A Dual-Processor Solution for the MAC Layer of a Software Defined Radio Terminal ABSTRACT
MACDISMCUHALOFS
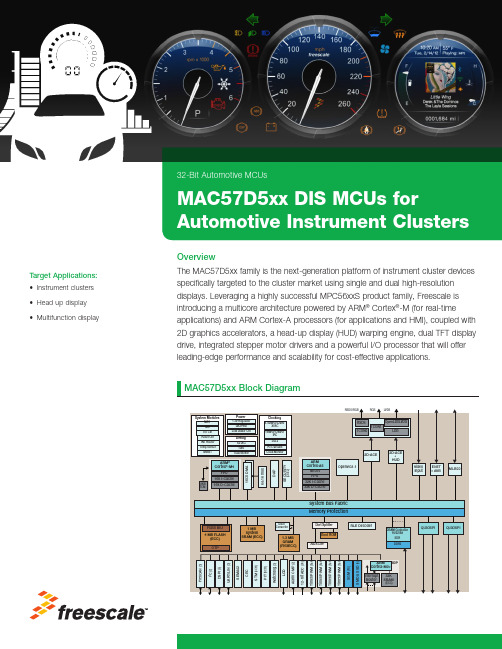
32-Bit Automotive MCUsMAC57D5xx DIS MCUs forOverviewThe MAC57D5xx family is the next-generation platform of instrument cluster devices specifically targeted to the cluster market using single and dual high-resolution displays. Leveraging a highly successful MPC56xxS product family, Freescale is introducing a multicore architecture powered by ARM ® Cortex ®-M (for real-timeapplications) and ARM Cortex-A processors (for applications and HMI), coupled with 2D graphics accelerators, a head-up display (HUD) warping engine, dual TFT display drive, integrated stepper motor drivers and a powerful I/O processor that will offer leading-edge performance and scalability for cost-effective applications.Target Applications:• Instrument clusters • Head up display • Multifunction displayFor current information about MAC57D5xx family of DIS MCUsproducts and documentation, please visit /MAC57D5xxFreescale and the Freescale logo are trademarks of Freescale Semiconductor, Inc., Reg. U.S. Pat. & Tm. Off. All other product or service names are the property of their respective owners. ARM and Cortex are registered trademarks of ARM Limited (or its subsidiaries) in the EU and/or elsewhere. All rights reserved. ©2014 Freescale Semiconductor, Inc.Document Number: MACDISMCUHALOFS REV 0This family supports up to two WVGA resolution displays, including one with in-line HUD hardware warping. Graphics content is generated using a powerful Vivante 2D graphics processing unit (GPU) supporting OpenVG1.1, and the 2D animation and composition engine (2D-ACE), which significantly reduces memory footprint for content creation. Embedded memories include up to 4 MB flash, 1 MB SRAM with ECC and up to 1.3 MB of graphics SRAM without ECC. Memory expansion is available through DDR2 and SDR DRAM interfaces while two flexible QuadSPI modules provide SDR and DDR serial flash expansion. In response to the growing desire for security and functional safety, the MAC57D5xx family integrates Freescale’s latest SHE-compliant Cryptographic Services Engine (CSE2) engine and delivers support for ISO26262 ASIL-B functional safety compliance.FeaturesCortex-A5, 32-bit CPU (Application processor)• FPU supporting double-precision floating-point operations • NEON Media Processing Engine • Memory management unit • Up to 320 MHzCortex-M4, 32-bit CPU (Vehicle processor)• 64 KB tightly-coupled memory (TCM)• Single precision FPU • Up to 160 MHzCortex-M0+, 32-bit CPU (I/O processor)• Intelligent stepper motor drive• Low-power mode peripheral managementMemory sub-system• System memory protection unit• 4 MB on-chip flash including small sectors for EEPROM emulation• 1 MB on-chip SRAM with ECC • 1.3 MB on-chip graphics SRAM with FlexECCExpandable Memory Interfaces• 2 x Dual QuadSPI serial flash controllers (including HyperFlash ™ support)• Supports SDR and DDR serial flash • DRAM controller supporting SDR and DDR2Graphics Features• Vivante GC355 GPU supporting OpenVG ™ 1.1• 2 x 2D-ACE display controllers supporting up to 2 x WVGA displays• In-line hardware HUD warping engine • Digital RGB, TCON0 (RSDS), TCON1 and OpenLDI/LVDS output options • Digital video input (VIU)• RLE decoder for memory-memory decompressionSafety and Security• Latest CSE2 security—Secure Boot, Secure Mileage & Component Protection • ISO 26262 ASIL-B Compliant MCUPeripherals:• 6 Stepper Motor Drivers with Freescale patented Stall Detection technology • Sound Generator Module (SGM) with PWM and I 2S outputs• Autonomous RTC (self calibrating)• Rich set of communication peripherals, including Ethernet-AVB, MLB50, CAN-FD, LIN, SPI, I 2C• Up to 32 Timer/PWM channels • 12-bit ADC and Analogue ComparatorsKey Electrical Characteristics• –40 °C to +105 °C (ambient)Package options• 516 MAPBGA, 208 LQFP , 176 LQFPEnablement• Software Support: AutoSAR, 2D-ACE, OpenVG, TinyUI, IOP/Stepper Motor, SGM, EthernetTools• Debugger: Green Hills, Lauterbach, IAR • Multicore compiler: ARM, Green Hills**Not all feature differences shown in table above, refer to Datasheet for specific feature details。
半导体传感器AD7324BRUZ中文规格书

The following is the list of Analog Devices, Inc. processors supported by the IAR Embedded WorkBench®develop-ment tools. For information about the IAR Embedded WorkBench product and software download, The ADSP-CM40x processors are based on the ARM Cortex®-M4 core and are designed for motor controland industrial applications.The ADSP-CM41x processors are based on the ARM Cortex-M4 and ARM Cortex-M0 cores and are de-signed for motor control and industrial applications.Product InformationProduct information can be obtained from the Analog Devices Web site and CrossCore Embedded Studio online Help system.Analog Devices Web SiteThe Analog Devices Web site, provides information about a broad range of products—ana-log integrated circuits, amplifiers, converters, and digital signal processors.To access a complete technical library for each processor family, go to:The manuals selection opens a list of current manuals related to the product as well as a link to the previ-ous revisions of the manuals. When locating your manual title, note a possible errata check mark next to the title that leads to the current correction report against the manual.Also note, is a free feature of the Analog Devices Web site that allows customization of a Web page to display only the latest information about products you are interested in. You can choose to receive weekly e-mail notifications containing updates to the Web pages that meet your interests, including documentation errata against all manuals. provides access to books, application notes, data sheets, code examples, and more. Visit to sign up. If you are a registered user, just log on. Your user name is your e-mail address. EngineerZoneEngineerZone is a technical support forum from Analog Devices. It allows you direct access to ADI technical sup-port engineers. You can search FAQs and technical information to get quick answers to your embedded processing and DSP design questions.Use EngineerZone to connect with other DSP developers who face similar design challenges. You can also use this open forum to share knowledge and collaborate with the ADI support team and your peers. Visit http:// to sign up.ADSP-BF7xx Blackfin+ Processor xxxNotation ConventionsText conventions used in this manual are identified and described as follows. Additional conventions, which apply only to specific chapters, may appear throughout this document.Example DescriptionFile > Close Titles in reference sections indicate the location of an item within the CrossCoreEmbedded Studio IDE's menu system (for example, the Close command appearson the File menu).{this | that}Alternative required items in syntax descriptions appear within curly brackets andseparated by vertical bars; read the example as this or that. One or the other isrequired.[this | that]Optional items in syntax descriptions appear within brackets and separated byvertical bars; read the example as an optional this or that.[this, …]Optional item lists in syntax descriptions appear within brackets delimited bycommas and terminated with an ellipse; read the example as an optional comma-separated list of this..SECTION Commands, directives, keywords, and feature names are in text with LetterGothic font.filename Non-keyword placeholders appear in text with italic style format.NOTE:NOTE: For correct operation, ...A note provides supplementary information on a related topic. In the online ver-sion of this book, the word NOTE: appears instead of this symbol. CAUTION:CAUTION: Incorrect device operation may result if ...CAUTION: Device damage may result if ...A caution identifies conditions or inappropriate usage of the product that couldlead to undesirable results or product damage. In the online version of this book,the word CAUTION: appears instead of this symbol.ATTENTION:ATTENTION: Injury to device users may result if ...A warning identifies conditions or inappropriate usage of the product that couldlead to conditions that are potentially hazardous for devices users. In the onlineversion of this book, the word ATTENTION: appears instead of this symbol. Register Documentation ConventionsRegister diagrams use the following conventions:•The descriptive name of the register appears at the top with the short form of the name.•If a bit has a short name, the short name appears first in the bit description, followed by the long name.•The reset value appears in binary in the individual bits and in hexadecimal to the left of the register.•Bits marked X have an unknown reset value. Consequently, the reset value of registers that contain such bits is undefined or dependent on pin values at reset.ADSP-BF7xx Blackfin+ Processor xxxiIntroduction 1 IntroductionThis Blackfin+ Processor Programming Reference provides details on the assembly language instructions used by Black-fin+ processors. The Blackfin+ architecture extends the Micro Signal Architecture (MSA) core developed jointly by Analog Devices, Inc. and Intel Corporation. This manual applies to all ADSP-BF7xx processor derivatives. All devi-ces provide an identical core architecture and instruction set. Additional architectural features are only supported by some devices and are identified in the manual as being optional features. A read-only memory-mapped register, FEATURE0, enables run-time software to query the optional features implemented in a particular derivative. Some details of the implementation may vary between derivatives. This is generally not visible to software, but system and test code may depend on very specific aspects of the memory microarchitecture. Differences and commonalities at a global level are discussed in the Memory chapter. For a full description of the system architecture beyond the Black-fin+ core, refer to the specific hardware reference manual for your derivative. This section points out some of the conventions used in this document.The Blackfin+ processor combines a dual-MAC signal processing engine, an orthogonal RISC-like microprocessor instruction set, flexible Single Instruction, Multiple Data (SIMD) capabilities, and multimedia features into a single instruction set architecture.Core ArchitectureThe Blackfin+ processor core contains two 16-bit multipliers (MACs), one 32-bit MAC, two 40-bit accumulators, one 72-bit accumulator, two 40-bit Arithmetic Logic Units (ALUs), four 8-bit video ALUs, and a 40-bit shifter, shown in the Processor Core Architecture figure. The Blackfin+ processors work on 8-, 16-, or 32-bit data from the register file.ADSP-BF7xx Blackfin+ Processor1–1。
IK Multimedia Installation and Authorization Manua

IK MultimediaInstallation and AuthorizationManualInstallation and Authorization ManualChapter 1 System RequirementsThe following are the system requirements for using your IKMultimedia product.Macintosh®- Power PC based MacintoshMinimum: 866 MHz G4 processor, 512 MB of RAM, Mac OS X 10.4or later.Suggested: dual 1.25 GHz G4 or G5 processor, 1 GB of RAM, Mac OSX 10.4 or later.- Intel based MacintoshMinimum: 1.5 GHz Intel Core Solo processor, 512 MB of RAM, MacOS X 10.4.4 or later.Suggested: 1.66 GHz Intel Core Duo processor, 1 GB of RAM, MacOS X 10.4.4 or later.Windows®Minimum: Pentium 1 GHz / Athlon XP 1.33 GHz, 512 MB of RAM,Windows XP/Vista.Suggested: Pentium 2.4 GHz / Athlon XP 1.33 GHz, 1 GB of RAM,Windows XP/Vista.2Installation and Authorization ManualChapter 2 InstallationMacintosh®NOTE: in order to be able to install and uninstall IK Multimediaproducts in your Macintosh computer (Power PC or Intel based) youmust be a user with Administrator rights.Double-click on the ‘Install’ icon and follow the onscreen instructions.The Standalone version is installed in your “Applications” folder.Documentation is placed in:Library / Documentation / IK Multimedia /UninstallDouble-click on the ‘Uninstall’ icon and follow the onscreen instruc-tions.Windows®NOTE: in order to be able to install and uninstall IK Multimediaproducts in a computer equipped with Windows Vista, you must bea user with Administrator rights.Double-click on the ‘Install’ icon and follow the onscreen instructions.The installer asks you to confirm the destination folder. In the desti-nation folder you will also find the documentation.To launch the Standalone version go to:Start menu, All ProgramsThe default destination folder is:Program Files \ IK Multimedia \UninstallIn the ‘Start’ menu, select ‘Control Panel’.Double-click ‘Add or Remove Programs’. A list of the softwareinstalled in your system is displayed.Select the IK Multimedia product you want to uninstall and click the‘Remove’ button. All the components will be removed from your sys-tem. If you added or changed files after the installation, it may bethat some files and folders are not removed. Delete them manually,from the destination folder you selected during installation.3Installation and Authorization ManualChapter 3 How the Authorization System worksYour IK Multimedia product must be authorized to work with unre-stricted functionality. It will run with full features for 10 days (graceperiod) which will start when launched for the first time, and revertto demo mode after. You will need to authorize the product withinthis time frame to enable permanent unrestricted functionality.To authorize your IK Multimedia product you’ll need three numbers:- Serial Number: this is written on the Registration Card(included with your IK boxed product, inside the license enve-lope) or the one that has been delivered to you (e.g. Onlinepurchase, such as a Digital Delivery, or update).- Digital ID: this will be shown during the authorization pro-cess and linked to the hardware where you are running thesoftware.- Authorization Code: this will be generated online by regis-tering and inserting the Serial Number and Digital ID. If youare a registered IK Multimedia user, having your User Nameand Password on hand, will help speed up the authorizationprocess.45Installation and Authorization ManualChapter 4 AuthorizationA built in software Wizard helps you in the authorization of your IK software. The first time the software is launched the Wizard is displayed (Step 1. Wizard Introduction). Click Cancel to return to the software and use the software within the 10 days grace period. Click Next to go to the Wizard’s next Step and authorize the software.The next Step (Step 2. Enter Serial Number) is for inserting the Serial Number. The Serial Number is written on the Registration Card (included with your IK boxed product, inside the license envelope) or the one that has been delivered to you (e.g. Online purchase, such as a Digital Delivery, or update). Type the Serial Number in the fields (using the TAB key to move from one field to the other). Once the Serial Number has beenStep 1. Wizard introductionStep 2. Enter Serial Number6Installation and Authorization Manualproperly inserted a green icon will display, showing that the number has been entered correctly. If a red icon is displayed the Serial Number inserted is not correct and you will be asked to re-type it in the fields. Once the Serial Number has been typed correctly, the Next button will enable you to move to the next Step of the Wizard.Now the Wizard will ask you if you are requesting an Authorization Code for the first time, or if you intend on reauthorizing your software with an Authorization Code previously received (Step 3. Authorization / Reauthorization). For a new authorization click the first option. If you choose the second option because you need to RE-AUTHORIZE your product, you’ll proceed directly to Step 7. In order to obtain the Authorization Code you’ll need to go online using an internet connection. In this window, (Step 4. Connect to Internet)Step 4. Connect to the InternetStep 3. Authorization/Reauthorization7Installation and Authorization Manual you are asked if you will connect to the internet using your current computer or a separate one. Make your choice and click on the Next button (if you connect to the internet using a different computer you’ll proceed directly to Step 6).In this page of the Wizard (Step 5. User Name and Password) you should type your IK Multimedia User Name and Password. If you have already registered any other IK Multimedia product you should use the same User Name and Password that you used previously to access the IK Multimedia User Area (where you can download updates and upgrades, requests new authorizations, manage your registration data, etc...). If you have never registered any other IK Multimedia product or if you can’t remember your previous registration informa-tion click on the second option. Once you are done click Next.Step 6a. Online registration on the same computerStep 5. User Name and Password8Installation and Authorization ManualAt this point the Wizard presents you with a window where you can find your Serial Number and the Digital ID required to register online (Step 6a. Online registration on the same computer). By clicking Register On Line, your default browser will be opened and directed to the IK Multimedia Registration Page (if the machine that you are installing on has an internet connection). Now simply fill out the mandatory fields of the Registration Page with your data. Your Serial Number and Digital ID should have been pre filled-in (otherwise COPY and PASTE them from your Wizard window to the Registration Page fields). If you would have inserted your User Name and Password, as a previously registered IK Multimedia user, the Registration Page will be pre-filled with your personal data making the authorization process faster.If you are authorizing your software from a separate computer, the Wizard will display a page (Step 6b. Online Registration on a separate computer) where you are asked to access the IK Multimedia Registration Page, online here:/IKReg.htmland register your software to obtain the Authorization Code. In this case, please carefully type your Serial Number and Digital ID in the corresponding field of the Registration Page. Be sure to fill out all the mandatory fields as well. Once your registration process has been completed, an Authorization Code will be displayed in the check out page of your IK Multimedia online registration (as well as sent to you by email). Copy the Authorization Code and click Next on the Wizard.You will now be prompted to paste the Authorization Code in the new Wizard window (Step7. Paste Authorization Code). Point the cursorStep 6b. Online Registrationon a separate computer9Installation and Authorization Manualin the first field of the Authorization Code in the Wizard and click on the Paste button. All the separated fields will be filled and a green icon will display, showing the Authorization Code has been entered correctly. If a red icon is displayed, the Serial Number inserted is not correct and you will be asked to re-type it in the fields (if you typed it manually).Once the green icon is displayed, click Next and the last page of the Wizard will appear (Step 8. Authorization Completed) listing your Serial Number, Digital ID and Authorization Code as a reference. Click Finish to start using your IK Multimedia product with unrestricted functionality.Step 7. Paste Authorization CodeStep 8. Authorization CompletedInstallation and Authorization ManualIf you have no access to the Internet, in the software CD you’ll find aPDF file called Authorization Request Form.Europe, Africa, Asia and Australia:Open the file (with Acrobat Reader), print the form, fill the requiredfields and fax everything to +39-059-2861671 to receive yourAuthorization Code within 24 hours of your fax (standard Europeanbusiness hours). Please write clearly: if we can’t decipher the codes, wewon’t be able to generate a working Authorization Code. If you don’thave access to a fax machine fill the aforementioned AuthorizationCode Request Form and mail it to the following address:IK Multimedia Production srlVia Dell’Industria 4641100 ModenaItalyNorth and South America:Open the file (with Acrobat Reader), print the form, fill therequired fields and fax everything to 954-846-9077 to receive yourAuthorization Code within 24 hours of your fax (10am-6pm EST).Please write clearly: if we can’t decipher the codes, we won’t be ableto generate a working Authorization Code. If you don’t have accessto a fax machine fill the aforementioned Authorization Code RequestForm and mail it to the following address:IK Multimedia US LLC1153 Sawgrass Corporate ParkwaySunrise, FL 33323USAYou’ll be given your Authorization Code by return mail within 15working days.For any question you may have, please refer to the FAQ at:/FAQ.phpwhere you’ll find answers to the most common questions.To submit a Technical Support Form, go to:/Support.phpTo contact US Tech Support Service by phone, please call at:(954) 846-9866For other requests such as Product, Sales, Web info or LicenseTransfer, please go to:/ContactIKForm.php1011Installation and Authorization ManualChapter 5 TroubleshootingWhere can I find my IK product Serial Number?The Serial Number is written in the Registration Card (included with your IK product, inside the license envelope). In the snap-shot, please check its exact location.For a clear characters identification, please analyze the leg-end. IMPORTANT: the number zero can easily be identified in your Serial Number because it is crossed by a line.Why is the Wizard rejecting my Serial Number?Probably because it found a typo, so please analyze the common errors:* Typing a 0 (“zero” number) instead of an O (“o” letter)* Typing 1 (“one” number) instead of an I (“i” letter)* Typing 2 (“two” number) instead of an Z (“z” letter)* Typing 5 (“five” number) instead of an S (“s” letter)* Typing 8 (“eight” number) instead of an B (“b” letter)* Typing a “.” (point) instead of a “-” (minus)1) Here you can find your SERIAL NUMBER2) At the bottom of the registration card a legend helps you identify the characters in your SERIAL NUMBER12Installation and Authorization Manual Suggestions:- When is possible, please copy and paste the information.- Cut off all the leading and trailing spaces. - Please type all codes UPPERCASE during the installation and registration process. - Check that the Serial number that you are entering is in correlation with the product installed.During the Product Registration process I received this message: The Serial Number is already registered...Remember that you are able to register your product only once. So, if you are trying to get a new Authorization Code, please read the related FAQ.Where can I find my Digital ID?The Digital ID is displayed in the Authorization window of your IK product. Why is my Digital ID being rejected during the Online Registration process?There probably is a typo on it. Remember that the Digital ID has NO letter “I” and “O”, only the numbers “1” (one) and “0” (zero). In order to prevent any further mistakes, please Copy the Digital ID from the Authorization Form to the RegistrationForm.Installation and Authorization ManualWhere can I find my Serial Number, Digital ID and the Authorization Code of a registered IK Product?In your IK product interface, locate the Authorization button and click on it. If your product version has no Authorization but-ton, you can also log in into the User Area and click on Requesta new Authorization Code. You will be able to check all the maininformation about your registered products.How can I get a new Authorization Code?Please log in into the User Area athttps:///Login/IKLogin.cgiThen, click on Request a new Authorization Code.I’ve already registered my product online, but I didn’t get an Authorization Code.Usually, this happens because the Digital ID was not submit-ted during the registration process. In order to get a new Authorization Code, please read the How can I get a new Authorization Code? FAQ.I need to log in into the User Area but I forgot my User Name and Password. What should I do?Please go to the User Area and enter your registered email address (in the proper empty box). You will receive an email with the necessary information to Log in.I have already installed, registered and authorized my IK product in my main computer. What do I have to do to use my IK product in other computers?You need to install the program and get a new Authorization Code. To learn how to get a new Authorization Code, please refer to “How can I get a new Authorization Code” paragraph in this chapter.I just bought an IK software. What should I do to register and authorize my new product?In the Support area of our website click on the Product Registration link, or click on the Tech Support Page link and click on option 1 (Register your product).13Installation and Authorization ManualIn the Serial Number field of the Product Registration Form,please insert the Serial Number written on the RegistrationCard (included with your IK boxed product, inside the licenseenvelope) or the one that has been delivered to you (e.g. Onlinepurchase, such as a Digital Delivery, or update).Complete the Registration Form and click Submit.Regarding the Authorization process, if you already typed yourDigital ID while filling the Product Registration Form, you willreceive an email from us with your Authorization Code. If not,after you launch the program the Product Authorization Wizardwill appear. Please read and follow the instructions provided ineach of the wizard’s windows and get an Authorization Code.14Installation and Authorization ManualIK Multimedia Production, Via dell’Industria 46, 41100, Modena, Italy.Phone: +39-059-285496 - Fax: +39-059-2861671IK Multimedia US LLC, 1153 Sawgrass Corporate Pkwy. Sunrise, FL 33323Phone: (954) 846-9101 - Fax: (954) 846-9077All specifications are subject to change without further notice.© 2007 IK Multimedia Production srl.Mac and the Mac logo are trademarks of Apple Computer, Inc.,registered in the U.S. and other countries.Windows Vista and the Windows logo are trademarks or registered trademarksof Microsoft Corporation in the United States and/or other countries.15P N : M N I -I K -0002。
Marketing in Practice 3

