ASA5500 ACL配置详解
cisco asa 5505命令一览

ciscoasa# ?aaa-server Specify a AAA server 指定一个AAA服务器:aaa配置activation-key Modify activation-key 修改激活码asdm Disconnect a specific ASDM session 自适应安全设备管理器(ASDM)。
blocks Set block diagnostic parameters 设置块诊断参数capture Capture inbound and outbound packets on one or 捕获入站和出站的包more interfacescd Change current directory 改变当前的目录clear Reset functions 复位功能client-update Execute client updates on all or specific 客户端更新tunnel-groupsclock Manage the system clock 管理系统时钟configure Configure using various methods 全局配置模式使用copy Copy from one file to another 复制拷贝文件cpu general CPU stats collection tools CPU状态收集工具crashinfo Crash information 死机信息crypto Execute crypto Commands 执行加密命令debug Debugging functions (see also 'undebug') 调试功能配置delete Delete a file 删除一个文件dir List files on a filesystem 列出文件disable Exit from privileged mode 退出特权模式dynamic-access-policy-config Activates the DAP selection configuration file. 激活DAP选择配置文件。
CiscoASA5505ipsecl2l配置

CiscoASA5505ipsecl2l配置CiscoASA5505 ipsec l2l配置Cisco ASA5505配置ASA(config)# crypto isakmp policy 10 #建立IKE策略,优先级为10ASA(config-isakmp-policy)# encryption 3des #使用3des加密ASA(config-isakmp-policy)# authentication pre-share #使用预共享的密码进行身份认证ASA(config-isakmp-policy)# hash md5 #指定hash算法为md5(其他sha、rsa)ASA(config-isakmp-policy)# lifetime 28800 #指定SA有效期时间。
默认86400秒,两端要一致ASA(config-isakmp-policy)# group 1 #指定密钥位数,1表示768位,2表示1024为,2更安全,更耗cpu资源ASA(config-isakmp-policy)# exitASA(config)# crypto isakmp key bj2legend add 210.82.111.121 #预共享密码,远程网关ipASA(config)# crypto ipsec transform-set bjicpark esp-3des esp-md5-hmac#定义一个IPSEC交换集,两端要一样ASA(config)# access-list bjparkvpn permit ip 172.18.5.0 255.255.255.128192.168.3.0 255.255.255.0 #定义加密通道ASA(config)# access-list bjparkvpn permit ip 172.18.5.0 255.255.255.128192.168.2.0 255.255.255.0ASA(config)# crypto map bjparkmap 20 match addressbjparkvpn #创建加密图ASA(config)# crypto map bjparkmap 20 set peer 210.82.111.121 #目标地址ASA(config)# crypto map bjparkmap 20 set transform-set bjpark #指定加密图使用的IPSEC交换集ASA(config)# crypto map bjparkmap interface outside #应用加密图到接口ASA(config)# crypto isakmp identity address #网关ID,默认IP地址,两端要一致ASA(config)# crypto isakmp enable outside #接口上开启ike ASA(config)# crypto isakmp nat-traversal 20 #支持nat穿越方正方御FG3000E防火墙配置:IKE协商模式:主动模式IKE算法:自动协商认证方式:预共享本地网关ID:无远程网关ID:无IPSec算法:自动协商高级选项:生存周期:ISAKMP SA:8小时0分0秒IPSec SA:24小时0分0秒支持DPD(Dead Peer Detection):选择打勾DPD探测频率:30秒DPD探测超时:10秒DPD超时操作:重新启动连接支持IP载荷压缩:不选择支持完美向前加密(PFS):不选择支持密钥重建(Rekeying):选择打勾重试次数:0相关知识点:对称加密或私有密钥加密:加密解密使用相同的私钥DES--数据加密标准 data encryption standard3DES--3倍数据加密标准 triple data encryption standardAES--高级加密标准 advanced encryption standard一些技术提供验证:MAC梷消息验证码 message authentication codeHMAC梷散列消息验证码 hash-based message authentication codeMD5和SHA是提供验证的散列函数对称加密被用于大容量数据,因为非对称加密站用大量cpu资源非对称或公共密钥加密:RSA rivest-shamir-adelman用公钥加密,私钥解密。
Cisco ASA5505防火墙详细配置教程及实际配置案例

Cisco ASA5505防火墙详细配置教程及实际配置案例interface Vlan2nameif outside ----------------------------------------对端口命名外端口security-level 0 ----------------------------------------设置端口等级ip address X.X.X.X 255.255.255.224 --------------------调试外网地址!interface Vlan3nameif inside ----------------------------------------对端口命名内端口security-level 100 ----------------------------------------调试外网地址ip address 192.168.1.1 255.255.255.0 --------------------设置端口等级!interface Ethernet0/0switchport access vlan 2 ----------------------------------------设置端口VLAN与VLAN2绑定!interface Ethernet0/1switchport access vlan 3 ----------------------------------------设置端口VLAN与VLAN3绑定!interface Ethernet0/2shutdown!interface Ethernet0/3shutdown!interface Ethernet0/4shutdown!interface Ethernet0/5shutdown!interface Ethernet0/6shutdown!interface Ethernet0/7shutdown!passwd 2KFQnbNIdI.2KYOU encryptedftp mode passivedns domain-lookup insidedns server-group DefaultDNSname-server 211.99.129.210name-server 202.106.196.115access-list 102 extended permit icmp any any ------------------设置ACL列表(允许ICMP全部通过)access-list 102 extended permit ip anyany ------------------设置ACL列表(允许所有IP全部通过)pager lines 24mtu outside 1500mtu inside 1500icmp unreachable rate-limit 1 burst-size 1no asdm history enablearp timeout 14400global (outside) 1 interface ----------------------------------------设置NAT地址映射到外网口nat (inside) 1 0.0.0.0 0.0.0.0 0---------------------------------NAT地址池(所有地址)0无最大会话数限制access-group 102 in interface outside ------------------―――设置ACL列表绑定到外端口route outside 0.0.0.0 0.0.0.0 x.x.x.x 1 ------------------设置到外网的默认路由timeout xlate 3:00:00timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout uauth 0:05:00 absoluteno snmp-server locationno snmp-server contactsnmp-server enable traps snmp authentication linkup linkdown coldstart telnet 0.0.0.0 0.0.0.0 inside ----------------------------------------设置TELNET所有地址进入telnet timeout 5ssh 0.0.0.0 0.0.0.0 outside ----------------------------------------设置SSH所有地址进入ssh timeout 30ssh version 2console timeout 0!dhcpd address 192.168.1.100-192.168.1.199inside ------------------设置DHCP服务器地址池dhcpd dns 211.99.129.210 202.106.196.115 interfaceinside ------------------设置DNS服务器到内网端口dhcpd enableinside --------------------------------------------------------------设置DHCP应用到内网端口!前几天去客户那调试CISCO-ASA-5505设备,第一次摸,跟PIX一样,呵呵.没有技术含量,都是最基本的.其他业务配置暂时没配,会及时更新的.Cisco ASA5505配置cisco, config, telnet, 防火墙, Cisco1.配置防火墙名ciscoasa> enableciscoasa# configure terminalciscoasa(config)# hostname asa55052.配置telnetasa5505(config)#telnet 192.168.1.0 255.255.255.0 inside ↑//允许内部接口192.168.1.0网段telnet防火墙3.配置密码asa5505(config)# password cisco ------------------远程密码asa5505(config)# enable password cisco ------------------特权模式密码4.配置IPasa5505(config)# interface vlan 2 ------------------进入vlan2asa5505(config-if)# ip address 218.16.37.222 255.255.255.192 ------------------vlan2配置IPasa5505(config)#show ip address vlan2 ------------------验证配置5.端口加入vlanasa5505(config)# interface e0/3 ------------------进入接口e0/3asa5505(config-if)# switchport access vlan 3 ------------------接口e0/3加入vlan3asa5505(config)# interface vlan 3 ------------------进入vlan3asa5505(config-if)# ip address 10.10.10.36 255.255.255.224 ------------------vlan3配置IPasa5505(config-if)# nameif dmz ------------------vlan3名asa5505(config-if)# no shutdown ------------------开启asa5505(config-if)# show switch vlan ------------------验证配置6.最大传输单元MTUasa5505(config)#mtu inside 1500 ------------------inside最大传输单元1500字节asa5505(config)#mtu outside 1500 ------------------outside最大传输单元1500字节asa5505(config)#mtu dmz 1500 ------------------dmz最大传输单元1500字节7.配置arp表的超时时间asa5505(config)#arp timeout 14400 ------------------arp表的超时时间14400秒8.FTP模式asa5505(config)#ftp mode passive ------------------FTP被动模式9.配置域名asa5505(config)#domain-name 10.启动日志asa5505(config)#logging enable ------------------启动日志asa5505(config)#logging asdm informational ------------------启动asdm报告日志asa5505(config)#Show logging ------------------验证配置11.启用http服务asa5505(config)#http server enable ------------------启动HTTP server,便于ASDM连接。
Waveslv_ASA5500原创笔记

