Formal Verification of MIX Programs
形式化验证讲义

形式化求精
形式化求精是Carroll Morgan(现为新南威尔士大学教授) 在1990年提出来的,最初是基于程序设计的概念,但在之 后逐步发展为一种通用的设计理论,也就是逐步细化的方 式。
形式化求精是将自动推理和形式化方法相结合而形成的一 门新技术,它研究从抽象的形式规格推演出具体的面向计 算机的程序代码的全过程。
立的层次或部分,封装并提供清晰接口。如系统开发 的层次模型,模块化技术,面向对象的技术等; 研究有效的程序开发模型及支持技术,设法屏蔽软件 开发中的难点、解决共性问题。如图形用户界面技术, 客户端-服务器模型,中间件技术,Web服务模型等;
软件问题的应对(2)
研究各种构件形式,以利用已有的开发成果,提高开发 层次,降低开发代价:子程序库、类库、组件库等;
20世纪80年代,在硬件设计领域形式化方法的工业应用结 果,掀起了软件形式化开发方法的学术研究和工业应用的 热 潮 , Pnueli 提 出 了 反 应 式 系 统 规 格 和 验 证 的 时 态 逻 辑 (temporal logic,简称TL)方法,Clarke和Emerson提出了 有穷状态并发系统的模型检验(model checking)方法;
是否一致并完整,有无矛盾或遗漏?找出并更正其中的错误 和缺陷;
运行中是否会出现不能容忍的状态(死锁、活锁等)。
系统集成项目管理工程师考试题及参考答案

系统集成项目管理工程师考试题及参考答案一、单选题(共100题,每题1分,共100分)1.项目经理编制了一份项目沟通计划。
其主要内容包括项目干系人要求、发布信息的描述、传达信息所需的技术方法和沟通频次。
这份计划中还欠缺的最主要内容是()。
A、沟通计划检查要求B、干系人分析C、信息接收的个人和组织D、沟通备忘录正确答案:C2.()can be considered as part of risk mitigation.A、Risk identificationB、Purchasing insuranceC、Assessment of outcomesD、Assessment of probabilities正确答案:D3.云计算中心提供的虚拟主机和存储服务属于()。
A、DaaSB、PaaSC、SaaSD、IaaS正确答案:D4.()不属于实施已批准变更的活动A、预防措施B、缺陷补救C、纠正措施D、影响分析正确答案:D5.人们对风险事件都有一定的承受能力,当()时,人们愿意承担的风险越大。
A、个人、组织拥有的资源越少B、项目的收益越大C、组织中高级别管理人员相对较少D、项目活动投入的越多正确答案:B6.生产过程中,需要通过统计返工和废品的比率来进行质量管理,这种方法在质量管理中属于( ) 。
A、标杆对照B、抽样统计C、质量成本法D、实验设计正确答案:D7.为了保护计算机机房及其设备的安全,()做法是不合适的。
A、机房地板的阻止应控制在不易产生静电的范围B、机房隔壁为卫生间或水房,一旦发生火灾便于取水灭火C、机房的供电系统应将计算机系统供电与其他供电分开D、机房设备应具有明显的且无法去除的标记,以防更换和便于追查正确答案:B8.针对信息系统审计流程,在了解内部控制结构、评价控制风险、传输内部控制后,下一步应当进行()。
A、内部控制测试B、有限的实质性测试C、外部控制测试D、扩大的实质性测试正确答案:A9.沟通管理计划的编制是确定()的过程,即明确谁需要何种信息,何时需要以及如何向他们传递。
认识形式化验证

认识形式化验证 软件开发中⼀般使⽤“测试”来找bug,这种⽅法只能找到bug,不能证明程序没有bug。
形式化验证是⽤逻辑来验证程序的可靠性,就是把⼀段程序⽤逻辑的⽅法证明⼀遍,证明它能得到预期的结果,没有bug。
⼀般这类研究主要应⽤于昂贵的航天器材的操作系统、危险的医疗设备的程序之中。
因为航天器材、医疗设备牵扯到⼈的⽣命,如果操作系统出现错误,那么很危险,⼜不能⽤测试⼀遍⼀遍的测,所以⽤形式化验证来做。
⽐如美国航天局NASA就会雇佣⼤批形式化验证的专家来验证他们操作系统的正确性。
学习这个⽅向,最好有⽐较好的逻辑知识(数理逻辑、拉姆达验算),最好⽐较了解程序(⽐如操作系统的设计、编译器的设计等)。
这个⽅向是⽐较犀利的研究⽅向,但不⼤容易出论⽂,需要长时间积累才能发⼀篇好论⽂。
这个⽅向只是科研⽅向,不适合找⼯作,如果你读完硕⼠打算找⼯作⽽不做研究,这个⽅向不适合。
因为企业没⼈⽤形式化验证来验证程序。
Formal Verification(形式验证) 在计算机硬件(特别是集成电路)和软件系统的设计过程中,形式验证的含义是根据某个或某些形式规范或属性,使⽤数学的⽅法证明其正确性或⾮正确性。
形式验证是⼀个系统性的过程,将使⽤数学推理来验证设计意图(指标)在实现(RTL)中是否得以贯彻。
形式验证可以克服所有3种仿真挑战,由于形式验证能够从算法上穷尽检查所有随时间可能变化的输进值。
形式验证形式验证的出现 由于仿真对于超⼤规模设计来说太耗费时间,形式验证就出现了。
当确认设计的功能仿真是正确的以后,设计实现的每⼀个步骤的结果都可以与上个步骤的结果做形式⽐较,也就是等价检查,如果⼀致就说明设计合理,不必进⾏仿真了。
形式验证主要是进⾏逻辑形式和功能的⼀致性⽐较,是靠⼯具⾃⼰来完成,⽆需开发测试向量。
⽽且由于实现的每个步骤之间逻辑结构变化都不是很⼤,所有逻辑的形式⽐较会⾮常快。
这⽐仿真的时间要少很多。
⼀般要做形式验证的步骤有:RTL和RTL。
持续工艺确认怎么做?——方法,和其与产品年度回顾的区别

持续工艺确认怎么做?——方法,和其与产品年度回顾的区别持续工艺确认(CPV,Continuous Process Verification)概念最早见于ICH Q8,连同生命周期、QBD(质量源于设计,重点词汇:设计空间)概念一并提出。
后在FDA制药工艺行业指南2011年版作了进一步的要求。
现欧盟GMP附录15《确认与验证》及中国GMP附件《确认与验证》已对它作出了一些要求。
但是具体的如何实施并未给出。
目前整个行业内大部分制药企业也在摸索和观望阶段。
本文介绍了持续工艺确认(CPV,Continuous Process Verification)的基本方法,以及它与产品年度回顾的区别。
供大家参考。
CPV 的方法CPV can usein-line,on-line or at-linemonitoring or controls to evaluate processperformance. These are based on product and process knowledge andunderstanding. Monitoring can also be combined with feedback loops to adjustthe process to maintain output quality. This capability also provides theadvantage of enhanced assurance of intra-batch uniformity, fundamental to theobjectives of process validation. Some process measurements and controls insupport of real-time release testing (RTRT) can also play a role in CPV.CPV可以使用在位,在线或近线监测和控制来评价工艺性能。
合同翻译(一)

合同翻译(一)英文合同翻译的用词特点:合同英语的用词极其考究,具有特定性.要求选词专业化(professional)、正式(formal)、准确(accurate)。
具体体现在下列方面:1.使用情态动词:在合同中使用may,shall, must,may not (或shall not)时要极其谨慎。
权利义务的约定部分构成了合同的主体,这几个词如选用不当,可能会引起纠纷.may旨在约定当事人的权利(可以做什么),shall约定当事人的义务(应当做什么时候),must用于强制性义务(必须做什么),may not (或shall not)用于禁止性义务(不得做什么)。
may do不能说成can do,shall do不能说成should do 或ought to do,may not do,在美国一些法律文件里可以用shall not,但绝不能用can not do或must not。
例如,在约定解决争议的途径时,可以说:The parties hereto shall,first of all,settle any dispute arising from or in connection with the contract by friendly negotiations。
Should such negotiations fail,such dispute may be referred to the People’s Court having jurisdiction onsuch dispute for settlement in the absence of any arbitration clause in the disputed contract or in default of agreement reached after such dispute occurs.本句中的shall和may表达准确.出现争议后应当先行协商,所以采用了义务性“约定",如果协商解决不了,作为当事人的权利,用选择性约定may 也很妥当.如果may和shall调换位置会怎么样?前半句的shall 换用may后,意思变成了当事人可以通过协商解决,意思上说得过去,但后半句的may换用shall后,变成了应当诉讼解决,好像一出事,就要先见官,这就有些不友好了。
英语作文-集成电路设计行业:从初学者到专家的必备技能

英语作文-集成电路设计行业:从初学者到专家的必备技能Integrated Circuit Design Industry: Essential Skills from Beginner to Expert。
Introduction:The integrated circuit (IC) design industry plays a crucial role in the development of modern technology. From smartphones to self-driving cars, ICs are the backbone of electronic devices. To excel in this industry, individuals need to acquire a set of essential skills that will take them from being a beginner to an expert. This article aims to provide an overview of these skills and their importance in the IC design industry.1. Solid Foundation in Electronics:A strong understanding of electronics is the foundation of IC design. Beginners should start by learning basic concepts such as Ohm's Law, Kirchhoff's Laws, and semiconductor physics. This knowledge will help them comprehend the behavior of electronic components and their interactions within an IC.2. Proficiency in Programming:Programming skills are becoming increasingly important in IC design. Beginners should focus on learning languages such as Verilog or VHDL, which are widely used in designing digital circuits. These languages allow designers to describe the behavior of their circuits and simulate their functionality before fabrication.3. Knowledge of IC Design Tools:Proficiency in using IC design tools is essential for both beginners and experts. Tools like Cadence or Synopsys provide a platform to design, simulate, and verify ICs. Beginners should familiarize themselves with these tools and learn how to navigate through their various features.4. Understanding of Digital and Analog Design:IC design encompasses both digital and analog circuits. Beginners should acquire a solid understanding of both domains. Digital design involves logic gates, flip-flops, and sequential circuits, while analog design deals with continuous signals and amplifiers. A comprehensive understanding of these concepts is crucial for successful IC design.5. Familiarity with Design Verification:Design verification is the process of ensuring that an IC design meets its specifications. Beginners should learn techniques such as functional simulation, timing analysis, and formal verification. These methods help identify and rectify design flaws, ensuring the reliability and functionality of the final product.6. Knowledge of Low Power Design:In today's world, power efficiency is a critical consideration in IC design. Beginners should be aware of low power design techniques such as clock gating, power gating, and voltage scaling. These techniques help reduce power consumption without compromising the performance of the IC.7. Awareness of Design for Testability:Design for Testability (DFT) is an essential aspect of IC design. It involves incorporating features that facilitate testing and fault diagnosis. Beginners should familiarize themselves with DFT techniques like scan chains, built-in self-test (BIST), and boundary scan. These techniques simplify the testing process, ensuring the quality and reliability of the manufactured IC.8. Continuous Learning and Adaptability:The field of IC design is ever-evolving, with new technologies and methodologies emerging regularly. To stay ahead, individuals must have a thirst for continuous learning and adaptability. Beginners should actively engage in professional development, attend conferences, and keep up with industry trends to enhance their skills and expertise.Conclusion:Becoming an expert in the IC design industry requires a combination of foundational knowledge, technical skills, and adaptability. By acquiring a solid understanding of electronics, programming, IC design tools, digital, and analog design, as well as verification and low power techniques, individuals can progress from being beginners to experts. Furthermore, a commitment to continuous learning and staying updated with industry advancements is crucial for long-term success in this dynamic field. With the right skills and dedication, one can thrive in the exciting world of integrated circuit design.。
混成系统形式化验证

