter selection is to avoid, as much as possible, any end-user involvement in the setup and configuration of B-NT. The parameter specification is oriented towards a mass-market, where the consumer often has little or no technical expertise.Wherever possible, existing management protocols will be utilized for communication of these configurable parameters to the B-NT. The goal is to support auto-configuration of B-NT parameters dealing with the protocols carried over the U-interface.This recommendation does not define the end-to-end provisioning/operations modelbut is cognizant that such an environment exists and will be the subject of future work.It is expected that the architectural underpinnings for delivery of these configurableparameters through a network to the B-NT will mark the end of the chain in an overall flow-through provisioning model. The architecture is not limited or bound to aspecific deployment scenario or model — instead it will be generic enough toaccommodate several models. Usage of these parameters does not require theexistence of a complete flow-through environment.2 ScopeThe scope of this recommendation is to provide a robust and reliable B-NT auto-configuration method that will enable a DSL B-NT to obtain automatically from thenetwork sufficient information to utilize Layer 2 connections to one or more network services. It is anticipated that a future recommendation will detail the specifics oflayer-3 auto-configuration.This document provides specific recommendations for Permanent Virtual Connections (PVCs) and Switched Virtual Connections (SVCs). However, the material concerning SVCs is not complete and subject for future work.This recommendation assumes existence of a packet stream transported over ATMvirtual channel connections. Since Layer 2 has multiple sublayers, and because thesublayers may exhibit tight functional coupling, there is no simple statement of scope that is precise in all cases. Therefore, the term “access protocol” is defined as all of the layer 2 protocols and encapsulations above the AAL.At completion of the procedures in this document, the B-NT will know:• What VCCs are provisioned• ATM Traffic Management parameters, AAL protocol and AAL parameters for each VCC• What access protocols are carried on those VCCs, and in what formats• Any associated characteristics of the access protocol.This recommendation addresses only auto-configuration of B-NT over the U interface.It does not address other network management of B-NT devices, such as faultdetection, performance, or firmware upgrade. This procedure augments preexistinginteroperability capabilities to allow auto-configuration of the parameters outlinedabove.3 DefinitionsThis document makes use of terms defined in DSL Forum TR-012 [1]. In addition tothose definitions, this document uses the following terms:3.1 Access ProtocolAn access protocol is all of the encapsulation and layer 2 protocols necessary to accessa service.3.2 ConnectionIn this recommendation, a “connection” is an ATM virtual channel connection fromthe B-NT, through the NAP, to the first-level aggregation point in a network including any access protocol.3.3 ServiceIn this document, a service is any layer 3 protocol capability that exists above theconnection that is required to provide access to an NSP. The term “service” in thecontext of this document implies layer 3 service connectivity.4 Auto-Configuration RequirementsThis recommendation is intended to meet the following requirements:• Minimize customer interaction and truck roll• Support arbitrary NAP/Multiple NSP/Customer relationships• Support independent NAP/NSP/Customer Premises Network management schemes• Support multiple services• Should work in existing networks, regulatory environments• Support non-disruptive incremental service provisioning• Allow incremental deployment/upgrade of auto-configuration framework• Permit transparent transmission of realm-specific autoconfiguration information through the NAP from the NSP to the customer premises• Security Aspects shall be considered• Use other existing standards wherever possible• Must support initial service provisioning as well as refresh and reconfiguration of services• Make possible bulk-provisioning of CPE, services and/or connections within this framework.5 Configuration Parameter CategoriesFor DSL B-NT to establish a connection, the B-NT must be configured with a set ofparameters. In the following table, the configurable parameters are identified andspecified as to whether they are always required or required conditionally upon thevalue of other configured objects.Parameter Required/ConditionalVPI/VCI RequiredPHY identifier ConditionalEncapsulation RequiredATM Traffic Management parameters RequiredAAL RequiredL2 Client Protocol ConditionalL2 Auth Type ConditionalL2 Auth Data ConditionalTable 1: Configuration ParametersTable ColumnsThe Parameter field is the name of the parameter or parameter group that is beingreferenced.The Required/Conditional field indicates whether a particular parameter or parameter category is considered required all cases or is conditionally required based on thevalues of other required objects.Although L2 Auth Type and L2 Auth Data are parameters that may be required forestablishing the connection, they are not auto-configured. Auto-configuration of these parameters would defeat the purposes for which they are intended.Parameter/Category DescriptionsVPI/VCI – The ATM VPI and VCI (Virtual Path Identifier/Virtual ChannelIdentifier) uniquely identify the ATM virtual channel connection between the B-NTand the DSLAM, and thus allow the B-NT to identify the ATM virtual channelconnection to an NSP.PHY Identifier – This parameter selects which latency channel (fast or interleaved) is to be used for this VCC. It is used only for dual latency DSL PHYs.Encapsulation – This parameter group indicates the encapsulation and service layerprotocol.ATM Traffic Management Parameters – This parameter group provides the ATM service category, traffic contract parameters (if any) and QoS parameters (if any) forthe connection.AAL – This parameter group selects the ATM adaptation layer protocol (e.g., AAL2, AAL5, etc.) and its parameters that are being used for this connection.L2 Client Protocol – (Layer-2 Client Protocol) This parameter selects the accessprotocol used to access the service.L2 Auth Type – This parameter selects what type of Layer 2 authentication isrequired