effect of node mobility and network aimension to be the zigbee routing method
图神经网络综述

第47卷第4期Vol.47No.4计算机工程Computer Engineering2021年4月April 2021图神经网络综述王健宗,孔令炜,黄章成,肖京(平安科技(深圳)有限公司联邦学习技术部,广东深圳518063)摘要:随着互联网和计算机信息技术的不断发展,图神经网络已成为人工智能和大数据处理领域的重要研究方向。
图神经网络可对相邻节点间的信息进行有效传播和聚合,并将深度学习理念应用于非欧几里德空间的数据处理中。
简述图计算、图数据库、知识图谱、图神经网络等图结构的相关研究进展,从频域和空间域角度分析与比较基于不同信息聚合方式的图神经网络结构,重点讨论图神经网络与深度学习技术相结合的研究领域,总结归纳图神经网络在动作检测、图系统、文本和图像处理任务中的具体应用,并对图神经网络未来的发展方向进行展望。
关键词:图神经网络;图结构;图计算;深度学习;频域;空间域开放科学(资源服务)标志码(OSID ):中文引用格式:王健宗,孔令炜,黄章成,等.图神经网络综述[J ].计算机工程,2021,47(4):1-12.英文引用格式:WANG Jianzong ,KONG Lingwei ,HUANG Zhangcheng ,et al.Survey of graph neural network [J ].Computer Engineering ,2021,47(4):1-12.Survey of Graph Neural NetworkWANG Jianzong ,KONG Lingwei ,HUANG Zhangcheng ,XIAO Jing(Federated Learning Technology Department ,Ping An Technology (Shenzhen )Co.,Ltd.,Shenzhen ,Guangdong 518063,China )【Abstract 】With the continuous development of the computer and Internet technologies ,graph neural network has become an important research area in artificial intelligence and big data.Graph neural network can effectively transmit and aggregate information between neighboring nodes ,and applies the concept of deep learning to the data processing of non-Euclidean space.This paper briefly introduces the research progress of graph computing ,graph database ,knowledge graph ,graph neural network and other graph-based techniques.It also analyses and compares graph neural network structures based on different information aggregation modes in the spectral and spatial domain.Then the paper discusses research fields that combine graph neural network with deep learning ,and summarizes the specific applications of graph neural networks in action detection ,graph systems ,text and image processing tasks.Finally ,it prospects the future development research directions of graph neural networks.【Key words 】graph neural network ;graph structure ;graph computing ;deep learning ;spectral domain ;spatial domain DOI :10.19678/j.issn.1000-3428.00583820概述近年来,深度学习技术逐渐成为人工智能领域的研究热点和主流发展方向,主要应用于高维特征规则分布的非欧几里德数据处理中,并且在图像处理、语音识别和语义理解[1]等领域取得了显著成果。
Ad_Hoc_网络拓扑控制算法的设计与仿真(攻略)

分类号密级U D C学位论文Ad Hoc 网络拓扑控制算法的设计与仿真作者姓名:叶宁指导教师:李喆教授东北大学信息科学与工程学院申请学位级别:硕士学科类别:工学学科专业名称:通信与信息系统论文提交日期:2008 年1 月10 日论文答辩日期:2008 年1 月19 日学位授予日期:答辩委员会主席:评阅人:东北大学2008 年 1 月A Thesis for the Degree of Master in Telecommunications and Informatio n Systems Design and Simulation of a Topology ControlAlgorithm for Ad Hoc Networksby Ye NingSupervisor :Professor Li ZheNortheastern UniversityJanuary 2008- I -独创声明本人声明所呈交的学位论文是在导师的指导下完成的。
论文中取得的研究成果除加以标注和致谢的地方外,不包含其他人已经发表或撰写过的研究成果,也不包括本人为获得其他学位而使用过的材料。
与我一同工作的同志对本研究所做的任何贡献均已在论文中作了明确的说明并表示诚挚的谢意。
学位论文作者签名:签字日期:学位论文版权使用授权书本学位论文作者和指导教师完全了解东北大学有关保留、使用学位论文的规定:即学校有权保留并向国家有关部门或机构送交论文的复印件和磁盘,允许论文被查阅和借阅。
本人同意东北大学可以将学位论文的全部或部分内容编入有关数据库进行检索、交流。
(如作者和导师同意网上交流,请在下方签名:否则视为不同意)学位论文作者签名:导师签名:签字日期:签字日期:东北大学硕士学位论文摘要- II -Ad Hoc 网络拓扑控制算法的设计与仿真摘要Ad Hoc网络作为一种无中心、自构建、自组织和自管理的新型网络,因其组网灵活、展开迅速、分布式控制等诸多的优点,在军事和民用领域有广泛应用,成为研究的热点。
Analyzing the Efficiency of Networking Algorithms

Analyzing the Efficiency of NetworkingAlgorithmsNetworking algorithms play a crucial role in optimizing the performance and efficiency of computer networks. These algorithms are designed to facilitate communication, data transfer, and resource allocation in a networked environment. In this article, we will analyze the efficiency of networking algorithms and explore their impact on network performance.One of the key aspects of networking algorithms is their ability to manage network traffic efficiently. Traffic management algorithms are designed to prioritize network traffic, allocate bandwidth, and minimize congestion. These algorithms play a crucial role in ensuring that data packets are transmitted and received in a timely manner, without exceeding the network's capacity.Efficient networking algorithms also play a vital role in routing data packets through a network. Routing algorithms determine the best path for data packets to travel from the source to the destination. These algorithms take into account factors such as network topology, traffic load, and link quality to ensure that data packets reach their destination in the most efficient manner possible.Another important aspect of networking algorithms is their ability to optimize the use of network resources. Resource allocation algorithms allocate bandwidth, processing power, and other resources in a way that maximizes network performance and minimizes wasted resources. These algorithms help ensure that network resources are used efficiently and effectively, without overloading or underutilizing any particular resource.Efficiency in networking algorithms can also be measured in terms of scalability. Scalability refers to the ability of a network to handle an increasing number of users, devices, and data traffic without a significant decrease in performance. Networking algorithms that are designed to scale efficiently can adapt to changing network conditions and accommodate growth without sacrificing performance or reliability.In addition to improving network performance, efficient networking algorithms can also enhance network security. Security algorithms are designed to protect network data, prevent unauthorized access, and detect and mitigate potential security threats. By efficiently implementing security algorithms, network administrators can ensure that sensitive data is protected and that network resources are secure from external threats.Analyzing the efficiency of networking algorithms involves assessing various performance metrics, such as throughput, latency, packet loss, and scalability. By evaluating these metrics, network administrators can identify areas where network performance can be improved and implement targeted solutions to enhance efficiency.Overall, networking algorithms play a critical role in optimizing the performance and efficiency of computer networks. By effectively managing network traffic, routing data packets, allocating resources, scaling network infrastructure, and enhancing network security, efficient networking algorithms can help organizations achieve reliable and high-performing networks that meet the demands of today's digital world.。
MFG 名词缩写
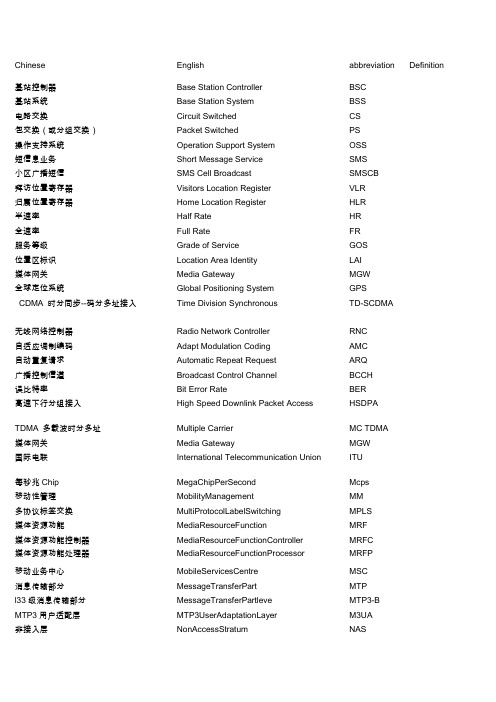
Chinese English abbreviation Definition基站控制器Base Station Controller BSC基站系统Base Station System BSS电路交换Circuit Switched CS包交换(或分组交换)Packet Switched PS操作支持系统Operation Support System OSS短信息业务Short Message Service SMS小区广播短信SMS Cell Broadcast SMSCB拜访位置寄存器Visitors Location Register VLR归属位置寄存器Home Location Register HLR半速率Half Rate HR全速率Full Rate FR服务等级Grade of Service GOS位置区标识Location Area Identity LAI媒体网关Media Gateway MGW全球定位系统Global Positioning System GPSCDMA 时分同步--码分多址接入Time Division Synchronous TD-SCDMA无线网络控制器Radio Network Controller RNC自适应调制编码Adapt Modulation Coding AMC自动重复请求Automatic Repeat Request ARQ广播控制信道Broadcast Control Channel BCCH误比特率Bit Error Rate BER高速下行分组接入High Speed Downlink Packet Access HSDPATDMA 多载波时分多址Multiple Carrier MC TDMA媒体网关Media Gateway MGW国际电联International Telecommunication Union ITU每秒兆Chip MegaChipPerSecond Mcps移动性管理MobilityManagement MM多协议标签交换MultiProtocolLabelSwitching MPLS媒体资源功能MediaResourceFunction MRF媒体资源功能控制器MediaResourceFunctionController MRFC媒体资源功能处理器MediaResourceFunctionProcessor MRFP移动业务中心MobileServicesCentre MSC消息传输部分MessageTransferPart MTPl33级消息传输部分MessageTransferPartleve MTP3-BMTP3用户适配层MTP3UserAdaptationLayer M3UA非接入层NonAccessStratum NASNodeB应用部分NodeBApplicationPart NBAP 操作维护OperationandMaintenance O&M全球移动通信系统Global System for Mobile Communications GSM码分多址Code Division Multiple Address CDMA时分复用Time Division Multiplexing TDM蜂窝电话的数据传输技术Cellular Digital Packet Data CDPD 个人通讯服务Personal Communications Service PCS时分多址Time Division Multiple Access TDMA第三代移动通信Third Generation 3G蜂窝移动电话系统Cellular Mobile Telephone System CMTSUMTS 通用移动电信系统Universal Mobile TelecommunicationsSystem全入网通信系统技术Total Access Communications System TACS 通用分组无线业务General Packet Radio Service GPRS 误块Error Block EB误块秒Errored Second ES网络单元Network Element NE网络管理层Network Management Layer NML网元层Network Element Layer NEL中国移动IP承载网IP Network IPNET 中国移动互联网China Mobile Network CMNET 域名系统Domain Name System DNS数据业务管理平台Data Services Management Platform DSMP 数字数据网络Digital Data Network DDN通用分组无线业务General Packet Radio Service GPRS 高级数据链路控制High Level Data Link Control HDLC 综合业务数字网Integrated services digital network ISDN 多媒体消息业务Multimedia Messaging Service MMS接入服务器Network Access Server NAS网络接入点Network Access Point NAP远程访问接入用户服务Remote Access Dialing User Service RADIUS端到端协议Peer-Peer Protocol PPP短消息业务Short Message Service SMS无线应用协议Wireless Application Protocol WAP接入层路由器Access Router AR核心接点路由器Core Router CR用户边缘设备Customer Edge CE服务商边缘路由器Provider Edge PE骨干接点路由器Backbone Router BR媒体网关Media Gateway MGW流控制传输协议Stream Control Transmission Protocol SCTP下一代网络Next Generation Network NGN无线局域网Wireless Local Area Network WLAN电路交换域circuit switched CS本地终端craft terminal local CTL文件传输协议file transfer protocol FTP移动交换中心mobile switching center MSC设备最初制造商original equipment manufacturer OEM操作维护终端operation and maintenance terminal OMT访问位置寄存器visitor location register VLR无线应用协议wireless application protocol WAP归属位置寄存器home location register HLR移动台Mobile Station MS自适应多速率Adaptive Multi-rate AMR BCCH 分配BCCH Allocation BA基站控制器Base Station Controller BSC基站识别码Base Station Identification Code BSIC基站收发信台Base Transceiver Station BTS小区识别号Cell Identity CI路测和拨打测试Driver Test & Call Quality Test DT&CQT非连续性发射Discontinuous Transmission DTX地理信息系统Geographic Information System GIS通用分组无线业务General Packet Radio Service GPRS高速下行分组接入High Speed Downlink Packet Access HSDPA跳频序列号Hopping Sequence Number HSN位置区码Location Area Code LAC移动分配Mobile Allocate MA移动分配索引Mobile Allocate Index MAIO管理信息库Management Information Base MIB操作维护中心Operation & Maintenance Center OMC无线网络控制器Radio Network Controller RNC简单网络管理协议Simple Network Management Protocol SNMP 独立专用控制信道Stand-Alone Dedicated Control Channel SDCCH分/插复用设备Add-drop Multiplexer ADM恒定比特率Constant Bit Rate CBR连接终端点Connection Termination Point CTP业务分类Class of Service Cos使用约束路由的LDP协议Constraint Based Routing LDP CR-LDP 数字交叉连接设备Digital Cross Connect Equipment DXC数据通信网Data Communication Network DCN网元管理系统Element Management System EMSEOMS 电子运维系统Electronic Opration and MaintenanceSystem网元管理层Element Management Lay EML以太网虚拟专线Ethernet Virtual Private Line EVPL虚拟以太网专用局域网Ethernet Virtual Private LAN EVPLAN 以太网专线Ethernet Private Line EPL以太网专用局域网Ethernet Private LAN EPLAN 转发等价类Forwarding Equivalence Class FEC通用成帧规程Generic Framing Procedure GFP图形用户界面Graphic User Interface GUI链路接入协议-SDH Link Access Procedure-SDH LAPS链路容量调整方案Link Capacity Adjustment Scheme LCAS标记分发协议Label Distribution Protocol LDP逻辑端口Logical Port LP标签交换路径Label Switch Path LSP标记交换路由器Label Switching Router LSR管理信息系统Management Information System MIS多协议标签交换Multi-Protocol Label Switch MPLS复用段Multiplex Section MS复用段共享保护环Multiplex Section-Shared Protection Ring MS-SPRING 多业务传送节点Multi-Service Transport Platform MSTP网元层Net Element Lay NEL网络管理层Net Management Lay NML网络管理系统Network Management System NMS网元Net Element NE非实时可变比特率non-real time Variable Bit Rate nrt-VBR峰值信元速率Peak Cell Rate PCR点对点协议Point to Point Protocol PPP物理终端点Physical Termination Point PTP再生段Regenerator Section RS资源预留协议Resource Reservation Protocol RSVP实时可变比特率real time Variable Bit Rate rt-VBR可持续信元速率Sustainable Cell Rate SCR存储局域网Storage Area Network SAN同步数字体系Synchronous Digital Hierarchy SDH业务等级协定Service Level Agreement SLA子网连接Sub-network Connection SNC子网管理系统Subnetwork Management System SNMS同步传输模块Synchronous Transmission Module STM生成树协议Spanning Tree Protocol STP终端复用设备Terminal Multiplexer TM透明局域网业务Transparent Local Area Network Service TLS电信管理网Telecommunications management net TMNOAM操作、管理、维护Operations, Administration andMaintenance未指定比特率Unspecified Bit Rate UBR用户参数控制/网络参数控制User Parameter Control/Network ParemeterUPC/NPCControl单向通道倒换环Unidirectional Path Switch Ring UPSR虚拟个人网Virtual Private Network VPN虚容器Virtual Concatenation VC虚级联组Virtual Concatenation Group VCG虚拟租用线Virtual Lend Line VLL虚拟局域网Virtual LAN VLAN虚拟私人专用局域网服务Virtual Private LAN Service VPLS波分复用Wavelength Division Multiplexing WDM绵阳MSCC MYMSCC 绵阳SERVER1 MYS1绵阳SERVER2 MYGS2 绵阳关口局MGW1 MYDM1 绵阳HLR MYHLR 绵阳BSCH1 MYBSCH1 成都软交换SERVER1 CDSSA1 成都软交换MGW1 CDTMGA1 成都A1 CDA1成都B3 CDB3鉴权算法A3 A3一个实现A3和A8功能的单独算法- A38加密算法A5/1 - A5/1加密算法A5/2 - A5/2加密算法A5/07 - A5/X产生密钥的算法A8 - A8突发访问Access Burst AB访问类别(从C0到C15) Access Class (C0 to C15) AC应用上下文Application Context自动拥塞控制Automatic Congestion Control ACC随路控制信道Associated Control Channel ACCH确认(用于信令)ACKnowledgement ACK累计呼叫记录Accumulated Call Meter ACM地址完全的消息Address Complete Message天线合成单元Antenna Combining Unit ACU管理中心ADministration Centre ADC模数转换Analogue to Digital Converter A/D缩位拨号Abbreviated Dialling Number ADN自适应差分脉冲编码调制Adaptive Differential Pulse Code Modulation ADPCM应用实体Application Entity AE回音控制Acoustic Echo Control AEC附加基本单元Additional Elementary Functions AE访问允许信道Access Grant Channel AGCH动作指示Action indicator Ai费用建议Advice of Charge AoCAoCC费用建议补充服务Advice of Charge Charging supplementaryservice费用建议信息补充服务Advice of Charge InformationAoCIsupplementary service费用服务单元Application Service Element ASE抽象语法表示1 Abstract Syntax Notation One ASN.1绝对无线频率信道数Absolute Radio Frequency Channel Number ARFCN自动重发请求Automatic ReQuest for retransmission ARQ加入(用于信令)ATTach ATT(flag) 访问单元Access Unit AU鉴权中心Authentication Centre AuC鉴权AUThentication AUT(H) BCCH分配BCCH Allocation BA限制所有呼入呼叫的补充服务Barring of All Incoming Calls supplementaryserviceBAIC限制所有呼出呼叫的补充服务Barring of All Outgoing Calls supplementaryserviceBAOC基站收发器代码Base Transceiver Station (BTS) ColourCodeBCC广播控制信道Broadcast Control Channel BCCH二进制编码的十进制Binary Coded Decimal BCD基站控制功能Base station Control Function BCF载波容量信息单元Bearer Capability Information Element BCIE误码率Bit Error Rate BER坏帧指示Bad Frame Indication BFI所有的限制呼入呼叫补充服务all Barring of Incoming call supplementaryservicesBI在注册的PLMN国家之外限制呼入呼叫的补充服务Barring of Incoming Calls when Roamingoutside the home PLMN countrysupplementary serviceBICRoam全速业务信道Fullrate traffic channel Bm 比特数Bit Number BN 所有的限制呼出呼叫补充服务all Barring of Outgoing call supplementaryservicesBO限制国际呼叫的补充服务Barring of Outgoing International Callssupplementary serviceBOIC除了直接呼叫注册的PLMN国家以外限制国际呼出呼叫的补充服务Barring of Outgoing International Callsexcept those directed to the Home PLMNCountry supplementary serviceBOICexHC载波服务Basic Service (group) BS 基本服务Bearer Service基本服务组Basic Service Group BSG基站控制器Base Station Controller BSC基站收发器鉴别码Base transceiver Station Identity Code BSIC一个临近小区的BSIC BSIC of an adjacent cell BSICNCELL 基站子系统Base Station System BSS基站子系统应用部分Base Station System Application Part BSSAP基站子系统管理应用部分Base Station System ManagementBSSMAPApplication PartBSSOMAP 基站子系统操作和维护应用部分Base Station System Operation andMaintenance Application Part基站收发器,即常说的手机基站Base Transceiver Station BTS有条件的Conditional C小区分配Cell Allocation CA收费建议信息harge Advice Information CAI小区广播Cell Broadcast CB小区广播中心Cell Broadcast Centre CBC小区广播信道Cell Broadcast Channel CBCH小区广播信息标识符Cell Broadcast Message Identifier CBMI国家代码Country Code CC呼叫控制Call ControlCCBS对占线用户的完成呼叫的补充服务Completion of Calls to Busy Subscribersupplementary service公用控制信道Common Control Channel CCCH条件呼叫转移Conditional Call Forwarding CCF控制信道Control Channel CCHCCITT国际电报电话咨询委员会Comité Consultatif InternationalTélégraphique et Téléphonique (TheInternational Telegraph and TelephoneConsultative Committee)当前呼叫记录Current Call Meter CCM容量/配置参数Capability/Configuration Parameter CCP控制信道协议实体Control Channel Protocol Entity CCPE电路Circuit Cct要计费的时间Chargeable DURation CDUR被呼叫的基站标识符called station identifier CED 中央设备识别寄存器Central Equipment Identity Register CEIR计费的结束点end of charge point CENDCEPT 欧洲邮政和远程通信会议Conférence des administrationsEuropéennes des Postes etTelecommunications变换工具Conversion Facility CF所有的呼叫转移服务all Call Forwarding services移动用户遇忙呼叫转移补充服务Call Forwarding on mobile subscriber BusyCFBsupplementary service移动用户不在服务区呼叫转移补充服务Call Forwarding on mobile subscriber NotCFNRcReachable supplementary service无应答呼叫转移补充服务Call Forwarding on No Reply supplementaryCFNRyserviceCFU无条件呼叫转移补充服务Call Forwarding Unconditionalsupplementary service计费点CHarging Point CHP 卡持有者验证信息Card Holder Verification information CHV 小区标识Cell Identity CI CUG索引CUG Index载波干扰比(载干比)Carrier to Interference Ratio CIR密钥序列码Ciphering Key Sequence Number CKSN呼叫线路标识Calling Line Identity CLICLIP 呼叫线路标识显示补充服务Calling Line Identification Presentationsupplementary serviceCLIR 呼叫线路标识限制补充服务Calling Line Identification Restrictionsupplementary service连接管理Connection Management CM命令(用于信令)CoMmanD CMD 信道模式更改Channel Mode Modify CMM 呼叫音调CalliNG tone CNG 连接的线路标识COnnected Line Identity COLI 连接的线路标识显示补充服务COnnected Line identification PresentationCOLPsupplementary service连接的线路标识限制补充服务COnnected Line identification RestrictionCOLRsupplementary service完成(用于信令)COMplete COM连接确认(用于信令)CONNect ACKnowledgement CONNACK 命令/相应区域比特Command/Response field bit C/R冗余循环校验(3比特)Cyclic Redundancy Check (3 bit) CRC呼叫重建立过程Call REestablishment procedure CRE电路交换公众数据网Circuit Switched Public Data Network CSPDN呼叫转移补充服务Call Transfer supplementary service CT信道测试Channel Tester信道类型Channel Type通用技术规定Common Technical Regulation CTR关闭用户组补充服务Closed User Group supplementary service CUG通用技术规定Common Technical Regulation CTR呼叫等待补充服务Call Waiting supplementary service CW数模转换Digital to Analogue Converter DAC哑元突发Dummy Burst DB专用控制信道Dedicated Control Channel DCCH数据电路终端Data Circuit terminating Equipment DCE数据通信功能Data Communication Function DCF数据转换模块Data Conversion Module DCM数据通信网Data Communication Network DCNDigital Cellular System at 1800MHz DCS1800 1800MHz数字蜂窝系统,和900MHz GSM系统并称双频网离开(用于信令)DETach DET断开连接(用于信令)DISConnect DISC数据链路层Data Link (layer) DL数据链路连接标识Data Link Connection Identifier DLCI数据链路鉴别器Data Link Discriminator DLD控制信道(应用于移动服务的ISDN术语)Control channel (ISDN terminology appliedDmto mobile service)数字无线移动Digital Mobile Radio DMR 数据网标识Data network identifier DNIC 拨号脉冲Dial/Dialled Pulse DP非连续的接收Discontinuous reception (mechanism) DRX 数据交换Data Switching Exchange DSE数字语音插值Digital Speech Interpolation DSI一号数字用户信令Digital Subscriber Signalling No1 DSS1 直接传送应用部分Direct Transfer Application Part DTAP 数据终端Data Terminal Equipment DTE双音多频。
车载网络Secure pseudonym generation for efficient broadcast authentication in VANETs

