TCP-IP Overview
tcpip四层协议

TCP/IP四层协议TCP/IP是一组用于互联网通信的协议集合,它由四个不同的层次组成,包括网络接口层、互联网层、传输层和应用层。
每个层次都有不同的功能和责任,共同构成了现代网络通信的基础架构。
网络接口层网络接口层是TCP/IP协议中最底层的一层,它定义了如何在物理网络上进行数据传输。
它负责将数据帧从一个主机传输到另一个主机,并处理硬件相关的细节,如电压、时钟等。
在这一层,数据被分成帧,并通过物理介质进行传输。
互联网层互联网层是TCP/IP协议中的第二层,它负责实现主机到主机之间的数据传输。
互联网层使用IP协议来定义主机的地址和路由选择。
IP地址是互联网上唯一标识一个主机的地址,它是一个32位的数字,被分为四个八位组,通常以点分十进制表示。
互联网层的一个重要功能是将数据包从发送主机路由到目标主机。
路由器是互联网层的关键组件,它根据IP地址的信息来决定最佳路径,并将数据包发送到下一个路由器,直到最终到达目标主机。
传输层传输层是TCP/IP协议的第三层,它负责在主机之间提供端到端的通信。
传输层有两个主要的协议:传输控制协议(TCP)和用户数据报协议(UDP)。
TCP是一种可靠的面向连接的协议,它确保数据的可靠传输。
它通过使用序列号、确认和重传等机制来保证数据的完整性和顺序性。
TCP适用于对数据传输的可靠性有较高要求的应用,如文件传输和电子邮件。
UDP是一种无连接的协议,它提供了一种简单的数据传输方式。
与TCP不同,UDP不保证数据的可靠传输。
它适合于对数据传输延迟要求较低的应用,如音频和视频流媒体。
应用层应用层是TCP/IP协议的最高层,它为用户提供了各种不同的网络服务。
应用层协议包括HTTP、FTP、SMTP等,它们负责在应用程序之间传输数据。
HTTP(超文本传输协议)是一种用于在Web浏览器和Web服务器之间传输数据的协议。
它负责在客户端和服务器之间传递HTML页面、图像、样式表等。
FTP(文件传输协议)是一种用于在主机之间传输文件的协议。
TCPIP的层次结构

TCPIP的层次结构TCP/IP 是万维网(WWW)的基础通信协议栈,是指在网络中,网络设备之间的数据通信时,采用的通信协议集合。
URL 就是采用 TCP/IP 协议集合传输数据的一种规范性的表示方式。
TCP/IP 协议一共分为四层,由底往上分别是:第四层:应用层:这是一种最易于人们理解的网络协议类型,也是最容易实现和调试的类型。
它关注的是用户和软件应用程序如何通过网络对话,是一种用来标准化网络应用程序接口的协议,是用户最高级别视角。
常用的协议有:Simple Mail TransferProtocol(SMTP)、 Hypertext Transfer Protocol(HTTP)、 File TransferProtocol(FTP)、DNS 协议等。
第三层:传输层:比如 TCP 和 UDP,这一层就是定义了如何从源地址传到目标地址,并确保传输可靠。
它就是允许网络应用程序在两台主机之间传输数据的,它只提供“端对端”的数据传输,但是它不提供如何在网络上传输的细节,它确保了传输的稳定和可靠性。
第二层:网络层:比如 Internet 协议(IP),这一层就负责选择传输到下一个节点的路径,它还会决定哪些路径更可靠以及哪些路径使得传输数据相对更高效,或者是最短的。
因此它负责网际和组网互联间的数据传输。
第一层:链路层:比如以太网协议(Ethernet),这一层使网络能够实现物理上的连接,如用网线连接硬件设备。
要完成网络报文在物理连接间的转发,则必须有一种用来处理物理和数据链路层功能的协议,如常用的以太网协议。
总的来说,使用 TCP/IP 协议存储在网络中的信息以及传输协议的内容,在从一台主机传输到另一台主机时,将依次经由应用层、传输层、网络层、链路层,最终完成数据传输。
TCP/IP 协议让计算机可以了解网络的另一台计算机以及网络外的所有其它主机的位置,来完成互联网的数据传输。
OSI七层模型和TCPIP模型及对应协议(详解)

OSI七层模型和TCPIP模型及对应协议(详解)1.OSI七层模型OSI(Open Systems Interconnection)七层模型是国际标准化组织(ISO)制定的一种网络体系结构模型,将计算机网络的功能划分为七个层次,每个层次负责不同的任务。
这些层次从底层到顶层分别为:物理层、数据链路层、网络层、传输层、会话层、表示层和应用层。
-物理层:负责传输比特流,即原始的0和1的比特流。
-数据链路层:将物理层传输的数据流划分为数据帧,并在物理传输媒介上发送和接收数据帧。
-网络层:负责通过不同网络节点进行数据的路由和转发,实现数据包的传输。
-传输层:负责端到端的通信连接,在传输过程中确保数据的可靠传输和错误控制。
-会话层:负责建立、管理和终止应用程序之间的通信会话。
-表示层:负责数据的格式化和解码、加密和解密,确保接收方能够正确理解发送方的数据。
-应用层:提供用户与网络的接口,支持各种应用程序的网络访问和通信。
2.TCP/IP模型TCP/IP模型是一种通信协议体系结构,目前是互联网的基础协议。
TCP/IP模型由四个层次构成,分别为网络接口层、互联网层、传输层和应用层。
-网络接口层:负责将数据帧从物理层传输到网络层,并对数据进行分割和重组。
-互联网层:负责将数据包从源主机传输到目的主机,包括IP协议、ARP协议和ICMP协议等。
-传输层:负责数据的可靠传输和错误控制,包括TCP(传输控制协议)和UDP(用户数据报协议)等。
-应用层:提供用户与网络的接口,支持各种应用程序的网络访问和通信,包括HTTP、FTP、SMTP等协议。
3.OSI七层模型和TCP/IP模型的对应关系及协议:-OSI的物理层对应TCP/IP的网络接口层,协议包括以太网、Wi-Fi 等。
-OSI的数据链路层对应TCP/IP的网络接口层,协议包括以太网、Wi-Fi等。
-OSI的网络层对应TCP/IP的互联网层,协议包括IP、ARP、ICMP等。
tcp ip工作原理

tcp ip工作原理今天咱们来唠唠TCP/IP的工作原理,这就像是探索网络世界里超级神秘又超级有趣的魔法一样哦。
咱先来说说啥是TCP/IP吧。
你可以把它想象成网络世界里的一套超酷规则,就像咱们在生活里玩游戏得有游戏规则一样。
TCP/IP呢,其实是一整套协议族,它就像是一群小伙伴,大家各司其职,一起让网络能够顺畅地运行。
那这个TCP啊,它就像是一个超级细心的快递小哥。
你想想,当你要在网络上发送一些数据,比如说你给朋友发一张超搞笑的图片或者一段很感人的文字。
这个数据就像是一个小包裹。
TCP小哥呢,它会先把这个小包裹好好地打包起来。
它可不会随随便便就把东西扔出去哦。
它会给这个包裹编上号,就像咱们给行李贴标签一样,这样接收方就能知道哪个包裹先来,哪个包裹后来啦。
而且呢,TCP小哥还特别负责,如果在运输过程中发现有包裹丢了,它会想尽办法重新发送,直到所有的包裹都安全到达目的地。
再来说说IP。
IP就像是一个超级导航员。
在这个大大的网络世界里,有无数的设备,就像无数的小房子一样。
每个设备都有自己的地址,这就是IP地址啦。
IP导航员的任务呢,就是要知道这些小房子在哪里,然后把TCP小哥打包好的包裹准确地送到对应的小房子里。
它不管这个小房子是近还是远,只要知道地址,就会努力把包裹送过去。
有时候,这个包裹可能要经过好多好多中间的小站点,就像快递要经过好几个转运中心一样,IP导航员会规划好路线,让包裹顺利到达。
当你在电脑上或者手机上发送一个请求,比如说你想打开一个超级有趣的网页。
你的设备就会按照TCP/IP的规则来操作啦。
应用层的软件,就像你手机上的浏览器,它会把你的请求告诉TCP。
TCP就开始忙乎起来,把请求数据打包编号。
然后IP就拿着这个打包好的东西,根据目的地的IP地址开始找路。
这个过程中,可能会经过路由器这些网络设备。
路由器就像是网络世界里的交通警察,指挥着数据流量的走向。
你看,TCP/IP的工作就像是一场精心编排的舞蹈。
TCP IP协议体系结构简介