软件学报ISSN 1000-9825, CODEN RUXUEW E-mail: jos@Journal of Software,2014,25(2):219−233 [doi: 10.13328/ki.jos.004535] +86-10-62562563 ©中国科学院软件研究所版权所有. Tel/Fax:∗混成系统形式化验证卜磊1,2, 解定宝1,21(南京大学计算机科学与技术系,江苏南京 210023)2(计算机软件新技术国家重点实验室(南京大学),江苏南京 210023)通讯作者: 卜磊, E-mail: bulei@摘要: 混成系统是实时嵌入式系统的一种重要子类,其行为中广泛存在离散控制逻辑跳转与连续实时行为交织混杂的情况,因此行为复杂,难以掌握与控制.由于此类系统广泛出现在工控、国防、交通等与国计民生密切相关的安全攸关的领域,因此,如何对相关系统进行有效的分析与理解,从而保障系统安全运营,是一项具有重要意义的工作.常规的系统安全性分析手段,如测试、仿真等仅能在一定输入的情况下运行系统来观测系统行为,无法穷尽地检测复杂混成系统在所有可能输入下的行为,因此并不足以保证系统的安全性.区别于测试等方法,形式化方法通过求解系统模型状态取值范围等方法来确认系统模型中一定不会出现相关错误.因此,其对于保障安全攸关混成系统的安全性具有十分重要的意义.形式化方法由形式化规约与形式化验证两个方面构成.因此从以上两个角度分别对形式化规约方向上现有混成系统建模语言、关注性质以及形式化验证方向的混成系统模型检验、定理证明的现有主要技术与方法进行了综述性的回顾与总结.在此基础上,针对现阶段实时嵌入式系统复杂化、网络化的特性,对混成系统形式化验证的重要关注问题与研究方向进行了探索与讨论.关键词: 混成系统;形式化方法;模型检验;定理证明中图法分类号: TP311文献标识码: A中文引用格式: 卜磊,解定宝.混成系统形式化验证.软件学报,2014,25(2):219−233./1000-9825/4535.htm英文引用格式: Bu L, Xie DB. Formal verification of hybrid system. Ruan Jian Xue Bao/Journal of Software, 2014,25(2):219−233 (in Chinese)./1000-9825/4535.htmFormal Verification of Hybrid SystemBU Lei1,2, XIE Ding-Bao1,21(Department of Computer Science and Technology, Nanjing University, Nanjing 210023, China)2(State Key Labotary for Novel Software Technology (Nanjing University), Nanjing 210023, China)Corresponding author: BU Lei, E-mail: bulei@Abstract: Hybrid System is a very important subclass of real time embedded system. The behavior of hybrid system is tangled withdiscrete control mode transformation and continuous real time behavior, therefore very complex and difficult to control. As hybrid systemis widely used in safety-critical areas like industry, defense and transportation system, it is very important to analyze and understand thesystem effectively to guarantee the safe operation of the system. Ordinary techniques like testing and simulation can only observe thebehavior of the system under given input. As they cannot exhaust all the possible inputs and scenarios, they are not enough to guaranteethe safety of the system. In contrast to testing based techniques, formal method can answer questions like if the system will never violatecertain specification by traversing the complete state space of the system. Therefore, it is very important to pursue the direction of formalverification of safety-critical hybrid system. Formal method consists of formal specification and formal verification. This paper reviews∗基金项目: 国家自然科学基金(61100036, 91318301, 61321491); 国家高技术研究发展计划(863)(2012AA011205); 江苏省自然科学基金(BK2011558)收稿时间:2013-05-07; 定稿时间: 2013-09-29220 Journal of Software软件学报 V ol.25, No.2, February 2014the modeling language and specification of hybrid system as well as techniques in model checking and theorem proving. In addition, it discusses the potential future directions in the related area.Key words: hybrid system; formal method; model checking; theorem proving1 混成系统简介在实时嵌入式系统,特别是复杂的实时控制系统中,广泛存在这样一类子系统,它们的行为中离散化的逻辑控制与连续性的时间性行为相互依赖,相互影响,彼此互为依存,息息相关.以列车控制系统为例,典型的列车控制系统一般存在多种不同的控制模式来应对当前的车况、路况以及各种突发事件,而系统中的重要参数,如列车速度、当前位置、与前车距离等等,会随着时间连续变化.列车在运行中会为了满足特定的时间约束或者调整当前参数的取值而调整列控模式,而在不同的列控模式下,列车中重要参数的变化规律完全不同,相应地,对各种事件的响应时间也会有所区别.在这种类似的系统中,逻辑控制与时间性行为并不是孤立的两个部分,而是交错地有机结合在一起,构成了一种非常复杂的系统,而这样的复杂实时系统因为其离散控制与实时连续行为混杂叠加的特性,一般被称为混成系统(hybrid system)[1].混成系统是一种嵌入在物理环境下的实时系统,一般由离散组件和连续组件连接组成,组件之间的行为由计算模型进行控制.对于经典混成系统,其构成体现了计算机科学和控制理论的交叉,一般分为两个层面:离散层与连续层.在连续层,一般通过系统变量对时间的微分方程来描述系统的实际控制操作模型以及系统中参数的演变规律;在离散层,则通过状态机、Petri网等高抽象层次的模型来描述系统的逻辑控制转换过程.在两层之间,通过一定的接口与规则将连续层的信号与离散层的控制模式进行关联与转换.大多数复杂实时控制系统行为都包含了连续变化的物理层与离散变化的决策控制层之间的交互过程,因此,混成系统在工业控制和国防等领域大量存在,特别是安全关键系统,如交通运输、航空航天、医疗卫生、工业控制等等系统.相应地,随着它们在人类生活中的应用面越来越广,重要性越来越高,对相应系统质量,特别是可信性的需求也快速提升,系统失效所造成的灾难也越来越沉重,甚至难以接受.在日常生活方面,车载导航系统的小小失误就可能造成交通事故,而飞机导航系统的失误则可能导致机毁人亡.如果扩展到国防军用领域,对软件系统的错误已经几乎进入了零容忍度的阶段.因此,如何对混成系统进行有效的可信性保障,已成为一个亟待解决的问题.一般而言,测试、仿真[2,3]等技术是研究和保障软件质量的主要方法.然而,这些方法主要以运行系统为发现问题的主要手段,由于人力无法穷尽地遍历系统所有可能的运行输入与场景,也就不足以保证检测的完备性,这也就可能给系统后期运行留下了不安全隐患.因此,在对系统错误零容忍的安全攸关系统领域,采用可证明系统模型正确性的形式化验证理论与技术[4,5]来对系统模型进行安全性验证就显得极为重要,这也成为相关领域近期主要关注的问题.形式化方法(formal method)是对以数学为基础的,用以对系统进行说明、设计和验证的语言、技术和工具的总称,其主要可以分为形式化规约(specification)与形式化验证(formal verification)两个方面.形式化规约就是用形式化语言在不同抽象层次上描述部分或整个系统的行为与性质.一般而言,我们称表示系统性质的语言为规约语言(specification language),比如各种时序逻辑(temporal logic)等;我们称描述系统行为的数学模型为系统刻画语言(system description language),如CSP[6]、状态图[7]等.在我们描述了系统的行为与需要满足的性质之后,就需要采用形式化验证来判定最终的软件产品是否满足这些需求和具备这些特征.通过验证,可以判定系统是否满足某个特定的性质,并在系统不满足性质时给出理由.目前,对软硬件系统的验证主要包括模型检验(model checking)[5]和定理验证(theorem proving)[8,9]两个方面.对应地,在混成系统形式化建模与验证方向的研究也主要在上述方向上展开,例如,如何设计具有足够表达能力的建模语言来描述混成系统中的复杂行为;如何设计有效的模型检验方法、定理证明方法来对大规模复杂系统进行有效的验证,回答系统是否满足特定性质的问题.在近20年的密集投入与研究之后,混成系统的形式化建模与验证已经取得了一系列成果[10].本文将对相关主要研究方向与成果进行概述性的总结与回顾.在此基卜磊 等:混成系统形式化验证 221础上,针对现阶段实时嵌入式系统所呈现的智能化、开放化等特征,本文对混成系统近期的研究热点以及下一阶段重点关注的问题进行了探讨与展望.2 混成系统建模语言针对混成系统行为中离散逻辑跳转与连续时间行为交织的特征,相关科研工作者对状态机、CSP 等建模语言进行了实时变量定义、微分方程连续行为等扩展,提出了包括混成自动机(hybrid automata)[1]、混成CSP [11,12]、混成Petri 网[13]、混成程序[14]等在内的一系列形式化建模语言.尽管以上语言之间各有侧重与不同,但是在如何表达系统中的离散与连续行为交织等特性方面,以上语言的扩展之间存在着大量的共通之处.在上述语言当中,混成自动机得到了最为广泛的认可与应用.下面我们就以混成自动机为例来说明相关建模语言是如何针对混成系统的相关特性进行建模与描述的.混成自动机是在状态机基础上进行实时连续变量扩展所构成的一种建模语言.可以定义混成自动机为多元组H =(X ,Σ,V ,E ,V 0,α,β,γ),其中,• X 是实数值系统变量的有限集合,X 中变量的个数也被称为自动机的维度.• Σ是事件名的有限集合,V 是位置节点的有限集合.• E 是转化关系的集合,E 中的元素e 具有形式(v ,σ,ϕ,ψ,v ′).其中,v ,v ′是V 中的元素;σ∈Σ是转换上的事件名;转换卫式ϕ是一个将E 中的转换e 标注为一组约束的标注函数,表示当系统行为触发转换e 时,相应变量的取值满足此约束;ψ是形为x :=c 的重置动作集合,表示当系统行为触发此转换后,相应变量x 的取值会被重置为c ,以上c ∈R ,x ∈X .• V 0⊆V 是初始位置的集合.• α是一个标注函数,它将每个位置映射到一个节点不变式,表示系统行为停留在相关节点时,相应变量取值满足此约束.• β是一个为V 中每个位置节点添加流条件(微分方程)的标注函数,表示当系统行为停留在相关节点时,相应变量取值变化随着时间增长满足此条件.对任意x ∈X ,有且仅有1个x 的流条件属于β(v ).• γ是一个标注函数,它将初始位置V 0中每个位置映射到一组初始条件,初始条件具有形式x :=a (x ∈X ,a ∈R ).对任意位置v ∈V 0,对任意x ∈X ,有且仅有1个x :=a ∈γ(v ).图1是一个经典的自动温度控制器模型[1],我们用此模型来对混成自动机及其各个组成部件进行一个简要的描述.此模型中,变量x 描述的是系统中实时变化的温度数值.当系统驻留在控制模式off 时,加热器被关闭,环境中的温度按照off 节点上的流条件0.1xx =− 下降(可理解为微分方程d x /d t =−0.1x );而当系统驻留在控制模式on 时,加热器被打开,环境中的温度按照on 节点上的流条件50.1xx =− 上升.系统的初始条件被设定为温度20°C,控制模式为off.转换卫式x <19与x >21表示当系统温度降低到19°C 以下时,控制模式就可以从off 切换到on,从而打开加热器;而当系统温度高于21°C 时,则正好相反,控制模式可以跳转到off 模式,从而关闭加热器.最后,在此模型中分别存在两个不变式:x ≥18与x ≤22,这表明了系统停留在控制模式off 和on 时,其实时变量x 的合法取值范围.Fig.1 Hybrid automata for temperature comtroller图1 温度控制器混成自动机模型显然,如果忽略变量x 以及相关的不变式、转换卫式、流条件等元素,这个混成自动机的结构就是一个基本的状态机图.通过将状态机图中的状态节点概念拓展到位置节点(可理解为控制模式),并在每个位置节点上添加相应的连续变量变化规则,可以描述系统在不同控制模式下的实时参数变化过程,从而描述混成系统的具体off0.1xx =− x ≥18 on 50.1x x =− x ≤22x >21x <19x =20222Journal of Software 软件学报 V ol.25, No.2, February 2014连续行为. 由于混成自动机中连续行为与离散行为共存的特质,混成自动机的行为非常复杂,难以控制与把握.因此,现在相关研究领域主要关注于其中一个比较特别的子类——线性混成自动机(linear hybrid automata).给定一 个变量集合X ,我们称表达式0li i i c x =∑~b 为线性表达式(linear term),其中,c i ∈R ,x i ∈X ,~∈{>,<,=,≤,≥},b ∈R .我们 称一组线性表达式的布尔组合(Boolean combination)为一个线性公式(linear formula).给定一个混成自动机H 满足下列条件,我们称其为线性混成自动机(linear hybrid automata):• 在任意控制转换e ∈E 上,转换卫式ϕ中任一约束均为线性公式;• 对任意控制位置v ∈V ,变量x 在α(v )中的定义均为线性公式;• 流条件是形如[,]xa b ∈ 或者x ~a 的变化率集合,其中,x ∈X ,a ,b ∈R ,a ≤b ,~∈{>,<,=,≤,≥}. 如果将图1中的温度控制器模型的流条件进行简单的转换,我们就可以获得一个线性混成自动机版本的温度控制器模型,如图2所示. Fig.2 Linear hybrid automata for temperature comtroller图2 温度控制器线性混成自动机模型线性混成自动机是混成自动机中的一种比较重要的子类.众所周知,线性系统的复杂度远低于非线性系统,并且现有数学技术在线性系统领域已经颇为成熟,可以处理相当大规模的问题空间;而在非线性系统上,现有的数学技术可以处理的问题空间非常有限,远远达不到实际应用的需求.因此,通过线性表达式来描述流条件、不变式、跳转条件等部件,可以大幅度降低系统的复杂度,并且使设计者更容易把握系统的行为,保证系统的正确性.尽管实际应用中的主要系统大部分需要使用非线性控制,特别是流条件部分,无法直接应用线性混成自动机来对系统建模或者描述,但是设计者可以通过抽象(abstraction)的方法拆分原系统的行为,使用一个包含更多控制节点的线性混成自动机模型来逼近非线性自动机的行为,并逐步逼近直到该线性混成自动机的精度可以在最大程度上拟合原非线性系统,从而通过对该线性混成自动机进行分析的方法达到分析原系统的目的[15].事实上,通过在标准线性混成自动机的基础上进一步添加相应的约束与限制,我们可以将其转化成一些非常重要的子类乃至于读者相对更加熟悉的建模语言,如下所示[16]:• 如果对任意控制位置v ∈V ,变量x 在β(v )的定义中均形如0,x= 即,变量x 在所有节点上的变化率均为0,则称x 为一个离散变量(discrete variable).如果一个线性混成自动机中所有变量均为离散变量,则称此自动机为离散系统(discrete system).• 如果对任意控制转换e ∈E ,离散变量x ∈X 在ψ中均形如x :=0或者x :=1,即,变量x 在系统触发每个跳转之后的新取值必为0或者1,则称此变量为一个命题(proposition).如果一个线性混成自动机中所有变量均为命题,则称此自动机为一个有穷状态系统(finite-state system).• 如果对任意控制位置v ∈V ,变量x 在β(v )的定义中均形如1x= ,即,变量x 在所有节点上的变化率均为1;并且如果对任意控制转换e ∈E ,离散变量x ∈X 在ψ中均形如x :=0或者x :=x ,即,系统触发每个跳转之后会将变量x 的值赋值为0或者不变,则称变量x 为一个时钟(clock).如果一个线性混成自动机中所有变量均是命题或者时钟,并且系统内所有线性公式均为形如x~c 或者x −y~c 的线性表达式的布尔组合,其中,x ,y ∈X ,~∈{>,<,=,≤,≥},c ∈Z ≥0,则称此线性混成自动机为时间自动机(timed automata)[17].• 如果存在非零整数k ∈Z ,并且对任意位置节点v ∈V ,变量x 在β(v )的定义中均形如xk = ,与上类似,如果对任意控制转换e ∈E ,变量x ∈X 在ψ中均形如x :=0或者x :=x ,则称变量x 为一个倾斜时钟(skewed clock),即,此变量在每个节点都按照一个不为1的固定变化率进行变化.如果一个线性混成自动机中每个变量均为命题或者倾斜时钟,则称此自动机为多级时间系统(multirate timed system).如果一个多级时间off2x=− x ≥18 on 4x = x ≤22x >21x <19x =20卜磊 等:混成系统形式化验证223系统中变量的变化率共有n 种,则称此系统为n 级时间系统(n -rate timed system). • 如果对任意位置v ∈V ,变量x 在β(v )的定义中均形如0x= 或者1x = ,即,变量x 在所有节点上的变化率不是0就是1;并且如果对任意控制转换e ∈E ,变量x ∈X 在ψ中均形如x :=0或者x :=x ,则称x 为一个积分器(integrator).如果一个线性混成自动机中所有变量均为命题或者积分器,则称此自动机为积分器系统(integrator system).3 混成系统模型检验模型检验是通过穷尽遍历待验证软件系统模型的状态空间来检验系统的行为是否具备预期性质的一种自动验证方法.自20世纪80年代被提出以来,模型检验技术得到了学术界、工业界的广泛重视,并在芯片设计等领域得到了广泛应用.如上文所述,混成自动机是混成系统最主流建模语言.目前,学术界对混成自动机模型检验研究主要集中在混成自动机的安全性性质(safety)[18,19]检验上.安全的直观概念解读为系统运行中不会发生不好的行为.安全性检验即检验从给定的初始条件出发,系统运行中是否会出现违背规约或者不安全的行为.由于混成自动机的运行既包含状态的离散变化,又包含状态的连续变化,其相应的模型检验问题十分困难.因此,目前对混成自动机的模型检验主要集中在安全性的一个子集——可达性问题(reachability)上.对于混成自动机H ,它的可达性规约由H 中的一个位置节点v 和一个变量约束集φ组成,我们通过符号R (v ,φ)来表示.H 满足R (v ,ϕ)可定义为:H 存在一个具体的实时行为可进入节点v ,并且当系统停留在节点v 中一段时间后,系统中实时变量x 取值可满足ϕ中的所有变量约束.可达性问题与安全性问题的关系在于,将系统不安全的行为构建成一个独立的离散“坏”状态,然后检验此“坏”状态是否可达:如可达,则系统中可能发生不安全行为;反之,则系统行为安全.因此,检验系统安全性的问题就变成了计算系统可达空间的问题.也就是说,我们要计算出系统的所有可达状态,并判定这些状态中是否有状态可以使规约R (v ,φ)成真.由于混成自动机中连续行为的存在,混成自动机拥有极为庞大的无限状态空间,所以我们不能像一般模型检验方法一样通过直接枚举遍历的方法来计算出整个可达集,而是必须通过符号化的方法来计算.目前,主流方法是通过一定的约束集来描述系统初始状态集合,并称其为系统初始可达空间.然后,基于系统的流条件、不变式、转换卫式等元素定义相应自动机上的Post 操作,以计算系统在当前状态集下后续可达状态集区间.将计算得到的状态集并入已有可达状态集空间并重复上述过程,直到系统可达状态空间集收敛,即,从当前所有可达状态空间上基于系统规定的连续/离散演变规则不再能抵达新的状态.此时,称所计算得到的状态空间为系统完整可达状态空间集,并进行判断计算所得系统完整可达状态空间集中是否有状态满足规约R (v ,ϕ):如有,则称系统满足相应可达性规约;否则称系统不满足相应规约.上述方法的可行性、有效性等等,与能否在任意的系统状态集上针对给定的微分方程等元素进行数值计算与推演从而生成后续可达状态集密切相关.众所周知,在任意形态数值状态域上进行任意形式的非线性微分方程计算复杂度极高,目前,数学领域还没有有效的方法来解决相应大规模问题.因此,针对一般混成自动机,目前可达集计算的主流方法为将系统的状态域用一种特定的数学形态来过抽象(over-approximation).目前常用的数学形态包括凸多面体(convex polyhedra)[20,21]、分段仿射系统(piecewise affine system)[22,23]、椭圆体(ellipsoidal)[24,25]等等.在使用以上数学形态对可达域进行标识之后,使用相关领域的成熟数学计算方法来求取从当前形态开始后继形态的演变范围及过程.但是,这类方法仍然存在很多问题:首先,过抽象带来的问题是状态域的表达不够精确;其次,此过程无法保证收敛,很可能一直循环而无法停止;最后,以上过抽象方法中数学计算复杂度很高,对系统资源消耗极大,从而无法对高维度复杂系统进行分析.实际上,即使是针对混成自动机中相对简单的子类,线性混成自动机,其可达性问题也已被证明是不可判定的[1,16,26,27].由于以上原因,相关方法在一般性非线性混成自动机上表现并不如人意.特别是由于非线性计算的高度复杂度,目前已有相关工具可验证非线性混成自动机模型的规模非常有限,文献[28]在对主流工具进行整体评估后得出结论为,现有工具很难验证超过5个变量的系统.由于线性数值域计算方法远成熟于非线性计算,复杂度224 Journal of Software 软件学报 V ol.25, No.2, February 2014也能得到较好的控制,因此基于上述理念,相关研究人员以多面体作为线性混成自动机基本状态域的数值表现形式,开发了一系列线性混成自动机模型检验工具,如HyTech [29],PHAVer [30]等,并成功地验证了飞机防撞系统等典型混成自动机案例.值得注意的是,上述线性混成自动机特指前文中所描述的流条件形如[,]xa b ∈ 的自动机形式,称其为线性混成自动机是因为相应流条件积分展开后可以得到变量x 的取值是与时间t 相关的线性函数.在相关研究中,存在另一类类似的混成自动机被称为线性混成系统(linear hybrid system),其流条件形如xAx b =+ ,相关研究者(特别是控制领域)普遍称其为线性混成系统是因为其流条件表现为x 的线性方程,但是其积分展开后会成为包含e t 的非线性方程,所以其并不是线性混成自动机.针对相应的自动机,也有大量相关工具被开发出来,其中较著名的包括来自美国卡耐基梅隆大学的Checkmate [31]、来自法国Verimag 实验室的d/d t [20]等等.目前,相关领域科研工作者在非线性混成自动机模型检验上投入了大量的精力并取得了一定的进展,特别是泰勒模型(Taylor model)、Support Function 等数学模型被应用到了混成系统状态域的表达与计算当中,近年出现的工具flow*[32]就是一个成功应用泰勒模型对非线性混成系统进行验证的示例.flow*要求混成自动机的流条件必须由多项式微分方程描述.用户给定初始区间与一个固定的基本时间步之后,可利用泰勒模型来分析其可达区间.事实上,泰勒模型很适合连续状态的计算,但是当进行离散跳转时,需要和转换卫式做相交操作,而这个操作的复杂度很高.与flow*不同,SpaceEx [33]可处理的系统是对线性混成系统,即,流条件为,xAx b =+ 进行一定放宽后的非线性自动机.SpaceEx 允许系统中的不变式、迁移卫式等元素为凸函数.同样地,在给定一个基本时间步之后,可以利用support function 来计算在此时间步之后的系统状态域.相关工具目前已经在部分非线性系统上进行了验证,但如何扩展可验证系统种类与规模,仍然是一项值得关注的问题.另一方面,反例制导的抽象精化(counter example guided abstraction refinement,简称CEGAR)[34]是一种非常有效的复杂系统形式化验证方法.其基本思想在于:在原系统因过于复杂而难以验证的情况下,对原系统进行抽象后,在简化系统上进行验证.由于系统抽象会引入一些原系统所不包含的行为,因此当进行安全性/可达性检查时,若抽象系统不满足相应规约,则原系统必然也不满足相应规约.然而当抽象系统满足相应规约时,满足此规约的可疑行为可能是由于抽象所带入,因此需要将相应的可疑行为在原系统上进行确认:若此行为在原系统上也满足,则验证结束;否则,分析此行为在抽象前后系统上的区别,从而指导下一轮精化后抽象的展开.通过循环迭代此步骤,可以有效地缩减每次待验证系统规模,从而对复杂系统进行分析.CEGAR 思想同样也在混成系统模型检验上得到了应用.Clarke [35],Alur [36]等人提出了大量混成系统CEGAR 验证方法来处理大规模复杂系统.相关方法提出,将状态谓词作用与混成系统状态空间上进行抽象.然而,此类方法在谓词精化中经常需要对系统状态空间进行拆分,从而大幅度增加了待验证系统的结构,难以对复杂系统开展验证.同样使用CEGAR 思想,针对线性混成自动机,Clarke 等人提出了一种称为迭代式松弛抽象(iterative relaxation abstraction,简称IRA)的CEGAR 框架[37].此方法的主要思路在于:每次抽象时,选取系统中部分实时变量进行丢弃,从而保持系统图形结构,但是对系统变量空间进行降维处理.在降维后的系统上采用PHAVer 等现有工具进行验证,若降维后系统上存在路径可满足相应可达性约束,则将此路径上的变量还原,采用南京大学团队提出的面向路径可达性验证方法[38]对原路径进行编码并验证其是否可行.若此路径在原系统中不可行,则抽取导致此路径在原系统中不可行的约束集,并基于此约束集中的变量修正下一轮系统抽象时所抛弃的变量集合的内容.此方法在典型案例上的性能明显优异于现有工具,如PHAVer 等等,但是由于此方法中仍然依赖于PHAVer 对抽象后系统进行验证,因此当抽象后系统仍然维度较高时,此方法也难以进行处理. 4 混成系统有界模型检验近年来,作为基于BDD(binary decision diagram)的符号化模型检验[39]的一种补充方法,有界模型检验(bounded model checking,简称BMC)技术[40]被提出并得到了广泛的应用.其基本思想是:将模型行为步数通过正整数k 来限制,将系统k 步内行为采用布尔约束编码,然后利用SAT 方法来寻找此布尔约束集的可行解,从而判定系统在k 步内行为是否有不满足规约的情况.文献[40]发现,虽然BMC 方法因为只能验证有限步数内系统。
ICCworkshop学习笔记