Assumption Model
Each vehicle V when registered with the CA is provided a public / private key pair and CApub The RA periodically pulls information from the CA to get the latest up to date CRL’s and registered vehicles information. Each RA maintains a topological overview of the entire area under its coverage Attacker can compromise at most one RSU under a RA’s range. At any time in the network there are more number of benign nodes than the compromised nodes.
24,000 of these due to collision with other vehicles / objects.
Costs more than $100 billion per year
Boost on-board luxury
Source: US Census Bureau :
Lane Change Warning
Intersection Collision Warning
Approaching Emergency vehicle
Rollover Warning
Work Zone Warning
Coupling/Decoupling
evolved packet core翻译

Evolved Packet Core1. IntroductionEvolved Packet Core (EPC) is a key component in modern mobile communication networks. It is responsible for providing advanced packet-based services to users while ensuring efficient network management and connectivity. In this article, we will delve into the intricacies of EPC, its architecture, functionalities, and its role in enabling next-generation mobile networks.2. EPC ArchitectureThe architecture of EPC comprises several key components that work together to deliver seamless connectivity and high-speed data transmission. These components include:2.1. Mobility Management Entity (MME)MME acts as the control plane entity in EPC and is responsible for managing the mobility aspects of user devices. It handles tasks such as authentication, location tracking, and handover management. MME ensures that users can move between different network cells seamlessly without any interruption in their service.2.2. Serving Gateway (S-GW)S-GW acts as an intermediate node between the radio access network and the core network. It is responsible for routing user data packets between the user device and the appropriate network elements. S-GW also performs tasks such as packet filtering, charging, and Quality ofService (QoS) enforcement.2.3. Packet Data Network Gateway (P-GW)P-GW serves as the interface between the EPC and external packet data networks such as the Internet or private networks. It handles tasks related to IP address allocation, authentication, and policy enforcement. P-GW also ensures secure and reliable data transmission between theusers and external networks.2.4. Policy and Charging Rules Function (PCRF)PCRF is responsible for enforcing policy and charging rules in EPC. It determines the appropriate QoS for each user and ensures that thenetwork resources are efficiently utilized. PCRF also plays a crucialrole in billing and charging, enabling service providers to offervarious data plans and billing options to their subscribers.3. Functionalities of EPCEPC provides a wide range of functionalities that enable advanced mobile services and seamless connectivity. Some of the key functionalities include:3.1. IP ConnectivityEPC ensures that users have seamless IP connectivity regardless of their location or the type of access network they are connected to. Itsupports both IPv4 and IPv6 addressing schemes, allowing for a smooth transition to the next-generation Internet protocol.3.2. Quality of Service (QoS) ManagementEPC enables service providers to deliver different levels of QoS tousers based on their specific requirements. It ensures that critical applications such as video streaming or VoIP receive higher priority, resulting in an improved user experience.3.3. Mobility ManagementEPC enables users to move between different network cells or access technologies without any interruption in their service. It ensures smooth handovers and seamless connectivity, enabling users to stay connected while on the move.3.4. Security and PrivacyEPC employs various security measures to protect user data and ensure privacy. It includes authentication mechanisms, encryption, and secure tunnels to prevent unauthorized access and data breaches.4. Benefits of EPCImplementing EPC in mobile networks offers several benefits to both service providers and end-users. Some of the notable benefits include:4.1. Enhanced User ExperienceEPC enables faster data transmission and lower latency, resulting in a superior user experience. It allows users to enjoy high-quality video streaming, seamless voice calls, and efficient browsing, even in high-traffic areas.4.2. Scalability and FlexibilityEPC architecture is designed to handle the growing demand for data-intensive services. It offers scalability and flexibility, allowing service providers to efficiently manage network resources and accommodate the increasing number of connected devices.4.3. Cost EfficiencyBy optimizing resource utilization and streamlining network management, EPC helps service providers reduce operational costs. It enables efficient traffic management, reduces equipment requirements, and simplifies network maintenance, resulting in significant cost savings.ConclusionEvolved Packet Core is an essential component in modern mobile networks. It provides advanced packet-based services, ensures seamless connectivity, and offers a range of functionalities that enhance the user experience. With its scalable architecture and cost-efficient operation, EPC serves as a foundation for next-generation mobile communication networks. By adopting EPC, service providers can deliver high-speed data services, meet the growing demands of users, and drive innovation in the telecommunications industry.。
计算机技术与人工智能的深度融合研究

I G I T C W产业 观察Industry Observation172DIGITCW2023.11在现代科技研究广度和深度的有效拓展下,计算机技术的应用范围不断扩大,为人类文明发展和社会进步提供了强劲推动力,构建了高效的计算机思维。
人工智能和计算机技术的深度融合使二者的优势得到了最大化拓展,为现代科技和工业建设提供了持久动力。
1 人工智能技术概述1.1 人工智能的概念人工智能是指计算机系统通过模拟人类智能、推理、学习、理解和创造等能力,实现自主决策和执行任务的能力。
它是计算机科学中的一个重要研究领域,也是未来科技发展的重要方向。
作为计算机科学的一个重要分支,人工智能融合了信息、语言、哲学等多项学科内容,在计算机思维支撑下,体现出了极高的学习、记忆优势,能结合相关指令,深层挖掘数据信息。
在现阶段发展中,人工智能的核心技术包括机器学习、深度学习、自然语言处理、计算机视觉、智能控制等,其中,机器学习是一种通过数据和算法,让计算机自主学习的技术;深度学习是机器学习的一个重要分支,它能通过多层神经网络,实现对大量数据的自动分析和处理;自然语言处理则能让计算机理解和生成自然语言,并将智能对话和交互变为可能。
人工智能技术旨在研究如何让计算机具备思考、学习、推理、理解自然语言等能力,通过与计算机技术的深度融合,实现智能化应用系统的不断挖掘。
1.2 人工智能的特点人工智能是以计算机技术为基础的新型科学技术,通过深度发展和研究,能够模拟人类思维、推计算机技术与人工智能的深度融合研究赵 严(太原学院,山西 太原 030000)摘要:随着国际竞争局势日趋白热化,竞争方向的转变与现代科技更新换代速度的提升,使得计算机技术与人工智能的深度融合显得更加紧迫。
这种融合不仅成为了大势所趋,也成为推动科技创新与持续发展不可或缺的因素。
人工智能的特点和计算机技术的广泛应用为其融合提供了得天独厚的优势,能够促进智能服务业务的发展,实现科技向生产力的快速转化。
移动通信英文缩写与中文对照

