微软mta98-349
(核)卫星遥感解译设备

名称:卫星遥感解译设备数量:1台(套)用途:开展生态环境遥感监测与评价工作配置要求: 应用软件 ERDAS IMAGINE 2011 遥感图像处理系统 1套; ARCGIS桌面产品及扩展模块1套;大幅面工程扫描仪ColorGiant CG510pro)1台;联想ThinkStation D20 4155-BF4图形工作站3台(套)技术参数1、应用软件: ERDAS IMAGINE 2011 遥感图像处理系统ERDAS IMAGINE-Professional遥感图像处理和分析核心模块专业版提供了高级高光谱影像分析、图形建模工具、基本雷达解译功能、ECW压缩功能和高级的分类工具如监督分类、影像分割、专家分类器及知识库建立工具、适合大范围调查的帧采样工具、分组工具及子像元分类工具。
另包含了IMAGINE Advantage的所有功能。
包括一组完整的工具以实现影像镶嵌,生成数字地面模型,高级的图像解译如空间、辐射及波谱增强/滤波/变换等,地形分析(坡度坡向),GIS分析,层叠等实用工具以及正射纠正等数据处理与分析任务。
它提供了一组强大的地理几何纠正、影像/矢量/注释编辑、影像预处理和管理、可视化和制图输出的工具2、ARCGIS桌面产品及扩展模块ARCINFO-CON-V10ArcInfo是最全面的、可扩展的GIS软件。
它囊括了ArcView和ArcEditor的全部功能并且增加了高级的地理处理和数据转换功能。
专业的GIS用户使用ArcInfo可以进行各方面的数据构建、模拟、分析以及地图的屏幕显示和输出。
(ArcInfo V10 Concurrent Use License.12 months Software Mmaintenance Service.)软件包括ArcInfo v10浮动许可。
12个月的维护服务。
ARCGIS-Spatial-CON(ArcGIS Extension Spatial Analyst, concurrent use license, 12 months of software maintenance.)模块包括ArcGIS 空间分析扩展浮动许可,包括12个月软件维护服务。
微软 MTA 数据库管理认证考试辅导指南说明书

白皮书系列微软MTA认证考试辅导指南数据库管理目录一、微软和它的软件帝国 (2)二、不可不知的微软认证 (2)三、MTA认证 (3)3.1 MTA认证是什么? (3)3.2 MTA考试科目 (3)3.3 MTA认证适用对象 (4)3.4 MTA认证的价值 (4)四、数据库管理认证介绍 (5)五、数据库管理考试大纲 (5)5.1了解核心数据库概念(20-25%) (6)5.2创建数据库对象(20-25%) (6)5.3操作数据(25-30%) (6)5.4了解数据存储(15-20%) (7)六、模拟题及解析 (7)6.1 单选题 (7)6.2 多选题 (8)6.3 判断题 (9)6.4 拖拽题 (10)七、MTA认证考试流程 (12)7.1 如何报考 (12)7.2 考前准备 (12)7.3 考试流程 (12)7.4 证书样本 (16)7.5 证书查询 (16)八、认证考务系统介绍 (17)8.1 考试信息获取 (18)8.2 考试成绩(测评报告)查询 (18)8.3 电子证书下载/打印 (19)九、白皮书系列介绍 (19)十、特别鸣谢 (20)10.1 微软中国 (20)10.2 培生教育 (20)10.3 思递波考试平台 (20)10.4 易讯教育 (21)一、微软和它的软件帝国毋庸置疑,微软作为世界第一大IT公司和电脑软件提供商,始终是全球计算机行业的风向标。
成立于1975年的微软是世界PC(Personal Computer,个人计算机)软件开发的先导,以研发、制造、授权和提供广泛的电脑软件服务为主营业务。
Microsoft Windows操作系统和Microsoft Office系列软件则无疑是微软最为著名和畅销的标志产品。
提到计算机,首先反应在人们脑海中的关键词中一定缺不了微软。
微软早已不仅仅是计算机软件开发商,更是众多计算机行业标准的缔造者。
熟练掌握微软研发的各种计算机软件使用,早已成为许多初入职场的新人必须掌握的工作技能,甚至成为他们职场进阶时的最佳助力,无论他们所从事的是什么职业,只要这份职业离不开计算机,那么,微软旗下总有一款软件会成为他们工作乃至生活中离不开的必需品。
微软安全更新指南说明书

The following table lists the security updates released by Microsoft on April 11.Eaton’s testing concluded on April 20 for all products. Please refer to the Microsoft Security Update Guide at for the details of individual updates.Microsoft Product Release Microsoft KB Article Current Status Client Recommendation Excel 2013No updates available this monthExcel 2016Windows 8.1 Extended Support ended Jan 10, 2023Windows 10 Versions 20H2, 21H2, 22H2 5025221 Testing Complete InstallWindows 11 Version 21H2 5025224 Testing Complete InstallWindows 11 Version 22H2 5025239 Testing Complete InstallWindows Server 2012 R2 5025285 Testing Complete InstallWindows Server 2016 5025228 Testing Complete InstallWindows Server 2019 5025229 Testing Complete InstallWindows Server 2022 5025230 Testing Complete Install Microsoft’s mainstream support has ended. Upgrade recommended.Microsoft’s extended support has ended. No further security updates are available. Upgrade required.The following table identifies with an “X” the Eaton software that has been successfully tested with the Microsoft security updates, including the Microsoft Windows operating system, Microsoft SQL Server, and Microsoft software versions with which the tests were performed. Shaded cells are not applicable for the specified product combination.Microsoft Product Eaton ProductOperating System, Software, SQL Server ProViewNXG3.8.0SMPGateway8.2R3SC22001.0R1SMP I/O3.0R5SMP IO-20001.3R1,1.6R2,2.0R1YukonEnterpriseSoftware9.2, 9.3Yukon FeederAutomationSoftware2.4R1,3.1R1,3.2R3YukonGridServer2.2 R2Yukon IEDManager Suite(IMS)7.4R1, 7.6R2,7.7R1YukonVisual T&DSoftware5.2R1Excel 2013Excel 2016Excel 2019 (365)Microsoft Edge X X X X X SQL Server 2012SQL Server 2014 XSQL Server 2016 X X SQL Server 2017 X X SQL Server 2019 X X X Windows Server 2012 R2 X X Windows Server 2016 X X X X Windows Server 2019 18091809 1809 X X X X Windows Server 2022 X XWindows 10 22H2 21H2 22H2 21H2 21H2 21H2 21H2 21H2 Windows 11 21H2 21H2 21H2 21H2 21H2This report provides the status of Eaton’s testing.Evaluating The initial state in the process. The security update is being evaluated.Testing The security update is being tested. The Client Recommendation will remain on “Hold” until all issues have been addressed.Testing Complete Testing has been completed and the Client Recommendation now contains the proposed course of action.Not Tested Testing has not been completed because the security update is not applicable to the product. This report provides Eaton’s recommendation based on the test results.Hold Initial state in the process. The customer should take no action until Eaton has tested the update and issued a recommendation.Install Eaton considers that this update addresses security issues with functions or services used by its product, or underlying platform services, which would be at risk if not updated.The update has been tested and no adverse side effects have been observed. The customer should install the update at the earliest convenience.Not Applicable Eaton considered the security update unnecessary and did not test it. The customer does not need to install it since it does not address any function or service used by the product.There are no understandings, agreements, representations, or warranties, express or implied, including warranties of merchantability or fitness for a particular purpose, other than those specifically set out by any existing contract between the seller and buyer. Any such contract states the entire obligation of the seller. The contents of this report shall not become part of or modify any such prior or existing agreement.The recommendations in this report are based on Eaton experience and judgment. THIS INFORMATION SHOULD NOT BE CONSIDERED AS ALL-INCLUSIVE OR COVERING ALL CONTINGENCIES. If further information is required, Eaton should be consulted. In no event will Eaton be responsible to the user in contract, in tort (including negligence), strict liability or otherwise for any special, indirect, incidental, or consequential damage or loss whatsoever; or claims against the user by its customers resulting from the use of recommendations.。
漏洞下载地址(Excel)

01069/Windows6.1-KB974431-x86.msuE875C/Windows6.1-KB974571-x86.msuFB548/Windows6.1-KB975467-x86.msu83DA3/Windows6.1-KB972270-x86.msu329BD/Windows6.1-KB977074-x86.msu DCF94/Windows6.1-KB975560-x86.msuE6D29/Windows6.1-KB977165-x86.msuAF2A5/Windows6.1-KB977377-x86.msuD12A6/Windows6.1-KB979099-x86.msuB70EE/Windows6.1-KB976422-x86.msu3D3FE/Windows6.1-KB977716-x86.msuD7D0F/Windows6.1-KB978044-x86.msu662CB/Windows6.1-KB978118-x86.msu23F3D/Windows6.1-KB978632-x86.msu4DD18/Windows6.1-KB979309-x86.msuindows6.1-KB975496-v2-x86.msuindows6.1-KB980408-x86.msu97BD9/Windows6.1-KB978542-x86.msuC6A38/Windows6.1-KB979482-x86.msu0AFDA/Windows6.1-KB980846-x86.msu16DAB/Windows6.1-KB2030901-x86.msu1D8F9/Windows6.1-KB982300-x86.msu0D3F7/Windows6.1-KB982316-x86.msu 91271/Windows6.1-KB982665-x86.msuDA90B/Windows6.1-KB982799-x86.msu2DDCB/Windows6.1-KB982110-x86.msuF261D/Windows6.1-KB2259539-x86.msu DFEA3/Windows6.1-KB2264107-v2-x86.msu AF27C/Windows6.1-KB2347290-x86.msu EACA4/Windows6.1-KB2386792-x86.msu 1316F/Windows6.1-KB979538-x86.msu1C27A/Windows6.1-KB2300535-x86.msu5ED38/Windows6.1-KB979687-x86.msuE5163/Windows6.1-KB979688-x86.msu 8814F/Windows6.1-KB982132-x86.msu 7275A/Windows6.1-KB2281679-x86.msu2A499/Windows6.1-KB2296011-x86.msu 1428D/Windows6.1-KB2345886-x86.msu BC558/Windows6.1-KB2378111-x86.msu 431E6/Windows6.1-KB2387149-x86.msuE5727/Windows6.1-KB2249857-x86.msu2E041/Windows6.1-KB2284742-x86.msu9F848/Windows6.1-KB2305420-x86.msu BDD1B/Windows6.1-KB2423089-x86.msu7AC7B/Windows6.1-KB2442962-x86.msu 8405E/Windows6.1-KB2419640-x86.msuB2A13/Windows6.1-KB2454826-v2-x86.msu 11BD8/Windows6.1-KB2467023-x86.msu68F96/Windows6.1-KB2502285-x86.msuD8B22/Windows6.1-KB2393802-x86.msu 16564/Windows6.1-KB2387530-x86.msuE2E44/Windows6.1-KB2484033-x86.msu61357/windows6.1-KB976932-X86.exe05440/Windows6.1-KB2479943-x86.msu4A332/Windows6.1-KB2483614-x86.msuF4EA8/Windows6.1-KB2505438-x86.msuA2D06/Windows6.1-KB2522422-x86.msuE9B2B/Windows6.1-KB2496898-v3-x86.msu445B6/Windows6.1-KB2491683-x86.msuD48D9/Windows6.1-KB2506212-x86.msu84F43/Windows6.1-KB2509553-x86.msuDDB7A/Windows6.1-KB2510531-x86.msu9F81F/Windows6.1-KB2511250-x86.msuAF3B1/Windows6.1-KB2511455-x86.msuindows6.1-KB982018-v3-x86.msuindows6.1-KB2487335-x86.msuBFB41/Windows6.1-KB2506628-x86.msu0A1C1/Windows6.1-KB2506928-v2-x86.msu02253/Windows6.1-KB2515325-x86.msu58F9A/Windows6.1-KB2529073-x86.msu33A6A/Windows6.1-KB2533552-x86.msuB7ECE/Windows6.1-KB2534366-x86.msuE2A4E/Windows6.1-KB2541014-x86.msuF8934/NDP40-KB2468871-v2-x86.exe57210/Windows6.1-KB2503665-x86.msu8AB7E/Windows6.1-KB2535512-x86.msu10CAE/Windows6.1-KB2536275-x86.msu0583C/Windows6.1-KB2548388-x86.msuB74D2/Windows6.1-KB2547666-x86.msu266F5/Windows6.1-KB2552343-x86.msu79CB9/Windows6.1-KB2532531-x86.msuF206D/Windows6.1-KB2533623-x86.msuBA18C/NDP40-KB2533523-x86.exeEC5CC/Windows6.1-KB2560656-x86.msu84A11/Windows6.1-KB2563227-x86.msu85DEA/NDP40-KB2487367-x86.exe70CCC/Windows6.1-KB2536276-v2-x86.msu81ADD/Windows6.1-KB2546868-x86.msu81ADD/Windows6.1-KB2546868-x86.msuC6AD6/Windows6.1-KB2570947-x86.msu6B685/office2010-kb2553065-fullfile-x86-glb.exe