Marketing in Practice ProjectAbout apple1. Wants are the form human needs takes as they are shaped by culture and individual personality.Human needs are states of felt deprivation. They include basic physical needs for food, clothing, warmth, and safety; social needs for belonging and affection;and individual needs for knowledge and safe-expression.So ipad as a product in order to fulfill the customers’ wants, having a lot of functions:IPad 2 mobility.Apple has been very focused on iPad 2 mobility. iPad2 are thinner than the old version is about 33%, but also much lighter than the old version of the iPad, although these differences is not obvious, but enough to help Apple sell more of these products. Tablet PC with the mobility, is able to carry the equipment around lightly, more lightly if the device smaller, of course, the better, Apple seems to understand this and respect the iPad 2 under the foot work, as all this functions show ipad2 features.The entertainment factorAt today's event, Apple spent a long time to introduce iPad 2 focus on entertainment features included. One major feature is that today's iPad 2 Tablet PC to support HDMI (high-definition output line) output function, which can output the user some video content to other devices on a higher resolution, such as TV sets. In addition, iPad 2 of the new operating system also has the AirPlay iOS 4.3 feature that allows users to enter the built-in slide show function. In addition, iPad 2 will also have iMovie and Garage Band functions, which they can help users edit video and audio content, so we will easily see, iPad 2 is already higher than the old version has been greatly improved.The battery lifeIf the Tablet PC's battery life will soon be consumed dry, then this is certainly not a good thing. The longer battery life, the Tablet PC will more attractive. Apple's well known that, according to Apple's side said the new iPad 2 tablet computer battery can achieve 10 hours duration, while the standby time to about a month or even longer. All in all, iPad 2 will be an effective platform, consumers will be happy to hear this news.Built-in 3G capabilities can be connected to the network AT & T and VerizonIPad first one of the main problem is that it only allows users to connect AT & T's wireless network, if users want to connect to Verizon's network, it may still need to install additional products, such as MiFi 2200 Hotspot and so on. But the good news is that the new iPad 2 has been able to allow users to connect this product to AT & T's 3G network or Verizon's 3G networks is not need to install other add-on products, which may also be a lot of consumers’ wants iPad 2.2. Describe the segment of market for iPad in China.Through market segmentation, companies divide large, heterogeneous markets into smaller segments that can be reached more efficiently and effectively with products and services that match their unique needs. So the segments of ipad in china are as follows:● Segmenting consumer markets in china● Segmenting business markets in chinaBusiness markets also use some additional variables, such as customer characteristics purchasing approaches, situational factors, and personal characteristics. And ipads’ business markets are as follows:a) Corporations,For large corporate customers, the company offers a lot services, which including travel management services, and so on.b) Small business customers Income(amonth)RMBPsychographics User rates Students’ iPad Under$2000 Fashion seek for myselfLighter userBusiness’ iPad$2000~$4000 ambition Medium user Loyal’ iPad $4000 and over authoritarian Heavy userFor small business customers, the company offers many services, which including special usage rewards, and so on3. Marketing intermediaries help the company to promote, sell, and distributeits products to final buyers; they include resellers, physical distribution firms, marketing services agencies, and financial intermediaries.●Resellers are distribution firms help the company to stock and move goodsfrom their points of origin to their destinations.●Physical distribution firms help the company to stock and move goods fromtheir points of origins to their destinations.●Marketing services agencies are the marketing research firms, advertisingagencies, media firms, and marketing consulting firms that help the company target and promote its products to the right markets.●Financial intermediaries include banks, credits companies, insurancecompanies, and other businesses that help finance transactions or insure against the risks associated with the buying and selling of goods.(b) A product’s position is the way the product is defined by consumers onimportant attributes-the place the product occupies in consumers’minds relatives to competing products.The low price strategy of IPad1400UnitPrice 1000(Dollars)600200PerformanceOrientationImac ipod touch ipod classic iphoneiPad4. Demographic is the study of human population in terms of size, density,location, age, gender, race, occupation, and other statistics. TheDemographic environment is of major interest to marketers because itinvolves people, and people make up markets.Population environment,which including population growth, population age structure, ethnic composition, educational level, family structure anddemographic migration. The case from iPad can be seen that the greatest impact on ipad’s marketing is the age composition of the population and the education level of population.●From the population age structure, Apple is taking the product innovationand its products to high performance, elegant design of the main. This is the object of many young people to follow, young people like innovation, like the good-looking designs. Ipad’s product innova tion, fashionmarketing strategy precisely fit the shape of a young consumerpsychology. The elderly are less demanding for the appearance andperformance requirements for the computer is not high. Therefore, ipad marketing in China mainly targeted at young people.●Also from the level of education, the major consumer groups of ipad arethe above white-collar workers or college students. Especially the senior staffs of the computer’s requirements are relatively high. They not only require a computer's performance, but also for the appearance ofcomputers and match their status with the company. Ipad marketingstrategy is that high-end line. While Apple's market share of Chinesestudents is not high, but most students are quite popular on the ipad. This part of the college students are ipad potential consumers, so this part of the market is needed for ipad.5. The technological environment is perhaps the most dramatic force nowshaping our destiny. Technology has released such wonders asantibiotics, robotic surgery, miniaturized electronics, laptop computer,and the internet. So the there are some technological environmentfactors that affect the Product development of iPad as follows:●The Mac OS systems are proprietary systems, under normalcircumstances can not be installed on a normal PC operating system.Apple MAC not only produced most of the hardware, even the MACoperating systems are used in the development of its own. Mac'soperating system is Mac OS X, the UNIX-based core system enhances the system stability, performance and responsiveness. It through the full symmetric multi-processing advantages of a dual-processor, providing unparalleled 2D, 3D and multimedia graphics performance and a wide range of font support and integration of PDA (personal digital processing) functions.●This technology is now Apple has a strong advantage. The current use ofordinary PC, mostly developed by Microsoft WINDOWS or LINUXoperating system, WINDOWS has a strong compatibility, LINUX humane of the graphical interface, and Mac OS operating system, both theadvantages of both, such as compatibility with standard and aesthetic user interface, which makes Apple's Mac OS systems in the currenttechnological environment is unique, has a strong competitive edge.●Apple computer technology the higher gold content, and rapidtechnological innovation. However, the technology surroundingenvironment is constantly changing, these changes include accelerating changes in technology, opportunities for technological change, increased investment in research and development of regulations and technicalinnovations continue to increase. For example, the April 19, LenovoGroup announced yesterday that its business area from a traditional PC to the mobile Internet development. This is the largest in recent years, Lenovo Group, a business transformation, founder of Lenovo, Lenovo chairman Liu at an unprecedented high-profile propaganda, said,"Lenovo will be desperate to put to stop the mobile Internet market,"Financial News for NetEase The title of the "determination and Lenovo Mobile Internet transition, Apple Last Stand", it is clear competitionLenovo and Apple market share, while Lenovo's mobile Internet strategy is still faced with many challenges, but Apple will undoubtedly adversely affect the market.●Because economic development is bound to promote technologicalprogress, technology innovation, made computer technology ininnovation, as the domestic computer products and technology, Apple Computer technology in China will gradually lose the advantage, ofcourse, it takes a long period of time, but in the long run, the domestic computer products, technical progress is an inevitable trend, which will certainly have future sales of Apple computers in China have animportant impact.6. (a) Using an Undifferentiated Marketing strategy, a firm might decide to ignore market segment differences and target the whole market with one offer. The Undifferentiated Marketing strategy focuses on what is in common in the needs of consumers rather than on what is different. The company designs a product and a marketing program that will appeal to the largest number of buyers. And the advantages and disadvantages of ipad use an Undifferentiated Marketing strategy.Ipad use an Undifferentiated Marketing strategy.●Undifferentiated Marketing strategy advantages is its low cost. Ipad’sSingle product line can produce the relative scale efficiency, storage and transport are also relatively convenient, advertising, logistics and other resources are concentrated in a product, it will help strengthen brand image.●Also, Undifferentiated Marketing strategy has its own shortcomings anddeficiencies, it can not meet the diverse needs of consumers, there aredifferences in some areas, no difference in the implementation of marketing, but companies ignore the objective is the existence of such differences can easily cause competitors find a breakthrough point, lose some customers. Therefore, an enterprise through a brand of a product to meet the diverse needs of consumers, it is almost impossible. Therefore, the enterprise was no difference in the choice of development strategy as the time to study its adaptability. In general, steel, cement and other businesses are more suited to this strategy.(b) Using a differentiated Marketing strategy, a firm might decide to targetseveral market segment and designs separate offers for each. and theadvantages and disadvantages of ipad use an differentiated Marketing strategy.●When ipad use an differentiated Marketing strategy, the advantages areas follows:Customers can better meet different needs, but also so that eachsub-markets to maximize the sales potential of the excavation, which will help to expand their market share. But also greatly reduce the operational risks; the failure of a sub-market will not cause trouble throughout the enterprise. Differentiated marketing strategy has greatly enhanced the competitiveness of enterprises, ipad set up several brands, companies can greatly increase consumer trust in products and purchase rates. A variety of advertising and multi-channel distribution, a variety of market research costs, management fees, are limited barriers to entry of small businesses, so, for the strong financial resources, robust technology, with high-quality products business, the difference of marketing is a good choice.●When ipad use an differentiated Marketing strategy,the disadvantagesare as follows:Meanwhile, there are differences of their own limitations, the biggest drawback is the high cost of marketing, and production is generally small quantities, so that the relative increase in the cost per unit of product, non-economic. In addition, market research, sales analysis, marketing plans, channel establishment, advertising, and many other aspects of logistics and distribution costs will no doubt increase substantially. This is why many companies do marketing differentiation, market share expansion, and sales increased, profits decreased the reason.(c)Concentrated MarketingUsing a concentrated Marketing strategy, instead of going after a small share of a large market, the firm goes after a large share of one or a few smaller segments or niches.●The advantages of ipad use a concentrated Marketing strategy. first theipad can achieves a strong market position because of its greaterknowledge of consumers needs in the niches it serves and the special reputation it requires. Second it can market more effectively byfine-tuning its products, prices, and program to the needs of carefullydefined segments. Third it can also market more efficiently, targeting its products or services, channels, and communication programs towardonly consumers that it can serve best and most profitably.●The disadvantages of iPad use a concentrated Marketing strategy. firstowing to the segments are fairly large and normally attract severalcompetitors, niches are smaller and may attract only or a fewcompetitors. Many companies start as nicher that may be unimportant to or overlooked by larger competitors. So iPad will have a lot of potential competitors.7. Describe some of the actions taken by Apple to build a brand for the Company’s product in the following areas:(a) Brand positioningMarketers need to position their brands clearly in target cu stomers’ minds. They can position brands at any of three levels. At the lowest level, they can position the brand on products’ attributes. And a brand can be better Positioned by associating its name with a desirable benefit. And the strongest brands go beyond attribute or benefit positioning; they are positioned on strong beliefs and values.、个性、与众不同、创新电脑产品有很多,它们是同质化的商品,但苹果不是,它的个性风格太强烈了,一眼就能识别,品牌忠诚度很高。
科技英语 主编 田文杰 课文翻译

Unit 1Artificial intelligence is the science and engineering of making intelligent machines,especially intelligent computer programs.人工智能是制造智能机器的科学与工程,特别是智能化的计算机程序。
It is related to the similar task of using computers to understand human intelligence,but AI does not have to confine itself to methods that are biologically observable.这与使用计算机来理解人类智能的类似任务有关,但是人工智能不需要把它局限在生物可观察的方法上。
In this unit,the two passages present a general picture of AI research .在这个单元,两个章节提出了人工智能研究的概况。
Text A briefly introduces the definition of AI,some kinds of architectures of AI system,essential capabilities to AI programs and so on.文章A简要介绍了人工智能的定义,人工智能的系统的几种体系结构、基本功能以及程序等等。
Text B explains a particular area of AI research--natural language processing including its definition and a legendary Turing’s Test.文章A解释特定地区研究人工智能的自然语言处理包括定义和传说中的图灵测试。
MIC5332中文资料
MIC5332
Micro-Power High Performance Dual 300mA ULDO™
General Description
The MIC5332 is a tiny dual low quiescent current LDO ideal for applications that are power sensitive. The MIC5332 integrates two high performance 300mA LDOs, and a POR generator into a 2mm x 2mm Thin MLF® package. This solution occupies the same PC board area of a single SOT-23 package.
Micrel Inc. • 2180 Fortune Drive • San Jose, CA 95131 • USA • tel +1 (408) 944-0800 • fax + 1 (408) 474-1000 •
January 2007
M9999-011608-A
Pin Configuration
VIN 1 GND 2 POR2 3 EN2 4
8 VOUT1 7 VOUT2 6 CSET2 5 EN1
8-Pin 2mm x 2mm Thin MLF® (MT) (Top View)
Pin Description
Pin Number 1 2 3
4
5
6
7 8
Pin Name VIN GND
Regulator Output – LDO2.
Regulator Output – LDO1.
DS-A82系列混合SAN产品介绍说明书

