Quality-of-service routing for tra c with performance guarantees
Web+Services的服务质量(Quality+of+Service)模型与度量研究

●
●●
●描述详细的服务质量信息。
该本体被分成三层:
●Profile层
它定义了Web服务界面的服务等级目标(Service.1evelObjective,SLO)。
该层中声明了一个QoSProfile类,作为所有服务质量规约的公共超类(superclass).用户提出的服务质量需求通过Inqu幻,QoS类来描述,Web服务提供者所能提供的服务质量则通过ProviderQoS类来描述,这两个类均继承自QoSProfile类。
将这两个类的实例进行匹配(Matchmal【in曲,以便寻找符合用户服务质量需求的Web服务,如图2.1所示:
图2.1文献1211中的服务质量规约
●属性定义层(PropertyDefinitionLayer)
该层中定义了一些通用的服务质量属性及其定义域(domain)、值域(range)和基数(cardinalityl等约束。
·度量指标层(MetricLayer)
该层定义了具体的服务质量度量指标,并提供了如何进行度量的信息。
度量指标被分成了两大类:原子度量指标(AtomicMetrics)和复合度量指标(ComplexMetrics),后者基于前者或者其他复合度量指标。
从前面这些相关研究可以看出,目前的WebServices服务质量模型主要考虑的都是通用的服务质量属性,忽略了与Web服务所应用的领域相关的服务质量属性在Web服务评价中的作用。
领域相关的服务质量属性反映了与特定领域中的业务内容、业务上下文以及服务提供商等相关的信息。
它们是服务用户在衡量
Web服务的服务质量以及选择Web服务时的重要参考因素。
Date Signed