A0594/Windows6.1-KB2564958-x86.msu423EF/Windows6.1-KB2579686-x86.msuDDDCD/Windows6.1-KB2578214-x86.msu1BCCC/Windows6.1-KB2598845-x86.msu106CB/Windows6.1-KB2607576-x86.msu059AF/Windows6.1-KB2618301-x86.msu7206B/Windows6.1-KB2619572-x86.msu05038/Windows6.1-KB2496290-v2-x86.msuB8F01/msoloc2010-kb2553310-fullfile-x86-glb.exeAB989/outlook2010-kb2553323-fullfile-x86-glb.exe 4452E/csi2010-kb2553455-fullfile-x86-glb.exe308F2/Windows6.1-KB2592525-x86.msuDF7DB/Windows6.1-KB2620704-x86.msu75690/Windows6.1-KB2544893-x86.msu68218/Windows6.1-KB2619339-x86.msu141B2/Windows6.1-KB2620712-x86.msu9DD04/powerpoint2010-kb2553185-fullfile-x86-glb.exe 0C83C/vviewer2010-kb2553353-fullfile-x86-glb.exe be72010-kb2553385-fullfile-x86-glb.exexcel2010-kb2553439-fullfile-x86-glb.exe4E7F9/nlgmslid2010-kb2596964-fullfile-x86-glb.exe FF59A/NDP40-KB2656351-x86.exe370D6/Windows6.1-KB2656355-x86.msu06E98/Windows6.1-KB2584146-x86.msu8481A/Windows6.1-KB2585542-x86.msu80106/Windows6.1-KB2631813-x86.msuF6470/Windows6.1-KB2632503-x86.msu266D9/Windows6.1-KB2644615-x86.msuF1D50/Windows6.1-KB2624668-x86.msu0A68B/csi2010-kb2597091-fullfile-x86-glb.exe CBBFC/NDP40-KB2600217-x86.exe1F9FB/Windows6.1-KB2639308-x86.msu29D6C/Windows6.1-KB2654428-x86.msu6E855/Windows6.1-KB2660075-x86.msuFC487/Windows6.1-KB2640148-v2-x86.msu72377/Windows6.1-KB2621440-x86.msu4C583/Windows6.1-KB2647753-v2-x86.msu98ABC/Office2010-kb2598245-fullfile-x86-glb.exe05FA9/Windows6.1-KB2653956-x86.msu362ED/Windows6.1-KB2679255-v2-x86.msuF03E7/outlookloc2010-kb2553248-fullfile-x86-glb.exe 4801E/oscmoss2010-kb2553267-fullfile-x86-glb.exe24C10/oscloc2010-kb2553406-fullfile-x86-glb.exeCD450/Windows6.1-KB2658846-x86.msuDF80D/Windows6.1-KB2659262-x86.msuFFA24/Windows6.1-KB2660649-x86.msu2B160/Windows6.1-KB2676562-x86.msuF2635/Windows6.1-KB2690533-x86.msu72820/Windows6.1-KB2604114-x86.msu5FE13/NDP40-KB2604121-x86.exe9C625/graph2010-kb2553371-fullfile-x86-glb.exeEE91D/onenote2010-kb2589345-fullfile-x86-glb.exeE8432/Windows6.1-KB2656410-x86.msu236F0/Windows6.1-KB2698707-x86.msuF2367/Windows6.1-KB2685939-x86.msu7E541/Windows6.1-KB2699779-v2-x86.msu4E674/Windows6.1-KB2709630-x86.msu5F3F6/Windows6.1-KB2667402-v2-x86.msuF3EE7/Windows6.1-KB2655992-x86.msuF58E1/Windows6.1-KB2691442-x86.msuF8EFA/infopath2010-kb2553431-fullfile-x86-glb.exe FA87F/imeloc2010-kb2598241-fullfile-x86-glb.exe be72010-kb2598243-fullfile-x86-glb.exeindows6.1-KB2712808-x86.msu0244E/csi2010-kb2598289-fullfile-x86-glb.exeF6849/Windows6.1-KB2707082-x86.msu17796/Windows6.1-KB2741355-x86.msu24D99/Windows6.1-KB2731771-x86.msu1224F/Windows6.1-KB2739159-x86.msu4B3C0/Windows6.1-KB2739286-x86.msu4297B/Windows6.1-KB2743555-x86.msu636C9/Windows6.1-KB2749655-x86.msuC0391/Windows6.1-KB2661254-x86.msuA5688/Windows6.1-KB2705219-v2-x86.msuEA90A/Windows6.1-KB2729094-v2-x86.msuBDD4E/Windows6.1-KB2732487-v2-x86.msuB7E8D/Windows6.1-KB2732500-v2-x86.msuEAA29/Windows6.1-KB2727528-x86.msuE31D8/NDP40-KB2729449-x86.exe8A5B7/Windows6.1-KB2729451-x86.msu58D90/NDP40-KB2737019-x86.exeD68FD/Windows6.1-KB2752161-x86.msu65987/Windows6.1-KB2761217-x86.msu17C85/groove2010-kb2589371-fullfile-x86-glb.exe 69595/csi2010-kb2687509-fullfile-x86-glb.exe0F909/outlookloc2010-kb2687623-fullfile-x86-glb.exe 37261/Windows6.1-KB2779562-x86.msu6C13E/Windows6.1-KB2748349-x86.msu8AAD9/Windows6.1-KB2758857-x86.msu89C06/Windows6.1-KB2770660-x86.msuB75C7/Windows6.1-KB2779272-x86.msu2A5D9/msconv972010-kb2687510-fullfile-x86-glb.exeD82E4/Windows6.1-KB2753842-v2-x86.msu094B3/Windows6.1-KB2726535-x86.msu622FE/Windows6.1-KB2736418-x86.msu4A7BF/NDP40-KB2736428-x86.exe925E7/NDP40-KB2742595-x86.exe9FD30/Windows6.1-KB2742598-x86.msu0F077/Windows6.1-KB2756920-x86.msu10CFD/Windows6.1-KB2757638-x86.msuA0920/Windows6.1-KB2769369-x86.msu5AE79/Windows6.1-KB2773072-x86.msu93271/Windows6.1-KB2785220-x86.msu25AD7/Windows6.1-KB2786400-x86.msu22057/NDP40-KB2789642-x86.exe8906D/Windows6.1-KB2789644-x86.msu56FCF/Windows6.1-KB2790113-x86.msu8AFFA/Windows6.1-KB2790655-x86.msu1D250/osetup2010-kb2553378-fullfile-x86-glb.exe EACA3/outlook2010-kb2597090-fullfile-x86-glb.exeB05EA/powerpoint2010-kb2598240-fullfile-x86-glb.exe 127B4/mscomctlocx2010-kb2687503-fullfile-x86-glb.exe32495/filterpack2010-kb2553501-fullfile-x86-glb.exeE29BF/vviewer2010-kb2687505-fullfile-x86-glb.exe8BF6D/onenote2010-kb2760600-fullfile-x86-glb.exe1EB53/usp102010-kb2767886-fullfile-x86-glb.exe3E23E/Windows6.1-KB2817183-x86.msu3ACB2/Windows6.1-KB2799926-x86.msuB35FD/Windows6.1-KB2808735-x86.msu80F62/Windows6.1-KB2813170-x86.msu88189/ipeditor2010-kb2760406-fullfile-x86-glb.exe BEBC9/Windows6.1-KB2840149-x86.msu8E33C/Windows6.1-KB2813347-x86.msu06AC3/Windows6.1-KB2847927-x86.msuC6299/officesp2010-kb2687455-fullfile-x86-zh-cn.exe4D8B1/targetdir2010-kb2825640-fullfile-x86-glb.exe owerpointloc2010-kb2553145-fullfile-x86-glb.exeart2010-kb2553157-fullfile-x86-glb.execcess2010-kb2553446-fullfile-x86-glb.exeD39D7/gfx2010-kb2589298-fullfile-x86-glb.exe8A5E9/oartconv2010-kb2589370-fullfile-x86-glb.exe1A918/msocf2010-kb2589375-fullfile-x86-glb.exeA7FBC/ace2010-kb2687423-fullfile-x86-glb.exe3734D/csi2010-kb2760598-fullfile-x86-glb.exeA8098/mso2010-kb2760758-fullfile-x86-glb.exeF41DC/osetup2010-kb2794737-fullfile-x86-glb.exe577E0/vviewer2010-kb2810066-fullfile-x86-glb.exe9F020/filterpack2010-kb2810071-fullfile-x86-glb.exe 62778/onenote2010-kb2810072-fullfile-x86-glb.exe51BF4/mso2010-kb2826026-fullfile-x86-glb.exe36358/kb24286772010-kb2827322-fullfile-x86-glb.exe ord2010-kb2827323-fullfile-x86-glb.exeart2010-kb2826023-fullfile-x86-glb.exeartconv2010-kb2826035-fullfile-x86-glb.exeleo2010-kb2589352-fullfile-x86-glb.exesores2010-kb2597087-fullfile-x86-glb.exe12169/outlook2010-kb2837597-fullfile-x86-glb.exe EBFCC/proofloc2010-kb2850079-fullfile-x86-glb.exe6AEB4/mshelp2010-kb2850016-fullfile-x86-glb.exeCBDB0/filterpack2010-kb2837594-fullfile-x86-glb.exe8E11D/visioloc2010-kb2553444-fullfile-x86-glb.exe owerpointloc2010-kb2837579-fullfile-x86-glb.exeffice2010-kb2879953-fullfile-x86-glb.exe66353/gkall2010-kb2825635-fullfile-x86-glb.exe65D44/vviewer2010-kb2837587-fullfile-x86-glb.exeEBC68/filterpack2010-kb2878281-fullfile-x86-glb.exe10C5C/visioloc2010-kb2880526-fullfile-x86-glb.exe6CC84/mscomct22010-kb2589288-fullfile-x86-glb.exe88F82/mscomctlocx2010-kb2810073-fullfile-x86-glb.exe 10E48/msaddndr2010-kb2880971-fullfile-x86-glb.exe art2010-kb2837581-fullfile-x86-glb.exexcel2010-kb2837600-fullfile-x86-glb.exe2BA0B/oartconv2010-kb2837606-fullfile-x86-glb.exe7DAEA/mso2010-kb2878252-fullfile-x86-glb.exe85D8A/excel2010-kb2889836-fullfile-x86-glb.exe 090F1/imeloc2010-kb2837582-fullfile-x86-glb.exe 31E8B/csi2010-kb2910903-fullfile-x86-glb.exe33F42/Windows-KB890830-V5.30-delta.exe。
破解微软黑屏和卸载反盗版补丁解决方法

破解微软黑屏和卸载反盗版补丁解决方法电脑的注意了!!!由于美国最近要针对中国上诉WTO知识产权保护问题,微软正在为美国政府搜集相关证据,在最近自动更新中包含检测盗版副本程序。
已经开启当提示要你安装正版增值计划请别安装!安装后会在任务栏右下角出现一个蓝色五角星符号!!!这样就会被微软追踪锁定!!!如果装了的,解决办法:打开注册表(开始----运行----输入regedit)然后依次打开HKEY_LOCAL_MACHINE\SOFTWARE\microsoft\WindowsNT\Curre ntVersion\Winlogon\Notify\WgaLogon,删除它(WgaLogon),再重新启动(一定要重起,要不然删不了C盘的文件),wgatray.exe就不会自动启动了,再把C:\windows\system32中的wgaTray.exe删除,再搜索一下,在另外的文件夹下还有,统统删除,(搜索的方法是开始---搜索--所有文件及文件夹---全部文件或部分文件名,写上"wgaTray.exe"后点搜索,搜索到后,点鼠标右键删除之),然后再次重起. 然后再次进到注册表HKEY_LOCAL_MACHINE\SOFTWARE\microsoft\WindowsNT\CurrentVersion\Winlogon\Notify\WgaLogon,删除它(和第一次的操作相同),至此问题解决了!关于卸载微软反盗版补丁(KB905474)的解决办法解决方法Windows Genuine Advantage 通知(KB905474)如何卸载微软反盗版补丁(KB905474)的解决办法解决方法:第一套方案:1.运行regedit进入注册表,HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsNT\CurrentVersion\Winlogon\Notify\WgaLogon,删除它,重新启动。
Windows 7 默认服务启动对照表
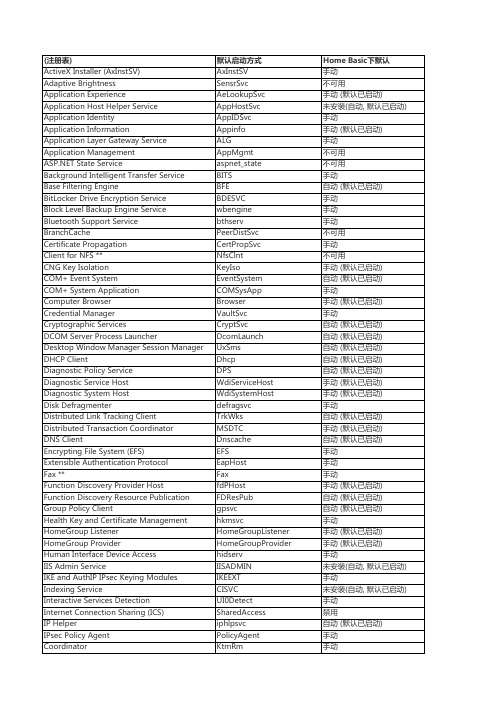
Remote Desktop Configuration ** Remote Desktop Services Remote Desktop Services UserMode Port Redirector Remote Procedure Call (RPC) Remote Procedure Call (RPC) Locator Remote Registry RIP Listener ** Routing and Remote Access RPC Endpoint Mapper SeaPort *** Secondary Logon Secure Socket Tunneling Protocol Service Security Accounts Manager Security Center Server Shell Hardware Detection Simple TCP/IP Services ** Smart Card Smart Card Removal Policy SNMP Service ** SNMP Trap Software Protection SPP Notification Service SSDP Discovery Storage Service Superfetch System Event Notification Service Tablet PC Input Service Task Scheduler TCP/IP NetBIOS Helper Telephony Telnet ** Themes Thread Ordering Server TPM Base Services UPnP Device Host User Profile Service Virtual Disk Volume Shadow Copy Web Management Service ** WebClient Windows Audio Windows Audio Endpoint Builder Windows Backup
