Definition and diagnostics for the model-observations - Knmi定义与诊断模型的观察——KNMI共16页
什么是 NDT

什么是 NDT ?NDT 是无损检测的英文(Non-destructive testing)缩写。
NDT 是指对材料或工件实施一种不损害或不影响其未来使用性能或用途的检测手段。
通过使用 NDT,能发现材料或工件内部和表面所存在的缺欠,能测量工件的几何特征和尺寸,能测定材料或工件的内部组成、结构、物理性能和状态等。
NDT 能应用于产品设计、材料选择、加工制造、成品检验、在役检查(维修保养)等多方面,在质量控制与降低成本之间能起最优化作用。
NDT 还有助于保证产品的安全运行和(或)有效使用。
NDT 包含了许多种已可有效应用的方法,最常用的 NDT 方法是:射线照相检测、超声检测、涡流检测、磁粉检测、渗透检测、目视检测、泄漏检测、声发射检测、射线透视检测等。
由于各种 NDT 方法,都各有其适用范围和局限性,因此新的 NDT 方法一直在不断地被开发和应用。
通常,只要符合 NDT 的基本定义,任何一种物理的、化学的或其他可能的技术手段,都可能被开发成一种 NDT 方法。
在我国,无损检测一词最早被称之为探伤或无损探伤,其不同的方法也同样被称之为探伤,如射线探伤、超声波探伤、磁粉探伤、渗透探伤等等。
这一称法或写法广为流传,并一直沿用至今,其使用率并不亚于无损检测一词。
在国外,无损检测一词相对应的英文词,除了该词的前半部分——即 non-destructive 的写法大多相同外,其后半部分的写法就各异了。
如日本习惯写作 inspection,欧洲不少国家过去曾写作 flaw detection、现在则统一使用 testing,美国除了也使用 testing 外,似乎更喜欢写作 examination 和 evaluation。
这些词与前半部分结合后,形成的缩略语则分别是 NDI、NDT 和 NDE,翻译成中文就出现了无损探伤、无损检查(非破坏检查)、无损检验、无损检测、无损评价等不同术语形式和写法。
实际上,这些不同的英文及其相应的中文术语,它们具有的意义相同,都是同义词。
ford 福特 全合成手动变速箱油 msds说明书

SAFETY DATA SHEET1. IdentificationFull Synthetic Manual Transmission FluidProduct identifierOther means of identification175246FIR No.Transmission fluidRecommended useNone known.Recommended restrictionsManufacturer/Importer/Supplier/Distributor informationCompany Name Ford Motor CompanyAddress Attention: MSDS Information, P.O. Box 1899Dearborn, Michigan 48121USATelephone1-800-392-3673SDS Information1-800-448-2063 (USA and Canada)Emergency telephonenumbersPoison Control Center: USA and Canada: 1-800-959-3673INFOTRAC (Transportation): USA and Canada 1-800-535-50532. Hazard(s) identificationNot classified.Physical hazardsNot classified.Health hazardsNot classified.Environmental hazardsNot classified.OSHA defined hazardsLabel elementsNone.Hazard symbolSignal word None.Hazard statement The mixture does not meet the criteria for classification.Precautionary statementPrevention Observe good industrial hygiene practices.Response Wash hands after handling.Storage Store away from incompatible materials.Disposal Dispose of waste and residues in accordance with local authority requirements.Hazard(s) not otherwise classified (HNOC)Direct contact with eyes may cause temporary irritation. Frequent or prolonged contact may defat and dry the skin, leading to discomfort and dermatitis. Inhalation of vapors/fumes generated by heating this product may cause respiratory irritation with throat discomfort, coughing or difficulty breathing.Supplemental information None.3. Composition/information on ingredientsMixturesCAS numberCommon name and synonymsChemical name%68649-42-3 Phosphorodithioic acid,O,O-di-C1-14-alkyl esters, zincsalts2 - 5Specific chemical identity and/or exact percentage (concentration) of composition has been withheld as a trade secret. 4. First-aid measuresMove to fresh air. Call a physician if symptoms develop or persist.InhalationWash off with soap and water. Get medical attention if irritation develops and persists.Skin contact Rinse with water. Get medical attention if irritation develops and persists.Eye contact Rinse mouth. Get medical attention if symptoms occur.IngestionDirect contact with eyes may cause temporary irritation.Most importantsymptoms/effects, acute and delayedTreat symptomatically.Indication of immediatemedical attention and special treatment needed Ensure that medical personnel are aware of the material(s) involved, and take precautions to protect themselves.General information5. Fire-fighting measuresFoam. Powder. Carbon dioxide (CO2).Suitable extinguishing media Do not use water jet as an extinguisher, as this will spread the fire.Unsuitable extinguishing mediaDuring fire, gases hazardous to health may be formed. Upon decomposition, this product emits carbon monoxide, carbon dioxide and/or low molecular weight hydrocarbons.Specific hazards arising from the chemicalSelf-contained breathing apparatus and full protective clothing must be worn in case of fire.Special protective equipment and precautions for firefighters Move containers from fire area if you can do so without risk.Fire fightingequipment/instructions Use standard firefighting procedures and consider the hazards of other involved materials.Specific methods No unusual fire or explosion hazards noted.General fire hazards6. Accidental release measuresAvoid inhalation of vapors or mists. Avoid contact with eyes, skin, and clothing. Keep unnecessary personnel away. For personal protection, see section 8 of the SDS.Personal precautions,protective equipment and emergency procedures The product is immiscible with water and will spread on the water surface.Large Spills: Stop the flow of material, if this is without risk. Dike the spilled material, where this is possible. Absorb in vermiculite, dry sand or earth and place into containers. Following product recovery, flush area with water.Small Spills: Wipe up with absorbent material (e.g. cloth, fleece). Clean surface thoroughly to remove residual contamination.Never return spills to original containers for re-use. For waste disposal, see section 13 of the SDS.Methods and materials for containment and cleaning upAvoid discharge into drains, water courses or onto the ground.Environmental precautions7. Handling and storageAvoid breathing mist or vapor. Avoid contact with eyes, skin, and clothing. Observe good industrial hygiene practices. For personal protection, see section 8 of the SDS.Precautions for safe handling Store in original tightly closed container. Store away from incompatible materials (see Section 10of the SDS).Conditions for safe storage,including any incompatibilities8. Exposure controls/personal protectionOccupational exposure limitsNot established.No biological exposure limits noted for the ingredient(s).Biological limit values Use adequate ventilation to control airborne concentrations below the exposure limits/guidelines. If user operations generate a vapor, dust and/or mist, use process enclosure, appropriate local exhaust ventilation, or other engineering controls to control airborne levels below the recommended exposure limits/guidelines.Appropriate engineering controlsIndividual protection measures, such as personal protective equipmentWear safety glasses with side shields (or goggles).Eye/face protectionSkin protectionSuitable chemical protective gloves should be worn when the potential exists for skin exposure.The choice of an appropriate glove does not only depend on its material but also on other quality features and is different from one producer to the other. Nitrile gloves are recommended.Hand protectionWear appropriate chemical resistant clothing if applicable.OtherIf engineering controls do not maintain airborne concentrations to a level which is adequate to protect worker health, an approved respirator must be worn. Respirator selection, use and maintenance should be in accordance with the requirements of OSHA Respiratory Protection Standard 29 CFR 1910.134 and/or Canadian Standard CSA Z94.4.Respiratory protectionWear appropriate thermal protective clothing, when necessary.Thermal hazards Always observe good personal hygiene measures, such as washing after handling the material and before eating, drinking, and/or smoking. Routinely wash work clothing and protective equipment to remove contaminants.General hygiene considerations9. Physical and chemical propertiesAppearanceLiquid.Physical state Liquid.Form Amber.Color Oily.OdorOdor threshold Not available.pHNot available.Melting point/freezing point Not available.Initial boiling point and boiling range Not available.Flash point 366.8 °F (186.0 °C) Cleveland Closed Cup Evaporation rate Not available.Not applicable.Flammability (solid, gas)Upper/lower flammability or explosive limits Flammability limit - lower(%)Not available.Flammability limit - upper (%)Not available.Explosive limit - lower (%)Not available.Explosive limit - upper (%)Not available.Vapor pressure Not available.Vapor density Not available.Relative density0.872Relative density temperature 59 °F (15 °C)Solubility(ies)Solubility (water)Insoluble Partition coefficient (n-octanol/water)> 3Auto-ignition temperature Not available.Decomposition temperature Not available.Viscosity76 cSt Viscosity temperature 104 °F (40 °C)Other informationDensity0.87 g/cm³ @ 15°C10. Stability and reactivityThe product is stable and non-reactive under normal conditions of use, storage and transport.Reactivity Material is stable under normal conditions.Chemical stabilityNo dangerous reaction known under conditions of normal use.Possibility of hazardous reactionsContact with incompatible materials.Conditions to avoid Strong oxidizing agents.Incompatible materials Upon decomposition, this product emits carbon monoxide, carbon dioxide and/or low molecular weight hydrocarbons.Hazardous decomposition products11. Toxicological informationInformation on likely routes of exposureInhalationInhalation of vapors/fumes generated by heating this product may cause respiratory irritation with throat discomfort, coughing or difficulty breathing. Prolonged inhalation may be harmful.Skin contact Frequent or prolonged contact may defat and dry the skin, leading to discomfort and dermatitis.Eye contact Direct contact with eyes may cause temporary irritation.IngestionIngestion may cause gastrointestinal irritation, nausea, vomiting and diarrhea.Symptoms related to the physical, chemical andtoxicological characteristics Direct contact with eyes may cause temporary irritation.Information on toxicological effectsAcute toxicityNot expected to be hazardous by OSHA criteria.Prolonged skin contact may cause temporary irritation.Skin corrosion/irritation Direct contact with eyes may cause temporary irritation.Serious eye damage/eye irritationRespiratory or skin sensitizationRespiratory sensitizationNot a respiratory sensitizer.This product is not expected to cause skin sensitization.Skin sensitization No data available to indicate product or any components present at greater than 0.1% are mutagenic or genotoxic.Germ cell mutagenicity CarcinogenicityThis product is not considered to be a carcinogen by IARC, ACGIH, NTP, or OSHA. Base oil severely refined: Not carcinogenic in animal studies. Representative material passes IP-346,Modified Ames test, and/or other screening tests.This product is not expected to cause reproductive or developmental effects.Reproductive toxicitySpecific target organ toxicity -single exposureNot classified.Specific target organ toxicity -repeated exposure Not classified.Aspiration hazard Not an aspiration hazard.Chronic effectsProlonged inhalation may be harmful.12. Ecological informationThe product is not classified as environmentally hazardous. However, this does not exclude the possibility that large or frequent spills can have a harmful or damaging effect on the environment.EcotoxicityNo data is available on the degradability of this product. Persistence and degradabilityBioaccumulative potentialPartition coefficient n-octanol / water (log Kow)Full Synthetic Manual Transmission Fluid > 33No data available.Mobility in soil Other adverse effectsNo other adverse environmental effects (e.g. ozone depletion, photochemical ozone creation potential, endocrine disruption, global warming potential) are expected from this component.13. Disposal considerationsCollect and reclaim or dispose in sealed containers at licensed waste disposal site. Don't pollute.Conserve resources. Return used oil to collection centers.Disposal instructions Dispose in accordance with all applicable regulations.Local disposal regulationsThe waste code should be assigned in discussion between the user, the producer and the waste disposal company.Hazardous waste code Dispose of in accordance with local regulations. Empty containers or liners may retain some product residues. This material and its container must be disposed of in a safe manner (see:Disposal instructions).Waste from residues / unused productsSince emptied containers may retain product residue, follow label warnings even after container is emptied. Empty containers should be taken to an approved waste handling site for recycling or disposal.Contaminated packaging14. Transport informationDOTNot regulated as dangerous goods.IATANot regulated as dangerous goods.IMDGNot regulated as dangerous goods.Not established.Transport in bulk according toAnnex II of MARPOL 73/78 and the IBC Code15. Regulatory informationThis product is not known to be a "Hazardous Chemical" as defined by the OSHA Hazard Communication Standard, 29 CFR 1910.1200.US federal regulationsTSCA Section 12(b) Export Notification (40 CFR 707, Subpt. D)Not regulated.CERCLA Hazardous Substance List (40 CFR 302.4)Phosphorodithioic acid, O,O-di-C1-14-alkyl esters, zinc salts (CAS 68649-42-3)Listed.SARA 304 Emergency release notificationNot regulated.Superfund Amendments and Reauthorization Act of 1986 (SARA)Immediate Hazard - No Delayed Hazard - No Fire Hazard - NoPressure Hazard - No Reactivity Hazard - NoHazard categoriesSARA 302 Extremely hazardous substanceNot listed.NoSARA 311/312 Hazardous chemicalSARA 313 (TRI reporting)Chemical name% by wt.CAS number Phosphorodithioic acid, O,O-di-C1-14-alkyl esters, zinc salts5.00000000000068649-42-3Other federal regulationsClean Air Act (CAA) Section 112 Hazardous Air Pollutants (HAPs) ListNot regulated.Clean Air Act (CAA) Section 112(r) Accidental Release Prevention (40 CFR 68.130)Not regulated.Not regulated.Safe Drinking Water Act(SDWA)California Safe Drinking Water and Toxic Enforcement Act of 1986 (Proposition 65): This material is not known to contain any chemicals currently listed as carcinogens or reproductive toxins.US state regulations International InventoriesAll components are listed or are exempt from listing on the Toxic Substances Control Act Inventory.16. Other information, including date of preparation or last revision02-08-2017Issue dateVersion 01Health: 1Flammability: 1Physical hazard: 0HMIS® ratingsHealth: 1Flammability: 1Instability: 0NFPA ratingsThis document was prepared by FCSD-Toxicology, Ford Motor Company, Fairlane Business Park IV, 17225 Federal Drive, Allen Park, MI 48101, USA, based in part on information provided by the manufacturer. The information on this data sheet represents our current data and is accurate to the best of our knowledge as to the proper handling of this product under normal conditions and in accordance with the application specified on the packaging and/or technical guidance literature.Any other use of the product which involves using the product in combination with any other product or any other process is the responsibility of the user. To the extent that there are anydifferences between this product’s Safety Data Sheet (SDS) and the consumer packaged product labels, the SDS should be followed.Preparation Information and DisclaimerXT-M5-QSPart number(s)。
中西医疗差异英文

Chinese Medicine
Employees a variety of therapies including global medicine, insurance, mass, dietary therapy, and exercise to restore balance and harmony within the body
02
Fundamental Differences between Eastern and Western
Medicine
Philosophical Basis
Chinese Medicine
Based on the concept of balance and harmony with nature Emphasis on the interconnectivity of bodily functions and the importance of qi (life force)
Western medicine, also known as allopathic medicine or biomedicine, is a system of medical practice that originated in Europe and later spread to other parts of the world
Western Medicine
Relies primary on physical examination, laboratory tests, imaging techniques, and other technical tools for diagnostics Focuses on identifying specific issues or conditions
Artisan Technology Group 产品说明书