TCP/IP协议体系结构简介TCP/IP协议体系结构简介1、TCP/IP协议栈四层模型TCP/IP这个协议遵守一个四层的模型概念:应用层、传输层、互联层和网络接口层。
网络接口层模型的基层是网络接口层。
负责数据帧的发送和接收,帧是独立的网络信息传输单元。
网络接口层将帧放在网上,或从网上把帧取下来。
互联层互联协议将数据包封装成internet数据报,并运行必要的路由算法。
这里有四个互联协议:网际协议IP:负责在主机和网络之间寻址和路由数据包。
地址解析协议ARP:获得同一物理网络中的硬件主机地址。
网际控制消息协议ICMP:发送消息,并报告有关数据包的传送错误。
互联组管理协议IGMP:被IP主机拿来向本地多路广播路由器报告主机组成员。
传输层传输协议在计算机之间提供通信会话。
传输协议的选择根据数据传输方式而定。
两个传输协议:传输控制协议TCP:为应用程序提供可*的通信连接。
适合于一次传输大批数据的情况。
并适用于要求得到响应的应用程序。
用户数据报协议UDP:提供了无连接通信,且不对传送包进行可*的保证。
适合于一次传输小量数据,可*性则由应用层来负责。
应用层应用程序通过这一层访问网络。
网络接口技术IP使用网络设备接口规范NDIS向网络接口层提交帧。
IP支持广域网和本地网接口技术。
串行线路协议TCP/IPG一般通过internet串行线路协议SLIP或点对点协议PPP在串行线上进行数据传送。
(是不是我们平时把它称之为异步通信,对于要拿L INUX提供建立远程连接的朋友应该多研究一下这方面的知识)?2、ARP要在网络上通信,主机就必须知道对方主机的硬件地址(我们不是老遇到网卡的物理地址嘛)。
地址解析就是将主机IP地址映射为硬件地址的过程。
地址解析协议A RP用于获得在同一物理网络中的主机的硬件地址。
解释本地IP地址(要了解地址解析工作过程的朋友看好了)主机IP地址解析为硬件地址:(1)当一台主机要与别的主机通信时,初始化ARP请求。
学习网络编程了解TCPIP协议和网络通信原理

学习网络编程了解TCPIP协议和网络通信原理学习网络编程了解 TCP/IP 协议和网络通信原理网络编程成为了当今信息时代中必备的技能之一。
学习网络编程意味着我们要了解 TCP/IP 协议和网络通信原理,因为它们是构建互联网世界的基石。
本文将深入探讨 TCP/IP 协议和网络通信原理,帮助读者全面了解这个领域。
一、TCP/IP 协议简介TCP/IP(Transmission Control Protocol/Internet Protocol)是一组用于实现互联网通信的协议集合。
它由两个基本协议构成:TCP 和 IP。
1. TCP(Transmission Control Protocol):TCP 是一种面向连接的可靠传输协议。
它通过将数据分割成小的数据包,并进行顺序管理和确认机制,在网络间确保可靠的数据传输。
TCP 还负责错误检测和差错纠正,确保数据完整性。
2. IP(Internet Protocol):IP 是一种无连接的不可靠传输协议。
它负责将数据包从源地址传递到目标地址,通过 IP 地址标识不同的网络设备和计算机。
IP 提供了最基础的寻址和路由功能,确保数据能够在网络中正确传递。
二、网络通信原理网络通信的基本原理是数据的传输和交换。
在理解网络通信原理之前,我们需要了解一些基本概念:1. 客户端(Client):客户端是发起请求的一方,它向服务器发送请求并接收响应。
客户端可以是个人计算机、智能手机等终端设备。
2. 服务器(Server):服务器是响应请求的一方,它接收客户端的请求并提供相应的服务或数据。
服务器通常是高性能、高可靠性的计算机。
3. 网络协议(Network Protocol):网络协议是计算机在网络中通信和交流的规则和约定。
TCP/IP 协议就是其中之一,它规定了数据的传输格式、传输方式和通信规则。
基于以上概念,网络通信的过程可以简化为以下几个步骤:1. 建立连接:客户端向服务器发送连接请求,服务器接收并确认连接请求,建立连接。
TCP IP协议论文

TCP/IP协议在网络中的应用(姓名)摘要:TCP/IP(Transmission Control Protocol/Internet Protocol)的简写,中文译名为传输控制协议/因特网互联协议,又叫网络通讯协议,这个协议是Internet最基本的协议、Internet国际互联网络的基础,简单地说,就是由网络层的IP协议和传输层的TCP协议组成的。
TCP/IP 是供已连接因特网的计算机进行通信的通信协议,是传输控制协议/网际协议。
它定义了电子设备(比如计算机)如何连入因特网,以及数据如何在它们之间传输的标准。
是互联网中的基本通信语言或协议。
它在计算机网络中发挥了重要的作用,本文即概述了TCP/IP协议在网络中的应用。
关键词:TCP/IP;计算机;因特网;应用;The applications of TCP/IP protocol in network(姓名)Abstract:TCP protocol IP(Transmission Control Protocol/Internet Protocol) the simplified, chinese translated name is a transmission control agreement with the agreement, and interconnected network of communication and internet protocols the agreement is the most basic agreement, internet international the internet. In short, with IP network layer of the agreement and the transport layer of the TCP protocol. TCP/IP is for the computers are connected via the internet communications, a transmission control agreement internet protocols. It defines the electronic devices ( such as computer )how the Internet, and the transmission of data between them. Internet standards are the basic communications language or protocols. It is in a computer network played an important role, this provides an overview of the TCP protocol in a network IP applications.Key words:TCP/IP;computer;Internet;application;1 TCP/IP协议的概况1.1 TCP/IP协议的定义TCP/IP 是供已连接因特网的计算机进行通信的通信协议。
tcp ip四层协议

tcp ip四层协议TCP/IP四层协议。
TCP/IP协议是互联网的核心协议之一,它是一种分层的协议体系,包括四层,应用层、传输层、网络层和数据链路层。
每一层都有其特定的功能和作用,下面我们来详细了解一下TCP/IP四层协议。
首先,我们来看应用层。
应用层是最靠近用户的一层,它提供了用户与网络应用软件之间的接口。
在这一层,常见的协议有HTTP、FTP、SMTP等,它们负责传输用户数据和控制信息。
应用层的协议是用户最直接接触到的,它们决定了用户能否顺利地使用各种网络应用。
接下来是传输层。
传输层主要负责端到端的通信和数据传输。
在这一层,最常见的协议是TCP和UDP。
TCP协议提供了可靠的、面向连接的数据传输服务,它能够保证数据的完整性和顺序性。
而UDP协议则是一种无连接的传输协议,它更加轻量级,适用于一些对实时性要求较高的应用。
然后是网络层。
网络层主要解决数据在网络中的传输问题,它使用IP协议进行数据包的传输和路由选择。
IP协议是整个TCP/IP协议族中最为核心的协议,它负责将数据包从源主机传输到目标主机。
此外,在网络层还有一些辅助协议,如ICMP协议用于网络故障排除,ARP协议用于地址解析等。
最后是数据链路层。
数据链路层负责将数据包转换为比特流,并通过物理介质进行传输。
在这一层,最常见的协议是以太网协议,它是目前最为广泛使用的局域网协议。
此外,数据链路层还包括了一些子层,如MAC子层和LLC子层,它们负责数据的帧封装和链路控制。
总的来说,TCP/IP四层协议是互联网通信的基础,它将整个通信过程分解为多个层次,每一层都有其特定的功能和作用。
通过了解这些层次,我们可以更好地理解互联网通信的原理,从而更好地进行网络应用开发和故障排除。
希望本文能够帮助大家更深入地了解TCP/IP协议。
TCP-IP四层体系结构及每层作用

