Space Efficient Algorithms for the
Data Structures and Algorithms
Divide and conquer is a powerful approach for solving conceptually difficult problems. Divide and conquer approach requires you to find a way of:
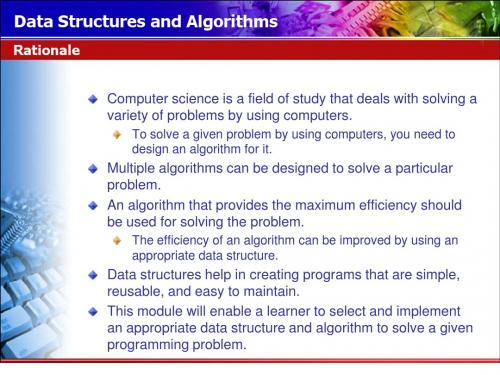
Multiple algorithms can be designed to solve a particular problem. An algorithm that provides the maximum efficiency should be used for solving the problem.
Data Structures and Algorithms
Rationale
Computer science is a field of study that deals with solving a variety of problems by using computers.
To solve a given problem by using computers, you need to design an algorithm for it.
Finding the shortest distance from an originating city to a set of destination cities, given the distances between the pairs of cities. Finding the minimum number of currency notes required for an amount, where an arbitrary number of notes for each denomination are available. Selecting items with maximum value from a given set of items, where the total weight of the selected items cannot exceed a given value.
三维空间避让算法

三维空间避让算法Avoidance algorithms in three-dimensional space are crucial for ensuring the safety and smooth operation of various autonomous systems, such as drones, robots, and self-driving cars. These algorithms enable the autonomous systems to navigate complex environments, avoid obstacles, and ensure collision-free movement. The algorithms use sensor data to detect obstacles in the environment and plan a path to safely navigate around them.三维空间避让算法是确保各种自主系统(如无人机、机器人和自动驾驶汽车)安全顺畅运行的关键。
这些算法使自主系统能够在复杂环境中导航、避开障碍物,并确保无碰撞移动。
算法利用传感器数据检测环境中的障碍物,并规划路径以安全绕过它们。
One important aspect of three-dimensional avoidance algorithms is their ability to handle dynamic and unpredictable obstacles. These algorithms must be able to quickly adapt to new obstacles that may appear in the environment and change their planned path accordingly. This requires real-time sensor data processing andefficient path planning algorithms to ensure the safety and efficiency of the autonomous system.三维避让算法的一个重要方面是它们能够处理动态和不可预测的障碍物。
汽车工程师的英文单词

汽车工程师的英文单词《Automobile Engineers》Automobile engineers play a crucial role in the modern world.Automobile engineers are involved in the design of cars from the ground up. They need to consider the overall shape and style of the vehicle. For example, they might use computer - aided design (CAD) software to create sleek and aerodynamic exteriors that not only look good but also reduce wind resistance.They also design the interior layout, ensuring that there is enough space for passengers to be comfortable and for all the necessary components like the dashboard, seats, and storage compartments.They are responsible for choosing the right materials for different parts of the car. For instance, they might select high - strength steel for the chassis to ensure the car's safety and durability.They work on the engine design as well. They have to optimize the engine's performance, making it powerful enough to provide good acceleration while also being fuel -efficient. This involves a deep understanding of thermodynamics and mechanical engineering principles. For example, they might develop new engine technologies like hybrid or electric powertrains to meet the growing demand for more environmentally friendly cars.Automobile engineers are at the forefront of ensuring vehicle safety. They design safety features such as airbags, anti - lock braking systems (ABS), and electronic stability control (ESC).They conduct extensive crash tests, both in computer simulations and in real - life scenarios, to make sure that the car can protect its occupants in case of an accident.A solid knowledge of mechanical engineering, including principles of mechanics, thermodynamics, and fluid dynamics is essential. For example, understanding how fluids flow in the engine cooling system or how heat is transferred in the engine combustion process.They also need to be proficient in using various engineering tools and software, such as CAD software for design and simulation software for testing the performance of different car components.When issues arise during the design or manufacturing process, automobile engineers need to be able to quickly identify the problem and come up with effective solutions. For example, if a new engine design is not meeting the expected fuel - efficiency standards, they have to analyze the various factors involved, such as the combustion process, the fuel injection system, or the engine's internal friction, and make the necessary adjustments.The development of a car is a complex process that involves many different departments and specialists. Automobile engineers need to work well with others, including designers, manufacturing engineers, and marketing teams. For instance, they need to communicate effectively with the design team to ensure that the engineering aspects of the car are in line with the overall design concept, and with the manufacturing team to ensure that the design can be produced efficiently and cost - effectively.With the increasing trend towards electric vehicles (EVs), automobile engineers will need to focus more on battery technology, electric motor design, and charging infrastructure. For example, they will need to develop batteries with higher energy density to increase the driving range of EVs.The development of autonomous vehicles also presents new challenges and opportunities. Engineers will need to work on advanced sensor technologies, artificial intelligence algorithms for vehicle control, and safety systems that can ensure the reliable operation of self - driving cars.There is a growing demand for more sustainable transportation solutions. Automobile engineers will be involved in developing cars that are not only fuel - efficient but also use more environmentally friendly materials and manufacturing processes. For example, they might explore the use of recycled materials in car interiors or develop manufacturing processes that reduce waste and emissions.In conclusion, automobile engineers are an integral part of the automotive industry, and their work will continue to shape the future of transportation.。
Optimizing Algorithm Efficiency

Optimizing Algorithm EfficiencyIn order to optimize algorithm efficiency, it is important to understand what efficiency means in the context of algorithms. Efficiency is the measure of how well an algorithm solves a problem in terms of time and space complexity. In other words, an efficient algorithm is one that can solve a problem quickly and with minimal use of resources.There are several ways to optimize algorithm efficiency. One common approach is to analyze the time complexity of an algorithm and identify ways to reduce the number of operations it performs. This can be done by eliminating unnecessary operations, reorganizing the order of operations, or using more efficient data structures.Another way to optimize algorithm efficiency is to analyze the space complexity of an algorithm and identify ways to reduce the amount of memory it uses. This can be done by storing data more efficiently, reusing data structures, or eliminating unnecessary storage.In addition to analyzing and optimizing the time and space complexity of an algorithm, there are other techniques that can be used to improve efficiency. One such technique is parallel processing, which involves breaking a problem into smaller subproblems that can be solved simultaneously on multiple processors. Parallel processing can greatly reduce the time it takes to solve a problem, especially for large-scale computations.Another technique for optimizing algorithm efficiency is to use heuristic methods, which are shortcuts or rules of thumb that can be used to quickly find a good solution to a problem. Heuristic methods are particularly useful for complex problems where traditional algorithms are too slow or too memory-intensive.Overall, optimizing algorithm efficiency requires a combination of analyzing time and space complexity, using parallel processing, and applying heuristic methods. By carefully considering these factors and implementing appropriate optimizations, it ispossible to create algorithms that are fast, memory-efficient, and able to solve complex problems effectively.。
计算机专业英语unit3 B课文

Computer programmingComputer programming, often shortened to programming or coding, is the process of writing , testing ,and maintaining the source code of computer programs. The source is written in a programming language. This code may be a modification of existing source or somethingcompletely new,the purpose being to create a program that exhibits the desired behavior. Theprocess of writing source code requires expertise in many different subjects, including kn owledge of the application domain,specialized algorithms, and formal logic.Within software engineering, programming is regarded as one phase in a software develo pment process.In some specialist applications or extreme situations a program may be written or mod ified (known as patching) by directly storing the numeric values of the machine code instr uctions to be executed into memory.There is an ongoing debate onthe extent to which the writing of programs is an art, a craft or an engineering discipline. Good programming is generally considered to be the measured application of all three: e xpert knowledge informing an elegant, efficient, and maintainable software solution. The discipline differs from many other technical professions in that programmers generally donot need to be licensed or pass any standardized, or governmentally regulated, certificati on tests in order to call themselves "programmers" or even "software engineers".Another ongoing debate is the extent to which the programming language used in wr iting programs affects the form that the final program takes. This debate is analogous to t hat surrounding the Sapir-Whorf hypothesis in linguistics.1.ProgrammersComputer programmers are those who write computer software. Theirjob usually involves .●Requirements analysis●Specification●Software architecture●Coding●Compilation●Software testing●Documentation●Integration●Maintenance2.Programming languagesDifferent proglamming languages support different styles of programming, called pr ogramming paradigms. The choice of language used is subject to many considerati ons, such as company policy, suitability to task, availability of third-party packages, or individual preference. Ideally the programming language best suited for the taskat hand will be selected. Trade-offs from this ideal involve finding enough program mers who know the language to build a team, the availability of compilers for that la nguage, and the efficiency with which programs written in a given language execute.3.Modern programming4.Algorithmic complexity5. The academic field and engineermg practice of computer programming are largelyconcerned with discovering and implementing the most efficient algorithms for a giv en class of problem. For this purpose, algorithms are classified into orders using so -called Big O notation, O(n), which expresses execution time, memory consumption , or another parameter in terms of the size of an input. Expert programmers are fam iliar with a variety of well-established algorithms and their respective complexities, a nd use this knowledge to consider design trade-offs between, for example, memory consumption and performance.Research in computer programming includes investigation into the unsolved pr oposition that P, the class of algorithms which can be deterministically solved in poly nomial time with respect to an input, is not equal to NP, the class of algorithms for w hich no polynomial-time solutions are known. Work has shown that many NP algorith ms can be transformed, in polynomial time. into others, such as the Travelling sales man problem, thus establishing a large class of "hard" problems which are for the pu rposes of analysis, equivalent.3.2 MethodologiesThe first step in every software development project should be requirements analy sis, followed by modeling, implementation, and failure elimination or debugging. T here exist a lot of differing approaches for each of those tasks. One approach popula r for requirements analysis is Use Case analysis. Popular modeling techniques inc lude Object-Oriented Analysis and Design (OOAD) and Model-Driven Architecture ( MDA). The Unified Modeling Language (UML) is a notation used for both OOAD and MDA. A similar technique used for database design is Entity-Relationship ModeIin g (ER Modeling). Implementation techniques include imperative languages (objec t-oriented or procedural), functional languages, and logic languages.Debugging is most often done with ISEs like Visual Studio, and Eclipse. Separate debuggers like gdb are also used.3.3 Mcasuring language usageIt ig very difficult to determine what the most popular of modern programming lan guages Some languages are very popular for particular kinds of applicaticms (e.g., C OBOL is still strong in corporate data center, oRen on large mainframes, FORTRAN in engineering applications. and C emhedded appticationsl. while some languages ar e regularly used to write manv different kinds applicalions.Methods of measuring language popularity include: counting the number of job ad vertisements that mention the language, the number of books teaching the language that are sold (this overestimates the importance of newer languages), and estimatesof the number of existing lines of code written in the language (this underestimates t he number of users of business languages such as COBOL).3.4. DebuggingDebugging is a very important task for every programmer, because an erroneous program is often useless. Languages like C and Assembler are very challenging even to expert programm ers because of failure modes like Buffer overruns, bad pointers or uninitialized memory.A buffer overrun can damage adjacent memory regions and cause a failure in a totally dif ferent program line. Because of those memory issues tools like Valgrind, Purify or Bound schecker are virtually a necessity for modern software development in the C- language. L anguages such as Java, PHP and Python protect the programmer from most of these run time failure modes, but this may come at the price of a dramatically lower execution spee d of the resulting program. This is acceptable for applications where execution speed is d etermined by other considerations such as database access or file IO. The exact r.nd urill depend upon specific implementation details. Modern Java virtual machines, of sophisti cated optimizations, including runtime conversion of interpret machine code.。
分解质因数 英语

分解质因数英语Title: Prime Factorization: Unlocking the Secrets of NumbersIntroductionPrime factorization is a fundamental concept in mathematics that has numerous applications in various fields, from computer science to cryptography. It involves breaking down a number into its prime factors, which are the prime numbers that, when multiplied together, result in theoriginal number. This process is not only essential for understanding the properties of numbers but also haspractical implications in areas such as number theory, algorithm design, and data encryption.The Importance of Prime FactorizationPrime factorization is a crucial tool in mathematics and computer science, as it helps us understand the structure andbehavior of numbers. By identifying the prime factors of a number, we can gain insights into its divisibility, its prime factors, and its relationship with other numbers. This information can be used to solve a wide range of problems, from finding the greatest common divisor (GCD) of two numbers to designing efficient algorithms for tasks such as integer factorization.In computer science, prime factorization is particularly important in the field of cryptography. Many modern encryption techniques, such as the RSA algorithm, rely on the difficulty of factoring large numbers into their prime factors. The security of these algorithms depends on the fact that it is computationally challenging to find the prime factors of a large number, especially as the number grows in size.The Process of Prime FactorizationThe process of prime factorization involves breaking down a number into its prime factors, which are the prime numbers that, when multiplied together, result in the original number. There are several techniques that can be used to performprime factorization, including the trial division method, the factor tree method, and the Sieve of Eratosthenes.The trial division method is one of the simplest and most straightforward approaches to prime factorization. Itinvolves dividing the number by each prime number, starting with the smallest prime number, until a factor is found. This process is repeated until all the prime factors of the number have been identified.The factor tree method, on the other hand, involves creating a visual representation of the prime factorization process. The number is first divided by its smallest prime factor, and then each of the resulting factors is furtherdivided by their respective prime factors. This process continues until all the prime factors have been identified.The Sieve of Eratosthenes is a more efficient algorithmfor finding prime numbers, which can be used as a starting point for prime factorization. This method involves systematically eliminating numbers that are not prime,starting with the smallest prime number, until all the prime numbers up to a given limit have been found.Applications of Prime FactorizationPrime factorization has a wide range of applications in various fields, including:1. Number theory: Prime factorization is essential for understanding the properties of numbers, such as divisibility, prime factors, and the relationship between different numbers.2. Computer science: Prime factorization is crucial in cryptography, where it is used to design secure encryptionalgorithms. It is also used in algorithm design, where it can be used to optimize the performance of certain algorithms.3. Engineering: Prime factorization is used in the design and analysis of electrical circuits, where it can be used to identify the prime factors of the impedance of a circuit.4. Finance: Prime factorization can be used in financial modeling and analysis, where it can be used to identify the prime factors of financial data and to identify patterns and trends.5. Physics: Prime factorization is used in particle physics, where it is used to identify the prime factors of the masses of subatomic particles.ConclusionPrime factorization is a fundamental concept in mathematics that has numerous applications in various fields. By understanding the process of prime factorization and itspractical implications, we can gain insights into the natureof numbers and develop more efficient and effective solutions to a wide range of problems. Whether it's in computer science, cryptography, or any other field, the ability to performprime factorization is a valuable tool that can help usunlock the secrets of numbers and unlock new opportunitiesfor innovation and discovery.。
逆命题和逆否命题 英语