Windows2022年测评指导书三级S3A3G3.0版
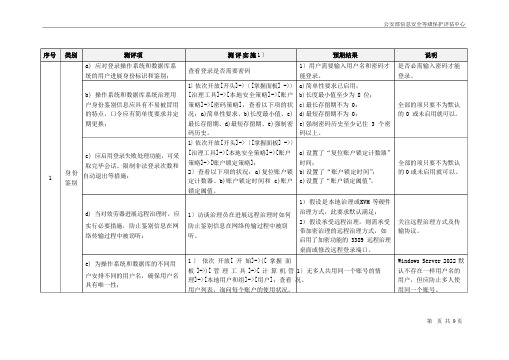
序号类别测评项a)应对登录操作系统和数据库系统的用户进展身份标识和鉴别;b)操作系统和数据库系统治理用户身份鉴别信息应具有不易被冒用的特点,口令应有简单度要求并定期更换;c)应启用登录失败处理功能,可采测评实施1〕查看登录是否需要密码1〕依次开放[开头]->〔[掌握面板] ->〕[治理工具]->[本地安全策略]->[账户策略]->[密码策略],查看以下项的状况:a)简单性要求、b)长度最小值、c)最长存留期、d)最短存留期、e)强制密码历史。
1〕依次开放[开头]->〔[掌握面板] ->〕[治理工具]->[本地安全策略]->[账户预期结果1〕用户需要输入用户名和密码才能登录。
a)简单性要求已启用;b)长度最小值至少为 8 位;c)最长存留期不为 0;d)最短存留期不为 0;e)强制密码历史至少记住 3 个密码以上。
a)设置了“复位账户锁定计数器”说明是否必需输入密码才能登录。
全部的项只要不为默认的 0 或未启用就可以。
取完毕会话、限制非法登录次数和1 身份自动退出等措施;鉴别d) 当对效劳器进展远程治理时,应策略]->[账户锁定策略];2〕查看以下项的状况:a)复位账户锁定计数器、b)账户锁定时间和 c)账户锁定阈值。
1〕访谈治理员在进展远程治理时如何时间;全部的项只要不为默认b)设置了“账户锁定时间”;的0或未启用就可以。
c)设置了“账户锁定阈值”。
1)假设是本地治理或KVM 等硬件治理方式,此要求默认满足;实行必要措施,防止鉴别信息在网络传输过程中被窃听;e) 为操作系统和数据库的不同用防止鉴别信息在网络传输过程中被窃听。
1 〕依次开放[ 开始]->([ 掌握面2)假设承受远程治理,则需承受带加密治理的远程治理方式,如启用了加密功能的 3389 远程治理桌面或修改远程登录端口。
关注远程治理方式及传输协议。
Windows Server 2022 默户安排不同的用户名,确保用户名具有唯一性;板 ]->)[ 管理工具 ]->[ 计算机管 1〕无多人共用同一个账号的情理]->[本地用户和组]->[用户];查看况。
▉▉▉微软MSDN中文(简体)资源全下载 ---整理过的(全得很)

产品类型: Operating Systems
产品名称: Windows Small Business Server 2008
名称: Disc 1: Windows Small Business Server 2008 Standard and Premium Installation (x64) - DVD (Chinese - Simplified)
产品类型: Servers
产品名称: BizTalk Server 2009
名称: BizTalk Server 2009 Accelerators Enterprise Edition (x86) - CD (Chinese-Simplified)
文件名: cn_biztalk_server_2009_accelerators_enterprise_x86_cd_x15-48256.iso
****************************************************
/archiver/?tid-486930.html
微软MSDN中文(简体)全下载
*****************************************************************************
产品类型: Business Solutions
产品名称: Dynamics CRM 4.0
名称: Dynamics CRM 4.0 Enterprise, Professional, and Workgroup Editions (x86) - DVD (Chinese-Simplified)
文件名: cn_disc_2_windows_essential_business_server_2008_standard_and_premium_management_server_x64_dvd_x14-73663.iso
微软高级威胁分析系统(Advanced Threat Analytics,简称ATA)说明书

Microsoft Advanced Threat Analytics (ATA)provides a simple and fast way to understand whatis happening within your network by identifyingsuspicious user and device activity with built-inintelligence and providing clear and relevant threatinformation on a simple attack timeline.Microsoft Advanced Threat Analytics leverages deep packet inspection technology, as well as information from additional data sources (SIEM and AD) to build an Organizational Security Graph and detect advanced attacks in near real time. The ATA system continuously goes through four steps to ensure protection:How it works Step 3: Detect After building an Organizational Security Graph, ATA can then look for any abnormalities in an entity’s behavior and identify suspicious activities — but not before those abnormal activities have been contextually aggregated and verified. ATA leverages years of world-class security research to detect known attacks and security issues taking place regionally and globally.ATA will also automatically guide you, asking you simple questions to adjustthe detection process according to your input.Step 1: Analyze After installation, by using pre-configured, non-intrusive port mirroring, allActive Directory-related traffic is copied to ATA while remaining invisible to attackers. ATA uses deep packet inspection technology to analyze allActive Directory traffic. It can also collect relevant events from SIEM (security information and event management) and other sources.Step 2: Learn ATA automatically starts learning and profiling behaviors of users, devices, and resources, and then leverages its self-learning technology to build an Organizational Security Graph. The Organizational Security Graph is a map of entity interactions that represent the context and activities of users, devices, and resources.Microsoft Advanced Threat AnalyticsStep 4: Alert While the hope is that this stage is rarely reached, ATA is there to alert you of abnormal and suspicious activities. To further increase accuracy and save you time and resources, ATA doesn’t only compare the entity’s behavior to its own, but also to the behavior of other entities in its interaction path before issuing an alert. This means that the number of false positives are dramatically reduced, freeing you up to focus on the real threats. At this point, it is important for reports to be clear, functional, and actionable in the information presented. The simple attack timeline is similar to a social media feed on a web interface and surfaces events in an easy-to-understand way.© 2015 Microsoft Corporation. All rights reserved. This document is provided "as-is." Information and views expressed in this document, including URL and other Internet Web site references, may change without notice. You bear the risk of using it. This document does not provide you with any legal rights to any intellectual property in any Microsoft product. You may copy and use this document for your internal, reference purposes. You may modify this document for your internal, reference purposes.。
2008r2 standard产品密钥 -回复

2008r2 standard产品密钥-回复"2008 R2 Standard 产品密钥" 是指微软推出的Windows Server 2008 R2 Standard 版本的产品密钥。
本文将逐步回答与这个主题相关的问题,以帮助读者了解这个产品密钥以及如何使用。
Windows Server 2008 R2 Standard 是基于Windows 7 构建的服务器操作系统。
它是一款强大的服务器系统,适用于中小型企业和部门服务器。
为了合法使用该系统,用户需要提供一个有效的产品密钥。
下面将一步一步回答与这个主题相关的问题。
问题一:什么是产品密钥?答:产品密钥是一串由数字和字母组成的代码,用于激活操作系统或软件。
每个产品密钥是独一无二的,用于确认用户合法地购买和使用相应的产品。
在使用Windows Server 2008 R2 Standard 版本之前,用户需要获得一个有效的产品密钥。
问题二:如何获取Windows Server 2008 R2 Standard 的产品密钥?答:有几种方法可以获取产品密钥。
首先,用户可以通过购买正版的Windows Server 2008 R2 Standard 来获得一个合法的产品密钥,这通常包括在产品包装或电子邮件中。
其次,用户还可以通过微软官方渠道获得产品密钥,例如,在微软的官方网站或认可的经销商处购买许可证。
问题三:如何使用产品密钥激活Windows Server 2008 R2 Standard 版本?答:在获得有效的产品密钥之后,用户可以按照以下步骤激活Windows Server 2008 R2 Standard 版本:1. 打开服务器的控制面板,选择"系统和安全"。
2. 在"系统" 下,找到并点击"激活Windows"。
3. 在打开的窗口中,输入产品密钥,并点击"下一步"。
AVer Document Camera Setup Guide

Setup your AVer Document Camera from home!Please first identify which AVer document camera you are using to know what software to install.A+ Suite (Sphere2 on Win10/Mac) or Sphere Lite (Chromebooks): AVer U70+, AVer U50, AVer M70HD, AVer 300AFHD, AVer F70W, AVer F50-8M, AVer F17-8M, M17-13MAVerTouch (Win10/Mac): AVer M15W, AVer M15-13M, AVer M70WA+ Interactive Software (Old Version on Win/Mac): V300AF ASIC, SPC300 ASIC, SPC300 +, CP130, CP150, CP300, SPB350, SPB370, CP135, CP155, CP355, V355AF, V310AF, SPB350+, V300AF+, F30, F50, U10, U15, AP20,M50, W30Sphere (Old Version on Win/Mac): PL50, SPB350, SPB370, SPB350+, M50, M70, V300AF+, F50, F30, F15 U15, W30A+ Suite (Sphere2):1.Download the A+ Suite software on your computer, go to:https:///education/support/aplus-suiteSelect the OS you are using to download the software (we will use Win10 in this tutorial)2.Open the downloaded .exe file to start the installationFollow the setup wizard to install the A+ Suite software3.After installation is completed, open the Sphere2 software4.Plug in the power adapter to your document camera and turn it on by pressing the power button (does notapply to U-series doc cams, your document camera may look different than the one pictured)5.Locate a USB port on your computer and connect your camera to it via USB cable that is included6.Select the visualizer icon on the top right of the Sphere2 software and select your camera7.You are now connected to your AVer document camera and can begin teaching!If you own an AVer F70W and wish to connect to your computer wirelessly, please follow this guide: https:///education/downloads/F70WV2-Quick-Guide-EN-v5-2020-02-24.pdfSphere Lite (Chromebook):1.Download the Sphere Lite software on your Chromebook, go to:https:///webstore/detail/sphere-lite/bhmibpbadaengbikmoglphhlhioajdjn?hl=enunch Sphere Lite app after installing3.Plug in the power adapter to your document camera and turn it on by pressing the power button (does notapply to U-series doc cams, your document camera may look different than the one pictured)4.Locate a USB port on your Chromebook and connect your camera to it via USB cable that is included5.Select your camera on the bottom left. You are now connected to your AVer document camera and can beginteaching!AVerTouch:1.Download the AVerTouch software on your computer, go to:https:///education/support/avertouchSelect the OS you are using to download the software (we will use Win10 in this tutorial)2.Unzip the downloaded .zip file3.Open the extracted folder and run the .exe to start the installation4.Follow the setup wizard to install the AVerTouch software5.After installation is completed, open the AVerTouch software6.Plug in the