Pervasive Technologies Labs
Biosensors and Bioelectronics

Biosensors and Bioelectronics Biosensors and bioelectronics are innovative technologies that have the potential to revolutionize the field of healthcare and diagnostics. These devices are designed to detect and analyze biological substances, such as proteins, DNA, and other biomolecules, with high sensitivity and specificity. They have a wide range of applications, including medical diagnostics, environmental monitoring, and food safety testing. However, despite their immense potential, there are still several challenges and limitations that need to be addressed in order to fully realize the benefits of biosensors and bioelectronics. One of the main challenges facing biosensors and bioelectronics is the need for improved sensitivity and specificity. While these devices have the capability to detect and analyze biological substances with high precision, there is still room for improvement in terms of their sensitivity and specificity. This is particularly important in the field of medical diagnostics, where accurate and reliable detection of biomarkers is crucial for early disease diagnosis and monitoring. Researchers and engineers are constantly working on developing new materials and technologies to enhance the sensitivity and specificity of biosensors and bioelectronics, but there is still a long way to go before these devices can be widely used in clinical settings. Another challenge is the need for improved stability and durability of biosensors and bioelectronics. Many of these devices are made from delicate materials that can degrade over time, leading to reduced performance and reliability. This is a significant concern, especially in applications where long-term stability and durability are essential, such as implantable biosensors for continuous monitoring of physiological parameters. Researchers are exploring new materials and fabrication techniques to improve the stability and durability of biosensors and bioelectronics, but more research and development are needed to address this challenge effectively. In addition to technical challenges, there are also regulatory and ethical considerations that need to be taken into account when developing and deploying biosensors and bioelectronics. These devices are often used to collect and analyze sensitive biological information, raising concerns about privacy and data security. There is also a need for clear regulations and guidelines to ensure the safety and effectiveness of biosensors and bioelectronicsin various applications. Furthermore, there are ethical considerations surrounding the use of these devices, particularly in the context of genetic testing and personalized medicine. It is important for researchers, engineers, and policymakers to work together to address these regulatory and ethical challenges and ensure that biosensors and bioelectronics are developed and used responsibly. Despite these challenges, biosensors and bioelectronics have the potential to make a significant impact on healthcare and diagnostics. These devices have the capability to provide rapid and accurate detection of biomarkers, enabling early disease diagnosis and personalized treatment. They also have the potential to improve the monitoring of physiological parameters, leading to better management of chronic conditions and improved patient outcomes. In addition, biosensors and bioelectronics have applications beyond healthcare, including environmental monitoring and food safety testing, where they can help ensure the safety and quality of our environment and food supply. In conclusion, biosensors and bioelectronics hold great promise for the future of healthcare and diagnostics, but there are still several challenges and limitations that need to be addressed. Improving the sensitivity and specificity, stability and durability, as well as addressing regulatory and ethical considerations, are essential for realizing the full potential of these devices. With continued research, development, and collaboration among researchers, engineers, and policymakers, biosensors and bioelectronics have the potential to revolutionize the way we diagnose and monitor diseases, as well as improve the safety and quality of our environment and food supply.。
拜本兰 创新产品——来自拜耳材料科技
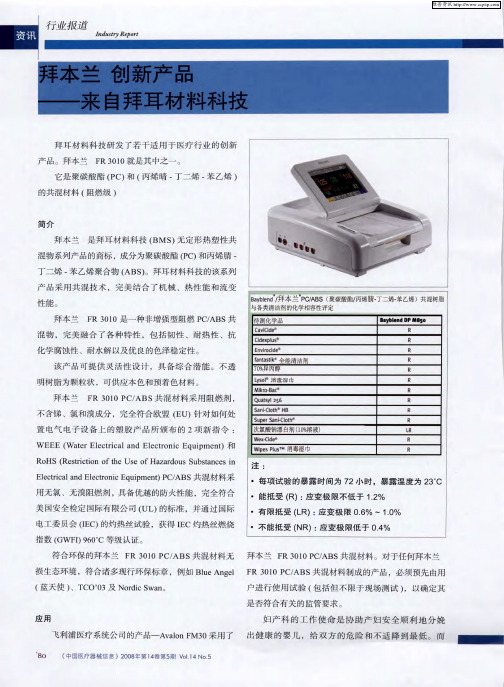
:
应 变极 限低 于 0 4 %
指 数 (G W
F I) 9 6 0 C
。
等级 认 证
。
符 合 环 保 的拜 本 兰 损生 态环 境
( 蓝天使 )
、
F R 3 0 10 P C / B S A
共 混 材料无
B lu
e
拜本 兰
F R 3 0 10 P C / B S A
共混 材料
。
对 于 任 何拜 本 兰
了保 证 监 护 仪 正 常 稳 定 地 运 转
,
该仪器能 然而
,
剂
,
不 仅 能 承 受短 时 间和 长 时 间 高温 接 触
。
而 且 不 含锑
、
。
为
氯和溴成 分
而 事实上
,
在加工 过程 中
,
该 产 品 中的 共混材
其外机壳必 须满足
挥 发 性 物 质 与不 含 阻 燃 剂 的 非 增 强 型 料 的 析 出 率 处 于 相 同水 平
v ol 14 N。 5
维普资讯
行 业 报道
I n d u s t ry R ep
o r
t
为 了配 合这
一
神圣 的工 作
,
飞 利 浦 医 疗 系 统 公 司认
,
由于拜本兰
F R 3 0 10 P C / B S A
共混 材料采用 阻燃
,
为采 用 高性 能 分 娩 监 护 仪 是 十 分 必 要 的 在 整 个 分 娩 过 程 中发 挥 强 大 的 监 护 作 用
是 拜 耳 材 料 科 技 (B
,
M S
) 无 定形热塑性共
一
混 物 系 列 产 品 的 商标 丁二 烯
量子计算机的性能优化技巧分享

量子计算机的性能优化技巧分享引言:随着科技的不断发展,量子计算机成为了未来计算领域的一颗明星。
量子计算机的特殊性质使得其在特定问题的求解上具有巨大的优势,但是现阶段量子计算机的性能仍然有限。
为了充分发挥量子计算机的优势,科学家们一直在探索各种性能优化技巧。
本文将分享一些目前可行的量子计算机性能优化技巧,希望能为读者在量子计算领域提供一些参考和启示。
一、量子纠错与错误消除量子计算机中的量子比特(qubit)常常遭受到干扰和错误,这使得计算结果的准确性和可靠性受到限制。
为了解决这个问题,科学家们提出了量子纠错和错误消除的方法。
量子纠错通过在量子门操作前后加入纠错机制来修复量子比特的错误。
错误消除则是在计算过程中通过重复多次计算并对结果取多数投票的方式来消除错误。
这些方法可以提高量子计算机的可靠性和稳定性,从而提高性能。
二、量子优化算法设计除了纠错和错误消除,还有一种更直接的方式来优化量子计算机的性能,那就是设计更高效的量子优化算法。
传统计算机的算法在量子计算机上并不能发挥出最佳性能,而量子计算机有自己的特点和优势。
因此,科学家们正在针对特定问题,设计出适合量子计算机的优化算法,以求得更优的解决方案。
例如,针对旅行商问题,已经有一些有效的量子优化算法被提出,并在实验中取得了较好的结果。
这种算法设计的创新和优化,将进一步提高量子计算机的性能。
三、智能编码与量子传输量子计算机中的量子比特数目通常较少,但是问题的规模往往很大,因此如何以更高效的方式来表示和传输信息是一个重要的问题。
智能编码是一种有效的手段,它可以将问题的复杂度降低并减少量子比特的使用。
通过合理设计编码方式,可以使得量子计算机在处理大规模问题时更高效。
另外,量子传输也是一项关键技术,它可以实现远距离量子信息的传递。
在量子计算领域,智能编码和量子传输的技术进步将有助于提高量子计算机的性能和扩展其应用范围。
四、噪声抑制与冷却技术量子计算机的性能也受到噪声的影响,而噪声主要来源于环境干扰、热漂移等因素。
ASPEN爱斯本医疗器械颈托、护腰招商