应该说是Internet四层体系结构1.数据链路层2.网络层3.传输层4.应用层,其中IP是在第二层网络层中,TCP是在第3层传输层中,Internet体系结构最重要的是TCP/IP协议,是实现互联网络连接性和互操作性的关键,它把许多台的Internet上的各种网络连接起来。
Internet的其他网络协议都要用到TCP/IP协议提供的功能,因而称我们习惯称整Internet协议族为TCP/IP协议族,简称TCP/IP协议也可称为TCP/IP四层体系结构,1.数据链路层:数据链路层是物理传输通道,可使用多种传输介质传输,可建立在任何物理传输网上。
比如光纤、双绞线等2.网络层:其主要功能是要完成网络中主机间“分组”(Packet)的传输。
含有4个协议:(1)网际协议IP负责分组数据的传输,各个IP数据之间是相互独立的。
(2)互联网控制报文协议ICMPIP层内特殊的报文机制,起控制作用,能发送报告差错或提供有关意外情况的信息。
因为ICMP的数据报通过IP送出因此功能上属于网络的第3层。
3)地址转换协议ARP为了让差错或意外情况的信息能在物理网上传送到目的地,必须知道彼此的物理地址,这样就存在把互联网地址(是32位的IP地址来标识,是一种逻辑地址)转换为物理地址的要求,这就需要在网络层上有一组服务(协议)能将IP地址转换为相应的网络地址,这组协议就是APP.(可以把互联网地址看成是外识别地址和物理地址看成是内识别地址)(4)反向地址转换协议RARPRARP用于特殊情况,当只有自己的物理地址没有IP地址时,可通过RARP获得IP 地址,如果遇到断电或重启状态下,开机后还必需再使用RARP重新获取IP地址。
广泛用于获取无盘工作站的IP地址。
3.传输层:其主要任务是向上一层提供可靠的端到端(End-to-End)服务,确保“报文”无差错、有序、不丢失、无重复地传输。
它向高层屏蔽了下层数据通信的细节,是计算机通信体系结构中最关键的一层。
简述TCP-IP参考模型定义及各层的主要功能
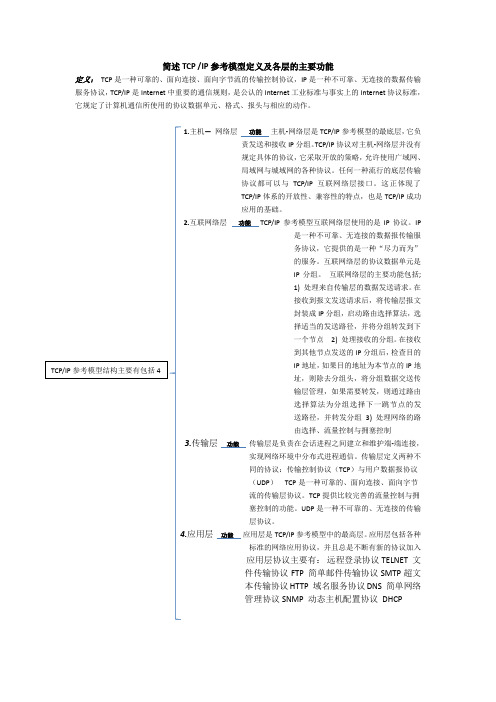
简述TCP /IP参考模型定义及各层的主要功能定义:TCP是一种可靠的、面向连接、面向字节流的传输控制协议,IP是一种不可靠、无连接的数据传输服务协议,TCP/IP是Internet中重要的通信规则,是公认的Internet工业标准与事实上的Internet协议标准,它规定了计算机通信所使用的协议数据单元、格式、报头与相应的动作。
1.主机—网络层功能主机-网络层是TCP/IP参考模型的最底层,它负责发送和接收IP分组。
TCP/IP协议对主机-网络层并没有规定具体的协议,它采取开放的策略,允许使用广域网、局域网与城域网的各种协议。
任何一种流行的底层传输协议都可以与TCP/IP互联网络层接口。
这正体现了TCP/IP体系的开放性、兼容性的特点,也是TCP/IP成功应用的基础。
2.互联网络层功能TCP/IP参考模型互联网络层使用的是IP协议。
IP是一种不可靠、无连接的数据报传输服务协议,它提供的是一种“尽力而为”的服务。
互联网络层的协议数据单元是IP分组。
互联网络层的主要功能包括;1) 处理来自传输层的数据发送请求。
在接收到报文发送请求后,将传输层报文封装成IP分组,启动路由选择算法,选择适当的发送路径,并将分组转发到下一个节点2) 处理接收的分组。
在接收到其他节点发送的IP分组后,检查目的IP地址,如果目的地址为本节点的IP地址,则除去分组头,将分组数据交送传输层管理,如果需要转发,则通过路由选择算法为分组选择下一跳节点的发送路径,并转发分组3) 处理网络的路由选择、流量控制与拥塞控制3.传输层功能传输层是负责在会话进程之间建立和维护端-端连接,实现网络环境中分布式进程通信。
传输层定义两种不同的协议:传输控制协议(TCP)与用户数据报协议(UDP)TCP是一种可靠的、面向连接、面向字节流的传输层协议。
TCP提供比较完善的流量控制与拥塞控制的功能。
UDP是一种不可靠的、无连接的传输层协议。
4.应用层功能应用层是TCP/IP参考模型中的最高层。
TCPIP体系结构

TCP/IP是分层体系结构
TCP/IP是互联网的核心,是实现异构网络互连的通信协议,通过它可以实现各种异构网络或异种机之间的互联通信。
TCP/IP(Transmission Control Protocol/Internet Protocol)协议,或称网络通信协议,它是一组互联网协议族,包括上百个各种功能的协议,是国际互联网络的基础。
TCP是指传输控制协议,规定一种可靠的数据信息传递服务。
IP是指互联网协议(网络通信协议),也就是为计算机网络相互连接进行通信而设计的协议。
任何厂家生产的计算机系统,只要遵守IP协议就可以与因特网互连互通。
TCP/IP是一个四层的分层体系结构,自上而下分为:应用层、传输层、网间网层和网络接口层。
1、网络接口层:这是TCP/IP软件的最低层,负责接收IP数据报并通过网络发送之,或者从网络上接收物理帧,抽出IP数据报,交给IP层。
2、网际层:负责相邻计算机之间的通信。
其功能包括三方面。
1是处理来自传输层的分组发送请求,收到请求后,将分组装入IP数据报,填充报头,选择去往信宿机的路径,然后将数据报发往适当的网络接口。
3、传输层:提供应用程序间的通信。
其功能包括:格式化信息流;提供可靠传输。
为实现后者,传输层协议规定接收端必须发回确认,并且假如分组丢失,必须重新发送。
4、应用层:向用户提供一组常用的应用程序,比如电子邮件、文件传输访问、远程登录等。
TCP协议结构

