matlab on aws ec2
ec2实列只允许远程安全连接的入站规则

EC2实例是Amazon Web Services(AWS)提供的一种弹性计算服务,用户可以在上面运行不同的工作负载,如全球信息站托管、应用程序部署、大数据处理等。
在使用EC2实例的过程中,安全性是一个非常重要的考虑因素,而远程安全连接的入站规则则是其中一项关键的安全设置。
一、什么是EC2实例?EC2实例是云计算领域中一种常见的服务器托管服务,用户可以通过AWS控制台或API创建、启动和停止EC2实例,并且可以根据实际需求选择不同规格的实例类型,比如计算密集型实例、存储优化型实例等。
EC2实例的灵活性和可扩展性使其成为许多企业和个人选择部署应用程序的首选评台。
二、为什么需要远程安全连接的入站规则?在使用EC2实例时,用户通常需要通过远程连接方式(如SSH、RDP 等)来管理实例、部署应用程序或者进行其他操作。
为了保证连接的安全性,用户需要设置一些入站规则来限制可以连接到实例的IP位置区域、协议和端口范围。
这样做可以有效地减少未经授权的访问,降低系统被攻击的风险。
三、如何设置远程安全连接的入站规则?1. 登入AWS控制台用户需要登入AWS管理控制台,并找到所需的EC2实例。
在EC2 Dashboard页面上,可以看到各个实例的基本信息和状态。
2. 进入安全组设置选择需要设置远程安全连接的实例,然后在实例详情页面中找到安全组设置。
安全组是一种虚拟防火墙,用于控制进出实例的流量。
3. 设置入站规则在安全组设置页面中,找到入站规则设置,点击“编辑入站规则”按钮。
根据实际需求,可以添加或修改规则,比如允许特定IP位置区域范围、特定协议和端口号的连接。
四、入站规则设置的注意事项1. 最小权限原则在设置入站规则时,应该遵循最小权限原则,即只开放必要的端口和协议,尽量避免开放所有流量。
如果只需要通过SSH连接到实例,则只需开放22端口的TCP流量。
2. 定期审查和更新规则安全设置并非一劳永逸,用户应该定期审查和更新入站规则,及时删除不再需要的规则,避免滥用或错误配置导致安全漏洞。
AWS EC2 登录和使用说明

连接到您的Linux实例收集实例信息请收集如下实例信息:Linux终端:使用ssh连接到Linux实例步骤一:使用chmod命令确保您的私有密钥不是公开可见的。
例如,如果您的私有密钥文件的名称是my-key-pair.pem,请使用以下命令:步骤二:使用ssh命令连接到实例。
您将指定私有密钥(.pem) 文件和user_name@public_dns_name。
对于Amazon Linux,用户名称是ec2-user。
对于RHEL5,用户名称是root或ec2-user。
对于Ubuntu,用户名称是ubuntu。
对于Fedora,用户名称是fedora或ec2-user。
对于SUSE Linux,用户名称是root 或ec2-user。
另外,如果ec2-user和root无法使用,请与您的AMI 供应商核实。
本次比赛是采用的Ubuntu系统,因此连接方式参考如下命令您将看到如下响应。
输入yes,您将看到如下响应使用SCP 将文件从Linux 传输到Linux 实例在您的本地计算机与Linux 实例之间传输文件的一种方法是使用安全复制(SCP)。
本节介绍了如何使用SCP 传输文件。
这个程序和使用SSH 连接到实例的程序非常相似。
1.在命令shell 中,将目录更改为您启动实例时所指定的私有密钥文件的位置。
2.使用chmod命令确保您的私有密钥不是公开可见的。
例如,如果您的私有密钥文件的名称是my-key-pair.pem,请使用以下命令:3.使用实例的公有DNS 名称将文件传输到您的实例。
举例来说,如果私有密钥文件的名称是my-key-pair、要传输的文件是SampleFile.txt、实例的公有DNS 名称是,则可以使用以下命令将文件复制到ubuntu主目录。
Tip对于Amazon Linux,用户名称是ec2-user。
对于RHEL5,用户名称是root或ec2-user。
对于Ubuntu,用户名称是ubuntu。
Amazon AWS EC2使用说明文档
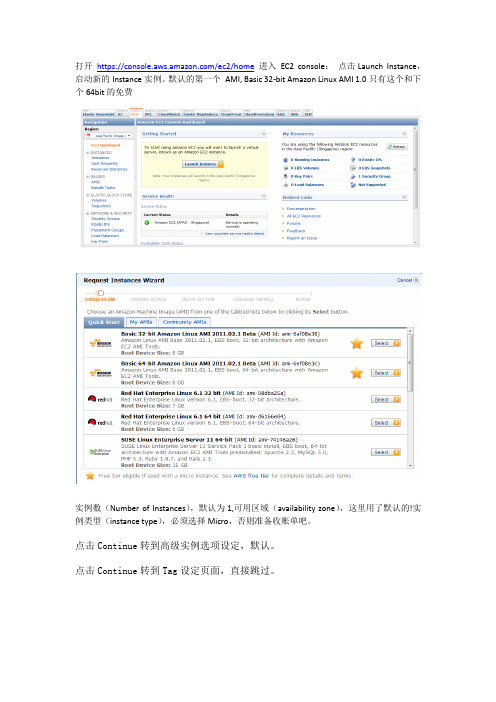
打开https:///ec2/home进入EC2 console:点击Launch Instance,启动新的Instance实例。
默认的第一个AMI, Basic 32-bit Amazon Linux AMI 1.0只有这个和下个64bit的免费实例数(Number of Instances),默认为1,可用区域(availability zone),这里用了默认的!实例类型(instance type),必须选择Micro,否则准备收账单吧。
点击Continue转到高级实例选项设定,默认。
点击Continue转到Tag设定页面,直接跳过。
点击Continue进入”Create Key Pair”,这一步比较关键,会下载一个pem结尾的密匙文件!用于连接建成的instance!随便起一个名字,特别提醒:由于ie安全设置,会阻止下载,等你点击同意时候,会刷新页面,导致无法下载密匙!建议先调低安全设置!略过截图!点击View your instances on the Instances page察看Instance状态。
您应该已经看到有一个 t1.micro status为Running,至此您的micro intance 已经启动,意味这您有一台可以ssh登陆的linux服务器啦。
SSH proxy在Linux下很简单,一条命令即可:以下为引用的内容:$mv ~/Downloads/fookey.perm ~/.ssh/$chmod 400 ~/.ssh/fookey.perm$ssh -i ~/.ssh/ec2.pem ec2-user@YOUR_AMAZON_PUBLIC_DNS -f -N -D 10003系统只允许通过key密钥登陆我们安装的AMI,默认登陆用户为ec2-user用你的Public DNS代替YOUR_AMAZON_PUBLIC_DNS1. SSH如果是Mac或者Linux用户,那么可以使用命令行方式的ssh,在EC2 Instance 上点右键,选择Connect,会出现以下页面提示你该如何通过ssh连接此实例。
云计算第三版Amazon云计算AWS