power adapter to your document camera and turn it on by pressing the power button (yourdocument camera may look different than the one pictured)7.Locate a USB port on your computer and connect your camera to it via USB cable that is includedNote: For M15W/M70W users, please make sure WiFi is turned off when trying to do a USB connection 8.The connected visualizer will appear within the AVerTouch software. Click the play icon to connect to thecameraIf you own an AVer M15W/M70W and wish to connect to your computer wirelessly, please follow this guide: M15W: https:///education/downloads/M15W-instruction-manual-EN-2019-12-20.pdfM70W: https:///education/downloads/M70W-instruction-manual-EN-v1-2019-12-20.pdfA+ Interactive Software:1.Download the A+ Interactive Software on your computer, go to:https:///education/support/averplusSelect the OS you are using to download the software2.Unzip the downloaded .zip file3.Open the extracted folder and run the .exe to start the installation4.Follow the setup wizard to install the A+ Interactive Software5.After installation is completed, open the A+ Interactive Software6.Power on and connect your doc cam to your computer via USB cable7.Select your visualizer within the software and you are now connected!Sphere:1.Download the Sphere on your computer, go to:https:///education/support/sphereSelect the OS you are using to download the software2.Run the downloaded .exe to start the installation3.Follow the setup wizard to install the Sphere software4.After installation is completed, open the Sphere Software5.Power on and connect your doc cam to your computer via USB cable6.Select your visualizer within the software and you are now connected!Using your AVer Document Camera with other platforms (Zoom, Skype, Google Hangout).Open up your software of choice and connect your AVer document camera to your computer via USB cable.Select your AVer document camera as your visualizer and you are successfully connected!(Please refer to Zoom, Skype, or Hangout user guides to navigate through their software)Zoom:https:///hc/en-us/articles/201362033-Getting-Started-on-Windows-and-MacSkype:https:///en/skype/windows-desktop/start/Hangout:https:///hangouts/?hl=en#topic=6386410Note: The following AVer doc cams are not UVC compliant and are not compatible with other platforms: F50, M70, PL50, W30, W30HD, Tabcam, 355AF, M50More HelpFor FAQs, technical support, software and instruction manual download, please visit:https:///education/support/Contact InformationAVer Information Inc.668 Mission Ct. Fremont, CA 94539, USAToll-free: 1(877)528-7824Local: 1(408)263-3828********************。
软件环境
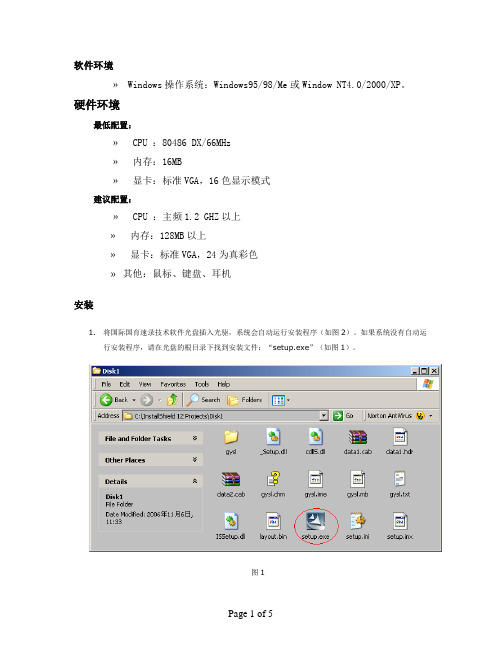
软件环境» Windows操作系统:Windows95/98/Me或Window NT4.0/2000/XP。
硬件环境最低配置:» CPU :80486 DX/66MHz» 内存:16MB» 显卡:标准VGA,16色显示模式建议配置:» CPU :主频1.2 GHZ以上» 内存:128MB以上» 显卡:标准VGA,24为真彩色»其他:鼠标、键盘、耳机安装1.将国际国育速录技术软件光盘插入光驱,系统会自动运行安装程序(如图2)。
如果系统没有自动运行安装程序,请在光盘的根目录下找到安装文件:“setup.exe”(如图1)。
图12.双击找到的安装文件“setup.exe”进入安装程序界面(如图2)图23.单击“下一步”,进入图3图34.在图3中选择“我接受该许可协议中的条款(A)”。
然后单击“下一步”,进入图4图45.输入用户姓名和单位名称。
然后单击“下一步”进入图5图5 6.单击“安装”,然后程序开始安装图67.等待软件安装过程结束(如图7)图78.单击“完成”结束软件安装卸载:如果你想从系统中删除国际国育速录技术软件的话,建议您按照如下操作:1. 在控制面板的“输入法”中删除国际国育速录技术软件;2. 在控制面板的“添加或删除程序”中删除国际国育速录技术软件的程序文件。
注意事项:如果正在打开使用输入法,为确保正确卸载,请在没有将国育速录设为默认输入法的情况下,重新启动系统后进行卸载;如果您了解输入法所使用的文件,可以在卸载后手工删除ime和引擎文件。
WindowsVista系统常用补丁功能介绍

WindowsVista系统常用补丁功能介绍随着Vista系统的广泛应用,微软公司推出了很多的补丁来弥补系统的不足或者提升性能,但是很多时候我们不知道遇到的问题应该安装哪个(些)补丁来解决。
在此针对vista系统常用补丁进行汇总,以方便大家查阅:925255 - 使用基于WPF的程序在Vista中运行动画时耗电量增加925528 - 关于USB接口可靠性的更新927341 - 休眠或睡眠后媒体中心的磁盘管理功能失去响应928089 - IE7反钓鱼功能评估网页内容导致计算机响应很慢928135 - 从休眠中恢复时死机928188 - 墨迹程序在数字化设备上工作不正常928253 - SATA光驱在Vista启动后丢失929191 - IBM和联想电脑启动时间比其他电脑长929427 - 关于应用程序兼容(Windows Vista Application Compatibility)的更新929451 - 当网卡GUID改变后Vista仍注册使用老IP地址929478 - 在便携式电脑上,当你使用安全删除硬件功能删除内置光驱后无法再次连接该设备929550 - 当你连接一个PCI ExpressCard 设备到便携式电脑上时,该设备不能正常工作929577 - 睡眠中恢复后蓝牙设备工作不正常929615 - 当你在你想要的语言下使用媒体中心看电视时听不到声音929685 - 从睡眠或休眠中恢复后高精度声音设备不能正常工作并随后重启929734 - 睡眠或休眠后遇到问题929735 - 使用高级查找功能,用公历日期查找文件时无法找到你想要的文件929761 - 当你使用Wusa.exe和 /quite选项尝试安装某个软件包时,该安装失败929762 - 唤醒连接到IEEE 1394设备的计算机时,收到"Stop 0x9F"出错信息929763 - Mongolian Baiti字体5.0版可能显示不正常929777 - 安装VISTA到超过3GB内存电脑时出错,出现错误信息:S 0x0000000A929909 - 使用Mobile Intel 945GM Express芯片的电脑,偶尔无法从睡眠中唤醒929913 - 运行sysprep ?Creseal命令时一个错误被记录到Setuperr.log文件中930163 - 当你从一个网卡切换到另一个网卡后再进行一个VPN拨号连接时,无法访问远程VPN服务器上的任何资源930193 - 运行Sysprep 命令收到"A fatal error occurred"出错信息930194 - VISTA安装后,使用SiI PATA芯片的计算机无法识别一个附加的支持刻录的光驱930261 - 启动VISTA时随机收到"Stop 0xA" 错误信息930311 - 便携式计算机从睡眠中唤醒后执行有关网络的任务时,偶尔会收到出错信息"S 0x0000007E"930495 - 从睡眠中唤醒或者重新连接一个IEEE 1394设备时,丢失该IEEE 1394设备930517 - 使用桥接方式上网时收到"受限制的网络"消息930568 - 当你尝试休眠或睡眠时收到错误信息:"S 0x000000FE BUGCODE_USB_DRIVER"930570 - 从睡眠或休眠中唤醒时,收到Usbhub.sys进程的错误信息"S 0x00000044"930819 - Windows Image Acquisition 程序可能失去响应930857 - Windows错误报告的可用更新:一个问题报告只有在得到你的允许后才会被发送930883 - 播放声音的程序停止工作并复制入口到Default Format audio format 列表930955 - Moveuser.exe与VISTA不兼容并被新的Win32_UserProfile WMI 功能替代930917 - 当你用Live File System组件格式化一张碟片后,该光碟显示为空白930979 - 使用 the BitLocker Drive Encryption功能后,你可能收到"Stop 0x0000007E"出错信息931369 - 使用ATI SB600系列芯片的计算机的Vista安装过程可能持续几个小时931573 - 在以前无需激活的计算机上你可能被提示要求激活Vista931671 - 当MODEM还在连接时进行睡眠可能收到 "S 0x0000009F"出错信息931770 - 当你从网络上的一台服务器复制文件到VISTA计算机时,该复制过程可能会失去响应931969 - 在某些程序中Microsoft Software License条款显示的语言不正确932079 - 在使用SATA硬盘且不支持Host-Initiated Link电源管理的便携式电脑上其电量消耗比预期的要多932094 - 使用 QuickTime 7播放扩展名为。
联想 适用于 会议室(MTR)的 ThinkSmart One 部署指南和用户指南

© Copyright Lenovo 2023
iii
iv 适用于 Microsoft Teams 会议室(MTR)的 ThinkSmart One 部署指南和用户指南
第 1 章 认识 ThinkSmart One
感谢您选择 ThinkSmart One。
ThinkSmart One 是市面上首款基于 Windows 的一体式条形音箱设备,具有视野宽阔的高分辨率 摄像头、优质的音效和运行 Microsoft Windows 的强大算力。借助 ThinkSmart One,最终用户 可以使用熟悉的 Microsoft Teams 会议室(简称 MTR)界面,而 IT 管理员则可以更轻松地部署 和管理 Windows 系统。
关于USB传输速率的声明
本设备各个 USB 接口的实际传输速率可能存在差异,且可能低于下表列出的数据速率,具体情况 取决于多种因素,例如主机和外围设备的处理性能、文件属性及其他与系统配置和操作环境有关 的因素。
USB 设备 3.2 Gen 2 / 3.1 Gen 2
数据速率(Gbit/s) 10
第 1 章 . 认 识 ThinkSmart One 3
关于USB传输速率的声明. . . . . . . . . . 3 规格 . . . . . . . . . . . . . . . . . . . 4 智能功能 . . . . . . . . . . . . . . . . . 5
第 2 章 部署的先决条件 . . . . . . . 7
硬件 . . . . . . . . . . . . . . . . . . . 7 软件 . . . . . . . . . . . . . . . . . . . 8 网络 . . . . . . . . . . . . . . . . . . . 8 部署和维护服务 . . . . . . . . . . . . . . 9
CA ARCserve

■ CA ARCserve® Backup for Windows 产品灾难恢复选件 ■ CA ARCserve® Backup for Windows 产品企业模块 ■ CA ARCserve® Backup for Windows 产品 IBM 3494 企业选件 ■ CA ARCserve® Backup for Windows 产品 SAP R/3 for Oracle 企业选件 ■ CA ARCserve® Backup for Windows 产品 StorageTek ACSLS 企业选件 ■ CA ARCserve® Backup for Windows 产品映像选件 ■ CA ARCserve® Backup for Windows Microsoft 卷影副本服务 ■ CA ARCserve® Backup for Windows 产品 NDMP NAS 选件 ■ CA ARCserve® Backup for Windows 产品存储区域网络 (SAN) 选件 ■ CA ARCserve® Backup for Windows 产品磁带存储库选件 ■ CA ARCserve® Backup Patch Manager ■ CA ARCserve® Backup 产品 UNIX 和 Linux 数据移动器 ■ CA ARCserve® Central Host-Based VM Backup ■ CA ARCserve® Central Protection Manager ■ CA ARCserve® Central Reporting ■ CA ARCserve® Central Virtual Standby ■ CA ARCserve® D2D ■ CA ARCserve® D2D On Demand ■ CA ARCserve® High Availability ■ CA ARCserve® Replication ■ CA VM:Tape for z/VM ■ CA 1® Tape Management ■ Common Services™ ■ eTrust® Firewall ■ Unicenter® Network and Systems Management ■ Unicenter® Software Delivery ■ Unicenter® VM:Operator®
UTM配置
1
1
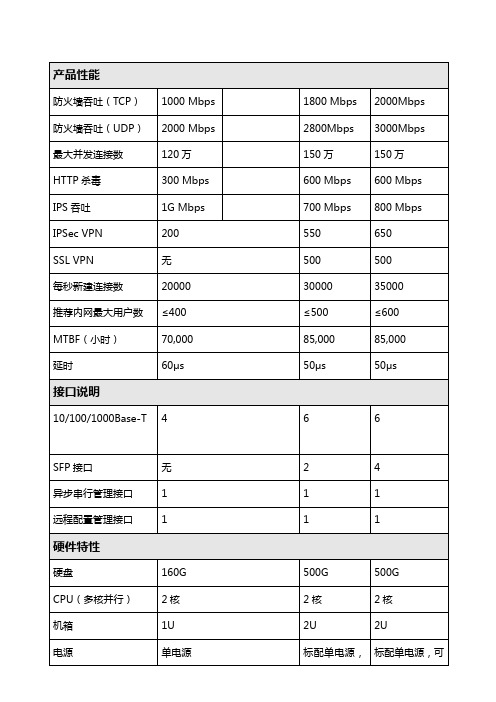
硬件特性
硬盘
160G
500G
500G
CPU(多核并行)
2核
2核
2核
机箱
1U
2U
2U
电源
单电源
标配单电源,可扩展冗余电源
标配单电源,可扩展冗余电源
根据公司目前状况,推动信息化建设,(UTM的具体要求及功能)
功能
要求
网络接入方式
可以支持路由、透明等接入模式
支持动态路由:RIP v1 &v2, OSPF, BGP,组播
支持安全规则对VPN隧道的引用,能对隧道内数据进行病毒查杀和内容过滤。
SSL VPN
支持SSL、VPN;
支持Tunnel,Web,Application模式
用户SSL VPN流量配额设置
支持HTTP,HTTPS,RDP,TELNET,SSH应用访问
支持登录页面自定义
支持基于证书的认证,VPN的AD扩展认证;RADIUS扩展认证;LDAP扩展认证;
支持绿色上网功能,内置URL分类库,支持关键字过滤,支持网站访问记录,具备强制安全搜索,阻挡搜索引擎的色情,成人,裸露信息,提供网址恶意转向防护功能;分类库大于80,网页库大于1200万条;
基于URL分类、自定义URL组进行带宽限速管理
支持基于身份验证的用户、用户组的Web过滤策略
支持自定义阻止URL的通知消息
配置文件自动备份且可以指定周期发送指定邮箱或FTP服务器目录
安全网关支持应用代理
支持多种管理方式,包括远程拨号、中文WEB、本地CONSOLE、远程SSH、TELNET、http、https等;
可通过同品牌控制软件实现远程集中监控管理功能:支持远程集中管理监控功能,配合在同一个管理平台下能够对所管理网络中所有的防火墙设备进行管理和监控,提供远程升级和配置变更、VPN策略集中下发,非常方便用户对防火墙软件版本和配置变更的管理;
河南理工大学办公软件正版化

河南理工大学办公软件正版化政府采购合同书合同备案编号:HPU政采-2018-A- 003政府采购编号:豫财单一采购-2017-643供方:北京金智华教科技有限公司签约时间:2018年1月16日需方:河南理工大学签约地点:焦作供、需双方依据国泰信华工程咨询有限公司签发的豫财单一采购[采购编中标通知书,根据《中华人民共和国合同法》等有关规定以及需方采购文件和供方投标文件的内容,供需双方经友好协商,现达成以下条款:一、合同标的与价款本合同所指货物为办公软件正版化(主要技术参数及配置见附件一、附件二),合同总价款为人民币)(含税)。
二、货物质量要求与售后服务要求供方应保证货物是全新、未使用过的,并完全符合强制性的国家技术质量规范和本合同附件一与附件二规定的质量、规格、性能及技术规范等要求。
售后服务要求按采购文件及投标文件相应条款执行(详见附件三)。
三、合同履行的地点及进度合同签字盖章生效后,供方应于2018年1 月17日前将合同条款中的全部货物运送到河南理工大学现教中心指定地点,并于2018年1月20日前按需方要求完成货物的安装、调试和人员培训,所发生的费用由供方负责。
需方应在货物到达指定地点后,提供符合安装条件的场地、电源、环境等。
四、技术资料合同生效后7天之内,供方应将每套货物的中文技术资料一套(如目录索引、操作手册、使用指南、维修指南(或)服务手册)寄给需方。