AN EV ALUATION OF MULTIPLE PATH ROUTING AND ITS IMPACT ON QUALITY OF SER VICE IN MOBILE AD HOC NETWORKSbyGregory B.GerouREMOVEiA thesis submitted to the Faculty and the Board of Trustees of the Colorado School of Mines in partial fulfillment of the requirements for the degree of Master of Science(Mathematical and Computer Sciences).Golden,ColoradoDateGregory B.GerouApproved:ABSTRACTThe topic of multi-path routing protocols has been investigated previously;how-ever,the effectiveness of multi-path routing to improve quality of service by maximiz-ing bandwidth availability,as well as the criteria for determining multi-path routes, have not been clear.For that reason,we have developed a Proactive Disjoint Multi-path Routing protocol(PDMR)that we use to compare single-path routing versus multi-path routing.The results of this investigation illustrate the performance of multi-path routes and their impact on quality of service in a variety of mobile ad hoc network scenarios.iiiTABLE OF CONTENTSABSTRACT (iii)LIST OF FIGURES (vi)LIST OF TABLES (viii)ACKNOWLEDGEMENTS (ix)Chapter1INTRODUCTION (1)Chapter2RELATED WORK (5)2.1MANET Multi-path Routing Protocols (7)2.1.1Diffusing Algorithm for Shortest Multi-path(DASM) (8)2.1.2Disjoint Pathset Selection Protocol(DPSP) (9)2.1.3Multi-path Dynamic Source Routing(MDSR) (11)2.1.4The Graph Multi-path Routing Protocol(GMR) (13)2.1.5The Split Multi-path Routing Protocol(SMR) (15)2.2MANET QoS Frameworks (16)2.2.1Core-Extraction Distributed Ad Hoc Routing(CEDAR) (16)2.2.2Insignia (19)2.2.3Stateless Wireless Ad Hoc Networks(SWAN) (19)Chapter3DISJOINT PATH CLASSIFICATION (21)Chapter4PDMR (26)4.1Network Topology Dissemination (27)4.2Multi-path Discovery Algorithm (28)4.3Multi-path Use Policies (31)4.4The Role of SWAN (32)Chapter5SIMULATION RESULTS (33)5.1Environment (33)5.2Static Network Models (37)5.3Mobile Network Models (46)5.4Contrived Network Model (53)ivChapter6CONCLUSIONS AND FUTURE WORK (58)6.1Conclusions (59)6.2Future Work (60)REFERENCES (63)vLIST OF FIGURES2.1DASM’s path classification example (10)2.2MDSR-Protocol1example (13)2.3MDSR-Protocol2example (13)2.4A comparison of GMR and MDSR (15)2.5CEDAR example network (18)3.1Node disjoint route with two paths (22)3.2Strict link disjoint route with two paths (23)3.3Loose link disjoint route with two paths (23)3.4Semi-node disjoint route with two paths of equal length (24)3.5Semi-node disjoint route with two paths of different length (24)3.6Disjoint route classification hierarchy (25)5.1Route frequencies for various network types(including Route Not Founderror frequencies)as the number of nodes in the network increases..38 5.2Route frequencies for various network types(without Route Not Founderror frequencies)as the number of nodes in the network increases..39 5.3Average route lengths for networks simulated within a region of300mx600m,as the number of nodes in the network increases (40)5.4The average difference between the two paths included in each multi-path route,as the number of nodes in the network increases (42)5.5Total delivery rate for a static network with seven concurrent QoStraffic sessions as the number of simultaneous best effort traffic sessionsvaries (43)5.6Best effort delivery rate for a static network with seven concurrent QoStraffic sessions as the number of simultaneous best effort traffic sessionsvaries (44)vi5.7QoS delivery rate for a static network with seven concurrent QoS trafficsessions as the number of simultaneous best effort traffic sessions varies45 5.8QoS delivery rate for a static network with four concurrent QoS trafficsessions as the number of simultaneous best effort traffic sessions varies46 5.9QoS delivery rate for a static network with one QoS traffic stream asthe number of simultaneous best effort traffic sessions varies (47)5.10QoS delivery rate for a static network with25best effort traffic sessionsas the number of simultaneous QoS traffic sessions varies (48)5.11QoS delivery rate for a static network with30best effort traffic sessionsas the number of simultaneous QoS traffic sessions varies (48)5.12Total delivery rate for a mobile network with seven concurrent QoStraffic sessions as the number of simultaneous best effort traffic sessionsvaries (49)5.13QoS delivery rate for a mobile network with seven concurrent QoStraffic sessions as the number of simultaneous best effort traffic sessionsvaries (49)5.14QoS delivery rate for a mobile network with two concurrent QoS trafficsessions,two concurrent best effort traffic sessions,and variousfixedroute lengths (50)5.15QoS delivery rate for a mobile network withfive concurrent QoS trafficsessions,five concurrent best effort traffic sessions,and variousfixedroute lengths (51)5.16QoS delivery rate for a mobile network with ten concurrent QoS trafficsessions,ten concurrent best effort traffic sessions,and variousfixedroute lengths (52)5.17Network topology for the contrived scenario (54)5.18Delivery rates for the contrived scenario (56)5.19Throughput rates for the contrived scenario (57)viiLIST OF TABLES2.1A breakdown of the fundamental components of each of the discussedmulti-path routing protocols (17)3.1Relationships between disjoint route types and existing multi-path pro-tocols (25)4.1Pseudocode describing the PDMR route discovery algorithm (30)5.1Simulation parameters (34)5.2Network model parameters for static(0m/s)simulations (36)5.3Network model parameters for mobile(1m/s)simulations (36)5.4Simulation parameters (54)viiiACKNOWLEDGEMENTSI am happy to thank my adviser,Dr.Tracy Camp,for her invaluable guidance and unending patience.I would also like to thank my thesis committee members,Dr. Mike Colagrosso and Dr.Jason Liu.Through the course of my research,their input has always steered me in the right direction.I also appreciate the support I have received from members of the Toilers research group.ixChapter1INTRODUCTIONA mobile ad hoc network(MANET)is a network of mobile nodes capable of com-municating without the use of any static network infrastructure.Nodes comprising a MANET are not always capable of communicating directly with the entire network. Limited transmission range implies multi-hop routing,the ability for a given node to transmit data to a destination by passing a packet through intermediate nodes. Transmission range limitations also introduce the hidden node problem,the poten-tial for transmission collisions observed by a node with two transmitting neighbors, each unaware of the other’s transmission.Multiple-hop routing and the hidden node problem are two examples of difficulties created by the wireless and mobile properties of MANETs.As applications from traditional wired networks are moved into the mobile wireless environment,these properties reveal new problems to be solved.Quality of Service(QoS)is an example of a traditional wired network desired property that creates new problems when applied to mobile ad hoc networks.QoS refers to the potential performance requirements of network traffic.For example,a particular application may demand that traffic be delivered with a quantified min-imum delay,or be allowed a specified amount of network bandwidth.Relative to wired networks,reliable QoS is difficult to achieve in MANETs due to higher network volatility.This volatility leads to difficulty in measuring network state,and applying those measurements to QoS traffic routing.Stine and Veciana suggest that to include useful quality of service mechanisms, MANET protocols and frameworks should place a greater emphasis on node statethan on link state[1].In terms of quality of service,node state refers to the available network resources and known characteristics observed at a given node,while link state refers to those resources and characteristics observed over a logical communication link between two nodes.This link is defined by the ability of neighboring nodes to directly communicate.An example of a link state measurement might be node A is transmitting1kb/s to node B;an example of a node state measurement might be node A is observing a local bandwidth usage of3.2kb/s(created both by its own transmissions and those of its neighbors).The emphasis of node state over link state impacts MANET routing protocols because it includes the impact of neighbor traffic on bandwidth availability.Addition-ally,it prioritizes efficient use of the RF transmission space surrounding a node rather than that of a link between a pair of nodes.As described in the previous example, link state measurements do not necessarily indicate available network resources.For example,suppose neighbor nodes A and C are reaching their maximum receivable bandwidth,but are not sending or receiving packets to or from each other.Although neither A nor C observe any bandwidth on their shared link,given that neither is capable of receiving further traffic,any new traffic between the two nodes will likely result in a transmission collision.In this example,a QoS framework based on link state measurements would likely yield poorer performance than a QoS framework based on node state measurements.The change in approach from a link-based to node-based paradigm is also evi-dent in comparing earlier QoS work to current QoS work.For example,the Core-Extraction Distributed Ad hoc Routing Algorithm(CEDAR)[2]and an in-band signaling system,Insignia[3],use link-based metrics while a later approach such as SWAN[4,5]relies on node-based measurements.SWAN has proved it is possible toobtain good quality of service by using a stateless,reservation-less approach.Specif-ically,SWAN enables the monitoring and shaping of available bandwidth.Although robust approaches to QoS in MANETs have been developed and pub-lished,most rely on the existence of a single-path that is capable of satisfying the resource requirements for the dataflow.A single path traffic session incurs a variety of costs such as large bandwidth use due to network traffic along the single path,in-creased delay due to possible transmission collisions and saturated forwarding queues, reduced battery life due to requisite retransmissions,etc.When a single path is used to transmit a stream of traffic,the costs associated along the single path with that traffic are imposed on the nodes along that path.This problem has motivated the development of protocols that leverage multi-paths to distribute the bandwidth costs associated with a data stream over a broader range of the network.In order for multiple paths to benefit traffic delivery,the following requirements must be met:1.The source and destination nodes are not bandwidth constrained.2.Intermediate nodes on the multi-paths are under load such that a)no singlepath can satisfy the bandwidth requirement,and b)considered together,their bandwidth capacity is sufficient to satisfy the bandwidth requirement.The goals of this thesis are twofold.Thefirst goal is to present our new multi-path protocol,the Proactive Disjoint Multi-path Routing protocol.The second goal is to use PDMR as a tool for evaluating single-versus multi-path routing techniques.Although the above requirements for improving traffic delivery with multi-path routing are relatively straightforward,it is necessary to determine if their frequency is sufficient to observe a significant improvement with multi-path routing relative to single-path routing.Chapter2covers related work,including both existing multi-path routing pro-tocols and established QoS frameworks.Chapter3covers the topic of disjoint routes, and the criteria for classifying various disjoint path types.This analysis is then ap-plied to the previously covered multi-path routing protocols.Chapter4describes the details of our Proactive Disjoint Multi-path Routing protocol(PDMR):a topology dissemination component,a multi-path discovery algorithm,path use policies,and admission and rate control components.Chapter5presents our PDMR simulation results and analysis.Chapter6presents the conclusions we draw from the results obtained over the course of our research.Chapter2RELATED WORKMultiple path routing is a concept that has been applied to several applications [16].However,the fundamental difficulties presented in MANETs caused by node mobility and communication over a volatile medium make new study of multi-path routing protocols within this context interesting.A significant amount of work has been published on the subject of multi-path routing in MANETs.In addition to the work covered in detail later in this chapter,Villela and Duarte present analysis regard-ing traffic throughput maximization using multi-path routing[9].Chen,Druschel and Subramania present a multi-path forwarding policy[10].Cidon,Rom,and Shavitt develop a mathematical model of a multi-path protocol with a QoS reservation mech-anism that shows1)in most networks more than two or three disjoint paths offer no improvement in performance,and2)real network behavior may deviate from the conditions required to obtain a benefit in performance from multi-path routing[11]. Ogier,Rutenburg,and Shacham present algorithms for computing disjoint paths, without an emphasis on wireless environments[12].Sidhu,Nair,and Abdallah also present a network-generic algorithm for disjoint path discovery[13].Taft-Plotkin, Bellur,and Ogier suggest multi-path routing as an implementation for providing QoS services[14].Vutukury,and Garcia-Luna-Aceves suggest a protocol that calculates multi-paths through the use of distance vector routing.Much of this work includes protocols for discovering and using multi-paths;additionally,Corson and Macher of-fer an evaluation framework for multi-path protocols[23].The framework identifies the following fundamental components of a multi-path protocol:1.Multiple Route Discovery.The procedure by which the protocol selects multi-path routes.This procedure generally includes provisions to avoid path looping, and heuristics to generate disjoint multi-path sets.2.Filtering Provision.A protocol component capable of eliminating undesirablemulti-path sets based on a metric such as path length,available bandwidth,etc.3.Path Usage Policy.The policy by which the protocol decides what and whento transmit along each of the paths in the multi-path set.Examples of such a policy are:•Load Balancing.The transmitting node will send each packet along the least recently used path.For instance,if the multi-path set is comprised of two paths,the transmitting node will alternate packet transmissions between the two paths.•Redundancy.The transmitting node will transmit each packet along all paths.In the case of redundant path usage,the source node must include a policy to determine the path order for the duplicate packet transmissions.When a node must transmit the same packet to two different destinations individually,a data forwarding policy defines the order of the transmissions to each of thesedestinations.Examples of a data forwarding mechanism include a round-robin approach,or a heuristic such as path length to determine path priority.The need for path prioritization in a forwarding mechanism is motivated by the dif-ference in predictable behavior between path options.4.Multi-path Maintenance Heuristic.In single-path routing,a set of rules mustbe built into the routing protocol to enable path recomputation.The only ad-ditional complexity,compared to single path routing,is the inclusion of multi-paths.Traditional single-path maintenance heuristics must be updated or re-placed to enable efficient use of multi-paths.5.Underlying Single Path Routing Protocol.The use of multi-paths implies theavailability of multi-paths,and multi-paths are not always available.If no multi-path is available,but a single path is available,the multi-path protocol must be capable of using and maintaining that single path.These components comprise a framework for evaluating multi-path routing proto-cols.In Section2.1,we discuss the prominent multi-path routing protocols currently available.We summarize these protocols by categorizing them via these fundamental components.Section2.2then covers the significant published QoS frameworks for MANETs.2.1MANET Multi-path Routing Protocols2.1.1Diffusing Algorithm for Shortest Multi-path(DASM)When a next hop is not defined for a given destination at a given node,that node queries its neighbors for information regarding the destination.If any of the neighbors have the requested destination node in their routing tables,a reply is sent to the querying node indicating the next hop and the total distance to the destination. If no neighbor has the requested destination node in their routing tables,the request is repeated.This process continues until a querying node has been answered with a distance to the destination.At network startup,when all routing tables are empty, this process takes the form of aflooded route request.As replies are sent back to the source,neighboring nodes promiscuously update their routing tables.We note that neighbors of each querying node may not hear route reply messages sent to the querying node.Thus,although the querying node may have successfully discovered the next hop to the destination,the route request will continue to be forwarded.Route replies include a hop distance measurement,enabling querying nodes to maintain a shortest path hop,and additionally maintain the shortest multi-path hop.DASM’s path usage policy dictates that when the shortest path fails,a shortest multi-path is used if one is available.If no shortest multi-path route is available when the shortest path route fails,a new route request is triggered.If a shortest multi-path is available and if both the shortest path and the shortest multi-paths have failed,a new route discovery is triggered.Table2.1describes DASM according to the fundamental components of multi-path protocols,and compares it to the other multi-path protocols described in this chapter.2.1.2Disjoint Pathset Selection Protocol(DPSP)Fig.2.1.DASM’s path classification examplepath information sufficient to build(at least)a partial graph representation of the network between the source and destination nodes.DPSP introduces the notion of path reliability for use in path selection.The protocol defines reliability as a function of both a path’s length and the delivery rate over each of the path’s links.This function is essentially DPSP’s pathfiltering provision.A path set is generated by performing a search on the graph for a maximally reliable path(according to DPSP’s reliability function).This path is added to a multi-path set;the intermediate nodes in the discovered path are removed from the graph(which we term a node disjoint filter),and a new search is performed.The algorithm includes a threshold mechanism to determine when additional paths no longer offer a reliability benefit,according to DPSP’s reliability function.Once a multi-path set has been calculated,data is transmitted redundantly on each of the paths,theoretically improving the probability the packetized data will arrive at the destination.The data forwarding mechanismuses a round robin scheme to determine a path order to be used for redundant datapacket transmissions.If the reliability of a calculated route falls below a defined threshold,a new route calculation is triggered.It is possible for the protocol to calculate a single path route,given that it meets the requirements to be considered reliable.Table2.1describes DPSP according to its fundamental components,and compares it to the other multi-path protocols described in this chapter.2.1.3Multi-path Dynamic Source Routing(MDSR)requests are forwarded at most once by any given node involved in any given route discovery.These additional routes are generally longer,as these route requests arrive after the primary source route’s request arrives.Route replies for each route are sent to the source.The MDSR route usage policy dictates secondary routes are only used after the primary route has failed.The use of previously discovered secondary routes reduces route discovery overhead.If only one RREQ is received by the destination (i.e.,there is only one path from source to destination),MDSR acts essentially the same as the single path DSR protocol.MDSR offers two mutually exclusive multi-path maintenance heuristics.The authors label these versions of MDSR as“Protocol1”and“Protocol2”.Protocol 1prevents intermediate node route caching for alternate routes,which implies that only the source is capable offixing a broken path.Figure2.2depicts an example of Protocol1for a given source,S,and destination,D;the dotted lines represent the primary route,and the solid lines represent the alternate paths.Protocol2,on the other hand,allows intermediate nodes to cache alternate routes;intermediate nodes use this information saved tofix routes when broken links are detected.For instance, if an intermediate node determines a current route has failed,it begins using any available cached alternate route to the destination.If no such route is cached,a route error is sent to the next upstream node where the process is repeated.Figure 2.3depicts an example of Protocol2;the dotted lines represent the primary route, and the solid lines represent the alternate routes.Protocol1offers the simplicity of maintaining alternate disjoint paths for each traffic session only at the source;Protocol 2requires more overhead for maintaining alternate disjoint paths at all intermediate nodes,but is able to offer backup path maintenance.Table2.1describes MDSR according to its fundamental components,and compares it to the other multi-pathprotocols described in this chapter.Fig.2.2.MDSR-Protocol1exampleFig.2.3.MDSR-Protocol2example2.1.4The Graph Multi-path Routing Protocol(GMR)from all received route requests are combined and forwarded as a single route request. This method enables the destination to build a graph representation of the network and to determine multiple link disjoint routes.Once these paths are communicated to the source,data packets begin transmitting.The published work on GMR does not specify what policy is used to determine how the multi-paths are employed,but it is reasonable to assume that once it has been determined that all calculated paths have failed,a new route discovery process is triggered.Additionally,it is possible for GMR to function as a single path routing protocol,assuming only a single path exists between the source and destination nodes.The motivation for GMR is a limitation of MDSR.Duplicate route requests are ignored in MDSR,just as they are in DSR.Thus,the set of multi-path routes discovered in MDSR is defined by the sequence in which route requests arrive at each node.For instance,in MDSR,a node that receives a route request will forward it and, therefore,belong to the growing potential route included in that request.All other route requests received by that node are ignored,which implies the route requests that reach the destination are comprised of mutually exclusive node sets.GMR,on the other hand,incorporates duplicate route requests,thus allowing potential overlapping route requests to reach the destination.Equipped with these additional,potentially overlapping options,the destination is more capable of calculating disjoint paths. Figure2.4illustrates this idea.The solid connecting lines indicate links potentially discovered by MDSR.The combination of the solid connecting lines and the dashed connecting lines are links potentially discovered by GMR.Figure2.4illustrates that GMR is capable of providing enough topological data to the destination node to build a graph representation of the pertinent network subset.MDSR is not capable of building such a graph.Table2.1describes GMR according to its fundamentalcomponents,and compares it to the other multi-path protocols described in this chapter.Fig.2.4.A comparison of GMR and MDSR2.1.5The Split Multi-path Routing Protocol(SMR)either1)continue using the single available path or2)trigger a new route discovery.Obviously the advantage of not automatically triggering a new route request is a decrease in routing overhead traffic.However,SMR’s authors also acknowledge that waiting until all available paths to a destination have failed implies that no data can be sent to the destination during the subsequent route discovery.SMR is configurable such that nodes initiate new route discoveries as soon as the shortest route breaks to ensure that an alternate path is available for data transmission during the route discovery process.If only one path is available,regardless of how SMR is configured, a new route discovery is triggered upon the failure of this single path.Table2.1 describes SMR according to its fundamental components,and compares it to the other multi-path protocols described in this chapter.2.2MANET QoS FrameworksCEDAR,the Core Extraction Distributed Ad hoc Routing algorithm[2]is a proposed QoS routing framework for small-to medium-sized ad hoc networks(tens to hundreds of nodes).The nodes in the network dynamically elect an approximate minimum dominating set of core nodes.A set of core nodes is considered a minimum dominating set if they represent the minimum number of nodes required to span thenetwork,i.e.,every non-core node is a one-hop neighbor of at least one core node. This network of core nodes is used to propagate link bandwidth information in two modes.First,information regarding a significant increase in available bandwidth on a given link is propagated by an increase wave,i.e.,a packet that is repeated over a broad range of the core network.A significant decrease in available bandwidth on a given link is propagated by a decrease wave,i.e.,a packet that is repeated over a smaller range of the core network.Essentially,information about usable links is shared over a large amount of the network and information about constrained links is shared locally.Figure2.5illustrates an example CEDAR network.The nodes depicted in solid black comprise the network’s core or the network’s approximated minimum dominating set;all other nodes are depicted as white-centered circles.The solid connecting lines denote links between pairs of nodes,while the dotted lines indicate the core network.Fig.2.5.CEDAR example network2.2.2InsigniaThe Stateless Wireless Ad Hoc Networks(SWAN)protocol[4]was also developed by the author’s of Insignia[3].SWAN offers a stateless/reservation-less efficient and effective QoS framework.The two components in SWAN are a rate controller and an admission controller.The goal of SWAN is to adapt bandwidth usage according to the measured one hop delay to ensure that1)delay does not become excessive and2) network bandwidth does not become saturated to the point of significant packet loss and reduced throughput.SWAN improves upon INSIGNIA by abandoning the idea of bandwidth reservations in favor of efficient use of the RF medium on a node-by-node basis.This modification improves network efficiency.SWAN handles best effort(non-priority)traffic easily,and includes provisions for priority packets to enable qualityof service support.QoS packets are given priority treatment in terms of admission and bandwidth usage.Upon network saturation,best effort packet throughput and delivery rates suffer before high priority throughput and delivery rates are impacted. In other words,by sacrificing best effort traffic delivery,a high network throughput of high priority traffic is maintained.In non-saturated conditions,high priority traffic continues to receive queuing preference,minimizing delay for QoS packets.。
网络服务质量(QoS)保障的关键技术与方法