3.1 基础存储架构Dynamo
《云计算》第三版配套PPT课件
成员资格及错误检测
为了避免新加入的节点之间不能及时发现其他节点的存在,Dynamo中设置了一些 种子节点(Seed Node)。种子节点和所有的节点都有联系。当新节点加入时, 它扮演一个中介的角色,使新加入节点之间互相感知。
新节点 1
新节点 2
直到N个节点全部传遍
结论:
Dynamo中的节点数不能太多 Amazon采用了分层Dynamo结构 来解决该问题
25 of 52
容错机制 《云计算》第三版配套PPT课件
由于成本方面的原因,Dynamo中很多服务器采用的是普通 PC主机; 其硬盘性能和专业服务器硬盘相差很远,出错很难避免; Dynamo中容错机制非常重要
11 of 52
《云计算》第三版配套PPT课件
数据均衡《云分计算布》第的三版问配套P题PT课件
➢一致性哈希算法
平衡性 单调性 分散性 负载
两步进行:
求出设备节点的哈希值,并
配置到环上的一个点;接着
计算数据的哈希值,按顺时
针方向将其存放到环上第一
个大于或等于数据哈希值的
节点上; 添加新节点时,按
照上述规则,调整相关数据
问题 数据均衡分布
数据备份 数据冲突处理 成员资格及错误检测 临时故障处理 永久故障处理
采取的相关技术 改进的一致性哈希算法 参数可调的弱quorum机制 向量时钟(Vector Clock) 基于Gossip协议的成员资格和错误检测 Hinted handoff(数据回传机制),
Merkle哈希树
种子节点
A B
C
24 of 52
3.1 基础存储架构Dynamo
AWS EC2 设置root 用户和密码登录操作文档

AWS操作文档目录AWS操作文档 (1)1.创建安全组 (1)1.1.修改默认安全组规则 (1)2.创建密钥对 (2)3.创建实例 (2)4.使用xshell 连接AWS 实例 (6)4.1.设置xshell 用户秘钥管理者 (6)4.2.连接AWS EC2 实例 (8)4.3.设置Root 账号密码 (9)4.4.设置Xshell 工具root 用户和密码 (11)1.创建安全组1.1.修改默认安全组规则➢控制台–> EC2 -> 安全组:增加80、22、8080 端口规则2.创建密钥对➢控制台-> EC2 -> 秘钥对➢下载到本地目录中3.创建实例➢控制台-> EC2 -> 实例:启动实例➢选择免费的类型➢默认下一步➢设置默认存储➢默认下一步➢选择现有的默认安全组➢启动➢选择创建的密钥对➢查看实例列表➢获得外网IP4.使用XSHELL 连接AWS 实例4.1.设置XSHELL 用户秘钥管理者➢Xshell –> 工具–> 用户秘钥管理者➢关闭窗口➢文件-> 新建-> x新建会话属性:输入名称,主机➢设置用户身份验证4.2.连接AWS EC2 实例➢点击:连接➢接收并保存➢连接成功4.3.设置ROOT 账号密码➢提权设置root 密码:$ sudo passwd root➢切换root 用户下,修改ec2-user 的密码:$ su root# passwd ec2-user➢设置sshd_config 文件,ssh 使用用户名和密码登录# sed -ri 's/^#?(PasswordAuthentication)\s+(yes|no)/\1 yes/' /etc/ssh/sshd_config # sed -ri 's/^#?(PermitRootLogin)\s+(yes|no)/\1 yes/' /etc/ssh/sshd_config# sed -ri 's/^/#/;s/sleep 10"\s+/&\n/' /root/.ssh/authorized_keys# systemctl restart sshd.service# touch /root/.Xauthority➢解决警告提示# yum install xorg-x11-xauth xterm –y4.4.设置XSHELL 工具ROOT 用户和密码➢打开Xshell -> 打开-> 创建的连接➢设置root 用户和密码➢Root 用户连接AWS EC2 实例。
Amazon EC2 Terminal User Manual

Amazon EC2Terminal User ManualSUNDE Amazon AWS EC2Customized Terminal is specialized for Amazon EC2cloud computing service.With only an AWS account,the users can access to the Amazon cloud computing platform through the terminal,instead of a PC,to create virtual machine instances,login,etc.The terminal can be used for any other cloud computing platforms which comply with Amazon cloud computing protocol specification.1、Terminal LoginTurn on the terminal to enter the login page.Enter the domain name,access key id and secret access key of the AWS EC2,click login button to access to Amazon.The access key id and secret access key are created automatically by the system when the users register on Amazon official website.They can be found in Security Credentials of the account.For more details please visit.Considering much contents need to be entered,the users can also save the login information to a file named login.txt and move the file to a USB disk root directory.The file format should be:Domain Name=Access Key ID=AKIAI7UZEYA4EPDKJWQSWSecret Access Key=JS9MH2nekLjfi53cR2IPFMfIzu78W+H2nekLjfi52、Terminal SetupClick the setup button of the login page,to enter the setup interface.The users can set up the IP address and screen resolution.On rare occasions, the users need to set up the date and time of the terminal with ctl+t keys,and the DNS server with ctl+s keys.Click Save button to save the setup,or Cancel to go back to setup interface.3、Create a InstanceThe so-called Instance,is the user’s virtual machine on the Amazon cloud computing platform.After login there will list all the user’s virtual machine Instances and operation buttons as follows:Click"new"button to get a guide as follows to create new instance.Choose an image from the Image List to create an Instance,click "next"to choose"private key".On the dropdown list,the users can choose an existed Private Key to create new virtual machine instance,either they can create a new Private Key firstly then later create virtual machine instance with the new Private key.With new Private key for example,enter the name of the Private key on the textbox,click"create a new key"to create the new key.After the key created,It will prompt you to insert USB disk,and let you save the file path of the key.Or,you can choose"without a key"to create the new instance.Please note you will not be able to connect to the Instance unless you already know the password built in to this AMI.Click"Next"to set up security.On Existing Security Groups list,choose an existed security group to create the new Instance,or choose“Click here to Create a new Security Group”.With to create a new security group for example,do as follows:Click"Next"to set up the configuration of the Instance.After set up the parameters,click"Create instance",then the new Instance will appear on the Instance list.4、Actions on InstanceOn the Instance list page,you can"start","terminate"an instance which is not running.For the Instances which is running,you can"terminate","stop","reboot", "connect"them."Refresh"button can refresh the virtual machine instance list.5、Connect an InstanceOn the virtual machine instance list,choose the instance you want to connect.Then click"Connect"button,it will prompt you to choose the Private Key for connection.Insert the USB disk and choose the suitable Private key.It will use the selected Private key to connect the Instance.If the Instance is with a Linux OS,then a user name for connection will be needed.The user name is usually"root",it also may be"ec2-user"or even other user names.To get the exact user name,you can connect to Amazon EC2 website through a browser in a PC,choose the instance and click“connect”in the"Instance Action"ComboBox,then find out the user name of the instance in the popup window.Enter the user name,the terminal will auto run SSH to connect the instance.The following screen shot shows an instance with“ec2-user”user name.If the instance is with a Windows OS,then the terminal will automatically connect to the instance through Remote Desktop Protocal(RDP)and start the Windows login page.After the remote operation ended,you can exit the instance and come back to the login page.There you can re-login,or shut off the power to end the operation directly.HUIYUAN Co.,LTD.info@2012-2。
Amazon_Web_Services_(AWS)_EC2_介绍

Amazon Web Services (AWS) EC2介绍Amazon Elastic Compute Cloud (Amazon EC2) 是一种Web 服务,可在云中提供大小可调的计算容量。
该服务旨在降低开发人员进行网络规模级云计算的难度。
Amazon EC2 的Web 服务接口非常简单,您可以轻松获取和配置容量。
使用该服务,您可以完全控制您的计算资源,并可以在成熟的亚马逊AWS 计算环境中运行。
Amazon EC2 将获取并启动新服务器实例所需要的时间缩短至几分钟,这样一来,在您的计算要求发生变化时,您便可以快速扩展计算容量。
Amazon EC2 按您实际使用的容量收费,从而改变了成本结算方式。
Amazon EC2 还为开发人员提供了创建故障恢复应用程序以及排除常见故障情况的工具。
ssssAmazon EC2优势1. 弹性Web 规模级计算有了Amazon EC2,您可以在几分钟(而不是几小时或几天)内增加或减少容量。
您可以同时管理一个、数百个,甚至数千个服务器实例。
当然,因为这全是通过Web 服务API 控制,所以您的应用程序可根据其自身需要自动扩展。
2. 完全控制您可以完全控制您的实例。
您拥有每个实例的管理员或根用户访问权,可以像与其他任何机器一样与这些实例互动。
您可以在停止运行实例的同时将数据保存在启动分区,然后用Web 服务API 重启。
使用Web 服务API 还可以远程重启实例。
您还拥有实例控制台输出的访问权。
3. 灵活的云托管服务有多种实例类型、操作系统和软件包供您选择。
有了Amazon EC2,您可以为您所选择的操作系统和应用程序选取理想的内存、CPU、实例存储和启动分区大小配置。
例如,可选的操作系统包括许多Linux 发行版和 Microsoft Windows Server。
4. 专为与其他Amazon Web Services 配合使用而设计Amazon EC2 与Amazon Simple Storage Service (Amazon S3)、Amazon Relational Database Service (Amazon RDS)、Amazon SimpleDB 和Amazon Simple Queue Service (Amazon SQS) 配合使用,为多种应用程序提供完整的计算、查询处理和存储解决方案。
微Focus PPM(项目和端口管理中心软件)版本:所有版本说明书

