2014年高考地理大题答题模板汇编(背熟可拿80%分数)
SSBU_D_20100630_分类代码转换对应表(依据400万-5万国家整合技术要求)

新分类代码旧分类代码说明110101110101大地原点110102110102三角点11010211020三角点110201110201水准原点110202110202水准点11020212020水准点11030013030卫星定位控制点110301110301卫星定位连续运行站点110302110302卫星定位等级点110402110402独立天文点11040213010独立天文点120100120100内图廓线12010099100内图廓线12010099000内图廓线120200120200坐标网线12020099200坐标网线12030095202经线12040095203纬线120401120401北回归线12040195204北回归线12040295201赤道210101210101地面河流21010121011地面河流21010121012地面河流210102210202地下河段21020221040地下河段210103210103地下河段出入口21010321041地下河段出入口210104210104消失河段21010421031消失河段21010421032消失河段210200210200时令河21020021021时令河21020021022时令河21030079012干涸河(干河床)210301210301河道干河210302210302漫流干河22000022020沟渠22000022030沟渠220100220100运河22010022010运河22010022011运河22010022012运河221000221000干沟220200220200干渠22020022020干渠220300220300支渠22030022030支渠220400220400坎儿井22040024120坎儿井220600220600输水渡槽220700220700输水隧道22070022070输水隧道22070022071输水隧道220800220800倒虹吸220900220900涵洞230101230101湖泊23010123010湖泊23010123011湖泊23010123012湖泊23010123013湖泊230102230102池塘23010224151池塘230200230200时令湖23020023020时令湖23020023021时令湖23020023022时令湖23020023023时令湖230300230300干涸湖、干涸水库、干涸池塘23030079030干涸湖、干涸水库、干涸池塘240101240101水库24010124010水库24010124012水库24010124013水库24010199002水库240102240102建筑中水库240103240103废弃的水库240200240200溢洪道250100250100海域25010026012海域250100910000海域250200250200海岸线25020026010海岸线25020026011海岸线25020026100海岸线25020026200海岸线250300250300干出线25040026030干出滩、滩涂250401250401沙滩25040126031沙滩250402250402沙砾滩、砾石滩25040226032沙砾滩、砾石滩250403250403岩石滩25040326033岩石滩250404250404珊瑚滩25040426034珊瑚滩250405250405淤泥滩25040526035淤泥滩250406250406沙泥滩25040626036沙泥滩250407250407红树林滩25040726037红树林滩250408250408贝类养殖场25040826038贝类养殖场250409250409狭窄干出滩250410250410干出滩中河道250411250411潮水构25041226039水产养殖滩250501250501危险岸区250502250502危险海区250601250601明礁25060126071明礁25060126072明礁25060126070明礁250602250602暗礁25060226080暗礁25060226081暗礁25060226082暗礁250603250603干出礁25060326090干出礁25060326091干出礁25060326092干出礁25060526100珊瑚礁边线250700250700海岛25070079200海岛25070026010海岛25070026011海岛25080026200滩、暗沙边线260200260200河、湖岛26020079200河、湖岛26020025051河、湖岛260300260300沙洲260400260400高水界260500260500岸滩260600260600水中滩26060025050水中滩260700260700泉26070025010泉26070025014泉260800260800水井26080024110水井26080024140水井260801260801水井房260900260900地热井261000261000贮水池、水窖261100261100瀑布、跌水26110025020瀑布、跌水261200261200沼泽、湿地26120085021沼泽、湿地26120085022沼泽、湿地26120085030沼泽、湿地26120185021能通行沼泽26120285022不能通行沼泽261300261300流向27010024045堤27010024090堤270101270101干堤27010124040干堤27010124045干堤270102270102一般堤27010224050一般堤27010224046一般堤270201270201水闸27020124061水闸27020124063水闸270202270202船闸270300270300扬水站27040024180行、蓄、滞洪区270500270500滚水坝27050024080滚水坝27050024070滚水坝270600270600拦水坝27060024080拦水坝27060024085拦水坝270700270700制水坝270801270801有防洪墙的加固岸270802270802无防洪墙的加固岸27090024080水坝31010131010首都310101AD首都31010331020省级城市31010431030地级城市31010431040地级城市31010531050县级城市31010531060县级城市31010631080乡、镇31010631061乡、镇31010631090乡、镇310107AK行政村31010731091行政村310108BB自然村31010831092自然村310109CC农林牧渔单位31010931100农林牧渔单位310109AM农林牧渔单位31011031091村庄310110BD村庄310200310200街区,居民地轮廓31020032010街区,居民地轮廓31020033010街区,居民地轮廓31020033020街区,居民地轮廓310300310300单幢房屋、普通房屋31030032021单幢房屋、普通房屋310500310500高层建筑区310600310600棚房310700310700破坏房屋310112AL县辖区311001311001地面窑洞311002311002地下窑洞311003311003蒙古包、放牧点31100332027蒙古包、放牧点311004311004晾房31100532025窑洞31100633010其它建筑区31110131010国务院311102311102省级政府311102AB省级政府31110231020省级政府31110233010省级政府31110233020省级政府311102AE省级政府311103311103地级政府311103AC地级政府31110331030地级政府31110331040地级政府311103AF地级政府311103AG地级政府31110333010地级政府31110333020地级政府311104311104县级政府311104AE县级政府311104AF县级政府311104AG县级政府31110431050县级政府31110431060县级政府311104AH县级政府311104AI县级政府311104AJ县级政府311104AK县级政府31110433010县级政府31110433020县级政府311105311105乡级政府311105AH乡级政府311105AI乡级政府311105AJ乡级政府31110531080乡级政府31110531061乡级政府31110531090乡级政府311105AN乡级政府311105AO乡级政府311200311200空地320101320101发电厂(站)32010193020发电厂(站)320102320102水厂32010293011水厂320103320103污水处理厂32010493012生物制剂厂320200320200矿井32020093120矿井320300320300露天采掘场320400320400乱掘地320500320500管道井(油、气)320600320600盐井320700320700废弃矿井320800320800海上平台320902320902探槽321000321000液、气贮存设备32100093180液、气贮存设备321101321101散热塔321102321102蒸馏塔321103321103瞭望塔321104321104水塔321105321105水塔烟囱321106321106烟囱321108321108放空火炬321200321200盐田、盐场32120093110盐田、盐场321300321300窑321400321400露天设备321600321600露天货场(栈)、选矿场、材料堆放场330200330200饲养场330300330300水产养殖场330400330400温室、大棚330500330500粮仓(库)33050093260粮仓(库)330601330601水磨房、水车330602330602风磨房、风车330604330604贮草场330605330605药浴池340101340101学校340102340102医院34010295020医院340103340103馆(科技馆、博物馆、展览馆等) 340301340301游乐场340302340302公园340303340303陵园340304340304动物园340305340305植物园340401340401露天体育场340402340402高尔夫球场340403340403体育馆340404340404游泳场、池340405340405跳伞塔340504340504电视发射塔34050495160电视发射塔340505340505移动通信塔340506340506微波塔340602340602垃圾台(场)340701340701公墓340702340702坟地340703340703独立坟340704340704殡葬场所340801340801专用供氧点340802340802口岸350100350100古迹、遗址35010033010古迹、遗址350101350101烽火台350102350102旧碉堡、旧地堡350201350201纪念碑、柱、墩350202350202北回归线标志塔350203350203牌楼、牌坊、彩门350204350204钟鼓楼、城楼、古关塞350205350205亭350206350206文物碑石350208350208塑像35030092999其它文化设施360100360100庙宇36010092110庙宇360200360200清真寺360300360300教堂360400360400宝塔、经塔36040092060宝塔、经塔360500360500敖包、经堆360600360600晒佛台370101370101气象台370102370102水文站370103370103地震台370104370104天文台370105370105环保监测站370200370200卫星地面站370300370300科学试验站38010052010城墙、长城380101380101砖石城墙(完好)38010152010砖石城墙(完好)380102380102砖石城墙(破坏)38010252013砖石城墙(破坏)380201380201围墙380202380202栅栏380203380203篱笆380205380205铁丝网、电网41000041010铁路41000041020铁路410101410101单线标准轨41010141022单线标准轨410102410102复线标准轨41010241021复线标准轨410103410103建设中铁路41010341023建设中铁路41020041030窄轨410201410201单线窄轨410202410202复线窄轨41020341031建设中窄轨410301410301火车站41030141060火车站410305410305站线410308410308天桥410309410309观景台42010042220国道42010042024国道42010042010国道42010042070国道42010042080国道42010042999国道420101420101国道(建成)42010142220国道(建成)420102420102国道(建筑中)42010242221国道(建筑中)42020042230省道42020042034省道420201420201省道(建成)42020142230省道(建成)420202420202省道(建筑中)42020242231省道(建筑中)420301420301县道(建成)420302420302县道(建筑中)420400420400乡道420500420500专用公路420600420600匝道420700420700县乡及其它公路42070042240县乡及其它公路42070042241县乡及其它公路42070042044县乡及其它公路42070042010县乡及其它公路42070042070县乡及其它公路42070042080县乡及其它公路42070042999县乡及其它公路430101430101地铁430102430102轻轨、磁悬浮430200430200快速路430501430501主干道43050142102主干道430502430502次干道43050242103次干道430503430503支线430600430600内部道路440100440100机耕路(大路)44010042110机耕路(大路)440200440200乡村路44020042120乡村路440300440300小路44030042130小路440400440400时令路440500440500山隘44050042150山隘440600440600栈道450101450101地铁站450102380402轻轨站450103450103长途汽车站450104450104加油(气)站450105450105停车场、服务区450106450106收费站450305450305铁路桥45030543010铁路桥450306450306公路桥45030643020公路桥450307450307铁路公路两用桥45030743030铁路公路两用桥450308450308立交桥45030843040立交桥450500450500人行桥45050043050人行桥450601450601火车隧道45060143071火车隧道450602450602汽车隧道45060243072汽车隧道450701450701火车明峒450702450702汽车明峒451001451001中国公路零公里标志451002451002路标451003451003里程碑451100451100野生动物通道451300451300防风墙46010045026船码头460101460101水运港客运站460102460102固定顺岸码头460103460103固定堤坝码头460104460104栈桥式码头460105460105浮码头460106460106干船坞460200460200防波堤460300460300停泊场46030045027停泊场46040044061助航标志460401460401灯塔460402460402灯桩460403460403灯船460404460404浮标460405460405岸标、立标460406460406信号杆46060045020港口47010044031通航河段起讫点47020044020航海线47020044030航海线480100480100机场48010046010机场490200490200简易轨道490300490300架空索道490501490501火车渡49050145041火车渡490502490502汽车渡49050245042汽车渡490503490503人渡490504490504汽车徒涉场490505490505行人徒涉场510100510100高压输电线510401510401变电所520101520101陆地通信线(地上)520102520102陆地通信线(地下)530400530400地上管道530500530500地下管道530600530600架空管道610100610100国外区域610100920000国外区域610200610200国外地区国界线61020061019国外地区国界线620201620201国界线(已定)62020161010国界线(已定)62020161011国界线(已定)62020161012国界线(已定)62020161013国界线(已定)62020161014国界线(已定)62020161015国界线(已定)620202620202国界线(未定)62020261020国界线(未定)62020261025国界线(未定)620300620300国界桩、碑62030061011国界桩、碑630100630100省级行政区域63020061030省级界线63020061031省级界线63020061032省级界线63020061033省级界线63020061034省级界线63020061035省级界线63020061036省级界线63020061037省级界线63020061060省级界线63020061090省级界线630201630201省级界线(已定)630202630202省级界线(未定)630300630300省级界桩、碑63030061031省级界桩、碑630400630400特别行政区界640100640100地级行政区域64020061040地级界线64020061041地级界线64020061042地级界线64020061043地级界线64020061044地级界线64020061045地级界线64020061047地级界线640201640201地级界线(已定)640202640202地级界线(未定)640300640300地级界桩、碑650100650100县级行政区域65020061050县级界线65020061051县级界线65020061052县级界线65020061053县级界线65020061054县级界线65020061055县级界线65020061057县级界线650201650201县级界线(已定)650202650202县级界线(未定)650300650300县级界桩、碑65030061051县级界桩、碑670101670101自然、文化保护区67010162020自然、文化保护区670102670102自然、文化保护区界67010262020自然、文化保护区界67010262021自然、文化保护区界67010262023自然、文化保护区界67010262025自然、文化保护区界670201670201特殊地区界域670202670202特殊地区区线67020262010特殊地区区线670401670401开发区、保税区670402670402开发区、保税区界线71010071010等高线71010071011等高线71010071000等高线71010071040等高线71010071012等高线71010071020等高线710101710101等高线(首曲线)710102710102等高线(计曲线)71010271010等高线(计曲线)710103710103等高线(间曲线)71010371011等高线(间曲线)710104710104等高线(助曲线)71010571000退化等高线71020071020草绘等高线710201710201草绘等高线(首曲线)710202710202草绘等高线(计曲线)71030071012雪山等高线71030071021雪山等高线71030071030雪山等高线710301710301雪被冰川等高线(首曲线) 710302710302雪被病床等高线(计曲线)71030371030雪被上退化等高线720100720100高程点72010072010高程点730200730200等深线73020027070等深线73020027071等深线73020027072等深线73020127070退化等深线740100740100水深点74010027060水深点740300740300干出高度点75010072011峰、柱750101750101岩峰750102750102黄土柱750103750103独立石750104750104土堆750105750105石堆750201750201岩溶漏斗750202750202黄土漏斗750203750203坑穴75020476030溶斗750300750300山洞、溶洞750400750400火山口75040078010火山口750501750501冲沟75050175010冲沟75050175011冲沟75050371030过冲沟陡崖等辅助线750601750601土质陡崖、土质有滩陡岸750602750602石质陡崖、石质有滩陡岸750603750603土质无滩陡岸750604750604石质无滩陡岸75060525060有滩陡岸75060625070无滩陡岸750701750701陡石山750702750702露岩地750703750703岩墙750801750801平沙地75080177020平沙地750802750802灌丛沙堆750803750803新月形沙丘75080377030新月形沙丘750804750804垄状沙丘75080477050垄状沙丘750805750805窝状沙丘75080577060窝状沙丘75080877100多小丘沙地750900750900雪山75090073012雪山75090073010雪山75090273020冰川751001751001沙土崩崖751002751002石崩崖751003751003滑坡751004751004泥石流751005751005熔岩流760200760200田坎、路堑、沟堑、路堤、单坡堤760401760401石垄760402760402土垄760501760501防风固沙石方格760502760502防风固沙草方格810302810302旱地810306810306水田810400810400园地810501810501成林810502810502幼林810503810503灌木丛810504810504竹林810505810505疏林810506810506迹地810507810507苗圃810508810508防火带810509810509零星树木810510810510行树、狭长林带810511810511独立树810512810512独立树丛810601810601高草地810602810602草地810603810603半荒草地810604810604荒草地820000820000城市绿地830100830100盐碱地830200830200小草丘地830301830301龟裂地830401830401沙砾地、戈壁地83040177150沙砾地、戈壁地830402830402石块地830403830403残丘地840404840404沙泥地91010186000沼泽戈壁盐碱地沙漠范围。
中国标准文献分类号CCS

中国标准文献分类号CCS中国标准文献分类法(中标分类CCS)代码名称A综合B农业、林业C医药、卫生、劳动保护D矿业E石油F能源、核技术G化工H冶金J机械K电工L电子元器件与信息技术M通信、广播N仪器、仪表P土木、建筑Q建材R公路、水路运输S铁路T车辆U船舶V航空、航天W纺织X食品Y轻工、文化与生活用品Z环境保护代码名称类注释A00/09标准化管理与一般规定AA10/19经济、文化AA20/39基础标准AA40/49基础学科AE20/29石油天然气EE30/49石油产品EE60/69石油产品添加剂EE90/99石油勘探、开发、集输设备E石油炼制设备入G90/93。
F00/09能源、核技术综合F各种能源综合性标准入本类F00/09。
常规能源:煤炭入D20/24,石油、天然气入E20/27,燃料油入E31,电工基础和产品标准(含电力)入K类。
用于生产、流通过程中保证符合文字标准要求的核技术标样分别入本类各有关类目。
综合性、系统性的电力标准入此。
F10/19能源FF20/29电力F电站、输配电工程入P类。
F40/49核材料、核燃料FF50/59同位素与放射源FF60/69核反应堆FF70/79辐射防护与监测FF80/89核仪器与核探测器F通用的仪器、仪表入N类。
F90/99低能加速器FG00/09化工综合G造纸入Y30/39,皮革入Y45/49,食品发酵、酿造入X60/69,绝缘漆入K15,食品添加剂入X40/49,合成饲料添加剂入B46,建筑胶粘剂入Q27,胶鞋入Y78。
用于生产、流通过程中保证符合文字标准要求的化工标样分别入本类各有关类目。
G10/14无机化工原料GG15/19有机化工原料GG20/29化肥、农药GG30/39合成材料G合成树脂、塑料、橡胶及胶粘剂等。
建筑用塑料制品入Q22,日用塑料制品入Y28,塑料鞋入Y75或Y78。
G40/49橡胶制品及其辅助材料G胶鞋入Y78。
G50/59涂料、颜料、染料GG60/69化学试剂G化学分析用标准物质入A65。
2014年高考大纲全国卷语文真题(word清晰版)

2014年普通高等学校招生全国统一考试(全国大纲卷)语文试题第Ⅰ卷一、(12分,每小题3分)1.下列词语中加点的字,读音全都正确的一组是(B)A.龃龉.(yǔ) 系.鞋带(xi) 舐.犊情深(shi) 曲.意逢迎(qū)B.倜傥.(tǎng) 纤.维素(xiān) 羽扇纶.巾(guān ) 针砭.时弊(biān)C.感喟.(kuì) 揭疮.疤(chuāng) 按捺.不住(nài) 大相径.庭(jing)D.霰.弹(xiàn ) 涮.羊肉(shuàn) 以儆.效尤(jǐng) 纵横捭.阖必(bì)2.下列各句中,加点的成语使用恰当的一项是(A)A.在评价某些历史人物时,我们不能只是简单地对他们盖棺论定....,,还应该特别注意研究他们的人生经历和思想变化轨迹。
B.这把吉他是我最要好的朋友出国前存在我这里的,本来说存一年,结果朋友一直没回来,这吉他到现在巳经由我敝帚自珍....了十年。
C.最美的是小镇的春天,草长莺飞,风声鹤唳....,走进小镇就如同置身于世外桃源,来此旅游的人一定会被这里的美丽景色深深吸引。
D.这个剧院的大型话剧、歌剧等演出票价不菲,让许多有艺术爱好而又收入不高的普通人叹为观止....,无法亲临现场享受艺术大餐。
3.下列各句中,没有语病的一句是答:DA.有的人看够了城市的繁华,喜欢到一些人迹罕至的地方去游玩,但这是有风险的,近年来已经发生了多次背包客被困野山的案情。
B.他家离铁路不远,小时候常常去看火车玩儿,火车每当鸣着汽笛从他身边飞驰而过时,他就很兴奋,觉得自己也被赋予了一种力量。
C.新“旅游法”的颁布实施,让很多旅行社必须面对新规定带来的各种新问题,不少旅行社正从过去拼价格向未来拼服务转型的阵痛。
D.哈大高铁施行新的运行计划后,哈尔滨至北京、上海等地的部分列车也将进一步压缩运行时间,为广大旅客快捷出行提供更多选择。
4.依次填人下面一段文字横线处的语句,衔接最恰当的一组是答:C信息时代给人们带来了一种新的极其便捷的阅读方式,那就是网络阅读。
HwAN_PNX490x_Audio_Tuning_CTA_pxxxxx_V1_0
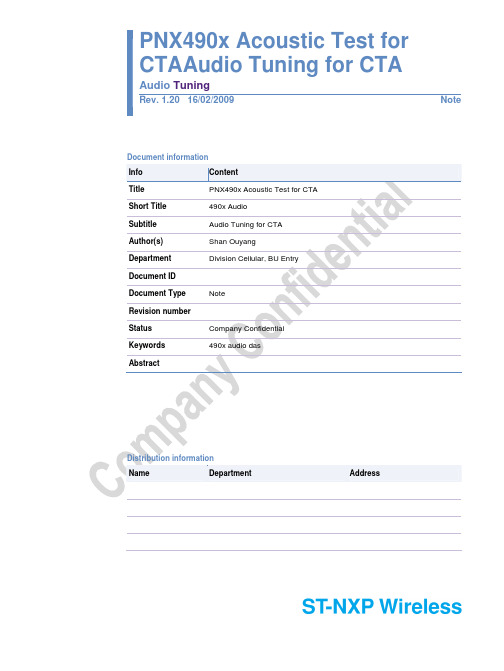