3G-MSC 3rd Generation Mobile Switching Centre 第三代移动交换中心3G-SGSN 3rd Generation Serving GPRS Support Node 第三代服务GPRS 的节点3GPP 3rd Generation partnership project 3 代合作项目AAL2 ATM Adaptation Layer type 2 ATM 适配层2AAL5 ATM Adaptation Layer type 5 ATM 适配层5ACIR Adjacent Channel Interference Ratio 邻道干扰比ACLR Adjacent Channel Leakage power Ratio 邻道泄漏功率比ACS Adjacent Channel Selectivity 邻道选择性210ALCAP Access Link Control Application Part 接入链路控制应用部分AMC Adapt Modulation Coding 自适应调制编码ARQ Automatic Repeat Request 自动重复请求ASN.1 Abstract Syntax Notation One 抽象语义描述1ATM Asynchronous Transfer Mode 异步传输模式AuC Authentication Centre 鉴权中心BCH Broadcast Channel 广播信道BCCH Broadcast Control Channel 广播控制信道BER Bit Error Rate 误比特率BGCF Breakout Gateway Control Function 突破网关控制功能BSC Base Station Controller 基站控制器BSS Base Station Subsystem 基站子系统BTS Base Transceiver Station 基站收发机CC Call Control 呼叫控制CCCH Common Control Channel 公共控制信道CCH Control Channel 控制信道CCPCH ` Common Control Physical Channel 公共控制物理信道CDMA Code Division Multiple Access 码分多址CDMA TDD CDMA Time Division Duplex 码分多址时分双工CFN Connection Frame Number 连接帧号CM Connection Management 连接管理CN Core Network 核心网CQI Channel Quality Indicator 信道质量指示CRC Cyclic Redundancy Check 循环冗余检验CRNC Controlling Radio Network Controller 控制的无线网络控制器CS Circuit Switched 电路交换CSCF Call Server Control Function 呼叫服务器控制功能DCA Dynamic channel allocation 动态信道分配DCCH Dedicated Control Channel 专用控制信道DCH Dedicated Transport Channel 专用传输信道DL Downlink 下行链路DOA Direction Of Arrival 到达方向DPCH Dedicated Physical Channel 专用物理信道DRNC Drift Radio Network Controller 漂移无线网络控制器DRNS Drift RNS 漂移RNSDS CDMA Direct Spreading CDMA 直接扩频码分多址DSCH Down-link Shared Channel 下行共享信道DTCH Down-link Traffic Channel 下行业务信道DwPCH Downlink Pilot Channel 下行导频信道DwPTS Downlink Pilot Time Slot 下行导频时隙EIR Equipment Identity Register 设备标识寄存器EP Elementary Procedure 基本过程FACH Forward Access Channel 前向接入信道211FDD Frequency Division Duplex 频分双工FFS For Further Study 进一步研究FP Frame Protocol 帧协议FPACH Fast Physical Access Channel 快速物理接入信道FT Frame Type 帧类型GGSN Gateway GPRS Support Node GPRS 网关支持节点GMM GPRS Mobility Management GPRS 移动性管理GMSC Gateway MSC 网关移动业务中心GPRS General Packet Radio Service 通用分组无线业务GPS Global Positioning System 全球定位系统GRR GPRS Radio Resources GPRS 无线资源GSM Global System for Mobile Communication 全球移动通信系统GTP GPRS Tunneling Protocol GPRS 隧道协议HARQ Hybrid Automatic Repeat Request 混合自动重复请求HFN Hyper Frame Number 超帧号HLR Home Location Register 归属位置寄存器HSDPA High Speed Downlink Packet Access 高速下行分组接入HSS Home Subscriber Server 归属用户服务器IMSI International Mobile Subscriber Identity 国际移动用户标识码IMT-2000 International Mobile Telecommunications 2000国际电联命名3 代移动通信系统IP Internet Protocol 因特网协议IS-2000 IS-95 Evolution Standard (cdma2000) cdma2000ITU International Telecommunication Union 国际电联L1 Layer 1 层1L2 Layer 2 层2LAN Local Area Network 本地网络LMU Location Measurement Unit 位置测量单元MAC Medium Access Control 媒质接入控制MAP Mobile Application Part 移动应用部分MC CDMA Multiple Carrier CDMA 多载波码分多址MC TDMA Multiple Carrier TDMA 多载波时分多址ME Mobile Equipment 移动设备MGCF Media Gateway Control Function 媒体网关控制功能MGW Media Gateway 媒体网关MIB Master Information Block 控制信息块Mcps Mega Chip Per Second 每秒兆ChipMM Mobility Management 移动性管理MPLS MultiProtocol Label Switching 多协议标签交换MRF Media Resource Function 媒体资源功能MRFC Media Resource Function Controller 媒体资源功能控制器MRFP Media Resource Function Processor 媒体资源功能处理器MSC Mobile Services Centre 移动业务中心212MTP Message Transfer Part 消息传输部分MTP3-B Message Transfer Part level 3 3 级消息传输部分M3UA MTP3 User Adaptation Layer MTP3 用户适配层NAS Non Access Stratum 非接入层NBAP NodeB Application Part Node B 应用部分O&M Operation and Maintenance 操作维护PC Power Control 功率控制PCCH Paging Control Channel 寻呼控制信道PCCPCH Primary Common Control Physical Channel 基本公共控制物理信道PCH Paging Channel 寻呼信道PDSCH Physical Downlink Shared Channel 物理下行链路共享信道PLMN Public Land Mobile Network 公共陆地移动网PPP Point-to-Point Protocol 点对点协议PRACH Physical Random Access Channel 物理随机接入信道PS Packet Switched 分组交换PSTN Public Swithed Telephone Network 公共电话交换网络PUSCH Physical Uplink Shared Channel 物理上行链路共享信道QAM Quadrature Amplitude Modulation 正交幅度调制QE Quality Estimate 质量评估QPSK QuadriPhase Shift Keying 四相移键控QoS Quality of Service 业务质量R-SGW Roaming Signalling Gateway 漫游信令网关RAB Radio access bearer 无线接入承载RACH Random Access Channel 随即接入信道RANAP Radio Access Network Application Part 无线接入网应用部分RAT Radio Access Technology 无线接入技术RL Radio Link 无线链路RLC Radio Link Control 无线链路控制RNC Radio Network Controller 无线网络控制器RNS Radio Network Subsystem 无线网络子系统RNSAP Radio Network Subsystem Application Part 无线网络子系统应用部分RNTI Radio Network Temporary Identity 无线网络临时识别RR Radio Resources 无线资源RRC Radio Resource Control 无线资源控制RSVP Resource ReserVation Protocol 资源保留协议RTCP Real Time Control Protocol 实时控制协议RTP Real Time Protocol 实时协议SA Service Area 服务区域SABP service area broadcast protocol 服务区广播协议SAP Service Access Point 服务接入点SBM Subnetwork Bandwidth Management 子网带宽管理SC TDMA Single Carrier TDMA 单载波时分多址SSCF Service Specific Co-ordination Function 特定业务协调功能213SCCP Signalling Connection Control Part 信令连接控制部分SCH Synchronization Channel 同步信道SCCPCH Secondary Common Control Physical Channel 辅助公共控制物理信道SCP Service Control Point 业务控制点SCTP Simple Control Transmission Protocol 简单控制传输协议SFN System Frame Number 系统帧号SGSN Serving GPRS Support Node GPRS 服务支持节点SIB System Information Block 系统信息块SIM Subscriber Identity Module 用户识别模块SLF Subscrīption Location Function 签约位置功能SM Session Management 会话管理SRNC Serving Radio Network Controller 服务无线网络控制SRNS Serving RNS 服务RNSSS7 Signalling System No. 7 7 号信令系统SSCF Service Specific Co-ordination Function 具体业务协调功能SSCF-NNI Service Specific Coordination Function – Network Node Interface 具体业务协调功能网元接口SSCOP Service Specific Connection Oriented Protocol 特定业务面向连接协议.STM Synchronous Transfer Mode 同步传输模式.T-SGW Transport Signalling Gateway 传输信令网关TB Transport Block 传输块TBS Transport Block Set 传输块集TCP Transfer Control Protocol 传输控制协议TDD Time Division Duplex 时分双工TDMA Time Division Multiple Access 时分多址接入TD-SCDMA Time Division Synchronous CDMA 时分同步--码分多址接入TFC Transport Format Combination 传送格式组合TFCI Transport Format Combination Indicator 传送格式组合指示TFCS Transport Format Combination Set 传送格式组合集TFI Transport Format Indicator 传送格式指示TFS Transport Format Set 传送格式集ToA Time of arrival 到达时间TPC Transmit Power Control 发射功率控制TSN Transmission Sequence Number 传输序列号TTI Transmission Time Interval 传输时间间隔UDP User Datagram Protocol 用户数据报协议UE User Equipment 用户设备UL Uplink 上行链路UMTS Universal Mobile Telecommunication System 陆地移动通信系统UpPTS Uplink Pilot Time slot 上行导频时隙UpPCH Uplink Pilot Channel 上行导频信道USCH Up-link Shared Channel 上行共享信道USIM UMTS Subscriber Identity Module UMTS 用户识别模块214UTRAN UMTS Terrestrial Radio Access Network UMTS 陆地无线接入网VC Virtual Circuit 虚电路VLR Visitor Location Register 访问位置寄存器WAP Wireless Application Protocol 无线应用协议WCDMA Wideband Code Division Multiple Access 宽带cdmaWG Working Group 工作组WWW World Wide Web 万维网XRES EXpected user RESponse 期待的用户响应1X EV 1X Evolution 1X增强1X EV-DO 1X Evolution Data Only 1X增强-数据1X EV-DV 1X Evolution Data & Voice 1X增强-数据与语音1xEV-DO 1x evolution Data Optimized 1x演进数据优化24PB 24V Power Board 24V电源板2G BTS 2G Base Station Transceiver 仅支持IS-95空中接口标准的BTS3G BTS 3G Base Station Transceiver 支持IS-2000空中接口标准的BTSAAAA Authentication Authorization Accounting 认证、授权、记帐AAL ATM Adaptation Layer ATM适配层AAL2 ATM Adaptation Layer type 2 ATM 适配层2AAL5 ATM Adaptation Layer type 5 ATM适配层5Abis Interface Abis Interface—the interface of BSC--BTS 基站控制器和基站收发信机间接口ABS Air Break Switch 空气开关AC Asynchronous Capsule 异步包ACB Amplifier Control Board 放大器控制板ACCH Associated Control Channel 随路控制信道ACCM Asynchronous Control Character Map 异步控制字符映射ACIR Adjacent Channel Interference Ratio 相邻信道干扰比ACK Acknowledgement 应答ACLR Adjacent Channel Leakage Power Ratio 相邻信道泄漏功率比ACS Adjacent Channel Selectivity 相邻信道选择性ADF Application Dedicated File 应用专用文件ADN Abbreviated Dialing Numbers 按字母顺序排列的电话号码薄AESA ATM End System Address ATM末端系统地址AGC Automatic Gain Control 自动增益控制AH Authentication Header 鉴权报头 AI Acquisition Indicator 捕获指示AICH Acquisition Indicator Channel 捕获指示信道AID Application IDentifier 应用标识符AIUR Air Interface User Rate 空中接口用户速率AK Anonymity key 匿名密钥ALC Automatic Level Control 自动电平控制ALCAP Access Link Control Application Protocol 接入链路控制应用协议 ALW Always 一直AM Acknowledged Mode 应答模式AMB Attenuation Matching Board 衰减匹配板AMF Authentication Management Field 鉴权管理域AMP Address Management Protocol 地址管理协议AMR Adaptive Multi Rate 可采纳的多速率AN Access network 接入网络ANID Access Network Identifiers 接入网标识AP Access preamble 接入前缀APB ATM Process Board ATM接入处理板APD AC Power Distribution Module 交流配电模块APDU Application Protocol Data Unit 应用协议数据单元API Application Programming Interface 应用程序接口ARM ARM processor ARM处理器ARP Address Resolution Protocol 地址解析协议ARQ Automatic Repeat Request 自动重发请求AS Access Stratum 接入层ASC Access Service Class 接入业务级A-SGW Access Signaling Gateway 接入信令网关ASN.1 Abstract Syntax Notation One 抽象语法表示1AT Access terminal 接入终端ATM Asynchronous Transfer Mode 异步传输模式ATR Answer To Reset 复位回答ATT Attenuator 衰减器AUC Authentication Center 鉴权中心AUTN Authentication token 鉴权标记AWGN Additive White Gaussian Noise 加性高斯白噪声A Interface A Interface—the interface of BSC-MSC 移动交换中心与基站子系统间接口BB-BDS Backplane of Baseband Digital Subsystem 基带数字子系统背板 BBDS Backplane of BDS BDS框的背板BBS BTS Baseband Subsystem 基站基带子系统BCC Bear Channel Connect 承载通路连接BCCH Broadcast Control Channel 广播控制信道BCFE Broadcast Control Functional Entity 广播控制功能实体BCH Broadcast Channel 广播信道BCS BTS Communication Subsystem 基站通信子系统BCSN Backplane of Circuit Switch Network 电路交换网背板BCTC Backplane of Control Center 控制中心背板BDM Baseband Digital Module 基带数字模块BDM1900 1.9G Baseband Digital Module 微基站1.9G基带数字模块BDM800 800M Baseband Digital Module 微基站800M基带数字模块 BDS Baseband Digital System 基带数字系统BER Bit Error Ratio 误码率,比特差错率BGPS Backplane of GPS GPS背板BGT Block Guard Time 块守护时间BIC Baseline Implementation CapabilitiesBID Binding Identity 捆绑标识BIM BDS Interface Module BDS系统接口模块B-ISDN ISDN Broadband ISDN 宽带BLER Block Error Rate 误块率BLPA Backplane of LPA LPA框的背板BMC Broadcast/Multicast Control 广播/多址控制BOC Bell Operating Company 贝尔运行公司BPD BDS Power Distribute BDS机柜电源分配模块BPSK Binary Phase Shift Keying 二进制移相键控BPSN Backplane of Packet Switch Network 分组交换网背板BPWS Backplane of PWS PWS框的背板BRFE Backplane of RFE RFE框的背板BRFS Backplane of TRX and BDM/RFM BDM/RFM和TRX的连接背板BS Base Station 基站BSC Base Station Controller 基站控制器BSM Base Station Management 基站管理系统BSP Board Support Package 板支持包BSS Base Station System 基站系统BSSAP Base Station Subsystem Application Part 基站子系统应用部分BTM BTS Test Module BTS告警模块BTRX Backplane of TRX TRX框的背板BTS Base Transceiver System 基站收发信机BUSN Backplane of Universal Switching Network 通用业务网背板BWT Block Waiting Time 块等待时间CCA Certificate Authentication 证书认证CAA Capacity Allocation Acknowledgement 空量分配应答CAMEL Customized Application for Mobile network Enhanced Logic 用于移动网络增强逻辑定制的应用CAP CAMEL Application Part CAMEL应用部分C-APDU Command APDU 命令APDUCB Cell Broadcast 小区广播CBA IPI CMM-Based Appraisals for Internal Process Improvement 用于内部过程改进的基于CMM的评价CBR Constant Bit Rate 固定比特率CBS Cell Broadcast Service 小区广播业务CC Control Channel 控制信道CC/PP Composite Capability/Preference Profiles 合成能力/优先档案CCB Configuration Control Board 配置控制委员会CCBS Completion of Calls to Busy Subscriber 呼叫忙用户的完成CCCH Common Control Channel 公共控制信道CCF Call Control Function 呼叫控制功能CCH Control Channel 控制信道CCK Corporate Control Key 合并控制键CCM Communication Control Module 通信控制模块CCP Compression Control Protocol 压缩控制协议CCPCH Common Control Physical Channel 公共控制物理信道CCTrCH Coded Composite Transport Channel 编码合成传送信道CD Capacity Deallocation/Collision Detection 空量解除分配/冲突检测 CDA Capacity Deallocation Acknowledgement 容量解除分配的应答CDF Command Dispatch Functions 命令分发功能CDMA Code Division Multiple Access 码分多址CDR Call Detail Record 呼叫细节记录CDSU Channel/Data Service Unit 信道/数据服务单元CE Channel Element 信道单元CEB Channel Element Board 信道单元板CES Channel Element Subsystem 信道单元子系统CFN Connection Frame Number 连接帧号CGI Common Gateway Interface 公共网关接口CHAP Challenge Handshake Authentication Protocol 质询握手认证协议 CHM Channel Processing Module 信道处理模块CHM-1X Channel Processing Module for cdma2000 信道处理模块,采用CSM5000芯片,支持IS-2000空中接口标准CHM-95 Channel Processing Module for IS-95 信道处理模块,采用CSM1.5芯片,支持IS-95空中接口标准CHUB Control HUB 控制流集线器CIB Circuit-bearer Interface Board 电路承载通道接口板CIC Circle Identify Code 地面电路识别号CLA Class 级CLK Clock 时钟CLKD CLOCK Distributor 时钟分发驱动板CLKG CLOCKGenerator 时钟产生CLNP Connectionless network protocol 无连接网络协议CLNS Connectionless network service 无连接网络业务CM Configuration Management 配置管理CMB Combiner 合路器CMF Connection Monitor Function 连接监控功能CMIP Common Management Information Protocol 公共管理信息协议 CMIS Common Management Information Service 公共管理信息服务CMM Capability Maturity Model 能力成熟度模型CMU Carnegie-Mellon University 卡耐基&8226;梅隆大学CN Core Network 核心网CNAP Calling Name Presentation 主叫号码显示CNL Co-operative Network List 合作操作网络表COA Care-of-Address 转交地址COCOMO Constructive Cost Model 构造性成本模型CONS Connection-oriented network service 面向连接的网络业务CPCH Common Packet Channel 公共分组信道CPCS Common Part Convergence Sublayer 公共聚合子层部分CPICH Common Pilot Channel 公共导频信道CPM Calling Processing Module 呼叫处理模块CPP Core Processor Part 核心处理部分CPS Common Part Sublayer 公共子层部分 CPU Central Processing Unit 中心处理单元CR Change Request 变更请求CRC Cyclic Redundancy Check 循环冗余校验CRF Command Resolve Function 命令解析功能CRNC Controlling Radio Network Controller 主控无线器C-RNTI Cell Radio Network Temporary Identity 小区无线网络临时识别符CS Circuit Switched 电路交换CSCF Call Server Control Function 呼叫服务器控制功能CSE Camel Service Environment Camel 业务环境CS-GW Circuit Switched Gateway 电路交换网关CSM Cell Site Modem 基站调制解调器CSM5000 Cell Site Modem ASIC 5000 基站调制解调器专用芯片CSU/DSU Channel Service Unit/ Digital Service Unit 信道数据服务单元 CTCH Common Traffic Channel 公共业务信道CTDMA Code Time Division Multiple Access 码时分多址C-TPDU Command TPDU 命令TPDUCW Continuous Wave (unmodulated signal) 连续波(未调制信号)DD_K DBS Kernel Module 数据库核心模块D_M D_Method 数据库关系表方法模块D_S D_Service 数据库维护模块D_V D_View 数据库存取接口模块DAC Digital-to-Analog Converter 数-模转换器DAD Destination Adress 目的地址DAM DECT Authentication Module DECT鉴权模型DBS Database Subsystem 数据库子系统DC Dedicated Control (SAP) 专用控制(SAP)DCA Dynamic Channel Allocation 动态的信道分配DCCH Dedicated Control Channel 专用控制信道DCH Dedicated Channel 专用信道DDI Direct Dial In 直接拨号进DECT Digital Enhanced Cordless Telecommunications 数字增强无绳电信 DF Dedicated File 专用文件DHCP Dynamic Host Configuration Protocol 动态的宿主配置协议DHO Diversity Handover 分集切换DIF Data Intermediate Frequency Module 数字中频模块diff-serv Differentiated services 特殊的业务DIU Digital Interface Module 数字(中频)接口模块DL Downlink (Forward Link) 下行链路(前向链路)DLC Data Link Control 数据链路层控制DN Destination Network 目的网络DNS Directory Name Service 目录名称业务DO Data Object 数据对象DoD Department of Defense 美国国防部DOI Domain of Interpretation 解析域DP Defect Prevention 缺陷预防DPC Destination Point Code 目的地信令点编码DPCCH Dedicated Physical Control Channel 专用物理控制信道DPCH Dedicated Physical Channel 专用物理信道DPDCH Dedicated Physical Data Channel 专用物理数据信道DRAC Dynamic Resource Allocation Control 动态的资源分配控制DRC Data Rate Control 数据速率控制DRNC Drift Radio Network Controller 变动的无线网络控制器DRNS Drift RNS 变动的RNSDRX Discontinuous Reception 非连续接收DSA Digital Signature Algorithm 数字签名算法DS-CDMA Direct-Sequence Code Division Multiple Access 直扩-码分多址DSCH Downlink Shared Channel 下行共享信道DSM Data Service Module 数据服务模块DTB Digital Trunk Board 数字中继板DTCH Dedicated Traffic Channel 专用业务信道DTI Digital Trunk Interface Element 数字中继接口单元DTMF Dual Tone Multiple Frequency 多音频拨号音DTX Discontinuous Transmission 非连续传输DUP Duplexer 双工器EECTRA European Committee of Telecommunications Regulatory Affairs 欧洲电信常规事务委员会EDC Error Detection Code byte 检错码字节EDGE Enhanced Data rates for GSM Evolution GSM改进型的增强数据速率EF Elementary File 基本文件EFD Event Forwarding Discriminator 事件前转辨别器E-GGSN Enhanced GGSN 增强的GGSNEGPRS Enhanced GPRS 增强的GPRSEHB (Ethernet HUB Board)以太网共享式HUB板E-HLR Enhanced HLR 增强的HLREIRP Equivalent Isotropic Radiated Power 等效各向内性辐射功率EJB Enterprise Java Beans 企业Java组件模型EMC Electromagnetic Compatibility 电磁兼容性EMF Network Element Mediation Function 网元中介功能EMI Electromagnetic interference 电磁干扰EMS electromagnetic susceptibility 电磁敏感性ESB Ethernet Switch Board 以太网交换板ESD electrostatic discharge 静电放电ESP Encapsulating Security Payload 封装安全载荷ESU Extended subscriber unit 扩展用户单元ETSI European Telecommunications Standards Institute 欧洲电信标准研究院etu elementary time unit 基本时间单元EUT equipment under test 被试设备FF/R-CCCH Forward / Reverse Common Control Channel 前反向公共控制信道F/R-DSCH Forward/Reverse Dedicated Signal Channel 前反向专用信令信道F/R-DCCH Forward / Reverse Dedicated Control Channel 前反向专用控制信道F/R-FCH Forward / Reverse Fundamental Channel 前反向基本信道F/R-PICH Forward / Reverse Pilot Channel 前反向导频信道F/R-SCCH Forward / Reverse Supplemental Code Channel 前反向补充码信道F/R-SCH Forward / Reverse Supplemental Channel 前反向补充信道FA Foreign Agent 外地代理FAC Foreign Agent Challenge 外地代理质询FACH Forward Access Channel 前向业务信道F-APICH Dedicated Auxiliary Pilot Channel 前向专用辅助导频信道F-ATDPICH Auxiliary Transmit Diversity Pilot Channel 辅助发射分级导频信道FAUSCH Fast Uplink Signaling Channel 快速上行链路信令信道FAX Facsimile 传真F-BCCH Broadcast Control Channel 前向广播控制信道FBI Feedback Information 反馈信息F-CACH Common Assignment Channel 前向公共指配信道FCI File Control Information 文件控制信息FCP Flow Control Protocol 流量控制协议F-CPCCH Common Power Control Channel 前向公共功率控制信道FCS Frame Check Sequence 帧校验序列FD Full duplex 全双工FDD Frequency Division Duplex 频分双工FDMA Frequency Division Multiple Access 频分多址FE Front End 射频收发前端FEC Forward Error Correction 前向纠错FER Frame Erasure Rate/Frame Error Rate 误帧率FFS For Further Study 为进一步研究Flexible-Rate Flexible Data Rate 灵活的数据速率FLPC Forward Link Power Control 前向链路功率控制FM Fault Management 故障管理FN Frame Number 帧号FNUR Fixed Network User Rate 固定的网络用户速率FP Function Point 功能点F-PCH Paging Channel 前向寻呼信道F-QPCH Quick Paging Channel 前向快速寻呼信道FS Frequency Synthesizer 频率合成器FSB Frequency Synthesizer Board 频率合成板F-SYNCH Sync Channel 前向同步信道FTAM File Transfer Access Maintenance 文件传输存取维护FTB Fiber Transceiver Board 光纤收发板FTC Forward Traffic Channel 前向业务信道F-TDPICH Transmit Diversity Pilot Channel 前向发射分集导频信道FTP File Transfer Protocol 文件传输协议GGC General Control (SAP) 一般控制(SAP)GCM GPS Control Module GPS控制模块GID1 Group Identifier (level 1) 组识别符(级别1)GID2 Group Identifier (level 2) 组识别符(级别2) GLI GE Line Interface GE线接口GMSC Gateway MSC 网关MSCGMSK Gaussian Minimum Shift Keying 最小高斯移位键控GP Guard Period 保护时间GPCM General Purpose Chip-select Machine 通用片选状态机GPRS General Packet Radio Service 通用分组无线业务GPS GPS Timing Module 定时频率模块GPSR Global Position System Receiver 全球定位系统接收机GPSTM GPS Timing Module GPS定时模块GRE Generic Routing Encapsulation 通用路由封装GSM Globe System for Mobil Communication 全球移动通信系统GSN GPRS Support Nodes GPRS支持的节点GTP GPRS Tunneling Protocol GPRS隧道传输协议HHA Home Agent 归属代理HCS Hierarchical Cell Structure 分层小区结构H-CSCF Home CSCF 归属CSCSHDLC High-level data link control HDLC协议HDR High Data Rate 高速数据速率HE-VASP Home Environment Value Added Service Provider 归属环境的增值业务提供者HF Human Factors 人为因素HHO Hard Handover 硬切换HIRS High-speed Interconnect Router Subsystem 高速互连路由子系统 HLR Home Location Register 归属位置寄存器HN Home Network 归属网络HO Handover 切换HPA High Power Amplifier 高功放HPLMN Home Public Land Mobile Network 归属公共陆地移动网络HPS Handover Path Switching 切换路径交换HRPD High rate packet data 高速率分组数据HRR Handover Resource Reservation 切换资源预留HSCSD High Speed Circuit Switched Data 高束的电路交换数据HSS Home Subscriber Server 归属用户服务器HTTP Hyper Text Transfer Protocol 超文本传输协议HTTPS Hyper Text Transfer Protocol 安全的超文本传输协议HWB HW-signal process Board HW信号处理板II/O Input/Output 输入/输出IANA Internet Assigned Numbering Authority 互联网地址分配机构I-Block Information Block 信息块IC Intergroup Coordination 组间协调ICC Integrated Circuit Card 集成电路卡ICGW Incoming Call Gateway 呼入网关ID Identifier 识别符IDEAL Initiating-Diagnosing-Establishing-Acting-Leveraging 启动、诊断、建立、行动、推行IE Information Element 信息元素IEC International Electrotechnical Commission 国际电气委员会IETF Internet Engineering Task Force 互联网工程任务组IF Intermediate Frequency 中频IFS Information Field Sizes 信息域大小IFSC Information Field Size for the UICC UICC的信息域大小IFSD Information Field Size for the Terminal 终端的信息域大小IIC Integrated Circuit Interface Circuit 集成电路接口电路IKE Internet Key Exchange 互联网密钥交换IM Intermodulation 互调失真IMA Inverse Multiplexing on ATM ATM上的反向复用IMAB IMA Board IMA/ATM协议处理板IMEI International Mobile Equipment Identity 国际移动设备识别IMGI International mobile group identity 国际移动组织识别IMSI International Mobile Subscriber Identity 国际移动用户识别IMT-2000 International Mobile Telecommunications 2000 国际移动电信2000IMUN International Mobile User Number 国际移动用户号IN Intelligent Network 智能网INAP Intelligent Network Application Part 智能网应用部分INF INFormation field 信息域IP Internet Protocol Internet协议IPB IP Process Board IP处理板IPCP IP Control Protocol IP控制协议IP-M IP Multicast IP多址广播IPSec IP Security IP安全协议ISAKMP Internet Security Association and Key Management Protocol 互联网SA和密钥管理协议ISCP Interference Signal Code Power 干扰信号码功率ISDN Integrated Services Digital Network 集成业务数字网ISM Integrated Software Management 集成软件管理ISO International Standardization Organization 国际标准化组织ISP Internet Service Provider Internet业务提供商ISUP ISDN User Part ISDN用户部分ITU International Telecommunications Union 国际电信联盟IUI International USIM Identifier 国际USIM识别符IWFB InterWorking Function Board IWF(用于手机上网的辅助设备)背板 JJ2EE Java 2 Platform Enterprise Edition Java2平台企业板JAR file Java Archive File Java档案文件JD Joint Detection 联合检测JDMK Java Dynamic Management Kit Java动态管理开发包JMS Java Message Service Java消息服务JNDI Java Naming Directory Interface Java命名的目录接口JP Joint Predistortion 联合预失真JPEG Joint Photographic Experts Group 摄影专家联合小组JTAPI Java Telephony Application Programming Interface Java电话的应用程序接口JTS Java Transaction Service Java事务处理服务JVM Java Virtual Machine Java虚拟机Kkbps kilo-bits per second 每秒千比特KP Key Practice 关键实践KPA Key Process Area 关键过程域KSLOC Kilo Source Lines Of Code 千行源代码ksps kilo-symbols per second 每秒千符号LL1 Layer 1 (physical layer) 层1(物理层)L2 Layer 2 (data link layer) 层2(数据链路层)L3 Layer 3 (network layer) 层3(网络层)L3Addr Layer 3 Address 第三层地址LAC Link Access Control 链路接入控制LAI Location Area Identity 位置区域识别LAN Local Area Network 本地网LATA Local Access and Transport Area 本地接入和传送区域LCD Low Constrained Delay 低限制延迟LCF Link Control Function 连接控制功能LCP Link Control Protocol 链路控制协议LCS Location Services 定位业务LE Local Exchange 本地交换机LEN Length 长度LFM Local Fibre Module 近端光模块LLC Logical Link Control 逻辑链路控制LMF 本地管理功能LMT Local Management Terminal 本地维护终端LN Logical Name 逻辑名LNA Low Noise Amplifier 低噪声放大器LOMC Local OMC 本地操作维护中心LOS Line Of Sight 视距LPA Linear Power Amplifier 线性功放LPF Low Pass Filter 低通滤波器LRU Large Replacing Unite 较大可替代单元LSA Localised Service Area 本地化的业务区LSB Least Significant Bit 最低有效比特LTZ Local Time Zone 本地时区LUP Location Update Protocol 位置更新协议MM&C Monitor and Control 监控MA Multiple Access 多址MAC Message authentication code (encryption context) 消息鉴权码(保密)MAF Application Management Features 管理应用功能MAHO Mobile Assisted Handover 移动台协助的切换MAP Mobile Application Part 移动应用部分MC Message Center 短消息中心(SMC)MCC Mobile Country Code 移动国家码MCE Module Control Element 模块控制单元Mcps Mega-chips per second 每秒兆chipsMCU Media Control Unit 媒质控制单元MDIV Diversity 分集接收滤波器MDIV800 Micro Diversity 微基站800M分集接收滤波器 MDN Mobile Directory Number 移动用户号码簿号码MDS Multimedia Distribution Service 多媒体分布业务MDUP Duplex 双工器MDUP800 Micro Duplex 微基站800M双工器ME Mobile Equipment 移动设备MEHO Mobile evaluated handover 移动台估计的切换MER Message Error Rate 误消息率MExE Mobile station (application) Execution Environment 移动台(应用)执行环境MF Mediation Function 中介功能MGCF Media Gateway Control Function 媒质关卡控制功能MGCP Media Gateway Control Part 媒质关卡控制部分MGPS Micro GPS 微基站GPSMGT Mobile Global Title 移动全球称号MGW Media GateWay 媒质关卡MHEG Multimedia and Hypermedia Information Coding Expert Group 多媒体和超媒体信息编码专家组MHz Mega Hertz 兆赫兹MIB Management Information Base 管理信息库MIF Management Information Function 管理信息功能MIN Mobile Identification Number 移动台识别码MIP Mobil IP 移动IPMIPS Million Instructions Per Second 每秒百万次指令MIT MO Instance Tree MO实例树MLNA Micro Low Noise Amplifier 低噪声放大器MLNA800 Micro Low Noise Amplifier 微基站800MLNAMM Mobility Management 移动性管理MMI Man Machine Interface 人机接口MML Man Machine Language 人机语言MNC Mobile Network Code 移动网络码MNIC Multi-service Network Interface Card 多功能接口网板MNP Mobile Number Portability 移动号可携带性MO Mobile Originated 移动台启呼MOF MO administration Function MO管理功能MOHO Mobile Originated Handover 移动台启呼的切换MONB MONIOTR BOARD 监控板MOS Mean Opinion Score 平均意见分MPA Micro Power Amplifier 微基站功放MPA800 Micro Power Amplifier 微基站800M功放MPB Main Process Board 主处理板MPC8260 Motorola Power PC 8260 摩拖罗拉的CPUMPC860 Motorola的高性能的通讯处理器MPD Micro-BTS Power Distribution 微基站电源模块MPEG Moving Pictures Experts Group 移动图像专家组MPM MSC Processing Module MSC处理模块MRB Media Resource Board 媒体资源板MRF Media Resource Function 媒质资源功能MS Mobile Station 移动台MSB Most Significant Bit 最高有效比特MSC Mobile Switching Center 移动交换中心MSE MExE Service Environment MexE业务环境MSG Management Steering Group 管理指导组MSID Mobile Station Identifier 移动台识别符MSIN Mobile Station Identification Number 移动台识别号码MSM Message Switching Module 消息交换模块MSP Multiple Subscriber Profile 多用户档案MSU Main subscriber unit 主用户单元MT Mobile Termination 面向终端的移动MTBF 平均无故障时间间隔MTP Message Transfer Part 消息传递部分MTP3-B Message Transfer Part level 3 消息传递部分级别3MTRX800 Micro Transmitter & Receiver 微基站800M收发信机MTSI Master To Slave Interface 主备用接口MUI Mobile User Identifier 移动用户识别符NNAD Node Address byte 节点地址字节NAI Network Access Identifier 网络接入标识NAS Non-Access Stratum 非接入层NBAPNBAP Node B Application Part Node B应用部分NCK Network Control Key 网络控制键NCM Network Control Module 网络控制模块NDC National Destination Code 国际目的码NDUB Network Determined User Busy 网络用户忙NE Network Element 网元。
粒子群优化算法PSO介绍中英文翻译word版