逆命题和逆否命题英语Inverse Propositions and Inverse NegationsLogical reasoning is a fundamental aspect of human cognition and communication. One of the key concepts in this domain is the idea of propositions and their logical relationships. Propositions are declarative statements that can be evaluated as either true or false. The study of the logical connections between propositions is a crucial component of formal logic and critical thinking.Among the various types of logical relationships between propositions, the concepts of inverse propositions and inverse negations are particularly important. These concepts are closely related, yet distinct, and understanding their nuances is essential for effective logical reasoning and problem-solving.An inverse proposition is a statement that is the logical opposite of another proposition. In other words, if a proposition is true, its inverse proposition is false, and vice versa. For example, the proposition "All cats are mammals" has the inverse proposition"Some cats are not mammals." The inverse proposition negates the original proposition by introducing a qualifier or condition that contradicts the original statement.Inverse negations, on the other hand, are the logical opposites of the negation of a proposition. In other words, the inverse negation of a proposition is the statement that is the logical opposite of the negation of that proposition. For instance, the proposition "All cats are mammals" has the negation "Not all cats are mammals." The inverse negation of this negation would be "Some cats are mammals."It is important to note that the inverse of a proposition and the inverse negation of a proposition are not the same thing. The inverse of a proposition is a new proposition that directly contradicts the original proposition, while the inverse negation of a proposition is the logical opposite of the negation of the original proposition.The distinction between inverse propositions and inverse negations becomes particularly relevant in the context of formal logic and mathematical reasoning. In these domains, the precise formulation and manipulation of logical statements are crucial for deriving valid conclusions and solving complex problems.For example, in the field of mathematical logic, the concept ofinverse propositions and inverse negations is essential for understanding the behavior of logical connectives, such as the AND, OR, and NOT operators. Mastering these logical relationships can help individuals navigate the intricacies of formal proofs, truth tables, and logical inference rules.Moreover, the understanding of inverse propositions and inverse negations has practical applications in various fields, including computer science, philosophy, and even everyday decision-making. For instance, in computer programming, the ability to recognize and manipulate logical statements is crucial for developing efficient algorithms and software solutions.In the realm of philosophy, the study of inverse propositions and inverse negations is closely linked to the analysis of logical fallacies and the development of sound argumentation strategies. Philosophers often use these concepts to critically examine the logical validity of arguments and to identify potential flaws or inconsistencies.In everyday life, the awareness of inverse propositions and inverse negations can also be beneficial. For instance, when making decisions or evaluating information, being able to recognize the logical relationships between statements can help individuals avoid cognitive biases, make more informed choices, and engage in moreeffective problem-solving.In conclusion, the concepts of inverse propositions and inverse negations are essential components of logical reasoning and critical thinking. By understanding the nuances of these concepts and their applications, individuals can enhance their ability to communicate effectively, analyze information more precisely, and make more informed decisions. As we navigate the complexities of the modern world, the mastery of these logical principles can serve as a powerful tool for navigating the intricacies of human cognition and communication.。
人工智能技术在航天领域的应用书籍英文版

人工智能技术在航天领域的应用书籍英文版全文共6篇示例,供读者参考篇1The Awesome Power of AI in Space ExplorationHave you ever dreamed of traveling to space and exploring other planets? Well, thanks to artificial intelligence (AI), that dream is becoming easier than ever before! AI is a type of super-smart computer technology that can think and learn just like humans. It's helping scientists and engineers in some amazing ways when it comes to space exploration. Let me tell you all about it!First off, AI is really great at spotting patterns and analyzing huge amounts of data. This is super helpful when studying images and data sent back by spacecraft exploring other planets or asteroids. Normal computers can get overwhelmed by all that information, but AI can quickly sort through it and find interesting things that human scientists might miss.For example, let's say a rover on Mars sends back thousands of images of rocks. An AI system can study all those pictures and identify which rocks look most interesting or different from therest. It can then flag those rocks for the human scientists to take a closer look. How cool is that?Another way AI helps is by controlling and operating robots and rovers on other planets. You see, sending commands from Earth to a rover on Mars takes a really long time because the planets are so far apart. By the time a command makes it to Mars, the situation may have already changed!But AI systems on the rovers can quickly make decisions and adjust as needed without having to wait for instructions from Earth. The AI can say "Oh, there's a big rock in my path. Let me just drive around it!" This AI autonomy makes space exploration way more efficient.AI also plays a role in designing spacecraft and planning flight paths. There are so many different factors to consider like gravity, air resistance, fuel efficiency and more. AI systems can run advanced calculations and simulations to find the best spacecraft designs and most optimal flight trajectories. This saves a ton of time, money and headaches for the engineers!Maybe the coolest use of AI is in identifying potential new discoveries in space data. AI software can be trained to recognize certain patterns that might indicate new planets, asteroids, stars, or even possible signs of alien life! With so much data constantlystreaming in from telescopes and probes, AI is essential for spotting interesting signals that humans could easily miss.As you can see, AI is becoming a true superstar when it comes to space exploration. It's like having a team of highly intelligent robot assistants working tirelessly to help scientists explore the cosmos. Who knows what mind-blowing discoveries AI will help make next?Isn't it amazing how advanced technology is allowing us to study space in ways we could barely imagine just a few decades ago? AI is seriously taking space research and exploration to new frontiers. The next generation of kids like you may even get to be the first space colonizers on Mars thanks to AI! How awesome would that be?So keep studying hard, feed your curiosity about space and science, and who knows? You may end up playing a pivotal role in humankind's next great leap among the stars with the help of AI! The future of space exploration is going to beout-of-this-world incredible. Let's explore it together!篇2The Awesome World of AI in Space ExplorationHave you ever dreamed of blasting off into space and exploring other planets? Well, thanks to artificial intelligence (AI), that dream is becoming a reality! AI is a type of super-smart computer technology that can think and learn like humans. And it's playing a huge role in helping us explore the great unknown of outer space.Let me tell you about some of the amazing ways AI is being used in space missions:Piloting SpacecraftFlying a spacecraft is no easy task, especially when you're millions of miles away from Earth. That's where AI comes in! Powerful AI systems can help pilot and navigate spacecraft, making countless calculations and decisions in a fraction of a second. This ensures that the spacecraft stays on course and avoids any obstacles in its path, like asteroid fields or cosmic debris.Analyzing Data from SpaceWhen we send probes and rovers to other planets, they collect a massive amount of data – things like images, soil samples, and readings on temperature, radiation levels, and more. But sifting through all that data can be overwhelming forhuman scientists. That's why AI is used to analyze and make sense of this information, identifying patterns and insights that might be missed by the human eye.Designing Better Rockets and SpacecraftBuilding a rocket or spacecraft that can withstand the extreme conditions of space is a huge challenge. But AI is lending a hand by simulating and testing different designs virtually, before anything is built in real life. This way, engineers can experiment with different materials, shapes, and configurations to find the most efficient and safest options.Exploring Extraterrestrial EnvironmentsWhen we send rovers to planets like Mars, we want them to be able to navigate the terrain and make decisions on their own, without having to wait for instructions from Earth (which can take a long time because of the vast distances involved). AI allows these rovers to perceive their surroundings, identify obstacles and scientifically interesting features, and make decisions about where to go and what to study next.Searching for Extraterrestrial LifeOne of the biggest questions humans have is whether we're alone in the universe or if there's life on other planets. AI isplaying a crucial role in this search by analyzing data from telescopes and space probes, looking for patterns and signs that could indicate the presence of life – things like unusual gases in a planet's atmosphere or biosignatures in soil samples.These are just a few of the ways AI is revolutionizing space exploration. As AI technology continues to advance, who knows what other amazing discoveries and achievements we'll unlock in our quest to understand the cosmos?Maybe one day, you could even be part of the team that designs an AI system for a mission to Mars or beyond! If you're into science, technology, and space, studying AI could open up a world of exciting possibilities.For now, keep reaching for the stars, and remember – with AI on our side, the sky is no longer the limit!篇3The Wonders of AI in Space ExplorationHave you ever dreamed of traveling to outer space? Of exploring distant planets and galaxies? Well, thanks to some really cool technology called Artificial Intelligence (AI), scientistsand engineers are able to explore the mysteries of the universe from right here on Earth!What is Artificial Intelligence?AI is like having a super smart robot helper that can process tons of information and solve complex problems faster than any human. It uses advanced computer programs and algorithms to analyze data, recognize patterns, and make decisions. Pretty neat, right?AI in Space MissionsAI plays a crucial role in space missions by helping scientists and engineers in many different ways. Let me give you some examples:Spacecraft NavigationNavigating a spacecraft through the vast expanse of space is no easy task. There are countless factors to consider, like the gravitational pull of planets, the trajectory of asteroids, and even tiny bits of space debris. AI systems can crunch all this data and calculate the safest and most efficient routes for spacecraft to travel.Robotic ExplorationHave you heard of the Mars Rovers? These are awesome robots that have been exploring the surface of Mars for years, taking pictures and collecting samples. AI helps these rovers to navigate the rough Martian terrain, avoid obstacles, and even choose which rocks to analyze based on their scientific value.Image and Data AnalysisSpacecraft and telescopes send back tons of data and images from space every day. AI algorithms can quickly analyze this data, identifying patterns and anomalies that human scientists might miss. This helps us learn more about the universe and make new discoveries.Fault Detection and RepairImagine being millions of miles away from Earth, and something goes wrong with your spacecraft. AI systems can monitor the various components of a spacecraft, detect any faults or anomalies, and even suggest ways to repair or work around the problem. This keeps astronauts safe and missions running smoothly.Mission PlanningPlanning a space mission is like a giant, complicated puzzle. There are so many factors to consider, like fuel consumption,launch windows, crew schedules, and scientific objectives. AI can simulate different scenarios and come up with the most efficient and effective mission plans.AI on Earth for Space ExplorationAI doesn't just help in space – it also plays a vital role in space exploration right here on Earth. For example:Telescope OperationsPowerful telescopes like the Hubble Space Telescope and the James Webb Space Telescope generate massive amounts of data. AI algorithms help astronomers sort through this data, identifying interesting celestial objects and events for further study.Satellite MonitoringThere are thousands of satellites orbiting Earth, monitoring everything from weather patterns to national security threats. AI systems can analyze data from these satellites in real-time, alerting authorities to potential storms, forest fires, or other emergencies.Rocket Design and TestingBuilding rockets is a complex engineering challenge. AI can simulate different rocket designs, test them in virtual environments, and optimize their performance before they're ever built and launched.The Future of AI in Space ExplorationAs AI technology continues to advance, its applications in space exploration will only become more exciting. Scientists are working on AI systems that can autonomously plan and execute entire space missions, from launch to landing.Imagine an AI-powered spacecraft that can explore distant planets and moons, making its own decisions and discoveries without human intervention. Or an AI system that can search for signs of life on exoplanets by analyzing their atmospheres and surface features.The possibilities are endless, and AI will undoubtedly play a crucial role in unlocking the secrets of the universe.ConclusionAI is truly a game-changer in the field of space exploration. From navigating spacecraft to analyzing data and planning missions, this incredible technology is helping us push theboundaries of what's possible. Who knows, maybe one day you'll even get to explore space with the help of an AI companion!篇4The Awesome Power of AI in Space Exploration!Have you ever dreamed of traveling to other planets or even galaxies far, far away? Well, get ready because artificial intelligence (AI) is making space exploration easier and more exciting than ever before! AI helps scientists and engineers solve really tough problems so they can build awesome rockets, satellites, rovers, and more to explore the mysteries of the cosmos.What is AI anyway? It's a type of computer software that can learn, reason, and make decisions in a way that's kind of like how humans think - but way faster! AI programs can look at huge piles of data and find hidden patterns that would take people forever to figure out.One of the coolest ways AI helps with space is in the design process for new spacecraft and rockets. Normally, humans have to spend months or years drawing up blueprints and running simulations to test all their ideas. But with AI, they can feed the computer tons of data on things like aerodynamics, propulsion,materials science, and more. Then the AI crunches those numbers to come up with optimized designs in just days or weeks!For example, NASA used AI to design a weird-looking shuttle with air-scooped engine designs for future missions to Mars. The AI found a shape that makes the vehicle lighter and more fuel efficient for interplanetary travel. Who knows what kinds of crazy, futuristic spaceships the AI will dream up next? Maybe one day we'll be zooming through the galaxy in something straight out of a sci-fi movie!AI also plays a huge role in getting spacecraft off the ground and navigating through space. Controlling powerful rockets that are blasting off into the atmosphere is an insanely difficult task with a bajillion different factors to consider at every second. But AI flight control systems can monitor all those variables like weather, fuel levels, trajectories, and so on - way better than any human possibly could. They can make split-second adjustments to keep the launch going smoothly.Then once the spacecraft is in space, AI guides it along the best possible path to its destination, whether that's orbiting the Earth, visiting the Moon, or flying by Mars. It has to take into account the gravitational pull of planets, the trajectories ofdebris fields, fuel efficiency, and tons of other variables. Without AI's help, we'd get hopelessly lost out there in the big cosmic ocean!AI's incredible processing power also comes in handy when rovers like Perseverance or Curiosity are exploring the surfaces of other planets and moons. These cool little robotic vehicles are loaded with scientific instruments that collect massive amounts of data every day on things like the soil composition, mineral content, atmospheric conditions, and potential signs of microbial life.All that data gets beamed back to Earth, where teams of scientists start analyzing it. But there's so much of it that it would take them years to go through it all - and by then, the rovers would have already moved on! That's why they use AI programs to rapidly process the raw data and identify anything interesting that human scientists should take a closer look at.The AI can spot subtle patterns and anomalies that we might miss. Then it flags those sections so researchers know exactly where to focus their eyes and efforts. Thanks to AI's tireless data-crunching abilities, scientists don't waste time and can make new discoveries way faster.Let's not forget about AI's role in deep space exploration too! You've probably heard of the Hubble Space Telescope and James Webb Space Telescope taking all those breathtaking pictures of galaxies billions of light years away. But do you know what helps them decide what areas of space to aim their cameras at and when?You guessed it - AI! These space telescopes are designed to search for things like potentially Earth-like exoplanets in the "goldilocks" zones of other solar systems where liquid water (and possibly life?!) could exist. But with billions upon billions of stars out there, how do they choose which ones to examine? AI algorithms analyze all the data we have on those star systems and prioritize the targets that are most promising.Then once the images come back from those observations, AI helps scientists study them for any signs of exoplanets or other incredible phenomena we've never seen before. For example, AI has discovered mysterious, ultra-powerful cosmic particles called "WIMPzillas" slamming into our galaxy from some unknown source! Who knows what other crazy new things AI will help scientists uncover?As you can see, AI is absolutely indispensable when it comes to exploring the great beyond. Its ability to rapidly process hugeamounts of data and come up with solutions to complex problems is helping us make new discoveries and go farther into space than ever before. From designing next-generation spacecraft to studying astronomical mysteries light years away, AI is expanding humanity's understanding of the cosmos every single day.So the next time you gaze up at the stars, remember that AI is playing a huge behind-the-scenes role in unraveling their secrets - and maybe even one day helping us travel between them! Isn't AI just the coolest? The future of space exploration is going to be an awesome cosmic adventure thanks to this incredibly powerful technology.篇5Exploring Artificial Intelligence in the Sky: How Smart Computers Help Us SoarHi there, young explorers! Today, we're going to talk about something truly out of this world – artificial intelligence (AI) and how it's helping us explore the vast unknown of space. Get ready to have your mind blown by the incredible ways thesesuper-smart computer programs are changing the game in the aerospace industry!What is Artificial Intelligence?Before we dive into the nitty-gritty of how AI is used in space exploration, let's first understand what it is. Artificial intelligence is like having a really, really smart friend who can process tons of information incredibly quickly and solve complex problems that would take humans ages to figure out. It's a computer program that can learn, reason, and make decisions just like humans do, but way faster and more efficiently.AI in Space ExplorationNow, let's talk about how these intelligent computer programs are helping us explore the great beyond. Buckle up, because the applications are truly mind-boggling!Rocket ScienceDid you know that AI plays a crucial role in designing and launching rockets into space? These smart programs can simulate countless scenarios, analyze vast amounts of data, and help engineers optimize every aspect of a rocket's design and trajectory. From ensuring the rocket has enough fuel to calculating the perfect launch window, AI makes sure our space missions go off without a hitch.Navigating the CosmosOnce a spacecraft is in space, AI takes over the navigation. These intelligent systems can process data from various sensors, cameras, and other instruments to ensure the spacecraft stays on course and avoids any potential hazards, like space debris or asteroids. AI also helps control the spacecraft's movements, making precise adjustments to its trajectory and orientation.Exploring Distant WorldsWhen it comes to exploring other planets, moons, and celestial bodies, AI is our best friend. Imagine trying to analyze all the data and images sent back by a rover on Mars or a probe orbiting Jupiter – it would take humans forever! But AI can quickly process this information, identifying interesting features, analyzing soil samples, and even helping to decide where to send the rover next.Searching for Extraterrestrial LifeOne of the most exciting applications of AI in space exploration is its potential to help us find evidence of extraterrestrial life. These smart programs can sift through vast amounts of data from telescopes and other instruments, looking for patterns or anomalies that could indicate the presence of life on other planets or in distant galaxies.Monitoring Space WeatherJust like we have weather on Earth, there's also space weather that can affect our missions and technology in space. AI helps us monitor and predict things like solar flares, cosmic radiation, and other space weather events that could potentially disrupt our spacecraft or communication systems.The Future of AI in Space ExplorationAs amazing as these applications already are, we've only scratched the surface of what AI can do for space exploration. In the future, we can expect AI to play an even bigger role in areas like:Designing and building advanced spacecraft and habitats for long-term space missionsAssisting astronauts during spacewalks and other complex tasksHelping us establish sustainable human settlements on other planets or moonsAnalyzing data from powerful new telescopes to unravel the mysteries of the universeThe possibilities are truly endless, and it's all thanks to the incredible power of artificial intelligence!Final ThoughtsAs you can see, AI is an incredibly powerful tool that's helping us push the boundaries of space exploration like never before. From designing rockets to searching for alien life, these super-smart computer programs are playing a crucial role in our quest to understand the cosmos.So, the next time you look up at the stars, remember the amazing AI technology that's helping us unravel the secrets of the universe. Who knows, maybe one day you'll be part of the team developing the next generation of AI systems that take us even further into the great beyond!篇6The Amazing Ways Artificial Intelligence Helps in Space ExplorationHi there, fellow space enthusiasts! Today, I want to tell you all about something really cool – how Artificial Intelligence (AI) is being used in space exploration. AI is like having a super-smartrobot helping scientists and astronauts explore the vastness of space.1. Smart Robots and Astronaut AssistantsImagine having a robot buddy who can help astronauts with their work in space. Well, that's exactly what AI does! AI-powered robots can be sent on space missions to assist astronauts with tasks like repairing equipment or carrying out experiments. These smart robots can even learn from their experiences and get better at their jobs over time. They can explore dangerous places that might be too risky for humans, making space exploration safer for everyone.2. Autonomous SpacecraftAnother amazing way AI is used in space is through autonomous spacecraft. These spacecraft can think for themselves and make important decisions without human intervention. They use AI algorithms to analyze data and navigate through space. With the help of AI, spacecraft can adjust their routes, avoid obstacles, and even land on other planets safely. It's like having a smart pilot flying the spacecraft!3. Understanding Space DataSpace is full of data, and analyzing all that information can be a big challenge. But thanks to AI, scientists can now process and understand space data more easily. AI algorithms can sift through vast amounts of data collected by telescopes and satellites, helping scientists make new discoveries. They can find patterns, identify celestial objects, and even predict space weather. AI is like a space detective, uncovering the secrets of the universe!4. Planning Space MissionsPlanning a space mission is a complex task. There are many factors to consider, like fuel consumption, spacecraft trajectory, and safety. AI can help scientists and engineers plan these missions more efficiently. By using AI algorithms, they can optimize routes, calculate fuel usage, and predict potential problems. This helps save time, money, and resources, making space exploration more successful.5. Assisting Astronaut HealthSpace travel can be tough on astronauts' bodies, but AI is here to help! AI technology can monitor astronauts' health and provide real-time assistance. It can analyze vital signs, detect any health issues, and even suggest remedies. This ensures thatastronauts stay healthy and safe during their missions. AI is like a space doctor, taking care of our brave astronauts.In conclusion, AI is an incredible tool that is revolutionizing space exploration. From smart robots to autonomous spacecraft, AI is helping us explore space like never before. It analyzes data, plans missions, and assists astronauts in their important work. So, the next time you look up at the stars, remember that AI is up there too, making the universe a little easier to understand. Keep dreaming big and reach for the stars!Word Count: 457I hope you find this article helpful and enjoyable to read. Happy exploring, young astronomers!。
关于航天发明的作文英语