FeaturesReliable System●Modular and no-cable design.●Dual controller.●Real-time cache.●Optional BBU (Backup Battery Unit).High-Performance and Extendable Hardware Platform ●64-bit multi-core processor.●PCI-E 2.0 bus.●Four 1000M Ethernet interfaces per controller.●SAS interface for storage enclosure.●High-density chassis. 4U chassis: 24 HDDs.HDD Detection and Repair/RAID Optimization●Detection before operation.●Detection in operation.●Fault repair.●RAID 0, 1, 3, 5, 6, 10, 50.●Global and local hot spare.●Quick RAID building.●Capability of cascading up to two storage enclosuresbehind a single SAS port.Advanced Data Protection●Synchronous backup of key information in system diskand HDD.●RAID-based tamper-proof data technology.●Auto data synchronization between devices.Energy Efficient●CPU load balance.●Auto fan tuning.User-Friendly UI●Quick configuration.●Various alarm management.●SADP protocol supported.●SNMP supported.Surveillance-Specialized Stream Media Direct Storage (Direct Streaming Mode)●Space pre-allocation strategy.●Direct storage for video stream and picture stream.●Supports direct IP camera/DVR/NVR streaming andrecording.●Supports camera access through RTSP, ONVIF, and PSIAprotocol.●Supports alarm/scheduled/manual recording.●N+1 technology.●Automatic network replenishment (ANR), timelyuploading, and video loss alarm.●Lock key videos.●Supports both Direct Streaming Mode and IPSAN Mode.●Search, play, and download videos by video type or videotime.IntroductionThe DS-A82 series is a dual controller-structure Hybrid SAN(Storage Area Network). Hikvision Hybrid SAN product creates a network with access to data storage servers, and it integrates Hikvision’s unique video direct streaming technology as well as supports IPSAN/FCSAN. This flexible, cost-effective solution features ONVIF-support tothird-party cameras, support for RTSP, and SIP protocols, and extended data retention. With no recording server needed, Hikvision’s Hybrid SAN systems truly make applications simple, flexible, and budget-friendlySpecificationModel DS-A82024DPerformance Direct Streaming mode:video (2 Mbps) + picture448-ch (recording + playback) IPSAN256-ch (recording + playback)Controller Controller Dual controllerProcessor64-bit multi-core processorCache per controller8 GB (extendable to 32 GB)/controllerHDD HDD slot24Interface/capacity SSD (optional), SAS/1TB, 2TB, 3TB, 4TB, 6TB,8TB,10TB,12TB,14TB,16TB Hot-swapping SupportedHDD support S ingle, RAID(Enterprise Hard Disk)RAID RAID0, 1, 3, 5, 6, 10, 50, JBOD, Hot-SpareNetwork Protocol iSCSI, RTSP, ONVIF, PSIAInterfaces Data network interfaceper controller4, 1000M Ethernet interface (4 × GbE or 2 × 10GbE is extendable)Management networkinterface1, 1000M Ethernet interface/ControllerMiniSAS interface SupportedVGA per controller1USB per controller3General Power supply RedundantConsumption (withHDDs)●Working: ≤ 507 W (1729 BTU with 24 HDDs);●Rated: ≤ 800 WEnvironmenttemperature●Working: +5 °C to +35 °C (41 °F to 95 °F)●Storing: -20 °C to +70 °C (-4 °F to 158 °F) Environment humidity●Working: 20% to 80%RH (non-condensing/frozen);●Storing: 5% to 90%RH (non-condensing/frozen) Chassis19-inch 4UDimensions (W × H × D)447 x 172 x 550 mm (17.6 x 6.8 x 21.7 in)Weight (without HDDs)≤ 33.5 Kg (73.9 lb)Typical ApplicationAvailable ModelsDS-A82024D000204170207。
AADvance培训手册中文版

AADvance培训⼿册中⽂版系统培训⼿册操作系统构建配置编程排除故障维护AADvance可编程控制器指南1.5版本2012年5⽉2AADvance System Training Manual, version 1.5注意The content of this document is confidential to ICS Triplex and their partners. This document contains proprietary information that is protected by copyright. All rights are reserved. No part of this documentation may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying and recording, for any purpose, without the express written permission of ICS Triplex.该⽂件内容对于ICS Triplex和他们的合作⽅均是机密的。
本⽂档包含有受版权保护的专有信息,公司保留其所有权。
没有ICS Triplex明确的书⾯许可,本⽂档的任何部分都不允许以任何电⼦或机械的形式或⽅式被复制和传播,包括复印和记录。
The information contained in this document is subject to change without notice. The reader should, in all cases, consult ICS Triplex to determine whether any such changes have been made.本⽂档所包含信息可以随时更改,不另⾏通知。
2021对外经济贸易大学MTI真题+答案

超详细!2021对外经济贸易大学MTI真题+答案211翻译硕士英语一、单选20题近义词辨析untacheduntachable unequal unequable固定搭配poverty alleviation(脱贫)depreciationvolatile “v”开头的很多词意辨析consultancy和 redundancy 区别很多题都是,一道题两个空,一般只清楚一个空,另一个空单词不认识,很难选二、文体改错10题comma price, run on, fragment 比较多,也有correct,choppy比较少,没有stringy三、阅读,2篇常规阅读,1篇5选5,1篇判断正误第一篇2017年12月六级真(第一套),判断正误Our world now moves so fast that we seldom stop tosee just how far we have come in just a few years. The latest iPhone 6s, forexample, has a dual-core processor and fits nicely into your pocket. comparison,you would expect to find a technological specification like this on yourstandard laptop in an office anywhere in the world.It's no wonder that new applications for theInternet of Things are moving ahead fast when almost every new device we buy hasa plug on the end of it or a wireless connection to the internet. Soon, our currentsmartphone lifestyle will expand to create our own smart home lifestyle too.All researches agree that close to 25 billiondevices, things and sensors will be connected 2020 which incidentally isalso the moment that Millennials (千禧一代) are expected to make up 75 percent of our overallworkforce, and the fully connected home will become a reality for large numbersof people worldwide.However, this is just the tip of the proverbialiceberg as smart buildings and even cities increasingly become the norm asleaders and business owners begin to wake up to the massive savings thattechnology can deliver through connected sensors and new forms of automationcoupled with intelligent energy and facilities management.Online security cameras, intelligent lighting and awealth of sensors that control both temperature and air quality are offering anunprecedented level of control, efficiency, and improvements to what were onceclassed necessary costs when running a business or managing a large building.We can expect that the ever-growing list ofdevices, systems and environments remain connected, always online and talkingto each other. The big benefit will not only be in the housing of this enormousand rapidly growing amount of data, but will also be in the ability torun realtime data analytics to extract actionable and ongoing knowledge.The biggest and most exciting challenge of thistechnology is how to creatively leverage this ever-growing amount of data todeliver cost savings, improvements and tangible benefits to both businesses andcitizens of these smart cities.The good news is that most of this technology isalready invented. Let's face it, it wasn't too long ago that the idea ofworking from anywhere and at anytime was some form of a distant Utopian (乌托邦式的) dream, and yet now we can perform almost anyoffice-based task from any location in the world as long as we have access tothe internet.It's time to wake up to the fact that making smartbuildings, cities and homes will dramatically improve our quality of life inthe years ahead.第二篇,选自2019年5月一篇经济学人文章Sleepless in Silicon ValleyWhy the techie obsession with sleep technologymakes perfect senseFirst, close the blackout blinds in your bedroom.Eat dinner at 4pm, and do not eat or drink anything after 6pm. Put on yourblue-light blocking glasses at 8pm. Set your bedroom temperature to 67oF{19.4C) and your electric blanket to 69.8oF {21 C). At 8.45pm, meditate forfive to ten minutes. Switch on your deep- wave sound machine. Put on yourQurasleep tracking ring. You are now, finally, ready for slumber. This may allsound a bit over the top. But this is the "sleep hygiene" routinedescribed in a recent blog post Bryan Johnson, who sold his previous companyto eBay for $800m and is now chief executive of Kernel, a startup developingbrain-computer interfaces. He admits that his sleep routine has "decimatedmy social life”, and that his partner sleeps in a different room, but says allthis troubleis worth it, because it has boosted his level of "deepsleep" as much as 157%. He has bought Oura rings for all his employees.Mr Johnson does not expect other people to copy hisroutine, but made it public to encourage the sharing of sleep habits and tips.Like many other techies, he regards sleep hygiene as an effective way tomaintain mental health, boost cognition and enhance productivity. In its mostrecent funding round, backers of Oura, the Finnish maker of the high-tech ring,included the co- founders of YouTube and Twitch, along with alumni ofFacebook,Skype and . The ring's most famous user is Jack Dorsey, the boss ofTwitter, whose unusual wellness regime-which also incorporates near-infraredsaunas, radiation blocking Faraday tents, fasting and cryotherapy- prompted theNew York Times this month to dub him “Gwyneth Paltrow for Silicon Valley”. Fortech tycoons, it seems, sleep is the new fitness.Those who want to monitor and improve their sleephaveno shortage of gadgets to choose from. As well as electric blankets andmattress- chillers, sound machines and "decimated my social life” smartrings, there are also smart pillows, sleep-tracking watches and bracelets,intelligentsleep masks, brain-stimulating headbands, bedside sleep sensors andcountless sleep- monitoring apps. The market for sleep technology was worth$58bn in 2014 and is expected to grow to $81bn 2020, according toPersistence, a market-research firm. Big companies in the field includehousehold names such as Apple, Bose, Nokia and Philips. After Mr Dorsey'senthusiastic endorsement, the Oura rings are back- ordered four to sixweeks.The mania for sleep technology makes perfect sensefor the tech industry, combining as it does several existing trends. For astart, it fits with the industry's metrics -driven worldview. Techies obsessabout OKRs {objectives and key results), KPIs {key performance indicators) anddigital-analytics dashboards showing the performance of specific products andfeatures. Applying similar techniques to sleep and other aspects of theirpersonal lives, an approach known as the "quantified self" seems alogical step. As those in the startup world like to say, channeling Peter Drucker,a management guru, "what's measured improves."Sleep- tracking also aligns neatly with Silicon Valley'scult of productivity, and the constant search for "life hacks" thatwill make entrepreneurs more effective, efficient and successful. This ranges fromwearing the same clothes every day, Steve Jobs-style (thus avoiding wastingtime deciding what to put on), to fastidious fitness routines and complicateddiets. Elaborate sleep regimes slot right in, because they promise clarity ofthought and improved cognitive performance. They also let people extend theirquantified· self and life- -hacking efforts into the one part of the day that waspreviously untouched: shut-eye.Relentlessly pursuing productivity only whileyou are awake is for wimps. Sleep -tracking means you can do it round theclock. Oura describes its sensor packed ring as a "secret weapon forpersonal improvement"- -another way to get ahead.1.下列说法符合文章标题的是?A how to?B how to achieve self-improvementC how to monitor your sleepingD seeping hyhegnie and technology that can improveefciency2.What dose "Iife hacks "mean?A life tipsB?C?D privacy monitoring3. What does the sentence mean "decimated m ysocial life”4. What does the sentence mean "the Oura ringsare back- ordered four to six weeks."?5.搞科技的为啥喜欢这个?选项为D.以上全部第三篇: Cosco CiscoIntel 这些公司预见未来,制定未来发展计划的情况,哪些公司可以紧跟时代潮流。
双核处理器(DualCoreProcessor)

双核处理器(Dual Core Processor)Dual core processor directory [hidden]brief introductionconceptSignificanceDual core and dual coreDeveloping trend[edit this paragraph] IntroductionDual Core Processor (dual core processor) refers to the integration of two computing cores on a single processor, thereby improving computing power. The concept of "dual core" was first proposed by IBM, HP, Sun and other high-end server vendors supporting RISC architecture. However, due to the high price and narrow application range of RISC architecture, it has not attracted extensive attention. In short, the dual core processor is based on a single semiconductor processor with two cores of the same function. In other words, integrate two physical processor cores into a single kernel. Chip manufacturers have also been looking for ways to improve performance without increasing the actual hardware coverage. Multicore processor solutions provide better performance for these requirements without increasing energy or physical space.[edit this paragraph] conceptThe concept of "dual core", which is gradually warming up recently, mainly refers to the dual core technology based on X86 open architecture. In this regard, the leading manufacturers are mainly Intel and AMD two. Among them, the two ideas are different. AMD was designed from the very beginning to take into account multi-core support. All components are directly connected to the CPU, eliminating the challenges and bottlenecks in the system architecture. The two processor cores are connected directly to the same kernel, and the communication between the cores at chip speed further reduces the latency between processors. Intel uses multiple cores to share the front end bus. Experts believe that the architecture of AMD makes it easier to implement dual core to multi-core, and the Intel architecture will encounter multiple kernel bottlenecks that contend for bus resources. Dual core processor technology is an effective way to improve processor performance. Because the processor's actual performance is the total number of processor instructions that a processor can perform during each clock cycle, a kernel is added, doubling the number of units executable per clock cycle. Here we have to emphasize the point is, if you want the system to achieve maximum performance, you must make full use of all two kernel execution units: all the execution units have a job! Why IBM, SUN, HP and other manufacturers of core products can not achieve universal access, because they are very expensive that has never been widely used. For example, the dual core IBM Power4 processor with 128MB L3 cache size is 115x115mm, and the production cost is quite high. Therefore, we cannot call dual core processors such as IBM, Power4, and HP PA8800 the predecessor of AMD's upcoming dualcore processor. At present, the application environment of X86 dual core processor has been quite mature, most operating system already supports parallel processing, most of the new or upcoming application software for parallel technology provides support, so the processor once listed, system performance will be able to rapidly enhance. As a result, the entire software market has been fully prepared for multi-core processor architectures.[edit this paragraph] significanceThe x86 multicore processor marks a major leap in computing technology. This important progress took place,It is time for businesses and consumers to face the growing trend of digital data and the globalization of the Internet and demand more convenience and advantages from the processor. Multicore processors, which are superior to the current single core processor in performance and productivity, will eventually become a widely distributed computing paradigm. Multi core processors will also be a key role in promoting the security of PC and virtual technology, protection and development of virtual technology can provide better and higher resource utilization and more substantial business computing market value. Ordinary consumers will also have more ways to achieve higher performance than ever before, thereby increasing their use in home PC and digital media computing systems. The creation of two or more powerful computing cores on a single processor opens up a whole new world of possibilities. Multi core processor can overcome processor design challenges today's technology -- an immediate economicand effective decrease with the single core processor frequency (i.e. "clock speed") rising and increased the heat and power consumption. Multicore processors help to provide superior performance for more advanced software in the future. Existing operating systems (such as MS, Windows, Linux, and Solaris) can benefit from multi-core processors. In the future, when market demand is further improved, multi-core processors can provide an ideal platform for reasonably improving performance. As a result, the next generation of software applications will be developed using multicore processors. No matter whether these applications can help the professional animation production company faster and more economical to produce more realistic movies, or to create a breakthrough way to produce more natural more inspired PC, practical use of multi-core processor hardware which will forever change the computing world. While dual core or even multicore chips have the opportunity to become one of the most important improvements in processor development history. It should be pointed out that one of the biggest challenges for dual core processors is the limit of processor energy consumption, performance enhancements, and energy consumption, however, cannot be increased. According to the famous soup hardware website documents show that the code Smithfield CPU thermal design power consumption of up to 130 watts, 13% higher than the current Prescott processor. As a result of today's energy consumption has been in a very high level, we need to avoid the CPU as a "small nuclear power plant, so energy consumption problem of the dual core or multi-core processor will be one of the important problems of AMD test and Intel. On multi-core processors, from a global perspective, AMD in the understanding of customers and to output the products that meet the needs of customers of the idea of walking in frontof Intel, from the last century since 90s has been planned with the significant progress, it first announced the placement in a single processor core.[Edit] dual core and dual coreDual core and dual core (Dual Core Dual CPU Vs.) are the physical construction differences between AMD and Intel in dual core processors. AMD two kernel in a Die (wafer), connected by direct architecture, a higher degree of integration. Intel is on a different Die (wafer) on the two kernel package together, so people will have Intel program called "double core",Think AMD's plan is the real "dual core."". From the user's point of view, the AMD scheme can make the pin, dual core CPU power consumption single core CPU, from a single core upgrade to a dual core, does not need to replace the power supply, cooling system and the motherboard chipset, and only need to refresh the BIOS software. This for the motherboard manufacturers, computer manufacturers and end the user's investment protection is very favorable. Customers can use their existing 90 nanometer infrastructure to migrate to a dual core system via BIOS changes. Single core and double core version of the computer manufacturers can easily provide the same hardware, so that customers who want to improve the performance and to maintain the environmental stability of IT can be upgraded to dual core without interruption to business conditions. In a high rack density environment, the system performance of the customer will be greatly improved by porting to dual core while maintaining power and infrastructure investments unchanged. With the same system footprint,customers will achieve higher levels of computing power and performance through the use of dual core processors.[edit this paragraph] trends2006 is destined to be CPU market front smoke four years, can also be said to be milestone year. AMD in the middle of the year to rise up, threw out the AM2 platform, and quickly replaced with the previous generation of products. As the processor giant Intel nature is not covered, two months later, Conroe this bomb down hard on the market, "to improve the performance of 40%, reducing the power consumption of 40% it is exciting", also hit the AMD out of the way, so he again use price strategy to protect the market. When all the people think that Intel will concentrate in the market after the release of the Conroe business, the popularity of the dual core platform, and relax on the development of new products on the occasion, Intel came again explosion news, November 12th, Intel will launch a new four core processor Kentsfield. From the core to the quad core, Intel only less than half a year, and even such a great leap forward, this is indeed very surprising. The distance Intel officially on sale there for a short time four core processor, but the Intel IDF in September has officially released the code for the four core processor Kentsfield, and the recent major media have got the product evaluation. And AMD, according to its Roadmap display, AMD four core architecture of the K8L processor will be available in 07 years, so that Intel's four core will be fully ahead of AMD three quarters.。
翻译