by the NSP (if any).L2 Auth Data – This parameter provides the authentication parameters to be used for instantiating the L2 connection to the NSP.6 ILMI-based B-NT Auto-ConfigurationDSLAMs supporting B-NT Auto-Configuration shall implement the subset of theATM Forum ILMI 4.0 specification (and its extensions) defined in this section.Interfaces to configure the network-side IME, although required, are not described in this recommendation.From the perspective of the B-NT, the following procedure shall be used for auto-configuration of PVC-based connections.1. The Network-side IME (Interface Management Entity)-based ILMI objects arepopulated (possibly through flow-through methods) with the values for theparticular subscriber/service associations. In this example, possible serviceendpoints include NSP1 and NSP 2.2. If the customer orders both these services, and if the two services are to beprovided across separate VCCs, the ILMI MIB containing the serviceconfiguration is instantiated with at least two entries in the Service Type andService Connection Info Tables (NSP1, NSP 2) and two entries in the VCC table(NSP1, NSP 2).3. The B-NT is powered on and the DSL physical connection is established. Anyphysical or TC layer configuration can be completed at this time.4. Cell delineation is achieved and the ILMI channel is initiated.5. The IMEs at both sides of the link send a Cold Start TRAP. The user-side IME inthe B-NT sends GETs for the ILMI Attachment Point Objects. The Network sideIME responds to these GETs. (NOTE: both the B-NT and Network should attemptthe exchange of Cold Start Traps several times to deal with cases where a trap iscorrupted).6. The User side IME sends a series of GETNEXT REQUESTs to the Network sideIME to obtain its user profile (ServiceType Table, VCC Table, ServiceConnInfoTable) and configuration parameters for each PVC. Two of the objects obtained.(the atmfAtmServiceLayer2ProtocolId andatmfAtmServiceLayer3ProtocolId object) contain information on howthe B-NT should access a particular service. The syntax of this object is describedin section 8.7. The ATM Layer is now active, PVCs are configured, and the B-NT has sufficientinformation to utilize the connection to the NSP.8. Whenever the network changes the configuration of any ATM connection on theU interface (including when the service table associated with that connection has changed), the Network-side IME sends either the atmfVCCchange oratmfVPCchange traps. This causes the User-side IME to query the Network-side IME for an update of the auto-configuration and other MIB elements regarding the connection that may have changed. A robust implementation SHOULD attempt to discover and apply the parameters modified on the Network-side IME, as thisprevents disruption to services being delivered across the IME representing the B-NT’s U interface. Section 8.3.5 of [2] specifies that the B-NT should reset the IME receiving the atmfVCCchange or atmfVPCchange when there are changes toobjects that are not in the Virtual Path Group or the Virtual Channel Group.SNMP traps are not assumed reliable, and SNMP version 1, as used by ILMI, does not provide for acknowledgement of traps. However, the parameter poll from the B-NT IME can be interpreted as the acknowledgement of these traps. If theNetwork-side IME does not receive the parameter poll before expiry of a timer (which is network specific) it may re-send the trap. However, the Network-side IME must allow sufficient time to prevent repeated action by the User-side IME, should the User-side IME's response to the first trap be delayed.After PVCs are auto-configured, the B-NT may undergo address registration if it supports SVCs; the procedures are defined in section 9.5 of [2].Use of SVCs and PVCs on the same DSL is not precluded.ILMI traffic requirements and policyFor the specific case of ILMI communication in the DSL auto-configuration architecture, the following requirements are used instead of the requirements of section 5.4 of ATMF ILMI 4.0:• The VCC used for ILMI communication MUST support a sustainable cell rate, R(s), no more than the minimum between 4 ATM cells per second and 1% of the xDSL Interface minimum line rate;• The peak cell rate, R(p), MUST NOT be more than 16 ATM cells per second; • The ILMI traffic burst length, L(b), MUST NOT be more than 12 ATM cells; • The Access Node and the B-NT SHOULD submit one request at a time and wait for the answer before submitting the next request. This allows the Access Node to perform the auto-configuration to B-NTs minimizing the possible re-transmission of messages from B-NT after time-out.Message Response TimeConsidering thousands of B-NTs are potentially connected to the Access Node, the message response time may exceed the requirement from section 5.5 of ATMF ILMI 4.0. As a consequence and according to the traffic policy above, the value of S = 5 seconds MUST be used as the minimum for re-transmission, instead of the previous default value of S = 1 second.ILMI Connectivity ProceduresThe Access Node does not periodically test ILMI Connectivity when LinkConnectivity is established, this in order to limit the overall ILMI traffic that theAccess Node must handle. It relies on the B-NT that may or may not perform this test to detect subsequent loss of ILMI Connectivity.When the B-NT is testing connectivity with the Access Node, the default andminimum testing value MUST be T = 30 seconds, instead of the previous defaultvalue of T = 5 seconds in section 8.3.1 of ATMF ILMI 4.0.7 Use of ILMI Layer 2 and Layer 3 Protocol Id ObjectsThis section describes the syntax and usage of the ILMIatmfAtmServiceLayer2ProtocolId and atmfAtmServiceLayer3ProtocolId objects.These objects are defined in the ATM Forum PVC Autoconfiguration Addendum [5].This recommendation defines how these objects shall be used to select accessprotocols that are used in the DSL environment. The syntax is based on ISO/IECTR9577 Network Layer Protocol Identification [9], and is compatible with the coding of the Broadband Low-Layer Information (B-LLI) information element in ITU-TRecommendation Q.2931 [10] (which is referenced by Sig 4.1). This coding wasselected because it:• Covers all wide-spread deployments.