Sizing Recommendationshttps:///ppm/Project and Portfolio Management Center Software version: All versionsDocument release date: June2023Send Us FeedbackLet us know how we can improve your experience with the SizingRecommendations.Send your email to: **********************Legal Notices©Copyright2023Open Text.The only warranties for products and services of Open Text and its affiliates and licensors (“Open Text”)are as may be set forth in the express warranty statements accompanying such products and services.Nothing herein should be construed as constituting an additional warranty.Open Text shall not be liable for technical or editorial errors or omissions contained herein.The information contained herein is subject to change without notice.DisclaimerCertain versions of software accessible here may contain branding from Hewlett-Packard Company(now HP Inc.)and Hewlett Packard Enterprise Company.This software was acquired on September1,2017by Micro Focus and is now offered by Open Text,a separately owned and operated company.Any reference to the HP and Hewlett Packard Enterprise/HPE marks is historical in nature,and the HP and Hewlett Packard Enterprise/HPE marks are the property of their respective owners.ContentsIntroduction4 Overview of PPM Center system4 Overview of PPM Center architecture5 Server cluster system and single-server configuration6 Defining sizes of PPM instances7 Hardware sizing recommendations8 Why the recommendations?8 Hardware sizing recommendation-Entry Level9 Hardware sizing recommendation-Small11 Hardware sizing recommendation-Medium12 Hardware sizing recommendation-Large13 Important notes on hardware sizing recommendations14IntroductionThis document provides hardware sizing recommendations when working with OpenText™PPM.This helps you achieve desirable performance when using PPM.The recommendations,derived from the PPM Sizing Tool which is designed and verified to be working by PPM,are intended for reference only.The reference configuration data supplied in this article is based on the lab performance testing. Please note that the testing environment may be different from your testing or production environment.Failure to test the transaction rate that is expected at the height of daily system usage in the testing environment,for example,every Friday afternoon is the peak time for Time Management module,may result in a recommendation that is not sufficient enough to support the requirements.In this case,contact Support for additional advices.This article includes the following information:l"Overview of PPM Center system"belowl"Hardware sizing recommendations"on page 8l"Sample Usage"on page 1Overview of PPM Center systemThis section provides general information about PPM Center system.With this background knowledge,you can have a better understanding of the hardware sizing recommendations.For more detailed information about PPM Center system,see the Installation and Administration Guide for PPM Center.If you are familiar with PPM Center system,you can safely skip this section.Overview of PPM Center architecturePPM Center is based on a three-tier architecture that consists of:l Client tierl Application server tierl Database tierThe architecture is shown in the following figure.Figure1:PPM Center architectureServer cluster system and single-server configurationThe three-tier architecture of PPM Center supports a variety of system configurations.You can deploy PPM Servers in a single-server configuration or a server cluster configuration.Server cluster configuration enables you to run PPM Center on several parallel servers.Server cluster configurations improve performance systems that handle high transaction volumes or a large number of concurrent users.In addition to handling higher user loads and providing greater scalability,the server cluster configuration supports load balancing and server failover features.The following is an example of server cluster configuration.Figure2:Server cluster configurationPPM Center test and development instances are typically single-server configurations that consist of one PPM Server and one Oracle database.The single PPM Server handles the entire user load and functions as the Web server.It alsohouses the file system for the program code,reports,execution logs,and attachments files.The Oracle database stores all other data.The following is an example of single-server configuration.Figure3:Single-server configurationDefining sizes of PPM instancesThis section defines the size of PPM Center instance deployed by your organization.The size is decided based on the number of concurrent users in PPM center at peak time,it is usually a percentage of PPM licensed users.If your organization uses multiple modules,you have to calculate the overall concurrent users in each module at peak time.Concurrent users in different modules have different weights according to their workload.l DM user is the baseline and has the standard weight1.l PjM and PgM users have the weight1.5.l The other modules have the weight1.So,for instance,if there are50users working on DM,50users working on PjM and 50users working on PgM,the estimated concurrent user would be:50*1+50*1.5+50*1.5=200Definition of PPM instance sizeHardware sizing recommendationsThe following hardware configurations are recommended for the entry-level,small, medium,and large PPM instances.Choose the hardware configuration in accordance with your PPM instance.The recommendations cover the web,application,and database tiers.And in each tier,the resources RAM,CPU,and disk space are considered.Why the recommendations?Database tier sizing is made by the Oracle Database Appliance OLTP Database Template Size,as shown below.For details,see https:///cd/E22693_01/doc.12/e55580/sizing.htm.For each node,we assume it supports200concurrent users at peak time,and they requires approximately200*1.5=300DB connections.Each connection has at most2sessions on average.We have600sessions,and according to the formula: Sessions=Processes*1.5+22.We need approximately400processes.We refer to the table above to decide the sizing recommendations for different levels of instances.Hardware sizing recommendation-Entry LevelApplication TierNumber of PPM Servers1If the application serveris hosted on a virtualmachine,the resources(CPU,RAM,and diskspace)should beincreased by30%.Customers should beaware that VM-basedserver could sometimesencounter performancefluctuation when thehost physical server hasa fluctuating workload. Number of CPUs per server6 2.27-3.0GHz per CPUcore dedicated for PPMuseRAM per server10GB Entry level serverdeploys user-trafficnode and backgroundservice node on thesame server,so RAMneeded on this sever:4GB(for User-traffic)+3GB(for BGservice)+3GB(forOS)=10GBDisk space per server80GBEC2(for PPM on AWS)C4.2.xlarge or C5.2xlargePPM Node Configuration in the Application TierNumber of user-traffic nodes11Number of background servicenodesDatabase TierNumber of CPUs4 2.27-3.0GHz per CPUcore dedicated for PPMuseRAM16GB Dedicated for PPM use Disk space480GBRDS(for PPM on AWS)DB.T3.xlargeHardware sizing recommendation-SmallNumber of CPUs6 2.27-3.0GHz per CPU corededicated for PPM use RAM32GB Dedicated for PPM use Disk space480GBRDS(for PPM on AWS)Db.t3.2xlargeHardware sizing recommendation-MediumNumber of background service nodes 2Customers may needmore service nodes ifthey have heavy usertraffic.Database TierNumber of CPUs16 2.27-3.0GHz per CPUcoreRAM128GB Dedicated for PPM use Disk space960GBRDS(for PPM on AWS)r5.4xlargeHardware sizing recommendation-LargeRAM per server20GB The server on which4nodes are deployedneeds20GB RAM,whilethe server on which3nodes are deployedneeds16GB RAM.Disk space per server100GBEC2(for PPM on AWS)t3.2xlargePPM Node Configuration in the Application TierNumber of user-traffic nodes12Could be increasedaccording to the numberof concurrent users atpeek time3Number of background servicenodesDatabase TierNumber of CPUs32 2.27-3.0GHz per CPUcoreRAM96GB Dedicated for PPM use Disk space960GBRDS(for PPM on AWS)r5.8xlargeImportant notes on hardware sizing recommendationsIn addition to the above hardware sizing recommendations,we suggest that you pay attention to the following items:l Operating SystemWe suggest you use the following:l Microsoft Windows Server,2008R2(64-bit),orl Red Hat Enterprise Linux6(64bit)l PPM CenterWe suggest you use the following:l PPM Center9.42.000x,orl PPM Center9.5xl PPM Center heap sizeWe suggest that heap size for each node should be4096MB at least.A background service node requires greater heap size than a user node.You can adjust heap size of the nodes on a server under the limit of the server memory. If you lower the total number of PPM nodes,you should increase the heap size, maxThreads,and database connections.l JDK SoftwareWe strongly recommend64-bit JDK software of the following versions:l 1.8.0Update101or laterl DatabaseThe database server should be a separate64-bit physical machine.Database and application servers should be located in the same data center.If you have heavy workload in database server,consider using Oracle RAC which improves performance by providing clustering and high availability in Oracle database environments.l Cluster NodeIf you have heavy background services workload,it is better to add one more PPM background service node.It is recommended to separate user nodes and background service nodes in different servers.All PPM nodes should be located in the same data center.l Virtual MachineHosting the PPM Oracle database schema on a virtual machine(VM)is strongly discouraged in a production environment for performance reasons.PPM has conducted performance benchmarks which show that for some common user scenarios(such as opening a PPM request),the performance of the system, when the database schema is hosted on a VM,can be severely degraded up to 50%compared with hosting the database on a dedicated physical machine. Note,however,that regardless of performance issues,we do not support running the PPM database schema on a VM as long as the configuration is officially supported by Oracle.As a result,such an architecture can be used for low-load environments where lower total cost of ownership(TCO)is more important than performance and user experience,which is typically the case for test or development environments.These performance concerns with VM hosting do not apply to PPM application server:R&D has no concern towards hosting PPM application servers on virtual machines,even in production environment,as long as the reduced performance of each PPM node resulting from VM hosting is compensated proportionally by increasing the number of PPM nodes in the cluster.l Hardware load balancerA hardware load balancer is recommended in the server cluster configuration, for it improves load distribution,transaction capacity,and system performance.l HP servers for referenceHere are some HP servers for your reference:l Web Server:HP ProLiant BL460c Gen8Server Blade-Single8Core E5-2600, 32G Mem,2*146GB HDDl App Server:HP ProLiant BL460c Gen8Server Blade-Single/Dual8Core E5-2600,32G Mem,3*500GB HDDl DB Server:HP ProLiant DL560Gen8Server-Quad8Core E5-4600,96G Mem, 16*146G HDDl Document management system sizingThe document management system(DMS)affects PPM performance.Take DMS sizing into considerations when adjusting hardware sizing.l If you apply PPM File System solution,attached documents are uploaded to the PPM Server file system.In this case,additional disk space is needed for document management in the application server.l If you apply PPM Database DMS solution,attached documents in PPM areuploaded to the PPM database.In this case,additional disk space is needed for document management in the database server.l If you apply PPM External Database DMS solution,attached documents inPPM are uploaded to the specified Oracle database on your network.In this case,additional disk space is needed for docuement management in thespecified Oracle database.For more information about DMS solutions,see the Document Management Guide and Reference.。
亚马逊 AWS 认证解决方案架构师–专业人员样题