网络服务质量(QoS)保障的关键技术与方法网络服务质量(Quality of Service,QoS)是指在网络通信过程中,对于不同类型的数据流能够提供不同的服务质量保障。
在如今信息爆炸的时代,人们对于网络服务质量的要求越来越高。
本文将介绍网络服务质量保障的关键技术与方法。
一、网络服务质量的定义与分类网络服务质量(QoS)是指在网络传输中所能提供的各项保障,包括带宽、延迟、丢包率、抖动等指标。
根据不同的应用要求,网络服务质量可以分为以下几类:1.1 宽带保证宽带是指网络中能够传输的数据量大小,它直接决定了网络的传输能力。
宽带保证是网络服务质量保障的首要任务,通过对网络带宽进行合理管理,确保各类应用能够得到足够的带宽资源。
1.2 延迟控制延迟是指数据从发送端到接收端所经历的时间,对于实时性要求较高的应用,如视频通话、在线游戏等,延迟控制非常重要。
通过优化网络拓扑结构、使用高效的传输协议等方法来降低延迟,提高用户体验。
1.3 抖动调整抖动是指数据到达接收端的时间间隔的不确定性,如果抖动过大,将导致音视频质量下降或者网络连接不稳定。
通过使用缓冲区、拥塞控制算法等方法来调整抖动,提高数据传输的稳定性。
1.4 丢包恢复丢包是指在传输过程中数据包丢失的情况,网络丢包率的大小直接影响着数据传输的可靠性。
通过使用错误校验、重传机制等方式来恢复丢失的数据包,确保数据的完整性和准确性。
二、关键技术及方法2.1 Traffic Shaping(流量整形)Traffic Shaping是一种控制流量传输速率的技术,通过对流量进行限制和调整,使得不同类型的数据能够按照事先设定的优先级和策略进行传输。
这种技术可以有效地防止网络拥塞,提升网络的吞吐量和稳定性。
2.2 Quality of Service Routing(QoS路由)QoS路由是指根据应用的服务质量需求,选择合适的路由路径,以提供最佳的服务质量保障。
通过动态地选择网络路径,可以在不同的网络拓扑和负载条件下,实现网络性能的最优化。
QOS(Quality Of Server)

QOS(Quality Of Server)(在拥塞时才用)哪些问题会影响网络的数据传输1、有限的带宽2、延迟3、抖动4、丢包解决可用带宽的方法:1、升级带宽,增加链路带宽2、让优先级高的流量先过3、压缩二层的帧4、压缩IP包的头部延迟的分类:1、处理延迟--网络设备将数据帧从入接口取出,将其放到接收队列,再放到出接口输出队列所需的时间2、排队延迟--数据包在接口的输出队列中等待的时间3、串行化延迟--将封装在数据帧中比特放到物理介质上的时间4、传播延迟--通过物理介质传输数据帧中的比特所需的时间注意:只有排队延迟可以通过使用QOS来进行控制QOS服务模型:1、尽力而为的服务--没有应用QOS,网络的默认行为2、集成服务--所有的中间系统和资源都显式的为流提供预定的服务,这种服务需要预留网络资源,确保网络能够满足通信流的特定服务要求。
3、区分服务--将根据服务要求将通信流分类,然后将它们加入到效率不同的队列中,使一些通信流优先于其他类别的通信流得到处理。
IntServ集成服务是通过使用RSVP(Resource Reservation Protocol资源预留协议)实现的,在两个端点中间网络设备上都要启用RSVP。
工作原理--数据流在发送之前,起始节点会向网络请求特定类型的服务,并将其流量配置文件告诉网络中的每个中间节点,请求网络提供一种能够满足其带宽和延迟要求的服务。
在从网络得到确认后,应用才开始发送数据。
资源预留的过程分为5步:1、数据发送方发送rsvp path控制消息,这种消息描述了将要被发送的数据的信息。
2、每个rsvp路由器收到path消息后,保存上一跳的IP地址,并继续向下发送。
3、接收站接收到rsvp path消息后,使用rsvp resv消息向上一跳路由器请求rsvp资源预留。
rsvp resv消息从接收方到发送方所经过的路径与rsvp path消息到来时完全相同。
4、rsvp路由器确定是否可以满足这些rsvp请求,如果不能,则拒绝。
20110929-视频会议基础知识(百问百答)