• Can be extended to most foreseeable applications, without requiring approval by other standards bodies• Is consistent with SVC signalingAdditional guidance on the use of the NLPID encoding is derived from are RFC 2684[14] (Multi-protocol Encapsulation over ATM, which obsoletes RFC 1483), and ITU-T Recommendation Q.2931 [10]. Further guidance is taken from RFC 1755 [11](Signaling for IP over ATM), and RFC 2364 [12] (PPP over ATM), which includessignaling. This recommendation extends the codings of these RFCs to cover specificaccess protocols common in the DSL environment.NOTE: This recommendation divides the access protocol into two parts: the“encapsulation” and the protocol included by the encapsulation. RecommendationQ.2931 and Sig 4.0 call these two parts “layer 2” and “layer 3.” However, the accessprotocol may be below layer 3 (e.g., Ethernet), even though it is specified in the “layer 3” parameter (atmfAtmServiceLayer3ProtocolId object or User Information Layer 3Protocol in the B-LLI Information Element).The encoding of the Layer2 and Layer 3 protocol ID objects is specifically chosen to be the same as that in the corresponding octet groups of the Q.2931 B-LLIInformation Element. The auto-configuration procedure requires using both the UserInformation Layer2 and User Information Layer 3 octet groups of the B-LLIInformation Element (as permitted by RFC1755).This recommendation does not provide a method to auto-configure multiple servicesover a single connection, other than to specify the highest common multi-protocolencapsulation. Further multiplexing may be done using in-band protocolidentification.ISO/IEC TR-9577 provides for an Initial Protocol Identification and a SubsequentProtocol Identification, thereby allowing for two sublayers of protocol (e.g., above the encapsulation layer). The Subsequent Protocol Identification is not presently neededin the DSL environment, and cannot be encoded in the B-LLI Information Element. 7.1 Usage of LLCThere are two categories of encapsulations: RFC 2684 LLC encapsulations, and “null”(sometimes called “VC-multiplexed”) encapsulations. This recommendation allowsconfiguration of LLC or “null” encapsulation, independent of the access protocol.The abstract syntax of the ILMI atmfAtmServiceLayer2ProtocolId object is an octet string. In the auto-configuration procedure for PVCs, the Network IME sets the object to either have a value equal to '0x00' (indicating the null encapsulation), or have a length of 1 octet with the value '0x0C' (indicating LLC encapsulation).7.2 Access ProtocolThere are a variety of access protocols in use in the DSL environment, e.g., Ethernet, IP, PPP, as well as combinations such as IP over Ethernet. This method configures the access protocol using the syntax of ISO/IEC TR9577 [9], but with additionalsemantics defined here. Since ISO/IEC TR9577 specifies a “protocol,” (rather than aprotocol and an encapsulation), this recommendation defines how the TR9577 syntax may be used to specify the “encapsulation”.The two basic rules for encoding of the Layer 3 protocol identifier octet string are:1. The “SNAP” encoding of Layer 3 protocol identifier indicates “LLC-SNAP” if theLayer 2 protocol identifier indicates "LLC". In this case, the first six octets of eachAAL5 PDU contain a SNAP header. Otherwise, SNAP is used only to select theaccess protocol used with the Null encapsulation.2. If the Layer 3 protocol identifier indicates Ethernet, it may be optionally followedby a 2-byte Ethertype, to further qualify the protocol supported. Such aspecification indicates Ethernet encapsulation, and support for the givenEthertype. Obviously related Ethertypes are also supported; for example, IP overEthernet (Ethertype 0x0800) includes support for ARP over Ethernet (Ethertype0x0806), and PPPoE (Ethertype 0x8864) includes support for PPPoE Setup(Ethertype 0x8863). (See “A Method for Transmitting PPP over Ethernet”, RFC2516 [13] for more information on PPPoE.)Another example is arbitrary Ethertypes directly over AAL5 (without the Ethernetencapsulation). Such protocols can be specified with a Layer-3-Information ofSNAP, and OUI of 00-00-00, and the Ethertype.The ILMI atmfAtmServiceLayer3ProtocolId object is an octet string. Inthe auto-configuration procedure for PVCs, the Network-side IME sets the object tothe octet string for the access protocol.7.3 Encapsulation Specification EncodingsThis section shows how the atmfAtmServiceLayer2ProtocolId andatmfAtmServiceLayer3ProtocolId objects shall be encoded for thosecombinations of access protocol and encapsulation that are widely used in the DSLenvironment. Other access protocols and encapsulations are not precluded, and shallbe encoded in a fashion consistent with this section and the ATM Forum PVCAutoconfiguration Addendum.The encapsulation identifier sequence specifies only the required lower protocol layers of the service. The service may support any combination of higher layer protocolsabove the lower layer service definition. For example, in the case of Ethernet bridged (RFC 2684) encapsulation, IP, IPX, AppleTalk could all be run as higher-layerprotocols. In the case of IP over Ethernet bridged (RFC 2684) encapsulation, only IPwould be run, including all associated helper protocols such as ARP and DHCP.The following table shows the encodings of these objects for combinations of accessprotocol and encapsulation. In some case, the semantics of each encoding is given inan adjoining row or column of the table. All encodings are in hexadecimal. All multi-octet values are NBO (Network Byte Order, or Big-Endian). The parsing rules may be represented as a tree, as shown in Figure 1. The “Diagram Case” column provides the tree branch corresponding to the protocol/encapsulation in the table.Access Protocol Dia-gramCase Encap Protocol StackingLayer2Pro-tocolIDLayer 3Protocol IDLLC/NoneISO9577PPPoA A LLC PPP 0C0B CFB Null PPP 000B CFPPPClassical IP C LLC IP 0C 0B8000000008 00snap OUIE’typeIPD Null IP 00 0B CCIPRFC2684 E LLC eth no fcs0C 0B800080C200 07Bridged F Null eth no fcs00 0B800080C200 07snap802.1 oui Eth no fcsLLCethfcs 0C0B800080C20001Null ethfcs 000B800080C20001snap802.1 oui Eth w/ fcsRFC2684 G LLC eth no fcs IP 0C 0B800080C200 07 08 00 Bridged H Null eth no fcs IP 00 0B800080C200 07 08 00 w/ IP snap802.1 oui Eth no fcs IPLLC eth fcs IP 0C 0B800080C200 01 08 00Null eth fcs IP 00 0B800080C200 01 08 00snap802.1 oui PID eth fcs IP RFC2684 J LLC eth no fcs PPP 0C 0B800080C200 07 88 64 Bridged K Null eth no fcs PPP 00 0B800080C200 07 88 64 W/ PPPoE snap802.1 oui Eth no fcs PPPoE LLC eth fcs PPP 0C 0B800080C200 01 88 64Null eth fcs PPP 00 0B800080C200 01 88 64snap802.1 oui PID eth fcs PPPoE