Your company’s on-premises content management system has the following architecture:∙Application Tier – Java code on a JBoss application server∙Database Tier – Oracle database regularly backed up to Amazon Simple Storage Service (S3) using the Oracle RMAN backup utility∙Static Content – stored on a 512GB gateway stored Storage Gateway volume attached to the application server via the iSCSI interfaceWhich AWS based disaster recovery strategy will give you the best RTO?A) Deploy the Oracle database and the JBoss app server on EC2. Restore the RMAN Oracle backups fromAmazon S3. Generate an EBS volume of static content from the Storage Gateway and attach it to theJBoss EC2 server.B) Deploy the Oracle database on RDS. Deploy the JBoss app server on EC2. Restore the RMAN Oraclebackups from Amazon Glacier. Generate an EBS volume of static content from the Storage Gateway and attach it to the JBoss EC2 server.C) Deploy the Oracle database and the JBoss app server on EC2. Restore the RMAN Oracle backups fromAmazon S3. Restore the static content by attaching an AWS Storage Gateway running on Amazon EC2 as an iSCSI volume to the JBoss EC2 server.D) Deploy the Oracle database and the JBoss app server on EC2. Restore the RMAN Oracle backups fromAmazon S3. Restore the static content from an AWS Storage Gateway-VTL running on Amazon EC2An ERP application is deployed in multiple Availability Zones in a single region. In the event of failure, the RTO must be less than 3 hours, and the RPO is 15 minutes. The customer realizes that data corruption occurred roughly 1.5 hours ago. Which DR strategy can be used to achieve this RTO and RPO in the event of this kind of failure?A) Take 15-minute DB backups stored in Amazon Glacier, with transaction logs stored in Amazon S3 every5 minutes.B) Use synchronous database master-slave replication between two Availability Zones.C) Take hourly DB backups to Amazon S3, with transaction logs stored in S3 every 5 minutes.D) Take hourly DB backups to an Amazon EC2 instance store volume, with transaction logs stored inAmazon S3 every 5 minutes.The Marketing Director in your company asked you to create a mobile app that lets users post sightings of good deeds known as random acts of kindness in 80-character summaries. You decided to write the application in JavaScript so that it would run on the broadest range of phones, browsers, and tablets. Your application should provide access to Amazon DynamoDB to store the good deed summaries. Initial testing of a prototype shows that there aren’t large spikes in usage. Which option provides the most cost-effective and scalable architecture for this application?A) Provide the JavaScript client with temporary credentials from the Security Token Service using a TokenVending Machine (TVM) on an EC2 instance to provide signed credentials mapped to an Amazon Identity and Access Management (IAM) user allowing DynamoDB puts and S3 gets. You serve your mobileapplication out of an S3 bucket enabled as a web site. Your client updates DynamoDB.B) Register the application with a Web Identity Provider like Amazon, Google, or Facebook, create an IAMrole for that provider, and set up permissions for the IAM role to allow S3 gets and DynamoDB puts. You serve your mobile application out of an S3 bucket enabled as a web site. Your client updates DynamoDB.C) Provide the JavaScript client with temporary credentials from the Security Token Service using a TokenVending Machine (TVM) to provide signed credentials mapped to an IAM user allowing DynamoDB puts.You serve your mobile application out of Apache EC2 instances that are load-balanced and autoscaled.Your EC2 instances are configured with an IAM role that allows DynamoDB puts. Your server updatesDynamoDB.D) Register the JavaScript application with a Web Identity Provider like Amazon, Google, or Facebook,create an IAM role for that provider, and set up permissions for the IAM role to allow DynamoDB puts.You serve your mobile application out of Apache EC2 instances that are load-balanced and autoscaled.Your EC2 instances are configured with an IAM role that allows DynamoDB puts. Your server updatesDynamoDB.You are building a website that will retrieve and display highly sensitive information to users. The amount of traffic the site will receive is known and not expected to fluctuate. The site will leverage SSL to protect the communication between the clients and the web servers. Due to the nature of the site you are very concerned about the security of your SSL private key and want to ensure that the key cannot be accidentally or intentionally moved outside your environment. Additionally, while the data the site will display is stored on an encrypted EBS volume, you are also concerned that the web servers’ logs might contain some sensitive information; therefore, the logs must be stored so that they can only be decrypted by employees of your company. Which of these architectures meets all of the requirements?A) Use Elastic Load Balancing to distribute traffic to a set of web servers. To protect the SSL private key,upload the key to the load balancer and configure the load balancer to offload the SSL traffic. Write your web server logs to an ephemeral volume that has been encrypted using a randomly generated AES key.B) Use Elastic Load Balancing to distribute traffic to a set of web servers. Use TCP load balancing on theload balancer and configure your web servers to retrieve the private key from a private Amazon S3bucket on boot. Write your web server logs to a private Amazon S3 bucket using Amazon S3 server-side encryption.C) Use Elastic Load Balancing to distribute traffic to a set of web servers, configure the load balancer toperform TCP load balancing, use an AWS CloudHSM to perform the SSL transactions, and write yourweb server logs to a private Amazon S3 bucket using Amazon S3 server-side encryption.D) Use Elastic Load Balancing to distribute traffic to a set of web servers. Configure the load balancer toperform TCP load balancing, use an AWS CloudHSM to perform the SSL transactions, and write yourweb server logs to an ephemeral volume that has been encrypted using a randomly generated AES key. You are designing network connectivity for your fat client application. The application is designed for business travelers who must be able to connect to it from their hotel rooms, cafes, public Wi-Fi hotspots, and elsewhere on the Internet. You do not want to publish the application on the Internet.Which network design meets the above requirements while minimizing deployment and operational costs?A) Implement AWS Direct Connect, and create a private interface to your VPC. Create a public subnet andplace your application servers in it.B) Implement Elastic Load Balancing with an SSL listener that terminates the back-end connection to theapplication.C) Configure an IPsec VPN connection, and provide the users with the configuration details. Create a publicsubnet in your VPC, and place your application servers in it.D) Configure an SSL VPN solution in a public subnet of your VPC, then install and configure SSL VPN clientsoftware on all user computers. Create a private subnet in your VPC and place your application servers in it.Your company hosts an on-premises legacy engineering application with 900GB of data shared via a central file server. The engineering data consists of thousands of individual files ranging in size from megabytes to multiple gigabytes. Engineers typically modify 5-10 percent of the files a day. Your CTO would like to migrate this application to AWS, but only if the application can be migrated over the weekend to minimize user downtime. You calculate that it will take a minimum of 48 hours to transfer900GB of data using your company’s existing 45-Mbps Internet connection.After replicating the application’s environment in AWS, which option will allow you to move the application’s data to AWS without losing any data and within the given timeframe?A) Copy the data to Amazon S3 using multiple threads and multi-part upload for large files over theweekend, and work in parallel with your developers to reconfigure the replicated application environment to leverage Amazon S3 to serve the engineering files.B) Sync the application data to Amazon S3 starting a week before the migration, on Friday morning performa final sync, and copy the entire data set to your AWS file server after the sync completes.C) Copy the application data to a 1-TB USB drive on Friday and immediately send overnight, with Saturdaydelivery, the USB drive to AWS Import/Export to be imported as an EBS volume, mount the resulting EBS volume to your AWS file server on Sunday.D) Leverage the AWS Storage Gateway to create a Gateway-Stored volume. On Friday copy the applicationdata to the Storage Gateway volume. After the data has been copied, perform a snapshot of the volume and restore the volume as an EBS volume to be attached to your AWS file server on Sunday.。
AWS云计算快速指南(英文)