视频会议基础知识百问百答1、下图是H.323协议的基本框架,请阐述图示要点?(提示:H.245/H.225/RAS等呼叫信令的传输特点,为什么分别基于TCP/UDP来传输)答:H.323呼叫建立过程涉及3种信令:RAS信令,H.225呼叫信令和H.245控制信令。
RAS信令用来完成终端与GK之间的登记注册、授权许可、带宽改变、状态和脱离解除等过程;H.225呼叫信令用来建立两个终端之间的连接,这个信令使用Q.931消息来控制呼叫的建立和拆除;H.245控制信令用来传送终端到终端的控制消息,包括主从判别、能力交换、打开和关闭逻辑信道、模式参数请求、流控消息和通用命令与指令等。
H.323会议系统是基于分组交换的,因而会议系统中的码流在传输之前就必须进行打包,根据数据包上的标签进行统计复用。
同时,由于会议系统中的不同信息码流各自有不同的特点。
所以,它们对下层网络的承载要求也不同。
对于IP网,在实现时可以用以下方法解决个问题:音频和视频码流对实时性要求很高,即使少量的时延,对视频会议来说也是无法忍受的。
但是,它们对于少量的包丢失却不太敏感。
因此,对于音频和视频码流,采用实时传输协议RTP来对它们进行打包再运用面向无连接的UDP协议进行实时传输。
对RAS信号也采用UDP协议来传输。
相反,数据和控制信号对于服务质量要求很高,少量的包丢失或出错都是无法忍受的。
因此对于数据和控制码流,在传输层运用面向连接、提供可靠服务的TCP协议,从而完成对它们的可靠传送。
2、简述H.323终端之间如何建立呼叫过程。
(提示:信令交互过程)答:H.323终端之间建立通信关系通常执行四个控制过程:RAS,H.225.0呼叫控制(Q.931信令),连接控制(H.245)及媒体RTP信道建立的过程。
3、GK的基本功能是什么?直接(Directed)和路由(Routed)工作模式的区别是什么?答:在H.323系统中,关守是可选择的,它为H.323端点提供呼叫控制服务。
QualityofService(QoS)详解剖析

QoS优先级详解在QoS的分类流程中最关键的是对各种不同包配置不同的优先级,对流入交换机的数据包按优先级排列,然后交换机就会根据这个优先级值执行相应的QoS 行为。
而对数据包进行优先级排列的第一步就要对数据包进行分类。
分类规则可以使用VLAN帧中的802.1p优先级、IP报文头的ToS(Type of Service,服务类型)字段的优先级位,识别出不同优先级特征的流量;也可以由网络管理者设置流分类的策略,例如综合源地址、目的地址、MAC地址、IP协议或应用程序的端口号等信息对流进行分类。
一般的分类依据封装报文的头部信息,使用报文的内容作为分类的标准是比较少见的。
分类的结果是没有范围限制的,它可以是一个由五元组(源地址、源端口号、协议号、目的地址、目的端口号)确定的狭小范围,也可以是到某网段的所有报文。
10.1.2 二层VLAN帧中的优先级二层帧中的优先级是专门针对VLAN帧的,因为普通二层帧中是不携带有优先级字段的。
VLAN帧中的优先级那就是我们通常所说的802.1p优先级(由IEEE 802.1p协议定义),位于VLAN帧中的“802.1Q Tag”字段的“PRI”子字段中,如图10-1所示。
图10-1 VLAN帧中的802.1p优先级字段IEEE 802.1p是IEEE 802.1Q(VLAN标签技术)标准的扩充协议,它们协同工作。
IEEE 802.1p的出现,使得第二层交换机能够提供流量优先级和动态组播过滤服务,其中流量优先级规范工作在媒体访问控制(MAC)层,组播流量过滤功能可确保该流量不超出第二层交换网络范围。
IEEE 802.1Q标准定义了为以太网MAC 帧添加的标签,但并没有定义和使用优先级字段,而使用IEEE 802.1p修改后的以太网MAC帧的以太网协议头中则定义了该字段。
802.1p优先级位于二层VLAN帧头部,适用于不需要分析三层报文头,而需要在二层环境下保证QoS的场合。
Linux内核QoS实现机制

Linux内核QoS实现机制1.QoS介绍QoS(Quality of Service)即服务质量。
对于网络业务,服务质量包括传输的带宽、传送的时延、数据的丢包率等。
在网络中可以通过保证传输的带宽、降低传送的时延、降低数据的丢包率以及时延抖动等措施来提高服务质量。
网络资源总是有限的,只要存在抢夺网络资源的情况,就会出现服务质量的要求。
服务质量是相对网络业务而言的,在保证某类业务的服务质量的同时,可能就是在损害其它业务的服务质量。
例如,在网络总带宽固定的情况下,如果某类业务占用的带宽越多,那么其他业务能使用的带宽就越少,可能会影响其他业务的使用。
因此,网络管理者需要根据各种业务的特点来对网络资源进行合理的规划和分配,从而使网络资源得到高效利用。
流量控制包括以下几种方式:⏹SHAPING(限制)当流量被限制,它的传输速率就被控制在某个值以下。
限制值可以大大小于有效带宽,这样可以平滑突发数据流量,使网络更为稳定。
shaping(限制)只适用于向外的流量。
⏹SCHEDULING(调度)通过调度数据包的传输,可以在带宽范围内,按照优先级分配带宽。
SCHEDULING(调度)也只适于向外的流量。
⏹POLICING(策略)SHAPING用于处理向外的流量,而POLICIING(策略)用于处理接收到的数据。
⏹DROPPING(丢弃)如果流量超过某个设定的带宽,就丢弃数据包,不管是向内还是向外。
2.内核实现过程图表 1 流量控制过程绿色部分就是Linux内核实现的QoS模块,其中ingress policing 是处理输入数据包的,而output queueing 则是处理输出数据包的。
2.1.Ingress实现机制Ingress QOS在内核的入口点有两个,但是不能同时启用,这取决于内核编译选项。
当打开了CONFIG_NET_CLS_ACT(from 2.6.8 release still available on 2.6.39 release)时,入口点在src/net/core/dev.c的netif_receive_skb函数中;当没有打开CONFIG_NET_CLS_ACT,而是打开了CONFIG_NET_CLS_POLICE (from 2.6.9 release to 2.6.24, thus this is an obsolete configuration)和CONFIG_NETFILTER时,就会在netfilter的PREROUTING钩子点处调用ing_hook函数。
Cisco 7750 SR OS Quality of Service 指南页面 663 配置命令
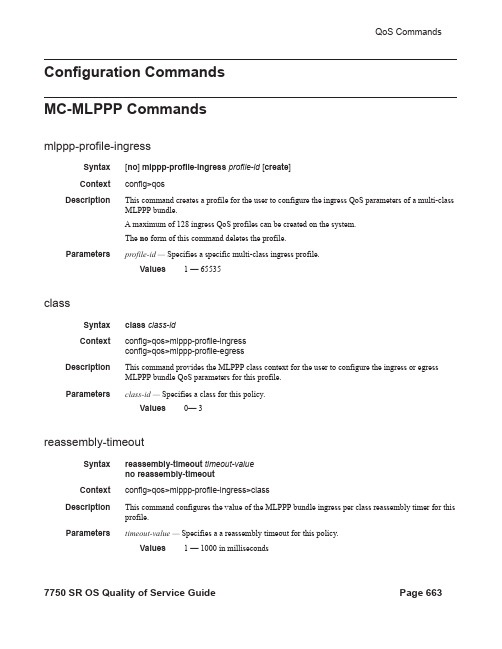
Configuration CommandsMC-MLPPP Commandsmlppp-profile-ingressSyntax[no] mlppp-profile-ingress profile-id[create]Context config>qosDescription This command creates a profile for the user to configure the ingress QoS parameters of a multi-class MLPPP bundle.A maximum of 128 ingress QoS profiles can be created on the system.The no form of this command deletes the profile.Parameters profile-id — Specifies a specific multi-class ingress profile.Values 1 — 65535classSyntax class class-idContext config>qos>mlppp-profile-ingressconfig>qos>mlppp-profile-egressDescription This command provides the MLPPP class context for the user to configure the ingress or egress MLPPP bundle QoS parameters for this profile.Parameters class-id — Specifies a class for this policy.Values0— 3reassembly-timeoutSyntax reassembly-timeout timeout-valueno reassembly-timeoutContext config>qos>mlppp-profile-ingress>classDescription This command configures the value of the MLPPP bundle ingress per class reassembly timer for this profile.Parameters timeout-value — Specifies a a reassembly timeout for this policy.Values 1 — 1000 in millisecondsdescriptionSyntax description description-stringno descriptionContext config>qos>mlppp-profile-ingressconfig>qos>mlppp-profile-egressDescription This command creates a text description stored in the configuration file for a configuration context.The description command associates a text string with a configuration context to help identify thecontext in the configuration file.The no form of this command removes any description string from the context.Default No description is associated with the configuration context.Parameters description-string — A text string describing the entity. Allowed values are any string up to 80characters long composed of printable, 7-bit ASCII characters excluding double quotes. If thestring contains special characters (#, $, spaces, etc.), the entire string must be enclosed withindouble quotes.mlppp-profile-egressSyntax[no] mlppp-profile-egress profile-id[create]Context config>qosDescription This command creates a profile for the user to configure the egress QoS parameters of a multiclass MLPPP bundle.A maximum of 128 egress QoS profiles can be created on the system.The no form of this command deletes the profile.Parameters profile-id — Specifies an ingress mlppp-profile ID.Values 1 — 65535max-queue-sizeSyntax max-queue-size queue-sizeno max-queue-sizeContext config>qos>mlppp-profile-egress>classDescription This command configures the maximum queue size for each MLPPP class queue for this profile.Parameters queue-size — Specifies the maximum queue size.Values 1 — 1000 in milliseconds of buffer spacemirSyntax mir mir-valueno mirContext config>qos>mlppp-profile-egress>classDescription This command configures the minimum information rate (MIR) scheduling parameter for each MLPPP class queue for this profile.Parameters mir-value — Specifies the MIR scheduling parameter.Values 1 — 100weightSyntax weight weight-valueno weightContext config>qos>mlppp-profile-egress>classDescription This command configures the WRR weight scheduling parameter for each MLPPP class queue for this profile.Parameters weight-value — Specifies the weight scheduling parameter.Values 1 — 100fcSyntax fc fc-name mlppp-class class-idno fc fc-nameContext config>qos>mlppp-profile-egress>classDescription This command configures the mapping of the system forwarding class to the MLPPP classes for this profile. There is a many-to-one relationship between the system forwarding class and an MLPPPclass.Parameters fc-name — Specifies the forwarding class name.Values b3, l2, af, l1, h2, ef, h1, ncclass-id — Specifies the class ID.Values0 — 3。
N-TRON 708FX2工业互联网交换机说明说明书

