Resource Configuration and Allocation A Case Study of Constrained Heuristics
LTE协议简介

UE IP address allocation
S1 Packet Filtering internet
EPC
eNB的功能
无线资源管理功能(Functions for Radio Resource Management)
无线承载控制(Radio Bearer Control) 无线接入控制(Radio Admission Control) 连接移动性控制(Connection Mobility Control) UE资源动态分配(Dynamic allocation of resources for UE)
控制平面功能
NAS控制协议 :
EPS承载管理; 鉴权; ECM-IDLE 移动性处理; ECM-IDLE 寻呼管理; 安全控制.
部署家庭基站(HeNB)的网络架构
MME / S-ห้องสมุดไป่ตู้W
MME / S-GW
S1
S1
S1 S1
S1
S1
S1
S1
X2
eNB
eNB
HeNB GW
E-UTRAN
层1(L1)协议框架--传输信道与物理信道的映射
物理层通过“传输信道”为MAC层和高层提供信息传输 的服务。传输信道与物理信道的映射关系如图。
舰载机甲板机务勤务保障作业调度与资源配置集成优化

舰载机甲板资机源务配勤置务集保成障优作化业调度与
崔荣伟1,韩 维1,苏析超2, ,王立国3,刘玉杰1
3.犝狀犻狋92955狅犳狋犺犲犘犔犃,犎狌犾狌犱犪狅125100,犆犺犻狀犪)
犃犫狊狋狉犪犮狋:Aimingattheproblemsexistingintheresearchonthecarrierbasedaircraftflightdeckoperation scheduling,such asthesingle operation execution mode,theincompleteconsideration ofthesupport equipment,andtheindependentresearchontheoptimizationofoperationschedulingandresourceallocation, etc,theconstraintssuchasoperationflow,operationexecution mode,resourcetransferandallocationare analyzed,andthe mobilesupportvehicleisincludedinthescopeofsupportresources,thentheintegrated optimizationmodelofoperationsschedulingandresourceconfigurationforpreflightpreparationstagehasbeen established.Thenondominatedsortinggeneticalgorithm II (NSGAII)isdesignedtosolvethe model. Simulationexperimentsshowthatthe makespanpresentsa marginaleffectastheconfigurednumberof resourcesincreases.Inordertomakesurethepreflightpreparationstageiscompletedwithinadeckcycle,the configurednumberofresourcesforeachsupportmissionhasaminimumvalue.
LTEeMTC协议介绍
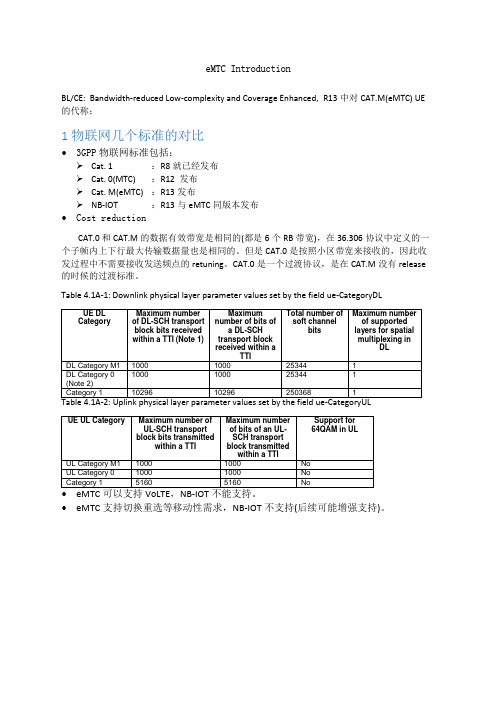
eMTC IntroductionBL/CE: Bandwidth-reduced Low-complexity and Coverage Enhanced,R13中对CAT.M(eMTC) UE 的代称;1 物联网几个标准的对比•3GPP物联网标准包括:➢Cat. 1 :R8就已经发布➢Cat. 0(MTC) :R12发布➢Cat. M(eMTC) :R13发布➢NB-IOT :R13与eMTC同版本发布•Cost reductionCAT.0 和CAT.M的数据有效带宽是相同的(都是6个RB带宽),在36.306协议中定义的一个子帧内上下行最大传输数据量也是相同的。
但是CAT.0是按照小区带宽来接收的,因此收发过程中不需要接收发送频点的retuning。
CAT.0是一个过渡协议,是在CAT.M没有release 的时候的过渡标准。
Table 4.1A-1: Downlink physical layer parameter values set by the field ue-CategoryDL•eMTC支持切换重选等移动性需求,NB-IOT不支持(后续可能增强支持)。
•物理层参数对比 eMTC Vs NB-Iot Vs Legacy LTE2 eMTC 基本参数和性能列表(与R9的对比)eMTC 基本特性:➢ 可以部署在任何LTE 频段上➢ 在同样的带宽内和其他LTE 业务共存 ➢ 支持FDD, TDD, half duplex modes ➢LTE 基站仅需要软件升级Main PHY/RF features:➢ 窄带收发,1.08MHz bandwidth ➢ 窄带跳频以获得频率分集增益➢ 上下行数据重传以获得覆盖增强(DL/UL harq 都支持重传子帧解调前数据合并) ➢相比于Cat 0,reduced bandwidth, reduced TM support, reduced HARQExtended C-DRX and I-DRX➢ Connected Mode(C-eDRX)✓ Extended DRX cycles of 5.12s and 10.24s are supported ➢ Idle Mode(I-eDRX)✓ Extended DRX cycles up to ~44min3 物理层信道和信号描述3.1 NarrowbandsBL/CE 接收和发送的带宽被称为Narrowband ,是在当前小区带宽中定义的连续6个RB ,并且对小区整个带宽的Narrowband 进行了编号,在PUSCH/PDSCH 的调度Grant 中,都会指示当前发送/接收使用哪一个narrowband 。
5G知识学习

一NR总体架构与功能划分1.1总体架构NG-RAN节点包含两种类型:l gNB:提供NR用户平面和控制平面协议和功能l ng-eNB:提供E-UTRA用户平面和控制平面协议和功能gNB与ng-eNB之间通过Xn接口连接,gNB/ng-eNB通过NG-C接口与AMF(Access and Mobility Management Function)连接,通过NG-U接口与UPF(User Plane Function)连接。
5G总体架构如下图所示,NG-RAN表示无线接入网,5GC表示核心网。
1.2 功能划分5G网络的功能划分如下图所示。
NG-RAN包含gNB或ng-eNB节点,5G-C一共包含三个功能模块:AMF,UPF和SMF(Session Management Function)。
1.2.1 gNB/ng-eNBl 小区间无线资源管理Inter Cell Radio Resource Management(RRM)l 无线承载控制Radio Bear(RB)Controll 连接移动性控制Connection Mobility Controll 测量配置与规定Measurement Configuration and Provision l 动态资源分配Dynamic Resource Allocation1.2.2 AMFl NAS安全Non-Access Stratum(NAS)Securityl 空闲模式下移动性管理Idle State Mobility Handling1.2.3 UPFl 移动性锚点管理Mobility Anchoringl PDU处理(与Internet连接)PDU Handling1.2.4 SMFl 用户IP地址分配UE IP Address Allocationl PDU Session控制1.3 网络接口1.3.1 NG接口NG-U接口用于连接NG-RAN与UPF,其协议栈如下图所示。
计算机网络服务质量优化方法论文

计算机网络服务质量优化方法探析摘要:相较于传统启发式的网络设计方法,优化方法可以从理论上找到问题的最优解,从而从根本上克服了启发式方法不能证明方案优劣程度的缺陷。
计算机网络的优化可以划分为资源分配、任务调度、网络资源部署和系统参数配置等4方面问题.对计算机网络服务质量的优化建模、求解、实施和评价成为当今研究的热点。
关键词:计算机网络;服务质量;资源配置中图分类号:tp393 文献标识码:a 文章编号:1007-9599 (2011) 22-0000-01computer network service quality optimization methods fan yusheng(jiangxi nursing vocational and technical college information center,nanchang 330039,china)abstract:in contrast to heuristic methods for network design,optimization approaches can find out the optimal solutions theoretically so that overcome the draw backs of heuristic methods which cannot be proven to beoptimal.optimization approaches in networks can be categorized into several different subjects:resource allocation,task scheduling, resource deployment,and parameter configuration.keywords:computer networks;quality of service;allocationof resources计算机网路业务随着信息社会的到来与发展,得到了逐步的开拓,同时各种业务对于网络的需求也在不断的上升。
资源配置名词解释