关于航天发明的作文英语Title: The Impact of Space Exploration on Inventions。
Space exploration has long captured the imagination of humanity, pushing the boundaries of what we know and what we can achieve. Beyond the exploration itself, the innovations spurred by the quest for space have had profound effects on our daily lives. In this essay, we will delve into the myriad inventions that have been born from the pursuit of space exploration and examine their impact on society.One of the most notable inventions resulting from space exploration is undoubtedly the Global Positioning System (GPS). Originally developed by the United States Department of Defense to aid in military navigation, GPS has since become an indispensable tool in civilian life. From guiding drivers to their destinations to enabling precise location tracking on smartphones, GPS has revolutionized how we navigate the world.Furthermore, advancements in materials science spurred by the need for lightweight yet durable spacecraft have led to the development of numerous everyday products. For instance, the lightweight materials used in space suitshave found applications in athletic apparel, making sports equipment more comfortable and performance-enhancing. Similarly, the insulation materials designed to protect spacecraft from extreme temperatures have been adapted for use in homes, improving energy efficiency and reducing heating and cooling costs.Space exploration has also driven innovation in healthcare technology. The rigorous demands of space travel necessitate compact and reliable medical equipment, leading to the development of portable diagnostic devices and telemedicine technologies. These innovations not onlybenefit astronauts in space but also improve healthcare access and delivery in remote or underserved areas on Earth.Moreover, space exploration has catalyzed advancementsin telecommunications technology. Satellites launched intoorbit for communication purposes have enabled global connectivity, facilitating instant communication and information exchange across the globe. From satellite television to high-speed internet, these technologies have transformed how we communicate, learn, and conduct business.Another area profoundly impacted by space explorationis environmental monitoring and disaster management. Satellites equipped with remote sensing instruments can monitor changes in Earth's climate, track deforestation,and detect natural disasters such as hurricanes andwildfires from space. This data is invaluable for disaster preparedness and response efforts, helping to mitigate the impact of natural disasters and protect vulnerable communities.In addition to tangible inventions, space exploration has also spurred advancements in computer technology and artificial intelligence. The computational challenges of space missions have driven the development of faster processors, more efficient algorithms, and intelligent software systems. These technologies have applications farbeyond space exploration, powering everything from smartphones to autonomous vehicles.Furthermore, the quest for space has inspired countless individuals to pursue careers in science, technology, engineering, and mathematics (STEM) fields. This influx of talent has led to a virtuous cycle of innovation, with bright minds collaborating to solve complex problems and push the boundaries of human knowledge and capability.In conclusion, the inventions born from space exploration have had a profound and far-reaching impact on society, touching virtually every aspect of our lives. From GPS and lightweight materials to healthcare technology and telecommunications, the benefits of space exploration extend far beyond the confines of our planet. As we continue to explore the cosmos, we can expect even more groundbreaking innovations that will shape the future of humanity for generations to come.。
Efficient Algorithms for Citation Network Analysis