708FX2 Industrial Ethernet SwitchN-Tron Networking SeriesThe N-TRON ® 708FX2 Industrial Ethernet Switch combines outstanding performance and ease of use. The fully managed switch is ideally suited for connecting Ethernet-enabled industrial and/or security equipment.PRODUCT FEATURES• Six 10/100BaseTX RJ-45 Ports• Two 100BaseFX Fiber ports, ST or SC style • -40o C to 85o C Operating temperature• ESD and Surge Protection Diodes on all Ports • Auto Sensing 10/100BaseTX, Duplex, and MDIX • Store-and-Forward Technology • Rugged DIN-Rail Enclosure• Redundant Power Inputs (10-30 VDC) • Con fi gurable Alarm Contact• Con fi gurable Bi-Color Fault Status LEDFully Managed Features:• Full SNMP and Web Browser Management• Detailed Ring Map and Fault Location Charting • N-Ring ™ Technology with ~30ms Healing • N-View ™ OPC Monitoring • Plug-and-Play IGMP Support• 802.1Q tag VLAN and Port VLAN • 802.1p QoS and Port QoS • EtherNet/IP ™ CIP Messaging• LLDP (Link Layer Discovery Protocol) • Trunking • Mirroring• 802.1d, 802.1w, 802.1D RSTP• DHCP Server, Option 82 relay, Option 61, IP Fallback• Port Security—MAC Address BasedManagement FeaturesThe 708FX2offers several management functions that can be easily con fi gured using a web browser.IGMP Snooping - Internet Group Management Protocol is a feature that allows the 708FX2switch to forward and filter multicast traffic intelligently.VLAN - Virtual Local Area Network allows you to segment the switch in order to create two or more separate local area network domains.QoS - Quality of Service provides prioritization of network traf fi c in order to provide better network service. The primary goal of QoS is to improve the latency of prioritized Ethernet packets required for ring management, real-time, and other interactive applications.Trunking - Trunking (link aggregation) enables multiple physical ports to be linked together and function as one uplink to another N-TRON trunking capable switch con fi gured in the same manner, thereby increasing the bandwidth between switches. This con fi guration can provide increased bandwidth and redundancy to applications requiring high levels of fault tolerant operation.Port Mirroring - This function allows the traf fi c on one port to be duplicated and sent to a designated mirror port. Port mirroring can be used to monitor Ethernet traf fi c on the designated source port using the assigned mirror port.HE INDUSTRIAL NETWORK COMPANYRapid Spanning TreeThis function allows the switch to be con fi gured in a ring or mesh topology, and provides support for redundant path communications with high-speed (rapid) healing.Remote Monitoring OptionsFor ease of configuration and monitoring, the 708FX2 offers web browser management and N-View OLE for Process Control (OPC) server software. The N-TRON N-View software can be combined with popular HMI software packages to add network traf fi c monitoring, trending, and alarming to any application using N-TRON switches. In addition SNMP is available for switch link and status monitoring. The Alarm Contact and Status LED can be con fi gured to respond to power failure on power input 1 or input 2, N-Ring Broken, Partial Break High, Partial Break Low, or if multiple ring managers are detected.N-Ring TechnologyThe switch's ring manager, using N-TRON's N-Ring technology, offers expanded ring size capacity, detailed fault diagnostics, and a standard healing time of ~30ms. The 708FX2 ring manager periodically checks the health of the ring via packets. If the ring manager stops receiving these health check packets, it converts the Ring to a linear bus topology within ~30ms. When all switches in the ring are N-TRON fully managed switches, a detailed ring map and fault location chart will also be provided on the ring manager’s web browser and OPC server to identfy the health status of the ring. N-Link allows the linking of two N-Rings. Up to 250 fully managed N-TRON switches can participate in N-Ring topologies.Industrial Packaging and Speci fi cationsThe 708FX2 is designed to operate in industrial environments. It is housed in a rugged steel DIN-Rail enclosure. It has extended industrial specifications and features to meet or exceed the operating parameters of the connected equipment. These include extended temperature ratings, extended shock and vibrations specs, redundant power inputs, and high MTBF (greater than 2M hours).Ease of UseThe 10/100BaseTX ports are auto sensing and auto configuring. Each copper port is automatically negotiated for maximum speed and performance by default, but can also be hard coded using the user interface. A high-speed processor allows wire speed capability on all 100BaseTX ports simultaneously.708FX2708FX2 Speci fi cationsSwitch PropertiesNumber of MAC Addresses: 8000Aging Time : Programmable Latency Typical: 2.9 μsSwitching Method : Store-and-Forward PhysicalHeight: 2.3" (5.8cm)Width:6" (15.3cm)Depth: 3.8" (9.6cm)Weight (max): 1.7 lbs (0.75kg)DIN-Rail Mount:35mmElectricalRedundant Input Voltage: 10-30 VDC Input Current (max): 330mA max @ 24VDC BTU/hr: 27 @ 24VDC N-TRON Power Supply: NTPS-24-1.3 (1.3 A @ 24V)EnvironmentalOperating Temperature: -40o C to 85o C Storage Temperature: -40o C to 85o C Operating Humidity: 5% to 95% (Non Condensing)Operating Altitude: 0 to 10,000 ft.Shock and Vibration (bulkhead mounted)Shock: 200g @10ms Vibration/Seismic: 50g, 5-200Hz, Triaxial Reliability MTBF: >2 Million Hours Network Media 10BaseT: >Cat3 Cable 100BaseTX: >Cat5 Cable 100BaseFX Multimode:50-62.5/125μm 100BaseFXE Singlemode: 7-10/125μmConnectors10/100BaseTX:Six (6) RJ-45 Copper Ports 100BaseFX: Two (2) SC or ST Fiber Duplex PortsRecommended Wiring ClearanceFront : 4" (10.16cm)Side : 1" (2.54cm)Regulatory ApprovalsFCC/CE (CFR 47, Part 15, Subpart B, Class A)EN 55011ICES-003- Class AEN61000-4-2/3/4/5/6/8/11, EN61000-6-2/4UL /cUL: Class I, Div 2, Groups A, B, C, D and T4A ANSI/ISA 12.12.01-2007ATEX II 3 G Ex nC (DEMKO 03 ATEX 0316686U)ABS Type Approval for Shipboard Applications DNV Type Approval Certi fi cation EN50155 for Railway Applications GOST-R Certi fi ed RoHS CompliantDesigned to comply with:IEEE 1613 for Electric Utility Substations NEMA TS1/TS2 for Traf fi c ControlTHE INDUSTRIAL NETWORK COMPANYFiber Transceiver CharacteristicsFiber Length 2km*15km**40km**80km**TX Power Min -19dBm -15dBm -5dBm -5dBm RX Sensitivity Max -31dBm -31dBm -34dBm -34dBm Wavelength1310nm1310nm1310nm1550nm* Multimode Fiber Optic Cable ** Singlemode Fiber Optic CableTHE INDUSTRIAL NETWORKCOMPANYTHE INDUSTRIAL NETWORK COMPANYw w w.r e d l i o n.n e tConnect. Monitor. Control.Americas *****************Asia-Pacific ****************EuropeMiddle East Africa******************+1 (717) 767-6511ADLD0292 080116 © 2016 Red Lion Controls, Inc. All rights reserved. Red Lion, the Red Lion logo, N-Tron and Sixnet are registered trademarks of Red Lion Controls, Inc. All other company and product names are trademarks of their respective owners.As the global experts in c ommunic ation, monitoring and c ontrol for industrial automation and networking, Red Lion has been delivering innovative solutions for over forty years. Our automation, Ethernet and cellular M2M technology enables companies worldwide to gain real-time data visibility that drives produc tivity. Produc t brands inc lude Red Lion, N-Tron and Sixnet. With headquarters in York, Pennsylvania, the company has offic es ac ross the Americ as, Asia-Pac ific and Europe. Red Lion is part of Spec tris plc , the produc tivity-enhanc ing instrumentation and controls company. For more information, please visit .。
降低客服业务流程错误的措施