绝对原创_____作者:waveslvASA5500 7.2版本之应用笔记1.默认http配置192.168.1.1(management口) 可以用SDM访问进行图形化配置interface management 0/0ip address 192.168.1.1 255.255.255.0nameif managementsecurity-level 100no shutdownasdm logging informational 100asdm history enablehttp server enablehttp 192.168.1.0 255.255.255.0 managementdhcpd address 192.168.1.2-192.168.1.254 managementdhcpd lease 3600dhcpd ping_timeout 750dhcpd enable managementPIX515/Einterface ethernet 1ip address 192.168.1.1 255.255.255.0nameif managementsecurity-level 100no shutdownasdm logging informational 100asdm history enablehttp server enablehttp 192.168.1.0 255.255.255.0 managementdhcpd address 192.168.1.2-192.168.1.254 managementdhcpd lease 3600dhcpd ping_timeout 750dhcpd enable managementno nat (inside) 1 清除NATwrite erase 清除startconfigclear config all 清除所有的配置2.multiple context不支持的特性:VPN 和dynamic routing protocols和mutlicast.在从single context转到mutliple context,startconfig是不被保存的,如果需要你应该备份它会生成两个新的文件:startconfig和admin.cfg,原来的running-config更名为old_running.cfghostname(config)# mode multiple如果需要从多文本模式变成单文本模式,你可能想把先头的运行文件恢复回来,因为在多文本模式下很多东西是不支持单文本的,执行以下命令:hostname(config)# copy flash:old_running.cfg startup-confighostname(config)# mode single3. 5505自适应防火墙配置PORT和VLAN.5505是不支持subinterface的E6/7端口是POE端口,支持IP Phones and wires access point4.同样安全级别的接口之间默认是不允许相互传输数据的,可以使用如下命令来打开这个开关:hostname(config)# same-security-trafficpermit inter-interface5.5500系列防火墙默认的登陆密码是cisco,你可以使用password xxxx来修改这个密码配置特权密码:enable password xxxxx6.防火墙路由配置:静态路由RIP OSPF在同一[接口]支持负载均衡三条:The security appliance supports up to three equal cost routes on the same interface for loadbalancing.hostname(config)# route if_name dest_ip mask gateway_ip [distance] 静态路由hostname(config)# route outside 0 0 192.168.1 1 默认路由静态路由追踪:即当主线路断开的情况下(即下一跳不可用的时候),移去主静态路由,把备份路由启起来进行热备,如果不配置,主静态路由会一直存在于路由表之中hostname(config)# sla monitor sla_id 定义一个sla IDhostname(config-sla-monitor)# type echo protocol ipIcmpEcho target_ip interface if_name 定义追踪下一跳hostname(config)# sla monitor schedule sla_id life forever start-time now 定义一个排程,决定什么时候开始追踪hostname(config)# track track_id rtr sla_id reachability 定义一个追踪ID hostname(config)# route if_name dest_ip mask gateway_ip [admin_distance] track track_id 定义追踪目的网络7.ospf 和RIP不能同时运行在ASA防火墙,也不支持RIP和OSPF的路由重新分配8.OSPF在接口下的配置:hostname(config)# router ospf 2hostname(config-router)# network 2.0.0.0 255.0.0.0 area 0hostname(config-router)# interface insidehostname(config-interface)# ospf cost 20hostname(config-interface)# ospf retransmit-interval 15hostname(config-interface)# ospf transmit-delay 10hostname(config-interface)# ospf priority 20hostname(config-interface)# ospf hello-interval 10hostname(config-interface)# ospf dead-interval 40hostname(config-interface)# ospf authentication-key ciscohostname(config-interface)# ospf message-digest-key 1 md5 ciscohostname(config-interface)# ospf authentication message-digestOSPF配置:接口参数' area参数' 路由汇总' 路由重新分布' 配置默认路由' 邻居UP或是DOWN通告(需要在邻居上配置)9. Defining Route MapsThe following example shows how to redistribute routes with a hop count equal to 1 into OSPF. The security appliance redistributes these routes as external LSAs with a metric of 5, metric type of Type 1, and a tag equal to 1.hostname(config)# route-map 1-to-2 permithostname(config-route-map)# match metric 1hostname(config-route-map)# set metric 5hostname(config-route-map)# set metric-type type-1DHCP配置:hostname(config)# dhcpd address 10.0.1.101-10.0.1.110 insidehostname(config)# dhcpd dns 209.165.201.2 209.165.202.129hostname(config)# dhcpd wins 209.165.201.5hostname(config)# dhcpd lease 3000hostname(config)# dhcpd domain hostname(config)# dhcpd enable inside不支持的参数配置:子网掩码DHCP中继配置:hostname(config)# dhcprelay server 201.168.200.4hostname(config)# dhcprelay enable insidehostname(config)# dhcprelay setroute insideVPN一般分为两种类型:lan to lan; remote access前者安全防火墙或是安全网关也有两种模式:initiator and responder 即发起者和响应者main mode or aggressive mode 主模式和挑战模式◆1'配置IKE:crypto isakmp policy 2 encryption des/3descrypto isakmp policy 2 authtication pre-sharecrypto isakmp policy 2 hash md5 /sha是默认的crypto isakmp policy 2 lifetime 86400crypto isakmp policy 2 group 2 默认是2 即1024bit2'在outside接口应用IKEcrypto isakmp enable outside3'关掉挑战模式crypto isakmp am-disable no crypto isakmp am-disable关掉了挑战模式,阻止了用cisco VPN client用预共享密钥的方式建立vpn连接,但可以用(基于证书的)ASA或是RSA的方式建立挑战模式默认是打开的,而且比main mode速度快,但他不提供认证保护4' 对端认证方式: address hostname key-id auto 四种默认为hostnamecrypto isakmp identity auto◆ Configuring IPSec (安全关联和协商)Understanding IPSec Tunnels 隧道Understanding Transform Sets 传输设置Defining Crypto Maps 定义加密图Applying Crypto Maps to Interfaces 把加密图应用到接口上Using Interface Access Lists 利用访问控制列表保护加密数据//不被保护的数据则使用deny 拒绝Changing IPSec SA Lifetimes 改变安全关联生命时间每一个静态MAP都必须指定一个ACL和PEER◆ Creating a Basic IPSec Configurationaccess-list 101 permit ip 10.0.0.0 255.255.255.0 10.1.1.0 255.255.255.0crypto ipsec transform-set myset1 esp-des esp-sha-hmaccrypto ipsec transform-set myset2 esp-3des esp-sha-hmaccrypto map mymap 10 match address 101crypto map mymap 10 set peer 192.168.1.100crypto map mymap 10 set transform-set myset1 myset2crypto map mymap 10 set security-association lifetime seconds 2700crypto map mymap interface outside 应用到接口上//在以下所属的情况,你可能需要定义多个不同的map,比如有两个ACL:分别保护两组不同的子网Acl permit 10.10.1.0 255.255.255.0 10.10.2.0 255.255.255.0Acl permit 10.10.3.0 255.255.255.0 10.10.4.0 255.255.255.0这样你则需要定义不同的序列号,定义不同的优先级◆ Dynamic crypto maps 动态加密图不会主动去初始化PEER, 只能接受响应动态加密图应该具有最低的优先级,(有最高的highest sequence numbers//序列号) 只有当其他的加密图不匹配的时候才执行crypto dynamic-map dyn1 10 match address 101crypto dynamic-map dyn 10 set transform-set myset1 myset2crypto dynamic-map dyn1 10 set security-association lifetime seconds 2700crypto ipsec transform-set myset1 esp-des esp-sha-hmaccrypto ipsec transform-set myset2 esp-3des esp-sha-hmaccrypto map mymap 200 ipsec-isakmp dynamic dyn1 // 需要绑定到静态加密图◆查看IPSEC 清除IPSECshow running-configuration cryptoshow running-config crypto ipsecshow running-config crypto isakmpshow running-config crypto mapshow running-config crypto dynamic-mapshow all crypto mapclear configure crypto //清除所有的crypto配置clear configure crypto ca trustpointclear configure crypto dynamic-mapclear configure crypto mapclear configure crypto isakmpclear configure crypto isakmp policyclear crypto isakmp sa★配置L2TP over IPSEC (不够安全的访问) //ASA5500系列防火墙本身是不支持L2TP, 但支持L2TP OVER IPSEC模式: 服务器与客户端模式LNS 和LAC 模式如果防火墙配置了L2TP OVER IPSEC,你要想用访问它,必须关掉本机已经安装好的cisco vpn client的服务再重新启动电脑hostname(config)# crypto ipsec transform-set trans_name mode transport //必须把mode配置为transport,因为默认为tunnelhostname(config)# group-policy group_policy_name attributes //创建一个组策略hostname(config-group-policy)# vpn-tunnel-protocol l2tp-ipsec //对于此组使用l2tp-ipsechostname(config)# tunnel-group name general-attributes //创建一个通用属性组hostname(config)# tunnel-group name type ipsec-ra //定义类型hostname(config-tunnel-general)# group-policy group_policy_namehostname(config-tunnel-general)# authentication-server-group LOCALhostname(config-tunnel-general)# address-pool pool_name //客户端可分配到的IP地址hostname(config)# tunnel-group name ppp-attributes //chap ;mschap(对于你使用微软的拨号程序); paphostname(config-ppp)# authentication paphostname(config)# username t_wmith password eu5d93h mschap //用于local验证用户hostname(config)# l2tp tunnel hello secondshostname(config)# crypto isakmp enablehostname(config)# crypto isakmp nat-traversal 30★隧道类型:三种 The default tunnel-group type is ipsec-ra1 general tunnel2 ipsec tunnel3 web tunnelConfiguring IPSec Remote-Access Tunnel GroupsThe contents of the default LAN-to-LAN tunnel group are as follows: //默认L-2-L配置tunnel-group DefaultL2LGroup type ipsec-l2ltunnel-group DefaultL2LGroup general-attributesno accounting-server-groupdefault-group-policy DfltGrpPolicytunnel-group DefaultL2LGroup ipsec-attributesno pre-shared-keypeer-id-validate reqno chainno trust-pointisakmp keepalive threshold 10 retry 2创建用户.关联于VPN组策略hostname(config)# username anyuser attributeshostname(config-username)# vpn-group-policy FirstGrouphostname(config-username)# vpn-simultaneous-logins 4 //限制同一个用户可以同时登陆的数量实例一:ipsec remote accesshostname(config)# interface ethernet0 //接口基本配置hostname(config-if)# ip address 10.10.4.200 255.255.0.0hostname(config-if)# nameif outsidehostname(config)# no shutdownhostname(config)# isakmp policy 1 authentication pre-share //配置IKE:hostname(config)# isakmp policy 1 encryption 3deshostname(config)# isakmp policy 1 hash sha //防止验证信息被篡改的一种方式hostname(config)# isakmp policy 1 group 2hostname(config)# isakmp policy 1 lifetime 43200 //A time limit for how long the security appliance uses an encryption key before replacing it.hostname(config)# isakmp enable outside //在外网口启用IKE hostname(config)# ip local pool testpool192.168.0.10-192.168.0.15 //定义一个远程用户登陆所获取到的内部IPhostname(config)# username testuser password 12345678 //定义一个远程访问用户hostname(config)# crypto ipsec transform set FirstSet esp-3des esp-md5-hmac //设置一个名字为Firstset的交换集, 包括加密方法和认证方式.hostname(config)# tunnel-group testgroup type ipsec-ra //定义一个隧道组hostname(config)# tunnel-group testgroup general-attributes //继承通用属性hostname(config-general)# address-pool testpool//使用先头定义好的ip地址池hostname(config)# tunnel-group testgroup ipsec-attributes //配置testgroup的IPSEC属性hostname(config-ipsec)# pre-shared-key 44kkaol59636jnfx //使用预共享密钥方式认证hostname(config)# crypto dynamic-map dyn1 1 set transform-set FirstSet //定义一个动态加密图,使用先头定义好的加密集hostname(config)# crypto dynamic-map dyn1 1 set reverse-route//hostname(config)# crypto map mymap 1 ipsec-isakmp dynamic dyn1 //需要定义一个静态加密图,再把动态加密图绑定到静态上hostname(config)# crypto map mymap interface outside //把静态加密图应用到外网接口上hostname(config)# write memory //保存配置实例二:LAN—TO—LANhostname(config)# interface ethernet0hostname(config-if)# ip address 10.10.4.100 255.255.0.0hostname(config-if)# no shutdownhostname(config)# isakmp policy 1 authentication pre-sharehostname(config)# isakmp policy 1 encryption 3deshostname(config)# isakmp policy 1 hash shahostname(config)# isakmp policy 1 group 2hostname(config)# isakmp policy 1 lifetime 43200hostname(config)# isakmp enable outsidehostname(config)# crypto ipsec transform set FirstSet esp-3des esp-md5-hmachostname(config)# access-list l2l_list extended permit ip 192.168.0.0 255.255.0.0150.150.0.0 255.255.0.0hostname(config)# tunnel-group 10.10.4.108 type ipsec-l2l //隧道组类型为l2l hostname(config)# tunnel-group 10.10.4.108 ipsec-attributes //不用配置通用属性hostname(config-ipsec)# pre-shared-key 44kkaol59636jnfxhostname(config)# crypto map abcmap 1 match address l2l_list //加密需要加密的数据hostname(config)# crypto map abcmap 1 set peer 10.10.4.108 //对端IP hostname(config)# crypto map abcmap 1 set transform-set FirstSethostname(config)# crypto map abcmap interface outsidehostname(config)# write memory诠释IPSEC RA1.定义外网接口.毕竟远程vpn进来的数据都是从OUTSIDE口进来的,至少我们应该为它配置ip 地址,让peer找到它,而且需要在防火墙上明确定义他是outside2.配置IKE协商并在outside口开启ike功能.IKE是用于和对端进行连接前的协商的,他指导对方如何建立IKE SA(安全关联),当然协商的东东必须一样了,要不然我们怎么同步呢? 故在两端需要配置一样的IKE策略,具体详细配置见上页,最后我们定义好了总的在哪个outside口开启这个功能吧3.地址池.当远程客户端连接上来的时候你总得给他一个内部的IP地址吧,所以我们得定义一个IP 地址池了,以后在tunnel-group中要用到的4.添加用户当远程客户端连接上来的时候你总得认识他是谁吧,所以我们添加一个用户是可以理解的,至于你给他什么样的权限,这点好象不是很重要5.设置传输集这个用途是什么,我现在还是蒙的,cisco文档是这样说的,传输集集成了加密方式和验证方式,我在想,既然我们都协商好了用DES或是3DES(在IKE策略定义里),那这里还多此一举干嘛啊,而且文档还称两端必须一样的传输集,最多可以定义11个绑定到加密图6.定义隧道组Vpn技术说白了就是加密技术和隧道技术,所以我们配置的时候自然不要忘了配置隧道了,隧道也是一些参数的集合而已,系统都有默认的隧道组的,你可以不定义,用默认的,有三种:RA ;L2L; WEB,当然我们还是自己定义一个来用比较安逸些.在不同的场合用不同的类型.在具体配置的时候,分两个阶段:通用属性+IPSEC属性, 通用里我们就把前面定义的哪个ip地址池在这里用上了, ipsec 则定义预共享的密钥7. 既然是RA 远程访问,对端则是动态的IP地址,所以我们需要定义动态加密图,在LAN---TO---LAN中则定义为静态加密图,不过动态加密图还是需要绑定到静态上的,定义好动态加密图使用前面我们定义的交换集,当然前面如果你定义了多个交换集,你选择一个则可以了, 最后我们把动态加密图绑定到静态图上, 最后还要把他应用到OUTSIDE接口上,这点是非常重要的总结: 这里好象没有用到组策略呢,我想应该是用的系统默认的组策略吧,L2L 的我这里就不多讲了,一个鸟样,只是我们不用定义动态加密图了,当然也不会用到用户和IP 地址池这个鬼东西了,因为毕竟我们是网关对网关啊,当然隧道组类型我们则用TYPE: L2L 了.哦,有个关键的东西没有讲到,就是我们需要自己定义一个ACL,来明确告诉vpn 要保护谁到谁的数据,并且我们在IPSEC 里面要指定用这个ACL,而且现在我们网关对网关了,所以我们需要定义Peer防火墙的配置原理1.访问原则 (路由模式)Inside 可以自由访问outside (我们可能会想为什么包能回来,因为防火墙会检查是否这是已经建立起来的session)Outside 可以访问DMZ (但必须通过ACL,filters,AAA)Inside 可以访问DMZ (但必须通过ACL,filters,AAA)Outside 不可以访问inside, 虽然The outside user might attempt to reach an inside user byusing an existing NAT session,但是不能成功,所以攻击是困难的DMZ 可以访问inside(但必须通过ACL,filters,AAA)2.透明防火墙 transparent firewall当一个现存的网络中,我们可以很容易的引入透明模式防火墙,因为我们不需要修改现在ipadd 规划★ 高级别接口 低级别接口 不需要ACL,反之,则需要默认可以传输的流量类型:IP 和ARP3.访问控制列表★类型:Standard : ospf 重新分布Extended : ip 传输访问控制, 标示NAT允许地址, vpn访问Webtype : webvpn控制Ethertype: 当防火墙为传输模式时,控制访问对于non-IP traffic★NAT,当你在防火墙上做了static nat时,即把一个公网IP影射到了一个内部私有IP,这时你需要做一个访问控制列表,外部地址访问内部主机,并且应该应用到outside接口上(进来的方向)内部地址访问外部网络时,你需要定义ACL,并应用带inside接口上(进防火墙的方向★extended ace基于源地址,目的地址,原端口,目的端口,协议,ICMPICMP是无连接的协议,所以你需要在双向上应用ACE★ethertype acetransparent firewall mode onlyEtherTypes are connectionless(无连接), 仅仅用在传输模式,也许就是应用到以太网环境吧★standard aceSingle context mode only标准访问控制列表不能应用在接口上控制流量★利用object group可以简单化ACEObject group 类型:protocol, network, servicers, icmp type. 可以嵌套使用★定义时间记录日志(log)hostname(config)# time-range for2006hostname(config-time-range)# absolute start 8:00 1 january 2006★记录日志(log)4. NAT★为什么要用NAT内部地址在internet上是不能路由的Nat隐藏了内部地址,免受外网的攻击可以解决公网地址紧缺的问题,采用地址复用技术★nat控制同等安全水平的接口no nat 但如果配置了Dyn nat,则必须匹配NAT ruleInside----->outside 需要nat★Dynamic nat and patNat 标记从哪个接口来的数据Global 标记从哪个接口出去通过ID进行匹配,两个不同的接口可以同时匹配同一个global id,也就是说inside 和dmz的真实IP都可以转换成同一个global id里面的IP地址See the following commands for this example:hostname(config)# nat (inside) 1 10.1.2.0 255.255.255.0hostname(config)# nat (dmz) 1 10.1.1.0 255.255.255.0hostname(config)# global (outside) 1 209.165.201.3-209.165.201.105 通过ACL进行网络访问控制how to control network access through the security appliance using access lists★任何的传输都可以自由的离开防火墙的任何接口,但要进入任何的接口都需要借助于ACL (除内网的数据传输进入inside口)★Outbound 和inbound 是相对于设备而言的开放内部网络主机209.165.201.12的www端口,只允许外部网络访问此端口(static nat) hostname(config)# access-list ACL_OUT extended permit tcp any host 209.165.201.12 eq www hostname(config)# access-group ACL_OUT in interface outside6 .QOS1.qos 概念(rate-limit,priority)The primary goal of QoS in the security appliance is to provide rate limiting on selected network traffic for both individual flow and VPN tunnel flow to ensure that all traffic gets its fair share of limited bandwidth.即: QOS在防火墙的应用终极目标是利用速度限制的方法,使个体传输和VPN数据流公平的共享有限的带宽,从儿是高带宽的,低延时的,重要的数据流得到保障的服务,但同时给予了其他的传输流基本的带宽需求(或是利用优先权排队机制达到同样的需求)2.qos实现创建一个传统的QOSConfiguring a traditional QoS policy for the security appliance consists of the following steps:•Defining traffic classes (class-map command).•Associating policies and actions with each class of traffic (policy-map command). •Attaching policies to logical or physical interfaces (service-policy command).interface GigabitEthernet0/3service-policy output policy-map-nameQOS只能用在接口output方向★hostname(config)# access-list non-tunneled extended permit tcp any any hostname(config)# class-map browsehostname(config-cmap)# description "This class-map matches all non-tunneled tcp traffic."hostname(config-cmap)# match access-list non-tunneled3.Defining a QoS Policy Map (最多可以定义256条police maps,每police可以包含最多256数据流)★Applying Rate LimitingLLQ traffic is not rate-limited.注∶You cannot enable both priority and policing together. 一个分类不能同时指定速度限制和优先级当一个service police应用或是取消在一个已经存在的vpn client/lan—lan ,是不会立即生效的,你需要清除连接或是重新连接★Activating the Service Policy一个police可以全局的应用或是指定某个接口,全局只能应用一个police,接口可以是虚拟的或是物理的若你想在接口下应用优先权排队,需要预先在全局模式下打开某个接口的优先权排队功能hostname(config)# priority-queue interfacehostname(config-priority-queue)#★view qos confighostname# show service-policy police //查看qos限速Global policy:Service-policy: global_fw_policyInterface outside:Service-policy: qosClass-map: browsepolice Interface outside:cir 56000 bps, bc 10500 bytesconformed 10065 packets, 12621510 bytes; actions: transmitexceeded 499 packets, 625146 bytes; actions: dropconformed 5600 bps, exceed 5016 bpshostname# show service-policy priority //查看qos优先权排队Global policy:Service-policy: global_fw_policyInterface outside:Service-policy: qosClass-map: TG1-voicePriority:Interface outside: aggregate drop 0, aggregate transmit 9383hostname# show running-config policy-map //查看qos限速配置!policy-map testclass class-defaultpolicy-map inbound_policyclass ftp-portinspect ftp strict inbound_ftppolicy-map qosclass browsepolice 56000 10500class TG1-voicepriorityclass TG1-BestEffortpolice 200000 37500hostname(config)# show running-config priority-queue test //查看qos优先权排队配置priority-queue testqueue-limit 2048tx-ring-limit 256hostname(config)#7.Configuring Application Layer Protocol Inspection (配置应用层协议深度检测)7.1 when 什么时候我们需要用到深度检测当一个用户建立一个连接,防火墙利用acl进行检查,通过则创建一个地址传输,为这此会话创建一个快速通道,so后续的包则不需要消耗更多的时间去检查很多协议都可能打开两个tcp或是udp端口,用一个知名的初始的端口号去建立session ,再去协商另一个端口号,比如ftp,数据传输20端口,控制传输21端口上述情况可能需要用到深度检测7.2 限制• State information for multimedia sessions that require inspection are not passed over the state link for stateful failover. The exception is GTP, which is replicated over the state link.• Some inspection engines do not support PAT, NAT, outside NAT, or NAT between same security interfaces.默认的inspection policy,a global policy,一个全局的策略,应用到了所有的接口,如果你想改变他或是添加一个新的默认没有打开的新的检测,你需要编辑default inspection policy and disable it and apply a new one7.4 DNS rewrite配置实例:The following example configures the security appliance for the scenario shown in Figure 25-2. It assumes DNS inspection is already enabled.hostname(config)# static (dmz,outside) 209.165.200.225 192.168.100.10 dns hostname(config)# access-list 101 permit tcp any host 209.165.200.225 eq www hostname(config)# access-group 101 in interface outsideThis configuration requires the following A-record on the DNS server:. IN A 209.165.200.225 // 需要ISP在公网dns里配置主机A记录总结:dns ipspection 对公网dns返回给防火墙的web地址进行检查,查找到rule记录里存在DNS可选项,则重新修改返回的web ip地址,再进而发给内网的web client客户端,接下来的通信则直接是inside―――》dmz---- 待续 2008-08-21 waveslv QQ 157407989。
asa5505思科防火墙