pixel Patterns Euler perimeter (equivalent interac t alternative Syntax capabilities民主democracy 科学science Approach motor diagnosis applications确no-stationary 不了harmonic by means of FFT aturation or control interaction broken bars and shorted stator turns using winding operation o到induction motor 解voltage component.C axial flux and d-q current and voltage component. majority of them based on destructive effect Stator winding faults functions (IMF) of the signal being analyzed; thus, it is notfunctions (IMF) of the signal being analyzed; thus, it is notphase-to-phase phase-to-ground phase否Armature faults tolerant in the presence of any single point I. INTRODUCTION intrinsic mode functions Index Terms Decompositiondemonstrateanalysis V alidate表明instantaneous frequencies 成本a collection of intrinsic mode functions analyzedStator conditionsanalyzes studypresents paper Abstract Wigner Ville DistributionDecompositionDetectionPermanent Magnet Synchronous MotorWignerDecomposition Ville Distribution failures in synchronous machines. demonstrateExperimental laboratory results validate instantaneous frequencies resulting Hilbert–Huang transform collection intrinsic mode Stator Current simulationmeans of speed transients circuit include either saturation or control interactions. From yearsfailures for Permanent Magnet Synchronous Motor analyzes Wigner Ville Distribution means oEmpirical Mode Decomposition Short Circuit Fault Short Circuit itCircuit Fault Detection in PMSMC Sequencer axial flux and d-q current and voltage component. Inter-integrated circuit moduleperipheralIntegrated Emulation synchronous serial I/OversionPlus Segregates Peripheral Framessegregatesdecoupled from increasing CPU clock speeds timing of peripheralsis fed into VBvalidfree running up counter maskedinterrupt linesblockBranch to SCI, skip ADC calibrationpresents a unified memory linker.execute code or for data variables. The partitioningprocessor Memory BusMultiplexes Frame V ersions Migration ninterference. icritical code locationsprogrammable strobe timingmultiplexes enables glueless interface Strobe programmableExternally modifiedExtending Asynchronous Stack on C28x devices, are mapped to both program and data space. Hence,Embedded Mapped flash/OTP Pipelining V alidate Strobe uniqueversioninterconnect.ArchitectureFetches Simultaneous data1-wait Random min Paged FLASH Programmable Programmed via Sectors configuration*spurious Certain memory ranges are EALLOW protected against sp restricted tPeripheralFrame Espeed transients nhanced capture input/output 2 tie conversionceramic bypass capacitorPositive Outpunce Medium Output.External Current Bias Resistor. Low Reference (executionDevice high-impedance stated for TI. Must be left unconnected. (I/O)Reserved fEmulatoEmulator adequate protection.internal pullup internal pulldown d Controller Area NetworkMultichannel Buffered Serial Port (McBSP)/SPI32-bit Capture inputs or auxiliary PWM outputsrespectivelyabbreviateddemanding control applications.Disable Individual Peripheral ClocksEmulation FeaturesJTAG Boundary Scan SupportProgrammableInternal or External ReferenceChannel Input MultiplexerUp to 6 Event Capture InpPWM OQuadrature Encoder InterfacesHRPWMUp to 6 HRPWM Outputs With 150 ps MEPResolutionPrevents Firmware Reverse EngineeringBlockOscillator–Dynamic PLL RatioSci pci capture modules失落Release note RTX Runtime Development KitEvaluationV ersion expires evaluation starvation exception. Issues That Have Been Resolved In RTX 7.0 execute real-time applications in the releasereleaseadministrator privileges. versionslog logout ofthe domainActive Directory, multiprocessor (MP) systems two process processorUpdate the “Emergency Recovery” disk for the system (i Computer node (click on the plus sign) to show its leaf. Computer nodeHardware>Device Manager HAL type. rebootedX Samples directory hear a steady 1 KHz tone for 15 seconds along with a histogramof the systems response time measurements. purchase order is processedRTX environment along with providing networking support to the RTX Peripherals hihg-resolution modules network core dual mac interface chip oscillator expansion fir reverse 复制I am always on you side 横波斯湾纵波pertain inertial magnitude vibration vibrate Amplitude expenditure quantify calibrate analogous constraint intelligible extraneous amplification modify sector portion ancestry barest precisseness intermediate usable pulse tolerances detail filter transducer spindle contact springmass elastic orifice buoyant venturi vane propeller opt contactor ical photoelectric cell lenses optical filters amplify attenuating telemeter integrate fiber resistance displacement index electron column 圆锥taper 正alphanumeric readout ink light beam photographic magnetic compute strain deed selectivein integration differentiating telemeter s ek comprehensible senses intend recognitione exception indicating oscilloscope oscillograph light beam odometer voltmeter cylinder piston stem scale division bears against compress applied indicate velocity voltage addition attenuatean anatrlog respect thereby velocity linear adynamic response available optimum component importan bond gage manufacture applied apply unit structure gage install ambiguous substituted predetermined period ic nonrepetitive transient aperiodi transient response wavefront static productivity significant management discipline detection prediction profitability inspectoion boundary catastrophic compensation Dictate unmanend rugged intrusive viscosity load consistency force Turbidity density optical refraction nucleonic mass overall monitors discrete frepuency monitor 连续的确shock pulse monitor signal averaging capacitive sensorinherent properties possess stiffness oscillates equilibrium bandwidth peak amplitude bar digits arrow minor source refresh ezplot subscript indices propertypertinent subject numerical upon represent significance interplay variable systematic manipulation deviations loosely procedures terminologies theory statisticalhypotheses theoretical calculate prime universe finite diameter 半径radius radii semidiameter marbles represent nebulous infinite yield specimen sample coal unit analytical velocity vacuo evaluated apparatus cumulative multisample intent estimate indicated applied express inasmuch resort thereof interchangeably instrument specification amount bias systematic alibration recure resolution precisionsensitivity illegitimate blunder computational chaotic insidious repetitive recure susceptible statistical propagation probability predictn predetermined dispersed termed deviation insertion coefficientjustify readout warranted take into account orifice sharpedged assumed incremental variations unrun ignite soak taper ball b dramatically rotating manifest degradation spectrum earing harmonics duration assume sharpedged微米micrometer micron 分米decimeter毫米coefficient nominal diverter synchronization distribution 厘米centimeter spall overroll stress short duration Domain rectification rectificate simulate harmonic resultant series summation sumtossed rigorous favorable heads and tails preclude 排除万难premise 前提likelihook dice histogram manipulate applicable disperse 分散curve premise dashsolid curve standard deviation arithmetic mean 方差epuation equation normal datum date date 操作entity 空虚vacuity 支持sustain bear abet aegis auspice 擦brush rub wipe scrape 资源exploit essence exploition polarization ultimately productive force develop configue abort palette captain label updates relevance autostemming off morniting monitoring abstract program standard deviationssu bset cluster attribute time stamp variant chart graph error outweigh essent issueial iillusion dramatically extraordinary contribute to contentment adopt meaningful phenomenon employees acknowledge laborious consequently funds fees tuition soar ing dramatically authors interpreting basis engineer comparison calibrate inch ancestry wavelength krypton radio strip transduction electricalintegrate ion differentiating telemetering comprehensible recognition indicating odometer voltmeters tire automobile cylinder piston resisting stem division bear compresses applied summing voltage accelerometer galvanometer type amplifieramplifie r resistance bios bond pdf PDF eq ordinate uatio n 横坐标abscissa 寝室bedchamber 宿舍dorm dormitory hostel lodging house symmetrical abide bia s error offset duplicateghost kid video badges porn demo embed blockset neural 铣刀sensor fusion fuck disastrous solitary absurd kindergartens nursery unfavorable devote supervise far outweigh profound raptures mere mention artisticand forever sculptures galleries rarities maintain essential essence infrastructure priority advocate invest sum inrural emigrants peasants sociologists scarce worsened loneliness obstacle alien dormitory library homelessness smoothly ashion merely 党员干部团员duplicate analyze application interpolation dimension data socket phase specify propertites binary byte scan refnum fret bound imaginary command state usage blunder sophisticated susceptible simplest doubted legitimate stem calibration synchronized fabrication vector described angel 键盘columns. Network layer bias competitive overall monitor discrete frequency monitor shock pulse kurtosis cepstrum analysis inductive sn capacitive electrically conducting filtersoptical oil turbidity magnetic plugs centrifuges particle counter ferrography wear debris acoustic debris strain access blower boiler brazing cou peak value sd plingkurtosis standard deviation skewness phase geometric mean arithmetic mean crest factorroot mean square handler polling adspacer config phase peak vector RMS transpose pertain operation performance develop angular fashion voltage mutual levels of significance thorough evaluation realize derive illegitimate source determination essential precision error competitive truncated valid 本科隐私intimacy 专业检测技术the technology of measurement and instrument仪器仪表vt九月份获得奖情况陇望蜀奖学金奖励制度成绩一等三好学生优秀excellent student 机器人优胜w 奖奖励比赛robot 竞赛活动t物理学competition of physics 软件包熟练master 轻松简单software of office 流利流畅娴熟熟悉familiarly 担任委员assume the commissioner of propagandize of class 宣传计量实习期practice of measurement The 2nd. Heavy Machinery Manufacturing Factory/Plant Practice of measurement inThe 2nd Heavy Machinery Manufacturing Factory in China 八月☐Aa电子工艺实习期technics of electron 实验室课程设计实习期Assume the commissioner of propagandize of class for one year and studying of☐担当担任make occupy act 宣传Ability to deal with personnel at all levels effectively. Ability to work independent1y, mature and resourceful.☐个人评价individual生产测试工程师production testing engineer 参加革命加入实验室友laboratory 困难重重师兄坚持原则优点缺点心理素质惊艳心态认真对待graveness 党员成绩斐然改进arrogance 源头确original 资源宠物form unit spuninst1)讲述DSP 的CPU,memory,program memory addressing,data memory addressin EVM 板,DSK 等原理图,完成DSP 、各控制信号管脚的连接、JTAG口的CCS supply Peripheral BusMemory Bus (Harvard Bus Architecture) . External Interface (XINTFExpansion (PIE) Block3.3 Register Map.Device Emulation Registers fpgaInterface JTAG test reset with internal pulldown. TRST, when driven high, gives the scan system control of the operations of the device. If this signal is not connected or driven low, the device operates in its functional mode, and the test reset signals are ignored.NOTE: TRST is an active high test pin and must be maintained low at all times during normal device operation. An external pulldown resistor is recommended on this pin. Thevalue of this resistor should be based on drive strength of the debugger pods applicable tothe design. A 2.2-k? resistor generally offers adequate protection. Since this isapplication-specific, it is recommended that each target board be validated for properoperation of the debugger and the application. (I, ↓){}Firmware Reverse Engineering Event Capture Inputs Serial Port Peripherals Multiplexed GPIO Pins With Input FilteringBoundary Scan SupportEmulation Featureunitauxiliary PWM QEPMultichannel Buffered Serial Port Serial Peripheral Interface (SPI)Serial PortTable 2-3 describes the signals. The GPIO function (shown in Italics) is the default at reset.alternate functions.indicated). All GPIO pins are I/O/Z and have an internal pullupenabled upon reset.,JTAGInternal Reference Positive Output.ceramic bypassADCREFP 56 P5 P5capa citor of 2.2 μF to analog ground. (O)Memory blocks are not to scale.Peripheral FrameAssumes。
MAC介绍
MAC(Media access control)是介质访问控制,也为媒体访问控制。
以太网协议是由一组IEEE 802.3标准定义的局域网协议集。
在以太网标准中,有两种操作模式:半双工和全双工。
半双工模式中,数据是通过在共享介质上采用载波监听多路访问/冲突检测(CSMA/CD)协议实现传输的。
它的主要缺点在于有效性和距离限制,链路距离受最小MAC帧大小的限制。
该限制极大地降低了其高速传输的有效性。
因此,引入了载波扩展技术来确保千兆位以太网中MAC帧的最小长度为512字节,从而达到了合理的链路距离要求。
在所有IEEE 802协议中,OSI数据链路层被划分为两个IEEE 802子层,即:媒体访问控制(MAC)子层和MAC客户端子层。
MAC子层有以下几个基本职能。
(1)数据封装、(2)发送媒体访问管理、(3)接收媒体访问管理、(4)接收数据解封。
Preamble(Pre):前导码字段,7字节。
Pre字段中1和0交互使用,接收站通过该字段知道导入帧,并且该字段提供了同步化接收物理层帧接收部分和导入比特流的方法。
Pre字段的每个字节的比特模式为“10101010”,用于实现收发双方的时钟同步。
Start-of-Frame Delimiter(SFD):帧起始定界符字段,1字节。
字段中1和0交互使用,结尾是两个连续的1,表示下一位是利用目的地址的重复使用字节的重复使用位。
SFD占1个字节,其比特模式为“10101011”,它紧跟在前导码后,用于指示一帧的开始。
前导码的作用是使接收端能根据“1”、“0”交变的比特模式迅速实现比特同步,当检测到连续两位“1”(即读到帧起始定界符字段SFD最末两位)时,便将后续的信息递交给MAC子层。
Destination Address(DA)/Source Addresses(SA):目的地址/源地址字段,6字节。
地址字段包括目的地址字段DA和源地址字段SA。
目的地址字段占2个或6个字节,用于标识接收站点的地址,它可以是单个的地址,也可以是组地址或广播地址。
专业英语(CPU)
• However, many applications that process in a linear fashion, including communications, backup and some types of numerical computation, won’t benefit as much and might even run slower on a dual-core processor than on a faster single-coreicore CPU from Intel is already on the market. By the end of 2006, Intel expects multicore processors to make up 40% of new desktops, 70% of mobile CPUs and a whopping 85% of all server processors that it ships. Intel has said that all of its future CPU designs will be multicore. Intel’s major competitors——including Advanced Micro Devices Inc., Sun Microsystems Inc. and IBM——each appear to be betting the farm on multicore processors.
• Besides running cooler and faster, multicore processors are especially well suited to tasks that have operations that can be divided up into separate threads and run in parallel. On a dual-core CPU, software that can use multiple threads, such as database queries and graphics rendering, can run almost 100% faster than it can on a single-CPU chip.
莫萨V2426A系列轨道电脑特性与优势说明书