PNX490x Acoustic Test for CTAAudio Tuning for CTAAudio TuningRev. 1.20 16/02/2009NoteDocument informationInfo ContentTitle PNX490x Acoustic Test for CTAShort Title 490x AudioSubtitle Audio Tuning for CTAAuthor(s) Shan OuyangDepartment Division Cellular, BU EntryDocument IDDocument Type NoteRevision numberStatus Company ConfidentialKeywords 490x audio dasAbstractDistribution informationName Department AddressST-NXP wireless490x AudioAudio TuningContact informationFor additional information, please visit: Revision history Rev Date Description 1.0 20090216 Creation1. Content1.Content (3)2.Abbreviations (4)3.References (4)4.Introduction (5)5.Introduction of Audio Test in China TypeApproval (5)5.1Specifications (5)5.2Test items of CTA (5)6.Hardware and Software requirements (6)6.1Test Setup (6)6.2List of Equipment (6)6.3Audio Tuning Tools (7)7.Audio Tuning Procedures (7)7.1Tuning of Receive Frequency Response(RFR) (9)7.2Tuning of Receive Loudness Rating (RLR) (11)7.3Tuning of Send Frequency Response(SFR) (12)7.4Tuning of Send Loudness Rating (SLR) (13)7.5Tuning of Sidetone Masking Rate (STMR)14 7.6Tuning of Sending Distortion (15)7.7Tuning of Receive Distortion (17)7.8Tuning of Idle Channel Noise Receiving (18)7.9Tuning of Idle Channel Noise Sending (18)7.10Tuning of Acoustic Echo Control (AEC) (19)8.Legal information (19)8.1Disclaimers (19)2. AbbreviationsAcronym DescriptionAudioMon PC software used to adjust the audio subsystem. Version 2.44 and aboveshould be used with 4902.PGA Programmable Gain AmplifierCODEC Basically COder DECoder but used in the document as “DAC+ADC”LRGP Loudness Rating Guardring PositionERP Ear Reference PointMRP Mouth Reference Point3. References[1] Hw_UM_PNX490x_Audio_Mon_User_Manual_p23958.pdf : AudioMon user manual[2] Hw_ApplicationNote_PNX4902_Audio_Subsystem_p28595 : Audio structures and performance presentation[3] YD/T 1538-2006, Technical Requirements and Testing Methods for Acoustics Performance of Digital Mobile Terminal[4] 3GPP TS26.131, TS26.1324. IntroductionThis document helps readers understand audio test and gives guidelines how to tune the audio parameters of platform to pass audio tests of China Type Approval.5. Introduction of Audio Test in China Type ApprovalAll the mobile terminals sold in China market need to pass China type approval (CTA). The main test authority named CTTL (China Telecommunication Technology Labs) which Located in Beijing.5.1 SpecificationsThe Chinese national standard YD/T1538-2006 is followed by CTA. It has the same requirements with other international specifications which are:FTA: 3GPP TS 51.0103GPP TS 26.131 & TS 26.132ITU-T: P.51, P.57, P.58, P.64, P.67...5.2 Test items of CTACurrently seven items need to be tested in CTA and six of them must pass the test.Sending Frequency Response (SFR)Sending Loudness Rating (SLR)Receiving Frequency Response (RFR)Receiving Loudness Rating (RLR) nom volReceiving Loudness Rating (RLR) max volSide tone Masking Rating (STMR)Distortion SendingAlso following additional items were required by CTTL from Jan.1 2009.Distortion ReceivingEcho Loss (EL)Idle Channel Noise Receiving nomIdle Channel Noise Receiving maxIdle Channel Noise SendingStability MarginNote 3GPP TSTest name Requirement26.131CTA 5.4.1 Sending frequency response (Template)CTA 5.2.2 Sending loudness rating (SLR) 5...11 dBCTA 5.4.2 Receiving frequency response (Template)CTA 5.2.2 Nom. Receiving loudness rating (RLR) -1...5 dBCTA 5.2.2 Max. Receiving loudness rating (RLR) ≥ -13 dBCTA 5.5.1 Side Tone Masking Rating (STMR) 15...23 dBNew 5.7.1 Acoustic Echo Control ≥ 46 dBNew 5.6 Stability Loss (Nooscillation)CTA 5.8.1 Distortion – Sending (Template)New 5.8.2 Distortion – Receiving (Template)New 5.3.1 Idle noise – Sending -64dBNew 5.3.2 Idle noise – Receiving (Nominal) -57 dBNew 5.3.2 Idle noise – Receiving (Maximum) -54 dB6. Hardware and Software requirements6.1 Test SetupThe audio test can be conducted via DAI interface or air interface. Nowadays air interface is more popular and is used in CTA. Below is the typical test setup:6.2 List of EquipmentBelow are equipments using in STN Shanghai.Rhode & Schwarz UPV. (CTA is using ACQUR from Head Acoustic)Rhode & Schwarz CMU 200Artificial EarArtificial Ear ITU type 1: B&K Type 4185Artificial Ear ITU type 3.2: B&K Type 4195Artificial Mouth. B&K Type 4227Telephone Test Head: B&K Type 4602BSound level calibrator B&K Type 4231Microphone power-supply: B&K 2690A0S2The terminal under test, artificial mouth and ear should be put together into an acoustic chamber.6.3 Audio Tuning ToolsAll the audio parameters of terminal are stored in flash memory. A PC tool TAT (Test and Auto Test) is used to read, edit, import and export the audio parameters.AudioMon is another PC tool which is used to modify audio parameters on the fly. Detailed user guide please refer to reference.7. Audio Tuning ProceduresChosen settings of the audio parameters are stored in audio data section of flash memory. It is normallynecessary to have different settings of the audio parameters for different audio accessories connected to the mobile terminal (for example normal usage using the internal microphone and earphone, portable headset, loudspeaker, Bluetooth® headset, and so on). Hence, normally one pair of dedicated data sections called DSPTxOrgan[x] & DSPRxOrgan[x] should be prepared for each audio accessory used.Since FTA/CTA only test headset mode which only DSPTxOrgan[0] (main mic) and DSPRxOrgan[0] (main speaker) is involved, the following descriptions are all refer to DSPOrgan[0].Before first audio tuning, the default audio parameters has been stored in the mobile terminal with original delivery.After mounting the terminal in test set and a call was established between terminal and CMU200, audio tuning can be start. It is recommended that the tuning executed in the following common order:31.2.3. After tuning parameters, reread all parameters from terminal RAM into other active memo.4. Save the active memo to a file which will contain new parameters.5. Use TAT to import new parameters into terminal flash memory.Before continuing with the actual tuning it is recommended that the reader gets familiar with related 3GPP specifications, R&S equipments operation and NXP testing tools.TIP:During audio test, MS signal power level of CMU200 should be set as PCL 12 in GSM900.7.1 Tuning of Receive Frequency Response (RFR)This section describes how to tune frequency response in the audio receive path.7.1.1 DescriptionThe input frequency response is specified as the transmission ratio in dB of the sound pressure in the artificial ear to the input voltage at the voice coder input of CMU200.The mobile under test is installed in the LRGP position (ITU-T P.76) and the speaker is sealed to the artificial ear.The voice coder is driven so that tones with an internal reference level of -16 dBm0 are obtained. The noisepressure in the artificial ear is measured and evaluated.If type 1 artificial ear is used, The receiving frequency response must be within the limit lines specified in table30.2 of 3GPP TS51.010. The absolute sensitivity is not yet taken into account.Frequency (Hz) Upper Limit (dB) Lower Limit (dB)100 -12 -200 0 -300 2 -7500 - -51000 0 -53000 2 -53400 2 -104000 2 -Note 1: All sensitivity values are expressed in dB on a coordinate axis.Note 2: The limit of “-” lies on a straight line drawn between the breaking points on alogarithmic (frequency)/linear (dB sensitivity) coordinate.Limit lines according to 3GPP TS51.010 table 30.2If type 3.2 artificial ear is used, The receiving frequency response must be within the limit lines specified in table2 of 3GPP TS26.131.Frequency (Hz) Upper Limit (dB) Lower Limit (dB)70 -10 -200 2 -300 - -9500 - -1000 - -73000 - -3400 - -124000 2 -Note 1: All sensitivity values are expressed in dB on a coordinate axis.Note 2: The limit of “-” lies on a straight line drawn between the breaking points on a logarithmic(frequency)/linear (dB sensitivity) coordinate.Limit lines according to 3GPP TS26.131 table 2The offset of the measured frequency response to the upper or lower limit curve is calculated and then the total curve is shifted by the mean value of the maximum and minimum offset. Then another limit check is performed.If the shifted curve is within the limit lines, PASS is output, otherwise FAIL is output. The limit check isperformed at each measured frequency. If the measured value and the end point of a limit curve are not at the same frequency, it may happen that the trace slightly crosses a corner of the limit trace although there are no limit violations.7.1.2 Procedure1. Turn off Downlink FIR&IIR filters in AudioMonDSP config section.2. Measure RFR and save curve to a file. Usethe PC which running AudioMon to open the data file and copy the curve data to clipart. The data format is like below: 100 1.36016106 1.98170455736302 112 2.45548160024953…3550 4.3738710304971 3750 -1.80146960957754 4000 -14.517183. Open filter design wizard of AudioMon. ① Flat both FIR and IIR filters. ② Paste measured spectrum ③ Select limit mask as TS26.131 ④ Press FIR auto correct⑤ If FIR auto calculation is ok then press OKbutton. FIR coefficients will be present in Filter section of AudioMon. Also some fine tuning may be implemented manually. ⑥ If FIR auto calculation is not ok then may needadjust IIR filters manually to compensate the lower spectrum first. ⑦ Repeat step 4 to 6 till the compensatedspectrum in limit mask.4. Turn on Downlink FIR&IIR filters in AudioMonDSP Config section. Enable DL filter coefficients and send them to target.5. Measure the frequency response again. Theactually measured spectrum may not same as calculated by AudioMon. If the frequency response is still fail, manually trim filters at some frequency points by using filter wizard.7.2 Tuning of Receive Loudness Rating (RLR)This section describes how to tune loudness rating in the audio receive path.7.2.1 DescriptionThe receiving loudness rating (RLR) takes into account the absolute loudness in the receive direction and weights the tones in compliance with the normal sensitivity of the average human ear. The RLR is calculated at frequency bands 4 to 17 according to Table 1 of ITU-T P.79. 200250315400500630 800 1000 1250 1600 2000 2500 3150 4000The RLR depends on the receive loudness set on the ME under test and according to 3GPP TS 26.131, should be between -1 dB and +5 dB at a rated loudness setting, with lower decibel values corresponding to greater loudness (-1 dB = maximum loudness, +5 dB = minimum loudness).7.2.2 ProcedureRLR should be tuned after RFR.1. Make sure volume is set as normal. MeasureRFR.2. In case the measured RLR does not fall within thespecified limits (RLR = 2±3 dB). There are two programmable gains in receive path can be used to compensate it. If the measured RLR is less than -1dB, gains should be reduced. If themeasured RLR is higher than 5dB, gains should be increased.① DSP gain may involve digital distortion whichmay cause receive distortion failed in high sound pressure. It’s better to keep DSP DL gain no higher than 6dB. ② FIR filter gain also can be used adjust thewhole spectrum loudness. If the measured RLR is not far away thespecified limits. Tune the frequency response to change the weight of tones also can reach the target. But the RFR must keep in the mask.DSP DL GainFIR filter gain3. It’s better to trim RLR within 3~4dB which is incompliance with requirement and benefits to idle channel noise and echo loss test cases.7.3 Tuning of Send Frequency Response (SFR)This section describes how to tune frequency response in the audio send path.7.3.1 DescriptionThe send frequency response is specified as the transmission ratio in decibel of the voltage at the decoder output to the input noise pressure at the artificial mouth.The mobile terminal under test should be installed in the LRGP according to ITU-T P.76 and the speaker must be sealed to the artificial ear.Tones with a sound pressure of -4.7 dBPa are created with an artificial mouth at the Mouth Reference Point (MRP), and the corresponding output voltage is measured at the instrument voice coder (for example, CMU) output and evaluated.The send frequency response must be within the tolerance mask specified according to below table. The maskis drawn with straight lines between the breaking points in the table on a logarithmic (frequency)/linear (dBSensitivity) coordinate. Test results shall be within the mask.Frequency (Hz) Upper Limit Lower Limit100 -12 -200 0 -300 0 -121000 0 -62000 4 -63000 4 -63400 4 -94000 0 -Note 1: All sensitivity values are expressed in dB on a coordinate axis.Note 2: The limit of “-” lies on a straight line drawn between the breaking points on a logarithmic(frequency)/linear (dB sensitivity) coordinate.7.3.2 ProcedurePlease refer to section 7.1.2 (RFR tuning procedure). The difference is the tuning is in audio uplink path.7.4 Tuning of Send Loudness Rating (SLR)This section describes how to tune loudness rating in the audio send path.7.4.1 DescriptionThe send loudness rating (SLR) takes into account the absolute loudness in the transmit direction and weights the tones in compliance with the normal sensitivity of the human ear.The SLR is calculated at frequency bands 4 to 17 according to Table 1 of ITU-T P.79.According to 3GPP TS26.131 the send loudness rating should be between 5 dB and 11 dB, with lower decibel-values corresponding to greater loudness (5 dB = maximum loudness, 11 dB = minimum loudness).7.4.2 ProcedureThe main procedure can refer to section 7.2.2 (RLR tuning procedure) but there are some differences.Except DSP UL gain and UL FIR gain, a two stage PGA is in analog part. Too high gain of analog PGA may cause MIC saturated or involve much noise in uplink path.A noise suppress function in DSP is recommended to turn on which benefits to idle channel noise performance.But this function will reduce sending loudness significantly. It has to be compensated by increase digital gains.Details of noise suppressor please have a look at reference.7.5 Tuning of Sidetone Masking Rate (STMR)This section describes how to tune the sidetone masking rating (STMR).7.5.1 DescriptionThe so-called sidetone path is the desired output from the part of the signal picked up by the microphone from the phone's speaker. We need sidetone because if we cannot hear ourselves