DES的C语言实现
DES算法的C语言实现
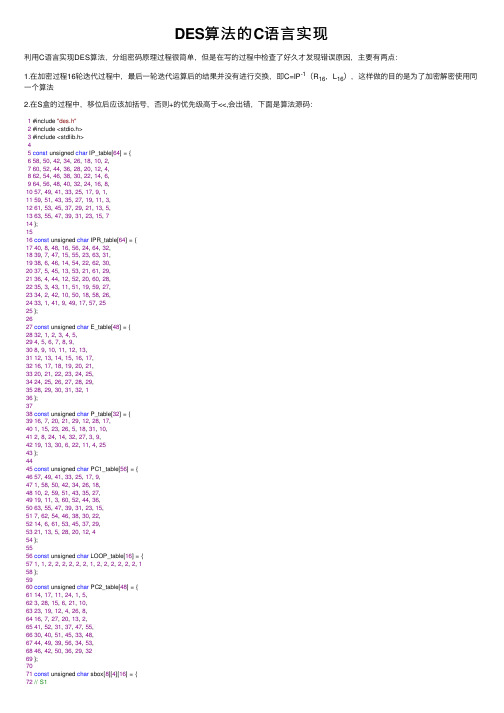
DES算法的C语⾔实现利⽤C语⾔实现DES算法,分组密码原理过程很简单,但是在写的过程中检查了好久才发现错误原因,主要有两点:1.在加密过程16轮迭代过程中,最后⼀轮迭代运算后的结果并没有进⾏交换,即C=IP-1(R16,L16),这样做的⽬的是为了加密解密使⽤同⼀个算法2.在S盒的过程中,移位后应该加括号,否则+的优先级⾼于<<,会出错,下⾯是算法源码:1 #include "des.h"2 #include <stdio.h>3 #include <stdlib.h>45const unsigned char IP_table[64] = {658, 50, 42, 34, 26, 18, 10, 2,760, 52, 44, 36, 28, 20, 12, 4,862, 54, 46, 38, 30, 22, 14, 6,964, 56, 48, 40, 32, 24, 16, 8,1057, 49, 41, 33, 25, 17, 9, 1,1159, 51, 43, 35, 27, 19, 11, 3,1261, 53, 45, 37, 29, 21, 13, 5,1363, 55, 47, 39, 31, 23, 15, 714 };1516const unsigned char IPR_table[64] = {1740, 8, 48, 16, 56, 24, 64, 32,1839, 7, 47, 15, 55, 23, 63, 31,1938, 6, 46, 14, 54, 22, 62, 30,2037, 5, 45, 13, 53, 21, 61, 29,2136, 4, 44, 12, 52, 20, 60, 28,2235, 3, 43, 11, 51, 19, 59, 27,2334, 2, 42, 10, 50, 18, 58, 26,2433, 1, 41, 9, 49, 17, 57, 2525 };2627const unsigned char E_table[48] = {2832, 1, 2, 3, 4, 5,294, 5, 6, 7, 8, 9,308, 9, 10, 11, 12, 13,3112, 13, 14, 15, 16, 17,3216, 17, 18, 19, 20, 21,3320, 21, 22, 23, 24, 25,3424, 25, 26, 27, 28, 29,3528, 29, 30, 31, 32, 136 };3738const unsigned char P_table[32] = {3916, 7, 20, 21, 29, 12, 28, 17,401, 15, 23, 26, 5, 18, 31, 10,412, 8, 24, 14, 32, 27, 3, 9,4219, 13, 30, 6, 22, 11, 4, 2543 };4445const unsigned char PC1_table[56] = {4657, 49, 41, 33, 25, 17, 9,471, 58, 50, 42, 34, 26, 18,4810, 2, 59, 51, 43, 35, 27,4919, 11, 3, 60, 52, 44, 36,5063, 55, 47, 39, 31, 23, 15,517, 62, 54, 46, 38, 30, 22,5214, 6, 61, 53, 45, 37, 29,5321, 13, 5, 28, 20, 12, 454 };5556const unsigned char LOOP_table[16] = {571, 1, 2, 2, 2, 2, 2, 2, 1, 2, 2, 2, 2, 2, 2, 158 };5960const unsigned char PC2_table[48] = {6114, 17, 11, 24, 1, 5,623, 28, 15, 6, 21, 10,6323, 19, 12, 4, 26, 8,6416, 7, 27, 20, 13, 2,6541, 52, 31, 37, 47, 55,6630, 40, 51, 45, 33, 48,6744, 49, 39, 56, 34, 53,6846, 42, 50, 36, 29, 3269 };7071const unsigned char sbox[8][4][16] = {72// S17314, 4, 13, 1, 2, 15, 11, 8, 3, 10, 6, 12, 5, 9, 0, 7,740, 15, 7, 4, 14, 2, 13, 1, 10, 6, 12, 11, 9, 5, 3, 8,754, 1, 14, 8, 13, 6, 2, 11, 15, 12, 9, 7, 3, 10, 5, 0,7615, 12, 8, 2, 4, 9, 1, 7, 5, 11, 3, 14, 10, 0, 6, 13,77//S27815, 1, 8, 14, 6, 11, 3, 4, 9, 7, 2, 13, 12, 0, 5, 10,793, 13, 4, 7, 15, 2, 8, 14, 12, 0, 1, 10, 6, 9, 11, 5,800, 14, 7, 11, 10, 4, 13, 1, 5, 8, 12, 6, 9, 3, 2, 15,8113, 8, 10, 1, 3, 15, 4, 2, 11, 6, 7, 12, 0, 5, 14, 9,82//S38310, 0, 9, 14, 6, 3, 15, 5, 1, 13, 12, 7, 11, 4, 2, 8,8413, 7, 0, 9, 3, 4, 6, 10, 2, 8, 5, 14, 12, 11, 15, 1,8513, 6, 4, 9, 8, 15, 3, 0, 11, 1, 2, 12, 5, 10, 14, 7,861, 10, 13, 0, 6, 9, 8, 7, 4, 15, 14, 3, 11, 5, 2, 12,87//S4887, 13, 14, 3, 0, 6, 9, 10, 1, 2, 8, 5, 11, 12, 4, 15,8913, 8, 11, 5, 6, 15, 0, 3, 4, 7, 2, 12, 1, 10, 14, 9,9010, 6, 9, 0, 12, 11, 7, 13, 15, 1, 3, 14, 5, 2, 8, 4,913, 15, 0, 6, 10, 1, 13, 8, 9, 4, 5, 11, 12, 7, 2, 14,92//S5932, 12, 4, 1, 7, 10, 11, 6, 8, 5, 3, 15, 13, 0, 14, 9,9414, 11, 2, 12, 4, 7, 13, 1, 5, 0, 15, 10, 3, 9, 8, 6,954, 2, 1, 11, 10, 13, 7, 8, 15, 9, 12, 5, 6, 3, 0, 14,9611, 8, 12, 7, 1, 14, 2, 13, 6, 15, 0, 9, 10, 4, 5, 3,97//S69812, 1, 10, 15, 9, 2, 6, 8, 0, 13, 3, 4, 14, 7, 5, 11,9910, 15, 4, 2, 7, 12, 9, 5, 6, 1, 13, 14, 0, 11, 3, 8,1009, 14, 15, 5, 2, 8, 12, 3, 7, 0, 4, 10, 1, 13, 11, 6,1014, 3, 2, 12, 9, 5, 15, 10, 11, 14, 1, 7, 6, 0, 8, 13,102//S71034, 11, 2, 14, 15, 0, 8, 13, 3, 12, 9, 7, 5, 10, 6, 1,10413, 0, 11, 7, 4, 9, 1, 10, 14, 3, 5, 12, 2, 15, 8, 6,1051, 4, 11, 13, 12, 3, 7, 14, 10, 15, 6, 8, 0, 5, 9, 2,1066, 11, 13, 8, 1, 4, 10, 7, 9, 5, 0, 15, 14, 2, 3, 12,107//S810813, 2, 8, 4, 6, 15, 11, 1, 10, 9, 3, 14, 5, 0, 12, 7,1091, 15, 13, 8, 10, 3, 7, 4, 12, 5, 6, 11, 0, 14, 9, 2,1107, 11, 4, 1, 9, 12, 14, 2, 0, 6, 10, 13, 15, 3, 5, 8,1112, 1, 14, 7, 4, 10, 8, 13, 15, 12, 9, 0, 3, 5, 6, 11112 };113114void ByteToBit(unsigned char* out, const unsigned char* in, const int bits){115for(int i=0;i<bits;i++)116out[i]=(in[i/8]>>(7-i%8))&1;117 }118119void BitToByte(unsigned char* out, const unsigned char* in, const int bits){120 memset(out, 0, (bits + 7) / 8);121for(int i=0;i<bits;i++)122out[i/8]|=in[i]<<(7-i%8);123 }124125void Transform(unsigned char* out,const unsigned char* in, const unsigned char* table, const int len){ 126 unsigned char tmp[64] = {0};127for (int i = 0; i < len; i++)128 tmp[i] = in[table[i] - 1];129 memcpy(out, tmp, len);130 }131132void RotateL(unsigned char* in, const int len, int loop){133static unsigned char tmp[64];134 memcpy(tmp, in, len);135 memcpy(in, in + loop, len - loop);136 memcpy(in + len - loop, tmp, loop);137 }138139static unsigned char subKey[16][48] = { 0 };140void setKey(const unsigned char* in){141char key[64] = { 0 };142 ByteToBit(key, in, 64);143char temp[56]={0};144 Transform(temp, key, PC1_table, 56);145for(int i=0;i<16;i++){146 RotateL(temp, 28, LOOP_table[i]);147 RotateL(temp + 28, 28, LOOP_table[i]);148 Transform(subKey[i], temp, PC2_table, 48);149 }150 }151152void xor(unsigned char* in1,const unsigned char* in2,int len){153for(int i=0;i<len;i++)154 in1[i]^=in2[i];155 }156157void sbox_exchange(unsigned char* out,const unsigned char* in){158char row, column;159for (int i = 0; i < 8; i++){160char num = 0;161 row = (in[6 * i]<<1)+ in[6 * i + 5];162 column = (in[6 * i + 1] << 3) + (in[6 * i + 2] << 2) + (in[6 * i + 3] << 1) + in[6 * i + 4]; 163 num = sbox[i][row][column];164for (int j = 0; j < 4; j++)165 {166out[4 * i + j] = (num >> (3 - j)) & 1;167 }168 }169 }170171void F_func(unsigned char* out,const unsigned char* in,unsigned char* subKey){172 unsigned char temp[48]={0};173 unsigned char res[32]={0};174 Transform(temp, in, E_table, 48);175 xor(temp,subKey,48);176 sbox_exchange(res,temp);177 Transform(out, res, P_table, 32);178 }179180void encryptDES(unsigned char* out,const unsigned char* in, const unsigned char* key){ 181 unsigned char input[64] = { 0 };182 unsigned char output[64] = { 0 };183 unsigned char tmp[64] = { 0 };184 ByteToBit(input, in, 64);185 Transform(tmp, input, IP_table, 64);186char* Li = &tmp[0], *Ri = &tmp[32];187 setKey(key);188for(int i=0;i<16;i++){189char temp[32]={0};190 memcpy(temp,Ri,32);191 F_func(Ri, Ri,subKey[i]);192 xor(Ri, Li, 32);193 memcpy(Li,temp,32);194 }195 RotateL(tmp, 64, 32);//the input is LR,output is RL196 Transform(output, tmp, IPR_table, 64);197 BitToByte(out, output,64);198 }199200void decryptDES(unsigned char* out,const unsigned char* in, const unsigned char* key){ 201 unsigned char input[64] = { 0 };202 unsigned char output[64] = { 0 };203 unsigned char tmp[64] = { 0 };204 ByteToBit(input, in, 64);205 Transform(tmp, input, IP_table, 64);206char* Li = &tmp[0], *Ri = &tmp[32];207 setKey(key);208 RotateL(tmp, 64, 32);209for (int i = 0; i < 16; i++){210char temp[32] = { 0 };211 memcpy(temp, Li, 32);212 F_func(Li, Li,subKey[15 - i]);213 xor(Li, Ri, 32);214 memcpy(Ri, temp, 32);215 }216 Transform(output, tmp, IPR_table, 64);217 BitToByte(out, output, 64);218 }。
用c语言实现des算法

用c语言实现des算法由于DES算法被广泛应用于加密和数据安全方面,因此在计算机科学领域,了解和实现DES算法是非常重要的。
C语言是一种强大的编程语言,其通用性和高效性使其成为实现DES算法的理想选择。
以下是使用C语言实现DES算法的步骤和方法:1.将明文和密钥转换为二进制格式在DES算法中,明文和密钥必须先转换为二进制格式才能进行加密或解密操作。
可以使用一个字符串数组来存储明文和密钥,然后使用C 语言的位运算符将每个字符转换为二进制格式。
2.对明文进行初始置换DES算法的第一步是对明文进行初始置换。
可以使用一个int型数据来存储初始置换后的结果。
3.密钥生成使用密钥生成算法来生成16个48位的子密钥。
可以使用一个二维数组来存储每个子密钥。
4.将初始置换后的明文分为左右两个部分将初始置换后的明文分为左右两个部分,每个部分32位。
5.进行16轮迭代在每轮迭代中,右半部分32位的明文和48位的子密钥进行异或运算,然后使用S盒置换和P盒置换来处理数据。
最后将结果与左半部分32位的明文异或,以更新下一轮迭代所需的数据。
6.合并左右两个部分在进行最后一轮迭代后,将左右两个部分合并成一段64位的二进制数据。
7.进行最后的逆置换使用逆置换来处理上一步生成的64位二进制数据,以生成最终的密文。
实现DES算法需要一定的数学知识和编程技能,因此建议有一定编程基础的人才尝试实现此算法。
列表:1.使用C语言实现DES算法步骤2.将明文和密钥转换为二进制格式的方法3.对明文进行初始置换的具体过程4.密钥生成算法的原理和实现方法5.如何将初始置换后的明文分为左右两个部分6.DES算法16轮迭代的详细过程7.如何合并左右两个部分的数据8.DES算法中的最后一步逆置换的作用和过程9.DES算法的应用场景和重要性10.如何使用C语言实现DES算法的具体步骤和技巧。
DES加密算法的C语言实现

57, 49, 41, 33, 25, 17, 9, 1, 58, 50, 42, 34, 26, 18, 10, 2, 59, 51, 43, 35, 27, 19, 11, 3, 60, 52, 44, 36, 63, 55, 47, 39, 31, 23, 15, 7, 62, 54, 46, 38, 30, 22, 14, 6, 61, 53, 45, 37, 29, 21, 13, 5, 28, 20, 12, 4 };
4, 5, 6, 7, 8, 9, 8, 9, 10, 11, 12, 13, 12, 13, 14, 15, 16, 17, 16, 17, 18, 19, 20, 21, 20, 21, 22, 23, 24, 25, 24, 25, 26, 27, 28, 29, 28, 29, 30, 31, 32, 1 };
FILE *input = fopen( argv[1], "r"); if(ferror( input ))
return 0 ; //创建文件 用于输出密文 FILE *encyption = fopen(argv[2],"w"); if(ferror( encyption ))
return 0 ; //创建文件 用于输出解密后的明文 FILE *decyption = fopen(argv[3],"w"); if(ferror( decyption ))
};
//S-盒置换 unsigned char S_Box[8][64] = {
/* S1 */
Generated by Foxit PDF Creator © Foxit Software For evaluation only.
DES对称加密算法详解和c++代码实现(带样例和详细的中间数据)