V2426A SeriesCompact,fanless,vibration-proof railway computersFeatures and Benefits•Intel Celeron/Core i7processor•2peripheral expansion slots for various I/O,WLAN,mini-PCIe expansionmodule cards•Dual independent DVI-I displays•2Gigabit Ethernet ports with M12X-coded connectors•1SATA connector and1CFast socket for storage expansion•M12A-coded power connector•Compliant with EN50121-4•Complies with all EN50155mandatory test items1•Ready-to-run Debian7,Windows Embedded Standard7,and Windows10Embedded IoT Enterprise2016LTSB platforms•-40to70°C wide-temperature models available•Supports SNMP-based system configuration,control,and monitoring(Windows only)CertificationsIntroductionThe V2426A Series embedded computers are based on the Intel3rd Gen processor,and feature4RS-232/422/485serial ports,dual LAN ports,3 USB2.0hosts,and dual DVI-I outputs.In addition,the V2426A Series computers comply with the mandatory test items of the EN50155standard, making them suitable for a variety of industrial applications.The dual megabit/Gigabit Ethernet ports with M12X-coded connectors offer a reliable solution for network redundancy,promising continuous operation for data communication and management.As an added convenience,the V2426A computers have6DIs and2DOs for connecting digital input/output devices.In addition,the CFast socket,SATA connector,and USB sockets provide the V2426A computers with the reliability needed for industrial applications that require data buffering and storage expansion.Moreover,the V2426A computers come with2peripheral expansion slots for inserting different communication modules(2-port CAN module,or HSDPA,GPS,or WLAN module),an8+8-port digital input/output module,and a2-port serial module,giving greater flexibility for setting up different industrial applications at field sites.Preinstalled with Linux Debian7or Windows Embedded Standard7,the V2426A Series provides programmers with a friendly environment for developing sophisticated,bug-free application software at a low cost.Wide-temperature models of the V2426A Series that operate reliably in a-40 to70°C operating temperature range are also available,offering an optimal solution for applications subjected to harsh environments.1.This product is suitable for rolling stock railway applications,as defined by the EN50155standard.For a more detailed statement,click here:/doc/specs/EN_50155_Compliance.pdfAppearanceFront View Rear ViewSpecificationsComputerCPU V2426A-C2Series:Intel®Celeron®Processor1047UE(2M cache,1.40GHz)V2426A-C7Series:Intel®Core™i7-3517UE Processor(4M cache,up to2.80GHz) System Chipset Mobile Intel®HM65Express ChipsetGraphics Controller Intel®HD Graphics4000(integrated)System Memory Pre-installed4GB DDR3System Memory Slot SODIMM DDR3/DDR3L slot x1Supported OS Linux Debian7Windows Embedded Standard7(WS7E)32-bitWindows Embedded Standard7(WS7E)64-bitStorage Slot 2.5-inch HDD/SSD slots x1CFast slot x2Computer InterfaceEthernet Ports Auto-sensing10/100/1000Mbps ports(M12X-coded)x2Serial Ports RS-232/422/485ports x4,software selectable(DB9male)USB2.0USB2.0hosts x1,M12D-coded connectorUSB2.0hosts x2,type-A connectorsAudio Input/Output Line in x1,Line out x1,M12D-codedDigital Input DIs x6Digital Output DOs x2Video Output DVI-I x2,29-pin DVI-I connectors(female)Expansion Slots2peripheral expansion slotsDigital InputsIsolation3k VDCConnector Screw-fastened Euroblock terminalDry Contact On:short to GNDOff:openI/O Mode DISensor Type Dry contactWet Contact(NPN or PNP)Wet Contact(DI to COM)On:10to30VDCOff:0to3VDCDigital OutputsConnector Screw-fastened Euroblock terminalCurrent Rating200mA per channelI/O Type SinkVoltage24to30VDCLED IndicatorsSystem Power x1Storage x1LAN2per port(10/100/1000Mbps)Serial2per port(Tx,Rx)Serial InterfaceBaudrate50bps to921.6kbpsFlow Control RTS/CTS,XON/XOFF,ADDC®(automatic data direction control)for RS-485,RTSToggle(RS-232only)Isolation N/AParity None,Even,Odd,Space,MarkData Bits5,6,7,8Stop Bits1,1.5,2Serial SignalsRS-232TxD,RxD,RTS,CTS,DTR,DSR,DCD,GNDRS-422Tx+,Tx-,Rx+,Rx-,GNDRS-485-2w Data+,Data-,GNDRS-485-4w Tx+,Tx-,Rx+,Rx-,GNDPower ParametersInput Voltage12to48VDCPower Connector M12A-coded male connectorPower Consumption 3.78A@12VDC0.96A@48VDCPower Consumption(Max.)47W(max.)Physical CharacteristicsHousing AluminumIP Rating IP30Dimensions(with ears)275x92x154mm(10.83x3.62x6.06in)Dimensions(without ears)250x86x154mm(9.84x3.38x6.06in)Weight3,000g(6.67lb)Installation DIN-rail mounting(optional),Wall mounting(standard) Protection-CT models:PCB conformal coating Environmental LimitsOperating Temperature Standard Models:-25to55°C(-13to131°F)Wide Temp.Models:-40to70°C(-40to158°F) Storage Temperature(package included)-40to85°C(-40to185°F)Ambient Relative Humidity5to95%(non-condensing)Standards and CertificationsEMC EN55032/24EMI CISPR32,FCC Part15B Class AEMS IEC61000-4-2ESD:Contact:6kV;Air:8kVIEC61000-4-3RS:80MHz to1GHz:20V/mIEC61000-4-4EFT:Power:2kV;Signal:2kVIEC61000-4-5Surge:Power:2kVIEC61000-4-6CS:10VIEC61000-4-8PFMFRailway EN50121-4,IEC60571Railway Fire Protection EN45545-2Safety EN60950-1,UL60950-1Shock IEC60068-2-27,IEC61373,EN50155Vibration IEC60068-2-64,IEC61373,EN50155DeclarationGreen Product RoHS,CRoHS,WEEEMTBFTime304,998hrsStandards Telcordia(Bellcore),GBWarrantyWarranty Period3yearsDetails See /warrantyPackage ContentsDevice1x V2426A Series computerInstallation Kit1x wall-mounting kitDocumentation1x document and software CD1x quick installation guide1x warranty cardDimensionsOrdering InformationModel Name CPU Memory(Default)OS CFast(CTO)Backup CFast(CTO)SSD/HDD Tray(CTO)PeripheralExpansionSlotsOperatingTemp.ConformalCoatingV2426A-C2Celeron1047UE4GB1(Optional)1(Optional)1(Optional)2-25to55°C–V2426A-C2-T Celeron1047UE4GB1(Optional)1(Optional)1(Optional)2-40to70°C–V2426A-C2-CT-T Celeron1047UE4GB1(Optional)1(Optional)1(Optional)2-40to70°C✓V2426A-C7Core i7-3517UE4GB1(Optional)1(Optional)1(Optional)2-25to55°C–V2426A-C7-T Core i7-3517UE4GB1(Optional)1(Optional)1(Optional)2-40to70°C–V2426A-C7-CT-T i7-3517UE4GB1(Optional)1(Optional)1(Optional)2-40to70°C✓V2426A-C2-W7E Celeron1047UE4GB8GB1(Optional)1(Optional)2-25to55°C–V2426A-C2-T-W7E Celeron1047UE4GB8GB1(Optional)1(Optional)2-40to70°C–V2426A-C7-T-W7E i7-3517UE4GB8GB1(Optional)1(Optional)2-40to70°C–Accessories(sold separately)Battery KitsRTC Battery Kit Lithium battery with built-in connectorCablesCBL-M12XMM8PRJ45-BK-100-IP67M12-to-RJ45Cat-5E UTP gigabit Ethernet cable,8-pin X-coded male connector,IP67,1mCBL-M12(FF5P)/Open-100IP67A-coded M12-to-5-pin power cable,IP67-rated5-pin female M12connector,1mA-CRF-RFQMAM-R2-50Wi-Fi Extension Cable QMA(male)to SMA(male)adapter with50cm cable x1A-CRF-QMAMSF-R2-50Cellular Extension Cable QMA(male)to SMA(female)adapter with50cm cable x1A-CRF-CTPSF-R2-50GPS Extension Cable TNC to SMA(female)adapter with50cm cable x1ConnectorsM12A-5PMM-IP685-pin male circular threaded D-coded M12USB connector,IP68M12X-8PMM-IP678-pin male X-coded circular threaded gigabit Ethernet connector,IP67M12A-5P-IP68A-coded screw-in sensor connector,female,IP68,4.05cmM12A-8PMM-IP678-pin male circular threaded A-codes M12connector,IP67-rated(for field-installation)Power AdaptersPWR-24270-DT-S1Power adapter,input voltage90to264VAC,output voltage24V with2.5A DC loadPower CordsPWC-C7AU-2B-183Power cord with Australian(AU)plug,2.5A/250V,1.83mPWC-C7CN-2B-183Power cord with two-prong China(CN)plug,1.83mPWC-C7EU-2B-183Power cord with Continental Europe(EU)plug,2.5A/250V,1.83mPWC-C7UK-2B-183Power cord with United Kingdom(UK)plug,2.5A/250V,1.83mPWC-C7US-2B-183Power cord with United States(US)plug,10A/125V,1.83mWall-Mounting KitsV2400Isolated Wall Mount Kit Wall-mounting kit with isolation protection,2wall-mounting brackets,4screwsStorage KitsFK-75125-02Storage bracket,4large silver screws,4soft washers,4small sliver bronze screws,1SATA powercable,4golden spacers(only for the V2406and V2426)Expansion ModulesEPM-DK022mini PCIe slots for wireless modules,-25to55°C operating temperatureEPM-DK03GPS receiver with2mini PCIe slots for wireless modules,-25to55°C operating temperatureEPM-30322isolated RS-232/422/485ports with DB9connectors,-40to70°C operating temperatureEPM-31122isolated CAN ports with DB9connectors,-25to55°C operating temperatureEPM-34388DIs and8DOs,with3kV digital isolation protection,2kHz counter,-40to70°C operating AntennasANT-WDB-ARM-02 2.4/5GHz,omni-directional rubber duck antenna,2dBi,RP-SMA(male)ANT-LTE-ASM-02GPRS/EDGE/UMTS/HSPA/LTE,omni-directional rubber duck antenna,2dBiANT-WCDMA-AHSM-04-2.5m GSM/GPRS/EDGE/UMTS/HSPA,omni-directional magnetic base antenna,4dBiANT-GPS-OSM-05-3M Active GPS antenna,26dBi,1572MHz,L1band antenna for GPSANT-LTEUS-ASM-01GSM/GPRS/EDGE/UMTS/HSPA/LTE,omni-directional rubber duck antenna,1dBiWireless Antenna CableA-CRF-MHFQMAF-D1.13-14.2Digital Interface Mini card internal antenna with QMA connector x1,locking washer x1,O-ring x1,nutx1Din Rail Mounting kitDK-DC50131DIN-rail mounting kit,6screwsWireless PackagesEPM-DK3G Package Gemalto PHS8-P3G mini card with digital interface,internal antenna,installation bracket,screws,locking washers,O-rings,nuts,and thermal padEPM-DK Wi-Fi Package SprakLAN WPEA-121N Wi-Fi mini card with digital interface,internal antenna,installation bracket,screws,locking washers,O-rings,nuts,and thermal padEPM-DK LTE-EU Package Gemalto PLS8-E LTE mini card with digital interface,internal antenna,installation bracket,screws,locking washers,O-rings,nuts,and thermal padEPM-DK LTE-US Package Gemalto PLS8-X LTE mini card with digital interface,internal antenna,installation bracket,screws,locking washers,O-rings,nuts,and thermal padWireless Antenna Packages3G Antenna Package3G external antenna with QMA(male)to SMA(female)adapter and50-cm cables x2,3G externalantenna with SMA connectors x2,cellular extension cableLTE-US Antenna Package LTE-US external antenna with QMA(male)to SMA(female)adapter and50-cm cables x2,LTE-USexternal antenna with SMA connector x2,cellular extension cableLTE-EU Antenna Package LTE-EU external antenna with QMA(male)to SMA(female)adapter with50-cm cables x2,LTE-EUexternal antenna with SMA connectors x2,cellular extension cableWi-Fi Antenna Package External antenna with QMA internal cable,Wi-Fi extension cableGPS Antenna Package External antenna with TNC to SMA(female)adapter and a50-cm cable,SMA antenna(26dBi,1572MHz,L1band),GPS extension cable©Moxa Inc.All rights reserved.Updated Apr16,2019.This document and any portion thereof may not be reproduced or used in any manner whatsoever without the express written permission of Moxa Inc.Product specifications subject to change without notice.Visit our website for the most up-to-date product information.。
g4900cpu

G4900 CPUIntroductionThe G4900 CPU is a budget-oriented processor manufactured by Intel. It is based on the 14nm process technology and belongs to the Pentium Gold family. Despite its affordable price, the G4900 CPU offers a decent level of performance for everyday computing tasks. In this document, we will explore the key features, specifications, and performance of the G4900 CPU.Key Features1.Dual-Core Architecture: The G4900 CPU features adual-core design, allowing it to handle multiple taskssimultaneously. This makes it suitable for multitasking and running several applications at the same time.2.Clock Speed: The base clock speed of the G4900CPU is 3.1 GHz, providing sufficient power for most daily computing tasks. However, it should be noted that theG4900 CPU lacks boost capabilities, meaning the clockspeed cannot be increased further.3.Hyper-Threading Support: Although the G4900CPU operates with two physical cores, it supports Hyper-Threading technology. This feature allows each core tohandle two threads concurrently, resulting in improvedmultitasking performance.4.Intel UHD Graphics 610: Integrated within theG4900 CPU is the Intel UHD Graphics 610, offering adequate graphics performance for everyday use and entry-level gaming. While it may not meet the demands of graphics-intensive applications, the GPU can handle HD video playback and basic photo editing.5.Low Power Consumption: With a TDP (Thermal Design Power) of only 54W, the G4900 CPU is energy-efficient. It generates less heat compared to higher-end processors, making it ideal for low-power systems or small form-factor computers.6.Socket Compatibility: The G4900 CPU utilizes the LGA 1151 socket, which provides compatibility with various Intel 300-series chipsets. This offers flexibility when choosing a motherboard for a system build.Specifications•Processor Type: Intel Pentium Gold G4900•Number of Cores: 2•Number of Threads: 2 (with Hyper-Threading)•Base Clock Speed: 3.1 GHz•Graphics: Intel UHD Graphics 610•Graphics Base Frequency: 350 MHz•Graphics Maximum Dynamic Frequency: 1.05 GHz•Lithography: 14nm•TDP: 54W•Socket: LGA 1151•Max Memory Size: 64GB•Memory Types: DDR4-2400•Max Number of Memory Channels: 2PerformanceThe G4900 CPU delivers satisfactory performance for everyday computing tasks. It is suitable for web browsing, office productivity, light gaming, and multimedia consumption. With its dual-core design and Hyper-Threading support, theG4900 CPU handles multitasking with relative ease.In terms of gaming, the G4900 CPU can run casual and older titles smoothly, but it may struggle with more demanding games that require higher CPU and GPU capabilities. For users looking to build a budget gaming system, pairing the G4900 CPU with a dedicated graphics card is recommended to achieve better gaming performance.When it comes to power consumption, the G4900 CPU excels in efficiency. It consumes less power compared tohigher-end processors, resulting in lower electricity bills and reduced heat generation.ConclusionThe G4900 CPU offers a cost-effective solution for users in need of a budget-oriented processor. With its dual-core architecture, Hyper-Threading support, and integrated UHD Graphics 610, the G4900 CPU provides satisfactory performance for everyday computing tasks, web browsing, office productivity, and light gaming. Its low power consumption makes it an ideal choice for low-power systems or small form-factor computers. However, users seeking higher gaming performance may prefer to pair the G4900 CPU with a dedicated graphics card. Overall, the G4900 CPU is a reliable option for those looking for an affordable processor without compromising essential features.。
HP工作站产品介绍说明书

Sales guide | Why a Workstation?
Workstations are designed for the demands of users who work with professional and technical applications, large and complex datasets or intricate 3D models.
Intel® Xeon® Processor technology.................................................................................................................................. 4 Storage even a server would envy.................................................................................................................................... 4 Leading-edge professional graphics................................................................................................................................ 4 HP Performance Advisor..................................................................................................................................................... 4 HP Remote Graphics Software.......................................................................................................................................... 4 Performance on display...................................................................................................................................................... 4 Mission-critical reliability........................................................................................................................................................ 5 A strenuous design standard............................................................................................................................................. 5 Independent Software Vendor (ISV) certification........................................................................................................... 5 Tested beyond industry standards................................................................................................................................... 5 Engineered BIOS................................................................................................................................................................... 5 ECC memory for data integrity........................................................................................................................................... 5 Expandable by design............................................................................................................................................................. 6 Tool-less chassis.................................................................................................................................................................. 6 Ultimate processing power................................................................................................................................................. 6 More memory, less waiting................................................................................................................................................ 6 Memory, storage and graphics that grow with your needs.............................................................................................. 6 Why an HP Workstation........................................................................................................................................................... 7
科技文翻译