A Quick Guide to use Cloud Computing through Amazon’sPlatformFarhat N.Memon,Anne M.Owen and Andrew P.Harrison Departments of Mathematical Sciences and Biological Sciences,University of Essex, Wivenhoe Park,Colchester,Essex,CO43SQ,United Kingdom/Email:fnmemo@;owena@;harry@1IntroductionThere was a time when companies used their own generators to produce electricity for running their factories or plants.This usually required a large capital expenditure when purchasing dynamos,and also required maintenance costs.This business model was quickly dropped and companies started to buy electricity from a utility supplier of electricity,because it proved to be cheaper and eas-ier to buy electricity as a commodity without worrying about maintenance and updating equipment. It is becoming increasingly apparent that computing is performing a similar transition at present, with computing,and other information technologies,being sold as a commodity which can be purchased from utility suppliers.The availability of significant computational opportunities is being provided by several companies,such as Amazon,Google,and Microsoft.They provide high-performance solutions that enable users to utilise their computational infrastructure,and to only pay for the resources used.The web services platform of these organisations are suitable for user groups of any size,including individuals.The“Cloud computing”concept is very simple:the com-puting resources are located somewhere(not in your office/computer room)and you will connect to them and use them according to your requirement.We are providing a quick guide to start using cloud computing through Amazon’s platform website. Users are not required for any long term commitment with Amazon and are allowed to choose any development platform or programming model that is most appropriate for their problems to be solved.Amazon Web Services(AWS)provide different services which includes Amazon Elastic Compute Cloud(Amazon EC2),Amazon Simple DB,Amazon Simple Storage Service(Amazon S3),Amazon CloudFront,Amazon Simple Queue Service(SQS),Amazon Elastic MapReduce,AWS Premium Support.Amazon Elastic Compute Cloud(EC2)is used to get Amazon’s high computing resources for which an Amazon Machine Image(AMI)is required.An AMI is an encrypted machine image(a file)that contains all the information required to boot an instance of your software and it is stored in Amazon Simple Storage Service(S3).Users can either create their own AMI or use public AMIs (a public AMI can be used as it is or with some modification).Figure1illustrates theflow of EC2. Although the detailed documentation is available at Amazon’s website,this paper provides a quick way for getting started with Amazon’s cloud computing.Figure1:Amazon Elastic Cloud Compute(EC2)Flow(Source:/)2Amazon Cloud Computing GuideFirst of all,you have to create your Amazon Web Services(AWS)account,Amazon Simple Storage Service(S3)account and Amazon Elastic Compute Cloud(EC2)account in order to use Amazon EC2.You will get your Access Key Identifiers by logging in to your EC2account(select’Security Credentials’link from’Your Account’menu).You are now able to start with Amazon EC2either through AWS management console or through command line tools.This paper covers the details of command line tools.These tools are available as a ZIPfile in Amazon EC2Resource Center via/connect/entry.jspa?externalID=351&categoryID=88In order to use command line tools,you have to go through the Access key Identifier process in which you will download twofiles:Private Keyfile and X.509Certificatefile that will be re-quired to set up Amazon command line tools.Amazon suggests that you create a.ec2directory in your home directory and save thesefiles in it.The following steps are required to access AWS services(EC2and S3)through command line tools,assuming a bash shell.The$dollar sign represents the command line prompt.2.1Setting Environment Variables2.1.1Java Home variableCommand line tools are written in java;so an environment variable(JAVAHOME= path–to–java2.1.2Command Line Tool Home VariableAn environment variable(EC2HOME= path–to–CommandLineT oolsAnother variable PATH indicates subdirectory bin through the following command:$export PATH=$PATH:$EC2PRIVATE CERT are required to be set that will point to your private key and certificate respectively through the following commands:$export EC2KEY=/.ec2/ private–key–filename$export EC2PRIVATECERT=/.ec2/cert-ABCYZTANYEC6QXYWB1XV7Y99MLN.pem2.3Find a suitable AMIThe following command shows a list of Amazon’s public AMIs and your AMIs.You can select the most suitable AMI for your requirement.$ec2-describe-images2.4Generate SSH Key PairIf you are using a public AMI,you will need a private/public key pair in order to login to the instance.This key pair is required because public AMI does not have any password.$ec2-add-keypair keypair–nameExample:$ec2-add-keypair fnm-keypairAmazon will return a keypair that must be saved in a localfile for later use.File name should start with“id rsa-fnm-keypair.2.5Running an InstanceThe following command launches an instance:$ec2-run-instances ami–ID –k keypair–nameExample:$ec2-run-instances ami-b55dbbdc–k fnm-keypairThis command will return an instance-ID that should be noted for later use.2.6Describe an Instance“ec2-describe-instances”is another useful command that shows the status of an instance including ami-ID,instance-ID,hostname(e.g:),and so on.$ec2-describe-instances instance–IDExample:$ec2-describe-instances i-e18583952.7Authorize Network Access to an InstanceBefore logging in to your instance,you are required to authorize access through the“ec2-authorize”command.2.7.1To authorise access for http$ec2-authorize security–group –p22Example:$ec2-authorize default–p222.7.2To authorise access for SSH$ec2-authorize security–group –p80Example:$ec2-authorize default–p80These are one-time commands needed to allow access from your home machine to Amazon servers.2.8Connect to your InstanceThe following two commands will connect you to your instance and allow you to login as root user to have full control over that instance.$ec2-get-console-output instance–ID$ssh–i keypair–filename root@ hostnameExample:$ec2-get-console-output i-e1858395$ssh–i id2.9Modifying an Existing AMIAfter launching a suitable public AMI,you can install/add your required software or tools.Once you have modified your instance,the following command from your home machine will upload your private key and X.509certificate.$scp–i keypair–filename private–key–filename certificate–filename root@ hostname :/mntExample:$scp–i idExample:$ec2-register fnm-essex-001/fnm-image.manifest.xmlAmazon EC2will return an AMI identifier that can be used to run instances of the new AMI. 2.12Terminate an InstanceFinally you will need the“ec2-terminate-instances”command to stop execution of your instance. The format of the command is:$ec2-terminate-instances instance−IDExample:$ec2-terminate-instances i-e18583952.13An Example to Run a C program at Amazon CloudThe following example illustrates how to execute a C program using Amazon machine.The AMI ID,instance ID and amazon host machine name used in this example are all imaginary.First we will run an instance of a selected AMI and then secure copy command(scp)will copy a C program in to the Amazon machine.You can copy your data as well with the“scp”command.We will then compile and execute the C program at the Amazon machine andfinally bring the output back to our home machine.$ec2-run-instances ami-a55r61bb–k fnm-keypair$ec2-get-console-output i-a1885632$ssh–i idrsa-fnm-keypair myprogram.C root@pute.:/rootAfter copying our C program,we will use Amazon shell once again to compile and execute our program.$cc myprogram.c$./a.out our–outputThe output of our program is stored in“our-output”file.We will now bring the output back to our machine by“scp”command from the home shell.$scp–i idReferences[1]Amazon Web Services./publicdatasets/[2]A.Bateman and M.Wood.Cloud Computing.Bioinformatics,25(12):1475,2009Online Journal:/cgi/reprint/25/12/1475。
aws 知识点总结