TCP协议结构篇一:TCP-IP协议数据报结构详解TCP/IP协议数据报结构详解TCP/IP协议中各层的数据报结构是一个比较抽象的内容,大家在日常学习过程中往往难以理解和掌握,常常是死记硬背把它记住了事。
本文首先利用Sniffer工具捕获了FTP命令操作过程中的所有数据包,然后对Sniffer工具中捕获的每一部分数据包的含义进行了详细的阐述,最后总结归纳出TCP/IP协议中网络接口层、网络层、传输层的数据报文结构,从而使大家加深对TCP/IP协议各层数据报结构的理解和掌握。
一、捕获FTP命令底层数据包1、搭建网络环境。
建立一台FTP服务器,设置IP地址为:76.88.16.16。
建立一台FTP客户端,IP地址设为76.88.16.104,在其上安装Sniffer软件。
将这两台设备通过集线器连接起来。
2、定义过滤器。
在FTP客户端上运行Sniffer软件,进入系统,点“Monitor”-“Matrixa”,选中本机,点鼠标右健,选择“Define Filter…”,在“Define Filter…”窗口,点“Advanced”,选择IP->TCP->FTP,点“确定”,即已定义好过滤器,如图1所示。
图13、捕获FTP命令数据包。
首先,在Sniffer中选择“Monitor”-“Matrix”,点击“Capture”命令开始捉包。
然后,在FTP客户端上进入DOS提示符下,输入“”命令,输入FTP用户名和口令,登录FTP服务器,进行文件的下载,最后输入“bye”命令退出FTP程序,完成整个FTP命令操作过程。
最后,点击Sniffer中的“停止捕捉”,选择“Decode”选项,完成FTP命令操作过程数据包的捕获,并显示在屏幕上。
下面对Sniffer捕获的底层数据包进行详细的介绍。
二、网络接口层DLC帧结构详解图2如图2所示,在Sniffer捕获的DLC数据帧中依次包括以下信息:目的MAC地址Destination=GigTecAAD4A3,源MAC地址Source=000C,以太网类型Ethertype=0800(IP),8表示为以太网。
TCPIP是什么

TCPIP是什么TCPIP(Transmission Control Protocol/Internet Protocol)是一种用于互联网通信的协议套件,它是互联网的核心协议。
TCPIP协议是一种通信规则,定义了数据在网络中的传输方式、报文的格式以及数据的处理方法,能够保证数据的正常传输和顺序交付。
TCPIP协议套件由多个协议组成,其中最核心的两个协议是TCP和IP。
TCP(Transmission Control Protocol)负责数据的传输,保证数据的可靠性和顺序性;IP(Internet Protocol)负责网络的路由和寻址,将数据分割成小块并通过不同的网络节点传输。
TCPIP协议套件遵循一种分层模型,即为OSI参考模型(Open System Interconnection Reference Model)的网络层和传输层提供具体的实现方式。
在此模型中,TCPIP协议套件位于第三层(网络层)和第四层(传输层),用于处理数据在网络中的传输和路由。
TCPIP协议套件具有以下特点和功能:1. 可靠性:TCP协议通过建立握手、确认和重传机制,保证数据的可靠传输。
当数据在传输过程中出现丢失或损坏时,TCP会自动进行重传,确保数据的完整性。
2. 顺序性:TCP协议保证数据的顺序性,即将发送的数据按照发送顺序进行接收和重组。
3. 路由和寻址:IP协议负责网络的路由和寻址,将数据从源主机发送到目标主机。
每个主机在网络中都有一个唯一的IP地址,它用于标识主机的位置和识别。
4. 分包和重组:IP协议将数据分割成小块(分包),并通过网络的各个节点进行传输。
接收端的IP协议则根据序号和标识字段对数据进行重组,还原为原始数据。
5. 多路复用和多路分解:TCPIP协议可以同时处理多个应用程序的数据传输,实现多路复用和多路分解的功能。
6. 网络互联:TCPIP协议套件允许不同类型的网络互相连接,实现全球范围内的互联网。
TCPIP路由技术(卷一)第二版

Chapter 1. TCP/IP ReviewChapter 2. IPv6 Overview※IPv6 Addresses1. Address Representation128位的IPv6地址被分为8个16位的段,用16进制数值表示,形如:3ffe:1944:0100:000a:0000:00bc:2500:0d0b书写IPv6地址的规则:1.每个段的开头的0可以被省略,例如上面的IPv6地址可以被写为:3ffe:1944:100:a:0:bc:2500:d0b;2.单一连续的多个段的0,可以被简写为“::”。
例如:ff02:0000:0000:0000:0000:0000:0000:0005可以被简写为ff02::5(“::”在一个IPv6地址中只能存在一个,否则会出现混淆);3.掩码的规则是:3ffe:1944:100:a::/64以下是部分特殊的IPv6地址:默认路由:::/0;unspecified地址,在NDP中使用:::/1282. IPv6 Address TypesIPv6地址的三种类型:1.Unicast2.Anycast3.MulticastIPv6地址中不存在广播地址,取而代之的是"all nodes" multicast地址(FF02::1)。
Global Unicast Addresses全球唯一的unicast地址。
其格式为:该格式在RFC 3587中定义,废弃和简化了之前将IPv6 unicast地址分为Top Level Aggregator (TLA)、Next-Level Aggregator (NLA)和其它区域的老格式。
主机部分(Host Portion)被称为Interface ID,Subnet ID包括在网络部分(Network Portion)中,global IPv6地址的Interface ID部分在大多数情况下长度为64位,Subnet ID在大多数情况下是16位。
TCPIP数据包结构详解

TCPIP数据包结构详解TCP/IP是一种广泛使用的网络协议,用于在Internet上进行数据通信。
TCP/IP数据包结构是指TCP/IP协议对数据包的组织和封装方式。
下面将详细介绍TCP/IP数据包结构。
TCP/IP数据包由多个部分组成,其中包括IP头部、TCP/UDP头部、数据(Payload)以及选项部分。
下面将逐一介绍每个部分的功能和结构。
1. IP头部(IP Header):IP头部是TCP/IP数据包的第一个部分,用于指定源IP地址和目标IP地址。
IP头部还包含其他一些字段,如版本号、服务类型、包长、标识符、标志位等。
-版本号:指定IP协议的版本,如IPv4或IPv6-服务类型:指定数据包的优先级。
-包长:指定整个IP数据包的长度。
-标识符:用于唯一标识一个数据包。
-标志位:用于控制数据包的分片和重组。
2. TCP/UDP头部(TCP/UDP Header):TCP/UDP头部紧随IP头部,用于指定源端口和目标端口。
TCP头部和UDP头部具有相似的结构。
-源端口:指定发送数据的应用程序端口。
-目标端口:指定接收数据的应用程序端口。
-序列号和确认号:用于实现TCP协议的可靠传输机制。
- 标识TCP选项:例如最大分段大小(Maximum Segment Size)等。
3. 数据(Payload):数据部分是TCP/IP数据包中的主要内容,包含应用层的数据信息。
例如,HTTP协议中的请求或响应报文就是通过数据部分传输的。
4. 选项部分(Options):选项部分是可选的,用于存储一些与特定协议相关的额外信息。
例如,TCP协议中的选项可以用于实现窗口缩放和选择确认等功能。
总结起来,TCP/IP数据包结构包括IP头部、TCP/UDP头部、数据和选项部分。
这些部分的结构和字段的具体定义可以根据具体的协议版本和实现来确定。
在实际的网络通信中,数据包会通过路由器和交换机等设备进行传输。
路由器根据IP头部中的目标IP地址进行路由选择,将数据包转发到正确的下一个网络节点。
TCPIP协议简介

