Chapter2DMD
进行性肌营养不良症课件

目录
• 疾病概述 • 临床表现及病情发展 • 诊断及鉴别诊断 • 治疗及干预措施 • 预防及控制策略 • 研究进展和未来展望
01
疾病概述
Chapter
定义和分类
定义
进行性肌营养不良症(PMD)是一类缓慢进行性 加重的肌肉萎缩、无力,直至最终失去运动功能的 神经肌肉疾病。
分类
主要表现为四肢近端无力、肌肉萎缩等, 但起病年龄较早,病情进展较快,常伴有 肺部感染等症状。
多发性肌炎
周围神经病
是一种自身免疫性疾病,主要表现为四肢 近端无力、肌肉疼痛、皮疹等症状,但肌 肉萎缩不明显,且常伴有皮疹等症状。
主要表现为四肢远端无力、肌肉萎缩等, 但起病年龄较早,病情进展较快,常伴有 感觉异常等症状。
产前诊断
通过基因检测技术,对怀孕期间的胎儿进行诊断,确认是否有进行性肌营养不 良症,以便尽早采取众意识
通过宣传和教育,提高公众对进行性肌营养不良症的认识和关注,促进早期发现 和治疗。
建立支持网络
为患者及其家庭提供心理、社会和医疗支持,建立互助网络,帮助他们更好地应 对疾病。
临床病史
体格检查
实验室检查
电生理检查
肌肉活检
询问患者的肌肉无力 、萎缩等症状出现的 时间、发展速度及伴 随症状等。
检测血清肌酶谱、肌 红蛋白等指标,评估 肌肉损伤程度。
通过取部分肌肉组织 进行病理学检查,确 诊进行性肌营养不良 症。
鉴别诊断
先天性肌营养不良
脊髓性肌萎缩症
与进行性肌营养不良相似,但起病年龄较 早,病情进展较慢,可伴有智力低下、心 脏异常等症状。
Chapter
早期表现
走路延迟
进行性肌营养不良症患者在早期 可能会出现走路延迟,相较于同 龄儿童,可能需要更长时间才能
2024届高考英语二轮复习阅读理解说明文解题技巧课件

benefits to the things you value. In the final chapter of part one, I’ll guide you through carrying out your own digital declutter. In doing so, I’ll
draw on an experiment I ran in 2018 in which over 1,600 people agreed to perform a digital declutter. You’ll hear these participants’ stories and learn what strategies worked well for them, and what traps they encountered that you
2023 C卷
语篇结构
para.1:
介绍书的写作目的
para.2-4:
介绍书的第一章节:
para.5
介绍书的第二章节:
总分总 总分
巧点拨1:同义替换表达
Step3:仔细阅读题干,精准定位信息 Step4:甄别选项,有效运用技巧
The goal of this book is to make the case for digital minimalism....and then to teach you how to adopt this philosophy if you decide it’s right for you.
28. What is the book aimed at? A. Teaching critical thinking skills. C. Solving philosophical problems.
湖北省沙市中学2024届高三上学期10月月考英语

2023—2024学年度上学期2021级10月月考英语试卷命题人:朱茂林审题人:Nancy第一部分听力(共两节,满分30分)该部分分为第一、第二两节,注意:回答听力部分时,请先将答案标在试卷上。
听力部分结束前,你将有两分钟的时间将你的答案转涂到答题卡上。
第一节(共5小题;每小题1.5分,满分7.5分)听下面5段对话。
每段对话后有一个小题,从题中所给的A、B、C三个选项中选出最佳选项。
听完每段对话后,你都有10秒钟的时间来回答有关小题和阅读下一小题。
每段对话仅读一遍。
1.What does the man plan to do for the summer vacation?A.Stay in London. B.Go sightseeing. C.See his parents.2.Why did the woman change the reservation?A.She canceled the party. B.She got the date wrong. C.She put off her plan. 3.What happened to the man?A.He found a car key. B.He lost his car key. C.He got his key ring. 4.What are the speakers talking about?A.The coming tests. B.The stress in life. C.The learning methods. 5.What is the weather like now?A.Rainy. B.Stormy. C.Fine.第二节(共15小题;每小题1.5分,满分22.5分)听下面5段对话或独白。
每段对话或独白后有几个小题,从题中所给的A、B、C三个项中选出最佳选项。
听每段对话或独白前,你将有时间阅读各个小题,每小题5秒钟;听后,各小题将给出5秒钟的作答时间。
爱情与金钱(中英对照)_书虫系列

目录1 Chapter (2)2 Chapter (6)3 Chapter (16)4 Chapter (24)5 Chapter (32)6 Chapter (41)7 Chapter (47)Love Or Money爱情与金钱1 Chapter1The Clarkson family lived in the country near Cambridge,about half a mile from the nearest village and about a mile from the river.They had a big,old house with a beautiful garden,a lot of flowers and many old.trees.克拉克森家住在剑桥附近的乡下,离最近的村庄约有半英里路,距离河有1英里左右。
他们有幢大而古老带有美丽花园的房子,花园里有许多花和许多古树。
One Thursday morning in July,Jackie came in from the garden.She was a tall,fat woman,thirty years old.It was the hottest day of the year,but she wore a warm brown skirt and yellow shirt.She went into the kitchen to get a drink of water.Just then the phone rang.7月的一个星期四早上,杰基从花园进了屋。
她是个高大,肥胖,30来岁的女人。
这是一年中最热的日子,而她却穿着暖色调的黄色衬衫和棕色裙子。
她走进厨房去喝水,这时电话响了。
'Cambridge 1379,'Jackie said.“剑桥1379号,”杰基说。
'Hello.This is Diane.I want to talk to Mother.'“你好!我是黛安娜。
Quantum Computing for Computer Scientists

More informationQuantum Computing for Computer ScientistsThe multidisciplinaryfield of quantum computing strives to exploit someof the uncanny aspects of quantum mechanics to expand our computa-tional horizons.Quantum Computing for Computer Scientists takes read-ers on a tour of this fascinating area of cutting-edge research.Writtenin an accessible yet rigorous fashion,this book employs ideas and tech-niques familiar to every student of computer science.The reader is notexpected to have any advanced mathematics or physics background.Af-ter presenting the necessary prerequisites,the material is organized tolook at different aspects of quantum computing from the specific stand-point of computer science.There are chapters on computer architecture,algorithms,programming languages,theoretical computer science,cryp-tography,information theory,and hardware.The text has step-by-stepexamples,more than two hundred exercises with solutions,and program-ming drills that bring the ideas of quantum computing alive for today’scomputer science students and researchers.Noson S.Yanofsky,PhD,is an Associate Professor in the Departmentof Computer and Information Science at Brooklyn College,City Univer-sity of New York and at the PhD Program in Computer Science at TheGraduate Center of CUNY.Mirco A.Mannucci,PhD,is the founder and CEO of HoloMathics,LLC,a research and development company with a focus on innovative mathe-matical modeling.He also serves as Adjunct Professor of Computer Sci-ence at George Mason University and the University of Maryland.QUANTUM COMPUTING FORCOMPUTER SCIENTISTSNoson S.YanofskyBrooklyn College,City University of New YorkandMirco A.MannucciHoloMathics,LLCMore informationMore informationcambridge university pressCambridge,New York,Melbourne,Madrid,Cape Town,Singapore,S˜ao Paulo,DelhiCambridge University Press32Avenue of the Americas,New York,NY10013-2473,USAInformation on this title:/9780521879965C Noson S.Yanofsky and Mirco A.Mannucci2008This publication is in copyright.Subject to statutory exceptionand to the provisions of relevant collective licensing agreements,no reproduction of any part may take place withoutthe written permission of Cambridge University Press.First published2008Printed in the United States of AmericaA catalog record for this publication is available from the British Library.Library of Congress Cataloging in Publication dataYanofsky,Noson S.,1967–Quantum computing for computer scientists/Noson S.Yanofsky andMirco A.Mannucci.p.cm.Includes bibliographical references and index.ISBN978-0-521-87996-5(hardback)1.Quantum computers.I.Mannucci,Mirco A.,1960–II.Title.QA76.889.Y352008004.1–dc222008020507ISBN978-0-521-879965hardbackCambridge University Press has no responsibility forthe persistence or accuracy of URLs for external orthird-party Internet Web sites referred to in this publicationand does not guarantee that any content on suchWeb sites is,or will remain,accurate or appropriate.More informationDedicated toMoishe and Sharon Yanofskyandto the memory ofLuigi and Antonietta MannucciWisdom is one thing:to know the tho u ght by which all things are directed thro u gh allthings.