aws 知识点总结1. AWS基本概念AWS的基本概念包括区域(Region)、可用区(Availability Zone)、虚拟私有云(VPC)、弹性计算云(EC2)、对象存储(S3)、关系数据库服务(RDS)等。
AWS的区域是指AWS数据中心所在的地理位置,每个区域包括多个可用区,每个可用区包括一个或多个数据中心。
VPC是AWS提供的一种网络隔离和管理工具,可以让用户在AWS云上创建一个与传统网络类似的虚拟网络环境。
EC2是AWS提供的一种弹性计算服务,用户可以在EC2上运行虚拟机,并根据需要进行扩展或缩减。
S3是AWS提供的一种无限容量、高可用的对象存储服务,用户可以在S3上存储和管理任意类型的数据。
RDS是AWS提供的一种托管式关系数据库服务,包括MySQL、PostgreSQL、Oracle、SQL Server等。
2. AWS服务模型AWS提供了三种基本的服务模型,包括基础设施即服务(IaaS)、平台即服务(PaaS)和软件即服务(SaaS)。
IaaS是指用户在云上租用计算、存储、网络等基础设施资源,例如EC2、S3等。
PaaS是指用户在云上租用应用程序开发和部署的平台服务,例如AWS Elastic Beanstalk、AWS Lambda等。
SaaS是指用户在云上租用已经构建好的应用程序,例如AWS提供的各种企业应用程序服务。
3. 计算服务AWS提供了多种计算服务,包括EC2、Elastic Beanstalk、Lambda、ECS等。
EC2是AWS 提供的一种弹性计算服务,用户可以在EC2上租用虚拟机,按小时计费。
Elastic Beanstalk是AWS提供的一种PaaS服务,可以在上面部署和管理Web应用程序。
Lambda是AWS提供的一种无服务器计算服务,用户可以在上面运行特定的代码片段,按使用时长计费。
ECS是AWS提供的一种容器服务,用户可以在上面运行容器化的应用程序。
亚马逊aws-sap考试题库

1.问题1一家公司正在将业务关键型应用程序迁移到AWS上。
它是使用Oracle数据库的传统三层Web应用程序。
数据在传输和静止时都必须加密。
该数据库承载12TB的数据。
允许通过内部网络与源Oracle数据库建立网络连接,该公司希望通过使用AWS托管服务来降低运营成本。
仅所有主键;但是,它包含许多二进制大对象(BLOB)字段。
由于许可限制,无法使用数据库的本机复制工具。
哪种数据库迁移解决方案将对应用程序的可用性产生最小的影响?A.为Amazon实例设置Amazon RDS。
在虚拟私有云中托管RDS数据库(VPC)子网具有Internet访问权限,并将RDS数据库设置为源数据库的加密只读副本。
使用SSL加密两个数据库之间的连接。
通过观察RDS ReplicaLag指标来监视复制性能。
在应用程序维护窗口期间,在没有更多复制滞后时,请关闭本地数据库,并将应用程序连接切换到RDS实例。
将只读副本提升为独立的数据库实例。
B.设置一个Amazon EC2实例并安装相同的Oracle数据库软件。
使用支持的工具创建源数据库的备份。
在应用程序维护窗口期间,将备份还原到在EC2实例中运行的Oracle数据库中。
设置Amazon RDS for Oracle实例,并在AWS托管的数据库之间创建导入作业。
作业完成后,关闭源数据库并将数据库连接切换到RDS实例。
C.使用AWS DMS在本地Oracle数据库和AWS上托管的复制实例之间加载和复制数据集。
提供一个AmazonRDS Oracle实例与透明数据加密(TDE)启用,其配置为目标的复制实例。
创建一个客户管理的AWS KMS 主密钥,将其设置为复制实例的加密密钥。
使用AWS DMS任务将数据加载到目标RDS实例中。
在应用程序维护窗口期间以及加载任务到达正在进行的复制阶段之后,将数据库连接切换到新数据库。
D.在应用程序维护窗口期间,在本地Oracle数据库上创建压缩的完整数据库备份。
aws 常用安全组规则

aws 常用安全组规则AWS常用安全组规则安全组是AWS中一种重要的网络安全功能,它可以用于控制进出EC2实例的网络流量。
通过配置安全组规则,我们可以实现对EC2实例的访问控制,保护云环境的安全。
本文将介绍一些常用的安全组规则,帮助读者更好地理解和应用这些规则。
1. 允许所有流量我们可以创建一条允许所有流量的安全组规则。
这样配置的安全组将允许所有的入站和出站网络流量通过。
这在某些特定场景下可能是必要的,但通常情况下不建议使用这种规则,因为这会增加安全风险。
2. 限制特定IP访问通过创建一条只允许特定IP访问的安全组规则,我们可以限制对EC2实例的访问。
例如,我们可以指定只有特定IP地址的用户可以通过SSH协议访问EC2实例。
这种方式可以有效地防止未经授权的访问,提高安全性。
3. 允许特定协议和端口我们还可以通过指定特定协议和端口来创建安全组规则。
例如,我们可以创建一条只允许HTTP流量通过的规则,或者只允许SMTP 流量通过的规则。
通过限制特定的协议和端口,我们可以精确控制网络流量,提高网络安全性。
4. 限制访问源IP范围为了进一步增强安全性,我们可以通过限制访问源IP范围来创建安全组规则。
例如,我们可以指定只有某个IP地址段的用户可以访问EC2实例。
这种方式可以防止来自其他地区的恶意访问,提高安全性。
5. 配置出站流量规则除了控制入站流量,我们还可以配置出站流量规则来增强安全性。
通过限制出站流量,我们可以防止EC2实例被滥用或成为僵尸主机。
例如,我们可以配置一条只允许特定协议和端口的出站规则,以防止恶意软件通过EC2实例传播。
6. 定期审核和更新安全组规则为了保持云环境的安全性,我们应该定期审核和更新安全组规则。
随着业务需求的变化,我们可能需要添加或删除一些规则。
另外,我们还应该定期检查安全组规则是否仍然适用于当前的网络环境,以防止安全漏洞的出现。
7. 使用安全组标签为了更好地管理和组织安全组规则,我们可以使用安全组标签。
亚马逊 AWS推出专业级解决方案架构师认证