加盟合作程序及条件:
1、线上需要提供京东、天猫、苏宁或淘宝C店的名称, 线下需要提供公司或者医院的资料。
2、申请成功后,授权并保证每月拿货不低于10万元。
美国爱斯本医疗技术公司尤其重视亚洲市场的开 发,将为亚洲市场提供更有针对性、更完备、更齐全、 操作更简易、使用更舒适的优质颈胸腰脊柱外固定产 品。
美国Aspen产品特点:
1、获有美国8种专利,FDA认证之高质量医疗用品 2、获有北美脊柱外科学会(NASS)颁发“最佳脊椎
技术及照护奖” 3、国际性医学会研究文献证实对椎体稳定整合、反压
产品资料:ASPEN高端儿童颈托
VISTA六段可调节颈托
爱斯本(ASPEN)QD护腰
爱斯本(ASPEN)SUMMIT631护 腰
爱斯本(ASPEN)SUMMIT637护 腰
爱斯本(ASPEN)LUMMAR护腰
爱斯本庆:重庆西南医院 四川:四川华西医院 北京:北京301医院 昆明:成都军区昆明总医院 广东:广州南方医院 浙江;杭州新华医院 上海:上海仁济医院
ASPEN爱斯本医疗器械招商
美国ASPEN爱斯本品牌简介:
美国爱斯本医疗产品公司是有设计、研发和销售 静雄要脊柱稳定及运动限制支具领域的主力军。公司 厂房占地面积51000平方英尺,分销渠道遍布全美,市 场占有率超过了70%,在经济危机肆掠的2009年,其 全球销售整张率达到18%,净收入曾张26%。25年以来, 美国公司的管理团队和员工致力于研究一系列先进一 流的脊柱外固定产品,为健康护理市场开创了新篇章。
疮之卓越功效 4、依人体工学与力学精密计算及设计生产 5、可调性:依不同身高与体型自由精准调节 6、完整支撑性:术后骨整合须要三个月完整支撑,
否则可能神经错位 7、脊柱外用支具类全球第一大品牌八、欧美国家市占
SPV立场提神筒

SPV立场提神筒立场电子科技发展上海有限公司目前已在中国和美国分别注册“SPV”作为品牌,并已在中国和美国初步建成研发中心,包括:调香实验室、香原料研发实验室、常规检测室、、工艺实验室、分析检测室,共六大实验室,可满足在标准和方法制定等方面的实验需求,以及在器具、香原料基础研发及香精复配制备方面的需求。
该研发中心现有技术人员30余人,未来并规划在美国建立研发生产工厂SPV立场提神筒是一款新型的提神产品,拥有多种口味,包括可乐(v3)、红牛(v5)、水果薄荷(v6)、炭烧咖啡(v8)等,方便携带,随时随地清新口气,提神醒脑。
与传统的电子烟相比,SPV立场提神筒品质更高,提神效果以及口感更佳,且不含尼古丁,不产生二手烟、焦油、一氧化碳、苯等有害成分。
现有口味:SPV(v3)可乐 SPV(v6)水果薄荷 SPV(v8)炭烧咖啡 SPV(v5)红牛SPV立场提神筒基本信息:工作电压:3.4v-4.1v烟支重量:约4.6g电池容量:90MAH单支口数:约150口SPV立场提神筒结构内置聚合物锂电池、气流传感器、控制电路、雾化器、雾化剂组成。
采用微智能电路,吸气时自动打开,提神筒开始工作,操作简单便捷。
SPV立场提神筒工作原理SPV立场提神筒中内置有气流感测器,并由微处理晶片控制各部件的工作状态,使该器械只有通过嘴吸气时雾化器才工作,工作状态下,雾化器将雾化剂雾化产生直径0. 5 - 1 . 5 um 左右的雾滴可通过吸嘴吸入口腔,产品的前端装有色发光二极体,在吸气时会闪光。
SPV立场提神筒核心技术♦新型雾化载体的研发♦新型原料的选择和获取,借助在二氧化碳超临界萃取、水蒸气蒸馏、分子蒸馏、膜分离、分段萃取等方面的技术积累,选择和制取创新型原料♦新型香原料制备工艺,采用高新技术制备香原料,并能保证供应稳定的完整工艺流程♦雾化液的所有成分都通过质量安全评估及测试,确保原料安全;♦每款产品由具有多年经验的调香高级专家精心调配,口味纯正,细腻优雅,醇和满足。
瑞士微科专业知识总结

品牌5大先进技术瑞士微科应用五大前沿“皮肤机能健康管理技术”,全面修复皮肤内机能,是国际化妆品领域抗衰技术的一大突破和创新。
1.皮肤微循环修复技术——保障细胞供养充足,自我制造胶原蛋白等必需物质。
国际专利技术,启动、疏通、修复细胞供养通道,令细胞得到由毛细血管输送的大量自身养分,激活成纤维母细胞长期产生大量自体胶原蛋白、弹力纤维、网状纤维并重组架构,同时分泌基质,大量吸附水分聚合,皮肤细胞得到循环系统所提供的大量营养物质及氧份(养分)支持。
瑞士微科——皮肤抗衰老的秘诀2.皮肤细胞生物分子激活技术(DNA修复技术)——靶向修复细胞DNA,保障恢复正常的细胞机能。
“细胞生物分子激活技术”的最新科技,能使营养物质直接穿透细胞膜进入细胞内,清除细胞膜上沉积的毒素,强壮细胞线粒体,直接修复受损细胞DNA,从而令细胞内的重要组成部分细胞核、线粒体、溶酶体及细胞膜运作正常,修复细胞达至健康。
3.网状层重塑定位科技——重塑网状层胶原和弹性纤维,让真皮层饱满紧致。
运用最新高科技特定的20万赫兹恒温生物探测波,直达真皮结缔组织纤维,梳理网状纤维、弹性纤维、胶原纤维排列整齐,形成粗大的纤维束交织成网,致密粗壮,塑紧定位,令皮肤底层的网状纤维重新架构。
同时让受阴受压的毛细血管、淋巴管循环畅通,进一步解决细胞供养的问题,恢复皮肤弹性,重塑轮廓。
4.靶向修复基底细胞科技——阻断黑色素,更新表皮层从表皮基底层逐层扫描到角质层,清除表皮细胞中的毒素,净化细胞孕育生存空间,同时加大细胞更新和储存营养的能力,帮助细胞从基底层逐层到角质层的推陈更新,加大表皮细胞中的健康比例,增强表皮层的自我修复和更新能力。
5.细胞激活4D科技应用数码4D深导科技,将高浓度活细胞因子真皮植入,建立“营养仓库”,激活自体细胞群,令成纤维母细胞及新生细胞数量增加,数倍提高胶原蛋白的产量,合成更多新的富有弹力的立体的三维网(胶原纤维、弹性纤维和网状纤维),恢复皮肤的弹性和立体轮廓。
监控技术是福是祸英语作文

监控技术是福是祸英语作文英文版:The advent of surveillance technology has been adouble-edged sword in modern society. On the one hand, it has significantly improved security and facilitated the maintenance of law and order. Surveillance cameras, for instance, can deter crime and provide crucial evidence when incidents do occur. Moreover, these technologies have been instrumental in areas such as traffic management, where they help monitor and regulate the flow of vehicles, thereby reducing congestion and enhancing road safety.However, the proliferation of surveillance technology also raises serious concerns about privacy and civil liberties. The pervasive nature of such technologies means that individuals can be monitored almost anywhere and at any time without their knowledge or consent. This can lead to a chilling effect on free speech and assembly, as people may feel uncomfortable expressing their opinions or gathering in public for fear of being watched.In addition, there is the risk of misuse ofsurveillance data. Unauthorized access or breaches can compromise personal information, leading to identity theft or other forms of exploitation. Furthermore, the potential for abuse by authorities poses a threat to democratic values, as unchecked surveillance can be used to intimidate and silence dissent.In conclusion, while surveillance technology offers undeniable benefits in terms of security and efficiency, it is essential to balance these advantages with theprotection of individual rights and freedoms. This can be achieved through the implementation of strict regulations and oversight mechanisms that ensure the responsible and ethical use of such technologies.中文翻译:监控技术的出现在现代社会中既是福也是祸。
介绍生活中的数字科技的英语作文