˜Heraclitu s of Ephe s u s(535–475B C E)a s quoted in Dio g ene s Laertiu s’sLives and Opinions of Eminent PhilosophersBook IX,1. More informationMore informationContentsPreface xi1Complex Numbers71.1Basic Definitions81.2The Algebra of Complex Numbers101.3The Geometry of Complex Numbers152Complex Vector Spaces292.1C n as the Primary Example302.2Definitions,Properties,and Examples342.3Basis and Dimension452.4Inner Products and Hilbert Spaces532.5Eigenvalues and Eigenvectors602.6Hermitian and Unitary Matrices622.7Tensor Product of Vector Spaces663The Leap from Classical to Quantum743.1Classical Deterministic Systems743.2Probabilistic Systems793.3Quantum Systems883.4Assembling Systems974Basic Quantum Theory1034.1Quantum States1034.2Observables1154.3Measuring1264.4Dynamics1294.5Assembling Quantum Systems1325Architecture1385.1Bits and Qubits138viiMore informationviii Contents5.2Classical Gates1445.3Reversible Gates1515.4Quantum Gates1586Algorithms1706.1Deutsch’s Algorithm1716.2The Deutsch–Jozsa Algorithm1796.3Simon’s Periodicity Algorithm1876.4Grover’s Search Algorithm1956.5Shor’s Factoring Algorithm2047Programming Languages2207.1Programming in a Quantum World2207.2Quantum Assembly Programming2217.3Toward Higher-Level Quantum Programming2307.4Quantum Computation Before Quantum Computers2378Theoretical Computer Science2398.1Deterministic and Nondeterministic Computations2398.2Probabilistic Computations2468.3Quantum Computations2519Cryptography2629.1Classical Cryptography2629.2Quantum Key Exchange I:The BB84Protocol2689.3Quantum Key Exchange II:The B92Protocol2739.4Quantum Key Exchange III:The EPR Protocol2759.5Quantum Teleportation27710Information Theory28410.1Classical Information and Shannon Entropy28410.2Quantum Information and von Neumann Entropy28810.3Classical and Quantum Data Compression29510.4Error-Correcting Codes30211Hardware30511.1Quantum Hardware:Goals and Challenges30611.2Implementing a Quantum Computer I:Ion Traps31111.3Implementing a Quantum Computer II:Linear Optics31311.4Implementing a Quantum Computer III:NMRand Superconductors31511.5Future of Quantum Ware316Appendix A Historical Bibliography of Quantum Computing319 by Jill CirasellaA.1Reading Scientific Articles319A.2Models of Computation320More informationContents ixA.3Quantum Gates321A.4Quantum Algorithms and Implementations321A.5Quantum Cryptography323A.6Quantum Information323A.7More Milestones?324Appendix B Answers to Selected Exercises325Appendix C Quantum Computing Experiments with MATLAB351C.1Playing with Matlab351C.2Complex Numbers and Matrices351C.3Quantum Computations354Appendix D Keeping Abreast of Quantum News:QuantumComputing on the Web and in the Literature357by Jill CirasellaD.1Keeping Abreast of Popular News357D.2Keeping Abreast of Scientific Literature358D.3The Best Way to Stay Abreast?359Appendix E Selected Topics for Student Presentations360E.1Complex Numbers361E.2Complex Vector Spaces362E.3The Leap from Classical to Quantum363E.4Basic Quantum Theory364E.5Architecture365E.6Algorithms366E.7Programming Languages368E.8Theoretical Computer Science369E.9Cryptography370E.10Information Theory370E.11Hardware371Bibliography373Index381More informationPrefaceQuantum computing is a fascinating newfield at the intersection of computer sci-ence,mathematics,and physics,which strives to harness some of the uncanny as-pects of quantum mechanics to broaden our computational horizons.This bookpresents some of the most exciting and interesting topics in quantum computing.Along the way,there will be some amazing facts about the universe in which we liveand about the very notions of information and computation.The text you hold in your hands has a distinctflavor from most of the other cur-rently available books on quantum computing.First and foremost,we do not assumethat our reader has much of a mathematics or physics background.This book shouldbe readable by anyone who is in or beyond their second year in a computer scienceprogram.We have written this book specifically with computer scientists in mind,and tailored it accordingly:we assume a bare minimum of mathematical sophistica-tion,afirst course in discrete structures,and a healthy level of curiosity.Because thistext was written specifically for computer people,in addition to the many exercisesthroughout the text,we added many programming drills.These are a hands-on,funway of learning the material presented and getting a real feel for the subject.The calculus-phobic reader will be happy to learn that derivatives and integrals are virtually absent from our text.Quite simply,we avoid differentiation,integra-tion,and all higher mathematics by carefully selecting only those topics that arecritical to a basic introduction to quantum computing.Because we are focusing onthe fundamentals of quantum computing,we can restrict ourselves to thefinite-dimensional mathematics that is required.This turns out to be not much more thanmanipulating vectors and matrices with complex entries.Surprisingly enough,thelion’s share of quantum computing can be done without the intricacies of advancedmathematics.Nevertheless,we hasten to stress that this is a technical textbook.We are not writing a popular science book,nor do we substitute hand waving for rigor or math-ematical precision.Most other texts in thefield present a primer on quantum mechanics in all its glory.Many assume some knowledge of classical mechanics.We do not make theseassumptions.We only discuss what is needed for a basic understanding of quantumxiMore informationxii Prefacecomputing as afield of research in its own right,although we cite sources for learningmore about advanced topics.There are some who consider quantum computing to be solely within the do-main of physics.Others think of the subject as purely mathematical.We stress thecomputer science aspect of quantum computing.It is not our intention for this book to be the definitive treatment of quantum computing.There are a few topics that we do not even touch,and there are severalothers that we approach briefly,not exhaustively.As of this writing,the bible ofquantum computing is Nielsen and Chuang’s magnificent Quantum Computing andQuantum Information(2000).Their book contains almost everything known aboutquantum computing at the time of its publication.We would like to think of ourbook as a usefulfirst step that can prepare the reader for that text.FEATURESThis book is almost entirely self-contained.We do not demand that the reader comearmed with a large toolbox of skills.Even the subject of complex numbers,which istaught in high school,is given a fairly comprehensive review.The book contains many solved problems and easy-to-understand descriptions.We do not merely present the theory;rather,we explain it and go through severalexamples.The book also contains many exercises,which we strongly recommendthe serious reader should attempt to solve.There is no substitute for rolling up one’ssleeves and doing some work!We have also incorporated plenty of programming drills throughout our text.These are hands-on exercises that can be carried out on your laptop to gain a betterunderstanding of the concepts presented here(they are also a great way of hav-ing fun).We hasten to point out that we are entirely language-agnostic.The stu-dent should write the programs in the language that feels most comfortable.Weare also paradigm-agnostic.If declarative programming is your favorite method,gofor it.If object-oriented programming is your game,use that.The programmingdrills build on one another.Functions created in one programming drill will be usedand modified in later drills.Furthermore,in Appendix C,we show how to makelittle quantum computing emulators with MATLAB or how to use a ready-madeone.