asa5505思科防火墙公司网络不断更新,新进一设备名为cicoASA-5505防火墙。
公司准备把四台监控系统服务器通过防火墙与公司现有网络隔离。
但是现有的服务器有三台在之前分别在给市煤管局、集团公司、国投总公司提供监控信息。
所以更改IP地址的话会很麻烦。
所以公司决定将原有三台电脑的IP 地址做地址转换。
开放相应端口即可。
公司现有网络段为192.168.0.0隔离后网络段为172.168.1.0IOS版本为ASA-7.2与之前版本的配置有一定区别。
下面说说具体的操作步骤:1、将四台监控系统服务器通过普通交换机连接接,交换机接防火墙1口,防火墙0口与公司现有网络交换机连接,用conole线将防火墙与PC连接到一起。
2、打开PC运行超级终端,出现新建连接界面,随便输入名称确定,出现借口选择界面,选择相应的COM口即可,确定出现COM口属性设置,恢复默认即可。
3、进入防火墙出现Pre-configurePI某Firewallnowthroughinteractiveprompt[ye]意思是否进入交互配置对话模式选择N4、进入防火墙的命令提示符界面,cicoaa>在后面输入enable 进入特权模式cicoaa#在后面输入conft进入全局配置模式。
这时。
就可以对防火墙进行配置了。
5、配置防火墙名cicoaa(config)#hotnamedyq配置防火墙密码(config)#enablepawordadmin配置IPdyq(config)#interfacevlan1dyq(config-if)#ipaddre192.168.0.251255.255.255.0dyq(config-if)#nohutdowndyq(config-if)#ecurity-level0dyq(config-if)#nameifoutidedyq(config-if)#e某itdyq(config)#interfacevlan2dyq(config-if)#ipaddre172.168.1.1255.255.255.0dyq(config-if)#nohutdowndyq(config-if)#ecurity-level100dyq(config-if)#nameifinidedyq(config-if)#e某it将e0和e1口加入VLANdyq(config)#interfaceethernet0/0dyq(config-if)#nohutdown dyq(config-if)#witchportaccevlan1dyq(config-if)#e某itdyq(config)#interfaceethernet0/1同上dyq(config)#acce-litacl_oute某tendedpermiticmpanyanydyq(config)#acce-litacl_oute某tendedpermittcpanyhot192.168.0.7eq1433dyq(config)#acce-litacl_oute某tendedpermittcpanyhot192.168.0.8eq8080dyq(config)#acce-litacl_oute某tendedpermittcpanyhot192.168.0.8eq445dyq(config)#acce-litacl_oute某tendedpermittcpanyhot192.168.0.8eq1433允许主机192.168.0.9开放80端口acl_out为访问控制列表号验证访问控制列表howacce-lit配置路由dyq(config)#routeoutide00192.168.0.1验证howroute配置静态NATdyq(config)#tatic(inide,outide)192.168.0.7172.168.1.10netmak255.255.255.255dy q(config)#tatic(inide,outide)192.168.0.8172.168.1.20netmak255.255.255.255dy q(config)#tatic(inide,outide)192.168.0.9172.168.1.30netmak255.255.255.255IP 地址转换内网IP172.168.1.某转换为外网IP192.168.0.某配置动态NAT(PAT)dyq(config)#global(outide)1interfacedyq(config)#nat(inide)1172.1 68.1.0255.255.255.0或者dyq(config)#nat(inide)100。
思科5505火墙配置