介绍生活中的数字科技的英语作文The Pervasive Presence of Digital Technologies in Our Daily LivesIn the modern era, digital technologies have become an integral part of our daily lives, seamlessly integrating into various aspects of our routines and activities. From the moment we wake up to the time we retire for the night, these innovative technologies are constantly at our fingertips, shaping the way we interact, communicate, work, and even entertain ourselves. The ubiquity of digital technologies has transformed the landscape of our daily lives, ushering in a new era of convenience, efficiency, and interconnectedness.One of the most prominent examples of digital technology in our daily lives is the smartphone. This pocket-sized device has become an indispensable tool, serving as a gateway to a vast array of functions and applications. With a simple tap or swipe, we can access a wealth of information, communicate with loved ones, manage our schedules, and even control various aspects of our homes. Smartphones have evolved beyond mere communication devices, becoming powerful multi-functional tools that seamlessly integrateour personal and professional lives.Beyond smartphones, digital technologies have also revolutionized the way we interact with our living spaces. Smart home technologies, such as voice-activated assistants, connected appliances, and intelligent lighting systems, have brought a new level of convenience and automation to our daily routines. With just a voice command or a tap on a smartphone, we can control the temperature, monitor our energy usage, and even receive real-time updates on the status of our household appliances. These technologies not only streamline our daily tasks but also contribute to a more energy-efficient and sustainable living environment.The integration of digital technologies extends to our modes of transportation as well. The rise of ride-sharing services, GPS-enabled navigation apps, and electric vehicles have transformed the way we commute and travel. Commuters can now plan their routes, book rides, and track the progress of their journeys with just a few taps on their smartphones. Furthermore, the increasing adoption of electric vehicles and the development of charging infrastructure have made sustainable transportation more accessible and practical for daily use.In the realm of entertainment, digital technologies have also left an indelible mark. Streaming platforms, such as Netflix, Hulu, and Amazon Prime, have revolutionized the way we consume media,allowing us to access a vast library of movies, TV shows, and documentaries at our convenience. Gone are the days of physical media and cable television; now, we can seamlessly transition between devices, picking up where we left off on our favorite shows or movies. Additionally, the proliferation of online gaming and virtual reality experiences has opened up new avenues for leisure and social interaction, blurring the lines between the physical and digital worlds.The impact of digital technologies extends beyond our personal lives and into the professional realm as well. Remote work and teleconferencing tools have become essential for many individuals and businesses, enabling seamless collaboration and productivity even in the face of geographical barriers. Cloud-based storage and file-sharing platforms have revolutionized the way we access, manage, and share information, allowing for greater efficiency and streamlined workflows. Furthermore, the rise of e-commerce and digital marketing has transformed the way we conduct business, offering new opportunities for entrepreneurs and small businesses to reach a global audience.The integration of digital technologies in our daily lives has also had a significant impact on our education and learning experiences. Online learning platforms, virtual classrooms, and educational apps have made knowledge more accessible and flexible, allowing individuals to learn at their own pace and from the comfort of theirhomes. Additionally, the use of digital tools and interactive learning materials has enhanced the overall educational experience, making learning more engaging and effective.While the pervasive presence of digital technologies in our daily lives has brought about numerous benefits, it has also raised concerns and challenges that require thoughtful consideration. Issues such as data privacy, cybersecurity, and the potential for digital addiction and overreliance on technology must be addressed to ensure a balanced and responsible integration of these technologies into our lives.In conclusion, the digital technologies that have become deeply embedded in our daily lives have transformed the way we live, work, and interact. From smartphones and smart home technologies to transportation and entertainment, these innovations have brought about unprecedented convenience, efficiency, and interconnectedness. As we continue to embrace the digital revolution, it is crucial that we navigate this landscape with a keen eye on the potential risks and challenges, ensuring that the integration of digital technologies enhances our lives in a sustainable and responsible manner.。
瑞士步琦:“浓缩”的精华

瑞士步琦:“浓缩”的精华作者:暂无来源:《食品安全导刊》 2010年第2期□ 嘉宾张清蕾瑞士步琦公司市场部经理□ 采编马永娇本刊记者入选理由瑞士步琦(Buchi)公司自1939年成立以来,一直致力于实验室常用仪器设备(中压分离纯化制备色谱、喷雾干燥仪、凯氏定氮仪、蛋白质和脂肪测定仪等)的生产和销售,而且确定了“在这些关键技术上保持产品开发、制造和应用的领先优势”的目标,如今已在实验室用蒸发仪、分离仪以及近红外色谱仪和品质控制参考方法等方面处于全球领先地位。
作为旋转蒸发仪的市场领导者,瑞士步琦曾在1957年推出世界上首台旋转蒸发仪,有效解决了化学实验室中有机溶液的快速回收问题。
之后瑞士步琦再接再厉,陆续推出了更多先进的浓缩产品,如R-210/215系列、Syncore PolyVap及M ulti系列(M ultiVapor P-12、M ultiVapor P-6)等等,这些浓缩产品大大提高了检测效率,受到业内人士的广泛认可。
用户点评旋转蒸发仪用户点评:我们中心使用瑞士步琦的旋转蒸发仪已经有很多年,可以说是瑞士步琦的忠实用户,而瑞士步琦也一直为我们提供良好的技术支持及满意的售后服务。
通过使用瑞士步琦的旋转蒸发仪,我们的工作效率得到了明显提高。
(陈颖,上海市食品药品检测中心)Multivapor P-6用户点评:由于我们每天要处理的样品较多,而Multivapor P-6可同时浓缩多样品的特点恰好能够满足我们的要求。
目前,Multi P-6在我们科室主要用于糕点中食用植物油的检测,具体作用是减压蒸馏石油醚与油的混合物,得到纯的浓缩食用植物油,待检。
采用Multivapor P-6一次可以处理6个样品(每个样品体积120mL)左右,一批样品处理时间只需20分钟左右,与以前用旋转蒸发仪只能处理单个样品相比,我们的工作量大大减少,效率得到了明显的提高。
此外,Multivapor P-6操作简单,全透明设计也非常适用于我们科室。
赢创推出新型SP系列二氧化硅

美国材料实验协会( m r aS c t te i Ma r l E 0 火焰蔓延实验 ,获得 A级防火涂料的评定。 A e cn oiy T sn t is 18 i e o tg ea )
硅树 脂涂 料可形 成无 痕 、防水 的密 封层 ,抗大气 和臭氧 氧化 及雨 雪风蚀 ,还 可 以抗裂 、抗剥 离、防缩、 以及 防止 变硬 和变脆 。
H S 3 和 H S 4 R R均为硅树脂橡胶喷涂材料产品,因不含溶剂而无挥发性 ,与传统石油成分 S 55 S 50 2
屋顶材料相 比, 更有助于环境保护。 此外, S 50 H S 4 中含有 2%可回收的三元乙丙橡胶( 0 含双环戊二稀) ,
因此可 提 高涂料 的物理 性能 。同时 ,该 涂料还 可 防紫外 线且 不易老化 。H S 3ad S 50 2 S 55nH S 4 R R也通 过
事业一次比一次拓展,企业一次比一次强盛 。尤其是最近几年来 ,巨化集团的氟化工主 业呈现出快速
发展的态势,初步实现了由传统型企业向新型现代化企业的转变 ,在国内氟化工领域始终保持着领先
镀膜与研发服务

镀膜与研发服务原子层沉积(ALD)镀膜和研发服务芬兰倍耐克公司的镀膜服务为评估针对特定应用的镀膜解决方案提供了最有效的手段,尤其是在评估方案的技术和工业可行性。
通过镀膜服务客户可以充分了解使用原子层沉积(ALD) 技术在实际操作中的可行性。
在客户在做出投资决定前,倍耐克公司的镀膜服务为客户提供了一种安全和可控的方法。
非常欢迎您带着面临的难题和我们联系,我们可以为您提供专业的研发服务和设备,几乎您所能想到的材料我们都可以为您实现。
作为倍耐克公司客户解决方案的一个有效组成部分,我们的研发部门提供全面和专业的ALD研发服务。
我们的研发团队在工业应用,可行性研究(技术和购置成本)和试制生产领域有着丰富的经验。
事实上,绝大多数倍耐克公司的设备在交付前都经过了镀膜验证和详细的工艺分析。
倍耐克公司每年为超过100家客户提供1000多个批次的镀膜服务,其中涵盖了从镀膜应用,工艺到设备设置等各种领域。
涉及的课题包括照明和光伏产业的阻挡层,厚度可调的医用涂层,高精度的光学镀膜和针对石化行业的耐高温涂层。
倍耐克公司为客户提供标准或量身定制的镀膜服务,客户可以选择各种基底和材料。
客户评价:”倍耐克公司的镀膜服务帮助我们研发出针对特定客户的镀膜解决方案,同时作为外部供应商解决了我们小批量ALD镀膜业务的需要。
倍耐克公司专业的ALD经验和充足的设备资源为我们的应用提供了一个宝贵和可行的ALD解决方案。
”Dr Jan-Uwe Schmidt -Dept. Engineering/MEMS Technology Development-Fraunhofer IPMS, Germany.C S , c n 11/2010Beneq Oy P.O. Box 262FI - 01511 Vantaa FinlandBeneq China Beneq Germany Beneq USATel. +358 9 7599 530**************Sales and Service Offices:Main Office:芬兰倍耐克有限公司上海代表处Tel. +86 21 6881 0151Fax +86 21 6881 0152倍耐克镀膜服务为客户带来的裨益• 快速切入到ALD镀膜技术,而且可以很快 得到初步的结果• 灵活的镀膜生产能力: 倍耐克公司现在拥 有7台 不同的镀膜设备,从适合于科研的 TFS 200到大批量工业化生产的P800.• 专业的服务人员随时为您提供包括咨询和 研发方面的服务• 充分利用倍耐克公司在镀膜方面的专业知 识• 简单快速地将工艺从做样品设备转移至 客户的研发设备或生产设备• 产品可以迅速投入市场• 在做投资前,风险低且可控。
雅本,雅本化学的技术优势

