操作系统 第二版中文版答案
现代操作系统(第二版)习题答案

MODERN OPERATING SYSTEMS SECOND EDITIONPROBLEM SOLUTIONSANDREW S. TANENBAUM Vrije Universiteit Amsterdam, The NetherlandsPRENTICE HALLUPPER SADDLE RIVER, NJ 07458SOLUTIONS TO CHAPTER 1 PROBLEMS1. An operating system must provide the users with an extended (i.e., virtual) machine, and it must manage the I/O devices and other system resources.2. Multiprogramming is the rapid switching of the CPU between multiple processes in memory. It is commonly used to keep the CPU busy while one or more processes are doing I/O.3. Input spooling is the technique of reading in jobs, for example, from cards, onto the disk, so that when the currently executing processes are finished, there will be work waiting for the CPU. Output spooling consists of first copying printable files to disk before printing them, rather than printing directly as the output is generated. Input spooling on a personal computer is not very likely, but output spooling is.4. The prime reason for multiprogramming is to give the CPU something to do while waiting for I/O to complete. If there is no DMA, the CPU is fully occupied doing I/O, so there is nothing to be gained (at least in terms of CPU utilization) by multiprogramming. No matter how much I/O a program does, the CPU will be 100 percent busy. This of course assumes the major delay is the wait while data are copied. A CPU could do other work if the I/O were slow for other reasons (arriving on a serial line, for instance).5. Second generation computers did not have the necessary hardware to protect the operating system from malicious user programs.6. It is still alive. For example, Intel makes Pentium I, II, and III, and 4 CPUs with a variety of different properties including speed and power consumption. All of these machines are architecturally compatible. They differ only in price and performance, which is the essence of the family idea.7. A 25×80 character monochrome text screen requires a 2000-byte buffer. The 1024 ×768 pixel 24-bit color bitmap requires 2,359,296 bytes. In 1980 these two options would have cost $10 and $11,520, respectively. For current prices, check on how much RAM currently costs, probably less than $1/MB.8. Choices (a), (c), and (d) should be restricted to kernel mode.9. Personal computer systems are always interactive, often with only a single user. Mainframe systems nearly always emphasize batch or timesharing with many users. Protection is much more of an issue on mainframe systems, as is efficient use of all resources.10. Every nanosecond one instruction emerges from the pipeline. This meansthe machine is executing 1 billion instructions per second. It does not matter at all how many stages the pipeline has. A 10-stage pipeline with 1 nsec per2 PROBLEM SOLUTIONS FOR CHAPTER 1stage would also execute 1 billion instructions per second. All that matters is how often a finished instructions pops out the end of the pipeline.11. The manuscript contains 80 × 50 × 700 = 2.8 million characters. This is, of course, impossible to fit into the registers of any currently available CPU and is too big for a 1-MB cache, but if such hardware were available, the manuscript could be scanned in 2.8 msec from the registers or 5.8 msec from the cache. There are approximately 2700 1024-byte blocks of data, so scanning from the disk would require about 27 seconds, and from tape 2 minutes 7 seconds. Of course, these times are just to read the data. Processing and rewriting the data would increase the time.12. Logically, it does not matter if the limit register uses a virtual address or a physical address. However, the performance of the former is better. If virtual addresses are used, the addition of the virtual address and the base register can start simultaneously with the comparison and then can run in parallel. If physical addresses are used, the comparison cannot start until the addition is complete, increasing the access time.13. Maybe. If the caller gets control back and immediately overwrites the data, when the write finally occurs, the wrong data will be written. However, if the driver first copies the data to a private buffer before returning, then the caller can be allowed to continue immediately. Another possibility is to allow the caller to continue and give it a signal when the buffer may be reused, but this is tricky and error prone.14. A trap is caused by the program and is synchronous with it. If the program is run again and again, the trap will always occur at exactly the same position in the instruction stream. An interrupt is caused by an external event and its timing is not reproducible.15. Base = 40,000 and limit = 10,000. An answer of limit = 50,000 is incorrect for the way the system was described in this book. It could have been implemented that way, but doing so would have required waiting until the address + base calculation was completed before starting the limit check, thus slowing down the computer.16. The process table is needed to store the state of a process that is currently suspended, either ready or blocked. It is not needed in a single process system because the single process is never suspended.17. Mounting a file system makes any files already in the mount point directory inaccessible, so mount points are normally empty. However, a system administrator might want to copy some of the most important files normally located in the mounted directory to the mount point so they could be found in their normal path in an emergency when the mounted device was being checked or repaired.PROBLEM SOLUTIONS FOR CHAPTER 1 318. Fork can fail if there are no free slots left in the process table (and possibly if there is no memory or swap space left). Exec can fail if the file name given does not exist or is not a valid executable file. Unlink can fail if the file to be unlinked does not exist or the calling process does not have the authority to unlink it. 19. If the call fails, for example because fd is incorrect, it can return −1. It can also fail because the disk is full and it is not possible to write the number of bytes requested. On a correct termination, it always returns nbytes.20. It contains the bytes: 1, 5, 9, 2.21. Block special files consist of numbered blocks, each of which can be read or written independently of all the other ones. It is possible to seek to any block and start reading or writing. This is not possible with character special files. 