Routed IPX LLC IPX 0C 0B80000000… …snap OUIEthertype L2TP / ATM M LLC L2TP 0C 0B8000005E00 07 NNullL2TP 000B8000005E0007snap IANA OUI PID L2TPArbitrary E’type/ ATM NullArbitraryE’type000B80000000XXXXsnap EthertypeOUIEthertype Table 2: Encapsulation EncodingsCase J: PPPoE LLC-SNAP encapsulated Case G: RFC 2684 Bridged IPFigure 1: Tree representation of access protocols and encapsulations8 Required ILMI ObjectsThe MIB tables, objects and traps specified in Table 3 are mandatory requirements, with the exception of the rules specified in section 8.1 , and must be imported from their corresponding MIBs to support auto-configuration of PVCs.Defined In Group How Indexed atmfVccTable By VCC ATM Forum ILMI Specification (af-ilmi-0065.000) atmfVccChange TRAPBy VCCatmfAtmServiceTypeTable By ServiceType atmfAtmServiceConnInfoTable By VCC atmfAAL1ProfileTable By Profile atmfAAL34ProfileTable By Profile ATM Forum Autoconfiguration of PVCs Specification (af-nm-0122.000) atmfAAL5ProfileTableBy Profile atmfAAL2CommonProfileTable By Profile atmfAAL2TrunkingProfileTable By Profile atmfAAL2LESProfileTableBy Profile atmfAtmServiceConnInfoExtensionTable By VCC atmfAtmServiceTypeExtensionTable By ServiceType ATM Forum Addendum to the ILMI Auto-configuration Extension (af-nm-00165.00)atmfAtmServiceConfFail TRAP,atmfAtmServieConfFailReason OBJECT, atmfAtmServiceConfFailOID OBJECTTable 3: Required ILMI ObjectsThe B-NT, by accessing the objects defined in Table 3, can obtain the necessary information to determine ILMI connectivity and configured PVCs in a PVC-only environment.8.1 ATM Service Category and Traffic Conformance Definition ObjectsThere are overlapping objects within the set of MIB tables identified in Table 3. These are related to the specification of the ATM service category and the conformance definition to be used for an ATM PVC. In order to provide compatibility with the ATM Forum Traffic Management Specification version 4.1 (af-tm-0121.000) and to remove the overlap within the MIB tables the following rules shall be used.1. To specify the ATM service category for a PVC the atmfAtmServiceTMCategoryobject defined in the atmfAtmServiceTypeTable of [4] shall be used. TheatmfVccServiceCategory object defined in the atmfVccTable is not applicable and shall not be used.2. To specify the ATM traffic conformance definition for a PVC theatmfAtmServiceTMConformanceDef object defined in theatmfAtmServiceTypeTable of [4] shall be used. The objectsatmfVccTransmitTrafficDescriptorType, atmfVccReceiveTrafficDescriptorType and atmfVccBestEffortIndicator defined in the atmfVccTable are not applicable and shall not be used. The interpretation ofatmfVccTransmitTrafficDescriptorParam1-5 andatmfVccReceiveTrafficDescriptorParam1-5 objects defined in the atmfVccTable shall remain the same as specified in section 7.1 of [2]. The traffic type shall be inferred from the value of the atmfAtmServiceTMConformanceDef object.9 References[1] Broadband Service Architecture for Access to Legacy Data Networks overADSL, Issue 1, TR-012, DSL Forum, June 1998[2] Integrated Local Management Interface 4.0, af-ilmi-0065.000, ATM Forum,September 1996[3] User-Based Security Model for SNMP Version 3, RFC 2574, Blumenthal U.,Wijnen B., April 1999[4] Auto-configuration of PVCs Specification, af-nm-0122.000, ATM Forum, May1999[5] Addendum to the ILMI Auto-Configuration Extension, af-nm-00165.00, ATMForum, April 2002[6] Point-to-Point Protocol, RFC 1661, Simpson W., June 1994[7] Internet Protocol Control Protocol, RFC 1332, McGregor G., May 1992[8] Dynamic Host Configuration Protocol, RFC 2131, Droms R., March 1997[9] Protocol Identification in the Network Layer, ISO/IEC TR 9577, 1990[10] Broadband Integrated Services Digital Network (B-ISDN); Digital SubscriberSignaling System No. 2 (DSS 2); User-Network Interface (UNI) Layer 3Specification for Basic Call/Connection Control, Q.2931, ITU-T, 1995[11] ATM Signaling Support for IP over ATM, RFC 1755, Perez, M. et al.,February 1995[12] PPP Over AAL5, RFC 2364, Gross, G. et al., July 1998[13] Method for Transmitting PPP Over Ethernet (PPPoE), RFC 2516, Mamakos,L., February 1999[14] Multiprotocol Encapsulation over ATM Adaptation Layer 5, RFC 2684,Grossman, D., Heinanen, J., September 1999[15] ATM over ADSL Recommendation, TR-017, DSL Forum, March 1999。
领域语言(DSL)的设计与实践 蔡学镛

2010-12-15如果你是音效程序库厂商你会提供怎样的接口?2010-12-15Music Programming in OOMusicScore myMs = new MusicScore(“超人不会飞”); myMs.setFreguency(4, 6);Track pianoTk = new Track(Instructment.PIANO1);Note n1 = new Note( Note.DO, 1);painoTk.add(n1);Note n2 = new Note( Note.RE, 1);painoTk.add(n2);...2010-12-15还有进步的空间吗?2010-12-15MS [4 | 6Do 4 Re 8 Mi 2 (Fa 8 So 8) | Si 4 Do 4 ……]2010-12-15还有再进步的空间吗?2010-12-152010-12-15还有再再进步的空间吗?2010-12-152010-12-15总结上述的讨论(以微软的技術变化為例) 2010-12-15编程世界正在朝着DSL的方向走! 2010-12-15除了用别人的DSL你也可以拥有自己的DSL 2010-12-15定义DSL•领域专家与编程专家一同定义DSL •DSL的定义可能会受到领域模型的影响•定义需要的类型–DSL的实践方式可能会影响能用的类型•找出领域的关键字–DSL的实践方式可能会影响能用的关键字•定义语法–DSL的实践方式可能会影响能用的语法2010-12-15DSL的实现方式…•自己写parser•使用XML•使用语言自己的DSL机制•使用ANTLR等Code Gen工具•使用MPS等DSL开发平台2010-12-15三个实际案例1.格式转换语言2.监控系统语言3.微博查询语言2010-12-15格式转换语言•我们有一个系统,可以将各种操作系统2010-12-15监控系统的DSL应用•每个监控过程都有相当高的重复性,可以被抽取出来。
genicam写法

GenICam是一种用于机器视觉应用的标准接口规范,它为机器视觉硬件和软件定义了一套通用的、开放的API(应用程序接口)。
GenICam可以用于描述机器视觉系统的硬件和软件,包括相机、图像处理软件和图像分析库等。
在GenICam中,可以使用XML(可扩展标记语言)来描述硬件和软件的功能和参数。
GenICam XML文件通常包括以下内容:
根元素:包含所有其他元素的元素,通常命名为“gcapi”。
设备元素:描述机器视觉设备的参数,包括制造商、型号、版本等。
功能元素:描述机器视觉设备的功能,包括输入/输出图像、设置设备参数等。
参数元素:描述机器视觉设备的参数,包括相机分辨率、曝光时间、增益等。
事件元素:描述机器视觉设备的事件,包括相机触发、帧捕获完成等。
在编写GenICam XML文件时,需要遵循GenICam规范中定义的语法和规则。
通常可以使用文本编辑器或XML编辑器来编写XML文件,并使用GenICam工具来验证文件的正确性和可读性。
总之,GenICam是一种用于描述机器视觉系统和设备的开放标准,它提供了一套通用的API 和XML文件格式来定义机器视觉应用的功能和参数。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