***************************************************************************1. 填充单元它是用来填充I/O单元和I/O单元之间的间隙。
对于标准单元则同样有标准填充单元(filler cell)它也是单元库中定义的与逻辑无关的填充物,它的作用主要是把扩散层连接起来满足DRC规则和设计需要,并形成电源线和地线轨道(power rails)2. 电压钳位单元tie cell数字电路中某些信号端口,或闲置信号端口需要钳位在固定的逻辑电平上,电压钳位单元按逻辑功能要求把这些钳位信号通过钳高单元(tie-high)与Vdd相连,或通过钳低单元(tie-low)与Vss相连使维持在确定的电位上。
电压钳位单元还起到隔离普通信号的特护信号(Vdd,Vss)的作用,在作LVS分析或形式验证(formal verification)时不致引起逻辑混乱。
3. 二极管单元为避免芯片加工过程中的天线效应导致器件栅氧击穿,通常布线完成后需要在违反天线规则的栅输入端加入反偏二极管,这些二极管可以把加工过程中金属层积累的电荷释放到地端以避免器件失效。
4. 去耦单元当电路中大量单元同时翻转时会导致充放电瞬间电流增大,使得电路动态供电电压下降或地线电压升高,引起动态电压降(IR-drop) 为避免动态电压降对电路性能的影响,通常在电源和地线之间放置由MOS管构成的电容,这种电容被称为去耦电容或去耦单元(decap cell) 他的作用是在瞬态电流增大,电压下降是电路补充电流以保持电源和地线这之间的电压稳定,防止电源线的电压降和地线电压的升高。
去耦单元是与逻辑无关的附加单元5. 时钟缓冲单元时序电路设计的一个关键问题是对时钟树的设计,芯片中的时钟信号需要传送到电路中的所有时序单元。
为了保证时钟沿到达各个触发器的时间偏差(skew)尽可能地小,需要插入时钟缓冲器减小负载和平衡延时,在标准单元库中专门设计了供时钟树选用的时钟缓冲单元(clock buffer)和时钟反向器单元(clock inverter)时钟树综合工具根据指定的时钟缓冲单元去自动构建满足时序要求的时钟网络。
软件系统形式化验证课程简介