22. System calls do not really have names, other than in a documentation sense. When the library procedure read traps to the kernel, it puts the number of the system call in a register or on the stack. This number is used to index into a table. There is really no name used anywhere. On the other hand, the name of the library procedure is very important, since that is what appears in the program.23. Yes it can, especially if the kernel is a message-passing system.24. As far as program logic is concerned it does not matter whether a call to a library procedure results in a system call. But if performance is an issue, if a task can be accomplished without a system call the program will run faster. Every system call involves overhead time in switching from the user context to the kernel context. Furthermore, on a multiuser system the operating system may schedule another process to run when a system call completes, further slowing the progress in real time of a calling process.25. Several UNIX calls have no counterpart in the Win32 API:Link: a Win32 program cannot refer to a file by an alternate name or see it in more than one directory. Also, attempting to create a link is a convenient way to test for and create a lock on a file.Mount and umount: a Windows program cannot make assumptions about standard path names because on systems with multiple disk drives the drive name part of the path may be different.Chmod: Windows programmers have to assume that every user can access every file.Kill: Windows programmers cannot kill a misbehaving program that is not cooperating.4 PROBLEM SOLUTIONS FOR CHAPTER 126. The conversions are straightforward:(a) A micro year is 10−6 × 365× 24× 3600= 31.536 sec. (b) 1000 meters or 1 km.(c) There are 240 bytes, which is 1,099,511,627,776 bytes. (d) It is 6 × 1024 kg. SOLUTIONS TO CHAPTER 2 PROBLEMS1. The transition from blocked to running is conceivable. Suppose that a process is blocked on I/O and the I/O finishes. If the CPU is otherwise idle, the process could go directly from blocked to running. The other missing transition,from ready to blocked, is impossible. A ready process cannot do I/O or anything else that might block it. Only a running process can block.2. You could have a register containing a pointer to the current process table entry. When I/O completed, the CPU would store the current machine state in the current process table entry. Then it would go to the interrupt vector for the interrupting device and fetch a pointer to another process table entry (the service procedure). This process would then be started up.3. Generally, high-level languages do not allow one the kind of access to CPU hardware that is required. For instance, an interrupt handler may be required to enable and disable the interrupt servicing a particular device, or to manipulate data within a process’stack area. Also, interrupt service routines must execute as rapidly as possible.4. There are several reasons for using a separate stack for the kernel. Two of them are as follows. First, you do not want the operating system to crash because a poorly written user program does not allow for enough stack space. Second, if the kernel leaves stack data in a user program’ s memory space upon return from a system call, a malicious user might be able to use this data to find out information about other processes.5. It would be difficult, if not impossible, to keep the file system consistent. Suppose that a client process sends a request to server process 1 to update a file. This process updates the cache entry in its memory. Shortly thereafter, another client process sends a request to server 2 to read that file. Unfortunately, if the file is also cached there, server 2, in its innocence, will return obsolete data. If the first process writes the file through to the disk after caching it, and server 2 checks the disk on every read to see if its cached copy is up-to-date, the system can be made to work, but it is precisely all these disk accesses that the caching system is trying to avoid.PROBLEM SOLUTIONS FOR CHAPTER 2 56. When a thread is stopped, it has values in the registers. They must be saved, just as when the process is stopped the registers must be saved. Timesharing threads is no different than timesharing processes, so each thread needs its own register save area.7. No. If a single-threaded process is blocked on the keyboard, it cannot fork.8. A worker thread will block when it has to read a Web page from the disk. If user-level threads are being used, this action will block the entire process, destroying the value of multithreading. Thus it is essential that kernel threads are used to permit some threads to block without affecting the others.9. Threads in a process cooperate. They are not hostile to one another. If yielding is needed for the good of the application, then a thread will yield. After all, it is usually the same programmer who writes the code for all of them.10. User-level threads cannot be preempted by the clock uless the whole process’ quantum has been used up. Kernel-level threads can be preempted individually. In the latter