粒子群优化算法(PSO)介绍在频谱资源日趋紧张的今天,想要通过增加频谱宽度来提高系统容量的方式已经很难实现;同时,想在时域、频域或码域进一步提高系统容量已经十分困难。
在这种情形下,人们把目光投向了空域,期望能够从中寻觅新的源泉。
随着人们对于无线移动通信的要求愈来愈高,专门是对高速多媒体传输的迫切需求,与之相关能够提高系统容量的技术也开始受到人们的特别重视。
20世纪90年代以来,对于群体智能的研究逐渐兴起。
Eberhart和Kennedy于1995年提出的粒子群优化算法(PSO),作为一种简单有效的优化算法迅速在各个领域取得了普遍的应用。
PSO算法的思想来源是鸟群在觅食进程中表现的群体智慧。
通常单个自然生物并非是智能的,可是整个生物群体却表现出处置复杂问题的能力,这就是群体智能。
各类生物聚集成生物种群,都有其内在行为规律,而人类作为高级生物,研究并掌握了这种规律,模拟设计出各类优化算法并运用于各类问题。
类似的还有按照生物繁衍特性产生的遗传算法,对蚂蚁群落食物收集进程的模拟产生的蚁群算法。
PSO算法目前已经普遍用于函数优化、神经网络训练、模糊系统控制和其他遗传算法涉及到的应用领域。
PSO算法较之其他的优化算法实现简单,也没有许多参数需要调整。
可是它也有着收敛过快、易收敛于局部极值的现象,专门是面对高维复杂的问题时如阵列天线方向图综合问题。
人们提出了很多的改良算法,来提高PSO算法的性能。
惯性权重和紧缩因子是目前应用比较普遍的对大体粒子群算法的改良,能够改善优化性能可是收敛较慢。
文献中将粒子群算法和遗传算法在方向图综合上的应用做了比较,能够看出粒子群算法较之遗传算法有计算量小易于实现等特点,但也能够看到大体的PSO算法和遗传算法的收敛速度都不快或往往在某个局部极值停滞太久很难跳出。
粒子群优化算法(PSO粒子群优化(PSO:Particle Swarm Optimization))是一种进化计算技术(evolutionary computation)是一种有效的全局优化技术,有Eberhart 博士和kennedy博士发明。
5G系统架构介绍