雅本化学的技术优势――手性技术
据了解,苏州雅本化学股份有限公司董事长蔡彤与中国科学院上海有机化学研究所所长丁奎岭博士,在太仓港区签订了手性技术联合实验室及产学研合作协议书。
根据协议,双方将共建手性技术联合实验室,专注于手性产品或单一对应体的合成和拆分技术的中试放大,着力建设手性产品特别是关系国计民生重大产品的产业化示范基地、手性技术产业集聚地,打造出有影响力的“手性谷”。
就化学制药领域而言,由于目前手性药物占全球药物销售总额的比重已接近60%,对于手性药物而言,在获得单一异构体的生产中,外消旋体的拆分是一个重要的途径。
在消旋过程中,理想的产出率只能达到50%,另一半异构体只能废弃,可能对环境造成污染。
但如果在消旋过程中转换无用的异构体以减少生产对环境可能造成的污染,成为医药生产企业和精细化工中间体生产企业面临的重大课题。
如果能解决无用异构体的处理,则不仅可极大提高生产效率、降低生产成本,更重要的是可真正实现“绿色化学”的目标。
雅本化学申请并发表的专利“经合成、拆分与消旋化制备手性药物左乙拉西坦中间体(S)-(+)-2-氨基丁酰胺盐酸盐的方法”(专利号:ZL200610030420.X)。
手性技术正是该司的技术优势。
该司致力于成为一家在手性技术领域首屈一指的医药化学公司。
博辉瑞进打造“生命黑科技”

博辉瑞进打造“生命黑科技”作者:暂无来源:《经理人》 2019年第9期博辉瑞进是一家致力于为外科手术和修复提供先进的全面解决方案,推动外科临床革新。
拥有自主知识产权的再生医学材料、植入性组织修复器械、智能化微创手术器械等平台性技术。
该公司自主研发的核心产品和技术——非交联细胞外基质源生物材料(SIS材料),是中国再生医学中的“黑科技”。
文 / 张艺琼很多科幻电影里都有这样的情节:主角身体受到严重创伤,在先进医疗技术帮助下,患者的创处很快痊愈,伤口也恢复如初。
在医学科技高速发展的今天,这种美好遐想正在逐步照进现实,这一切都源于一项可以改变人类命运和未来的学科—再生医学(regenerative medicine)。
美国生物学家、诺贝尔奖得主吉尔伯特曾预言:“用不了50年,人类将能够培育出人体所有器官。
”随着干细胞、组织工程等研究的不断深入,“再生医学”这门新型学科开始引领一场影响深远的医学革命。
根据公开信息,中国在科技方面的研发开支额度已经从1996年的59亿美元增长到了今天的440亿美元。
其中,中国再生医学研发资助的约78%被用于产品开发,另外约16.8%用于应用研究。
中国已经开发出了大量灵长类动物群用于临床前测试,而且一系列疗法开始了临床测试。
根据MRC(Myofunctional Research Center)认为,中国对临床应用的迫切要求—这让它可以迅速产生新的科学知识—是以损害一些基础研究为代价的,这些基础研究旨在克服控制干细胞行为和分化等技术挑战。
另外,中国研发预算只有5.2%分配给了基础研究,相比之下,日本、韩国和美国的比例是13%到19%。
即便是那些分配给支持“战略基础研究”的基础研究资助也被设计成鼓励应用。
在再生医学方面要取得卓越成就,中国各科研机构和商业企业,面临的难度不小。
再生医学“黑科技”“再生医学是一门对于生命探索的科学,作为一名生物科研工作者,就是把不可能变为可能。
”北京博辉瑞进生物科技有限公司(以下简称“博辉瑞进”)董事长赵博如是说。
英语长难句50句

in case of emergency. they were just as confused and helpless as anybody else. [结构分析] 此句是由 for 引导的一个并列复合句,共有三层含义,但位置比较特殊。其中结
果在前,原因在后,让步从句在句中,翻译时必须按照汉语习惯顺序作必要的调整。 [语法难点] for 引导的并列从句,as … as 比较结构。 [词汇知识] stand by 袖手旁观;待机;维持,遵守
In case of 如果;万一 emergency 紧急情况,突然事件,非常时刻,紧急事件 [参考译文] 尽管警察已接到命令,要做好准备以应付紧急情况,但人们不敢出门,因为警察 也和其他人一样不知所措和无能为力。
genera‐tion after the energetic founders. [结构分析] 该句主干为 The change met… and prevented 。that 后边引导的是一定语从句,
作后置定语,修饰 the decline in efficiency; 介词短语 in ten second and third generation 作
universe formed an ordered structure that the macrocosmic pattern of the whole is
repro‐duced in the microcosmic pattern of parts so that it is possible to draw inferences by
感受大自然神奇的馈赠,储存肌肤年轻的资本——以色列IBR公司全新抗衰老产品推介

素 ) p y o l e e( 和 h t fu n 六 氢 番 茄 红 素 ), 大 家 是 熟 知 的有 色 类 胡 萝 卜 素 如 p 胡 萝 卜 、叶 黄 素 一 素 等 的合 成 前 驱 物 ; 那 与 些 有 色 的 类胡 萝 I 相 、 素
以色 列I R B 公司凭借 其 独特 的地 理 优 势 和技 术平 台, 地 中海 的盐 生杜 氏藻 中提 取 无 色 类胡 萝 I , 从 、 素 获 得产 品一 R C C , I — L  ̄ 以及 从 富含 类 胡 萝 卜 B 素的 非转
基 因番 茄 中获 取 无 色类 胡萝 卜 I R- CL ⑧, 素一B T C 它们 能有 效 对 抗 自由基 , 少 自由基 带来 的各 种 损伤 。 减 大
p yo n 八 氢 番茄 红 h t e e(
理 揭 示 了细 胞 的有 限 复制 能 力 主 要 是 依 赖 于 染 色体 末 端 的DN 重 复 序 列 ( A 又称 “ 粒 ” 。“ 粒 ” 端 ) 端 也被 科 学家 称作 “ 生命 时 钟 ” 在 新 细 胞 中, , 细胞 每 分 裂一 次 , 粒 就 缩短 一次 ,“ 粒 ” 端 端 不能 再 缩 短 时, 胞 就 细
I R 有 的专 利 产 品 为 化 妆 品带 来 革 命 性 B 独
原 料 ,公 司 也 因此 于2 0 及 2 0 连 续 两 年 05 06
荣获 欧洲BS B原料研 发创新奖 。其独特 的
肌 肤 “ 眠 ” 理 念 和 专 有 的 “ 色 类 胡 萝 休 无 卜 ” ,以 其 特 有 的 角 度 解 析 肌 肤 衰 老 , 素 引领 个 人 护肤 品最 新 潮 流 。
因此 ,“ 缓 细胞 分 裂 ”就 能保 护 “ 粒 ”, 存 减 端 储 有 限的 细胞 资本 , 长 细胞 的生 命周 期 , 而 延 缓 肌 延 从 肤 的衰老 。
数字科技的好处与坏处英语作文 范文模板