降低客服业务流程错误的措施英文回答:Measures to Reduce Errors in Customer Service Business Processes.1. Establish clear and concise processes.Well-defined processes provide a framework for customer service representatives to follow, reducing the likelihood of errors. These processes should be documented and easily accessible to all staff.2. Train staff thoroughly.Proper training ensures that customer service representatives have the knowledge and skills to handle customer interactions effectively. Representatives should be trained on the company's products, services, and policies, as well as communication and problem-solvingtechniques.3. Use technology to automate tasks.Automation can reduce the risk of human error by eliminating manual processes. For example, automatedrouting systems can direct incoming calls to the most appropriate representative based on the customer's inquiry.4. Implement quality control measures.Monitoring and evaluating the performance of customer service processes is crucial for identifying and addressing areas for improvement. This can involve reviewing call recordings, customer feedback, and other metrics.5. Encourage a culture of continuous improvement.Foster a work environment where customer service representatives are encouraged to identify and suggest ways to improve processes. This can be achieved through regular feedback sessions, brainstorming workshops, and otherinitiatives.6. Empower customer service representatives.Empowering customer service representatives with the authority to make decisions can reduce the risk of errors. This allows representatives to resolve customer issues quickly and effectively, without having to consult with supervisors.7. Use knowledge management tools.Centralized knowledge management tools provide customer service representatives with easy access to up-to-date information and resources. This reduces the likelihood of errors due to outdated or inaccurate information.8. Leverage artificial intelligence (AI)。
中国移动GPON设备ONU要求V3.1

GPON设备ONU用户端设备要求目录1概述............................................................................................................................................. - 1 -2GPON系统参考模型..................................................................................................................... - 1 -3设备类型和接口......................................................................................................................... - 2 -3.1设备类型 (2)3.2设备接口 (3)3.2.1PON接口 ........................................................................................................................ - 3 -3.2.2用户侧接口................................................................................................................ - 3 -3.2.3管理接口(可选) .................................................................................................... - 4 -4设备功能要求............................................................................................................................. - 4 -4.1设备基本功能要求 (4)4.1.1动态带宽分配功能(DBA) .................................................................................... - 4 -4.1.2ONU的初始化自动配置................................................................................................ - 5 -4.1.3数据加密功能............................................................................................................ - 5 -4.1.4FEC(前向纠错)要求................................................................................................. - 5 -4.1.5ONU掉电通知功能........................................................................................................ - 5 -4.1.6光链路测量和诊断功能 ............................................................................................ - 6 -4.1.7PPPoE仿真拨号功能 .................................................................................................... - 6 -4.1.8设备管理方式............................................................................................................ - 6 -4.1.9POE/POE+功能............................................................................................................. - 6 -4.1.10时间同步.................................................................................................................... - 6 -4.2以太网功能要求 (7)4.2.1以太网基本功能要求 ................................................................................................ - 7 -4.2.2VLAN功能 ...................................................................................................................... - 8 -4.2.3策略控制功能............................................................................................................ - 9 -4.2.4流量镜像.................................................................................................................... - 9 -4.3组播功能 (9)4.3.1组播协议.................................................................................................................. - 10 -4.3.2组播功能.................................................................................................................. - 10 -4.3.3组播性能................................................................................................................... - 11 -4.4多业务Q O S机制 (11)4.4.1多业务QoS总体要求 ................................................................................................ - 11 -4.4.2业务等级协定(SLA) ............................................................................................ - 11 -4.4.3业务流分类功能 ....................................................................................................... - 11 -4.4.4优先级标记.............................................................................................................. - 12 -4.4.5优先级队列机制 ...................................................................................................... - 12 -4.4.6流限速...................................................................................................................... - 13 -4.4.7缓存管理.................................................................................................................. - 13 -4.5安全性要求 (13)4.5.1用户认证及用户接入线路(端口)标识 .............................................................. - 13 -4.5.3防DoS攻击 ............................................................................................................... - 15 -4.5.4UNI端口环路检测 ....................................................................................................... - 15 -4.5.5以太网OAM功能 .............................................................................错误!未定义书签。
Qos原理及配置(中文版)

语音、多媒体业务提供高质量的服务
Best-Effort 模型
Best-Effort是单一的服务模型,也是最简单的服务
模型。
应用程序可任意发送任意报文,不需要事先得到批
准或通知网络
网络尽最大可能发送这些报文,但对时延,可靠性
等性能不提供任何保障
Best-Effort
service是目前Internet的缺省服务模型,
令牌漏桶
流量监管采用“令牌漏桶”(Token Bucket)的算法,每种业 务都拥有相应数量的令牌(Token),令牌按照规定速率发出。
令牌桶的特点:令牌桶可被看是一个存放令牌的容器,它有一
定的容量。系统按设定的速度向桶中放置令牌,当桶中令牌满 时,多出的令牌溢出,桶中令牌不再增加
CAR 的配置
对出路由器A 以太网口1 的所有报文应用CAR 策略,对满足条 件的报文直接进行转发,丢弃不满足条件的报文
配置步骤
配置路由器Router A: # 对进入路由器A 以太网口0 的所有报文应用CAR 策略
[RouterA-Ethernet0]ip address 190.0.0.1 255.255.255.0 [RouterA-Ethernet0]qos car inbound any cir 8000 cbs 15000 ebs 8000 conform pass exceed discard
它尽力而为(Best-effort)地将报文送到目的地,但是对报文的
吞吐量、延迟、延迟抖动、丢包率等都不能预期,可能很好, 也可能极差,一切都要视网络状况而定。
随着计算机网络的高速发展,对带宽、延迟、抖动敏感的且实
时性强的语音、图象、重要数据同时在网上传输,使得网络资 源极大地丰富。但是同时人们对于网络传输数据质量的要求也
QOS

QOS(quality of service)服务质量一、我们为什么需要QOS?ck of bandwidth 缺少带宽2.delay 延时i:处理延时ii:队列延时iii:传输延时3.packet drop 丢包(i:避免网络产生拥塞;ii:给必要的流量保留一点的带宽)二、什么是qos?定义:在网络资源和带宽一定的情况下,避免网络产生拥塞和使某些流量的数据包优先得到转发和处理。
三、qos的实施?1.CLI 2.MQC(更具有灵活性)四、qos的三种模型?Best-Effort Service 尽力而为服务模型所有网络设备全部都是尽自己最大努力传输数据,所有数据尽管传,不需要得到许可,有多少传多少,任何数据都不能得到保证,延迟也无法预计,所以尽力而为服务模型,其实并没有实施任何 QOS,默认的网络都工作在这种模型下。
Integrated Service 综合服务模型,简称 Intserv该种模型也叫资源预留,也就是说给某种流量在网络里边预留一定的带宽,对流量所需带宽是一种绝对的保障。
例如一个视频程序在正常通信下需要 100K 的带宽,那么视频程序在连接之前,必须向网络申请自己需要 100K 的带宽,当网络同意后,视频便可连接,并且将保证能够得到 100K 的带宽,而不会有任何延迟。
Integrated service 使用RSVP协议来预留带宽I:在接口下启用RSVP协议,默认预留带宽为接口的75%。
Ii:发送预留带宽请求router(config)#ip rsvp sender 100.1.1.1 10.1.1.2 tcp 80 10000 12.1.1.2 f0/0 200 10说明:配置为目标地址 100.1.1.1,源地址 10.1.1.2,且目标端口为 TCP 80,源端口为10000,上一跳为 12.1.1.2,进口为 f0/0 的流量请求保留带宽 200Kbit,Bc 为 10Kbit。
5G 优化案例:5G游戏业务QoS保障案例