during a call, our brain refuses to accept that anyone else can hear us and we tend to speak too loudly.The artificial mouth generates tones with a sound pressure of -4.7 dBPa at the MRP, and the sound pressure is measured in the artificial ear.When the mobile terminal is set to the rated receiving loudness, the STMR should be between 18±5 dBaccording to 3GPP TS 26.131.TIP:According to the old spec (TS 51.010), STMR requirement has been 13±5 dB. Please note this has been modified in new spec which applies in CTA.A high level of sidetone has a significant effect on the use of the mobile terminal in high ambient noiseconditions, making received speech extremely difficult to recognize.Sidetone is related to SLR and RLR. Any attempt to change them to achieve compliance with loudness rating requirements can also have a marked effect on sidetone performance.7.5.2 Procedure1. Active sidetone in audio path of AudioMon CodecConfig section.2. Measure STMR in UPV, adjust sidetone gain inAudioMon Codec Misc section till the measuredSTMR is between 13~23dB.7.6 Tuning of Sending DistortionThis section describes how to tune sending distortion.7.6.1 DescriptionThe S/N ratio in the transmit path is measured as a function of the sound level.A sine-wave signal with a frequency in the range of 1004Hz to 1025Hz shall be applied in the test. The level ofthis signal at the MRP shall be adjusted until the output of the terminal is -10dBm0. The level of the signal at the MRP is then the ARL.The ratio of the signal to total distortion power (SINAD value) of the received signal is measured at the CMU’s decoder output. The SINAD value is measured at sound pressures between -35 dB and +10dB relative to the acoustic reference level ARL and compared with the limit lines specified in table as belowLevel Relative to ARL Sending Level Ratio (dB)-35 17.5-30 22.5-20 30.7-10 33.30 33.7+7 31.7+10 25.5Limits for intermediate levels are found by drawing straight lines between the breaking points in the table on a linear (dB signal level)/linear (dB ratio) coordinate.7.6.2 ProcedureMeasure the sending distortion in UPV. According to the result, there are there scenarios to be analyzedrespectively.1. The curve failed in high sound pressure part. The distortion mainly caused by signal distortiondue to too high amplifier gain in uplink path. Reduce a certain PGA gain can resolve this problem.2. The curve failed in low sound pressure part and the failure is very significant (normally around20dB to the limit). This can be concluded the test signal is removed by uplink noise suppressor inDSP. Tune noise suppressor parameters can resolve this problem.3. The curve failed in low sound pressure part and the failure is slight. The reason is very complex. Mainlycaused by noise in MIC circuit. Optimize MIC circuit or replace MIC itself is helpful.Also it is worth to retrim sending frequency response. The main part of MIC noise is in lower frequency (217Hz and the harmonics) and the test signal is around 1K Hz. Thus, reduce lower frequency weight and increase 1KHz weight in spectrum can improve the S/N rate. Below are some examples:7.7 Tuning of Receive DistortionThis section describes how to tune receive distortion.7.7.1 DescriptionFor handset terminal, headset terminal, handheld hands-free terminal and Desktop-operated hands-freeterminal, when RLR is equal to the nominal value, receiving distortion shall be measured between MRP and the input port of the reference speed coder/decoder of the SS.The ratio of signal-to-total distortion power measured with the proper noise weighting (see Table 4 of ITU-T Recommendation G.223) shall be above the limits given in below table. For sound pressures ≥+10dBPa at the ERP there is no requirement on distortion.Receiving Level at Digital Interface of the TestedReceiving Level Ratio (dB)Apparatus (dBm0)-45 17.5-40 22.5-30 30.5-20 33.0-10 33.5-3 31.20 25.5Limits for intermediate levels are found by drawing straight lines between the breaking points on a linear (dB signal level)/linear (dB ratio) coordinate.7.7.2 ProcedureThe tuning method is very similar with tuning sending distortion. Please refer to section 7.6.2.The lower sound pressure part failure may caused by improper setting of Noise Gate.The high sound pressure part failure may caused by two high PGA gain setting especially the DSP DL gain.7.8 Tuning of Idle Channel Noise ReceivingThis section describes how to tune the idle channel noise receiving.7.8.1 DescriptionThe sound pressure in the artificial ear is measured with the mobile terminal set up in a quiet environment (<30 dB(A)).The sound pressure in the artificial ear is measured with A-weighting on.With optimum volume set on the mobile, the sound pressure should not exceed -57 dBPa(A).At maximum volume, the sound pressure should not exceed -54 dBPa(A).This measurement makes high demands on the sound insulation of the test chamber and the S/N ratio of the measuring microphone including preamplifier in the artificial ear. The artificial ear is observed sensitive withTDD noise. Please make sure the mobile power level is PCL12 and keep the cable of artificial ear as short as possible exposing in RF.7.8.2 ProcedureWith proper RLR, RFR and noise gate settings, normally no more tuning needed for this test case.If audio parameter modification still can not make the test pass, add two serial 10 Ohm resistors in receiver path should be considered.7.9 Tuning of Idle Channel Noise SendingThis section describes how to tune the idle channel noise sending.7.9.1 DescriptionThe noise voltage at the voice decoder output is measured with the mobile terminal set up in a quietenvironment (< 30 dB(A)).The decoder output voltage is measured, psophometrically weighted according to ITU-T G.223 and calculated at the internal level in dBm0p.The idle noise level should not exceed -64 dBm0p.7.9.2 ProcedureWith proper SLR, SFR and noise suppressor settings, normally no more tuning needed for this test case.7.10 Tuning of Acoustic Echo Control (AEC)This section describes how to tune the acoustic echo control. It has been said Echo Loss (EL) in 3GPP TS51.010.7.10.1 DescriptionThe AEC is the attenuation between the voice coder input and the voice decoder output. Normally the echocaused by internal acoustic coupling between the mobile phone receiver and the microphone. Since the echo considerably reduces the sound transmission quality, it should not exceed a certain value. 3GPP TS26.131specifies an echo loss of at least 46 dB.To obtain realistic results, an artificial voice is used for the echo loss test. Before the actual test, a trainingsequence consisting of 10s artificial voice (male) and 10s artificial voice (female) according to ITU-TRecommendation P.50 shall be applied.7.10.2 ProcedureEcho loss is measured on maximum volume.With default acoustic template, the echo canceller and echo suppressor are active. EL test case should be no problem to pass. But if the terminal under test has problems in mechanic design, there is not a full isolationbetween MIC and receiver within the mechanic for example, EL will fail. In this case, the best solution is tooptimize mechanic. But if change mechanic is impossible, reduce the RLR in maximum volume, increaseattenuation of ES are also considered.8. Legal information8.1 DisclaimersGeneral _Information in this document is believed to be accurate and reliable. However, ST-NXP wireless does not give any representations or warranties,expressed or implied, as to the accuracy or completeness of such information and shall have no liability for the consequences of use of such information.Right to make changes _ ST-NXP wireless reserves the right to make changes to information published in this document, including without limitationspecifications and product descriptions, at any time and without notice. This document supersedes and replaces all information supplied prior to the publication hereof.Suitability for use _ ST-NXP wireless Semiconductors products are not designed, authorized or warranted to be suitable for use in medical, military, aircraft, space or life support equipment, nor in applications where failure or malfunction of a NXP Semiconductors product can reasonably be expected to result inpersonal injury, death or severe property or environmental damage. ST-NXP wireless accepts no liability for inclusion and/or use of ST-NXP wireless products in such equipment or applications and therefore such inclusion and/or use is at the customer’s own risk.Applications _ Applications that are described herein for any of these products are for illustrative purposes only. ST-NXP wireless makes no representation or warranty that such applications will be suitable for the specified use without further testing or modification.ST-NXP wireless 490x AudioAudio TuningNotesHwAN_PNX4902_Audio_Subsystem © NXP Semiconductors 2007. All rights reserved. Application note Rev. 1.2— 27/11/0821 of 21。
Informix错误代码中文解释

所有错误可以用finderr+错误代码查到,英文的,这里中文注释便于理解。
-100 错误的描述:C—ISAM错误;向具有唯一索引的字段加入一个重复值。
系统的操作:该语句不被处理。
更正的方法:检查是否用iswrite,isrewrite,isrewcurr或isaddindex的方法,向一个具有唯一索引的字段加入一重复值。
-101 错误的描述:C-ISAM错误;文件没有打开。
系统的操作:该语句不被处理。
更正的方法:检查C-ISAM错误:C-ISAM文件是否已用isopen调用打开,或者是否向一个以只读打开的C-ISAM文件中执行写操作。
-102 错误的描述:C—ISAM错误:C—ISAM函数含有非法参数系统的操作:该语句不被处理更正的方法:检查C—ISAM调用的第一个参数,是否超出相应的值域-103 错误的描述:C—ISAM错误;非法的关键字说明(太多的分量或太长)系统的操作:该语句不被处理。
更正的方法:检查组成该关键字说明的一个或多个元素,是否超出相应的值域。
(每个关键字的说明最多允许8个分量和120个字符)-104 错误的描述:C—ISAM错误:打开文件太多系统的操作:该语句不被处理。
更正的方法:在UNIX系统中(以及多数DOS系统中),每个进程打开文件夹的最大个数为20。
-105 错误的描述:C—ISAM错误:C—ISAM文件格式有误。
系统的操作:该语句不被处理。
更正的方法:C—ISAM文件的格式已被破坏,对该文件运行bcheck程序,修复被破坏了的索引。
如果bcheck不能修复该文件,须从后援存储介质上重新装入数据。
-106 错误的描述:C—ISAM错误;非互斥访问。
系统的操作:该语句不被处理。
更正的方法:当要增加或删除一个索引时,必须以互斥访问打开文件。
-107 错误的描述:C—ISAM错误:记录被锁住。
系统的操作:该语句不被处理。
更正的方法:由该调用请求的文件或记录不能被访问,这是因为该文件被其它用户锁住。
visual-basic-题库

Visual basic题库一、单项选择题(34道小题,共34分)1、Byte型数据的长度是( )字节。
(1分)A、2B、1C、4D、82、Integer型数据的长度是( )字节。
(1分)A、1B、2C、4D、83、以下变量名正确的是( ) 。
(1分)A、aB、sinC、a#bD、a%b4、下列数据是常量的是( )。
(1分)A、aB、2C、piD、M5、下列数据是常量的是( )。
(1分)A、aB、#8/8/2008#C、piD、M6、使用语句Dim a(2) As String 声明数组a之后,以下说法正确的是()。
(1分)A、a数组中的所有元素值都为0B、a数组中的所有元素值不确定C、a数组中的所有元素值都为EmptyD、a数组中的所有元素值都为"",即为空字符串。
7、声明一个第二维上界为5的二维整型数组,正确的是()。
(1分)A、Dim a(5,4) As IntegerB、Dim a(6,5) As IntegerC、Dim a(4,3) As IntegerD、Dim a(3,2) As Integer8、语句Dim A(5,6) As Integer ,则所定义的数组A中共有( )个元素。
(1分)A、30B、42C、20D、259、变量a的类型为Double,有赋值语句a=10.3/2,则a的值为()。
(1分)A、5B、6C、5.15D、5.210、变量L的值为-8,则-L^2的值为()。
(1分)A、64B、-64C、16D、-1611、求正切值的函数是( )。
(1分)A、absB、expC、logD、tan12、求以e为底对数值的函数是( )。
(1分)A、absB、expC、logD、tan13、去除符号串左右两边的空格的函数是( )。
(1分)A、lenB、leftC、midD、trim14、Int(10*Rnd()+3)产生的数据范围是( )。
(1分)A、[3,12]B、[3,13]C、(0,1)D、(3,100)16、Fix(2.5)的结果是( )。
质量管理学复习试题及答案概要

一、填空1.所有取值能一一列出的随机变量称为(离散型随机变量)。
2.在质量管理中, 正态分布确定的参数σ越小,表明质量的( 一致性 ) 越好。
3.已知总体为N(、2), 则样本平均数的数字特征值与总体的数字特征值的关系是: E(样本平均数)=( μ) , D(样本平均数)=( σ2/n )。
4.控制图采用3σ为控制界限, 是因为在该点(错发警报)的错误和(漏发警报)的错误造成的总损失最小。
5.X控制图是用来反映和控制产品质量数据( 集中趋势)的变化的。
6.X控制图的上控制界限为(X~+m3 A2R)。
7.表示(相邻观察数据)相差的绝对值被称为移差。
8.抽样后在控制图上打点, 出现连续7点上升, 被称为: ( 单调链)。
9.推动PDCA循环的关键是(执行)阶段。
10.因果图中的( 特性)指生产过程或工作过程中出现的结果。
11.当分布中心, 与公差中心偏离了, 修正后的过程能力指数()。
1.预防周期性维护方式的特点是: 定期全面进行(预检预修)工作。
2.选控的概念是将系统因素进一步划分为: (非控系统因素)和(欲控系统因素)。
3.质量体系就是为了达到(质量目标)所建立的综合体。
4.二.单项选择题5.传统质量管理的主要特征是( A )。
A 按照规定的技术要求, 对产品进行严格的质量检验B 按照过去的经验进行质量检验C 按照领导的意图进行质量检验2000年版ISO9000族标准将由四项基本标准及若干份支持性技术报告构成。
四项基本标准中——ISO9001是: ( C )。
A质量体系审核指南 B 质量管理体系—指南C 质量管理体系—要求D 质量管理体系—概念和术语6.造成产品质量异常波动的原因是( B )。
A偶然性原因、B系统性原因、C不可避免的原因7.相关系数的取值范围是( D )。
A 0≤γ<1B 0≤γ≤1C − 1≤γ≤0D − 1≤γ≤1每吨铸件成本(元)和每一工人劳动生产率(吨)之间回归方程为y=270-0.5x。
3GPP TS 36.331 V13.2.0 (2016-06)