(Our choice of MATLAB was dictated by the fact that it makes very easy-to-build,quick-and-dirty prototypes,thanks to its vast amount of built-in mathematicaltools.)This text appears to be thefirst to handle quantum programming languages in a significant way.Until now,there have been only research papers and a few surveyson the topic.Chapter7describes the basics of this expandingfield:perhaps some ofour readers will be inspired to contribute to quantum programming!This book also contains several appendices that are important for further study:Appendix A takes readers on a tour of major papers in quantum computing.This bibliographical essay was written by Jill Cirasella,Computational SciencesSpecialist at the Brooklyn College Library.In addition to having a master’s de-gree in library and information science,Jill has a master’s degree in logic,forwhich she wrote a thesis on classical and quantum graph algorithms.This dualbackground uniquely qualifies her to suggest and describe further readings.More informationPreface xiii Appendix B contains the answers to some of the exercises in the text.Othersolutions will also be found on the book’s Web page.We strongly urge studentsto do the exercises on their own and then check their answers against ours.Appendix C uses MATLAB,the popular mathematical environment and an es-tablished industry standard,to show how to carry out most of the mathematicaloperations described in this book.MATLAB has scores of routines for manip-ulating complex matrices:we briefly review the most useful ones and show howthe reader can quickly perform a few quantum computing experiments with al-most no effort,using the freely available MATLAB quantum emulator Quack.Appendix D,also by Jill Cirasella,describes how to use online resources to keepup with developments in quantum computing.Quantum computing is a fast-movingfield,and this appendix offers guidelines and tips forfinding relevantarticles and announcements.Appendix E is a list of possible topics for student presentations.We give briefdescriptions of different topics that a student might present before a class of hispeers.We also provide some hints about where to start looking for materials topresent.ORGANIZATIONThe book begins with two chapters of mathematical preliminaries.Chapter1con-tains the basics of complex numbers,and Chapter2deals with complex vectorspaces.Although much of Chapter1is currently taught in high school,we feel thata review is in order.Much of Chapter2will be known by students who have had acourse in linear algebra.We deliberately did not relegate these chapters to an ap-pendix at the end of the book because the mathematics is necessary to understandwhat is really going on.A reader who knows the material can safely skip thefirsttwo chapters.She might want to skim over these chapters and then return to themas a reference,using the index and the table of contents tofind specific topics.Chapter3is a gentle introduction to some of the ideas that will be encountered throughout the rest of the ing simple models and simple matrix multipli-cation,we demonstrate some of the fundamental concepts of quantum mechanics,which are then formally developed in Chapter4.From there,Chapter5presentssome of the basic architecture of quantum computing.Here one willfind the notionsof a qubit(a quantum generalization of a bit)and the quantum analog of logic gates.Once Chapter5is understood,readers can safely proceed to their choice of Chapters6through11.Each chapter takes its title from a typical course offered in acomputer science department.The chapters look at that subfield of quantum com-puting from the perspective of the given course.These chapters are almost totallyindependent of one another.We urge the readers to study the particular chapterthat corresponds to their favorite course.Learn topics that you likefirst.From thereproceed to other chapters.Figure0.1summarizes the dependencies of the chapters.One of the hardest topics tackled in this text is that of considering two quan-tum systems and combining them,or“entangled”quantum systems.This is donemathematically in Section2.7.It is further motivated in Section3.4and formallypresented in Section4.5.The reader might want to look at these sections together.xivPrefaceFigure 0.1.Chapter dependencies.There are many ways this book can be used as a text for a course.We urge instructors to find their own way.May we humbly suggest the following three plans of action:(1)A class that provides some depth might involve the following:Go through Chapters 1,2,3,4,and 5.Armed with that background,study the entirety of Chapter 6(“Algorithms”)in depth.One can spend at least a third of a semester on that chapter.After wrestling a bit with quantum algorithms,the student will get a good feel for the entire enterprise.(2)If breadth is preferred,pick and choose one or two sections from each of the advanced chapters.Such a course might look like this:(1),2,3,4.1,4.4,5,6.1,7.1,9.1,10.1,10.2,and 11.This will permit the student to see the broad outline of quantum computing and then pursue his or her own path.(3)For a more advanced class (a class in which linear algebra and some mathe-matical sophistication is assumed),we recommend that students be told to read Chapters 1,2,and 3on their own.A nice course can then commence with Chapter 4and plow through most of the remainder of the book.If this is being used as a text in a classroom setting,we strongly recommend that the students make presentations.There are selected topics mentioned in Appendix E.There is no substitute for student participation!Although we have tried to include many topics in this text,inevitably some oth-ers had to be left out.Here are a few that we omitted because of space considera-tions:many of the more complicated proofs in Chapter 8,results about oracle computation,the details of the (quantum)Fourier transforms,and the latest hardware implementations.We give references for further study on these,as well as other subjects,throughout the text.More informationMore informationPreface xvANCILLARIESWe are going to maintain a Web page for the text at/∼noson/qctext.html/The Web page will containperiodic updates to the book,links to interesting books and articles on quantum computing,some answers to certain exercises not solved in Appendix B,anderrata.The reader is encouraged to send any and all corrections tonoson@Help us make this textbook better!ACKNOLWEDGMENTSBoth of us had the great privilege of writing our doctoral theses under the gentleguidance of the recently deceased Alex Heller.Professor Heller wrote the follow-ing1about his teacher Samuel“Sammy”Eilenberg and Sammy’s mathematics:As I perceived it,then,Sammy considered that the highest value in mathematicswas to be found,not in specious depth nor in the overcoming of overwhelmingdifficulty,but rather in providing the definitive clarity that would illuminate itsunderlying order.This never-ending struggle to bring out the underlying order of mathematical structures was always Professor Heller’s everlasting goal,and he did his best to passit on to his students.We have gained greatly from his clarity of vision and his viewof mathematics,but we also saw,embodied in a man,the classical and sober ideal ofcontemplative life at its very best.We both remain eternally grateful to him.While at the City University of New York,we also had the privilege of inter-acting with one of the world’s foremost logicians,Professor Rohit Parikh,a manwhose seminal contributions to thefield are only matched by his enduring com-mitment to promote younger researchers’work.Besides opening fascinating vis-tas to us,Professor Parikh encouraged us more than once to follow new directionsof thought.His continued professional and personal guidance are greatly appre-ciated.We both received our Ph.D.’s from the Department of Mathematics in The Graduate Center of the City University of New York.We thank them for providingus with a warm and friendly environment in which to study and learn real mathemat-ics.Thefirst author also thanks the entire Brooklyn College family and,in partic-ular,the Computer and Information Science Department for being supportive andvery helpful in this endeavor.1See page1349of Bass et al.