另外一套完整的上述资料供方应包装好随同每批货物装箱发运。
五、使用合同文件和资料事先未经需方书面同意,供方不得将由需方或代表需方提供的有关合同或任何合同条文、规格、计划、模型等提供给与履行本合同无关的任何其他人。
即使向与履行本合同有关的人员提供,也应注意保密并限于履行合同所必需的范围。
六、检验和测试货物抵达目的地后,由需方对货物的质量、规格、数量和重量进行检验,如果发现规格、数量或两者有与合同规定不一致的地方;或对成套货物安装调试、人员培训有异议的;或证实货物是有缺陷的,包括潜在的缺陷或使用不符合要求的材料等,需方应尽快以书面形式通知供方。
Microsoft Azure与Fortinet企业级安全解决方案合作 white paper说明书

Executive summarySecurity today requires consistent tools and policies across data centers,branch offices, and clouds. The goal is to attain uniform policy enforcement,visibility, and orchestration wherever the compute occurs. The averagesecurity stack, which includes multiple, disparate tools, can lead to operationalsilos and security gaps that prevent organizations from achieving this goal.Organizations must realize the importance of converging and uniting security,network, and computing practices. An integrated suite of security productsthat provides protection, no matter where their applications and data live, isthe answer.The organizations that power the world run on Microsoft Azure and protecttheir clouds and data centers with Fortinet’s enterprise-class securitysolutions. Because of the extensive partnership between Microsoft andFortinet, Azure customers of any size can leverage jointly engineered solutionsto migrate to– and grow in–the cloud with confidence.Understanding the security challenges of cloud adoptionMoving to the cloud has many benefits, from the possibility of creating newrevenue streams to a shortened time to market. But cloud migrations alsoraise particular security considerations. According to the Fortinet 2023 CloudSecurity Report 1, ninety-five percent of enterprises reported being “very” to“highly” concerned about cloud security. Several variables contribute to thisfeeling, including:• Attack surfaces expand as organizations grow• Increased complexity from hybrid and multi-cloud deployments• Lack of visibility due to fragmented security solutions• Ever-increasing number of networks, devices, and applicationswith remote work• Shortage of skilled security professionals to tackle a rapidlyevolving threat landscapeFortinet offers trailblazing protection for AzureBacked by the continuous research of FortiGuard Labs , the Fortinet SecurityFabric is essential to reducing complexity and increasing overall securityeffectiveness across today’s expanding networks. Azure customers canleverage solutions from Fortinet and Microsoft that are designed to worktogether to achieve comprehensive visibility and multi-layered security.SOLUTION BRIEFStep Up Y our Security onMicrosoft Azure with Fortinet Why Fortinet More than 100 integrations between Fortinet and Microsoft.Recognized as winner of the Microsoft Partner of the Year Award.A Leader in the 2022 Gartner Magic quadrant for Network Firewalls, SD-WAN, SIEM, and Enterprise Wired and Wireless LAN Infrastructure.Microsoft has been a Fortinet Fabric Ready Partner since 20171 2023 Fortinet Cloud Security ReportManaging different Azure security use cases with FortinetUse case #1Safely migrate and build on AzureWhether you are a Fortinet customer migrating applications to Azure, or an Azure user seeking superior protection for your environment, pairing Fortinet and Microsoft is an effective joint approach for securing your cloud deployments. Fortinet protects Azure-based applications and workloads with solutions for network, cloud platform, and application defense. Fortinet offers a superior set of security solutions that are natively integrated into the Azure infrastructure and available on the Microsoft Commercial Marketplace. Better still, Fortinet’s security solutions are all part of a security fabric that extends across clouds and data centers.The Fortinet Security Fabric is backed by FortiGuard Labs, which gathers and analyzes over 14 billion security events per day. Utilizing artificial intelligence and machine learning, it continuously improves threat intelligence in real-time. The Fortinet Security Fabric uses this data to identify and defend against the latest threats.• Fortinet solutions integrate with numerous Azure services, including Azure Sentinel, Azure Active Directory, Azure Security Center, Microsoft Defender for Cloud, Azure Cloud Functions, Azure Application Gateway, and more.• FortiGate Next-Generation Firewall (NGFW) for Azure secures native, hybrid, and multi-cloud environments. FortiGate NGFW can recognize and understand unique applications and make relevant security decisions around proprietary traffic, detect botnets, and segment traffic.• FortiWeb web application firewall (WAF) protects business-critical web applications and their APIs from attacks. Advanced ML-powered features improve security and reduce administrative overhead.• Integration with Azure Virtual Machine facilitates scale-up and scale-out security.Use case #2Defend web applications and their APIs built on AzureAccording to Verizon’s 2022 Data Breach Investigation Report, web applications are the top action vector in security incidents, and in 42 percent of breaches.2FortiWeb Cloud can protect all of an organization’s web applications and APIs in one solution that is simple to deploy and easy to manage. With FortiWeb Cloud, organizations benefit from enterprise-level features while saving time and budget. FortiWeb Cloud delivers advanced visual analytics and machine learning capabilities to defend against such threats as the OWASP Top 10 and zero-day attacks. It goes beyond traditional WAFs to offer advanced features, including:• API discovery and protection to enable B2B communications and support your mobile applications.• Bot management to take action on malicious bots, while welcoming good bots, with automated identification and mitigation.• Threat analytics to reduce alert fatigue and ensure analysts can quickly focus on the most important threats.• The latest threat intelligence with signature updates and analytics from FortiGuard Labs.2 2022 Data Breach Investigations Report | VerizonUse case #3Build a global SD-WAN with Azure Virtual WAN integrationAzure Virtual WAN is a networking service that allows customers to leverage the Azure network backbone so they canbuild high-speed global transit network architectures. Fortinet FortiGate Secure SD-WAN for Microsoft Azure vWAN can be deployed directly into the Microsoft WAN hub, securing both north/south and east/west traffic and allowing organizations to utilize Microsoft Azure as a global backbone for their secure SD-WAN deployments.This solution deploys a set of FortiGate NGFWs as a managed application in Azure vWAN to support a secure SD-WAN with layer 4-7 inspection. Fortinet Secure SD-WAN delivers enterprise-class security and branch networking between Azure VNETs, the internet, and corporate branches or datacenters. Organizations can easily integrate SD-WAN and NGFW intoall traffic flows, and enforce layer 4-7 inspection and control powered by FortiGuard Labs. Cost-effective and offering fast connectivity, FortiGate for Azure vWAN delivers operational efficiencies through automation, deep analytics, and self-healing. • Deploy the FortiGate NGFW within vWAN to secure intra-cloud connectivity, as well as-site-to site, remote userand private connectivity.• Centralize control with FortiManager, which offers a single pane of glass view that reduces vulnerabilitiesfrom configuration errors.• Remain compliant with FortiAnalyzer, which simplifies compliance management and reporting with customizable regulatory templates, audit logging, and role-based access control, eliminating the need for many manual processes related to auditing.Use case #4Improve protections for Microsoft Windows on Azure Virtual DesktopsA complete desktop and app virtualization solution, Windows Virtual Desktop (WVD) runs in the cloud. In order to facilitate remote work, more companies are turning to WVD. However, these installations need sophisticated routing and securityin order to connect to data centers, branches, and client-to-site access to Azure services. By offering network inspection across all of these footprints with virtual private network (VPN) linkages from the endpoint into the cloud, FortiGate includes the ability to enforce advanced security policies such as zero trust and data leak prevention.• FortiGate NGFW adds to the core capabilities of Azure by providing network inspection across data centers, branches, and client-to-site access to Azure resources via virtual private network (VPN). It interconnects from the endpoint, through the premise, and into the cloud.• FortiGate’s deep packet inspection capabilities, along with SSLi for inspecting encrypted traffic, ensure network security.