5G 游戏业务 QoS 保障案例XX目录QoS 保障异常问题........................................................................................... 错误!未定义书签。
一、承载和QoS 保障 (3)1.1承载 (3)1.2QoS 保障 (3)1.2.1PDCP 参数 (4)1.2.2MAC 调度参数 (4)1.2.3切换参数 (5)1.2.4NSA DC 默认承载配置 (5)二、问题描述 (6)三、问题根因........................................................................................... 错误!未定义书签。
四、经验总结 (10)5G游戏业务QoS保障案例XX【摘要】5G NSA 的专有承载 QoS 保障测试中,使用 QCI=3 专有承载后,业务时延有所降低。
本文主要探讨 QoS 保障的措施,分析了 QCI3 专载异常的原因。
【关键字】QoS 保障承载 QCI 默认承载PDPC MAC 调度【业务类别】优化方法一、基于QCI 承载的业务QoS 保障方法论承载是 QoS 的基本粒度,承载分为默认承载和专有承载。
QoS(Quality of Service)是业务传输质量的一种表述,也是业务传输质量的保障机制。
1.1承载一个 EPS 承载唯一标识某一个 UE 和一个服务网关之间同一种 QoS 的所有业务流。
承载分为默认承载和专有承载。
默认承载是在 PDN 连接存在期间会始终保持建立一个承载,来给UE 提供“永远在线”的 IP 连接。
专有承载是连接到相同 PDN 的其它 EPS 承载,当 UE 需要访问特定业务时,UE 和核心网之间就需要建立专有承载。
1.2QoS 保障不同的业务有不同的 QoS 要求,不同业务用户的体验要求不同,如语音要清晰、视频画面要流畅、浏览网页速度要快,需要将这些体验映射为各个节点能识别处理的技术参数,即QoS 参数,对于 QoS 最重要的参数是 QCI(QoS Class Identifier)和 ARP(Allocation and Retention Priority)。
智能管理级高速伸缩Gigabit Ethernet PoE+交换机数据表说明书

Control and Configure Beyond Plug-and-Play ConnectivityNETGEAR Smart Managed Plus Switches with PoE meets business networks growing need by providing fundamental network features such as simplified VLANs, QoS set-up and IGMP Snooping that will help optimize the performance of business networks. Smart Managed Plus Switches are the perfect upgrade from the plug-and-play unmanaged switch, delivering essential networking features at a very affordable price. The GS305EP/GS305EPP with 4-port PoE+ and GS308EP/GS308EPP with 8-port PoE+ models support Power-over-Ethernet (PoE) and can power devices such as VoIP phones, surveillance IP cameras, wireless access points and many other applications. These new Plus switches models include uninterruptable PoE to help optimize the performance and troubleshooting of business networks. The new and improved business-friendly GUI allows easy management and simple configuration. With the growing deployment of applications and an all-in-one solution, providing management and power to these applications would be ideal.Highlights• Enable network configuration andmanagement at the price point ofunmanaged switches• Simple, yet useful network set-up on top of plug-and-play connectivity• Business-friendly and easy-to-use web browser-based management GUI • VLAN support for traffic segmentation• Quality of Service (QoS) for traffic prioritization • Auto “denial-of-service” (DoS) prevention • Troubleshoot connection issues via cable test • Loop detection and broadcast storm controls • Rate limiting for better bandwidth allocation • Port mirroring for network monitoring • Jumbo frame support• Advanced features such as per port PoE controls• Uninterrupted PoE keeps PoE power on even when the switch is updating firmware or performing software reboot.• 802.3at standard offering 30W/port • Fanless and versatile mounting option (desktop and wall-mountable)IN UNMANAGED, WEB,& SMART SWITCHESSmall Office/Home Office Network DiagramTechnical SpecificationsFeatures GS305EP GS305EPP GS308EP GS308EPP 10/100/1000 RJ45 Copper Ports (Auto Uplink)5588 Enclosure Metal Metal Metal Metal Connector T ype Metal Metal Metal Metal PoE# of PoE ports4488# PoE+ 802.3at Ports4488T otal PoE/PoE+ Budget63W120W62W123W Uninterrupted PoE Yes Yes Yes Yes Performance SpecificationForwarding modes Store-and-forwardBandwidth10Gbps10Gbps16Gbps16Gbps Max MAC entries4K4K4K4K Buffer Size192KB192KB192KB192KB Energy Efficient Ethernet (IEEE 802.3az)compliant Yes Yes Yes Yes Priority queuing WRR WRR WRR WRR Jumbo frame support9,216 bytes9,216 bytes9,216 bytes9,216 bytes Acoustic noise level @ 25° C (dBA) (ANSI-S10.12)0000 Mean Time Between Failures (MTBF) @ 25° C1,164,104 hours853,770 hours859,126 hours842,428 hours L2 Services - VLANSVLAN (# Supported)64646464 IEEE 802.1Q VLAN T agging Yes Yes Yes Yes Port-based VLANs Yes Yes Yes YesL2 Services - AvailabilityLink Aggregation/Port Trunking Yes Yes Yes Yes Number of Static Manual LAGs and # of members2/42/42/42/4L2 Services - Multicast FilteringIGMP snooping (v1, v2, and v3)Yes Yes Yes Yes Block unknown multicast Yes Yes Yes Yes Supported Multicast groups128128128128L3 Services - DHCPDHCP client Yes Yes Yes YesTechnical SpecificationsQuality of Service GS305EP GS305EPP GS308EP GS308EPP Rate Limiting Yes Yes Yes Yes DSCP Yes Yes Yes Yes IEEE 802.1p COS Yes Yes Yes Yes Port-based VLAN Yes Yes Yes Yes WRR (Weighted Round Robin)Yes Yes Yes Yes Strict Priority queue technology No No No No IEEE Network Protocols• IEEE 802.3 Ethernet• IEEE 802.3ab 1000BASE-T • IEEE 802.3u 100BASE-T • IEEE 802.3ab 1000BASE-T • EEE 802.1p Class of Service • IEEE 802.1Q VLAN Tagging• IEEE 802.3x Full-duplex Flow Control • IEEE 802.3af PoE• IEEE 802.3at PoE+ManagementSystem Password Yes Yes Yes Yes Web browserbased management GUI Yes Yes Yes Yes PC Utility No No No No One-to-one Port Mirroring Yes Yes Yes Yes Cable T est Utility Yes Yes Yes Yes Config upload (to server)Yes Yes Yes Yes LEDsPer port Speed, Link, Activity, PoEPer device Power, system, PoE MaxPhysical SpecificationsDimensions (W x D x H)158 x 101 x 27 mm(6.2 x 4.0 x 1.1 in)158 x 101 x 27 mm(6.2 x 4.0 x 1.1 in)158 x 101 x 27 mm(6.2 x 4.0 x 1.1 in)158 x 101 x 27 mm(6.2 x 4.0 x 1.1 in)Weight 0.39 kg(0.86 lb)0.40 kg(0.88 lb)0.49 kg(1.08 lb)0.49 kg(1.08 lb)Environmental SpecificationsOperatingOperating temperature32° to 104°F (0° to 40°C)Humidity (relative)90% maximum relative humidity (RH), non-condensing Altitude10,000 ft (3,000 m) maximumStorageStorage temperature– 4° to 158°F (–20° to 70°C)Humidity (relative)95% maximum relative humidity (RH), non-condensing Altitude10,000 ft (3,000 m) maximumTechnical Specifications Electromagnetic Emissions and ImmunityCertifications CE mark, commercial FCC Part 15 class B CE/EN55032/24VCCIACMACSA safetyKCBSMIWarranty and SupportHardware Warranty (All Except China/India)5-year warrantyChina/India1-year warrantyExternal Power Adapter Warranty2-year warrantyT echnical Support (online, phone) 90 days free of T echnical Support with registrationProSUPPORT OnCall 24x7 Service PlansCategory S1: PMB0S11-10000S PMB0S31-10000S PMB0S51-10000SPackage ContentsAll ModelsNETGEAR Smart Managed Plus SwitchPower adapter Detachable power cable (varies by region)Wall installation kitRubber feetInstallation guide*This product comes with a limited warranty that is valid only if purchased from a NETGEAR authorized reseller, and covers unmodified hardware, fans and internal power supplies –not software or external power supplies, and requires product registration at https:///business/registration within 90 days of purchase; see https:///about/warranty for details. Intended for indoor use only.† NETGEAR #1 in US Market Share according to NPD data for Unmanaged and Smart Switches, September 2019. NETGEAR #1 in Europe Market Share according to Context data for Unmanaged and Smart Switches, September 2019.NETGEAR and the NETGEAR Logo are trademarks of NETGEAR, Inc. in the United States and/or other countries. Other brand names mentioned herein are for identification purposes only and may be trademarks of their respective holder(s). Information is subject to change without notice. ©NETGEAR, Inc. All Rights reserved.NETGEAR,Inc.350E.PlumeriaDrive,SanJose,CA95134-1911USA,1-888-NETGEAR(638-4327),E-mail:****************,D-GS305EP/GS305EPP/GS308EP/GS308EPP-16Oct20。
QoS模型术语详