TCP/IP协议简介其他的体系结构:IBM/SNA、DECnet、Apple Talk、IPX、Banyan/VINESφ TCP/IP协议栈的结构TCP/IP协议栈是由多个协议组成,也采用分层结构。
·网络接口层(Network accrss layer)对应OSI的1、2层。
·网络(网际)层协议(Internet layer)对应OSI的3层,包括IP/ARP/RARP/ICMP·传输层协议(Transport layer)对应OSI的第4层,包括TCP/UDP。
·应用层协议(Application layer)对应OSI的5~7层,包括Telnet/FTP/SMTP/。
φ IP寻址IP地址的分类及寻址规则:·IP地址回顾TCP/IP网上的计算设备或主机(也称为节点)都分配有一个唯一的地址,叫做IP地址。
IP地址属于三层逻辑地址,用来标识TCP/IP网络中的每一台设备,采用分成结构,32位,共4个8位组,采用网络位+主机位的形式。
·IP地址的分类地址类型引导位网络位地址范围地址结构主机位可用地址数A类 0 1-126(127保留)网+主+主+主 16777214B类 10 128-191 网+网+主+主 65534C类 110 192-223 网+网+网+主 254D类 1110 224-239 组播地址E类 1111 240-研究用地址*127.X.X.X用于本地回送测试IP网络地址由NIC统一分配,以保证IP地址的唯一性注意:NIC分配的是网络地址,而不是具体的IP地址。
具体主机的IP地址由得到某一网络地址的机构或组织自行决定如何分配。
·私有地址(Private address)用于企业内部网的IP地址分配,不会被任何INTERNET上的路由器转发10.0.0.0-10.255.255.255 1个A类地址172.16.0.0-172.31.255.255 16个B类地址192.168.0.0-192.168.255.255 256个C类地址注意:拥有私有IP地址的主机不可直接接入INTERNET,要通过NAT/PAT转换,以公有IP的形式接入。
TCPIP详解
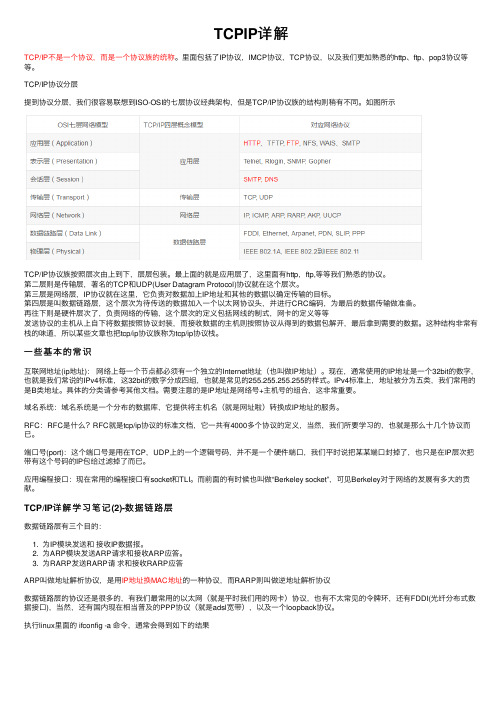
TCPIP详解TCP/IP不是⼀个协议,⽽是⼀个协议族的统称。
⾥⾯包括了IP协议,IMCP协议,TCP协议,以及我们更加熟悉的http、ftp、pop3协议等等。
TCP/IP协议分层提到协议分层,我们很容易联想到ISO-OSI的七层协议经典架构,但是TCP/IP协议族的结构则稍有不同。
如图所⽰TCP/IP协议族按照层次由上到下,层层包装。
最上⾯的就是应⽤层了,这⾥⾯有http,ftp,等等我们熟悉的协议。
第⼆层则是传输层,著名的TCP和UDP(User Datagram Protocol)协议就在这个层次。
第三层是⽹络层,IP协议就在这⾥,它负责对数据加上IP地址和其他的数据以确定传输的⽬标。
第四层是叫数据链路层,这个层次为待传送的数据加⼊⼀个以太⽹协议头,并进⾏CRC编码,为最后的数据传输做准备。
再往下则是硬件层次了,负责⽹络的传输,这个层次的定义包括⽹线的制式,⽹卡的定义等等发送协议的主机从上⾃下将数据按照协议封装,⽽接收数据的主机则按照协议从得到的数据包解开,最后拿到需要的数据。
这种结构⾮常有栈的味道,所以某些⽂章也把tcp/ip协议族称为tcp/ip协议栈。
⼀些基本的常识互联⽹地址(ip地址):⽹络上每⼀个节点都必须有⼀个独⽴的Internet地址(也叫做IP地址)。
现在,通常使⽤的IP地址是⼀个32bit的数字,也就是我们常说的IPv4标准,这32bit的数字分成四组,也就是常见的255.255.255.255的样式。
IPv4标准上,地址被分为五类,我们常⽤的是B类地址。
具体的分类请参考其他⽂档。
需要注意的是IP地址是⽹络号+主机号的组合,这⾮常重要。
域名系统:域名系统是⼀个分布的数据库,它提供将主机名(就是⽹址啦)转换成IP地址的服务。
RFC:RFC是什么?RFC就是tcp/ip协议的标准⽂档,它⼀共有4000多个协议的定义,当然,我们所要学习的,也就是那么⼗⼏个协议⽽已。
端⼝号(port):这个端⼝号是⽤在TCP,UDP上的⼀个逻辑号码,并不是⼀个硬件端⼝,我们平时说把某某端⼝封掉了,也只是在IP层次把带有这个号码的IP包给过滤掉了⽽已。
什么是TCPIP-tcpip详解

TCP/IP是Transmission Control Protocol/Internet Protocol(传输控制协议/网际互联协议)的缩写。
它是1978年~1979年由美国国防部高级研究计划局开发的用于异构网络的通信协议,协议包含了远程登录(Telnet)、文件传送(FTP)、电子邮件(SMTP)等,适用于各种不同的计算机系统的互联。
TCP/IP是目前十分流行的一种网络协议,它可提供任意互连的网络间的通信,几乎所用的网络操作系统都支持TCP/IP协议。
它是目前广泛使用的Internet的基础,虽然它不是国际标准,但事实上已成为计算机网络的工业标准。
2、TCP/IP应用两例TCP/IP应用一:远程登录(Telnet)UNIX是一个多用户系统。
多用户系统都有用户帐号概念。
用户帐号规定了用户对系统的使用权,用户登录进入后就可以访问系统的全部或部分资源。
远程登录就是指一个远地用户通过TCP/IP进入帐号,访问远地资源。
TELNET协议的目的是提供一个通用、双向、基于8位字符的通信服务。
它是面向终端的处理。
是一种网络上的虚终端。
(NVT)远程登录的目的在于访问远地系统的资源。
一个用户在登录后系统并不区分是否是本地用户。
所以用户在本地可以作的任何操作都可在远地进行。
如用户需要进行编译等操作是就需要TELNET到服务器上进行。
微机上的TELNET程序很多。
一般WINDOWS下的比较好(常见的有NETTERM、TERATERM、EASN等),大多支持中文。
DOS下的支持中文的TELNET较少。
TELNET到主机后使用主机操作系统命令。
(一般是UNIX命令)TCP/IP应用二:文件传输(FTP)FTP是用于TCP/IP网络的文件传输应用。
是TCP/IP中使用最广泛的应用之一。
FTP是基于客户/服务器模型设计的,客户和服务器之间利用TCP建立连接。
FTP服务器在这里是指提供FTP服务的机器。
任何一个UNIX系统都提供FTP Server服务。
网络编程-TCPIP各层介绍(5层模型讲解)