亚马逊AWS推出专业级解决方案架构师认证完成Amazon EC2实例的初始化几分钟就够了,那么证明您的AWS架构专业能力需要用多长时间呢?AWS专业级解决方案架构师认证新鲜出炉!2013年4月,AWS正式启动了AWS认证项目,同时公布了AWS首个专业技能考试:AWS 助理级解决方案架构师认证。
此后,我们又针对开发人员和系统运维管理员相继推出了另外两个助理级别考试。
今天,我们很高兴的推出首个专业级的认证考试–AWS专业级解决方案架构师认证。
AWS专业级解决方案架构师认证能够检验应试者在AWS云平台上的高级技术技能和相关工作经验,这些技能和经验专注在分布式应用设计和分布式系统架构方面。
该考试的目的是甄选出那些经验丰富、能够解决专业的、复杂问题的从业人员。
该考试向已经获得了助理级解决方案架构师认证的AWS用户、合作伙伴和员工开放,这是AWS解决方案架构师认证体系发展的最新进展。
为什么要获得AWS认证?随着对云计算技能和AWS专业知识需求的增长,用户们渴望在AWS平台上设计和实施IT 基础架构时能得到富有经验的、胜任的技术专家的协助。
AWS认证可以帮助用户识别合格的、有能力熟练运用AWS云平台的候选人,他们有能力协助用户在AWS云平台上设计、以及实施各种系统。
同时,认证也能帮助IT专业人员获得在专业技能上的肯定以及更好的职业发展。
哪些人员能够参加考试?考生必须首先获得助理级解决方案架构师认证。
除此之外,考生还应具备多年在AWS平台上设计、部署可扩展的、高可用的、容错的以及可靠的云架构的实践经验。
考生应有能力评估云端应用的需求,并能够为在AWS平台上实施、部署和预配应用提供架构级别的建议。
我们提供考前学习的相关培训吗?Architectingon AWS–高级概念是一门合适的考前培训课程。
AWSEC2知识点总结

AWSEC2知识点总结EC2简介1. EC2的特性EC2是AWS提供的⼀种计算服务,它以EC2实例(EC2 Instance)的形式存在,因此⼀个EC2实例可以被认为是⼀个虚拟机预配置的EC2镜像被称之为Amazon Machine Images (AMI),⼀个AMI包含了你打包的好操作系统,以及相应的应⽤程序和配置不同的EC2实例类型包含了不同的CPU,内存,存储和⽹络性能AWS默认以及建议使⽤密钥对(Key Pair)的形式访问EC2实例,AWS将保存公钥,您将负责保存私钥EC2实例存储(Instance store volumes)是⼀种短暂性的存储,⼀旦您停⽌或者终⽌您的EC2实例,这个存储内的数据将永久消失EBS存储(Amazon EBS volumes)是⼀种持续性的存储,不管EC2实例是什么状态,你都可以保留EBS存储内的数据。
这种类型的存储对于进⾏数据盘的迁移⾮常⽅便,使⽤场景也⽐较多。
安全组(Security Group)会通过检测数据包的端⼝、协议、源IP地址从⽽从当防⽕墙的作⽤弹性IP(Elastic IP address)可以⽅便您为您的EC2实例分配⼀个固定的公⽹IP地址,并且保证每次关机重启该地址依旧有效。
虚拟私有云(Virtual Private Cloud, VPC)是AWS的⽹络组件,可以让你的AWS资源与其他⽤户的资源在逻辑上进⾏隔离。
您也可以使⽤VPC与您的物理数据中⼼进⾏连接。
2. 如何访问EC2AWS提供了⾮常多的⽅法⽅便您来访问EC2实例,下⾯将⼀⼀进⾏列举。
并且会在后续课程通过视频的⽅式为⼤家进⾏演⽰。
AWS 命令⾏(CLI)- 您可以通过⼀些终端软件并利⽤命令⾏的⽅式访问您的Windows,Mac和Linux实例AWS EC2管理平台 – 您可以通过基于web的⽤户界⾯来访问您的EC2实例(通过java等插件)AWS CLI⼯具 – 您可以通过AWS CLI⼯具来访问AWS的多个组件Windows PowershellAWS APIAWS SDK3. EC2实例的计费类型EC2的实例计费类型有很多种,每⼀种都有⾃⼰的使⽤场景,不同的客户可能对计费类型的需求也不⼀样。
matlab on every用法

Matlab是一种用于数学计算、数据分析和可视化的强大软件工具。
它提供了丰富的函数库和工具包,可以帮助用户快速高效地进行科学计算和工程分析。
在众多的Matlab功能中,以Matlab on every功能为主题,本文将介绍Matlab on every的用法和相关知识。
一、Matlab on every是什么Matlab on every指的是Matlab支持在每个领域的应用。
无论是在科学研究、工程技术、金融分析还是教育培训中,都可以看到Matlab 的身影。
Matlab提供了丰富的工具和函数,可以满足不同领域用户的需求,帮助他们解决复杂的数学计算和数据分析问题。
Matlab on every的理念是让Matlab成为每个领域的首选工具,为用户提供全面的支持和帮助。
二、Matlab on every的用法1. 科学研究领域在科学研究领域,科研人员常常需要进行复杂的数学计算和数据分析。
Matlab提供了众多的工具和函数,可以帮助科研人员快速高效地完成各种科学计算和数据处理任务。
Matlab提供了丰富的数学函数库,可以进行各种数学运算和数据模型拟合;Matlab还提供了强大的绘图工具,可以帮助科研人员对数据进行可视化展示。
Matlab在科学研究领域有着广泛的应用,成为科研人员首选的数学计算和数据分析工具。
2. 工程技术领域在工程技术领域,工程师和技术人员经常需要进行复杂的工程计算和仿真分析。
Matlab提供了丰富的工程工具和函数,可以帮助工程师和技术人员快速准确地进行各种工程计算和仿真分析。
Matlab提供了强大的控制系统设计工具,可以帮助工程师设计各种复杂的控制系统;Matlab还提供了丰富的信号处理工具,可以帮助工程师对各种信号进行分析和处理。
Matlab在工程技术领域有着广泛的应用,成为工程师和技术人员首选的工程计算和仿真工具。
3. 金融分析领域在金融分析领域,金融分析师常常需要进行复杂的金融建模和数据分析。
删除ec2实例

删除ec2实例
如果您已经不再需要EC2实例,可以考虑删除它,以避免不必要的费用和资源占用。
以下是删除EC2实例的步骤:
1. 登录AWS控制台,并选择EC2。
2. 在EC2控制台上,选择要删除的实例。
3. 单击“实例操作”下拉菜单,并选择“实例状态”>“停止实例”。
4. 等待实例停止完全。
5. 选中要删除的实例,并单击“实例操作”下拉菜单中的“实例状态”>“终止实例”。
6. 在弹出的确认窗口中,选择“是,终止”。
7. 等待几分钟,直到实例被完全删除。
注意:终止EC2实例将永久删除该实例及其相关数据,因此请确保在进行此操作之前备份任何重要数据。
- 1 -。
aws试题