3GPP TS 36.331 V13.2.0 (2016-06)Technical Specification3rd Generation Partnership Project;Technical Specification Group Radio Access Network;Evolved Universal Terrestrial Radio Access (E-UTRA);Radio Resource Control (RRC);Protocol specification(Release 13)The present document has been developed within the 3rd Generation Partnership Project (3GPP TM) and may be further elaborated for the purposes of 3GPP. The present document has not been subject to any approval process by the 3GPP Organizational Partners and shall not be implemented.This Specification is provided for future development work within 3GPP only. The Organizational Partners accept no liability for any use of this Specification. Specifications and reports for implementation of the 3GPP TM system should be obtained via the 3GPP Organizational Partners' Publications Offices.KeywordsUMTS, radio3GPPPostal address3GPP support office address650 Route des Lucioles - Sophia AntipolisValbonne - FRANCETel.: +33 4 92 94 42 00 Fax: +33 4 93 65 47 16InternetCopyright NotificationNo part may be reproduced except as authorized by written permission.The copyright and the foregoing restriction extend to reproduction in all media.© 2016, 3GPP Organizational Partners (ARIB, ATIS, CCSA, ETSI, TSDSI, TTA, TTC).All rights reserved.UMTS™ is a Trade Mark of ETSI registered for the benefit of its members3GPP™ is a Trade Mark of ETSI registered for the benefit of its Members and of the 3GPP Organizational PartnersLTE™ is a Trade Mark of ETSI currently being registered for the benefit of its Members and of the 3GPP Organizational Partners GSM® and the GSM logo are registered and owned by the GSM AssociationBluetooth® is a Trade Mark of the Bluetooth SIG registered for the benefit of its membersContentsForeword (18)1Scope (19)2References (19)3Definitions, symbols and abbreviations (22)3.1Definitions (22)3.2Abbreviations (24)4General (27)4.1Introduction (27)4.2Architecture (28)4.2.1UE states and state transitions including inter RAT (28)4.2.2Signalling radio bearers (29)4.3Services (30)4.3.1Services provided to upper layers (30)4.3.2Services expected from lower layers (30)4.4Functions (30)5Procedures (32)5.1General (32)5.1.1Introduction (32)5.1.2General requirements (32)5.2System information (33)5.2.1Introduction (33)5.2.1.1General (33)5.2.1.2Scheduling (34)5.2.1.2a Scheduling for NB-IoT (34)5.2.1.3System information validity and notification of changes (35)5.2.1.4Indication of ETWS notification (36)5.2.1.5Indication of CMAS notification (37)5.2.1.6Notification of EAB parameters change (37)5.2.1.7Access Barring parameters change in NB-IoT (37)5.2.2System information acquisition (38)5.2.2.1General (38)5.2.2.2Initiation (38)5.2.2.3System information required by the UE (38)5.2.2.4System information acquisition by the UE (39)5.2.2.5Essential system information missing (42)5.2.2.6Actions upon reception of the MasterInformationBlock message (42)5.2.2.7Actions upon reception of the SystemInformationBlockType1 message (42)5.2.2.8Actions upon reception of SystemInformation messages (44)5.2.2.9Actions upon reception of SystemInformationBlockType2 (44)5.2.2.10Actions upon reception of SystemInformationBlockType3 (45)5.2.2.11Actions upon reception of SystemInformationBlockType4 (45)5.2.2.12Actions upon reception of SystemInformationBlockType5 (45)5.2.2.13Actions upon reception of SystemInformationBlockType6 (45)5.2.2.14Actions upon reception of SystemInformationBlockType7 (45)5.2.2.15Actions upon reception of SystemInformationBlockType8 (45)5.2.2.16Actions upon reception of SystemInformationBlockType9 (46)5.2.2.17Actions upon reception of SystemInformationBlockType10 (46)5.2.2.18Actions upon reception of SystemInformationBlockType11 (46)5.2.2.19Actions upon reception of SystemInformationBlockType12 (47)5.2.2.20Actions upon reception of SystemInformationBlockType13 (48)5.2.2.21Actions upon reception of SystemInformationBlockType14 (48)5.2.2.22Actions upon reception of SystemInformationBlockType15 (48)5.2.2.23Actions upon reception of SystemInformationBlockType16 (48)5.2.2.24Actions upon reception of SystemInformationBlockType17 (48)5.2.2.25Actions upon reception of SystemInformationBlockType18 (48)5.2.2.26Actions upon reception of SystemInformationBlockType19 (49)5.2.3Acquisition of an SI message (49)5.2.3a Acquisition of an SI message by BL UE or UE in CE or a NB-IoT UE (50)5.3Connection control (50)5.3.1Introduction (50)5.3.1.1RRC connection control (50)5.3.1.2Security (52)5.3.1.2a RN security (53)5.3.1.3Connected mode mobility (53)5.3.1.4Connection control in NB-IoT (54)5.3.2Paging (55)5.3.2.1General (55)5.3.2.2Initiation (55)5.3.2.3Reception of the Paging message by the UE (55)5.3.3RRC connection establishment (56)5.3.3.1General (56)5.3.3.1a Conditions for establishing RRC Connection for sidelink communication/ discovery (58)5.3.3.2Initiation (59)5.3.3.3Actions related to transmission of RRCConnectionRequest message (63)5.3.3.3a Actions related to transmission of RRCConnectionResumeRequest message (64)5.3.3.4Reception of the RRCConnectionSetup by the UE (64)5.3.3.4a Reception of the RRCConnectionResume by the UE (66)5.3.3.5Cell re-selection while T300, T302, T303, T305, T306, or T308 is running (68)5.3.3.6T300 expiry (68)5.3.3.7T302, T303, T305, T306, or T308 expiry or stop (69)5.3.3.8Reception of the RRCConnectionReject by the UE (70)5.3.3.9Abortion of RRC connection establishment (71)5.3.3.10Handling of SSAC related parameters (71)5.3.3.11Access barring check (72)5.3.3.12EAB check (73)5.3.3.13Access barring check for ACDC (73)5.3.3.14Access Barring check for NB-IoT (74)5.3.4Initial security activation (75)5.3.4.1General (75)5.3.4.2Initiation (76)5.3.4.3Reception of the SecurityModeCommand by the UE (76)5.3.5RRC connection reconfiguration (77)5.3.5.1General (77)5.3.5.2Initiation (77)5.3.5.3Reception of an RRCConnectionReconfiguration not including the mobilityControlInfo by theUE (77)5.3.5.4Reception of an RRCConnectionReconfiguration including the mobilityControlInfo by the UE(handover) (79)5.3.5.5Reconfiguration failure (83)5.3.5.6T304 expiry (handover failure) (83)5.3.5.7Void (84)5.3.5.7a T307 expiry (SCG change failure) (84)5.3.5.8Radio Configuration involving full configuration option (84)5.3.6Counter check (86)5.3.6.1General (86)5.3.6.2Initiation (86)5.3.6.3Reception of the CounterCheck message by the UE (86)5.3.7RRC connection re-establishment (87)5.3.7.1General (87)5.3.7.2Initiation (87)5.3.7.3Actions following cell selection while T311 is running (88)5.3.7.4Actions related to transmission of RRCConnectionReestablishmentRequest message (89)5.3.7.5Reception of the RRCConnectionReestablishment by the UE (89)5.3.7.6T311 expiry (91)5.3.7.7T301 expiry or selected cell no longer suitable (91)5.3.7.8Reception of RRCConnectionReestablishmentReject by the UE (91)5.3.8RRC connection release (92)5.3.8.1General (92)5.3.8.2Initiation (92)5.3.8.3Reception of the RRCConnectionRelease by the UE (92)5.3.8.4T320 expiry (93)5.3.9RRC connection release requested by upper layers (93)5.3.9.1General (93)5.3.9.2Initiation (93)5.3.10Radio resource configuration (93)5.3.10.0General (93)5.3.10.1SRB addition/ modification (94)5.3.10.2DRB release (95)5.3.10.3DRB addition/ modification (95)5.3.10.3a1DC specific DRB addition or reconfiguration (96)5.3.10.3a2LWA specific DRB addition or reconfiguration (98)5.3.10.3a3LWIP specific DRB addition or reconfiguration (98)5.3.10.3a SCell release (99)5.3.10.3b SCell addition/ modification (99)5.3.10.3c PSCell addition or modification (99)5.3.10.4MAC main reconfiguration (99)5.3.10.5Semi-persistent scheduling reconfiguration (100)5.3.10.6Physical channel reconfiguration (100)5.3.10.7Radio Link Failure Timers and Constants reconfiguration (101)5.3.10.8Time domain measurement resource restriction for serving cell (101)5.3.10.9Other configuration (102)5.3.10.10SCG reconfiguration (103)5.3.10.11SCG dedicated resource configuration (104)5.3.10.12Reconfiguration SCG or split DRB by drb-ToAddModList (105)5.3.10.13Neighbour cell information reconfiguration (105)5.3.10.14Void (105)5.3.10.15Sidelink dedicated configuration (105)5.3.10.16T370 expiry (106)5.3.11Radio link failure related actions (107)5.3.11.1Detection of physical layer problems in RRC_CONNECTED (107)5.3.11.2Recovery of physical layer problems (107)5.3.11.3Detection of radio link failure (107)5.3.12UE actions upon leaving RRC_CONNECTED (109)5.3.13UE actions upon PUCCH/ SRS release request (110)5.3.14Proximity indication (110)5.3.14.1General (110)5.3.14.2Initiation (111)5.3.14.3Actions related to transmission of ProximityIndication message (111)5.3.15Void (111)5.4Inter-RAT mobility (111)5.4.1Introduction (111)5.4.2Handover to E-UTRA (112)5.4.2.1General (112)5.4.2.2Initiation (112)5.4.2.3Reception of the RRCConnectionReconfiguration by the UE (112)5.4.2.4Reconfiguration failure (114)5.4.2.5T304 expiry (handover to E-UTRA failure) (114)5.4.3Mobility from E-UTRA (114)5.4.3.1General (114)5.4.3.2Initiation (115)5.4.3.3Reception of the MobilityFromEUTRACommand by the UE (115)5.4.3.4Successful completion of the mobility from E-UTRA (116)5.4.3.5Mobility from E-UTRA failure (117)5.4.4Handover from E-UTRA preparation request (CDMA2000) (117)5.4.4.1General (117)5.4.4.2Initiation (118)5.4.4.3Reception of the HandoverFromEUTRAPreparationRequest by the UE (118)5.4.5UL handover preparation transfer (CDMA2000) (118)5.4.5.1General (118)5.4.5.2Initiation (118)5.4.5.3Actions related to transmission of the ULHandoverPreparationTransfer message (119)5.4.5.4Failure to deliver the ULHandoverPreparationTransfer message (119)5.4.6Inter-RAT cell change order to E-UTRAN (119)5.4.6.1General (119)5.4.6.2Initiation (119)5.4.6.3UE fails to complete an inter-RAT cell change order (119)5.5Measurements (120)5.5.1Introduction (120)5.5.2Measurement configuration (121)5.5.2.1General (121)5.5.2.2Measurement identity removal (122)5.5.2.2a Measurement identity autonomous removal (122)5.5.2.3Measurement identity addition/ modification (123)5.5.2.4Measurement object removal (124)5.5.2.5Measurement object addition/ modification (124)5.5.2.6Reporting configuration removal (126)5.5.2.7Reporting configuration addition/ modification (127)5.5.2.8Quantity configuration (127)5.5.2.9Measurement gap configuration (127)5.5.2.10Discovery signals measurement timing configuration (128)5.5.2.11RSSI measurement timing configuration (128)5.5.3Performing measurements (128)5.5.3.1General (128)5.5.3.2Layer 3 filtering (131)5.5.4Measurement report triggering (131)5.5.4.1General (131)5.5.4.2Event A1 (Serving becomes better than threshold) (135)5.5.4.3Event A2 (Serving becomes worse than threshold) (136)5.5.4.4Event A3 (Neighbour becomes offset better than PCell/ PSCell) (136)5.5.4.5Event A4 (Neighbour becomes better than threshold) (137)5.5.4.6Event A5 (PCell/ PSCell becomes worse than threshold1 and neighbour becomes better thanthreshold2) (138)5.5.4.6a Event A6 (Neighbour becomes offset better than SCell) (139)5.5.4.7Event B1 (Inter RAT neighbour becomes better than threshold) (139)5.5.4.8Event B2 (PCell becomes worse than threshold1 and inter RAT neighbour becomes better thanthreshold2) (140)5.5.4.9Event C1 (CSI-RS resource becomes better than threshold) (141)5.5.4.10Event C2 (CSI-RS resource becomes offset better than reference CSI-RS resource) (141)5.5.4.11Event W1 (WLAN becomes better than a threshold) (142)5.5.4.12Event W2 (All WLAN inside WLAN mobility set becomes worse than threshold1 and a WLANoutside WLAN mobility set becomes better than threshold2) (142)5.5.4.13Event W3 (All WLAN inside WLAN mobility set becomes worse than a threshold) (143)5.5.5Measurement reporting (144)5.5.6Measurement related actions (148)5.5.6.1Actions upon handover and re-establishment (148)5.5.6.2Speed dependant scaling of measurement related parameters (149)5.5.7Inter-frequency RSTD measurement indication (149)5.5.7.1General (149)5.5.7.2Initiation (150)5.5.7.3Actions related to transmission of InterFreqRSTDMeasurementIndication message (150)5.6Other (150)5.6.0General (150)5.6.1DL information transfer (151)5.6.1.1General (151)5.6.1.2Initiation (151)5.6.1.3Reception of the DLInformationTransfer by the UE (151)5.6.2UL information transfer (151)5.6.2.1General (151)5.6.2.2Initiation (151)5.6.2.3Actions related to transmission of ULInformationTransfer message (152)5.6.2.4Failure to deliver ULInformationTransfer message (152)5.6.3UE capability transfer (152)5.6.3.1General (152)5.6.3.2Initiation (153)5.6.3.3Reception of the UECapabilityEnquiry by the UE (153)5.6.4CSFB to 1x Parameter transfer (157)5.6.4.1General (157)5.6.4.2Initiation (157)5.6.4.3Actions related to transmission of CSFBParametersRequestCDMA2000 message (157)5.6.4.4Reception of the CSFBParametersResponseCDMA2000 message (157)5.6.5UE Information (158)5.6.5.1General (158)5.6.5.2Initiation (158)5.6.5.3Reception of the UEInformationRequest message (158)5.6.6 Logged Measurement Configuration (159)5.6.6.1General (159)5.6.6.2Initiation (160)5.6.6.3Reception of the LoggedMeasurementConfiguration by the UE (160)5.6.6.4T330 expiry (160)5.6.7 Release of Logged Measurement Configuration (160)5.6.7.1General (160)5.6.7.2Initiation (160)5.6.8 Measurements logging (161)5.6.8.1General (161)5.6.8.2Initiation (161)5.6.9In-device coexistence indication (163)5.6.9.1General (163)5.6.9.2Initiation (164)5.6.9.3Actions related to transmission of InDeviceCoexIndication message (164)5.6.10UE Assistance Information (165)5.6.10.1General (165)5.6.10.2Initiation (166)5.6.10.3Actions related to transmission of UEAssistanceInformation message (166)5.6.11 Mobility history information (166)5.6.11.1General (166)5.6.11.2Initiation (166)5.6.12RAN-assisted WLAN interworking (167)5.6.12.1General (167)5.6.12.2Dedicated WLAN offload configuration (167)5.6.12.3WLAN offload RAN evaluation (167)5.6.12.4T350 expiry or stop (167)5.6.12.5Cell selection/ re-selection while T350 is running (168)5.6.13SCG failure information (168)5.6.13.1General (168)5.6.13.2Initiation (168)5.6.13.3Actions related to transmission of SCGFailureInformation message (168)5.6.14LTE-WLAN Aggregation (169)5.6.14.1Introduction (169)5.6.14.2Reception of LWA configuration (169)5.6.14.3Release of LWA configuration (170)5.6.15WLAN connection management (170)5.6.15.1Introduction (170)5.6.15.2WLAN connection status reporting (170)5.6.15.2.1General (170)5.6.15.2.2Initiation (171)5.6.15.2.3Actions related to transmission of WLANConnectionStatusReport message (171)5.6.15.3T351 Expiry (WLAN connection attempt timeout) (171)5.6.15.4WLAN status monitoring (171)5.6.16RAN controlled LTE-WLAN interworking (172)5.6.16.1General (172)5.6.16.2WLAN traffic steering command (172)5.6.17LTE-WLAN aggregation with IPsec tunnel (173)5.6.17.1General (173)5.7Generic error handling (174)5.7.1General (174)5.7.2ASN.1 violation or encoding error (174)5.7.3Field set to a not comprehended value (174)5.7.4Mandatory field missing (174)5.7.5Not comprehended field (176)5.8MBMS (176)5.8.1Introduction (176)5.8.1.1General (176)5.8.1.2Scheduling (176)5.8.1.3MCCH