⽹络编程-TCPIP各层介绍(5层模型讲解)1、TCP/IP五层协议讲解物理层--数据链路层--⽹络层--传输层--应⽤层我们将应⽤层,表⽰层,会话层并作应⽤层,从tcp/ip五层协议的⾓度来阐述每层的由来与功能,搞清楚了每层的主要协议就理解了整个互联⽹通信的原理。
⾸先,⽤户感知到的只是最上⾯⼀层应⽤层,⾃上⽽下每层都依赖于下⼀层,所以我们从最下⼀层开始切⼊,⽐较好理解每层都运⾏特定的协议,越往上越靠近⽤户,越往下越靠近硬件2、物理层物理层由来:上⾯提到,孤⽴的计算机之间要想⼀起玩,就必须接⼊internet,⾔外之意就是计算机之间必须完成组⽹物理层功能:主要是基于电器特性发送⾼低电压(电信号),⾼电压对应数字1,低电压对应数字03、数据链路层(以太⽹协议:)数据链路层由来:单纯的电信号0和1没有任何意义,必须规定电信号多少位⼀组,每组什么意思数据链路层的功能:定义了电信号的分组⽅式以太⽹协议:早期的时候各个公司都有⾃⼰的分组⽅式,后来形成了统⼀的标准,即以太⽹协议ethernetethernet规定⼀组电信号构成⼀个数据包,叫做‘帧’每⼀数据帧分成:报头head和数据data两部分mac地址:(⽹卡的地址)head中包含的源和⽬标地址由来:ethernet规定接⼊internet的设备都必须具备⽹卡,发送端和接收端的地址便是指⽹卡的地址,即mac地址mac地址:每块⽹卡出⼚时都被烧制上⼀个世界唯⼀的mac地址,长度为48位2进制,通常由12位16进制数表⽰(前六位是⼚商编号,后六位是流⽔线号)⼴播:有了mac地址,同⼀⽹络内的两台主机就可以通信了(⼀台主机通过arp协议获取另外⼀台主机的mac地址)ethernet采⽤最原始的⽅式,⼴播的⽅式进⾏通信,即计算机通信基本靠吼4、⽹络层(ip协议)⽹络层由来:有了ethernet、mac地址、⼴播的发送⽅式,世界上的计算机就可以彼此通信了,问题是世界范围的互联⽹是由⼀个个彼此隔离的⼩的局域⽹组成的,那么如果所有的通信都采⽤以太⽹的⼴播⽅式,那么⼀台机器发送的包全世界都会收到,这就不仅仅是效率低的问题了,这会是⼀种灾难必须找出⼀种⽅法来区分哪些计算机属于同⼀⼴播域,哪些不是,如果是就采⽤⼴播的⽅式发送,如果不是,就采⽤路由的⽅式(向不同⼴播域/⼦⽹分发数据包),mac地址是⽆法区分的,它只跟⼚商有关⽹络层功能:引⼊⼀套新的地址⽤来区分不同的⼴播域/⼦⽹,这套地址即⽹络地址4.1、IP协议:规定⽹络地址的协议叫ip协议,它定义的地址称之为ip地址,⼴泛采⽤的v4版本即ipv4,它规定⽹络地址由32位2进制表⽰范围0.0.0.0-255.255.255.255⼀个ip地址通常写成四段⼗进制数,例:172.16.10.1⼦⽹掩码:将ip地址分为⽹络地址和主机地址所谓”⼦⽹掩码”,就是表⽰⼦⽹络特征的⼀个参数。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Cisco − TCP/IP OverviewTable of ContentsTCP/IP Overview (1)Document ID: 13769 (1)Introduction (1)TCP/IP Technology (2)TCP (2)IP (3)Routing in IP Environments (5)Interior Routing Protocols (7)RIP (7)IGRP (7)EIGRP (7)OSPF (8)Integrated IS−IS (8)Exterior Routing Protocols (8)EGP (8)BGP (8)Cisco's TCP/IP Implementation (9)Access Restrictions (9)Tunneling (9)IP Multicast (9)Suppressing Network Information (10)Administrative Distance (10)Routing Protocol Redistribution (10)Serverless Network Support (10)Network Monitoring and Debugging (10)Summary (11)NetPro Discussion Forums − Featured Conversations (11)Related Information (11)TCP/IP OverviewDocument ID: 13769IntroductionTCP/IP TechnologyTCPIPRouting in IP EnvironmentsInterior Routing ProtocolsRIPIGRPEIGRPOSPFIntegrated IS−ISExterior Routing ProtocolsEGPBGPCisco's TCP/IP ImplementationAccess RestrictionsTunnelingIP MulticastSuppressing Network InformationAdministrative DistanceRouting Protocol RedistributionServerless Network SupportNetwork Monitoring and DebuggingSummaryNetPro Discussion Forums − Featured ConversationsRelated InformationIntroductionIn the two decades since their invention, the heterogeneity of networks has expanded further with the deployment of Ethernet, Token Ring, Fiber Distributed Data Interface (FDDI), X.25, Frame Relay, Switched Multimegabit Data Service (SMDS), Integrated Services Digital Network (ISDN), and most recently, Asynchronous Transfer Mode (ATM). The Internet protocols are the best proven approach to internetworking this diverse range of LAN and WAN technologies.The Internet Protocol suite includes not only lower−level specifications, such as Transmission Control Protocol (TCP) and Internet Protocol (IP), but specifications for such common applications as electronic mail, terminal emulation, and file transfer. Figure 1 shows the TCP/IP protocol suite in relation to the OSI Reference model. Figure 2 shows some of the important Internet protocols and their relationship to the OSI Reference Model. For information on the OSI Reference model and the role of each layer, please refer to the document Internetworking Basics.The Internet protocols are the most widely implemented multivendor protocol suite in use today. Support for at least part of the Internet Protocol suite is available from virtually every computer vendor.TCP/IP TechnologyThis section describes technical aspects of TCP, IP, related protocols, and the environments in which these protocols operate. Because the primary focus of this document is routing (a layer 3 function), the discussion of TCP (a layer 4 protocol) will be relatively brief.TCPTCP is a connection−oriented transport protocol that sends data as an unstructured stream of bytes. By using sequence numbers and acknowledgment messages, TCP can provide a sending node with delivery information about packets transmitted to a destination node. Where data has been lost in transit from source to destination, TCP can retransmit the data until either a timeout condition is reached or until successful delivery has been achieved. TCP can also recognize duplicate messages and will discard them appropriately. If the sending computer is transmitting too fast for the receiving computer, TCP can employ flow control mechanisms to slow data transfer. TCP can also communicates delivery information to the upper−layer protocols and applications it supports. All these characteristics makes TCP an end−to−end reliable transport protocol. TCP is specified in RFC 793 .Figure 1 TCP/IP Protocol Suite in Relation to the OSI Reference ModelFigure 2 Important Internet Protocols in Relation to the OSI Reference ModelRefer to the TCP section of Internet Protocols for more information.IPIP is the primary Layer 3 protocol in the Internet suite. In addition to internetwork routing, IP provides error reporting and fragmentation and reassembly of information units called datagrams for transmission over networks with different maximum data unit sizes. IP represents the heart of the Internet Protocol suite.Note: The term IP in the section refers to IPv4 unless otherwise stated explicitly.IP addresses are globally unique, 32−bit numbers assigned by the Network Information Center. Globally unique addresses permit IP networks anywhere in the world to communicate with each other.An IP address is divided into two parts. The first part designates the network address while the second part designates the host address.The IP address space is divided into different network classes. Class A networks are intended mainly for use with a few very large networks, because they provide only 8 bits for the network address field. Class B networks allocate 16 bits, and Class C networks allocate 24 bits for the network address field. Class C networks only provide 8 bits for the host field, however, so the number of hosts per network may be a limiting factor. In all three cases, the left most bit(s) indicate the network class. IP addresses are written in dotted decimal format; for example, 34.0.0.1. Figure 3 shows the address formats for Class A, B, and C IP networks. Figure 3 Address Formats for Class A, B, and C IP NetworksIP networks also can be divided into smaller units called subnetworks or "subnets." Subnets provide extra flexibility for the network administrator. For example, assume that a network has been assigned a Class A address and all the nodes on the network use a Class A address. Further assume that the dotted decimal representation of this network's address is 34.0.0.0. (All zeros in the host field of an address specify the entire network.) The administrator can subdivide the network using subnetting. This is done by "borrowing" bits from the host portion of the address and using them as a subnet field, as depicted in Figure 4.Figure 4 "Borrowing" BitsIf the network administrator has chosen to use 8 bits of subnetting, the second octet of a Class A IP address provides the subnet number. In our example, address 34.1.0.0 refers to network 34, subnet 1; address 34.2.0.0 refers to network 34, subnet 2, and so on.The number of bits that can be borrowed for the subnet address varies. To specify how many bits are used to represent the network and the subnet portion of the address, IP provides subnet masks. Subnet masks use the same format and representation technique as IP addresses. Subnet masks have ones in all bits except those that specify the host field. For example, the subnet mask that specifies 8 bits of subnetting for Class A address 34.0.0.0 is 255.255.0.0. The subnet mask that specifies 16 bits of subnetting for Class A address 34.0.0.0 is 255.255.255.0. Both of these subnet masks are pictured in Figure 5. Subnet masks can be passed through a network on demand so that new nodes can learn how many bits of subnetting are being used on their network. Figure 5 Subnet MasksTraditionally, all subnets of the same network number used the same subnet mask. In other words, a network manager would choose an eight−bit mask for all subnets in the network. This strategy is easy to manage forboth network administrators and routing protocols. However, this practice wastes address space in some networks. Some subnets have many hosts and some have only a few, but each consumes an entire subnet number. Serial lines are the most extreme example, because each has only two hosts that can be connected via a serial line subnet.As IP subnets have grown, administrators have looked for ways to use their address space more efficiently. One of the techniques that has resulted is called Variable Length Subnet Masks (VLSM). With VLSM, a network administrator can use a long mask on networks with few hosts and a short mask on subnets with many hosts. However, this technique is more complex than making them all one size, and addresses must be assigned carefully.Of course in order to use VLSM, a network administrator must use a routing protocol that supports it. Cisco routers support VLSM with Open Shortest Path First (OSPF), Integrated Intermediate System to Intermediate System (Integrated IS−IS), Enhanced Interior Gateway Routing Protocol (Enhanced IGRP), and static routing. Refer to IP Addressing and Subnetting for New Users for more information