(1998).More informationxvi PrefaceSeveral faculty members of Brooklyn College and The Graduate Center were kind enough to read and comment on parts of this book:Michael Anshel,DavidArnow,Jill Cirasella,Dayton Clark,Eva Cogan,Jim Cox,Scott Dexter,EdgarFeldman,Fred Gardiner,Murray Gross,Chaya Gurwitz,Keith Harrow,JunHu,Yedidyah Langsam,Peter Lesser,Philipp Rothmaler,Chris Steinsvold,AlexSverdlov,Aaron Tenenbaum,Micha Tomkiewicz,Al Vasquez,Gerald Weiss,andPaula Whitlock.Their comments have made this a better text.Thank you all!We were fortunate to have had many students of Brooklyn College and The Graduate Center read and comment on earlier drafts:Shira Abraham,RachelAdler,Ali Assarpour,Aleksander Barkan,Sayeef Bazli,Cheuk Man Chan,WeiChen,Evgenia Dandurova,Phillip Dreizen,C.S.Fahie,Miriam Gutherc,RaveHarpaz,David Herzog,Alex Hoffnung,Matthew P.Johnson,Joel Kammet,SerdarKara,Karen Kletter,Janusz Kusyk,Tiziana Ligorio,Matt Meyer,James Ng,SeverinNgnosse,Eric Pacuit,Jason Schanker,Roman Shenderovsky,Aleksandr Shnayder-man,Rose B.Sigler,Shai Silver,Justin Stallard,Justin Tojeira,John Ma Sang Tsang,Sadia Zahoor,Mark Zelcer,and Xiaowen Zhang.We are indebted to them.Many other people looked over parts or all of the text:Scott Aaronson,Ste-fano Bettelli,Adam Brandenburger,Juan B.Climent,Anita Colvard,Leon Ehren-preis,Michael Greenebaum,Miriam Klein,Eli Kravits,Raphael Magarik,JohnMaiorana,Domenico Napoletani,Vaughan Pratt,Suri Raber,Peter Selinger,EvanSiegel,Thomas Tradler,and Jennifer Whitehead.Their criticism and helpful ideasare deeply appreciated.Thanks to Peter Rohde for creating and making available to everyone his MAT-LAB q-emulator Quack and also for letting us use it in our appendix.We had a gooddeal of fun playing with it,and we hope our readers will too.Besides writing two wonderful appendices,our friendly neighborhood librar-ian,Jill Cirasella,was always just an e-mail away with helpful advice and support.Thanks,Jill!A very special thanks goes to our editor at Cambridge University Press,HeatherBergman,for believing in our project right from the start,for guiding us through thisbook,and for providing endless support in all matters.This book would not existwithout her.Thanks,Heather!We had the good fortune to have a truly stellar editor check much of the text many times.Karen Kletter is a great friend and did a magnificent job.We also ap-preciate that she refrained from killing us every time we handed her altered draftsthat she had previously edited.But,of course,all errors are our own!This book could not have been written without the help of my daughter,Hadas-sah.She added meaning,purpose,and joy.N.S.Y.My dear wife,Rose,and our two wondrous and tireless cats,Ursula and Buster, contributed in no small measure to melting my stress away during the long andpainful hours of writing and editing:to them my gratitude and love.(Ursula is ascientist cat and will read this book.Buster will just shred it with his powerful claws.)M.A.M.。
Ovation I O Reference Manual

This publication adds the Eight Channel RTD module to the Ovation I/O Reference Manual. It should be placed between Sections 19 and 20.Date: 04/03IPU No.243Ovation ® Interim Publication UpdatePUBLICATION TITLEOvation I/O Reference ManualPublication No. R3-1150Revision 3, March 2003Section 19A. Eight Channel RTDModule19A-1. DescriptionThe Eight (8) channel RTD module is used to convert inputs from Resistance Temperature Detectors (RTDs) to digital data. The digitized data is transmitted to the Controller.19A-2. Module Groups19A-2.1. Electronics ModulesThere is one Electronics module group for the 8 channel RTD Module:n5X00119G01 converts inputs for all ranges and is compatible only with Personality module 5X00121G01 (not applicable for CE Mark certified systems).19A-2.2. Personality ModulesThere is one Personality module groups for the 8 channel RTD Module:n5X00121G01 converts inputs for all ranges and is compatible only with Electronics module 5x00119G01 (not applicable for CE Mark certified systems).19A-2.3. Module Block Diagram and Field Connection WiringDiagramThe Ovation 8 Channel RTD module consists of two modules an electronics module contains a logic printed circuit board (LIA) and a printed circuit board (FTD). The electronics module is used in conjunction with a personalty module, which contains a single printed circuit board (PTD). The block diagram for the 8 channel RTD moduleis shown in Figure 19A-1.Table 19A-1. 8 Channel RTD Module Subsystem ChannelsElectronic Module Personality Module85X00119G015X00121G01Figure 19A-1. 8 Channel RTD Module Block Diagram and Field Connection Wiring Diagram19A-3. SpecificationsElectronics Module (5X00119)Personality Module (5X00121)Table 19A-2. 8 Channel RTD Module SpecificationsDescription ValueNumber of channels8Sampling rate50 HZ mode: 16.67/sec. normally. In 3 wire mode, leadresistance measurement occurs once every 6.45 sec.during which the rate drops to 3/sec.60 HZ mode: 20/sec. normally. In 3 wire mode, leadresistance measurement occurs once every 6.45 sec.during which the rate drops to 2/sec.Self Calibration Mode: Occurs on demand only. The ratedrops to 1/sec. once during each self calibration cycle.RTD ranges Refer to Table 19A-3.Resolution12 bitsGuaranteed accuracy (@25°C)0.10% ±[0.045 (Rcold/Rspan)]% ± [((Rcold + Rspan)/4096 OHM)]% ± [0.5 OHM/Rspan]% ±10 m V ± 1/2LSBwhere:Rcold and Rspan are in Ohms.Temperature coefficient 10ppm/°CDielectric isolation:Channel to channel Channel to logic 200V AC/DC 1000 V AC/DCInput impedance100 M OHM50 K OHM in power downModule power 3.6 W typical; 4.2 W maximumOperating temperature range0 to 60°C (32°F to 140°F)Storage temperature range-40°C to 85°C (-40°F to 185°F)Humidity (non-condensing)0 to 95%Self Calibration On Demand by Ovation ControllerCommon Mode Rejection120 dB @ DC and nominal power line frequency+/- 1/2%Normal Mode Rejection100 dB @ DC and nominal power line frequency+/- 1/2%Table 19A-3. 