英文文献翻译专业班级:自动化06-1班学生姓名:周鑫学号:060410122 二〇一〇年六月一日1.英文资料8051 Embedded System Based on GPRS terminal to achieveWith the surge in demand for wireless data and GPRS mobile services in the painting fully operational, the application of wireless data communications more widely. GPRS network not only has covered a wide range of data transmission speed, high quality, always-on and meter fees in accordance with merit, and itself a packet-based data network to support TCP / IP protocol, without going through the PSTN network switch, etc. Then, communicate directly with the Internet network. GPRS wireless Internet access business, therefore, environmental monitoring, traffic monitoring, mobile office industry with unmatched cost advantage.GPRS terminals to meet the low-cost, compact and mobile and flexible, etc., are now widely used in microcomputer control on the GPRS terminal, and the introduction of embedded system TCP / IP protocol stack. The main difficulty now is: Run the TCP / IP protocol on the computer memory, computing speed higher, and will occupy a lot of system resources; and embedded systems are mostly 8-bit microcontroller, the hardware resources are very limited, support for TCP / IP protocol is difficult. This article uses real-time operating system in embedded uC / OS-II in the transplant of a small TCP / IP protocol stack uIP the ways in which embedded systems based on 8051 GPRS terminal can transmit data in the network; the same time improve the system performance, improved reliability, enhanced system scalability and product development can be continuity.A data transmission network based on GPRSGPRS is based on the introduction of GSM Packet Control Unit (PCU), Service Support Node (SGSN) and gateway support node (GGSN), and other new parts consisting of wireless data transmission system, its users to form groups at the end Next to send and receive data. GPRS network based data transmission system shown in Figure 1. Process-specific data:GPRS terminal through the interface from the client system, remove the user data;GPRS packet data after processing the form sent to the GSM base station (BSS);Packet data packaged by the SGSN, sent to the GPRS IP backbone network;If the packet data is sent to another GPRS terminals are first sent to the destination SGSN, and then sent to the CPBS terminal via BSS; if packet data is sent to the external network (such as the Internet), packets will be grouped by the GGSN to perform the conversion After sending to the external network.2 embedded real-time operating system uC / OS-IIuC / OS-II by Jean J. Prepared by Mr. Labrosse, now a popular free open source real-time operating system. It can be widely used from 8 to 64 different types of SCM, different sizes of embedded systems. With detailed notes of the uC / OS-II source code is only 200 pages or so; of which 95% is written in C, and the MCU type associated with the 8088 assembly code written in no more than 200 lines. uC / OS-II is not only compact in structure, can be cured, can be cut, multi-task and can be denied based real-time kernel, etc; and real-time, stability, reliability skirts have also been widely recognized. uC / OS-II can be compiled to the minimum core 2KB, generally take up memory in 10KB of magnitude for 8051-based embedded system needs. In the system, embedded uC / OS-II can be divided into many tasks throughout the process, relatively independent of each task, and then set the timeout function for each task, time after use, must surrender the right to use MCU. Even if a task problem, it will not affect the operation of other tasks. Embedded microcontroller system in uC / OS-II to improve system reliability, make it easy to debug programs, but also enhance the system scalability and product development can be continuity.However, uC / OS-II real-time operating system kernel is just a, compared with commercial real time operating system package, it lacks the Utilities section, such as file systems, remote function call library, communication software library. Communications software, including: TCP / IP software libraries, Bluetooth communication software library, IrDA infrared communications software libraries. This type of software solution in two ways: one is to purchase third party software; the other is to write your own. If only with MCU TCP / IP protocol in some of the features, you can use a small free open source TCP / IP protocol stack, it ported to uC / OS-II. Currently uC / OS-II's latest version V2.70, but now widespread study and application of the V2.52.3 small TCP / IP protocol stack uIPuIP computer by the Swiss Academy of Sciences, Adam Dunkels a free open source development such as small TCP / IP protocol stack, it is designed for 8-bit and 16-bit MCU write. uIP entirely in C language, it is to ensure a complete TCP / IP stack under the premise of retaining only the most necessary for a series of features to the code at least, occupied RAM minimum; it can only handle a single network interface .Normal TCP / IP stack with BSD socket API, need to multi-tasking operating system from the lower support, and task management, context switching and stack space allocation should occupy much of the overhead, beyond the eight-machine system capacity. uIP using an event-driven interface, by calling the application respond to events. The corresponding application as C function calls. Typically, uIP the source code although only a few KB, RAM occupied by only a few hundred bytes, but uIP provides necessary network communication protocols, including: ARP, SLIP, IP, UDP, ICMP (PINC) and TCP; to meet the 8-bit MCU access to TCP / IP network (such as the Internet) needs. UIP the latest version of the current V0.9, consistent with Internet standards.4 GPRS terminals and hardware implementation of the principleGPRS terminal control module controlled by the TCP / IP module and the wireless transmission module. The block diagram shown in Figure 2.4.1 Control ModuleThe role of the control module are:AT command control module initialization through GPRS wireless module, so attached to the GPRS network, access network operators dynamically allocated to GPRS terminal IP address and with the aim to establish a connection between the terminal or server;RS232 serial control module to the client system by sending and receiving data or instructions;RS232 serial port to the control module through TCP / IP modules send and receive data;control module independently or under remote control commands to take other action.Winbond MCU control module of the eight selection machine WINBOODW77E58. W77E58 is produced by Taiwan's Winbond, and MCS51 MCU-compatible and can be programmed repeatedly fast microprocessors, integrated within its 32KB of reprogrammable Flash ROM, 256 bytes of on-chip memory, IKB use MOVX instruction accesses the SRAM, a programmable watchdog timer, three 16-bit timers, two enhanced full-duplex serial port, on-chip RC oscillator, dual 16-bit data pointer, and many other features. On many occasions, almost no expansion of peripheral chips can meet the system requirements. Because of its design with a new microprocessor core, to remove and store the extra clock cycles, the crystal in the same frequency, according to the instructions of different types, which generally runs faster than the traditional 8051 Series 1.5 ~ 3 times. In general, an average of up to 2.5times. In addition, because a fully static CMOS design W77E58 can work in low-speed oscillator frequency. 8051 compared with the ordinary, if W77E58 with low frequency, in the same instruction throughput, W77E58 in power, will also be greatly enhanced.4.2 TCP / IP moduleTCP / IP module through RS232 serial communication with the GPRS wireless modules provide non-transparent and transparent two-way channel. Corresponding to the module has two transmission modes: transparent mode and non-transparent mode. Software switch module in a different transmission mode, the data flows are also different. When sending AT command set, the module into the transparent mode, you can directly access the GPRS wireless module; when the module into the non-transparent transmission mode, the user data from the serial port into the TCP / IP module, the first 10 d into the TCP / IP packet, and then Send to a GPRS module through the serial port; GPRS wireless module into its package GPRS GPRS packet data packet transmitted online. TCP / IP module from the 8051 microcontroller-based embedded system. Embedded systems use WINBOODW77E58 as microprocessors, embedded real-time operating systems use uC / OS-II, and then in the uC / OS-II in transplant uIP achieve TCP / IP protocol stack.4.3 GPRS wireless moduleGPRS wireless module as GPRS wireless terminal transceiver module, the From the TCP / IP module receives the TCP / IP packet and from the base station receives the GPRS packet data processing before forwarding the corresponding agreement. SIEMENS GPRS wireless module uses the company's MC35 GPRS modules. MC35 module mainly by the RF antenna, the internal Flash, SRAM, GSM baseband processor, power supply and a matching 40-pin ZIF socket component. GSM baseband processor is the core component, which acts as a protocol processor to handle the external system through the serial port to send over the AT command. Main achieved RF antenna signal modulation and demodulation, and the external RF signal and the internal signal conversion between the baseband processor. Matching power supply for the processor and the RF section provides the necessary power. MC35 GPRS module supports GSM900 and GSMl800 dual-band network, to receive rates up to 86.20kbps, send rates up to 21.5kbps, and easy integration. Maximum data throughput of course, also depends on the GPRS network support.5 TCP / IP software implementation5.1 uC / OS-II in 8051 on the transplantationuC / OS-II software is free, non-commercial use, such as research and teachingare free. Any user can download from the Internet, its source code, through appropriate modifications to be transplanted, hardware and systems to meet their own needs. To transplant, need to understand the uC / OS-II operating system, the overall structure, as shown in Figure 3 is the uC / OS-II structure and the relationship with the hardware.And processor-independent code contains uC / OS-II system function, making the system transplantation generally do not need to modify this part; Just UCOS-II. C file included in your project, you can be uC / OS-II in all MCU independent code contains the code to the transplant.And application-related code is the user according to their own custom application system suitable core services, which includes two files: OS_CFG. H, INCLUDES. H. One OS_CFG. H is used to configure the kernel, users needed to customize the kernel, set the system's basic information, such as system can provide the maximum number of tasks, whether custom mail service, the need for system tasks pending features, the availability of dynamic change task priority function. The INCLUDES. H is the system header files.Processor contains the code related to different types of MCU on the support needs of this part of the MCU according to their own modifications. For the Keil C51 compiler and the technical features of the 8051 chip, uC/OS- Ⅱ transplant and three documents related to: processor associated C file (OS_CPU.H, OS_CPU_C.C) and the compilation of documents (OS_CPU_A.ASM).(1) modify OS_CPU. HFile OS_CPU. H includes the use of # define statements related to the definition of processor constant, macro, and type. Transplantation, the main contents of the amendment are:The data type of compiler-related settings. Keil C51 compiler reference to the help file C51. PDF, the specific path for the \ Keil \ C51 \ HLP \ C51. PDF.use the # define statement defines two macros switch interrupts, the specific implementation are:# Define OS_ENTER_CRITICAL () EA = 0 / / off interrupts# Define OS_EXIT_CRITICAL () EA = 1 / / Open interruptAccording to the 8051 definition of the direction of the stack OS_STK_GROWTH.# Define OS_STK_GROWTH 0 / / 8051 stack increment from the bottom up OS_STK_GROWTH set to 0, that stack from the bottom (low address) up (high address) increments; set OS_STK_GROWTH to 1, indicating the stack from the(high address) down (low address) decrease.uC / OS-II from the low priority task to switch to high-priority tasks need to use OS_STK_SW (), through the implementation of OS_STK_SW () imitation interrupt generation. Will provide the majority of CPU instructions soft interrupt or trap (TRAP) to complete this function. Interrupt service routines or instruction trap handler (also called exception handling functions) of the interrupt vector address must point to the assembly language functions OSCtxSw (). Since 8051 there is no soft interrupt instruction, so instead of using program calls.# Define OS_TASK_SW () OSCtxSw ()(2) modify OS_CPU_C. CuC / OS-II porting examples require the user to write a simple C function 10, which OSTaskStklnit () is necessary, the other nine functions must be declared, but not necessarily contain any code. Because the default Keil C51 compiler to function as non-reentrant structure, but the system requirements for multi-task operation concurrent cause re-entry, so each C function and the declaration marked reentrant keyword, the compiler generated code running in support of the function reentrant. Another "pdata", "data" in uC / OS-II used to do some function parameter, but it is also a Keil C51 keyword, this will cause a compiler error. Usually the "pdata''into" ppdala "," data "into" ddata "to solve this problem. Specific changes to the code as follows:In the 8051's uC / OS-II, the transplanted uIP does not require the existing TCP / IP source code to make any changes, it must be for the network equipment (such as LAN chip, serial, etc.) to write a driver. Meanwhile, the integration of some existing systems have to deal with accordingly, for example, when data arrives or periodic timer count full, etc., the main control system should call uIP function [Liu. Portable concrete steps are as follows:In the directory uip-0.9 / directory to create its own, such as uip-0.9/8051 /;the uip_arch. c file from the directory uip-0.9/unix / copied to the directory uip-0.9/8051 in; it contains the C language with 32-bit adder, checksum algorithm;the uipopt. his ulP configuration file, which includes not only the IP address, such as uIP outlets and at the same time such as setting the maximum connection options, but also the system architecture and C compiler specific options;Reference examples unix / tapdev. c and uip / slipdev. c, write drivers for the serial port;Reference examples unix / main. c, write your own master control system to be called in due course ulP function;Compile the source code.This paper describes the embedded system based on the 8051 implementation of GPRS terminals, and introduces embedded RTOS uC / OS-II based on the 8051 transplant, and small TCP / IP protocol stack uIP transplantation: the use of the GPRS network and the GPRS terminals GPRS Internet to the corresponding terminal and the corresponding Internet terminal for data transfer. In the GPRS terminal TCP / IP module to introduce real time operating system will not only improve the system performance, improve system reliability, and enhance the system scalability and product development can be continuity.2.中文资料基于8051嵌入式系统的GPRS终端实现随着数据无线传输需求的骤增和中画移动GPRS业务全面投入运营,无线数据通信的应用越来越广泛。
MTOS-UX OS Awareness Manual TRACE32 Directory说明书

OS Awareness Manual MTOS-UXRelease 09.2023TRACE32 Online HelpTRACE32 DirectoryTRACE32 IndexTRACE32 Documents ......................................................................................................................OS Awareness Manuals ................................................................................................................OS Awareness Manual MTOS-UX (1)History (3)Overview (3)Brief Overview of Documents for New Users3 Supported Versions4Configuration (5)Manual Configuration5 Automatic Configuration6 Hooks & Internals of MTOS-UX6Features (7)SYSC Terminal Emulation7 Display of Kernel Resources8 Task Stack Coverage8 Task Runtime Statistics9 Task State Analysis9 Function Runtime Statistics10 MTOS-UX specific Menu11MTOS-UX Commands (12)TASK.DispEvent Display global event flags12 TASK.DispFixed Display fixed pools12 TASK.DispmBuff Display message buffers13 TASK.DispMbx Display mailboxes13 TASK.DispPool Display common pools14 TASK.DispSem Display semaphores15 TASK.DispsVar Display shared variables15 TASK.DispTask Display tasks16 TASK.DispTIme Display time & TOD17 TASK.DispUnit Display peripheral units17 TASK.MAP Mapping suggestion17MTOS-UX PRACTICE Functions (18)TASK.CONFIG()OS Awareness configuration information18Version 09-Oct-2023 History04-Feb-21Removed legacy command T ASK.T ASKState.OverviewThe OS Awareness for MTOS-UX contains special extensions to the TRACE32 Debugger. This chapter describes the additional features, such as additional commands and statistic evaluations.Brief Overview of Documents for New UsersArchitecture-independent information:•“Training Basic Debugging” (training_debugger.pdf): Get familiar with the basic features of a TRACE32 debugger.•“T32Start” (app_t32start.pdf): T32Start assists you in starting TRACE32 PowerView instances for different configurations of the debugger. T32Start is only available for Windows.•“General Commands” (general_ref_<x>.pdf): Alphabetic list of debug commands.Architecture-specific information:•“Processor Architecture Manuals”: These manuals describe commands that are specific for the processor architecture supported by your Debug Cable. T o access the manual for your processorarchitecture, proceed as follows:-Choose Help menu > Processor Architecture Manual.•“OS Awareness Manuals” (rtos_<os>.pdf): TRACE32 PowerView can be extended for operating system-aware debugging. The appropriate OS Awareness manual informs you how to enable theOS-aware debugging.Supported VersionsCurrently MTOS-UX is supported for the version MTOS-UX/68k V 3.6 on the Freescale Semiconductor 68332/376.ConfigurationManual ConfigurationFormat:TASK.CONFIG mtos <magic_address> <args><magic_address>Specifies a memory location that contains the current running task. Thisaddress can be found at the label “LCLBAS”.<args>The configuration requires one additional argument that specifies an MTOS-UX internal table. Give the label “GBLBAS”.This command configures the OS Awareness for MTOS-UX with manual setup.The TASK.CONFIG command loads an extension definition file called “mtos.t32” (directory“~~/demo/m68k/kernel/mtosux”). It contains all necessary extensions.; manual configuration for MTOS-UX supportTASK.CONFIG mtos LCLBAS GBLBASIf you want to have dual port access for the display functions (display ’On The Fly’), you have to map emulation memory to the address space of all used system tables. See also TASK.MAP.See also the example “~~/demo/m68k/kernel/mtosux/mtos.cmm”Automatic ConfigurationFormat:TASK.CONFIG mtosThis command configures the OS Awareness for MTOS-UX with automatic setup.The TASK.CONFIG command loads an extension definition file called “mtos.t32” (directory“~~/demo/m68k/kernel/mtosux”). It contains all necessary extensions.This configuration tries to locate the MTOS-UX internals automatically. For this purpose the symbols’LCLBAS’ and ’GBLBAS’ must be loaded and accessible at any time, the OS Awareness is used.Each T ASK.CONFIG argument can be substituted by ’0’, which means, that this argument will be searched and configured automatically. For a full automatic configuration omit all arguments to the command: ; full automatic configuration for MTOS-UX supportTASK.CONFIG mtosIf a system symbol is not available, or if another address should be used for a specific system variable, then the corresponding argument must be set manually with the appropriate address.If you want to have dual port access for the display functions (display ’On The Fly’), you have to mapemulation memory to the address space of all used system tables. See also TASK.MAP.See also the example “~~/demo/m68k/kernel/mtosux/mtos.cmm”Hooks & Internals of MTOS-UXThe local ram data table (LCL) is used for determination of the current running task. The global ram data table (GBL) and its referenced tables are used for detecting all MTS-UX system resources.FeaturesThe OS Awareness for MTOS_UX supports the following features.SYSC Terminal EmulationThe T erminal Emulation window can be used to communicate with the target system console, called ’SYSC’.The communication is done via two memory cells, requiring no external hardware interface. See the TERM command for a description of the terminal emulation.On request LAUTERBACH can provide you with the source code for the target interface routine.The example (“~~/demo/m68k/kernel/mtosux/mtos.cmm”) contains this interface and the terminal emulation for output messages. The example also contains the MTOS-UX dynamic debugger, which uses the system console, too. Invoke the MTOS-UX dynamic debugger by pressing CTRL-D inside the system console window.Display of Kernel ResourcesThe extension defines new PRACTICE commands to display various kernel resources. The followinginformation can be displayed:tasks(DispT ask)time & TOD(DispTIme)global event flag groups(DispEvent)common memory pools(DispPool)fixed block memory pools(DispFixed)message buffers(DispmBuff)mailboxes(DispMbx)semaphores(DispSem)controlled shared variables(DispsVar)physical I/O units(DispUnit)For a detailed description of each command refer to the chapter “MTOS-UX PRACTICE Commands”.When working with emulation memory or shadow memory, these resources can be displayed “On The Fly”,i.e. while the target application is running, without any intrusion to the application. If using this dual portmemory feature, be sure that emulation memory is mapped to all places, where MTOS-UX holds its tables.When working only with target memory, the information will only be displayed, if the target application is stopped.Task Stack CoverageFor stack usage coverage of tasks, you can use the TASK.STacK command. Without any parameter, this command will open a window displaying with all active tasks. If you specify only a task magic number as parameter, the stack area of this task will be automatically calculated.T o use the calculation of the maximum stack usage, a stack pattern must be defined with the command TASK.STacK.PATtern (default value is zero).T o add/remove one task to/from the task stack coverage, you can either call the TASK.STacK.ADD or TASK.STacK.ReMove commands with the task magic number as the parameter, or omit the parameter and select the task from the TASK.STacK.* window.It is recommended to display only the tasks you are interested in because the evaluation of the used stack space is very time consuming and slows down the debugger display.Task Runtime StatisticsNOTE:This feature is only available, if your debug environment is able to trace taskswitches (program flow trace is not sufficient). It requires either an on-chip tracelogic that is able to generate task information (eg. data trace), or a softwareinstrumentation feeding one of TRACE32 software based traces (e.g. FDX orLogger). For details, refer to “OS-aware Tracing” (glossary.pdf).Based on the recordings made by the Trace (if available), the debugger is able to evaluate the time spent ina task and display it statistically and graphically.T o evaluate the contents of the trace buffer, use these commands:Trace.List List.TASK DEFault Display trace buffer and task switchesTrace.STATistic.TASK Display task runtime statistic evaluationTrace.Chart.TASK Display task runtime timechartTrace.PROfileSTATistic.TASK Display task runtime within fixed time intervalsstatisticallyTrace.PROfileChart.TASK Display task runtime within fixed time intervals ascolored graphTrace.FindAll Address TASK.CONFIG(magic) Display all data access records to the “magic”locationTrace.FindAll CYcle owner OR CYcle context Display all context ID records The start of the recording time, when the calculation doesn’t know which task is running, is calculated as “(unknown)”.Task State AnalysisNOTE:This feature is only available, if your debug environment is able to trace taskswitches and data accesses (program flow trace is not sufficient). It requireseither an on-chip trace logic that is able to generate a data trace, or a softwareinstrumentation feeding one of TRACE32 software based traces (e.g. FDX orLogger). For details, refer to “OS-aware Tracing” (glossary.pdf).The time different tasks are in a certain state (running, ready, suspended or waiting) can be evaluated statistically or displayed graphically.This feature requires that the following data accesses are recorded:•All accesses to the status words of all tasks•Accesses to the current task variable (= magic address)Adjust your trace logic to record all data write accesses, or limit the recorded data to the area where all TCBs are located (plus the current task pointer).Example: This script assumes that the TCBs are located in an array named TCB_array and consequently limits the tracing to data write accesses on the TCBs and the task switch.Break.Set Var.RANGE(TCB_array) /Write /TraceDataBreak.Set TASK.CONFIG(magic) /Write /TraceDataT o evaluate the contents of the trace buffer, use these commands:Trace.STATistic.TASKState Display task state statisticTrace.Chart.TASKState Display task state timechartThe start of the recording time, when the calculation doesn’t know which task is running, is calculated as “(unknown)”.Function Runtime StatisticsNOTE:This feature is only available, if your debug environment is able to trace taskswitches (program flow trace is not sufficient). It requires either an on-chip tracelogic that is able to generate task information (eg. data trace), or a softwareinstrumentation feeding one of TRACE32 software based traces (e.g. FDX orLogger). For details, refer to “OS-aware Tracing” (glossary.pdf).All function-related statistic and time chart evaluations can be used with task-specific information. The function timings will be calculated dependent on the task that called this function. T o do this, in addition to the function entries and exits, the task switches must be recorded.T o do a selective recording on task-related function runtimes based on the data accesses, use the following command:; Enable flow trace and accesses to the magic locationBreak.Set TASK.CONFIG(magic) /TraceDataT o do a selective recording on task-related function runtimes, based on the Arm Context ID, use the following command:; Enable flow trace with Arm Context ID (e.g. 32bit)ETM.ContextID 32T o evaluate the contents of the trace buffer, use these commands:Trace.ListNesting Display function nestingTrace.STATistic.Func Display function runtime statisticTrace.STATistic.TREE Display functions as call treeTrace.STATistic.sYmbol /SplitTASK Display flat runtime analysisTrace.Chart.Func Display function timechartTrace.Chart.sYmbol /SplitTASK Display flat runtime timechartThe start of the recording time, when the calculation doesn’t know which task is running, is calculated as “(unknown)”.MTOS-UX specific MenuThe menu file “mtos.men” contains a menu with MTOS-UX specific menu items. Load this menu with the MENU.ReProgram command.Y ou will find a new menu called MTOS-UX.•The item “SYSC Terminal” brigs up a terminal emulation window, which communicates with the preconfigured MTOS-UX system console. The “Break to .SYSD” item initiates a <CTRL-D> keyto the system console and thus starts the MTOS-UX dynamic debugger.•The “Display” Topics launch the kernel resource display windows.•The “Stack Coverage” submenu starts and resets the MTOS-UX specific stack coverage, and provides an easy way to add or remove tasks from the stack coverage window.•The Analyzer->List pull-down menu is changed. Y ou can additionally choose for an analyzer list window showing only task switches (if any) or task switches and defaults.•The “Perf” menu contains the additional submenus for task runtime statistics, task related function runtime statistics and statistics on task states. For the function runtime statistics, aprepare command file called “men_ptfp.cmm” is used. This command file must be adapted toyour application.MTOS-UX CommandsTASK.DispEventDisplay global event flagsDisplays a table with all created global event flag groups.TASK.DispFixedDisplay fixed poolsDisplays a table with all created fixed block memory pools.Format:TASK.DispEventFormat:TASK.DispFixedTASK.DispmBuff Display message buffers Format:TASK.DispmBuffDisplays a table with all created message buffers.TASK.DispMbx Display mailboxes Format:TASK.DispMbxDisplays a table with all created mailboxesTASK.DispPool Display common pools Format:TASK.DispPoolDisplays a table with all created common memory pools.TASK.DispSem Display semaphores Format:TASK.DispSemDisplays a table with all created semaphores.TASK.DispsVar Display shared variables Format:TASK.DispsVarDisplays a table with all created controlled shared variablesTASK.DispTask Display tasks Format:TASK.DispTask [<task>]<task>:<magic_number> | <task_key>Displays a table with all MTOS-UX tasks or one task in detail.Without any parameters, a summary table of all created tasks is shown.The magic number is a unique ID to the OS Awareness to specify a specific task. It is equal to the MTOS-UX task ID. A double click on the magic number or on the key opens the detailed task window. A double click on the entry address or on the pc address opens a Data.List window on this address.If you specify a task magic number or a task key as parameter, this task is shown in detailed. An given task magic number is not checked for validation.TASK.DispTIme Display time & TOD Format:TASK.DispTImeDisplays a window with the milliseconds since MTOS-UX start and with the time-of-day string, reported by MTOS-UX.TASK.DispUnit Display peripheral units Format:TASK.DispUnitDisplays a table with all created peripheral I/O units.TASK.MAP Mapping suggestion Format:TASK.MAPDisplay a mapping suggestion to have dual port access.T o display the MTOS-UX resources in real-time (“On-The-Fly”), emulation memory must be mapped to the MTOS-UX internal tables. If you do not know, where these tables are located (magics!), this command gives you a suggestion, which memory areas to map.While leaving the window open, and creating more objects, the memory usage will be accumulated to the addresses used while running.It is recommended to map more memory than suggested, this increases the chance, that new created object will be in the mapped memory area.MTOS-UX PRACTICE FunctionsThere are special definitions for MTOS-UX specific PRACTICE functions.TASK.CONFIG()OS Awareness configuration information Syntax:TASK.CONFIG(magic | magicsize)Parameter and Description:magic Parameter Type: String (without quotation marks).Returns the magic address, which is the location that contains thecurrently running task (i.e. its task magic number).magicsize Parameter Type: String (without quotation marks).Returns the size of the magic number (1, 2 or 4).Return Value Type: Hex value.。
华为AR100和AR120系列企业路由器数据手册说明书