PNOZ mc3pConfigurable Control System PNOZmultiContentsContents PageChapter 1Introduction1.1Validity of the documentation1-11.1.1Retaining the documentation1-11.2Overview of documentation1-21.3Definition of symbols1-3Chapter 2Overview2.1Unit structure2-12.1.1Scope of supply2-12.1.2Unit features2-12.2Front view2-2Chapter 3Safety3.1Intended use3-13.1.1System requirements3-13.2Safety regulations3-23.2.1Use of qualified personnel3-23.2.2Warranty and liability3-23.2.3Disposal3-23.2.4For your safety3-3Chapter 4Function description4.1Unit description4-14.1.1Operation4-14.1.2Input and output data4-14-24.1.3Assigning the inputs/outputs in thePNOZmulti Configurator to the EtherCATinputs/outputs4.1.4Block diagram4-2Chapter 5Installation5.1General installation guidelines5-15.1.1Dimensions5-15.2Connecting the base unit and expansion5-2modulesContentsChapter 6Commissioning6.1Wiring6-16.1.1General wiring guidelines6-16.1.2Connecting the supply voltage6-16.1.3PROFIBUS DP interface6-16.2Preparing for operation6-26.2.1Setting the station address6-26-26.2.2Download modified project to the controlsystem PNOZmulti6.2.3Connection example6-3Chapter 7Operation7.1Messages7-17.2Display elements7-27.2.1Display elements for device diagnostics7-2Chapter 8Technical Details8.1Technical Details8-18.2Order reference8-21Introduction1.1Validity of the documentationThis documentation is valid for the product PNOZ mc3p. It is valid untilnew documentation is published.This operating manual explains the function and operation, describesthe installation and provides guidelines on how to connect the product.1.1.1Retaining the documentationThis documentation is intended for instruction and should be retainedfor future reference.1Introduction1.2Overview of documentation1 IntroductionThe introduction is designed to familiarise you with the contents, struc-ture and specific order of this manual.2 OverviewThis chapter provides information on the product's most important fea-tures.3 SafetyThis chapter must be read as it contains important information on in-tended use.4 Function DescriptionThis chapter describes the product's mode of operation.5 InstallationThis chapter explains how to install the product.6 CommissioningThis chapter describes the product's commissioning and wiring.7 OperationThis chapter describes how to operate the product and gives tips in thecase of a fault.8 Technical DetailsThis chapter contains the product's technical details and order refer-ence.1Introduction2Overview2.1Unit structure2.1.1Scope of supply❝Expansion module PNOZ mc3p❝Jumper 774 6392.1.2Unit featuresUsing the product PNOZ mc3p:Expansion module for connection to a base unit from the configurablecontrol system PNOZmultiThe product has the following features:❝Can be configured in the PNOZmulti Configurator❝Connection for PROFIBUS-DP❝Station addresses from 0 ... 99, selected via rotary switch❝Status indicators for communication with PROFIBUS-DP and for er-rors❝24 virtual outputs on the control system PNOZmulti can be defined inthe PNOZmulti Configurator for communication with the fieldbusPROFIBUS DP. The number of inputs and outputs can be extendedto 128. Please note that when the extended inputs and outputs 24 -127 are used they have different properties (see document entitled"Communication Interfaces").❝Max. 1 PNOZ mc3p can be connected to the base unit❝Please refer to the document "PNOZmulti System Expansion" for thePNOZmulti base units that can be connected3.1Intended useThe expansion module PNOZ mc3p is used for communication be-tween the configurable control system PNOZmulti and PROFIBUS-DP.PROFIBUS-DP is designed for fast data exchange at field level. The ex-pansion module PNOZ mc3p is a passive subscriber (Slave) ofPROFIBUS-DP (DPV0). The basic functions of communication withPROFIBUS-DP conform to EN 50170. The central controller (Master)reads input information from the slaves and writes output information tothe slaves as part of each cycle. As well as the cyclical transfer of usabledata, PROFIBUS-DP can also be used for diagnostics and commission-ing functions. Data traffic is monitored on the Master/Slave side.The expansion module may only be connected to a base unit from theconfigurable control system PNOZmulti (please refer to the document"PNOZmulti System Expansion" for details of the base units that can beconnected)The configurable control system PNOZmulti is used for the safety-relat-ed interruption of safety circuits and is designed for use in:❝E-STOP equipment❝Safety circuits in accordance with VDE0113 Part 1 and EN60204-1The expansion module may not be used for safety-related functions.Intended use includes making the electrical installation EMC-compliant.The product is designed for use in an industrial environment. It is notsuitable for use in a domestic environment, as this can lead to interfer-ence.The following is deemed improper use in particular:❝Any component, technical or electrical modification to the product❝Use of the product outside the areas described in this manual❝Use of the product outside the technical details (see chapter entitled“Technical Details”)3.1.1System requirementsPlease refer to the "Product Modifications" document in the "Versionoverview" section for details of which versions of the base unit andPNOZmulti Configurator can be used for this product.3.2.1Use of qualified personnelThe products may only be assembled, installed, programmed, commis-sioned, operated, maintained and decommissioned by competent per-sons.A competent person is someone who, because of their training, experi-ence and current professional activity, has the specialist knowledge re-quired to test, assess and operate the work equipment, devices,systems, plant and machinery in accordance with the general standardsand guidelines for safety technology.It is the company's responsibility only to employ personnel who:❝Are familiar with the basic regulations concerning health and safety /accident prevention❝Have read and understood the safety guidelines given in this descrip-tion❝Have a good knowledge of the generic and specialist standards ap-plicable to the specific application.3.2.2Warranty and liabilityAll claims to warranty and liability will be rendered invalid if:❝The product was used contrary to the purpose for which it is intended❝Damage can be attributed to not having followed the guidelines in themanual❝Operating personnel are not suitably qualified❝Any type of modification has been made (e.g. exchanging compo-nents on the PCB boards, soldering work etc.).3.2.3Disposal❝In safety-related applications, please comply with the mission time t Min the safety-related characteristic data.❝When decommissioning, please comply with local regulations regard-ing the disposal of electronic devices (e.g. Electrical and ElectronicEquipment Act).3.2.4For your safetyThe unit meets all necessary conditions for safe operation. However,you should always ensure that the following safety requirements aremet:❝This operating manual only describes the basic functions of the unit.Information on the advanced functions can be found in the online helpfor the PNOZmulti Configurator and in the PNOZmulti technical cata-logue. Only use these functions after you have read and understoodthe documentation. All necessary documentation can be found on thePNOZmulti Configurator CD.❝Do not open the housing or make any unauthorised modifications.❝Please make sure you shut down the supply voltage when performingmaintenance work (e.g. exchanging contactors).4.1.1OperationThe virtual inputs and outputs that are to be transferred via PROFIBUSare selected and configured in the PNOZmulti Configurator. The baseunit and the expansion module PNOZ mc3p are connected via a jumper.The expansion module PNOZ mc3p is also supplied with voltage via thisjumper.The station address is set via rotary switches. After the supply voltage isswitched on or the PNOZmulti control system is reset, the expansionmodule PNOZ mc3p is configured and started automatically.LEDs indicate the status of the expansion module on PROFIBUS.The configuration is described in detail in the PNOZmulti Configurator'sonline help.4.1.2Input and output dataThe data is structured as follows:❝Input rangeThe inputs are defined in the master and transferred to the PNOZmul-ti. Each input has a number, e.g. input bit 4 of byte 1 has the numberi12.❝Output rangeThe outputs are defined in the PNOZmulti Configurator. Each outputthat is used is given a number there, e.g. o0, o5... The status of out-put o0 is stored in bit 0 of byte 0; the status of output o5 is stored inbit 5 of byte 0 etc.❝Output range only: Byte 3Bits 0 … 4: Status of LEDs on the PNOZmulti–Bit 0: OFAULT–Bit1:IFAULT–Bit 2: FAULT–Bit3:DIAG–Bit4:RUNBit 5: Data is being exchanged.Detailed information on data exchange (tables, segments) is available inthe document "Communication Interfaces" in the section entitled "Field-bus modules".5.2Connecting the base unit and expansion modulesYou can install a maximum of 1 PNOZ mc3p to the left of the base unit.❝Do not connect a terminator to the last expansion module on the left-hand side.❝Install the expansion module in the position in which it is configuredin the PNOZmulti Configurator.7.1MessagesWhen the supply voltage is switched on, the PNOZmulti safety systemcopies the configuration from the chip card.The LEDs "POWER","DIAG", "FAULT", "IFAULT" and "OFAULT" light upon the base unit.The expansion module PNOZ mc3p is configured and started automat-ically. The "ONLINE" and "OFFLINE" LEDs indicate the status of thePNOZ mc3p on PROFIBUS-DP.If the expansion module PNOZ mc3p does not receive a configurationfrom the base unit for a period of 30 s, the expansion modulePNOZ mc3p connects to PROFIBUS-DP and "ONLINE" status is dis-played on PROFIBUS-DP. The error message "External Error" is sent tothe Master.8.1Technical DetailsThe standards current on 2011-09 apply.Technical detailsElectrical dataModule's supply voltage via base unit 5 V DC Voltage tolerance -2 %/+2 %Power consumption 2.5 W Status display LED TimesSupply interruption before de-energisation 20 msFieldbus interface Fieldbus interface PROFIBUS DP Device type Slave Station address 0 - 99dTransmission rate 9.6 kBit/s - 12 MBit/sConnectionFemale 9-pin D-SUB connector Galvanic isolation yesTest voltage500 V ACEnvironmental data Ambient temperature 0 - 60 °C Storage temperature-25 - 70 °CClimatic suitability in accordance with EN 60068-2-30, EN 60068-2-7893 % r. h. at 40 °C Condensation not permitted EMCEN 61131-2Vibration to EN 60068-2-6Frequency10 - 150 Hz Max. acceleration1g Airgap creepage in accordance with EN 61131-2Overvoltage category III Pollution degree2Rated insulation voltage 30 V Shock stress EN 60068-2-2715g 11 msMechanical data Protection typeMounting (e.g. cabinet)IP54Housing IP20Terminals IP20DIN rail Top hat rail 35 x 7.5 EN 50022Recess width 27 mm Housing material Housing PPO UL 94 V0FrontABS UL 94 V0Dimensions Height 94.0 mm Width 22.5 mm Depth 119.0 mm Weight119 g8.2Order referenceOrder referenceProduct type Features Order no. PNOZ mc3p Fieldbus module, PROFIBUS-DP773 732Order reference: Terminator, jumperProduct type Features Order no. PNOZmulti bus terminator Terminator779 110 KOP-XE Jumper774 639...21010-E N -05, 2012-04 P r i n t e d i n G e r m a n y© P i l z G m b H & C o . K G , 2011+49 711 3409-444****************Pilz GmbH & Co. KG Felix-Wankel-Straße 273760 Ostfildern, Germany Telephone: +49 711 3409-0Telefax: +49 711 3409-133E-Mail:***************** Technical supportIn many countries we arerepresented by our subsidiaries and sales partners.Please refer to our homepage for further details or contact our headquarters.d u r a N E T p ®, P i l z ®, P I T ®, P M C p r o te g o ®, P M I ®, P N O Z ®, P r i m o ®, P S E N ®, P S S ®, P V I S ®, S af e t y B U S p ®, S a f e t y E Y E ®, S a f e t y N E T p ®, t h e s p i r i t o f s a f e t y ® a r e r eg i s t e r e d a n d p r o t e c t e d t r a d e m a r k s P i l z G m b H & C o . K G i n s o m e c o u n t r i e s . W e w o u l d p o i n t o u t th a t p r o d u c t f e a t u r e s m a y v a r y f r o m t h e d e t ai l s s t a t e d i n t h i s d o c u m e n t , d e p e n d i n g o n t h e s t a t u s a t t h e t i m e o f p u b l i c a t i o n a n d t h e s c o p e t h e e q u i p m e n t . W e a c c e p t n o r e s p o n s i b i l i t y f o r t h e v a l i d i t y , a c c u r a c y a n d e n t i r e t y o f t h e t e x t a n d g r a p h i c s p r e s e n t e d i n t h i s i n f o r m a t i o n . P l e a s e c o n t a c t o u r T e c h n i c a l S u p p o r t i f y o u h a v e a n y q u e s t i o n s .。
汽车法规--ISO9141-2的国际标准文档4(pdf 58)