DSL Implementation inMetaOCaml,Template Haskell,and C++Krzysztof Czarnecki1,John O’Donnell2,J¨o rg Striegnitz3,and Walid Taha41University of Waterloo,Canada2University of Glasgow,United Kingdom3Research Centre J¨u lich,Germany4Rice University,USAAbstract.A wide range of domain-specific languages(DSLs)has beenimplemented successfully by embedding them in general purpose lan-guages.This paper reviews embedding,and summarizes how two alter-native techniques—staged interpreters and templates—can be used toovercome the limitations of embedding.Both techniques involve a formof generative programming.The paper reviews and compares three pro-gramming languages that have special support for generative program-ming.Two of these languages(MetaOCaml and Template Haskell)areresearch languages,while the third(C++)is already in wide industrialuse.The paper identifies several dimensions that can serve as a basis forcomparing generative languages.1IntroductionA basic design choice when implementing a programming language is whether to build an interpreter or a compiler.An interpreter realizes the actions of the pro-gram by stepping through the source program.A compiler consists of a translator and a runtime system.The translator maps the source program to a program in an existing language,while the runtime environment provides the primitives needed for the resulting program to be executable.Translation can be to a lower-level language—as is the case in traditional compilers—or to a high-level language for which we already have an implementation.An interesting special case occurs when no translation is needed.This means that the new language is both syntactically and semantically a subset of an existing host language.In this case,all we need is to implement the runtime system as a library in the host language.This approach of embedded languages has recently gained significant popularity in the functional programming com-munity[19].Functional languages make it possible to implement DSLs that are more sophisticated than is possible with traditional languages.For exam-ple,lambda abstractions can be used conveniently to allow DSLs with binding constructs,and nontrivial type systems for the DSLs can be encoded within the sophisticated type systems provided by functional languages.From the DSL implementer’s point of view,the benefits of this approach include reusing the parser,type checker,and the compiler of an existing language to implement anew one.Examples of embedded DSLs include parsing[32,22,37],pretty print-ing[21],graphics[12,11],functional reactive programming[20],computer music [18],robotics[40],graphical user interfaces[4],and hardware description lan-guages[1,31,36].While this approach works surprisingly well for a wide range of applications,embedding may not be appropriate if there is–Mismatch in concrete syntax.A prerequisite for embedding is that the syn-tax for the new language be a subset of the syntax for the host language.This excludes many stylistic design choices for the new language,including potentially useful forms of syntactic sugar and notational conventions.Fur-thermore,as DSLs become easier to implement,we can expect an increase in the use of graphical notations and languages,which often do not use the same syntax as potential host languages.–Mismatch in semantics.The embedding approach requires that the seman-tics for the DSL and host languages coincide for the common subset.For ex-ample,two languages may share the same syntax but not the same semantics if one is call-by-value and the other is call-by-name.A more domain-specific example arises in the Hydra language[36],which uses the same syntax as Haskell,but which has a different semantics.Even when these problems can be avoided,the resulting implementation may be lacking in a number of ways:–Domain-specific type-systems.Often DSLs are designed to have limited ex-pressiveness.This is generally hard to achieve with embedding because the DSL inherits the type system of the host language.For instance,consider a host language with subtyping and dynamic dispatch and a DSL for which we want just static method binding.–Error messages.Similarly,when an embedded program fails to type check in the host language,the error messages are expressed in terms that are often incomprehensible(and arguably irrelevant)to the DSL user.–Debugging support.Trying to use the debugger for the existing language is not always useful,as it often exposes details of the runtime system for the host language which are of no interest to the DSL user.–Domain-specific optimizations.Embedding does not lend itself naturally to realizing optimizations that are valid only for the domain,or that simply do not happen to be provided by the existing language implementation.This situation is further aggravated by the fact that the official definitions of many popular host languages do not specify what optimizations the compiler must perform.Contributions and organization of the rest of this paper While there have been a number of promising proposals for addressing each of these points (c.f.[39]for typing,[10,8,58]for optimizations),all these approaches use pro-gram manipulation and generation,which can involve substantially more effort, care,and expertise on the part of the DSL implementer[47].Because of the potential for specialized programming language support to help in controllingthe complexity of generative programs,we compare three languages in terms of what they offer to support these approaches.Thefirst two are the research languages MetaOCaml[2,33]and Template Haskell[44],presented in Sections2 and3respectively.The third is the C++language(Section4),which is already in industrial use for generative programming,although it was not designed with that purpose in mind.Throughout the paper,an attempt is made to introduce only the essential terminology for each of the languages,and to introduce termi-nology useful for comparing and contrasting these languages.Section5presents a comparative analysis of the three languages.The goal of this analysis is to identify and highlight the key differences between the three languages and the design philosophies they represent.Section6concludes.2MetaOCamlMetaOCaml is a multi-stage extension of the OCaml programming language[2, 33].Multi-stage programming languages[51,47,52]provide a small set of con-structs for the construction,combination,and execution of program fragments. The key novelty in multi-stage languages is that they can have static type sys-tems that guarantee a priori that all programs generated using these constructs will be well-typed.The basics of programming in MetaOCaml can be illustrated with the following declarations:let rec power n x=(*int->.<int>.->.<int>.*)if n=0then.<1>.else.<.~x*.~(power(n-1)x)>.let power3=(*int->int*).!.<fun x->.~(power3.<x>.)>.Ignoring the code type constructor.<t>.and the three staging annotations brackets.<e>.,escapes.~e and run.!,the above code is a standard definition of a function that computes x n,which is then used to define the specialized func-tion x3.Without staging,the last step just produces a function that invokes the power function every time it gets a value for x.The effect of staging is best under-stood by starting at the end of the example.Whereas a term fun x->e x is a value,an annotated term.