资源配置名词解释资源配置( resource allocation):指对有限的经济资源进行合理配置,使各种生产要素和生产条件充分发挥作用,取得最佳经济效益。
一般包括五个方面的内容:联合国在1975年对资源配置给出了四种定义:“资源配置是一个经济学的术语,用来描述生产一种商品所需的投入要素的数量及其分配情况,或者说,这些要素在生产过程中的组合”;“资源配置是指把稀缺的人力、物力、财力集中于某项事业或项目,而且是使它们能够充分发挥效能的那些事项”;“资源配置就是使经济活动与可以获得的资源相匹配的过程,具体地说,资源配置是指在某特定经济环境下,如何以最优化的成本获得最大的经济利益,也就是根据特定的目标函数选择最优方案以达到配置目标的过程”;“资源配置是由两部分组成:一是关于哪些方案可以为实现目标带来最大利益;二是判断这些方案是否为最优化方案。
最优化问题比较复杂,涉及计算问题。
”(《西方经济学概论》李海云等编著,高等教育出版社)从一般意义上讲,资源配置就是指一定时期内各种资源在各种用途之间的重新安排,即资源的合理配置。
狭义的资源配置是指经济资源的配置,但在生态经济学中也涉及到资源的重新配置问题。
资源配置的原则主要有:( 1)公平性原则;( 2)竞争性原则;( 3)稳定性原则;( 4)节约性原则;( 5)区域均衡性原则。
从配置的范围上看,可分为宏观配置和微观配置两种。
从配置的层次上看,可分为战略配置和战术配置。
从配置的方式上看,可分为行政配置、市场配置和计划配置三种。
从配置的方向上看,可分为横向配置和纵向配置两种。
资源配置的作用表现在两个方面:首先,配置能使资源充分有效地利用,从而提高经济效益。
其次,通过对资源的配置,还可以调整生产结构,协调经济发展速度。
以上四个定义是联合国对资源配置概念的不同理解。
正确理解资源配置概念,首先要对资源配置的含义作出明确的界定。
在笔者看来,资源配置就是对资源在各用途之间进行重新安排的过程,即按照一定的目标函数,寻求效益的最大化。
集装箱码头泊位、岸桥协调调度优化外文文献翻译

文献出处:Martin E。
The optimization of container berths and shore bridge coordination scheduling [J]. Journal of the Transportation Research Board,2015,6(3):40-50.原文The optimization of container berths and shore bridge coordination schedulingMartin EAbstractThe global economic development, the container quickly raised up into exports。
Rapid growth of the import and export cargo throughput brings to the container terminal larger benefits at the same time increase the burden of the port,have higher requirements on the terminal operation efficiency. How is the existing equipment of container terminals, reasonable resource allocation and scheduling, is common problem facing the container terminal. Therefore,how to improve the terminal facilities such as the maximum utilization of resources,to meet the increasing port demand,improve their competitive advantage,and has more practical meaning to improve the working efficiency of the container terminal. The main content of this study is berth, gantry cranes and set card co—allocation research,has plans to all ship to the port assignments during mathematical model is established with the target of minimum cost,according to the characteristics of the scale model by genetic algorithm,finally validates the effectiveness of the model.Keywords: System engineering; Water transportation; Gantry cranes allocation;Dynamic scheduling;1 IntroductionContainer terminal logistics is an organic system, made of interactive and dy namic components, such as containers, ships, berths, yards, tracks, quay cranes an d yard cranes trucks, labors and communications,in a limited terminal space。
PMP新版模拟试题(经典)

3. Ideally, communication between the project manager and the project team members should take place: A. Via daily status reports. B. Through approved documented forms. C. By written and oral communication. D. Through the formal chain of command.
5. 你在一家日本汽车制造企业担任项目经理,你的项目是为亚洲市场设计新一代的四驱 运动型轿车。你的团队需要确定悬挂、轮胎和底盘的组合,以保证轿车的高速行驶稳定 性。目前,你需要测量两个变量的关系:轮胎大小和整车稳定性。你可以使用下面哪一 个图? A. 控制图
B. Байду номын сангаас势图 C. 散点图 D. 帕累托图
PMBOK 第四版 PMP 模拟试题 2
1. Project sponsors have the GREATEST influence on the scope, quality, time, and cost of the project during the: A. Concept phase. B. Planning phase. C. Execution phase. D. Close-down phase.
4. 你被任命去负责更新公司的 IT 设施,具体来说,就是要带领你的团队实施公司的财务 总账系统,改善会计和房地产流程,开发租赁追踪纪录系统,并实施人力资源和工资单 系统。你得团队已经完成了启动/计划活动,并获得了项目章程、项目范围和具体工作包 的批准。你的团队正在完成所有的工作包,但是你收到一个变更请求,要求你为租赁追 踪纪录系统增加额外的报表功能。幸运的是,你判断这一功能变更对“三重约束”中的 要素没有影响。接下来,哪一个选项是你的最佳行动? A. 既然该变更对项目没有影响,也很容易实施,就实施这一变更请求 B. 就如何实施这一变更请求调查备选方案,使它对项目的影响降至最低 C. 让变更控制委员会审核这一变革更请求 D. 评估这一变革更请求对项目其他约束条件的影响
5G系统BWP功能配置和资源调度研究

图1BWP带宽示意公共资源主要是随机接入信道(Random Access资源、同步信号块(Synchronization Signal、信道状态信息参考信号(Channel StateSignal,CSI-RS)和信道探测参考信号Signal,SRS);控制资源主要是物理下行控制信道Downlink Control Channel,PDCCH)和物理上行控制Physical Uplink Control Channel,PUCCH)资源允许灵活地配置公共资源和控制资源,用一句话形容就是,小区就能做到。
配置灵活带来的好处是适应性大劣势就是很容易造成资源浪费。
对于用户尤其是公网频谱利用效率是主要追求目标。
接下来,以Division Duplexing,TDD)模式小区,在FR1峰值带宽是100MHz,对应的子载波间隔是30kHzResource Block,RB)为例,介绍如何高效地配置适应多的控制资源和公共资源[9]。
资源分为SSB和控制资源集0(Control CORESET0)为两部分。
SSB用于传输主信息块Block,MIB)信息,频域占用20个RB。
用于接收系统信息块(System Information Block,SIB 中配置,分为时域2个符号频域24个RB和时域个RB两种。
把SSB放在小区下边带,资源对小区资源配置影响,不会截断资源的连续性。
个符号频域48个RB的CORESET0资源,优势是不会影响使用1个符号,提升资源利用率。
SSB资源位置示意所示,蓝色部分显示CORESET0从小区下边带开始,图2SSB资源位置示意是下行参考信号,用于探测下行信道信号质量;是上行参考信号,用于检测上行信道信号质量。
把参考信号设置在特殊时隙,CSI-RS设置在上下行转换间隙之前,SRS设置在GP之后,如图3所示。
不同共用相同的时域位置。
频域位置由所属BWP确定,频域位置和范围,既要限制在BWP频域范围之内,频域覆盖范围。
华为-LTE交流(概念)

TD-LTE技术交流Content1 TD-LTE基本原理和关键技术2 华为TDS升级方案3 TD-LTE第一阶段规模试验网总结LTE 发展驱动力语音收入下降开源:提升带宽,发掘新业务LTE / SAE 成本现网成本网络成本高节流:引入新架构,降低业务成本运营商需要在吸引用户、增加收入的同时,大幅度降低网络建设和运营成本LTE设计目标与接入网架构目标:打造新一代无线通信系统,全面支撑高性能数据业务的,“确保在未来10年内领先”。
●带宽灵活:支持1.4MHz, 3MHz, 5MHz, 10Mhz, 15Mhz,20MHz●高速率:20M带宽下行100Mbps,上行50Mbps(实际速率更高)●低时延:控制面小于100ms,用户面(单向)小于5ms●支持高速移动:>350km/h的用户提供100kbps的接入服务●支持与现有3GPP和非3GPP系统的互操作●网络扁平,低成本建网,取消CS域,CS域业务在PS域实现,如VOIP架构:与传统3G网络比较,LTE的网络结更加简单扁平,没有RNC,减少时延☐2004年12月3GPP 正式成立了LTE 的研究项目。
☐原定2006年6月完成的研究项目SI (Study Item )推迟到2006年9月。
完成可行性研究,并输出技术报告。
☐2006年9月正式开始工作项目WI (Work Item )/标准制定阶段,原定为2007年9月完成第一个标准版本,现已延期。
☐目前LTE 处于Stage3 (Protocol)研究阶段,正在各个子组会议上热烈的讨论。
☐LTE 是在R8中提出的,它在R9中得到了进一步增强。
R9中包含了LTE 的大量特性。
其中最重要的一个方面是支持更多的频段。
R10包含了LTE Advanced 的标准化,即3GPP 的4G 要求。
这样,R10对LTE 系统进行了一定的修改来满足4G 业务☐目前协议仍在不断完善中。
LTE 标准化进程LTE WI stageLTE SI stage Delayed2006 Mar2006 Jun2006 Sep2005 Dec2006 Dec2007 Dec2008 Dec2007 Jun2008 Jun2007 Mar2007 Sep2008 Mar2008 Sep2009 MarLTE enhancement and improvementLTE Rel8 (Approval)LTE SILTE WI LTE Rel8(Spec finished)LTE 系统结构的特点:扁平化HLR SGSN /GGSN MSC ServerMGW IP / ATM回传网NodeB NodeB NodeB UEUEUERNCIu 接口Iub 接口IP 承载网HSSSGW/PGWMMEIMS…… e NodeBe NodeBe NodeB扁平化的网络结构,提升了业务传送的效率S1-UMME SGiE-UTRANS1-CS11Operator’s IP ServiceS6aHSSS-GWS5PDN-GWRxGxLTE/SAE 网络架构PCRFLTE 的接入网E-UTRAN 由e-NodeB 组成,提供用户面和控制面。
test-Chapter 1 Introduction to Management and Organizations