8 Channel RTD RangesScale #(HEX)Wires Type Tempo FTempo CRcold(ohm)Rhot(ohm)Excitationcurrent(ma)Accuracy± ±countsAccuracy± ±% ofSPAN1310OhmPL0 to1200–18 t o6496106.3 1.090.222310OhmCU 0 to302–18 t o1508.516.5 1.0 130.32D350OhmCU 32 to2840 to1405080 1.0110.2711350OhmCU 32 to2300 to1105378 1.0120.30193100Ohm PL –4 to334–16 t o16892163.671.0110.27223100Ohm PL 32 to5200 to269100200 1.0100.25233100Ohm PL 32 to10400 to561100301 1.0100.25253120Ohm NI –12 t o464–11 t o240109360 1.0100.25263120Ohm NI 32 to1500 to70120170 1.0130.32283120Ohm NI 32 to2780 to122120225 1.0110.27804100Ohm PL 32 to5440 to290100 208 1.0100.25814100Ohm PL 356 t o446180 t o230168 186 1.0300.74824200Ohm PL 32 to6980 to370200 473 1.0120.30834200Ohm PL 514 t o648268 t o342402452 1.0290.71844100Ohm PL 32 to1240 to51100120 1.0190.47854100Ohm PL 32 to2170 to103100 140 1.0130.3286 4100Ohm PL 32 to4120 to211100 180 1.0110.27874100Ohm PL 32 to7140 to379100 240 1.0100.25884120Ohm PL 511 t o662266 t o350200230 1.0240.5919A-4. 8 Channel RTD Terminal Block Wiring Information19A-4.1. Systems Using Personality Module 5X00121G01 Each Personality module has a simplified wiring diagram label on its side, which appears above the terminal block. This diagram indicates how the wiring from the field is to beconnected to the terminal block in the base unit. The following table lists and defines the abbreviations used in this diagram.Table 19A-4. Abbreviations Used in the DiagramAbbreviation Definition+IN, -IN Positive and negative sense input connectionEarth ground terminal. Used for landing shields when the shield is to begrounded at the module.PS+, PS-Auxiliary power supply terminals.RTN Return for current source connection.SH Shield connector. used for landing shields when the shield is to begrounded at the RTD.SRC Current source connection.Note:PS+ and PS- are not used by this module.19A-5. 8 Channel RTD Module Address Locations19A-5.1. Configuration and Status RegisterWord address 13 (D in Hex) is used for both module configuration and module status. The Module Status Register has both status and diagnostic information. The bit information contained within these words is shown in Table 19A-5.Definitions for the Configuration/Module Status Register bits:Bit 0:This bit configures the module (write) or indicates the configuration state of the module (read). A “1” indicates that the module is configured. Note that until the module is configured, reading from addresses #0 through #11 (B in Hex) will produce an attention status.Bit 1:This bit (write “1”) forces the module into the error state, resulting in the error LED being lit. The read of bit “1” indicates that there is an internal module error,or the controller has forced the module into the error state. The state of this bit is always reflected by the module’s Internal Error LED. Whenever this bit is set,an attention status is returned to the controller when address #0 through #11(B in Hex) are read.Table 19A-5. 8 Channel RTD Configuration/Status Register (Address 13 0xD in Hex)Bit Data Description -Configuration Register (Write)Data Description -Status Register (Read)0Configure Module Module Configured(1 = configured; 0 = unconfigured)1Force errorInternal or forced error(1 = forced error; 0 = no forced error)250/60 Hz select (0 = 60Hz, 1 = 50Hz)50/60 Hz System (1 = 50Hz) d(read back)3SELF_CAL (Initiates Self Calibration)Warming bit (set during power up or configuration)40050060Module Not Calibrated 708CH.1 _ 3/4 Wire.CH.1 _ 3/4 Wire - Configuration (read back)9CH.2 _ 3/4 Wire.CH.2 _ 3/4 Wire - Configuration (read back)10CH.3 _ 3/4 Wire.CH.3 _ 3/4 Wire - Configuration (read back)11CH.4 _ 3/4 Wire.CH.4 _ 3/4 Wire - Configuration (read back)12CH.5 _ 3/4 Wire.CH.5 _ 3/4 Wire - Configuration (read back)13CH.6 _ 3/4 Wire.CH.6 _ 3/4 Wire - Configuration (read back)14CH.7 _ 3/4 Wire.CH.7 _ 3/4 Wire - Configuration (read back)15CH.8 _ 3/4 Wire.CH.8 _ 3/4 Wire - Configuration (read back)Bit 2:The status of this bit (read) indicates the conversion rate of the module, write to this bit configures the conversion rate of A/D converters as shown below.see Table 19A-6.Bit3:Write: This bit is used to initiate self-calibration. Read: This bit indicates that the module is in the “Warming” state. this state exists after power up and ter-minates after 8.16 seconds. the module will be in the error condition during the warm up period.Bit4 & 5:These bits are not used and read as “0” under normal operation.Bit 6:This bit (read) is the result of a checksum test of the EEPROM. A failure of this test can indicate a bad EEPROM, but it typically indicates that the module has not been calibrated. A “0” indicates that there is no error condition. If an error is present, the internal error LED is lit and attention status will be returned for all address offsets 0-11 (0x0 - 0xB). The “1” state of this bit indicates an unre-coverable error condition in the field.Bit 7:This bits is not used and read as “0” under normal operation.Bit 8 - 15:These bits are used to configure channels 1 - 8 respectively for 3 or 4 wire op-eration. A “0” indicates 3 wire and a “1” indicates 4 wire operation, see Table 19A-7 and Table 19A-8).Word address 12 (0xC) is used to configure the appropriate scales for Channels 1 - 4 (refer to Table 19A-7 and Table 19A-8).Table 19A-6. Conversion Rate Conversion Rate (1/sec.)Bit 260 (for 60Hz systems)050 (for 50Hz systems)1Table 19A-7. Data Format for the Channel Scale Configuration Register(0xC)Bit Data Description Configuration (Write)Data Description Status (Read)0 Configure Channel #1scale - Bit 0Channel #1 scale configuration (read back) - Bit 01Configure Channel #1scale - Bit 1Channel #1 scale configuration (read back) - Bit 12Configure Channel #1scale - Bit 2Channel #1 scale configuration (read back) - Bit 23Configure Channel #1scale - Bit 3Channel #1 scale configuration (read back) - Bit 34Configure Channel #2 scale - Bit 0Channel #2 scale configuration (read back) - Bit 05Configure Channel #2 scale - Bit 1Channel #2 scale configuration (read back) - Bit 16Configure Channel #2 scale - Bit 2Channel #2 scale configuration (read back) - Bit 27Configure Channel #2 scale - Bit 3Channel #2 scale configuration (read back) - Bit 38Configure Channel #3 scale - Bit 0Channel #3 scale configuration (read back) - Bit 09Configure Channel #3 scale - Bit 1Channel #3 scale configuration (read back) - Bit 1Caution:Configuring any or all channel scales while the system is running will cause all channels to return attention status for up to two seconds following the reconfiguration.Caution:Configuring any or all channel scales while the system is running will cause all channels to return attention status for up to two seconds following the reconfiguration.10Configure Channel #3 scale - Bit 2Channel #3 scale configuration (read back) - Bit 211Configure Channel #3 scale - Bit 3Channel #3 scale configuration (read back) - Bit 312Configure Channel #4 scale - Bit 0Channel #4 scale configuration (read back) - Bit 013Configure Channel #4 scale - Bit 1Channel #4 scale configuration (read back) - Bit 114Configure Channel #4 scale - Bit 2Channel #4 scale configuration (read back) - Bit 215Configure Channel #4 scale - Bit 3Channel #4 scale configuration (read back) - Bit 3Table 19A-8. Data Format for the Channel Scale Configuration Register(0xE)Bit Data Description Configuration (Write)Data Description