asa 5505 常用配置2009-06-01 16:13asa 55051.配置防火墙名ciscoasa> enableciscoasa# configure terminalciscoasa(config)# hostname asa55052.配置telnetasa5505(config)#telnet inside//允许内部接口3.配置密码asa5505(config)# password cisco//远程密码asa5505(config)# enable password cisco //特权模式密码4.配置IPasa5505(config)# interface vlan 2//进入vlan2asa5505(config-if)# ip address//vlan2配置IPasa5505(config)#show ip address vlan2 //验证配置5.端口加入vlan//进入接口e0/3asa5505(config-if)# switchport access vlan 3 //接口e0/3加入vlan3asa5505(config)# interface vlan 3//进入vlan3asa5505(config-if)# ip address//vlan3配置IPasa5505(config-if)# nameif dmz//vlan3名asa5505(config-if)# no shutdown//开启asa5505(config-if)# show switch vlan//验证配置6.最大传输单元MTUasa5505(config)#mtu inside 1500//inside最大传输单元1500字节asa5505(config)#mtu outside 1500//outside最大传输单元1500字节asa5505(config)#mtu dmz 1500//dmz最大传输单元1500字节7.配置arp表的超时时间//arp表的超时时间14400秒8.FTP模式asa5505(config)#ftp mode passive//FTP被动模式9.配置域名asa5505(config)#domain-name 10.启动日志asa5505(config)#logging enable//启动日志asa5505(config)#logging asdm informational //启动asdm报告日志asa5505(config)#Show logging//验证配置11.启用http服务asa5505(config)#http serverenable//启动HTTP server,便于ASDM连接。
ASA5505配置文档及其指令说明

asa(config)#securit-level 0 //安全级别0
asa(config)#ip address *.*.*.* 255.255.255.0 //配置公网IP地址
asa(config)#duplex full
(括号内序顺是先内后外,外边的顺序是先外后内)
例如:
asa(config)#static (inside,outside) 133.0.0.1 192.168.0.8
表示内部ip地址192.168.0.8,访问外部时被翻译成133.0.0.1全局地址
**************************************************************************
其中:
internal_if_name表示内部网络接口,安全级别较高,如inside。
external_if_name表示外部网络接口,安全级别较低,如outside。
outside_ip_address表示外部网络的公有ip地址。
inside_ ip_address表示内部网络的本地ip地址。
nameif inside 定义端口为内
security-level 100 定义端口安去昂等级为100
no shut
ip address 192.168.1.1 255.255.255.0
3、定义内部NAT范围。
nat (inside) 1 0.0.0.0 0.0.0.0 任何IP都可以NAT,可以自由设置范围。
asa#conf t
asa(config)# hostname asa //设置主机名
思科5505配置详解
*如果内部有服务器需要映射到公网地址(外网访问内网)则需要static和conduit或者acl.
static (in side, outside) 222.240.254.194 192.168.1.240
nat命令配置语法:n at (if_ name) n at_id local_ip [n etmark]
必要的漏洞)
ACL实现的功能和conduit一样都可实现策略访问,只是ACL稍微麻烦点。conduit现在在
7版本已经不能用了。
Access-list101permit tcp any host 222.240.254.194 eq 101 in in terface outside (绑定到接口)
1、定义外口
in terface Ethernet。/。进入端口nameif outside定义端口为外口security-level0定义安全等级为0no shut激活端口
ip address .X驱>255.255.255.248设置IP
2、定义内口
in terface Ethernet0/1
n ameif in side定义端口为内
或
global (outside) 1 in terface当ISP只分配给一个IP是,直接使用分配给外口的IP地址。
5、设置默认路由
route outside0 0218.17.148.14指定下一条为IPS指定的网关地址
查看NAT转换情况
show xlate
:6个基本命令:n ameif、in terface、ip address、n at、global、route。
ASA_5505入门配置手册

1. 初始配置ciscoasa> enable 从进入用户模式进入特权模式ciscoasa# configure terminal 从特权模式进入全局配置模式ciscoasa(config)# hostname AYKJ-FW 更改防火墙名称AYKJ-FW(config)# passwd aykj 配置远程登录密码AYKJ-FW(config)# enable password aykj 配置enable密码2. 端口配置AYKJ-FW(config)# interface Vlan2 创建SVI口,ASA5505必须通过SVI口配置地址AYKJ-FW(config)# nameif outside 定义为outside口,即连接外网接口AYKJ-FW(config)# security-level 0 定义安全级别,范围0~100,其中inside、outside 口安全级别为系统自动定义和生成AYKJ-FW(config)# ip address 221.226.186.58 255.255.255.252 配置运营商分配公网地址AYKJ-FW(config)# interface Vlan3AYKJ-FW(config)# nameif inside 定义为inside口,即连接内网接口AYKJ-FW(config)# security-level 100 inside口默认安全级别100AYKJ-FW(config)# ip address 10.0.0.1 255.255.255.0 配置内网口地址3. 管理配置AYKJ-FW(config)# telnet 0.0.0.0 0.0.0.0 inside 允许内网所有地址通过telnet登录防火墙AYKJ-FW(config)# ssh 0.0.0.0 0.0.0.0 outside 允许外网所有地址通过ssh登录防火墙AYKJ-FW(config)# ssh version 1 使用ssh版本1AYKJ-FW(config)# http server enable 开启web页面,即开启asdm,与传统的如ASA5520等有专门管理口的防火墙不同,ASA5505只要启用服务,并应用到端口,那么只要网络通畅就可以通过asdm管理,更加灵活AYKJ-FW(config)# http 0.0.0.0 0.0.0.0 insideAYKJ-FW(config)# http 0.0.0.0 0.0.0.0 outside 这两条命令意味着所有只要能够访问防火墙的地址均可以通过asdm管理防火墙4. 路由配置AYKJ-FW(config)# route outside 0.0.0.0 0.0.0.0 221.226.186.57 配置上网默认路由,下一条为运营商分配的网关AYKJ-FW(config)# route inside [内网网段] [掩码] [防火墙内网口] 配置内网路由,由于本次内网与防火墙在一个地址段,所以不需要5. NAT配置5.1 动态NAT配置AYKJ-FW(config)# global (outside) 1 interface 将outside接口设置为NA T的外网接口AYKJ-FW(config)# nat (inside) 1 10.0.0.0 255.255.255.0 允许内网网段通过NA T访问互联网5.2 静态NAT映射AYKJ-FW(config)# access-list perout extended permit tcp any host 221.226.186.58 eq www 首先在防火墙外网口开放需要做映射的端口AYKJ-FW(config)# access-group perout in interface outside 在外网口启用该ACLAYKJ-FW(config)# static (inside,outside) tcp interface www 10.0.0.150 www netmask 255.255.255.255 将内网服务器的端口映射到外网AYKJ-FW(config)# global (inside) 1 interfaceAYKJ-FW(config)# static (inside,inside) tcp 221.226.186.58 www 10.0.0.150 www netmask 255.255.255.255 以上两条命令的作用是当内网用户通过外网地址去访问内网服务器时,直接映射到内网,如果不做则内网用户不能通过外网地址访问内网服务器6. VPN配置6.1 VPN基础配置AYKJ-FW(config)# ip local pool vpn 10.0.1.210-10.0.1.220 mask 255.255.255.0 创建vpn 地址池,地址池应与本地网段不在同一个段AYKJ-FW(config)# access-list inside_nat0_outbound extended permit ip 10.0.0.0255.255.255.0 10.0.1.0 255.255.255.0 定义vpn流量与内网流量的互访AYKJ-FW(config)# nat (inside) 0 access-list inside_nat0_outbound 该流量不参与nat翻译AYKJ-FW(config)# access-list split standard permit 10.0.0.0 255.255.255.0 定义vpn用户允许访问网段AYKJ-FW(config)# username asa password cisco 创建vpn用户,不做策略则该用户可以通过SSL和IPSEC拨入VPN6.2 SSL(WEB) VPN配置AYKJ-FW(config)# webvpn 配置webvpnAYKJ-FW(config-webvpn)# enable outside 在外网口启用webvpnAYKJ-FW(config-webvpn)# svc image disk0:/anyconnect-win-2.4.1012-k9.pkg 调用vpn 客户端软件AYKJ-FW(config-webvpn)# svc enable 启用客户端软件AYKJ-FW(config)# group-policy ssl internal 创建webvpn组策略AYKJ-FW(config)# group-policy ssl attributes 配置组策略属性AYKJ-FW(config-group-policy)# vpn-tunnel-protocol svc webvpn 启用webvpn隧道AYKJ-FW(config-group-policy)# split-tunnel-policy tunnelspecified 只允许split匹配流量通过vpn隧道AYKJ-FW(config-group-policy)# split-tunnel-network-list value split 水平分割策略使用split,由于vpn用户没有网关,需要通过该策略使vpn用户访问内网AYKJ-FW(config)# tunnel-group ssl type remote-access 创建vpn隧道,类型为远程接入AYKJ-FW(config)# tunnel-group ssl general-attributes 配置vpn隧道基础属性AYKJ-FW(config-tunnel-general)# address-pool vpn 调用vpn地址池6.3 IPSEC VPN 配置AYKJ-FW(config)# crypto isakmp enable outside 在outside口启用ipsec vpnAYKJ-FW(config)# crypto isakmp disconnect-notify 连接中断时报错AYKJ-FW(config)# crypto isakmp policy 10 配置策略优先级AYKJ-FW(config-isakmp-policy)# authentication pre-share 通过预共享密钥拨入vpn AYKJ-FW(config-isakmp-policy)# encryption 3des通过3des格式加密数据AYKJ-FW(config-isakmp-policy)# hash md5 通过md5算法校验数据AYKJ-FW(config-isakmp-policy)# group 2 设置迪夫-赫尔曼算法组AYKJ-FW(config-isakmp-policy)# lifetime 86400 设置连接时长AYKJ-FW(config)# group-policy aykj internal创建ipsec vpn策略组AYKJ-FW(config)# group-policy aykj attributes 配置策略组属性AYKJ-FW(config-group-policy)# vpn-tunnel-protocol IPSec 启用ipsec vpn隧道AYKJ-FW(config-group-policy)# split-tunnel-policy tunnelspecified 只允许split匹配流量通过vpn隧道AYKJ-FW(config-group-policy)# split-tunnel-network-list value split 水平分割策略使用split,由于vpn用户没有网关,需要通过该策略使vpn用户访问内网AYKJ-FW(config)# tunnel-group aykj type remote-access 创建vpn隧道,类型为远程接入AYKJ-FW(config)# tunnel-group aykj general-attributes 配置隧道基础属性AYKJ-FW(config-tunnel-general)# address-pool vpn调用地址池AYKJ-FW(config-tunnel-general)# default-group-policy aykj 调用组策略AYKJ-FW(config)# tunnel-group aykj ipsec-attributes 配置隧道ipsec属性AYKJ-FW(config-tunnel-ipsec)# pre-shared-key aykj 预共享密钥为aykj。
Cisco ASA5500 配置手册