information validity and notification of changes (176)5.8.2MCCH information acquisition (178)5.8.2.1General (178)5.8.2.2Initiation (178)5.8.2.3MCCH information acquisition by the UE (178)5.8.2.4Actions upon reception of the MBSFNAreaConfiguration message (178)5.8.2.5Actions upon reception of the MBMSCountingRequest message (179)5.8.3MBMS PTM radio bearer configuration (179)5.8.3.1General (179)5.8.3.2Initiation (179)5.8.3.3MRB establishment (179)5.8.3.4MRB release (179)5.8.4MBMS Counting Procedure (179)5.8.4.1General (179)5.8.4.2Initiation (180)5.8.4.3Reception of the MBMSCountingRequest message by the UE (180)5.8.5MBMS interest indication (181)5.8.5.1General (181)5.8.5.2Initiation (181)5.8.5.3Determine MBMS frequencies of interest (182)5.8.5.4Actions related to transmission of MBMSInterestIndication message (183)5.8a SC-PTM (183)5.8a.1Introduction (183)5.8a.1.1General (183)5.8a.1.2SC-MCCH scheduling (183)5.8a.1.3SC-MCCH information validity and notification of changes (183)5.8a.1.4Procedures (184)5.8a.2SC-MCCH information acquisition (184)5.8a.2.1General (184)5.8a.2.2Initiation (184)5.8a.2.3SC-MCCH information acquisition by the UE (184)5.8a.2.4Actions upon reception of the SCPTMConfiguration message (185)5.8a.3SC-PTM radio bearer configuration (185)5.8a.3.1General (185)5.8a.3.2Initiation (185)5.8a.3.3SC-MRB establishment (185)5.8a.3.4SC-MRB release (185)5.9RN procedures (186)5.9.1RN reconfiguration (186)5.9.1.1General (186)5.9.1.2Initiation (186)5.9.1.3Reception of the RNReconfiguration by the RN (186)5.10Sidelink (186)5.10.1Introduction (186)5.10.1a Conditions for sidelink communication operation (187)5.10.2Sidelink UE information (188)5.10.2.1General (188)5.10.2.2Initiation (189)5.10.2.3Actions related to transmission of SidelinkUEInformation message (193)5.10.3Sidelink communication monitoring (195)5.10.6Sidelink discovery announcement (198)5.10.6a Sidelink discovery announcement pool selection (201)5.10.6b Sidelink discovery announcement reference carrier selection (201)5.10.7Sidelink synchronisation information transmission (202)5.10.7.1General (202)5.10.7.2Initiation (203)5.10.7.3Transmission of SLSS (204)5.10.7.4Transmission of MasterInformationBlock-SL message (205)5.10.7.5Void (206)5.10.8Sidelink synchronisation reference (206)5.10.8.1General (206)5.10.8.2Selection and reselection of synchronisation reference UE (SyncRef UE) (206)5.10.9Sidelink common control information (207)5.10.9.1General (207)5.10.9.2Actions related to reception of MasterInformationBlock-SL message (207)5.10.10Sidelink relay UE operation (207)5.10.10.1General (207)5.10.10.2AS-conditions for relay related sidelink communication transmission by sidelink relay UE (207)5.10.10.3AS-conditions for relay PS related sidelink discovery transmission by sidelink relay UE (208)5.10.10.4Sidelink relay UE threshold conditions (208)5.10.11Sidelink remote UE operation (208)5.10.11.1General (208)5.10.11.2AS-conditions for relay related sidelink communication transmission by sidelink remote UE (208)5.10.11.3AS-conditions for relay PS related sidelink discovery transmission by sidelink remote UE (209)5.10.11.4Selection and reselection of sidelink relay UE (209)5.10.11.5Sidelink remote UE threshold conditions (210)6Protocol data units, formats and parameters (tabular & ASN.1) (210)6.1General (210)6.2RRC messages (212)6.2.1General message structure (212)–EUTRA-RRC-Definitions (212)–BCCH-BCH-Message (212)–BCCH-DL-SCH-Message (212)–BCCH-DL-SCH-Message-BR (213)–MCCH-Message (213)–PCCH-Message (213)–DL-CCCH-Message (214)–DL-DCCH-Message (214)–UL-CCCH-Message (214)–UL-DCCH-Message (215)–SC-MCCH-Message (215)6.2.2Message definitions (216)–CounterCheck (216)–CounterCheckResponse (217)–CSFBParametersRequestCDMA2000 (217)–CSFBParametersResponseCDMA2000 (218)–DLInformationTransfer (218)–HandoverFromEUTRAPreparationRequest (CDMA2000) (219)–InDeviceCoexIndication (220)–InterFreqRSTDMeasurementIndication (222)–LoggedMeasurementConfiguration (223)–MasterInformationBlock (225)–MBMSCountingRequest (226)–MBMSCountingResponse (226)–MBMSInterestIndication (227)–MBSFNAreaConfiguration (228)–MeasurementReport (228)–MobilityFromEUTRACommand (229)–Paging (232)–ProximityIndication (233)–RNReconfiguration (234)–RNReconfigurationComplete (234)–RRCConnectionReconfiguration (235)–RRCConnectionReconfigurationComplete (240)–RRCConnectionReestablishment (241)–RRCConnectionReestablishmentComplete (241)–RRCConnectionReestablishmentReject (242)–RRCConnectionReestablishmentRequest (243)–RRCConnectionReject (243)–RRCConnectionRelease (244)–RRCConnectionResume (248)–RRCConnectionResumeComplete (249)–RRCConnectionResumeRequest (250)–RRCConnectionRequest (250)–RRCConnectionSetup (251)–RRCConnectionSetupComplete (252)–SCGFailureInformation (253)–SCPTMConfiguration (254)–SecurityModeCommand (255)–SecurityModeComplete (255)–SecurityModeFailure (256)–SidelinkUEInformation (256)–SystemInformation (258)–SystemInformationBlockType1 (259)–UEAssistanceInformation (264)–UECapabilityEnquiry (265)–UECapabilityInformation (266)–UEInformationRequest (267)–UEInformationResponse (267)–ULHandoverPreparationTransfer (CDMA2000) (273)–ULInformationTransfer (274)–WLANConnectionStatusReport (274)6.3RRC information elements (275)6.3.1System information blocks (275)–SystemInformationBlockType2 (275)–SystemInformationBlockType3 (279)–SystemInformationBlockType4 (282)–SystemInformationBlockType5 (283)–SystemInformationBlockType6 (287)–SystemInformationBlockType7 (289)–SystemInformationBlockType8 (290)–SystemInformationBlockType9 (295)–SystemInformationBlockType10 (295)–SystemInformationBlockType11 (296)–SystemInformationBlockType12 (297)–SystemInformationBlockType13 (297)–SystemInformationBlockType14 (298)–SystemInformationBlockType15 (298)–SystemInformationBlockType16 (299)–SystemInformationBlockType17 (300)–SystemInformationBlockType18 (301)–SystemInformationBlockType19 (301)–SystemInformationBlockType20 (304)6.3.2Radio resource control information elements (304)–AntennaInfo (304)–AntennaInfoUL (306)–CQI-ReportConfig (307)–CQI-ReportPeriodicProcExtId (314)–CrossCarrierSchedulingConfig (314)–CSI-IM-Config (315)–CSI-IM-ConfigId (315)–CSI-RS-Config (317)–CSI-RS-ConfigEMIMO (318)–CSI-RS-ConfigNZP (319)–CSI-RS-ConfigNZPId (320)–CSI-RS-ConfigZP (321)–CSI-RS-ConfigZPId (321)–DMRS-Config (321)–DRB-Identity (322)–EPDCCH-Config (322)–EIMTA-MainConfig (324)–LogicalChannelConfig (325)–LWA-Configuration (326)–LWIP-Configuration (326)–RCLWI-Configuration (327)–MAC-MainConfig (327)–P-C-AndCBSR (332)–PDCCH-ConfigSCell (333)–PDCP-Config (334)–PDSCH-Config (337)–PDSCH-RE-MappingQCL-ConfigId (339)–PHICH-Config (339)–PhysicalConfigDedicated (339)–P-Max (344)–PRACH-Config (344)–PresenceAntennaPort1 (346)–PUCCH-Config (347)–PUSCH-Config (351)–RACH-ConfigCommon (355)–RACH-ConfigDedicated (357)–RadioResourceConfigCommon (358)–RadioResourceConfigDedicated (362)–RLC-Config (367)–RLF-TimersAndConstants (369)–RN-SubframeConfig (370)–SchedulingRequestConfig (371)–SoundingRS-UL-Config (372)–SPS-Config (375)–TDD-Config (376)–TimeAlignmentTimer (377)–TPC-PDCCH-Config (377)–TunnelConfigLWIP (378)–UplinkPowerControl (379)–WLAN-Id-List (382)–WLAN-MobilityConfig (382)6.3.3Security control information elements (382)–NextHopChainingCount (382)–SecurityAlgorithmConfig (383)–ShortMAC-I (383)6.3.4Mobility control information elements (383)–AdditionalSpectrumEmission (383)–ARFCN-ValueCDMA2000 (383)–ARFCN-ValueEUTRA (384)–ARFCN-ValueGERAN (384)–ARFCN-ValueUTRA (384)–BandclassCDMA2000 (384)–BandIndicatorGERAN (385)–CarrierFreqCDMA2000 (385)–CarrierFreqGERAN (385)–CellIndexList (387)–CellReselectionPriority (387)–CellSelectionInfoCE (387)–CellReselectionSubPriority (388)–CSFB-RegistrationParam1XRTT (388)–CellGlobalIdEUTRA (389)–CellGlobalIdUTRA (389)–CellGlobalIdGERAN (390)–CellGlobalIdCDMA2000 (390)–CellSelectionInfoNFreq (391)–CSG-Identity (391)–FreqBandIndicator (391)–MobilityControlInfo (391)–MobilityParametersCDMA2000 (1xRTT) (393)–MobilityStateParameters (394)–MultiBandInfoList (394)–NS-PmaxList (394)–PhysCellId (395)–PhysCellIdRange (395)–PhysCellIdRangeUTRA-FDDList (395)–PhysCellIdCDMA2000 (396)–PhysCellIdGERAN (396)–PhysCellIdUTRA-FDD (396)–PhysCellIdUTRA-TDD (396)–PLMN-Identity (397)–PLMN-IdentityList3 (397)–PreRegistrationInfoHRPD (397)–Q-QualMin (398)–Q-RxLevMin (398)–Q-OffsetRange (398)–Q-OffsetRangeInterRAT (399)–ReselectionThreshold (399)–ReselectionThresholdQ (399)–SCellIndex (399)–ServCellIndex (400)–SpeedStateScaleFactors (400)–SystemInfoListGERAN (400)–SystemTimeInfoCDMA2000 (401)–TrackingAreaCode (401)–T-Reselection (402)–T-ReselectionEUTRA-CE (402)6.3.5Measurement information elements (402)–AllowedMeasBandwidth (402)–CSI-RSRP-Range (402)–Hysteresis (402)–LocationInfo (403)–MBSFN-RSRQ-Range (403)–MeasConfig (404)–MeasDS-Config (405)–MeasGapConfig (406)–MeasId (407)–MeasIdToAddModList (407)–MeasObjectCDMA2000 (408)–MeasObjectEUTRA (408)–MeasObjectGERAN (412)–MeasObjectId (412)–MeasObjectToAddModList (412)–MeasObjectUTRA (413)–ReportConfigEUTRA (422)–ReportConfigId (425)–ReportConfigInterRAT (425)–ReportConfigToAddModList (428)–ReportInterval (429)–RSRP-Range (429)–RSRQ-Range (430)–RSRQ-Type (430)–RS-SINR-Range (430)–RSSI-Range-r13 (431)–TimeToTrigger (431)–UL-DelayConfig (431)–WLAN-CarrierInfo (431)–WLAN-RSSI-Range (432)–WLAN-Status (432)6.3.6Other information elements (433)–AbsoluteTimeInfo (433)–AreaConfiguration (433)–C-RNTI (433)–DedicatedInfoCDMA2000 (434)–DedicatedInfoNAS (434)–FilterCoefficient (434)–LoggingDuration (434)–LoggingInterval (435)–MeasSubframePattern (435)–MMEC (435)–NeighCellConfig (435)–OtherConfig (436)–RAND-CDMA2000 (1xRTT) (437)–RAT-Type (437)–ResumeIdentity (437)–RRC-TransactionIdentifier (438)–S-TMSI (438)–TraceReference (438)–UE-CapabilityRAT-ContainerList (438)–UE-EUTRA-Capability (439)–UE-RadioPagingInfo (469)–UE-TimersAndConstants (469)–VisitedCellInfoList (470)–WLAN-OffloadConfig (470)6.3.7MBMS information elements (472)–MBMS-NotificationConfig (472)–MBMS-ServiceList (473)–MBSFN-AreaId (473)–MBSFN-AreaInfoList (473)–MBSFN-SubframeConfig (474)–PMCH-InfoList (475)6.3.7a SC-PTM information elements (476)–SC-MTCH-InfoList (476)–SCPTM-NeighbourCellList (478)6.3.8Sidelink information elements (478)–SL-CommConfig (478)–SL-CommResourcePool (479)–SL-CP-Len (480)–SL-DiscConfig (481)–SL-DiscResourcePool (483)–SL-DiscTxPowerInfo (485)–SL-GapConfig (485)。
2014年高考真题解析分类汇编纯word可编辑-语文-词语熟语

17.[2014·安徽卷] 下列各句中,加点的词语使用恰当的一句是(3分)()A.2013年,广州恒大足球队问鼎亚冠联赛,结束了中国俱乐部足球队二十余年无缘亚洲冠军的局面,这对处于低谷之中的中国足球来说弥足珍贵....。
B.随着4G时代的到来,国产智能手机纷纷登堂入室....,截至今年第一季度,联想、华为、中兴和小米等品牌手机在全球市场已占有三分之一的份额。
C.近两年,我国发明专利申请和授权的数量快速增长,专利申请质量蒸蒸日上....,这表明我国专利申请结构进一步优化,自主创新能力进一步增强。
D.去年我国电子商务交易总额高达10万亿元,其中网络商品零售额超过了1.8万亿元,凭此成绩,我国当仁不让....地跃居全球网络商品零售榜首。
17.A[解析] 本题考查正确使用词语(包括熟语)。
解答本题时应将筛选法与排除法相结合。
A.“弥足珍贵”指更加值得珍爱、重视。
B. 登堂入室:堂、室,古代宫室,前面是堂,后面是室。
比喻学问或技能由浅入深,循序渐进,达到更高的水平。
望文生义。
C. 蒸蒸日上:蒸蒸,上升、兴盛的样子。
形容事业天天向上发展,十分兴旺。
对象用错。
D. 当仁不让:泛指遇到应该做的事,积极主动去做,不退让。
不合语境。
[2014·北京卷] 阅读下面的文字,完成1~4题。
“千门万户曈曈日,总把新桃换旧符。
”贴春联是中国人过年时的一项传统民俗活动。
人们通常在除夕这天,将写好的春联贴于门上。
春联的字数可多可少,但上下联必须构成对仗,如四言联“春安夏泰,秋稔.(rěn)冬祥”,六言联“冬尽梅花点点,□□□□□□”。
春联寓意吉祥,言简意赅.(ɡāi),深受人们喜爱。
春联是仅在春节这一特定时节张贴的对联,而对联还有其他种类,如婚联、寿联、挽联,以及为园林建筑__甲__(题写/题签)的楹.(yínɡ)联等。
对联的撰.写,往往注重其__乙__(蕴涵/内涵)与品味。
尤其是名联佳对,文辞讲究,意蕴.丰富,__丙__(吟咏/涵泳)起来锒锒..上口,齿颊..留香。
2014年全国高考语文真题专题分类汇编:字音题(含详细解答)

2014年普通高等学校招生全国统一考试语文试卷字音题汇编(浙江卷)1.下列词语中,加点字的注音全都正确的一项是A.摭.(zhí)拾哄.(hōng)笑擎.(qín)天柱钻.(zuān)木取火B.屏.(bǐng)息包扎.(zhā)夹(jiā)克衫言之凿凿(záo)C.孱(càn)弱牌坊(fāng)干.(gàn)细胞铩.(shā)羽而归D.吟哦.(ã)皲.(jūn)裂胳.(gā)肢窝蜚.(fēi)声中外1.答案:D解析:A项,“擎”应读“qíng”;B项,“扎”应读“zā”;C项,“孱”应读“chán”(重庆卷)1.下列词语中,字形和加点字的读音全都正确的一组是A.屋檐下绿草如茵刀把.子bà相.机行事xiàngB.势利眼卑躬屈膝撒.大网 sǎ博闻强识.zhìC.一溜烟通货膨胀狙.击手jū蓦.然回首mùD.辨证法中流砥柱沏.茶喝qī杀一儆.百jǐng【答案】1. A【解析】本题考查“识记现代汉语普通话常用字的字音”和“识记并正确书写现代常用规范汉字”的能力,能力层级为A。
主要考查同音字的字形和重庆人容易读错的字音。
B项中“撒大网”中的“撒”应读sā;B项中“蓦然回首”中的“蓦”应读mî;D项中“辨证法”中的“辨”应为“辩”本题难度不太大,可由易到难地进行排除。
C项比较好排除,D项一般,主要是A项和B项有些迷惑性,做题时要特别注意。
(安徽卷)15.下面词语中加点的字,每对读音完全相同的一组是(3分)A.蓓.蕾/烘焙.拾.级/拾.麦穗箪.食壶浆/殚.精竭虑B.倚.重/旖.旎禅.趣/口头禅.卷帙.浩繁/秩.序井然C.毗邻./聆.听包扎./扎.辫子济.世安民/光风霁.月D.翡.翠/斐.然开拓./拓.荒者物产丰饶./百折不挠.【解析】B(北京卷)阅读下面的文字,完成1—4题。
“千门万户曈曈日,总把新桃换日符。
あ行

あ行あいそう(愛想)・お酒ばかり飲む夫に愛想を尽かした妻は、離婚した。
「討厭」・あの店員は愛想がよい。
「招待」・愛想を言う。
「客套話」・愛想がない。
「親切」・おーい、お愛想。
「結帳」あいだがら(間柄)・林先生と山田さんは、師弟の間柄だそうです。
「關係」あえて(敢えて)・あなたの将来のために、あえて忠告します。
「特意、勉強」・どうしても行きたいなら、私はあえて反対しない。
「並不」あくどい・あの男のあくどいやり方に泣かされた人も多い。
「太過火、惡毒」・色があくどい、味があくどい。
「過艷、太膩」あざ(痣)・私は生まれながらに、左手に小さなあざがあります。
あさましい(浅ましい)・祖父が亡くなったとたん、遺産をめぐってあさましい争いが始まった。
「卑鄙、可恥」あざむく(欺く)・敵を欺くために、一度退却するふりをした。
「欺騙」・花をあざむく器量。
「賽過」あざわらう(嘲笑う)・助けを求めにきた人を、何もせずあざわらっていたあの男はひどい。
あせる(褪せる、焦る)・朝寝坊をしたので焦って出かけた。
「急躁、着急」・何度も洗濯したのでTシャツの色が褪せた。
「褪色」あっけない・有名な大学の試験だから、難しいと思ったが、あっけないほどやさしかった。
「太簡単、没意思」あつらえる(誂える)・兄は、既成服に合わない体形なので、服をあつらえている。
「訂做」あとまわし(後回し)・彼は自分のことを後回しにしても、他の人を助けるような人だ。
「推遲、緩辦」あべこべ・道を曲がるのを間違えたらしく、あべこべの方向へ行ってしまった。
「相反、顛倒」あやつる(操る)・彼女が横領したのは、陰で誰かに操られたからに違いない。
「操縱」あやぶむ(危ぶむ)・遭難した船の行方は、いまだに分からず、乗組員の生存が危ぶまれている。
「認爲危險」あやふや・彼のあやふやな態度に、彼女は激怒した。
「含糊」あやまち(過ち)・誰でも若い時は、過ちの一つや二つはおかす。
「過錯」あらかじめ(予め)・あらかじめ必要なものをメモして行くと、無駄な買物をしない。
基于周期采样的分布式动态事件触发优化算法