Chapter 1 Introduction to Management and Organizations1) Today's managers are just as likely to be women as they are men.Answer: TRUEPage Ref: 4 Topic: Who Are Managers?2) In order to be considered a manager, an individual must coordinate the work of others. Answer: TRUEPage Ref: 5 Topic: Who Are Managers?3) Supervisors and foremen may both be considered first-line managers.Answer: TRUEPage Ref: 6 Topic: Who Are Managers?4) Effectiveness is concerned with the means of getting things done, while efficiency is concerned with the attainment of organizational goals.Answer: FALSEPage Ref: 7 Topic: What Is Management?5) A goal of efficiency is to minimize resource costs.Answer: TRUEPage Ref: 7 Topic: What Is Management?6) Managers who are effective at meeting organizational goals always act efficiently. Answer: FALSEPage Ref: 7 Topic: What Is Management?7) The four contemporary functions of management are planning, organizing, leading, and controlling.Answer: TRUEPage Ref: 8 Topic: What Do Managers Do?8) Directing and motivating are part of the controlling function of management.Answer: FALSEPage Ref: 8 Topic: What Do Managers Do?9) Fayol's management functions are basically equivalent to Mintzberg's management roles. Answer: FALSEPage Ref: 8-9 Topic: What Do Managers Do?10) Mintzberg's informational management role involves receiving, collecting, and disseminating information.Answer: TRUEPage Ref: 9 Topic: What Do Managers Do?11) Resource allocation and disturbance handling are both considered decisional roles. Answer: TRUEPage Ref: 9 Topic: What Do Managers Do?12) A finance manager who reads the Wall Street Journal on a regular basis would be performing the figurehead role.Answer: FALSEPage Ref: 9 Topic: What Do Managers Do?13) Katz concluded that managers need three essential skills: technical, human, and conceptual. Answer: TRUEPage Ref: 10-11 Topic: What Do Managers Do?14) Conceptual skills become less important as a manager moves into top management. Answer: FALSEPage Ref: 11 Topic: What Do Managers Do?15) In today's world, organizational managers at all levels and in all areas need to encourage their employees to be on the look-out for new ideas and new approaches.Answer: TRUEPage Ref: 13 Topic: What Do Managers Do?16) Only first-line managers and employees need to be concerned with beingcustomer-responsive.Answer: FALSEPage Ref: 13 Topic: What Do Managers Do?17) Which of the following statements regarding managers in today's world is accurate?A) Their age range is limited to between 30 and 65.B) They are found only in large corporations.C) They can be found exclusively in for-profit organizations.D) The single most important variable in employee productivity and loyalty is the quality of the relationship between employees and their direct supervisors.Answer: DPage Ref: 5 Topic: Who Are Managers?18) Someone who works with and through other people by coordinating their work activities in order to accomplish organizational goals is ________.A) an assembly line workerB) a laborerC) a managerD) a salespersonAnswer: CPage Ref: 5 Topic: Who Are Managers?19) In the past, nonmanagerial employees were viewed as employees who ________.A) reported to top executivesB) reported to middle managersC) supervised othersD) had no others reporting to themAnswer: DPage Ref: 5 Topic: Who Are Managers?20) Which of the following types of managers is responsible for making organization-widedecisions and establishing the plans and goals that affect the entire organization?A) first-line managersB) top managersC) production managersD) research managersAnswer: BPage Ref: 6 Topic: Who Are Managers?21) All levels of management between the supervisory level and the top level of the organization are termed ________.A) middle managersB) first-line managersC) supervisorsD) foremenAnswer: APage Ref: 6 Topic: Who Are Managers?22) Which of the following levels of management is associated with positions such as executive vice president, chief operating officer, chief executive officer, and chairman of the board?A) team leadersB) middle managersC) first-line managersD) top managersAnswer: DPage Ref: 7 Topic: Who Are Managers?23) Agency head or plant manager is most likely associated with which of the following?A) team leadersB) middle managersC) first-line managersD) top managersAnswer: BPage Ref: 6 Topic: Who Are Managers?24) The lowest level of management is ________.A) a nonmanagerial employeeB) a department of research managerC) a vice presidentD) a first-line managerAnswer: DPage Ref: 5 Topic: Who Are Managers?25) Which of the following best reflects the management structure of a traditional organization?A) pyramidB) circleC) hub with spokesD) infinite lineAnswer: APage Ref: 6 Topic: Who Are Managers?26) ________ is the process of getting activities completed efficiently and effectively with and through other people.A) LeadingB) ManagementC) SupervisionD) ControllingAnswer: BPage Ref: 6 Topic: What Is Management?27) The distinction between a managerial position and a nonmanagerial position is ________.A) planning the work of othersB) coordinating the work of othersC) controlling the work of othersD) organizing the work of othersAnswer: BPage Ref: 6 Topic: What Is Management?28) Which of the following is an example of an efficient manufacturing technique?A) cutting inventory levelsB) increasing the amount of time to manufacture productsC) increasing product reject ratesD) decreasing product outputAnswer: APage Ref: 7 Topic: What Is Management?29) Wasting resources is considered to be an example of ________.A) efficiencyB) effectivenessC) inefficiencyD) ineffectivenessAnswer: CPage Ref: 7 Topic: What Is Management?30) Effectiveness is synonymous with ________.A) cost minimizationB) resource controlC) goal attainmentD) efficiencyAnswer: CPage Ref: 7 Topic: What Is Management?31) Efficiency refers to ________.A) the relationship between inputs and outputsB) the additive relationship between costs and benefitsC) the exponential nature of costs and outputsD) increasing outputs regardless of costAnswer: APage Ref: 7 Topic: What Is Management?32) In successful organizations, ________.A) low efficiency and high effectiveness go hand in handB) high efficiency and low effectiveness go hand in handC) high efficiency and high effectiveness go hand in handD) high efficiency and high equity go hand in handAnswer: CPage Ref: 7 Topic: What Is Management?33) ________ was a French industrialist who first identified the basic management functions.A) WeberB) TaylorC) HerzbergD) FayolAnswer: DPage Ref: 8 Topic: What Do Managers Do?34) Today, the basic management functions are considered to be ________.A) planning, coordinating, staffing, and directingB) planning, organizing, leading, and directingC) commanding, organizing, leading, and staffingD) planning, organizing, leading, and controllingAnswer: DPage Ref: 8 Topic: What Do Managers Do?35) Writing an organizational strategic plan is an example of the ________ management function.A) leadingB) coordinatingC) planningD) organizingAnswer: CPage Ref: 8 Topic: What Do Managers Do?36) Organizing includes ________.A) defining organizational goalsB) hiring organizational membersC) motivating organizational membersD) determining who does what tasksAnswer: DPage Ref: 8 Topic: What Do Managers Do?37) A manager resolving conflict among organizational members is performing what function?A) controllingB) commandingC) directingD) leadingAnswer: DPage Ref: 8 Topic: What Do Managers Do?38) The process of monitoring, comparing, and correcting is called ________.A) controllingB) coordinatingC) leadingD) organizingAnswer: APage Ref: 8 Topic: What Do Managers Do?39) ________ developed a categorization scheme for defining what managers do, consisting of10 different but highly interrelated roles.A) Henri FayolB) Henry FordC) Henry MintzbergD) Henry MorrisAnswer: CPage Ref: 9 Topic: What Do Managers Do?40) According to Mintzberg's management roles, the ________ roles are those that involve people and other duties that are ceremonial and symbolic in nature.A) informationalB) interpersonalC) technicalD) decisionalAnswer: BPage Ref: 9 Topic: What Do Managers Do?41) The roles of disseminator, figurehead, negotiator, liaison, and spokesperson are more important at the ________ levels of the organization.A) lowerB) middleC) higherD) supervisoryAnswer: CPage Ref: 9 Topic: What Do Managers Do?42) A human resource manager attending a local Society for Human Resource Management meeting would be functioning in which role?A) informationalB) leaderC) liaisonD) disseminatorAnswer: CPage Ref: 9 Topic: What Do Managers Do?43) The ________ role is more important for lower-level managers than it is for either middle- or top-level managers.A) leaderB) entrepreneurC) spokespersonD) disseminatorAnswer: APage Ref: 10 Topic: What Do Managers Do?44) According to Mintzberg's management roles, the ________ roles involve receiving, collecting, and disseminating information.A) interpersonalB) informationalC) technicalD) decisionalAnswer: BPage Ref: 9 Topic: What Do Managers Do?45) All of the following are examples of informational roles according to Mintzberg