about IP addressing and subnetting.On some media, such as IEEE 802 LANs, IP addresses are dynamically discovered through the use of two other members of the Internet protocol suite: Address Resolution Protocol (ARP) and Reverse Address Resolution Protocol (RARP). ARP uses broadcast messages to determine the hardware (MAC layer) address corresponding to a particular network−layer address. ARP is sufficiently generic to allow use of IP with virtually any type of underlying media access mechanism. RARP uses broadcast messages to determine the network−layer address associated with a particular hardware address. RARP is especially important to diskless nodes, for which network−layer addresses usually are unknown at boot time.Routing in IP EnvironmentsAn "internet" is a group of interconnected networks. The Internet, on the other hand, is the collection of networks that permits communication between most research institutions, universities, and many other organizations around the world. Routers within the Internet are organized hierarchically. Some routers are used to move information through one particular group of networks under the same administrative authority and control. (Such an entity is called an autonomous system.) Routers used for information exchange within autonomous systems are called interior routers, and they use a variety of interior gateway protocols (IGPs) to accomplish this end. Routers that move information between autonomous systems are called exterior routers; they use the Exterior Gateway Protocol (EGP) or Border Gateway Protocol (BGP). Figure 6 shows the Internet architecture.Figure 6 Representation of the Internet ArchitectureRouting protocols used with IP are dynamic in nature. Dynamic routing requires the software in the routing devices to calculate routes. Dynamic routing algorithms adapt to changes in the network and automatically select the best routes. In contrast with dynamic routing, static routing calls for routes to be established by the network administrator. Static routes do not change until the network administrator changes them.IP routing tables consist of destination address/next hop pairs. This sample routing table from a Cisco router shows that the first entry is interpreted as meaning "to get to network 34.1.0.0 (subnet 1 on network 34), the next stop is the node at address 54.34.23.12":R6−2500# show ip routeCodes: C − connected, S − static, I − IGRP, R − RIP, M − mobile, B − BGPD − EIGRP, EX − EIGRP external, O − OSPF, IA − OSPF inter areaN1 − OSPF NSSA external type 1, N2 − OSPF NSSA external type 2E1 − OSPF external type 1, E2 − OSPF external type 2, E − EGPi − IS−IS, su − IS−IS summary, L1 − IS−IS level−1, L2 − IS−IS level−2ia − IS−IS inter area, * − candidate default, U − per−user static routeo − ODR, P − periodic downloaded static routeGateway of last resort is not set34.0.0.0/16 is subnetted, 1 subnetsO 34.1.0.0 [110/65] via 54.34.23.12, 00:00:51, Serial054.0.0.0/24 is subnetted, 1 subnetsC 54.34.23.0 is directly connected, Serial0R6−2500#As we have seen, IP routing specifies that IP datagrams travel through an internetwork one router hop at a time. The entire route is not known at the outset of the journey. Instead, at each stop, the next router hop is determined by matching the destination address within the datagram with an entry in the current node's routing table. Each node's involvement in the routing process consists only of forwarding packets based on internal information. IP does not provide for error reporting back to the source when routing anomalies occur.This task is left to another Internet protocol t he Internet Control Message Protocol (ICMP).ICMP performs a number of tasks within an IP internetwork. In addition to the principal reason for which it was created (reporting routing failures back to the source), ICMP provides a method for testing node reachability across an internet (the ICMP Echo and Reply messages), a method for increasing routing efficiency (the ICMP Redirect message), a method for informing sources that a datagram has exceeded its allocated time to exist within an internet (the ICMP Time Exceeded message), and other helpful messages. All in all, ICMP is an integral part of any IP implementation, particularly those that run in routers. See the Related Information section of this document for more information on ICMP.Interior Routing ProtocolsInterior Routing Protocols (IGPs) operate within autonomous systems. The following sections provide brief descriptions of several IGPs that are currently popular in TCP/IP networks. For additional information on these protocols, please refer to the links in the Related Information section below.RIPA discussion of routing protocols within an IP environment must begin with the Routing Information Protocol (RIP). RIP was developed by Xerox Corporation in the early 1980s for use in Xerox Network Systems (XNS) networks. Today, many PC networks use routing protocols based on RIP.RIP works well in small environments but has serious limitations when used in larger internetworks. For example, RIP limits the number of router hops between any two hosts in an internet to 16. RIP is also slow to converge, meaning that it takes a relatively long time for network changes to become known to all routers. Finally, RIP determines the best path through an internet by looking only at the number of hops between the two end nodes. This technique ignores differences in line speed, line utilization, and all other metrics, many of which can be important factors in choosing the best path between two nodes. For this reason, many companies with large internetworks are migrating away from RIP to more sophisticated routing protocols.IGRPWith the creation of the Interior Gateway Routing Protocol (IGRP) in the early 1980s, Cisco Systems was the first company to solve the problems associated with using RIP to route datagrams between interior routers. IGRP determines the best path through an internet by examining the bandwidth and delay of the networks between routers. IGRP converges faster than RIP, thereby avoiding the routing loops caused by disagreement over the next routing hop to be taken. Further, IGRP does not share RIP's hop count limitation. As a result of these and other improvements over RIP, IGRP enabled many large, complex, topologically diverse internetworks to be deployed.EIGRPCisco has enhanced IGRP to handle the increasingly large, mission−critical networks being designed today. This enhanced version of IGRP is called Enhanced IGRP. Enhanced IGRP combines the ease of use of traditional distance vector routing protocols with the fast rerouting capabilities of the newer link state routing protocols.Enhanced IGRP consumes significantly less bandwidth than IGRP because it is able to limit the exchange of routing information to include only the changed information. In addition, Enhanced IGRP is capable of handling AppleTalk and Novell IPX routing information, as well as IP routing information.OSPFOSPF was developed by the Internet Engineering Task Force (IETF) as a replacement for RIP. OSPF is based on work started by John McQuillan in the late 1970s and continued by Radia Perlman and Digital Equipment Corporation (DEC) in the mid−1980s. Every major IP routing vendor supports OSPF.OSPF is an intradomain, link state, hierarchical routing protocol. OSPF supports hierarchical routing within an autonomous system. Autonomous systems can be divided into routing areas. A routing area is typically a collection of one or more subnets that are closely related. All areas must connect to the backbone area.OSPF provides fast rerouting and supports variable length subnet masks.Integrated IS−ISISO 10589 (IS−IS) is an intradomain, link state, hierarchical routing protocol used as the DECnet Phase V routing algorithm. It is similar in many ways to OSPF. IS−IS can operate over a variety of subnetworks, including broadcast LANs, WANs, and point−to−point links.Integrated IS−IS is an implementation of IS−IS for more than just OSI protocols. Today, Integrated IS−IS supports both OSI and IP protocols.Like all integrated routing protocols, Integrated IS−IS calls for all routers to run a single routing algorithm. Link state advertisements sent by routers running Integrated IS−IS include all destinations running either IP or OSI network−layer protocols. Protocols such as ARP and ICMP for IP and End System−to−Intermediate System (ES−IS) for OSI must still be supported by routers running Integrated IS−IS.Exterior Routing ProtocolsEGPs provide routing between autonomous systems. The two most popular EGPs in the TCP/IP community are discussed in this section.EGPThe first widespread exterior routing protocol was the Exterior Gateway Protocol. EGP provides dynamic connectivity but assumes that all autonomous systems are connected in a tree topology. This was true in the early Internet but is no longer true.Although EGP is a dynamic routing protocol, it uses a very simple design. It does not use metrics and therefore cannot make true intelligent routing decisions. EGP routing updates contain network reachability information. In other words, they specify that certain networks are reachable through certain routers. Because of its limitations with regard to today's complex internetworks, EGP is being phased out in favor of routing protocols such as BGP.BGPBGP represents an attempt to address the most serious of EGP's problems. Like EGP, BGP is an interdomain routing protocol created for use in the Internet core routers. Unlike EGP, BGP was designed to prevent routing loops in arbitrary topologies and to allow policy−based route selection.BGP was co−authored by a Cisco founder, and Cisco continues to be very involved in BGP development. The latest revision of BGP, BGP4, was designed to handle the scaling problems of the growing Internet.Cisco's TCP/IP ImplementationIn addition to IP and TCP, the Cisco TCP/IP implementation supports ARP, RARP, ICMP, Proxy ARP (in which the router acts as an ARP server on behalf of another device), Echo, Discard, and Probe (an address resolution protocol developed by Hewlett−Packard Company and used on IEEE 802.3 networks). Cisco routers also can be configured to use the Domain Name System (DNS) when host name−to−address mappings are needed.IP hosts need to know how to reach a router. There are several ways this can be done:•Add a static route in the host pointing to a router.