第38卷第3期2024年5月山东理工大学学报(自然科学版)Journal of Shandong University of Technology(Natural Science Edition)Vol.38No.3May 2024收稿日期:20230323基金项目:江苏省自然科学基金项目(BK20200824)第一作者:夏伦超,男,20211249098@;通信作者:赵中原,男,zhaozhongyuan@文章编号:1672-6197(2024)03-0058-07基于周期采样的分布式动态事件触发优化算法夏伦超1,韦梦立2,季秋桐2,赵中原1(1.南京信息工程大学自动化学院,江苏南京210044;2.东南大学网络空间安全学院,江苏南京211189)摘要:针对无向图下多智能体系统的优化问题,提出一种基于周期采样机制的分布式零梯度和优化算法,并设计一种新的动态事件触发策略㊂该策略中加入与历史时刻智能体状态相关的动态变量,有效降低了系统通信量;所提出的算法允许采样周期任意大,并考虑了通信延时的影响,利用Lyapunov 稳定性理论推导出算法收敛的充分条件㊂数值仿真进一步验证了所提算法的有效性㊂关键词:分布式优化;多智能体系统;动态事件触发;通信时延中图分类号:TP273文献标志码:ADistributed dynamic event triggerring optimizationalgorithm based on periodic samplingXIA Lunchao 1,WEI Mengli 2,JI Qiutong 2,ZHAO Zhongyuan 1(1.College of Automation,Nanjing University of Information Science and Technology,Nanjing 210044,China;2.School of Cyber Science and Engineering,Southeast University,Nanjing 211189,China)Abstract :A distributed zero-gradient-sum optimization algorithm based on a periodic sampling mechanism is proposed to address the optimization problem of multi-agent systems under undirected graphs.A novel dynamic event-triggering strategy is designed,which incorporates dynamic variables as-sociated with the historical states of the agents to effectively reduce the system communication overhead.Moreover,the algorithm allows for arbitrary sampling periods and takes into consideration the influence oftime delay.Finally,sufficient conditions for the convergence of the algorithm are derived by utilizing Lya-punov stability theory.The effectiveness of the proposed algorithm is further demonstrated through numer-ical simulations.Keywords :distributed optimization;multi-agent systems;dynamic event-triggered;time delay ㊀㊀近些年,多智能体系统的分布式优化问题因其在多机器人系统的合作㊁智能交通系统的智能运输系统和微电网的分布式经济调度等诸多领域的应用得到了广泛的研究[1-3]㊂如今,已经提出各种分布式优化算法㊂文献[4]提出一种结合负反馈和梯度流的算法来解决平衡有向图下的无约束优化问题;文献[5]提出一种基于自适应机制的分布式优化算法来解决局部目标函数非凸的问题;文献[6]设计一种抗干扰的分布式优化算法,能够在具有未知外部扰动的情况下获得最优解㊂然而,上述工作要求智能体与其邻居不断地交流,这在现实中会造成很大的通信负担㊂文献[7]首先提出分布式事件触发控制器来解决多智能体系统一致性问题;事件触发机制的核心是设计一个基于误差的触发条件,只有满足触发条件时智能体间才进行通信㊂文献[8]提出一种基于通信网络边信息的事件触发次梯度优化㊀算法,并给出了算法的指数收敛速度㊂文献[9]提出一种基于事件触发机制的零梯度和算法,保证系统状态收敛到最优解㊂上述事件触发策略是静态事件触发策略,即其触发阈值仅与智能体的状态相关,当智能体的状态逐渐收敛时,很容易满足触发条件并将生成大量不必要的通信㊂因此,需要设计更合理的触发条件㊂文献[10]针对非线性系统的增益调度控制问题,提出一种动态事件触发机制的增益调度控制器;文献[11]提出一种基于动态事件触发条件的零梯度和算法,用于有向网络的优化㊂由于信息传输的复杂性,时间延迟在实际系统中无处不在㊂关于考虑时滞的事件触发优化问题的文献很多㊂文献[12]研究了二阶系统的凸优化问题,提出时间触发算法和事件触发算法两种分布式优化算法,使得所有智能体协同收敛到优化问题的最优解,并有效消除不必要的通信;文献[13]针对具有传输延迟的多智能体系统,提出一种具有采样数据和时滞的事件触发分布式优化算法,并得到系统指数稳定的充分条件㊂受文献[9,14]的启发,本文提出一种基于动态事件触发机制的分布式零梯度和算法,与使用静态事件触发机制的文献[15]相比,本文采用动态事件触发机制可以避免智能体状态接近最优值时频繁触发造成的资源浪费㊂此外,考虑到进行动态事件触发判断需要一定的时间,使用当前状态值是不现实的,因此,本文使用前一时刻状态值来构造动态事件触发条件,更符合逻辑㊂由于本文采用周期采样机制,这进一步降低了智能体间的通信频率,但采样周期过长会影响算法收敛㊂基于文献[14]的启发,本文设计的算法允许采样周期任意大,并且对于有时延的系统,只需要其受采样周期的限制,就可得到保证多智能体系统达到一致性和最优性的充分条件㊂最后,通过对一个通用示例进行仿真,验证所提算法的有效性㊂1㊀预备知识及问题描述1.1㊀图论令R表示实数集,R n表示向量集,R nˑn表示n ˑn实矩阵的集合㊂将包含n个智能体的多智能体系统的通信网络用图G=(V,E)建模,每个智能体都视为一个节点㊂该图由顶点集V={1,2, ,n}和边集E⊆VˑV组成㊂定义A=[a ij]ɪR nˑn为G 的加权邻接矩阵,当a ij>0时,表明节点i和节点j 间存在路径,即(i,j)ɪE;当a ij=0时,表明节点i 和节点j间不存在路径,即(i,j)∉E㊂D=diag{d1, ,d n}表示度矩阵,拉普拉斯矩阵L等于度矩阵减去邻接矩阵,即L=D-A㊂当图G是无向图时,其拉普拉斯矩阵是对称矩阵㊂1.2㊀凸函数设h i:R nңR是在凸集ΩɪR n上的局部凸函数,存在正常数φi使得下列条件成立[16]:h i(b)-h i(a)- h i(a)T(b-a)ȡ㊀㊀㊀㊀φi2 b-a 2,∀a,bɪΩ,(1)h i(b)- h i(a)()T(b-a)ȡ㊀㊀㊀㊀φi b-a 2,∀a,bɪΩ,(2) 2h i(a)ȡφi I n,∀aɪΩ,(3)式中: h i为h i的一阶梯度, 2h i为h i的二阶梯度(也称黑塞矩阵)㊂1.3㊀问题描述考虑包含n个智能体的多智能体系统,假设每个智能体i的成本函数为f i(x),本文的目标是最小化以下的优化问题:x∗=arg minxɪΩðni=1f i(x),(4)式中:x为决策变量,x∗为全局最优值㊂1.4㊀主要引理引理1㊀假设通信拓扑图G是无向且连通的,对于任意XɪR n,有以下关系成立[17]:X T LXȡαβX T L T LX,(5)式中:α是L+L T2最小的正特征值,β是L T L最大的特征值㊂引理2(中值定理)㊀假设局部成本函数是连续可微的,则对于任意实数y和y0,存在y~=y0+ω~(y -y0),使得以下不等式成立:f i(y)=f i(y0)+∂f i∂y(y~)(y-y0),(6)式中ω~是正常数且满足ω~ɪ(0,1)㊂2㊀基于动态事件触发机制的分布式优化算法及主要结果2.1㊀考虑时延的分布式动态事件触发优化算法本文研究具有时延的多智能体系统的优化问题㊂为了降低智能体间的通信频率,提出一种采样周期可任意设计的分布式动态事件触发优化算法,95第3期㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀夏伦超,等:基于周期采样的分布式动态事件触发优化算法其具体实现通信优化的流程图如图1所示㊂首先,将邻居和自身前一触发时刻状态送往控制器(本文提出的算法),得到智能体的状态x i (t )㊂然后,预设一个固定采样周期h ,使得所有智能体在同一时刻进行采样㊂同时,在每个智能体上都配置了事件检测器,只在采样时刻检查是否满足触发条件㊂接着,将前一采样时刻的智能体状态发送至构造的触发器中进行判断,当满足设定的触发条件时,得到触发时刻的智能体状态x^i (t )㊂最后,将得到的本地状态x^i (t )用于更新自身及其邻居的控制操作㊂由于在实际传输中存在时延,因此需要考虑满足0<τ<h 的时延㊂图1㊀算法实现流程图考虑由n 个智能体构成的多智能体系统,其中每个智能体都能独立进行计算和相互通信,每个智能体i 具有如下动态方程:x ㊃i (t )=-1h2f i (x i )()-1u i (t ),(7)式中u i (t )为设计的控制算法,具体为u i (t )=ðnj =1a ij x^j (t -τ)-x ^i (t -τ)()㊂(8)㊀㊀给出设计的动态事件触发条件:θi d i e 2i (lh )-γq i (lh -h )()ɤξi (lh ),(9)q i (t )=ðnj =1a ij x^i (t -τ)-x ^j (t -τ)()2,(10)㊀㊀㊀ξ㊃i (t )=1h[-μi ξi (lh )+㊀㊀㊀㊀㊀δi γq i (lh -h )-d i e 2i (lh )()],(11)式中:d i 是智能体i 的入度;γ是正常数;θi ,μi ,δi 是设计的参数㊂令x i (lh )表示采样时刻智能体的状态,偏差变量e i (lh )=x i (lh )-x^i (lh )㊂注释1㊀在进行动态事件触发条件设计时,可以根据不同的需求为每个智能体设定不同的参数θi ,μi ,δi ,以确保其能够在特定的情境下做出最准确的反应㊂本文为了方便分析,选择为每个智能体设置相同的θi ,μi ,δi ,以便更加清晰地研究其行为表现和响应能力㊂2.2㊀主要结果和分析由于智能体仅在采样时刻进行事件触发条件判断,并在达到触发条件后才通信,因此有x ^i (t -τ)=x^i (lh )㊂定理1㊀假设无向图G 是连通的,对于任意i ɪV 和t >0,当满足条件(12)时,在算法(7)和动态事件触发条件(9)的作用下,系统状态趋于优化解x ∗,即lim t ңx i (t )=x ∗㊂12-β2φm α-τβ2φm αh -γ>0,μi+δi θi <1,μi-1-δi θi >0,ìîíïïïïïïïï(12)式中φm =min{φ1,φ2}㊂证明㊀对于t ɪ[lh +τ,(l +1)h +τ),定义Lyapunov 函数V (t )=V 1(t )+V 2(t ),其中:V 1(t )=ðni =1f i (x ∗)-f i (x i )-f ᶄi (x i )(x ∗-x i )(),V 2(t )=ðni =1ξi (t )㊂令E (t )=e 1(t ), ,e n (t )[]T ,X (t )=x 1(t ), ,x n (t )[]T ,X^(t )=x ^1(t ), ,x ^n (t )[]T ㊂对V 1(t )求导得V ㊃1(t )=1h ðni =1u i (t )x ∗-x i (t )(),(13)由于ðni =1ðnj =1a ij x ^j (t -τ)-x ^i (t -τ)()㊃x ∗=0成立,有V ㊃1(t )=-1hX T (t )LX ^(lh )㊂(14)6山东理工大学学报(自然科学版)2024年㊀由于㊀㊀X (t )=X (lh +τ)-(t -lh -τ)X ㊃(t )=㊀㊀㊀㊀X (lh )+τX ㊃(lh )+t -lh -τhΓ1LX^(lh )=㊀㊀㊀㊀X (lh )-τh Γ2LX^(lh -h )+㊀㊀㊀㊀(t -lh -τ)hΓ1LX^(lh ),(15)式中:Γ1=diag (f i ᶄᶄ(x ~11))-1, ,(f i ᶄᶄ(x ~1n ))-1{},Γ2=diag (f i ᶄᶄ(x ~21))-1, ,(f i ᶄᶄ(x ~2n))-1{},x ~1iɪ(x i (lh +τ),x i (t )),x ~2i ɪ(x i (lh ),x i (lh+τ))㊂将式(15)代入式(14)得㊀V ㊃1(t )=-1h E T (lh )LX ^(lh )-1hX ^T (lh )LX ^(lh )+㊀㊀㊀τh2Γ2X ^T (lh -h )L T LX ^(lh )+㊀㊀㊀(t -lh -τ)h2Γ1X ^T (lh )L T LX ^(lh )㊂(16)根据式(3)得(f i ᶄᶄ(x ~i 1))-1ɤ1φi,i =1, ,n ㊂即Γ1ɤ1φm I n ,Γ2ɤ1φmI n ,φm =min{φ1,φ2}㊂首先对(t -lh -τ)h2Γ1X ^T (lh )L T LX ^(lh )项进行分析,对于t ɪ[lh +τ,(l +1)h +τ),基于引理1和式(3)有(t -lh -τ)h2Γ1X ^T (lh )L T LX ^(lh )ɤβhφm αX ^T (lh )LX ^(lh )ɤβ2hφm αðni =1q i(lh ),(17)式中最后一项根据X^T (t )LX ^(t )=12ðni =1q i(t )求得㊂接着分析τh2Γ2X ^(lh -h )L T LX ^(lh ),根据引理1和杨式不等式有:τh2Γ2X ^T (lh -h )L T LX ^(lh )ɤ㊀㊀㊀㊀τβ2h 2φm αX ^T (lh -h )LX ^(lh -h )+㊀㊀㊀㊀τβ2h 2φm αX ^T (lh )LX ^(lh )ɤ㊀㊀㊀㊀τβ4h 2φm αðni =1q i (lh -h )+ðni =1q i (lh )[]㊂(18)将式(17)和式(18)代入式(16)得㊀V ㊃1(t )ɤβ2φm α+τβ4φm αh -12()1h ðni =1q i(lh )+㊀㊀㊀τβ4φm αh ðni =1q i (lh -h )+1h ðni =1d i e 2i(lh )㊂(19)根据式(11)得V ㊃2(t )=-ðni =1μih ξi(lh )+㊀㊀㊀㊀ðni =1δihγq i (lh -h )-d i e 2i (lh )()㊂(20)结合式(19)和式(20)得V ㊃(t )ɤ-12-β2φm α-τβ4φm αh ()1h ðni =1q i (lh )+㊀㊀㊀㊀τβ4φm αh 2ðn i =1q i (lh -h )+γh ðni =1q i (lh -h )-㊀㊀㊀㊀1h ðni =1(μi -1-δi θi)ξi (lh ),(21)因此根据李雅普诺夫函数的正定性以及Squeeze 定理得㊀V (l +1)h +τ()-V (lh +τ)ɤ㊀㊀㊀-12-β2φm α-τβ4φm αh()ðni =1q i(lh )+㊀㊀㊀τβ4φm αh ðni =1q i (lh -h )+γðni =1q i (lh -h )-㊀㊀㊀ðni =1(μi -1-δiθi)ξi (lh )㊂(22)对式(22)迭代得V (l +1)h +τ()-V (h +τ)ɤ㊀㊀-12-β2φm α-τβ2φm αh-γ()ðl -1k =1ðni =1q i(kh )+㊀㊀τβ4φm αh ðni =1q i (0h )-㊀㊀12-β2φm α-τβ4φm αh()ðni =1q i(lh )-㊀㊀ðlk =1ðni =1μi -1-δiθi()ξi (kh ),(23)进一步可得㊀lim l ңV (l +1)h -V (h )()ɤ㊀㊀㊀τβ4φm αh ðni =1q i(0h )-16第3期㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀夏伦超,等:基于周期采样的分布式动态事件触发优化算法㊀㊀㊀ðni =1(μi -1-δi θi )ðl =1ξi (lh )-㊀㊀㊀12-β2φm α-τβ2φm αh-γ()ð l =1ðni =1q i(lh )㊂(24)由于q i (lh )ȡ0和V (t )ȡ0,由式(24)得lim l ң ðni =1ξi (lh )=0㊂(25)基于ξi 的定义和拉普拉斯矩阵的性质,可以得到每个智能体的最终状态等于相同的常数,即lim t ңx 1(t )= =lim t ңx n (t )=c ㊂(26)㊀㊀由于目标函数的二阶导数具有以下性质:ðni =1d f ᶄi (x i (t ))()d t =㊀㊀㊀㊀-ðn i =1ðnj =1a ij x ^j (t )-x ^i (t )()=㊀㊀㊀㊀-1T LX^(t )=0,(27)式中1=[1, ,1]n ,所以可以得到ðni =1f i ᶄ(x i (t ))=ðni =1f i ᶄ(x ∗i )=0㊂(28)联立式(26)和式(28)得lim t ңx 1(t )= =lim t ңx n (t )=c =x ∗㊂(29)㊀㊀定理1证明完成㊂当不考虑通信时延τ时,可由定理1得到推论1㊂推论1㊀假设通信图G 是无向且连通的,当不考虑时延τ时,对于任意i ɪV 和t >0,若条件(30)成立,智能体状态在算法(7)和触发条件(9)的作用下趋于最优解㊂14-n -1φm -γ>0,μi+δi θi <1,μi-1-δi θi >0㊂ìîíïïïïïïïï(30)㊀㊀证明㊀该推论的证明过程类似定理1,由定理1结果可得14-β2φm α-γ>0㊂(31)令λn =βα,由于λn 是多智能体系统的全局信息,因此每个智能体很难获得,但其上界可以根据以下关系来估计:λn ɤ2d max ɤ2(n -1),(32)式中d max =max{d i },i =1, ,n ㊂因此得到算法在没有时延情况下的充分条件:14-n -1φm -γ>0㊂(33)㊀㊀推论1得证㊂注释2㊀通过定理1得到的稳定性条件,可以得知当采样周期h 取较小值时,由于0<τ<h ,因此二者可以抵消,从而稳定性不受影响;而当采样周期h 取较大值时,τβ2φm αh项可以忽略不计,因此从理论分析可以得出允许采样周期任意大的结论㊂从仿真实验方面来看,当采样周期h 越大,需要的收剑时间越长,但最终结果仍趋于优化解㊂然而,在文献[18]中,采样周期过大会导致稳定性条件难以满足,即算法最终难以收敛,无法达到最优解㊂因此,本文提出的算法允许采样周期任意大,这一创新点具有重要意义㊂3㊀仿真本文对一个具有4个智能体的多智能体网络进行数值模拟,智能体间的通信拓扑如图2所示㊂采用4个智能体的仿真网络仅是为了初步验证所提算法的有效性㊂值得注意的是,当多智能体的数量增加时,算法的时间复杂度和空间复杂度会增加,但并不会影响其有效性㊂因此,该算法在更大规模的多智能体网络中同样适用㊂成本函数通常选择凸函数㊂例如,在分布式传感器网络中,成本函数为z i -x 2+εi x 2,其中x 表示要估计的未知参数,εi 表示观测噪声,z i 表示在(0,1)中均匀分布的随机数;在微电网中,成本函数为a i x 2+b i x +c i ,其中a i ,b i ,c i 是发电机成本参数㊂这两种情境下的成本函数形式不同,但本质上都是凸函数㊂本文采用论文[19]中的通用成本函数(式(34)),用于证明本文算法在凸函数上的可行性㊂此外,通信拓扑图结构并不会影响成本函数的设计,因此,本文的成本函数在分布式网络凸优化问题中具有通用性㊂g i (x )=(x -i )4+4i (x -i )2,i =1,2,3,4㊂(34)很明显,当x i 分别等于i 时,得到最小局部成本函数,但是这不是全局最优解x ∗㊂因此,需要使用所提算法来找到x ∗㊂首先设置重要参数,令φm =16,γ=0.1,θi =1,ξi (0)=5,μi =0.2,δi =0.2,26山东理工大学学报(自然科学版)2024年㊀图2㊀通信拓扑图x i (0)=i ,i =1,2,3,4㊂图3为本文算法(7)解决优化问题(4)时各智能体的状态,其中设置采样周期h =3,时延τ=0.02㊂智能体在图3中渐进地达成一致,一致值为全局最优点x ∗=2.935㊂当不考虑采样周期影响时,即在采样周期h =3,时延τ=0.02的条件下,采用文献[18]中的算法(10)时,各智能体的状态如图4所示㊂显然,在避免采样周期的影响后,本文算法具有更快的收敛速度㊂与文献[18]相比,由于只有当智能体i 及其邻居的事件触发判断完成,才能得到q i (lh )的值,因此本文采用前一时刻的状态值构造动态事件触发条件更符合逻辑㊂图3㊀h =3,τ=0.02时算法(7)的智能体状态图4㊀h =3,τ=0.02时算法(10)的智能体状态为了进一步分析采样周期的影响,在时延τ不变的情况下,选择不同的采样周期h ,其结果显示在图5中㊂对比图3可以看出,选择较大的采样周期则收敛速度减慢㊂事实上,这在算法(7)中是很正常的,因为较大的h 会削弱反馈增益并减少固定有限时间间隔中的控制更新次数,具体显示在图6和图7中㊂显然,当选择较大的采样周期时,智能体的通信频率显著下降,同时也会导致收敛速度减慢㊂因此,虽然采样周期允许任意大,但在收敛速度和通信频率之间需要做出权衡,以选择最优的采样周期㊂图5㊀h =1,τ=0.02时智能体的状态图6㊀h =3,τ=0.02时的事件触发时刻图7㊀h =1,τ=0.02时的事件触发时刻最后,固定采样周期h 的值,比较τ=0.02和τ=2时智能体的状态,结果如图8所示㊂显然,时延会使智能体找到全局最优点所需的时间更长,但由于其受采样周期的限制,最终仍可以对于任意有限延迟达成一致㊂图8㊀h =3,τ=2时智能体的状态36第3期㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀㊀夏伦超,等:基于周期采样的分布式动态事件触发优化算法4 结束语本文研究了无向图下的多智能体系统的优化问题,提出了一种基于动态事件触发机制的零梯度和算法㊂该机制中加入了与前一时刻智能体状态相关的动态变量,避免智能体状态接近最优值时频繁触发产生的通信负担㊂同时,在算法和触发条件设计中考虑了采样周期的影响,在所设计的算法下,允许采样周期任意大㊂对于有时延的系统,在最大允许传输延迟小于采样周期的情况下,给出了保证多智能体系统达到一致性和最优性的充分条件㊂今后拟将本算法向有向图和切换拓扑图方向推广㊂参考文献:[1]杨洪军,王振友.基于分布式算法和查找表的FIR滤波器的优化设计[J].山东理工大学学报(自然科学版),2009,23(5):104-106,110.[2]CHEN W,LIU L,LIU G P.Privacy-preserving distributed economic dispatch of microgrids:A dynamic quantization-based consensus scheme with homomorphic encryption[J].IEEE Transactions on Smart Grid,2022,14(1):701-713.[3]张丽馨,刘伟.基于改进PSO算法的含分布式电源的配电网优化[J].山东理工大学学报(自然科学版),2017,31(6):53-57.[4]KIA S S,CORTES J,MARTINEZ S.Distributed convex optimization via continuous-time coordination algorithms with discrete-time communication[J].Automatica,2015,55:254-264.[5]LI Z H,DING Z T,SUN J Y,et al.Distributed adaptive convex optimization on directed graphs via continuous-time algorithms[J]. IEEE Transactions on Automatic Control,2018,63(5):1434 -1441.[6]段书晴,陈森,赵志良.一阶多智能体受扰系统的自抗扰分布式优化算法[J].控制与决策,2022,37(6):1559-1566. [7]DIMAROGONAS D V,FRAZZOLI E,JOHANSSON K H.Distributed event-triggered control for multi-agent systems[J].IEEE Transactions on Automatic Control,2012,57(5):1291-1297.[8]KAJIYAMA Y C,HAYASHI N K,TAKAI S.Distributed subgradi-ent method with edge-based event-triggered communication[J]. IEEE Transactions on Automatic Control,2018,63(7):2248 -2255.[9]LIU J Y,CHEN W S,DAI H.Event-triggered zero-gradient-sum distributed convex optimisation over networks with time-varying topol-ogies[J].International Journal of Control,2019,92(12):2829 -2841.[10]COUTINHO P H S,PALHARES R M.Codesign of dynamic event-triggered gain-scheduling control for a class of nonlinear systems [J].IEEE Transactions on Automatic Control,2021,67(8): 4186-4193.[11]CHEN W S,REN W.Event-triggered zero-gradient-sum distributed consensus optimization over directed networks[J].Automatica, 2016,65:90-97.[12]TRAN N T,WANG Y W,LIU X K,et al.Distributed optimization problem for second-order multi-agent systems with event-triggered and time-triggered communication[J].Journal of the Franklin Insti-tute,2019,356(17):10196-10215.[13]YU G,SHEN Y.Event-triggered distributed optimisation for multi-agent systems with transmission delay[J].IET Control Theory& Applications,2019,13(14):2188-2196.[14]LIU K E,JI Z J,ZHANG X F.Periodic event-triggered consensus of multi-agent systems under directed topology[J].Neurocomputing, 2020,385:33-41.[15]崔丹丹,刘开恩,纪志坚,等.周期事件触发的多智能体分布式凸优化[J].控制工程,2022,29(11):2027-2033. [16]LU J,TANG C Y.Zero-gradient-sum algorithms for distributed con-vex optimization:The continuous-time case[J].IEEE Transactions on Automatic Control,2012,57(9):2348-2354. [17]LIU K E,JI Z J.Consensus of multi-agent systems with time delay based on periodic sample and event hybrid control[J].Neurocom-puting,2016,270:11-17.[18]ZHAO Z Y.Sample-baseddynamic event-triggered algorithm for op-timization problem of multi-agent systems[J].International Journal of Control,Automation and Systems,2022,20(8):2492-2502.[19]LIU J Y,CHEN W S.Distributed convex optimisation with event-triggered communication in networked systems[J].International Journal of Systems Science,2016,47(16):3876-3887.(编辑:杜清玲)46山东理工大学学报(自然科学版)2024年㊀。
压缩语段

下面是5月21日某报刊发的一则消息,请概括 其主要信息。(不超过60字) (2002北京高考题) 5月27日至28日,“志愿服务国际会议”将在北 京召开。届时,来自世界五大洲和近30个国家及 联合国有关方面的160多名代表将出席会议。这次 会议是由团中央和联合国开发计划署联合主办的。 据了解,会议以“新世纪的志愿服务:认知、 支持、发展”为主题,旨在借助国际志愿者年形 成的社会舆论氛围,提高社会各界对志愿服务理 念的认识,促进各国政府和公众进一步认可志愿 者对社会所做出的贡献,积极支持和参与志愿服 务,推动全球志愿服务事业的向前发展。 答案:5月27日至28日,由团中央和联合国开发计 划署主办的“志愿服务国际会议”将在北京召开, 会议的主题是“认知、支持、发展”。
2014-10-12 4
题型示例
下面是发掘杭州雷峰塔地宫的一段报道。请将 关于地宫开启过程的文字进行压缩,不出现具体 时间,不超过35个字。(4分) (2003年全国卷) 上午9时整,考古队进入现场开始发掘。打开 参考答案一:移开地宫口的巨石露出盖 地宫并不容易,直到 9时45分,考古人员才将压在 板,清理盖板并绘图,撬开盖板打开地宫。 地宫洞口的 750公斤重的巨石移开,露出93厘米长 参考答案二:先移开地宫口的巨石露出 宽、 13 厘米厚的大理石盖板。盖板上没有任何文 盖板,然后清理盖板并绘图,最后撬开盖板 字,但考古人员在紫红色的泥土中发现了 10枚唐 打开地宫。 10时5分盖板基本清理完毕。10时 开元通宝铜钱。 30分盖板绘图完毕。11时整盖板还没有打开,发 掘现场发现越来越多的钱币。 11时11分,最激动 人心的时候到了,考古人员开始用撬杠撬开盖板。 11时18分,考古人员翻开大理石盖板,地宫口终 于打开了!