数字科技的好处与坏处英语作文范文模板In the ever-evolving landscape of the digital age, the embrace of digital technology has become ubiquitous, reshaping various facets of human existence. This essay delves into the advantages and drawbacks of digital technology, scrutinizing its impacts on society, economy, and individual lives.Digital technology, with its rapid advancements, has undeniably revolutionized communication. Distance is no longer a barrier, as individuals can connect instantaneously across the globe. Social media platforms facilitate networking and foster virtual communities, transcending geographical limitations. Moreover, digital communication enhances accessibility for individuals with disabilities, promoting inclusivity and diversity.Another boon of digital technology lies in its transformative effect on education. Online learning platforms offer flexible and personalized learning experiences, catering to diverse learning styles. Studentscan access a wealth of educational resources at their fingertips, fostering self-directed learning and intellectual exploration. Additionally, digital tools such as simulations and virtual reality augment traditional pedagogical methods, enriching the learning process and enhancing comprehension.Furthermore, digital technology has revolutionized various industries, propelling economic growth and innovation. Automation streamlines production processes, increasing efficiency and reducing operational costs for businesses. E-commerce platforms provide a global marketplace for entrepreneurs, enabling small businesses to compete on a level playing field with corporate giants. Additionally, digital marketing strategies leverage data analytics to target specific consumer demographics, optimizing advertising campaigns and driving sales.Despite its myriad benefits, digital technology also harbors inherent risks and challenges. One of the foremost concerns is the erosion of privacy in the digital age. Pervasive surveillance technologies and data miningpractices encroach upon individuals' privacy rights, raising ethical and legal dilemmas. Moreover, the proliferation of fake news and misinformation in digital spaces undermines the fabric of democratic societies, eroding trust in institutions and exacerbating social polarization.Furthermore, the digital divide exacerbates existing socioeconomic disparities, perpetuating inequalities in access to information and opportunities. Marginalized communities, lacking access to reliable internet connectivity and digital literacy skills, are left behind in the digital revolution. This digital divide widens the gap between the haves and have-nots, exacerbating socioeconomic inequalities and hindering inclusive development.Additionally, the overreliance on digital technology poses risks to mental and physical well-being. Excessive screen time and social media usage have been linked to various health issues, including eye strain, sleep disturbances, and diminished interpersonal relationships. Moreover, theomnipresence of digital devices fosters addiction-like behaviors, leading to compulsive internet usage and digital dependency.In conclusion, digital technology presents a double-edged sword, offering unprecedented opportunities for connectivity, innovation, and economic growth, while also posing significant risks to privacy, equality, and well-being. To harness the benefits of digital technology while mitigating its adverse effects, policymakers, businesses, and individuals must adopt a balanced approach,prioritizing ethical considerations, digital inclusion, and holistic well-being in the digital age.。
有关ai看法英语作文

有关ai看法英语作文Here is an English essay on the topic of AI:The Rise of Artificial Intelligence: Promises and PerilsArtificial Intelligence (AI) has emerged as one of the most transformative and pervasive technologies of our time. As AI systems become increasingly sophisticated, they are poised to revolutionize countless aspects of our lives, from healthcare and transportation to entertainment and education. However, the rapid advancements in AI also raise significant ethical, social, and philosophical questions that demand careful consideration.At its core, AI refers to the development of computer systems capable of performing tasks that typically require human intelligence, such as learning, problem-solving, and decision-making. The field of AI has witnessed remarkable progress in recent years, driven by the exponential growth in computing power, the availability of vast amounts of data, and the refinement of machine learning algorithms. Today, AI-powered systems can excel at a wide range of tasks, from playing complex games like chess and Go to analyzing medical images and predicting weather patterns.One of the most promising aspects of AI is its potential to enhance human capabilities and improve our quality of life. In the healthcare sector, for instance, AI-powered tools are being used to assist in the early detection of diseases, personalize treatment plans, and streamline administrative tasks, freeing up healthcare professionals to focus more on patient care. Similarly, in the transportation industry, autonomous vehicles and intelligent traffic management systems powered by AI can potentially reduce accidents, alleviate congestion, and provide more efficient and sustainable mobility solutions.Moreover, AI has the capacity to enhance human creativity and problem-solving by augmenting our cognitive abilities. AI-powered assistants can help us generate new ideas, write more effectively, and solve complex problems more efficiently. In the field of scientific research, AI algorithms are already aiding researchers in making new discoveries and accelerating the pace of innovation.However, the rise of AI also presents a range of challenges and potential risks that must be addressed. One of the primary concerns is the impact of AI on employment and the job market. As AI systems become more capable of performing tasks traditionally carried out by humans, there is a legitimate fear that certain jobs will become obsolete, leading to widespread job displacement andsocioeconomic disruption. This issue raises complex questions about the need for reskilling, education, and the reorganization of work.Another crucial area of concern is the ethical and social implications of AI. As AI systems are increasingly involved in decision-making processes that affect people's lives, there is a growing need to ensure that these systems are designed and deployed in a responsible and accountable manner. Questions around algorithmic bias, privacy, and the transparency of AI-powered decisions must be addressed to safeguard individual rights and societal well-being.Furthermore, the development of advanced AI, particularly in the realm of artificial general intelligence (AGI), which aims to create machines with human-like cognitive capabilities, raises profound philosophical and existential questions. The prospect of superintelligent AI systems that surpass human intelligence raises concerns about the potential loss of human agency and control, as well as the possible existential risks that such systems may pose to humanity.To navigate the promises and perils of AI, a multifaceted approach is required. Policymakers, technologists, ethicists, and the public must engage in an ongoing dialogue to establish robust governance frameworks, ethical guidelines, and regulatory mechanisms that can ensure the responsible development and deployment of AI.Investments in education and workforce development are crucial to equipping people with the skills and knowledge necessary to thrive in an AI-powered future.Additionally, the research and development of AI must be guided by a deep commitment to human-centric values, including fairness, transparency, and the preservation of human autonomy. By striking a careful balance between the potential benefits of AI and the mitigation of its risks, we can harness this transformative technology to enhance human flourishing and create a more equitable, sustainable, and prosperous future.In conclusion, the rise of artificial intelligence is a complex and multifaceted phenomenon that holds both immense promise and significant challenges. As we navigate this technological revolution, it is incumbent upon us to approach AI with a nuanced understanding, a commitment to ethical principles, and a vision for a future in which human values and well-being remain at the forefront.。
泽柏(北京)科技发展有限公司