Reference Booksand Other Materials
(Including title, author, press and publication date)
课程说明
内
容
简
介
随着系统复杂性的增加,设计出错的可能性也正在增加。在系统设计过程中,由于顶层说明的定义是人工的,并且综合设计的细化过程通常需要人工的精细调整才能达到更高的性能,所以有必要保证中间设计步骤与用户说明的特性的一致性和正确性。成功的设计方法要求验证设计是设计过程的必需部分,而不是可有可无的。对于一个数字系统,花费在验证设计上的时间是花费在设计上时间的80%。设计验证是任何重大系统开发过程面临的主要挑战。虽然传统的模拟技术仍被用于验证设计,但是越来越复杂的设计使得该技术创建足够多的向量集变得很困难,甚至是不可能。所以,需要一种新的验证方法来应付这种情况。形式化验证技术已经成为保证系统正确性的一种强有力的方法。
Evaluation of Learning
The written test (100%)
Total Hours
(including Lecture hours Lab hours)
Textbooks
(Including title, author, press and publication date)
Course Description
Software systems are widely used in applications where failure is unacceptable. Because of the success of the Internet and embedded systems in automobiles, airplanes, and other safety critical systems, we are likely to become even more dependent on the proper functioning of computing devices in the future. Due to this rapid growth in technology, it will become more important to develop methods that increase our confidence in the correctness of such systems. Traditional verification techniques use simulators with handcrafted or random test vectors to validate the design. Unfortunately, generating test vectors is very labor-intensive. The overall complexity of the designed systems implies that simulation cannot remain the sole means of design verification, and one must look at alternative methods to complement simulation. Recent years have brought about the development of powerful formal verification tools for verifying of software systems. By now, the information technology industry has realized the impact and importance of such tools in their own design and implementation processes.
单周期cpu设计文档
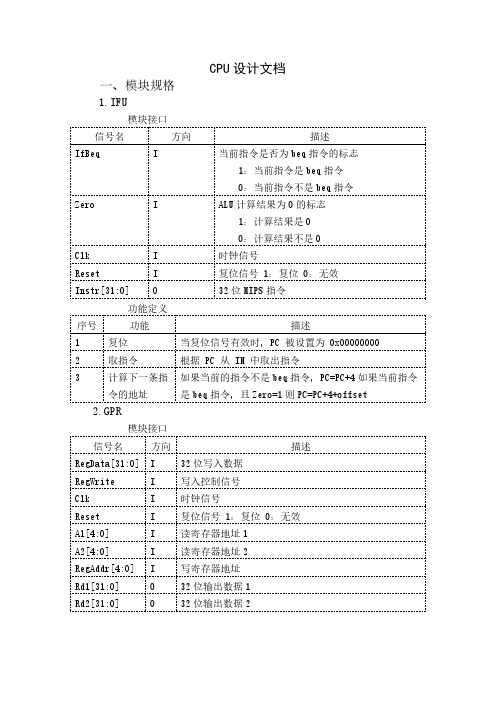
Extop
O
控制 ext 拓展方式 00:无符号扩展 01:高 16 位补 0 10:低 16 位补 0
Aluop[2:0]
O
控制 cpu 进行相应的运算 000:加 001:减 01unc[5:0]
100001 000000 100011 000000 001101 100011 101011 000100 001111 000000 000000
2.GPR
模块接口 信号名 RegData[31:0] RegWrite Clk Reset A1[4:0] A2[4:0] RegAddr[4:0] Rd1[31:0] Rd2[31:0] 方向 I I I I I I I O O 32 位写入数据 写入控制信号 时钟信号 复位信号 1:复位 0:无效 读寄存器地址 1 读寄存器地址 2 写寄存器地址 32 位输出数据 1 32 位输出数据 2 描述
Opcode[5:0]
addu RegDst RegWrite ALUsrc MemtoReg MemWrite nPC_sel 1 1 0 0 0 0
subu 1 1 0 0 0 0
ori 0 1 1 0 0 0
lw 0 1 1 1 0 0
sw X 0 1 X 1 0
beq X 0 0 X 0 1
功能定义 序号 1 2 3 复位 取指令 计算下一条指 令的地址 功能 描述 当复位信号有效时,PC 被设置为 0x00000000 根据 PC 从 IM 中取出指令 如果当前的指令不是 beq 指令,PC=PC+4 如果当前指令 是 beq 指令,且 Zero=1 则 PC=PC+4+offset
MemtoReg= o5 o4 o3 o2 o1o0
IC验证工程师招聘笔试题与参考答案(某大型国企)2024年

2024年招聘IC验证工程师笔试题与参考答案(某大型国企)(答案在后面)一、单项选择题(本大题有10小题,每小题2分,共20分)1、以下关于数字电路中CMOS电路的特点,描述错误的是:A、功耗低B、抗干扰能力强C、工作速度慢D、易于集成2、在数字电路设计中,以下哪种电路结构可以实现基本逻辑门的功能?A、与门B、或门C、非门D、异或门3、题干:在集成电路验证过程中,以下哪个说法是正确的?A. 验证环境应该尽可能简单,以确保验证的准确性B. 验证环境应该尽可能复杂,以模拟真实应用场景C. 验证环境应介于简单和复杂之间,以确保验证效率和准确性D. 验证环境的复杂程度由验证团队的主观意愿决定4、题干:以下关于Verilog语言中initial块和always块的说法,哪个是正确的?A. initial块和always块都是顺序执行,initial块在仿真开始时执行一次,always块在每个仿真时间步长开始时执行一次B. initial块和always块都是顺序执行,initial块在仿真开始时执行一次,always块在仿真结束时执行一次C. initial块是顺序执行,在仿真开始时执行一次;always块是并行执行,在每个仿真时间步长开始时执行一次D. initial块是并行执行,在仿真开始时执行一次;always块是顺序执行,在每个仿真时间步长开始时执行一次5、在IC验证流程中,以下哪个阶段不属于功能验证阶段?A. 初始环境搭建B. 测试用例开发C. 验证环境搭建D. 仿真和调试6、以下哪种工具在IC验证中主要用于仿真和调试?A. UVMB. VCSC. VerilatorD. GDB7、在IC验证过程中,以下哪个术语用于描述验证环境中的测试案例?A. TestbenchB. Testbench CodeC. Testbench ModuleD. Testbench Stimulus8、以下哪种验证方法不依赖于模拟硬件或软件,而是使用实际硬件进行验证?A. Simulation-based VerificationB. FPGA-based VerificationC. Formal VerificationD. Emulation-based Verification9、题目:在数字电路中,以下哪种触发器在时钟信号的上升沿触发?A. 主从触发器B. 同步触发器C. 异步触发器D. 边沿触发器 10、题目:在以下关于Verilog HDL的描述中,哪项是错误的?A. Verilog HDL支持硬件描述语言和测试语言B. Verilog HDL中,always块可以用来描述时序逻辑和组合逻辑C. Verilog HDL中,initial块通常用来初始化时序逻辑D. Verilog HDL中,task和function都可以被调用以执行特定功能二、多项选择题(本大题有10小题,每小题4分,共40分)1、以下哪些技术或工具是IC(集成电路)验证工程师在日常工作中所必须熟悉的?()A、Verilog/VHDLB、SystemVerilogC、UVM(Universal Verification Methodology)D、TLM(Transaction-Level Modeling)E、SPICE(Simulation Program with Integrated Circuit Emphasis)F、GDB(GNU Debugger)2、在IC验证过程中,以下哪些是验证工程师需要关注的验证阶段?()A、功能验证B、时序验证C、功耗验证D、安全验证E、兼容性验证F、性能验证3、以下哪些工具或技术是IC验证工程师在芯片设计验证过程中常用的?()A. SystemVerilogB. Verilog-AC. UVM(Universal Verification Methodology)D. waveform viewerE. DFT(Design-for-Test)4、在IC验证过程中,以下哪些步骤是验证工程师需要完成的?()A. 验证需求分析B. 验证环境搭建C. 验证计划制定D. 验证用例编写E. 验证结果分析5、以下哪些是IC验证工程师在验证过程中常用的验证方法?()A. 仿真验证B. 系统级验证C. 单元级验证D. 代码覆盖率分析E. 动态功耗分析6、以下哪些是UVM(Universal Verification Methodology)验证环境中常见的组件?()A. SequenceB. ScoreboardC. AgentD. DriverE. Monitor7、以下哪些是IC(集成电路)验证工程师在验证过程中需要关注的时序问题?()A. setup timeB. hold timeC. clock domain crossingD. metastabilityE. power integrity8、在IC验证过程中,以下哪些工具或技术被广泛用于提高验证效率?()A. UVM(Universal Verification Methodology)B. assertion-based verificationC. formal verificationD. coverage-driven verificationE. simulation acceleration9、以下哪些技术是IC验证工程师在工作中常用的验证方法?()A. 仿真验证B. 硬件加速验证C. 实验室测试D. 动态功耗分析 10、以下关于验证计划的描述,正确的是哪些?()A. 验证计划应包含验证目标、验证策略、验证环境等B. 验证计划应详细列出所有的验证用例和测试项C. 验证计划应根据项目进度动态调整D. 验证计划应确保验证过程的可追溯性三、判断题(本大题有10小题,每小题2分,共20分)1、IC验证工程师在验证过程中,只需关注设计规格书,无需考虑其他相关文档。
Briefly describe the properties

1.Briefly describe the properties (advantages and/or disadvantages) ofwaterfall model and incremental model.瀑布模型优点:(1)可强迫开发人员采用规范化的方法(2)严格地规定了每个阶段必须提交的文档(3)要求每个阶段交出的所有产品都必须是经过验证的缺点:(1)由于瀑布模型几乎完全依赖于书面的规格说明,很可能导致最终开发出的软件产品不能真正满足用户的需要(2)只适用于项目开始时需求已经确定的情况增量模型优点:(1)能在较短时间内向用户提交完成一些有用功能的工作产品(2)逐步增加产品的功能可以使用户有较充裕的时间学习和适应新产品(3)项目失败的风险较低(4)优先级最高的服务首先交付,然后再将其他增量构件逐次集成进来,这意味着,最重要的部分将接受最多的测试缺点:(1) 与其他模型相比,需要更精心的设计2.Briefly describe the following requirement modeling notations, data-flowdiagram(DFD) and event trace. And which UML diagrams can be use to represent them, respectively?数据流图(DFD):对功能以及从一个功能到另一个功能的数据流建模。
对应UML中的用例图。
事件踪迹:关于现实世界实体之间交换的事件序列的图形描述。
对应UML 中的序列图3.What is component cohesive? List three types of component cohesive.构件内聚:一个构件功能强度的度量。
分为:巧合内聚、逻辑内聚、时态内聚、过程内聚、通信内聚、顺序内聚和功能内聚。
(列出三个即可)4.Briefly describe the testing process in system test.单元测试和集成测试后,进行系统测试,系统测试主要包括四个步骤:(1) 功能测试:检查集成的系统是否按照需求中指定的那样执行它的功能(2) 性能测试:将集成的构件与非功能需求进行比较(3) 验收测试:客户参与的测试,目标是确保系统符合他们对需求的理解(4) 安装测试:在实际运行环境中进行的测试。
静态时序分析(PrimeTime)&形式验证(Formality)详解

摘要:本文介绍了数字集成电路设计中静态时序分析(Static Timing Analysis)和形式验证(Formal Verification)的一般方法和流程。
这两项技术提高了时序分析和验证的速度,在一定程度上缩短了数字电路设计的周期。
本文使用Synopsys 公司的PrimeTime进行静态时序分析,用Formality进行形式验证。
由于它们都是基于Tcl(Tool Command Language)的工具,本文对Tcl也作了简单的介绍。
关键词:静态时序分析形式验证 PrimeTime Formality Tcl目录第一章绪论 (1)1.1 静态时序分析1.2 时序验证技术第二章PrimeTime简介 (3)2.1 PrimeTime的特点和功能2.2 PrimeTime进行时序分析的流程2.3 静态时序分析中所使用的例子2.4 PrimeTime的用户界面第三章Tcl与pt_shell的使用 (6)3.1 Tcl中的变量3.2 命令的嵌套3.3 文本的引用3.4 PrimeTime中的对象3.4.1 对象的概念3.4.2 在PrimeTime中使用对象3.4.3 针对collection的操作3.5 属性3.6 查看命令第四章静态时序分析前的准备工作 (12)4.1 编译时序模型4.1.1 编译Stamp Model4.1.2 编译快速时序模型4.2 设置查找路径和链接路径4.3 读入设计文件4.4 链接4.5 设置操作条件和线上负载4.6 设置基本的时序约束4.6.1 对有关时钟的参数进行设置4.6.2 设置时钟-门校验4.6.3 查看对该设计所作的设置4.7 检查所设置的约束以及该设计的结构第五章静态时序分析 (18)5.1 设置端口延迟并检验时序5.2 保存以上的设置5.3 基本分析5.4 生成path timing report5.5 设置时序中的例外5.6 再次进行分析第六章 Formality简介 (22)6.1 Formality的基本特点6.2 Formality在数字设计过程中的应用6.3 Formality的功能6.4 验证流程第七章形式验证 (27)7.1 fm_shell命令7.2 一些基本概念7.2.1 Reference Design和Implementation Design7.2.2 container7.3 读入共享技术库7.4 设置Reference Design7.5 设置Implementation Design7.6 保存及恢复所作的设置7.7 验证第八章对验证失败的设计进行Debug (32)8.1 查看不匹配点的详细信息8.2 诊断程序8.3 逻辑锥8.3.1 逻辑锥的概念8.3.2 查看不匹配点的逻辑锥8.3.3 使用逻辑锥来Debug8.3.4 通过逻辑值来分析第一章 绪论我们知道,集成电路已经进入到了VLSI和ULSI的时代,电路的规模迅速上升到了几十万门以至几百万门。
形式化验证操作系统