2014-10-12 6
Selective Markov Models for Predicting Web-Page Accesses

Selective Markov Models for Predicting Web-PageAccesses∗Mukund Deshpande and George KarypisUniversity of Minnesota,Department of Computer Science/Army HPC Research CenterMinneapolis,MN55455Technical Report#00-056{deshpand,karypis}@Last updated on October30,2000at10:52amAbstractThe problem of predicting a user’s behavior on a web-site has gained importance due to the rapid growth of the world-wide-web and the need to personalize and influence a user’s browsing experience.Markov models and their variations have been found well suited for addressing this problem.Of thedifferent variations or Markov models it is generally found that higher-order Markov models display highpredictive accuracies.However higher order models are also extremely complicated due to their largenumber of states that increases their space and runtime requirements.In this paper we present differenttechniques for intelligently selecting parts of different order Markov models so that the resulting modelhas a reduced state complexity and improved prediction accuracy.We have tested our models on variousdatasets and have found that their performance is consistently superior to that obtained by higher-orderMarkov models.Keywords:world wide web,web mining,Markov models,predicting user behavior.∗This work was supported by NSF CCR-9972519,EIA-9986042,ACI-9982274,by Army Research Office contract DA/DAAG55-98-1-0441,by the DOE ASCI program,and by Army High Performance Computing Research Center contract num-ber DAAH04-95-C-0008.Access to computing facilities was provided by AHPCRC,Minnesota Supercomputer Institute.Related papers are available via WWW at URL:/˜karypis1IntroductionIn recent years,the problem of modeling and predicting a user’s surfing behavior on a web-site has attracted a lot of research interest as it can be used to improve the web cache performance[SKS98,Bes95,PM96], recommend related pages[DH99,PPR96],improve search engines[BP98],understand and influence buying patterns[CPM+98],and personalize the browsing experience[PP99].The significance of this problem is ev-ident by the fact that at the SIGKDD2000Conference[KB00]the problem of predicting and understanding a user’s browsing and purchasing behavior was the topic of the KDDCup2000Competition.Markov models[Pap91]have been used for studying and understanding stochastic processes,and were shown to be well-suited for modeling and predicting a user’s browsing behavior on a web-site.In general, the input for these problems is the sequence of web-pages that were accessed by a user and the goal is to build Markov models that can be used to model and predict the web-page that the user will most likely access next.Padbanabham and Mogul[PM96]use N-hop Markov models for improving pre-fetching strategies for web caches.Pitkow et al.[PP99]proposed a longest subsequence models as an alternative to the Markov model.Sarukkai[Sar00]use Markov models for predicting the next page accessed by the user.Cadez et al.[CHM+00]use Markov models for classifying browsing sessions into different categories.In many applications,first-order Markov models are not very accurate in predicting the user’s browsing behavior,since these models do not look far into the past to correctly discriminate the different observed patterns.As a result,higher-order models are often used.Unfortunately,these higher-order models have a number of limitations associated with high state-space complexity,reduced coverage,and sometimes even worse prediction accuracy.One simple method to overcome some of these problems is to train varying order Markov models and use all of them during the prediction phase,as is done in the All-K th-Order Markov model proposed in[PP99].However,this approach further exacerbates the problem of state-space complexity.An alternate approach proposed by Pitkow et al.[PP99]is to identify patterns of frequent accesses,which they call longest repeating subsequences,and then use this set of sequences for prediction. However,even though this approach is able to reduce the state-space complexity by up to an order of magnitude,it also reduces the prediction accuracy of the resulting model.In this paper we present techniques for intelligently combining different order Markov models so that,the resulting model has a low state complexity,improved prediction accuracy,and retains the coverage of the All-K th-Order Markov models.The key idea behind our work is that many of the states of the different order Markov models can be eliminated without affecting the performance of the overall scheme.In particular, we present three schemes for pruning the states of the All-K th-Order Markov model,called(i)support pruning(ii)confidence pruning(iii)error pruning.Our experiments on a variety of data sets have shown that the proposed pruning schemes consistently outperform the All-K th-Order Markov model and other single-order Markov models,both in term of state complexity as well as improved prediction accuracy.For many problems,our schemes prune up to90%of the states from the All-K th-Order Markov model,and improve the accuracy by up to11%.Even though our algorithms were developed in the context of web-usage data,we have successfully used these techniques for prediction in different applications,as well.For example,these models were used to predict the next command typed by the user in word processor based on his/her past sequence of commands or for predicting the alarm state of telephone switches based on its past states.These applications will be discussed in detail in Section4.1.The rest of this paper is organized as follows.Section2presents an overview of Markov models followed by a brief overview of the problem of predicting a user’s browsing behavior.Section3presents a detaileddescription of our selective Markov models.Section4provides a detailed experimental evaluation of our algorithms on a variety of data sets.Finally,Section5offers some concluding remarks.2Markov Models for Predicting User’s ActionsAs discussed in the introduction,techniques derived from Markov models have been extensively used for predicting the action a user will take next given the sequence of actions he or she has already performed. For this type of problems,Markov models are represented by three parameters<A,S,T>,where A is the set of all possible actions that can be performed by the user;S is the set of all possible states for which the Markov model is built;and T is a|S|×|A|Transition Probability Matrix(TPM),where each entry t i j corresponds to the probability of performing the action j when the process is in state i.The state-space of the Markov model depends on the number of previous actions used in predicting the next action.The simplest Markov model predicts the next action by only looking at the last action performed by the user.In this model,also known as thefirst-order Markov model,each action that can be performed by a user corresponds to a state in the model.A somewhat more complicated model computes the predictions by looking at the last two actions performed by the user.This is called the second-order Markov model, and its states correspond to all possible pairs of actions that can be performed in sequence.This approach is generalized to the K th-order Markov model,which computes the predictions by looking at the last K actions performed by the user,leading to a state-space that contains all possible sequences of K actions.For example,consider the problem of predicting the next page accessed by a user on a web site.The input data for building Markov models consists of web-sessions,where each session consists of the sequence of the pages accessed by the user during his/her visit to the site.In this problem,the actions for the Markov model correspond to the different pages in the web site,and the states correspond to all consecutive pages of length K that were observed in the different sessions.In the case offirst-order models,the states will correspond to single pages,in the case of second-order models,the states will correspond to all pairs of consecutive pages,and so on.Once the states of the Markov model have been identified,the transition probability matrix can then be computed.There are many ways in which the TPM can be built.The most commonly used approach is to use a training set of action-sequences and estimate each t ji entry based on the frequency of the event that action a i follows the state s j.For example consider the web-session W S2({P3,P5,P2,P1,P4})shown in Figure1.If we are usingfirst-order Markov model then each state is made up of a single page,so the first page P3corresponds to the state s3.Since page p5follows the state s3the entry t35in the TPM will be updated.Similarly,the next state will be s5and the entry t52will be updated in the TPM.In the case of higher-order model each state will be made up of more than one actions,so for a second-order model thefirst state for the web-session W S2consists of pages{P3,P5}and since the page P2follows the state {P3,P5}in the web-session the TPM entry corresponding to the state{P3,P5}and page P2will be updated.Once the transition probability matrix is built making prediction for web sessions is straight forward.For example,consider a user that has accessed pages P1,P5,P4.If we want to predict the page that will be accessed by the user next,using afirst-order model,we willfirst identify the state s4that is associated with page P4and look up the TPM tofind the page p i that has the highest probability and predict it.In the case of our example the prediction would be page P5.Web Sessions:W S1:{P3,P2,P1}W S2:{P3,P5,P2,P1,P4}W S3:{P4,P5,P2,P1,P5,P4} W S4:{P3,P4,P5,P2,P1}W S5:{P1,P4,P2,P5,P4}1st Order P1P2P3P4P5 s1={P1}00021 s2={P2}40001 s3={P3}01011 s4={P4}01002 s5={P5}030202nd Order P1P2P3P4P52nd Order P1P2P3P4P5{P1,P4}01000{P3,P5}01000{P1,P5}00010{P4,P2}00001{P2,P1}00011{P4,P5}02000{P2,P5}00010{P5,P2}30000{P3,P2}10000{P3,P4}00001Figure1:Sample web sessions with the corresponding1st&2nd order Transition Probability Matrices.2.1Limitations of Markov ModelsIn many applications,first-order Markov models are not successful in predicting the next action to be taken by the user.This is because these models do not look far into the past to correctly discriminate the different behavioral modes of the different users.As a result,in order to obtained good predictions higher-order models must be used(e.g.,second and third).Unfortunately,these higher-order models have a number of limitations associated with(i)high state-space complexity,(ii)reduced coverage,and(iii)sometimes even worse prediction accuracy.The number of states used in these models tend to rise exponentially as the order of the model increases. This is because,the states of higher-order models are nothing but different combinations of the actions ob-served in the dataset.This dramatic increase in the number of states can significantly limit the applicability of Markov models for applications in which fast predictions are critical for real-time performance or in appli-cations in which the memory constraints are tight(e.g.embedded models for web-access caching[PM96]). Furthermore,there may be many examples in the test set that do not have corresponding states in higher-order Markov model;thus,reducing their coverage.In such scenarios higher-order models must make a default prediction that can lead to lower accuracies.To better understand these shortcomings we conducted an experiment on one of our web datasets.We compared various higher-order Markov models starting from thefirst all the way to thefifth order Markov model.If a higher-order model was unable to make a prediction for a particular web-session,it was ignored from accuracy calculations(i.e.,the accuracy is calculated only on those examples on which the prediction was made).The results are plotted in Figure2,and we can see that as the order of the model increases the accuracy increases accompanied by a decrease in the coverage.At the same time,as the order of the model increases,the number of states used for the model also increase dramatically.One simple method to overcome the problem of low coverage is to train varying order Markov models and then combine them for prediction[PP99].In this scheme,for each test instance,the highest-order Markov model that covers the instance is used for prediction.For example,if we build thefirst,second, and third-order Markov models,then given a test instance,wefirst try to make a prediction using the third-order model.If this model does not contain the corresponding state,then we try to make a prediction using the second-order model,and so on.This scheme is called the All-K th-Order Markov model[PP99].Note that even though the All-K th-Order Markov model solves the problem of low coverage it exacerbates theFigure2:Plot comparing accuracy,coverage and model size with the order of Markov model.problem of model size,as the states of all the different order models are part of the model.Finally,as the number of states in higher-order Markov models increase the number of training-set in-stances used to compute the state-action transition probabilities for each of the states tends to decrease.A consequence of this reduction in the support of individual states,is that some of the estimated state-action transition probabilities are not accurate.As a result,the overall accuracy achieved by higher-order Markov models can sometimes be lower that achieved by the corresponding lower-order Markov models.3Selective Markov ModelsAs discussed in the previous section,All-K th-Order Markov model holds the promise of achieving higher prediction accuracies and improved coverage than any single-order Markov model,at the expense of a dra-matic increase in the state-space complexity.This led us to develop techniques for intelligently combining different order Markov models so that the resulting model has low state complexity,improved prediction accuracy,and retains the coverage of the All-K th-Order Markov model.Our schemes were motivated by the observation that given a sequence of actions for which we need to predict the next most probable action,there are multiple states in the All-K th-Order Markov model that can be used to perform that prediction.In fact,there can be as many states as the number of the different order Markov models used to form the All-K th-Order Markov model.Now,depending on the particular set of states involved,each of them can have different prediction accuracies.Based on this observation,we can then start from the All-K th-Order Markov model and eliminate many of its states that are expected to have low prediction accuracy.This will allow us to reduce the overall state complexity without affecting the performance of the overall scheme.The starting point for all of our algorithms is the All-K th-Order Markov model obtained by building asequence of increasing order Markov models.However,instead of using this model for prediction,we use a number of techniques to eliminate certain states across the different order Markov models.The set of states that survive this step,then become thefinal model used for prediction.The goals of this pruning step is primarily to reduce the state complexity and secondarily improve the prediction accuracy of the resulting model.We will refer to these models as selective Markov models.The key step in our algorithm is the scheme used to determine to potential accuracy of a particular state. In the rest of this section we present three different schemes with an increasing level of complexity.The first scheme simply eliminates the states that have very low support.The second scheme uses statistical techniques to identify states for which the transition probabilities to the two most prominent actions are not statistically significant.Finally,the third scheme uses an error-based pruning approach to eliminate states with low prediction accuracy.3.1Support-Pruned Markov ModelThe support-pruned Markov model(SPMM)is based on the observation that states that have low support in the training set tend to also have low prediction accuracies.Consequently,these low support states can be eliminated without affecting the overall accuracy as well as coverage of the resulting model.The amount of pruning in the SPMM scheme is controlled by the parameterφreferred to as the frequency threshold.In particular,SPMM eliminates all the states of the different order Markov models that are supported by fewer thanφtraining-set instances.There are a number of observations to be made about the SPMM scheme.First,the same frequency threshold is used for all the models regardless of their order.Second,this pruning policy is more likely to prune