• FortiGate’s support for secure SD-WAN allows for secure connectivity among branches and virtual desktops.• FortiGate is ideal for enforcing zero trust policies, promoting rigorous validation before remote users and devices access their Microsoft environment.• Secure RISE with SAPSeek a security partner, not a productMaking a decision in cloud security should focus on seeking the best globalsecurity partner, not on tactical decisions about products.Fortinet, a leading security provider and the worldwide leader of unified threatmanagement solutions, keeps your workloads and applications safe on MicrosoftAzure. Powered by comprehensive threat intelligence and more than 20 yearsof cybersecurity innovation and experience, the broad suite of Fortinet solutionsprotects any application on Azure.To learn how to gain the most advanced protection on Azure, visit:/azure Copyright © 2023 Fortinet, Inc. All rights reserved. Fortinet, FortiGate, FortiCare and FortiGuard, and certain other marks are registered trademarks of Fortinet, Inc., and other Fortinet names herein may also be registered and/or common law trademarks of Fortinet. All other product or company names may be trademarks of their respective owners. Performance and other metrics contained herein were attained in internal lab tests under ideal conditions, and actual performance and other results may vary. Network variables, different network environments and other conditions may affect performance results. Nothing herein represents any binding commitment by Fortinet, and Fortinet disclaims all warranties, whether express or implied, except to the extent Fortinet enters a binding written contract, signed by Fortinet’s General Counsel, with a purchaser that expressly warrants that the identified product will perform according to certain expressly-identified performance metrics and, in such event, only the specific performance metrics expressly identified in such binding written contract shall be binding on Fortinet. For absolute clarity, any such warranty will be limited to performance in the same ideal conditions as in Fortinet’s internal lab tests. Fortinet disclaims in full any covenants, representations, and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise revise this publication without notice, and the most current version of the publication shall be applicable.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Question: 1PowerShellis used to:A. monitor user keystrokes.B. repair damaged hard disk drive sectors.C. automate a routine task.D. extend the life of the battery.Answer: CQuestion: 2Windows Aero is a:A. pointing device.B. device driver.C. desktop theme.D. Windows application.Answer: CQuestion: 3Which describes the purpose of Power Saver mode for a portable computer?A. To lock the computer when it is idleB. To prevent unauthorized programs from consuming resourcesC. To protect the display from burned-in imagesD. To shut down idle devices to conserve battery chargeAnswer: DQuestion: 4You want to change your default home page in Internet Explorer. In which location should you modify settings?A. Trusted SitesB. ViewC. Internet OptionsD. FavoritesAnswer: BQuestion: 5Every time you insert a music CD, you receive a dialog box that asks which action you want Windows to perform. Which should you configure so that your personal computer automatically identifies an audio CD and starts playing music?A. The Autoplay settingsB. The Ease of Access settingsC. a desktop gadgetD. The Personalization settingsAnswer: AQuestion: 6You need to modify the time displayed in the system tray. Which Control Panel feature should you use?A. Appearance and PersonalizationB. Display PropertiesC. Administrative ToolsD. Clock, Language, and RegionAnswer: DQuestion: 7You insert a software installation CD into your Windows 7 computer. The CD does not launch automatically. You need to perform a manual installation. What should you do?A. From Control Panel, use Programs.B. From Control Panel, use Ease of Access.C. Browse the contents of the hard disk drive and locate the Program Files folder.D. Browse the contents of the CD and locate the Setup file.Answer: DQuestion: 8A Windows service is a:A. program or process that runs in the background and does not require user intervention.B. hardware driver that provides support to a specific device.C. program or process that runs in the foreground.D. hardware driver that provides support to the operating system.Answer: AQuestion: 9Which Windows feature should you use to protect a computer against spyware?A. Group PolicyB. User Account ControlC. Windows DefenderD. Encrypting File SystemAnswer: DQuestion: 10Which feature allows you to create a new virtual application?A. Application Virtualization SequencerB. Windows InstallerC. Remote Desktop ConnectionD. Windows Virtual PCAnswer: AQuestion: 11Which action will trigger a user account control (UAC) prompt in Windows?A. Accessing the InternetB.Changing the time zone C.Installing a new program D.Restarting WindowsE. Changing settings in the Display Properties dialog boxAnswer: CQuestion: 12Where will you find information about removing computer viruses?A. Help and SupportB. System RestoreC. Disk CleanupD. System InformationAnswer: AQuestion: 13A Windows 7 library:A. organizes user files from disparate locations.B. makes copies of user files in a central location.C. encrypts files by using the Encrypting File System (EFS).D. restores files from system backup.Answer: AQuestion: 14You need to upgrade your computer from the FAT file system to an NTFS file system. What should you do?A. Use the Backup and Restore tool.B. Clear the hard disk drive by using the Format tool.C. Use the Convert C:/fs:ntfs command.D. Run the Windows Easy Transfer tool.Answer: CQuestion: 15The Encrypting File System (EFS) is a:A. digital document that verifies the identity of a user.B. specially made hard disk drive that requires a password.C. sequence of characters used to encrypt and decrypt information stored in a folder.D. feature that enables filesto be stored in a secure format.Answer: CQuestion: 16You need to configure a folder that allows everyone in your department to view and edit the files in the folder. You also need to ensure that users outside the department cannot access the files. What should you do?A. Grant access to a single user by using the Share With menu.B. Grant read access to specific people by using the Share With menu.C. Place the files in one of the Windows public folders.D. Grant read/write access to specific people by using the Share With menu.Answer: DQuestion: 17You need to configure a folder that allows everyone in your group to view and modify files. Which item in the Share With menu should you use?A. Specific PeopleB. Nobod yC. Homegroup (Read/Write)D. Homegroup (Read)Answer: CQuestion: 18Windows hides some files by default to:A. avoid accidental modification or deletion of system files.B. protect the confidentiality of the contents of files.C. improve access to system files.D. save disk space.Answer: AQuestion: 19You need a script to run at a specific time. Which Windows component should you use?A. Task ManagerB. Device ManagerC. Task SchedulerD. Event ViewerAnswer: CQuestion: 20You need to find out whether your computer has received the most recent critical Windows updates. What should you do?A. From the Computer Management console, view Services and Applications.B. From Windows Update, select View Update History.C. From Administration Tools, view Event Logs.D. From Control Panel, use Programs.Answer: CQuestion: 21Your computer is slow to start, and file access in Windows is slow. Which Windows feature should you use to improve performance?A. System RestoreB. windows DefenderC. Disk DefragmenterD. Disk FormatAnswer: AQuestion: 22Which feature ensures that your personal computer always has the latest patches and fixes for the operating system?A. Reliability and Performance MonitorB. Programs and FeaturesC. System Configuration UtilityD. Windows UpdateAnswer: DQuestion: 23Which Windows component should you use to make a cop y of all files on your computer?A. Disk CleanupB. System Image BackupC. System RestoreD. Disk ManagementAnswer: BQuestion: 24Which two editions of Windows 7 support Windows XP mode? (Each correct answer presents a complete solution. Choose two.)A. Home PremiumB. StarterC. UltimateD. ProfessionalAnswer: C, DExplanation:Using Windows XP Mode, you can run programs that were designed for Windows XP on computers running Windows 7 Professional, Enterprise, or Ultimate editions.Question: 25You plan to upgrade your computer to Windows 7. Which tool should you use to find out whether your current applications will