SSF 14230Road Vehicles - Diagnostic SystemsKeyword Protocol 2000 - Part 2 - Data Link LayerSwedish Implementation StandardBased on ISO 14230-2 Data Link LayerStatus:Issue 1Date: April 22, 1997This document is based on the InternationalStandard ISO 14230 Keyword Protocol 2000 andhas been further developed to meet Swedishautomotive manufacturer's requirements by theSwedish Vehicle Diagnostics Task Force.It is based on mutual agreement between thefollowing companies:•Saab Automobile AB•SCANIA AB•Volvo Car Corp.•Volvo Bus Corp.•Mecel ABFile: 14230-2s.DOC / Definition by “Samarbetsgruppen för Svensk Fordonsdiagnos” / Author: L. Magnusson Mecel ABDocument updates and issue historyThis document can be revised and appear in several versions. The document will be classified in order to allow identification of updates and versions.A. Document status classificationThe document is assigned the status Outline, Draft or Issue.It will have the Outline status during the initial phase when parts of the document are not yet written.The Draft status is entered when a complete document is ready, which can be submitted for reviews. The draft is not approved. The draft status can appear between issues, and will in that case be indicated together with the new issue number E.g. Draft Issue 2.An Issue is established when the document is reviewed, corrected and approved.B. Version number and history procedureEach issue is given a number and a date. A history record shall be kept over all issues.Document in Outline and Draft status may also have a history record.C. HistoryIssue #Date Comment197 04 22Frst issueTable of Content1. SCOPE (1)2. NORMATIVE REFERENCE (2)3. PHYSICAL TOPOLOGY (3)4. MESSAGE STRUCTURE (4)4.1 Header (4)4.1.1 Format byte (4)4.1.2 Target address byte (5)4.1.2.1 Physical addressing (5)4.1.2.2 Functional addressing (5)4.1.3 Source address byte (5)4.1.4 Length byte (5)4.1.5 Use of header bytes (6)4.2 Data Bytes (6)4.3 Checksum Byte (6)4.4 Timing (7)4.4.1 Timing Exceptions (9)4.4.2 Periodic transmission (9)4.4.3 Server (ECU) Response Data Segmentation (12)4.5 End Of Message (12)5. COMMUNICATION SERVICES (13)5.1 StartCommunication Service (14)5.1.1 Service Definition (14)5.1.1.1 Service Purpose (14)5.1.1.2 Service Table (14)5.1.1.3 Service Procedure (14)5.1.2 Implementation (14)5.1.2.1 Key bytes (15)5.1.2.2 Fast Initialisation (17)5.2 StopCommunication Service (19)5.2.1 Service Definition (19)5.2.1.1 Service Purpose (19)5.2.1.2 Service Table (19)5.2.1.3 Service Procedure (19)5.2.2 Implementation (20)5.3 AccessTimingParameter Service (21)5.3.1 Service Definition (21)5.3.1.1 Service Purpose (21)5.3.1.2 Service Table (21)5.3.1.3 Service Procedure (22)5.3.2 Implementation (23)5.4 SendData Service (25)5.4.1 Service Definition (25)5.4.1.1 Service Purpose (25)5.4.1.2 Service Table (25)5.4.1.3 Service Procedure (25)5.4.2 Implementation (26)6. ERROR HANDLING (27)6.1 Error handling during physical/functional Fast Initialisation (27)6.1.1 Client (tester) Error Handling during physical/functional Fast Initialisation (27)6.1.2 Server (ECU) Error Handling during physical Fast Initialisation (27)6.1.3 Server (ECU) Error Handling during functional Fast Initialisation (28)6.2 Error handling after Initialisation (28)6.2.1 Client (tester) communication Error Handling (28)6.2.2 Server (ECU) communication Error Handling. physical addressing (29)6.2.3 Server (ECU) Error Handling, functional addressing (29)APPENDIX A - ARBITRATION1. DEFINITIONS (1)1.1 Random response time (1)1.2 Start bit detection (1)1.3 Transmission latency (1)1.4 Collision detection (1)2. MAINSTREAM COMMUNICATION (1)APPENDIX B - TIMING DIAGRAMS1. PHYSICAL ADDRESSING (1)1.1 Physical addressing - single positive response message (1)1.2 Physical addressing - more than one positive response message (3)1.3 Physical addressing - periodic transmission (5)2. FUNCTIONAL ADDRESSING (7)2.1 Functional addressing - single positive response message -single server (ECU) addressed (7)2.2 Functional addressing - more than one response message -single server (ECU) addressed (9)2.3 Functional addressing - single positive response message -more than one server (ECU) (11)2.4 Functional addressing - more than one response message -more than one server (ECU) (13)APPENDIX C - MESSAGE FLOW EXAMPLES1. PHYSICAL INITIALISATION - MORE THAN ONE SERVER (ECU) INITIALISED (1)2. PERIODIC TRANSMISSION MODE (4)2.1 Message Flow Example A (4)2.2 Message Flow Example B (5)IntroductionThis document (The Swedish Keyword Protocol 2000 Implementation Standard) is based on the ISO 14230-2 International Standard. Changes are indicated by changing the font from "Arial" to "Times New Roman"!It has been established in order to define common requirements for the implementation of diagnostic services for diagnostic systems.To achieve this, the standard is based on the Open System Interconnection (O:S:I.) Basic Reference Model in accordance with ISO 7498 which structures communication systems into seven layers. When mapped on this model, the services used by a diagnostic tester and an Electronic Control Unit (ECU) are broken into:- Diagnostic services (layer 7)- Communication services (layers 1 to 6)See figure 1 below.1. ScopeThis national Standard specifies common requirements of diagnostic services which allow a tester to control diagnostic functions in an on-vehicle Electronic Control Unit (e.g. electronic fuel injection, automatic gear box, anti-lock braking system,...) connected on a serial data link embedded in a road vehicle.It specifies only layer 2 (data link layer). Included are all definitions which are necessary to implement the services (described in "Keyword Protocol 2000 - Part 3:Implementation) on a serial link (described in "Keyword Protocol 2000 - Part 1: Physical Layer") Also included are some communication services which are needed for communication/session management and a description of error handling.This Standard does not specify the requirements for the implementation of diagnostic services.The physical layer may be used as a multi-user-bus, so a kind of arbitration or bus management is necessary. If arbitration is used it shall comply to the technique described in Attachment A. The car manufacturers are responsible for the correct working of bus management.Communication between ECUs are not part of this document.The vehicle diagnostic architecture of this standard applies to:• a single tester that may be temporarily or permanently connected to the on-vehicle diagnostic data link and• several on-vehicle electronic control units connected directly or indirectlySee figure 2 below.2. Normative ReferenceThe following standards contain provisions which, through reference in this text, constitute provisions of this document. All standards are subject to revision, and parties to agreement based on this document are encouraged to investigate the possibility of applying the most recent editions of the standards listed below. Members of ISO maintain registers of currently valid International Standards.ISO 7498-1:1984Information processing systems - Open systemsinterconnection - Basic reference model.SAE J-1979:Dec,1991E/E Diagnostic Test ModesSAEJ-2178 :June, 1993Class B Data Communication Network MessagesISO 14229:1996Road Vehicles - Diagnostic systems -Diagnostic Services SpecificationSSF 14230-1:1997Road Vehicles - Diagnostic systems - Keyword Protocol 2000 -Issue 2Part 1: Physical LayerSSF 14230-3:1996Road Vehicles - Diagnostic systems - Keyword Protocol 2000 -Draft Part 3: ImplementationISO 14230-4:1996Road Vehicles - Diagnostic systems - Keyword Protocol 2000 -Part 4: Requirements For Emission related Systems3. Physical topologyKeyword Protocol 2000 is a bus concept (s. diagram below). Figure 3 shows the general form of this serial link.Figure 3 - TopologyThe K-Line is used for communication and initialisation. Special cases are node-to-node-connections, that means there is only one ECU on the line, which also can be a bus converter.4. Message structureThis section describes the structure of a message.The message structure consists of three parts:• header• data bytes• checksumHeader Data bytes ChecksumFmt Tgt1 Src1 Len1SId2 . .Data2 . . CSmax . 4 byte max. 255 byte 1 byte1 bytes are optional, depending on format byte2 Service Identification, part of data bytesHeader and Checksum byte are described in this document. The area of data bytes always begins with a Service Identification. Use of the data bytes for communication services is described in this document. Use of the data bytes for diagnostic services is described in "Keyword Protocol 2000 - Part 3: Implementation".4.1 HeaderThe header consists of 3 or 4 bytes. A format byte includes information about the form of the message. A separate length byte allows message lengths up to 255 bytes.4.1.1 Format byteThe format byte contains 6 bit length information and 2 bit address mode information. The tester is informed about use of header bytes by the key bytes (s.5.1.2.1).msb lsbA1A0L5L4L3L2L1L0• A1,A0: Define the form of the header which will be used by the message:A1A0Mode Mnemonic HeaderMode210Header with address information, physical target address HM2 311Header with address information, functional target address HM3HM0 and HM1 are not defined in this document.HM3 (functional target address) shall only be used in request messages see §5.1.2.2.2• L5..L0: Define the length of the data field of a message, i.e. from the beginning of the data field (Service Identification byte included) to Checksum byte (not included). A message length of 1 to 63 bytes is possible. If L0 to L5 = 0 then the additional length byte is included.In the Swedish Implementation Standard L0 to L5 shall always be set to 0 (except in theStartCommunicationRequest message, see §5.1.2.2).This is the target address for the message. It may be a physical or a functional address. For emission related (CARB) messages this byte is defined in ISO 14230 KWP 2000 Part 4: Requirements For Emission related Systems.4.1.2.1 Physical addressingPhysical addressing (HM2) can be used in both request and response messages. The target address of a physically addressed request shall be interpreted as a physical server (ECU) address, the source address is the physical address of the client (tester).In the response message the target and source addresses are also physical addresses (HM2). Physical addresses shall be according to SAE J2178-Part 1, or as specified by the vehicle manufacturer.4.1.2.2 Functional addressingFunctional addressing (HM3) can only be used in request messages. The target address of a functionally addressed request shall be interpreted as a functional (group) address, the source address is the physical address of the client (tester).In the response messages the target and source addresses are physical addresses, i.e. response messages are always physically addressed (HM2).Functional addressing requires that the servers (ECUs) must support arbitration (see appendix A).4.1.3 Source address byteThis is the address of the transmitting device. It must be a physical address (also in the case where the target address is a functional address). There are the same possibilities for the values as described for physical target address bytes. Addresses for testers are listed in SAE J2178 Part 1, but the ECU must accept all tester addresses.4.1.4 Length byteThis byte is provided if the length in the header byte (L0 to L5) is set to 0. It allows the user to transmit messages with data fields longer then 63 bytes. With shorter messages it may be omitted. This byte defines the length of the data field of a message, i.e. from the beginning of the data field (Service Identification byte included) to Checksum byte (not included). A data length of 1 to 255 bytes is possible. The longest message consists of a maximum of 260 byte (255 data bytes + 4 bytes header + Checksum). For messages with data fields of less than 64 bytes there are two possibilities: Length may be included in the format byte or in the additional length byte. An ECU may support both possibilities, the tester is informed about this capability through the keybytes ( see section 5.1.2.1).Length Length provided inFmt byte Length byte< 64XX00 0000present< 64XXLL LLLL not present≥ 64XX00 0000presentXX: 2 bit address mode information (see §4.1.1)LL LLLL: 6 bit length informationIn the Swedish Implementation Standard the Length byte shall always be provided (L0 to L5 = 0) (except in the StartCommunicationRequest message, see §5.1.2.2).With the above definitions there are two different forms of message. These are shown diagramatically below.LengthFmt Tgt Src SId Data CSChecksumHeader with address information, no additional length byteLengthFmt Tgt Src Len SId Data CSChecksumHeader with address information, with additional length byteFmt Format byteTgt Target addressSrc Source addressLen additional length byteSId Service Identification byteData depending on serviceCS Checksum byte4.2 Data BytesThe data field may contain up to 255 bytes of information. The first byte of the data field is the Service Identification Byte. It may be followed by parameters and data depending on the selected service. These bytes are defined in "Keyword Protocol 2000 - Part 3: -Implementation" (for diagnostic services) and in section 5 of this document (for communication services).4.3 Checksum ByteThe Checksum byte (CS) inserted at the end of the message block is defined as the simple 8-bit sum series of all bytes in the message, excluding the Checksum.If the message is<1> <2> <3> ... <N> , <CS>where <i> (1 ≤ i ≤ N) is the numeric value of the i th byte of the message, then:<CS> = <CS>Nwhere <CS>i (i = 2 to N) is defined as<CS>i = { <CS> i-1 + <i> } Modulo 256 and <CS>1 = <1>Additional security may be included in the data field as defined by the manufacturer.4.4 TimingDuring normal operation the following timing parameters are relevant:Value DescriptionP1Inter byte time in ECU response.P2Time between end of tester request and start of ECU response, or time between end of ECU response and start of next ECU response.The next ECU response may be from the same ECU or it may be from another ECUin case of functional addressing.P3Time between end of ECU response and start of new tester request, or time between end of tester request and start of new tester request if ECU fails torespond.P3 shall be measured from the last byte in the latest response message from anyECU responding.P4Inter byte time in tester request.There are two sets of default timing parameters, normal and extended. Only normal timing parameters are supported by this document (Swedish Implementation Standard).Table 1a shows the timing parameters which are used as default (all values in ms).Table 1a - Normal Timing Parameter Set, default valuesTiming min. values max. valuesParameter default defaultP1020P2 P2*2525505000P3555000P4520Note: The timing parameter P2* becomes active if the server (ECU) responds with Negative response and the response code $78 "reqCorrectlyRcvd-RspPending", see §4.4.1.The values of the timing parameters may be changed with the communication service "AccessTimingParameters" (see §5.3).Table 1b shows the resolution and the possible limits within which the timing parameters can be changed with AccessTimingParameters (ATP).Table 1b -Normal Timing Parameter Set, lower and upper limitsAll values in msTiming Min. values Max. valuesParameter Lower limit Resolution 1Upper limit Resolution 1P10---20---P200.589600 ; ∞see Table 1cP300.563500∞250 see note 2P400.520---1) Min./Max. value calculation method [ms] = ATP parameter value * Resolution2) ATP parameter value = $FF => Max. value = ∞Table 1c - P2max Timing Parameter calculationTiming Parameter Hex valueof ATPparamete rResolutionin [ms]valuein [ms]Maximum value calculation methodin [ms]P2max01 to F02525 to 6000(hex value) - (Resolution) F1F2F3F4F5F6 F7 F8 F9 FA FB FC FD FE see maximumvaluecalculationmethod640012800192002560032000384004480051200576006400070400768008320089600(low nibble of hex value) - 256 - 25Example of $FA:($0A - $0100) - 25 = 64000FF---∞= ∞The P2max timing parameter calculation uses 25 [ms] resolution in the range of $01 to $F0.Beginning with $F1 a different calculation method shall be used by the server and the client in order to reach P2max timing values greater than 6000 [ms].Calculation Formula for P2max values > $F0Calculation_Of_P2max [ms] = (low nibble of ATP parameter P2max) * 256 * 25Note:The P2max timing parameter value shall always be a single byte value in the AccessTimingParameter service. The timing modifications shall be activated by implementation of the AccessTimingParameter service.Users must take care for limits listed above and the following restrictions:P3min > P2max(to avoid collisions in case of func. addressing or data segm.)P3min > P4min(to guarantee that the ECU can receive the first byte)Pimin < Pimax for i=1,...,4When the tester and listening ECUs detect the end of a message by time-out, the following restrictions are also valid:P2min > P4maxP2min > P1maxIt is in the system designers responsibility to ensure proper communication in the case of changing the timing parameters from the default values.He also has to make sure that the chosen communication parameters are possible for all ECUs which participate in the session.The possible values depend on the capabilities of the ECU. In some cases the ECU possibly needs to leave its normal operation mode for switching over to a session with different communication parameters.For complete timing diagrams see appendix B.4.4.1 Timing ExceptionsThe extended P2 timing window is a possibility for (a) server(s) to extend the time to respond on a request message. A timing exception is only allowed with the use of one or multiple negative response message(s) with response code $78 (requestCorrectlyReceived-ResponsePending) by the server(s). This response code shall only be used by a server in case it cannot send a positive or negative response message based on the client's request message within the active P2 timing window.After the transmission of the first negative response message, with response code $78, from the server (ECU) the timing parameter P2* becomes active, instead of the original timing parameter P2, in both the server and the client.The timing parameter P2* shall be generated as described in the following formula: P2*min = P2minP2*max = P3maxThe server(s) shall send multiple negative response messages with the negative response code $78 if required.As soon as the server has completed the task (routine) initiated by the request message it shall send either a positive or negative response message (with a response code other than $78) based on the last request message received. When the client has received the response message, which has been preceded by the negative response message(s) with response code $78, the timing parameter P2 becomes active again in both the server and the client. The client shall not repeat the request message after the reception of a negative response message with response code $78.4.4.2Periodic transmissionThe Keyword Protocol 2000 Periodic Transmission Mode shall be enabled by starting a diagnostic session with the startDiagnosticSession service and the diagnosticMode (DCM_) parameter set to $82 for PeriodicTransmission.PeriodicTransmission shall be supported in connection with physical addressing, normal and modified timing. The description below explains in steps how the PeriodicTransmission mode shall be activated, handled and de-activated.Step #1:To enable the PeriodicTransmission mode in the client (tester) and the server (ECU) the client (tester) shall transmit a startDiagnosticSession request message containing thediagnosticMode parameter for the PeriodicTransmission. After the reception of the firstpositive response message from the server (ECU) the PeriodicTransmission mode isenabled and periodic transmission mode communication structure and timing becomesactive. From now on, the server (ECU) shall periodically transmit the last responsemessage with current (updated, if available) data content, until the client (tester) sends arequest message within the timing window P3*. The timing parameters can be changedwithin the possible limits of the periodic transmission timing parameter set (see Table1d) with the communication service AccessTimingParameters.Step #2:After reception of any request message within the timing window P3*, the server (ECU) shall periodically transmit the corresponding response message which can be either apositive or a negative response message.Step #3:After reception of a stopDiagnosticSession or stopCommunication request message within the timing window P3*, the server (ECU) shall transmit the correspondingpositive response message only once.After reception of a stopDiagnosticSession or stopComunication positive responsemessage the periodicTransmissionMode is disabled and the default diagnostic sessionwith the default timing values, defined by the key bytes becomes active.After reception of a stopDiagnosticSession or stopComunication negative responsemessage the periodicTransmissionMode shall continue. In such case the server (ECU)shall transmit negative response messages unless the client (tester) sends a new requestmessage within the timing window P3*.During the standardDiagnosticModeWithPeriodicTransmission the following rules have to be considered:1.The client (tester) has to ignore the original timing window P3 and shall generate a new timingparameter for the jump-in timing window, which is called from now on P3*.The timing parameter P3* shall be generated as described in the following formula:P3*max = P2min - 2 msP3*min = P3minNote: The original P3max timing parameter is only used for time out detection during negative response message handling with the response code $78 "reqCorrectlyRcvd-RspPending".2.The timing window P3*, which starts at P3*min and ends at P3*max, shall be at least 5ms. It isimportant for the client (tester) to guarantee a minimum size of the jump-in window for the start of a request message.3.The timing window P3* starts and ends before the timing window P2 starts.4.P1max shall not exceed P2min. This is required in order to support resynchronisation betweenthe server (ECU) and client (tester) to meet the error handling requirements.5.Default and optimised timing parameter valuesThe timing table below specifies the timing parameter values with the diagnostic mode standardDiagnosticModeWithPeriodicTransmission.Table 1d -Timing parameter - periodic transmission.All values in msTiming minimum values maximum valuesParameter lower limit default resolution 1default upper limit resolution 1 P100---20200.5P27250.55089600; ∞see Table 1cP2* 37250.5500063500∞250 see note 2P3050.5500063500∞250 see note 2P3* 4050.523125.50.5P4050.520200.51) Min./Max. value calculation method [ms] = ATP parameter value * Resolution2) ATP parameter value = $FF => Max. value = ∞3) The timing parameter P2* becomes active if the server (ECU) responds with Negative response and the response code $78 "reqCorrectlyRcvd-RspPending", see §4.4.14) The timing parameter P3* can be changed, indirectly, by changing the timing parameters P2 and P3 with the service “AccessTimingParameters”.6.When implementing the standardDiagnosticModeWithPeriodicTransmission the followinglimits and restrictions must be considered as listed below:•Pimin < Pimax for i=1, ,4•P1max < P2min•P3min ≤ P2min - 10msIt is the system designers responsibility to ensure proper communication in the case of changing the timing parameters from their default values.It is also the system designers responsibility to ensure proper communication when periodic transmission is used in combination with multiple diagnose, see §5.1.2.2.For complete timing diagrams and message flow examples see appendix B and C.4.4.3Server (ECU) Response Data SegmentationServer (ECU) Response Data Segmentation is used if a client (tester) has sent a request message which causes the server (ECU) to split the response message content (data bytes) into several data segments. The data segments shall be transmitted consecutively in repeated response messages. Each message shall be transmitted within the timing window P2. The data field of each response message shall consist of the Service ID and the corresponding data segment (see figure 5).Data segmentation shall be detected by the client (tester) by comparing source addresses and Service IDs which must be identical for all response messages during segmentation.Server (ECU) response data segmentation shall only be used when the data length exceeds the maximum length that the server (ECU) can transmit in a single message. Data segmentation shall not be supported in periodic transmission mode.This procedure shall also be used to meet the requirements of ISO 14230-4 Keyword Protocol 2000 - Part 4: Requirements For Emission Related Systems.If data segmentation is used the following restriction shall apply:P3min > P2max4.5End Of MessageThe end of a received message shall be detected as:Number of bytes received equals message length (as defined in the format byte or length byte) orTime-out of inter byte time in the received message (P1max exceeded in ECU transmission, P4max exceeded in tester transmission)whichever occurs first.5. Communication servicesSome services are necessary to establish and maintain communication. They are not diagnostic services because they do not appear on the application layer. They are described in the formal way and with the conventions defined in ISO/WD 14229, i.e. a definition of the service purpose, a service table and a verbal description of the service procedure. A description of implementation on the physical layer of Keyword Protocol 2000 is added.The StartCommunication Service and the AccessTimingParameters Service are used for starting a diagnostic communication. In order to perform any diagnostic service, communication must be initialised and the communication parameters need to be appropriate to the desired diagnostic mode. A chart describing this is shown in figure 6.Figure 6 - Use of communication services。
斑马技术公司DS8108数字扫描仪产品参考指南说明书

对医学伦理的看法和建议英语作文300词

医学伦理:挑战与建议In the realm of healthcare, ethics plays a pivotal role, guiding practitioners in their decisions and actions. As medicine advances, so do the ethical challenges it faces.In this essay, I delve into the complexities of medical ethics, offering insights and recommendations foraddressing these challenges.Firstly, the principle of non-maleficence, or doing no harm, is fundamental to medical ethics. However, with the advent of innovative technologies like genetic editing and advanced diagnostics, the definition of harm has expanded. For instance, the ethical implications of altering aperson's genetic code to prevent future diseases are profound and far-reaching. It raises questions about the limits of medical intervention and the potential misuse of technology.Secondly, the principle of beneficence, or doing good,is equally important. Medical professionals have a duty to promote the well-being of their patients. However, this can be complicated by resource allocation issues, especially in settings where healthcare resources are limited. Forinstance, in times of pandemics or disasters, decisions about who receives care and who does not can be fraught with ethical dilemmas.To address these challenges, I propose several recommendations. Firstly, continuous education and training for medical professionals on ethical principles and their application in real-world scenarios is crucial. This will help practitioners make informed decisions in complex ethical situations.Secondly, the involvement of patients and theirfamilies in ethical decision-making is essential. Patients have a right to understand the ethical implications oftheir treatment options and make informed choices. Medical professionals should strive to communicate clearly and comprehensively, respecting the autonomy of their patients. Lastly, the development of ethical frameworks and guidelines specific to emerging technologies and practices is necessary. These frameworks should address the unique ethical challenges posed by these technologies and provide practitioners with clear direction on how to proceed.In conclusion, medical ethics is a dynamic and evolving field, requiring continuous attention and reflection. By prioritizing education, patient autonomy, and the development of ethical frameworks, we can hope to address the challenges of medical ethics and ensure that healthcare remains a force for good in society.**医学伦理:挑战与建议**在医疗保健领域,伦理道德发挥着至关重要的作用,它引导着从业者做出决策和采取行动。
ENCOUNTERTRUE-TIMEATPG