形式化验证seL4操作系统王俊超摘要:完全的形式化验证是确保系统不会出现编程和设计错误的唯一方法。
本文假设编译器,汇编代码和硬件层都是正确的,在此基础之上介绍了对seL4内核从抽象规约层到C语言实现层的形式化机器验证。
目前为止,seL4是第一个经过形式化验证并证明功能正确性的完整的通用的操作系统内核。
这里所指的功能性是说实现总是严格的满足上一抽象层内核行为的规约。
本文证明了seL4操作系统在任何情况下都不会崩溃以及执行不安全的操作,更重要的是,可以精确的推断出seL4在所有情况下的行为。
关键词:seL4;形式化验证;操作系统1.引言操作系统的可靠性和安全性几乎与计算机系统等价,因为内核可以在处理器的最高权限上工作,可以随意的访问硬件。
因此,操作系统内核实现出现的任何一个微小的错误都会导致整个计算机系统的崩溃。
为了保证操作系统的安全性,传统的一些做法有减少高权限的代码的数量,从而避免bug出现在较高的权限层内。
那么,如果代码的数量较少,便可以通过形式化的机器验证方法来证明内核的实现满足规约,并且在实现时不会有程序员由于编码引入的实现漏洞。
本文通过机器检验的形式化证明验证了seL4的功能正确性,目前,seL4所能达到的功能如下:能够在现实生活中使用,并且其性能与当前性能最好的微内核相当;其行为在抽象层进行了精确的规约;其形式化设计用来证明一些需要的属性比如中断等的安全性;其实现满足规约;访问控制机制能够保证高强度的安全性。
目前,seL4是第一个被完全形式化验证其功能正确性的操作系统内核,所以,它是一个前所未有的具有高度安全性和可靠性的底层系统级平台。
在本文所描述的功能正确性要比模型检验、静态分析以及采用类型安全编程语言实现的内核要强的多。
本文不仅对内核的规约层面进行了分析,同时也对于内核的精细的行为进行了规约和验证。
此外,本文还创立了一套融合了传统操作系统研发技术和形式化方法技术,用来快速实现内核设计与实现的方法学,经过实践证明,利用这套方法学开发出的操作系统不仅在安全性上有着充分的保障,在性能上也不会受到影响。
集成电路设计中的电路验证设计

集成电路设计中的电路验证设计集成电路设计是一个复杂且繁琐的过程,其中包括了许多关键的步骤。
在这些步骤中,电路验证设计被认为是确保集成电路性能、功能正确性的重要环节。
本文将详细介绍集成电路设计中的电路验证设计,分析其重要性,并探讨其关键技术和方法。
电路验证设计的定义和重要性电路验证设计是在集成电路设计过程中,通过对设计进行仿真和测试,以确保电路的功能和性能满足设计要求的过程。
其目的是发现和修复设计中的错误,避免在制造和应用过程中出现问题。
电路验证设计在集成电路设计中占据着重要的地位。
一方面,随着集成电路的规模越来越大,复杂度越来越高,电路验证设计能够有效提高设计的正确性,降低设计风险。
另一方面,通过电路验证设计,可以大大缩短设计周期,提高设计效率,降低制造成本。
电路验证设计的关键技术电路验证设计涉及到许多关键技术,其中包括:功能验证功能验证是电路验证设计的基础,其主要目的是验证电路的功能是否满足设计要求。
功能验证通常采用模拟器进行,通过对电路进行激励,观察其响应,以判断其功能是否正确。
时序验证是电路验证设计的另一个关键环节。
其主要目的是验证电路的时序性能是否满足设计要求。
时序验证通常采用时序分析器进行,通过对电路的时序特性进行建模和分析,以判断其时序性能是否正确。
可靠性验证可靠性验证是电路验证设计的另一个重要环节。
其主要目的是验证电路的可靠性是否满足设计要求。
可靠性验证通常采用统计方法进行,通过对电路进行大量的测试,以判断其可靠性是否正确。
功耗验证功耗验证是电路验证设计的另一个关键环节。
其主要目的是验证电路的功耗是否满足设计要求。
功耗验证通常采用功耗分析器进行,通过对电路的功耗特性进行建模和分析,以判断其功耗是否正确。
电路验证设计是集成电路设计中不可或缺的一个环节。
通过电路验证设计,可以有效提高电路的功能、性能、可靠性和功耗等方面的正确性,降低设计风险,缩短设计周期,提高设计效率,降低制造成本。
验证方法和技术在电路验证设计中,有多种验证方法和技术可供选择,这些方法和技术各有优缺点。
IC验证工程师招聘笔试题及解答(某大型国企)

招聘IC验证工程师笔试题及解答(某大型国企)一、单项选择题(本大题有10小题,每小题2分,共20分)1、IC验证工程师在验证流程中,以下哪个阶段通常负责确保设计规格的正确性和完整性?A、功能验证B、形式验证C、静态时序分析D、后端验证答案:A 解析:在IC验证流程中,功能验证阶段的主要任务是确保设计规格的正确性和完整性,通过模拟和测试验证设计的功能是否符合预期。
形式验证主要关注逻辑结构的正确性,静态时序分析关注时序约束的满足,后端验证关注物理层面的实现。
2、以下哪个工具通常用于检查设计中的逻辑错误和冗余,而不需要运行仿真?A、仿真软件B、形式验证工具C、静态分析工具D、功耗分析工具答案:C 解析:静态分析工具可以在不运行仿真的情况下检查设计中的逻辑错误和冗余。
这些工具分析设计文件,查找潜在的错误和不一致性,而不需要实际运行设计来验证其功能。
仿真软件需要运行仿真来测试设计,形式验证工具用于确保逻辑结构的正确性,功耗分析工具用于评估设计的功耗。
3、在数字电路中,以下哪种触发器可以实现边沿触发的功能?A. 触发器DB. 触发器JKC. 触发器TD. 触发器RS答案:B 解析:JK触发器是一种可以边沿触发也可以电平触发的触发器。
当J 和K输入端同时为1或0时,JK触发器可以实现边沿触发的功能。
而在其他触发器中,如D触发器、T触发器和RS触发器,通常只有电平触发功能,无法实现边沿触发。
4、以下哪个描述是正确的关于Verilog语言中initial和always语句的区别?A. initial语句用于初始化电路,而always语句用于描述电路的行为。
B. initial语句用于描述电路的行为,而always语句用于初始化电路。
C. initial和always语句都用于初始化电路。
D. initial和always语句都用于描述电路的行为。
答案:A 解析:在Verilog语言中,initial语句用于初始化电路,即在仿真开始时执行一次,通常用于赋初值。
Simplifying circuits for formal verification using parametric representation