except________.A) liaisonB) monitorC) disseminatorD) spokespersonAnswer: APage Ref: 9 Topic: What Do Managers Do?46) All of the following are managerial roles that are more important at the higher levels of the organization except ________.A) leaderB) disseminatorC) figureheadD) negotiatorAnswer: APage Ref: 10 Topic: What Do Managers Do?47) Which of the following represents the most useful way of describing the manager's job?A) rolesB) functionsC) skillsD) organizational levelAnswer: BPage Ref: 10 Topic: What Do Managers Do?48) All three of Mintzberg's interpersonal roles are part of the ________ function.A) organizingB) planningC) leadingD) controllingAnswer: CPage Ref: 9 Topic: What Do Managers Do?49) Which of the following individuals identified the three essential managerial skills?A) KatzB) LewisbergC) RainesD) ChambersAnswer: APage Ref: 10 Topic: What Do Managers Do?50) The three essential managerial skills include ________.A) technical, human, and empiricalB) human, empirical, and conceptualC) technical, interpersonal, and controllingD) technical, human, and conceptualAnswer: DPage Ref: 10 Topic: What Do Managers Do?51) Which of the following is true concerning technical and managerial skills?A) Human skills and technical skills remain equally important as managers move to higher levels.B) Technical-skill needs remain necessary and human skills decrease as managers move to higher levels.C) Human skills remain necessary and technical-skill needs decrease as managers move to higher levels.D) Both human-skill and technical-skill needs decrease as managers move to higher levels. Answer: CPage Ref: 10 Topic: What Do Managers Do?52) Managers with good ________ are able to communicate, motivate and lead to get the best out of their people.A) human skillsB) conceptual skillsC) technical skillsD) visual skillsAnswer: APage Ref: 11 Topic: What Do Managers Do?53) Technical skills include ________.A) leadership and efficiency in a certain specialized fieldB) knowledge of and proficiency in a certain specialized fieldC) familiarity with and interest in a general field of endeavorD) skill and interest in a general field of endeavorAnswer: BPage Ref: 10 Topic: What Do Managers Do?54) The ability to work well with other people, both individually and in a group, describes which of the following skills ________.A) technical skillsB) assessment skillsC) planning skillsD) human skillsAnswer: DPage Ref: 11 Topic: What Do Managers Do?55) Which of the following skills are more important at lower levels of management, as these managers are dealing directly with employees doing the organization's work?A) humanB) technicalC) conceptualD) empiricalAnswer: BPage Ref: 10 Topic: What Do Managers Do?56) Budgeting is associated with the management functions of planning and ________.A) directingB) organizingC) leadingD) controllingAnswer: DPage Ref: 8 Topic: What Do Managers Do?57) Mentoring is primarily associated with the management function of ________.A) planningB) organizingC) leadingD) controllingAnswer: CPage Ref: 8 Topic: What Do Managers Do?58) An organization is ________.A) the physical location where people workB) a collection of individuals working for the same companyC) a deliberate arrangement of people to accomplish some specific purposeD) a group of individuals focused on profit making for their shareholdersAnswer: CPage Ref: 14 Topic: What Is an Organization?59) A deliberate arrangement of people to accomplish some specific purpose is ________.A) a structureB) a processC) an organizationD) an assembly operationAnswer: CPage Ref: 14 Topic: What Is an Organization?60) A difference between traditional organizations and new organizations is that the new organizations tend to be more ________.A) stableB) command orientedC) rule orientedD) dynamicAnswer: DPage Ref: 14 Topic: What Is an Organization?61) Which of the following best describes the concept that management is needed in all types and sizes of organizations, no matter the country in which they're located?A) the partiality of managementB) the segmentation of managementC) the universality of managementD) the cultures of managementAnswer: CPage Ref: 14 Topic: Why Study Management?62) Universality of management means that ________.A) all managers in all organizations perform the four management functionsB) all managers in all organizations can perform their job the same wayC) all organizations can hire any manager to perform the management jobsD) any manager can work in any organization and perform any management job Answer: APage Ref: 15 Topic: Why Study Management?63) Organizations that are well managed ________.A) choose the best suppliers for their productsB) compete on an international basis because they have the best productsC) always have the lowest-cost productsD) develop a loyal customer base, grow, and prosperAnswer: DPage Ref: 15 Topic: Why Study Management?64) Which of the following types of managerial positions is most likely to involve clerical duties?A) shift supervisorB) regional department headC) project managerD) chief executive officerAnswer: APage Ref: 16 Topic: Why Study Management?65) A manager's success is typically ________.A) dependent on how hard the manager worksB) how closely the manager supervises the employeesC) based on how skilled the manager is at the technical elements of the jobD) dependent on others' work performanceAnswer: DPage Ref: 16 Topic: Why Study Management?66) A primary responsibility of managers is creating a work environment that ________.A) is safe and well litB) is clean and organizedC) allows employees to do their work to the best of their abilityD) provides excellent customer serviceAnswer: CPage Ref: 16 Topic: Why Study Management?67) Which of the following represents a challenge of management?A) enjoy relatively easy workB) work with a variety of peopleC) have little influence on organizational outcomesD) have to deal with a variety of personalitiesAnswer: DPage Ref: 16 Topic: Why Study Management?68) Each of the following represents a challenge of management except ________.A) must operate with limited resourcesB) are highly valued by organizationsC) must motivate workers in uncertain situationsD) success depends on others' performanceAnswer: BPage Ref: 16 Topic: Why Study Management?69) In a short essay, list and discuss the 10 managerial roles developed by Mintzberg. Include specific examples of each role and group each according to interpersonal, informational, and decisional roles.Answer:Interpersonal Rolesa. Figurehead symbolic head; obliged to perform a number of routine duties of a legal or social nature. Examples include greeting visitors and signing legal documents.b. Leader responsible for the motivation and activation of subordinates; responsible for staffing, training, and associated duties. Examples include performing virtually all activities that involve subordinates.c. Liaison maintains self-developed network of outside contacts and informers who provide favors and information. Examples include acknowledging mail, doing external board work, and performing other activities that involve outsiders.Informational Rolesa. Monitor seeks and receives wide variety of internal and external information to develop thorough understanding of organization and environment. Examples include reading periodicals and reports, and maintaining personal contacts.b. Disseminator transmits information received from outsiders or from subordinates to members of the organization. Examples include holding informational meetings and making phone calls to relay information.c. Spokesperson transmits information to outsiders on organization's plans, policies, actions, results, and so on. Examples include holding board meetings and giving information to the media.Decisional Rolesa. Entrepreneur searches organization and its environment for opportunities and initiates "improvement projects" to bring about changes. Examples include organizing strategy and review sessions to develop new programs.b. Disturbance handler responsible for corrective action when organization faces important, unexpected disturbances. Examples include organizing strategy and review sessions that involve disturbances and crises.c. Resource allocator responsible for the allocation of organizational resources of allkinds making or approving all significant organizational decisions. Examples include scheduling, requesting authorization; performing any activity that involves budgeting and the programming of subordinates' work.d. Negotiator responsible for representing the organization at major negotiations. Examplesinclude participating in union contract negotiations.The interpersonal roles are roles that involve people and other duties that are ceremonial and symbolic in nature. The three interpersonal roles include being a figurehead, leader, and liaison. The informational roles involve receiving, collecting, and disseminating information. The three informational roles include a monitor, disseminator, and spokesperson. Finally, the decisional roles revolve around making choices. The four decisional roles include entrepreneur, disturbance handler, resource allocator, and negotiator.Page Ref: 8-9Topic: What Do Managers Do?。
资源分配英语