DES对称加密算法详解和c++代码实现(带样例和详细的中间数据)特点:1.DES是对称性加密算法,即加密和解密是对称的,⽤的是同⼀个密钥2.DES只处理⼆进制数据,所以需要将明⽂转换成为2进制数据3.DES每次处理64位的数据,所以应该将明⽂切割成64位的分组,当最后⼀组数据不⾜64位的时候,⾼位补04.DES使⽤64位的密钥,但因为密钥中的每8位会被忽略,所以有效的密钥长度是56位,从⽽产⽣16个48位的⼦密钥(变换过程后⾯会说明)5.每64位数据⼀个块,是DES的永恒组织⽅式具体样例分析:(仅以⼀组64位数据为例分析加密过程)明⽂M是:8787878787878787密钥K是:0E329232EA6D0D73上⾯的信息都是16进制的,转换为2进制明⽂M是:0000 0001 0010 0011 0100 0101 0110 0111 1000 1001 1010 1011 1100 1101 1110 1111密钥K是:00010011 00110100 01010111 01111001 10011011 10111100 11011111 11110001第⼀步:根据密钥⽣成16个⼦密钥1.根据密钥初始置换表将64位的密钥转化为58位的密钥57 49 41 33 25 17 91 58 50 42 34 26 1810 2 59 51 43 35 2719 11 3 60 52 44 3663 55 47 39 31 23 157 62 54 46 38 30 2214 6 61 53 45 37 2921 13 5 28 20 12 4由于上表中第⼀个元素为57,这将使原秘钥的第57位变换为新秘钥K+的第1位。
同理,原秘钥的第49位变换为新秘钥的第2位……原秘钥的第4位变换为新秘钥的最后⼀位。
注意原秘钥中只有56位会进⼊新秘钥,上表也只有56个元素。
原密钥K:00010011 00110100 01010111 01111001 10011011 10111100 11011111 11110001新密钥K:1111000 0110011 0010101 0101111 0101010 1011001 1001111 00011112.将新密钥拆分成C0和D0,每组都有28位⽐如新密钥C0:1111000 0110011 0010101 0101111D0:0101010 1011001 1001111 00011113.根据密钥轮次左移表,左移特定的位数1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 161 12 2 2 2 2 2 1 2 2 2 2 2 2 1⽐如第⼀轮是左移1位,第⼆轮也是左移1位,第三轮是左移两位所以C1:1110000110011001010101011111D1:1010101011001100111100011110下⾯给出C1,D1到C16,D16的数据:C1 = 1110000110011001010101011111D1 = 1010101011001100111100011110C2 = 1100001100110010101010111111D2 = 0101010110011001111000111101C3 = 0000110011001010101011111111D3 = 0101011001100111100011110101C4 = 0011001100101010101111111100D4 = 0101100110011110001111010101C5 = 1100110010101010111111110000D5 = 0110011001111000111101010101C6 = 0011001010101011111111000011D6 = 1001100111100011110101010101C7 = 1100101010101111111100001100D7 = 0110011110001111010101010110C8 = 0010101010111111110000110011D8 = 1001111000111101010101011001C9 = 0101010101111111100001100110D9 = 0011110001111010101010110011C10 = 0101010111111110000110011001D10 = 1111000111101010101011001100C11 = 0101011111111000011001100101D11 = 1100011110101010101100110011C12 = 0101111111100001100110010101D12 = 0001111010101010110011001111C13 = 0111111110000110011001010101D13 = 0111101010101011001100111100C14 = 1111111000011001100101010101D14 = 1110101010101100110011110001C15 = 1111100001100110010101010111D15 = 1010101010110011001111000111C16 = 1111000011001100101010101111D16 = 0101010101100110011110001111需要记住的是:每⼀对Cn 和 Dn都是由前⼀对Cn-1 和 Dn-1移位⽽来!4.得到Cn,Dn后合并CnDn,然后根据密钥压缩置换表将56位密钥压缩成48位的⼦密钥密钥压缩置换表:14 17 11 24 1 53 28 15 6 21 1023 19 12 4 26 816 7 27 20 13 241 52 31 37 47 5530 40 51 45 33 4844 49 39 56 34 5346 42 50 36 29 32每对⼦秘钥有56位,但PC-2仅仅使⽤其中的48位。
C语言加密与解密算法

C语言加密与解密算法在计算机科学与信息安全领域,加密与解密算法起着至关重要的作用。
加密算法用于将原始数据转换为不可读的密文,而解密算法则用于将密文还原为可读的原始数据。
C语言是一种常用的编程语言,具备高效性和灵活性,适用于加密与解密算法的开发。
本文将介绍几种常用的C语言加密与解密算法。
一、凯撒密码算法凯撒密码算法是一种最简单的替换加密算法,通过将字母按照固定的偏移量进行替换来实现加密与解密。
以下是一个简单的C语言凯撒密码实现例子:```c#include <stdio.h>void caesarEncrypt(char* message, int key) {int i = 0;while (message[i] != '\0') {if (message[i] >= 'a' && message[i] <= 'z') {message[i] = (message[i] - 'a' + key) % 26 + 'a';} else if (message[i] >= 'A' && message[i] <= 'Z') {message[i] = (message[i] - 'A' + key) % 26 + 'A';}i++;}}void caesarDecrypt(char* message, int key) {int i = 0;while (message[i] != '\0') {if (message[i] >= 'a' && message[i] <= 'z') {message[i] = (message[i] - 'a' - key + 26) % 26 + 'a'; } else if (message[i] >= 'A' && message[i] <= 'Z') {message[i] = (message[i] - 'A' - key + 26) % 26 + 'A'; }i++;}}int main() {char message[] = "Hello, World!";int key = 3;printf("Original message: %s\n", message);caesarEncrypt(message, key);printf("Encrypted message: %s\n", message);caesarDecrypt(message, key);printf("Decrypted message: %s\n", message);return 0;}```以上程序演示了凯撒密码的加密与解密过程,通过指定偏移量实现对消息的加密与解密。
C语言实现CBC模式DES加密

C语⾔实现CBC模式DES加密#define SECTION_SIZE 8 //每段密⽂字节数,DES为8个字节64位#define GET_BIT(x,y) (x |((BYTE)0xff <<9-y) | ((BYTE)0xff >>y)) //将X的第Y位保留,其余位置1#define FORM_DWORD(p1,p2,p3,p4) ((((DWORD)p1) <<24) | (((DWORD)p2) <<16) | (((DWORD)p3) <<8) | ((DWORD)p4)) //四个字节形成⼀个双字#define FORM_BYTE(x,y) ((BYTE)((x & ((DWORD)0xffffffff << 8*(4-y)) & ((DWORD)0xffffffff >> (y-1)*8)) >>(4-y)*8))//将双字X的第Y个字节提取出来#define GET_BIT_LOW(x,y) ((x & ( (BYTE)0xff<<(8-y)) & (BYTE)0xff >> (y-1)) >> (8-y)) //拿到字节X的第Y位//#define ENCRPT //如果定义则为加密,⽆定义为解密#define CHANGE //未⽤//------------------------------------------------------------------------------------------BYTE DisPlaceIPTable[] = { 58, 50, 42, 34, 26, 18, 10, 2, 60, 52, 44, 36, 28, 20, 12, 4,62, 54, 46, 38, 30, 22, 14, 6, 64, 56, 48, 40, 32, 24, 16, 8,57, 49, 41, 33, 25, 17, 9, 1, 59, 51, 43, 35, 27, 19, 11, 3,61, 53, 45, 37, 29, 21, 13, 5, 63, 55, 47, 39, 31, 23, 15, 7};BYTE DisPlaceRIPTable[] = { 40, 8, 48, 16, 56, 24, 64, 32, 39, 7, 47, 15, 55, 23, 63, 31,38, 6, 46, 14, 54, 22, 62, 30, 37, 5, 45, 13, 53, 21, 61, 29,36, 4, 44, 12, 52, 20, 60, 28, 35, 3, 43, 11, 51, 19, 59, 27,34, 2, 42, 10, 50, 18, 58, 26, 33, 1, 41, 9, 49, 17, 57, 25};BYTE DisPlaceKEYTable[] = { 57, 49, 41, 33, 25, 17, 9, 1, 58, 50, 42, 34, 26, 18, 10, 2, 59, 51, 43, 35, 27, 19, 11, 3, 60, 52, 44, 36,63, 55, 47, 39, 31, 23, 15, 7, 62, 54, 46, 38, 30, 22, 14, 6, 61, 53, 45, 37, 29, 21, 13, 5, 28, 20, 12, 4, };BYTE MoveCount[] = { 1, 1, 2, 2, 2, 2, 2, 2, 1, 2, 2, 2, 2, 2, 2, 1 };BYTE PC_2[] = { 14, 17, 11, 24, 1, 5, 3, 28, 15, 6, 21, 10, 23, 19, 12, 4, 26, 8, 16, 7, 27, 20, 13, 2,41, 52, 31, 37, 47, 55, 30, 40, 51, 45, 33, 48, 44, 49, 39, 56, 34, 53, 46, 42, 50, 36, 29, 32 };BYTE E_Table[] = { 32, 1, 2, 3, 4, 5,4, 5, 6, 7, 8, 9,8, 9, 10, 11, 12, 13,12, 13, 14, 15, 16, 17,16, 17, 18, 19, 20, 21,20, 21, 22, 23, 24, 25,24, 25, 26, 27, 28, 29,28, 29, 30, 31, 32, 1 };BYTE S1[4][16] = { 14, 4, 13, 1, 2, 15, 11, 8, 3, 10, 6, 12, 5, 9, 0, 7,0, 15, 7, 4, 14, 2, 13, 1, 10, 6, 12, 11, 9, 5, 3, 8,4, 1, 14, 8, 13, 6, 2, 11, 15, 12, 9, 7, 3, 10, 5, 0,15, 12, 8, 2, 4, 9, 1, 7, 5, 11, 3, 14, 10, 0, 6, 13};BYTE S2[4][16] = { 15, 1, 8, 14, 6, 11, 3, 4, 9, 7, 2, 13, 12, 0, 5, 10,3, 13, 4, 7, 15, 2, 8, 14, 12, 0, 1, 10, 6, 9, 11, 5,0, 14, 7, 11, 10, 4, 13, 1, 5, 8, 12, 6, 9, 3, 2, 15,13, 8, 10, 1, 3, 15, 4, 2, 11, 6, 7, 12, 0, 5, 14, 9 };BYTE S3[4][16] = { 10, 0, 9, 14, 6, 3, 15, 5, 1, 13, 12, 7, 11, 4, 2, 8,13, 7, 0, 9, 3, 4, 6, 10, 2, 8, 5, 14, 12, 11, 15, 1,13, 6, 4, 9, 8, 15, 3, 0, 11, 1, 2, 12, 5, 10, 14, 7,1, 10, 13, 0, 6, 9, 8, 7, 4, 15, 14, 3, 11, 5, 2, 12 };BYTE S4[4][16] = { 7, 13, 14, 3, 0, 6, 9, 10, 1, 2, 8, 5, 11, 12, 4, 15,13, 8, 11, 5, 6, 15, 0, 3, 4, 7, 2, 12, 1, 10, 14, 9,10, 6, 9, 0, 12, 11, 7, 13, 15, 1, 3, 14, 5, 2, 8, 4,3, 15, 0, 6, 10, 1, 13, 8, 9, 4, 5, 11, 12, 7, 2, 14 };BYTE S5[4][16] = { 2, 12, 4, 1, 7, 10, 11, 6, 8, 5, 3, 15, 13, 0, 14, 9,14, 11, 2, 12, 4, 7, 13, 1, 5, 0, 15, 10, 3, 9, 8, 6,4, 2, 1, 11, 10, 13, 7, 8, 15, 9, 12, 5, 6, 3, 0, 14,11, 8, 12, 7, 1, 14, 2, 13, 6, 15, 0, 9, 10, 4, 5, 3 };BYTE S6[4][16] = { 12, 1, 10, 15, 9, 2, 6, 8, 0, 13, 3, 4, 14, 7, 5, 11,10, 15, 4, 2, 7, 12, 9, 5, 6, 1, 13, 14, 0, 11, 3, 8,9, 14, 15, 5, 2, 8, 12, 3, 7, 0, 4, 10, 1, 13, 11, 6,4, 3, 2, 12, 9, 5, 15, 10, 11, 14, 1, 7, 6, 0, 8, 13 };BYTE S7[4][16] = { 4, 11, 2, 14, 15, 0, 8, 13, 3, 12, 9, 7, 5, 10, 6, 1,13, 0, 11, 7, 4, 9, 1, 10, 14, 3, 5, 12, 2, 15, 8, 6,1, 4, 11, 13, 12, 3, 7, 14, 10, 15, 6, 8, 0, 5, 9, 2,6, 11, 13, 8, 1, 4, 10, 7, 9, 5, 0, 15, 14, 2, 3, 12 };BYTE S8[4][16] = { 13, 2, 8, 4, 6, 15, 11, 1, 10, 9, 3, 14, 5, 0, 12, 7,1, 15, 13, 8, 10, 3, 7, 4, 12, 5, 6, 11, 0, 14, 9, 2,7, 11, 4, 1, 9, 12, 14, 2, 0, 6, 10, 13, 15, 3, 5, 8,2, 1, 14, 7, 4, 10, 8, 13, 15, 12, 9, 0, 3, 5, 6, 11 };BYTE result[] = { 16, 7, 20, 21, 29, 12, 28, 17, 1, 15, 23, 26, 5, 18, 31, 10,2, 8, 24, 14, 32, 27, 3, 9, 19, 13, 30, 6, 22, 11, 4, 25 };//---------------------------------------------------------------------------------typedef struct _BIT{BYTE a : 1;BYTE b : 1;BYTE c : 1;BYTE d : 1;BYTE e : 1;BYTE f : 1;}BIT,*PBIT;typedef struct _8_BIT{BYTE a : 1;BYTE b : 1;BYTE c : 1;BYTE d : 1;BYTE e : 1;BYTE f : 1;BYTE g : 1;BYTE h : 1;}E_BIT,*P4_BIT;LPVOID getTable(int index);DWORD data_rl(DWORD x, BYTE y, BYTE z);PBYTE SHL_Connect(PBYTE p1, PBYTE p2, int index);void ExchangeDword(PVOID p1, PVOID p2);void DisPlaceItem(PVOID fileVa, PBYTE KEY, int length);// DESEncryption.cpp : Defines the entry point for the console application.//#include "stdafx.h"#include "windows.h"#include "myEncpy.h"int _tmain(int argc, _TCHAR* argv[]){//get plaintextHANDLE hFile = CreateFile(L"d:\\a.txt", GENERIC_ALL, FILE_SHARE_READ, 0, OPEN_EXISTING, FILE_ATTRIBUTE_READONLY, NULL); if (hFile == INVALID_HANDLE_VALUE){printf_s("can not create file... d:a.txt");system("pause");return0;}HANDLE hFileMapping = CreateFileMapping(hFile, 0, PAGE_READWRITE, 0, 0, L"myshare");if (hFileMapping == INVALID_HANDLE_VALUE){printf_s("can not create filemapping");system("pause");return0;}LPVOID fileVa = MapViewOfFile(hFileMapping, FILE_MAP_ALL_ACCESS, 0, 0, 0);if (fileVa == NULL){printf_s("can not get mapview");system("pause");return0;}//printf_s("%s\n", fileVa);//使⽤内存映射打开⼤⽂件//---------------------------------------------------------------//get parameter,key,subkeyBYTE KEY[8] = { 'a', 'b', 'c', 'd', 'e', 'f', 'g', 'h' }; //定义密钥DisPlaceItem(KEY, DisPlaceKEYTable,7);PBYTE SubKey[16];BYTE C0[4] = { KEY[0], KEY[1], KEY[2], KEY[3]&0xf0 };BYTE D0[4] = { KEY[3] & 0x0f, KEY[4], KEY[5], KEY[6] };for (int i = 0; i < 16; i++){PBYTE p = SHL_Connect(C0, D0, i);DisPlaceItem(p, PC_2, 6);SubKey[i] = p; //⽣成16个⼦密钥}//-----------------// begain encrypBYTE CBC_IV[] = { 0x11, 0x32, 0x43, 0x54, 0x65, 0x76, 0x87, 0xa8 };//初始化向量未向PBYTE fileOffset =(PBYTE)fileVa; //明⽂起始位置DWORD fileSize = GetFileSize(hFile, 0); //得到明⽂⼤⼩for (DWORD index = 0; index < fileSize / SECTION_SIZE ; index ++) //⽬前只针对凑满8个字节的部分进⾏加密{fileOffset = fileOffset + index *SECTION_SIZE;//for (int i = 0; i < SECTION_SIZE; i++)//{// *(fileOffset + i) ^= CBC_IV[i];//}#ifdef CHANGEDisPlaceItem(fileOffset, DisPlaceIPTable, 8); //IP置换#endif#ifdef ENCRPTfor (int j =0; j <16; j++)#elsefor (int j = 15; j >= 0; j--){#endifBYTE L0[4], R0[6];memcpy(L0, fileOffset, 4);memcpy(R0, fileOffset + 4, 4); //分别拿到左边右边4个字节#ifdef ENCRPTif (j !=15)#elseif (j != 0)#endifmemcpy(fileOffset, R0, 4); //如果不是最后⼀次加密或者解密,则右边直接写回左边elsememcpy(fileOffset + 4, R0, 4);DisPlaceItem(R0, E_Table, 6); //扩展置换PBYTE pbyte1 = SubKey[j];for (int i = 0; i < 6; i++){R0[i] ^= pbyte1[i]; //与右边进⾏异或}//partion----------------------------------------BIT mybit[8] = {0};///////////////////////BYTE t[48]; //把6字节分为6位⼀组共8组int tIndex = 1;int rIdex = 0;for (int i = 0; i < 48; i++){BYTE a = R0[rIdex];t[i] = GET_BIT_LOW(R0[rIdex], tIndex);if (tIndex % 8 == 0){rIdex++;tIndex = 1;}else{tIndex++;}}tIndex = 0;for (int i = 0; i < 48; i+=6){mybit[tIndex].a = t[i];mybit[tIndex].b = t[i+1];mybit[tIndex].c = t[i+2];mybit[tIndex].d = t[i+3];mybit[tIndex].e = t[i+4];mybit[tIndex].f = t[i+5];tIndex++;}//此时mybit⾥⾯放着分组之后的每⼀位////////////////////////BYTE Str[4];int EIndex = 0;BYTE(*tempTable)[16] = 0;for (char i = 0; i < 8; i += 2) //根据mybit拿到表中的数并组合成str{tempTable = (BYTE(*)[16])getTable(i + 1);BYTE sum1 = tempTable[mybit[i].a*2 + mybit[i].f][mybit[i].b*8 + mybit[i].c*4 + mybit[i].d*2 + mybit[i].e];tempTable = (BYTE(*)[16])getTable(i + 2);BYTE sum2 = tempTable[mybit[i + 1].a*2 + mybit[i + 1].f][mybit[i + 1].b*8 + mybit[i + 1].c*4 + mybit[i + 1].d*2 + mybit[i + 1].e]; BYTE sum = sum1 << 4 | sum2;memcpy(Str + EIndex, &sum, 1);EIndex++;}#ifdef CHANGEDisPlaceItem(Str, result, 4); //结果与左边置换#endiffor (int i = 0; i < 4; i++){L0[i] ^= Str[i];}#ifdef ENCRPTif (j != 15)#elseif (j != 0) //将左边写到右边#endifmemcpy(fileOffset + 4, L0, 4);elsememcpy(fileOffset, L0, 4);}#ifdef CHANGEDisPlaceItem(fileOffset, DisPlaceRIPTable, 8);//IP逆置换#endif//memcpy(CBC_IV, fileOffset, 8);//-----------------------------------------------}printf_s("got it");for (int i = 0; i < 16; i++){free(SubKey[i]);}CloseHandle(hFile);CloseHandle(hFileMapping);UnmapViewOfFile(fileVa);system("pause");return0;}void DisPlaceItem(PVOID fileVa,PBYTE KEY,int length) //fileva为需要置换的内容⾸地址 key为置换表,length为输出字节数{PBYTE File = (PBYTE)fileVa;BYTE Result[8] ;memset(Result, 0xff, 8);int DisIndex = 1;for (int i = 0; i < length; i++){int bitofEach = 1;while (true){BYTE temp1 = KEY[DisIndex-1];BYTE ByteIndex = temp1 / 8;ByteIndex = temp1 % 8 == 0 ? ByteIndex -1 : ByteIndex;BYTE BitIndex = temp1- ByteIndex*8;BYTE temptemp = *(File + ByteIndex);if (bitofEach < BitIndex){temptemp = *(File + ByteIndex) << (BitIndex - bitofEach);}else if (bitofEach>BitIndex){temptemp = *(File + ByteIndex) >> (bitofEach - BitIndex);}BYTE t = GET_BIT(temptemp, bitofEach);Result[i] = Result[i] & GET_BIT(temptemp, bitofEach);if (DisIndex % 8 == 0)break;DisIndex++;bitofEach++;}DisIndex++;}memcpy(fileVa, Result, length);}PBYTE SHL_Connect(PBYTE p1, PBYTE p2, int index) //循环移位并连接{PBYTE pbyte = (PBYTE)malloc(7);DWORD d1 = FORM_DWORD(p1[0], p1[1], p1[2], p1[3]);DWORD d2 = FORM_DWORD(p2[0], p2[1], p2[2], p2[3]) <<4;d1 = data_rl(d1, MoveCount[index], 32);d2 = data_rl(d2, MoveCount[index], 32) >>4;for (int i = 0; i < 4; i++){*(p1 + i) = FORM_BYTE(d1, i + 1);*(p2 + i) = FORM_BYTE(d2, i + 1);}memcpy(pbyte, p1, 3);BYTE temp = p1[3] | p2[0];*(pbyte + 3) = temp;memcpy(pbyte + 4, p2, 3);return pbyte;}DWORD data_rl(DWORD x, BYTE y, BYTE z) //移位的实现{DWORD temp;temp = x >> (y - z );temp = temp << 4;x = x << z;x = x | temp;return x;}LPVOID getTable(int index) {switch (index){case1:return S1;break;case2:return S2;break;case3:return S3;break;case4:return S4;break;case5:return S5;break;case6:return S6;break;case7:return S7;break;case8:return S8;break;default:break;}}。
DES算法源代码