Encounter True-Time ATPGPart of the Encounter Test family, Encounter True-Time ATPG offers robust automated test patterngeneration (ATPG) engines, proven to generate the highest quality tests for all standard design-for-test (DFT) methods, styles, and flows. It supports not only industry-standard stuck-at and transition fault models, but also raises the bar on fault detection by providing defect-based, user-definable modeling capability with its patented pattern fault technology.Pattern fault technology is what enables the Encounter “gate-exhaustive” coverage(GEC) methodology, proven to be two-to-four times more efficient at detecting gate intrinsic faults than any other static methodologies available on the market (e.g. SSF, N-Detect).For delay test, True-Time ATPGincludes a dynamic timing engine and uses either circuit timing information or constraints to automaticallygenerate transition-based fault tests and faster-than-at-speed tests for identifying very deep sub-micron design-process feature defects (e.g. certain small delay defects).Figure 1: Encounter True-Time ATPG provides a timing-based ATPG engine driven by SDF or SDC informationOn-product clock generation (OPCG) produces and applies patterns to effectively capture this class of faults while minimizing false failures. Use of SDF or SDC information ensures the creation of a highly accurate timing-based pattern set.True-Time ATPG optimizes test coverage through a combination of topological random resistant fault analysis (RRFA) and deterministic fault analysis (DFA)with automated test point insertion—far superior to traditional test coverage algorithms. RRFA is used for early optimi-zation of test coverage, pattern density, and runtime performance. DFA is applied downstream for more detailed circuit-level fault analysis when the highest quality goals must be met.To reduce scan test time while maintaining the highest test coverage, True-Time technology provides intelligent ATPG with on-chip compression (XOR- or MISR-based). It is also power-aware and uses patented technologies to significantly reduce and manage power consumption during manufacturing test.True-Time ATPG also offers a customizable environment to suityour project development needs.The GUI provides highly interactive capabilities for coverage analysis and debug; it includes a powerful sequence analyzer that boosts productivity. Encounter True-Time ATPG is available in two offerings: Basic and Advanced.Benefits• Ensures high quality of shipped silicon with production-proven 2-4x reduction in test escapes• Provides superior partial scan coverage with proprietary pattern fault modeling and sequential ATPG algorithms• Optimizes test coverage with RRFA and DFA test point insertion methodology • Boosts productivity by integrating with Encounter RTL Compiler• Delivers superior runtime throughput with high-performance model build and fault simulation engines as well as distributed ATPG • Lowers cost of test with patterncompaction and compressiontechniques that maintain fullscan coverage• Balances tester costs with diagnosticsmethodologies by offering flexiblecompression architectures with fullX masking capabilities (includingOPMISR+ and XOR-based solutions)• Supports low pin-count testingvia JTAG control of MBIST andhigh-compression ratio technology• Supports reduced pin-count testing forI/O test• Interfaces with Encounter Power Systemfor accurate power calculation andpattern IR drop analysis• Reduces circuit and switching activityduring manufacturing test to managepower consumption• Reduces false failures due tovoltage drop• Provides a GUI with powerfulinteractive analysis capabilitiesincluding a schematic viewer andsequence analyzerEncounter TestPart of the Encounter digital design andimplementation platform, the EncounterTest product family delivers an advancedsilicon verification and yield learningsystem. Encounter Test comprises threeproduct technologies:• Encounter DFT Architect: ensuresease of use, productivity, and predict-ability in generating ATPG-readynetlists containing DFT structures, fromthe most basic to the most complex;available as an add-on option toEncounter RTL Compiler• Encounter True-Time ATPG: ensuresthe fewest test escapes and the highestquality shipped silicon at the lowestdevelopment and production costs• Encounter Diagnostics: delivers themost accurate volume and precisiondiagnostics capabilities to accelerateyield ramp and optimize device andfault modelingEncounter Test also offers a flexible APIusing the PERL language to retrieve designdata from its pervasive database. Thisunique capability allows you to customizeSoC Test Infrastructure• Maximize productivity• Maximize predictabilityTest Pattern Generation• Maximize product quality• Minimize test costsDiagnostic• Maximize yeld and ramp• Maximize silicon bring-upEncounter DFT Architect• Full-chip test infrastructure• Scan compression(XOR and MISR), BIST,IEEE1500, 1149.1/6• ATPG-aware insertionverification• Power-aware DFT and ATPGEncounter True-Time ATPG• Stuck-at, at-speed, andfaster-than-at-speed testing• Design timing drivestest timing• High-quality ATPGEncounter Diagnostics• Volume mode finds criticalyield limiters• Precision mode locatesroot cause• Unsurpassed silicon bring-upprecisionSiliconFigure 2: Encounter Test offers a complete RTL-to-silicon verification flow and methodologies that enable the highest quality IC devices at the lowest costreporting, trace connections in the design, and obtain information that might be helpful for debugging design issues or diagnostics.FeaturesTrue-Time ATPG BasicTrue-Time ATPG Basic contains thestuck-at ATPG engine, which supports:• High correlation test coverage, easeof use, and productivity through integration with the Encounter RTL Compiler synthesis environment• Full scan, partial scan, and sequential ATPG for edge-triggered andLSSD designs• Stuck-at, IDDQ, and I/O parametric fault models• Core-based testing, test data migration, and test reuse• Special support for custom designs such as data pipelines, scan control pipelines, and safe-scan• Test pattern volume optimization using RRFA-based test point insertion• Test coverage optimization usingDFA-based test point insertion• Pre-defined (default) and user-defined defect-based fault modeling andgate-exhaustive coverage based on pattern fault technology• Powerful GUI with interactive analysis capabilitiesPattern fault capability enables defect-based testing with a patented technology for accurately modeling the behavior of nanometer defects, such as bridges and opens for ATPG and diagnostics, and for specifying the complete test of a circuit. The ATPG engine, in turn, uses this definition wherever the circuit is instan-tiated within a design. By default, pattern faults are used to increase coverage of XOR, LATCH, FLOP, TSD, and MUX primi-tives. They can also be used to model unique library cells and transition and delay-type defects.True-Time ATPG AdvancedTrue-Time ATPG Advanced offers thesame capabilities as the Basic configu-ration, plus delay test ATPG functionality.It uses post-layout timing data from theSDF file to calculate the path delay of allpaths in the design, including distributiontrees of test clocks and controls. Usingthis information, you can decide on thebest cycle time(s) to test for in a givenclock domain.True-Time ATPG Advanced is capableof generating tests at multiple testfrequencies to detect potential early yieldfailures and certain small delay defects.You can specify your own cycle time orlet True-Time ATPG calculate one basedon path lengths. It avoids generating testsalong paths that exceed tester cycle timeand/or mask transitions along paths thatexceed tester cycle time. True-Time ATPGgenerates small delay defect patternsbased on longest path analysis to ensurepattern efficiency.A unique feature of the Advancedoffering is its ability to generate faster-than-at-speed tests to detect small delaydefects that would otherwise fail duringsystem test or result in early field failures.True-Time ATPG Advanced also usestester-specific constraint informationduring test pattern generation. Thecombination of actual post-layout timingand tester constraint information withTrue-Time ATPG Advanced algorithmsensures that the test patterns will work“first pass” on the tester.The test coverage optimizationmethodology is expanded beyond RRFAand DFA-based test point insertion(TPI) technology. The combinationof both topological and circuit-levelfault analysis with automated TPIprovides the most advanced capabilityfor ensuring the highest possible testcoverage while controlling the numberof inserted test points. DFA-based TPIBridge TestingFigure 3: Pattern faults model any type ofbridge behavior; net pair lists automaticallycreate bridging fault models; ATPG anddiagnostics use the models to detect andisolate bridgesFigure 4: Power-aware ATPG for scan and capture modes prevents voltage-drop–induced failures in test modeCadence is transforming the global electronics industry through a vision called EDA360.With an application-driven approach to design, our software, hardware, IP, and services helpcustomers realize silicon, SoCs, and complete systems efficiently and profitably. © 2012 Cadence Design Systems, Inc. All rights reserved. Cadence, the Cadence logo, Conformal, Encounter, and VoltageStorm are registered trademarks of Cadence Design Systems, Inc. All other s are properties of their respective holders.has links to Encounter Conformal ® Equivalence Checker to ensure the most efficient, logically equivalent netlist modifications with maximum controllability and observability.The ATPG engine works with multiple compression architectures to generate tests that cut costs by reducing scan test time and data volume. Actual compression ratios are driven by the compression architecture as well asdesign characteristics (e.g. available pins, block-level structures). Users can achieve compression ratios exceeding 100x.Flexible compression options allow you to select a multiple input signature register (MISR) architecture with the highest compression ratio, or an exclusive-or (XOR)–based architecture that enables a highly efficientcombinational compression ratio and a one-pass diagnostics methodology. Both architectures support a broadcast type or XOR-based decompressor.On-product MISR plus (OPMISR+) uses a MISR-based output compression, which eliminates the need to check the response at each cycle. XOR-based compression uses an XOR-tree–based output compression to enable a one-pass flow through diagnostics.Additionally, intelligent ATPG algorithms minimize full-scan correlation issues and reduce power consumption, deliv-ering demonstrated results of >99.5 stuck-at test coverage with >100x test time reduction. Optional X-state masking capability is available on a per-chain/ per-cycle basis. Masking is usuallyrequired when using delay test because delay ATPG may generate unknown states in the circuit.Using the Common Power Format (CPF), True-Time ATPG Advanced automatically generates test modes to enable individual power domains to be tested independently or in small groups. This, along with automaticrecognition and testing of power-specific structures (level shifters, isolation logic, state retention registers) ensures the highest quality for low-power devices.Power-aware ATPG uses industry-leading techniques to manage and significantly reduce power consumption due to scan and capture cycles during manufacturing test. The benefit is reduced risk of false failures due to voltage drop and fewer reliability issues due to excessive power consumption. True-Time ATPG Advanced uses algorithms that limit switching during scan testing to further reduce power consumption.Encounter Test offers a flexible API using the PERL language to retrievedesign data from its pervasive database. This unique capability allows users to customize reporting, trace connections in the design, and obtain information that might be helpful for debugging design issues or diagnostics.Platforms• Sun Solaris (64-bit)• HP-UX (64-bit)• Linux (32-bit, 64-bit)• IBM AIX (64-bit)Cadence Services and Support• Cadence application engineers can answer your technical questions by telephone, email, or Internet—they can also provide technical assistance and custom training • Cadence certified instructors teach more than 70 courses and bring their real-world experience into the classroom • More than 25 Internet Learning Series (iLS) online courses allow you the flexibility of training at your own computer via the Internet • Cadence Online Support gives you24x7 online access to a knowledgebase of the latest solutions, technicaldocumentation, software downloads, and more。
《分子诊断学》教学大纲

《分子诊断学》课程教学大纲课程名称:分子诊断学(Molecular Diagnose)主讲教师:杨晶(教授),申鹤云(副教授)课程编号:学时:24学分:1.5预修课程:生物化学、细胞生物学、微生物学课程简介:分子诊断学是建立在分子生物学和免疫学基础上的医学诊断技术,在充分借鉴现代基因组学与蛋白质组学的研究成果基础上,通过建立各种适用的检测技术将疾病相关基因、蛋白与临床诊断紧密结合,为疾病预防,疾病预警和疗效评价服务,其核心是基因诊断和以单抗为基础的免疫学诊断。
分子诊断技术以其显著优势和巨大潜力,成为保障人类健康的最重要的生物技术之一。
本课程主要介绍分子诊断的常用技术及在科研和临床上的应用,包括ELISA 技术、免疫胶体金层析技术、化学发光技术、时间分辨技术、分子杂交技术、荧光定量PCR技术以及各种芯片技术等,掌握临床常见感染性疾病、单基因疾病和多基因疾病分子诊断策略和方法。
教材:临床分子诊断学郑芳陈昌杰华中科技大学出版社2014.7第一章绪论(2 学时)shen一、主要内容:(一) 分子诊断学的定义及其研究范畴(二) 分子诊断学的发展简史(三) 分子诊断学在医学中的应用二、学习重点和难点:重点:掌握分子诊断学的定义,了解分子诊断学经历了 3 个阶段的发展历史。
难点:一些新型分子诊断技术在医学中的应用。
第二章免疫学诊断技术(6 学时)shen一、主要内容:(一) 抗原抗体反应(二) 免疫浊度测定(三) 放射免疫分析技术(四) 酶免疫分析技术(五) 荧光抗体分析技术(六) 时间分辨免疫荧光技术(七) 荧光偏振免疫分析技术(八) 化学发光免疫分析技术(九) 金标免疫分析技术(十) 标记免疫分析的质量控制二、学习重点和难点:重点:放射免疫分析、酶免疫分析技术、荧光抗体分析技术和免疫浊度检测等技术原理,各种反应模式的原理及应用。
难点:一些新型示踪物的示踪原理(要求一定的物理学和化学知识)。
第三章分子生物学诊断技术(基因诊断技术)(6 学时)一、主要内容:(一)PCR 及衍生技术 1. PCR 技术的基本原理 2. PCR 衍生技术 3. 荧光定量PCR 技术 4. PCR 方法的标准化(二)核酸分子杂交技术 1. 核酸杂交的基本原理 2. 核酸探针 3. 核酸分子杂交技术二、学习重点和难点:重点:FQ-PCR、原位PCR、PCR-RFLP、PCR-ELISA、PCR-SSCP、Southern blot、 Northern blot、原位杂交等技术的原理及其在临床检测中的实际应用。
思科中国招聘 - 关于毕业生和实习生

HW Test EngineerJob De scriptionThe following are responsibilities associated with this test engineering position:∙Understanding general switching product hardware architecture and its functionality∙Review HW design specification, create test plans and generate test tools under standard HW test processes and procedures∙Set up HW test environment with UUT and/or instruments/cable plants/etc.∙Execute manual/automated test suites according to test plan and as per guidance from Cisco tech leads.∙Work with HW/SW designers to troubleshoot and root cause issues found during the test.∙Handle various test equipments like environmental chambers, AC or DC power supplies, traffic generator and a wide range of networking equipment necessary to execute HW test suites ∙Work is reviewed for soundness of technical judgment and overall adequacy and accuracy.∙Uses acquired professional knowledge to make decisions. Exercises judgment within defined standards and consults with Cisco tech leads.EducationTypically requires MSEE/CS/Automation Control or 2 years with BSEE/CS/Automation ControlSkills RequiredThe following requirements are critical:∙General knowledge of L2/L3 Switching product and HW architecture∙Experience with test equipments such as AC or DC Power supplier, IP Traffic Generator, oscilloscope, signal analyzer.∙high speed signal measurement techniques such as Eye-Diagram, return loss, jitter.∙Experience with the use of equipment UNIX environment and script programming using Tcl/Tk and shell language∙Excellent written and verbal communications, team work mindset∙Familiarity with Cisco products and Cisco IOS is preferred∙HW testing Experience of troubleshooting network is highly desirableDiagnostic Software EngineerCisco CSSTG IntroductionCloud Services and Switching Technology Group (CSSTG) develops industry leading Catalyst 6500 data center switches. CSSTG team at Cisco China Research and Developm ent Center, Shanghai, China, concentrates on next-generation System Engineering developments for Cat6K.ResponsibilityResponsibilities:∙Design and develop component and system level diagnostics software/firmware for system, board, FPGA and ASIC design verification and validation in engineering and manufacturing;∙Work closely with HW design, SW development and manufacturing teams to support system bring up, failure analysis and manufacturing processes, and promote team collaboration;∙Participate in embedded software, device driver and/or kernel development;Scalable SW design for multi-processors, multi-processes, and multi-thread systems in C andC++ environment;∙Author diagnostic functional specification to provide guidelines for implementation to achieve the highest level of test coverage with fault isolation at the component level;∙Initiate informal reviews of ideas and technical objectives within and across functional teams;RequirementsMust have skill/experiences∙Strong C programming experience and debugging skills∙Fluent English speaking and writingGood to have skill/experiences∙Embedded real-time OS/system skills∙Networking knowledge such as TCP/IP or socket programming experience∙Hands-on Linux programming/development experience∙Hands-on knowledge of a scripting language, TCL or PERL∙Device driver and register level programming∙Experience with large-scale team-based software developmentEducational BackgroundMSEE/CE/CS student with related project or work experienceLogic Design & Verification EngineerParticipate in the design and verification of complex, high performance and high integration ASICs and FPGAs used in Cisco networking equipments.Responsibilities include:1.Implementation of complex ASICs and/or FPGAs.2.Take part in the architecture definition, implementation and verification phases.3.Detailed design specification and test plan development.4.Develop and implement block level RTL, perform synthesis and achieve timing closure.5.Standalone module, full chip and system level verification, formal verification and equivalence checking.6.Work with cross-functional teams (hardware, software, diagnostics, signal integrity group).7.Assist in complex subsystem level bring-up, integration, and unit test verification.CABU Hardware Engineer (Board Design)Job Description:-Participates on a project team of engineers involved in the hardware specification, board design, development and verification for the leading CMTS routing products.-Work is reviewed upon completion for adequacy in meeting objectives.-Interfaces cross-functionally at the working team level.-Work under direction of the project leader to define features and participate in problem resolution.-Work closely with diagnostics and software developers throughout the developm ent process.-Job involves participating in EDVT /Compliance test.-Works under department strategy and direction.-Translates departm ent goals into own work assignments.-Independently determines and develops approach to solutions.-Skills required:-Experience in board design.-Additional skills would be having the capability of proficiency with IBIS (or equivalent) circuit simulation, field-solver and time/frequency domain analysis, familiarity with high speed serdesdesign, PLL design and LVDS, LVPECL, CML and other high-performance I/O technologies.-Experience correlating simulation results with lab measurements using oscilloscopes, TDRs and spectrum analyzers is a plus.-Requires excellent communication skills.-Tackles complex issues in creative ways.-Problem solving requires originality and ingenuity using knowledge gained while specia lizing in field.-Self motivation, team work and strong communication skills are essentialApplication Software EngineerCisco ESTG Introduction:Enterprise Switch Technology Group (ESTG) develops industry leading innovation could access platform. CSSTG team at Cisco China Research and Development Center, Shanghai, China, concentrates on next-generation System Engineering development.Responsibilities:∙Programming in an embedded software environment∙Program script-based development tools∙Linux driver or application developmentRequirements:Must have skill/experiences∙Strong C programming experience and debugging skills∙Deeply understanding embedded system∙Fluent English speaking and writingGood to have skill/experiences∙Embedded real-time OS/system skills∙Networking knowledge such as TCP/IP or socket programming experience∙Multimedia knowledge such decode, encode or Gstream framework∙Hands-on Linux programming/development experience∙Hands-on knowledge of a scripting language, shell or python∙Device driver and application level programming, such as QT developm entEducational Background∙Typically requires MSEE/CS/Automation Control。
安全整合级别(SIL)指南说明书