GTP-U UDP
IP Data link layer Physical layer
用户面
CP: S1控制平面接口位于E-NodeB和MME之间,
传输网络层是利用IP传输,这点类似于用户 平面;为了可靠的传输信令消息,在IP曾之 上添加了SCTP;应用层的信令协议为S1AP
S1-AP
SCTP IP
Non-4GPP IP Accesse
S-GW – P-GW
接口功能 采用GTP协议,在MME和GW设备间建立隧道,传送 信令 采用GTP协议,在MME和SGSN设备间建立隧道,传 送信令 采用GTP协议,在S-GW和SGSN设备间建立隧道,传 送数据和信令 完成用户位置信息的交换和用户签约信息的管理
Inter Cell RRM
RB Control
●
Connection Mobility Cont.
Radio Admission Control
eNB Measurement Configuration & Provision
Dynamic Resource Allocation (Scheduler)
SAE-GW: SGW+PGW
SGi
●
S6d HSS
S6a
PCRF Gx
PGW
S2a/c S2b
ePDG
Non 4GPP Access Network
S4
SGW
S10x
SGSN
S3
S11 MME
S5 (GTP)
S10x
Mobility based on MIP
EPC
BSC
S10 RNC
S1-MME
S1-U
S4
人工智能对环境影响英语作文

人工智能对环境影响英语作文Artificial Intelligence and Its Environmental ImpactThe rapid advancement of artificial intelligence (AI) has brought about numerous benefits to society, revolutionizing various industries and transforming our daily lives. However, the environmental impact of this technological revolution has become a growing concern, as the development and implementation of AI systems can have significant consequences on our planet. In this essay, we will explore the multifaceted relationship between artificial intelligence and the environment, examining both the potential benefits and the potential drawbacks.One of the primary ways in which AI can positively impact the environment is through its ability to optimize resource utilization and improve energy efficiency. AI-powered systems can analyze vast amounts of data, identify patterns, and make informed decisions that minimize waste and reduce energy consumption. For instance, AI-enabled smart grids can optimize the distribution of electricity, reducing energy losses and ensuring more efficient use of renewable energy sources. Similarly, AI-powered logistics and transportation systems can optimize routing and scheduling, leading to reducedfuel consumption and lower carbon emissions.Furthermore, AI can play a crucial role in environmental monitoring and conservation efforts. AI-powered sensors and satellite imagery can be used to detect and track environmental changes, such as deforestation, habitat loss, and the spread of invasive species. This information can then be used by policymakers and conservation organizations to implement targeted interventions and develop more effective strategies for protecting the environment. Additionally, AI-powered simulations and predictive models can help researchers and decision-makers better understand complex environmental systems and make more informed decisions.However, the environmental impact of AI is not limited to its potential benefits. The development and deployment of AI systems can also have significant negative consequences, particularly in terms of energy consumption and resource usage. The training and operation of AI models, especially those based on deep learning, can be highly energy-intensive, requiring vast amounts of computing power and generating significant greenhouse gas emissions. As the demand for AI-powered applications continues to grow, the energy footprint of these systems could become a significant contributor to global climate change.Moreover, the manufacture and disposal of the hardware requiredfor AI systems can also have a significant environmental impact. The extraction of raw materials, the production of electronic components, and the disposal of e-waste can all contribute to environmental degradation, pollution, and the depletion of natural resources. This issue is particularly pressing as the rapid pace of technological change often leads to the premature obsolescence of AI hardware, further exacerbating the problem of e-waste.To mitigate the environmental impact of artificial intelligence, a multifaceted approach is necessary. Researchers and developers must prioritize the development of energy-efficient AI systems, exploring ways to reduce the energy consumption of training and deployment processes. This may involve the use of more efficient hardware, the optimization of algorithms, and the incorporation of renewable energy sources into the infrastructure supporting AI systems.Additionally, the life cycle of AI hardware must be addressed, with a focus on sustainable design, responsible sourcing of materials, and the implementation of comprehensive recycling and disposal programs. Governments and policymakers can play a crucial role in this regard, by implementing regulations and incentives that encourage the development of environmentally-friendly AI technologies and the responsible management of AI-related waste.Furthermore, the integration of AI with other emerging technologies, such as renewable energy, smart city infrastructure, and sustainable agriculture, can amplify the positive environmental impact of artificial intelligence. By leveraging the power of AI to optimize these systems, we can unlock new opportunities for environmental conservation and sustainable development.In conclusion, the relationship between artificial intelligence and the environment is a complex and multifaceted one. While AI has the potential to significantly contribute to environmental protection and sustainability, its development and deployment must be carefully managed to mitigate the potential negative consequences. By prioritizing energy efficiency, responsible hardware management, and the strategic integration of AI with other sustainable technologies, we can harness the power of artificial intelligence to create a more environmentally-conscious future. As we continue to advance in the field of AI, it is crucial that we remain mindful of its environmental impact and work towards creating a harmonious balance between technological progress and environmental stewardship.。
Research Summary