<fun x->.~(e.<x>.)>.is not.Brackets indicate that we are constructing a future stage computation,and an escape indicates that we must perform an immediate computation while building the bracketed computation.The application e.<x>.has to be performed even though x is still an uninstantiated symbol.In the power example,power3.<x>.is performed immediately,once and for all,and not repeated every time we have a new value for x.In the body of the definition of the power function,the recursive applica-tion of power is also escaped to make sure that they are performed immediately. The run.!on the last line invokes the compiler on the generated code fragment, and incorporates the result of compilation into the runtime system.The basic approach to implementing DSLs in MetaOCaml is the staged in-terpreter approach[13,26,25,43].First,an interpreter is implemented and testedfor the DSL.Then,the three staging constructs are used to produce an imple-mentation that performs the traversal of the DSL program in a stage earlier than the execution of the essence of the program.Implementations derived in this manner can be as simple as an interpretive implementation,and at the same time have the performance of a compiled implementation.2.1A QBF InterpreterWe consider a simplistic DSL motivated by the logic of quantified boolean for-mulae(QBF).The syntax of such a language can be represented in OCaml as follows:type bexp=True(*T*)|False(*F*)|And of bexp*bexp(*T^F*)|Or of bexp*bexp(*T v T*)|Not of bexp(*not T*)|Implies of bexp*bexp(*F=>T*)|Forall of string*bexp(*forall x.x and not x*)|Var of string(*x*)Formulae such as∀p.T⇒p can be represented using this datatype by the value Forall("p",Implies(True,Var"p")).Implementing this DSL would involve implementing an interpreter that checks the validity of the formula.Such a function is implemented concisely by the following(Meta)OCaml code:exception VarNotFound;;let env0x=raise VarNotFoundlet ext env x v=fun y->if y=x then v else env ylet rec eval b env=match b withTrue->true|False->false|And(b1,b2)->(eval b1env)&&(eval b2env)|Or(b1,b2)->(eval b1env)||(eval b2env)|Not b1->not(eval b1env)|Implies(b1,b2)->eval(Or(b2,And(Not(b2),Not(b1))))env|Forall(x,b1)->let trywith bv=(eval b1(ext env x bv))in(trywith true)&&(trywith false)|Var x->env xThefirst line declares an exception that may be raised(and caught)by the code to follow.We implement an environment as a function that takes a name and either returns a corresponding value or raises an exception if that value is not found.The initial environment env0always raises the exception because it contains no proper bindings.We add proper bindings to an environment usingthe function ext,which takes an environment env,a name x,and a value v. It returns a new environment that is identical to env,except that it returns v if we look up the name x.The evaluation function itself takes a formula b and environment env and returns a boolean that represents the truth of the formula.2.2A Staged QBF InterpreterAn interpreter such as the one above is easy to write,but has the undesirable property that it must repeatedly traverse the syntax of the DSL program while evaluating it.For the interpreter above,when a formula contains quantifiers, sub-terms will be evaluated repeatedly,and traversing them multiple times can have a significant effect on the time and space needed to complete the compu-tation.Staging can allow us to separate the two distinct stages of computation: traversing the term and evaluating it.The above interpreter can be staged by adding brackets.<...>.and escapes.~...as follows:let rec eval’b env=match b withTrue->.<true>.|False->.<false>.|And(b1,b2)->.<.~(eval’b1env)&&.~(eval’b2env)>.|Or(b1,b2)->.<.~(eval’b1env)||.~(eval’b2env)>.|Not b1->.<not.~(eval’b1env)>.|Implies(b1,b2)->.<.~(eval’(Or(b2,And(Not(b2),Not(b1))))env)>.|Forall(x,b1)->.<let trywith bv=.~(eval’b1(ext env x.<bv>.))in(trywith true)&&(trywith false)>.|Var x->env xWhereas eval interleaves the traversal of the term with performing the com-putation,eval’traverses the term exactly once,and produces a program that does the work required to evaluate it.This is illustrated by the following session in the MetaOCaml interactive bytecode interpreter:#let a=eval’(Forall("p",Implies(True,Var"p")))env0;;a:bool code=.<let trywith=fun bv->(bv||((not bv)&&(not true)))in((trywith true)&&(trywith false))>.Note that the resulting computation is using only native OCaml operations on booleans,and there are no residual representations of the DSL program that was parsed.MetaOCaml allows us to execute generated code fragments by invoking the compiler on each code fragment,and then incorporating the result into the run-time environment.This is done concisely using the run construct.!:#.!a;;-:bool=false2.3Domain-specific Analysis and OptimizationsBecause functional programming languages have concise notation for represent-ing parse trees(algebraic datatypes),domain-specific optimizations can be de-fined concisely in MetaOCaml.Pattern matching is particularly convenient when we want to implement such optimizations:let rec optimize e=match e with...|Or(e,False)->optimize e|And(e,True)->optimize e...Note that here we are pattern matching on the datatype used to represent the DSL programs,not on the MetaOCaml code type(which is the return type of the staged interpreter above).Pattern matching on the code type is not encour-aged5,primarily because it is currently not known how to allow it without either allowing ill-typed code to be generated or to make substantial changes to the MetaOCaml type system[49].This way the programmer is sure that once a par-ticular code fragment is generated,the meaning of this code fragment will not change during the course of a computation.2.4The User’s ViewStaged interpreters can be provided as libraries that have the same interface as a traditional interpreter.For example,we can redefine eval as:#let eval a env=.!