a r X i v :c s /0309023v 1 [c s .D L ] 14 S e p 2003Efficient Algorithms for Citation Network AnalysisVladimir BatageljUniversity of Ljubljana,Department of Mathematics,Jadranska 19,1111Ljubljana,Slovenia e-mail:vladimir.batagelj@uni-lj.siAbstractIn the paper very efficient,linear in number of arcs,algorithms for determining Hum-mon and Doreian’s arc weights SPLC and SPNP in citation network are proposed,and some theoretical properties of these weights are presented.The nonacyclicity problem in citation networks is discussed.An approach to identify on the basis of arc weights an im-portant small subnetwork is proposed and illustrated on the citation networks of SOM (self organizing maps)literature and US patents.Keywords:large network,acyclic,citation network,main path,CPM path,arc weight,algorithm,self organizing maps,patent1IntroductionThe citation network analysis started with the paper of Garfield et al.(1964)[10]in which the introduction of the notion of citation network is attributed to Gordon Allen.In this paper,on the example of Asimov’s history of DNA [1],it was shown that the analysis ”demonstrated a high degree of coincidence between an historian’s account of events and the citational relationship between these events ”.An early overview of possible applications of graph theory in citation network analysis was made in 1965by Garner [13].The next important step was made by Hummon and Doreian (1989)[14,15,16].They proposed three indices (NPPC,SPLC,SPNP)–weights of arcs that provide us with automatic way to identify the (most)important part of the citation network –the main path analysis.In this paper we make a step further.We show how to efficiently compute the Hummon and Doreian’s weights,so that they can be used also for analysis of very large citation networks with several thousands of vertices.Besides this some theoretical properties of the Hummon and Doreian’s weights are presented.The proposed methods are implemented in Pajek –a program,for Windows (32bit),for analysis of large networks .It is freely available,for noncommercial use,at its homepage [4].For basic notions of graph theory see Wilson and Watkins [18].Table1:Citation network characteristicsnetwork m n0k C∆in24 DNA6013700 2231218161340 Small world198816316000 105911024282320 Cocitation49293519020 308412678321052 Kroto319500116660 447023704247350 Zewail542531015166382 8843782126310984 Desalination25751141111573121 377476813764117327700Figure1:Citation Network in Standard FormLet I={(u,u):u∈U}be the identity relation on U andQ∩I=∅.The relation Q⋆=3Analysis of Citation NetworksAn approach to the analysis of citation network is to determine for each unit/arc its impor-tance or weight.These values are used afterward to determine the essential substructures in the network.In this paper we shall focus on the methods of assigning weights w:R→I R+0to arcs proposed by Hummon and Doreian[14,15]:•node pair projection count(NPPC)method:w d(u,v)=|R inv⋆(u)|·|R⋆(v)|•search path link count(SPLC)method:w l(u,v)equals the number of”all possible search paths through the network emanating from an origin node”through the arc(u,v)∈R, [14,p.50].•search path node pair(SPNP)method:w p(u,v)”accounts for all connected vertex pairs along the paths through the arc(u,v)∈R”,[14,p.51].3.1Computing NPPC weightsTo compute w d for sets of units of moderate size(up to some thousands of units)the matrix representation of R can be used and its transitive closure computed by Roy-Warshall’s algorithm [9].The quantities|R⋆(v)|and|R inv⋆(u)|can be obtained from closure matrix as row/column sums.An O(nm)algorithm for computing w d can be constructed using Breath First Search from each u∈U to determine|R inv⋆(u)|and|R⋆(v)|.Since it is of order at least O(n2)this algorithm is not suitable for larger networks(several ten thousands of vertices).3.2Search path count methodTo compute the SPLC and SPNP weights we introduce a related search path count(SPC) method for which the weights N(u,v),uRv count the number of different paths from s to t (or from Min R to Max R)through the arc(u,v).To compute N(u,v)we introduce two auxiliary quantities:let N−(v)denotes the number of different s-v paths,and N+(v)denotes the number of different v-t paths.Every s-t pathπcontaining the arc(u,v)∈R can be uniquely expressed in the formπ=σ◦(u,v)◦τwhereσis a s-u path andτis a v-t path.Since every pair(σ,τ)of s-u/v-t paths gives a corresponding s-t path it follows:N(u,v)=N−(u)·N+(v),(u,v)∈RwhereN−(u)= 1u=sv:vRu N−(v)otherwiseandN+(u)= 1u=tv:uRv N+(v)otherwiseThis is the basis of an efficient algorithm for computing the weights N(u,v)–after the topo-logical sort of the network[9]we can compute,using the above relations in topological order, the weights in time of order O(m).The topological order ensures that all the quantities in the right side expressions of the above equalities are already computed when needed.The counters N(u,v)are used as SPC weights w c(u,v)=N(u,v).3.3Computing SPLC and SPNP weightsThe description of SPLC method in[14]is not very precise.Analyzing the table of SPLC weights from[14,p.50]we see that we have to consider each vertex as an origin of search paths.This is equivalent to apply the SPC method on the extended network N l=(U′,R l)R l:=R′∪{s}×(U\∪R(s))It seems that there are some errors in the table of SPNP weights in[14,p.51].Using the definition of the SPNP weights we can again reduce their computation to SPC method applied on the extended network N p=(U′,R p)R p:=R∪{s}×U∪U×{t}∪{(t,s)}in which every unit u∈U is additionaly linked from the source s and to the sink t.3.4Computing the numbers of paths of length kWe could use also a direct approach to determine the weights w p.Let L−(u)be the number of different paths terminating in u and L+(u)the number of different paths originating in u.Then for uRv it holds w p(u,v)=L−(u)·L+(v).The procedure to determine L−(u)and L+(u)can be compactly described using two fami-lies of polynomial generating functionsP−(u;x)=h(u)k=0p−(u,k)x k and P+(u;x)=h−(u)k=0p+(u,k)x k,u∈Uwhere h(u)is the depth of vertex u in network(U,R),and h−(u)is the depth of vertex u in network(U,R inv),The coefficient p−(u,k)counts the number of paths of length k to u,and p+(u,k)counts the number of paths of length k from u.Again,by the basic principles of combinatoricsP−(u;x)= 0u=s1+x· v:vRu P−(v;x)otherwiseandP+(u;x)= 0u=t1+x· v:uRv P+(v;x)otherwiseand both families can be determined using the definitions and computing the polynomials in the(reverse for P+)topological ordering of U.The complexity of this procedure is at most O(hm).FinallyL−(u)=P−(u;1)and L+(v)=P+(v;1)In real life citation networks the depth h is relatively small as can be seen from the Table 1.The complexity of this approach is higher than the complexity of the method proposed in subsection 3.3–but we get more detailed information about paths.May be it would make sense to consider ’aging’of references by L −(u )=P −(u ;α),for selected α,0<α≤1.3.5Vertex weightsThe quantities used to compute the arc weights w can be used also to define the corresponding vertex weights tt d (u )=|R inv ⋆(u )|·|R ⋆(u )|t c (u )=N −(u )·N +(u )t l (u )=N ′−(u )·N ′+(u )t p (u )=L −(u )·L +(u )They are counting the number of paths of selected type through the vertex u .3.6Implementation detailsIn our first implementation of the SPNP method the values of L −(u )and L +(u )for some large networks (Zewail and Lederberg)exceeded the range of Delphi’s LargeInt (20decimal places).We decided to use the Extended real numbers (range =3.6×10−4951..1.1×104932,19-20significant digits)for counters.This range is safe also for very large citation networks.To see this,let us denote N ∗(k )=max u :h (u )=k N −(u ).Note that h (s )=0and uRv ⇒h (u )<h (v ).Let u ∗∈U be a unit on which the maximum is attained N ∗(k )=N −(u ∗).ThenN ∗(k )=v :vRu ∗N −(v )≤v :vRu ∗N ∗(h (v ))≤v :vRu ∗N ∗(k −1)==deg in (u ∗)·N ∗(k −1)≤∆in (k )·N ∗(k −1)where ∆in (k )is the maximal input degree at depth k .Therefore N ∗(h )≤ hk =1∆in (k )≤∆h in .A similar inequality holds also for N +(u ).From both it followsN (u,v )≤∆h (u )in ·∆h −(v )out≤∆H −1where H =h (t )and ∆=max(∆in ,∆out ).Therefore for H ≤1000and ∆≤10000we getN (u,v )≤∆H −1≤104000which is still in the range of Extended reals.Note also that in the derivation of this inequality we were very generous –in real-life networks N (u,v )will be much smaller than ∆H −1.Very large/small numbers that result as weights in large networks are not easy to use.One possibility to overcome this problem is to use the logarithms of the obtained weights –logarith-mic transformation is monotone and therefore preserve the ordering of weights (importance of vertices and arcs).The transformed values are also more convenient for visualization with line thickness of arcs.4Properties of weights4.1General properties of weightsDirectly from the definitions of weights we getw k(u,v;R)=w k(v,u;R inv),k=d,c,pandw c(u,v)≤w l(u,v)≤w p(u,v)Let N A=(U A,R A)and N B=(U B,R B),U A∩U B=∅be two citation networks,andN1=(U′A,R′A)and N2=((U A∪U B)′,(R A∪R B)′)the corresponding standardized networks of thefirst network and of the union of both networks.Then it holds for all u,v∈U A and for all p,q∈R At(1)k(u)t(2)k(v),andw(1)k(p)w(2)k(q),k=d,c,l,pwhere t(1)and w(1)is a weight on network N1,and t(2)and w(2)is a weight on network N2.This means that adding or removing components in a network do not change the ratios(ordering)of the weights inside components.Let N1=(U,R1)and N2=(U,R2)be two citation networks over the same set of units U and R1⊆R2thenw k(u,v;R1)≤w k(u,v;R2),k=d,c,p4.2NPPC weightsIn an acyclic network for every arc(u,v)∈R holdR inv⋆(u)∩R⋆(v)=∅and R inv⋆(u)∪R⋆(v)⊆Utherefore|R inv⋆(u)|+|R⋆(v)|≤n and,using the inequality √2(a+b),alsow d(u,v)=|R inv⋆(u)|·|R⋆(v)|≤1Rv⇒R⋆(u)⊂R⋆(v)The weights w d are larger in the’middle’of the network.A more uniform(but less sensitive)weight would be w s(u,v)=|R inv⋆(u)|+|R⋆(v)|or in the normalized form w′s(u,v)=14.3SPC weightsFor theflow N(u,v)the Kirchoff’s node law holds:For every node v in a citation network in standard form it holdsincomingflow=outgoingflow=t c(v)Proof:N(x,v)= x:xRv N−(x)·N+(v)=( x:xRv N−(x))·N+(v)=N−(v)·N+(v) x:xRvN(v,y)= y:vRy N−(v)·N+(y)=N−(v)· y:vRy N+(y)=N−(v)·N+(v) y:vRy2 From the Kirchoff’s node law it follows that the totalflow through the citation network equals N(t,s).This gives us a natural way to normalize the weightsN(u,v)w(u,v)=Figure2:Preprint transformationBut,new problems arise:What is the right value of the’aging’factor?Is there an efficient algorithm to count the restricted trails?The other possibility,since a citation network is usually almost acyclic,is to transform it into an acyclic network•by identification(shrinking)of cyclic groups(nontrivial strong components),or •by deleting some arcs,or•by transformations such as the’preprint’transformation(see Figure2)which is based on the following idea:Each paper from a strong component is duplicated with its’preprint’version.The papers inside strong component cite preprints.Large strong components in citation network are unlikely–their presence usually indicates an error in the data.An exception from this rule is the citation network of High Energy Particle Physics literature[20]from arXiv.In it different versions of the same paper are treated as a unit.This leads to large strongly connected components.The idea of preprint transformation can be used also in this case to eliminate cycles.6First Example:SOM citation networkThe purpose of this example is not the analysis of the selected citation network on SOM(self-organizing maps)literature[12,24,23],but to present typical steps and results in citation net-work analysis.We made our analysis using program Pajek.First we test the network for acyclicity.Since in the SOM network there are11nontrivial strong components of size2,see Table1,we have to transform the network into acyclic one.We decided to do this by shrinking each component into a single vertex.This operation produces some loops that should be removed.Figure3:Main path and CPM path in SOM network with SPC weights Now,we can compute the citation weights.We selected the SPC(search path count)method. It returns the following results:the network with citation weights on arcs,the main path network and the vector with vertex weights.In a citation network,a main path(sub)network is constructed starting from the source vertex and selecting at each step in the end vertex/vertices the arc(s)with the highest weight, until a sink vertex is reached.Another possibility is to apply on the network N=(U,R,w)the critical path method (CPM)from operations research.First we draw the main path network.The arc weights are represented by the thickness of arcs.To produce a nice picture of it we apply the Pajek’s macro Layers which contains a sequence of operations for determining a layered layout of an acyclic network(used also in analysis of genealogies represented by p-graphs).Some experiments with settings of different options are needed to obtain a right picture,see left part of Figure3.In its right part the CPMTable2:15Hubs and AuthoritiesRank Hub Id Authority Id1CLARK-JW-1991-V36-P1259HOPFIELD-JJ-1982-V79-P25540.063660.334273HUANG-SH-1994-V17-P212KOHONEN-T-1990-V78-P14640.057210.123985SHUBNIKOV-EI-1997-V64-P989#GARDNER-E-1988-V21-P2570.054960.093537VEMURI-V-1993-V36-P203MCELIECE-RJ-1987-V33-P4610.054090.076569BUSCEMA-M-1998-V33-P17RUMELHART-DE-1985-V9-P750.052580.0727111WELLS-DM-1998-V41-P173ANDERSON-JA-1977-V84-P4130.052330.0703313SMITH-KA-1999-V11-P15KOSKO-B-1987-V26-P49470.051490.0580215KOHONEN-T-1990-V78-P1464GROSSBERG-S-1987-V11-P23 path is presented.We see that the upper parts of both paths are identical,but they differ in the continuation. The arcs in the CPM path are thicker.We could display also the complete SOM network using essentially the same procedure as for the displaying of main path.But the obtained picture would be too complicated(too many vertices and arcs).We have to identify some simpler and important subnetworks inside it.Inspecting the distribution of values of weights on arcs(lines)we select a threshold0.007 and determine the corresponding arc-cut–delete all arcs with weights lower than selected threshold and afterwards delete also all isolated vertices(degree=0).Now,we are ready to draw the reduced network.Wefirst produce an automatic layout.We notice some small unimportant components.We preserve only the large main component,draw it and improve the obtained layout manually.To preserve the level structure we use the option that allows only the horizontal movement of vertices.Finally we label the’most important vertices’with their labels.A vertex is considered important if it is an endpoint of an arc with the weight above the selected threshold(in our case 0.05).The obtained picture of SOM’main subnetwork’is presented in Figure4.We see that the SOMfield evolved in two main branches.From CARPENTER-1987the strongest(main path) arc is leading to the right branch that after some steps disappears.The left,more vital branch is detected by the CPM path.Further investigation of this is left to the readers with additional knowledge about the SOMfield.As a complementary information we can determine Kleinberg’s hubs and authorities vertex weights[17].Papers that are cited by many other papers are called authorities;papers that cite many other documents are called hubs.Good authorities are those that are cited by good hubsFigure4:Main subnetwork at level0.007and good hubs cite good authorities.The15highest ranked hubs and authorities are presented in Table2.We see that the main authorities are located in eighties and the main hubs in nineties. Note that,since we are using the relation uRv≡u is cited by v,we have to interchange the roles of hubs and authorities produced by Pajek.An elaboration of the hubs and authorities approach to the analysis of citation networks complemented with visualization can be found in Brandes and Willhalm(2002)[8].7Second Example:US patentsThe network of US patents from1963to1999[21]is an example of very large network (3774768vertices and16522438arcs)that,using some special options in Pajek,can still be analyzed on PC with at least1G memory.The SPC weights are determined in a range of1 minute.This shows that the proposed approach can be used also for very large networks.The obtained main path and CPM path are presented in Figure5.Collecting from the United States Patent and Trademark Office[22]the basic data about the patents from both paths,see Table3-6,we see that they deal with’liquid crystal displays’.But,in this network there should be thousands of’themes’.How to identify them?Using the arc weights we can define a theme as a connected small subnetwork of size in the interval k ..K(for example,between k=1Table3:Patents on the liquid-crystal display patent author(s)and titleMar13,1951Jun29,1954May30,1967May19,1970Jan18,1972May30,1972Jul11,1972Sep19,1972Oct10,1972May8,1973Jun19,1973Oct23,1973Nov20,1973Mar5,1974Mar12,1974Apr23,1974May7,1974Mar18,1975Apr8,1975May6,1975Jun24,1975Mar30,1976May4,1976Jun1,1976Aug17,1976Dec28,1976Mar8,1977Mar22,1977Apr12,1977Table4:Patents on the liquid-crystal display patent author(s)and titleJun14,1977Jun28,1977Mar7,1978Apr4,1978Apr11,1978Sep12,1978Oct3,1978Dec19,1978Apr17,1979May15,1979Apr1,1980Apr15,1980May13,1980Oct21,1980Apr14,1981Sep22,1981Oct6,1981Nov24,1981May18,1982Jul20,1982Sep14,1982Nov2,1982Nov30,1982Jan11,1983May31,1983Jun7,1983Jun7,1983Aug23,1983Nov15,1983Dec6,1983Dec27,1983Jun19,1984Jun26,1984Jul17,1984Sep18,1984Table5:Patents on the liquid-crystal display patent author(s)and titleSep18,1984Oct30,1984Mar5,1985Apr9,1985Apr30,1985Jul2,1985Nov5,1985Dec10,1985Apr22,1986Nov11,1986Dec23,1986Apr14,1987Apr21,1987Sep22,1987Nov3,1987Nov24,1987Dec1,1987Dec15,1987Jan12,1988Jan26,1988Jun21,1988Sep13,1988Jan3,1989Jan10,1989Apr11,1989May23,1989Oct31,1989Sep18,1990May21,1991May21,1991Jun16,1992Jun23,1992Dec15,1992Dec29,1992Table6:Patents on the liquid-crystal display patent author(s)and titleSep7,1993Feb1,1994May3,1994June7,1994Dec20,1994Apr18,1995Jul23,1996Aug6,1996Sep10,1996Nov4,1997Jun23,1998Jan5,1999Nov23,1999Dec21,19992510205010011001000sizef r e qFigure 6:Island size frequency distributionTable8:Some patents from the’foam’island patent author(s)and titleNov29,1977Sep29,1981Nov2,1982Jul10,1984Jan29,1985Oct1,1985Dec22,1987May22,1990Feb26,1991Dec8,1992Feb16,1993May3,1994Sep24,1996Table9:Some patents from’fiber optics and bags’island patent author(s)and titleJul24,1984Apr16,1985Jul23,1985May20,1986Jun30,1987Jan12,1988Nov15,1988Nov22,1988Mar7,1989Mar7,1989May9,1989Jan1,1991Mar5,1991Feb23,1993May3,1994Nov15,1994The subnetworks approach onlyfilters out the structurally important subnetworks thus pro-viding a researcher with a smaller manageable structures which can be further analyzed using more sophisticated and/or substantial methods.9AcknowledgmentsThe search path count algorithm was developed during my visit in Pittsburgh in1991and pre-sented at the Network seminar[2].It was presented to the broader audience at EASST’94in Budapest[3].In1997it was included in program Pajek[4].The’preprint’transformation was developed as a part of the contribution for the Graph drawing contest2001[5].The al-gorithm for the path length counts was developed in August2002and the Islands algorithm in August2003.The author would like to thank Patrick Doreian and Norm Hummon for introducing him into thefield of citation network analysis,Eugene Garfield for making available the data on real-life networks and providing some relevant references,and Andrej Mrvar and Matjaˇz Zaverˇs nik for implementing the algorithms in Pajek.This work was supported by the Ministry of Education,Science and Sport of Slovenia, Project0512-0101.References[1]Asimov I.:The Genetic Code,New American Library,New York,1963.[2]Batagelj V.:Some Mathematics of Network work Seminar,Department ofSociology,University of Pittsburgh,January21,1991.[3]Batagelj V.:An Efficient Algorithm for Citation Networks Analysis.Paper presented atEASST’94,Budapest,Hungary,August28-31,1994.[4]Batagelj V.,Mrvar A.:Pajek–program for analysis and visualization of large networks.http://vlado.fmf.uni-lj.si/pub/networks/pajek/http://vlado.fmf.uni-lj.si/pub/networks/pajek/howto/extreme.htm [5]Batagelj V.,Mrvar A.:Graph Drawing Contest2001Layoutshttp://vlado.fmf.uni-lj.si/pub/GD/GD01.htm[6]Batagelj V.,Zaverˇs nik M.:Generalized Cores.Submitted,2002./abs/cs.DS/0202039[7]Batagelj V.,Zaverˇs nik M.:Islands–identifying themes in large networks.In preparation,August2003.[8]Brandes U.,Willhalm T.:Visualization of bibliographic networks with a reshaped land-scape metaphor.Joint Eurographics–IEEE TCVG Symposium on Visualization,D.Ebert, P.Brunet,I.Navazo(Editors),2002.http://algo.fmi.uni-passau.de/˜brandes/publications/bw-vbnrl-02.pdf[9]Cormen T.H.,Leiserson C.E.,Rivest R.L.,Stein C.:Introduction to Algorithms,SecondEdition.MIT Press,2001.[10]Garfield E,Sher IH,and Torpie RJ.:The Use of Citation Data in Writing the History ofScience.Philadelphia:The Institute for Scientific Information,December1964./papers/useofcitdatawritinghistofsci.pdf[11]Garfield E.:From Computational Linguistics to Algorithmic Historiography,paper pre-sented at the Symposium in Honor of Casimir Borkowski at the University of Pittsburgh School of Information Sciences,September19,2001./papers/pittsburgh92001.pdf [12]Garfield E.,Pudovkin A.I.,Istomin,V.S.:Histcomp–(comp iled Hist oriography program)/histcomp/guide.html/histcomp/index.html[13]Garner R.:A computer oriented,graph theoretic analysis of citation index structures.Flood B.(Editor),Three Drexel information science studies,Philadelphia:Drexel Univer-sity Press1967./rgarner.pdf[14]Hummon N.P.,Doreian P.:Connectivity in a Citation Network:The Development of DNATheory.Social Networks,11(1989)39-63.[15]Hummon N.P.,Doreian P.:Computational Methods for Social Network Analysis.SocialNetworks,12(1990)273-288.[16]Hummon N.P.,Doreian P.,Freeman L.C.:Analyzing the Structure of the Centrality-Productivity Literature Created Between1948and1979.Knowledge:Creation,Diffusion, Utilization,11(1990)4,459-480.[17]Kleinberg J.:Authoritative sources in a hyperlinked environment.In Proc9th ACMSIAMSymposium on Discrete Algorithms,1998,p.668-677./home/kleinber/auth.ps/kleinberg97authoritative.html[18]Wilson,R.J.,Watkins,J.J.:Graphs:An Introductory Approach.New York:John Wileyand Sons,1990.[19]Pajek’s datasets–citation networks:http://vlado.fmf.uni-lj.si/pub/networks/data/cite/[20]KDD Cup2003:/projects/kddcup/index.html/[21]Hall,B.H.,Jaffe,A.B.and Tratjenberg M.:The NBER U.S.Patent Citations Data File.NBER Working Paper8498(2001)./patents/[22]The United States Patent and Trademark Office./netahtml/srchnum.htm[23]Bibliography on the Self-Organizing Map(SOM)and Learning Vector Quantization(LVQ)a.de/bibliography/Neural/SOM.LVQ.html[24]Neural Networks Research Centre:Bibliography of SOM papers.http://www.cis.hut.fi/research/refs/。
欧拉定理的英文