2 What is a Safety Integrity Level (SIL)?
A SIL is a measure of the performance needed for a safety function to reduce the risk of a process hazard to a tolerable level. There are 4 SILs. SIL4 provides the highest level of safety integrity and the greatest amount of risk reduction, and SIL1 the lowest. Determining a SIL target is based on the assessment of the likelihood of a hazard and the severity of its consequences.
3 Safety Requirement Specification
Hazard and Risk Assessment allows the specification of safety requirements for the Safety Instrumented System (SIS). The Safety Requirement Specification (SRS) facilitates the Design and Engineering of the SIS by not only specifying the target SIL and the hardware reliability measure but also performance requirements to ensure that the SIF can act quickly enough to protect the plant.
血流储备分数英语

血流储备分数英语Blood Reserve Score (BRS) is a quantitative measure used in medical contexts to assess a person's blood volume and circulation status. It serves as a crucial indicator in diagnosing and managing various medical conditions, especially those related to cardiovascular health. Understanding the concept of BRS requires delving into its components, its significance in clinical practice, and its implications for patient care.**1. Understanding Blood Reserve Score (BRS):****1.1 Definition:** BRS is a numerical value that represents the body's capacity to maintain adequate blood circulation and perfusion under different physiological conditions. It takes into account factors such as blood volume, cardiac output, and vascular tone to provide a comprehensive assessment of circulatory function.**1.2 Components:** BRS incorporates several key parameters, including total blood volume, plasma volume, red blood cell mass, and vascular compliance. These components reflect the body's ability to regulate blood flow and pressure to meet the metabolic demands of tissues and organs.**1.3 Calculation:** Various methods exist forcalculating BRS, ranging from simple clinical assessments to more complex laboratory tests. Common techniques include measuring hematocrit levels, blood pressure, and cardiac output, either directly or indirectly through specialized imaging or diagnostic procedures.**2. Significance in Clinical Practice:****2.1 Diagnostic Utility:** BRS serves as a valuable tool in diagnosing and monitoring a wide range of medical conditions, such as hypovolemia, heart failure, and septic shock. By assessing the body's blood reserve capacity,healthcare providers can identify abnormalities in circulation early on and initiate appropriate interventions.**2.2 Prognostic Value:** In addition to its diagnostic role, BRS also carries prognostic significance in predicting patient outcomes. Low BRS values often correlate with increased morbidity and mortality rates, particularly in individuals with pre-existing cardiovascular diseases or critical illnesses.**2.3 Treatment Guidance:** Knowledge of a patient's BRS can guide treatment decisions, such as fluid resuscitation, vasopressor therapy, or volume optimization strategies. By tailoring interventions to individual BRS levels, healthcare providers can optimize circulatory support while minimizing the risk of adverse events.**3. Implications for Patient Care:****3.1 Personalized Medicine:** The integration of BRS into clinical practice enables a more personalized approachto patient care. By considering each individual's circulatory reserve capacity, healthcare providers can tailor treatment plans to optimize outcomes and reduce the likelihood of complications.**3.2 Risk Stratification:** BRS facilitates risk stratification by identifying patients at higher risk of hemodynamic instability or cardiovascular decompensation. Early identification of at-risk individuals allows for proactive management strategies aimed at preventing adverse events and improving overall prognosis.**3.3 Monitoring and Follow-up:** Regular assessment of BRS allows for ongoing monitoring of circulatory function and response to therapy. Serial measurements can help track changes in blood volume, cardiac performance, and vascular tone over time, guiding adjustments to treatment strategies as needed.**4. Future Directions:****4.1 Technological Advancements:** Advances in medical technology continue to refine our understanding and assessment of BRS. Emerging techniques, such as non-invasive imaging modalities and point-of-care diagnostics, hold promise for more accurate and accessible BRS measurements in diverse clinical settings.**4.2 Research Opportunities:** Further research into BRS and its clinical implications is warranted to elucidate its role in various disease states and treatment modalities. Longitudinal studies investigating the relationship between BRS and patient outcomes can provide valuable insights into its predictive value and therapeutic relevance.**4.3 Integration into Clinical Guidelines:** As evidence supporting the utility of BRS accumulates, there is potential for its integration into clinical practice guidelines and protocols. Standardized approaches to BRS assessment andinterpretation can streamline decision-making processes and optimize patient care across healthcare settings.In conclusion, Blood Reserve Score (BRS) represents a valuable tool for assessing circulatory function and guiding clinical management in diverse medical contexts. By incorporating BRS into routine practice, healthcare providers can enhance diagnostic accuracy, improve risk stratification, and optimize treatment strategies to ultimately improve patient outcomes.。
comsol错误提示及解决方法

Diagnostics : Error MessagesError MessagesThis section summarizes the most common error messages and solver messages generated by COMSOL Multiphysics. All error messages are numbered and sorted in different categories according to the following table.TABLE 2-1: ERROR MESSAGE CATEGORIESNUMBERS CATEGORY1000–1999 Importing Models2000–2999 Geometry Modeling3000–3999 CAD Import4000–4999 Mesh Generation5000–5999 Point, Edge, Boundary, and SubdomainSpecification6000–6999 Assembly and Extended Mesh7000–7999 Solvers8000–8999 Postprocessing9000–9999 GeneralFor error messages that do not appear in the following lists, contact COMSOL’s support team for help.2000–2999 Geometry ModelingTABLE 2-2: GEOMETRY MODELING ERROR MESSAGESERRORNUMBERERROR MESSAGE EXPLANATION2118 Negative output fromempty inputIncorrect Geometry M-file.2119 Non scalar output fromempty inputIncorrect Geometry M-file.2120 Normal directions areinconsistentIncorrect input data from STL/VRML import.2138 Self intersections notsupported Curves resulting in self-intersections are not supported.2140 Singular extrusions notsupportedError in input parameters.2141 Singular revolutions notsupported The revolved mesh has a singularity at the z axis. If possible, create the cylinder using a 3D primitive or by revolving the geometry before meshing.2146 Subdomain mustbounded at least fourboundary segmentsIncorrect geometry for mapped mesh.2147 Subdomain must boundone connected edgecomponent onlyIncorrect geometry for mapped mesh. 2190 Invalid radius or distance Incorrect input parameters to fillet/chamfer.2197 Operation resulted inempty geometry object Geometry operation resulted in an empty geometry object which is not allowed. Make sure an empty geometry object is not created.2209 Geometry to revolve maynot cross axis ofrevolution The axis of revolution and the geometry intersect. Check the dimension of the geometry and the definition of the axis for the revolution.4000–4999 Mesh Generation TABLE 2-3: MESH GENERATION ERROR MESSAGESERRORNUMBERERROR MESSAGE EXPLANATION4002 A degeneratedtetrahedron wascreated The mesh generator ran into numerical difficulties while creating tetrahedrons with a size based on user-controlled parameters. Causes could be too small and narrow subdomains relative to the rest of the geometry or exceedingly short boundary segments. Try to avoid creating small and narrow subdomains and very short boundary segments that are adjacent to longer boundary segments.4003 A degeneratedtriangle wascreated The mesh generator ran into numerical difficulties while creating triangles with a size based on user-controlled parameters. Causes could be too small and narrow subdomains relative to the rest of the geometry or exceedingly short boundary segments. Try to avoid creating small and narrow subdomains and very short boundary segments that are adjacent to longer boundary segments.4012 Cannot createmapped mesh forthis geometry The geometry does not fulfill the topological requirements for a mapped mesh. Changes in input parameters or further subdomain division can possibly help this.4026 Failed creatematching edgediscretizations Cannot make mapped mesh with the given input parameters.4029 Failed to insertpoint Problems inserting point at given coordinate. Manually inserting a point there may help.4031 Failed to respectboundary elementon geometry edge The mesh generator failed in making the elements compatible with the geometry object’s edges. The reason for this could be that the face mesh is too coarse or contains adjacent elements with large differences in scale. Another reason can be that some subdomains in the geometry are too narrow with respect to the rest of the geometry.4032 Failed to respectboundary elementon geometry faceSee Error message 4031.4044 Internal errorboundaryrespectingSee Error message 4031.4054 Invalid topology ofgeometry The geometry object cannot be used for creating a mapped mesh. It must be subdivided.4055 Isolated entitiesfound Entities that are not connected to the boundaries of a geometry objects is found. The mapped mesh generator does not support such isolated entities.4119 Singular edgedetectedThe geometry object contains an edge of zero length. 6000–6999 Assembly and Extended MeshTABLE 2-4: ASSEMBLY AND EXTENDED MESH ERROR MESSAGESERRORNUMBERERROR MESSAGE EXPLANATION6008 Circularvariabledependencydetected A variable has been defined in terms of itself, possibly in a circular chain of expression variables. Make sure that variable definitions are sound. Be cautious with equation variables in equations.6063 Invalid degreeof freedomname The software does not recognize the name of a degree of freedom. Check the names of dependent variables that you have entered for the model. See also Error 7192.6139 Wrong numberof DOFs ininitial value The current solution or the stored solution has for some reason the wrong number of degrees of freedom, sometimes due to a change of the implementation of elements between two versions of the software. To overcome the problem, go to the Initial value area in the Solver Manager, and select Initial value expression. Then the initial value expressions is evaluated without using the current or stored solution.6140 Wrong numberof dofs inlinearizationpoint The current solution or the stored solution has for some reason the wrong number of degrees of freedom, sometimes due to a change of the implementation of elements between two versions of the software. To overcome the problem, go to the Value of variables not solved for and linearization point area in the Solver Manager, and click the Use setting from Initial value frame button or the Zero button.6163 Divide by zero A property in the model contains a divisor that becomes zero.Check to make sure that division by zero does not occur inany expression or coefficient.6164 Duplicatevariable name A variable name has two different definitions. For instance, the same variable name appears two or more times for a dependent variable, a constant, an expression variable, or acoupling variable. Remove or rename one of the variables.6170 Failed toevaluatevariable An error occurred when evaluating the variable. The domains in which COMSOL Multiphysics tried to evaluate the variable are indicated. Also, the error message shows the expression that COMSOL Multiphysics was unable to evaluate. Make sure that you have defined the variables correctly in the indicated domains.6176 Attempt toevaluate reallogarithm ofnegative number An expression contains log(a), where a becomes negative or zero. To make the logarithm well-defined, make sure that a>0. Often, a becomes only slightly negative (due to approximations in the solution process). Then, a possible solution is to use log(a+e), where e is a small constant. Another remedy is to use log(abs(a)). If you do want to have a complex logarithm, go to the Advanced tab of Solver Parameters and select the Use complex functions with real input check box.6177 Matrix has zeroon diagonal When the equations have a structure such that the stiffness matrix (Jacobian matrix) has zeros on the diagonal, it is not possible to use the following linear systemsolvers/preconditioners/smoothers: all versions of SOR and Diagonal scaling (Jacobi). Try the Vanka preconditioner/smoother instead.6188 Out of memoryduring assembly The software ran out of memory during assembly of the finite element model. See error 7144 regarding generalmemory-saving tips.6194 Attempt toevaluatenon-integralpower ofnegative number An expression contains a^b, where a becomes negative and b is not an integer. To make the power well-defined, make sure that a>0. Often, a becomes only slightly negative (due to approximations in the solution process). Then, a possible solution is to use (a+e)^b, where e is a small constant. Another remedy is to use abs(a)^b. If you do want to have a complex number a^b, go to the Advanced tab of Solver Parameters and select Use complex functions with real input.6199 Attempt toevaluate realsquare root ofnegative number The model contains a sqrt (square root) function that takes the square root of a negative number. Either make sure that the square-root argument is nonnegative or select the Use complex functions with real input check box on the Advanced tab in the Solver Parameters dialog box.6204 Undefinedfunction call An expression contains an undefined function name. Check that the function name is correct and that the function is in COMSOL Multiphysics’ or MATLAB’s path.6206 Internalevaluation error:unexpected NaNencountered Not-A-Number (NaN) appears unexpectedly. A possible cause is improperly defined coupling variables. As a first step, check that the definitions of the source and destination domains of any coupling variables or periodic boundary conditions are correct.6245 Unsupportedintegration order Integration order is too high. For triangular elements the order can be up to 10, and for tetrahedral elements the order can be up to 8. Find more information in the section “Numerical Quadrature” on page 505.6259 Failed toevaluatevariableJacobian An error occurred when evaluating the Jacobian of the indicated variable. The domains in which COMSOL Multiphysics tried to evaluate the variable are indicated. Make sure that you have defined the variable correctly in the indicated domains.7000—7999 Solvers and Preconditioners TABLE 2-5: SOLVER ERROR MESSAGESERRORNUMBERERROR MESSAGE EXPLANATION7001 Adaption onlyimplemented for It is only possible to use adaptive mesh refinement in 3D for models using tetrahedral mesh elements.tetrahedral meshes Either turn off adaptive mesh refinement or switchfrom brick or prism elements to tetrahedral elements.7002 Adaption onlyimplemented fortriangular meshes It is only possible to use adaptive mesh refinement in 2D for models using triangular mesh elements. Either turn off adaptive mesh refinement or switch from quadrilateral elements to triangular elements.7022 Segregated solver stepsdo not involve all ofsolcomp The groups for the segregated solver do not include all dependent variables. One reason for this error could be that some boundary conditions (for example, for laminar inflow in fluid-flow models) add dependent variables that are not initially in the model.7043 Initial guess leads toundefined function value This error message usually appears when you have set up an expression that returns “not a value,” that is, it is undefined, for the initial condition you have set. For instance, this happens if an expression contains a divisor that becomes zero or a logarithm of a negative value. To solve the problem, change the expression or the initial value so that the expression is well-defined when substituting the initial value of the variables. Also, watch out for warnings in the Log window.7067 System matrix is zero This error message appears if there are no volumeelements in the mesh. In the case that you have amapped surface mesh, try sweeping or extruding thesurface mesh to get a volume mesh.7069 Maximum number oflinear iterations reached The iterative linear system solver did not converge due to a bad initial guess or a bad preconditioner. Increase the limit on the number of linear iterations or use a better preconditioner. If possible, use a direct linear system solver.7081 No parameter namegiven The parametric solver does not find a name for the parameter. Check the Name of parameter edit field on the General page of the S olver Manager.7092 Out of memory inAlgebraic multigrid The Algebraic multigrid solver/preconditioner ran out of memory. See error 7144 regarding general memory-saving tips.7093 Out of memory duringback substitution The solver ran out of memory during back substitution. See error 7144 regarding general memory-saving tips.7094 Out of memory duringLU factorization The solver ran out of memory during LU factorization. See error 7144 regarding general memory-saving tips.7111 Singular matrix The system matrix (Jacobian matrix or stiffnessmatrix) is singular, so the solver cannot invert it.Usually this means that the system isunderdetermined. Check that all equations are fullyspecified and that the boundary conditions areappropriate. For instance, in a stationary model youusually need to have a Dirichlet condition on someboundary. A singular matrix could also occur if meshelements are of too low quality. If the minimumelement quality is less than 0.005 you might be introuble. Another reason for this error message is thatyou have different element orders for two variablesthat are coupled by, for example, a weak constraint.Use the same element order for all variables that arecoupled.7136 Very ill-conditionedpreconditioner. Therelative residual is morethan 1000 times largerthan the relativetolerance You need to improve the quality of the preconditioner to get an accurate solution. For the Incomplete LU preconditioner, lower the drop tolerance.7144 Out of memory inadaptive solver The adaptive solver ran out of memory. The adaptive mesh refinement has generated a too fine mesh. In general, when you run out of memory, try to use memory-efficient modeling techniques such asutilizing symmetries, solving models sequentially, and selecting memory-efficient solvers. See the chapter “Solving the Model” on page 377 in the COMSOL Multiphysics User’s Guide for more information. See also the COMSOL Installation and Operations Guide for information about system memory management.7145 Out of memory ineigenvalue solver The eigenvalue solver ran out of memory. See error 7144 regarding general memory-saving tips.7146 Out of memory instationary solver The stationary solver ran out of memory. See error 7144 regarding general memory-saving tips.7147 Out of memory intime-dependent solver The time-dependent solver ran out of memory. See error 7144 regarding general memory-saving tips.7192 Invalid degree offreedom name in manualscaling The name of a dependent variable in the Manual scaling edit field on the Advanced page in the Solver Parameters dialog box does not match any of the dependent variables in the model.7199 Reordering failed One of the PARDISO reordering algorithms failed.Try a different reordering algorithm or try turning offrow preordering.7248 Undefined value found See the explanation of error 7043 for some possiblereasons as to why this error number appears. In mostsituations you get a more detailed description of theerror by pressing the Details button.7297 Undefined value found This error number appears if one of the linear systemsolvers encounters an undefined value (such valuesappear, for instance, if a division by zero has beenperformed or if some arithmetic operation results in alarger number than can be represented by thecomputer). For direct solvers this error might appearif the stiffness matrix (Jacobian matrix) is singular oralmost singular. For iterative solvers this error mightappear, for instance, if the iterative process diverges.Press the Details button to see which linear solvercaused the error.9000–9999 General ErrorsTABLE 2-6: GENERAL ERROR MESSAGESERRORNUMBERERROR MESSAGE EXPLANATION9037 Failed to initialize3D graphics.OpenGL not fullysupported OpenGL is not available on the computer. This can happen if your graphics card does not support OpenGL or if you have a Unix/Linux computer where OpenGL has not been configured.9040 Fatal error If you receive this error, click the Detail button. Copy andpaste the entire error message and send it tosupport@ along with your license file anddetails of how to reproduce the error.9052 Invalidaddress/port You did not enter the correct server name or server port when trying to connect a client to a server.9084 Server connectionerror The client somehow lost the connection to the server. For example, the server crashed unexpectedly, or the power saving mechanism on a laptop shut down the TCP/IP connection.9143 License error The most common reasons for this message:The license file license.dat has been removed from the rightdirectory in the COMSOL software installation. Thelicense.dat file must be located in the$COMSOL35a/license directory, where $COMSOL35a isthe COMSOL 3.5a installation directory.The license manager has not started properly. Please findthe FLEXlm log file (named by the person who started thelicense manager). Inspect this file to see the server status.Send it to support@ if you are in doubt abouthow to interpret this file.It is crucial that you use the correct license.dat file on boththe server and the clients9178 Error in callback An error occurred when calling a MATLAB function fromCOMSOL Multiphysics. Make sure that the M-file thatdefines the function is correct and exists in the current path.Check that the function is written so that all inputs arevectors of the same size and the output is a vector of thesame size.Solver Error MessagesThese error messages can appear during solution and appear on the Log tab in the Progress window.TABLE 2-7: SOLVER ERROR MESSAGES IN LOG WINDOWSOLVER ERRORMESSAGEEXPLANATIONCannot meet error tolerances. Increase absolute or relative tolerance. The time-dependent solver cannot solve the model to the specified accuracy.Error in residual computationError in Jacobian computation The evaluation of the residual or the Jacobian generated an error during a time-dependent solution. An additional message states the direct error. Some possible reasons are division by zero, range and overflow errors in mathematical functions, and interpolation failure in coupling variables withtime-dependent mesh transformation.Failed to find a solution The nonlinear solver failed to converge. An additional error message gives some more details. See the description for that message.Failed to find a solution for all parameters, even when using the minimum parameter step During a parametric solution, the nonlinear iteration did not converge despite reducing the parameter step length to the minimum allowed value. The solution may have reached a turning point or bifurcation point.Failed to find a solution for initial parameter The nonlinear solver failed to converge for the initial value of the parameter during a parametric solution. An additional error message gives some more details. See the description for that message.Failed to find consistent initial values The time-dependent solver could not modify the initial conditions given to a DAE system to satisfy the stationary equations at the initial time. Make sure the initial values satisfy the equations and boundary conditions. In many cases, this can be achieved by solving for only the algebraic variables using a stationary solver before starting thetime-dependent solver.Ill-conditioned preconditioner. Increase factor in error estimate to X The preconditioner is ill-conditioned. The error in the solution might not be within tolerances. To be sure to have a correct solution, open the Linear System Solver Settings dialog box from the General tab of Solver Parameters. Select Linear system solver in the tree, and increase Factor in error estimate to the suggested number X. Alternatively, use a better preconditioner or tune the settings for the preconditioner.Inf or NaN found, even when using the minimum damping factor Despite reducing the step size to the minimum value allowed, the solver cannot evaluate the residual or modified Newton direction at the new solution iterate. This essentially means that the currentapproximation to the solution is close to the boundary of the domain where the equations are well-defined. Check the equations for divisions by zero, powers, and other functions that can become undefined for certain inputs.Inverted mesh element near coordinates (x, y, z) In some mesh element near the given coordinates, the (curved) mesh element is (partially) warped inside-out. More precisely, the Jacobian matrix for the mapping from local to global coordinates has a negative determinant at some point. A possible reason is that the linear mesh contains a tetrahedron whose vertices all lie on a boundary. When improving the approximation of the boundary using curved mesh elements, the curved mesh element becomes inverted. To see whether this is the case, you can change Geometry shape order to 1 in the Model Settings dialog box, which means that curved mesh elements will not be used. You can usually avoid such bad tetrahedra by using a finer mesh around the relevant boundary. Another reason for this error message can be that the mesh becomes inverted when using a deformed mesh.Last time step is not converged. The last time step returned from the time-dependent solver is not to be trusted. Earlier time steps are within the specified tolerances.Matrix is singular When encountered during time-dependent solution:the linear system matrix (which is a linearcombination of the mass-, stiffness-, and possibly,damping-matrices) is singular. Usually the problemoriginates from the algebraic part of a DAE. Inparticular, the cause can often be found in weakconstraints or constraint-like equations like thecontinuity equation in incompressible flow.Maximum number of linear iterations reached The iterative linear system solver failed to compute a Newton direction in the specified maximum number of iterations.Maximum number of Newton iterations reached The nonlinear solver could not reduce the error below the desired tolerance in the specified maximum number of iterations. This is sometimes a sign that the Jacobian is not complete or badly scaled. It may even be almost singular, if the system is underdetermined. If the returned solution seems reasonable, it might be enough to restart the solver with this solution as the initial guess.No convergence, even when using the minimum damping factor The nonlinear solver reduced the damping factor below the minimum value allowed. The solver reduces the damping factor each time a computed step did not lead to a decrease in the error estimate. Make sure the model is well-posed, in particular that there are enough equations and boundary conditions to determine all degrees of freedom. If the model is well-posed, it should have one or more isolated solutions. In that case, the error is probably due to the initial guess being too far from any solution.Nonlinear solver did not converge During a time-dependent solution, the nonlinear iteration failed to converge despite reducing the time step to the minimum value allowed. Usually, the error is related to the algebraic part of a DAE. For example, the algebraic equations can have reached a turning point or bifurcation point. The error can also appear when the algebraic equations do not have a unique solution consistent with the given initial conditions. Make sure algebraic equations have consistent initial values and that they have a unique solution for all times and values reached by the other variables.Not all eigenvalues returned When the eigenvalue solver terminated (stopped by the user or due to an error), it had not found the requested number of eigenvalues. The eigenvalues returned can be trusted.Not all parameter After premature termination of the parametricsolver, only some of the requested solutions havesteps returned been computed.Predicted solution guess leads to undefined function value The solver computes the initial guess for the new parameter value based on the solution for the previous parameter value. This initial guess led to an undefined mathematical operation. Try using another Predictor on the Parametric tab of Solver Parameters.Repeated error test failures. May have reached a singularity. During a time-dependent solution, the error tolerances could not be met despite reducing the time step to the minimum value allowed.Returned solution has not converged. The solution returned by the stationary solver is not to be trusted. It might, however, be useful as initial guess after modifying equations or solver settings.The elasto-plastic solver failed to find a solution The Newton iteration loop for the computation of the plastic state at some point in the geometry did not converge.。
Table of Contents