Status (Read)0 Configure Channel #5 scale - Bit 0Channel #5 scale configuration (read back) - Bit 01Configure Channel #5 scale - Bit 1Channel #5 scale configuration (read back) - Bit 12Configure Channel #5 scale - Bit 2Channel #5 scale configuration (read back) - Bit 23Configure Channel #5 scale - Bit 3Channel #5 scale configuration (read back) - Bit 34Configure Channel #6 scale - Bit 0Channel #6 scale configuration (read back) - Bit 05Configure Channel #6 scale - Bit 1Channel #6 scale configuration (read back) - Bit 16Configure Channel #6 scale - Bit 2Channel #6 scale configuration (read back) - Bit 27Configure Channel #6 scale - Bit 3Channel #6 scale configuration (read back) - Bit 38Configure Channel #7 scale - Bit 0Channel #7 scale configuration (read back) - Bit 09Configure Channel #7 scale - Bit 1Channel #7 scale configuration (read back) - Bit 110Configure Channel #7 scale - Bit 2Channel #7 scale configuration (read back) - Bit 211Configure Channel #7 scale - Bit 3Channel #7 scale configuration (read back) - Bit 312Configure Channel #8 scale - Bit 0Channel #8 scale configuration (read back) - Bit 013Configure Channel #8 scale - Bit 1Channel #8 scale configuration (read back) - Bit 114Configure Channel #8 scale - Bit 2Channel #8 scale configuration (read back) - Bit 215Configure Channel #8 scale - Bit 3Channel #8 scale configuration (read back) - Bit 3Table 19A-7. Data Format for the Channel Scale Configuration Register(0xC)19A-6. Diagnostic LEDsTable 19A-9. 8 Channel RTD Diagnostic LEDsLED DescriptionP (Green)Power OK LED. Lit when the +5V power is OK.C (Green)Communications OK LED. Lit when the Controller is communicatingwith the module.I (Red)Internal Fault LED. Lit whenever there is any type of error with themodule except to a loss of power. Possible causes are:n - Module initialization is in progress.n - I/O Bus time-out has occurred.n - Register, static RAM, or FLASH checksum error.n - Module resetn - Module is uncalibrated.n - Forced error has been received from the Controllern - Communication between the Field and Logic boards failedCH1 - CH 8 (Red)Channel error. Lit whenever there is an error associated with a channel or channels. Possible causes are:n - Positive overrangen - Negative overrangen Communication with the channel has failed。
Fujitsu PRIMERGY Linux安装后操作指南(适用于x86版本3.0)说明书

2005-11-01 Notes on Using Red Hat Enterprise Linux AS (v.3 for x86) PrefaceAbout This ManualThis manual provides notes on PRIMERGY operation with Linux installed. Be sure to read this manual before using Linux.Intended ReadersThis manual is intended for persons who operate PRIMERGY.Organization of This ManualThis manual consists of the following chapters:Chapter 1 Notes on OperationThis chapter provides notes on operation after installation. Be sure to read this chapterbefore operating PRIMERGY with Linux installed.Chapter 2 Addition of Peripheral Devices and Option CardsThis chapter explains the procedures for adding peripheral devices and cards afterinstallation and provides notes on adding these options. Read this chapter as required.Chapter 3 OthersThis chapter explains other functions and provides other notes such as notes on limits.Operation VerificationThe operations of the products described in this manual have been confirmed by Fujitsu. Please note, however, that these operations are subject to change without prior notice.Support & ServiceA support service(SupportDesk Product basic service), available for a fee, provides customers usingLinux with an enhanced sense of security and confidence. Customers concluding a support and service agreement are entitled to receive support in such areas as assistance with queries regarding this manual and questions and problems that may come up during the installation and operation of this product.Please consider taking advantage of this service option by concluding a support and service agreement with us.CopyrightAll rights Reserved, Copyright (C) FUJITSU LIMITED 20051. Notes on Operation1.1 Assignment of Device NamesLinux assigns device names to a variety of devices, such as the hard disk drive, in the order that it recognizes them during its startup sequence. If the system is restarted after a device such as a hard disk drive or controller fails, the assigned device names may be changed because the system cannot recognize a device that has failed.Example: When hard disk drives are connected to SCSI ID 1, 2, and 3, device names /dev/sda, /dev/sdb, and /dev/sdc are assigned respectively to the disk drives. If /dev/sdb failsunder this condition, the device previously assigned /dev/sdc/ is moved up by one andrecognized as /dev/sdb after the system is restarted.If an assigned device is unexpectedly changed, it may prevent the system from starting or,in the worst case, may damage your data. If a device fault is detected, therefore, Fujitsurecommends starting the system in rescue mode and checking for hardware faults beforerestarting the system (*1). Repair the hardware fault, restore the system by means suchas the backup tape, and then restart the system.*1 For details on starting the system in rescue mode, see Section 1.4, "Starting theSystem in Rescue Mode."After starting the system, use the fdisk command to check whether the relevant hard diskdrive can be recognized, and take necessary steps such as checking for hardware errormessages in /var/log/messages.1.2 Installation of Red Hat Enterprise Linux AS (v.3 for x86) PackagesRed Hat Enterprise Linux provides installation types so that the optimum system can be constructed according to the use purpose. For this reason, packages required for your purposes might not be installed. If a required package has not been installed, log in as the root and install it by executing the following procedure:Install the necessary packages by using the installation CDs (1/4 to 4/4) that have beencreated according to the Installation Procedure included in the driver kit.# mount -r /dev/cdrom /mnt/cdrom# cd /mnt/cdrom/RedHat/RPMS# rpm -ivh <package_file>Example: To install package "make"# rpm -ivh make-3.79.1-17.i386.rpm# cd /# umount /mnt/cdrom# eject* Remove the CD.1.3 Installing and Setting Up Global Array Manager (GAM)Use Global Array Manager (GAM) as a RAID management tool in a system with a mounted onboard SCSI-RAID and SCSI-RAID card (PG-142E3).For details on installing GAM-Client (Windows), see "Outline of Installation Procedure for Global Array Manager-Client", which is an attachment.The GAM-Server (Linux) installation procedure is explained below.[Notes]1)The screen display may become unstable during GAM installation or GAM service startup.This is not an operational problem.2)Specify the port numbers shown below for GAM service.Take care when configuring firewall settings.Port numbers: 157,158(1)To install GAM-Server (Linux), insert the driver CD into the CD-ROM drive, and entercommands as follows:# mount -r /dev/cdrom /mnt/cdrom# cd /mnt/cdrom/UTY/GAM/Linux# rpm -ivh gam-server-6.02-21.i386.rpm# rpm -ivh gam-agent-6.02-21.i386.rpm- Enter the following only if onboard SCSI for RX200 S2# rpm -ivh 1030SNMPAgent-2.4-3.i386.rpm# sh ./insgam* Confirm that “GAM is installed successfully.” is displayed.