A[i]=A[i+2];
A[26]=n;
A[27]=m;
n=B[0];
m=B[1];
for(i=0;i<26;i++)
B[i]=B[i+2];
B[26]=n;
B[27]=m;
}
for(i=0;i<28;i++) //将A和B合并成56位
{
keyAB[i]=A[i];
}
getchar();
//生成子密钥
printf("请输入8位密钥:\n");
gets(InputKey);
while(InputKey[7]=='\0'||InputKey[8]!='\0')
{
printf("您输入的密钥位数有误,请重新输入8位密钥:\n");
gets(InputKey);
}
for(i=0;i<8;i++) //将密钥转化成64位二进制数放到一维数组key中
14, 17, 11, 24, 1, 5,
3, 28, 15, 6, 21, 10,
23, 19, 12, 4, 26, 8,
16, 7, 27, 20, 13, 2,
41, 52, 31, 37, 47, 55,
30, 40, 51, 45, 33, 48,
44, 49, 39, 56, 34, 53,
{
if(move[t]==1) //按照循环移位表将Ai和Bi分别左移move[t]位
{
n=A[0];
for(i=0;i<27;i++)
DES算法的C语言实现

DES算法的程序实现说明:在VC++6.0中新建基于控制台的Win32应用程序,程序清单如下:#iinclude “memory.h”#include “stdio.h”Enum {ENCRYPT,DECRYPT}Void Des_Run(char Out[8],char In[8],bool Type=ENCRYPT); //设置密钥Void Des_SetKey(const char Key[8]);Static void F_func(bool In[32],const bool Ki[48]); //f函数Static void s_func(bool Out[32],const bool In[48]); //S盒代替Static void Transform(bool *out,bool *In,const char *Table,int len); //变换Static void Xor(bool *InA,const bool *InB,int len); //异或Static void RotateL(bool *In,int len,int loop);//循环左移//字节组转换成位组Static void ByteToBit(bool *out,const char *In,int bits);//位组转换成字节组Static void BitToByte(char *Out,const bool *In,int bits);//置换IP表Const static char IP_Table[64]={58,50,42,34,26,18,10,2,60,52,44,36,28,20,12,4,62,54,46,38,30,22,14,6,64,56,48,40,32,24,16,8,57,49,41,33,25,17,9,1,59,51,.43,35,27,19,11,3,61,53,45,37,29,21,13,5,63,55,47,39,31,23,15,7};//逆置换IP-1表Const static char IPR_Table[64]={40,8,48,16,56,24,64,32,39,7,47,15,55,3138,6,46,14,54,22,62,30,37,5,45,13,53,21,61,2936,4,44,12,52,20,60,28,35,3,43,11,51,19,59,2734,2,42,10,50,18,58,26,23,1,41,9,49,17,57,25};//逆置换IP-1表Const static char IPR_Table[64]={40,8,48,16,56,24,64,32,39,7,47,15,55,23,63,31;38,6,46,14,54,22,62,30,37,5,45,13,53,21,61,29;36,4,44,12,52,20,60,28,35,3,43,11,51,19,59,27,34,2,42,10,50,18,58,26,33,1,41,9,49,17,57,25};//E位选择表Static const char E_Table[48]={32,1,2,3,4,5,6,7,8,9,8,9,10,11,12,13,14,15,16,17,16,17,18,19,20,21,22,23,24,25,24,25,26,27,28,29,30,31,32,1};//P换位表Const static char P_Table[32]={Const static char P_Table[32]={16,7,20,21,29,12,28,17,1,15,23,26,5,18,31,10, 2,8,24,14,32,27,3,9,19,13,30,6,22,11,4,25 };//PC1选位表Const static char PC1_Table[56]={57,49,41,33,25,17,9,1,58,50,42,34,26,18, 10,2,59,51,43,35,27,19,11,3,60,52,44,36, 63,55,47,39,31,23,15,7,62,54,46,38,30,22, 14,6,61,53,45,37,29,21,13,5,28,20,12,4};//PC2选位表Const static char PC2_Table[48]={14,17,11,24,1,5,3,28,15,6,21,10,23,19,12,4,26,8,16,7,27,20,13,2,41,52,31,37,47,55,30,40,51,34,33,48,44,49,39,56,34,53,46,42,50,36,29,32};//左移位数表Const static char LOOP_Table[16]={1,1,2,2,2,2,2,2,1,2,2,2,2,2,2,1};//S盒Const static char S_Box[8][4][16]={//S114,4,13,1,2,15,11,8,3,10,6,12,5,9,0,7,0,15,7,4,14,2,13,1,10,6,12,11,9,5,3,8,4,1,14,8,13,6,2,11,15,12,9,7,3,10,5,0,15,12,8,2,4,9,1,7,5,11,3,14,10,0,6,13,//S215,1,8,14,6,11,3,4,9,7,2,13,12,0,5,10,3,13,4,7,15,2,8,14,12,0,1,10,6,9,11,5,0,14,7,11,10,4,13,1,5,8,12,6,9,3,2,15,13,8,10,1,3,15,4,2,11,6,7,12,0,5,14,9,//S310,0,9,14,6,3,15,5,1,13,12,7,11,4,2,8,13,7,0,9,3,4,6,10,2,8,5,14,12,11,15,1,13,6,4,9,8,15,3,0,11,1,2,12,5,10,14,7,1,10,13,0,6,9,8,7,4,15,14,3,11,5,2,12,//S47,13,14,3,0,6,9,10,1,2,8,5,11,12,4,15,13,8,11,5,6,15,0,3,4,7,2,12,1,10,14,9,10,6,9,0,12,11,7,13,15,1,3,14,5,2,8,4,3,15,0,6,10,1,13,8,9,4,5,11,12,7,2,14,//S52,12,4,1,7,10,6,8,5,3,15,13,0,14,9,14,11,2,12,4,7,13,1,5,0,15,10,3,9,8,6,4,2,1,11,10,13,7,8,15,9,12,5,6,3,0,14,11,8,12,7,1,14,2,13,6,15,0,9,10,4,5,3,//S612,1,10,15,9,2,6,8,0,13,3,4,14,7,5,11,10,15,4,2,7,12,0,5,6,1,13,14,0,11,3,8,9,14,15,5,2,8,12,3,7,0,4,10,1,13,11,6,4,3,2,12,9,5,15,10,11,14,1,7,6,0,8,13,//S74,11,2,14,15,0,8,13,3,12,9,7,5,10,6,1,13,0,11,7,4,0,1,10,14,3,5,12,2,15,8,6,1,4,11,13,12,3,7,14,10,15,6,8,0,5,9,26,11,13,8,1,4,10,7,9,5,0,15,14,2,3,12,//S813,2,8,4,6,15,11,1,10,9,3,14,5,0,12,7,1,15,13,8,10,3,7,4,12,5,6,11,0,14,9,2,7,11,4,1,9,12,14,2,0,6,10,13,15,3,5,8,2,1,14,7,4,10,8,13,15,12,9,0,3,5,6,11};Static bool SubKey[16][48]; //16圈子密钥Void Des_Run(char Out[8],char In[8],bool Type){Static bool M[64],Tmp[32],*Li=&M[0],*Ri=&M[32]; ByteToBit(M,In,64);Transform (M,M,IP_Table,64);If (Type==ENCRYPT){For (int i=0;i<16;i++){memcpy(Tmp,ri,32);F_func(Ri,SubKey[i]);Xor(Ri,Li,32);Memcpy(Li,Tmp,32);}}else{For (int i=15;i>=0;i--) {Memcpy(Tmp,Li,32);F_func(Li,SubKey[i]);Xor(Li,Ri,32);Memcpy(Ri,Tmp,32);}}Transform(M,M,IPR_Table,64);BitToByte(Out,M,64);}Void Des_SetKey(const char Key[8]){Static bool K[64],*KL=&K[0],*KR=&K[28];ByteToBit(K,Key,64);Transform(K,K,PC1_Table,56);For (int i=0;i<16;i++){RotateL(KL,28,LOOP_Table[i]);RotateL(KR,28,LOOP_Table[i]);Transform(SubKey[i],K,PC2_Table,48);}}Void F_func(bool In[32],const bool Ki[48]){static bool MR[48];Transform(MR,In,E_Table,48);Xor(MR,Ki,48);S_func(In,MR);Transform(In,In,P_Table,32);}Void S_func(bool Out[32],const bool In[48]){For (char i=0,j,k;i<8;i++;In+=6,Out+=4){J=(In[0]<<1)+In[5];K=(In[1]<<3)+(In[2]<<2)+(In[3]<<1)+In[4];ByteToBit(Out,&S_Box[i][j][k],4);}}Void Transform(bool *Out,bool *In,const char *Table,int len) {Static bool Tmp[256];For (int i=0;i<len;i++)Tmp[i]=In[Table[i]-1];Memcpy(Out,Tmp,len);}Void Xor(bool *InA,const bool *InB,int len){For (int i=0;i<len;i++)InA[i]^=InB[i];}Void RotateL(bool *In,int len,int loop){Static bool Tmp[256];Memcpy(Tmp,In,loop);Memcpy(In,In+loop,len-loop);Memcpy(In+len-loop,Tmp,loop);}}Void ByteToBit(bool *Out,const char *In,int bits){For (int i=0;i<bits;i++)Out[i]=(In[i/8]>>(i%8)) &1;}Void BitToByte(char *Out,const bool *In,int bits){Memset (Out,0,(bits+7)/8);For (int i=0;i<bits;i++)Out[i/8]!=In[i]<<(i%8);}Void main(){char key[8]={1,9,8,0,9,1,7,2},str[]=”Hello”;Puts(“Before encrypting”);Puts(str);Des_SetKey(key);Des_Run(str,str,ENCRYPT); //调用Des_Run函数对输入的明文进行加密//其中第1个参数str是输出的密文,第2个参数str是输入的明文Puts(“After encrypting”);Puts(str);Puts(“After decrypting”);Des_Run(str,str,DECRYPT);Puts(str);}。
DES在C#和DELPHI下的实现