资源分配英语
资源分配英语,即Resource Allocation in English,是指为了提高资源的利用效率,通过科学的方法和手段对资源进行规划、分配和调配等一系列管理活动。
资源分配在各个领域都有广泛应用,如信息技术、经济管理、军事等方面。
在信息技术领域中,资源分配可以指对计算机资源进行合理规划和调度,以提高计算机的运行效率。
例如,在多任务运行时,通过资源分配可以避免出现资源争夺的情况,从而保证各个任务都能得到足够的资源,以达到最优的运行效果。
在经济管理领域中,资源分配可以指合理配置各种生产要素,包括劳动力、资本、土地等,以提高生产效率和经济效益。
例如,在生产过程中,通过对各种要素的分配和调配,可以最大限度地提高产出,降低成本。
在军事领域中,资源分配可以指在战争中针对各种作战需要,合理规划和调配作战资源,以达到战术目标。
例如,在战争中,通过资源分配可以确保各个部队都能得到足够的物资、武器和装备,以达到最优的战斗效果。
总的来说,资源分配英语是一项非常重要的管理活动,它可以在各个领域中提高资源的利用效率,从而达到更好的效益。
5G PDSCH调度介绍

5G PDSCH调度介绍概述NR调度算法依据下面三类:•优先级计算调度器根据调度输入的信息,确定承载的调度优先级和选定调度的用户,保证调度公平性的同时,最大化系统吞吐量。
•MCS(Modulation and Coding Scheme)选择调度器根据调度输入的信息,确定每一个调度用户的MCS,不同调制方式下采用不同的信道编码效率。
对于信道质量好的场景,提供高阶的调制方式和高的编码效率。
调制阶数和编码效率越高,传输效率越高。
•资源分配调度器需要为UE指示调度所在slot,以及该slot内调度的OFDM(OrthogonalFrequency Division Multiplexing)符号的起止位置,同时根据用户数据量和选定的MCS,确定用户分配的RB(Resource Block)数和RB位置。
RE(Resource Element)是NR系统最小的时频资源单位,在频域上占据一个子载波,在时域上占据一个OFDM符号。
RB是NR系统在物理层数据传输的资源分配最小单位,在频域上包含12个子载波,在时域上无要求。
TBS(Transport Block Size)是指传输块大小。
PDSCH时频域资源包括PDSCH时域资源和PDSCH频域资源。
分配PDSCH时频域资源是指给用户分配合适的资源大小和资源位置。
分配PDSCH频域资源:3GPP TS 38.214 V15.4.0中的5.1.2.2 Resource allocation in frequency domain章节规定了type 0和type1两种资源分配方式。
type0是RBG粒度的分配方式,支持非连续分配和连续分配;type1是RB粒度的分配方式,仅支持连续分配。
当前用户级控制信息和数据信息采用type0连续分配方式。
以一个RBG包括4个RB为例,type0连续分配方式如图所示,调度器给UE1分配了1个RBG,给UE2分配了2个RBG,给UE3分配了1个RBG。
BBU软件架构

Inter-Cell Interference Coordination (ICIC): Managing the radio resources (notably the radio resource blocks) such that inter-cell interference is kept under control Load Balancing (LB): Influence the traffic load distribution in such a manner that radio resources remain highly utilized and the QoS of in-progress sessions are maintained to the possible extent (may result in handover decisions) Inter-RAT Radio Resource Management: In connection with inter-RAT mobility (taking into account the involved RAT resource situation, UE capabilities & operator policies)
GPIO
IO 1x sR
1x sRIO
SRIO SW DSP (MSC-8156) 4x
64
OX
DL FPGA (V6-240)
122.88M
4X 4X To Other Peripheral
DDR3
64
AD 9522 AD 9516 OCXO
SYN FPGA
GPS Receiver (Optional)
RESOURCE ALLOCATION

专利名称:RESOURCE ALLOCATION发明人:JOHANSSON, Staffan, Engelbert,RYNBÄCK, Patrik, Johan, Erik,ANDERSSON,Christoffer,JÖNSSON, Nils, Tore,Erik,JOHANSSON, Peter申请号:SE1999000664申请日:19990423公开号:WO99/056475P1公开日:19991104专利内容由知识产权出版社提供摘要:A pool of resource units is configured using a structure having plural levels including first level and second level resource blocks. Each first level resource block corresponds to an individual resource unit, where an individual resource unit is the smallest resource that can be allocated from the resource pool. The first level resource blocks are provided in groups. Each second level resource block corresponds to one of the groups of the first level resource blocks. The second level resource blocks are also provided in groups forming a next higher level of the resource pool. If a request is made for a first level resource block, an available first level resource block is allocated. If a first level resource block is not available, then an available first level resource block is created by converting a second level resource block into a corresponding group of first level resource blocks. One of the converted first level resource blocks is then allocated to the request. Resource blocks are restored to the resource unit pool structure first to any incomplete first level resource block grouping. If that returned block completes the grouping, a new second level resource block is made available. The resource pool may bereconfigured as needed to ensure an efficient configuration. First and second pools of resource units are configured using a structure having plural levels including first and second level resource units. A relationship is established between one of the two pools of resource units. A request is made for a resource that requires a resource unit from both of the first and second resource unit pools. A single allocation procedure is employed to allocate resource units from both pools. If one of the resource units is available in one pool, the relationship ensures that the required corresponding resource unit in another pool is also available.申请人:TELEFONAKTIEBOLAGET LM ERICSSON (publ)地址:SE国籍:SE代理机构:ERICSSON RADIO SYSTEMS AB更多信息请下载全文后查看。
dolphinscheduler sql task error

dolphinscheduler sql task error "DolphinScheduler SQL Task Error: Troubleshooting Guide"Introduction to DolphinScheduler SQL Task ErrorDolphinScheduler is a powerful open-source Big Data visual workflow scheduler system. It supports various types of tasks, including SQL tasks. However, as with any complex software, users may encounter errors while working with DolphinScheduler's SQL tasks. In this article, we will provide a comprehensive troubleshooting guide to help address these errors, step by step.1. Understanding DolphinScheduler and SQL TasksBefore diving into troubleshooting, it's important to have a clear understanding of DolphinScheduler and SQL tasks. DolphinScheduler provides the ability to create complex workflow processes and manages the execution of tasks. SQL tasks allow users to execute SQL scripts against databases, enabling data processing and transformation.2. Common DolphinScheduler SQL Task ErrorsTo effectively troubleshoot DolphinScheduler SQL task errors, it's crucial to be familiar with common errors encountered. Here are some of the most common errors and their potential causes:a. Connection Errors: Failure to establish a connection with the database can result from incorrect connection settings or network issues.b. Syntax Errors: SQL queries may fail due to syntax errors in the script. These errors can include missing or misplaced brackets, incorrect column names, or unsupported SQL functions.c. Permissions Issues: Insufficient permissions for the user executing the SQL task can lead to errors. Ensure that the user has appropriate privileges to access and modify the necessary data.d. Data Inconsistencies: Data inconsistencies in the database can cause SQL queries to fail. Ensure that the data being accessed by the SQL task is accurate and consistent.e. Resource Constraints: Insufficient resources, such as CPU ormemory, can cause SQL tasks to fail. Check the resource allocation settings and adjust them if necessary.3. Analyzing DolphinScheduler SQL Task Error LogsWhen troubleshooting DolphinScheduler SQL task errors, investigating the logs is crucial. Error logs provide valuable information about the error, including the query executed, exception details, and potential causes. Analyze the logs to identify the specific error and understand its origin.4. Verifying Database ConnectionIf a connection error is encountered, start by verifying the database connection settings. Ensure that the connection information, such as the hostname, port, username, and password, is correct. Test the connection using external database management tools, such as SQL clients, to validate connectivity.5. Review SQL Script SyntaxIn the case of syntax errors, review the SQL script carefully. Payattention to proper syntax, including correct column names, table names, and SQL functions. Validate the script using a SQL editor or an online SQL syntax validator.6. Checking User PermissionsIf permissions issues are suspected, check the user's privileges in the database. Ensure that the user has sufficient read and write permissions on the required tables and databases. Grant necessary privileges if needed.7. Resolving Data InconsistenciesFor data inconsistencies causing SQL task errors, investigate the source of the inconsistencies. Analyze the data in the affected tables and determine if any modifications are required. Rectify the inconsistencies, such as fixing incorrect values or updating missing data.8. Resource Allocation AdjustmentsIf the SQL task fails due to resource constraints, review the resourceallocation settings. Increase the allocated resources, such as CPU or memory, if available. Optimize the task's resource consumption by tuning the SQL query or adjusting the task's configuration.9. Testing and MonitoringAfter implementing the necessary adjustments and corrective actions, retest the SQL task. Monitor the task's execution closely and validate the results. If the error persists, revisit the logs and analyze any new error messages.ConclusionDolphinScheduler SQL task errors can be challenging to troubleshoot, but by following a systematic approach, they can be effectively resolved. Understanding the common errors, reviewing logs, verifying database connections, checking syntax, and addressing permission issues are crucial steps in resolving SQL task errors. Additionally, addressing data inconsistencies and optimizing resource allocations will improve overall task performance.Remember to test and monitor the task after implementing changes to ensure successful execution. With the troubleshooting guide provided, users can confidently tackle DolphinScheduler SQL task errors and achieve smoother workflow processes。
水资源管理与调配业务流程