# cd /# umount /mnt/cdrom# eject* Remove the CD.(2)For user accounts in Linux, create "gamroot" as a user account with GAM administratorauthority and then create user accounts (e.g., "gamuser") with user authority.(If a user account with user authority has already been created, another account need not be created.) # adduser gamroot# passwd gamrootChanging password for user gamrootNew-password <--- Enter a password.Retype new password <--- Re-enter the same password for confirmation.passwd: all authentication tokens updated successfully* Create a user account with user authority in the same way as explained above.(3)Edit three lines as shown below in the /etc/sysconfig/gam file.Events can be posted to GAM-Client after this editing is completed.# vi /etc/sysconfig/gam[Before editing]START_GAMEVENT=nGAMEVENT_OPTIONS=""[After editing]START_GAMEVENT=y <--- Change "n" to "y".GAMEVENT_OPTIONS="-h ip-address" <--- Specify the IP address of the managementWindows system on which GAM-Client isinstalled.[Before editing]START_GAMEVLOG=n[After editing]START_GAMEVLOG=y <--- Change "n" to "y".(4)Restart the system.# shutdown -r now* The following message may be displayed after the system starts. It does not indicate an operational problem.[Message]gamagent: gamagent: Connection refusedgamagent connect failure1.4 Starting the System in Rescue ModeUsing only one of the installation CDs that have been created according to the Installation Procedure included in the driver kit, you can start the system in rescue mode. This may enable system recovery in the event of a problem that prevents the system from starting normally.This section explains only how to start the system as one that has minimum functionality.Start the system in rescue mode as follows:(1)Start the system from installation CD 1/4 that was created according to the InstallationProcedure included in the driver kit. Enter the appropriate response in the following window,and press the [Enter] key.(2)In the Choose a Language window, select "English" and select "OK."(3)In the Keyboard Type window, select "jp106" and select "OK."If an accessory keyboard such as of a flat display (PG-R1DP3) is used, select "us" here.(4)In the following window, select "Yes."(5)In the following window, select "Add Device."(6)In the Driver List window, select the drivers for the devices installed in the system, and select"OK." The following drivers must be selected:[onboard SCSI type for TX200 S2][onboard SCSI type or onboard SCSI-RAID type for RX200 S2]Two drivers must be selected. Select drivers as follows:1.Select the driver shown below, and select "OK.""LSI Logic Fusion MPT Base Driver (mptbase)"2.The Device Selection window is displayed. Select "AddDevice."3. A list of drivers is displayed. Select the driver shown below, and select "OK.""LSI Logic Fusion MPT SCSI Driver (mptscsih)"[SCSI-RAID card(PG-140D1/PG-142E3) for TX200 S2][onboard SCSI-RAID type for RX300 S2]Select the driver shown below, and select "OK.""LSI MegaRAID controller (megaraid2)"(7)Make sure that the selected driver is displayed in the following window, and select "Done."(8)The Setup Networking window is displayed. Select "No" because network settings need not beconfigured at this time.(9)Select "Continue" in the Rescue window.(10)If the root partition (/) in the existing Linux system has been mounted successfully under/mnt/sysimage, this is reported in the Rescue window. Select "OK."(11)When the prompt is displayed, enter the chroot command to change the root path to the harddisk drive.sh-2.05b# chroot /mnt/sysimage(12)This completes startup in rescue mode. To exit rescue mode, enter the exit command twice.sh-2.05b# exit <--- Exit from the chroot environment.sh-2.05b# exit <--- Exit from the rescue mode.1.5 Power-off at ShutdownPower is not automatically turned off at shutdown.When [Power down] is displayed on the console screen, press the power switch to turn off the power.Note that the power is automatically turned off when the system is shut down in an environment in which ServerView is installed.2. Addition of Peripheral Devices and Option Cards2.1 Adding a SCSI DiskThe number of LUNs is set to 1 by default. To add a SCSI disk, shared disk, or tape library, log in as the root and define the number of LUNs as shown below. Multiple LUN referencing is enabled after the system is started next.(1)Add the following lines to /etc/modules.conf:options scsi_mod max_scsi_luns=N <--- Add* N is the number of LUNs. Define the appropriate number.(2)Enter the mkinitrd command to create initrd.To create initrd, enter the mkinitrd command appropriate for the type of kernel used.* Enter the following command to check the type of kernel used:# uname -r[2.4.21-32.0.1.EL (kernel for single CPU)]# cp /boot/initrd-2.4.21-32.0.1.EL.img /boot/initrd-2.4.21-32.0.1.EL.img.bak# mkinitrd -f /boot/initrd-2.4.21-32.0.1.EL.img 2.4.21-32.0.1.EL[2.4.21-32.0.1.EL smp (kernel for multi-CPU)]#cp /boot/initrd-2.4.21-32.0.1.ELsmp.img /boot/initrd-2.4.21-32.0.1.ELsmp.img.bak# mkinitrd -f /boot/initrd-2.4.21-32.0.1.EL smp.img 2.4.21-32.0.1.EL smp(3)Restart the system.Enter the following command to restart the system.# shutdown -r now2.2 Adding Option CardsIf any of the option cards supported by the models listed in the following table is added after system installation, kudzu is automatically started at system startup. This section explains the operations that enable the system to automatically recognize the added card at each subsequent system startup.The table lists models and the option cards supported by them.TX200 S2 RX200 S2 RX300 S2PG-128 V -- -- SCSI cardPG-130L -- V V PG-140D1V V -- SCSI-RAID cardPG-142E3V V -- PG-1852 V V -- PG-1853 V -- -- PG-1853L -- V -- PG-1862 V V -- PG-1882 V -- -- PG-1882L -- V V PG-1892 V -- -- LAN cardPG-1892L -- V V PG-FC106V V V onboard Fibre-Channel cardPG-FC107V V VSCSI cardPG-128 -- -- V SCSI-RAID cardPG-142E3-- -- V PG-1852 -- -- V PG-1853 -- -- V PG-1862 -- -- V PG-1882 -- -- V LAN cardPG-1892 -- -- V PG-FC106-- -- V Raiser Card Fibre-Channel cardPG-FC107-- -- VV: Supported --: Not supported- TX200 S2 or RX300 S2If any of the option cards supported by the models listed in the above table is added after system installation, kudzu is automatically started at system startup. To add a fibre channel card, follow the steps below. Except for a fibre channel card, select "configure."To add a LAN card, configure network settings according to the instructions displayed in the window. Login as a root user at system startup, and perform the operations explained in Section 2.3, "Executing mkinitrd."This section explains the operations that enable the system to automatically recognize the added card at each subsequent system startup.[A fibre channel card is added](1)If a fibre channel card is added after system installation,kudzu is automatically started at system startup.Always select "ignore ."