(eval’a env);;This function has the same signature as the one above,but different perfor-mance characteristics.Because MetaOCaml is an extension of a general purpose programming language(OCaml),implementing parsers and loaders is not prob-lematic,and it is easy to see how we can directly execute small DSL programs written in concrete syntax,and load bigger ones from afile:#eval(parse"forall x.x and not x");;#eval(parse(load"myTheorem.dsl");;3Template HaskellTemplate Haskell is an extension of Haskell that supports compile-time prepro-cessing of Haskell source programs[9,44].The goal of Template Haskell is to enable the Haskell programmer to define new language features without having to modify the compilers[28,29,16].5Using coercions it is possible to expose the underlying representation of the MetaO-Caml code type,which is the same as the datatype for parse trees used in the OCaml compiler.To illustrate some of the constructs of Template Haskell,we present an analog of the power example above.The expand power function builds an expression that multiplies n copies of the expression x together,and mk power yields a function that computes x n for any integer x.module A whereimport Language.Haskell.THSyntaxexpand_power::Int->Q Exp->Q Expexpand_power n x=if n==0then[|1|]else[|$x*$(expand_power(n-1)x)|]mk_power::Int->Q Expmk_power n=[|\x->$(expand_power n[|x|])|]A specialized function power3is now defined using$to splice in the code pro-duced at compile time by mk power3.module Main whereimport Language.Haskell.THSyntaximport Apower3::Int->Intpower3=$(mk_power3)In this example,quotations[|e|]and splice$e are analogous to the brack-ets and escape of MetaOCaml.However,there are three key differences.First, in place of MetaOCaml’s parameterized type constructor.<t>.the type for quoted values in Template Haskell is always Q Exp.Second,in the definition of module Main,the splice occurs without any explicit surrounding quotations.To compare this with MetaOCaml,the module(apart from the import directive) could be interpreted as having implicit quotations.6Third,there is no explicit run construct.The staged interpreter approach can be used in Template Haskell.A Tem-plate Haskell version of the QBF Interpreter example would be similar to the MetaOCaml version.Programs can be staged using quasi-quotes and splices. But the primary approach to implementing DSLs in Template Haskell is a vari-ation of the embedding approach.In particular,Template Haskell allows the programming to alter the semantics of a program by transforming it into a dif-ferent program before it reaches the compiler.This is possible because Template Haskell allows the inspection of quoted values.3.1Building and Inspecting Abstract Syntax TreesTemplate Haskell provides an algebraic data type for representing Haskell code as an abstract syntax tree.A part of the datatype is the following:6This analogy has in fact been formalized for macro languages[14,50].data Lit=...|Integer Integer|...data Exp=...|Var String|Lit Lit|App Exp Exp|...|Tup[Exp]|...data Pat=PLit Lit|Pvar String|Ptup[Pat]|...data Dec=Fun String[Clause]|Val Pat RightHandSide[Dec]|...data Clause=Clause[Pat]RightHandSide[Dec]data RightHandSide=Guarded[(Exp,Exp)]|Normal ExpIn addition to quotations,trees can be built explicitly using the constructors shown above.Template Haskell also provides a set of monadic operations7to construct syntax trees,which offer better support for variable renaming and input/output.Alternatively,the abstract syntax tree may be defined using a quoted ex-pression,which is more readable than explicit construction.The entire contents of a module may be quoted,in order to produce a list of abstract syntax trees comprising the entire contents of the module.An example of a quoted definition (which represents a program in the Hydra DSL)is:[|circ x y=(a,b)where a=inv xb=xor2a y|]The value of the quoted expression is a monadic computation that,when per-formed,produces the abstract syntax tree:Fun"circ"[Clause[Pvar"x’0",Pvar"y’1"](Normal(Tup[Var"a’2",Var"b’3"]))[Val(Pvar"a’2")(Normal(App(Var"Signal:inv")(Var"x’0")))[],Val(Pvar"b’3")(Normal(App(App(Var"Signal:xor2")(Var"a’2"))(Var"y’1")))[]]]This abstract syntax tree consists of one clause corresponding to the single defin-ing equation.Within the clause,there are three pieces of information:the list of patterns,the expression to be returned,and a list of local definitions for a and b.The variables have been renamed automatically in order to prevent acciden-tal name capture;for example x in the original source has become x’0in the abstract syntax tree.The numbers attached to variable names are maintained in a monad,and the DSL programmer can create new names using a monadic gensym operation.In general,it is easier to work with code inside[||]brackets;this is more concise and the automatic renaming of bound variables helps to maintain correct lexical scoping.However,the ability to define abstract syntax trees directly offers moreflexibility,at the cost of added effort by the DSL implementor.7In Haskell,computations are implemented using an abstract type constructor calleda monad[34,41].Yet another way to produce an abstract syntax tree is to reify an ordinary Haskell definition.For example,suppose that an ordinary Haskell definition f x =...appears in a program.Although this user code contains no quotations or splices,the DSL implementation can obtain its abstract syntax tree:ftree= reifyDecl f.Values and types can be reified,as well as operatorfixities(needed for compile time code to understand expressions that contain infix operators)and code locations(which enables the compile time code to produce error messages that specify where in the sourcefile a DSL error occurs).Once a piece of Haskell code has been represented as an abstract syntax tree, it can be analyzed or transformed using standard pattern matching in Haskell. This makes it possible to transform the code into any Haskell program that we wish to use as the DSL semantics for this expression.3.2The User’s ViewAs with MetaOCaml,the staged interpreter can be made available to the user as a library function,along with a parser and a loader.Such functions can only be used at compile time in Template Haskell.It is worth noting,however,that Template Haskell does allow compile-time IO,which is necessary if we want to allow loading DSL programs fromfiles.Additionally,Template Haskell’s quotations make it possible to use Haskell syntax to represent a DSL program.Template Haskell also makes it possible to quote declarations(and not just expressions)using the[d|...