DES在C#和DELPHI下的实现DES在C#下是由des来实现的,需要KEY和IV,其中如果KEY或者IV不足8字节,用#0 来补足代码如下:byte[] key = new byte[8];byte[] iv = new byte[8];for (inti = 0;i < 8 ;i ++){if (i<temp.Length){key[i] = temp[i];}else{key[i] = 0;}if (i< temp1.Length){iv[i] = temp1[i];}else{iv[i] = 0;}}private string EncryptString(string Value,byte[] key,byte[] iv){DESCryptoServiceProvider des = new DESCryptoServiceProvider();ICryptoTransformct;MemoryStreamms;CryptoStreamcs;byte[] byt;//des.KeySize = key.Length;//des.ValidKeySize(key.Length);//ct = des.CreateEncryptor(key,iv);des.Key = key;des.IV = iv;//des.GenerateIV();ct = des.CreateEncryptor();//des.GenerateIV;byt = Encoding.UTF8.GetBytes(Value);ms = new MemoryStream();cs = new CryptoStream(ms, ct, CryptoStreamMode.Write);cs.Write(byt, 0, byt.Length);cs.FlushFinalBlock();cs.Close();byte[] bytesCipher=ms.ToArray();return Convert.ToBase64String(bytesCipher);}private string DecryptString(string Value,byte[] key,byte[] iv){DESCryptoServiceProvider des = new DESCryptoServiceProvider();ICryptoTransformct;MemoryStreamms;CryptoStreamcs;byte[] byt;des.Key = key;des.IV = iv;ct = des.CreateDecryptor();//ct = des.CreateDecryptor(key,iv);byt = Convert.FromBase64String(Value);ms = new MemoryStream();cs = new CryptoStream(ms, ct, CryptoStreamMode.Write);cs.Write(byt, 0, byt.Length);cs.FlushFinalBlock();cs.Close();byte[] bytesCipher = ms.ToArray();return Encoding.UTF8.GetString(bytesCipher);}DELPHI下要实现相应的加密和解密,需要自己写DES代码,并加上CBC方式的异或这里要说明一点,我发现C#下DES明文在加密前,有补足8的倍数的情况,即如果如果是“11111”就会补成“11111#3#3#3”,如果是“11111111”就会“11111111#8#8#8#8#8#8#8#8”,然后在进行异或,最后加密!演示代码如下:Encrypt := true;temp := edit2.Text;res := '';for i:=0 to 7 do beginifi> (length(temp)-1) thenkey[i] :=0elsekey[i] := byte(temp[i+1]);end;temp := edit3.Text;for i:=0 to 7 do beginifi> (length(temp)-1) theniv[i]:=0elseiv[i] := byte(temp[i+1]);end;InitEncryptDES(Key, Context, Encrypt);temp := edit1.Text;len := length(temp);temp := temp+ char( 8- (len mod 8));posnum := 0;for i:=0 to len do beginposchar:= temp[i+1];Block[posnum] := byte(poschar);posnum := posnum +1;ifposnum = 8 then beginEncryptDESCBC(Context, IV, Block);for j:= 0 to 7 do beginres := res + char(block[j]);end;iv := block;posnum := 0;end;end;if posnum<> 0 then beginfor i:=posnum to 7 do beginBlock[i] := byte(poschar);end;EncryptDESCBC(Context, IV, Block);for j:= 0 to 7 do beginres := res + char(block[j]);end;posnum := 0;end;edit4.Text := IdEncoderMIME1.EncodeString(res);Encrypt := false;temp := edit2.Text;res := '';for i:=0 to 7 do beginifi> (length(temp)-1) thenkey[i] :=0elsekey[i] := byte(temp[i+1]);end;temp := edit3.Text;for i:=0 to 7 do beginifi> (length(temp)-1) theniv[i] := 0elseiv[i] := byte(temp[i+1]);end;InitEncryptDES(Key, Context, Encrypt);//for i:=0 to 7 do block[0] := 0;temp := IdDecoderMIME1.DecodeString(edit4.Text) ; posnum := 0;for i:=0 to length(temp)-1 do beginBlock[posnum] := byte(temp[i+1]);posnum := posnum+1;ifposnum = 8 then beginbak := block;EncryptDESCBC(Context, IV, Block);for j:= 0 to 7 do begin// temp := temp+inttostr(byte(block[i]))+' '; res := res + char(block[j]);end;iv := bak;posnum := 0;end;end;ifposnum<> 0 then begin showmessage('解密出错'); end else begintemp:='';//len := res[length(res)] ; for i:= 1 to length(res) do begin temp := temp+char(res[i]); end;edit1.Text := trim(temp); end;。
用C语言实现DES加密和解密

用C语言实现DES加密与解密#include<iostream.h>int IP[64] = {58,50,42,34,26,18,10,2,60,52,44,36,28,20,12,4,62,54,46,38,30,22,14,6,64,56,48,40,32,24,16,8,57,49,41,33,25,17,9,1,59,51,43,35,27,19,11,3,61,53,45,37,29,21,13,5,63,55,47,39,31,23,15,7};int IP_1[64] = {40,8,48,16,56,24,64,32,39,7,47,15,55,23,63,31,38,6,46,14,54,22,62,30,37,5,45,13,53,21,61,29,36,4,44,12,52,20,60,28,35,3,43,11,51,19,59,27,34,2,42,10,50,18,58,26,33,1,41,9,49,17,57,25};int E[48] = {32,1, 2, 3, 4, 5,4, 5, 6, 7, 8, 9,8, 9, 10,11,12,13,12,13,14,15,16,17,16,17,18,19,20,21,20,21,22,23,24,25,24,25,26,27,28,29,28,29,30,31,32,1};int P[32]={16 ,7 , 20 , 21 , 29,12 ,28 , 17 ,1, 15 ,23 , 26 ,5, 18 ,31 , 10 ,2, 8 , 24 , 14 ,32,27, 3 , 9 ,19,13, 30 , 6 ,22,11 ,4 , 25 };19,11,3,60,52,44,36,63,55,47,39,31,23,15,7,62,54,46,38,30,22,14,6,61,53,45,37,29,21,13,5,28,20,12,4},PC2[48]={14,17,11,24,1,5,3,28,15,6,21,10,23,19,12,4,26,8,16,7,27,20,13,2,41,52,31,37,47,55,30,40,51,45,33,48,44,49,39,56,34,53,46,42,50,36,29,32};Char_to_Int(in,Msg_Int,8);//正确O_to_B(Msg_Int,Msg_Bin,8);//正确cout<<endl;Convert(Msg_Bin,Msg_Bin_PC1,PC1,56); Divide(Msg_Bin_PC1,C[0],D[0],56);for(i=0;i<16;i++){if(i==0){RLC1(C[i],C[i+1],28);RLC1(D[i],D[i+1],28);}else if(i==1){RLC1(C[i],C[i+1],28);RLC1(D[i],D[i+1],28);}else if(i==8){RLC1(C[i],C[i+1],28);RLC1(D[i],D[i+1],28);}else if(i==15){RLC1(C[i],C[i+1],28);RLC1(D[i],D[i+1],28);}else{RLC2(C[i],C[i+1],28);RLC2(D[i],D[i+1],28);Combine(C[i+1],D[i+1],Key_Bin,56); Convert(Key_Bin,out[i],PC2,48);}//生成子密钥正确void S_box(int in[],int out[]){int i;int SBox[8][64] ={{14,4,13,1,2,15,11,8,3,10,6,12,5,9,0,7, 0,15,7,4,14,2,13,1,10,6,12,11,9,5,3,8, 4,1,14,8,13,6,2,11,15,12,9,7,3,10,5,0, 15,12,8,2,4,9,1,7,5,11,3,14,10,0,6,13 },{15,1,8,14,6,11,3,4,9,7,2,13,12,0,5,10, 3,13,4,7,15,2,8,14,12,0,1,10,6,9,11,5, 0,14,7,11,10,4,13,1,5,8,12,6,9,3,2,15, 13,8,10,1,3,15,4,2,11,6,7,12,0,5,14,9 },{10,0,9,14,6,3,15,5,1,13,12,7,11,4,2,8, 13,7,0,9,3,4,6,10,2,8,5,14,12,11,15,1, 13,6,4,9,8,15,3,0,11,1,2,12,5,10,14,7, 1,10,13,0,6,9,8,7,4,15,14,3,11,5,2,12 },{7,13,14,3,0,6,9,10,1,2,8,5,11,12,4,15, 13,8,11,5,6,15,0,3,4,7,2,12,1,10,14,9, 10,6,9,0,12,11,7,13,15,1,3,14,5,2,8,4, 3,15,0,6,10,1,13,8,9,4,5,11,12,7,2,14 },{2,12,4,1,7,10,11,6,8,5,3,15,13,0,14,9, 14,11,2,12,4,7,13,1,5,0,15,10,3,9,8,6, 4,2,1,11,10,13,7,8,15,9,12,5,6,3,0,14, 11,8,12,7,1,14,2,13,6,15,0,9,10,4,5,3, },{12,1,10,15,9,2,6,8,0,13,3,4,14,7,5,11, 10,15,4,2,7,12,9,5,6,1,13,14,0,11,3,8, 9,14,15,5,2,8,12,3,7,0,4,10,1,13,11,6, 4,3,2,12,9,5,15,10,11,14,1,7,6,0,8,13 },4,11,2,14,15,0,8,13,3,12,9,7,5,10,6,1,13,0,11,7,4,9,1,10,14,3,5,12,2,15,8,6,1,4,11,13,12,3,7,14,10,15,6,8,0,5,9,2,6,11,13,8,1,4,10,7,9,5,0,15,14,2,3,12},{13,2,8,4,6,15,11,1,10,9,3,14,5,0,12,7,1,15,13,8,10,3,7,4,12,5,6,11,0,14,9,2,7,11,4,1,9,12,14,2,0,6,10,13,15,3,5,8,2,1,14,7,4,10,8,13,15,12,9,0,3,5,6,11}};int s1,s3,s2[8];for(i=0;i<8;i++){s1=in[i*6]*2+in[i*6+5]*1;s3=in[i*6+1]*8+in[i*6+2]*4+in[i*6+3]*2+in[i*6+4]*1; s2[i]=SBox[i][s1*16+s3];}int j;for(i=0;i<8;i++)for(j=i*4+3;j>=i*4;j--){out[j]=s2[i]%2; s2[i]=s2[i]/2;void Encode(unsigned char in[],unsigned char Final_H[],int K[16][48]) {int i;intORINT[8],ORBYTE[64],FinalBYTE[64],LR[64],R48[48],S_in[48],S_out[32],F_RL[32],Fi nalINT[8],L[17][32],R[17][32];char ORH[16];void DeCode(unsigned char in[],unsigned char Final_H[],int K[16][48]) {int i;intORINT[8],ORBYTE[64],LR[64],R48[48],S_in[48],S_out[32],F_RL[32],FinalBYTE[64],Fi nalINT[8],L[17][32],R[17][32];char ORH[16];Char_to_Int(in,ORINT,8);cout<<"!!!!!"<<endl;O_to_B(ORINT,ORBYTE,8);Convert(ORBYTE,LR,IP,64);Divide(LR,L[0],R[0],64);for(i=1;i<17;i++){COPY(R[i-1],L[i],32);Convert(R[i-1],R48,E,48);XOR(R48,K[16-i],S_in,48);S_box(S_in,S_out);Convert(S_out,F_RL,P,32);XOR(L[i-1],F_RL,R[i],32);}Combine(R[16],L[16],LR,64);Convert(LR,FinalBYTE,IP_1,64);B_to_H(FinalBYTE,Final_H);}void main(){int i;unsigned char Msg[8],UnCodeMsg[16],CodeMsg[16],Key[8],Msg_H[16],CodeChar[8];int SKey[16][48];int OrByte[64],OrInt[8],FinalByte[64],FinalInt[8];cout<<"请输入明文:"<<endl;for(i=0;i<8;i++)cin>>Msg[i];cout<<"请输入初始密钥:"<<endl;for(i=0;i<8;i++)cin>>Key[i];GetKey(Key,SKey);Encode(Msg,CodeMsg,SKey);cout<<"十六进制的密文:"<<endl;for(i=0;i<16;i++)cout<<CodeMsg[i];cout<<endl;cout<<"字符型密文:"<<endl;H_to_B(CodeMsg,FinalByte);B_to_O(FinalByte,FinalInt,8);Int_to_Char(FinalInt,CodeChar,8); for(i=0;i<8;i++)cout<<CodeChar[i];cout<<endl;cout<<"请输入十六进制的密文:"<<endl;for(i=0;i<16;i++)cin>>CodeMsg[i];B_to_O(FinalByte,FinalInt,8);Int_to_Char(FinalInt,CodeChar,8); cout<<"请输入解密密钥:"<<endl;for(i=0;i<8;i++)cin>>Key[i];GetKey(Key,SKey);DeCode(CodeChar,Msg_H,SKey);//for(i=0;i<16;i++)//cout<<Msg_H[i];cout<<endl;H_to_B(Msg_H,OrByte);B_to_O(OrByte,OrInt,8);Int_to_Char(OrInt,Msg,8);cout<<"明文是:"<<endl;for(i=0;i<8;i++)cout<<Msg[i];cout<<endl;}欢迎您的下载,资料仅供参考!。
DES算法的C语言代码及实现