Research SummarySandeep K.S.Gupta1Research Accomplishments in Wireless Networks and Mobile Computing The combination of wireless communication infrastructure and portable computing devices has laid the foundation for a new network computing paradigm,called mobile computing,which permits access to information and collaboration with others while on the move[30].Wireless mobile networks are characterized by severe constraints on resources, such as bandwidth and battery power,and by rapidfluctuations in availability of these resources;this makes it difficult for the system software to provide guaranteed quality-of-service at levels required by many distributed and collabora-tive applications.Further,mobility adds a new dimension to the distributed computing paradigm which has implications for specification,design,verification,and implementation of both system and application software[41].A challeng-ing issue is to determine the interface and the guarantees that system software can efficiently provide to developers of both location-independent and location-dependent(context-aware)[47]applications on mobile networks[42].This has resulted in research on adaptive applications and system software which can gracefully respond to changes in oper-ating conditions[4].My current research is focused on developing adaptive solutions for resource allocation,location management,unicast and multicast routing protocols and caching schemes in wireless networks for supporting mobile computing.1.1Adaptive Unicast and Multicast Protocols for Mobile Ad Hoc NetworksA mobile ad hoc network consists of mobile computing devices with radio transmission and reception capability.Two node are neighbors in the network and can communicate directly when they are within transmission range of each other and radio propagation condition in the vicinity of these nodes is munication between non-neighboring nodes requires a multi-hop routing protocol.Although mobile ad hoc networks have been mainly used in military ap-plications,they are being increasingly used for civilian applications such as virtual class rooms,wireless local area networks,and law enforcement.It is predicted that in the future such ad hoc networks in collaboration with cellular and overlay networks will provide a ubiquitous computing environment[56].Design and development of commu-nication support for distributed and collaborative applications on mobile ad hoc networks is the current emphasis of my research.The motivation for this work stems from the challenges mobile ad hoc networks pose for supporting the reliable and efficient communication services necessary for distributed computing[43,24].Mobile ad hoc networks present a different network model from the ones used for traditional communication protocol design and implementa-tion.The topology of the network changes with node movements,variations in the radio propagation conditions,and depletion of battery power of the nodes.The rate of topological changes can be different at different times,as well as in different regions of the network.The network can experience frequent network partitioning and may require reconfig-uration of partitioned subnetworks.Moreover,radio bandwidth is a comparatively precious resource and needs to be conserved.Since this dynamic network model is considerably different from that of the current static network model used for developing communication protocols,it is necessary to investigate the appropriateness of existing protocols and develop efficient,reliable,and scalable collective communication protocols for mobile ad hoc networks.In our work,we have defined a mobility-tolerant communication protocol[26]to be one which can function cor-rectly in the presence of transient failures due to mobility of hosts in the network.Development of efficient and scalable mobility-tolerant protocols for group communication is one of my major research thrust.The goal is to develop group communication protocols for one-to-many and many-to-many interaction patterns which adapt to the rate of change of mobility,distribution(spread)and size of the group,and size of the network.We are developing efficient protocolswhich maintain minimal state information,use a minimal number of control messages,react to topological changes only when necessary,and localize the reaction to the neighborhood of the topology change.We aim to provide solutions to the following questions:What guarantees/interface group communication services on mobile ad hoc networks should provide to the tra-ditional and emerging distributed and collaborative applications?How can these group communication services be efficiently implemented in a mobility-tolerant manner on mo-bile ad hoc networks using the underlying point-to-point(unicast)routing and data link layer support?How to characterize the performance of a mobility-tolerant protocol through analysis and simulation?1.1.1Adaptive Protocol for Reliable Multicast[24,28]In this work,we have developed a multicast protocol which combines the advantages of multicast protocol presented by Gerla et.al[5]and by Pagani and Rossi[43].This protocol uses core-based tree(CBT)and incorporates mechanisms for gluing together fragments of this tree when it gets fragmented due to movement of A graph-theoretic notion of for-warding region is introduced which is used to glue together fragments of a multicast trees.The gluing process involves flooding of the forwarding region of only those nodes that witness topology change due to node mobility.Delivery of multicast messages to mobile nodes is expedited through(i)pushing of the message by witness nodes in their forward-ing regions and(ii)pulling of messages by a mobile node during(re)joining process.Hence,the protocol conserves network bandwidth by using a combination of the push-pull approach and by restrictingflooding only to the essential parts of the network that is affected by topology change.We have developed a theoretical model to compute the proba-bility of packet loss(as a function of the mobility rate)for our proposed scheme compared to the the CBT protocol;we have also evaluated the effectiveness of forwarding regions as compared to traditionalflooding.Our analysis shows that the proposed scheme significantly outperforms CBT.1.1.2Self-Stabilizing Multicast Communication Protocols[27,26,7]We are currently applying the paradigm of self-stabilization in distributed fault tolerant algorithm design to tackle the problem of topology change in mobile networks.Self-stabilizing distributed algorithms converge to a global legiti-mate state in presence of any number of intermittent faults while using only local knowledge for actions at each node. Hence,self-stabilizing protocols provide means for tolerating transient faults.However,self-stabilizing protocols pro-vide a non-masking approach to fault tolerance.The service provided by a self-stabilizing protocol may be unavailable while it is stabilizing.Further,the self-stabilizing protocols only guarantee that the protocol will eventually stabilize. Hence,providing no guarantee on how soon the service will become available after the occurrence of faults.These two features of self-stabilizing protocols present many interesting challenges in employing self-stabilizing protocols in mobile ad hoc networks;some of which are i)how can the self-stabilizing protocols be enhanced so that the service remains available while the multi-cast tree is being adapted to the new topology?and ii)how can the self-stabilization protocol be triggered in a controlled manner so as to not overwhelm the system in presence of high mobility?Efficient solutions for performing multi-casting in mobile ad hoc networks will rely on what support underlying data link layer can provide and how the network layer multi-cast protocol can exploit these facilities to intelligently control the overheads while providing desirable QoS.Our goal is to take a synergistic approach in designing the multi-cast protocols so as to make them compatible with the underlying networking layers.In our preliminary work,we have adapted two self-stabilizing protocol for maintaining multicast tree in a mobile ad hoc networks.Thefirst is based on pruning and rooting a minimum spanning tree[27,26]and the other one is based on pruning and rooting a shortest-path tree[7].This work is supported by a grant from NSF.Under this grant we will develop adaptive multi-cast protocols for mobile ad hoc networks with different performance/cost tradeoffs.1.1.3Witness-Aided Routing(WAR)Protocol[1,2]Host mobility and higher link instability are the most prominent factors which affect the performance of routing pro-tocols for ad hoc networks.Unlike proactive protocols,which attempt to reduce the effect of mobility by periodically upgrading routing information(at the expense of network resources),reactive-style protocols are more prone to routingfailures due to the lack of up to date information about network topology.Furthermore,end-to-end guarantees are more difficult to obtain as the network size increases,which hints that end-to-end error recovery may not be a feasible idea for large networks.Further,mobile ad hoc networks may exhibit unidirectional links due to the nature of wireless com-munication.Presence of unidirectional links interferes with the controlflow of many existing unicast routing protocols for such networks,which adversely effects their performance and limits their applicability.We have developed a new protocol designed to support unicast routing over both bidirectional and unidirectional links in ad hoc networks.The WAR(Witness-Aided Routing)protocol is a reactive routing protocol.It is based on the concept of witness host,whose role is to help in bypassing a unidirectional or a failed link along the path.Hence,WAR uses local error recovery as opposed to end-to-end error recovery used by other reactive protocol such as Dynamic Source Routing(DSR)protocol.We have analytically compared the effect of local error recovery vs.end-to-end error recovery in reactive protocols.Our results show that the performance of DSR degrades extremely fast as the route length increases(that is,DSR is not scalable),while WAR maintains both low latency and low resource consumption regardless of the route length.1.2Adaptive Channel Allocation for Wireless Networks[25,29,31]A problem related to efficiently performing communication in mobile networks is the problem of channel(bandwidth) allocation.Channel allocation is needed for supporting connection-oriented traffic.Along with Pradip Srimani,I have developed a distributed and dynamic channel allocation techniques which combines the previously known basic search and basic update scheme[25,29].We have developed another channel allocation scheme[31].This scheme combines the static and dynamic scheme to further minimize the channel allocation time as well as maintain the advantage of dis-tributed dynamic allocation.In this scheme,each node(cell)in the system continually monitors its own load(rate of request of channels)and switches back and forth between static(fixed channel allocation scheme)and dynamic(search-based or update-based)modes of allocation depending upon threshold values of loads.The threshold values are used tofine-tune the overall system performance.Each node adapts to its own load independent of other nodes in its inter-ference region.1.3Adaptive Location Management[53,54]Location management is an essential service in mobile networks.It provides mechanisms for recording and querying location of mobile units in the network.This is needed for establishing calls or delivering messages to mobile units.In personal communication service(PCS)networks,location management protocols such as IS-41and GSM use statically defined Registration Areas(RAs).Each RA consists of all the communication cells in its geographical area.Associ-ated with each RA is a database called Location Registrar.Further,each mobile unit has a pre-assigned Home Location Registrar(HLR).A mobile unit informs its location(location update operation)whenever it moves from one communi-cation cell to another.When the move results in move from one registration area to another updates are made to home location registrar.In order to locate a mobile unit the initiator of the call or(sender of the message)first contacts the HLR of the destination mobile unit to know its current location(registration area).Location Management based on statically defined registration areas is unable to adapt to changing mobility and call patterns of the users.We developed an extension to PCS location management protocol which uses dynamically overlapped registration areas.Overlapping of registration areas helps in reducing the number of location updates for afixed mobility pattern. Further,dynamically changing the registration area is used to adapt to changes in aggregate mobility and call pattern. This reduces and balances the signaling and database access load on the mobile services stations(MSS).In order to study the adaptiveness of the proposed scheme,we have simulated our scheme under various mobility and call patterns. Our simulation results show that by dynamically adapting the registration areas to aggregate mobility and call pattern of the mobile units is useful when the mobility pattern exhibit locality.For such mobility and call patterns,the proposed scheme can greatly reduce the average signaling and database access load on MSSs.Further,the cost of adapting the registration areas is shown to be low in terms of memory and communication requirements.1.4Efficient Cache Management Scheme[32,33]Caching data at the mobile hosts(MHs)in a wireless network helps alleviate problems associated with slow,limited bandwidth wireless links,by reducing latency and conserving bandwidth.Battery power is conserved by reducing the number of up-link requests.A mobile computing environment is a distributed system,thus when data at the server changes,the client hosts must be made aware of this fact in order for them to invalidate their cache otherwise the host would continue to answer queries with the cached values returning incorrect data.The nature of the physical medium coupled with the fact that disconnections from the network are very frequent in mobile computing environments de-mand a cache invalidation strategy with minimum possible overheads.We have developed a new cache maintenance scheme,called AS.The objective of the proposed scheme is to min-imize the overhead for the MHs to validate their cache upon reconnection,to allow stateless servers,and to minimize the bandwidth requirement.The general approach is i)to use asynchronous invalidation messages,and ii)to buffer invalidation messages from servers at the MH’s Home Location Cache(HLC)while the MH is disconnected from the network and re-deliver these invalidation messages to the MH when it gets reconnected to the e of asyn-chronous invalidation messages minimizes access latency,buffering of invalidation messages minimizes the overhead of validating MH’s cache after each disconnection and use of HLC off-loads the overhead of maintaining state of MH’s cache from the servers.The MH can be disconnected from the server either voluntarily(e.g.switching off the laptop) or involuntarily(e.g.wireless link failure,handoff delay);we capture the effects of both by using a single parameter s:the percentage of time a mobile host is disconnected from the network.We have demonstrated the efficiency of our scheme through simulation and performance modeling.In particular, we have shown that the average data access latency and the number of up-link requests by a MH decrease by using the proposed strategy at the cost of using buffer space at the HLC.We have compared our AS scheme with other caching schemes such as Barbara and Imilienski’s TS and AT scheme[3]in terms of performance metrics like latency,number of up-link requests etc.under both high and low rate of change of data at servers for various values of the parameter. We have also developed a mathematical model for the scheme which matches closely with the simulation results. 1.5Performance Evaluation of IEEE802.11MAC Protocol[35,36]With the standardization of IEEE802.11Wireless Local Area Network(WLAN)protocol specification,WLANs are becoming increasingly popular.The problem of hidden terminals in presence of obstacles and client mobility is unique to wireless networks and it is essential to study their effects on network performance.In this paper we investigate the performance of IEEE802.11wireless local area network(WLAN)protocol in the presence of mobile and hidden terminals.In order to study the joint effect of hidden terminals and user mobility on the performance of IEEE802.11 DCF,we have extended Tobagi and Kleinrock’s[48]hearing graph framework to model hidden terminals in a static environment.We derive a combined mobility and hidden terminal model using a Markov chain from the hearing graph of a given physical layout.The simple model uses two parameters:,which controls the number of hidden terminals in the steady state,and,which controls the rate of mobility of each terminal.By varying the values of and we can systematically generate scenario with different number of hidden terminals and different mobility rates for a particular physical layout with static obstructions.We have developed a discrete event simulator which uses the parameterized model to obtain the throughput and blocking probability behavior of an IEEE802.11based ad hoc network in the presence of certain static obstructions. Our simulations suggest that the IEEE802.11protocol is robust enough to handle moderate conditions of hidden termi-nals and mobility,but the performance may degrade under extreme conditions.Carefully selecting protocol parameters (RTS and Fragmentation Threshold)can help improve the performance even under extreme conditions.2Other Research Accomplishments2.1SSA-based Flow-Sensitive Type Analysis Technique for Object-Oriented Programs[37,38]An important step in compile-time optimization of object-oriented languages with polymorphic and virtual functions is static determination of concrete types(classes)of variables referring to objects.This information is essential for iden-tifying monomorphic call sites and hence opening opportunities for interprocedural optimizations.We have developed an SSA based interprocedural static type analysis algorithm,which combines constant propagation and type propaga-tion.This algorithm enhances Wegman and Zadeck’s[55]sparse conditional constant propagation(SCC)algorithm to perform simultaneous type analysis on a modified-SSA representation of a object-oriented program.Due to synergy between constant and types propagation,the proposed algorithm detects more constants and provides more precise type information than the case wherein the two analysis are performed separately.The worst-case behavior of this algorithm is polynomial in the number of classes declared in the program.To show empirically that our algorithm can improve the run-time performance of object-oriented programs,we have performed some experimental tests using Bench++ benchmark tool from AT&T Research Labs.These tests have shown that combined type and constant propagation is beneficial in codes with control dependent instantiations.2.2Optimizing Object-Oriented Programs for EPIC Architectures[44,45,46]The direct costs of virtual function calls in object-oriented programs is a runtime overhead incurred by the number of operations required to compute a target function address and the time to perform these operations.We have been look-ing into ways of exploiting EPIC technology to benefit object-oriented programs.This research has primarily focused on virtual function calls,and how their costs can be reduced by use of EPIC features.A number of innovative ways have been proposed that transform the dynamic dispatch sequence of a virtual function call into a stream-lined virtual function call,or into a statically-bound function call.These transformations rely on static analysis techniques such as type and constant propagation or class hierarchy analysis,along with front-end optimizations such as statically-binding virtual function calls that are monomorphic or with runtime class testing,and then using back-end optimizations that utilize control speculation,data speculation,predication and an exposed memory hierarchy.In particular we have developed two techniques:i)Predicated VFT Loading and ii)Predicated Class Testing that use an Explicit Parallel Instruction Computing(EPIC)architectural feature known as predication,to reduce the direct cost of virtual function calls.These techniques employ predication to conditionally perform cost-saving transforma-tions to the original dispatch sequence of a virtual function call in order to reduce the memory latency associated with these calls,or to transform the virtual function calls into statically-bound function calls.Predicated VFT loading is based on the possibility that the same virtual function table(VFT)will be shared between several virtual function calls, and whereby exploits this possibility by interleaving the function calls for objects whose types cannot be determined statically.Runtime class testing is a technique whereby virtual function calls are transformed into statically-bound function calls through a series of conditional branches.Through this transformation,the overhead of virtual function calls can be significantly reduced.However,the drawback of these tests is that by relying on conditional branches,the amount of instruction-level parallelism(ILP)is limited and the mispredict penalties can be relatively high.Predicated class testing improves the benefits of class testing by eliminating these drawbacks of runtime class testing.By use of the Trimaran research tool and analytical cost models,this research has successfully shown the quantitative benefits of applying EPIC technology towards object-oriented programs.This research has been performed in conjunction with the VLSI Technology Center at Hewlett-Packard.2.3Compilation and Program SynthesisMy early work was on compilation and synthesis of programs for distributed memory machines[13,12,8,9,14,10, 15,11].One of the goal of this project was to develop a tool for designing efficient algorithms for computing Fouriertransforms on different parallel machines.In this project,I worked with my Ph.D.advisors Prof.C.-H.Huang and Prof.P.Sadayappan(from Ohio State University),Prof.R.W.Johnson(from St.Cloud State University),and some other graduate students.This work resulted in a parallel programming tool called EXTENT(EXpert system for TENsor product Translation)[6].My contribution to this project was to develop program synthesis techniques for distributed-memory machines from a mathematical representation of the computation.The mathematical representation consisted of tensor product and other matrix operations.We looked at two approaches to program synthesis:i)using point-to-point communication and ii)using data redistributions.The problem of efficiently performing data redistribution is a specific case of a more general problem of how to generate communication-efficient code for array expressions in-volving distributed arrays.This problem arises in compilation of programs expressed in languages such as HPF(High-Performance Fortran).We developed compilation schemes for efficient execution of array expressions on distributed-memory machines[16,17,15].After completing my Ph.D.at Ohio State University in1995,I continued working on the problem of program synthesis as a Post Doctoral student under the guidance of Professor Reif at Duke University.Here I worked with Prof. Reif and his Ph.D.student,Zhiyong Li,on the problem of extending my Ph.D.work on synthesizing communication-efficient programs to synthesize I/O-efficient programs for parallel I/O system[20,39,40].In the fall of1995I joined Ohio University as a Visiting Assistant Professor.At Ohio University,I worked with Sudha Krishnamurthy,who was doing Masters under my supervision,on the problem of statically determining the data distributions which are suitable for global array in an HPF-like program.We developed an interprocedural technique which extended the work by Kennedy and Kremer[34]on intra-procedural data distribution analysis[18,19].2.4Collective Communication on K-ary N-cubesAll-to-all personalized communication pattern(plete-exchange)is the most dense communication pattern among various communication patterns which arise in the implementation of various applications on distributed mem-ory machines.I along with Yu-chee Tseng,who was my colleague at Ohio State University,developed a direct(i.e. without message combining)complete-exchange protocol for wormhole routed multidimensional torus networks.Our algorithm used optimal number of contention-free communication phases[49,50].The algorithm used the property that a2D torus network can be viewed as a cross product graph of two rings.Wefirst developed an optimal complete exchange communication schedule for a ring and then extended it to a tours network by using a notion of cross product of communication ter in collaboration with Dhableshwar Panda(a faculty at Ohio State University),we developed indirect complete exchange algorithms for wormhole routed2D and3D networks[51,52].Besides communication protocols for torus networks,I have also done some work on barrier synchronization al-gorithms for k-ary n-cubes[21]and processor allocation for torus connected multiprocessor systems[22,23]. References[1]I.D.Aron and S.K.S.Gupta.A witness-aided routing protocol for mobile ad hoc networks with unidirectionallinks.In H.V.Leong,W.-C.Lee,B.Li,and L.Yin,editors,Proc.of First Int’l Conference on Mobile Data Access (Lecture Notes in Computer Science LNCS1748),Dec.1999.[2]I.D.Aron and S.K.S.Gupta.Analytical comparision of local and end-to-end error recovery in reactive rout-ing protocols for mobile ad hoc networks.In Proc.4th Int’l Workshop on Modeling Analysis and Simulation of Wireless and Mobile Systems(MSWiM’00),Aug.2000.[3]D.Barbara and T.Imielinski.Sleepers and Workaholics:Caching Strategies in Mobile Environments.Very LargeDatabases Journal,Dec.1995.[4]V.Bharghavan.Challenges and solutions to adaptive computing and seamless mobility over heterogeneous wire-less networks.International Journal on Wireless Personal Communications:Special Issue on Mobile Wireless Networking,Mar.1997.[5]C.C.Chiang and M.Gerla.Routing and multicast in multihop,mobile wireless networks.In Proceedings ofICUPC’97,Oct.1997.[6]D.L.Dai,S.K.S.Gupta,S.D.Kaushik,J.H.Lu,R.V.Singh,C.-H.Huang,P.Sadayappan,and R.W.John-son.EXTENT:A portable programming environment for designing and implementing high-performance block-recursive algorithms.In Supercomputing’94,pages49–58,1994.[7]S.K.S.Gupta,A.Bouabdallah,and P.K.Srimani.Self-stabilizing protocol for shortest-path tree for multicastrouting in mobile ad hoc networks.In Proc.EuroPar2000,Apr.2000.[8]S.K.S.Gupta,C.-H.Huang,P.Sadayappan,and R.W.Johnson.On the synthesis of parallel programs fromtensor product formulas for block recursive algorithms.In U.Banerjee,D.Gelernter,A.Nicolau,and D.Padua, editors,Conf.Rec.5th Int’l Workshop on Languages and Compilers for Parallel Computing,volume757of LNCS, chapter17,pages264–280.Springer Verlang,1993.[9]S.K.S.Gupta,C.-H.Huang,P.Sadayappan,and R.W.Johnson.Programming FFT in High Performance Fortran.In Proc.Int’l Conf.on Parallel and Distributed Systems,pages284–289,1993.[10]S.K.S.Gupta,C.-H.Huang,P.Sadayappan,and R.W.Johnson.A framework for generating distributed-memoryparallel programs for block recursive algorithms.J.Parallel and Distributed Computing,34(2):137–153,May 1996.[11]S.K.S.Gupta,C.-H.Huang,P.Sadayappan,and R.W.Johnson.A technique for overlapping computation andcommunication for block-recursive algorithms.Concurrency:Practice And Experience,10(2):73–90,Feb.1998.[12]S.K.S.Gupta,S.D.Kaushik,C.-H.Huang,J.R.Johnson,R.W.Johnson,and P.Sadayappan.A methodologyfor the generation of data distributions to optimize communication.In Fourth IEEE Symposium on Parallel and Distributed Processing,pages436–441,Dec.1992.[13]S.K.S.Gupta,S.D.Kaushik,C.-H.Huang,J.R.Johnson,R.W.Johnson,and P.Sadayappan.Towards automaticderivation of data distributions from tensor product formulas.In Proc.3rd Workshop on Compilers for Parallel Computers,pages372–392,Vienna,Austria,July1992.[14]S.K.S.Gupta,S.D.Kaushik,C.-H.Huang,J.R.Johnson,R.W.Johnson,and P.Sadayappan.A methodologyfor the generation of data distributions to optimize communication.ACM SIGPLAN Notices,Proc.of Workshop on Langauges,Compilers,and Run-time Environments for Distributed-Memory Multiprocessors,28(1):82–82, 1993.[15]S.K.S.Gupta,S.D.Kaushik,C.-H.Huang,and piling array expressions for efficient exe-cution on distributed-memory machines.J.Parallel and Distributed Computing,32(2):155–172,1996. [16]S.K.S.Gupta,S.D.Kaushik,S.Mufti,S.Sharma,C.-H.Huang,J.R.Johnson,R.W.Johnson,and P.Sadayappan.On the generation of efficient data communication for distributed-memory machines.In Proc.Int’l Computing Symposium,Taiwan,pages504–513,1992.Techinal Report OSU-CIS-RC-5/92-TR13,Dept.of Computer and Information Science,The Ohio State University,May1992.[17]S.K.S.Gupta,S.D.Kaushik,S.Mufti,S.Sharma,C.-H.Huang,and P.Sadayappan.On compiling array expres-sions for efficient execution on distributed-memory machines.In Proc.Int’l Conf.Parallel Processing,volume II, pages301–305,1993.[18]S.K.S.Gupta and S.Krishnamurthy.An interprocedural framework for determining efficient data redistributionsin distributed memory machines.In Proc.6th Symp.on the Frontiers of Massively Parallel Computation,pages 223–240,Annapolis,Maryland,1996.[19]S.K.S.Gupta and S.Krishnamurthy.An interprocedural framework for determining array data redistribution.J.Information Science and Engineering,Special Issue on Compiler Techniques for High-Performance Computing, 14(1):27–51,Mar.1998.。
人工智能赋能高质量发展的实践路径