描述 货号 适应显微镜 描述 货号 适应显微镜 描述 货号 适应显微镜 描述 货号 适应显微镜
描述 货号 适应显微镜 描述 货号 适应显微镜 描述 货号 适应显微镜
描述 货号 适应显微镜
描述 货号 适应显微镜
描述 货号 适应显微镜
信息描述 Bulb 110V 15W Tungsten 380018-1830-000 KF 2 Bulb 12V 100W Halogen - Jenaphot 000000-0213-940 JENALAB;JENALUMAR;ENAMED; JENAPHOT;JENAPLAN; JENATECH;JENAVAL;JENAVERT Bulb 12V 100W Halogen Rectangular Filament 380059-1660-000 Axiomat;Axioplan;ICM 405;IM 35 Inverted Microscope;PHOTOMIKROSKOP III;Standard WL Bulb 12V 100W Halogen Square Filament Axioline 380079-9540-000 Axio Examiner.A1;Axio Examiner.D1;Axio Examiner.Z1;Axio Imager.A1;Axio Imager.A1m;Axio Imager.A2;Axio Imager.A2m;Axio Imager.D1; Axio Imager.D1 for epi-fluorescence with ApoTome equipment;Axio Imager.D1m;Axio Imager.D2;Axio Imager.D2m;Axio Imager.M1;Axio Imager.M1 for KS ELISPOT;Axio Imager.M1m;Axio Imager.M2;Axio Imager.M2m;Axio Imager.Z1;Axio Imager.Z1 + ApoTome;Axio Imager.Z1m;Axio Imager.Z2;Axio Imager.Z2m;Axio Observer.A1;Axio Observer.A1 Entry;Axio Observer.A1m;Axio Observer.D1;Axio Observer.D1 + ApoTome;Axio Observer.D1 Entry;Axio Observer.D1 Mid Range ;Axio Scope.A1;Axio Observer.D1 TIRF 3;Axio Observer.D1m; Axio Observer.Z1;Axio Observer.Z1 Cell Observer;Axio Observer.Z1 Cell Observer SD;Axio Observer.Z1 High End;Axio Observer.Z1 Mid Range;Axio Observer.Z1 TIRF 3;Axio Observer.Z1m;Axio Observer.Z1m ACR;Axio Scope.A1 Pol;Axio Scope.A1 Vario;Axiolab;Axioplan 2 Img;Axioplan 2 Imaging E; Axioskop 2 MAT;Axioplan 2 Imaging for epi-fluorescence with "ApoTome" equipment; Axioplan 2 Imaging MAT;Axioskop 2 FS MOT;Axioskop 2 FS Plus;Axioskop 2 MAT mot;Axioskop 2 MOT Plus;Axioskop 2 Plus; Axiovert 135;Axioskop 40 A Pol;Axiotech vario;Axiovert 200;Axiovert 200 M;Axiovert 200 for epi-fluorescence with ApoTome equipment;Axiovert 200 M for epi-fluorescence with ApoTome equipment;Axiovert 200 M MAT;Axiovert 200 MAT;Axiovert 25 CA;Axiovert 40 MAT;Axiovert 40 MAT (W0,8);PALM CombiSystem Rel. 4.2;PALM MicroBeam Rel.4.2;PALM MicroTweezers Rel.4.2 Bulb 12V 10W Halogen Frosted - DV4-C Trans 000000-0407-307(G4, Halostar OSRAM 64415F) Stemi 2000;Stemi 2000 C;;Stemi 2000 CS;Stemi DR 1040;Stemi DR 1063;Stemi DR 1663;Stemi DV4 Bulb 12V 20W Halogen Reflector - DV4-C Epi (GU4, Decostar OSRAM 44890 WFL) Stemi DR 1040;Stemi DR 1063;Stemi DR 1663;Stemi DV4;Stereomikroskop DV4 (<1992) Bulb 12V 30W Halogen 380120-7040-000 PHOTOMIKROSKOP I;PHOTOMIKROSKOP II;PHOTOMIKROSKOP III;Standard 14;Standard 16;Standard 18;Standard WL;Universal research microscope Bulb 12V 35W Halogen - "Axiovert" 40/200 and "Axio Observer" 000000-0234-793 Axio Observer.A1;Axio Observer.A1m;Axio Observer.D1;Axio Observer.Z1;Axiovert 200;Axiovert 200 M;Axiovert 200 M MAT;Axiovert 200 MAT;Axiovert 25 CA;Axiovert 40 C;Axiovert 40 CFL;Axiovert 40 MAT;Axiovert 40 MAT (W0,8) Bulb 12V 35W Halogen Reflector GU5.3 000000-0425-360 Axioskop 2 FS MOT;Axioskop 2 FS Plus;Axioskop 2 MAT;Axioskop 2 MAT mot;Axioskop 2 MOT Plus;Axioskop 2 Plus;Axioskop 40;Axioskop 40 A Pol;Axioskop 40 FL;Axioskop 40 Pol Bulb 12V 50W Halogen 380079-9550-000 Axioskop 50
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Checkpoint/RestartSystem Services Interface(SSI)Modulesfor LAM/MPIAPI Version1.0.0/SSI Version1.0.0Sriram SankaranJeffrey M.SquyresBrian BarrettAndrew Lumsdaine/Open Systems LaboratoryPervasive Technologies LabsIndiana UniversityCS TR578August4,2003Contents1Overview51.1General Scheme (5)1.2Terminology (5)1.2.1The cr SSI Type (5)1.2.2Action Points (6)1.3Restrictions and Limitations (6)1.4The crlam SSI Type (7)1.5The crmpi SSI Type (8)2Services Provided by the cr SSI102.1Header Files (10)2.2Module Selection Mechanism (10)2.3Types (10)2.3.1lam ssi crmpi base handler state t (10)2.4Global Variables (11)2.4.1int lam ssi cr did (11)2.4.2int lam ssi cr verbose (11)2.5Global Variables for crmpi (11)2.5.1lam ssi crmpi base handler state (12)2.6Utility Functions for crlam (12)2.6.1lam ssi crlam base checkpoint() (12)2.6.2lam ssi crlam base continue() (12)2.6.3lam ssi crlam base restart() (12)2.6.4lam ssi crlam base create restart argv() (13)2.6.5lam ssi crlam base do exec() (13)2.7Utility Functions for crmpi (13)2.7.1lam ssi crmpi base checkpoint() (13)2.7.2lam ssi crmpi base continue() (14)2.7.3lam ssi crmpi base restart() (14)3cr SSI Module API143.1crlam SSI Module API (14)3.1.1Data Item:lscrl meta info (16)3.1.2Function Call:lscrl query (16)3.1.3Function Call:lscrla checkpoint (16)3.1.4Function Call:lscrla continue (17)3.1.5Function Call:lscrla disable checkpoint (17)3.1.6Function Call:lscrla enable checkpoint (17)3.1.7Function Call:lscrla finalize (18)3.1.8Function Call:lscrla init (18)3.1.9Function Call:lscrla restart (19)3.2crmpi SSI Module API (19)3.2.1Data Item:lscrm meta info (20)3.2.2Function Call:lscrm query (20)3.2.3Function Call:lscrma init (21)3.2.4Function Call:lscrma finalize (21)3.2.5Function Call:lscrma app suspend (21)4To Be Determined22 5Acknowledgements22 References22List of Figures1mpirun uses its crlam module to notify the crmpi module in each of the MPI processes to effect checkpoint/restart functionality (6)2Overview of the crmpi module management role (7)3lam ssi crlam100t:The crlam basic type for exporting the module meta informa-tion and initial query function pointer (15)4lam ssi crlam actions100t:The crlam type for exporting API function pointers.15 5struct lam ssi crmpi100:The crmpi basic type for exporting the module meta information and function pointers (19)6struct lam ssi crmpi actions100:The crmpi type for exporting API function pointers (20)1OverviewBefore reading this document,readers are strongly encouraged to read the general LAM/MPI System Ser-vices Interface(SSI)overview([1]).This document uses the terminology and structure defined in that document.The cr SSI type is used to provide checkpoint-restart support to MPI-1jobs.1Its primary responsibility is to ensure that all the processes in an MPI job arrive at a consistent global state before their process images are saved to stable storage by interfacing to a back-end checkpointing system.1.1General SchemeLAM’s cr framework is modeled on involuntary coordinated checkpoint/restart functionality.cr modules provide the necessary coordination,bookkeeping,and interface to back-end checkpoint systems.mpirun is initial entry point to checkpoint and restart MPI applications.A checkpoint is initiated by the asynchronous delivery of a checkpoint request to mpirun.2mpirun propagates this request out to all MPI processes and then allows itself to be checkpointed.The MPI processes are interrupted and may coordinate amongst themselves to prepare for checkpoint(e.g.,by draining all in-flight messages).When ready,the MPI processes allow themselves to be checkpointed.After a successful checkpoint,both mpirun and the MPI processes continue as if nothing had happened.An MPI job can be restarted by restoring the mpirun process image that was saved at checkpoint time.3 The resumed mpirun process will exec()a new copy of itself with an application schema suitable for restarting the MPI application.The MPI processes will be restarted and may coordinate amongst each other to re-create network connections,etc.When the MPI layer has fully re-established itself,control will be returned to the MPI application as if nothing had happened.mpirun also resumes waiting for the MPI applications to terminate(i.e.,its normal function).1.2TerminologyThe following sections define terminology that is used throughout this document.1.2.1The cr SSI TypeThe cr SSI type is composed of two SSI subtypes:crmpi and crlam.Hence,a given cr component is actually comprised of two modules–one of each subtype.These two modules work together at run-time to effect the overall checkpoint/restart functionality.Specifically,the two modules will both have the same name and will therefore be considered together during the selection process.crmpi modules are used to invoke checkpoint/restart functionality in MPI processes(i.e.,processes that invoke MPI INIT and MPI FINALIZE).Coordination between running MPI processes at checkpoint and restart time is accomplished,in part,by mpirun.4mpirun uses crlam modules to perform this coordination and bookkeeping.See Figure1.These two SSI kinds have much common functionality,but are unique in tangible ways.Throughout the rest of the document,the two SSI types will be referred to collectively as the cr SSI when describing common features data structures,APIs,etc.,and individually as crlam or crmpi when functionality that is unique to that type is discussed.1MPI-2jobs–particularly dynamic jobs–are not yet supported.2Currently,the checkpoint/restart request delivery utilizes module-specific mechanisms.3Similar to the checkpoint request,this is through a cr module-specific mechanism.4Checkpointing and restarting non-MPI programs(and therefore lamexec)is not currently supported.Figure1:mpirun uses its crlam module to notify the crmpi module in each of the MPI processes to effect checkpoint/restart functionality.1.2.2Action PointsThree main action points are defined in the cr SSI model:•Checkpoint:this action is invoked when a checkpoint request is received.•Continue:this action is invoked immediately after a successful checkpoint.No processes will have migrated.•Restart:this action is invoked upon restart,and is effectively the same as continue,except that some processes may have migrated to new locations.1.3Restrictions and LimitationsEach back-end checkpointing system may impose restrictions on exactly what the MPI process may have checkpointed and restarted.Although other MPI SSI types(e.g.,rpi and coll)are responsible for ensuring that their resources can be reliably checkpointed and restarted,all non-MPI resources(e.g.,file descriptors, shared memory,etc.)are the responsibility of the MPI application.Such resources may or may not be automatically saved/restored by the back-end checkpoint system.cr module authors are strongly encouraged to clearly document exactly what system-level resources will automatically be saved and restored.MPI applications may only be checkpointed after all MPI processes have invoked MPI INIT.Once any MPI process in the overall application invokes MPI FINALIZE,the job is no longer checkpointable. Application authors are advised to invoke MPI INIT as close to the beginning of main()as possible,and invoke MPI BARRIER immediately before MPI FINALIZE in order to maximize the window of checkpoint availability.An MPI process is checkpointable when the following conditions are met:•The MPI process is operating at MPI THREAD SERIALIZED or higher.5•A valid pair of cr modules have been selected(crlam and crmpi).This may imply a specific MPI thread level.