run on Windows 7?A. Application Compatibility ToolkitB. Windows Anytime UpgradeC. Windows UpdateD. Windows Service PackAnswer: AQuestion: 26You need to install Windows 7 over an existing version of Windows. Which type of installation should you use to retain all your files, settings, and programs on your computer?A. use the Windows Easy Transfer tool, and select Custom (advanced).B. use the Windows 7 installation disk to perform a system repair.C. use the Windows Easy Transfer tool, and select Upgrade.D. use the Windows 7 installation disk to perform a clean installation.Answer: CQuestion: 27You need to find out the amount of physical memory available to Windows 7. Which command should you use?A. sysedit.exeB. msinfo32.exeC. msconfig.exeD.wmimgmt.mscAnswer: BQuestion: 28The Windows 7 USB/DVD Download Tool allows you to:A. create a bootable version of Windows 7 on a USB stick or a writable DVD.B. create backups of data files from your computer to a USB stick or a writable DVD.C. install Microsoft .NET Framework on a USB stick or a writable DVD.D. download files from the Internet directly to a USB stick or a writable DVD.Answer: AQuestion: 29You want to upgrade your computer from Windows Vista to Windows 7. What is the minimum processor speed required to run a 64-bit version of Windows 7?A. 800 MHzB. 1.0GHzC.1.2 GHz D.1.8 GHzAnswer: BQuestion: 30Which two features are supported by the Infrared Data Association (IrDA) protocol? (Each correct answer presents a complete solution. Choose two.)A. Data can be transferred across short distances.B. One computer can control another computer through a wireless connection.C. Some features of another computer can be controlled by using a remote control unit.D. The computer can identify Bluetooth devices.Answer: A, CQuestion: 31Which feature allows you to change the display resolution of a computer monitor?A. Computer Management ConsoleB. System Configuration ToolC. Appearance and PersonalizationD. Device ManagerAnswer: CQuestion: 32Which file system is designed for transfer of large files between a personal computer and flash devices?A. FAT16 file systemB. FAT32 file systemC. exFAT file systemD. NTFS file systemAnswer: CQuestion: 33DRAG DROPYou need to enable connection to a Bluetooth device. What should you do? (To answer, move the four appropriate actions from the list of actions to the answer area and arrange them in the correct order.)Answer:ExhibitQuestion: 34Which two steps should you perform to install a local printer that connects directly to your personal computer? (Each correct answer presents part of the solution. Choose two.)A. Connect the printer to an available USB port and allow Windows to locate and install the appropriate driver.B. Connect the Ethernet cable from your printer to the RJ45 connector on the personal computer and follow the Windows prompts.C. Follow the manufacturer's directions by using the installation CD provided along with the printer.D. Use the Add Network Printer feature from Control Panel.Answer: A, DQuestion: 35Which feature allows you to pause the printing of all documents waiting to print on a specific printer?A. The Print Setup pageB. The printer's Properties pageC. The printer's shortcut menuD. The Computer Management consoleAnswer: CQuestion: 36Which Windows feature allows secure printing over the Internet?A. Secure Transfer Protocol (STP)B. Internet Printing Protocol (IPP) by using HTTPSC. Voce over Internet Protocol (VoIP)D. Web2PrintAnswer: BQuestion: 37You want to repair Windows by using the Windows 7 System Recovery Disc. Before youbegin, which files should you back up to protect your personal data?A. All files in the Program Files directory.B. All files in the Windows directory.C. All files in drive C.D. Everything in My Documents.Answer: DQuestion: 38Which Windows feature allows you to request that someone else control your computer from their computer?A. Remote AssistanceB. Action CenterC. Sync CenterD.Connect NowAnswer: AQuestion: 39Which Windows feature should you use to find patches for Internet Explorer?A. Sync CenterB. System InformationC. Internet PropertiesD. Windows UpdateAnswer: DQuestion: 40A service pack is software that:A. includes all previously released important and recommended Windows Updates.B. cleans the registry and file system.C. includes a reinstallation of the operating system.D. enables remote servicing.Answer: AQuestion: 41You attempt to update your video driver. Your screen stops responding. You need to be able to restore the previous video driver. Which Windows feature should you use?A. Disk DefragmenterB. Disk CleanupC. Check Disk (Chkdsk)D. Safe ModeAnswer: DQuestion: 42You need to be able to access a file stored in a shared folder on your network even when you are disconnected from the network. What should you do?A. Configure the folder permissions as Read/Write.B. Make the folder available offline.C. From Control Panel, use Network and Internet.D. Type the IP address of the network computer in the Address field of Internet Explorer. Answer: AQuestion: 43You need to be able to recover an encrypted file even if you lose the key. What should you do?A. Use the Encrypting File System (EFS).B. Use System Restore to create a system restore point.C. Use Bitlocker encryption.D. Create a recovery certificate and store it on a portable device.Answer: DQuestion: 44Which is the largest single file that you can store on a FAT32 file system?A. 4GBB. 8GBC. 16GBD. 32GBAnswer: AQuestion: 45The purpose of a Public folder is to:A. share files with only one person on a network.B. share files with everyone on a network.C. share files with a selected group of people on a network.D. back up files to a location on a network.Answer: BQuestion: 46You want to view a folder of pictures from an external hard disk drive in your Windows 7 Pictures library. What should you do?A. Use the Include in Library menu to add the folder in Windows Explorer.B. Create a connection to the folders by using the Network and Sharing Center.C. Access the pictures by using a shared folder.D. Enable password-protected sharing.Answer: CQuestion: 47BitLocker prevents:A. the operating system from overwriting protected sectors on the hard disk drive.B. unauthorized users from accessing the Internet.C. unauthorized access to files.D. programs from accessing the memory of other programs.Answer: CQuestion: 48You attempt to install Windows 7 on your personal computer. You receive an error message stating that your product key is not valid. What is causing the error?A. You accidentally entered the product key in lower case.B. Your product key does not match the version of Windows that you are installing.C. The product key you are trying to use has expired.D. You reformatted your hard disk drive before you installed Windows.Answer: BQuestion: 49You need to allow others to access your Windows 7 computer by using the Remote Desktop connection. What should you do?A. Click Turn on network discovery in Network and Sharing Center.B. Enable Remote Desktop Connections in System Properties.C. Start the Remote Desktop Connection client in Accessories.D. Set the security level to medium in Internet Options.Answer: BQuestion: 50You need to migrate files and settings from a Windows XP computer to another computer that runs Windows 7. Which tool should you use?A. Windows Easy TransferB. Windows 7 Compatibility CheckerC. Windows Upgrade AdvisorD. Application Compatibility ToolkitAnswer: AQuestion: 51Which Windows feature will allow you to run automated scripts on a remote computer?A. Windows Remote ManagementB. Remote Access ServicesC. Remote Desktop ConnectionD. Virtual Private NetworkAnswer: AQuestion: 52Which Windows 7 feature should you use to ensure that only administrators can install new software?A. Network and Sharing CenterB. User Account ControlC. Microsoft Management ConsoleD. Ease of AccessAnswer: BQuestion: 53You need to manage service dependencies on your Windows 7 computer. Which feature should you use?A. Action CenterB. Event ViewerC.Task SchedulerD. Computer Management ConsoleAnswer: DQuestion: 54The Windows Action Center allows you to:A. choose options during system startup.B. view alerts and take appropriate actions to keep Windows running smoothly.C. view and modify settings of installed programs.D. manage the documents in the print queue.Answer: BQuestion: 55Which feature allows you to run applications hosted on network file servers or web servers?A. Windows Virtual PCB. Remote Desktop ConnectionC. Windows InstallerD. Application Virtualization ClientAnswer: DQuestion: 56Which is the fastest way to ensure that new desktop icons align into straight columns and