Cisco ASA5500系列防火墙基本配置手册一、配置基础1.1用户接口思科防火墙支持下列用户配置方式:Console,Telnet,SSH(1.x或者2.0,2.0为7.x新特性),ASDM的http方式,VMS的Firewall Management Center。
支持进入Rom Monitor模式,权限分为用户模式和特权模式,支持Help,History和命令输出的搜索和过滤。
用户模式:Firewall> 为用户模式,输入enable进入特权模式Firewall#。
特权模式下输入config t 可以进入全局配置模式。
通过exit,ctrl-z退回上级模式。
配置特性:在原有命令前加no可以取消该命令。
Show running-config 或者 write terminal显示当前配置。
Show running-config all显示所有配置,包含缺省配置。
Tab可以用于命令补全,ctrl-l可以用于重新显示输入的命令(适用于还没有输入完命令被系统输出打乱的情况),help和history相同于IOS命令集。
Show命令支持 begin,include,exclude,grep 加正则表达式的方式对输出进行过滤和搜索。
Terminal width 命令用于修改终端屏幕显示宽度,缺省为80个字符,pager命令用于修改终端显示屏幕显示行数,缺省为24行。
1.2初始配置跟路由器一样可以使用setup进行对话式的基本配置。
二、配置连接性2.1配置接口接口基础:防火墙的接口都必须配置接口名称,接口IP地址和掩码和安全等级。
接口基本配置:Firewall(config)# interface hardware-id 进入接口模式Firewall(config-if)# speed {auto | 10 | 100 | nonegotiate} 设置接口速率Firewall(config-if)# duplex {auto | full | half} 接口工作模式Firewall(config-if)# [no] shutdown 激活或关闭接口Firewall(config-if)# nameif if_name 配置接口名称Firewall(config-if)# security-level level 定义接口的安全级别例:interface GigabitEthernet0/0nameif outsidesecurity-level 0ip address 125.78.33.22 255.255.255.248!interface GigabitEthernet0/1nameif insidesecurity-level 100ip address 192.168.18.254 255.255.255.0在配置中,接口被命名为外部接口(outside),安全级别是0;被命名为内部接口(inside),安全级别是100.安全级别取值范围为1~99,数字越大安全级别越高。
CISCO_ASA_5500产品手册

CISCO ASA 5500 系列自适应安全设备Cisco® ASA 5500 系列自适应安全设备除了提供前所未有的服务灵活性、模块化可扩展性、特性可延伸性和更低的部署和运营成本之外,还可为各类企业、服务提供商和任务关键型数据中心提供一套功能强大的高度集成、以市场为主导的安全服务。
经过市场验证的安全功能• ——Cisco ASA 5500系列整合了多种全功能、高性能安全服务,其中包括应用层防火墙、SSL 和IPsec VPN 、IPS全局相关服务和担保、抗病毒、反垃圾邮件、防网络钓鱼和网页过滤服务。
结合实时的信誉技术,这些技术提供高效的网络层和应用层安全、基于用户的访问控制、蠕虫防护、恶意软件防护、员工更高的工作效率、即时消息传送和点对点控制、以及安全的远程用户和站点连接。
唯一采用市场领先声誉技术的IPS ——Cisco IPS 全局相关服务提供过去 IPS 两倍的效率和担保,保证客户无后顾之忧。
Cisco ASA 5585-X 提供一系列桌面和移动平台的无缝式客户端和无客户端访问,并通过集成的 Web 安全和 IPS 策略执行和威胁保护实现永久安全的移动。
图 1. CISCO ASA 5500 系列自适应安全设备CISCO ASA 5500 系列帮助企业提高在保护自身网络和应用方面的工作效率,并通过以下方面提供卓越的投资保护:Cisco ASA 5500 系列自适应安全设备是Cisco 无边界安全网络的核心组件,提供出色的可扩展性,广泛的技术和解决方案,以及高效、永久的安全性,以满足多种部署需求。
通过整合世界上最被公认的防火墙;提供 Cisco 全局相关服务和担保的综合、高效的入侵防御系统(IPS);以及高性能 VPN 和始终开通的远程访问,Cisco ASA 5500 系列为企业提供安全的高性能连接并保护关键资产实现最高生产率。
可扩展的集成服务体系结构——Cisco ASA 5500系列通过硬件和软件可扩展性的独特结合以及强大的模块策略框架 (MPF) 向企业提• 供强大的自适应保护,免受快速演变的威胁环境干扰。
ASA5505基本配置笔记

9. 设置指向内部网和外部网的缺省路由
route inside 0 0 inside_default_router_ip_address
route outside 0 0 outside_default_router_ip_address
10. 配置静态IP地址对映:
static outside ip_address inside ip_address
<cபைடு நூலகம்nfig>#http server enable
<config>#http 192.168.1.0 255.255.255.0 inside
<config>#telnet 192.168.1.0 255.255.255.0 inside
<config>#ssh 192.168.1.0 255.255.255.0 inside
2.把端口指定到相应VLAN中
<config>#int Eth0/0
<config-if>#switchport access vlan 1
<config-if>end
<config>#int Eth0/1
<config-if>switchport access vlan 2
foreign_ip 表示可访问global_ip的外部ip,其中表示所有的ip。
12. 设置telnet选项:
telnet local_ip [netmask]
local_ip 表示被允许通过telnet访问到pix的ip地址(如果不设此项,
PIX的配
置只能由consle方式进行)。
ASA5500配置说明

择1024 bit
2. 保存RSA Keys到flash,
hostname(config)# write mem
3. 指定允许从哪个接口和哪个源地址通过SSH连入到ASA hostname(config)# ssh
source_IP_address mask source_interface
access-group outside_permit in interface outside
//把outside_permit控制列表运用在外部接口的入口方向。
route outside 0.0.0.0 0.0.0.0 202.98.131.126 1 //定义一个默认路由。
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
static (dmz,outside) tcp interface 30010 192.168.2.2 30010 netmask 255.255.255.255
static (dmz,outside) tcp interface 3389 192.168.2.2 3389 netmask 255.255.255.255
//端口映射 可以解决内部要公布的服务太多,而申请公网IP少问题。
static (dmz,outside) tcp interface 30001 192.168.2.2 30001 netmask 255.255.255.255
//把dmz区192.168.2.2 30002 映射给外部30002端口上。
//访问控制列表
access-list outside_permit extended permit tcp any interface outside range 30000
Cisco ASA 5500和ASA 5500-X系列下一代防火墙数据册说明书