Simplifying Circuits for Formal VerificationUsing Parametric RepresentationIn-Ho Moon,Hee Hwan Kwak,James Kukula,Thomas Shiple,and Carl PixleySynopsys Inc.,Hillsboro,ORSynopsys Inc.,Grenoble,Francemooni,hkwak,kukula,shiple,cpixley@ Abstract.We describe a new method to simplify combinational circuits whilepreserving the set of all possible values(that is,the range)on the outputs.Thismethod is performed iteratively and on thefly while building BDDs of the cir-cuits.The method is composed of three steps;1)identifying a cut in the circuit,2)identifying a group of nets within the cut,3)replacing the logic driving the groupof nets in such a way that the range of values for the entire cut is unchanged and,hence,the range of values on circuit outputs is unchanged.Hence,we parame-terize the circuit in such a way that the range is preserved and the representationis much more efficient than the original circuit.Actually,these replacements arenot done in terms of logic gates but in terms of BDDs directly.This is allowedby a new generalized parametric representation algorithm to deal with both inputand output variables at the same time.We applied this method to combinationalequivalence checking and the experimental results show that this technique out-performs an existing related method which replaces one logic net at a time.Wealso proved that the previous method is a special case of ours.This technique canbe applied to various other problem domains such as symbolic simulation andimage computation in model checking.1IntroductionGiven a complex Boolean expression that defines a function from an input bit vector to an output bit vector,one can compute by a variety of methods the range of output values that the function can generate.This range computation has a variety of applications such as equivalence checking and model checking.BDDs(Binary Decision Diagrams[4]) and SAT(Satisfiability[13,19])are two major techniques that can be used to perform the computation.In this paper we present a new BDD-based method,and describe its use in equivalence checking.However this new method can also be applied to other areas.The Boolean equivalence checking problem is to determine whether two circuits are equivalent.Typically,the circuits are at different levels of abstraction,one is a reference design and the other is its implementation.Equivalence checking is being used inten-sively in industrial design and is a mature problem.However there are still many real designs that current state-of-the-art equivalence checking tools cannot verify.BDD-based equivalence checking is trivial if the BDD size does not grow too large, however that is not the case in most of real designs.Therefore cut-based method[2,14,10]has been used to avoid building huge monolithic BDDs.The cut-based method introduces free variables for the nets in a cut,causing the false negative problem[2] since we lose the correlations on the free variables.When the verification result is false, this method has to resolve the false negatives by composing the free variables with their original functions.Even though this method has been used successfully,it still suffers from false negative resolutions that are very expensive and infeasible in many cases in real designs.To overcome the false negative problem,Moondanos et al.proposed the normalized function method[18].Instead of simply introducing a free variable for a net on a cut,the function driving the net is replaced with a simplified function which preserves the range of values on the cut.This simplified function is called a normalized function.However we have observed that the normalized function is not optimal and we have generalized the normalized function not to have redundant variables,as explained in Section4.A similar approach to the normalized function has been presented by Cerny and Mauras[6],which uses cross-controllability and cross-observability to compute the range of a cut from primary inputs,and the reverse range from primary outputs.Then equivalence checking can be done by checking whether the reverse range covers the range.In this method,once a set of gates is composed to compute the range,the vari-ables feeding only the gates are quantified,just as the fanout-free variables are quanti-fied in the normalized function.However this method suffers from BDD blowup since the range computation is expensive and the range of a cut represented by BDDs is very large in general.In this paper we present a new method to simplify circuits while preserving the range of all outputs.The method makes the work of Cerny and Mauras practical and also extends normalized functions to apply to a set of nets in a cut,instead of a single net.The new method is performed iteratively and on thefly while building BDDs of the circuits and is composed of three steps;1)identifying a cut in the circuit,2)identifying a group of nets within the cut,3)replacing the logic driving the group of nets in such a way that the range of values for the entire cut is unchanged and,hence,the range of values on circuit outputs is unchanged.We apply the range computation selectively by first identifying the group to be replaced in step2)and then estimating the feasibility and the gain from the computation in step3).Furthermore once the range is computed, we do not keep the computed range as Cerny and Mauras do.Instead we try to get a simplified circuit from the range by using a parametric representation[1,11].We also prove that the normalized function method is a special case of our method.Parametric representation has been used to model the verification environment based on design constraints[1,11].Various parametric representations of Boolean expressions have been discussed in[5,7,8,9,1,11].Parametric representation using BDDs was introduced by Coudert et al.[7,8]and improved by Aagaard et al.[1].The authors in[1] proposed a method to generate the parameterized outputs as BDDs from the constraints represented by a single BDD[1].However this method can deal with only the output variables of the environment,in other words the variables do not depend on the states of the design.Kukula and Shiple presented a method to deal with the output variables as well as the input variables that depend on the states of the design[11].Howeverthis method takes the environment represented by a relation BDD and generates theparameterized outputs as circuits instead of BDDs.In this paper we also present a generalized approach of the parametric representa-tions to deal with the input and output variables as well as to generate the parameterizedoutputs as BDDs.We also identify that the method in[1]is a special case of the one in[11]in the framework of our generalized approach.Combining the range computation and the generalized parametric representationmakes more efficient and compact representations of the circuits under verification so that the circuits can be easily verified.This approach can be applied to not only equiv-alence checking but also symbolic simulation as well as image computation.The rest of the paper is organized as follows.Section2reviews background material and Section3discusses prior work.We present our algorithm tofind sets of variablesfor early quantification in Section4.Section5shows the overall algorithm for equiv-alence checking and compares ours to the prior work.Section6describes a specialtype of range computation and Section7presents our methods for parametric represen-tation.Section8shows the relationship between normalization and parameterization. Experimental results are shown in Section9and we conclude with Section10.2PreliminariesImage computation isfinding all successor states from a given set of states in one stepand is a key step in model checking to deal with sequential circuits[15,17,16].Let and be the sets of present and next state variables and be the set of primary input variables.Suppose we have a transition relation that represents alltransitions,being true of just those triples of,,and,such that there is a transition from state to state,labeled by input.Image for given set of states is formally defined asRange computation is a special type of image computation where is the universe, in other words itfinds all possible successor states in a transition system.Rangeis defined as(1) 3Related Work3.1NormalizationTo overcome the false negative problem in BDD-based equivalence checking,Moon-danos et al.proposed a normalization method[18].The authors split the set of input variables of the current cut into and.is the set of fanout-free variables,in other words,the variables feeding only one net in the cut.is the set of fanout variables that fanout to more than one net in the cut.Then,the function of a net can be simpli-fied without causing false negatives by using its normalized function that preserves therange of the cut.To make the normalized function of,possible term and forced term of are defined as below.Then the normalized function is defined by(2) where is an that is newly introduced.3.2Parameterization with Output VariablesParametric representation using BDDs was introduced by Coudert et al.[7,8]and im-proved by Aagaard et al.[1].The authors in[1]used the parametric representation to make the verification environment from the input constraints of the design under veri-fication.Thus only output variables of the environment are considered since there is no constraint relating the states of the design.The basic idea is that each variable is parameterized with three cases for each path from the root to the leaf of the constraint BDD.However this operation is performed implicitly by calling recursively and by using a cache.The three cases are1) the positive cofactor of a node is empty,2)the negative cofactor is empty,and3)both cofactors are non-zeroes;BDD ONE or a parametric variable is assigned for each case,respectively.Then,the sub-results from the two children of a branch are merged by3.4Cross-Controllability and Cross-Observability RelationsCerny and Mauras have used cross-controllability and cross-observability for equiva-lence checking[6].Suppose we make a cut in a circuit containing two outputs of imple-mentation and specification,namely and,respectively.Let be the set of input variables and and be the set of cut variables in the implementation and specification, respectively.We then compute,which is the relation between and,and,which is the relation between and.Then cross-controllability is defined asCross-controllabilityWe can see that the cross-controllability is the range of the cut.Similarly,we compute ,which is the relation between and,and,which is the relation between and.Then cross-observability is defined asCross-observabilityWe can also see that the cross-observability is the reverse range of the two outputs in terms of and.Then equivalence checking can be done byCross-controllability Cross-observability(3) The authors proposed the three different checking strategies and one of those is forward sweep.In the strategy,the cut is placed at the primary outputs and the cross-controllability of the cut is computed by composing gates iteratively from the inputs to the outputs in such a way to eliminate any local variables that feed only some of the gates to be composed.When all gates are composed,Equation3is applied with trivial cross-observability.4Definition of and SetsIn this section,we start with an example to show that the method in Section3.1can introduce redundant variables.Then we define the set of variables we can early quan-tify not to have those redundant variables in simplifying the functions in a given cut. Furthermore we extend the definition to handle a group in the cut.Consider two functions and in terms of variables,,and.Then,from the normalization method,becomes and becomes.Then, the normalized functions for and are as below.In this example,it is easy to see that the variable is redundant in since the variable occurs only in.Actually the range of is tautologous.Socould be just,which is optimum.This is because even though the variable fans out to both and,the effect of the signal to is blocked by the signal,which is non-reconvergent.Therefore,we can move the signal into in this case so that we can quantify even.Now we formally define and for a cut.is the set of variables to keep in the simplified functions and is the set of variables to quantify out.Let be the set of functions for the nets in the current cut and be the set of variables that are in the support of the functions.Then, let us define quantified functions as below.(4)(5)where is the set of fanout-free variables in as shown in Section3.1.Let us also define a function(6)(7)where is the set of fanout variables in.Then and can be used instead of and in exactly the same way as in the method in Section3.1.We can further optimize the size of and by afixpoint computation as shown in Figure1so that we can quantify more variables as early as possible.In Figure1,Line1computes the initial and by assigning and,respec-tively.Line2computes the quantified functions using Equation4and5for each func-tion.For each variable in,Equation6is tested in Line4.If the condition is not satisfied,the variable is moved from to and is quantified from each and. The do-while loop in Line3is continued until and reach thefixed point.Using this and,Equation2can be improved by(8)By applying the new normalized function to the example,we get the optimally normalized functions=and=.Now we extend and to simplify many functions in a selected group at once in the cut.Since some variables in can feed only the nets in the group,these variables can be quantified when we build the relation of the group.This technique is already applied in[6].The extended and for the group are defined aswhere is the set of variables in that feed only the nets in the group and the variables in are local,meaning that the variables do not affect the other functions outside the group.FindFixpointKQ(,)1Find the initial and2for each()Compute and by quantifying3do=04for each()if(non-blocked1)++==Update each and by quantifyingwhile(0)return andFig.1.Procedure tofind thefixpoint K.5Overall Algorithm for Equivalence CheckingFigure2illustrates our overall algorithm for equivalence checking.CheckEquivalence takes a[3].The miter contains a specification circuit and its implementation circuit and the two circuits are XNORed so that the miter output is when the circuits are equivalent.First we set a cut in the circuit and this cut is moved from primary inputs toward the miter output.For a cut in the do-while loop in Line1,we build BDDs in Line2. If we fail to build the BDDs,we return in Line3.If the cut has reached the miter output,we decide the equivalence in Line4.Line5computes and.Then a group containing a subset of is selected iteratively in Line6by estimating the feasibility of range computation and the number of variables that can be quantified out. Line6refines and with respect to the selected group and this refinement will be explained in Section6.Line8computes the range of the group and Line9parameterizes the range if the range computation was successful and the range is deleted in Line10.The range computation and parameterization will be explained in Section6and Section7.There can be many heuristics for setting a cut andfinding a group and these problems are also crucial in terms of performance in practice.We refer the reader to[12]for detailed heuristics for identifying cuts and groups. The circuit topology is used for setting a cut and estimating the number of variables to quantify and to introduce forfinding a group.5.1Comparison to Prior WorkThe overall algorithm in Figure2is conceptually the combination of the work in[6,11, 18].However there are significant differences from their work.CheckEquivalence()1doSet a cut and let be the set of functions in the cut2Build BDDs for each function in3if(failed to build BDDs)return INCONCLUSIVE4if(reached to the compare point)if(BDD ONE(the compare point))return EQUIV ALENTelsereturn INEQUIV ALENT5Compute and6while(=FindGroup())7Compute and8if(=ComputeRange(,))9Parameterize(,)10Deletewhile(TRUE)Fig.2.Overall procedure for equivalence checking.Our algorithm is conceptually similar to the forward sweep in Section3.4.However the major differences are as follows.Our method1.does not require success of range computation.In general range computation is veryexpensive and requires huge memory space,and thus BDDs blow up quite often during the range computation.In[6]their method aborts once a range computation fails,whereas in our algorithm even if the range computation fails,we can take another group.2.does not keep the range.In many cases the size of the range BDD of a group isrelatively much larger than the shared size of the BDDs representing the circuits of the group.This is possible due to the parameterization of the range and the simpler BDDs representing the parameterized functions.3.does not need the range of all nets in the cut.The method in[6]requires the globalrange of the cut since all computed ranges are kept even though local range ofa group is computed at every composition,whereas our method throws away acomputed range once it is parameterized.4.may still have redundant variables theoretically.The method in[6]does not haveany redundant variables since the method keeps the ranges,whereas ours may still have some redundant variables in theory.However ours is practically optimal by computing in Section4since ours looks ahead only intermediate results of the range.Our parametric representation produces exactly the same functions as in[11].How-ever there are the following differences.Our method1.performs only single phase,instead of3phases.2.does not visit all BDD nodes.3.produces outputs as BDDs,instead of circuits.4.handles BDDs with complement arcs.Our approach is also quite similar to the normalized function method in[18].How-ever the normalized function method simplifies one function at a time,whereas our method can simplify multi functions at a time by using range computation and para-metric representation.Thus our method can simplify further as well as ours has more chances to simplify.Moreover the method in[18]can produce redundant variables as shown in Section4,whereas ours has very little chances.We also show that the normal-ization is a special case of parameterization.6-set Preserving Range ComputationThe key idea in Figure2is that we try to simplify the functions in the selected group by first computing the range of the group,and then parameterizing the computed range to get simpler functions.As shown in Figure2,once wefind a group containing a subset of all nets in the current cut,we then compute a special type of range of the group so that we preserve the range of all the nets in the cut.This is called-set preserving range computation and is formally defined aswhere is the conjuncted relations of all nets in the group,is the range variables for the nets in,and and are the extended and for the group.Theorem1.Once we preserve the relations between-set variables and the range variables in,the total range of all the nets in the cut is preserved.Proof.Suppose we have a cut and we make a group containing a subset of all nets in the cut.Let be the relation of all nets in,be the relation of all remaining nets outside,be the set of variables belong to and feeding any net in,andbe the set of variables belong to and feeding any net outside.And let be the set of range variables for the nets in and be for the nets outside.The total range of the cut without parameterization is(9)Now suppose that we parameterize the group by quantifying the variables in and introducing new parametric variables so that we preserve the relations between the variables in and the range variables such that(10)Parameterization preserving Equation10is the work in[11].By applying Equa-tion10,we can compute the total range with the parameterization as below.(11)Equation11is equal to Equation9,therefore we can conclude that the total range is preserved.7-set Preserving Parametric RepresentationOnce the-set preserving range of the group is computed in Section6,we try to get simpler functions of the group by parameterizing the range so that we preserve the range of the group as well as the total range of the cut with the parameterized functions.This is called-set preserving parametric representation.In-set preserving parametric representation,the input variables are the variables in and the output variables are the range variables.Thus we parameterize only the range variables by preserving the relations with the variables.Section7.1extends the method in[11]to make the differences mentioned in Sec-tion5.1,and Section7.2modifies the BFS(Breadth-first-search)approach in Section7.1 to a DFS(Depth-first-search)and shows that the two methods produce the same result. Section7.3describes the concept of the generalized parametric representation.7.1BFS ParameterizationKukula and Shiple presented a method of parametric representation to generate circuits from the relation BDD of the design environment[11].This method deals with the out-put variables of the environment as well as the input variables that depend on the states of the design under verification.For this purpose,input and output template modules are pre-defined and the parametric representations from the relation are obtained as a circuit by replacing each BDD node of the relation with the template modules.The equation form of the input template module in[11]is as below.(12) All BDD nodes of input variables in the relation are replaced with this module.Also the equation form of the output template module in[11]is as follows.(13)(14)All BDD nodes of output variables in the relation are replaced with this module.We have extended this method to generate BDDs directly so that we do not need to build BDDs for the parameterized circuits,and to handle complement arcs on BDDs. More differences have already been mentioned in Section5.1.The extension is based on the following observations.First from Equation12and 13of the input and output template modules,and are s of and child node,respectively.Thus,,and of a node whose function is and whose variable is can be rewritten by(15)where is the set of all output variables below in the BDD.This observation makes the computations without looking at children nodes when we generate BDDs directly. Secondly,and are used to make union of all s and s that point to a same child node and to makeof the child node.Thirdly,of an output variable is used to sum the s of all nodes of the variable and similarly are used to sum the s(Equation14)of all nodes of the variable.Fourthly,of a node is the case set to constrain the parameterization of the node.Fifthly,adding a mux for each output variables is to take care of the don’t care space of the variable.By using the observations,we propose the algorithm shown in Figure3that pro-duces BDDs directly with a single event-driven BFS step.The algorithm takes a rela-tion and a set of output variables.Line1finds all supports in and.Line2 initializes andfinds the variables in that do not occur in and assigns a parametric variable.Also is set to the level of the lowest output variable in so that we do not traverse the BDD nodes below the variable.Line3computes of the top node and adds an event on the node with the asof the node.Each output variable has an event queue.Each event queue for the cur-rent variable is selected in Line4and each event is poped in Line6until the event queue becomes empty in Line5.Line7is the case of input variables and if any child node is not below,is computed and is called.If an event is already in the queue,the active condition of the event is updated by adding the new.Otherwise a new event is created and added.Line8is the case of output variables and,,,,and are computed by the ob-servations mentioned above.Adding events is the same as in the case of input variables. Line9computes the parameterized output when the event queue becomes empty for the variable.Notice that this algorithm produces exactly the same function as in[11].BFSZEROif()if(Supp())=else=else=3==bdd topget level()))=PushQueue(,,)if((=bdd topget level()))PushQueue(,,)if((=bdd top7.2DFS ParameterizationThe algorithm in Figure3can be implemented in a DFS manner by using, ,and in Equation15.The algorithm is shown in Figure4and is quite similar to that in[1]except one difference,that the algorithm can handle both input and output variables.The algorithm takes(a relation),(the set of output variables),(the set of variables in and),(the set of parametric variables corresponding to),and (the number of variables in).Line1lookups the cache and returns the computed result if exists.Line2computes the positive and negative cofactors of with respect to thefirst variable in.Line3is the case of input variables and assigns to the input variable itself.Line4is the case of output variables and computes the parameterized output using Equation15.Line5recurs for each positive and negative cofactors.Line 6merges two sub-results from Line5by usingPR(,,,,)1if(=LookupCache(,,))return res2==3if()=4else===()5=DFSPR(,,&,&,-1)6for(=0,...,-2)if()=bddLet be the parameterized output of the top node of the BDD and be that of its child node and be that of its child node.Notice that both children nodes are in the same level of the BDD.Let be the parameterized output of the variable of the children nodes and we compute with the BFS and DFS separately.First we compute with the DFS.Then and of can be considered as on-set and off-set with respect to the output variable,respectively.Then we can define new on-set on and new off-set off as follows.onoffThen the generalized parametric representation for the node ison offwhere is a parametric variable.This parameterizes the output node regardless of pres-ence of input variables.8Relationship between Parameterization and Normalization Suppose we have a group containing only one net and let be the range vari-able of the net.Then-set preserving range is(18) Now we compute the parametric representation of to get a simplified function of. Since is the only range variable,we canfind its on-set on and off-set off.onoffTherefore the parametric representation of ison offwhere is a parametric variable.We can see that Equation19is exactly the same form as Equation8.Furthermore Equation19produces even more simplified circuits since is a superset of in Equation8,that is,more variables can be quantified with than with.Therefore normalization is a special case of parameterization when the numberof output variables is just one and when is replaced with.In the real implementation of this case,we do not need to compute in Equa-tion18since we can compute directly from.9Experimental ResultsWe have implemented the algorithm in Figure2and compared it to the normalized function method and also compared the BFS parameterization with the DFS.We have run all experiments on a750MHz SUN UltraSPARC-III with8GB memory.Table1shows the effectiveness of the method we present.The designs in thefirst column of the table are single compare points that are known as very hard and that existing state-of-the-art equivalence checkers fail to verify with various techniques such as BDD,SAT,ATPG,functional learning and so on.The designs are further modified to make them even harder by merging all internal equivalent points that are found by the various techniques.The second column shows the number of gates and the third and fourth columns give the number of primary input variables and the logic depth from an output to its inputs.The remaining columns compare the verification results.NONE stands for the method to build monolithic BDDs and NORM is the normalized function method.BFS PR is with the DFS.The results with NONE illustrate where the monolithic BDDs blow up;the numbers in the parentheses show in which level of depth it aborts.NORM verified3out of10 cases and there is an improvement in case by building BDDs12more depths compared to NONE.BFS PR verified8out of10cases and this shows that our method outperforms the normalized function method.However there are some cases in which ours also fails,and the failure cases can be categorized as follows:1)The BDDs are built to greater depths,however building BDDs even with the improvement is still too hard for the remaining part of the circuits as in test9.2)There is no improvement at all,meaning that even though the circuits are simplified by our method,it does not help much to build the BDDs for the remaining part of the circuits as in test10.Design Gates Depth NONE BFS DFS128Abort(35)Verified131Abort(55)Verified134Abort(49)Verified60Verified Verified57Verified Verified303Abort(16)Verified306Verified Verified1284Abort(14)Verified148Abort(25)Abort(27)202Abort(17)Abort(17)Table1.Verification results for different methods.Table2shows the performance in terms of time taken and consumed peak memory. In the table,the numbers with(*)show the time and peak memory until the cases were aborted at the depths shown in Table 1.For the designs()in which both NORM and ours can verify,even though ours uses the expensive range computations,the results were faster in and.However with the result was slower.This implies that identifying groups to apply the range computation is very crucial in performance since there were52range computations with more than one net in the case and we were able to get the range only8out of52cases.For the other。
裴悟达 VC Formal