水资源管理与调配业务流程Water resource management and allocation is a crucial aspect of sustainable development, as water is a finite and essential resource for all living beings on Earth. 水资源管理与调配是可持续发展的关键,因为水是地球上所有生物的有限且重要的资源。
The process of managing and allocating water resources involves a complex interplay of factors such as supply and demand, environmental considerations, social equity, and economic efficiency. 管理和配置水资源的过程涉及供需、环境考虑、社会公平和经济效益等因素的复杂相互作用。
In order to ensure the effective and efficient management of water resources, it is essential to have a well-defined and transparent business process in place. 为了确保水资源的有效和高效管理,有必要建立一个明确定义和透明的业务流程。
This includes clear guidelines for monitoring water usage, conducting regular assessments of water availability, implementing measures for water conservation, and establishing mechanisms for resolving conflicts over water allocation. 这包括监测用水量的明确指南,定期评估水资源的可用性,实施节水措施,以及建立解决水资源调配冲突的机制。
大学是否应该向公众开放英语作文

大学是否应该向公众开放英语作文Title: The Case for University Campuses to Open Their Doors to the PublicIntroduction:Universities have long been regarded as bastions of knowledge, innovation, and cultural exchange. These institutions not only serve as educational hubs for students but also as centers of research and community engagement. However, access to university campuses is often restricted to enrolled students, faculty, and staff. In recent years, there has been a growing conversation about whether universities should open their doors to the general public. This essay explores the potential benefits and challenges of making university campuses more accessible to the public.The Benefits of Opening Universities to the Public:1. Community Engagement:One of the primary benefits of opening university campuses to the public is the opportunity for increased community engagement. Universities can host various events, such as lectures, workshops, and cultural festivals, that are open to the public. This allows members of the community to participate in intellectual and cultural activities,fostering a sense of connection between the university and the surrounding area.2. Lifelong Learning:By welcoming the public onto their campuses, universities can offer opportunities for lifelong learning. Many universities have resources such as libraries, museums, and galleries that could be made available to the public, providing access to knowledge and culture beyond traditional academic settings.3. Civic Engagement and Democratic Dialogue:Universities are well-positioned to facilitate civic engagement and democratic dialogue. By opening their doors, universities can host public discussions and debates on issues relevant to society. This creates a space for the exchange of ideas and promotes civic participation among community members.4. Economic Stimulus:Opening university campuses to the public can also have economic benefits. Tourists and visitors may be attracted to visit these institutions, which can stimulate local businesses and the economy. Additionally, partnerships with local businesses can be formed, creating mutually beneficial relationships.5. Enhancing University Reputation:A university that is open to the public can enhance its reputation as a responsible and engaged institution. This can attract prospective students, faculty, and donors who valuethe university's commitment to community involvement and public good.Challenges and Considerations:1. Security Concerns:One of the primary challenges of opening university campuses to the public is the potential for increased security risks. Universities must ensure that adequate measures are in place to protect students, faculty, staff, and visitors from harm.2. Preservation of Academic Environment:Maintaining the integrity of the academic environment is crucial when considering opening campuses to the public. Universities must balance accessibility with the need for a conducive environment for learning and research.3. Resource Allocation:Making university facilities available to the public requires additional resources for maintenance, security, and programming. Universities must carefully consider how to allocate their resources to accommodate the needs of both their internal community and the general public.4. Legal and Regulatory Issues:There may be legal and regulatory considerations when it comes to allowing public access to university campuses. Universities must work within the framework of local laws and regulations to ensure compliance and liability protection.5. Cultural Sensitivity:Universities must also consider the cultural sensitivity required when opening their campuses to diverse populations. It is essential to respect the varied backgrounds and perspectives of the public while maintaining a welcoming and inclusive environment.Conclusion:The case for opening university campuses to the public is compelling. The potential benefits of increased community engagement, lifelong learning, civic participation, economic stimulus, and enhanced reputation make this a worthwhile endeavor for universities to consider. However, it is important to address the challenges and considerations associated with increased public access. By carefully balancing the benefits with the potential drawbacks, universities can play a vital role in enriching the lives of their communities while maintaining their core missions of education and research.In essence, the decision to open university campuses to the public is a complex one that requires thoughtful deliberation. As universities navigate this issue, they must remain committed to their educational mission while embracing the opportunities for broader societal impact. Ultimately, byopening their doors, universities can extend their reach beyond the confines of their campuses and contribute to the betterment of society as a whole.。
木桶定律的基本内容