欧拉定理的英文Euler's TheoremLeonhard Euler, a renowned Swiss mathematician, is widely regarded as one of the most influential figures in the history of mathematics. His contributions to the field are vast and diverse, spanning numerous areas of study, including number theory, calculus, and graph theory. One of Euler's most significant achievements is the formulation of Euler's theorem, a fundamental principle that has had a profound impact on our understanding of the properties of numbers and their relationships.Euler's theorem, also known as Fermat's little theorem, states that for any positive integer a and any prime number p, if a and p are relatively prime (meaning they have no common factors other than 1), then a raised to the power of (p-1) is congruent to 1 modulo p. In other words, the remainder when a raised to the power of (p-1) is divided by p is always 1.Mathematically, Euler's theorem can be expressed as:a^(p-1) ≡ 1 (mod p)where a is any positive integer, p is a prime number, and the symbol ≡ means "is congruent to."The proof of Euler's theorem is based on the concept of modular arithmetic, which deals with the properties of numbers when they are divided by a fixed number, called the modulus. In modular arithmetic, two numbers are considered congruent if they have the same remainder when divided by the modulus.To prove Euler's theorem, we can use the concept of the Euler totient function, denoted as φ(n), which represents the number of positive integers less than or equal to n that are relatively prime to n. Euler showed that for any positive integer n, the following property holds:a^(φ(n)) ≡ 1 (mod n)where a is any positive integer that is relatively prime to n.When n is a prime number p, the Euler totient function simplifies to φ(p) = p-1, as all the positive integers less than p are relatively prime to p. Substituting this into the above equation, we get Euler's theorem:a^(p-1) ≡ 1 (mod p)Euler's theorem has numerous applications in various areas of mathematics and computer science. In number theory, it is used to study the properties of modular arithmetic and to develop algorithms for cryptography. In computer science, it is employed in the design of efficient algorithms for tasks such as primality testing and modular exponentiation.One of the most notable applications of Euler's theorem is in the field of public-key cryptography, particularly in the widely used RSA (Rivest-Shamir-Adleman) algorithm. The RSA algorithm relies on the fact that for any positive integers a and n that are relatively prime, the following property holds:a^(φ(n)) ≡ 1 (mod n)This property is a direct consequence of Euler's theorem and is crucial for the security of the RSA algorithm.In addition to its practical applications, Euler's theorem is also of great theoretical importance. It provides insights into the structure of finite groups and the properties of modular arithmetic, which are fundamental concepts in abstract algebra and number theory.Euler's theorem is a testament to the elegance and power ofmathematical reasoning. Its simplicity and far-reaching implications have made it a cornerstone of modern mathematics, and its influence continues to be felt in various fields of study. As we delve deeper into the realm of mathematics, Euler's theorem remains a shining example of the beauty and depth of the subject, inspiring generations of mathematicians to push the boundaries of our understanding.。
关于算法利与弊的作文800字

关于算法利与弊的作文800字英文回答:Advantages and Disadvantages of Algorithms.Advantages:Efficiency: Algorithms provide a structured andefficient way to solve complex problems by reducing timeand effort. They optimize performance by automating tasks and reducing the need for manual intervention.Accuracy: Algorithms follow predefined rules and logic, eliminating human error and ensuring consistent results. They provide reliable and predictable outcomes.Scalability: Algorithms can handle large datasets effectively and adapt to changing requirements. As data grows or requirements evolve, algorithms can be scaled to meet the increasing demands.Objectivity: Algorithms are unbiased and make decisions based solely on the input data, eliminating personal biases and subjectivity. This ensures fair and unbiased outcomes.Automation: Algorithms automate repetitive tasks, freeing up human resources for more complex and creative endeavors. They enhance productivity and efficiency by automating processes.Disadvantages:Limited Creativity: Algorithms are bound by their predefined rules and cannot generate original ideas or solve problems that require human creativity. They are best suited for tasks that follow a clear set of rules.Black Box: Some algorithms can be complex and opaque, making it difficult to understand how they reach their conclusions. This lack of transparency can hinder decision-making and accountability.Bias: Algorithms can inherit biases from the data they are trained on, leading to unfair or discriminatory outcomes. It is essential to carefully evaluate data and mitigate potential biases to ensure fairness.Computational Cost: Some algorithms requiresignificant computational resources and time to process large datasets. This can be a limitation for applications with real-time or low-latency constraints.Ethical Concerns: The use of algorithms in decision-making raises ethical concerns about privacy, transparency, and fairness. It is important to address ethical implications and establish guidelines for responsible algorithm development and deployment.中文回答:算法的利与弊。
文献综述和外文翻译的撰写要求

Keeping organizational information in a file-processing system has a number of major disadvantages.
?Data redundancy and inconsistency. Since the files and application programs are created by different programmers over a long period, the various files are likely to have different formats and the programs may be written in several programming languages. Moreover, the same information may be duplicated in several places (files). For example, the address and telephone number of a particular customer may appear in file that consists of savings-account records and in a file that consists of checking-account records. This redundancy leads to higher storage and access cost. In addition, it may lead to data inconsistency; that is, the various copies of the same data may no longer agree. For example, a changed coustomer address may be reflected in savings-account records but not elsewhere in the system.
写2024年新闻的英语作文好

写2024年新闻的英语作文好Headline: Technological Advancements Shape the Future of Human Endeavors.Date: January 1, 2024。
Article:As the world ushers in the Year of the Dragon, an era of transformative technological advancements lies ahead, poised to reshape the lives of humans across the globe. From groundbreaking scientific breakthroughs to futuristic innovations, 2024 promises to be a pivotal year in the realm of human ingenuity.Artificial Intelligence: The Arrival of Cognitive Assistants.Artificial intelligence (AI) continues its relentless march forward, offering unprecedented capabilities thatblur the lines between human and machine. In 2024, AI assistants become ubiquitous, empowering individuals with hyper-personalized experiences. These intelligent companions enhance productivity, automate tasks, and provide real-time insights, becoming indispensable tools in all aspects of life.Robotics: The Rise of Collaborative Automation.Robotics takes center stage in 2024, with collaborative robots (cobots) seamlessly integrating into workplaces. Unlike their industrial predecessors, cobots are designed to interact safely with human counterparts, enhancing productivity while freeing up workers for higher-value tasks. This harmonious partnership between humans and machines promises to revolutionize industries from manufacturing to healthcare.Virtual and Augmented Reality: Immersive Experiences.Virtual and augmented reality (VR and AR) technologies reach new heights of immersion in 2024. VR headsetstransport users into virtual worlds, offering unparalleled entertainment experiences. AR overlays digital information onto the real world, enhancing everyday activities withreal-time data and interactive elements. From virtual tourism to surgical simulations, these technologies empower humans to explore new possibilities and problem-solve in innovative ways.Quantum Computing: Unlocking Computational Frontiers.Quantum computing, a revolutionary approach to computing, enters the mainstream in 2024. Quantum computers harness the principles of quantum mechanics to perform calculations exponentially faster than traditional computers. This breakthrough unlocks new possibilities in fields such as drug discovery, materials science, and financial modeling, promising to accelerate innovation and scientific advancement.Renewable Energy: Accelerating the Transition.The global transition to renewable energy gainsmomentum in 2024. Solar, wind, and geothermal technologies become increasingly cost-effective, leading to widespread adoption in both developed and developing countries. The integration of smart grids and energy storage systems enables the efficient distribution and utilization of renewable energy sources, reducing dependence on fossil fuels and paving the way for a sustainable future.Biotechnology: Advancing Health and Longevity.Biotechnology makes significant strides in 2024, offering transformative advancements in healthcare. Gene editing techniques, such as CRISPR-Cas9, enable the precise manipulation of DNA, opening new avenues for treating genetic diseases. Personalized medicine tailored to individual genetic profiles empowers doctors to tailor treatments with unprecedented effectiveness.Space Exploration: Reaching for the Stars.Humanity's quest for the stars continues in 2024. Private space companies launch ambitious missions to theMoon and Mars, paving the way for future human settlements beyond Earth. Advanced propulsion systems and reusable spacecraft enable more efficient and cost-effective exploration, fostering new scientific discoveries and inspiring the next generation of space pioneers.Transportation: A Revolution in Mobility.The realm of transportation experiences a paradigmshift in 2024. Electric vehicles gain widespread acceptance, offering zero-emission solutions and reducing reliance on fossil fuels. Autonomous vehicles, equipped with advanced sensors and AI algorithms, hit the roads, enhancing safety and convenience. Air taxis and eVTOLs (electric vertical take-off and landing aircraft) take flight, revolutionizing urban transportation and enabling faster, more efficient travel.Conclusion:As we embark on 2024, the future holds boundless possibilities shaped by technological advancements.Artificial intelligence, robotics, virtual reality, quantum computing, renewable energy, biotechnology, space exploration, and transportation are just a glimpse of the transformative innovations that lie ahead.These advancements have the potential to empower humanity with unprecedented capabilities, enhance our lives, and address some of the world's most pressing challenges.As we navigate this rapidly evolving technological landscape, it is crucial to embrace innovation while ensuring ethical and responsible development for thebenefit of all.。
技术原理英文表达

技术原理英文表达Technology Principles: Exploring the Fundamental ConceptsTechnology has become an integral part of our daily lives, shaping the way we communicate, work, and interact with the world around us. At the core of this technological revolution are the underlying principles that govern the development and application of various technological systems. These principles, often rooted in scientific and mathematical foundations, are the building blocks that enable the creation of innovative solutions to complex problems.One of the fundamental principles in technology is the concept of systems. A system can be defined as a set of interconnected components that work together to achieve a specific purpose. This principle is applicable across a wide range of technological domains, from simple mechanical devices to complex computer networks. Understanding the structure and behavior of these systems is crucial for designing, implementing, and optimizing technological solutions.Another key principle is the concept of information and data. Technology is often used to collect, process, and transmit information, and the way in which this information is managed canhave a significant impact on the effectiveness and efficiency of a technological system. Principles such as data representation, encoding, and compression are essential for ensuring the accurate and efficient transfer of information.The principle of energy and power is also fundamental to technology. Many technological systems rely on the generation, transmission, and utilization of energy, and the understanding of principles such as thermodynamics, electricity, and magnetism is crucial for the development of energy-efficient technologies.Additionally, the principle of materials and structures is essential in the design and construction of technological devices and systems. The properties of materials, such as strength, flexibility, and thermal conductivity, play a crucial role in determining the performance and reliability of technological solutions.The principle of algorithms and programming is another key aspect of technology. The development of software and the design of efficient algorithms are essential for the creation of intelligent and adaptable technological systems. This principle encompasses concepts such as data structures, logic, and computational complexity.Furthermore, the principle of communication and networking iscentral to the interconnectedness of modern technology. The ability to transmit and receive information across various platforms and devices is crucial for the development of technologies that enable seamless collaboration and information sharing.Finally, the principle of user interaction and design is essential for the development of user-friendly and intuitive technological solutions. The way in which users interact with technology can have a significant impact on its adoption and effectiveness, and principles such as human-computer interaction and user-centered design are crucial for creating technologies that meet the needs and expectations of end-users.In conclusion, the fundamental principles that underlie the development and application of technology are diverse and interdependent. By understanding and applying these principles, technologists and engineers can create innovative solutions that address the challenges of the modern world and improve the quality of life for individuals and communities around the globe.。
空间维度英语

空间维度英语Space DimensionsThe concept of space dimensions has fascinated humanity for centuries. From the ancient philosophers to modern-day physicists, the exploration of the nature of space and its underlying structure has been a driving force behind scientific and philosophical inquiry. In this essay, we will delve into the intriguing world of space dimensions, examining their significance, the theories that govern them, and the implications they hold for our understanding of the universe.At the most fundamental level, space is often described as a three-dimensional Euclidean construct, where objects can be positioned and measured along the x, y, and z axes. This classical view of space, rooted in the works of mathematicians and physicists like Euclid and Newton, has served as the foundation for our understanding of the physical world for centuries. However, as our scientific knowledge has advanced, the concept of space has become increasingly complex and multifaceted.One of the most significant developments in the understanding ofspace dimensions came with the advent of Einstein's theory of general relativity. This groundbreaking theory challenged the Newtonian view of space and time as separate entities, proposing instead that they are intrinsically linked, forming a four-dimensional space-time continuum. According to general relativity, the presence of matter and energy in the universe warps and distorts the fabric of this space-time, giving rise to the phenomenon of gravity.This four-dimensional space-time model has had profound implications for our understanding of the universe. It has allowed us to explain and predict a wide range of cosmic phenomena, from the behavior of black holes to the expansion of the universe. Moreover, it has opened up the possibility of exploring additional spatial dimensions beyond the three we directly perceive.String theory, a leading candidate for a unified theory of all fundamental forces in nature, posits the existence of up to 11 spatial dimensions. These extra dimensions, which are hypothesized to be curled up and hidden from our direct observation, are believed to play a crucial role in the underlying structure of the universe. By incorporating these additional dimensions, string theory aims to reconcile the seemingly incompatible theories of quantum mechanics and general relativity, providing a more comprehensive understanding of the fundamental nature of reality.The concept of higher-dimensional spaces has also found applications in fields such as mathematics and computer science. In mathematics, the study of n-dimensional spaces, where n can be any positive integer, has led to the development of powerful tools and insights that have advanced our understanding of geometry, topology, and abstract algebra. In computer science, the notion of multidimensional data structures and algorithms has enabled the efficient processing and visualization of complex, high-dimensional datasets.Furthermore, the exploration of space dimensions has also sparked the imagination of science fiction writers and futurists. The idea of beings or objects existing in dimensions beyond our own has been a recurring theme in literature and popular culture, often raising intriguing questions about the nature of reality and the limits of human perception.However, the study of space dimensions is not without its challenges. The experimental verification of the existence of additional spatial dimensions, as proposed by string theory, remains an ongoing challenge for physicists. The difficulty lies in the fact that these hypothetical dimensions are believed to be microscopic in scale, making them extremely difficult to detect and observe directly.Despite these challenges, the pursuit of understanding spacedimensions continues to be a vital and captivating area of scientific inquiry. As our technological capabilities advance and our theoretical models become more sophisticated, we may uncover new insights into the fundamental structure of the universe and the nature of reality itself. The exploration of space dimensions promises to push the boundaries of our knowledge and inspire us to delve deeper into the mysteries of the cosmos.In conclusion, the concept of space dimensions is a rich and multifaceted topic that has captivated the minds of thinkers and researchers throughout history. From the classical Newtonian view of three-dimensional space to the modern theories of higher-dimensional spaces, the study of space dimensions has profoundly shaped our understanding of the physical world and the universe at large. As we continue to explore and unravel the complexities of space, we may unlock new realms of discovery and unlock the secrets of the cosmos.。
英语作文我最喜欢数学