case, if a thread runs too long, the clock will interrupt the current process and thus the current thread. The kernel is free to pick adifferent thread from the same process to run next if it so desires.11. In the single-threaded case, the cache hits take 15 msec and cache misses take 90 msec. The weighted average is 2/3×15+ 1/3 ×90. Thus the mean request takes 40 msec and the server can do 25 per second. For a multithreaded server, all the waiting for the disk is overlapped, so every request takes 15 msec, and the server can handle 66 2/3 requests per second.12. Yes. If the server is entirely CPU bound, there is no need to have multiple threads. It just adds unnecessary complexity. As an example, consider a telephone directory assistance number (like 555-1212) for an area with 1 million people. If each (name, telephone number) record is, say, 64 characters, th e entire database takes 64 megabytes, and can easily be kept in the server’ s memory to provide fast lookup.13. The pointers are really necessary because the size of the global variable is unknown. It could be anything from a character to an array of floating-point numbers. If the value were stored, one would have to give the size to create3global, which is all right, but what type should the second parameter of set3global be, and what type should the value of read3global be?14. It could happen that the runtime system is precisely at the point of blocking or unblocking a thread, and is busy manipulating the scheduling queues. This would be a very inopportune moment for the clock interrupt handler to begin inspecting those queues to see if it was time to do thread switching, since they might be in an inconsistent state. One solution is to set a flag when the runtime system is entered. The clock handler would see this and set its own flag,6 PROBLEM SOLUTIONS FOR CHAPTER 2then return. When the runtime system finished, it would check the clock flag, see that a clock interrupt occurred, and now run the clock handler.15. Yes it is possible, but inefficient. A thread wanting to do a system call first sets an alarm timer, then does the call. If the call blocks, the timer returns control to the threads package. Of course, most of the time the call will not block, and the timer has to be cleared. Thus each system call that might block has to be executed as three system calls. If timers go off prematurely, all kinds of problems can develop. This is not an attractive way to build a threads package.16. The priority inversion problem occurs when a low-priority process is in its critical region and suddenly a high-priority process becomes ready and is scheduled. If it uses busy waiting, it will run forever. With user-level threads, it cannot happen that a low-priority thread is suddenly preempted to allow a high-priority thread run. There is no preemption. With kernel-level threads this problem can arise.17. Each thread calls procedures on its own, so it must have its own stack for the local variables, return addresses, and so on. This is equally true for user-level threads as for kernel-level threads.18. A race condition is a situation in which two (or more) processes are about to perform some action. Depending on the exact timing, one or the other goesfirst. If one of the processes goes first, everything works, but if another one goes first, a fatal error occurs.19. Yes. The simulated computer could be multiprogrammed. For example, while process A is running, it reads out some shared variable. Then a simulated clock tick happens and process B runs. It also reads out the same variable. Then it adds 1 to the variable. When process A runs, if it also adds one to the variable, we have a race condition.20. Yes, it still works, but it still is busy waiting, of course.21. It certainly works with preemptive scheduling. In fact, it was designed for that case. When scheduling is nonpreemptive, it might fail. Consider the case in which turn is initially 0 but process 1 runs first. It will just loop forever and never release the CPU.22. Yes it can. The memory word is used as a flag, with 0 meaning that no one is using the critical variables and 1 meaning that someone is using them. Put a 1 in the register, and swap the memory word and the register. If the register contains a 0 after the swap, access has been granted. If it contains a 1, access has been denied. When a process is done, it stores a 0 in the flag in memory. PROBLEM SOLUTIONS FOR CHAPTER 2 723. To do a semaphore operation, the operating system first disables interrupts. Then it reads the value of the semaphore. If it is doing a down and the semaphore is equal to zero, it puts the calling process on a list of blocked processes associated with the semaphore. If it is doing an up, it must check to see if any processes are blocked on the semaphore. If one or more processes are blocked, one of then is removed from the list of blocked processes and made runnable. When all these operations have been completed, interrupts can be enabled again.24. Associated with each counting semaphore are two binary semaphores, M, used for mutual exclusion, and B, used for blocking. Also associated with each counting semaphore is a counter that holds the number of up s minus the number of down s, and a list of processes blocked on that semaphore. To implement down, a process first gains exclusive access to the semaphores, counter, and list by doing a down on M. It then decrements the counter. If it is zero or more, it just does an up on M and exits. If M is negative, the process is put on the list of blocked processes. Then an up is done on M and a down is done on B to block the process. To implement up, first M is down ed to get mutual exclusion, and then the counter is incremented. If it is more than zero, no one