DES算法的C语言代码及实现首先新建头文件des_encode.H内容如下:void EncodeMain(); //EncodeMain functionvoid DecodeMain(); //Sorry ,it has not usedvoid Decode(int *str,int *keychar); //decode :input 8 chars,8 keycharsvoid Encode(int *str,int *keychar); //encode: input 8 chars,8 keycharsvoid keyBuild(int *keychar); //create key arrayvoid StrtoBin(int *midkey,int *keychar); //change into binaryvoid keyCreate(int *midkey2,int movebit,int i); //call by keyBuildvoid EncodeData(int *lData,int *rData,int *srt); //encodedata functionvoid F(int *rData,int *key); //F functionvoid Expand(int *rData,int *rDataP); //Expand functionvoid ExchangeS(int *rDataP,int *rData); //S-diagram changevoid ExchangeP(int *rData); //P changevoid FillBin(int *rData,int n,int s); // data to binary;call by S-Diagram change functionvoid DecodeData(int *str,int *lData,int *rData); //DecodeData from binaryint IP1[]={58, 50, 42, 34, 26, 18, 10, 2, 60, 52, 44, 36, 28, 20, 12, 4, //initial change62, 54, 46, 38, 30, 22, 14, 6, 64, 56, 48, 40, 32, 24, 16, 8,57, 49, 41, 33, 25, 17, 9, 1, 59, 51, 43, 35, 27, 19, 11, 3,61, 53, 45, 37, 29, 21, 13, 5, 63, 55, 47, 39, 31, 23, 15, 7,};int IP2[]={40, 8, 48, 16, 56, 24, 64, 32, 39, 7, 47, 15, 55, 23, 63, 31, //opp initial change38, 6, 46, 14, 54, 22, 62, 30, 37, 5, 45, 13, 53, 21, 61, 29,36, 4, 44, 12, 52, 20, 60, 28, 35, 3, 43, 11, 51, 19, 59, 27,34, 2, 42, 10, 50, 18, 58, 26, 33, 1, 41, 9, 49, 17, 57, 25};int s[][4][16]={{ //S-diagram array{14,4,13,1,2,15,11,8,3,10,6,12,5,9,0,7},{0,15,7,4,14,2,13,1,10,6,12,11,9,5,3,8},{4,1,14,8,13,6,2,11,15,12,9,7,3,10,5,0},{15,12,8,2,4,9,1,7,5,11,3,14,10,0,6,13}},{{15,1,8,14,6,11,3,4,9,7,2,13,12,0,5,10},{3,13,4,7,15,2,8,14,12,0,1,10,6,9,11,5},{0,14,7,11,10,4,13,1,5,8,12,6,9,3,2,15},{13,8,10,1,3,15,4,2,11,6,7,12,0,5,14,9}},{{10,0,9,14,6,3,15,5,1,13,12,7,11,4,2,8},{13,7,0,9,3,4,6,10,2,8,5,14,12,11,15,1},{1,10,13,0,6,9,8,7,4,15,14,3,11,5,2,12} },{{7,13,14,3,0,6,9,10,1,2,8,5,11,12,4,15}, {13,8,11,5,6,15,0,3,4,7,2,12,1,10,14,9}, {10,6,9,0,12,11,7,13,15,1,3,14,5,2,8,4}, {3,15,0,6,10,1,13,8,9,4,5,11,12,7,2,14} },{{2,12,4,1,7,10,11,6,8,5,3,15,13,0,14,9}, {14,11,2,12,4,7,13,1,5,0,15,10,3,9,8,6}, {4,2,1,11,10,13,7,8,15,9,12,5,6,3,0,14}, {11,8,12,7,1,14,2,13,6,15,0,9,10,4,5,3} },{{12,1,10,15,9,2,6,8,0,13,3,4,14,7,5,11}, {10,15,4,2,7,12,9,5,6,1,13,14,0,11,3,8}, {9,14,15,5,2,8,12,3,7,0,4,10,1,13,11,6}, {4,3,2,12,9,5,15,10,11,14,1,7,6,0,8,13} },{{13,0,11,7,4,9,1,10,14,3,5,12,2,15,8,6}, {1,4,11,13,12,3,7,14,10,15,6,8,0,5,9,2}, {6,11,13,8,1,4,10,7,9,5,0,15,14,2,3,12} },{{13,2,8,4,6,15,11,1,10,9,3,14,5,0,12,7}, {1,15,13,8,10,3,7,4,12,5,6,11,0,14,9,2}, {7,11,4,1,9,12,14,2,0,6,10,13,15,3,5,8}, {2,1,14,7,4,10,8,13,15,12,9,0,3,5,6,11} }};int Ex[48]={ 32,1,2,3,4,5, //Expand array 4,5,6,7,8,9,8,9,10,11,12,13,12,13,14,15,16,17,16,17,18,19,20,21,20,21,22,23,24,25,24,25,26,27,28,29,28,29,30,31,32,1};int P[32]={16,7,20,21, //P-change29,12,28,17,1,15,23,26,5,18,31,10,2,8,24,14,32,27,3,9,19,13,30,6,22,11,4,25};int PC1[56]={57,49,41,33,25,17,9, //PC-1 in keyBuild 1,58,50,42,34,26,18,10,2,59,51,43,35,27,19,11,3,60,52,44,36,63,55,47,39,31,33,15,7,62,54,46,38,30,22,14,6,61,53,45,37,29,21,13,5,28,20,12,4};int PC2[48]={14,17,11,24,1,5, //PC-2 in keyBuild3,28,15,6,21,10,23,19,12,4,26,8,16,7,27,20,13,2,41,52,31,37,47,55,30,40,51,45,33,48,44,49,39,56,34,53,46,42,50,36,29,32};再创建des.cpp内容如下:#include<stdio.h>#include<string.h>#include"des_encode.h"int key[16][48];char str[8];void main() //main function{EncodeMain();}void EncodeMain() //EncodeMain function {int i;char keychar[8];int key2[8];int strkey[8];printf("请输入8个要加密的字符:\n");scanf("%c",&str[i]);getchar();for(i=0;i<8;i++)strkey[i]=str[i];printf("\n输入明文的十六进制为:\n"); for(i=0;i<8;i++)printf("%10x",strkey[i]);printf("\n请输入密钥(8个字符):\n"); for(i=0;i<8;i++)scanf("%c",&keychar[i]);for(i=0;i<8;i++)key2[i]=keychar[i];getchar();// printf("%c",keychar[i]);Encode(strkey,key2);printf("\n加密后十六进制密文是:\n"); for(i=0;i<8;i++)printf("%10x",strkey[i]);printf("\n\n清输入解密密码\n");for(i=0;i<8;i++)scanf("%c",&keychar[i]);key2[i]=keychar[i];Decode(strkey,key2);for(i=0;i<8;i++)printf("%10x",strkey[i]);for(i=0;i<8;i++)str[i]=strkey[i];printf("\n明文为:\t");for(i=0;i<8;i++)printf("%c",str[i]);printf("\n\n");}void keyBuild(int *keychar){ //create key array int i,j;int movebit[]={1,1,2,2,2,2,2,2,1,2,2,2,2,2,2,1};int midkey2[56];int midkey[64];StrtoBin(midkey,keychar);for(i=0;i<56;i++)midkey2[i]=midkey[PC1[i]-1];for(i=0;i<16;i++)keyCreate(midkey2,movebit[i],i);}void StrtoBin(int *midkey,int *keychar){ //change into binary int trans[8],i,j,k,n;n=0;for(i=0;i<8;i++){j=0;while(keychar[i]!=0){trans[j]=keychar[i]%2;keychar[i]=keychar[i]/2;j++;}for(k=j;k<8;k++)trans[k]=0;for(k=0;k<8;k++)midkey[n++]=trans[7-k];}}void keyCreate(int *midkey2,int movebit,int n){int i,temp[4];temp[0]=midkey2[0];temp[1]=midkey2[1];temp[2]=midkey2[28];temp[3]=midkey2[29];if(movebit==2){for(i=0;i<26;i++){midkey2[i]=midkey2[i+2];midkey2[i+28]=midkey2[i+30];}midkey2[26]=temp[0];midkey2[27]=temp[1];midkey2[54]=temp[2];midkey2[55]=temp[3]; }else{ for(i=0;i<27;i++){midkey2[i]=midkey2[i+1];midkey2[i+28]=midkey2[i+29];}midkey2[27]=temp[0];midkey2[55]=temp[2];}for(i=0;i<48;i++)key[n][i]=midkey2[PC2[i]-1];}void EncodeData(int *lData,int *rData,int *str){ //encodedata function int i,j,temp[8],lint,rint;//int h;int data[64];lint=0,rint=0;for(i=0;i<4;i++){j=0;while(str[i]!=0){temp[j]=str[i]%2;str[i]=str[i]/2;j++;}while(j<8)temp[j++]=0;for(j=0;j<8;j++)lData[lint++]=temp[7-j];j=0;while(str[i+4]!=0){temp[j]=str[i+4]%2;str[i+4]=str[i+4]/2;j++;}while(j<8)temp[j++]=0;for(j=0;j<8;j++)rData[rint++]=temp[7-j]; }for(i=0;i<32;i++){data[i]=lData[i];data[i+32]=rData[i];}for(i=0;i<32;i++){lData[i]=data[IP1[i]-1];//printf("P1:%5d:%5d,%5d\n",IP1[i],lData[i],data[IP1[i]-1]) ;rData[i]=data[IP1[i+32]-1];}}void F(int *rData,int *key){ //F functionint i,rDataP[48];Expand(rData,rDataP);for(i=0;i<48;i++){rDataP[i]=rDataP[i]^key[i];// printf("%10d",rDataP[i]);if((i+1)%6==0)printf("\n");}ExchangeS(rDataP,rData);ExchangeP(rData);}void Expand(int *rData,int *rDataP){ //Expand functionint i;for(i=0;i<48;i++)rDataP[i]=rData[Ex[i]-1];}void ExchangeS(int *rDataP,int *rData){ //S-diagram changeint i,n,linex,liney;linex=liney=0;for(i=0;i<48;i+=6){n=i/6; //printf("%10d\n",(rDataP[i]<<1));linex=(rDataP[i]<<1)+rDataP[i+5];liney=(rDataP[i+1]<<3)+(rDataP[i+2]<<2)+(rDataP[i+3]<<1)+rDataP[i+4];FillBin(rData,n,s[n][linex][liney]);}}void ExchangeP(int *rData){ //P changeint i,temp[32];for(i=0;i<32;i++)temp[i]=rData[i];for(i=0;i<32;i++)rData[i]=temp[P[i]-1];}void FillBin(int *rData,int n,int s){ // data to binary;call by S-Diagram change functionint temp[4],i;for(i=0;i<4;i++){temp[i]=s%2;s=s/2;for(i=0;i<4;i++)rData[n*4+i]=temp[3-i];}void DecodeData(int *str,int *lData,int *rData){ //DecodeData from binary int i;int a,b;int data[64];a=0,b=0;for(i=0;i<32;i++){data[i]=lData[i];data[i+32]=rData[i];}for(i=0;i<32;i++){lData[i]=data[IP2[i]-1];rData[i]=data[IP2[i+32]-1];}for(i=0;i<32;i++){a=(lData[i]&0x1)+(a<<1);b=(rData[i]&0x1)+(b<<1);if((i+1)%8==0){str[i/8]=a;a=0;//printf("%d",i/8);str[i/8+4]=b;b=0;//printf("%d",i/8+4);}}void Encode(int *str,int *keychar){ //encode: input 8 chars,8 keychars int lData[32],rData[32],temp[32],rDataP[48];int i,j;keyBuild(keychar);EncodeData(lData,rData,str);for(i=0;i<16;i++){for(j=0;j<32;j++)temp[j]=rData[j];F(rData,key[i]);for(j=0;j<32;j++){rData[j]=rData[j]^lData[j];}for(j=0;j<32;j++)lData[j]=temp[j];}DecodeData(str,rData,lData);}void Decode(int *str,int *keychar){ //decode :input 8 chars,8 keychars int lData[32],rData[32],temp[32],rDataP[48];int i,j;keyBuild(keychar);EncodeData(lData,rData,str); //这个位置for(i=0;i<16;i++){for(j=0;j<32;j++)temp[j]=rData[j];F(rData,key[15-i]);for(j=0;j<32;j++){rData[j]=rData[j]^lData[j];}for(j=0;j<32;j++){lData[j]=temp[j];}}DecodeData(str,rData,lData);}。
des加密算法的实现及应用

DES加密算法的实现及应用学生姓名:梁帅指导老师:熊兵摘要随着信息与通信技术的迅猛发展和广泛应用,人们通过互联网进行信息交流,难免涉及到密码保护问题,这就需要使用DES加密技术来对数据进行加密保护。
本课程设计介绍了DES加密的基本原理以及简单的实现方法。
本课程设计基于C语言,采用DES算法技术,设计了DES加密程序,实现了DES加密解密功能。
经测试,程序能正常运行,实现了设计目标。
关键词DES加密,C语言,信息交流1 引言1.1本文主要内容DES是一个分组密码算法,使用64位密钥(除去8位奇偶校验,实际密钥长度为56位)对64比特的数据分组(二进制数据)加密,产生64位密文数据。
DES是一个对称密码体制,加密和解密使用同意密钥,解密和加密使用同一算法(这样,在硬件与软件设计时有利于加密单元的重用)。
DES的所有的保密性均依赖于密钥。
DES算法的入口参数有三个:Key、Data、Mode。
其中Key为8个字节共64位,是DES算法的工作密钥;Data也为8个字节64位,是要被加密或被解密的数据;Mode为DES的工作方式,有两种:加密或解密。
DES算法是这样工作的:如Mode为加密,则用Key 去把数据Data进行加密,生成Data的密码形式(64位)作为DES的输出结果;如Mode为解密,则用Key去把密码形式的数据Data解密,还原为Data的明码形式(64位)作为DES的输出结果。
在通信网络的两端,双方约定一致的Key,在通信的源点用Key对核心数据进行DES加密,然后以密码形式在公共通信网(如电话网)中传输到通信网络的终点,数据到达目的地后,用同样的Key对密码数据进行解密,便再现了明码形式的核心数据。
这样,便保证了核心数据(如PIN、MAC等)在公共通信网中传输的安全性和可靠性DES的加密过程:第一阶段:初始置换IP。
在第一轮迭代之前,需要加密的64位明文首先通过初始置换IP 的作用,对输入分组实施置换。
C语言实现DES加密解密算法

C语言实现DES加密解密算法
最近几十年里,DES(Data Encryption Standard)算法的发展起到
了极其重要的作用。
Des算法是一种基于分组密码的算法。
算法将64位
的明文数据块按位分组成8个字节,每一组以8位为单位转换成一个64
位的密文数据块,采用16轮的分组加密,每次密码变化,保证加密强度。
本文详细介绍了DES算法的C语言实现,并分别介绍了加解密算法的实现
步骤以及DES加解密测试过程。
一、DES算法C语言实现
1.函数原型
DES算法的实现包括加密和解密函数,函数原型如下:
unsigned char* DesEncrypt(unsigned char *src, unsigned char
*key); // DES加密函数
unsigned char* DesDecrypt(unsigned char *src, unsigned char
*key); // DES解密函数
输入参数src是指明文源数据,key是加解密密钥,输出参数为一个
指向加解密结果的字符串指针。
2.加解密算法
(1)DES加密算法
DES加密算法步骤如下:
(i)初始置换:将64位明文块做一次IP置换得到L0R0。
(ii)迭代轮换:对L0R0经过16次迭代轮换后,最终结果为
L16R16
(iii)逆置换:L16R16进行逆置换得到64位密文。
(2)DES解密算法
DES解密算法步骤和DES加密算法步骤是一样的,只是将置换步骤改为逆置换,将轮换步骤改为逆轮换即可。
三、DES加解密测试
1.程序测试
在C语言编写完DES加解密算法之后。
C语言实现数据加密算法