In the vast and intricate tapestry of knowledge, there exists a discipline that has captivated my intellectual curiosity and ignited an insatiable thirst for understanding: mathematics. It is not merely a subject, but rather a language, a tool, an art form, and a philosophy rolled into one, offering an infinite universe of possibilities to explore and unravel. This essay is an ode to my favorite academic pursuit, delving into the multifaceted allure of mathematics from various perspectives, elucidating why it occupies a hallowed place in my heart and mind.First and foremost, mathematics is a language of unparalleled precision and elegance. Unlike natural languages that often leave room for ambiguity and interpretation, mathematical notation and symbols convey ideas with absolute clarity, transcending linguistic barriers and cultural differences. It is a universal language that allows thinkers across the globe to communicate complex concepts unambiguously, fostering collaboration and advancing human understanding. The beauty of this language lies in its concise yet powerful expressions, such as Euler's identity (e^(iπ) + 1 = 0), which elegantly encapsulates fundamental constants, mathematical operations, and the mysterious interplay between real and imaginary numbers. This precision and conciseness make mathematics a sublime form of communication, capable of expressing profound truths about the world in a manner that is both aesthetically pleasing and intellectually stimulating.Moreover, mathematics is a formidable problem-solving tool, empowering us to navigate and make sense of the complexities inherent in our world. From predicting the trajectory of celestial bodies to designing efficient algorithms for data analysis, mathematics provides a systematic framework for modeling real-world phenomena and solving practical challenges. Its utility spans diverse fields, including physics, engineering, economics, biology, computer science, and more, serving as the bedrock upon which countless scientific advancements have been built. The power of mathematical reasoning lies in its ability to abstract away unnecessary details, distill complex systems into their essential components, and employ logical deductions to arrive at valid conclusions. This analytical prowess grants us unprecedented insight into the workings of the universe, enabling us to harness its laws for the betterment of society.Furthermore, mathematics is an art form in its own right, characterized by creativity, ingenuity, and a profound aesthetic appeal. Just as a painter creates visual masterpieces on canvas, mathematicians craft elegant proofs, elegant theorems, and exquisite geometric constructions. The process of mathematical discovery involves a blend of intuition, imagination, and perseverance, much like the creative endeavors of poets, musicians, or architects. The beauty of mathematics lies not only in its end products – the elegant equations, symmetrical patterns, or fractal geometries – but also in the intellectual journey leading to their conception. This artistic dimension of mathematics imbues it with a unique charm, inviting us to appreciate its aesthetic qualities while simultaneously engaging our analytical faculties.Additionally, mathematics embodies a philosophical dimension that prompts deep contemplation about the nature of reality, truth, and knowledge. It confronts us with timeless questions such as: What is infinity? Does mathematical truth exist independently of human thought? How do we know that our mathematical models accurately reflect the world? Engaging with these inquiries pushes the boundaries of our understanding, fostering intellectual humility and a sense of wonder about the mysteries that lie beyond our grasp. Moreover, the axiomatic foundations of mathematics – the set of assumptions from which all subsequent knowledge is derived – mirror the quest for epistemological certainty that lies at the core of philosophical inquiry. Thus, mathematics not only provides tools for understanding the world but also invites us to ponder the very nature of understanding itself.Lastly, the study of mathematics cultivates valuable cognitive skills that extend far beyond the discipline itself. It sharpens logical reasoning, critical thinking, and problem-solving abilities, equipping learners with a mental toolkit that serves them well in any intellectual pursuit or professional endeavor. Furthermore, the rigorous and structured nature of mathematical thinking fosters discipline, perseverance, and attention to detail, traits that are indispensable in today's fast-paced and demanding society. The intellectual rigor and mental agility honed through the study of mathematics instill in us a mindset that embraces complexity, seeks clarity, and thrives on continuous learning and self-improvement.In conclusion, my love for mathematics stems from its multifaceted allure as a precise language, a powerful problem-solving tool, an artistic endeavor, a philosophical pursuit, and a catalyst for cognitive development. It is a discipline that transcends mere academic study, offering a window into the elegant order underlying the cosmos, a means to unlock the secrets of the natural world, and a path to personal and intellectual growth. As I continue to delve deeper into this fascinating realm, I am constantly reminded of the words of the great mathematician G.H. Hardy: "A mathematician, like a painter or a poet, is a maker of patterns. If his patterns are more permanent than theirs, it is because they are made with ideas." Indeed, it is the eternal and immutable nature of these patterns, crafted from the purest of ideas, that renders mathematics an inexhaustible source of fascination, inspiration, and joy for me.。
整数分拆的英语

整数分拆的英语Integers are fundamental mathematical concepts that have fascinated mathematicians and scientists for centuries. The study of integer partitions, which involves decomposing an integer into a sum of smaller integers, has been a topic of great interest in the field of combinatorics. In this essay, we will explore the concept of integer partitions and delve into the various techniques and applications associated with this intriguing mathematical phenomenon.The notion of integer partitions can be traced back to the eighteenth century, when the renowned mathematician Leonhard Euler began investigating the properties of integer partitions. An integer partition of a positive integer n is a way of expressing n as a sum of positive integers, where the order of the summands does not matter. For example, the integer 4 can be partitioned in the following ways: 4,3+1, 2+2, 2+1+1, 1+1+1+1.One of the key properties of integer partitions is that the number of distinct partitions of a given integer n, denoted as p(n), follows a pattern that can be described by a mathematical function known as the partition function. This function, which was first studied by Euler, provides a way to calculate the number of partitions of a giveninteger. The partition function is defined recursively, and its evaluation can be quite challenging, especially for large values of n.The study of integer partitions has numerous applications in various fields of mathematics and science. In combinatorics, integer partitions are used to model and analyze a wide range of problems, such as the distribution of electrons in atoms, the arrangement of particles in statistical mechanics, and the design of efficient algorithms for solving optimization problems.In number theory, integer partitions are closely related to the study of modular forms and the theory of partitions. Researchers have explored the connections between integer partitions and other mathematical concepts, such as Dirichlet series, generating functions, and the theory of asymptotic analysis. These connections have led to the development of powerful techniques for studying the properties of integer partitions and their associated functions.Furthermore, the study of integer partitions has implications in the field of computer science, where it is used in the design of efficient algorithms for problems such as knapsack problems, bin packing, and scheduling optimization. The ability to understand and analyze the structure of integer partitions has been instrumental in the development of these algorithms and the optimization of their performance.In addition to the theoretical and practical applications of integer partitions, the study of this topic has also led to the development of various visualization techniques. Researchers have created graphical representations of integer partitions, such as Ferrers diagrams and Young diagrams, which provide a visual aid for understanding the structure and properties of these mathematical objects.In conclusion, the study of integer partitions is a rich and fascinating area of mathematics that has far-reaching applications in various fields. From the historical development of the partition function to the modern applications in computer science and optimization, the exploration of integer partitions has been a driving force in the advancement of mathematical knowledge and the development of practical solutions to complex problems. As the field continues to evolve, researchers and enthusiasts alike will undoubtedly continue to uncover new insights and applications of this captivating mathematical concept.。
Space-efficient