DATASHEETOverview SoC design complexity demands fast and comprehensive verification methods to accelerate verification and debug, as well as shorten overall schedule and improve predictability. The VC Formal™ next-generation formal verification solution has the capacity, speed and flexibility to verify some of the most difficult SoC design challenges, and includes comprehensive analysis and debug techniques to quickly identify root causes in the Verdi ® debug platform. The VC Formal solution consistently delivers higher performance and capacity, with more bugs found, more proofs on larger designs and achieves faster coverage closure through the native integration with VCS ® functional verification solution.Verification Challenges and Modern Formal Verification The VC Formal solution includes a comprehensive set of formal applications (Apps), including Property Verification (FPV), Automatic Extracted Properties (AEP), Coverage Analyzer (FCA), Connectivity Checking (CC), Sequential Equivalence Checking (SEQ), Register Verification (FRV), X-Propagation Verification (FXP), Testbench Analyzer (FTA), Regression Mode Accelerator (RMA), Datapath Validation (DPV), Functional Safety (FuSa), and a portfolio of Assertion IPs (AIP) for verification of standard bus protocols. Formal methods are techniques that can perform analysis on the design independent of, or in conjunction with simulation, and have the power to identify design problems that can otherwise be missed until very late in the project schedule, or even in the manufactured silicon, when changes are expensive and debug is highly challenging and time consuming. When applied early in the design cycle, these methods can identify RTL issues such as functional correctness and completeness well before the simulation test environment is up and running.Delivering thehighest performanceand capacity withmore design bugsfound, more proofs,and faster coverageclosureVC Formal Next-Generation Formal VerificationAdditional applications of formal technology can verify SoC connectivity correctness and completeness, and help isolate differences between two disparate versions of the design RTL.Once the simulation environment is available, formal methods can complement simulation to add additional analysis for even better results, for example, for unreachable coverage goals.By employing formal techniques at the appropriate time in the design and verification process, bugs can be caught significantly earlier in the project, including hard-to-find-bugs that typically elude verification until late in the project. The result is a higher quality design and overall schedule improvements as well as better predictability.Design Coverage Task progressTarget propertiesOverall statusInteractiveTcl shellInteractiveWaveform viewerFigure 2: Unified Verdi Debug for Formal and SimulationVC FormalVC Formal is a high capacity, high performance formal verification solution that includes best-in-class algorithms, methodologies, databases and user interfaces. Built from the ground up, this solution was architected to address today’s most challenging verification tasks, and provides the very latest and best formal verification engines available.Formal complexityanalysisBug hunting modeRun progressreportingOver constraint/boundedcoverage Formal core coverageNavigatorFigure 3: VC Formal Property Verification (FPV)Key Features and Benefits• Assertion-Based Property Verification (FPV): Formal proof-based techniques to verify SystemVerilog Assertion (SVA) properties to ensure correct operation across all possible design activity even before the simulation environment is available. Advanced assertion visualization, property browsing, grouping and filtering allows simple concise access to results.• Datapath Validation (DPV): Integrated HECTOR™ technology within VC Formal and contains custom optimizations and engines for datapath verification (ALU, FPU, DSP etc.) using transaction level equivalence. This app leverages the Verdi graphical user interface for debug.• Automatic Extracted Property Checks (AEP): Automatic functional analysis for out of bound arrays, arithmetic overflow, X-assignments, simultaneous set/reset, full case, parallel case, multi driver/conflicting bus and floating bus checks without the need for dedicated tests• Formal Coverage Analysis (FCA): Complementing simulation flows, VC formal provides proof that uncovered points in coverage goals are indeed unreachable, allowing them to be removed from further analysis—saving significant manual effort• Connectivity Checking (CC): Verification of connectivity at the SoC level. Flexible input format ensures ease of integration.Powerful debugging, including value annotation, schematic viewing, source code browsing and analysis reporting speeds analysis. Automatic root-cause analysis of unconnected connectivity checks saves significant debug time• Sequential Equivalency Checking (SEQ): Verify modifications to the designs that do not affect the output functionality. For example, changes after register retiming, insertion of clock gating for power optimization or microarchitecture changes can be exhaustively verified without running any simulations.• Register Verification (FRV): Formally verify that the attributes and behaviors of configuration and status register addresses and fields are correctly implemented and accessed. For example, attributes such as "read only", "read/write" or "reset value" can be defined in IP-XACT and formally verified, eliminating the need for directed simulation tests.• X-Propagation Verification (FXP): Checks for unkown signal value (X) propagation through the design and allows tracing of the failed property to source X in the Verdi schematic and waveform.• Formal Testbench Analyzer with Certitude Integration (FTA): Certitude™ provides the unique capability to assess the quality of formal environment. The native integration of Certitude with VC Formal provides meaningful property coverage measurements as part of formal signoff, and identifies any weaknesses such as missing or incorrect properties or constraints. The native integration delivers 5-10X faster performance compared to stand-alone fault injection methods• Security Verification (FSV): Helps formally verify that secure data should not reach non-secure destinations and ensures data integrity, where non-secure data should not over-write (or reach) secure destinations• Regression Mode Accelerator (RMA): Provides significant performance improvement to formal property verification using Machine Learning technology. Use of this app accelerates formal propety verification to achieve better convergence of formal proofs for subsequent runs and enables significant saving of compute resources in nightly formal regressions.• Assertion IP (AIP): A portfolio of high performance and optimized Assertion IPs for standard bus protocols are available for all VC Formal Apps as well as VCS and ZeBu®. Some of the most popular titles available are Arm® AMBA® APB, AHB, AXI3, AXI4, ACE-lite, ACE, and CHI protocols.• Functional Safety (FuSa): Functional safety verification is an essential requirement for automotive SoC and IP designs. This App formally identifies and classifies faults based on observability or detectability criteria. Complementing fault simulation with Z01X™, the combined solution reduces the effort and time required to achieve the test coverage closure.• Advanced Debug and Interactivity: Advanced debugging interface built on Unified Verdi GUI based RTL and waveformvisualization solutions, including schematic value annotation, on the fly assertion and constraint editing, proof progress feedback, and cone of influence analysis allows users greater visibility and control• Formal Scoreboard: Exhaustively verifies the data integrity of data path designs. Ensures that data is transported through the design without being lost, re-ordered, corrupted or duplicated• Formal Coverage: Advanced technologies enable formal metrics and methodology to achieve signoff for property verificationUnique Values• Industry-leading performance and capacity: Ability to efficiently run on large designs. At least 5X performanceand capacity gains• Excellent ease of adoption and ease-of-use: Use model and commands tightly aligned with Synopsys implementation tools. VC Formal scripts are very similar to Design Compiler® TCL script, and share common commands and syntax• Run control features: Enabling grid, pause/resume and save/restore• Excellent connectivity checking features, including schematic value annotation and root-cause analysis: Significantly improving state-of-the-art debug, including debug of disconnected nets• Engine analysis and control: Ability to examine and control engine activity across the run, and on the fly to better ensure closure on even the most challenging formal problemsConclusionAdoption of advanced formal verification techniques is growing rapidly to improve design verification. The automation of certain verification tasks, such as SoC connectivity verification, formal coverage analysis, and sequential equivalence checking significantly accelerates the ease of technology adoption. In addition, the common script environment and common setup makes adding launching new formal apps as simple as typing in a few new commands into a previously created script, or a simple click on the GUI. With the integration of industry-standard VCS® simulation and Verdi® debug solutions, the true power of formal verification can be realized.By employing next-generation formal verification at opportune points in the design verification process, challenging bugs can be caught significantly earlier in the verification schedule, resulting in a higher quality design, overall schedule improvements as well as better predictability.For more information about Synopsys products, support services or training, visit us on the web at: , contact your local sales representative or call 650.584.5000.©2022 Synopsys, Inc. All rights reserved. Synopsys is a trademark of Synopsys, Inc. in the United States and other countries. A list of Synopsys trademarks isavailable at /copyright.html . All other names mentioned herein are trademarks or registered trademarks of their respective owners.。
欧洲高校计算机专业的形式化方法课程教学