C语言实现数据加密算法数据加密是对敏感信息进行转换的过程,以保护数据的机密性和完整性。
C语言提供了强大的工具和库来实现各种加密算法,包括对称加密和非对称加密等。
对称加密算法是一种使用相同密钥加密和解密数据的方法。
其中最常见的算法是DES(Data Encryption Standard)和AES(Advanced Encryption Standard)。
下面是一个实现AES算法的示例代码:```c#include <stdio.h>#include <stdlib.h>#include <string.h>#include <openssl/aes.h>void encrypt_data(const unsigned char *data, size_t len, const unsigned char *key, unsigned char *encrypted_data) AES_KEY aes_key;AES_set_encrypt_key(key, 128, &aes_key);AES_encrypt(data, encrypted_data, &aes_key);void decrypt_data(const unsigned char *encrypted_data,size_t len, const unsigned char *key, unsigned char *data) AES_KEY aes_key;AES_set_decrypt_key(key, 128, &aes_key);AES_decrypt(encrypted_data, data, &aes_key);int maiunsigned char data[AES_BLOCK_SIZE] = "hello world!";size_t len = sizeof(data);unsigned char encrypted_data[AES_BLOCK_SIZE];encrypt_data(data, len, key, encrypted_data);unsigned char decrypted_data[AES_BLOCK_SIZE];decrypt_data(encrypted_data, len, key, decrypted_data);printf("Original Data: %s\n", data);printf("Encrypted Data: ");for (int i = 0; i < len; i++)printf("%02x ", encrypted_data[i]);}printf("\nDecrypted Data: %s\n", decrypted_data);return 0;```以上代码使用了OpenSSL库中的AES加密算法。
DES算法的C语言实现

DES算法的C语言实现作者:王颖,石云峰来源:《电脑知识与技术》2011年第10期摘要:对称密码算法又称单钥或私钥或传统密码体制,其发方和收方使用相同的密钥,即加密密钥和解密密钥是相同的。
在众多的常规密码中影响最大的是DES密码。
该文介绍DES 算法的C语言实现。
关键词:DES;密钥;初始置换;逆置换中图分类号:TP311文献标识码:A文章编号:1009-3044(2011)10-2295-02The Realization of DES Algorithm with C LanguageWANG Ying, SHI Yun-feng(College of the Information Technology, Dalian Ocean University, Dalian 116023, China)Abstract: Symmetric key cryptography, also called single key or private key or traditional cryptography, whose sender and receiver use the same key, in the other word, the encrypt key is just the decipher key. DES is the representative of the symmetric key cryptography. This paper describes DES algorithm using C language.Key words: DES;key; initial permutation; inverse permutation随着计算机网络不断渗透到各个领域,密码学的应用也随之扩大。
而DES是国际上商用保密通信和计算机通信的最常用的加密算法[1]。
本文重点介绍DES算法的C语言实现。
DES加密C语言实现源代码

void *memcpy( void *dest, const void *src, unsigned char count ){// ASSERT((dest != NULL)&&(src != NULL));unsigned char *temp_dest = (unsigned char *)dest;unsigned char *temp_src = (unsigned char *)src;while(count--) // 不对是否存在重叠区域进行判断{*temp_dest++ = *temp_src++;}return dest;}unsigned char *memset(unsigned char *dst,unsigned char value,unsigned char count) {unsigned char *start = dst;while (count--)*dst++ = value;return(start);}// 初始置换表IPunsigned char IP_Table[64] = { 57,49,41,33,25,17,9,1,59,51,43,35,27,19,11,3,61,53,45,37,29,21,13,5,63,55,47,39,31,23,15,7,56,48,40,32,24,16,8,0,58,50,42,34,26,18,10,2,60,52,44,36,28,20,12,4,62,54,46,38,30,22,14,6};//逆初始置换表IP^-1unsigned char IP_1_Table[64] = {39,7,47,15,55,23,63,31,38,6,46,14,54,22,62,30,37,5,45,13,53,21,61,29,36,4,44,12,52,20,60,28,35,3,43,11,51,19,59,27,34,2,42,10,50,18,58,26,33,1,41,9,49,17,57,25,32,0,40,8,48,16,56,24}; //扩充置换表Eunsigned char E_Table[48] = {31, 0, 1, 2, 3, 4,3, 4, 5, 6, 7, 8,7, 8,9,10,11,12,11,12,13,14,15,16,15,16,17,18,19,20,19,20,21,22,23,24,23,24,25,26,27,28,27,28,29,30,31, 0};//置换函数Punsigned char P_Table[32] = {15,6,19,20,28,11,27,16,0,14,22,25,4,17,30,9,1,7,23,13,31,26,2,8,18,12,29,5,21,10,3,24};//S盒unsigned char S[8][4][16] =// S1 {{{14,4,13,1,2,15,11,8,3,10,6,12,5,9,0,7}, {0,15,7,4,14,2,13,1,10,6,12,11,9,5,3,8}, {4,1,14,8,13,6,2,11,15,12,9,7,3,10,5,0}, {15,12,8,2,4,9,1,7,5,11,3,14,10,0,6,13}}, // S2{{15,1,8,14,6,11,3,4,9,7,2,13,12,0,5,10}, {3,13,4,7,15,2,8,14,12,0,1,10,6,9,11,5}, {0,14,7,11,10,4,13,1,5,8,12,6,9,3,2,15}, {13,8,10,1,3,15,4,2,11,6,7,12,0,5,14,9}}, //S3{{10,0,9,14,6,3,15,5,1,13,12,7,11,4,2,8}, {13,7,0,9,3,4,6,10,2,8,5,14,12,11,15,1}, {13,6,4,9,8,15,3,0,11,1,2,12,5,10,14,7}, {1,10,13,0,6,9,8,7,4,15,14,3,11,5,2,12}}, // S4{{7,13,14,3,0,6,9,10,1,2,8,5,11,12,4,15}, {13,8,11,5,6,15,0,3,4,7,2,12,1,10,14,9}, {10,6,9,0,12,11,7,13,15,1,3,14,5,2,8,4}, {3,15,0,6,10,1,13,8,9,4,5,11,12,7,2,14}}, //S5{{2,12,4,1,7,10,11,6,8,5,3,15,13,0,14,9},{14,11,2,12,4,7,13,1,5,0,15,10,3,9,8,6},{4,2,1,11,10,13,7,8,15,9,12,5,6,3,0,14}, {11,8,12,7,1,14,2,13,6,15,0,9,10,4,5,3}},//S6{{12,1,10,15,9,2,6,8,0,13,3,4,14,7,5,11}, {10,15,4,2,7,12,9,5,6,1,13,14,0,11,3,8},{9,14,15,5,2,8,12,3,7,0,4,10,1,13,11,6},{4,3,2,12,9,5,15,10,11,14,1,7,6,0,8,13}},// S7{{4,11,2,14,15,0,8,13,3,12,9,7,5,10,6,1}, {13,0,11,7,4,9,1,10,14,3,5,12,2,15,8,6},{1,4,11,13,12,3,7,14,10,15,6,8,0,5,9,2},{6,11,13,8,1,4,10,7,9,5,0,15,14,2,3,12}},//S8{{13,2,8,4,6,15,11,1,10,9,3,14,5,0,12,7},{1,15,13,8,10,3,7,4,12,5,6,11,0,14,9,2},{7,11,4,1,9,12,14,2,0,6,10,13,15,3,5,8},{2,1,14,7,4,10,8,13,15,12,9,0,3,5,6,11}}};//置换选择1unsigned char PC_1[56] = {56,48,40,32,24,16,8,0,57,49,41,33,25,17,9,1,58,50,42,34,26,18,10,2,59,51,43,35,62,54,46,38,30,22,14,6,61,53,45,37,29,21,13,5,60,52,44,36,28,20,12,4,27,19,11,3};//置换选择2unsigned char PC_2[48] = {13,16,10,23,0,4,2,27,14,5,20,9,22,18,11,3,25,7,15,6,26,19,12,1,40,51,30,36,46,54,29,39,50,44,32,46,43,48,38,55,33,52,45,41,49,35,28,31};// 对左移次数的规定unsigned char MOVE_TIMES[16] = {1,1,2,2,2,2,2,2,1,2,2,2,2,2,2,1}; //字节转换成二进制unsigned char ByteToBit(unsigned char ch, unsigned char bit[8]) {unsigned char cnt;for(cnt = 0;cnt < 8; cnt++){*(bit+cnt) = (ch>>cnt)&1;}return 0;}// 二进制转换成字节unsigned char BitToByte(unsigned char bit[8],unsigned char *ch){unsigned char cnt;for(cnt = 0;cnt < 8; cnt++){*ch |= *(bit + cnt)<<cnt;}return 0;}// 将长度为8的字符串转为二进制位串unsigned char Char8ToBit64(unsigned char ch[8],unsigned char bit[64]){unsigned char cnt;for(cnt = 0; cnt < 8; cnt++){ByteToBit(*(ch+cnt),bit+(cnt<<3));}return 0;}// 将二进制位串转为长度为8的字符串unsigned char Bit64ToChar8(unsigned char bit[64],unsigned char ch[8]){unsigned char cnt;memset(ch,0,8);for(cnt = 0; cnt < 8; cnt++){BitToByte(bit+(cnt<<3),ch+cnt);}return 0;}// 密钥置换1unsigned char DES_PC1_Transform(unsigned char key[64], unsigned char tempbts[56]) {unsigned char cnt;for(cnt = 0; cnt < 56; cnt++){tempbts[cnt] = key[PC_1[cnt]];}return 0;}//密钥置换2unsigned char DES_PC2_Transform(unsigned char key[56], unsigned char tempbts[48]) {unsigned char cnt;for(cnt = 0; cnt < 48; cnt++){tempbts[cnt] = key[PC_2[cnt]];}return 0;}//循环左移unsigned char DES_ROL(unsigned char data[56], unsigned char time){unsigned char temp[56];//保存将要循环移动到右边的位memcpy(temp,data,time);memcpy(temp+time,data+28,time);//前28位移动memcpy(data,data+time,28-time);memcpy(data+28-time,temp,time);//后28位移动memcpy(data+28,data+28+time,28-time);memcpy(data+56-time,temp+time,time);return 0;}//IP置换unsigned char DES_IP_Transform(unsigned char data[64]){unsigned char cnt;unsigned char temp[64];for(cnt = 0; cnt < 64; cnt++){temp[cnt] = data[IP_Table[cnt]];}memcpy(data,temp,64);return 0;}// IP逆置换unsigned char DES_IP_1_Transform(unsigned char data[64]) {unsigned char cnt;unsigned char temp[64];for(cnt = 0; cnt < 64; cnt++){temp[cnt] = data[IP_1_Table[cnt]];}memcpy(data,temp,64);return 0;}//扩展置换unsigned char DES_E_Transform(unsigned char data[48]) {unsigned char cnt;unsigned char temp[48];for(cnt = 0; cnt < 48; cnt++){temp[cnt] = data[E_Table[cnt]];}memcpy(data,temp,48);return 0;}//P置换unsigned char DES_P_Transform(unsigned char data[32]) {unsigned char cnt;unsigned char temp[32];for(cnt = 0; cnt < 32; cnt++){temp[cnt] = data[P_Table[cnt]];}memcpy(data,temp,32);return 0;}// 异或unsigned char DES_XOR(unsigned char R[48], unsigned char L[48] ,unsigned char count) {unsigned char cnt;for(cnt = 0; cnt < count; cnt++){R[cnt] ^= L[cnt];}return 0;}// S盒置换unsigned char DES_SBOX(unsigned char data[48]){unsigned char cnt;unsigned char line,row,output;unsigned char cur1,cur2;for(cnt = 0; cnt < 8; cnt++){cur1 = cnt*6;cur2 = cnt<<2;// 计算在S盒中的行与列line = (data[cur1]<<1) + data[cur1+5];row = (data[cur1+1]<<3) + (data[cur1+2]<<2)+ (data[cur1+3]<<1) + data[cur1+4];output = S[cnt][line][row];// 化为2进制data[cur2] = (output&0X08)>>3;data[cur2+1] = (output&0X04)>>2;data[cur2+2] = (output&0X02)>>1;data[cur2+3] = output&0x01;}return 0;}//交换unsigned char DES_Swap(unsigned char left[32], unsigned char right[32]){unsigned char temp[32];memcpy(temp,left,32);memcpy(left,right,32);memcpy(right,temp,32);return 0;}//生成子密钥unsigned char DES_MakeSubKeys(unsigned char key[64],unsigned char subKeys[16][48]){unsigned char temp[56];unsigned char cnt;DES_PC1_Transform(key,temp);// PC1置换for(cnt = 0; cnt < 16; cnt++) //16轮跌代,产生16个子密钥{DES_ROL(temp,MOVE_TIMES[cnt]);// 循环左移DES_PC2_Transform(temp,subKeys[cnt]);//PC2置换,产生子密钥}return 0;}//加密单个分组unsigned char DES_EncryptBlock(unsigned char plainBlock[8], unsigned char subKeys[16][48], unsigned char cipherBlock[8]){unsigned char plainBits[64];unsigned char copyRight[48];unsigned char cnt;Char8ToBit64(plainBlock,plainBits);//初始置换(IP置换)DES_IP_Transform(plainBits);// 16轮迭代for(cnt = 0; cnt < 16; cnt++){memcpy(copyRight,plainBits+32,32);DES_E_Transform(copyRight); // 将右半部分进行扩展置换,从32位扩展到48位DES_XOR(copyRight,subKeys[cnt],48); // 将右半部分与子密钥进行异或操作DES_SBOX(copyRight); // 异或结果进入S盒,输出32位结果DES_P_Transform(copyRight); // P置换DES_XOR(plainBits,copyRight,32); //将明文左半部分与右半部分进行异或if(cnt != 15){DES_Swap(plainBits,plainBits+32);//最终完成左右部的交换}}DES_IP_1_Transform(plainBits); //逆初始置换(IP^1置换)Bit64ToChar8(plainBits,cipherBlock);return 0;}// 解密单个分组unsigned char DES_DecryptBlock(unsigned char cipherBlock[8], unsigned char subKeys[16][48],unsigned char plainBlock[8]){unsigned char cipherBits[64];unsigned char copyRight[48];short cnt;Char8ToBit64(cipherBlock,cipherBits);//初始置换(IP置换)DES_IP_Transform(cipherBits);// 16轮迭代for(cnt = 15; cnt >= 0; cnt--){memcpy(copyRight,cipherBits+32,32);//将右半部分进行扩展置换,从32位扩展到48位DES_E_Transform(copyRight);// 将右半部分与子密钥进行异或操作DES_XOR(copyRight,subKeys[cnt],48);//异或结果进入S盒,输出32位结果DES_SBOX(copyRight);// P置换DES_P_Transform(copyRight);//将明文左半部分与右半部分进行异或DES_XOR(cipherBits,copyRight,32);if(cnt != 0){// 最终完成左右部的交换DES_Swap(cipherBits,cipherBits+32);}}// 逆初始置换(IP^1置换)DES_IP_1_Transform(cipherBits);Bit64ToChar8(cipherBits,plainBlock);return 0;}//加密文件unsigned char DES_Encrypt(unsigned char *keyStr,unsigned char *plainFile,unsigned char *cipherFile){unsigned char keyBlock[8],bKey[64],subKeys[16][48];memcpy(keyBlock,keyStr,8); //设置密钥Char8ToBit64(keyBlock,bKey); //将密钥转换为二进制流DES_MakeSubKeys(bKey,subKeys); //生成子密钥DES_EncryptBlock(plainFile,subKeys,cipherFile);return 1;}//解密文件unsigned char DES_Decrypt(unsigned char *keyStr,unsigned char *cipherFile,unsigned char *plainFile){// unsigned char plainBlock[8],cipherBlock[8],unsigned char bKey[64],keyBlock[8],subKeys[16][48];memcpy(keyBlock,keyStr,8); //设置密钥Char8ToBit64(keyBlock,bKey); //将密钥转换为二进制流DES_MakeSubKeys(bKey,subKeys); //生成子密钥DES_DecryptBlock(cipherFile,subKeys,plainFile);return 1;}/****************************************************************************** ****************** 作者:win2kddk* 说明:3重DES是使用16字节密钥将8字节明文数据块进行3次DES加密和解密。
DES加密算法的C语言实现