木桶定律的基本内容The Law of the Wooden Barrel, also known as the Law of Diminishing Marginal Returns, is a fundamental concept in economics and production theory. This law states that as more and more of a variable input is added to a fixed input, the marginal product of the variable input eventually decreases. In other words, at some point, adding more of the variable input will not increase output proportionally, but will actually lead to a decrease in output per unit of input.木桶定律,又被称为边际效用递减法则,是经济学和生产理论中的一个基本概念。
这一法则指出,当越来越多的可变输入加入到一个固定输入中时,可变输入的边际产品最终会减少。
换句话说,在某一点上,增加更多的可变输入将不会按比例增加产出,而实际上会导致每单位输入的产出减少。
The concept of the Law of the Wooden Barrel can be understood through a simple analogy with a wooden barrel. Imagine a wooden barrel being filled with water. The barrel represents the fixed input, while the water represents the variable input. As more water is added to the barrel, the water level rises. However, at a certain point,adding more water will not increase the water level as much as before. This is because the barrel can only hold a certain amount of water, and filling it beyond that point will lead to spillage and waste.木桶定律的概念可以通过一个简单的比喻来理解,比如一个木桶装满了水。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Resource Configuration and Allocation: A Case Study of Constrained HeuristicsSathi, N., Fox, M. S., Goyal, R. and Kott, A.A version of the paper that appeared in IEEE Expert 7(2):26-35, April 1992When Customers order specific quantities of products with particular features or components, inventory managers must perform two tasks: first they design feasible product configurations of component parts based on physical compatibility's anduser-specified preferences, and then they try to allocate optimal quantities of components to those specified configurations based on available inventory. If a component can be used across multiple configurations, supplying one configurationcan affect an inventory manager's ability to supply other configurations. Themanager must project how many orders can be configured from an inventory andwhich components will need to be ordered - a time-consuming job.These tasks are difficult because feasible product configurations are limited by interactive constraints (electrical, thermal, geometric, and so on), and because limited inventory and alternative configurations increase the complexity of allocating resources. Alternative configurations represent alternative ways a single product canbe supplied, and an order for n products can be and often is satisfied by more thanone configuration.We have applied constrained heuristic search techniquesl to the problems of product configuration and inventory planning. Our interactive, real-time decision support system, called Coral, maximizes the total number of products requested, given one or more substitutable configurations. This gives inventory managers a tool formanaging and allocating component inventories and thus maximizing the number of complete orders. Coral is also intended to-perform "what-if" analyses on possibleorder demands. This approach views configuration and allocation asconstraint-satisfaction and optimization problems, where constraints guide the problem solving (that is, searching). Spex, a problem-independent version of the configuration module, has been developed and applied to other configuration problems.Problem definition: Planning ammunition roundsConfiguring complete ammunition rounds and allocating inventory can be a problemfor army logistics.2 A complete round of ammunition contains projectiles, cartridgecases, propelling charges, primers, and fuses. An army unit's mission and environment dictate the requirements for a complete round. For example, an area with reduced visibility might require Illum (illumination) rounds consisting of Illum projectiles fitted with time fuses. Similarly, material targets require HE (high-energy) projectiles. For maximum tactical flexibility, planners can use different components across different types of rounds. For example, for a 155-mm towed Howitzer artillery, an HE projectile with a normal cavity can be fitted with any of six types of fuses: three PD (point-detonating) models, two MTSQ (mechanical-time super-quick) models, or a Prox (proximity) model. Similarly, one kind of PD fuse can be used across various projectile types (Agent, HE, or Hera) for the same Howitzer. Thus, the same components can be used to configure different types of rounds. This interchangeability increases the difficulty of determining the impact of one type of round on inventory and thereby its effect on the availability of other types of rounds. The configuration/allocation problem is made more difficult, from a decision-support perspective, by the way that problems can be posed. The following are common planning problems in field situations:Maximize the number of 155-mm HE, Illum, and Smoke rounds available atATP- I (the ammunition transfer point, where ammunition from the rear istransferred to the front), using any combination of compatible components.Configure the maximum number of 105-mm Smoke rounds with 20 percent PDfuses, 50 percent Prox fuses, and 30 percent MTSQ fuses.Configure the maximum number of 155-mm HE, 105-mm Smoke, and 105-mmIllum rounds from the inventory at ATP-I and ATP-2 storage locations. Ifdifferent rounds compete for components, maintain the following proportion:40 percent HE rounds, 30 percent Smoke rounds, and 30 percent Illum rounds.Configure the maximum number of rounds from the inventory at ATP-3. Ifdifferent rounds compete for components, maintain the following proportions:40 percent 155-mm HE rounds: 20 percent use PD fuses, 50 percentuse Prox fuses, and 30 percent use MTSQ fuses; half use percussionprimers and half use electric-percussion primers; ¥ 30 percent 105-mmSmoke rounds, with 10 percent CP fuses, 40 percent Delay fuses, and50 percent Prox fuses; and 30 percent 1 05-mm Illum rounds with a defaultmix of fuse, primer, and propelling-charge components.The configuration and allocation task is further complicated by the need to explore alternative requirements. For example, the planner might want to see how well the same set of goals can be accomplished with different inventories, or compare how well a single inventory can accomplish several different sets of goals. By making small changes in the goals, the planner can perform "what-if" analysis-for example, determining how many 155-mm HE rounds can be configured if the target for 155-mm Apers (antipersonnel) rounds is increased. The planner might also want to generate unrelated plans for various sets of storage locations, each with its own set of goals. Figure I describes inputs, outputs, and constraints for the ammunition-round planning problem.Planners usually view inventory from the component level rather than from the configuration level, so it is difficult for them to project which components need to be ordered and how the components in inventory can be put together into complete rounds that are likely to be needed. It is time consuming to play what-if games on the possible availability of ammunition rounds and to answer questions like these:What is the maximum number of different rounds in the inventory?What are the relative numbers of rounds of different types present?Which part numbers can be configured together in a single round type?What will be the inventory shortfall if certain types of rounds with a givencomposition need to be configured?Constrained heuristic searchPrevious research has focused on solving either the configuration or the resource allocation problem, each independent of the other (see the sidebar). In Coral,we view both as instances of constrained heuristic search. CHS is a problem-solving method that formalizes the concept of problem structure and its analysis, and provides powerful heuristic advice to guide search. In particular, the model augments the definition of a problem space (composed of states, operators, and an evaluation function) by refining a state to include1.the problem topology, or structural characterization;2.problem textures, which measure a problem topology to focus search andreduce backtracking; and3.the problem objective, a means for rating alternative solutions.A problem's topology is defined by a constraint graph in which nodes are variables and arcs are constraints. Problem objectives are embedded in the topology as utilities (that is, a number between O and 1 that reflects how well the value optimizes the objective) associated with values in a variable' s domain. Propagation across constraints within a topology (also known in the constraint-satisfaction literature as arc consistency) reduces the domain of variables and alters the utilities associated with the remaining values. After propagation, a value's utility is no longer locally defined but reflects its global interaction, via constraints, with other variables. Search operators in constrained heuristic search have many roles. They refine problems by adding new variables and constraints, reduce the number of solutions by reducing the domain of variables (for example, by assigning a value to a variable), and reformulate problems by relaxing or omitting constraints or variables.For constrained heuristic search to be well focused, we must decide where to apply an operator in the problem topology. Features of the topology must exist thatdifferentiate one subgraph from another, and these features must be related to the problem's goals. Seven features, called problem textures, have been identified and are being analyzed.[3]Given these definitions of problem topology and textures, the problem-solving model begins the search process with a single state that includes the initial problem topology. The model propagates constraints through the graph, computes texture measures, and selects a decision node (described in more detail below). The system then generates a new state by selecting an operator that either adds structure to the topology or further restricts a variable's domain at the decision node. Thus. Through the search process, the constraint graph is successively transformed into a solution. With this approach we can construct a nearly optional solution more quickly, manipulate the goals interactively, and gauge the impact of changes.Coral architectureCoral's architecture has three major modules, shown in Figure 2: a configurator, a resource allocator, and a plan analysis module.The configurator creates all feasible configurations of a product based on compatibility constraints. These configurations are then given to the resource allocator, which assigns quantities to each feasible configuration based on component inventory and quantity and composition constraints. The analysis module identifies bottleneck components and analyzes user-specified constraints on composition. For example, if a user-specified composition can be relaxed, the module can determine how many more orders can be filled.The configurator. We use a technique that is well suited for configuring "decomposable" artifacts with reasonably well defined structures and constraints. [4] This methodology is one of the decompositional approaches to configuration, and is intended for a weakly connected, "nearly decomposable" configuration artifact.[5,6] Such an artifact can be subdivided into parts or characteristics with relatively weak interactions. Some of these parts or characteristics can, in turn, be decomposed into sub-characteristics or parts, and so on. Similarly, the task of configuring an order can be subdivided in the tasks of configuring its major modules (or major features); the task of configuring a major module can be decomposed into tasks of configuring its major components or subfeatures, and so on, until we reduce the problem to the task of choosing between standard arrangements or parts.The decompositional model represents the configuration process as a sequence of refinements, each of which starts with an incomplete configuration state and produces a configuration state of a greater completeness ( in the sense that the new state contains more information about the configuration object). It does this by adding t one of the components its more detailed description (either its specific "committed" implementation, or its decompositional description). The newconfiguration state's structure is the same as the initial state's structure, at least at the level of abstraction found in the initial state.Problem topology. Decomposition treats the artifact as a tree-like structure. The root of the tree corresponds to the final configuration artifact. The leave are elementary objects, which are either predefined or are simple enough to be configured by predefined procedures. In general, each part of the tree can be configured in more that one way and, correspondingly, can have more that one decomposition. Hence, the problem topology is represented by an And-Or tree, as shown in Figure 3, and is known before the configuration process begins. In a decomposable configuration problem, all possible configurations of the artifact are implicitly defined by the problem topology (also known as the configuration knowledge tree). However, the space of all possible configurations is usually very large, and finding a configuration that satisfies a certain set of requirements (constraints and goals) is a computationally explosive problem. (It is an example of a disjunctive constraint graph,[7] which can also be represented as a dynamic constraint graph.