higher-order states as higher order states have less support;thus dramatically reducing the state-space complexity of the resulting scheme.Third,the frequency threshold parameterφ,specifies the actual number of training-set instances that must be supported by each state and not the fraction of training-set instances as it is often done in the context of association rule discovery[AIS93].This is done primarily for the following two reasons:(i)the trust-worthiness of the estimated transition probabilities of a particular state depend on the actual number of training-set instances and not on the relative number;(ii)the total number of training-set instances is in general exponential on the order of the Markov model,thus the same fractional pruning threshold will have a completely different meaning for the different order Markov models.3.2Confidence-Pruned Markov ModelOne of the limitations of the SPMM scheme is that it does not capture all the parameters that influence the accuracy of the state.In particular the probability distribution of outgoing actions from a state is completely ignored.For example,consider a Markov state which has two outgoing actions/branches,such that one of them is substantially more probable than the other.Even if the overall support of this state is somewhat low, the predictions computed by this state will be quite reliable because of the clear difference in the outgoing probabilities.On the other hand,if the outgoing probabilities in the above example are very close to each other,then in order for that difference to be reliable,they must be based on a large number of training instances.Ideally,we would like the pruning scheme to not only consider the support of the state but also weigh the probability distribution of the outgoing actions before making its pruning decisions.This observation led to us to develop the confidence-pruned Markov model(CPMM)scheme.CPMM uses statistical techniques to determine for each state,if the probability of the most frequently taken action is significantly different from the probabilities of the other actions that can be performed from this state.If theprobability differences are not significant,then this state is unlikely to give high accuracy and it is pruned. In contrast,if the probability differences are significant the state is retained.The CPMM scheme determines if the most probable action is significantly different than the second most probable action by computing the100(1−α)percent confidence interval around the most probable action and checking if the probability of the second action falls within that interval.If this is true,then the state is pruned,otherwise it is retained.Ifˆp is the probability of the most probable action,then its100(1−α) percent confidence interval is given byˆp−zα/2ˆp(1−ˆp)n≤p≤ˆp+zα/2ˆp(1−ˆp)n,(1)where zα/2is the upperα/2percentage point of the standard normal distribution and n is the frequency of the Markov State[MR94].The degree of pruning in CPMM is controlled byα(confidence coefficient).As the value ofαdecreases the size of the confidence interval increases,resulting in more pruning.Also note,that if a state has a large number of examples associated with it,then Equation1will compute a tighter confidence interval.As a result,even if the difference in the probabilities between the two most probable actions is relatively small, the state will most likely be retained.As our earlier discussion indicated this feature is desirable.3.3Error-Pruned Markov ModelIn the previous schemes we used either the support of a state or the probability distribution of its outgoing branches to gauge the potential error associated with it.However,the error of each state can be also auto-matically estimated and used to decide whether or not to prune a particular state.A widely used approach to estimate the error associated with each state is to perform a validation step.During the validation step, the entire model is tested using part of the training set(validation set)that was not used during the model building phase.Since we know the actual actions performed by the sequences in the validation set,we can easily determine the error-rates and use them for pruning.This led us to develop the error pruned Markov model(EPMM)scheme.Specifically,we have developed two different error-based pruning strategies that use a different definition as to what constitutes the error-rate of a Markov state.We will refer to these schemes as overall error pruning and individual error pruning.The overall error pruning scheme works as follows.First,for each sequence in the validation set we use each one of the K single-order Markov models to make a prediction.For each prediction we record whether that prediction was correct or not.Once all the sequences in the validation set have been predicted,we use these prediction statistics to calculate the error-rate of each state.Next,for each state of the highest-order Markov model we identify the set of states in the lower-order models that are its proper subsets.For example,if the highest-order state corresponds to the action-sequence{a5,a3,a6,a7},then the lower-order states that are identified are{a3,a6,a7}(third-order),{a6,a7}(second-order)and{a7}(first-order).Now if the error-rate of the highest-order state is higher than any of its subset lower-order sates,it is pruned.The same procedure of identifying the subset states and comparing their error-rates is repeated for all the states in the lower-order Markov models as well,except thefirst-order Markov model.The states from thefirst-order Markov model are never pruned so as not to reduce the coverage of the resulting model.In the second scheme wefirst iterate over all the higher-order states,and for each of them wefind its subset states(as described in the previous scheme).Then,we identify all the examples in the validation set that can be predicted using the higher-order state(i.e.,the validation examples which have a sequence ofactions corresponding to the higher-order state).This set of examples are then predicted by the higher-order state and its subset states and the error-rates on these examples for each one of the states is computed.If the error-rate of the higher-order state is greater than any of its subset states,the higher-order Markov state is pruned.The same procedure is repeated for all the lower-order Markov models except thefirst-order Markov model.Though both schemes follow a similar procedure of locating subset states and pruning the ones having high error-rates,they differ on how the error-rates for each state is computed.In thefirst scheme,every lower-order Markov state has a single error-rate value that is computed over the entire validation set.In the second scheme,each of the lower-order Markov states will have many error-rate values as it will be validated against a different set of examples for each one of its superset higher-order states.4Experimental ResultsWe experimentally evaluated the performance of the proposed Selective Markov models on a variety of data sets.In the rest of this section we briefly describe these data sets,our experimental methodology,and present the results obtained by our schemes.4.1DatasetsWe have evaluated the performance of the proposed Selective Markov models schemes on four datasets, whose characteristics are shown in the Table1.Dataset#Sessions Avg.Ses.Length#of unique actionsEC1234,954 3.18967874EC2144,3677.939336,554OWL22,884 3.26735160TC1142,983 2.67119151Table1:Preliminary dataset statistics.•ECommerce Web Logs:We used the web server logs from two large E-Commerce companies for our analysis.These logs werefirst cleaned using the WebSIFT system[CTS99]and then broken down into series of sessions,each session corresponds to the sequence of web pages accessed by the user during his/her visit to the site.Note that the session contains only the accesses to web pages and accesses to images are ignored.In our model each session corresponds to an example in the train/test set and the page accessed by the user is considered as an action.These two datasets will be referred as EC1and EC2.From Table1we can see that EC1has a total of234,954sessions,an average length of3.18pages/sessions and a total of874unique web-pages.Similarly,EC2has144,367sessions of average length7.93pages/sessions and about6,554unique web-pages.•OWL Dataset:This dataset contains the log of editing commands typed by different users in Mi-crosoft Word over a period of2years[Lin00].The goal of the model built on this dataset was to predict the next command typed by the user based on the user’s past sequence of commands.Such predictive system could be used to make online recommendations to the user about commands which could be typed next.This dataset will be referred as OWL.In this dataset,each session corresponds to the sequence of commands typed by a user on a particular document in one sitting.The different commands typed by the users constitute as the actions of the Markov model.•Telephone Switch Dataset:This dataset was obtained from a large telecommunications company which maintains nationwide telephone networks.The dataset contains the log of different alarms generated by a telephone switch over a period of one month.Each session in this dataset corresponds to the sequence of alarms given out by the switch that are related to the same problem.For this dataset the alarm generated by the switch is considered as an action.This dataset will be referred as TC1.4.2Experimental Design&MetricsTo make the evaluation of different schemes manageable,we limit ourselves to the problem of predicting just the last action of a test example/session.For evaluation purposes we divide the complete dataset into training set and test set.Depending on the model,the training set may further be divided into a validation set. During the testing step the model is given a trimmed session for prediction i.e.,the last part of the session is removed.The prediction made by the model is then compared with the removed part of the session to compute model’s accuracy.In some cases,Markov model based schemes are unable to make a prediction for a session in the test set.This could be either because the length of test session is less than the order of the model or the model has not seen a similar session in the training step.In our evaluation scheme we will only consider sessions which are longer than the highest-order of the model and if a model is unable to predict for these long sessions,it is considered as a wrong prediction.In all of our experiments,for both the All-K th-Order Markov model and selective Markov model schemes we combinedfirst-,second-,and third-order Markov models,i.e.,K=3.The overall performance of the various Markov model-based algorithms were evaluated in terms of their accuracy and their model size.The accuracy of a model is defined as the number of correct predictions divided by the total number of predictions,and the model size is defined as the total number of states in the model.Accuracy measures the predictive ability of the model,whereas the model size gives us an insight into the memory and time requirements of the model.4.3Results for Support Pruned Markov ModelThe goal of ourfirst set of experiments was to study the effect of the frequency threshold(φ)parameter on the performance of the support-pruned Markov model.To achieve this we performed an experiment in which we used different values forφranging from0(no pruning)up to24in increments of two,and measured both the accuracy as well as the number of states in the resulting Markov model.These results are shown in Table2for the four different data sets in our experimental testbed.To better visualize the results we plotted the accuracy obtained by the SPMM scheme for different values ofφover that obtained whenφ=0(i.e.,the original All-K th-Order Markov model).These plots are shown in Figure3.A number of interesting observations can be made by looking at Figure3.First,for all four data sets we can see that in the beginning the increase in the frequency threshold is accompanied by an increase in the accuracy for the SPMM.In particular,accuracy improvements for the EC1and OWL datasets are quite substantial.Second,as we continue to further increase the frequency threshold the accuracy achieved on the different datasets starts toflatten out or even decrease.For EC1and EC2datasets the overall accuracy remains about the same,whereas there is sharp drop for both OWL and the TC1datasets.The decrease in the overall accuracy for increasing values of theφis because some useful Markov states are being pruned from the model;thus,affecting its overall accuracy.Third,each one of the four datasets achieve their maximum accuracy levels at different values of the frequency threshold,indicating that the optimal value ofφis dataset dependent.Fourth,the overall accuracy tends to change smoothly withφ;thus,making it possible to use a。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
跨国公司进军我国的利与弊:利: 引进资本和技术,促进我国经济发展,利于我国经济同世界经济接轨.
弊: 对我国传统工业造成冲击
⑻ 西气东输、西电东送工程对东、西部地区影响:
① 对西部的意义:
a.改变西部的能源消费结构,促进西部地区生态建设,利于退耕还林和水土保持;
b. 带动相关产业发展,调整产业结构;
c. 增加就业机会;d. 有利于加强基础设施的建设。
② 对东部地区:缓解东部地区能源紧张状况;改善能源消费结构,保护环境
1.降水:当地气候特征情况;迎风坡降水多,雪线低(eg.喜玛拉雅山南坡比北坡雪线低)
2.气温:阳坡雪线高于阴坡;不同纬度的温度变化、0℃等温线的海拔的高低
☆影响山地垂直带谱的因素:
⑵ 我国能源消费利用变化特点:
煤炭比例下降,石油、天然气、水电、核电比例上升。
⑶ 我国主要的核电站:广东-大亚湾、岭澳;浙江-秦山;江苏-田湾等。
建设原因:常规能源分布少;人口集中,工农业发达,能源需求大。
⑷ 目前能源利用紧张原因:
① 我国经济发展速度快,能源需求量大;
十六、文化小专题:
⑵ 为什么说都江堰是顺应了自然规律?
① 既可防洪又可灌溉② 没有带来环境污染和生态破坏
变式:为什么说江南丘陵的梯田顺应了自然规律? ① 丘陵地区坡度较小,开垦梯田后,既没有造成环境污染,也没有造成水土流失等生态问题;②开垦梯田后,既充分利用了地形、光热等自然资源,又使农业得以充分发展。
6.下垫面:地面反射率(冰雪反射率大,气温低);绿地气温日、年较差小于裸地
7.人类活动:热岛效应、温室效应等
☆影响降水的因素:
1.气候:大气环流(气压带、风带、季风)
2.地形:迎风坡、背风坡
3.地势(海拔高度):降水在一定高度达最大值
4.海陆位置:距海远近
⑻ 西亚地区倍受西方列强关注,原因:① 西亚石油资源丰富,是西方列强主要的能源供应地;② 地处两洋三洲五海之地,交通、战略位置重要.
港口的建设:上海、纽约、天津等
⑴ 荷兰的鹿特丹的区位因素:
自然区位:① 位于莱茵河口,河海联运便利;
② 港阔水深,不淤不冻;③地形平坦,有利于建港口。
2.地形(高度、地势):阴坡、阳坡,不同海拔高度的山地、平原、谷地、盆地(如:谷地盆地地形热量不易散失,高大地形对冬季风阻挡,同纬度山地比平原日较差、年较差小等)
3.海陆位置:海洋性强弱引起气温年较差变化
4.洋流:暖流:增温增湿;寒流:降温减湿
5.天气状况:云雨多的地方气温日、年较差小于云雨少的地方
⑤ 稳妥发展核电;⑥因地制宜地发展沼气、太阳能、水能、风能、海洋能等;
⑦ 加大技术革新,提高能源的利用率;⑧加强宣传,提高公民节约能源的意识;
⑨ 实现产业升级,适当限制耗能大的工业发展;⑩利用乙醇汽油。
⑹ 中哈输油管道的建设是两国双赢的结果原因:
① 哈萨克斯坦可以将石油资源优势转化为经济优势;促进哈萨克斯坦
社会经济因素:经济腹地广阔;以鹿特丹 为依托;
位于第二条欧亚大陆桥的终点,连接欧亚大陆两岸
⑵ 上海港的区位因素不利方面:
三角洲地形坡度缓,水流慢,泥沙容易淤积,影响通航。
十九、三峡工程小专题:
意义:① 防洪(提高荆江河段防洪标准;缓解洪水对武汉市的威胁;
减轻洞庭湖淤积;大幅度减少分蓄洪造成的损失)
⑷ 在规划黄山旅游规模时应注意的问题是:旅游活动的规模与黄山游览区的环境承载量相适应
⑸ 黄山与庐山较好协调了旅游活动的规模与黄山游览区的环境承载量的关系,均获"世界人类和自然遗产"殊荣,成为著名旅游区
⑹ 制约黄山夏季旅游游客数量的最主要因素是:环境承载量
⑺ 黄山与庐山两地开发条件不同,主要原因是:环境承载量;地区接待能力
① 400毫米等降水量线通过的地方② 季风区与非季风区分界线;
③ 内流区与外流区的分界线; ④ 牧区与农耕区通过的地方;
⑤ 内蒙古高原和东北平原的界线
⑥ 我国地势第二级阶梯与第三级阶梯的界线;
⑧森林景观与草原景观界线。
(思路:地形界线、气候(气温、降水、风)界线、植被界线、农业界线)
芝加哥是美国中部商业中心的原因。
⑸ 世界主要金融中心
① 世界著名国际金融中心:纽约、伦敦、苏黎世
② 世界主要国际金融中心:巴黎、法兰克福、东京、香港
二十二、我国重要的地理界线:
⑴ 秦岭一淮河一线是我国的一条重要地理分界线,这条线的南北景观有很大的差异:
① 黄土高原的南界;②大致是1月0℃等温线、800毫米等降水量线通过的地方;
⑶ 庐山黄山比较:① 游览价值:黄山大,庐山小;② 市场距离:黄山较短,庐山较长;③ 地区接待能力:黄山较小,庐山较大;④ 交通通达性:黄山道路较少,交通不便;庐山有京九铁路和长江航线,通达度较好。⑤环境承载量:黄山缺少较大平台,环境承载量较小;庐山有较大平台,生活、服务设施齐全,环境承载量大
⑶ 中国为什么要加入WTO? ① 当前世界国家、地区间的经济联系日益密切;② 可增强我国与世界各国的经济交流,提高我国企业技术和管理水平,增强产品的竞争力,改善出口商品构成;③利于改变国际经济旧秩序,提高我国在世界贸易格局中的地位。
⑷ 解决发展中国家经济发展的关键是:改变国际经济旧秩序,建立起相互尊重主权、平等互利的国际经济新秩序
二十一、商业贸易与金融小专题:
⑴ 商业中心形成的条件:
① 周围有稳定的商品来源区和销售区;②便利的交通运输条件,便于商品集散。
⑵ 商业网点的组织形式:
人口密集、交通方便的地区(大城市)-----商业街和商业小区
人口稀少地区--------货郎担、大篷车等流动形式
⑶ 商业中心的布局原则和区位:
5.洋流:暖流:增温增湿;寒流:降温减湿
6.下垫面:湖泊、河流、植被覆盖状况
7.人类活动:改变下垫面影响降水
☆描述河流的水文特征:
1.流量:大小、季节变化、有无断流(取决于降水特征、雨水补给、河流面积大小)
2.含沙量:取决于流域的植被状况
3.结冰期:有无、长短
(8) 对黄山开发为旅游区的影响作出评价:
利:增加地区的经济收入,带动相关产业发展;增加就业机会,促进经济发展。
弊:环境污染、动植物的破坏、背景环境的破坏、文物古迹的破坏、对正常社会秩序的冲击
(9)对黄山的开发条件作出评价:(从游览价值方面分析) ①"黄山天下奇",具有较高的美学价值和科学价值,质量较高;② 集群状况优良;③ 附近没有雷同景点,具有较好的地域组合状况。
移 民方针:开发性移民---------通过发展经济来安置移民
开发性移民好处:开发性移民把移民安置和库区经济发展结合起来,两者相互
促进,有利于移民的长治久安
二十、能源小专题:
⑴ 我国能源利用的现状:
以煤炭为主,利用石油、天然气,积极发展水电,稳妥发展核电,因地制宜
发展太阳能、风能、沼气、地热能、海洋能等。
② 我国耗能大的工业发展快,加剧了能源紧张;
③ 能源利用率低,浪费严重;
④ 能源勘探、开采跟不上国民经济需求;
⑤ 国际石油价格上涨;
⑥ 我国缺少石油储备体系。
⑸ 调整措施:
① 采取多元化战略,进口石油;② 建立石油储备体系;
③ 加大能源勘探、采取,增加能源产量;④加快西电东送、西气东输工程建设;
⑶ 民族风情、民族的节日元宵节舞龙灯--汉族 泼水节--傣族 那达慕大会--蒙古族
芦笙节--苗族 火把节---彝族
十七、黄山与庐山旅游问题:
⑴ 欣赏黄山云海,最佳季节是夏季,最佳天气是雨过天晴。
⑵ 黄山四绝中的"怪石"在游览时,应选择特定的观赏位置才能欣赏到这些岩石地貌的酷似造型.
第二版块 应用案例模板
自然地理部分
☆如何描述地形特征:
1.地形类型:平原、山地、丘陵、高原、盆地等
2.地势起伏状况
3.主要地形分布(多种地形条件下)
4.重要地形剖面特征(剖面图中)
☆影响气温的因素:
1.纬度(决定因素):影响太阳高度、昼长、太阳辐射量、气温日较差,年较差(低纬度地区气温日、年较差小于高纬度地区)
(10)西欧旅游业发达的原因:① 欧洲西部自然条件多种多样,自然景观丰富;② 历史文化灿烂,各地有独特的风土人情,人文景观丰富;③欧洲西部经济发达,交通便利,为旅游业发展提供了有利条件。
十八:政治经济地理格局小专题:
⑵ 我国(发展中国家)如何吸引外来直接投资,促进经济发展:①持续的改革,改善投资环境,吸引投资商;② 制定有效的产业政策:在经济发达地区发展:知识和技术密集型产业。在经济欠发达地区发展:劳动密集和资源密集型产业。③ 加大教育投入提高人口素质;④争取国内、国际稳定的政治局势。
② 发电(缓解华中、华东地区能源紧张状况)③变输煤为输电,减轻铁路运输的压力;
③ 水电代替火电,环境效益十分显著);
④ ⑤ 航运、供水和灌溉、南水北调、水产养殖、旅游。
成败的关键:移民
移民安置最大困难:库区移民环境容量不足
移民安置政策:本地安置(就近后靠安置)和异地安置相结合的农村移民政策
市场最优原则-----------城市的几何中心
交通最优原则-----------市区环路边缘或市区边缘的高速公路沿线
⑷ 上海成为全国最大的商业城市的原因:
①ቤተ መጻሕፍቲ ባይዱ上海本身拥有较强的商品生产能力和商品经济发达的腹地