|]operator: code=[d|v1=[1,2,3]v2=[1,2,3]v3=[1,2,3]r=v1’add’(v2’mul’v3)|]Then,another module could apply a staged interpreter to this code in order to transform the original code into an optimized version and splice in the result.Template Haskell also allows templates to construct declarations that intro-duce new names.For example,suppose we wish to provide a set of specialized power functions,power2,power3,up to some maximum such as power8.We can write a Template Haskell function that generates these functions,using the mk power defined above,along with the names,and then splices them into the program:$(generate_power_functions8)4C++TemplatesOriginally,templates were intended to support the development of generic con-tainers and algorithms.Driven by the practical needs of library implementers,the C++template mechanism became very elaborate.By chance rather than by design,it now constitutes a Turing-complete,functional sub-language of C++ that is interpreted by the C++compiler[54,57].Consequently,a C++program may contain both static code,which is evaluated at compile time,and dynamic code,which is compiled and later executed at runtime.Static computations are encoded in the C++type system,and writing static programs is usually referred to as Template Metaprogramming[57].Before giving a short overview of what static code looks like,we recapitulate some C++template basics.4.1Template BasicsC++supports two kinds of templates:class templates and function templates. The basic use of class templates in C++is to define generic components.For example,we can define a generic vector as a class template with element type and size as parameters:template<class T,int size>class Vector{public:T&operator[](int i);//...T data[size];};A template is instantiated in a typedef statement as follows:typedef Vector<float,10>MyVector;Here,the type parameter T in the original definition is simply replaced by float and size by10.Now we can use MyVector as a regular C++class:MyVector v;v[3]=2.2;A template can be specialized by providing a definition for a specialized imple-mentation as follows:template<int size>class Vector<bool,size>{//...//use just enough memory for‘size’bitschar data[(sizeof(char)+size-1)/sizeof(char)];};Such specializations are useful because one general implementation of a tem-plate might not be efficient enough for some argument values.Now,whenever we instantiate Vector with bool as itsfirst parameter,the latter specialized implementation will be used.Function templates are parameterized functions.A function template to swap two values may be implemented like this:template<class T>void swap(T&a,T&b){const T c=a;a=b;b=c;}The function template swap can be called as if it were an ordinary C++func-tion.The C++compiler will automatically infer and substitute the appropriate parameter type for T:int a=5,b=9;swap(a,b);4.2Template MetaprogrammingTemplate Metaprogramming adds two rather unusual views of class templates: class templates as data constructors of a datatype and class templates as func-tions.To introduce these views,we will compare them with the corresponding Haskell definitions.Here is an example of C++template program defining a list,followed by the corresponding Haskell code.C++:struct Nil{};template<int H,class T> struct Cons{};typedefCons<1,Cons<2,Nil>>list;Haskell:data List=Nil|Cons Int List list=Cons1(Cons2Nil)The C++definitions for Nil and Cons have different dynamic and static semantics.Dynamically,Nil is the name of a class,and Cons is the name of a class template.Statically,both Nil and Cons can be viewed as data constructors corresponding to the Haskell declaration on the right.All such constructors can be viewed as belonging to a single“extensible datatype”,which such definitions extend.The C++template instantiation mechanism[23]provides the semantics for compile-time computations.Instantiating a class template corresponds to apply-ing a function that computes a class.In contrast,class template specialization allows us to provide different template implementations for different argument values,which serves as a vehicle to support pattern matching,as common in functional programming languages.Next,we compare how functions are imple-mented at the C++compile time and in Haskell:C++:template<class List>struct Len;template<>struct Len<Nil>{enum{RET=0};};template<int H,class T>struct Len<Cons<H,T>>{enum{RET=1+Len<T>::RET};};Haskell:len::List->int;len Nil=0len(Cons h t)=1+(len t)The template specializations Len<Nil>and Len<Cons<H,T>>handle the empty and non-empty list cases,respectively.In contrast to Haskell or ML,the relative order of specializations in the program text is insignificant.The compiler selects the“best match”(which is precisely defined in the C++standard[23]).This calling scheme makes static functions very extensible.Having an exten-sible datatype and extensible functions,C++Template Metaprogramming does not suffer from the extensibility problem[27].The::operator is used to access the name space of the class.For example, Len<list>::RET will evaluate to2.The member being accessed could also be a computed type or a static member function.Template Metaprogramming also supports higher-order functions through so-called template template parameters.In relation to DSL implementation,C++templates can be used in two dis-tinct ways:at the type level,and at the expression level.Thefirst is comparable to Template Haskell’s mechanism to analyze and build new declarations.The second is comparable to the staged interpreters approach,except that no parser has to be implemented.4.3Type-driven DSLsTemplate Metaprogramming allows us to write configuration generators[5].Typ-ically,such generators must check parameters,compute default values,and per-form any computations necessary for assembling generic components.Syntacti-cally,type-driven DSLs are subsets of C++type expressions.To give a concrete example of such a type-driven DSL,consider a generator for different imple-mentations of matrix types.The DSL program(which results in invoking the generator)can be written as follows:typedef MatrixGen<ElemType<float>,Optim<space>,Shape<u_triang>>::RET M1; typedef MatrixGen<Shape<l_triang>,Optim<speed>>::RET M2; MatrixGen takes a list of properties,checks their validity,completes the list of properties by computing defaults for unspecified properties,and computes the appropriate composition of elementary generic components such as containers, shape adapters and bounds checkers.This configuration generator uses a specific style for specifying properties that simulates keyword parameters:for example, when we write ElemType<float>we have a parameter float wrapped in the。