•The selected rpi module is cr-aware.5This condition may be relaxed in future versions of this API.See Section4on page22.•The available coll module(s)is(are)cr-aware.“cr-aware”means that rpi and coll modules are able to coordinate with the crmpi module in order to prepare for,continue after,and restart after a checkpoint.Hence,the crmpi module type is a manager of the other MPI SSI module types;when a checkpoint request arrives,the crmpi module simply invokes“prepare to checkpoint”methods on the rpi and coll modules(see Figure2).These modules then do whatever is required to prepare themselves for checkpointing.A similar pattern is used after a successful checkpoint and when restarting from a prior checkpoint.This preserves an abstraction barrier between the crmpi module and system resources used by the underlying network(s)used by the MPI process.3. MPI modulesprepare forcheckpointFigure2:The crmpi module receives an asynchronous checkpoint request.It notifies the other MPI modules to prepare themselves for checkpoint.The MPI modules,each of which may be using its own private network for MPI messages,is responsible for all aspects of checkpointing and restarting itself.The crmpi module,therefore,is not involved in the details of closing/re-opening network devices,etc.Since mpirun is used as the entry point for checkpoint requests,the use of the“-nw”(no wait)switch is not supported.Specifically,if an MPI application is launched with“-nw”,it cannot be checkpointed.Also note that the LAM universe is not checkpointed or restarted.The cr SSI type only saves and restarts mpirun and MPI processes.The LAM run-time environment is considered transient without permanent state that needs to be saved.It is an exercise outside the scope of this document to reliably kill and restart the LAM universe for the checkpointed MPI jobs to run in.This may involve some kind of interaction with a resource scheduler;for example,it is possible to checkpoint an MPI job on one set of nodes,kill the LAM universe that it was running in,start a new LAM universe on a different set of nodes,and restart the MPI application in the new universe.1.4The crlam SSI TypeSection3.1details the API for crlam modules.It is relatively small and assumes asynchronous handling created by the crlam initialization function.The following is a typical chronology of events in mpirun during a checkpointed MPI application(items marked with(API)represent events involved with crlam API function calls):1.The user invokes mpirun C mpi application.2.mpirun launches mpi application across the LAM universe.3.mpirun is told which crlam module to use.6This indicates that all MPI processes have invokedMPI INIT.4.mpirun opens,selects,and initializes the specified crlam module.(API)5.mpirun indicates that it is able to checkpoint the MPI application.(API)6.mpirun goes into a blocking loop waiting for any MPI process to die.7.A checkpoint request arrives.8.Appropriate handlers must be active in mpirun(the exact mechanisms are crlam-module specific;signal handlers and separate threads that were previously created by the crlam module initialization function are typical approaches)that can receive asynchronous checkpoint requests.Note that these requests will likely interrupt mpirun in a blocking LAM library call.Since the LAM library is not currently thread-safe,some kinds of actions must be performed either outside of the LAM library or in a new[child]process that can freely utilize the LAM library.The following must occur at each action point:•Checkpoint:–Propagate the checkpoint request to the MPI processes.(API)–Allow mpirun to be checkpointed.•Continue:–No additional processing is required.(API)•Restart:–Re-exec mpirun with an application schema suitable for restarting the entire MPI applica-tion.Re-execing mpirun avoids the problem of breaking out of the blocking LAM librarycall by effectively re-initializing mpirun with a“new”parallel application.(API)9.Resume the blocking loop waiting for MPI processes to terminate.10.When one MPI process invokes MPI FINALIZE,mpirun indicates that it is no longer able to check-point the MPI application.(API)11.mpirun completes the loop,exiting after all MPI processes have invoked MPI FINALIZE.(API) 1.5The crmpi SSI TypeLAM’s checkpoint/restart model is built upon involuntary checkpoints;checkpoint requests should be able to be received and handled at any time.Similar to crlam,the crmpi SSI type allows for each module to define its own mechanisms for asynchronous interruptions,although signals and separate threads are commonly used.As discussed in Section1.3,the crmpi SSI type is only responsibly for the high-level coordination required in MPI processes for receiving checkpoint requests,coordinating the checkpoint,continue,and restart action points,and interfacing to the back-end checkpointing system.crmpi modules are not respon-sible for closing/re-establishing network connections,draining“inflight”MPI messages,replaying mes-sage streams,or any other prepare-to-checkpoint/restart-from-checkpoint actions.crmpi modules invoke 6The MPI processes collectively decide which crmpi module to use,and then send the name back to mpirun.methods on other MPI modules for“prepare to checkpoint,”“continue after checkpoint,”and“restart after checkpoint.”Section3.2details the API for crmpi modules.It is even smaller than the crlam API and assumes asynchronous handling created by the crmpi initialization function.The following is a typical chronology of events in an MPI process that is checkpointed(items marked with(API)represent events involved with crlam API function calls):1.The MPI process invokes MPI INIT.2.A set of SSI modules are opened,selected,and initialized for the process,including a crmpi module.(API)3.The name of the selected crmpi module is sent back to mpirun(so that it can select the correspondingcrlam module).4.MPI INIT returns and the MPI process progresses.5.A checkpoint request arrives.6.Appropriate handlers must be active in the MPI process(the exact mechanisms are crmpi-modulespecific;signal handlers and separate threads that were previously created by the crmpi module ini-tialization function are typical approaches)that can receive asynchronous checkpoint requests.When the checkpoint request arrives,the MPI process may or may not be in an MPI function call.•If the MPI process is not in an MPI function call,the crmpi module can continue with thecheckpoint procedure.•If the MPI process is in an MPI function call,it must either wait for the function call tofinish orinterrupt it7(deadlocks are possible,for example,if the MPI process is blocking while receivingan MPI message that was not sent before the checkpoint).7.The crmpi module gains control of and locks the MPI library8to prevent the MPI process from[re-]entering the MPI library during the checkpoint/continue/restart action points).The following must occur at each action point:•Checkpoint:–Coordinate with the other active MPI modules to prepare them for checkpoint.–Allow the MPI process to be checkpointed.•Continue:–Coordinate with the other active MPI modules to continue after the successful checkpoint.•Restart:–Coordinate with the other active MPI modules to restart after a prior successful checkpoint.8.Unlock the MPI library and return control to the main MPI process.9.The MPI process invokes MPI FINALIZE.The crmpi module isfinalized and closed.(API)7The interrupt mechanism is not yet standardized.See Section4on page22.8The locking mechanism is standardized but not yet well abstracted to the cr type.See Section4on page22.2Services Provided by the cr SSISeveral services are provided by the cr SSI that are available to all cr modules.2.1Header FilesThe following headerfiles must be included(in order)in all module sourcefiles that want to use any of the common cr SSI services described in this document:§¤#include<lam−ssi.h>#include<lam−ssi−cr.h>¦¥Both of thesefiles are included in the same location:share/ssi/include.If using GNU Automake and the top lam srcdir macro as recommended in[1],the following can be added to the AM CPPFLAGS macro(remember that LAM BUILDING must be defined to be1):§¤AM CPPFLAGS=\−I$(top lam builddir)/share/include\−I$(top lam srcdir)/share/include\−I$(top lam srcdir)/share/ssi/include¦¥All threeflags are necessary to obtain the necessary headerfiles(note that the build directory is explicitly included in order to support VPATH builds properly,even though it will be redundant in non-VPATH builds).2.2Module Selection MechanismThe selection of a cr SSI module persists through the life of an MPI job.It is selected during MPI INIT and remains selected until MPI FINALIZE.The MPI processes in the job collectively decide on which crmpi module to select and then pass its name to mpirun.mpirun then selects the corresponding crlam module (which may be none).Hence,mpirun and all of the MPI processes that it launched all share a common cr module selection.2.3TypesSome types are used in different API calls and throughout the checkpoint/restart-aware RPIs.2.3.1lam ssi crmpi base handler state tThis type is an enumerated value used to describe the state of the crmpi handler thread in an MPI process:§¤typedef enum{LAM SSI CRMPI BASE HANDLER STATE IDLE,LAM SSI CRMPI BASE HANDLER STATE WAITING,LAM SSI CRMPI BASE HANDLER STATE RUNNING,LAM SSI CRMPI BASE STATE MAX}lam ssi crmpi base handler state t;¦¥The three possible values are:•HANDLER STATE IDLE:The handler thread is inactive(and likely either non-existent or blocking, depending on the crmpi module’s implementation).