Table of ContentsModule 1: Getting Started With Altium Designer1.1Introduction to Altium Designer.........................................................................................1-11.2The Altium Designer environment.....................................................................................1-21.3Document Editor Overview................................................................................................1-61.4Working with projects and documents............................................................................1-10Module 2: Help and DXP system menu2.1Using the Help system.......................................................................................................2-12.2Using the Altium website...................................................................................................2-32.3DXP System menu...........................................................................................................2-10Module 3: Schematic Editor Basics3.1Schematic Editor basics....................................................................................................3-13.2Schematic graphical objects..............................................................................................3-43.3Schematic electrical objects..............................................................................................3-9Module 4: Schematic Capture4.1Introduction to Schematic Capture....................................................................................4-14.2The Schematic Editor workspace......................................................................................4-24.3Libraries and components.................................................................................................4-94.4Placing and wiring............................................................................................................4-17Module 5: Multi-Sheet Design5.1Multi-Sheet Design.............................................................................................................5-1Module 6: Building the Project6.1Assigning designators........................................................................................................6-16.2Compiling and verifying the project...................................................................................6-5Module 7: Setting Up for Transfer to PCB and Importing Data7.1Setting Up for Transfer to PCB..........................................................................................7-1Module 8: PCB Editor Basics8.1PCB Editor Basics..............................................................................................................8-18.2PCB design objects............................................................................................................8-4Module 9: Setting up the PCB9.1Setting up the PCB.............................................................................................................9-19.2Creating a new PCB..........................................................................................................9-69.3Setting up the PCB layers................................................................................................9-10Module 10: Global Editing10.1Editing Multiple Text Objects...........................................................................................10-110.2The Data Editing System.................................................................................................10-4Module 11: PCB Design Flow, Transferring a Design and Navigation11.1PCB design process........................................................................................................11-111.2Transferring design information to the PCB......................................................................11-311.3Using the PCB Panel.......................................................................................................11-711.4Project Navigation and Cross Probing..........................................................................11-16Module 12: Design Rules12.1Design rules and design rule checking...........................................................................12-1Module 13: Classes and Rooms13.1Object classes..................................................................................................................13-113.2Rooms..............................................................................................................................13-3Module 14: Placement and Re-annotation14.1Component Placement tools...........................................................................................14-114.2Re-Annotation and back annotate...................................................................................14-3Module 15: Schematic Library Editor15.1Introduction to Library Editing..........................................................................................15-115.2Schematic Library Editor..................................................................................................15-2Module 16: PCB Library Editor16.1PCB Library Editor...........................................................................................................16-116.23D dimensional component detail.................................................................................16-14Module 17: Linking Models, Parameters, Library Package and Updates17.1Adding Model and Parameter Detail to a Component..................................................17-117.2Component Auditing........................................................................................................17-817.33D PCB Components....................................................................................................17-1417.4Library Package types...................................................................................................17-1817.5Library Reports...............................................................................................................17-20Module 18: Routing and Polygons18.1Routing.............................................................................................................................18-118.2Testpoint System...........................................................................................................18-1018.3Adding and removing teardrops....................................................................................18-1518.4Automatic routing...........................................................................................................18-1618.5Polygons and the Polygon Manager.............................................................................18-19Module 19: Output Generation and CAM File Editing19.1Bill of Materials.................................................................................................................19-119.2Output Generation............................................................................................................19-819.3CAM Editor.....................................................................................................................19-20Module 20: Interfacing to 3D Mechanical CAD20.1Interfacing to 3D Mechanical CAD..................................................................................20-1。
FMEDA Development
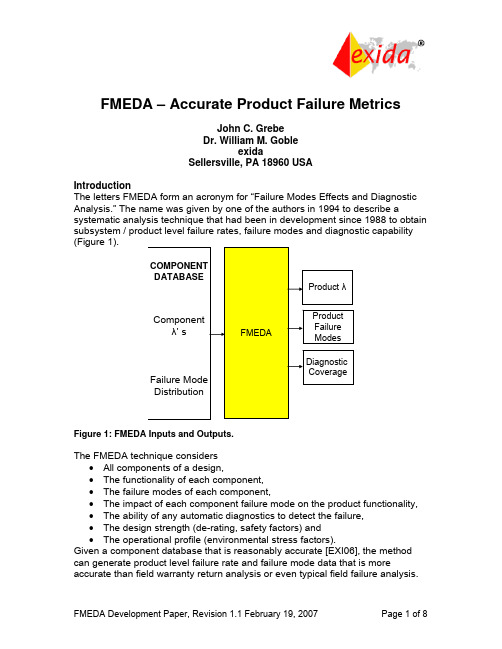
FMEDA – Accurate Product Failure MetricsJohn C. GrebeDr. William M. GobleexidaSellersville, PA 18960 USAIntroductionThe letters FMEDA form an acronym for “Failure Modes Effects and Diagnostic Analysis.” The name was given by one of the authors in 1994 to describe asystematic analysis technique that had been in development since 1988 to obtain subsystem / product level failure rates, failure modes and diagnostic capability (Figure 1).Figure 1: FMEDA Inputs and Outputs.The FMEDA technique considers• All components of a design,• The functionality of each component,• The failure modes of each component,• The impact of each component failure mode on the product functionality, • The ability of any automatic diagnostics to detect the failure,• The design strength (de-rating, safety factors) and• The operational profile (environmental stress factors).Given a component database that is reasonably accurate [EXI06], the method can generate product level failure rate and failure mode data that is moreaccurate than field warranty return analysis or even typical field failure analysis.An FMEDA is an extension of the well proven FMEA technique and can be used on electrical or mechanical products [GOB03, GOB07].FMEA/FMECAA Failure Modes and Effects Analysis, FMEA, is a structured qualitative analysis of a system, subsystem, process, design or function to identify potential failure modes, their causes and their effects on (system) operation.The concept and practice of performing a FMEA, has been around in some form since the 1960’s. The practice was first formalized in 1970s with the development of US MIL STD 1629/1629A.In early practice its use was limited to select applications and industries where cost of failure is particularly high. The primary benefits were to qualitatively evaluate the safety of a system, determine unacceptable failure modes, identify potential design improvements, plan maintenance activities and help understand system operation in the presence of potential faults.The Failure Modes, Effects and Criticality Analysis, FMECA, was introduced to address a primary barrier to effective use of the detailed FMEA results by the addition of a criticality metric. This allowed users of the analysis to quickly focus on the most important failure modes/effects in terms of consequence but still did not address the likelihood or probability of the failure mode which is just as important in prioritization to drive improvements based on cost / benefit comparisons.FMEDA DevelopmentThe Failure Modes, Effects and Diagnostic Analysis, FMEDA, technique was developed in the late 1980’s based in part on a paper in the 1984 RAMS Symposium [COL84]. The FMEDA added two additional pieces of information to the FMEA analysis process. The first piece of information added in an FMEDA is the quantitative failure data (failure rates and the distribution of failure modes) for all components being analyzed. The second piece of information added to an FMEDA is the ability of the system or subsystem to detect internal failures via automatic on-line diagnostics. This is crucial to achieving and maintaining reliability in increasing complex systems and for systems that may not be fully exercising all functionality under normal circumstances such as a low demand Emergency Shutdown System, ESD System.There is a clear need for a measurement of automatic diagnostic capability. This was recognized in the late 1980’s [AME87]. In that context the principles and basic methods for the modern FMEDA were first documented in the book Evaluating Control System Reliability [Gob92]. The actual term FMEDA was firstused in 1994 [MOR94] and after further refinement the methods were published in the late 1990’s [GOB98a, GOBL98b, GOB99]. FMEDA techniques have been further refined during the 2000’s primarily during IEC 61508 preparation work. The key changes have been:1. IEC 61508 Failure Mode Definitions – New Definitions2. Functional Failure Modes3. Mechanical Component UsageWith these changes, the FMEDA technique has matured to become more complete and useful.FMEDA – IEC 61508The IEC 61508 standard officially recognizes the FMEDA technique and most IEC 61508 assessment bodies rely upon FMEDA results to verify that sufficient safety has been achieved for a particular application. Within the field of functional safety, standardized failure modes are also defined which also helped to improve the ease of performing the FMEDA and interpreting its results.The official approval of IEC 61508, Part 2 in 2000 provided documentation on what is expected of a FMEDA and how to use the data in the area of functional safety. This has lead to significantly increased use of the FMEDA within the relevant industries and a rapid evolution of the methods and tools with the required component level failure rate and failure mode data.IEC 61508 use of the FMEDA is focused on determination of two safety integrity measurements; the dangerous undetected failure rate and a metric known as the Safe Failure Fraction, SFF. The SFF represents the percentage of failures that are not dangerous and are detected. However, additional quantitative results important to system level modeling can also be easily derived out of the same FMEDA and this has driven further evolution of the process and enhanced the value of its results while remaining faithful to the original intent of the IEC 61508. Draft versions of future updates of the IEC 61508 standard are now working to capture some of these advancements.IEC 61508 Failure Mode DefinitionsIEC61508 Part 4 (1998) defines a dangerous failure as a failure which “has the potential to put the safety-related system in a hazardous or fail-to-function state.” The standard also defines a safe failure as a failure which “does not have the potential to put the safety-related system in a hazardous or fail-to-function state.” IEC61508 Part 2 further explains a “safe” failure as a failure leading to a safe shut-down or having no impact on the safety integrity of the E/E/PE safety-related system.This significantly simplified and ambiguous definition of a safe failure, if followed, literally leads to results that do not provide data that is very relevant to applications and leads to multiple unanticipated interpretations of the standard. Some of these interpretations can provide unintended loop holes that result in circumstances where the addition of unrelated functionality to a product can improve the SFF metric without any improvement in safety integrity.New Failure Mode DefinitionsKey players in the industry, including exida, are dedicated to improvement of functional safety while remaining faithful to the original intent of IEC61508. exida has proposed multiple refinements to the failure mode definitions and began using those new definitions in 2003 when doing FMEDA analysis. The more refined failure mode definitions are expected to be included in subsequent versions of IEC 61508. To understand the required changes it is first necessary to better understand the ambiguity of the current official definition of “safe failure.” As currently defined a safe failure includes all failures not considered dangerous. This includes “failure leading to a safe shut-down or having no impact on the safety integrity of the E/E/PE safety-related system.” A failure that has no impact on the safety integrity function would most likely not even be noticed by a user of the product and can fall into two general categories.No Impact – Category 1, No EffectMost components have multiple failure modes and these failure modes are more or less important depending on how they are used within a particular design. For instance failure modes of a resistor include change in value within the range of one-half to two times its original value, open circuit and short circuit faults. If this resistor is used as part of an analog circuit monitoring a particular voltage or current level, the drift failure mode will directly result in a significant error in measurement and most likely be dangerous.If the same resistor was used in series with the base of a transistor used to drive an on-off relay coil, the product would most likely continue to operate and produce the desired output state even if the resistor drifts over this relatively wide range of values. Resistor drift in this application has no effect of the functionality. Therefore this failure mode is called “No Effect” as although the component is part of the desired function this particular failure mode has no effect on the desired function. If this resistor were to fail open circuit there would be an impact on the function so all failure modes of the component cannot be ignored.No Impact – Category 2, Not a PartThe purpose of some components is to support human interface display and auxiliary functions that are not part of the circuitry providing the functionality of the product being relied upon for the application. For instance a resistor can be used to set the current level for an indicating LED that lights up whencommunications are taking place so that it can be easily seen if communications are active. Failure of the resistor such that the LED does not light up during communications has no impact on the normal operation of the product. In fact any of the failure modes of the resistor are unlikely to impact performance of the function of the product. This category of components are referred to as “Not a part” since they are not a part of the implementation of the desired function. New Definition of “Safe” FailuresNote that “no effect” refers to one particular failure mode of a component that is used by the desired function (and other failure modes of that part will lead to loss of function) and “not a part” refers to an entire component that is not necessary or used in the implementation of the desired function but both can be considered “safe” by the current IEC61508 definition.A more useful and non-ambiguous definition of a safe failure in the context of a safety system is one that leads to a false trip (in the absence of a fault tolerant architecture) which is clearly the opposite of a dangerous failure (failure to perform the safety function or inability to trip when needed). This definition of “safe” also has the additional benefit of providing an estimated false trip rate for a safety product which is also very important to a potential user of the product as it typically leads to lost production and is possibly an initiating event for another hazard scenario.Safe Failure Fraction calculationThe remaining question is how the “No Effect” and “Not a part” failure rates are used (or not used) in the calculation of the SFF. The most conservative method is to exclude both from the calculation which provides the lowest SFF estimate for a product. This approach only considers the safe and dangerous failures as those that directly impact the desired safety function. This policy was followed by conservative vendors including exida once the problem was recognized in the time period approximately represented by the years 2000 through 2002.It is clearly bad policy to count the “Not a part” failures as “safe.” This is because a product designer with a design that is close to a particular SFF threshold could potentially reach that threshold by adding extraneous components which provide no improvement for safety functionality.Around the year 2003 the consensus of the key industry experts in this area settled on interpretation of the original “safe failures” as the newly defined safe failures plus No Effect but excluding Not a Part failures. The results in the sum of the newly defined safe failure and the no effect failures being used for the safe failure portion of the SFF calculation and the “Not a part” failure rates are not considered relevant to safety calculations. FMEDA result reports began publishing numbers for the additional failure rate categories.The result of this change is that the total failure rate reported by the FMEDA represents the total failure rate for all the components even if some of those failure rates do not lead to an observable failure at the product level. Observed failure rates at the product level are predicted by the total failure rate minus the no effect failure rate because the no effect failures would, in most cases, only be discovered by full parametric testing of the individual components.Functional Failure Mode AnalysisAlso in the early 2000’s functional failure mode analysis was added to the FMEDA process. In early FMEDA work, component failure modes were mapped directly to “safe” or “dangerous” categories per IEC 61508. This was relatively easy since everything that was not “dangerous” was “safe.” With multiple failure mode categories now existing, direct assignment became more difficult. In addition, it became clear that the category assignment might change if a product were used in different applications. With direct failure mode category assignment during the FMEDA, a new FMEDA was required for each new application or each variation in usage.Under the functional failure mode approach, the actual functional failure modes of the product are identified. During the detailed FMEDA, each component failure mode is mapped to a functional failure mode. The functional failure modes are then categorized according to product failure mode in a particular application. This eliminates the need for more detailed work when a new application is considered.Mechanical FMEDA TechniquesIt became clear in the early 2000’s that many products being used in safety critical applications had mechanical components. An FMEDA done without considering these mechanical components was incomplete and potentially misleading. The fundamental problem in using the FMEDA technique was the lack of a mechanical component database that included part failure rates and failure mode distributions.Using a number of published reference sources, exida began development of a mechanical component database in 2003 [Gob03]. After a few years of research and refinement [GOB07], the database has been published [exi06]. This has allowed the FMEDA to be used on combination electrical / mechanical components and purely mechanical components.The FutureThis paper explains how FMEDA techniques have evolved over the past decade since the first efforts to define the process were made. One result of this is thatolder FMEDA reports (2002 and before) should not be used and should never be compared to newer work.It is clear that further refinement of the component database with selective calibration to different operation profiles is needed. In addition, comparisons of FMEDA results with field failure studies have shown that human factors, especially maintenance procedures, have an impact on the failure rates and failure modes of products. As more data becomes available, these factors can also be added to FMEDA analysis.References[Col84] Collett, R. E. and Bachant, P. W., “Integration of BIT Effectiveness with FMECA,” 1984 Proceedings of the Annual Reliability and Maintainabiltiy Symposium, NY: New York, IEEE, 1984.[AME87] H.A. Amer,and E. J. McCluskey, “Weighted Coverage in Fault-Tolerant Systems,” 1987 Proceedings of the Annual Reliability and Maintainabiltiy Symposium, NY: NY, IEEE, 1987.[GOB92] Goble, W.M., Evaluating Control Systems Reliability, Techniques and Applications, NC: Research Triangle Park, Instrument Society of America, 1992. [MOR94] FMEDA Analysis of CDM (Critical Discrete Module) – QUADLOG, Moore Products Co., PA: Spring House, 1994.[GOB98a] Goble, W.M., The Use and Development of Quantitative Reliability and Safety Analysis in New Product Design, University Press, Eindhoven University of Technology, Netherlands: Eindhoven, 1998.[GOB98b] Goble, W.M., Control Systems Safety Evaluation and Reliability, second edition, NC: Research Triangle Park: ISA, 1998.[GOB99] W. M. Goble and A. C. Brombacher, “Using a Failure Modes, Effects and Diagnostic Analysis (FMEDA) to Measure Diagnostic Coverage in Programmable Electronic Systems,” Reliability Engineering and System Safety, Vol. 66, No. 2, November 1999.[GOB03] W. M. Goble, “Accurate Failure Metrics for Mechanical Instruments,” Proceedings of IEC 61508 Conference, Germany: Augsberg, RWTUV, January 2003.[EXi06] Electrical & Mechanical Component Reliability Handbook, exida, PA: Sellersville, 2006. See [GOB07] W.M. Goble and J.V. Bukowski, “Development of a Mechanical Component Failure Database,” 2007 Proceedings of the Annual Reliability and Maintainabiltiy Symposium, NY: NY, IEEE, 2007.Revision HistoryRev. 1.0,Goble, Grebe Initial release, February 19, 2007 Rev. 1.1, Goble, Grebe Review results included, February 19,2007。
听学术讲座对重要的点的总结英语作文