第1题Q1.家公司在具有Amazon BS2存储的单个m42xlarge Amazon E2实例上运行遗留系统EC2实例时运行Web服务器和自我管理的Orade数据库每12小时对EBS卷进行一次快照,并从完全配置的EC2实例间建AMI最近终止EC2实例的事件导教数小时的停机时间。
该应用程序已从AMI成功启动,但EBS快照的存续时间和数据库的修复导致丢失了8个小时的数据。
在系统操作员手动执行这些过程的同时,系统也停机了4个小时,哪些体系结构更改将最大理程度地减少停机时间并减少丢失数据的机会?A.创建一个Amazon Cloud Watch警报以自动恢复实例,创建一个脚本,该脚本将在重新启动后检查并修复数据库将Operations团队订阅到Cloud Watch警报生成的Amazon SNS消息B.在Ehatic Losd Badincer/Appiation Load Balancr之后的m4.xlarog EC2变例上运行应用程序.跨多个可用区Auto Scaling组中运行EC2实例,实数数量最少为2将数据库迁移到Amazon RDS Oracde Multi-AZ数据库实例C.在Elastic Load Balaner/Appliation Load Balnacer之后的m4.2xlarge EC2实例上运行应用程序在Auto Scaling组中运行EC2实例,以最少—个实例数访问多个可用区。
将数据迁移到Amaon RDS Orade Multi-AZ数据库实例D.将Web服务器实例数增加到两个m4.xlarge实例,并使用Amazon Route S3循环负均衡来分散负载在Web服务器上启用Route S3健康检查,将数据库迁移Amaon RDS Orade Multi-AZ 数据库实例第2题Q2.解决方案架树师正在与一家在AWs中运行标准三量Web应用程序的公司合作.Web和应用程序层在Amazon EC2上运行,数细库院在Amazon RDS上运行.该公司正在重新设计Web和应用程序层以使用Amazon API Gateway和AWS Lsmbda,并且该公司计划在6个月内能署新应用程序.IT经理已要求解决方案架构师在出此期间降低本.哪种解决方方案在保持可靠性的同时最具成本效益?A.将竞价型实例用于Web层。
AWS Prescriptive Guidance 使用 Control-M 工作流编排工具与 AW

AWS Prescriptive Guidance 使用 Control-M 工作流编排工具与 AWS Mainframe Modernization 集成AWS Prescriptive Guidance: 使用 Control-M 工作流编排工具与 AWS Mainframe Modernization 集成Copyright © 2023 Amazon Web Services, Inc. and/or its affiliates. All rights reserved.Amazon 的商标和商业外观不得用于任何非 Amazon 的商品或服务,也不得以任何可能引起客户混淆、贬低或诋毁 Amazon 的方式使用。
所有非 Amazon 拥有的其它商标均为各自所有者的财产,这些所有者可能附属于 Amazon、与 Amazon 有关联或由 Amazon 赞助,也可能不是如此。
Table of Contents简介 (1)概览 (1)目标成果 (2)本指南中的术语 (2)假设 (2)架构 (4)工作流集成 (5)部署作业类型 (5)创建连接配置文件 (5)创建作业和计划 (6)使用工作流启动作业 (7)按计划自动运行作业 (9)基础作业根据事件运行 (9)监控作业 (9)Control-M 监控 (9)AWS 管理控制台 (10)最佳实践 (11)相关资源 (12)文档历史记录 (13)术语表 (14)DevOps 术语 (14)迁移术语 (15)现代化术语 (19)概览使用 Control-M 工作流编排工具与 AWS Mainframe Modernization 集成Sunil Bemarkar、Pablo Alonso Prieto、Vaidy Sankaran 和 Vij Balakrishna,Amazon WebServices(AWS)以及 Joe Goldberg,BMC Software, Inc.2022 年 11 月为了满足业务和数字化转型的需求,客户正在对大型机应用程序进行现代化改造,以提高敏捷性、降低成本并加快创新速度。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
5. Set up your network.
6. Set up client MATLAB with Parallel Computing on desktop computers of users.
7. Set up the license manager.
2013-9-22 13
Set up the desktop computer to connect with Amazon services.
2013-9-22
7
MATLAB Distributed Computing Server™
MATLAB Distributed Computing server consists of workers that perform computations on the cluster computers. The server and the scheduler are installed on the cluster. You need to run as many server instances as the number of MATLAB workers your parallel computations require.
2013-9-22 16
Application—Parallel Computing
1. Select the EC2 Configuration as the default from the Parallel menu in MATLAB. 2. You can also query the cluster status using the findResource command; 3. You can use the matlabpool command to initiate an interactive session for using parfor or any of the parallel routines available; 4. Use functions such as batch, createMatlabpoolJob, createJob, or createParallelJob for sending MATLAB scripts and functions for offline execution on the Amazon EC2 cluster.
2013-9-22
5
Overall architecture
2013-9-22
6
Parallel Computing Toolbox™
MATLAB and the toolbox are on a client that connects to a cluster to access compute services offered by the MATLAB Distributed Computing Server and with which the users interact directly.
2013-9-223M源自TLAB and Amazon EC2
Full name: Parallel Computing with MATLAB on Amazon Elastic Compute Cloud Tow companies we need to know: Amazon Web services MathWorks
2013-9-22
15
network setup(VPN)
Using virtual private networks (VPN) is one of the several ways to set up the communication between different software components. We successfully experimented with OpenVPN, an open source VPN program. In fact, we must establish two VPNs. The first VPN is required between the clients within your organization and Scheduler-AMI (which runs the job manager) to enable users to find the job manager and to submit jobs and retrieve results from the job manager. A second VPN is required between the Worker-AMIs and the Scheduler-AMI. The two VPNs must be configured to push out their virtual networks to each other. This setup is required for workers to establish interactive connections with the client MATLAB running on users’ desktops as well as to establish the license manager for checking out worker keys.
2013-9-22
9
License manager
License Manager is for managing software licenses.
2013-9-22
10
How can we use MATLAB on AWS EC2?
We need to done these work if we want to use the MATLAB on the Amazon Cloud: Get Services from Amazon, including EC2 (Elastic Compute Cloud), S3 (Simple Storage Service).
Get license for MATLAB and Parallel Computing Toolbox, Distributed Computing Sever.
These services/softwares are not free! Trial software is not available for students !
2013-9-22 14
setting up MATLAB Distributed Computing server
Two approaches: 1. Bundle and upload the installer from your desktop. You can copy required files from the MathWorks installation DVD or download the files from your MathWorks account. If you use this option, you must use the Amazon com-mand line utilities to bundle and upload the installation files to the base AMI. 2. Download the installer directly to a running instance using a Web browser. Again, this requires logging in to you MathWorks account and downloading the appropriate installers for MATLAB Distributed Computing Server.
MATLAB on Amazon EC2
running MATLAB on the cloud
中科院自动化所 覃政科
2013-9-22
1
OUTLINE
Introduction Middleware Setup Application Future work
MATLAB
Toolbox
Amazon services
Set up the desktop computer to connect with Amazon services. The first, Simple Storage Service (S3) The Amazon EC2 service Choosing an Amazon EC2 AMI and Instance
Amazon services.
3. Set up MATLAB Distributed Computing Server to run on the Amazon cluster.
2013-9-22 12
Steps to setup MATLAB on AWS EC2
4. Set up the scheduler.
MATLAB ON AWS EC2
Server
Distributed sever
Scheduler
Network
License Manager
2013-9-22
2
MATLAB
Math, Statistics, Optimization Control System Design and Analysis Signal Processing and Communications Image Processing and Computer Vision Test & Measurement Computational Finance Computational Biology Code Generation Application Deployment Database Connectivity and Reporting Parallel Computing