was blocked, so all that needs to be done is to up M. If, however, the counter is now negative or zero, some process must be removed from the list. Finally, an up is done on B and M in that order.25. If the program operates in phases and neither process may enter the next phase until both are finished with the current phase, it makes perfect sense to use a barrier.26. With round-robin scheduling it works. Sooner or later L will run, and eventually it will leave its critical region. The point is, with priority scheduling, Lnever gets to run at all; with round robin, it gets a normal time slice periodically, so it has the chance to leave its critical region.27. With kernel threads, a thread can block on a semaphore and the kernel can run some other thread in the same process. Consequently, there is no problem using semaphores. With user-level threads, when one thread blocks on a semaphore, the kernel thinks the entire process is blocked and does not run it ever again. Consequently, the process fails.28. It is very expensive to implement. Each time any variable that appears in a predicate on which some process is waiting changes, the runtime system must re-evaluate the predicate to see if the process can be unblocked. With the Hoare and Brinch Hansen monitors, processes can only be awakened ona signal primitive.8 PROBLEM SOLUTIONS FOR CHAPTER 229. The employees communicate by passing messages: orders, food, and bags in this case. In UNIX terms, the four processes are connected by pipes. 30. It does not lead to race conditions (nothing is ever lost), but it is effectively busy waiting.31. If a philosopher blocks, neighbors can later see that he is hungry by checking his state, in test, so he can be awakened when the forks are available.32. The change would mean that after a philosopher stopped eating, neither of his neighbors could be chosen next. In fact, they would never be chosen. Suppose that philosopher 2 finished eating. He would run test for philosophers 1 and 3, and neither would be started, even though both were hungry and both forks were available. Similary, if philosopher 4 finished eating, philosopher 3 would not be started. Nothing would start him.33. Variation 1: readers have priority. No writer may start when a reader is active. When a new reader appears, it may start immediately unless a writer is currently active. When a writer finishes, if readers are waiting, they are all started, regardless of the presence of waiting writers. Variation 2: Writers have priority. No reader may start when a writer is waiting. When the last active process finishes, a writer is started, if there is one; otherwise, all the readers (if any) are started. Variation 3: symmetric version. When a reader is active, new readers may start immediately. When a writer finishes, a new writer has priority, if one is waiting. In other words, once we have started reading, we keep reading until there are no readers left. Similarly, once we have started writing, all pending writers are allowed to run.34. It will need nT sec.35. If a process occurs multiple times in the list, it will get multiple quanta per cycle. This approach could be used to give more important processes a larger share of the CPU. But when the process blocks, all entries had better be removed from the list of runnable processes.36. In simple cases it may be possible to determine whether I/O will be limiting by looking at source code. For instance a program that reads all its input filesinto buffers at the start will probably not be I/O bound, but a problem that reads and writes incrementally to a number of different files (such as a compiler) is likely to be I/O bound. If the operating system provides a facility such as the UNIX ps command that can tell you the amount of CPU time used by a program , you can compare this with total time to complete execution of the program. This is, of course, most meaningful on a system where you are the only user.37. For multiple processes in a pipeline, the common parent could pass to the operating system information about the flow of data. With this information PROBLEM SOLUTIONS FOR CHAPTER 2 9the OS could, for instance, determine which process could supply output to a process blocking on a call for input.38. The CPU efficiency is the useful CPU time divided by the total CPU time. When Q ≥ T, the basic cycle is for the process to run for T and undergo a process switch for S. Thus (a) and (b) have an efficiency of T/(S + T). When the quantum is shorter than T, each run of T will require T/Q process switches, wasting a time ST/Q. The efficiency here is thenT + ST/Q T 333333333which reduces to Q/(Q + S), which is the answer to (c). For (d), we just substitute Q for S and find that the efficiency is 50 percent. Finally, for (e), as Q → 0 the efficiency goes to 0.39. Shortest job first is the way to minimize average response time. 0 < X≤ 3: X , 3, 5, 6, 9.3 < X≤ 5: 3, X , 5, 6, 9.5 < X≤ 6: 3, 5, X , 6, 9.6 < X≤ 9: 3, 5, 6, X , 9.X >9: 3, 5, 6, 9, X.40. For round robin, during the first 10 minutes each job gets 1/5 of the CPU. At the end of 10 minutes, C finishes. During the next 8 minutes, each job gets 1/4 of the CPU, after which time D finishes. Then each of the three remaining jobs gets 1/3 of the CPU for 6 minutes, until B finishes, and so on. The finishing times for the five jobs are 10, 18, 24, 28, and 30, for an average of 22 minutes. For priority scheduling, B is run first. After 6 minutes it is finished. The other jobs finish at 14, 24, 26, and 30, for an average of 18.8 minutes. If the jobs run in the order A through E, they finish at 10, 16, 18, 22, and 30, for an average of 19.2 minutes. Finally, shortest job first yields finishing times of 2, 6, 12, 20, and 30, for an average of 14 minutes.41. The