DES加密算法的C语言实现DES(Data Encryption Standard)是一种对称密钥加密算法,它的核心思想是将明文分成64位的数据块,并通过一系列的轮次操作对数据块进行加密,最终得到密文。
下面是一种用C语言实现DES加密算法的示例代码:```c#include <stdio.h>unsigned char initial_permutation(unsigned char block)unsigned char result = 0;result ,= (block & 0x80) >> 7;result ,= (block & 0x40) >> 5;result ,= (block & 0x20) >> 3;result ,= (block & 0x10) >> 1;result ,= (block & 0x08) << 1;result ,= (block & 0x04) << 3;result ,= (block & 0x02) << 5;result ,= (block & 0x01) << 7;return result;unsigned char final_permutation(unsigned char block)unsigned char result = 0;result ,= (block & 0x80) >> 7;result ,= (block & 0x40) >> 5;result ,= (block & 0x20) >> 3;result ,= (block & 0x10) >> 1;result ,= (block & 0x08) << 1;result ,= (block & 0x04) << 3;result ,= (block & 0x02) << 5;result ,= (block & 0x01) << 7;return result;void des_encrypt(unsigned char* plaintext, unsigned char* key, unsigned char* ciphertext)unsigned char block;unsigned char round_key;unsigned char i;// Initial Permutationblock = initial_permutation(*plaintext);// Round Permutationfor (i = 0; i < 16; i++)round_key = key[i];block ^= round_key;block = substitution(block);block = permutation(block);}// Final Permutation*ciphertext = final_permutation(block);int maiunsigned char plaintext = 0x55; // 明文unsigned char key[16] = {0x12, 0x34, 0x56, 0x78, 0x9A, 0xBC, 0xDE, 0xEF, 0xFE, 0xDC, 0xBA, 0x98, 0x76, 0x54, 0x32, 0x10}; // 密钥unsigned char ciphertext;des_encrypt(&plaintext, key, &ciphertext);printf("明文: 0x%02X\n", plaintext);printf("密钥: ");for (unsigned char i = 0; i < 16; i++)printf("%02X ", key[i]);}printf("\n");printf("密文: 0x%02X\n", ciphertext);return 0;```上述代码实现了DES算法的加密功能。
des密码算法实验c语言

des密码算法实验c语言以下是一个使用C语言实现DES密码算法的简单实验示例:```c#include <stdio.h>#include <stdlib.h>#include <string.h>#include <openssl/des.h>int main() {// 输入明文char plaintext[8] = "12345678";// 初始化DES密钥DES_cblock key = {0x01, 0x23, 0x45, 0x67, 0x89, 0xAB, 0xCD, 0xEF};DES_key_schedule keysched;DES_set_key_unchecked(&key, &keysched);// 加密unsigned char ciphertext[8];DES_cblock ivec = {0}; // 初始化向量DES_ncbc_encrypt(plaintext, ciphertext, sizeof(plaintext),&keysched, &ivec, DES_ENCRYPT);// 输出密文printf("Ciphertext: ");for (int i = 0; i < sizeof(plaintext); i++) {printf("%02X", ciphertext[i]);}printf("\n");// 解密unsigned char decryptedtext[8];memset(ivec, 0, sizeof(ivec)); // 重置初始化向量DES_ncbc_encrypt(ciphertext, decryptedtext, sizeof(plaintext), &keysched, &ivec, DES_DECRYPT);// 输出明文printf("Plaintext: ");for (int i = 0; i < sizeof(plaintext); i++) {printf("%c", decryptedtext[i]);}printf("\n");return 0;}```在这个实验中,我们使用了OpenSSL库中的DES函数来实现DES 密码算法。
DES_加密解密算法的C++实现--实验报告