QoS模型术语详解随着数据设备对QoS实现的越来越多,我们也应该更多地去关注QoS方面的知识。
但是在阅读QoS文献的时候,发现太多的QoS术语让我们对相关文档望而却步。
如果要对各种QoS模型做详尽的阐述,限于篇幅不太可能,而且也没有必要,因为关于QoS文献很多。
本文试图对QoS模型及其中的术语做深入浅出的解释,并给出出现该术语的RFC,以便大家做深入的了解,希望对大家的学习有所帮助。
QoSQoS,英文全称Quality of Service,即服务质量。
不同网络的服务质量指标不同,不同的组织对QoS也有不同的定义:电信网的QoS由ITU(国际电信联盟)定义;ATM网络的QoS由ATM论坛定义;IP网络的QoS由IETF定义。
IP QoSIP网络服务质量由RFC 2386定义,具体的服务质量指标可以量化为带宽、延迟、延迟抖动、丢失率和吞吐量等。
以下术语都是与IP QoS相关的术语。
QoS模型目前IETF定义了两种QoS模型:综合服务(IntServ)和区分服务(DiffServ),综合服务是一种基于资源预留的端到端服务质量模型;区分服务是基于每跳PHB的服务质量模型。
IntServ模型RFC1633定义的IntServ模型只是一个基本的体系架构,它规定了在网络上保证QoS 的一些基本要素。
IntServ的基本思想是网络中的每个网络单元,包括主机和路由器,在需要进行数据传输时首先在传输路径上进行资源预留,这种预留是基于流的,相比较DiffServ 来讲,属于精细粒度的预留。
IntServ模型可以用在视频流和音频流应用方面,它可以保证多媒体流在网络拥塞时不受干扰。
在IntServ中,Flow Specs作为资源预留的描述,RSVP 作为资源预留的信令。
Flow Specs中文翻译成流规范,流规范包括两个方面:1、流是什么样子的?在流描述(T-Specs,Traffic Specification)中定义。
logistics service quality

logistics service qualityLogistics service quality is a measure of how well a logistics provider is able to meet the requirements of its customers. It defines how efficient, reliable and cost-effective a logistics provider can be when it comes to delivering goods on time and at the right place. Logistics service quality covers various aspects, including customer service, product availability, delivery speed, safety, reliability, and value for money.Customer service is an important aspect of logistics service quality. A good logistics provider should be able to provide quality customer service to both business clients and individual consumers. This includes being available to answer questions, assist with order fulfillment, and quickly respond to any complaints or problems. The logistics provider should also have a comprehensive knowledge of the products they are shipping and be able to provide accurate information on those products.Product availability is another important component of logistics service quality. A good logistics provider should ensure that the products they are shipping are always in stock and ready to ship. This means that they should have an efficient system for monitoring inventory levels and be able to quickly restock any items that run out. Additionally, the logistics provider should also make sure that their products are shipped quickly and accurately.Delivery speed is one of the most important factors when it comes to logistics service quality. Customers want to get their orders as quickly as possible, and a good logistics provider should be able to provide this. The provider should be able to offer different options for delivery, such as express delivery or same-day delivery. Additionally, the logistics provider should be able to give customers an accurate estimate of whentheir orders will arrive.Safety is also a key factor when it comes to logistics service quality. The logistics providershould have procedures in place to ensure that the products they are shipping are safe and secure. This includes having secure packaging, using tracking numbers to monitor shipments, and making sure that all items are insured. Additionally, the logistics provider should be able to provide accurate information about the safety of their products to their customers.Reliability is also crucial to logistics service quality. Customers want to know that their orders will arrive on time and in the condition they were promised. A good logistics provider should have a system in place to track shipments to ensure that they arrive on time and without any issues. Additionally, the provider should also be able to quickly resolve any issues that arise during the course of the shipment.Finally, value for money is an important part of logistics service quality. Customers want to get the best deals for their orders, and a goodlogistics provider should be able to provide this. The provider should be able to offer competitiverates and discounts and should be willing to negotiate on pricing. Additionally, the provider should also be able to provide full transparency on their services and fees, so customers can make informed decisions when choosing a logistics provider.。
路由器QOS技术

网络拥塞的产生
流量聚合
100Mbps 100Mbps
Data-flow
民族 安全 创新 服务
网络拥塞的后果
尾丢弃(Tail Drop):当发生拥塞时,接口输出队列被占满, 后面要入队的报文被丢弃。 尾丢弃是最普通的丢弃机制,也是系统默认的丢弃机制。 对TCP流来讲,尾丢弃有以下缺陷: (1)TCP全局同步; (2)TCP饿死、延迟、抖动
服务模型,是指一组端到端的Qos功能 Best-Effort service 尽力而为服务 Integrated service (Intserv) 集成服务
Differentiated service (Diffserv) 区分服务
民族 安全 创新 服务
Best-Effort service
民族 安全 创新 服务
QOS技术目标
支持为用户提供专用带宽 减少报文的丢失率 避免和管理网络拥塞 流量整形 设置报文的优先级
民族 安全 创新 服务
课程内容
1
QOS技术概念 QOS服务模型
网络拥塞的产生和避免 拥塞管理技术
2
3 4 5
流量监管与流量整形
民族 安全 创新 服务
QOS服务模型
民族 安全 创新 服务
Differentiated service
Differentiated service 区分服务
Diffserv是一个多服务模型,可以满足不同的Qos维护状态,它根据每个报文指定的QoS,来提供特定的 服务,包括进行报文的分类、流量整形、流量监管和排队。 主要实现技术包括CAR,队列技术。
router1(config)#interface serial 0/0
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
40
40
Call Blocking Rate (%)
30
30
20
20
10
10
0 150
200
a MCI: 60 40 Audio Video
50
Bandwidth Blocking Rate (%)
250 300 350 Traffic Load (MB/s)
400
450
0 120
160
b Clustered: All Video
Shortest,distP; 1 =
k X1 i=1
Ri
where R1; ; Rk are the bandwidths available on the links on path P. This algorithm has been shown to be e ective when selecting routes for high-bandwidth connections Ma et.al, 1996. Our study uses two topologies Figure 1. The tra c load is a combination of audio and video sessions. We assume that the requested bandwidth is uniformly distributed between 16 64 kilobits second for an audio session,
Widest-shortest path: a feasible path with the minimum hop count.
If there are several such paths, the one with the maximum bandwidth is selected. If several such paths exist, one is randomly selected. Shortest-widest path: a feasible path with the maximum bandwidth. If there are several such paths, the one with the minimum hop count is selected. If several such paths exist, one is randomly selected. Dynamic-alternative path: a widest minimal-hop path. If no feasible minimal hop path exists, nd the widest path that is one hop longer. If several such paths exist, one is randomly selected. Reject the request otherwise. Shortest-distP; 1: a path with the shortest distance
200 240 Traffic Load (MB/s)
280
320
Figure 2 Blocking rate as a function of an evenly distributed network load
40 Widest-Shortest Shortest-Widest Shortest-Dist(P, 1) Dynamic-Alternative
30
20
300 340 Traffic Load (MB/s)
380
Figure 3 Call blocking rate as a function of network load: MCI topology,
100 Video tra c, Unevenly distributed load and between 1 5 megabits second for a video session. Sessions have a Poisson arrival rate. Based on Bolotin 1994, we use a lognormal long-tail call holding time distribution. All four algorithms use the dynamic link state information residual bandwidth with a refresh rate of 30 seconds. A common performance metric for tra c with bandwidth guarantees metric is the Call Blocking Rate, the percentage of session requests that is rejected. This metric is however misleading if sessions can request di erent amounts of bandwidth. Thus, we introduce a new metric, the Bandwidth Blocking Rate, which takes the session bandwidth into account: bandwidthi bandwidth blocking rate = Pi bandwidthi i
BANDWIDTH GUARANTEES
50
Bandwidth Blocking Rate (%)
3
Widest-Shortest Shortest-Widest Shortest-Dist(P, 1) Dynamic-Alternative
50 Widest-Shortest Shortest-Widest Shortest-Dist(P, 1) Dynamic-Alternative
b Clustered Topology
Figure 1 Topologies
2 BANDWIDTH GUARANTEES
For services with bandwidth guarantees, QoS routing tries to identify a feasible path, i.e. a path on which all links have an unserved bandwidth that is higher than the requested bandwidth. Several path selection algorithms have been proposed see Section 4, but a systematic evaluation of algorithms is missing. In this section we present initial results of a simulation study comparing the following four algorithms:
Quality-of-Service QoS routing tries to select a path that satis es a set of QoS constraints, while also achieving overall network resource e ciency. We present initial results on QoS path selection for tra c requiring bandwidth and delay guarantees. For tra c with bandwidth guarantees, we found that several routing algorithms that favor paths with fewer hops perform well. For tra c with delay guarantees, we show that for a broad class of WFQ-like scheduling algorithms, the problem of nding a path satisfying bandwidth, delay, delay-jitter, and or bu er space constraints while at the same time deriving the bandwidth that has to be reserved to meet these constraints, is solvable by a modi ed version of the Bellman-Ford shortest-path algorithm in polynomial time. Routing, quality of service, integrated services networks
Quality-of-Service Routing for Tra c with Performance Guarantees
Qingming Ma and Peter Steenkiste Computer Science Department, Carnegie Mellon University Pittsburgh, PA 15213, USA, fqma, prsg@
c IFIP 1997. Published by Chapman & Hall
2
Quality-of-Service Routing for Tra c with Performance Guarantees
T3 OC3
45 Mbs 100 Mbs 155 Mbs
a MCI topology
Abstract