Data Sheet Cisco ASA 5500 and ASA 5500-X SeriesNext-Generation Firewalls for the Internet EdgeCisco® ASA 5500 and ASA 5500-X Series Next-Generation Firewalls integrate the world’s most proven stateful inspection firewall with a comprehensive suite of highly integrated next-generation firewall services for networks of all sizes - small and midsize businesses with one or a few locations, large enterprises, service providers, and mission-critical data centers. The Cisco ASA 5500 and ASA 5500-X SeriesNext-Generation Firewalls deliver MultiScale™ performance with unprecedented services flexibility, including next-generation firewall capabilities, modular scalability, feature extensibility, and lower deployment and operations costs.Midsize businesses protecting the Internet edge require the same level of protection as large enterprise networks. You require enterprise-strength security, but purchasing a firewall that was built to handle the performance needs and budget of a large enterprise would be unnecessary and a waste of company resources. You need a firewall that provides the performance you need at a price you can afford, along with the visibility and control you need to take advantage of new applications and devices without compromising security.Features and BenefitsCisco ASA 5500 and ASA 5500-X Series Next-Generation Firewalls are available in a wide range of sizes and performance levels to fit your network and budget while offering the same proven level of security that protects some of the largest networks at some of the most security-conscious companies in the world. The ASA 5500 and ASA 5500-X Next-Generation Series Firewalls scale to meet the performance and security requirements of a wide range of network applications, to correspond with your changing needs.Like their enterprise counterparts, Cisco ASA 5500 and ASA 5500-X Series Next-Generation Firewalls for the Internet edge protect critical assets through:●Exceptional next-generation firewall services that provide the visibility and control your enterprise needs tosafely take advantage of new applications and devices1●Application Visibility and Control (AVC) to control specific behaviors within allowed micro-applications●Web Security Essentials (WSE) to restrict web and web application usage based on reputation of the site●Broad and deep network security through an array of integrated cloud- and software-based next-generationfirewall services backed by Cisco Security Intelligence Operations (SIO)●Highly effective intrusion prevention system (IPS) with Cisco Global Correlation●High-performance VPN and always-on remote access●The ability to enable additional security services quickly and easily in response to changing needs1 Please contact your sales representative for availability.Cisco ASA 5525-X, 5545-X, and 5555-XThe Cisco ASA 5525-X, 5545-X, and 5555-X are next-generation firewalls that combine the most widely deployed stateful inspection firewall in the industry with a comprehensive suite of next-generation network security services - for comprehensive security without compromise. They help meet evolving security needs by delivering multiple next-generation security services, multigigabit performance, flexible interface options, and redundant power supplies, all in a compact 1-RU form factor. These firewalls optionally provide broad and deep network security services through an array of integrated cloud- and software-based security services, including Application Visibility and Control (AVC), Web Security Essentials (WSE), Cisco Cloud Web Security (CWS), and the only context-aware IPS - with no need for additional hardware modules.The ASA 5525-X, 5545-X, and 5555-X Next-Generation Firewalls are part of the ASA 5500-X Series, which is built on the same proven security platform as the rest of the ASA family of firewalls and delivers superior performance for exceptional operational efficiency. These models are designed to meet evolving security needs by providing, among other things, innovative next-generation firewall services that make it possible to take advantage of new applications and devices without compromising security. Unlike other next-generation firewalls, the Cisco ASA 5500-X Series keeps pace with rapidly evolving needs by offering end-to-end network intelligence gained from combining the visibility from local traffic with in-depth global network intelligence through:●Cisco TrustSec® technology●Cisco AnyConnect® Secure Mobility Solution for unique mobile client insight●Cisco Security Intelligence Operations (SIO) for near-real-time threat information and proactive protection●Cisco ASA Next-Generation Firewall ServicesWith up to 4 Gbps of firewall throughput, 1,000,000 concurrent firewall connections, 50,000 connections per second, and 6 integrated Gigabit Ethernet interfaces, the ASA 5525-X, 5545-X, and 5555-X are excellent choices for businesses requiring high performance, cost effectiveness, exceptional application visibility and control, and an extensible security solution that can grow with their changing needs.Cisco ASA 5520, 5540, and 5550The Cisco ASA 5520, 5540, and 5550 are modular, high-performance firewalls that deliver security services with Active/Active high availability and Gigabit Ethernet connectivity for medium-sized enterprise networks. With Gigabit Ethernet interfaces and support for up to 200 VLANs, businesses can easily deploy the Cisco ASA 5520, 5540, and 5550 into multiple zones within their network. The Cisco ASA 5520, 5540, and 5550 scale with businesses as their network security requirements grow, delivering solid investment protection.Businesses can extend their SSL and IPsec VPN capacity to support a larger number of mobile workers, remote sites, and business partners. Up to 5000 Cisco AnyConnect and/or clientless VPN peers can be supported. VPN capacity and resiliency can be increased by taking advantage of integrated VPN clustering and load-balancing capabilities. The Cisco ASA 5520, 5540, and 5550 support up to 10 firewalls in a cluster, offering a maximum of 50,000 AnyConnect and/or clientless VPN peers or 50,000 IPsec VPN peers per cluster. For business continuity and event planning, the Cisco ASA 5520, 5540, and 5550 can also benefit from Cisco VPN Flex licenses, which enable administrators to react to or plan for short-term “bursts” of concurrent Premium VPN remote-access users for up to two months.The advanced application-layer security and content security defenses provided by these firewalls can be extended by deploying the high-performance intrusion prevention and worm mitigation capabilities of the Advanced Inspection and Prevention Security Services Module (AIP SSM) or the comprehensive malware protection of the Content Security and Control Security Services Module (CSC SSM). Using these optional security context capabilities, businesses can deploy up to 100 virtual firewalls within a physical appliance to enable compartmentalized control of security policies on a departmental level. This virtualization strengthens security and reduces overall management and support costs while consolidating multiple security devices into a single appliance.Table 1 compares the features and capacities of the Cisco ASA 5500 and ASA 5500-X Series Next-Generation Firewalls for the Internet Edge.Table 1. Cisco ASA 5500 and ASA 5500-X Series Next-Generation Firewalls for the Internet EdgeUp to 450 Mbps 2 Gbps Up to 650 Mbps 3 Gbps Up to 1.2 Gbps 4 Gbps2 Maximum throughput measured with UDP traffic under ideal conditions.3 Multiprotocol: Traffic profile consisting primarily of TCP-based protocols/applications, such as HTTP, SMTP, FTP, IMAPv4, BitTorrent, and DNS.4 Firewall traffic that does not go through the IPS service can have higher throughput.5 Throughput was measured using ASA CX Software Release 9.1.1 with multiprotocol traffic profile with both AVC and WSE. Traffic logging was enabled as well.6 VPN throughput and sessions count depend on the ASA device configuration and VPN traffic patterns. These elements should be taken into consideration as part of your capacity planning.7 Separately licensed feature; includes two SSL licenses with base system.Regulatory and Standards ComplianceSafety UL 60950, CSAC22.2 No. 60950,EN 60950 IEC60950,AS/NZS60950 IEC 60950-1:2005, 2nd EditionEN 60950-1:2006+A11: 2009UL 60950-1:2007,2nd Edition;CSA C22.2 No.60950-1-07, 2ndEditionUL 60950, CSAC22.2 No. 60950,EN 60950 IEC60950,AS/NZS60950IEC 60950-1:2005, 2nd EditionEN 60950-1:2006+A11: 2009UL 60950-1:2007,2nd Edition;CSA C22.2 No.60950-1-07, 2ndEditionUL 60950, CSAC22.2 No. 60950,EN 60950 IEC60950,AS/NZS60950IEC 60950-1:2005, 2nd EditionEN 60950-1:2006+A11: 2009UL 60950-1:2007,2nd Edition;CSA C22.2 No.60950-1-07, 2ndEditionElectromagnetic Compatibility (EMC) CE marking, FCCPart 15 Class A,AS/NZS CISPR22Class A, VCCIClass A, EN55022Class A, CISPR22Class A,EN61000-3-2,EN61000-3-3CE: EN550222006+A1: 2007Class A; EN550241998+A1:2001+A2:2003; EN61000-3-2 2009;EN61000-3-3 2008;FCC:CFR 47, Part15 Subpart BClass A2010,ANSI C63.42009;ICES-003 ISSUE 4FEBRUARY.2004;VCCI:V-3/2011.04;C-TICK:AS/NZSCISPR 22,2009KC:KN22 & KN24CE marking, FCCPart 15 Class A,AS/NZS CISPR22Class A, VCCIClass A, EN55022Class A, CISPR22Class A,EN61000-3-2,EN61000-3-3CE: EN550222006+A1: 2007Class A; EN550241998+A1:2001+A2:2003; EN61000-3-2 2009;EN61000-3-3 2008;FCC:CFR 47, Part15 Subpart BClass A2010,ANSI C63.42009;ICES-003 ISSUE 4FEBRUARY.2004;VCCI:V-3/2011.04;C-TICK:AS/NZSCISPR 22,2009KC:KN22 & KN24CE marking, FCCPart 15 Class A,AS/NZS CISPR22Class A, VCCIClass A, EN55022Class A, CISPR22Class A,EN61000-3-2,EN61000-3-3CE: EN550222006+A1: 2007Class A; EN550241998+A1:2001+A2:2003; EN61000-3-2 2009;EN61000-3-3 2008;FCC:CFR 47, Part15 Subpart BClass A2010,ANSI C63.42009;ICES-003 ISSUE 4FEBRUARY.2004;VCCI:V-3/2011.04;C-TICK:AS/NZSCISPR 22,2009KC:KN22 & KN24Industry Certifications Common CriteriaEAL4 US DoDApplication-LevelFirewall forMedium-RobustnessEnvironments,Common CriteriaEAL2 for IPS onAIP SSM-10 and -20, FIPS 140-2Level 2, and NEBSLevel 3In process:Common CriteriaEAL4+ US DoDApplication-LevelFirewall forMedium-RobustnessEnvironments, andCommon CriteriaEAL4 forIPsec/SSL VPNIn process FIPS 140-2 Level2In process:Common CriteriaEAL4+ US DoDApplication-LevelFirewall forMedium-RobustnessEnvironments, andCommon CriteriaEAL4 forIPsec/SSL VPNIn process FIPS 140-2 Level2In process:Common CriteriaEAL4+ US DoDApplication-LevelFirewall forMedium-RobustnessEnvironments, andCommon CriteriaEAL4 forIPsec/SSL VPNIn processCisco ASA 5500 Series Security Services Processors, Modules, and CardsThe Cisco ASA 5500 Series brings a new level of integrated security performance to networks with its highly effective IPS services and multiprocessor hardware architecture. This architecture allows businesses to adapt and extend the high-performance security services profile of the Cisco ASA 5500 Series. Customers can add additional high-performance services using security services modules with dedicated security co-processors, and can custom-tailor flow-specific policies using a highly flexible policy framework. This adaptable architecture enables businesses to deploy new security services when and where they are needed, such as adding the broad range of intrusion prevention and advanced antiworm services delivered by the IPS modules via the AIP SSM and AIP SSC, or the comprehensive malware protection and content security services enabled by the CSC SSM. Further, the Cisco ASA 5500 Series architecture allows Cisco to introduce new services to address new threats, giving businesses outstanding investment protection.The Cisco ASA 5500 Series AIP SSM and AIP SSC are inline, network-based solutions that accurately identify, classify, and stop malicious traffic before it affects business continuity for IPv4, IPv6, and hybrid IPv6 and IPv4 networks. They combine inline prevention services with innovative technologies, resulting in total confidence in the provided protection of the deployed IPS solution, without the fear of legitimate traffic being dropped. The AIP SSM and AIP SSC also offer comprehensive network protection through their unique ability to collaborate with other network security resources, providing a proactive approach to protecting the network.Accurate inline prevention technologies provide unparalleled confidence to take preventive action on a broader range of threats without the risk of dropping legitimate traffic. These unique technologies offer intelligent, automated, contextual analysis of data and help ensure that businesses are getting the most out of their intrusion prevention solutions. Furthermore, the IPS SSP, AIP SSM, and AIP SSC use multivector threat identification to protect the network from policy violations, vulnerability exploitations, and anomalous activity through detailed inspection of traffic in Layers 2 through 7.Table 2 details the AIP SSM models that are available, and their respective performance and physical characteristics.Table 2. Characteristics of Cisco ASA 5500 Series AIP SSM Models225 Mbps with Cisco ASA 5520 375 Mbps with Cisco ASA 5520500 Mbps with Cisco ASA 5540 450 Mbps with Cisco ASA 5520 650 Mbps with Cisco ASA 5540Cisco ASA 5500 Series Content Security and Control ModuleThe Cisco ASA 5500 Series CSC SSM delivers industry-leading threat protection and content control at the Internet edge, providing comprehensive antivirus, antispyware, file blocking, antispam, antiphishing, URL blocking and filtering, and content filtering services in an easy-to-manage solution. The CSC SSM bolsters the Cisco ASA 5500 Series’ strong security capabilities, providing customers with additional protection of and control over the content of their business communications. The module provides additional flexibility and choice over the functioning and deployment of Cisco ASA 5500 Series firewalls. Licensing options enable organizations to customize the features and capabilities to each group’s needs, with features that include advanced content services and increased user capacity. The CSC SSM ships with a default feature set that provides antivirus, antispyware, and file blocking services.A Plus license is available for each CSC SSM at an additional charge, delivering capabilities such as antispam, antiphishing, URL blocking and filtering, and content control services. Businesses can extend the user capacity of the CSC SSM by purchasing and installing additional user licenses. A detailed listing of these options is shown in Table 3 and in the CSC SSM data sheet.Table 3. Characteristics of Cisco ASA 5500 Series CSC SSMsCisco ASA 5520 Cisco ASA 5520Cisco ASA 5540Cisco ASA 5500 Series 4-Port Gigabit Ethernet ModuleThe Cisco ASA 5500 Series 4-Port Gigabit Ethernet SSM enables businesses to better segment network traffic into separate security zones, providing more granular security for their network environment. These zones can range from the Internet to internal corporate departments/sites to DMZs. This high-performance module supports both copper and optical connection options by including four 10/100/1000 copper RJ-45 ports and four SFP ports. Businesses can choose between copper or fiber ports, providing flexibility for data center, campus, or enterprise edge connectivity. The module extends the I/O profile of the Cisco ASA 5500 Series to a total of five Fast Ethernet and four Gigabit Ethernet ports on the Cisco ASA 5510. Table 4 lists the characteristics of the Cisco ASA 5500 Series 4-Port Gigabit Ethernet SSMs.Table 4. Characteristics of Cisco ASA 5500 Series 4-Port Gigabit Ethernet SSMsFour 10/100/1000BASE-TFour (Gigabit Ethernet Optical SFP 1000BASE-SX or LX/LH transceiver supported)Cisco ASA 5500-X Series 6-Port Gigabit Ethernet Interface CardsCisco ASA 5500-X Series 6-port Gigabit Ethernet Interface Cards extend the I/O profile of the ASA 5525-X through ASA 5555-X by providing additional GE ports. The cards provide the following benefits:●Better segmentation of network traffic (into separate security zones)●Fiber-optic cable connectivity for long distance communication●Load sharing of traffic as well as protection against link failure by using EtherChannel●Support for Jumbo Ethernet frames of up to 9000 bytes●Protection against cable failure for the most demanding Active/Active and full mesh firewall deployments Table 5 lists the characteristics of the Cisco ASA 5500-X Series 6-Port Gigabit Ethernet Interface Cards.Table 5. Characteristics of Cisco ASA 5500-X Series 6-Port Gigabit Ethernet Interface CardsSix 10/100/1000BASE-T Six (Gigabit Ethernet Optical SFP 1000BASE-SX or LX/LHtransceiver supported)Ordering InformationTo place an order, visit the Cisco Ordering Home Page. Table 6 provides ordering information for the Cisco ASA 5500 Series and ASA 5500-X Series Next-Generation Firewalls.Table 6. Ordering InformationTo Download the SoftwareVisit the Cisco Software Center to download Cisco ASA Software.Service and SupportCisco services help you protect your network investment, optimize network operations, and prepare your network for new applications to extend network intelligence and the power of your business.Included in the “Operate” phase of the service lifecycle are Cisco Sec urity IntelliShield Alert Manager Service, Cisco SMARTnet® Service, Cisco Service Provider Base, and Cisco Services for IPS. These services are suitable for enterprise, commercial, and service provider customers.Cisco Security IntelliShield Alert Manager Service provides a customizable, web-based threat and vulnerability alert service that allows organizations to easily access timely, accurate, and credible information about potential vulnerabilities in their environment.Cisco Services for IPS supports modules, platforms, and bundles of platforms and modules that feature IPS capabilities. Cisco SMARTnet and Service Provider Base support other products in this family.Cisco CapitalFinancing to Help You Achieve Your ObjectivesCisco Capital can help you acquire the technology you need to achieve your objectives and stay competitive. We can help you reduce CapEx. Accelerate your growth. Optimize your investment dollars and ROI. Cisco Capital financing gives you flexibility in acquiring hardware, software, services, and complementary third-party equipment. And there’s just one predictable payment. Cisco Capital is available in more than 100 countries. Learn more.For More InformationFor more information, please visit the following links:●Cisco ASA 5500 and ASA 5500-X Series Next-Generation Firewalls: /go/asa●Cisco Adaptive Security Device Manager: /go/asdm●Cisco Security Services: /en/US/products/svcs/ps2961/ps2952/serv_group_home.html●Cisco ASA 5500 Series and ASA 5500-X Series Licensing Information:/en/US/products/ps6120/products_licensing_information_listing.html。
ASA5500防火墙全套产品参数信息