DES_加密解密算法的C++实现--实验报告1实验⼀1、实验题⽬利⽤C/C++编程实现DES加密算法或MD5加密算法。
我选择的是⽤C++语⾔实现DES的加密算法。
2、实验⽬的通过编码实现DES算法或MD5算法,深⼊掌握算法的加密原理,理解其实际应⽤价值,同时要求⽤C/C++语⾔实现该算法,让我们从底层开始熟悉该算法的实现过程3、实验环境操作系统:WIN7旗舰版开发⼯具:Visual Studio 2010旗舰版开发语⾔:C++4、实验原理DES加密流程2如上图所⽰为DES的加密流程,其中主要包含初始置换,压缩换位1,压缩换位2,扩展置换,S盒置换,异或运算、终结置换等过程。
初始置换是按照初始置换表将64位明⽂重新排列次序扩展置换是将原32为数据扩展为48位数据,它主要由三个⽬的:1、产⽣与⼦密钥相同的长度2、提供更长的结果,使其在加密过程中可以被压缩3、产⽣雪崩效应,使得输⼊的⼀位将影响两个替换S盒置换是DES算法中最核⼼的内容,在DES中,只有S盒置换是⾮线性的,它⽐DES 中其他任何⼀步都提供更好的安全性终结置换与初始置换相对应,它们都不影响DES的安全性,主要⽬的是为了更容易将明⽂与密⽂数据⼀字节⼤⼩放⼊DES的f 算法中DES解密流程与加密流程基本相同,只不过在进⾏16轮迭代元算时,将⼦密钥⽣成的K的次序倒过来进⾏迭代运算5、实验过程记录在对DES算法有了清晰的认识后,编码过程中我将其分为⼏个关键部分分别进⾏编码,最后将整个过程按顺序执⾏,即可完成DES的加密,代码的主要⼏个函数如下:代码// : 定义控制台应⽤程序的⼊⼝点。
//#include "" #include "" #include #include #include using namespace std;//置换矩阵int IP_EX[64]= { 58, 50, 42, 34, 26, 18, 10, 2, 60, 52, 44, 36, 28, 20, 12, 4, 62, 54, 46, 38, 30, 22, 14, 6, 64, 5 6, 48, 40, 32, 24, 16, 8, 57, 49, 41, 33, 25, 17, 9, 1, 59, 51, 43, 35, 27, 19, 11, 3, 61, 53, 45, 37, 29, 21, 13,5, 63, 55, 47, 39, 31, 23, 15, 7};int IP_ANTEX[64]= { 40, 8, 48, 16, 56, 24, 64, 32, 39, 7, 47, 15, 55, 23, 63, 31, 38, 6, 46, 14, 54, 22, 62, 30, 37 , 5, 45, 13, 53,21, 61, 29, 36, 4, 44, 12, 52, 20, 60, 28 , 35, 3, 43, 11, 51, 19, 59, 27, 34, 2, 41, 10, 50, 18, 58, 26, 33, 1, 41, 9, 49, 17, 57, 25 };//扩展矩阵int EXTEND[48]= {32, 1, 2, 3, 4, 5, 4, 5, 6, 7, 8, 9,8, 9, 10, 11, 12, 13, 12, 13, 14, 15, 16, 17, 16, 17, 18, 19, 20, 21, 20, 21, 22, 23, 24, 25, 24, 25, 26, 27, 28, 29, 28, 29, 30, 31, 1, 2};//S盒int S[8][4][16]= { { {14, 4, 13, 1, 2, 15, 11, 8, 3, 10, 6, 12, 5, 9, 0, 7}, {0, 15, 7, 4, 14, 2, 13, 1, 10, 6, 12, 11, 9, 5, 3, 8}, {4, 1, 14, 8, 13, 6, 2, 11, 15, 12, 9, 7, 3, 10, 5, 0}, {15, 12, 8, 2, 4, 9, 1, 7, 5, 11, 3, 14, 10, 0, 6, 13}}, { {15, 1, 8, 14, 6, 11, 3, 4, 9, 7, 2, 13, 12, 0, 5, 10}, {3, 13, 4, 7, 15, 2, 8, 14, 12, 0, 1, 10, 6, 9, 11, 5 }, {0, 14, 7, 11, 10, 4, 13, 1, 5, 8, 12, 6, 9, 3, 2, 15 }, {13, 8, 1 0, 1, 3, 15, 4, 2, 11, 6, 7, 12, 0, 5, 14, 9} }, { {10, 0, 9, 14, 6, 3, 15, 5, 1, 13, 12, 7, 11, 4, 2, 8}, {13, 7, 0, 9, 3, 4, 6, 10, 2, 8, 5, 14, 12, 11, 15, 1}, {13, 6, 4, 9, 8, 15, 3, 0, 11, 1, 2, 12, 5, 10, 14, 7}, {1, 10, 13, 0, 6, 9, 8, 7, 4, 15, 14, 3, 11, 5, 2, 12} }, { { 7, 13, 14, 3, 0, 6, 9, 10, 1, 2, 8, 5, 11, 12, 4, 15}, {13, 8, 11, 5, 6, 15, 0, 3, 4, 7, 2, 12, 1, 10, 14, 9}, {10, 6, 9, 0, 12, 11, 7, 13, 15, 1, 3, 14, 5, 2, 8, 4}, {3, 15, 0, 6, 10, 1, 13, 8, 9, 4, 5, 11, 12, 7, 2, 14} }, { {2, 12, 4, 1, 7, 10, 11, 6, 8, 5, 3, 15, 13, 0, 14, 9}, {14, 11, 2, 12, 4, 7, 13, 1, 5, 0, 15, 10, 3, 9, 8, 6}, {4, 2, 1, 11, 10, 13, 7, 8, 15, 9, 12, 5, 6, 3, 0, 14}, {11, 8, 12, 7, 1, 14, 2, 13, 6, 15, 0, 9, 10, 4, 5, 3} },{ {12, 1, 10, 15, 9, 2, 6, 8, 0, 13, 3, 4, 14, 7, 5, 11}, {10, 15, 4, 2, 7, 12, 9, 5, 6, 1, 1 3, 14, 0, 11, 3, 8}, {9, 14, 15, 5, 2, 8, 12, 3, 7, 0, 4, 10, 1, 13, 11, 6}, {4, 3, 2, 12, 9, 5, 15, 10, 11, 14, 1, 7, 6, 0, 8, 13}}, { {4, 11, 2, 14, 15, 0, 8, 13, 3, 12, 9, 7, 5, 10, 6, 1}, {13, 0, 11, 7, 4, 9, 1, 10, 14, 3, 5, 12, 2, 15, 8, 6}, {1, 4, 11, 13, 12, 3, 7, 14, 10, 15, 6, 8, 0, 5, 9, 2}, {6, 11, 13, 8, 1, 4, 10, 7, 9, 5, 0, 15, 14, 2, 3, 12}}, { {13, 2, 8, 4, 6, 15, 11, 1, 10, 9, 3, 1 4, 5, 0, 12, 7}, {1, 15, 13, 8, 10, 3, 7, 4, 12, 5, 6, 11, 0, 14, 9, 2}, {7, 11, 4, 1, 9, 12, 14, 2, 0, 6, 10, 13, 15, 3, 5, 8}, {2, 1, 14, 7, 4, 10, 8, 13, 15, 12, 9, 0, 3, 5, 6, 11}}};int DIREX[32]= { 16, 7, 20, 21, 29, 12, 28, 17, 1, 15, 23, 26, 5, 18, 31, 10, 2, 8, 24, 14, 32, 27, 3, 9, 19, 13, 30, 6, 22, 11, 4, 25 };//左移移位表int MOVELEFT[16]= { 1,1,2,2,2,2,2,2, 1,2,2,2,2,2,2,1};//压缩换位表2int CutEX[48]= { 14, 17, 11, 24, 1, 5,3, 28, 15, 6, 21, 10, 23, 19, 12, 4, 26, 8, 16, 7, 27, 20, 13, 2, 41, 52, 31, 37, 47, 55, 30, 40, 51, 45, 33, 48, 44, 49, 39, 56, 34, 53, 46, 42, 50, 36, 29, 32};typedef char ElemType;ElemType subsec[16][48];//Byte转bitint ByteToBit(ElemType ch,ElemType bit[8]) {for(int index = 7;index >= 0;index--) {bit[index] = (ch>>index)&1; //cout<<(int)bit[index]; }return 0; }//bit转Byteint BitToByte(ElemType bit[8],ElemType &ch) { ElemType tempch=0; Ele mType tempbit[8]; for(int i=0;i<8;i++) {tempbit[i]=bit[i];}tempbit[7]=0;for(int index = 7;index >=0;index--){tempch=tempch|(tempbit[index]<<(index)); } ch=tempch;//cout<<(char)tempch<return 0;}//按64位分⼀组void Get64Bit(ElemType ch[8],ElemType bit[64]) { ElemType temp[8]; i nt count=0; for(int i=0;i<8;i++) { ByteToBit(ch[i],temp); for (int j=0;j<8;j++) { bit[count*8+j]=temp[7-j];}count++;}}//初始置换void InitialEX(ElemType Inorder[64],ElemType Disorder[64]) { for(int i= 0;i<64;i++) { Disorder[i]=Inorder[IP_EX[i]-1]; }}//逆置换void AntiEx(ElemType Disorder[64]) { ElemType temp[64]; for(int i=0; i<64;i++) {temp[i]=Disorder[i];}for(int i=0;i<64;i++) { Disorder[i]=temp[IP_ANTEX[i]-1];}}//扩展置换void ExpandEX(ElemType RightMsg[32],ElemType ExpandMsg[48]) {for(int i=0;i<48;i++) { ExpandMsg[i]=RightMsg[EXTEND[i]-1];}}//16轮加密迭代void MoveLeft(ElemType C[28],ElemType D[28],ElemType L0[32],ElemType R0[32 ]) { ElemType Secret[48]; //⼦密钥ElemType Result[48]; //每轮异或结果ElemType Sout[32];//每轮S盒输出ElemType DirOut[32]; //直接置换输出ElemType RResult[32]; ElemType LResult[32]; ElemType ExpandMsg[48];ElemType temp[32]; for(int i=0;i<32;i++) { LResult[i]=L0[i];RResult[i]=R0[i];}for(int i=0;i<16;i++) { if(MOVELEFT[i]==1) { for(int j= 0;j<27;j++) { C[i]=C[i+1];}C[27]=0;} else { for(int j=0;j<26;j++) {C[i]=C[i+2]; }C[26]=0; C[27]=0;}ExpandEX(RResult,ExpandMsg); GetCD48(C,D,Secret);for(int j=0;j<48;j++){subsec[15-i][j]=Secret[j]; //获取界⾯的⼦密钥}XOR(ExpandMsg,Secret,Result); //S盒置换getSOut(Result,Sout); //直接置换DirExchange(Sout,DirOut); //与L进⾏异或XORLR(DirOut,LResult,temp); for(int i=0;i<32;i++) { LResu lt[i]=RResult[i];}for(int i=0;i<32;i++) {RResult[i]=temp[i]; }for(int i=0;i<32;i++) { L0[i]=LResult[i]; R0[i]=RResult [i];}}/*cout<<"zuo"<}}cout<<"右边"<{cout<}}*/LResult[j]=RResult[j];}for(int j=0;j<32;j++) { RResult[j]=temp[j]; }。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
DES的C语言实现#include<stdio.h>Intasciim[8],m_16[16],m[64],asciik[8],k_16[16],k[64],m_ip[64],l[32],r[32],k_pc1[56],c[28],d[28],cd[5 6],k_pc2[48],re[48],sh[32],tempr[32],m0[64],m00[64],res[8];int type;int ip[64]={58,50,42,34,26,18,10,2,60,52,44,36,28,20,12,4,62,54,46,38,30,22,14,6,64,56,48,40,32,24,16,8,57,49,41,33,25,17,9,1,59,51,43,35,27,19,11,3,61,53,45,37,29,21,13,5,63,55,47,39,31,23,15,7};int ip_1[64]={40,8,48,16,56,24,64,32,39,7,47,15,55,23,63,31,38,6,46,14,54,22,62,30,37,5,45,13,53,21,61,29,36,4,44,12,52,20,60,28,35,3,43,11,51,19,59,27,34,2,42,10,50,18,58,26,33,1,41,9,49,17,57,25};int pc_1[56]={57,49,41,33,25,17,9,1,58,50,42,34,26,18,10,2,59,51,43,35,27,19,11,3,60,52,44,36,63,55,47,39,31,23,15,7,62,54,46,38,30,22,14,6,61,53,45,37,29,21,13,5,28,20,12,4};int pc_2[48]={14,17,11,24,1,5,3,28,15,6,21,10,23,19,12,4,26,8,16,7,27,20,13,2,41,52,31,37,47,55,30,40,51,45,33,48,44,49,39,56,34,53,46,42,50,36,29,32};int exe[48]={32,1,2,3,4,5,4,5,6,7,8,9,8,9,10,11,12,13,12,13,14,15,16,17,16,17,18,19,20,21,20,21,22,23,24,25,24,25,26,27,28,29,28,29,30,31,32,1};int p[32]={16,7,20,21,29,12,28,17,1,15,23,26,5,18,31,10,2,8,24,14,32,27,3,9,19,13,30,6,22,11,4,25};int s[8][4][16]={{{14,4,13,1,2,15,11,8,3,10,6,12,5,9,0,7},{0,15,7,4,14,2,13,1,10,6,12,11,9,5,3,8},{4,1,14,8,13,6,2,11,15,12,9,7,3,10,5,0},{15,12,8,2,4,9,1,7,5,11,3,14,10,0,6,13}},{{15,1,8,14,6,11,3,4,9,7,2,13,12,0,5,10},{3,13,4,7,15,2,8,14,12,0,1,10,6,9,11,5},{0,14,7,11,10,4,13,1,5,8,12,6,9,3,2,15},{13,8,10,1,3,15,4,2,11,6,7,12,0,5,14,9}},{{10,0,9,14,6,3,15,5,1,13,12,7,11,4,2,8},{13,7,0,9,3,4,6,10,2,8,5,14,12,11,15,1},{13,6,4,9,8,15,3,0,11,1,2,12,5,10,14,7},{1,10,13,0,6,9,8,7,4,15,14,3,11,5,2,12}},{{7,13,14,3,0,6,9,10,1,2,8,5,11,12,4,15},{13,8,11,5,6,15,0,3,4,7,2,12,1,10,14,9},{10,6,9,0,12,11,7,13,15,1,3,14,5,2,8,4},{3,15,0,6,10,1,13,8,9,4,5,11,12,7,2,14}},{{2,12,4,1,7,10,11,6,8,5,3,15,13,0,14,9},{14,11,2,12,4,7,13,1,5,0,15,10,3,9,8,6},{4,2,1,11,10,13,7,8,15,9,12,5,6,3,0,14},{11,8,12,7,1,14,2,13,6,15,0,9,10,4,5,3}},{{12,1,10,15,9,2,6,8,0,13,3,4,14,7,5,11},{10,15,4,2,7,12,9,5,6,1,13,14,0,11,3,8},{9,14,15,5,2,8,12,3,7,0,4,10,1,13,11,6},{4,3,2,12,9,5,15,10,11,14,1,7,6,0,8,13}},{{4,11,2,14,15,0,8,13,3,12,9,7,5,10,6,1},{13,0,11,7,4,9,1,10,14,3,5,12,2,15,8,6},{1,4,11,13,12,3,7,14,10,15,6,8,0,5,9,2},{6,11,13,8,1,4,10,7,9,5,0,15,14,2,3,12}},{{13,2,8,4,6,15,11,1,10,9,3,14,5,0,12,7},{1,15,13,8,10,3,7,4,12,5,6,11,0,14,9,2},{7,11,4,1,9,12,14,2,0,6,10,13,15,3,5,8},{2,1,14,7,4,10,8,13,15,12,9,0,3,5,6,11}}};int print(int *jg,int a,int b)// 输出函数,第一个参数是要输出的数组,第二个参数数组的长度,第三个参数是每行数的个数{int i;for(i=0;i<a;i++){if(i%b==0){printf("\n");}printf("%d",jg[i]);}return 1;}int ascii_to_erjinzhi(int *ascii,int *jg)//这是将8位的ascii矩阵转换成为64位二进制的jg矩阵{int i,j,tempb;for(i=0,j=7;i<8;i++){tempb=(int) ascii[i];while(tempb>1){jg[j]=(int) (tempb%2);tempb=(int) (tempb/2);j--;}switch(tempb){case 0:jg[j]=0;break;case 1:jg[j]=1;break;}while(j%8!=0){j--;jg[j]=0;}j=(i+1)*8+7;}return 1;}int input_16(int *ja,int *jb,int *jc)//以16进制的形式输入,ja是16进制的矩阵,jb是16进制矩阵转换成8位的十进制矩阵,//jc是再将它转换成64位的二进制矩阵{int i,j;for(i=0;i<16;i++){ja[i]=getchar();if(ja[i]==' '||ja[i]=='\n'){i--;}}for(i=0;i<16;i++){if(i%2==0&&i!=0){printf("H ");}printf("%c",ja[i]);}for(i=0;i<16;i++){if(ja[i]<='9'){ja[i]=ja[i]-48;}else if(ja[i]>='A'&&ja[i]<='F'){ja[i]=ja[i]-55;}else{ja[i]=ja[i]-87;}}for(i=0,j=0;i<8;i++,j=j+2){jb[i]=ja[j]*16+ja[j+1];}ascii_to_erjinzhi(jb,jc);//printf("\n二进制表示是:");//print(jc,64,8);return 1;}int shuziinput(int *ja,int *jb)//以ascii码的数字的形式输入{int i;for(i=0;i<8;i++){scanf("%d",&ja[i]);}ascii_to_erjinzhi(ja,jb);return 1;}int zifuinput(int *ja,int *jb)//以ascii码的字符形式输入{int i;for(i=0;i<8;i++){ja[i]=getchar();if(ja[i]==' '||ja[i]=='\n')//如果没有换行符在密钥输入的时候密钥初始值就是10{ //如果写的是换行时break是那么密钥不能输入,直接出结果。
如果先调用密钥输入明文直接出结果i--;}else{continue;}}for(i=0;i<8;i++){printf("%d ",ja[i]);}ascii_to_erjinzhi(ja,jb);// printf("\n二进制表示是:");// print(jb,64,8);getchar();return 1;}int input(int signal)//输入明文或者密文函数{printf("请选择输入方式(ASCII码字符形式输入1,ASCII码数字形式输入2,十六进制形式输入3)");scanf("%d",&type);if(signal==1){printf("请输入明文:\n");}else if(signal==2){printf("请输入密文:\n");}if(type==1){zifuinput(asciim,m);}else if(type==2){shuziinput(asciim,m);//printf("chenggong");}else{input_16(m_16,asciim,m);}return 1;}int miyaoinput()//密钥的输入{printf("\n请输入密钥:\n");if(type==1){zifuinput(asciik,k);}else if(type==2){shuziinput(asciik,k);}else{input_16(k_16,asciik,k);}return 1;}int ipzhihuan()//IP置换{int i,j;for(i=0;i<64;i++){j=(ip[i]-1);m_ip[i]=m[j];}// printf("\nIP置换后:");// print(m_ip,64,8);return 1;}int ipnizhihuan()//IP逆置换{int i,j;//print(m0,64,8);for(i=0;i<64;i++){j=(ip_1[i]-1);m00[i]=m0[j];}// printf("\n nizhihuanhou\n");// print(m00,64,8);return 1;}int pc1zhihuan()//PC1置换{int i,j;for(i=0;i<56;i++){j=(pc_1[i]-1);k_pc1[i]=k[j];}// printf("\npc_1置换后的结果是:"); // print(k_pc1,56,7);return 1;}int pc2zhihuan(int *ja,int *jb)//PC2置换{int i,j;for(i=0;i<48;i++){j=(pc_2[i]-1);jb[i]=ja[j];}// printf("\npc_2置换后的结果是:"); // print(jb,48,6);return 1;}int pzhihuan(int *ja,int *jb)//P置换{int i,j;for(i=0;i<32;i++){j=(p[i]-1);jb[i]=ja[j];}//printf("\np置换后的结果是:"); // print(jb,32,8);return 1;}int initlr(int *ja)//初始化l和r{int i;for(i=0;i<32;i++){l[i]=ja[i];}for(i=32;i<64;i++){r[i-32]=ja[i];}//printf("\nl是:");// print(l,32,8);// printf("\nr是:");// print(r,32,8);return 1;}int initcd(int *ja)//初始化C D{int i;for(i=0;i<28;i++){c[i]=ja[i];}for(i=28;i<56;i++){d[i-28]=ja[i];}//printf("\nc是:");/////print(c,28,7);//printf("\nd是:");//print(d,28,7);return 1;}int zuoyi1(int *ja)//以下都是左移{int i,temp[28];//printf("\n左移一位前的结果:"); // print(ja,28,7);temp[27]=ja[0];for(i=1;i<28;i++){temp[i-1]=ja[i];}for(i=0;i<28;i++){ja[i]=temp[i];}//printf("\n左移一位后的结果:"); // print(ja,28,7);return 1;}int youyi1(int *ja){int i,temp[28];//printf("\n右移一位之前:\n");//print(ja,28,7);temp[0]=ja[27];for(i=1;i<28;i++){temp[i]=ja[i-1];}for(i=0;i<28;i++){ja[i]=temp[i];}//printf("\n右移一位后的结果:");//print(ja,28,7);return 1;}int zuoyi2(int *ja){int i,temp[28];//printf("\n左移两位前的结果:");//print(ja,28,7);temp[26]=ja[0];temp[27]=ja[1];for(i=0;i<26;i++){temp[i]=ja[i+2];}for(i=0;i<28;i++){ja[i]=temp[i];}//printf("\n左移两位后的结果:");//print(ja,28,7);return 1;}int youyi2(int *ja){int i,temp[28];//printf("\n右移两位前的结果:");//print(ja,28,7);temp[0]=ja[26];temp[1]=ja[27];for(i=2;i<28;i++){temp[i]=ja[i-2];}for(i=0;i<28;i++){ja[i]=temp[i];}//printf("\n右移两位后的结果:");//print(ja,28,7);return 1;}int exetent(int *ja,int *jb)//E膨胀{int i,k;for(i=0;i<48;i++){k=(exe[i]-1);jb[i]=ja[k];}// printf("\nE膨胀后的结果是:");//print(jb,48,6);return 1;}int yihuo48(int *ja,int *jb)//48位异或{int i;for(i=0;i<48;i++){ja[i]=(ja[i]^jb[i]);}// printf("\n异或后的结果是:");//print(ja,48,6);return 1;}int yihuo32(int *ja,int *jb){int i;for(i=0;i<32;i++){ja[i]=(ja[i]^jb[i]);}// printf("\n异或后的结果是:");//print(ja,32,8);return 1;}int shzhihuan(int *ja,int *jb)//S盒置换{int i,j,a,b,temp;for(j=0;j<8;j++){i=j*6;a=ja[i]*2+ja[i+5]*1;b=ja[i+1]*8+ja[i+2]*4+ja[i+3]*2+ja[i+4]*1;temp=s[j][a][b];i=j*4+3;while(temp>1){jb[i]=(int) (temp%2);temp=(int) (temp/2);i--;}switch(temp){case 0:jb[i]=0;break;case 1:jb[i]=1;break;}while(i%4!=0){i--;jb[i]=0;}}//printf("\n经过s盒置换后结果是:");//print(jb,32,8);return 1;}int zuhecd(int *ja,int *jb)//将C D组合{int i;for(i=0;i<28;i++){cd[i]=ja[i];cd[i+28]=jb[i];}//print(cd,56,7);return 1;}int zhuanhuan(int *ja,int *jb)//将32位的jb赋值给ja {int i;for(i=0;i<32;i++){ja[i]=jb[i];}return 1;}int zuhe64(int *ja,int *jb,int *jc){int i;for(i=0;i<32;i++){jc[i]=ja[i];jc[i+32]=jb[i];}return 1;}int erjinzhi_to_ascii(int *jz,int *jg)//二进制转换成ASCII码{int i,j;for(i=0;i<8;i++){j=i*8;jg[i]=(jz[j]*128+jz[j+1]*64+jz[j+2]*32+jz[j+3]*16+jz[j+4]*8+jz[j+5]*4+jz[j+6]*2+jz[j+7]*1);}return 1;}int main(){int i,signal;printf("DES 加密与解密\t (加密输入1,解密输入2)\n");scanf("%d",&signal);input(signal);miyaoinput();ipzhihuan();initlr(m_ip);pc1zhihuan();initcd(k_pc1);for(i=0;i<16;i++){if(i>0){initcd(cd);}if(signal==1){if(i==0||i==1||i==8||i==15){zuoyi1(c);zuoyi1(d);}else{zuoyi2(c);zuoyi2(d);}}else if(signal==2){if(i==1||i==8||i==15){youyi1(c);youyi1(d);}else if(i==0){zuhecd(c,d);pc2zhihuan(cd,k_pc2);zhuanhuan(tempr,r);exetent(r,re);yihuo48(re,k_pc2);shzhihuan(re,sh);pzhihuan(sh,r);yihuo32(r,l);zhuanhuan(l,tempr);continue;}else{youyi2(c);youyi2(d);}}zuhecd(c,d);pc2zhihuan(cd,k_pc2);zhuanhuan(tempr,r);exetent(r,re);yihuo48(re,k_pc2);shzhihuan(re,sh);pzhihuan(sh,r);yihuo32(r,l);zhuanhuan(l,tempr);}zhuanhuan(tempr,l);zhuanhuan(l,r);zhuanhuan(r,tempr);zuhe64(l,r,m0);ipnizhihuan();erjinzhi_to_ascii(m00,res);printf("\n结果是:\n");for(i=0;i<8;i++){printf("%d ",res[i]);}printf("\n");for(i=0;i<8;i++){printf("%c ",res[i]);} Retern 1;。