DatasheetProduct OverviewThe AR100 and AR120 series are fixed interface routers that provide a comprehensive platform for a variety of network topologies, including IMS, NGN, WAN and PSTN. The AR100 and AR120 also employ embedded hardware encryption for security as well as a voice Digital Signal Processor (DSP) for voice services.The AR100 and AR120 series are mature, stable and quiet routers that offer high performance functionality for small networks, enabling small businesses to greatly increase productivity at a lower cost.AR100s and AR120s are easy to deploy, configure and customize, greatly reducing cost of deployment and maintenance, while offering maximum value to customers. These models allow network administrators to expand their networks easily and quickly, saving time and costs. The routers support firewalls, call processing, and application program functionalities.The AR100 and AR120 series includes the following models:●AR109, AR109W, AR109GW-L●AR129CVW, AR129CGVW-L, AR129CVThe specifications for these models are shown in the following table.Table1: AR100 ModelsAR109AR109WAR109GW-LTable2: AR120 ModelsAR129CVAR129CVWAR129CGVW-LProduct Features and BenefitsSmall Size and High Performance●More applications: Huawei series routers use the dual-core processor that isolates the control plane from the forwarding plane and processes more enterprise applications. Huawei series routers improve user experience for multimedia service when streams overlap.●Higher performance: The AR100s and AR120s can process various enterprise applications, and its service processing capability is four times that in the industry.●Greater potential: Huawei series routers provide the capability to migrate services to the 3G and LTE networks.Low Investment with High Returns●Easy to construct: The AR100s and AR120s supports plug-and-play, intelligent configuration, and deployment using the USB flash drive. It can function immediately after being installed. Users do not need to configure an IP address manually. The PPP and VPN indicators show the status of corresponding services. The AR100s and AR120s helps to quickly construct an enterprise IT network.●Simplified solution: Huawei provides an all-around solution that integrates the routing, switching, voice, security, and wireless services. Customers can customize solutions as required.●Easy to expand: Huawei series routers have four/eight FE/GE ports, can access more employee for small enterprises. The two uplink WAN ports implement load balancing and link protection, maximizing the return on investments.Small footprint on a Comprehensive Platform●Maturity and Stableness: The AR100s and AR120s uses the Huawei VRP operating system and VSP voice platform. In addition, the AR100s and AR120s uses modularized hardware design, which brings good user experience.●Low-noise office: Huawei series routers have no fan, which brings low noise and good user experience.●Secure environment: The lightning failure rate of AR100s and AR120s is only 3% of industry average. The AR100s and AR120s can be applied in the harsh environment.Sample DeploymentsWAN AccessExample deployment in branch networks for WAN access. In this example, the AR100s and AR120s function as the egress routers on enterprise branch networks and provide multiple access methods, including Ethernet, xDSL, 3G, LTE and WLAN. Enterprise Voice Services DeploymentIP PBX with WAN and PSTN AccessThis illustration shows AR120 series router deployed at an enterprise branch with access to a WAN and a PSTN. If a fault occurs on the WAN, the PSTN acts as a backup to the WAN and ensures that call services remain uninterrupted. AR120s are deployed at enterprise branch offices to provide intelligent, integrated dialing across the network. When deployed as voice service gateways, AR120s can function as IP PBX boxes and SIP access gateways.IP PBX.AR120s have a built-in PBX, which supports the enterprise main number, interactive voice response (IVR), and billing query functions. These features help enhance the corporate image of small businesses by allowing them to look more professional to their customers, while simultaneously improving the efficiency of their enterprise communications.SIP Server.AR120s have a built-in SIP server that ensures reliability of voice services. If the SIP server at the headquarters office becomes unreachable, the local built-in SIP server at the branch office ensures that communication remains uninterrupted between branch offices and the PSTN network.SIP Access GatewayThe AR120 series routers provide integrated voice, fax, and IP services. The AR120s can function as SIP access gateways for enterprise branch offices that transform traditional phone signals into Voice over IP (VoIP). Typically, AR120s are connected upstream from the IMS and NGN networks to enable anytime voice communication on any media, such as phones, handsets, and computers.VPN Deployment for Secure Enterprise CommunicationsVPNs Connecting Branches and Partners to HeadquartersThis illustration shows how to deploy AR100s and AR120s using VPNs to connect branches and partners to headquarters.AR100s and AR120s provide various VPN tunnel protocols to ensure secure communications between:∙Enterprise branches and other branch offices∙Enterprise branches and headquarters∙Partners and enterprise resourcesAR100s and AR120s support the following VPN tunnel protocols:∙GRE VPN∙IPSEC VPN∙DSVPNL2TP VPNAR100s and AR120s support fast tunnel set-up and authentication.Wireless Access and Management in Branch3G/LTE and Wi-Fi Wireless Access applicationThe AR100s, AR120s routers complied with 3G and LTE standards including HSPA+ and FDD LTE, meeting the wireless communication requirements between branches and the headquarters. In addition, the 3G or LTE data link can be used as a backup for wired link to protect the xDSL, FE/GE uplinks. The backup link improves network stability and reduces network construction costs.Some models of AR100s, AR120s routers are dual SIM devices, providing dual SIM standby. The customers can switch the SIM card manually according to 3G/LTE network standards. In addition, the device can switch to the backup SIM card when signal is weak to avoid link interruption.The AR100s, AR120s routers integrated WLAN wireless access capabilities, support 802.11a/b/g/n standard communication, Built-in AC function make the deployment and management more conveniently. Its wireless features can meet users’ demand for wireless access, and help enterprises to build a branch network flexibly.Wireless AC Management applicationThe AR120s routers integrated AC (Access Controller, a wireless controller) functionality, which can manage the wireless AP (Access Point) in wireless LAN. AR supported rich certification and flexible user access control, which can provide security access guarantee for Wi-Fi users. The rich wireless capabilities integrated in one device, this can realize centralized management of wired and wireless network, meet the customers’ requirements of building different scale enterprises networks.Technical Specifications Table 1: AR100s Technical SpecificationsTable 2: AR120s Technical SpecificationsThis content is applicable only to regions outside mainland China. Huawei reserves the right to interpret this content.*** Note: Service performance depending on specific feature configuration.****Note: When the altitude is between 1800 m and 5000 m, the highest operating temperature reduces by 1°C every time the altitude increases by 220 m.Ordering InformationThe AR100, AR120 series routers are configured by selecting and installing the appropriate configuration module. The configuration module ordering information and descriptions are shown in the following table1-3.Table 1: Chassis OptionsTable 2: Power Module OptionsTable 3: SD Card and USB Disk OptionsHUAWEI AR100 and AR120 Series Enterprise RoutersDatasheetCopyright © Huawei Technologies Co., Ltd. 2019. All rights reserved.No part of this document may be reproduced or transmitted in any form or by any means without priorwritten consent of Huawei Technologies Co., Ltd.Trademarks and Permissionsand other Huawei trademarks are trademarks of Huawei Technologies Co., Ltd.All other trademarks and trade names mentioned in this document are the property of their respectiveholders.NoticeThe purchased products, services and features are stipulated by the contract made between Huaweiand the customer. All or part of the products, services and features described in this document may notbe within the purchase scope or the usage scope. Unless otherwise specified in the contract, allstatements, information, and recommendations in this document are provided "AS IS" withoutwarranties, guarantees or representations of any kind, either express or implied.The information in this document is subject to change without notice. Every effort has been made in thepreparation of this document to ensure accuracy of the contents, but all statements, information, andrecommendations in this document do not constitute a warranty of any kind, express or implied. Huawei Technologies Co., Ltd. Address: Huawei Industrial Base Bantian, Longgang Shenzhen 518129 People's Republic of China Website: 。
诺瓦科技无线LED控制卡LED多媒体播放器TB2详细参数说明书
Trademark
is a trademark of Xi’an NovaStar Tech Co., Ltd.
Statement
You are welcome to use the product of Xi’an NovaStar Tech Co., Ltd. (hereinafter referred to as NovaStar). This document is intended to help you understand and use the product. For accuracy and reliability, NovaStar may make improvements and/or changes to this document at any time and without notice. If you experience any problems in use or have any suggestions, please contact us via contact info given in document. We will do our best to solve any issues, as well as evaluate and implement any suggestions.
4 Software Structure ........................................................................................................................ 8
4.1 System Software .......................................................................................................................................... 8 4.2 Related Configuration Software ................................................................................................................... 8
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
A Dual-Processor Solution for the MAC Layer of a SoftwareDefined Radio TerminalHyunseok Lee,Trevor MudgeAdvanced Computer Architecture LaboratoryDepartment of Electrical Engineering and Computer ScienceUniversity of Michigan{leehzz,tnm}@ABSTRACTConsiderable work has been devoted to studyingflexible computation structures for the physical layer of a software defined radio(SDR)terminal.However there has been al-most no research on protocol processors for the upper layer protocols such as the media access control(MAC)and link protocol.A general purpose processor(GPP)is sufficient for the protocol processing of a single mode terminal.How-ever,in the case of a multi-mode system required for SDR, there is a very wide set of possibilities for the MAC layer.In principle these too could be handled by a GPP.However, we show that a better solution is to use a GPP augmented by a small supplemental processor.The GPP is responsi-ble for the relatively complex protocol operations in the ac-tive mode,and the supplemental processor handles the idle mode operations.This separation of responsibilities simpli-fies the implementation of hard real-time responses required by some protocols(for example IEEE802.11),while main-taining the programmability needed to handle a wide rangeof protocols.In addition,this organization allows a signif-icant power savings in the idle mode.This is important because the protocol processor must process a large num-ber of tiny idle mode tasks whose aggregate effect over time dominates the power consumption in a wireless terminal.As part of our study we develop a hardware model of the supplemental processor in Verilog and its software model in ing commercial CAD tools we synthesized out design and evaluated the power consumption and response time of the platform.Our results show that the proposed platform meets the real-time deadlines at low power while maintain-ing programmability.Categories and Subject DescriptorsC.1.4[Processor Architectures]:Other Architecture Styles–Mobile processorsPermission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on thefirst page.To copy otherwise,to republish,to post on servers or to redistribute to lists,requires prior specific permission and/or a fee.CASES’05,September24–27,2005,San Francisco,California,USA. Copyright2005ACM1-59593-149-X/05/0009...$5.00.General TermsDesign,PerformanceKeywordsWireless platform,SDR terminal,Protocol processing1.INTRODUCTIONSoftware defined radio(SDR)is a wireless communication system whose function blocks are implemented by software routines so that various wireless protocols can easily be sup-ported by simple software changes.The concept of SDR originated in the military,but now it is emerging as im-portant commercial technology.For instance,4G,the next generation of wireless communication systems requires that multiple wireless protocols be supported[15].Although the concept of SDR is very attractive,there are many obstacles on the way to its commercialization;the particularly power consumption.There has been a lot of research effort on the physical layer but there has been almost no research on protocol proces-sors executing upper layer protocols.In the past this was implemented on aflexible general purpose processor(GPP) for single mode terminals.In this paper,we analyze the im-pact of multiple wireless protocols on the architecture of the protocol processor and propose a dual-processor hardware solution.To derive the requirements of the protocol processor we analyzed a collection of differnt wireless communication stan-dards including Bluetooth,IEEE802.11a/b/g,GSM,IS-95, IS-2000,and W-CDMA.One important requirement is the need for a tight response time of10us in the case of the IEEE 802.11protocol.Fast response time is needed because the whole channel is occupied by a terminal when it is generatinga response message.Thus,the protocol processor must re-spond quickly in order to maximize channel throughput.In addition,as explained in Section3.2,wireless terminals per-form many operations even during idle periods.A common characteristic of these idle period operations is a light work-load-a simplefield matching in most cases.Although the power consumption of each idle operation is very small,the aggregated idle power becomes dominant because a wireless terminal is idle most of the time.As shown in Figure1,we propose a heterogeneous dual-processor architecture consisting of a conventional main proces-sor and a simple supplemental processor.The main proces-sor provides the processing power needed for heavily loadedFigure1:Proposed hardware platform for upper layer protocol processing in an SDR terminalactive state protocol operations,whereas the supplemental processor provides an adequate but power efficient process-ing capability for the idle mode.As we will show in Section4.1,other candidate platforms employing a single GPP ora GPP plus ASICs have problems with scheduling or pro-grammability.The reason for using a GPP with minimal functionality as the supplemental processor is to achieve programming flexibility.However a GPP is power inefficient and slower than an ASIC solution.To see how these points impact the system we develop both hardware and software models for the supplemental processor and evaluate it with commercial CAD tools.The evaluation results are presented in Sec-tion5.They show that the supplemental processor provides flexibility with very little power overhead.The use of multiprocessor architectures for power reduc-tion purposes is not new.The paper by Olsen showed that a heterogeneous multiprocessor architecture is power effi-cient for hand held devices such as a personal data assis-tant(PDA),because it allows the user idle period to be efficiently managed[14].The paper by Kumar showed that a heterogeneous multiprocessor with a single instruction set architecture(ISA)is also power efficient even for general applications[9].The contribution of our study is to apply the heterogeneous multiprocessor concept to SDR for the upper layer protocol processing.There have been several studies on small microprocessors that consume less than1 mW power employing asynchronous logic or sub-threshold circuits[7][12].However,in this work we implement the supplemental processor using a conventional designflow,be-cause results in Section5.5show that any additional power gain will not be significant.2.OVERVIEW2.1Wireless Communication Networks Roughly speaking it is possible to classify wireless com-munication systems into three types:wireless personal area networks(WPAN),wireless local area networks(WLAN), and wireless wide area networks(WWAN).The WPAN sys-tem enables users to connect to various personal devices over short distances without wires.An application might be syn-chronizing data between a PDA and a desktop computer. Bluetooth is the most popular system at the moment. WLAN systems originated from wired LAN systems.They aim to replace existing wired LANs by high speed wireless channels.A typical terminal in this network is a laptop hav-ing wireless access.IEEE802.11a/b/g systems are the most widely used WLAN systems.Finally WWAN systems evolved from a telephone net-work.The early generation of WWAN systems such as AMPS,GSM,and IS-95provide voice service without spa-tial limitations.The3rd generation systems provide mul-timedia services like video telephony on wireless channels. The CDMA-2000and W-CDMA systems are common ex-ample.In the future,we will need terminals that simultaneously support many of the above protocols to seamless span WPANs, WLANs,WWANs,plus their future derivatives.2.2Wireless Protocol StackWe can divide the wireless protocol stacks into two cat-egories by workload characteristics:the physical layer and the upper layers.The physical layer consists of various real-time and computation intensive operations such as forward error correction and modulation.Due to the tight power budget and high computation requirements it is common to implement the physical layer in ASICs.In contrast the upper layer protocols consist of various control intensive operations such as media access control,re-transmission of corrupted frames,terminal mobility support, and radio resource control.Thus the upper layer protocols are implemented on a GPP except for some hard realtime operations such as MAC response generation and encryp-tion/decryption.Although both physical and upper layers are within the scope of SDR,we only focus on upper layer protocol process-ing in this paper.2.3SDR terminalConverging the features of several single mode terminals into one SDR terminal allows us more convenient wireless network access.For instance,we commonly use both cellu-lar phone and wireless LAN card.A cellular phone provides a low speed but seamless wireless connection whereas a wire-less LAN card provides a high speed Internet connection at limited area.The SDR technology enables us to adaptively select optimal network according to environment. Furthermore there exist several different wireless protocols even for almost identical services,for example W-CDMA and cdma2000.Some countries deploy the W-CDMA sys-tem for wireless multimedia service and other countries do cdma2000.The SDR allows international roaming with one terminal.3.SYSTEM REQUIREMENTS3.1Hard Realtime ResponseSourceTerminalDestinationTerminalFigure2:Data transmission procedure for IEEE 802.11networksPICH PCHSignal from basestation to terminalsTerminal1No paging message to terminal 1 