first time it gets 1 quantum. On succeeding runs it gets 2, 4, 8, and 15, so it must be swapped in 5 times.42. A check could be made to see if the program was expecting input and did anything with it. A program that was not expecting input and did not process it would not get any special priority boost.43. The sequence of predictions is 40, 30, 35, and now 25.44. The fraction of the CPU used is 35/50 + 20/100 + 10/200 + x/250. To beschedulable, this must be less than 1. Thus x must be less than 12.5 msec. 45. Two-level scheduling is needed when memory is too small to hold all the ready processes. Some set of them is put into memory, and a choice is made 10 PROBLEM SOLUTIONS FOR CHAPTER 2from that set. From time to time, the set of in-core processes is adjusted. This algorithm is easy to implement and reasonably efficient, certainly a lot better than say, round robin without regard to whether a process was in memory or not.46. The kernel could schedule processes by any means it wishes, but within each process it runs threads strictly in priority order. By letting the user process set the priority of its own threads, the user controls the policy but the kernel handles the mechanism.47. A possible shell script might beif [ ! –f numbers ]; then echo 0 > numbers; fi count=0 while (test $count != 200 ) docount=‘expr $count + 1 ‘ n=‘tail –1 numbers‘ expr $n + 1 >>numbers doneRun the script twice simultaneously, by starting it once in the background (using &) and again in the foreground. Then examine the file numbers . It will probably start out looking like an orderly list of numbers, but at some point it will lose its orderliness, due to the race condition created by running two copies of the script. The race can be avoided by having each copy of the script test for and set a lock on the file before entering the critical area, and unlocking it upon leaving the critical area. This can be done like this:if ln numbers numbers.lock then n=‘tail –1 numbers‘ expr $n + 1 >>numbersrm numbers.lock fiThis version will just skip a turn when the file is inaccessible, variant solutions could put the process to sleep, do busy waiting, or count only loops in which the operation is successful.SOLUTIONS TO CHAPTER 3 PROBLEMS1. In the U.S., consider a presidential election in which three or more candidates are trying for the nomination of some party. After all the primary electionsPROBLEM SOLUTIONS FOR CHAPTER 3 11are finished, when the delegates arrive at the party convention, it could happen that no candidate has a majority and that no delegate is willing to change his or her vote. This is a deadlock. Each candidate has some resources (votes) but needs more to get the job done. In countries with multiple political parties in the parliament, it could happen that each party supports a different version of the annual budget and that it is impossible to assemble a majority to pass the budget. This is also a deadlock.2. If the printer starts to print a file before the entire file has been received (this is often allowed to speed response), the disk may fill with other requests that can’ t be printed until the first file is done, but which use up disk space needed to receive the file currently being printed. If the spooler does not start to print a file until the entire file has been spooled it can reject a request that is too big.Starting to print a file is equivalent to reserving the printer; if the reservation is deferred until it is known that the entire file can be received, a deadlock of the entire system can be avoided. The user with the fil e that won’ t fit is still deadlocked of course, and must go to another facility that permits printing bigger files.3. The printer is nonpreemptable; the system cannot start printing another job until the previous one is complete. The spool disk is preemptable; you can delete an incomplete file that is growing too large and have the user send it later, assuming the protocol allows that4. Yes. It does not make any difference whatsoever.5. Yes, illegal graphs exist. We stated that a resource may only be held by a single process. An arc from a resource square to a process circle indicates that the process owns the resource. Thus a square with arcs going from it to two or more processes means that all those processes hold the resource, which violates the rules. Consequently, any graph in which multiple arcs leave a square and end in different circles violates the rules. Arcs from squares to squares or from circles to circles also violate the rules.6. A portion of all such resources could be reserved for use only by processes owned by the administrator, so he or she could always run a shell and programs needed to evaluate a deadlock and make decisions about which processes to kill to make the system usable again.7. Neither change leads to deadlock. There is no circular wait in either case.8. Voluntary relinquishment of a resource is most similar to recovery through preemption. The essential difference is that computer processes are not expected to solve such problems on their own. Preemption is analogous to the operator or the operating system acting as a policeman, overriding the normal rules individual processes obey.12 PROBLEM SOLUTIONS FOR CHAPTER 39. The process is asking for more resources than the system has. There is no conceivable way it can get these resources, so it can never finish, even if no other processes want any resources at all.10. If the system had two or more CPUs, two or more processes could run in parallel, leading to diagonal trajectories.11. Yes. Do the whole thing in three dimensions. The z-axis measures the number of instructions executed by the third process.12. The method can only be used to guide the scheduling if the exact instant at which a resource is going to be claimed is known in advance. In practice, this is rarely the case.13. A request from D is unsafe, but one from C is safe.14. There are states that are neither safe nor deadlocked, but which lead to deadlocked states. As an example, suppose we have four resources: tapes, plotters, scanners, and CD-ROMs, as in the text, and three processes competing for them. We could have the following situation:Has Needs Available。