ASA——下一代防火墙Cisco ASA 5500系列自适应安全设备产品简介Cisco® ASA 5500 系列自适应安全设备是思科专门设计的解决方案,将最高的安全性和出色VPN服务与创新的可扩展服务架构有机地结合在一起。
作为思科自防御网络的核心组件,Cisco ASA 5500系列能够提供主动威胁防御,在网络受到威胁之前就能及时阻挡攻击,控制网络行为和应用流量,并提供灵活的VPN连接。
思科强大的多功能网络安全设备系列不但能为保护家庭办公室、分支机构、中小企业和大型企业网络提供广泛而深入的安全功能,还能降低实现这种新安全性相关的总体部署和运营成本及复杂性。
Cisco ASA 5500 系列在一个平台中有力地提供了多种已经获得市场验证的技术,无论从运营角度还是从经济角度看,都能够为多个地点部署各种安全服务。
利用其多功能安全组件,企业几乎不需要作任何两难选择,也不会面临任何风险,既可以提供强有力的安全保护,又可以降低在多个地点部署多台设备的运营成本。
Cisco ASA 5500系列包含全面的服务,通过为中小企业和大型企业定制的产品版本,能满足各种部署环境的特定需求。
这些版本为各地点提供了相应的服务,从而达到出色的保护效果。
每个版本都综合了一套Cisco ASA 5500系列的重点服务(如防火墙、IPSec和SSL VPN、IPS,以及Anti-X 服务),以符合企业网络中特定环境的需要。
通过确保满足每个地点的安全需求,网络整体安全性也得到了提升。
图1. Cisco ASA 5500系列自适应安全设备Cisco ASA 5500 系列能够通过以下关键组件帮助企业更有效地管理网络并提供出色的投资保护:经过市场验证的安全与VPN功能- 全特性、高性能的防火墙,入侵防御系统(IPS), Anti-X和IPSec/SSL VPN 技术提供了强大的应用安全性、基于用户和应用的访问控制、蠕虫与病毒防御、恶意软件防护、内容过滤以及远程用户/站点连接。
Cisco-ASA-5500防火墙个人基本配置手册-去水印
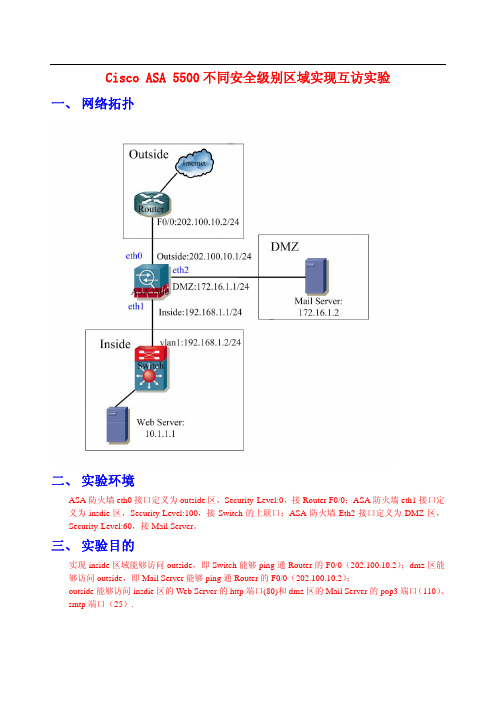
Cisco ASA 5500不同安全级别区域实现互访实验一、 网络拓扑二、 实验环境ASA防火墙eth0接口定义为outside区,Security-Level:0,接Router F0/0;ASA防火墙eth1接口定义为insdie区,Security-Level:100,接Switch的上联口;ASA防火墙Eth2接口定义为DMZ区,Security-Level:60,接Mail Server。
三、 实验目的实现inside区域能够访问outside,即Switch能够ping通Router的F0/0(202.100.10.2);dmz区能够访问outside,即Mail Server能够ping通Router的F0/0(202.100.10.2);outside能够访问insdie区的Web Server的http端口(80)和dmz区的Mail Server的pop3端口(110)、smtp端口(25).四、 详细配置步骤1、端口配置CiscoASA(config)# interface ethernet 0CiscoASA(config)#nameif ousideCiscoASA(config-if)# security-level 0CiscoASA(config-if)# ip address 202.100.10.1 255.255.255.0CiscoASA(config-if)# no shutCiscoASA(config)# interface ethernet 1CiscoASA(config)#nameif insideCiscoASA(config-if)# security-level 100CiscoASA(config-if)# ip address 192.168.1.1 255.255.255.0CiscoASA(config-if)# no shutCiscoASA(config)# interface ethernet 2CiscoASA(config)#nameif dmzCiscoASA(config-if)# security-level 50CiscoASA(config-if)# ip address 172.16.1.1 255.255.255.0CiscoASA(config-if)# no shut2、路由配置CiscoASA(config)# route outside 0.0.0.0 0.0.0.0 202.100.10.2 1 #默认路由CiscoASA(config)# route inside 10.0.0.0 255.0.0.0 192.168.1.2 1 #外网访问内网服务器的路由3、定义高安全接口区域需要进行地址转换的IP范围CiscoASA(config)# nat (inside) 1 0 0CiscoASA(config)# nat (dmz) 1 0 04、定义低安全接口区域用于高安全接口区域进行IP转换的地址范围CiscoASA(config)# global (outside) 1 interfaceCiscoASA(config)# global (dmz) 1 interface5、定义静态IP映射(也称一对一映射)CiscoASA(config)# static (inside,outside) tcp 202.100.10.1 www 10.1.1.1 www netmask 255.255.255.255#实现从outside区访问inside区10.1.1.1的80端口时,就直接访问10.1.1.1:80 对outside区的映射202.100.10.1:80CiscoASA(config)# static (dmz,outside) tcp 202.100.10.1 pop3 172.16.1.2 pop3 netmask 255.255.255.255#实现从outside区访问dmz区172.16.1.2的110时,就直接访问172.16.1.2:110 对outside区的映射202.100.10.1:110CiscoASA(config)# static (dmz,outside) tcp 202.100.10.1 smtp 172.16.1.2 smtp netmask 255.255.255.255#实现从outside区访问dmz区172.16.1.2的25时,就直接访问172.16.1.2:25 对outside区的映射202.100.10.1:256、定义access-listCiscoASA(config)# access-list 101 extended permit ip any anyCiscoASA(config)# access-list 101 extended permit icmp any anyCiscoASA(config)# access-list 102 extended permit tcp any host 10.1.1.1 eq wwwCiscoASA(config)# access-list 102 extended permit icmp any anyCiscoASA(config)# access-list 103 extended permit tcp any host 172.16.1.2 eq pop3CiscoASA(config)# access-list 103 extended permit tcp any host 172.16.1.2 eq smtp7、在接口上应用access-listCiscoASA(config)# access-group 101 in interface outsideCiscoASA(config)#access-group 102 in interface insideCiscoASA(config)#access-group 103 in interface dmz五、 实验总结1、当流量从高权限区域流向低权限区域时1、只要路由配通了,无须配置nat/global,也无须配置access-list,就可以直接telnet低权限区域主机;2、只要路由配通了,同时配置了access-list,无须配置nat/global,就可以直接ping通低权限区域主机;3、只要路由配通了,同时配置了nat/global/access-list,此时telnet/ping均会执行地址转换2、当流量从低权限区域流向高权限区域时1、即使路由已经配通了,也不能成功访问;2、路由已经配通了,同时必须正确配置了static IP地址映射及access-list,才能成功访问;3、调通路由是基础,同时只跟static/access-list有关,而跟nat/global毫无关系。
CiscoASA5505防火墙详细配置教程及实际配置案例