人工智能赋能高质量发展的实践路径The practice of enabling high-quality development through artificial intelligenceArtificial intelligence (AI) has emerged as a transformational technology that has the potential togreatly impact various industries and sectors. From healthcare, finance, and transportation to education, AI is being increasingly utilized to drive efficiency, enhance decision-making processes, and improve overall productivity. In order to harness the full potential of AI and ensurehigh-quality development, it is essential to follow a practical pathway of implementation.人工智能(AI)已经成为一种具有重大影响的革命性技术,有潜力在各个行业和领域产生巨大的影响。
从医疗保健、金融和交通运输到教育,越来越多地利用人工智能来推动效率提升、增强决策过程并改进整体生产力。
为了充分发挥人工智能的潜力并确保高质量发展,必须遵循实际可行的实施路径。
Firstly, organizations need to have a clear understandingof their needs and goals before implementing AI solutions. This involves conducting thorough assessments of existing processes, identifying areas that can benefit from AI integration, and defining specific objectives to be achieved through its implementation.在实施人工智能解决方案之前,组织需要明确自身的需求和目标。
人工智能对社会的影响及未来发展趋势英语作文范文

人工智能对社会的影响及未来发展趋势英语作文范文Artificial intelligence (AI) has been transformingsociety in myriad ways, and its impact will only continue to grow in the future. This essay aims to discuss the societal implications of AI and delve into the future trends of its development.One significant effect of AI on society is the automation of various industries and job sectors. As AI becomes more advanced, it has the potential to replace human workers injobs that are repetitive or require basic skills. For example, in manufacturing, robots can perform tasks with moreprecision and efficiency than humans. While this automation improves productivity and reduces costs for businesses, italso raises concerns about unemployment rates and income inequality. Consequently, societies must adapt by providingretraining programs and fostering the growth of new industries to support displaced workers.Another aspect of AI's influence on society is its ethical implications. As AI systems become more autonomous and capable of decision-making, questions arise about the accountability and responsibility for their actions. For instance, autonomous vehicles need to make split-second decisions that may impact human lives. Determining the moral framework that AI should follow in these situations is a complex and ongoing challenge. Society must establish robust regulations and ethical guidelines to ensure that AI systems operate in a manner that aligns with human values and interests.AI also holds promise in improving healthcare outcomes and revolutionizing medical diagnosis and treatment. Machine learning algorithms can analyze vast amounts of patient data to identify patterns and predict diseases. This earlydetection can lead to more effective treatments andultimately save lives. Additionally, AI-powered roboticsurgery systems enable surgeons to perform intricate procedures with greater precision. However, concerns relatedto privacy, data security, and the ethical use of patientdata must be addressed to fully harness AI's potential in healthcare.In the realm of education, AI has the potential to personalize and enhance the learning experience for students. Intelligent tutoring systems can adapt to individual learning styles and provide targeted feedback and assistance. Moreover, AI can automate administrative tasks, allowing teachers to focus more on delivering quality education. However, caution must be exercised to ensure that AI in education does notlead to excessive data collection or replace the crucial role of human teachers in fostering creativity and criticalthinking in students.Looking ahead, several trends are likely to shape the future development of AI. One such trend is the increasing collaboration between humans and AI systems. Rather than replacing humans completely, AI will augment human abilities and complement their skills. This collaboration will lead to more efficient and productive outcomes across various industries, including healthcare, finance, and customer service.Furthermore, the field of AI is likely to witness advancements in explainability and transparency. As AI algorithms become more complex, understanding their decision-making processes becomes essential. Research and development efforts are focusing on developing AI systems that can provide explanations for their actions. This will enhance trust and acceptance of AI in society and enable effective oversight and regulation of AI applications.Lastly, the integration of AI with other emerging technologies holds immense potential. AI-powered smart devices, Internet of Things (IoT) systems, and big data analytics can create a connected and intelligent ecosystem. This convergence will lead to more personalized and intuitive experiences for consumers, making everyday life more convenient and efficient.In conclusion, AI's impact on society is substantial, and its future development shows immense potential. While it brings about automation and ethical concerns, AI also offers opportunities for enhancing healthcare, education, and collaboration between humans and machines. As AI continues to evolve, it is crucial for society to navigate these changes responsibly, ensuring that the benefits are maximized while mitigating potential risks.。
人工智能英语作文

Artificial Intelligence AI has become an integral part of modern technology, transforming various aspects of our lives.From personal assistants like Siri and Alexa to autonomous vehicles and advanced healthcare diagnostics,AI is reshaping the future.The Evolution of AI:The concept of AI dates back to the mid20th century when computer scientists began to explore the possibility of creating machines that could think and learn.Over the decades, AI has evolved from simple rulebased systems to complex neural networks capable of processing vast amounts of data and making decisions.Applications of AI:1.Healthcare:AI is used in diagnosing diseases,predicting patient outcomes,and even in robotic surgery,where precision is crucial.2.Finance:AI algorithms are employed in fraud detection,risk management,and automated trading systems.3.Transportation:Selfdriving cars and drones are examples of AIs impact on transportation,promising safer and more efficient travel.4.Customer Service:AI chatbots provide24/7customer support,answering queries and resolving issues swiftly.cation:Adaptive learning platforms powered by AI personalize education to meet the needs of individual students.Challenges of AI:Despite its benefits,AI also presents challenges such as:Ethical Concerns:Issues like data privacy and the potential for AI to make biased decisions are significant.Job Displacement:The automation of tasks by AI could lead to job losses in certain sectors.Security Risks:AI systems can be vulnerable to hacking and misuse.The Future of AI:The future of AI is promising but requires careful management.It is essential to develop AI responsibly,ensuring it benefits humanity while addressing the ethical and societal implications.The collaboration between governments,businesses,and academia will be crucial in shaping AIs role in the future.Conclusion:Artificial Intelligence is not just a technological advancement it is a catalyst for a new era of innovation.As we move forward,it is imperative to educate ourselves about AI,engage in thoughtful discussions about its implications,and work towards a future where AI is a force for good,enhancing our lives without compromising our values.。
5G NR数字蜂窝移动通信网无线操作维护中心(OMC-R)测量报告技术要求