•Run RIP or some other IGP on the host.Run the ICMP Router Discovery Protocol (IRDP) in the host.••Run Proxy ARP on the router.Cisco routers support all of these methods.Cisco provides many TCP/IP value−added features that enhance applications availability and reduce the total cost of internetwork ownership. The most important of these features are described in the following section.Access RestrictionsMost networks have reasonably straightforward access requirements. To address these issues, Cisco implements access lists, a scheme that prevents certain packets from entering or leaving particular networks. An access list is a sequential list of instructions to either permit or deny access through a router interface based on IP address or other criteria. For example, an access list could be created to deny access to a particular resource from all computers on one network segment but permit access from all other segments. Another access list could be used to permit TCP connections from any host on a local segment to any host in the Internet but to deny all connections from the Internet into the local net except for electronic mail connections to a particular designated mail host. Access lists are extremely flexible, powerful security measures and are available not only for IP, but for many other protocols supported by Cisco routers.Other access restrictions are provided by the Department of Defense−specified security extensions to IP. Cisco supports both the Basic and the Extended security options as described in RFC 1108 of the IP Security Option (IPSO). Support of both access lists and the IPSO makes Cisco a good choice for networks where security is an issue.TunnelingCisco's TCP/IP implementation includes several schemes that allow foreign protocols to be tunneled through an IP network. Tunneling allows network administrators to extend the size of AppleTalk and Novell IPX networks beyond the size that their native protocols can handle.IP MulticastThe applications that use the TCP/IP protocol suite continue to evolve. The next set of applications on which a lot of work is being done include those that use video and audio information. Cisco continues to be actively involved with the Internet Engineering Task Force (IETF) in defining standards that will enable network administrators to add audio and video applications to their existing networks. Cisco supports the Protocol Independent Multicast (PIM) standard. In addition, Cisco's implementation provides interoperability with theMBONE, a research multicast backbone that exists today.IP multicasting (the ability to send IP datagrams to multiple nodes in a logical group) is an important building block for applications such as video. Video teleconferencing, for example, requires the ability to send video information to multiple teleconference sites. If one IP multicast datagram containing video information can be sent to multiple teleconference sites, network bandwidth is saved and time synchronization is closer to optimal.Suppressing Network InformationIn some cases, it may be useful to suppress information about certain networks. Cisco routers provide an extensive set of configuration options that allow an administrator to tailor the exchange of routing information within a particular routing protocol. Both incoming and outgoing information can be controlled using a set of commands designed for this purpose. For example, networks can be excluded from routing advertisements, routing updates can be prevented from reaching certain networks, and other similar actions can be taken.Administrative DistanceIn large networks, some routers and routing protocols are more reliable sources of routing information than others. Cisco IP routing software permits the reliability of information sources to be quantified by the network administrator with the administrative distance metric. When administrative distance is specified, the router can select between sources of routing information based on the reliability of the source. For example, if a router uses both IGRP and RIP, one might set the administrative distances to reflect greater confidence in the IGRP information. The router would then use IGRP information when available. If the source of IGRP information failed, the router automatically would use RIP information as a backup until the IGRP source became available again.Routing Protocol RedistributionTranslation between two environments using different routing protocols requires that routes generated by one protocol be redistributed into the second routing protocol environment. Route redistribution gives a company the ability to run different routing protocols in workgroups or areas where each is particularly effective. By not restricting customers to using only a single routing protocol, Cisco's route redistribution feature minimizes cost while maximizing technical advantage through diversity.Cisco permits routing protocol redistribution between any of its supported routing protocols. Static route information can also be redistributed. Further, defaults can be assigned so that one routing protocol can use the same metric for all redistributed routes, thereby simplifying the routing redistribution mechanism. Serverless Network SupportCisco pioneered the mechanisms that allow network administrators to build serverless networks. Helper addresses, RARP, and BOOTP allow network administrators to place servers far away from the workstations that depend on them, thereby easing network design constraints.Network Monitoring and DebuggingWith today's complex, diverse network topologies, a router's ability to aid the monitoring and debugging process is critical. As the junction point for multiple segments, a router sees more of the complete network than most other devices. Many problems can be detected and/or solved using information that routinely passes through the router.The Cisco IP routing implementation provides commands that display:•The current state of the routing table, including the routing protocol that derived the route, thereliability of the source, the next IP address to send to, the router interface to use, whether the network is subnetted, whether the network in question is directly connected, and any routing metrics.•The current state of the active routing protocol process, including its update interval, metric weights (if applicable), active networks for which the routing process is functioning, and routing information sources.•The active accounting database, including the number of packets and bytes exchanged betweenparticular sources and destinations.•The contents of the IP cache, including the destination IP address, the interface through which thatdestination is reached, the encapsulation method used, and the hardware address found at thatdestination.IP−related interface parameters, including whether the interface and interface physical layer hardware are up, whether certain protocols (such as ICMP and Proxy ARP) are enabled, and the current security level.IP−related protocol statistics, including the number of packets and number of errors received and sent •by the following protocols: IP, TCP, User Datagram Protocol (UDP), EGP, IGRP, Enhanced IGRP, OSPF, IS−IS, ARP, and Probe.•Logging of all BGP, EGP, ICMP, IGRP, Enhanced IGRP, OSPF, IS−IS, RIP, TCP, and UDPtransactions.•The number of intermediate hops taken as a packet traverses the network.•Reachability information between nodes.SummaryIP is one of over 20 protocols that can be simultaneously routed and bridged by any Cisco routers. Cisco has added features to its IP implementation that optimize the performance of Cisco routers in larger,enterprise−wide internetworks.NetPro Discussion Forums − Featured ConversationsNetworking Professionals Connection is a forum for networking professionals to share questions, suggestions, and information about networking solutions, products, and technologies. The featured links are some of the most recent conversations available in this technology.NetPro Discussion Forums − Featured Conversations for RPService Providers: MPLSVirtual Private Networks: ServicesVirtual Private Networks: SecurityRelated Information•Troubleshooting TCP/IP•IP Routed Protocols Support Page•IP Routing Support Page•Technical Support − Cisco SystemsAll contents are Copyright © 1992−2005 Cisco Systems, Inc. All rights reserved. Important Notices and Privacy Statement. Updated: Jan 06, 2005Document ID: 13769。