操作系统(第二版)习题答案

第1章一、填空1.计算机由硬件系统和软件系统两个部分组成,它们构成了一个完整的计算机系统。
2.按功能划分,软件可分为系统软件和应用软件两种。
3.操作系统是在裸机上加载的第一层软件,是对计算机硬件系统功能的首次扩充。
4.操作系统的基本功能是处理机(包含作业)管理、存储管理、设备管理和文件管理。
5.在分时和批处理系统结合的操作系统中引入“前台”和“后台”作业的概念,其目的是改善系统功能,提高处理能力。
6.分时系统的主要特征为多路性、交互性、独立性和及时性。
7.实时系统与分时以及批处理系统的主要区别是高及时性和高可靠性。
8.若一个操作系统具有很强的交互性,可同时供多个用户使用,则是分时操作系统。
9.如果一个操作系统在用户提交作业后,不提供交互能力,只追求计算机资源的利用率、大吞吐量和作业流程的自动化,则属于批处理操作系统。
10.采用多道程序设计技术,能充分发挥CPU 和外部设备并行工作的能力。
二、选择1.操作系统是一种B 。
A.通用软件B.系统软件C.应用软件D.软件包2.操作系统是对C 进行管理的软件。
A系统软件B.系统硬件C.计算机资源D.应用程序3.操作系统中采用多道程序设计技术,以提高CPU和外部设备的A 。
A.利用率B.可靠性C.稳定性D.兼容性4.计算机系统中配置操作系统的目的是提高计算机的B 和方便用户使用。
A.速度B.利用率C.灵活性D.兼容性5.C 操作系统允许多个用户在其终端上同时交互地使用计算机。
A.批处理B.实时C.分时D.多道批处理6.如果分时系统的时间片一定,那么D ,响应时间越长。
A.用户数越少B.内存越少C.内存越多D.用户数越多三、问答1.什么是“多道程序设计”技术?它对操作系统的形成起到什么作用?答:所谓“多道程序设计”技术,即是通过软件的手段,允许在计算机内存中同时存放几道相互独立的作业程序,让它们对系统中的资源进行“共享”和“竞争”,以使系统中的各种资源尽可能地满负荷工作,从而提高整个计算机系统的使用效率。
实用操作系统教程【第2版】课后习题参考答案
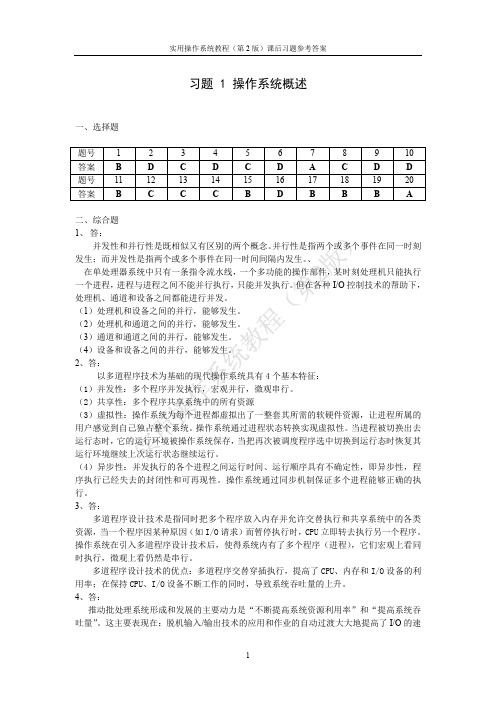
习题 1 操作系统概述一、选择题题号 1 2 3 4 5 6 7 8 9 10 答案 B D C D C D A C D D题号11 12 13 14 15 16 17 18 19 20 答案 B C C C B D B B B A二、综合题1、答:并发性和并行性是既相似又有区别的两个概念。
并行性是指两个或多个事件在同一时刻发生;而并发性是指两个或多个事件在同一时间间隔内发生。
、在单处理器系统中只有一条指令流水线,一个多功能的操作部件,某时刻处理机只能执行一个进程,进程与进程之间不能并行执行,只能并发执行。
但在各种I/O控制技术的帮助下,处理机、通道和设备之间都能进行并发。
(1)处理机和设备之间的并行,能够发生。
(2)处理机和通道之间的并行,能够发生。
(3)通道和通道之间的并行,能够发生。
(4)设备和设备之间的并行,能够发生。
2、答:以多道程序技术为基础的现代操作系统具有4个基本特征:(1)并发性:多个程序并发执行,宏观并行,微观串行。
(2)共享性:多个程序共享系统中的所有资源(3)虚拟性:操作系统为每个进程都虚拟出了一整套其所需的软硬件资源,让进程所属的用户感觉到自己独占整个系统。
操作系统通过进程状态转换实现虚拟性。
当进程被切换出去运行态时,它的运行环境被操作系统保存,当把再次被调度程序选中切换到运行态时恢复其运行环境继续上次运行状态继续运行。
(4)异步性:并发执行的各个进程之间运行时间、运行顺序具有不确定性,即异步性,程序执行已经失去的封闭性和可再现性。
操作系统通过同步机制保证多个进程能够正确的执行。
3、答:多道程序设计技术是指同时把多个程序放入内存并允许交替执行和共享系统中的各类资源,当一个程序因某种原因(如I/O请求)而暂停执行时,CPU立即转去执行另一个程序。
操作系统在引入多道程序设计技术后,使得系统内有了多个程序(进程),它们宏观上看同时执行,微观上看仍然是串行。
多道程序设计技术的优点:多道程序交替穿插执行,提高了CPU、内存和I/O设备的利用率;在保持CPU、I/O设备不断工作的同时,导致系统吞吐量的上升。
《操作系统》第二版 徐宗元OS-习题答案

习题参考答案1.6.3选择题1.(1) (5) (6) (7) (10)2. A—(2) B—(1) C—(1) D—(4) E--(3)3. A—(3) B—(4) C—(1) D—(3) E—(4)4. A—(8) B--(9) C—(1) D—(5) E—(2)5. A—(5) B—(2)6. A—(2) B—(3) C—(4) E—(1)7. A—(2) B—(1) C—(3) E—(4)8. A—(2) B—(4) C—(3)9. A—(4) B—(5)10. A—(4) B—(2)11. A—(3) B—(1) C—(1) D—(3) E--(4)12. A—(3) B—(2) C—(4) D—(1) E--(2)13. A—(2)14. A—(1)15. A—(3) B—(4)16. A—(1)17. A—(2) B—(4) C—(3) D—(1)18. A—(3)19. A—(4)1.6.4 问答题3.答:批处理OS:目标是提高系统资源的利用效率。
系统自动地连续处理一批作业,用户不能直接干预作业执行。
没有多路性、独立性、交互性、及时性,系统要求可靠。
适合对处理结束时间要求不太严格、作业运行步骤比较规范、程序已经过考验的作业成批处理。
分时OS:目标是为了满足多个用户及时进行人-机交互的需要。
系统采用时间片轮转方式,多个用户同时在各自的终端上与系统进行交互式工作,系统对各用户请求及时响应。
有多路性(多个用户同时在各自的终端上工作)、独立性(用户感觉独占计算机)、交互性(用户能与系统进行广泛的人机对话)、及时性(系统对各用户请求及时响应),系统要求可靠。
适用于频繁交互的作业,如程序调试、软件开发等。
实时OS:目标是为了提高系统的响应时间,对随机发生的外部事件作出及时响应并对其进行处理。
系统采用“事件驱动”方式,接收到外部信号后及时处理,并且要求在严格的时限内处理完接收的事件,实时性(快速的响应时间)和高度可靠性是实时OS最重要的设计目标。
操作系统第二版第二章课后习题答案

第二章进程和线程作业答案1,2,4,6,7,10,11,12,14, 211.在操作系统中为什么要引入进程概念它与程序的差别和关系是怎样的答:由于多道程序的并发执行时共享系统资源,共同决定这些资源的状态,因此系统中各程序在执行过程中就出现了相互制约的新关系,程序的执行出现“走走停停”的新状态。
用程序这个静态概念已经不能如实反映程序并发执行过程中的这些特征。
为此,人们引入“进程(Process)”这一概念来描述程序动态执行过程的性质。
进程和程序是两个完全不同的概念。
进程与程序的主要区别:进程和程序之间存在密切的关系:进程的功能是通过程序的运行得以实现的,进程活动的主体是程序,进程不能脱离开具体程序而独立存在。
2.PCB的作用是什么它是怎样描述进程的动态性质的答:PCB是进程组成中最关键的部分。
每个进程有惟一的进程控制块;操作系统根据PCB对进程实施控制和管理,进程的动态、并发特征是利用PCB表现出来的;PCB是进程存在的唯一标志。
PCB中有表明进程状态的信息,该进程的状态包括运行态、就绪态和阻塞态,它利用状态信息来描述进程的动态性质。
4. 用如图2-26所示的进程状态转换图能够说明有关处理机的大量内容。
试回答:①什么事件引起每次显着的状态变迁②下述状态变迁因果关系能否发生为什么(A)2→1 (B)3→2 (C)4→1答:(1)就绪→运行:CPU空闲,就绪态进程被调度程序选中运行→阻塞:运行态进程因某种条件未满足而放弃CPU的占用。
阻塞→就绪:阻塞态进程所等待的事件发生了。
运行→就绪:正在运行的进程用完了本次分配给它的时间片(2)下述状态变迁(A)2→1,可以。
运行进程用完了本次分配给它的时间片,让出CPU,从就绪队列中选一个进程投入运行。
(B)3→2,不可以。
任何时候一个进程只能处于一种状态,它既然由运行态变为阻塞态,就不能再变为就绪态。
(C)4→1,可以。
某一阻塞态进程等到的事件出现了,而且此时就绪队列为空,该进程进入就绪队列后马上又被调度运行。
linux操作系统第二版课后习题答案

linux操作系统第二版课后习题答案Linux操作系统第二版课后习题答案Linux操作系统是一种开源的操作系统,广泛应用于服务器、嵌入式设备、移动设备等领域。
对于学习Linux操作系统的同学来说,课后习题是巩固知识、提高技能的重要途径。
本文将为大家提供一些关于Linux操作系统第二版课后习题的答案,希望能够对大家的学习有所帮助。
1. 什么是Linux操作系统?Linux操作系统是一种基于Unix的开源操作系统,由Linus Torvalds于1991年开发。
它具有稳定、安全、可靠的特点,并且可以在不同的硬件平台上运行。
Linux操作系统采用分层结构,包括内核、系统库、命令行工具和图形界面等组件。
2. Linux操作系统的特点有哪些?Linux操作系统具有以下特点:- 开源:Linux操作系统的源代码对所有人开放,任何人都可以查看、修改和分发。
- 多用户、多任务:Linux操作系统支持多用户同时登录,并且可以同时运行多个任务。
- 稳定性:Linux操作系统具有较高的稳定性,可以长时间运行而不会出现崩溃或死机。
- 安全性:Linux操作系统有较好的安全性,可以通过权限管理、防火墙等措施来保护系统安全。
- 可定制性:Linux操作系统可以根据用户的需求进行定制,用户可以选择安装需要的组件和应用程序。
3. 如何在Linux系统中创建用户?在Linux系统中,可以使用以下命令来创建用户:```useradd username```其中,username是要创建的用户名。
创建用户后,可以使用以下命令设置用户密码:```passwd username```然后,用户就可以使用自己的用户名和密码登录系统了。
4. 如何在Linux系统中安装软件包?在Linux系统中,可以使用包管理器来安装软件包。
不同的Linux发行版可能使用不同的包管理器,如Debian系列使用apt,Red Hat系列使用yum。
以Debian系列为例,可以使用以下命令来安装软件包:```sudo apt-get install package_name```其中,package_name是要安装的软件包的名称。
操作系统第二版课后习题答案

操作系统第二版课后习题答案操作系统第二版课后习题答案操作系统是计算机科学中的重要领域,它负责管理计算机硬件和软件资源,为用户提供良好的使用体验。
在学习操作系统的过程中,课后习题是巩固和深化知识的重要方式。
本文将为大家提供操作系统第二版课后习题的答案,帮助读者更好地理解和掌握操作系统的知识。
第一章:引论1. 操作系统的主要功能包括进程管理、内存管理、文件系统管理和设备管理。
2. 进程是指正在执行的程序的实例。
进程控制块(PCB)是操作系统用来管理进程的数据结构,包含进程的状态、程序计数器、寄存器等信息。
3. 多道程序设计是指在内存中同时存放多个程序,通过时间片轮转等调度算法,使得多个程序交替执行。
4. 异步输入输出是指程序执行期间,可以进行输入输出操作,而不需要等待输入输出完成。
第二章:进程管理1. 进程调度的目标包括提高系统吞吐量、减少响应时间、提高公平性等。
2. 进程调度算法包括先来先服务(FCFS)、最短作业优先(SJF)、优先级调度、时间片轮转等。
3. 饥饿是指某个进程长时间得不到执行的情况,可以通过调整优先级或引入抢占机制来解决。
4. 死锁是指多个进程因为争夺资源而陷入无限等待的状态,可以通过资源预分配、避免环路等方式来避免死锁。
第三章:内存管理1. 内存管理的主要任务包括内存分配、内存保护、地址转换等。
2. 连续内存分配包括固定分区分配、可变分区分配和动态分区分配。
3. 分页和分段是常见的非连续内存分配方式,分页将进程的地址空间划分为固定大小的页,分段将进程的地址空间划分为逻辑段。
4. 页面置换算法包括最佳置换算法、先进先出(FIFO)算法、最近最久未使用(LRU)算法等。
第四章:文件系统管理1. 文件是操作系统中用来存储和组织数据的逻辑单位,可以是文本文件、图像文件、音频文件等。
2. 文件系统的主要功能包括文件的创建、删除、读取、写入等操作。
3. 文件系统的组织方式包括层次目录结构、索引结构、位图结构等。