Space-efficient construction variants of dynamicprogrammingHans L.Bodlaender∗Jan Arne Telle†AbstractMany dynamic programming algorithms that solve a decision problem can be modified to algorithms that solve the construction variant of the problemby additional bookkeeping and going backwards through stored answers to sub-problems.It is also well known that for many dynamic programming algorithms,one can save memory space by throwing away tables of information that is nolonger needed,thus reusing the memory.Somewhat surprisingly,the observa-tion that these two modifications cannot be combined is frequently not made.Inthis paper we consider the case of dynamic programming algorithms on graphsof bounded treewidth.We give algorithms to solve the construction variants ofsuch problems that use only twice the amount of memory space of the decisionversions,with only a logarithmic factor increase in running ing theconcept of strong directed treewidth we then discuss how these algorithms canbe applied to dynamic programming in general.Keywords:Algorithms and data structures;dynamic programming;mem-ory use of algorithms;treewidth.1IntroductionDynamic Programming(DP)is one of the most common algorithmic techniques. It is well known that many dynamic programming algorithms that solve a deci-sion problem can be modified to one that solves the construction variant of the problem by additional bookkeeping and going backwards through stored answers to subproblems.It is also well known that for many dynamic programming algorithms, one can save memory space by throwing away tables of information that is no longer needed,thus reusing the memory.Somewhat surprisingly,the observation that these two modifications cannot be combined is frequently not made:when the‘textbook’modification to save memory is made to a dynamic programming algorithm,the in-formation to construct solutions is deleted,and the‘textbook’modification to obtain an algorithm for the construction problem cannot be applied.When the data for an algorithm do notfit into the main memory,but must be written to or obtained from secondary memory(e.g.,a hard disk),then this has a severe impact on the time spent by the algorithm.Modern computers have large amounts of memory.Still,there are cases where the use of memory indeed still is an issue.For instance,if we allow a dynamic programming algorithm to run for several days,then the borderline between instances that can and cannot be handled often is determined by whether the data for the programfit into main memory.This happens for example for algorithms that use dynamic programming on graphs of bounded treewidth.These observations were the starting point for our investigations.In this paper,we view DP as an algorithmic method applicable to a problem whose optimal solution for an input of size n can be found by combining optimal solutions to various subproblems.We associate with such a DP algorithm a directed acyclic graph D that will be central in our discussion.Each relevant subproblem is a node s of D,and represents a storage location for the solution value to this subproblem, which is typically a boolean value for a decision problem or a positive integer for an optimization problem.The solution value v(s)stored at s is computed,as specified by the DP algorithm,by v(s):=f(v(s1),v(s2),...,v(s k)),for some specified function f and subproblems s1,s2,...,s k.If the function f is a simple optimization over values of the k arguments,we have a case of serial DP,with a single optimal subproblem yielding the optimal solution at s.In other cases the function f is a more complicated optimization,such as over sums of certain pairs of argument values,which would give an example of non-serial DP.The digraph D will have a directed edge s i s for each 1≤i≤k representing the fact that the value stored at s i is needed to compute the value stored at s.In a DP algorithm the resulting digraph D should have no directed cycles,i.e.it should be a dag,and it should have only a single sink,representing the full problem instance.In many formulations of DP the sink appears as a last maximization or minimization step over all entries in a certain range.For the optimization(and decision)version of the problem,where we are simply asking for the solution value for the overall problem,we simply return v(t),the value stored in the sink t of D.We define the space usage of this version of DP to be the maximum number of subproblem solution values kept in memory in course of the algorithm.The solution value to a subproblem s i must therefore remain in memory until solutions to all subproblems s with an edge s i s have been computed.To arrive at the optimum space usage for a given DP algorithm on an input giving a dag D we thus define Space opt(D)as the minimization of space usage over all topological sorts of D.Since we throw out the solution to a subproblem from memory as soon as allowed,the maximum number of storage locations,i.e.the space usage,for a particular topological sort v1,v2,...,v m is the maximum over all1≤i≤m of |{v j:j<i∧∃v j v k∈E(D)∧k≥i}|.Several textbooks on algorithms will mention this space-saving technique for a DP optimization problem.We now turn to the construction version of DP,which is the subject of the current paper.In this version we need tofind not only the value of an optimal solution,but also some object that achieves this value.Many textbooks mentioning DP describe2the following scheme for the construction version:first solve the optimization version, and then retrace from the sink of the dag D back through nodes that gave rise to this optimal value.However,we know no examples of algorithms textbooks that both mention the space-saving technique and the scheme for the construction versions, and note that one cannot use both schemes simultaneously.In fact,the scheme for the construction version requires us to store solutions to all subproblems,in case this subproblem is hit by the retracing,thus requiring|V(D)|storage locations which is usually orders of magnitude higher than the Space opt(D)required for the optimization version.Thus,we need a different scheme for saving space when doing construction versions of problems.The only fast space efficient construction versions of a DP application that we have found in the literature are for alignment problems in computational biology.No-tably,a1975CACM-paper by Hirschberg[10]addresses this issue for the problem known as’longest common subsequence’,strongly related to’string alignment’.The construction version is in this case solved with the same asymptotic time and space complexity as the optimization version.This result is based on a property of the problem which says that it can be broken into two parts where one corresponds to viewing the strings in reverse order.By combining the solutions to these two problems onefinds a’mid-way’alignment point,and can subsequently recurse on two sub-problems whose two dags have combined size half of the original dag.This technique has become famous in thefield of computational biology,and mentioned in textbooks,see e.g.[8],but is based on the problem-specific property mentioned above,and cannot be surmised from the dag D.This explains why a discussion of space-efficient construction versions for DP is dif-ficult to carry out in a general setting,precisely because problem-specific properties may be necessary to get the best results.In this paper we primarily discuss two DP case studies in thefield of graph problems:DP on a path decomposition and DP on a tree decomposition.For a graph with small treewidth the DP on its as-sociated tree decomposition will allow the solution of various otherwise intractable graph problems,see e.g.[3,7].Various classes of graphs have small treewidth,for example the control-flow graphs of goto-free C programs have treewidth at most6 [14,6,9].Experiments and applications show that this is also useful in a practical setting.The algorithm of Lauritzen et al.[12]to solve the probabilistic inference problem on probabilistic networks is the most commonly used algorithm for this problem and uses DP on a tree decomposition.Koster et al.[11]used DP on tree decompositions to solve instances of frequency assignment problems,and Alber et al.[2]use such methods for solving the vertex cover problem on planar graphs.We show how to solve the construction variants of these problems while using only a negligible(twice)amount of more memory than for the optimization version,with a logarithmic factor increase in running time.Table1compares our result to the trade-offbetween time and space achievable by the previously best-known results. The result quoted under pre-1998simply stores all tables and retraces an optimal solution,which is in general clearly impractical since each table could be of size3post-1998 Time O(n2) Space p≤2log na,b,c d,b,c e,b,c e,f,ce,f,g c/8e/5g/9Figure 1:Example graph G with tree-decompositionalgorithms rely on the fact that any bag X i is a separator of the graph,but the specific details of these algorithms are not of great importance to the exposition here.We have a path decomposition X 1,X 2,...,X t of an undirected graph G of pathwidth k ,where t is linear in |V (G )|.For simplicity we assume that |X i |=k +1for each 1≤i ≤t ,and that the tables to be filled are T 1[1..p (k )],T 2[1..p (k )],...,T t [1..p (k )].Thus,T i [j ]should store the optimal value to a solution of the problem restricted to the graph induced by nodes X 1∪X 2∪···∪X i ,where the subgraph on nodes X i are restricted to behave in a specified fashion as indicated by the table index j .The size p (k )of the tables depends on the particular problem at hand,but for any problem which in general is NP-hard,it will be exponential in k .In the optimization version of the dynamic programming algorithm we keep only 2tables in memory at any time,starting with tables T 1and T 2,then T 2and T 3,etc.In Figure 2is a very simple example of a weighted graph G on 6nodes and its path decomposition on 5bags with 3nodes in each bag,for which we want to solve the maximum weighted independent set problem:In the 2-dimensional array in Table 2below each column represents a table associated with a bag X i of the path decomposition.In each bag we have ordered the nodes it contains.The leftmost column indicates the 8indices of each table,e.g.index 101represents partial solutions where the first and third,but not the second,node in the bag should belong to the independent set.Thus,the 101row has the entry −∞whenever the first and third node are adjacent,such as for the bag efg ,since an independent set cannot contain two neighboring nodes.Nodes have been ordered so that they maintain the property of being first/second/third in every bag,note that this is always possible for a path decomposition where every bag has the same size,but not always possible for a tree decomposition.We have filled the tables with values as would be done by the optimization version of dynamic programming,storing also for each value the index of the previous column that gave rise to this value.If several such indices give the same value we just picked one arbitrarily.After solving the optimization version (the forward direction),the standard algorithm for the construction variant would then trace these pointers from the optimal entry at index 110in the last table,back to the first,hitting the entries indicated by the stars in those cells,giving the optimal solution {a,d,e,f }with weight 19.Note that the sequence of dependency pointers,p 1,p 2,...,p t (100,5dbc efc 0004/1007/000 0018/0018/001 0107/01014/000 011−∞−∞1007/100*12/100 101−∞13/101 110−∞19/100* 111−∞−∞dbc efc 00003/000 001−∞−∞010−∞10/000 011−∞−∞10038/100 101−∞−∞110−∞15/100 111−∞−∞the same,find a small set of special nodes,such that after splitting the tree at these nodes we are left with small subtrees.A tree decomposition of a graph G=(V,E)is a pair(T,X)with T=(I,F)a tree, and X={X i|i∈I}a family of subsets of V,such that for all nodes i1,i2,i3∈I,if i2is on the path from i1to i3in T,then X i1∩X i3⊆X i2;for all{v,w}∈E,there is an i∈I with v,w∈X i,and i∈I X i=V.We call the sets X i the bags.The width of(T,X)is max i∈I|X i|−1,and the treewidth of a graph G is the minimum width of a tree decomposition of G.Like pathwidth,treewidth has nice algorithmic properties,and allows many problems that are hard on general graphs to be solved in linear or polynomial time when restricted to graphs of bounded treewidth;see e.g.,[3,7,11].These algorithms are again usually of dynamic programming type and have the following form.A node of T is chosen as root.For each node i,we compute a table.These tables are computed in bottom up order:to compute a table,we use the information of the tables of the children,plus some‘local information’about the subgraph induced by bag X i.The decision problem can be solved once the table of the root is known.For the construction problem,a corresponding solution can be constructed by going downwards from root to leaves using the information in the tables.We consider now one illustrative example.Assume we have a tree decomposition(T,X)of a graph G of treewidth k.For an optimization version of DP,for example answering the question’What is the size of the largest independent set in G?’,the information contained in the table at a child node of T is superfluous once the table of its parent has been updated.Since the size of tables is exponential in k,it is in practice very important to carefully re-utilize these memory locations in order to minimize time-consuming I/O to external memory.A simple linear-time algorithm will in a pre-processing stepfind a bottom-up traversal of T that minimizes the number of tables stored at any time during the dynamic programming.This number p lies between the pathwidth of T and twice the pathwidth of T plus one[4].The construction variant of DP on tree decompositions,of the form’Find a largest independent set in G’,can be solved in the standard manner,byfirst performing the’forward’direction thatfinds an optimal value,and then tracing an optimal entry in thefinal table(the root)back through those entries in earlier tables that gave rise to it(down to the leaves).However,this requires all tables to be stored in memory,and is clearly impractical.Our current aim is to solve the construction variant as fast as possible under the practically oriented constraint that we store only an asymptotically optimal number of tables,i.e.linear in the pathwidth of T. We use the following definition to split a tree into several subtrees for the recursion.Definition1Let(T,r)be a tree T rooted at node r and let x be a node of T. Splitting at x creates two rooted subtrees(T1,x),(T2,r)such that T1∪T2=T and T1∩T2=x,i.e.with T1the subtree of T rooted at x and T2the subtree of T rooted at r having x as a leaf.When splitting at several nodes,simply split one node x at a time,in the subtree containing x.8Before describing our method for a tree T,let us remark that if applied to a path as in the previous section,it wouldfirst consider the halfway node x andfind an optimum entry in the table at x by recording pointers to that table,before recursing on the two paths resulting from splitting at x.For a tree T we need to split at several nodes.Lemma1Let(T,r)be a rooted tree on n nodes with each node having≤c children. For any s≤cn/2we have2s≤cn/scn/2each of the following problems can be solved on G in O(n log s n)time using O(s+w)additional memory:find a(node or edge)set S such that Q(S)holds in G;find a set S such that|S|is minimum(maximum)over all sets such that Q(S)holds in G.9Figure2:To the left a tree having n=20with s=4special nodes circled and arrows indicating stored pointers to tables after thefirst stage,used for retracing an optimal solution.To the right the5subtrees in the recursion after splitting,with triangles denoting tables having pre-initialized optimal entries.Proof.By the results of[3]the optimization version of any such problem can be solved in O(n)time by a table-based DP method,and[4]gives a bottom-up traversal of T for such a DP method that stores at most2(w+1)tables in memory.We use this traversal during the space-efficient construction version of DP described in this section,choosing s special nodes at each subtree.With s special nodes we need additional memory equivalent to at most s tables,to store the pointers to the tables at the special nodes.Note that in the recursion we work on each subtree separately, re-using memory.Thus we store at most s+2(w+1)tables,each of size depending only on the constant k,for O(s+w)additional memory total.Assuming the tree has n nodes,then by Lemma1each subtree in the recursion will have size at most cn/s.Thus we have at most log s n levels of recursion,for c constant.At each level of recursion the number of subtrees increase by at most a multiplicative factor s+1, and the sum of nodes in all subtrees at one level by an additive factor bounded by the number of subtrees.Thus we have at most O(n)subtrees and O(n)nodes total at any level.The time for each recursive level is O(n)and the total running time is therefore O(n log s n).4Generalizing from the Case StudiesLet us now look at the general case of DP.Described intuitively,the construction version of DP is usually solved byfirst solving the optimization version by moving in a forward direction in the associated DP dag D,and then retracing from the sink of the dag D back through nodes that gave rise to the optimal value.For the case of serial DP this retracing chooses a single optimal subproblem in each step,and the nodes in the’optimal subgraph’form a path.In the path decomposition example,there would be a node of the dag D for each entry T i[j]of a table,with an arc from T i[j]to T i+1[j ]for some j >j if the entry at j was computed by an optimization over a range of entries that included j.In addition we would have a sink node t with incoming arcs from each node associated with the last table.We thus have a case of serial DP and the optimal subgraph that we retrace from the sink is a path.The dag D is itself not a path,but we still managed to break D into two parts by use of the path decomposition which imposes a path structure on D.Our technique for achieving space usage of2tables at the expense of an extra logarithmic factor in the runtime relied heavily on this path structure.In the tree decomposition example,we had a case of non-serial DP,where the nodes hit in the’optimal subgraph’during retracing will form a tree.Here,we managed to break D into parts by help of the tree-structure imposed on it by a tree decomposition,and our space-efficient technique relied on this tree-structure. What can we learn in general from the two case studies?The core of the general technique is tofind a small and good separator of the dag D,and break the problem into the parts that result from splitting at the separator.The path decomposition (and tree decomposition)(T,X)of G was computed from the graph G,and the resulting DP dag D(T,X)was then defined,based on the problem at hand and on (T,X).The clue to our space-saving techniques was that D(T,X)inherited the path (or tree)structure.In the general DP case we are handed the dag D without recourse to a path or tree decomposition.How then to apply the same technique of imposing a path(or tree)structure on the dag D?The right theoretical tool here is the concept of strong directed treewidth.Strong treewidth,as defined by Seese in[13],is related to a strong tree decomposition. These differ from a tree decomposition in that each node appears in exactly one bag(the bags are thus a partitioning of the graph nodes),and edges of the graph are now allowed to go between nodes in adjacent bags,and not necessarily in the same bag.Since our dag is directed we do not allow the bag containing t to be the child of the bag containing s if we have an edge from node s to t,thus no edges point downwards.As usual,the goal is to minimize the size of the largest bag.With this definition,the tree structure naturally induced by T on the dag D(T,X)is a strong tree-decomposition of D(T,X).Thus,to generalize our technique we could use a good strong directed tree-decomposition of the dag D.However,as the dag D is usually too large to be kept in memory,and no polynomial time algorithm is11known for computing an optimal strong directed tree-decomposition of a digraph (we conjecture this is NP-hard),this is only of theoretical interest.The practical approach tofinding fast construction variants must instead rely on problem-specific properties.Here it is helpful to note that the dag D for a DP algo-rithm is not some arbitrary dag,but arises from some fairly clear structural aspects of the problem at hand,by defining the value of an optimal solution recursively in terms of the optimal solutions to subproblems.This(simple)recursive definition will also define the structure of the dag D,and a starting point is to look for’sep-arator theorems’like our splitting Lemma1for graphs with this structure.Such separator theorems are well-known for various classes of graphs,like planar graphs, and in particular for most graph classes with a recursive structural definition.On a case-by-case basis one can then,depending on the separator theorems available for the particular dag,develop fast and space-efficient construction algorithms similar to the ones given here.Acknowledgements.Thanks to Fedor Fomin for fruitful discussions on this topic. References[1]J.Alber,H.L.Bodlaender,H.Fernau,T.Kloks,R.Niedermeier:Fixed Param-eter Algorithms for Dominating Set and related problems on Planar Graphs.Algorithmica Vol.33,2002,461–493.[2]J.Alber,F.Dorn,and R.Niedermeier.Experimental evaluation of a treedecomposition based algorithm for vertex cover on planar graphs.To appear in Discrete Applied Mathematics,2004.[3]S.Arnborg,gergren,and D.Seese.Easy problems for tree-decomposablegraphs.J.Algorithms,12,308–340(1991).[4]B.Aspvall,A.Proskurowski,J.A.Telle,Memory requirements for table compu-tations in partial k-tree algorithms,Algorithmica,Special issue on Treewidth, Graph Minors and Algorithms,H.Bodlaender eds.,Vol.27,Number3,2000, 382–394.[5]H.L.Bodlaender.A linear time algorithm forfinding tree-decompositions ofsmall treewidth.SIAM put.,25,1305–1317(1996).[6]H.Bodlaender,J.Gustedt,J.A.Telle,Linear-time register allocation for afixed number of registers,Proceedings SODA’98,574–583,San Fransisco,USA.[7]H.L.Bodlaender,Treewidth:Algorithmic Techniques and Results.ProceedingsMFCS’97,LNCS1295:29–36.12[8]D.Gusfield,Algorithms on strings,trees,and sequences,Cambridge UniversityPress(1997).[9]J.Gustedt,O.Mæhle,J.A.Telle,The Treewidth of Java Programs,ProceedingsALENEX’02—4th Workshop on Algorithm Engineering and Experiments,San Francisco,January4-5,2002,LNCS2409:86–97.[10]D.S.Hirschberg,A linear space algorithm for computing longest common sub-sequences,put.Mach.,18,341–343(1975).[11]A.M.C.A.Koster,S.P.M.van Hoesel,and A.W.J.Kolen.Solving partialconstraint satisfaction problems with tree works,40,170–180(2002).[12]uritzen,D.J.Spiegelhalter,Local computations with probabilities ongraphical structures and their application to expert systems,The Journal of The Royal Statistical Society.Series B(Methodological).50:157-224,1988. [13]D.Seese.Tree-partite graphs and the complexity of algorithms.In L.Budach,editor,Proc.1985Int.Conf.on Fundamentals of Computation Theory,Lecture Notes in Computer Science199,pages412–421,Berlin,1985.Springer Verlag.[14]M.Thorup,Structured Programs have Small Tree-Width and Good RegisterAllocation,Information and Computation142,159–181,1998.13。
Computer-programming