中国移动通信企业标准QB-╳╳-╳╳╳-╳╳╳╳5G数字蜂窝移动通信网无线操作维护中心(OMC-R)测量报告技术要求5G digital cell mobile communications network OMC-Rmeasurement report technical specification目录1范围 (1)2规范性引用文件 (1)3术语、定义和缩略语 (1)4OMC-R测量报告总则 (2)5OMC-R测量报告数据定义 (2)5.1.测量报告数据定义模板 (2)5.2.测量报告数据 (3)6OMC-R测量报告数据格式要求 (10)6.1.总则 (10)6.2.测量报告文件命名规则 (11)6.3.XML文件格式 (11)6.3.1.XML文件结构图 (11)6.3.2.标签说明 (12)6.3.2.1.xml标签属性 (12)6.3.2.2.fileHeader标签属性 (12)6.3.2.3.gNB标签属性 (13)6.3.2.4.measurement标签属性 (13)6.3.2.5.object标签属性 (13)6.3.3.标签说明字符集限定 (13)6.3.4.测量报告统计数据Schema定义 (14)6.3.5.测量报告样本数据Schema定义 (15)7OMC-R测量报告文件生成要求 (17)7.1.时延要求 (17)7.2.文件及数据要求 (17)7.3.存储要求 (18)8编制历史................................................................................................... 错误!未定义书签。
前言本标准旨在明确中国移动通信集团公司对5G无线主设备测量报告的技术要求,并为相关设备的集中采购提供技术参考。
本标准主要包括5G数字蜂窝移动通信网无线操作维护中心(OMC-R)提供的无线测量报告的数据内容和格式。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Effect of node mobility and network dimension to theZigbee routing methodJiasong Mu/Kaihua LiuSchool of Electronic Information EngineeringTianjin UniversityTianjin Chinamujiasong@Abstract—Both the hierarchical tree routing and the table-driven routing algorithm are available in Zigbee specification. However, the routing selection method is not included in the standard. In this article, we analyzed the effect of the node mobility and the change of the network dimension in Zigbee networks. We used OPNET modeler to simulate the Zigbee networks. The simulation results showed the performances of different routing algorithms in the same conditions. We also simulate the performances of different routing methods with the change of the node mobility and network dimension. We analyzed the reasons and made a conclusion. To the networks, of which, the structure is stable or the change of the structure is not much, we figured out the routing selection strategy based on the scale of the networks. We also find the critical boundary for the different routing method. Tree routing may have better performance when the nodes move less than 3 times on average in 100 seconds, the routing discovery method should be used when nodes move more than 4 times.Zigbee; routing selection methond; node mobilityI.I NTRODUCTIONThe ZigBee Alliance published the ZigBee specification version 1.0 (ZigBee v.1.0) to enable reliable, low-cost and low-power wireless monitoring and control in December 2004. The ZigBee v.1.0 defines network and application layers on top of medium access control (MAC) and physical (PHY) layers of IEEE 802.15.4[1]. The ZigBee v.1.0 is one of the first wireless ad-hoc network standards. Since ZigBee devices are designed for low cost and low data rates, it is expected their use in home and building automation with significantly small costs. Moreover, ZigBee networks support star and mesh topology, self-forming and self-healing as well as more than 65000 address spaces; thus, network can be easily extended in terms of size and coverage area.One of the most important research topics on wireless ad-hoc networks has been the routing protocol. There have been many studies on the routing protocols for wireless ad-hoc networks. ZigBee combines the hierarchical routing protocol (HRP) and the well-known ad-hoc on-demand distance vector (AODV) routing protocol in order to meet the objectives such as cost-effectiveness and path robustness. However, since the ZigBee specification and its applications is getting more and more developed recently, the application configuration, performance analysis and optimization remain further discussed[2]. There is still no ZigBee module in the simulation tool extensively used for the network simulation and so there is no relative analysis about the performance of the ZigBee routing [3]. And the routing strategy and its optimization of ZigBee must also be taken into consideration.The rest of this paper is organized as follows. In section II, the ZigBee protocol will be introduced. Section III will explain the routing algorithm used in ZigBee network. In section IV, the simulation results and analysis will be shown. Finally in section V, there will be the conclusion and the further work.II.O VERVIEW OF THE Z IG B EE P ROTOCOL The protocol stack of ZigBee networks is detailed in Fig.1. Based on the IEEE 802.15.4 protocol, the ZigBee specification defines the standard of higher layers. At the PHY layer, IEEE 802.15.4 defines a total of 27 channels: 16 channels at a maximum rate of 250 kbps in the ISM 2.4-2.4835 GHz band, 10 channels at 40 kbps in the ISM 902 - 928 MHz band, and one channel at 20 kbps in the 868.0 - 868.6 MHz band. At the MAC layer, Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) or the optional slotted CSMA/CA mechanism are used, and respectively utilize by the beaconless and beaconed modes.Two device types are specified within the IEEE 802.15.4 framework: full function device (FFD) and reduced function device (RFD). An FFD generally has more responsibilities in that they must maintain routing tables, participate in route discovery and repair, maintain beaconing framework, and handle node joins. Moreover, an FFD has the capability of communicating with any other devices within its transmissionrange. On the other hand, RFD simply maintains the minimumFigure 1. ZigBee protocol stack978-1-4244-3709-2/10/$25.00 ©2010 IEEEamount of knowledge to stay on the network, and it does not participate in routing. RFDs can only associate and communicate with FFDs. Three device types are defined in ZigBee: ZigBee coordinator, ZigBee routers, and ZigBee end devices. An RFD can only be a ZigBee end device; whereas an FFD can be either a ZigBee coordinator or ZigBee router. The ZigBee coordinator is responsible for starting a new network. ZigBee coordinator and routers are "routing capable", while the ZigBee end devices can't participate in routing and have to rely on their corresponding ZigBee parent routers for that functionality [4].III. Z IG B EE R OUTING A LGORITHMSA. Address Allocation Mechanism and Tree RoutingThe address of device in a ZigBee network is assigned by its parent node following the tree structure. The parameter nwkmaxChildren (m C ) represents the largest number of children nodes which can associate with a router or a coordinator. The parameter nwkmaxRouters (m R ) means the number of children nodes which can be a router. The parameter nwkMaxDepth (m L ) decides the most depth in the network. And for the same network, different nodes usually have the constant m C and m R .Every potential parent is provided with a finite sub-block of the address space, which is used to assign network addresses to its children. Given nwkmaxChildren (m C ), nwkMaxDepth (m L ), and nwkmaxRouters (m R ), we can compute the functiond Cskip as the size of the address sub-block distributed by eachparent at depth d as follows:10,0,1(1),1,1.1,1m m d m m m L d m m m m m m R Cskip C L d R R C R C R R −−⎧⎪=⎪⎪=+⋅−−=⎨⎪>+−−⋅⎪⎪−⎩(1)Network addresses 1,d rn A + and 1,d el A + shall be assigned to the n-th router child and l-th end device child at depth d+1 in a sequential manner, respectively, according to (2):()1,1,11d rn parent d d el parent d m A A Cskip n A A Cskip R l++=+−+=+⋅+(2)Where 1m n R ≤≤, and parent A represents the address of the parent.The tree routing algorithm supports simple but reliable routing for any destination address. In ZigBee, network addresses are assigned using the distributed addressing scheme mentioned above. Due to such addressing scheme, the networkconstructs a tree topology; each device can manage the address space of its descendant. If the destination address is in the address space that a node is managing, the node forwards the packet to one of its child nodes. Otherwise, it forwards the packet to its parent node. The parent or child node which receives the packet selects the next hop node according to the destination address in the same manner. Although the tree routing is efficient in the view point of memory usage, we can see that the tree routing requires no memory cache. However, because the tree topology cannot offer the shortest paths, the routing cost is sometimes inefficient.B. Table-driven RoutingTable-driven routing is basically similar to the Ad-hoc On-demand Distance Vector (AODV) routing protocol for general multi-hop ad-hoc network in ZigBee networks. Although the ZigBee node cannot maintain a 2-hop routing table due to the limit of memory and energy like other AODV networks. The ZigBee specification defines the table-driven routing method in the ZigBee network the AODV [5].In ZigBee mesh routing, route requests (RREQ) are broadcasted on-demand when data is to be transmitted to a destination of an unknown path. Routes are constructed based on the route replies (RRPL from intermediate nodes and destination node), and a route error (RERR) message is transmitted to the user when a path can't be found. The route repair mechanism repairs invalid routes when a previous route cannot be found. Since only coordinators/routers (FFDs) can actively participate in mesh routing, the end devices (RFDs) have to rely exclusively on their parent nodes to perform mesh routing on their behalves.C. Routing Selection in ZigBeeAccording to the standard in the network layer, the DiscoverRoute field of the data frame head is defined as the routing approach for data frames [2]. And it can have three values as followed: •Suppress route discovery (SRD): the network only uses the routing tables that exist already. The network disables the routing discovery progress when there is no corresponding address of the destination node •Enable route discovery (ERD): if there is the routing address in the routing table, the routing will follow this routing table. Otherwise, the router will initiate the routing discovery. When this node has no ability to initiate the routing discovery, it will exploit the Tree Routing.•Force route discovery (FRD): The node has to initiate the routing discovery constrainedly no matter whether there is the corresponding routing table or not.In the ZigBee specification, the ERD is the initial value of this field, and there is no relative information about the selection of routing method and how these parameters are configured in order to choose the routing strategy.IV. S IMULATION AND A NALYSISWe used the OPNET modeler to simulate the ZigBee network. The parameters were shown in TABLE I and II. To identify the performance in different situations, we both simulated the stable and unstable net structure for 100 seconds. We defined the stable network as follows: the node had a probability to stay following the exponential distribution which the expectation was 150 seconds, the moving speed of the node was a uniform distribution from 10 to 30 m/s, and the distance the node moved was a uniform distribution from 10 to 50 meters. As the parameter set like this, more than half of the nodes would not move during the simulation and only a few nodes would changed the position more than 1 time.To the unstable network, the probability of the node to stay following the exponential distribution which the expectation was 20 seconds, the moving speed set to the uniform between 10 to 50 m/s, and the distance was the same. In an unstable network, almost all the node moved. The structure changed frequently.We also simulated 2 scales of network. In a small network, the simulation range was 100m*100m, and there were 10 nodes deployed randomly. A large network had a range of 300m*300m and 30 nodes, in which the initial position of the nodes was random.To see the performance of each type of routing method, the statistic Network Load was shown. For every single node had the same parameter on sending packets, which was 100bit long for each packet and the packet interval time, followed the exponential distribution which the expectation was 1 second and the destination of the packet was random, the network load indicated the efficiency of the routing method. And to reduce the effect caused by the network initialization, the data started from 10 seconds. And all the nodes in the network were ZigBee FFDs. We simulated 10 times for each condition and calculated the average.The performance of 3 kinds of routing method in the small stable network was shown in Fig.2, from which, we could see the FRD had the worst performance because of its non-stop routing discovery. The SRD and ERD had similar results. The ERD had more bits because it may have routing request, and it had a better performance later due to the shortest path it may find.TABLE I. P ARAMETERS FOR DIFFERENT DIMENSIONSParameters Small Network Large Network Network Size 100m*100m 300m * 300mNumber of Nodes 10 30Simulation Duration100 seconds Packet Size100 bit TABLE II.P ARAMETERS FOR DIFFERENT MOBILITYParameters Unstable StableProbability to stay exponential distributionexpectation 20 seconds exponential distribution expectation 150 seconds Moving SpeedUniform (10m/s,30m/s) Uniform (10m/s,50m/s) Moving DistanceUniform (10m,50m) Uniform (10m,50m) Fig.3 illustrated the small unstable network. While the network load of FRD didn’t change much compare to the stable one, it still was the most inefficiency. The SRD had much more bits because the node would rejoin the network more frequently caused by the variety of the network structure. The large stable network performance was shown in Fig.4. FRD had most network load. Although ERD might find the shortest path, the routing discovery occupied the network transmission a lot due to the limit of the memory cache of the nodes. The stable structure made the SRD the most efficient and stable.As indicated in Fig.5, the ERD had the best performance while the FRD and SRD had a similar high inefficiency. The FRD tried to make a routing discovery no matter whether it was needed or not. And SRD had to maintain a tree topology when the structure changed at any moment, which made it inefficient and unstable.Time (s)N e t w o r k L o a d (b i t /s )Figure 2.Routing performance in small stable networksTime (s)N e t w o r k L o a d (b i t /s )Figure 3. Routing performance in small unstable networksTime (s)N e t w o r k L o a d (k b i t /s )Figure 4.Routing performance in large stable networks4Time (s)N e t w o r k L o a d (k b i t /s )Figure 5. Routing performance in large unstable networksTo analyze the effect of mobility and dimensions to SRD and ERD in detail, we also simulated the routing performance for their changing separately. To see the effect of dimensions, we used a 300m*300m network, all the nodes were in the stable condition, and the communication parameters keep the same as above. We set the number of the nodes as 10,15,20,25 and 30. Fig.6 showed the result, from which, we may find the network load of ERD growing faster and the growing rate was more stable. The SRD performance was connected with the initial tree structure of the network. However, in the low memory cache situation, the routing request method is not always the most efficient one.Fig.7 demonstrates the effect of mobility factor. The network was 300m*300m and 30 nodes in total. With the same transmission parameters, we changed the expectation of the moving probability of every node. The expectation to stay was 150s, 50s, 20s, 5s and 1s. As illustrated, the SRD is much more sensitive to the node mobility, its performance declines fast with the rapid change of the network structure. On the other hand, the ERD may always maintain the routing efficiently with routing discovery progress. We also find the criticalboundary to the SRD better performance. The node expectation of the node moving probability to stay was around 20 up, which means the node may move about 3 to 4 times in 100 seconds duration in the network, the ERD and SRD have similar capability. In a network which the change of the structure is predictable, the ERD performs better when the nodes move more than 4 times on average in 100 seconds, andthe SRD could achieve better performance when nodes move less than 3 times.Node NumbersN e t w o r k L o a d (b i t /s )Figure 6. Routing performance for SRD and ERD for different node numberExpectaion of the probability of the node to stay (s)N e t W o r k L o a d (b i t /s )Figure 7. Routing performance for SRD and ERD for different nodemobilityV.C ONCLUSIONAs analyzed in the last paragraph, we found the FRD always had the worst performance in all the scenes we simulated. Although the forced routing made the network always find the shortest path. In the dynamic networks, ERD had the most efficiency. As mentioned in the third paragraph, the working mechanism of ERD was similar as the AODV, which could manage the routing well in the mobile networks. As to the stable network, ERD and SRD had similar efficiency in the small ones. However, the SRD based on tree routing, required no memory cache. SRD also had the lowest network load when the scale of the network expanded. Whereas the ERD might do reduplicate routing due to the restricted memory space. The SRD was the best routing option for the stable networks and the ERD performed most efficient in the unstable networks. We also find the tolerance of the network mobility for the efficiency of SRD. In a lager network, SRD has better performance when the nodes move less than 3 times on average in 100 seconds duration, and it performs poorly when the times of movement was more than 4 times.For our further work, we will try to make the node justify the network structure automatically in a simple way without too much memory and calculation requirements. In this way, we may find a self-adapting routing selection strategy for ZigBee networks.R EFERENCES[1]Taehong Kim, Daeyoung Kim, Noseong Park; Seong-eun Yoo andLopez T.S, “Shortcut Tree Routing in ZigBee Networks”, Wireless Pervasive Computing, 2007[2]Ran Peng, Sun Mao-heng and Zou You-min, “ZigBee Routing SelectionStrategy Based on Data Services and Energy-Balanced ZigBee Routing”.IEEE Asia-Pacific Conference on Dec. 2006 Page(s):400 – 404.[3]P. Kinney, “ZigBee Technology: Wireless Control that Simply Works”,Communication Design Conference, October, 2003[4]Liang Nia-Chiang, Chen Ping-Chieh Sun, Tony and Yang Guang“Impact of Node Heterogeneity in ZigBee Mesh Network Routing.”, IEEE International Conference on Volume 1, 8-11 Oct. 2006 Page(s):187 - 191[5]Jae Yeol Ha, Hong Seong Park, Sunghyun Choi, Wook Hyun Kwon,“EHRP: Enhanced hierarchical routing protocol for Zigbee mesh networks” Communications Letters, IEEE Volume 11, Issue 12, December 2007 Page(s):1028-1030.。