rows?A. Right-click Desktop, select Properties, and then click Appearance.B.Right-click Desktop, select View, and then clickAuto arrange icons.C. Right-click Taskbar, select Tile Vertically, and then click Tile Horizontally.D. Right-click Desktop and select Refresh.Answer: BQuestion: 57Which prevents you from establishing a Remote Desktop connection to a remote computer?A. Incorrect monitor settings in Device Manager.B. Incorrect screen resolution in the Display Properties dialog box.C. Incorrect port settings in Windows Firewall.D. Incorrect security settings in Internet Explorer.Answer: CQuestion: 58The Remote Desktop Connection is used to:A. search the Internet.B. attend a webinar.C. access another personal computer.D. conduct a Lync Online Meeting.Answer: CQuestion: 59You need to configure a mouse for a left-handed user. What should you do?A. Configure alternate input devices.B. Use Device Manager to modify settings in the Mouse Properties dialog box.C. Use Control Panel to modify settings in the Mouse Properties dialog box.D. Use the manufacturer’s website to update the mouse driver.Answer: CQuestion: 60Your computer is running slower than usual. Where should you look to find out which applications are consuming the maximum number of resources?A. Administrative ToolsB. Device ManagerC. System TrayD. Task ManagerE. Network and Sharing CenterAnswer: DQuestion: 61You want to connect to a wireless access point. You need to view a list of available networks. Which two actions should you perform? (Each correct answer presents a complete solution. Choose two.)A. Click the network icon in the notification area.B. From Control Panel, use Windows Mobility Center.C. From Control Panel, use Network and Sharing Center.D. From Control Panel, use Sync Center.E. From Control Panel, use Ease of Access.Answer: A, CQuestion: 62What is the maximum size of a virtual hard disk?A. 2 terabytesB. 5terabytesC.16 terabytes D.500GBAnswer: AQuestion: 63Which online service allows you to store and retrieve files over the Internet?A. Windows Future StorageB. Windows Live SkyDriveC. Windows Media CenterD. Windows Storage ServerAnswer: BQuestion: 64Which feature allows you to manually configure a hardware device?A. Windows Task ManagerB. Ease of AccessC. Device ManagerD. Registry EditorAnswer: CQuestion: 65DRAG DROPYou need to install a new webcam on your personal computer. What should you do? (To answer, move the four appropriate actions from the list of actions to the answer area and arrange them in the correct order.)Exhibit:Question: 66You have several active jobs in the print queue. You need to view the print queue. What should you do?A. Use the Printer icon on the system tray.B. Use the Windows Task Manager.C. Click the Print button in the application that is printing.D. Use the Computer Management console.Answer: AQuestion: 67Where should you view the list of services on your Windows 7 computer?A. From the Windows Task Manager dialog boxB. From the Windows RegistryC. From the System Properties dialog boxD. From the Windows Action CenterAnswer: AQuestion: 68Which Windows feature allows you to run a program on your computer that is installed on another computer?A. Windows Virtual PCB. Microsoft Application VirtualizationC. Remote Desktop ConnectionD. System Center Service ManagerAnswer: DQuestion: 69Which feature should you use to restrict certain actions only to an administrator account on a Windows 7 computer?A. Windows Experience IndexB. User Account ControlC. BitLockerD. Computer ManagementAnswer: BQuestion: 70You have a legacy application that must be used in Windows 7. Which feature should you use if the legacy application runs poorly or fails to run?A. Programs in Control PanelB. Windows InstallerC. Windows Easy TransferD. Program Compatibilit y AssistantAnswer: DQuestion: 71You need to find out whether your computer can run a program that performs resource intensive tasks. Which Windows feature should you use?A. System Configuration UtilityB. Memory Diagnostics ToolC. Reliability and Performance MonitorD. Windows Experience IndexAnswer: DQuestion: 72Which feature ensures that the latest device drivers are installed on your computer?A. Reliability and Performance MonitorB. Windows UpdateC. Task SchedulerD. System configuration UtilityAnswer: BQuestion: 73Which feature should you use to install the most recent definitions for Windows Defender?A. Windows UpdateB. Sync CenterC. Windows InstallerD. Programs and FeaturesAnswer: AQuestion: 74Which Windows feature allows you to roll back your computer’s settings to a previous date and time?A. System RestoreB. Safe ModeC. Disk CloningD. Disk MirroringAnswer: AQuestion: 75Which feature allows you to transfer information from your computer to your mobile phone?A. Windows Mobility CenterB. Device ManagerC. Sync CenterD. Windows Easy TransferAnswer: AQuestion: 76You have a document that you update regularly. To access it directly froma/an:A. folder.B. icon.C. library.D. shortcut.Answer: DQuestion: 77You need to prevent specific users from logging on to a computer from 24:00 hours to 07:00 hours. Which Control Panel feature should you use?A. User Account ControlB. Administrative ToolsC. Clock, Language, and RegionD. Parental ControlsAnswer: DQuestion: 78Which Windows feature allows you to manually control another Windows computer?A. Remote Control MonitorB. Remote Desktop ConnectionC. Remote Power ManagementD. Remote Procedure CallAnswer: BQuestion: 79You plan to upgrade your computer to Windows 7. You need to view a report that identifies potential compatibility problems with your computer’s hardware, devices, and programs. Which tool should you use?A. Sync CenterB. Windows Anytime UpgradeC. Windows Upgrade AdvisorD. Windows Easy TransferAnswer: DQuestion: 80Which two versions of Windows 7support the Encrypting File System(EFS)functionality? (Each correct answer presents a complete solution. Chose two.)A. Ultimate EditionB. Home Premium EditionC. Professional EditionD. Starter EditionAnswer: A, CExplanation:EFS is not fully supported on Windows 7 Starter, Windows 7 Home Basic, and Windows 7 Home Premium.Question: 81You need to remotely control another computer by using a Remote Desktop connection. Where should you start the Remote Desktop Connection client?A. From the Actions menu in Windows Live MessengerB. From the User Accounts settings in Control PanelC. From the Accessories folder in All ProgramsD. From the Internet Options dialog box in Internet ExplorerAnswer: CQuestion: 82Which is a potential risk when redirecting a USB storage device during a Remote Desktop session?A. Access can be slower.B. The device can stop working.C. The session can stop responding.D. Data can be lost.Answer: DQuestion: 83You want to change the default printer used by the Quick Print feature in some applications. Where should you change the Windows default printer?A. In the printer’s Properties windowB. In the print queueC. Within the Print Setup pageD. Within the Devices and Printers user interfaceAnswer: DQuestion: 84What should you do to secure and protect the connection to a Bluetooth device?A. Turn off make device discoverable after connecting your devices.B. Reset the Bluetooth device to factory default settings after making a connection.C. Turn off the Bluetooth device when not in use.D. Use unique pairing codes when connecting your devices.Answer: DQuestion: 85You want to upgrade your Windows operating system to Windows 7. Which feature should you use to find out whether the existing devices will work after the upgrade?A. System ManagerB. Windows 7 Compatibility CenterC. Device ManagerD. Windows UpdateAnswer: DQuestion: 86Which Windows technology increases system performance by using flash memory?A. Direct Memory AccessB. File compressionC. Connect NowD. ReadyBoostAnswer: DQuestion: 87Which Windows feature should you use to assign a drive letter to a shared folder on the network?A. Public Folder SharingB. Computer Management ConsoleC. Advanced SharingD. Map Network DriveAnswer: DQuestion: 88You attempt to print to a network printer, but you are unable to find the printer when you search for available printers. What is a reason that you might not be able to find the printer?A. Windows Firewall is blocking network discovery.B. The computer that the printer is connected to is turned off.C. The printer does not have the Plug and Play functionality.D. The printer is out of paper.Answer: AQuestion: 89Which program will run on a 64-bit version of the Windows operating system?A. A 32-bit laser printer driverB. A 32-bit video card driverC. A 32-bit version of Microsoft OfficeD. A 32-bit wireless network adapter driverAnswer: C。