linux操作系统(第二版)课后习题答案

linux操作系统(第二版)课后习题答案Linux操作系统(第二版)课后习题答案在学习Linux操作系统的过程中,课后习题是非常重要的一部分。
通过做课后习题,我们可以更好地巩固所学的知识,加深对Linux操作系统的理解。
下面我将为大家总结一些常见的课后习题答案,希望对大家的学习有所帮助。
1. 什么是Linux操作系统?它有哪些特点?答:Linux操作系统是一种开源的Unix-like操作系统,具有多用户、多任务和多线程的特点。
它具有稳定性高、安全性好、性能优越等特点。
2. 请简要介绍Linux文件系统的组成结构。
答:Linux文件系统的组成结构包括根目录、用户目录、系统目录、设备文件、普通文件等。
其中根目录是整个文件系统的起点,用户目录是每个用户的个人目录,系统目录包括系统文件和程序文件,设备文件用于访问设备,普通文件包括文本文件、二进制文件等。
3. 请简要介绍Linux系统的启动过程。
答:Linux系统的启动过程包括硬件初始化、引导加载程序启动、内核初始化、用户空间初始化等步骤。
其中硬件初始化是指计算机硬件的自检和初始化,引导加载程序启动是指引导加载程序加载内核,内核初始化是指内核加载并初始化各种设备和服务,用户空间初始化是指启动系统的用户空间进程。
4. 请简要介绍Linux系统的文件权限管理。
答:Linux系统的文件权限管理包括文件所有者、文件所属组、文件权限等。
文件所有者是指文件的所有者,文件所属组是指文件所属的组,文件权限包括读、写、执行权限等。
5. 请简要介绍Linux系统的进程管理。
答:Linux系统的进程管理包括进程的创建、销毁、调度等。
进程的创建是指创建新的进程,进程的销毁是指销毁已有的进程,进程的调度是指对进程进行调度和管理。
通过以上课后习题的答案总结,我们可以更好地了解Linux操作系统的基本知识和常见操作。
希望大家在学习过程中多做课后习题,加深对Linux操作系统的理解,提高自己的操作技能。
操作系统(第二版)课后习题答案

故需要一次间接寻址,就可读出该数据
如果要求读入从文件首到263168Byte处的数据(包括这个数据),读岀过程:首先根据直接寻
址读出前10块;读出一次间接索引指示的索引块1块;将索引下标从0〜247对应的数据块全部 读入。即可。共读盘块数10+1+248=259块
3.某文件系统采用索引文件结构,设文件索引表的每个表目占用3Byte,存放盘块的块号,盘块 的大小为512Byte。此文件系统采用直接、一次间接、二次间接、三次间接索引所能管理的最大
(1)|100-8|+|18-8|+|27-18|+|129-27|+|110-129|+|186-110|+|78-186|+|147-78|+|41-147|+ |10-47|+|64-10|+|12-64|=728
8:00
10:00
120mi n
1
2
8:50
50min
10:00
10:50
120mi n
3
9:00
10mi n
10:50
11:00
120mi n
12
4
9:50
20mi n
11:00
11:20
90mi n
平均周转时间T=,平均带权周转时间W=
②SJF短作业优先法)
作业
到达时间
运行时间
开始时间
完成时间
周转时间
页面长度为4KB,虚地址空间共有土)个页面
3.某计算机系统提供24位虚存空间,主存空间为218Byte,采用请求分页虚拟存储管理,页面尺
寸为1KB。假定应用程序产生虚拟地址(八进制),而此页面分得的块号为100(八进制),说明
操作系统第二版课后习题答案

1.什么是操作系统其主要功能是什么操作系统是控制和管理计算机系统内各种硬件和软件资源有效组织多道程序运行的系统软件(或程序集合),是用户和计算机直接的程序接口.2.在某个计算机系统中,有一台输入机和一台打印机,现有两道程序投入运行,程序A、B 同时运行,A略早于B。
A的运行轨迹为:计算50ms、打印100ms、再计算50ms、打印100ms,结束。
B的运行轨迹为:计算50ms、输入80ms、再计算100ms,结束。
试说明:(1)两道程序运行时,CPU是否空闲等待若是,在那段时间段等待(2)程序A、B是否有等待CPU的情况若有,指出发生等待的时刻。
0 50 100 150 200 250 300⑴cpu有空闲等待,在100ms~150ms的时候.⑵ 程序A没有等待cpu,程序B发生等待的时间是180ms~200ms.1.设公共汽车上,司机和售票员的活动如下:司机的活动:启动车辆;正常行车;到站停车。
售票员的活动:关车门;售票;开车门。
在汽车不断的到站、停车、行驶过程中,用信号量和P、V操作实现这两个活动的同步关系。
semaphore s1,s2;s1=0;s2=0;cobegin司机();售票员();coendprocess 司机(){while(true)(P(s1) ;启动车辆;正常行车;到站停车;V(s2);)}process售票员()(while(true)(关车门;V(s1);隹票•口xK;P(s2);开车门;上下乘客;))2.设有三个进程P、Q、R共享一个缓冲区,该缓冲区一次只能存放一个数据,P进程负责循环地从磁带机读入数据并放入缓冲区,Q进程负责循环地从缓冲区取出P进程放入的数据进行加工处理,并把结果放入缓冲区,R进程负责循环地从缓冲区读出Q进程放入的数据并在打印机上打印。
请用信号量和P、V操作,写出能够正确执行的程序。
semaphore sp,sq,sr;int buf;sp=1;sq=0;sr=0;cobeginprocess P()(while(true)(从磁带读入数据;P(sp);Buf=data;V(sq);))process Q()(while(true)(P(sq);data=buf;力口工data;buf=data;V(sr);))process R()(while(true)(P(sr);data=buf;V(sp);打印数据;coend.3.简述计数信号量的值与资源使用情况的关系。
操作系统实用教程(第二版)-OS习题答案

操作系统实⽤教程(第⼆版)-OS习题答案操作系统习题解答1. 存储程序式计算机的主要特点是什么?答:主要特点是以顺序计算为基础,根据程序规定的顺序依次执⾏每⼀个操作,控制部件根据程序对整个计算机的活动实⾏集中过程控制,即为集中顺序过程控制。
这类计算是过程性的,实际上这种计算机是模拟⼈们的⼿⼯计算的产物。
即⾸先取原始数据,执⾏⼀个操作,将中间结果保存起来;再取⼀个数,和中间结果⼀起⼜执⾏⼀个操作,如此计算下去。
在遇到多个可能同时执⾏的分⽀时,也是先执⾏完⼀个分⽀,然后再执⾏第⼆个分⽀,直到计算完毕。
2. 批处理系统和分时系统各具有什么特点?答:批处理系统是在解决⼈⼀机⽭盾以及⾼速度的中央处理机和低速度的I/O设备这两对⽭盾的过程中发展起来的。
它的出现改善了CPU和外设的使⽤情况,其特点是实现了作业的⾃动定序、⾃动过渡,从⽽使整个计算机系统的处理能⼒得以提⾼。
在多道系统中,若采⽤了分时技术,就是分时操作系统,它是操作系统的另⼀种类型。
它⼀般采⽤时间⽚轮转的办法,使⼀台计算机同时为多个任务服务。
对⽤户都能保证⾜够快的响应时间,并提供交互会话功能。
它与批处理系统之间的主要差别在于,分时系统是⼈机交互式系统,响应时间快;⽽批处理系统是作业⾃动定序和过渡,⽆⼈机交互,周转时间长。
3. 实时系统的特点是什么?⼀个实时信息处理系统和⼀个分时系统从外表看来很相似,它们有什么本质的区别呢?答:实时系统对响应时间的要求⽐分时系统更⾼,⼀般要求响应时间为秒级、毫秒级甚⾄微秒级。
将电⼦计算机应⽤到实时领域,配置上实时监控系统,便组成各种各样的专⽤实时系统。
实时系统按其使⽤⽅式不同分为两类:实时控制系统和实时信息处理系统。
实时控制是指利⽤计算机对实时过程进⾏控制和提供监督环境。
实时信息处理系统是指利⽤计算机对实时数据进⾏处理的系统。
实时系统⼤部分是为特殊的实时任务设计的,这类任务对系统的可靠性和安全性要求很⾼。
与分时系统相⽐,实时系统没有那样强的交互会话功能,通常不允许⽤户通过实时终端设备去编写新的程序或修改已有的程序。
《Linux操作系统(第2版) )》课后习题答案

《Linux操作系统(第2版)》课后习题答案练习题一、选择题1. Linux最早是由计算机爱好者 B 开发的。
A. Richard PetersenB. Linus TorvaldsC. Rob PickD. Linux Sarwar2. 下列 C 是自由软件。
A. Windows XPB. UNIXC. LinuxD. Windows 20003. 下列 B 不是Linux的特点。
A. 多任务B. 单用户C. 设备独立性D. 开放性4. Linux的内核版本是 A 的版本。
~A. 不稳定B. 稳定的C. 第三次修订D. 第二次修订5. Linux安装过程中的硬盘分区工具是 D 。
A. PQmagicB. FDISKC. FIPSD. Disk Druid6. Linux的根分区系统类型是 C 。
A. FATl6B. FAT32C. ext4D. NTFS二、填空题1. GNU的含义是:GNU's Not UNIX。
2. Linux一般有3个主要部分:内核(kernel)、命令解释层(Shell或其他操作环境)、实用工具。
3. 安装Linux最少需要两个分区,分别是swap交换分区和/(根)分区。
4. Linux默认的系统管理员账号是root 。
;三、简答题(略)1.简述Red Hat Linux系统的特点,简述一些较为知名的Linux发行版本。
2.Linux有哪些安装方式安装Red Hat Linux系统要做哪些准备工作3.安装Red Hat Linux系统的基本磁盘分区有哪些4.Red Hat Linux系统支持的文件类型有哪些练习题一、选择题1. C 命令能用来查找在文件TESTFILE中包含四个字符的行A. grep’’TESTFILEB. grep’….’TESTFILEC. grep’^$’TESTFILED. grep’^….$’TESTFILE—2. B 命令用来显示/home及其子目录下的文件名。
linux操作系统(第二版)课后习题答案

linux操作系统(第二版)课后习题答案Linux操作系统(第二版)课后习题答案Linux操作系统是一种开源的操作系统,广泛应用于各个领域。
在学习Linux操作系统的过程中,课后习题是一个非常重要的部分,通过解答习题可以加深对知识点的理解和应用能力的提升。
本文将为大家提供一些关于Linux操作系统(第二版)课后习题的答案,希望能对大家的学习有所帮助。
一、选择题1. Linux操作系统最早由谁创建?答:Linus Torvalds2. Linux操作系统是哪种类型的操作系统?答:开源操作系统3. Linux操作系统的内核是?答:Linux内核4. Linux操作系统的特点是?答:稳定、安全、可定制性强5. Linux操作系统最早是为了什么目的而创建的?答:为了个人电脑而创建的二、判断题1. Linux操作系统只能运行在服务器上,不能用于个人电脑。
答:错误2. Linux操作系统的文件系统是大小写敏感的。
答:正确3. Linux操作系统只能使用命令行界面,不能使用图形界面。
答:错误4. Linux操作系统不支持多用户同时登录。
答:错误5. Linux操作系统没有商业公司支持,完全由志愿者维护。
答:错误三、填空题1. Linux操作系统的命令行界面称为______。
答:Shell2. Linux操作系统的默认Shell是______。
答:Bash3. Linux操作系统的配置文件一般存放在______目录下。
答:/etc4. Linux操作系统的进程管理工具是______。
答:ps5. Linux操作系统的软件包管理工具是______。
答:apt四、简答题1. 请简要介绍一下Linux操作系统的文件系统结构。
答:Linux操作系统的文件系统结构是由根目录/开始的,包括了多个目录和文件。
常见的目录包括/bin、/etc、/home、/usr等。
其中/bin存放了一些系统命令,/etc存放了系统的配置文件,/home存放了用户的主目录,/usr存放了系统的应用程序和文件。
《Linux操作系统(第2版))》课后习题答案

《 Linux 操作系统(第 2 版)》课后习题答案1.6练习题一、选择题1. Linux 最早是由计算机爱好者B开发的。
A. Richard PetersenB. Linus TorvaldsC. Rob PickD. Linux Sarwar2.下列 C 是自由软件。
A. Windows XPB. UNIXC. LinuxD. Windows 20003.下列B不是 Linux的特点。
A. 多任务B.单用户C. 设备独立性D. 开放性4.Linux 的内核版本 2.3.20 是A的版本。
A. 不稳定B. 稳定的C. 第三次修订D. 第二次修订5.Linux 安装过程中的硬盘分区工具是D。
A. PQmagicB. FDISKC. FIPSD. Disk Druid6.Linux 的根分区系统类型是 C 。
A. FATl6B. FAT32C. ext4D. NTFS二、填空题1. GNU 的含义是: GNU's Not UNIX 。
2.Linux 一般有 3 个主要部分:内核( kernel)、命令解释层( Shell 或其他操作环境)、实用工具。
3.安装 Linux 最少需要两个分区,分别是swap 交换分区和 /(根)分区。
4.Linux 默认的系统管理员账号是root。