CiscoASA5505防火墙详细配置教程及实际配置案例interfaceVlan2nameifoutside对端口命名外端口security-level0设置端口等级ipaddressX.X.X.X255.255.255.224调试外网地址!interfaceVlan3nameifinside对端口命名内端口security-level100调试外网地址ipaddress192.168.1.1255.255.255.0设置端口等级!interfaceEthernet0/0switchportaccessvlan2设置端口VLAN与VLAN绯定!interfaceEthernet0/1switchportaccessvlan3设置端口VLAN与VLAN3W定!interfaceEthernet0/2shutdown!interfaceEthernet0/3shutdown!interfaceEthernet0/4shutdowninterfaceEthernet0/5shutdown!interfaceEthernet0/6shutdown!interfaceEthernet0/7shutdown!passwd2KFQnbNIdI.2KYOUencryptedftpmodepassivednsdomain-lookupinsidednsserver-groupDefaultDNSname-server211.99.129.210name-server202.106.196.115access-list102extendedpermiticmpanyany设置ACL歹U表(允许ICMP全部通过)access-list102extendedpermitipanyany设置ACL列表(允许所有IP全部通过)pagerlines24mtuoutside1500mtuinside1500icmpunreachablerate-limit1burst-size1noasdmhistoryenablearptimeout14400global(outside)1interface设置NAT地址映射到外网口nat(inside)10.0.0.00.0.0.00NAT地址池(所有地址)0无最大会话数限制access-group102ininterfaceoutside设置ACL列表绑定到外端口routeoutside0.0.0.00.0.0.0x.x.x.x1设置到外网的默认路由timeoutxlate3:00:00timeoutconn1:00:00half-closed0:10:00udp0:02:00icmp0:00:02timeoutsunrpc0:10:00h3230:05:00h2251:00:00mgcp0:05:00mgcp-pat0:05:00timeoutsip0:30:00sip_media0:02:00sip-invite0:03:00sip-disconnect0:02:00timeoutuauth0:05:00absolutenosnmp-serverlocationnosnmp-servercontactsnmp-serverenabletrapssnmpauthenticationlinkuplinkdowncoldstarttelnet0.0.0.00.0.0.0inside设置TELNETS有地址进入telnettimeout5ssh0.0.0.00.0.0.0outside设置SSH所有地址进入sshtimeout30sshversion2consoletimeout0dhcpdaddress192.168.1.100-192.168.1.199inside设置DHCP!艮务器地址池dhcpddns211.99.129.210202.106.196.115interfaceinside设置DNS服务器到内网端口dhcpdenableinside设置DHCPZ用到内网端口前几天去客户那调试CISCO-ASA-5505设备,第一次摸,跟PIX一样,呵呵.没有技术含量,都是最基本的.其他业务配置暂时没配,会及时更新的.CiscoASA5505配置cisco,config,telnet,防火墙,Cisco1.配置防火墙名ciscoasa>enableciscoasa#configureterminalciscoasa(config)#hostnameasa55052.配置telnetasa5505(config)#telnet192.168.1.0255.255.255.0insideT〃允许内部接口192.168.1.0网段telnet防火墙3.配置密码asa5505(config)#passwordcisco远程密码asa5505(config)#enablepasswordcisco特权模式密码4.配置IPasa5505(config)#interfacevlan2进入vlan2asa5505(config-if)#ipaddress218.16.37.222255.255.255.192vlan2配置IPasa5505(config)#showipaddressvlan2验证配置5.端口力口入vlanasa5505(config)#interfacee0/3进入接口e0/3asa5505(config-if)#switchportaccessvlan3接口e0/3力口入vlan3asa5505(config)#interfacevlan3进入vlan3asa5505(config-if)#ipaddress10.10.10.36255.255.255.224vlan3配置IPasa5505(config-if)#nameifdmzvlan3名asa5505(config-if)#noshutdown开启asa5505(config-if)#showswitchvlan验证配置6.最大传输单元MTUasa5505(config)#mtuinside1500inside最大传车^单元1500字节asa5505(config)#mtuoutside1500outside最大传输单元1500字节asa5505(config)#mtudmz1500dmz最大传输单元1500字节7.配置arp表的超时时间asa5505(config)#arptimeout14400arp表的超日^时间14400秒8.FTP模式asa5505(config)#ftpmodepassiveFTP被动模式9.配置域名asa5505(config)#10.启动日志asa5505(config)#loggingenable启动日志asa5505(config)#loggingasdminformational启动asdm报告日志asa5505(config)#Showlogging验证配置11.启用http服务asa5505(config)#httpserverenable启动HTTPserver便于ASDM连接。
Cisco ASA 5500 常用配置命令手册

Cisco ASA 5500 常用配置命令手册默认分类 2010-03-03 16:36:09 阅读56 评论0字号:大中小订阅Cisco ASA 5500 常用配置命令手册1. 常用技巧Shruntp查看与ntp有关的Shru crypto 查看与vpn有关的Shru | inc crypto 只是关健字过滤而已2.故障倒换failoverfailoverlan unit primaryfailoverlan interface testint Ethernet0/3failover link testint Ethernet0/3failover mac address Ethernet0/1 0018.1900.5000 0018.1900.5001 failover mac address Ethernet0/0 0018.1900.4000 0018.1900.4001 failover mac address Ethernet0/2 0018.1900.6000 0018.1900.6001 failover mac address Management0/0 0018.1900.7000 0018.1900.7001 failover interface iptestint 10.3.3.1 255.255.255.0 standby 10.3.3.2注:最好配置虚拟MAC地址sh failover显示配置信息write standby写入到备用的防火墙中failover命令集如下:interface Configure the IP address and mask to be used for failover and/orstateful update informationinterface-policy Set the policy for failover due to interface failureskey Configure the failover shared secret or keylan Specify the unit as primary or secondary or configure the interface and vlan to be used for failover communication link Configure the interface and vlan to be used as a link for stateful update informationmac Specify the virtual mac address for a physical interfacepolltime Configure failover poll intervalreplication Enable HTTP (port 80) connection replicationtimeout Specify the failover reconnect timeout value forasymmetrically routed sessionssh failover 命令集如下:history Show failover switching historyinterface Show failover command interface informationstate Show failover internal state informationstatistics Show failover command interface statistics information| Output modifiers<cr>3配置telnet、ssh及http管理usernamejiang password Csmep3VzvPQPCbkx encrypted privilege 15 aaa authentication enable console LOCALaaa authentication telnet console LOCALaaa authentication ssh console LOCALaaa authorization command LOCALhttp 192.168.40.0 255.255.255.0 managementssh 192.168.40.0 255.255.255.0 inside4. vpn常用管理命令shvpn-sessiondb full l2l 显示site to site 之vpn通道情况shipsec stats 显示ipsec通道情况shvpn-sessiondb summary 显示vpn汇总信息shvpn-sessiondb detail l2l 显示ipsec详细信息shvpn-sessiondb detail svc 查看ssl client信息shvpn-sessiondb detail webvpn查看webvpn信息shvpn-sessiondb detail full l2l 相当于linux下的ipsec whack –status 如果没有建立连接,则表示ipsec通道还没有建立起来。
思科ASA5500系列自适应安全设备

Cisco ASA 5500 系列自适应安全设备Cisco ASA 5500系列自适应安全设备,这一思科下一代安全设备系列是具有特定用途的解决方案,结合了最佳安全VPN服务,以及一个创新的自适应识别和防御(AIM)架构。
Cisco ASA 5500系列充分采用了思科在业界领先并屡获大奖的安全和VPN方面的技术与产品,集成了包括Cisco PIX 500系列防火墙,Cisco IPS 4200系列入侵防御系统和Cisco VPN3000系列VPN集中器的最新技术。
作为思科自防御网络的一个关键组件,Cisco ASA 5500系列提供了主动威胁防御,可在攻击发生之前就在网络中终止它们,可以控制网络活动和应用流量,并提供灵活的VPN连接。
它是一个强大的多功能网络安全设备系列,为保护中小型企业和大型企业网络提供了广泛,深入的安全功能,且在提供这种全新安全水平的同时,降低了总部署和运营成本及复杂度。
返回页首三大安全要素。
单一防御点只有思科可提供防御网络- 一种将集成安全功能内嵌于整个网络的安全构想。
该网络可主动保护终端和基础设施,管理数据流,消除威胁,保护通过有线和无线网络传输的关键数据,并处理误报警。
一旦企业无需要再担心潜在威胁,他们就可集中精力于自身的发展,确信其网络将能安全地根据需要而扩展。
自防御网络的作用•保护基础设施制平面监管可管理数据流,以保护思科路由器和交换机免遭攻击。
•Cisco Auto Secure特性可即时禁用思科路由器中的非关键流程,由此可减少遭受潜在威胁的风险。
•思科异常流量检测器和防护模块可区分正常流量和恶意流量,在发生分布式拒绝服务(DDoS)攻击时保持业务连续性。
•思科安全监控,分析,响应系统(CS-MARS)结合了网络智能,上下文关联,因素分析,异常流量检测,热点识别和自动防御功能,可随时准确地识别,管理和消除网络攻击。
返回页首产品关键特性1.表示平台上支持的最大并发VPN连接数目2.专用带外管理断口(不通过Cisco ASA 5500 自适应安全设备路由任何流量3.许可特性4.A/S=主用/备用;A/A=主用主用Cisco ASA 5500 系列自适应安全设备简介2006-06-23 17:43 Cisco .com我要评论(0)•摘要:Cisco ASA 5500 系列充分利用了思科在开发业界领先、屡获大奖的安全和VPN解决方案过程中积累的丰富经验,并集成了Cisco PIX 500系列安全设备、Cisco IPS 4200系列入侵防范系统和Cisco VPN 3000系列集中器中采用的最新技术。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
访问控制列表(ACL)是防火墙配置中最常用的技术之一,下面以Cisco ASA5500为例介绍一下在不同的应用环境中访问控制列表的具体配置。
1)发布服务器
要将内部服务器发布要公网上,只要配置一个静态NAT和与之对应的ACL就可以,下面是将内部地址192.168.0.100服务器的WWW发布的具体配置,公网地址200.200.200.200。
static (inside,outside) 200.200.200.200 192.168.0.100
access-list OUTSIDE_IN extended permit tcp any host 200.200.200.200 eq ww w
access-group OUTSIDE_IN in interface outside
2)基于时间的ACL
ASA5500支持基于时间的ACL,下面的例子将周一到周五工作时间的www流量限制为1Mb/ s。
time-range working_time
periodic weekdays 9:00 to 17:00
access-list HTTP extended permit tcp any eq 80 any time-rang working_time class-map HTTP
match port tcp eq www
policy-map HTTP
class HTTP
police output 1000000 1000
service-policy HTTP interface inside
3)Lan-to-Lan VPN ACL
基于端口的ACL对于VPN流量是不起作用的,因此需要使用vpn-filter命令来对Lan-to-La n和Remote AccessVPN流量进行过滤和控制。
下面的例子只允许本地10.10.10.0/24网段的PC访问VPN对段192.168.0.100服务器的FTP服务,在这里需要注意ACL中的源地址是指VPN对段的地址。
access-list Filter extended permit tcp host 192.168.0.100 eq ftp 10.10.10.0 25 5.255.255.0
group-policy VPN_1 internal
group-policy VPN_1 attributes
vpn-filter value Filter
tunnel-group x.x.x.x type ipsec-l2l
tunnel-group x.x.x.x general-attributes
default-group-policy VPN_1
4)Remote Access VPN ACL
下面的例子只允许远程接入VPN的客户端访问内部地址为10.10.10.100的服务器。
access-list RAVPN extended permit ip any host 10.10.10.100
group-policy VPN_2 internal
group-policy VPN_2 attributes
vpn-filter value RAVPN
vpn-tunnel-protocol IPSec
tunnel-group VPN_2 general-attributes default-group-policy VPN_2。