听学术讲座对重要的点的总结英语作文全文共3篇示例,供读者参考篇1Title: Summary of Key Points from Academic LectureIntroduction:Recently, I had the opportunity to attend an academic lecture on a topic that resonates with my field of study. The lecture was informative, engaging, and thought-provoking, and I walked away with a deeper understanding of the subject matter. In this summary, I will highlight some of the key points that were discussed during the lecture.Key Points:1. Importance of Research: The speaker emphasized the importance of conducting rigorous research in order to advance knowledge in a particular field. Research serves as the foundation for academic progress and contributes to the development of new theories and concepts.2. Critical Thinking: Critical thinking was highlighted as a crucial skill for academic success. The ability to analyzeinformation, evaluate arguments, and make logical connections is essential for engaging with complex ideas and formingwell-supported conclusions.3. Collaboration and Networking: The speaker stressed the value of collaboration and networking in academia. By working with colleagues, sharing ideas, and building professional relationships, researchers can expand their knowledge, access new resources, and enhance the impact of their work.4. Ethical Considerations: Ethical considerations were discussed in relation to research conduct. Researchers must adhere to ethical guidelines, maintain integrity in their work, and prioritize the well-being of research participants in order to uphold the credibility and validity of their findings.5. Impact and Dissemination: The speaker underscored the importance of disseminating research findings to a wider audience. By publishing in reputable journals, presenting at conferences, and engaging with the public, researchers can enhance the visibility and impact of their work and contribute to the advancement of knowledge in their field.Conclusion:In conclusion, the academic lecture was a valuable experience that provided me with insights into the key principles and practices of successful research in academia. By focusing on the importance of research, critical thinking, collaboration, ethics, and impact, the lecture reinforced the foundational principles of academic scholarship and inspired me to continue pursuing excellence in my own research endeavors. I look forward to applying the knowledge and skills gained from the lecture to my future work and contributing to the ongoing discourse in my field.篇2Title: Summary of Key Points from Academic LectureIntroductionRecently, I attended an academic lecture on the topic of artificial intelligence and its impact on society. The speaker, a renowned expert in the field, presented a wealth of information and insights that shed light on the current and future implications of this rapidly advancing technology. In this paper, I will summarize the key points from the lecture, which I believe are crucial for understanding the significance of artificial intelligence in our society.Key Points1. Definition and Scope of Artificial IntelligenceThe speaker began by defining artificial intelligence as the simulation of human intelligence processes by machines, particularly computer systems. He emphasized that AI encompasses a wide range of capabilities, including learning, reasoning, problem-solving, perception, and language understanding. The scope of AI applications is vast, ranging from self-driving cars and virtual assistants to healthcare diagnostics and financial analysis.2. Ethical and Social Implications of AIOne of the most pressing issues raised during the lecture was the ethical and social implications of AI. The speaker highlighted the potential risks associated with the use of AI, such as job displacement, privacy concerns, and bias indecision-making algorithms. He stressed the importance of developing ethical guidelines and regulatory frameworks to ensure that AI technologies are used responsibly and in the best interests of society.3. Impact of AI on Economics and Labor MarketAnother key point discussed was the impact of AI on the economy and the labor market. The speaker argued that AI has the potential to increase productivity and drive economic growth, but also to disrupt traditional industries and occupations. He pointed out that certain jobs may be at risk of automation, leading to job losses and income inequality. However, he also noted that AI could create new opportunities for entrepreneurship and innovation in emerging industries.4. Future Trends in Artificial IntelligenceThe lecture concluded with a discussion of future trends in artificial intelligence. The speaker highlighted the rapid pace of technological advancement in AI, with the potential for breakthroughs in machine learning, natural language processing, and robotics. He predicted that AI will continue to impact various sectors of society, including healthcare, transportation, finance, and education. He also emphasized the need for ongoing research and development to address the challenges and opportunities presented by AI.ConclusionIn conclusion, the academic lecture on artificial intelligence provided valuable insights into the current state and future direction of this transformative technology. The key pointsdiscussed, including the definition and scope of AI, ethical and social implications, economic impact, and future trends, underscored the importance of understanding and engaging with AI in a thoughtful and responsible manner. As we navigate the opportunities and challenges presented by AI, it is essential to consider the broader implications for society and to work towards harnessing the potential benefits of AI while mitigating its risks.篇3Summary of Important Points on Listening to Academic LecturesAttending academic lectures is an essential part of the learning process for students in various fields of study. These lectures provide valuable insights and information that can help students enhance their knowledge and understanding of a particular subject. In order to make the most out of academic lectures, it is important to pay attention to key points and take notes effectively. This article will provide a summary of important points to keep in mind when listening to academic lectures.First and foremost, it is crucial to be actively engaged during the lecture. This means being attentive and focused on thespeaker, as well as being open to new ideas and perspectives. It is also important to participate in discussions and ask questions when necessary. Taking an active role in the lecture can help enhance your understanding of the material and make the learning experience more engaging and enjoyable.Secondly, it is important to take notes effectively during the lecture. This involves jotting down key points, main ideas, and important details discussed by the speaker. It is helpful to use a systematic approach to note-taking, such as using bullet points or organizing information in a structured manner. Taking notes can help you retain information better and serve as a useful reference when studying for exams or writing papers.Additionally, it is important to review your notes regularly after the lecture. This can help reinforce your understanding of the material and clarify any confusing or difficult concepts. It is also beneficial to review any additional materials provided by the lecturer, such as slides or handouts, to further enhance your understanding of the topic.Furthermore, it is important to actively engage with the material outside of the lecture. This can involve reading relevant textbooks, articles, or research papers related to the topic discussed in the lecture. It is also helpful to participate in studygroups or discussion forums to exchange ideas and perspectives with other students.In conclusion, listening to academic lectures is a valuable learning experience that can help students enhance their knowledge and understanding of a particular subject. By actively engaging with the material, taking notes effectively, reviewing notes regularly, and engaging with the material outside of the lecture, students can make the most out of their academic lectures and improve their overall learning experience.。
et200S_diag
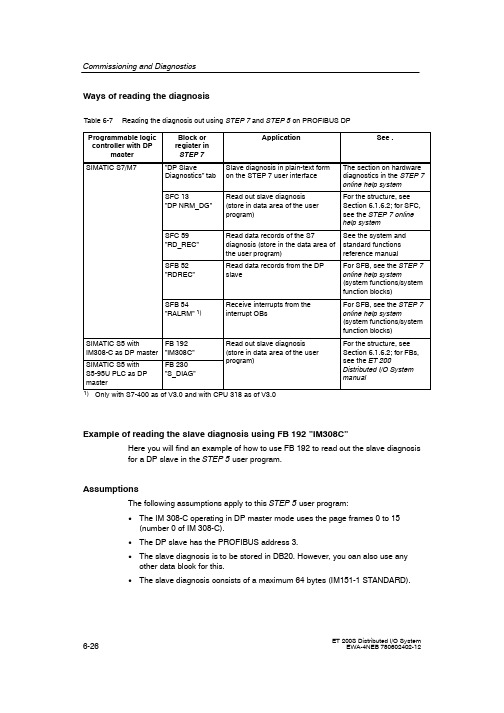
Ways of reading the diagnosisTable6-7Reading the diagnosis out using STEP7and STEP5on PROFIBUS DPProgrammable logic controller with DPmasterBlock orregister inSTEP7Application See.SIMATIC S7/M7 DP SlaveDiagnostics tab Slave diagnosis in plain-text formon the STEP7user interfaceThe section on hardwarediagnostics in the STEP7online help systemSFC13DP NRM_DG Read out slave diagnosis(store in data area of the userprogram)For the structure,seeSection6.1.6.2;for SFC,see the STEP7onlinehelp systemSFC59RD_REC Read data records of the S7diagnosis(store in the data area ofthe user program)See the system andstandard functionsreference manualSFB52 RDREC Read data records from the DPslaveFor SFB,see the STEP7online help system(system functions/systemfunction blocks)SFB54RALRM 1)Receive interrupts from theinterrupt OBsFor SFB,see the STEP7online help system(system functions/systemfunction blocks)SIMATIC S5withIM308-C as DP master FB192IM308CRead out slave diagnosis(store in data area of the user)For the structure,seeSection6.1.6.2;for FBs,th200SIMATIC S5with S5-95U PLC as DP master FB230S_DIAGprogram)see the ETDistributed I/O Systemmanual1)Only with S7-400as of V3.0and with CPU318as of V3.0Example of reading the slave diagnosis using FB192 IM308CHere you will find an example of how to use FB192to read out the slave diagnosisfor a DP slave in the STEP5user program.AssumptionsThe following assumptions apply to this STEP5user program:The IM308-C operating in DP master mode uses the page frames0to15(number0of IM308-C).The DP slave has the PROFIBUS address3.The slave diagnosis is to be stored in DB20.However,you can also use anyother data block for this.The slave diagnosis consists of a maximum64bytes(IM151-1STANDARD).ET200S Distributed I/O SystemSTEP5user programSTL Explanation :A DB30:SPA FB192Name:IM308CDPAD:KH F800 IMST:KY0,3 FCT:KC SD GCGR:KM0 TYP:KY0,20 STAD:KF+1 LENG:KF-1 ERR:DW0Default address area of the IM308-CIM no.=0,PROFIBUS address of DP slave=3 Function:Read slave diagnosticsNot evaluatedS5data area:DB20Diagnostic data from data word1Diagnosis length=joker length(all permitted bytes)Error code stored in DW0of DB30ET200S Distributed I/O SystemExample of reading the S7diagnosis using SFC13 DP NRM_DGHere you will find an example of how to use SFC13to read out the slavediagnosis for a DP slave in the STEP7user program.AssumptionsThe following assumptions apply to this STEP7user program:The diagnostic address of the ET200S is1022(3FE H).The slave diagnostic information is to be stored in DB82:starting at address0.0,length64bytes.The slave diagnostics is max.64bytes(IM151-1STANDARD in DPV0operation).STEP7user programSTL ExplanationCALL SFC13REQ:=TRUELADDR:=W#16#3FERET_VAL:=MW0RECORD:=P#DB82.DBX0.0BYTE64 BUSY:=M2.0Read requestDiagnostic address of the ET200SRET_VAL of SFC13Data mailbox for the diagnosis in DB82Read operation runs over several OB1cyclesET200S Distributed I/O System6.1.6.2Structure of slave diagnostic data Structure of slave diagnostic dataFigure6-20Structure of slave diagnostic dataET200S Distributed I/O SystemNoteThe length of the diagnostic message frame varies:Between6and43bytes in the IM151-1BASICwith IM151-1STANDARD,IM151-1FO STANDARD and IM151-1HIGHFEATURE(depending on configuration)--between6and62bytes in DPV0operation--between6and110bytes in DPV0operation(STANDARD)--between6and128bytes in DPV0operation(HIGH FEATURE)You can find out the length of the last diagnostic message frame received in: STEP7from the RET_VAL parameter of the SFC13.STEP5from the ERR parameter of the FB192.ET200S Distributed I/O System6.1.6.3Station statuses1to3DefinitionStation statuses1to3provide an overview of the status of a DP slave. Station status1Table6-8Structure of station status1(byte0)ET200S Distributed I/O SystemET 200S Distributed I/O SystemStation status 2Table 6-9Structure of station status 2(byte 1)Bit Meaning01:New parameters have to be assigned to the DP slave.11:A diagnostic message has been issued.The DP slave will not work until the fault has been corrected (static diagnostic message).21:The bit is always set to 1 in the DP slave.31:Response monitoring has been enabled for this DP slave.41:The DP slave has received the FREEZE control command 1.51:The DP slave has received the SYNC control command 1.60:The bit is always at 0.71:The DP slave has been disabled,that is,it has been removed from the processing in progress.1The bit is updated only if another diagnostic message changes,too.Station status 3Table 6-10Structure of station status 3(byte 2)6.1.6.4Master PROFIBUS AddressDefinitionThe master PROFIBUS address diagnostic byte contains the PROFIBUS addressof the DP master that:Assigned parameters to the DP slave andHas read and write access to the DP slaveThe master PROFIBUS address is in byte3of the slave diagnosis.6.1.6.5Manufacturer IDDefinitionThe manufacturer ID contains a code that describes the type of the DP slave. Manufacturer IDTable6-11Structure of the manufacturer ID(Bytes4,5)Byte4Byte5Manufacturer ID for80H F3H ET200S with IM151-1BASIC80H6A H ET200S with IM151-1STANDARD80H6B H ET200S with IM151-1FO STANDARD80H E0H ET200S with IM151-1HIGH FEATUREET200S Distributed I/O SystemET 200S Distributed I/O System6.1.6.6Module diagnosisDefinitionThe module diagnosis indicates whether or not modules of the ET 200S have errors/faults.The module diagnosis begins as of byte 6and comprises:3bytes in the case of the IM151-1BASIC9bytes in the case of the IM151-1STANDARD;IM151-1FO STANDARD and IM151-1HIGH FEATURE.Module diagnosisThe module diagnosis for the ET 200S with the IM151-1BASIC is structured as follows:Byte 6Bit no.Byte 7Byte 871365420Module:1to 8Module:9to 12713654281112109Events on thecorresponding module are indicated by set bits.70Bit no.Length of the module diagnosis including byte 6(=3bytes)Code for ID-related diagnostics0165110000*****Always 0Figure 6-21Structure of the ID-related diagnosis for the ET 200S with the IM151-1BASICET 200S Distributed I/O System The module diagnosis for the ET 200S with the IM151-1STANDARD,IM151-1FO STANDARD and IM151-1HIGH FEATURE is structured as follows:Byte 6Bit no.Byte 7Byte 871365420Byte 9Byte 10Byte 11Byte 12Byte 13Byte 14Module:1to 8Module:9to 16Module:17to 24Module:25to 32Module:33to 40Module:41to 48Module:49to 56Module:57to 63713654281615131411121091819202322211728243627293031323435262539403738473341464849504345444253525456556151586259605763Events on thecorresponding module are indicated by set bits.70Bit no.Length of the module diagnosis including byte 6(=9bytes)Code for ID-related diagnostics0165100100*Always 0*Figure 6-22Structure of the ID-related diagnosis for the ET 200S with the IM151-1STANDARD,IM151-1FO STANDARD and IM151-1HIGH FEATURECommissioning and DiagnosticsET 200S Distributed I/O System 6.1.6.7Module informationDefinitionThe module status indicates the status of the configured modules and expands on the module diagnosis as regards the configuration.The module status begins after the module diagnosis and comprises:7bytes in the case of the IM151-1BASIC20bytes in the case of the IM151-1STANDARD,IM151-1FO STANDARD and IM151-1HIGH FEATURE.Module statusThe module status for the ET 200S with the IM151-1BASIC is structured as follows:Byte 9Byte 1070Byte 117082H 0H 0H76541320Byte 13Byte 12Bit no.Modules 1to 4Byte 14Modules 5to 8Byte 15Modules 9to 1200B :module OK;valid user data01B :module error;invalid user data10B :incorrect module;invalid user data11B :no module (or module failure);invalid user dataStatus type:Module Status irrelevant irrelevant 70Bit no.Code for module status0056Length of the module statusincluding byte 15(=7bytes)1110001234Figure 6-23Structure of the module status for the ET 200S with the IM151-1BASICCommissioning and DiagnosticsET 200S Distributed I/O System The module status for the ET200S with the IM151-1STANDARD,IM151-1FO STANDARD,and IM151-1HIGH FEATURE is structured as follows:Byte 15Byte 1670Byte 177082H 0H 0H76541320Byte 19Byte 18Bit no.Modules 1to 4Byte 20Modules 5to 8Byte 21Modules 9to 12Byte 22Modules 13to 16Byte 23Modules 17to 20Byte 24Modules 21to 24Byte 25Modules 25to 28Byte 26Modules 29to 32Byte 27Modules 33to 36Byte 28Modules 37to 40Byte 29Modules 41to 44Byte 30Modules 45to 48Byte 31Modules 49to 52Byte 32Modules 53to 56Byte 33Modules 57to 60Byte 34Modules 61to 63Status type:Module Status irrelevant irrelevant 70Bit no.Code for module status0056Length of the module statusincluding byte 15(=20bytes)001010123400B :module OK;valid user data01B :module error;invalid user data10B :incorrect module;invalid user data11B :no module (or module failure);invalid user data**always 00Figure 6-24Structure of the module status for ET 200S with the IM151-1STANDARD;IM151FO STANDARD and IM151HIGH FEATURE。
hotplugtest use of undeclared identifier