三、简答题(略)1.简述 Red Hat Linux 系统的特点,简述一些较为知名的Linux 发行版本。
2.Linux 有哪些安装方式?安装 Red Hat Linux 系统要做哪些准备工作?3.安装 Red Hat Linux 系统的基本磁盘分区有哪些?4.Red Hat Linux 系统支持的文件类型有哪些?2.6练习题一、选择题1.C命令能用来查找在文件TESTFILE中包含四个字符的行?A. grep ’????’TESTFILEB. grep’⋯.’TESTFILEC. grep’^????$’TESTFILED. grep’^⋯ .$’TESTFILE2.B命令用来显示/home及其子目录下的文件名。
现代操作系统第二版中文版答案

MODERN OPERATING SYSTEM第一章答案1. 操作系统必须向用户提供一台扩展(即,实际上)的机器,和它必须管理I/O设备和其它系统资源。
2. 多道程序就是CPU在内存中多个进程之间迅速切换。
它一般被用来使CPU保持忙碌,当有一个或多个进程进行I/O时。
3. 输入spooling是作业中的读入技术,例如,从卡片在磁盘,这样当当前执行的进程完成时,将等候CPU。
输出spooling在打印之前首先复制打印文件,而非直接打印。
在个人计算机上的输入spooling很少,但是输出spooling非常普遍。
4. 多道程序的主要原因是当等候I/O完成时CPU有事可做。
如果没有DMA,I/O操作时CPU 被完全占有,因此,多道程序无利可图(至少在CPU利用方面)。
无论程序作多少I/O操作,CPU都是100%的忙碌。
当然,这里假定主要的延迟是数据复制时的等待。
如果I/O很慢的话,CPU可以做其它工作。
5. 第二代计算机没有必要的硬件保护操作系统免受恶意的用户程序的侵害。
6. 它依然存在。
例如,Intel以各种各样的不同的属性包括速度和能力消耗来生产Pentium I, II, III和4。
所有这些机器的体系结构都是兼容的,仅仅是价格上的不同,这些都是家族思想的本质。
7. 25 X 80字符的单色文本屏幕需要2000字节的缓冲器。
1024 X 768象素24位颜色的位图需要2359296字节。
1980年代这两种选择将分别地耗费$10和$11520。
而对于当前的价格,将少于$1/MB。
8. 选择(a),(c),(d)应该被限制在内核模式。
9. 个人的计算机系统总是交互式的,而且经常只有一个用户。
而大型机系统几乎总有许多用户强调批处理或者分时。
除了对所有资源的有效使用,大型机系统上的保护更加重要。
10. 从管道中每纳秒出现一条指令。
意味着该机器每秒执行十亿条指令。
它对于管道有多少个阶段全然不予理睬。
即使是10-阶段管道,每阶段1 nsec,也将执行对每秒十亿条指令。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
MODERN OPERATING SYSTEM第一章答案1. 操作系统必须向用户提供一台扩展(即,实际上)的机器,和它必须管理I/O设备和其它系统资源。
2. 多道程序就是CPU在内存中多个进程之间迅速切换。
它一般被用来使CPU保持忙碌,当有一个或多个进程进行I/O时。
3. 输入spooling是作业中的读入技术,例如,从卡片在磁盘,这样当当前执行的进程完成时,将等候CPU。
输出spooling在打印之前首先复制打印文件,而非直接打印。
在个人计算机上的输入spooling很少,但是输出spooling非常普遍。
4. 多道程序的主要原因是当等候I/O完成时CPU有事可做。
如果没有DMA,I/O操作时CPU 被完全占有,因此,多道程序无利可图(至少在CPU利用方面)。
无论程序作多少I/O操作,CPU都是100%的忙碌。
当然,这里假定主要的延迟是数据复制时的等待。
如果I/O很慢的话,CPU可以做其它工作。
5. 第二代计算机没有必要的硬件保护操作系统免受恶意的用户程序的侵害。
6. 它依然存在。
例如,Intel以各种各样的不同的属性包括速度和能力消耗来生产Pentium I, II, III和4。
所有这些机器的体系结构都是兼容的,仅仅是价格上的不同,这些都是家族思想的本质。
7. 25 X 80字符的单色文本屏幕需要2000字节的缓冲器。
1024 X 768象素24位颜色的位图需要2359296字节。
1980年代这两种选择将分别地耗费$10和$11520。
而对于当前的价格,将少于$1/MB。
8. 选择(a),(c),(d)应该被限制在内核模式。
9. 个人的计算机系统总是交互式的,而且经常只有一个用户。
而大型机系统几乎总有许多用户强调批处理或者分时。
除了对所有资源的有效使用,大型机系统上的保护更加重要。
10. 从管道中每纳秒出现一条指令。
意味着该机器每秒执行十亿条指令。
它对于管道有多少个阶段全然不予理睬。
即使是10-阶段管道,每阶段1 nsec,也将执行对每秒十亿条指令。
因为无论那种情况,管道末端输出的指令数都是一样的。
11. 原稿包含80 X 50 X 700 = 2800000字符。
当然,这不可能放入任何目前的CPU中,而且对于1MB的cache来说也太大了,但是如果可能的话,在寄存器中只需2.8msec,在Cache 中需要5.8msec。
整本书大约有2700个1024字节的数据块,因此从磁盘扫描大约为27秒,从磁带扫描则需2分钟7秒。
当然,这些时间仅为读取数据的时间。
处理和重写数据将增加时间。
12. 从逻辑上说,边界寄存器使用虚拟地址或者物理地址没有任何关系。
然而,前者的性能更好。
如果使用虚拟地址,虚拟地址和基址寄存器的相加,与比较可以同时开始,而且可以并行。
如果使用物理地址,相加完成之前是不能进行比较的,这就增加了存取时间。
13. 也许。
如果调用者取回控制,并且在最终发生写操作时立即重写数据,将会写入错误的数据。
然而,如果驱动程序在返回之前首先复制将数据复制到一个专用的缓冲器,那么调用者可以立即继续执行。
另一个可能性是允许调用者继续,并且在缓冲器可以再用时给它一个信号,但是这需要很高的技巧,而且容易出错。
14. 陷井由程序造成的,并且与它同步。
如果程序一而再地被运行,陷井将总在指令流中相同位置的精确发生。
而中断则是由外部事件和其时钟造成的,不具有重复性。
15. Base = 40000,Limit = 10000。
按照本书中描述的方法Limit = 50000是不正确的。
这种方法也是可以执行的,不过这样做将等待addree + Base完成后才能开始边界检查,将会使计算机速度减慢。
16. 进程表是为了存储当前被挂起、甚或是被延迟和阻塞的进程状态。
在单一进程的系统中是不需要,因为单一进程从不挂起。
17. 装配文件系统将使得装配目录中已有的任何文件都不可访问,因此装配点通常都是空的。
然而,系统管理人员可能需要将某些位于被装配目录中的非常重要的文件复制到装配点,使得他们在进行设备检查或修理时,可以在紧急事件中的普通路径上找到这些文件。
18. 如果进程表中没有空闲的槽(或者没有内存和交换空间),Fork将失败。
如果所给的文件名不存在,或者不是一个有效的可执行文件,Exec将失败。
如果将要解除链接的文件不存在,或者调用Unlink的进程没有权限,则unlink将失败。
19. 如果fd不正确,调用失败,将返回.1.。
同样,如果磁盘满,调用也失败,要求写入的字节数和实际写入的字节数可能不等。
在正确终止时,总是返回nbytes。
20. 包含字节:1,5,9,2。
21. 块特殊文件包含被编号的块,每一块都可以独立地读取或者写入。
而且可以定位于任何块,并且开始读出或写入。
这些对于字符特殊文件是不可能的。
22. 系统调用实际上并没有名称,除了在文件中这样描述之外。
当库例程read陷入内核时,它将系统调用号码放入寄存器或者堆栈中。
该号码通常用于一张表的索引。
这里确实没有使用任何名称。
而另一方面,库例程的名称是十分重要的,因为它将用于程序中。
23. 是的,尤其当系统内核是消息传递系统时。
24. 就程序逻辑而言,库例程调用哪个系统调用是没有关系的。
但是,如果需要考虑性能问题,无需系统调用就可以完成的任务将使程序运行更快。
所有的系统调用都会导致用户环境和内核环境的切换开销。
更进一步,在多用户系统中,在系统调用完成之前,操作系统可能调度到其他的进程,这将使得调用过程的处理更加迟缓。
25. 某些UNIX调用没有相应的Win32 API:Link:Win32程序不能给文件另外一个名称,或者使某个文件出现在多个目录中。
同时,试图创建链接可以便于测试,并且在文件上加锁。
Mount 和umount:Windows程序不能创建关于标准的路径的假定命名,因为具有多个磁盘驱动器的系统上路径名,其驱动器部分是不同的。
Chmod:Windows程序员不得不假定所有的用户都能访问每个文件。
Kill:Windows程序员不能kill行为失常的程序。
26. 这些都可以直接转换:(a) micro year = 106 X 365 X 24 X 3600 = 31.536 sec。
(b) 1km。
(c)有240字节,也就是1,099,511,627,776字节。
(d)它是6 X 1024公斤。
SOLUTIONS TO CHAPTER 2 PROBLEM1. 从阻塞到运行的转换是可以想象的。
假设某个进程在I/O上阻塞,而且I/O结束,如果此时CPU空闲,该进程就可以从阻塞态直接转到运行态。
而另外一种转换(从阻塞态到就绪态)是不可能的。
一个就绪进程是不可能做任何会产生阻塞的I/O或者别的什么事情。
只有运行的进程才能被阻塞。
2. 应该有一个寄存器包含当前进程表项的指针。
当I/O结束时,CPU将把当前的机器状态存入到当前进程表项中。
然后,将转到中断设备的中断向量,读取另一个过程表项的指针(服务例程)。
然后,就可以启动这个进程了。
3. 通常,高级语言不允许访问CPU硬件,而这种访问是必需的。
例如,中断处理程序可能需要禁用和启用某个特定设备的中断服务,或者处理进程堆栈区的数据。
另外,中断服务例程需要尽快地执行。
4. 内核使用单独的堆栈有若干的原因。
其中两个原因如下:首先,不希望操作系统崩溃,由于某些用户程序不允许足够的堆栈空间。
第二,如果内核将数据保留在用户空间,然后从系统调用返回,那么恶意的用户可能使用这些数据找出某些关于其它进程的信息。
5. 即使是有可能实现,也是很难保持文件系统的一致性。
假设某个客户进程给服务器进程1发送请求要更新文件。
该进程更新其内存的cache项。
然后,另一个客户进程给服务器进程2发送请求读取该文件。
不幸的是,如果该文件还在cache中,服务器进程2对此毫不知情,将返回过时的数据。
如果第一个进程在缓冲后将文件写到磁盘中,而服务器进程2每次读取时检查磁盘其缓存的备份是否是最新的,系统还可以工作,但是需要避免磁盘访问的所有缓存系统。
6. 当线程停止时,其值保留在寄存器中。
当进程停止时寄存器必须被保存。
分时线程与分时进程没有区别,因此每个线出都需要其自己的寄存器保存区。
7. 不会。
如果单线程进程在键盘上阻塞,就不能创建子进程。
8. 当工作者线程从磁盘读取Web页时,它就会被阻塞。
如果使用用户级线程,该动作将阻塞整个进程,而破坏多线程的价值。
这就是使用内核线程的原因:某些线程的阻塞不会影响到其他线程。
9. 进程中的线程是相互协作的,而不是相互对立的。
如果放弃是为了应用程序,那么线程将放弃CPU。
毕竟,通常是同一个程序员写的代码。
10. 用户级线程不能按时钟剥夺,除非整个进程的时间片用完。
内核级线程可以单独地被剥夺。
在后一种情况下,如果线程运行过久,时钟将中断该当前进程,因而当前线程也被中断。
内核可以自由地从同一个进程中选取其他线程运行。
11. 在单线程情况下,cache命中需15 msec,cache未命中需要90 msec。
其加权平均为2/3 * 15 + 1/3 * 90。
因此,平均请求为40 msec,而服务器每秒可处理25个。
对于多线程服务器,所有磁盘等待都是重叠的,因此每个请求都耗时15 msec,而服务器每秒可处理66.6666个请求。
12. 是的。
如果服务器是完全CPU绑定的,则不需要多线程。
这只会增加不必要的复杂性。
假设某个百万人口区域的电话查号系统(类似于114),如果每个(姓名, 电话号码)记录为64个字符,整个的数据库则为64MB,这就很容易全部读入服务器内存中以提供快速的查询。
13. 指针是确实必要的,因为全局变量的大小是未知的。
它可能是从字符到浮点数数组的任何类型。
如果保存其值,就不得不把其大小传递给create_global,这都没有问题,但是必须将其类型作为set_global的第二个参数,那么read_global返回值的类型是什么呢?14. runtime系统可以正好在这一时刻阻塞或者解除阻塞某个线程,并且忙于处理调度队列。
此时并不适合于时钟中断处理程序开始检查该队列是否应该进行线程切换,因为它们可能处于不一致的状态。
解决方法可以是:当进入runtime系统后,设置一个标志。
时钟处理程序将看到该标志,并且设置其自己的标志,然后返回。
当runtime系统完成时,它将检测时钟标志,看是否有时钟中断发生,并且现在运行时钟处理程序。
15. 这是可能的,不过效率很低。
线程想要做一个系统调用,首先设定警报定时器,然后才执行调用。
如果线程阻塞,定时器将控制归还给线程包。
当然,大多数调用是不阻塞的,而定时器必须被清除。
每个可能被阻塞的系统调用都必须作为3个系统调用来执行。
如果定时器过早时效,各种问题都可能发生。