99文章编号:1672-5913(2008)10-0099-05欧洲高校计算机专业的形式化方法课程教学古天龙,董荣胜(桂林电子科技大学,广西 桂林 541004)摘 要:本文对欧洲高等院校的计算机相关专业形式化方法教育进行了介绍,主要包括形式化方法课程的知识体系、形式化方法教育的课程及其内容。
关键词:计算机学科;形式化方法;知识体系;欧洲高校 中图分类号:G642 文献标识码:B形式化方法是基于严密的、数学上的形式机制的计算机系统研究方法。
从20世纪90年代开始,计算机学科相关专业的形式化方法的教育引起了欧美教育界的高度重视和关注。
欧洲的英国、德国、法国、意大利、荷兰、西班牙等国家的高校相继为研究生开设了形式化方法方面的课程,并推广至本科生教育。
从20世纪90年代中期开始,美国高校也开展了形式化方法教育研究,并在美国顶尖的35所大学的计算机学科实施了研究生和本科生的教育实践。
IEEE-CS 和ACM 联合任务组于2005年9月提交了计算教程CC2005(Computing Curricula 2005)最终报告,该报告的软件工程分册CCSE(Computing Curriculum- Software Engineering 2004)将“软件工程的形式化方法(Formal Methods in Software Engineering)”列为一门核心课程。
CC2005最终报告的推出对计算机学科相关专业的形式化方法教育产生了重要的影响。
欧洲形式化方法协会于2001年成立了专门的形式化方法教育研究分会FME-SoE(Formal Methods Europe Association - Subgroup on Education),目的在于研究并提出高等院校本科生形式化方法教育的知识体系及课程内容。
该组织于2004年11月发布了对欧洲11个国家、58所高等院校中的117门形式化方法教育相关课程的调研报告。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Formal Verification of MIX ProgramsJean-Christophe Filliˆa treCNRSLRI,Univ Paris-Sud,Orsay F-91405INRIA Futurs,ProVal,Orsay F-91893AbstractWe introduce a methodology to formally verify MIX programs.It consists in annotatinga MIX program with logical annotations and then to turn it into a set of purely sequentialprograms on which classical techniques can be applied.Contrary to other approaches ofverification of unstructured programs,we do not impose the location of annotations but onlythe existence of at least one invariant on each cycle in the controlflow graph.A prototypehas been implemented and used to verify several programs from The Art of ComputerProgramming.1IntroductionMIX is a machine introduced by D.Knuth in The Art of Computer Programming[5]and equipped with an assembly language.If it looks outdated compared to today’s computers,it is nonetheless a language with a clearly exposed semantics and the vehicle of many algorithms described in this set of books.It is thus quite natural to consider proving such programs in a formal way. Moreover,the techniques involved in the verification of assembly-like programs have direct applications in domains such as Proof Carrying Code[8]or safety of low-level C programs.Our approach to formally verifying MIX programs is built on previous works on the veri-fication of C and Java programs[3].The general idea is to specify a program using logical annotations inserted in its source code,and then to translate the program into an intermedi-ate language suitable for Hoare logic[4].The output is a set of verification conditions,that is a set of logical formulae whose validity implies the correctness of the program.Discharg-ing the verification conditions can be done using existing theorem provers,either automatic or interactive.The formal specification of structured programs is naturally done using pre-and postcon-ditions for functions and loop invariants.Assembly programs,on the contrary,do not favor any particular program point for logical assertions.Recent work has identified the entry points of natural loops as obvious candidates for such assertions[1],but ourfirst experiments show that it can be a constraint.This is why we choose an approach where assertions can be freely inserted at any program point.We only impose that any cycle in the controlflow graph contains at least one assertion.Then it is possible to turn a MIX program into a set of purely sequential programs without jumps(either conditional or unconditional).In a second step,these programs are interpreted in a model where it is possible to apply the usual techniques of Hoare logic.Section2introduces our methodology.Section3describes a prototype and ourfirst experi-ments.We conclude with possible future work.X EQU1000ORIG3000MAXIMUM STJ EXIT←−PreINIT ENT30,1JMP CHANGEMLOOP CMPA X,3JGE*+3CHANGEM ENT20,3LDA X,3DEC31←−InvJ3P LOOP←−PostEXIT JUMP*Figure1:Program M(TAOCP,vol.1,page145).2MethodologyWefirst show how to annotate a MIX program using logical assertions(section2.1).Then we give an algorithm to turn this program into a set of purely sequential programs(section2.2).Finally we explain how to get verification conditions from these sequential programs(section2.3)and we prove the soundness of our method(section2.4).2.1SpecificationLet us consider thefirst program illustrating MIX,namely program Mfinding the maximum of the elements of an array[5,page145].This program is given Figure1.It assumes that the size of the array is in register I1,that the array contains at least one element,and that the elements are stored in memory at addresses X+1,...,X+I1.When the program return,accumulator A contains the maximum element and register I2an index where it appears.Thefirst step consists in specifying this behavior by inserting logical annotations in program M.There are three such annotations:•a precondition indicating the assumption at the program entry point,namelyPre≡I1≥1inserted at program point MAXIMUM;•a postcondition indicating the expected property at the end of execution,namely the annotationPost≡1≤I2≤I1∧A=X[I2]∧∀i,1≤i≤I1⇒A≥X[i] inserted a program point EXIT;•and an invariant indicating the property maintained by the program,namely the anno-tationInv≡0≤I3≤I1∧1≤I2≤I1∧A=X[I2]∧∀i,I3<i≤I1⇒A≥X[i] inserted right before instruction J3P.These three annotations are indicated on Figure1.The meaning of an annotation is clear:each time execution reaches an annotation,it must be verified.Figure2:Controlflow graph for program M.traverse(n)=if n is currently visited then fail(we found a cycle with no invariant)if n has not yet been visited thenfor each transition n s→mcall traverse(m)if m is an invariant I thenassociate to n the code s;assert Ielseassociate to n the code s;s for each code s associated to mif n is an invariant J the prefix each code of m by assume JFigure3:Sequentialization algorithm.2.2SequentializationThe next step is to turn the MIX program into a set of purely sequential programs which do not contain jumps anymore,and whose correctness imply the correctness of the initial program. To do so,wefirst build the controlflow graph,where nodes correspond to program points and transitions to sequences of instructions and test results.Such a controlflow graph for program M is given Figure2.The key idea is to impose the presence of(at least)one annotation on each cycle in the controlflow graph.Annotations are considered as invariants here:they must be verified when reached initially and maintained by any path used to come back.(In the remainder of this section we will refer to annotations as invariants instead of assertions to make it clearer.) Our sequentialization algorithm simply performs a depth-first traversal of the graph from the entry point,associating to each node a set of purely sequential programs.Pseudo-code for this algorithm is given Figure3.The result of sequentialization is the set of programs associated to the entry point and to each invariant encountered during the traversal.The result for program M is the set of four codes,given Figure4.Keyword assume introduces an assumption and keyword assert a property to be verified.These programs are naturally interpreted as follows:seq1is the initial validity of the invariant Inv;seq2and seq3express the preservation of Inv on the two possible paths;finally seq4expresses the validity of the postcondition.It is important to notice that this algorithm is not related to MIX but could be used with any assembly-like language.seq1≡assume Pre ENT30,1 ENT20,3 LDA X,3 DEC31 assert Inv seq2≡assume Invassume I3>0CMPA X,3assume CMP≥0DEC31assert Invseq3≡assume Invassume I3>0CMPA X,3assume CMP<0ENT20,3LDA X,3DEC31assert Invseq4≡assume Invassume I3≤0assert Post Figure4:Sequentializing program M.2.3Generating the Verification ConditionsThe last step consists in generating verification conditions from the sequential programs i.e.log-ical formulae whose validity implies the correctness of the initial program.For this purpose,we can use traditional Hoare logic[4],or more conveniently a calculus of weakest preconditions[2], provided some logical model of MIX programs:•registers A,X,I1,...I6are modeled as global integer variables;•the memory is modeled as a global array of integers;•flags E,G and L are interpreted as the sign of a unique global variable CMP. Furthermore,we make the following assumptions:•direct use of register J is not supported(only the co-routine pattern is recognized and handled separately);•input-output instructions are not modeled:they can be used in programs but the user has to state assumptions about data which is read.2.4SoundnessIn this section we prove the soundness of our method.Let us write S={seq1,...,seq k}the set of purely sequential programs resulting from the sequentialization.Each seq i has the following shapeassume P is iassert Q iwhere P i and Q i are user invariants and s i is a purely sequential program which does not contain any invariant(but with possible assume declarations corresponding to test results).Let us assume an operational semantics for purely sequential MIX programs,as a set of states and a transition relation between states written S1s−→S2which means“execution of program s in state S1leads to state S2”.We note S|=I if invariant I holds in state S.The correctness of each program seq i means that in any state S1such that S1|=P i and for any state S2such that S1s i−→S2we have S2|=Q i.Note that we are only considering partial correctness.Soundness can be stated as follows:Theorem1(soundness)Let S be a state satisfying the invariant I at entry point,i.e.S|=I, and let us consider an execution reaching a program point with an invariant J in state S .Then S |=J.Proof.Let us consider all the intermediate states where the execution reaches an invariant. By definition of the sequentialization algorithm,there is afinite number of steps between two such states(otherwise we would have a cycle in the controlflow graph without any invariant). Therefore the execution looks like−→S n=S−→S2...s nS=S0s1−→S1s2where each state S i is associated to an invariant I i,with I0=I and I n=J.Each triple (I i−1,s i,I i)exactly corresponds to one sequential program in S,since invariant I i−1can be reached in the controlflow graph from the entry point,and since there is path from I i−1to I i in this graph which does not cross any other invariant.Then proving S i|=I i is a straightforward induction,since S0|=I0by assumption and since the correctness of the sequential programs implies that if S i−1|=I i−1and S i−1s i−→S i then S i|=I i.3Implementation3.1PrototypeWe implemented our method as a prototype tool,called demixify,taking annotated MIX programs as input and generating verification conditions in the native syntax of several theorem provers. Our tool uses the back-end of the Why platform[3],which provides an intermediate language dedicated to program verification.Thus our prototype is simply a front-end which parses annotated MIX programs,performs the sequentialization and then prints the resulting programs in the syntax of the Why tool.Then we rely on the Why tool to compute the verification conditions and to dispatch them to interactive provers(such as Coq,PVS,Isabelle/HOL,etc.) or automatic provers(Simplify,Ergo,Yices,etc.).In practice,demixify is run on afile file.mix to produce a Whyfile file.why.Then it is possible to use tools from the Why platform on thisfile(to compute the verification conditions,display them,launch provers,display the results,etc.).Inside file.mix annotations are inserted between brackets.One pair of brackets{P}stands for an assertion to be verified at the corresponding program point and double brackets{{P}}stands for an invariant.A quotation mechanism allows to insert pure Why code inside the inputfile,using the syntax{{{ why code}}}.This is typically used to insert a prelude containing parameters for the program or logical declarations for its specification.Within annotations,the current values of registers is referred to using the names A,I1,I2, etc.The current value at address p in memory is denoted by mem[p].3.2Case StudiesUp to now,we only verified very simple MIX programs,such as program M above(which is verified fully automatically).We briefly describe some of these case studies in this section.3.2.1Sequential SearchingWe consider here three implementations of sequential searching from Section6.1of The Art of Computer Programming[7,page397].The goal is to check whether a given value stored at address K appears in an array of N values stored at addresses KEY+1,...,KEY+N.First,we introduce KEY,K and N as parameters,using the quotation for Why code: {{{logic KEY,K,N:int}}}Thefirst implementation(Program S page397)simply scans the array from index1to index N.It can be annotated as follows:start:{{N≥1}}lda Kent11-N2H:{{1≤N+I1≤N∧A=mem[K]∧∀i,1≤i<N+I1⇒mem[K]=mem[KEY+i]}}cmpa KEY+N,1je successinc11j1np2Bfailure:{∀i,1≤i≤N⇒mem[K]=mem[KEY+i]}hltsuccess:{mem[K]=mem[KEY+N+I1]}The postcondition is split into two assertions at labels failure and success,respectively.The loop invariant is here located at the loop entry point(label2H).It may seem unnecessary to add A=mem[K]in the loop invariant,since A and K are not modified in the loop body,but there is currently no mechanism to get such invariant for free.When demixify is run on this program,it generates10verification conditions(when splitting conjunctions),all discharged automatically using an automatic theorem prover such as Simplify or Ergo.The next implementation(Program Q page397)improves on the previous one by setting a sentinel at address KEY+N+1,namely the value to be searched for.The annotated code is as follows:start:{{N≥1}}lda Ksta KEY+N+1ent1-Ninc11{{1≤N+I1≤N+1∧A=mem[K]∧mem[KEY+N+1]=A∧∀i,1≤i<N+I1⇒mem[K]=mem[KEY+i]}}cmpa KEY+N,1jne*-2j1np successfailure:{∀i,1≤i≤N⇒mem[K]=mem[KEY+i]}hltsuccess:{mem[K]=mem[KEY+N+I1]}The specification is exactly the same,apart from the addition of a specification for the sentinel in the loop invariant,namely mem[KEY+N+1]=A.Note that the loop invariant is placed one instruction after the loop entry point(which is located here right before instruction inc11). As we already did with program M,we notice that it is convenient to have freedom in invariant locations.For this second implementation,12verification conditions are generated and all are automatically discharged.The last improvement consists in unrolling the loop once,in order to save one increment (Program Q’page398).The specification is exactly the same as for program Q:start:{{N≥1}}lda Ksta KEY+N+1ent1-1-N3H:inc12{{1≤N+I1≤N+1∧A=mem[K]∧mem[KEY+N+1]=A∧∀i,1≤i<N+I1⇒mem[K]=mem[KEY+i]}}cmpa KEY+N,1je4Fcmpa KEY+N+1,1jne3Binc114H:j1np successfailure:{∀i,1≤i≤N⇒mem[K]=mem[KEY+i]}hltsuccess:{mem[K]=mem[KEY+N+I1]}Again the loop invariant is not placed at the loop entry point but immediately after the in-crement instruction(inc12here).Running demixify on program Q’results in14verification conditions.All are automatically discharged,but one.Not surprisingly,this is the preservation of the property∀i,1≤i<N+I1⇒mem[K]=mem[KEY+i]when I1is incremented by2,i.e.after two successive negative tests.Thus the proof requires two case analyzes to distinguish between1≤i<N+I1,i=N+I1and i=N+I1+1.It seems to be out of reach of the heuristics involved in the automatic theorem provers we are using. 3.2.2Selection SortOur last case study is a proof of straight selection sort[7,Program S page140].The purpose of this program is to sort in place the values stored at locations INPUT+1,...,INPUT+N,in increasing order.We start a Why prelude with the declaration of parameters N and INPUT:{{{logic N,INPUT:intNext we introduce predicate definitions to simplify annotations.Thefirst such predicate is the main invariant of selection sort,which states that the upper part of the array INPUT+ i,...,INPUT+N is already sorted and that all values in the lower part are smaller than values in the upper part:predicate Inv(a:int array,i:int)=sorted_array(a,INPUT+i,INPUT+N)andforall k,l:int.1<=k<=i-1->i<=l<=N->a[INPUT+k]<=a[INPUT+l]Here we use a predefined predicate sorted array from Why’s standard library.The second predicate is the permutation property.Indeed,we not only need to prove that thefinal array is sorted but also that it is a permutation of the initial.For this purpose we introduce an auxiliary variable mem0representing the initial contents of the memory and we use a predefined predicate sub permut from Why’s standard library:logic mem0:int farraypredicate Perm(m:int array)=sub_permut(INPUT+1,INPUT+N,m,mem0)}}}We are now in position to annotate the MIX code for selection sort:init:{{N≥2∧Perm(mem)}}ent1N-12H:{{1≤I1≤N−1∧Inv(mem,I1+2)∧Perm(mem)}}ent20,1ent31,1lda INPUT,38H:{{1≤I1≤N−1∧Inv(mem,I1+2)∧Perm(mem)∧1≤I2<I3≤I1+1∧A=mem[INPUT+I3]∧∀k,I2+1≤k≤I1+1⇒mem[INPUT+k]≤mem[INPUT+I3]}} cmpa INPUT,2jge*+3ent30,2lda INPUT,3dec21j2p8Bldx INPUT+1,1stx INPUT,3sta INPUT+1,1dec11j1p2B{sorted array(mem,INPUT+1,INPUT+N)∧Perm(mem)}This annotated code generates42verification conditions,all discharged automatically.3.2.3Other Case StudiesA proof of algorithm I(inversion of a permutation in place)is already engaged.We could also consider the formal proof of Knuth’s algorithm for thefirst N prime numbers performed by L.Th´e ry a few years ago[9]:the proof was done using Why and Coq directly and we could turn it into a proof of the original MIX code.4Conclusion and Future WorkWe have presented a methodology for the formal verification of MIX programs.A prototype has been implemented and thefirst experiments are encouraging.There are many possible extensions for this work.One improvement would be the ability to prove the termination of MIX programs,by addition of variants on each cycle of the controlflow graph,as we did for invariants. Another interesting extension would be formal reasonings regarding the complexity of MIX programs,since one of MIX’s main interests is precisely to allow a detailed complexity analysis. For this purpose,we could automatically associate counters to program lines in our model of MIX programs,and make it possible for the user to refer to these counters in annotations. Acknowledgements.I am sincerely grateful to L.Th´e ry for his suggestion to consider the formal proof of MIX programs.References[1]Mike Barnett and K.Rustan M.Leino.Weakest-Precondition of Unstructured Programs.In6th ACM SIGPLAN-SIGSOFT Workshop on Program Analysis for Software Tools and Engineering(PASTE),Lisbon Portugal,September2005.[2]Edsger W.Dijkstra.A discipline of programming.Series in Automatic Computation.Pren-tice Hall Int.,1976.[3]Jean-Christophe Filliˆa tre and Claude March´e.The Why/Krakatoa/Caduceus Platform forDeductive Program Verification.In19th International Conference on Computer Aided Ver-ification,2007.[4]C.A.R.Hoare.An axiomatic basis for computer munications of theACM,12(10):576–580,583,1969.[5]D.E.Knuth.The Art of Computer Programming.Volume1:Fundamental Algorithms.Addison-Wesley,1968.[6]D.E.Knuth.The Art of Computer Programming.Volume2:Seminumerical Algorithms.Addison-Wesley,1969.[7]D.E.Knuth.The Art of Computer Programming.Volume3:Sorting and Searching.Addison-Wesley,1973.[8]George C.Necula.Proof-carrying code.In Conference Record of POPL’97:The24th ACMSIGPLAN-SIGACT Symposium on Principles of Programming Languages,pages106–119, Paris,France,jan1997.[9]Laurent Th´e ry.Proving Pearl:Knuth’s algorithm for prime numbers.In Proceedings ofthe16th International Conference on Theorem Proving in Higher Order Logics(TPHOLs 2003),2003.。