[8]The topology is traversed hierarchically from top to bottom; higher level disjunctive decisions activate lower level variables and constraints. Constraint checking takes place only among active variables. Each constraint acts on one or more components, either by checking that the constrained component satisfies a certain condition encoded in the constraint, or by verifying proper relations between two or more components (for example, their compatibility). The constraint' s primary role is to evaluate the choice of values for the decision variables. This procedure accepts the values of one or more decision variables and returns the utility associated with this combination of values.Operators. Operators use domain-specific knowledge to guide their search through the space of possible configurations. They are expected to guess which value of the decision variable should be tried first when constraints do not have enough information to provide the answer, or to guess which variable should be assigned next when there are no fully constrained variables. Because there are two kinds of nodes (And-nodes and Or-nodes), there are two kinds of operators, And-specialists and Or-specialists.And-specialists choose the sequence in which the components defined in anAnd-node are to be instantiated. Depending on the active goals and constraints for a given configuration session, the sequence can vary, leading to different configurations. In choosing a sequence, an And-specialist refers to previous decisions, the constraints relevant to its node, and the configuration goals. To order the And-node parts, Coral enters all this information into the And-specialist' s rule or procedure and then processes it. Or-specialists select the most appropriate alternative among several that are associated with their respective Or-node. EachOr-specialist contains procedures or rules that consider previous decisions, constraints on its node, and configuration goals when making a selection. These procedures and rules can be used to1.rank all available alternatives and pick the one with the highest ranking, a single alternative that is suitable under current conditions, or3.generate an alternative (for example, by looking up a parts list).Search. The process of defining a valid configuration is a search for a consistent subtree of the configuration knowledge tree, where each Or-node is assigned a single alternative. The initial state is composed of the problem topology, that is, the configuration knowledge tree.1.The configurator begins the search by selecting one of the states (a partialconfiguration). When a single optimum configuration is sought, it isbeneficial to select a state in a "best-first" fashion. If all feasibleconfigurations need to be defined, the selection can be made at random.2.The local And-specialists rank the children of And-nodes, thereby selectingthe branch where the next configuration decision should be made. The firstunresolved Or-node found is the decision node.3.The local Or-specialist then selects and assigns the most promisingalternative to the decision Or-node. If all alternatives have been exhausted,the partial configuration is deleted and the process returns to step 1.4.The configurator adds the new assignment to the partial alternative, creatinga new state with an extended partial configuration. The module identifies andchecks all constraints relevant to the last assignment. A constraint ispotentially relevant if it is related either to the decision node itself or to any ofits ancestors (either an And-node or an Or-node). If the new partialconfiguration passes all the constraints, it is added to the list of partialconfigurations, and the process iterates from step 1.5.If the partial configuration violates a constraint, the configurator canreconsider previous decisions through dependency-based andknowledge-based backtracking, since a specific constraint can be associatedwith information about ways to fix that violation. [8,9]6.Search ends when a feasible sub tree is found.The resource allocator. For each requested product, the configurator provides the resource allocator with one or more configurations that satisfy the product requirements. Each acceptable product configuration requires the conjunctive allocation of one or more of each component. Maximizing the total number of product configurations depends on the allocator's ability to allocate bottleneck components. We can optimize the solution to this problem using constrained heuristic search. Problem topology. The problem topology is composed of nodes representinguser-defined product specifications, acceptable product configurations generated by the configurator, and components. Links be-tween nodes represent demand.For the problem of planning complete ammunition rounds, let's assume the user has specified the following composition:Roundl (155-mm HE): 40 percentRoundn (105-mm Apers): 60 percentFor Roundl, the user wants to maintain this component composition:Projectiles: lOO percentPD fuses: 60 percentMTSQ fuses: 40 percentFor Roundn the user requests 20 percent more fuses than projectiles, and wants to maintain the following component composition:Projectiles: l00 percentPD fuses: 60 percentMTSQ fuses: 60 percentThe configurator generates two feasible configuration types for each round: CT1 and CT2 for Round1, and CTn-1 and CTn for Roundn. Each configuration type contains feasible configurations based on compatibility constraints. The constraint graph for this problem is shown in Figure 4.The solution process. The allocator first constructs the initial state using the constraint graph as the state's problem topology (see Figure 5). The allocator then performs the following actions:1.Propagate constraints.Calculate component demand. Calculate each configuration's demandfor a component by multiplying the expected quantity by the numberof components required per configuration. For each component,determine the demand by summing each configuration's demand forthe component.Calculate max_rounds. For each configuration, determine how manyrounds of this configuration can be created given current inventoriesand independent of other configurations .1.Measure textures.Calculate component contention. For each component,determine the amount of contention by dividing demand foreach component by available quantity. The greater thenumber, the greater the contention.Calculate configuration reliance. A product's reliance on aspecific configuration is a function of the number of feasibleconfigurations of that product.2.Select a decision node by choosing a component and a configuration ofwhich it is a member. For example, we can start with the most or the leastcontentious components, or with the configuration that requires the mostcomponents. The heuristics for selecting a decision node include:Select the component with the greatest contention.If there is more than one component with the same contention, selectthe one with the smaller number of configurations.For a given component, select the configuration with the greatestreliance.3.Generate a new state. Once the allocator has selected a component, itgenerates a new state and allocates the quantity to the chosen configuration.Coral changes the constraint graph in the new state as follows:Decrement the component node's quantity by the amount allocated.Append the component node's allocation in the form(<configuration>, <amount allocated>).Set the configuration node's allocated amount to the specifiedamount.Assign and allocate other components to the chosen configurationnode.The analysis module. After running the resource allocator, Coral collects data for analysis and presentation to the user. The analysis module reports the results of the planning process, analyzes and reports on bottleneck components and remaining inventory, and replans through selective violation of constraints.There are cases where none of the alternative configurations can be used. This means that either the user requirements have over constrained the problem so that no solution is possible (in which case we relax the constraints), or bad choices have been made earlier in the solution process. For this reason, the system must record each decision and its alternatives so that dependency-directed backtracking can take place. The user can then answer "what-if" questions by reexecuting the algorithm after changing constraint graph parameters.An exampleWe developed a histogram-based input interface to enter order-composition specifications (see Figure 6), and used a tabular report (see Figure7) to enter definitions of ammunition rounds.Configuration. Figure 8 presents the configuration knowledge tree for the ammunition problem. Since a specification for separate loading rounds requires different ammunition components such as projectiles, propelling charges, primers, and fuses, we formed an And-node schema called Separate-loading-round and included all its parts. To include the different types of projectiles, we formed anOr-node schema called Projectile and listed alternatives such as HE, Hera, and Illum types.In this problem, the constraints almost exclusively deal with the compatibility of components and characteristics. The most important sources of constraints are the existing compatibility charts that list binary or higher order compatibility constraints. For example, PD fuse model number MK27 is Compatabile-only-with model MK 11 or M3Al of HE projectile, if model Ml or M2 of a 40-mm artillery cannon is used.User preferences on round type, component type, or component model provide another source of constraints. For example, at the level of rounds, the user might specify all 155-mm HE rounds (leading to many feasible configurations). At the component type level, the user might specify only PD or Prox fuses in 155-mm HE rounds. At the component model level, the user might specify only model M107 projectiles in 155-mm HE rounds (leading to the fewest feasible configurations). Example operators include the component-round local specialist (a heuristic for obtaining an optimal sequence of component classes for a given class of round) and the component-class local specialist (a heuristic for obtaining a reduced set of components, or model numbers, to match). The configuration process traverses the disjunctive constraint graph, in a best-first manner from top to bottom, using operators to order the instantiation of disjuncts and conjuncts. Only selected nodes have their constraints checked.Resource allocation. Each acceptable configuration of a complete round requires the conjunctive allocation of one or more projectiles, fuses, primers, and propellants. Specifications of the rounds define the demand for each component, which definesthe demand for each configuration type, which defines the demand for each configuration, which defines the demand for each component resource.Different types of constraints apply during resource allocation. The availability of the total number of components at given storage areas can affect the total number of rounds that can be configured from those locations .Also, the user can specify preferences for configurations or compositions with different levels of detail. The user can also specify an absolute number, a relative percentage, or an objective, like "maximize." At the level of rounds, the user might specify 100 155-mm HE rounds. At the component type level, the user might also specify 60 percent of PD fuses and 60 percent of Prox fuses per round (that is, 1.2 fuses per other components).We constructed a linear-programming model of the allocation portion of this problem. Tests demonstrated that optimal solutions could be obtained in those cases where a solution existed. But the nature of the ammunition configuration problem is such that a problem specification often does not entail a feasible solution. Thelinear-programming approach fails to provide a solution when the component inventory cannot satisfy all the orders. To make the allocator "user-friendly," it relaxes less important constraints or user preferences to compute the solution that matches the user's needs most closely.Figure 9 shows an example system out- put of the maximum number of configurable ammunition rounds. It shows that Coral has met percentage, quantity, and maximization goals effectively.Analysis. Coral performed the analysis tasks mentioned earlier: reporting the results of the planning process, analyzing and reporting on bottleneck components and remaining inventory, and replanning through selective constraint violation. Figure 10 shows a replanning analysis, including how many more rounds can be configured by selectively violating unimportant constraints.System performance. We developed three test cases within creasing complexity to validate system performance, and ran them on a Symbolics 3640. The first test case specified two rounds. The objective was to maximize the number of rounds while keeping the percentage relationship between the two rounds constant. The second test case specified three rounds. and its objective was to maximize the number of rounds. The third test case specified eight rounds: Six rounds had a percentage relationship with each other, and two rounds had a specified quantity. The objective was to maximize the number of rounds while meeting these constraints.Table I presents the performance of Coral's configurator and resource allocator modules in these test cases. In the third test, with a search space of 200,000 items and more than 1,000 constraints, the system needed less than 30 seconds of processor time to generate all feasible configurations, as well as allocations of components to feasible round configurations, for given ammunition round descriptions. The overall statistics show that processor time does not relate monotonically to the number of configurations but instead depends on the number of constraints and the complexity of underlying compatibility constraints.CORAL demonstrates the power of constrained heuristic search to solve configuration and allocation problems. Carnegie Group has created a generic version of the configurator called Spex. It is a reusable shell for developing applications that access parts databases for rapid product configuration. Spex has been applied to domains such as motor configuration, thus demonstrating the generality of our approach.[10]Research on the constrained heuristic search problem-solving paradigm continues. Major areas of concern include the development of additional textures, automating the process of problem reformulation through topological transformation, and distributed constrained heuristic search. Concurrently we have successfully applied the paradigm to spatial planning, transportation planning and scheduling, and factory scheduling.Acknowledgments。