hotplugtest use of undeclared identifierUnder the hot-plug testing scenario, encountering an error message stating "use of undeclared identifier" typically occurs when the compiler encounters a variable or function name that it does not recognize or cannot find within the scope of the program. In this case, the identifier "hotplugtest" is being used but has not been declared or defined anywhere in the code.To resolve the "use of undeclared identifier" error, it is crucial to understand the scope rules of the programming language being used and ensure that all necessary declarations or definitions are provided. Here are some related concepts and guidelines that can be referred to when encountering this error:1. Variable Declaration: Before using any variable in a program, it must be declared with a valid data type. For example, in C++, the code would typically start with variable declarations such as int, float, or double, followed by the variable name. An example of a correct variable declaration would be "int hotplugtest;". Ensure that the variable "hotplugtest" is declared in the appropriate scope before using it in the program.2. Variable Scope: Variables have a specific scope within a program, determining where they can be accessed. If the variable "hotplugtest" is declared within a specific block or function, it may not be accessible outside of that block or function. It is important to ensure that the variable declaration is within the necessary scope for it to be recognized throughout the program.3. Function Declarations and Definitions: Similar to variables,functions must be declared or defined before using them in a program. If the error message "use of undeclared identifier" refers to a function, ensure that the function is declared or defined before calling it. The declaration often involves specifying the return type and function signature, while the definition contains the actual implementation of the function.4. Header Files: If the "use of undeclared identifier" error occurs when using a variable or function from an external library or module, it is often because the necessary header files have not been included correctly. In many programming languages like C or C++, external libraries or modules require corresponding header files to be included to make their declarations accessible. Check if the required headers are included in the program.5. Typographical Errors: Often, the error message "use of undeclared identifier" can occur due to typographical mistakes in the code. Double-check the spelling and case-sensitivity of the variable or function names to ensure they match the intended declaration or definition.6. Name Conflicts: It is possible that the identifier "hotplugtest" is conflicting with another identifier in the program. If there is already a variable or function with the same name, it can cause the "use of undeclared identifier" error. Ensure that each identifier within the program has a unique name to avoid conflicts.In conclusion, the error message "use of undeclared identifier" indicates that the compiler encountered an identifier (such as a variable or function name) that has not been declared or defined inthe program. By considering the principles of variable declaration, function declaration, scope, header files, typographical errors, and name conflicts, programmers can effectively troubleshoot and resolve these errors.。
Signal and Image Processing

Signal and Image Processing Signal and image processing are crucial fields in the realm of technology and communication. These processes involve manipulating signals and images to extract meaningful information, enhance quality, and facilitate various applications. Signal processing deals with analyzing, modifying, and synthesizing signals such as audio, video, and data, while image processing focuses on manipulating digital images to improve visual quality, extract information, and enable computer vision tasks. Both disciplines play a vital role in numerous industries, including healthcare, telecommunications, multimedia, and security. In the realm of healthcare, signal and image processing technologies have revolutionized diagnostics, treatment, and monitoring of patients. Medical imaging techniqueslike MRI, CT scans, and X-rays rely on sophisticated image processing algorithms to generate detailed images of internal organs and tissues, aiding in the detection of diseases and abnormalities. Signal processing techniques are also used in analyzing physiological signals like ECG and EEG to diagnose cardiac arrhythmias, brain disorders, and sleep disorders. These technologies have significantly improved patient care by enabling early detection and accurate diagnosis of various medical conditions. In the field of telecommunications, signal processing plays a crucial role in ensuring efficient communication and data transmission. Digital signal processing techniques are used in encoding, decoding, and compressing audio and video signals to reduce bandwidth requirements and enhance the quality of multimedia content. Image processing algorithms are employed in image and video compression, noise reduction, and enhancement to deliver high-quality visual content over networks. These advancements have led to the proliferation of high-definition video streaming, video conferencing, and multimedia communication services, transforming the way people interact and communicate globally. In the realm of multimedia, signal and image processing technologies have revolutionized content creation, editing, and distribution. Image processing algorithms like image segmentation, object recognition, and pattern recognition are used in video editing software, augmented reality applications, and virtual reality systems to create immersive visual experiences. Signal processing techniques such as audio filtering, equalization, and synthesisare employed in audio editing software, music production tools, and speech recognition systems to enhance sound quality and extract meaningful information from audio signals. These technologies have empowered content creators, artists, and musicians to unleash their creativity and produce captivating multimedia content. In the field of security and surveillance, signal and image processing technologies play a critical role in ensuring public safety, crime prevention, and threat detection. Image processing algorithms like face recognition, object tracking, and anomaly detection are used in surveillance cameras, facial recognition systems, and security checkpoints to identify and track individuals, monitor suspicious activities, and prevent security breaches. Signal processing techniques such as audio analysis, acoustic sensing, and sound localization are employed in gunshot detection systems, audio surveillance tools, and perimeter security solutions to detect and respond to potential threats in real-time. These technologies have bolstered security measures, law enforcement efforts, and emergency response capabilities, safeguarding communities and public spaces from various security risks. In conclusion, signal and image processing technologies have transformed various industries and applications, driving innovation, efficiency, and quality in communication, healthcare, multimedia, and security. These technologies continue to evolve and advance, opening new possibilities and opportunities for research, development, and implementation in diverse fields. As we navigate the digital age and embrace the power of signals and images, it is essential to harness the potential of signal and image processing to address complex challenges, improve processes, and enhance experiences for individuals and societies worldwide.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
• Diagnostics of key processes relevant for the effects of the different modes of transportations:
– stratosphere-troposphere exchange of O3 and NOx – boundary layer venting – convective transport of pollutants emitted at the surface
Fundamental evaluation ofrison with observations: • Comparison of observed and modelled tropospheric
ozone and CO (O3 at various altitudes, surface O3, CO) • Time series • Model biases • Correlations • Skill scores
Biogenic NO, isoprene, and monoterpene emissions soon available by MPI for chemistry
Lightning NOx: 5 Tg (N)/yr
Transport emissions: from Activity 1 if available (report by Peter) otherwise road traffic (Volker), air traffic (AERO2K or DLR1992), shipping emissions (via UiO, Endresen)
2019 quasi-monthly means (dates where ozonesonde data available only)
Brunner et al. (2019)
Testing the skill of the models: Taylor diagrams
• correlation coefficient, • pattern root-mean square (RMS) error, • ratio of modelled/observed standard
Definition and diagnostics for the model-observations comparison
Christina Schnadt Poberaj
Evaluation of multi-model performance (WP 3.1.1)
• Definition of model simulations: simulations of selected years, comparison of model results
Model-model intercomparisons: • Intercomparisons between models: zonal means and
horizontal distributions of relevant species (O3, CO, CH4, NO2, (NOx), CH2O, HNO3, OH, SO2, H2SO4)
Evaluation of multi-model performance
• Definition of model simulations: simulations of selected years, comparison of model results
with observations in the ETHmeg database
Identify model biases: Scatterplots O3, NOx, CO, …
Model biases at individual ozonesonde stations or airports (MOZAIC airport profiles)
TM4, RETRO project
Boundary conditions for 2019 runs:
Model will be run in the same set-up as in the current impact study (WP3.1.2)
Anthropogenic emissions year 2000: EDGAR 3.2 Fast Track 2000 - GHGs CO2, CH4, N2O, and F-gases (HFCs, PFCs, and SF6) - air pollutants CO, NMVOC, NOx, SO2 Large-scale biomass burning: annual burned area estimates for 2019-2000 average, or actual 2000 area, or EDGAR 3.2 emission factors, or factors compiled by Andreae and Merlet (2019)
Model evaluation of RETRO 2019 test simulations using ozonesonde station data (left) and CMDL stations data for surface ozone and CO (right)
Brunner et al. (2019)
Model evaluation: year 2019 Campaign data to be used: SPURT, UTOPOHIAN_Act, MOZAIC, CONTRACE, VINTERSOL, INTEX, SCIAMACHY NO2 columns
Evaluation of multi-model performance