There is a paging message to terminal 1 Figure 3:Paging Procedure of cdma2000and W-CDMA networksThe IEEE 802.11network differs from other wireless net-works in having short intervals between control packets as part of the data transmission.As shown in Figure 2,the transmitter and receiver exchange the request to send (RTS)and clear to send (CTS)MAC control packets prior to data transmission.This reserves a wireless channel,and the re-ceiver transmits an acknowledge (ACK)packet after data transmission to release the wireless channel.Because the re-served link cannot be used by other terminals while prepar-ing a MAC response,the IEEE 802.11protocol requires a very fast MAC response in order to maximize network throughput.For the MAC response generation,we need to analyze the header of the received MAC packet after decryp-tion.3.2Processing Tiny Operations3.2.1Paging in cdma200and W-CDMAPaging is a procedure whereby a network identifies the base-stations having the best wireless paths to a destina-tion terminal before establishing a user session.A terminal must be in its ready state to receive paging messages from base-stations during idle mode.WWAN networks have a two phase paging procedure so as to minimize the power consumed for paging message reception.In phase one,ter-minals periodically wake-up and decode the paging indica-tion channel (PICH)that carries simple on/offinformation indicating the existence of a paging message in the following paging channel (PCH)slot.The bits on the PICH are not protected by a forward error correction scheme such as a convolutional code.The reason for using an uncoded chan-nel is to save power by powering offerror correction,because it is one of the most power consuming blocks in a wireless terminal.In phase two,the terminals that have detected the transmission of a paging message through decoding the PICH start decoding the PCH with full functionality includ-ing error correction.In Figure 3,the first PICH bits indicate that there is no paging message in the following PCH slot,so the termi-nal turns of its receiver to save power.However the second PICH indicates that a paging message will be transmitted in the following PCH slot.Thus the terminal starts PCH de-coding.Although PCH decoding is a small task,the proto-col processor must be activated,because the paging message includes upper layer information.3.2.2Location Update in cdma2000and W-CDMADuring the idle mode,the terminals of a WWAN can drift in any direction.If there is no rough estimation of a termi-ATIM windowATIM windowTerminal 1Terminal 2Terminal 3Figure 4:Power management procedure of IEEE 802.11networknal location,a network needs to broadcast a paging mes-sage on the entire network.This is inefficient and avoided by a location update procedure.Several base stations logi-cally comprise a location update area.Whenever a terminal passes the boundary of a location update area,it sends a lo-cation update message to the base-stations in order to notify that it is moving to an adjacent location update area.Thus the network can limit the broadcasting range of a paging message to within the current location update area.3.2.3Power Management Procedures in IEEE 802.11NetworkIn an IEEE 802.11network,packet transmission is only allowed during the ad hoc network indication map (ATIM)windows.This restriction is to minimize terminal power consumption during the idle periods between packet bursts.As show in Figure 4,all terminals simultaneously wake up in ATIM windows.The terminals that have buffered traffic exchange ATIM request and ACK messages with the desti-nation terminals,so that the destination terminals remain awake in the following idle period.In the interval between ATIM windows,source and destination terminals perform actual traffic transmission while the remaining terminals turn offtheir receivers to save power.To decode the ATIM packet,the MAC layer and the encryption engine must be involved.3.2.4Operation StatesWWAN and WPAN networks have several operation states for terminal power saving and better radio resource uti-lization.Busy periods,short idle periods,and long idle periods between packet arrivals are mapped on different operation states that have different power and radio re-source overhead requirements.A W-CDMA network has Cell DCH,Cell FACH,Cell PCH,and URA PCH states,and a CDMA-2000network has Active,Control Hold,Sus-pended and Dormant states.Similarly Bluetooth has Ac-tive,Sniff,Hold and Park states.Among the above states,Cell PCH,URA PCH,Suspended,Dormant,Sniffand Park states are defined for idle period handling.They should be low power state.In these states the terminal performs vari-ous operations based on simple field matching.(a) (b) (c)Figure 5:Candidate platforms for the protocol processor of an SDR terminal4.PLATFORM DESIGN 4.1Platform ComparisonFor multiple wireless protocol processing we can consider three types of processor platforms:1)a single GPP;2)a GPP with ASICs;and 3)two or more GPP cores.The sin-gle GPP based platform,shown in Figure 5(a),provides the highest level of flexibility but has a scheduling problem.As we saw in Section 3.1,the protocol processor must generate a MAC response message within 10usec in order to support the IEEE 802.11protocol.In addition generally it is nec-essary to use a realtime operating system (RTOS)to cope with the algorithm complexity of the upper layer protocols.However,RTOSs are not able to context switch that fast e.g.uClinux,a Linux based RTOS,requires more than 10usec [5].This rules out organization (a).Another candidate platform is shown in Figure 5(b).A GPP is assisted by ASICs that cover idle periods and re-altime operations.Many commercial IEEE 802.11modems are based on this architecture to satisfy hard realtime re-sponse requirement [11][4][8].The GPP can be scheduled ef-ficiently because the ASICs take over the burden of hard re-altime MAC protocol processing,and ASICs are also power efficient.However,it is difficult to accommodate future pro-tocol extensions with this architecture,because of the hard-wired nature of ASICs.As an alternative to either of these extremes,we propose the dual-processor platform shown in Figure 5(c).Because both processors are programmable,they provide a high de-gree of flexibility.Two processors can be schedule inde-pendently by a task partitioning:complex tasks requiring an RTOS on the main processor,and simple hard realtime tasks on the supplemental processor.The simple tasks on the supplemental processor can be programmed without an RTOS.It allows us to meet the requirement of hard realtime response.As we will see in Section 5.5,the power consump-tion of the supplemental processor is almost as low as an ASIC without sacrificing flexibility.4.2Task PartitioningIn this subsection we explore the task partitioning and its mapping to the hardware.Two major issues of the task partitioning are the number of tasks mapped onto the sup-plemental processor and the complexity of the interface be-tween two processors.In this paper we propose assigning only idle period tasks and hard realtime tasks to the sup-Figure 6:Proposed dual-processor platform for the protocol processor of an SDR terminalplemental processor.This assignment minimizes power and simplifies the interface between the two processors.The number of tasks that can be placed onto the supplemental processor is limited by the hard realtime scheduling require-ments.If complex algorithms are mapped onto the supple-mental processor,it becomes difficult to program without the assistance of an RTOS.As we discussed in Section 4.1,it is impossible to meet the response time requirements if we use an RTOS.In addition,the heavy workload would result in complex hardware and raise power overhead during idle period oper-ations.The interface between two processors remains sim-ple only if we map idle mode tasks onto the supplemental processor.Most idle period tasks discussed in the previous section are essentially just a simple field match except for the IEEE 802.11networks where additional decryption of packets may be required.Therefore the length of the data needed for this field matching is less than packet header size -smaller than several tens of bytes in wireless communica-tions.The supplemental processor’s program can thus be very simple and does not require the support of an RTOS.4.3Proposed Platform4.3.1Main ProcessorThe data rate of applications executed on the main proces-sor varies widely from voice at 9.6Kbps to packet data at several Mbps.To support such widely differing date rates with minimum power consumption,dynamic voltage scal-ing (DVS)and dynamic frequency scaling (DFS)techniques are essential for the main processor.The quality of service (QoS)parameters,determined at an initial session setup,can be used to indicate voltage and frequency scaling.For example,information that an established session has a con-stant bit rate permits aggressive processor scheduling with-out any slack.At short idle periods between packet bursts,a clock gating technique can be applied instead of DVS or DFS.Because the supplemental processor covers long idle periods the main processor has no need for leakage current reduction schemes such as adaptive body biasing -it can simply be shut off.This simplifies the main processor if it has a supplemental processor compared to the typical low power GPP for other portable devices [13][6].4.3.2Supplemental ProcessorThe simplicity of tasks performed on the supplemental processor allows us to minimize its functionality.The in-struction set of this processor consists only of the essential instructions required to perform small control actions like paging message decoding.The width of the datapath needs to be32bit for fast packet processing.However,we used a processor model with an8bit datapath for our experiments because it was difficult tofind a small32bit commercial model with a complete programming environment.In Sec-tion5.3.2,we will show how a32bit datapath yields better power performance than an8bit datapath.Thus our power studies using a8bit processor are a worst case.The supplemental processor requires a timer to generate events because many operations in wireless protocols are timer based.The timer events are processed by interrupt handling logic.The supplemental processor has two inter-rupt ports,one for an interrupt from the baseband modem indicating the arrival of a new packet,and another port for an interrupt from the timer.A clock gating technique is used in the supplemental processor to reduce the power dis-sipation during idle periods between interrupt events.The timer,interrupt handling logic,and clock gating provide an efficient implementation method for event driven applica-tions.In addition,the supplemental processor is equipped with a hardware comparator.The hardware comparator is de-signed for thefield matching operation that the supplemen-tal processor is frequently called on to perform.The supplemental processor needs a hardware random number generator(RNG)that is used for a random back-offoperation performed in the MAC layer.The execution time of a software based RNG is too long to meet the tim-ing requirements.The randomness required for the back-offoperation need not be of a high quality,so a linear feed-back shift register(LFSR)is adequate.However we need to consider the impact of the initial seed of the LFSR.The initial value of aflip-flop is not random because small dif-ferences in the size of the transistors in aflip-flop lead to bias.This in turn can induce a load sharing problem in the ad hoc mode of the IEEE802.11network.The overhead of periodic beacon packet transmission is unevenly distributed if we use a LFSR without a proper random seed.To avoid such a situation we place a direct access path so that the power manager can load the initial seed into the LFSR. 4.3.3MemoriesAs shown in Figure6,the memory in our platform can be classified into three types,program memory,state mem-ory,and data memory.The program memory stores the execution code of the processors.The program memory of the supplemental processor is accessed by both the main and supplemental processor.The main processor loads the execution program of the supplemental processor prior to activating it.A single port SRAM is used for the program memories of both processors.Meanwhile the state memory stores protocol state infor-mation such as a terminal identifier and the QoS parameters of established sessions.When supporting the IEEE802.11 protocol,both the main and supplemental processor need to be activated at the same time and simultaneously access the state memory.Thus a dual port memory is used for the state memory.The size of this memory varies according to the protocol.However,because the supplemental processor needs just a small portion of the state information,the size of the state memory need not exceed several hundred bytes.BasebandmodemSupplemetnalprocessorMainprocessorTimeFigure7:Packet reception procedure while execut-ing the IEEE802.11protocolThe data memory stores user traffic processed by the pro-tocol layers.The baseband modem stores packets which are received from antenna at the data memory of the supple-mental processor.The processed packet is passed to the main processor by memory copy to the data memory of the main processor.For transmission,packets are copied in the reverse direction.4.3.4Power ManagerA power manager controls the power state of all blocks in a wireless terminal.Therefore,it is always powered even at idle periods.It has a timer to trigger a periodic wake-up event.There are three input ports in the power manager. One input port from the main processor is used to config-ure the operation mode of the power manager according to the operating state change of a protocol.Another input port is assigned to the supplemental processor.Through this port,a request for the activation of the main proces-sor is transmitted when the supplemental processor receives a communication request.The third port is connected to the baseband modem.If the baseband modem detects a signal on a PICH,it requests activation of the supplemen-tal processor for PCH decoding through the third interrupt port.4.4Application ExamplesBecause the protocol processor discussed in this paper aims to support multiple wireless protocols,its operation procedure changes according to the type of protocol loaded onto the platform.Figure7shows the interaction between the main processor and the supplemental processor when the IEEE802.11protocol is loaded onto the protocol processor. The operation procedure shown in Figure7is when the data packet matches with the terminal’s address.When this oc-curs the supplemental processor assists the main processor by independently generating MAC response messages dur-ing the data reception procedure.Figure8shows the paging procedure when the W-CDMA protocol is loaded onto the platform.The operation proce-dure shown in Figure8is when the destination of the paging message matches with the terminal.After periodically be-ing activated by the power manager,the baseband modem wakes up the supplemental processor if the PICH bits in-dicate there will be a paging message on the PCH channel. Only the supplemental processor is activated while decoding a paging message.The main processor is not activated un-Baseband modem Power manager Main processorSupplemental processor Figure 8:Paging message reception procedure while executing the W-CDMA protocoltil the supplemental processor decodes the paging message completely.5.EXPERIMENT AND ANALYSIS 5.1Models for Experiment5.1.1Main ProcessorAs our main processor model we used the OPENRISC1200,a 32bit open source RISC processor [3].The features of OPENRISC are very similar to other commercial GPPs used in mobile devices except that it does not support power re-duction techniques like DVS,DFS,and clock gating.How-ever,this is not important because this model is only used for wake-up power measurement,where these techniques are not involved.We don’t measure the dynamic power of the main processor,because it consumes far more power than the supplemental processor.The features of our HDL model for the main processor are as follows.•32bit RISC processor•Single issue 5-stage pipeline in-order machine •Harvard architecture •32bit Hardware Multiplier •8K data cache with MMU •8K instruction cache with MMU5.1.2Supplemental ProcessorAlthough we will show that a 32bit processor is optimal for the supplemental processor in Section 5.2.2,we take as a base the architecture of a commercial 8bit processor,Mi-crochip’s 16F84,in order to develop a power model of the supplemental processor [1].It is used for a sensor network node that has similar requirements.We added a RNG,a hardware comparator,and a data memory interface for fast packet processing.Figure 9shows the architecture of the supplemental processor model.The detailed configuration of the supplemental processor is as follows.•8bit RISC architecture•Single issue 2-stage pipeline in-order machine •Harvard architecture•33instructions •68x 8bit registers•Hardware timer,interrupt handler,and clock gating •Hardware random number generator•Interface to data memory •Hardware 48bit comparator •4K x 14bit program memory •4K x 8bit dual-port state memory5.1.3Application SoftwareFor this study we selected the power managment proce-dures for the IEEE 802.11protocol,which is depicted in Figure 4,as the application model for our dynamic power measurements.This procedure was selected because it is currently one of the most complex and time constrained ap-plications for packet reception.The IEEE 802.11application model is divided into two parts:an interrupt service routine and the main routine.In order to avoid an event loss,the interrupt service rou-tine performs only a minimal number of operations such as hardware re-initialization.The main routine consists of an infinite loop.At the beginning of each iteration,the main routine checks the event flags.If there are no events,the main routine enters a clock-gated mode to save power by executing sleep instructions.If an interrupt is generated by the timer or the baseband modem,the main routine acti-vates the clock signal and checks the event flags to identify the interrupt source.In the event of a packet reception,the main routine loads the packet header into the hardware comparator to analyze whether the packet matches with the terminal’s address or the broadcast address.If the packet matches and is valid,the main routine performs the ap-propriate actions like generating a response message and informing the main processor of a packet reception.5.2Dynamic PowerDynamic power is only consumed during instruction exe-cution.To measure it we synthesized our hardware model using Synopsys’Design Compiler and extracted power re-sults with PrimePower.Memory was created with Artisan’s memory compiler.Figure 10shows the experiment flow used for dynamic power measurement.We did not consider the power consumption due to interconnection wire because gen-erally it is not dominating factor at 0.18u technology which we used for the experiment.5.2.1Power Consumption Profile of the Supplemen-tal ProcessorFigure 11shows the power consumption profile of the sup-plemental processor when it executes the software model outlined at Section 5.1.3.We see that the blocks that con-sume the most powers in the supplemental processor are the timer and the program memory.The timer is power hun-gry because it has to continuously monitor when to wake-up.Reducing power consumption of the timer will have a notice-able impact on the supplemental processor’s dynamic power.In addition,its program memory consumes a large fraction of power because it is relatively large compared to other blocks on the supplemental processor.Thus it is important。