•HANDLER STATE WAITING:The handler thread is waiting for the main application thread to either leave the MPI library,or yield control.•HANDLER STATE RUNNING:The handler thread is actively working on a checkpoint,continue,or restart operation.2.4Global VariablesSeveral global variables are available to all cr modules.These variables are extern’ed in<lam-ssi-cr.h>.2.4.1int lam ssi cr didThis int is set by the cr SSI open function,and will therefore be usable from every cr API function.It is the debug stream ID specific to the cr SSI modules(see[1]for a description of LAM/MPI debug streams).If cr modules do not create their own debug streams,they should use lam ssi cr did.Debug streams should be used in conjunction with lam ssi cr verbose.Note,however,than debug streams should be used with care(and/or“compiled out”with preprocessor directives when not in use) because even if their output is not displayed,they still invoke a function call and may generate overhead at run-time.2.4.2int lam ssi cr verboseThe lam ssi cr verbose variable will be set by the cr SSI initialization function,and will therefore be usable by every cr API function.lam ssi cr verbose is used to indicate how many“status”messages should be displayed.This does not pertain to error messages that the module may need to print–only messages that are superfluous “what’s going on”kind of messages.The value of this variable should be interpreted as following:•Less than zero:do not output any status messages.•Zero:print minimal amounts of status messages.This typically corresponds to the“-v”flag on various LAM commands.•Greater than zero:print status messages–potentially more than if the value were zero;exact meaning is left up to the module.A value of1000typically corresponds to the“-d”flag on various LAM commands.2.5Global Variables for crmpiThe global variables listed below are available to crmpi modules.These variables are extern’ed in<lam-ssi-cr.h>.2.5.1lam ssi crmpi base handler stateThis variable is available in crmpi only.It is of type lam ssi crmpi base handler state t,de-scribed in Section2.3.1.This variable must be maintained by the crmpi handler thread to track its current status in order notify other SSI modules that they are being interrupted.§¤volatile lam ssi crmpi base handler state t lam ssi crmpi base handler state;¦¥It may be necessary for the application thread(s)to perform some action based on the execution state of the thread-based checkpoint/restart handler.This variable is marked volatile so that it will not be cached by the application thread(s)if the crmpi handler thread changes its value.2.6Utility Functions for crlamThe general utility functions listed below are provided to all modules by the crlam SSI.2.6.1lam ssi crlam base checkpoint()§¤int lam ssi crlam base checkpoint(struct gps∗world,int nprocs);¦¥This function must be invoked from the thread-based checkpoint/restart handler when mpirun receivesa checkpoint request.After preparing mpirun9to be checkpointed,it will invoke the selected crlam module’s lscrla checkpoint()API function(see Section3.1.3).The world array must containa struct gps element for each MPI process that needs to receive the checkpoint request.nprocs is the length of the world array.It returns zero on success,LAMERROR otherwise.2.6.2lam ssi crlam base continue()§¤int lam ssi crlam base continue(void);¦¥This function must be invoked from the thread-based checkpoint/restart handler when mpirun contin-ues after a successful checkpoint.After preparing mpirun to continue after the checkpoint,it will invoke the selected crlam module’s lscrla continue()API function(see Section3.1.4).It returns zero on success,LAMERROR otherwise.2.6.3lam ssi crlam base restart()§¤int lam ssi crlam base restart(char∗executable,char∗app schema);¦¥This function must be invoked from the signal-based checkpoint/restart handler when mpirun restarts. After preparing mpirun to be checkpointed,it will invoke the selected crlam module’s lscrla restart() API function(see Section3.1.4).executable should be a string path to mpirun to re-launch,and app schema should be the string path to the application schema that can be used to re-launch the MPI application.It returns zero on success,LAMERROR otherwise.9This function will likely also be used in lamexec if checkpointing of non-MPI programs is ever supported.2.6.4lam ssi crlam base create restart argv()§¤int lam ssi crlam base create restart argv(char∗∗argv,OPT∗ad);¦¥Based on arguments argv and ad,this function creates an internal list of arguments that will be given to mpirun when it is restarted.This function is typically invoked by the crlam’s lscra init()API function with the argv and ad parameters that it receives as arguments(see Section3.1.8).The internal set of arguments that is created is not returned to the caller;it is used by lam ssi crlam-base do exec().Note that OPT*is an internal LAM type for holding command line parameters.Its use is documented in the all opt(3)manual page.It returns zero on success,LAMERROR otherwise.2.6.5lam ssi crlam base do exec()§¤int lam ssi crlam base do exec(char∗executable,char∗app schema);¦¥The use of this function is optional;if it is not used,cr modules need to provide equivalent functionality.This function can be either invoked by the crlam module’s lscr restart()API function call(see Section3.1.9),or is used as the lscr restart()API function itself.The utility function lam crlam-base create restart argv()must have been invoked before this function is called.This utility function launches a new mpirun process via execve(2)with the command line argu-ments that were previously setup,and an application schema that can re-launch the MPI job.Since this function execve()’s a new process,it never returns.It returns zero on success,LAMERROR otherwise.2.7Utility Functions for crmpiThe general utility functions listed below are provided to all modules by the crmpi SSI.2.7.1lam ssi crmpi base checkpoint()§¤int lam ssi crmpi base checkpoint(void);¦¥This function should be invoked from the MPI thread-based checkpoint/restart handler when a check-point request arrives.crmpi base checkpoint()is used to prepare the other SSI modules in use by the MPI process to be checkpointed.This function invokes the appropriate action function exported by each SSI module that needs pre-checkpoint handling.Currently,this means:•The function lsra checkpoint()rpi API function will be invoked on all active rpi SSI mod-ules.•The function lsca checkpoint()coll API function will be invoked on each existing MPI com-municator.crmpi base checkpoint()will return0if all the invoked functions return0,or LAMERROR if any of them returned LAMERROR.2.7.2lam ssi crmpi base continue()§¤int lam ssi crmpi base continue(void);¦¥This function should be invoked from the MPI thread-based checkpoint/restart handler after a checkpoint completes successfully.crmpi base continue()is used to trigger post-checkpoint actions in other SSI modules in use by the MPI process after a checkpoint.This function invokes the appropriate action function exported by each SSI module that needs pre-checkpoint handling.Currently,this means:•The lsra continue()rpi API function will be invoked on all active rpi SSI modules.•The lsca continue()coll API function will be invoked on each existing MPI communicator.crmpi base continue()will return0if all the invoked functions return0,or LAMERROR if any of them returned LAMERROR.2.7.3lam ssi crmpi base restart()§¤int lam ssi crmpi base restart(void);¦¥This function should be invoked from the thread-based checkpoint/restart handler when an MPI process is restarted.crmpi base restart()is used to trigger pre-restart actions in other SSI modules in use by the MPI process when it is restarted.This function invokes the appropriate action function exported by each SSI module that needs pre-restart handling.Currently,this means:•The lsra restart()rpi API function will be invoked on all active rpi SSI modules.•The lsca restart()coll API function will be invoked on each existing MPI communicator.crmpi base restart()will return0if all the invoked functions return0,or LAMERROR if any of them returned LAMERROR.3cr SSI Module API3.1crlam SSI Module APIThis is version1.0.0of the crlam SSI module API.Each crlam SSI module must export a lam ssi crlam100t named lam ssi crlam<name>-module.This type is defined in Figure3.A second struct is used to hold the majority of function pointers andflags for the module.It is only used if the module is selected,and is shown in Figure4.The majority of the elements in Figures3,and4are function pointer types;each is discussed in detail below.When describing the function prototypes,the parameters are marked in one of three ways:•IN:The parameter is read–but not modified–by the function.•OUT:The parameter,or the element pointed to by the parameter may be modified by the function.•IN/OUT:The parameter,or the element pointed to by the parameter is read by,and may be modified by the function.§¤typedef struct lam ssi crlam100{lam ssi100t lscrl meta info;/∗cr lam API function pointers∗/lam ssi crlam query fn t lscrl query;}lam ssi crlam100t;¦¥Figure3:lam ssi crlam100t:The crlam basic type for exporting the module meta information and initial query function pointer.§¤typedef struct lam ssi crlam actions100{/∗cr lam action API functions pointers∗/lam ssi crlam checkpoint fn t lscrla checkpoint;lam ssi crlam continue fn t lscrla continue;lam ssi crlam disable checkpoint fn t lscrla disable checkpoint;lam ssi crlam enable checkpoint fn t lscrla enable checkpoint;lam ssi crlamfinalize fn t lscrlafinalize;lam ssi crlam init fn t lscrla init;lam ssi crlam restart fn t lscrla restart;}lam ssi crlam actions100t;¦¥Figure4:lam ssi crlam actions100t:The crlam type for exporting API function pointers.。