Computer programmingComputer programming (often shortened to programming or coding) is the process of designing. writing, and debugging the source code of computer programs. This source code is written in a programming language。
The purpose of programming is to create a program that exhibits a certain desired behavior. The process of writing source code often requires expertise in many different subjects。
including knowledge of the application domain, specialized algorithms and formal logic。
计算机编程(通常缩短编程或编码)设计的过程。
编写和调试计算机程序的源代码。
这个源代码是用编程语言编写的。
编程的目的是创建一个程序,展示一定的预期行为.编写源代码的过程通常需要专业知识在很多不同的科目。
包括应用程序域的知识,专门的算法和形式逻辑。
Within software engineering。
programming (the implementation) is regarded as one phase in a software development process. Whatever the approach to software development maybe, the final program must satisfy some fundamental properties。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Space Efficient Algorithms for theBurrows-Wheeler BacktransformationUlrich Lauther Tam´a s LukovszkiSiemens AG,Corporate Technology81730Munich,Germany{uther,Tamas.Lukovszki}@Abstract The Burrows-Wheeler transformation is used for effective datacompression,e.g.,in the well known program pression and de-compression are done in a block-wise fashion;larger blocks usually resultin better compression rates.With the currently used algorithms for de-compression,4n bytes of auxiliary memory for processing a block of nbytes are needed,0<n<232.This may pose a problem in embed-ded systems(e.g.,mobile phones),where RAM is a scarce resource.Inthis paper we present algorithms that reduce the memory need withoutsacrificing speed too much.The main results are:Assuming an input string of n characters,0<n<232,the reverse Burrows-Wheeler transformation can be done with1.625n bytes of auxiliary memory and O(n)runtime,using just a fewoperations per input character.Alternatively,we can use n/t bytes and256t n operations.The theoretical results are backed up by experimentaldata showing the space-time tradeoff.1IntroductionThe Burrows-Wheeler transformation(BWT)[6]is at the heart of modern,very effective data compression algorithms and programs,e.g.,bzip2[13].BWT-based compressors usually work in a block-wise manner,i.e.,the input is divided into blocks and compressed block by rger block sizes tend to result in better compression results,thus bzip2uses by default a block size of900,000bytes and in its low memory mode still100,000bytes.The standard algorithm for decom-pression(reverse BWT)needs auxiliary memory of4bytes per input character, assuming4-byte computer words and thus n<232.This may pose a problem in embedded systems(say,a mobile phone receiving a software patch over the air interface)where RAM is a scarce resource.In such a scenario,space requirements for compression(8n bytes when a suffix array[10]is used to calculate the for-ward BWT)is not an issue,as compression is done on a fullfledged host.In the target system,however,cutting down memory requirements may be essential.1.1The BWT BacktransformationWe will not go into details of the BW-transformation here,as it has been de-scribed in a number of papers[2,4,6,7,8,11]and tutorials[1,12]nor do we give aproof of the reverse BWT algorithm.Instead,we give the bare essentials needed to understand the problem we solve in the following sections.The BWT(con-ceptually)builds a matrix whose rows contain n copies of the n character input string,row i rotated i steps.The n strings are then sorted lexicographically and the last column is saved as the result,together with the”primary index”,i.e., the index of the row that contains-after sorting-the original string.Thefirst column of the sorted matrix is also needed for the backtransformation,but it needs not to be saved,as it can be reconstructed by sorting the elements of the last column.(Actually,as we will see,thefirst column is also needed only conceptually.)Figure1shows thefirst andlast columns resulting from theinput string”CARINA”.Thearrow indicates the primary in-dex.Note that we have num-bered the occurrences of each character in both columns,e.g., row2contains the occurrence0 of character”A”in L,row5con-tains occurrence1.We call these numbers the rank of the charac-ter within column L.F LA N Abase: 0001A12C03I04N0R50CA0R0I0A1C: 2I: 3N: 4R: 5rankFigure1.First(F)and last(L)column for the input string”CARINA”.To reconstruct the input string,we start at the primary index in L and output the corresponding character,”A”,whose rank is0.We look for A0in column F,find it at position0and output”N”.Proceeding in the same way, we get”I”,”R”,”A”,and eventually”C”,i.e.,the input string in reverse order. The position in F for a character/rank pair can easily be found if we store for each character of the alphabet the position of itsfirst occurrence in F;these values are called base in Figure1.This gives us a simple algorithm when the vectors rank and base are available: int h=primary_index;for(int i=0;i<n;i++){char c=L[h];output(c);h=base[c]+rank[h];}The base-vector and rank can easily be calculated with one pass over L and another pass over all characters of the alphabet.(We assume an alphabet of256 symbols throughout this paper.)for(int i=0;i<256;i++)base[i]=0;for(int i=0;i<n;i++){char c=L[i];rank[i]=base[c];base[c]++;}int total=0;for(int i=0;i<256;i++){int h=base[i];base[i]=total;total+=h;}These algorithms need O(n)space(n words for the rank-vector)and O(n) time.Alternatively,we could do without precalculation of rank-values and cal-culate rank[h]whenever we need it,by scanning L and counting occurrences of L[h].This would give us O(1)space and O(n2)time.The question,now,is:is there a data structure that needs significantly less than n words without increasing run time excessively?In this paper we present efficient data structures and algorithms solving following problems:Rank searching:The input must be preprocessed into a data structure,such that for a given index i,it supports a query for rank(i).This query is referred to as rank-query.Rank-position searching:The input must be preprocessed into a data struc-ture,such that for a given character c and rank r,it supports a query for index i,such that rank(i)=r.This query is referred to as rank-position-query.(This allows traversing L and F in the direction opposite to that discussed so far, producing the input string in forward order).1.2Computation ModelAs computation model we use a random access machine(RAM)(see e.g.,in [3]).The RAM allows indirect addressing,i.e.,accessing the value at a relative address,given by an integer number,in constant time.In this model it is also assumed that the length of the input n can be stored in a computer word. Additionally,we assume that the size|A|of the alphabet A is a constant,and particularly,|A|−1can be stored in a byte.Furthermore,we assume that a bit shift operation in a computer word,word-wise and and or operations,converting a bit string stored in a computer word into an integer number and vice-versa and algebraic operations on integer numbers(’+’,’-’,’*’,’/’,’mod’,where’/’denotes the integer division with remainder)are possible in constant time.1.3Previous ResultsIn[14]Seward describes a slightly different method for the reverse BWT by handling the so-called transformation vector in a more explicit way.He presents several algorithms and experimental results for the reverse BWT and answering rank-queries(more precisely,queries”how many symbols x occur in column L up to position i?”,without the requirement L[i]=x).A rigorous analysis of the algorithms is omitted in[14].The algorithms described in[14],basis and bw94need5n bytes of memory storage and support a constant query time;algoritm MergedTL needs4n bytes if n is limited to224and supports a constant query time.The algorithm indexF needs2.5n bytes if n<220and O(log|A|)query time.The algorithms tree and treeopt build256trees(one for each symbol)on sections of the vector L.They need2n and1.5n bytes,respectively,if n<220and support O(log(n/∆)+c x∆)query time,where∆is a given parameter depending on the allowed storage and c x is a relatively big multiplicator which can depend on the queried symbol x.1.4Our ContributionsWe present a data structure which supports answering a rank-query Q(i)inO(1)time using n(ℓ−12ℓ)bytes,where w denotes the length of a computerword in bytes,and|A|is the size of the alphabet.If|A|≤256and w=4(32 bit words),by settingℓ∈{12,13},we obtain a data structure of1316n or1.5625bytes.Thus,the spacerequirement is strictly less than that of the trivial data structure,which stores the rank for each position as an integer in a computer word and that of the methods in[14]with constant query time.The preprocessing needs O(n)time and O(|A|)working storage.We also present data structures of n bytes,where we allow at most L=29 sequential accesses to a data block of L bytes.Because of caching and hardware prefetching mechanism of todays processors,with this data structure we obtain a reasonable query time.Furthermore,we present a data structure,which supports answering a rank-query Q(i)in O(t)time using t random accesses and c·t sequential accesses to the memory storage,where c is a constant,which can be chosen,such that the speed difference between non-local(random)accesses and sequential accessesis utilized optimally.The data structure needs n(8+|A|log ct)ct2bytes.Fort=ω(1),this results in a sub-linear space data structure,e.g.,for t=Θ(n1/d) we obtain a data structure of12ℓ+ℓ)bits,whichsupports answering rank-position-queries in O(log(n/2ℓ))time.The preprocess-ing needs O(n)time and O(|A|+2ℓ)working storage.Forℓ=13,we obtain a data structure of143present experimental results for the reverse BWT.Finally,in Section5we give conclusions and discuss open problems.2Algorithms for Rank-QueriesBefore we describe the algorithm we need some definitions.For a string S of length n(i.e.of n symbols)and integer number i,0≤i<n we denote by S[i] the symbol of S at the position(or index)i,i.e.,the index counts from0.For a string S and integers0≤i,j<n,we denote by S[i..j]the substring of S starting at index i and ending at j,if i≤j,and the empty string if i>j. S[i..i]=S[i]is the symbol at index i.The rank of symbol S[i]at the position i is defined as rank(i):=|{j:0≤j<i,S[j]=S[i]}|,i.e.,the rank of the k th occurrence of a symbol is k−1.2.1A Data Structure of13L )=n(ℓ−1+8w|A|2−ℓ)bits.We obtain the continuous minimum of this expression at the point,in which the derivative is0.Thus,we need1+8w|A|2−ℓ(−ln2)=0.After reorganizing this equality,we obtain2−ℓ=1Since|A|≤256,for w=4(32bit words),the continuous minimum is reached inℓ≈3+2+8−0.159.Settingℓ=12orℓ=13(and the block size L=4096 or L=8192,respectively),the size of the data structure becomes138n bytes.The preprocessing needs O(n)time and O(|A|)workingstorage.Remark:If the maximum number of occurrences of any symbol in the input is smaller than the largest integer that can be stored in a computer word,i.e. n<2p and p<8w,then we can store the values of b[j,x]using p bits instead of a complete word.Then the size of the data structure is n(ℓ−1+p|A|16bytes,and for p=24one of n51Utilizing processor caching–data structure of≤n bytes:The pro-cessors in modern computers use caching,hardware prefetching,and pipelining techniques,which results in significantly higher processing speed,if the algorithm accesses consecutive computer words than in the case of non-local accesses(re-ferred to as random accesses).In case of processor caching,when we access a computer word,a complete block of the memory will be moved into the proces-sor cache.For instance,in Intel Pentium4processors,the size of such a block (the so-called L2cache line size)is128bytes(see,e.g.[9]).Using this feature, we also obtain a fast answering time,if we get rid of storing the values of r[i], but instead of this,we compute r[i]during the query by scanning the block(of L bytes)containing the string index i.More precisely,it is enough to scan the half of the block:the lower half in increasing order of indices,if i mod L<L/2,and the upper half in decreasing order of indices,otherwise.In that way we obtain a data structure of size n|A|w/L bytes.Theorem2.Let S be a string of length n.S can be preprocessed into a data structure D(S),which supports answering a rank query Q(i)by performing1 random access to D(S)(and to S)and at most L/2sequential accesses to S. The data structure uses n|A|w/L bytes,where w is the length of a computer word in bytes.The preprocessing needs O(n)time and O(|A|)working storage.For|A|≤256,w=4and L=210,the size of the data structure is n bytes.If n<2p,p<8w,then we get a data structure of n bytes by using a block size of L=p|A|/8bytes.2.2A Sub-linear Space Data StructureIn this Section we describe a sub-linear space data structure for supporting rank-queries in strings in O(t)time for t=ω(1).Similarly to the data structure described in Section2.1,we divide the string S into n∗=⌈nc·t ⌉and x∈A needs n·(8+|A|log cn)8·c·tbytes.Additionally to the linear space data structure,the blocks are organized in ˆn=⌈nc·t2⌉and x∈A,such thatˆb[k,x]contains the number of occurrences of symbol x in the super-blocks0,...,k.These values are stored as integers.Storing all values needs n·|A|ct +8w|A|ct)(1+o(1))bits.The preprocessing needs O(n)time and O(|A|)working storage. Note,that for a block size of L=ct=29bytes and t≥167w,supports answering a rank-query Q(i)in O(t)time using t random accesses and ct/2sequential accesses.The prepro-cessing needs O(n)time and O(|A|)working storage.If we allow in Theorem3,for instance,a query time O(n1/d),then we can storethe value of b∗[j,x]in log nd n1−1/d|A|computerwords.Corollary2.Let S be a string of length n.S can be preprocessed into a data structure which supports answering a rank-query Q(i)in O(n1/d)time.The data structure uses13An Algorithm for Rank-Position-QueriesIn this Section we consider the inverse problem of answering rank-queries,the problem of answering rank-position-queries.A rank-position-query Q∗(x,k),x∈A,r∈I N0,reports the index0≤i<n in the string S,such that S[i]=x and rank(i)=k,if such an index exist,and”no index”otherwise.We show,how topreprocess S into a data structure of n(|A|w8)bytes,which supports answeringrank-position-queries in O(log(n/L))time.We divide the string S into n′=⌈n/L⌉blocks,each containing L=2ℓconsecutive symbols.The rank-position-query Q∗(x,k)will work in two steps: 1.Find the block B[j],which contains the index of the k th occurrence of x inS,and determine k0the overall number of occurrences of x in the blocks B[0],...,B[j−1].2.Find the relative index i′of the k′(:=k−k0)th occurrence of x within B[j],if i′exists,and return with index i=i′+jL,and return with”no index”otherwise.Data structure for Step1:For each block B[j],0≤j<n′and each symbol x∈A,we store an integer value b[j,x],which contains the overall number of occurrences of symbol x in blocks B[0],...,B[j−1],i.e.in S[0..jL−1].For storing the values b[j,x],0≤j<n′,x∈A,we need n′|A|=⌈n/L⌉|A|computer words,i.e.⌈n/L⌉8w|A|bits.The values of all b[j,x]can be computed in O(n) time using O(|A|)working storage.Let j be the largest number,such that b[j,x]<k.Then B[j]is the block, which contains the index of the k th occurrence of x,if S contains at least k occurrences of x,and B[j]is the last block otherwise.We set k0=b[j,x].Using this data structure,Step1can be performed in O(log(n/L))time by logarithmic search for determining j.Data structure for Step2:For each block B[j],0≤j<n′and each symbol x∈A,we store a sorted list p[j,x]of relative positions of the occurrences of symbol x in B[j],i.e.if B[j][i′]=x,0≤i′<L,then p[j,x]contains an element for i′.The relative index i′of the k′th occurrence of x in B[j]is the k′th element of the list p[j,x].Note,that the overall number of list elements for a block B[j] is L and each relative position can be stored inℓbits.Therefore,we can store all lists for B[j]in an array a[j]of L elements,where each element of a[j]consists ofℓbits.Additionally,for each0≤j<n′and x∈A,we store in s[j,x]the start index of p[j,x]in a[j].Since0≤s[j,x]<L,s[j,x]can be stored inℓbits.Therefore,the storage requirement of storing a[j]and s[j,x],0≤j<n′, x∈A,is nℓ+nℓ|A|/L bits.These values can be computed in O(n)time using O(L+|A|)working storage.(First we scan B[j]and build linked lists for p[j,x]: for0≤i′<n′,if B[j][i′]=x,then we append a list element for i′to p[j,x].Then we compute a[j]and s[j,x]for each x∈A from the linked lists.)Let k′=k−k0. Then the index i′of the k′th occurrence of symbol x in B[j]can be computed in O(1)time:i′=a[j][s[j,x]+k′−1],if s[j,x]+k′<s[j,x+1],where x+1is the symbol following x in the alphabet A.Otherwise,we return”no index”.Summarizing the description of this Section we obtain the following. Theorem4.Let S be a string of length n and L=2ℓ.S can be preprocessed into a data structure which supports answering a rank-position-query Q∗(x,k)in O(log(n/L))time.The data structure uses n(8w|A|L )bits,where wis the number of bytes in a computer word.For|A|≤256,w=4,andℓ=12,the size of the data structure is1438·n bits.Thepreprocessing needs O(n)time and O(|A|+L)working storage.Remark:If we do not store the values of p[j,x],but instead of this,we compute the relative index of the k′th occurrence of x for Q∗(x,k)during the query time, we can obtain a sub-linear space data structure at the cost of longer query times. 4Experimental ResultsAs each rank value is used exactly once in the reverse BWT,the space and runtime requirements depend solely on the size of the input,not on its content -as long as we ignore caching effects.Therefore,we give afirst comparison of algorithms based on only onefile.We used a binaryfile with2542412characters as input.Experiments were carried out on a1GHz Pentium III running Linux kernel2.4.18and using g++-3.4.1for compilations.When implementing the13Space[byte/input char]4byte rank values0.3711.625no rankfields,1024characters per block 3.4770.5input characters(resulting in256search steps on average for each rank com-putation)the increase in time for the reverse BWT is less than ten fold.In an embedded system where decompressed data are written to slowflash memory, writing toflash might dominate the decompression time.To further consolidate results,we give run times for the three methods for thefiles of the Calgary Corpus[15],which is a standard test suite and collection of reference results for compression algorithms(see e.g.,in[5]).As runtimes were too low to be reliably measured for some of thefiles,eachfile was run ten times. Table2summarizes the running times.n byteFile4n byte8[bytes]data structurepaper50.175 2.632132860.316obj10.195 2.536381050.358progc0.185 2.594465260.361progp0.191 2.718531610.355progl0.205 2.795821990.344trans0.201 2.6521024000.410bib0.283 2.7902468140.442news0.350 3.1285132160.323book20.388 3.4597687710.649the memory requirement for decompression may be essential in some embedded devices(e.g.,mobile phones),where RAM is a scarce resource.We showed that the reverse BWT can be done with1.625n bytes of auxiliary memory and O(n)runtime.Alternatively,we can use n/t bytes and256t n operations.We also presented several time-space tradeoffs for the variants of our solution.These results are based on our new data structures for answering rank-queries and rank-position-queries.The theoretical results are backed up by experimental data showing that our algorithms work quite well in practice.The question,if the space requirement of the data structures for rank-queries and rank-position-queries can be further reduced in our computational model,is still open.Improvements on the presented upper bounds have a practical impact. The problems of establishing lower bounds and improved time-space tradeoffs are open,as well.References1.J.Abel.Grundlagen des Burrows-Wheeler-Kompressionsalgorithmus(in german).Informatik-Forschung und Entwicklung,2003.http://www.data-compression.info/JuergenAbel/Preprints/Preprint BWCA.pdf.2.Z.Arnavut.Generalization of the BWT transformation and inversion ranks.InProc.IEEE Data Compression Conference(DCC’02),page447,2002.3.M.J.Atallah,editor.Algorithms and Theory of Computation Handbook.CRCPress,1999.4. B.Balkenhol and S.Kurtz.Universal data compression based on the Burrows-Wheeler transformation:Theory and practice.IEEE Trans.on Computers, 23(10):1043–1053,2000.5.T.C.Bell,J.G.Cleary,and I.H.Witten.Text Compression.Prentice Hall,Engle-wood Cliffs,NJ,1990.6.M.Burrows and D.J.Wheeler.A block-sorting lossless data compression algorithm.Tech.report124,Digital Equipment Corp.,1994.http://gatekeeper.research./pub/DEC/SRC/research-reports/abstracts/src-rr-124.html.7.P.Fenwick.Block sorting text compression–final report.Technical report,De-partment of Computer Science,The University of Auckland,1996.ftp://ftp.cs./pub/staff/peter-f/TechRep130.ps.8.P.Ferragina and pression boosting in optimal linear time usingthe Burrows-Wheeler transform.In Proc.15th ACM-SIAM Symposium on Discrete Algorithms(SODA’04),pages655–663,2004.9.Tom’s hadware guide./cpu/20001120/p4-01.html.10.U.Manber and E.Meyers.Suffix arrays:A new method for on-line string searches.SIAM Journal on Computing,22:935–948,1993.11.G.Manzini.An analysis of the Burrows-Wheeler transform.Journal of the ACM,48(3):407–430,2001.12.M.Nelson.Data compression with the Burrows-Wheeler transform.Dr.Dobb’sJournal,9,1996.13.J.Seward.Bzip2manual,/1.0.3/bzip2-manual-1.0.3.html.14.J.Seward.Space-time tradeoffs in the inverse B-W transform.In Proc.IEEE DataCompression Conference(DCC’01),pages439–448,2001.15.I.H.Witten and T.C.Bell.The Calgary Text Compression Corpus.available viaanonymous ftp at:ftp.cpcs.ucalgary.ca/pub/projects/pression.corpus.。