(2)Add the following line to /etc/modules.conf.If SCSI or SCSI-RAID device is installed in the system,number the end of "scsi_hostadapter", as "2, 3, ...".options scsi_mod max_scsi_luns=128 Add- RX200 S2If any of the option cards supported by the models listed in the above table is added after systeminstallation, kudzu is automatically started at system startup.To add a fibre channel card or LAN card, follow the steps below.Except for a fibre channel card and LAN card, select "configure." Login as a root user at system startup, and perform the operations explained in Section 2.3, "Executing mkinitrd."This section explains the operations that enable the system to automatically recognize the added card at each subsequent system startup.[A LAN card(PG-1852, PG-1862, PG-1882L or PG-1892L) is added](1)If any of the LAN cards supported by the models listed in the above table is addedafter system installation, kudzu is automatically started at system startup.Always select " ignore."(2)Add the following lines to /etc/modules.conf.[ PG-1852, PG-1853L,PG-1892L, or PG-1882L]alias eth0 e1000alias eth1 e1000alias eth2 e1000 <--- Add[ PG-1862]alias eth0 e1000alias eth1 e1000alias eth2 e1000 <--- Addalias eth3 e1000 <--- Add(3)Set up the network.[ PG-1852, ,PG-1853L ,PG-1892L, or PG-1882L]# netconfig -d eth0# netconfig -d eth1# netconfig -d eth2[ PG-1862]# netconfig -d eth0# netconfig -d eth1# netconfig -d eth2# netconfig -d eth3[A fibre channel card is added](1)If a fibre channel card is added after system installation,kudzu is automatically started atsystem startup.Always select "ignore ."(2)Add the following line to /etc/modules.conf.If SCSI or SCSI-RAID device is installed in the system,number the end of "scsi_hostadapter",as "2, 3, ...".options scsi_mod max_scsi_luns=128 Add2.3 Executing mkinitrd(1) Create initrd by executing the mkinitrd command.Create initrd by executing the mkinitrd command according to the kernel used.* Enter the following command to check the kernel used:# uname -rCommand execution examples are shown below.[2.4.21-32.0.1.EL (kernel for a single CPU)]# cp /boot/initrd-2.4.21-32.0.1.EL.img /boot/initrd-2.4.21-32.0.1.EL.img.bak# mkinitrd -f /boot/initrd-2.4.21-32.0.1.EL.img 2.4.21-32.0.1.EL[2.4.21-32.0.1.EL smp (kernel for multi-CPUs)]# cp /boot/initrd-2.4.21-32.0.1.EL smp.img /boot/initrd-2.4.21-32.0.1.ELsmp.img.bak# mkinitrd -f /boot/initrd-2.4.21-32.0.1.EL smp.img 2.4.21-32.0.1.EL smp(2) Restart the system.Restart the system as follows:# shutdown -r now3. Others3.1 Sound FunctionNo sound function is supported.3.2 PCI Hot Plug FunctionThe PCI hot plug function is not supported.3.3 Usable KernelsThe kernels that can be used vary depending on the hardware conditions.See the table below for the kernels that can be used.Note that middleware specifications might limit the kernel to be selected. In this case, select the kernel in accordance with the middleware specifications.Hardware conditionsKernel to be selectedMemory Number of logical CPUs (*1)for single CPU1CPU Kernel Up to 4 GB2 or more CPUs Kernel for multi-CPUMore than 4 GB and up to 8 GB No conditions Kernel for multi-CPU(*1) Even when only one CPU is installed, the number of logical CPUs is 2if Hyper Threading = Enabled.3.4 Distribution LimitationsOperation is not guaranteed if one of the following CPU, memory, and file system limitations is exceeded:Maximum number of logical CPUs: 16Maximum memory size: 8 GBFile system: Less than 1 TB3.5 Installation ProcedureFor information on the procedure for installing Red Hat Enterprise Linux ES (v.3 for x86), see the Installation Procedure included in the "Installation Kit" downloaded from Download Search.Attachment Outline of Global Array Manager Client Installation* Perform this operation only when an onboard SCSI-RAID or a SCSI-RAID card (PG-140D1 or PG-142E3) are mounted.* GAM-Client runs on Windows2000 and Windows2003. Prepare a management Windows system.1. Insert the driver CD into the CD-ROM drive in the management Windows system.2. Execute setup.exe in RHEL3¥UTY¥GAM¥Windows on the driver CD.3. When the "Welcome" window is displayed, click "Next."4. The "Software License Agreement" window is displayed. Read the statements and click "Yes" if youaccept the terms of this agreement.5. The "Select Components" window (Figure 1) is displayed. Confirm that the check box before "GlobalArray Manager Client" is selected. Clear the "Global Array Manager Server" and "SAN Array Manager Client" check boxes, and click "Next."Figure 1* "SAN Array Manager Client" is not supported. Do not install it.6.The "Choose Destination Location" window is displayed.Click "Browse," specify the location that you want as the installation destination, and click "Next."* If GAM-Client is already installed, a message confirmingwhether to overwrite is displayed. Click "OK" to continue.7. A dialog box for specifying the GAM-Client installation destination is displayed. Click "Next." and thesetup program starts copying files.8. The "Setup Complete" window is displayed.Click "Finish" to exit the GAM-Client installation wizard.-- END --。
通用电气绿带DOE读本

higher order interactions, but not other main effects, 2- or 3-factor interactions. Two-factor interactions are confounded not with each other, but with 3-factor or higher order interactions. In other words, 2-factor interactions are clear of each other.
Higher Order Interactions
– – 1 5 16 42 99 219 466 968 • • • 32,647 • • • 1,048,365
2023/12/30
3
Example of Information Available...
...from a Full Factorial (4 Factors)
This can result in a large number of runs, even with a relatively small number of factors.
For a 2 level factorial with k factors…..Number of run=2k.
13
A 2-factor Experiment With Confounded Effects
Run Factor A
Factor B
Response
1
–
2
Businessresearchmethods.pdf

Title: Business Research Methods (7th ed.)Authors: Donald R. Cooper & Pamela S. SchindlerMcGraw Hill International Edition, Statistics and Probability series ISBN 0071181091, pp 798 + CD-ROM Presumably this text was sent to LTSN Maths, Stats & OR because it’s been published as part of McGraw Hill’s Statistics and Probability series. However, although the intended readership of the text is not explicitly stated it is clear that the text is aimed at the general undergraduate business studies student and not at the specialist maths/stats/OR student. Accordingly, I’ve considered the text from two slightly different perspectives.Reviewed by: Mik WisniewskiDepartment of Management ScienceStrathclyde UniversityEmail:*****************The first considers the value of the text from the perspective of service teaching: teaching business and management students about maths/stats/OR. The second considers the value of the text from the perspective of teaching maths/stats/OR students about the role and use of quantitative techniques in wider business decision making.The text is written by two US academics and is clearly aimed at the US market. The text is structured into four – fairly traditional - parts with individual chapters in each part.I Introduction to Business Research Chapter 1Research in BusinessChapter 2Addressing Management Problems withScientific ThinkingChapter 3The Research Process Chapter 4The Research Proposal Chapter 5Ethics in Business Research II The Design of Research Chapter 6Design Strategies Chapter 7Sampling Design Chapter 8MeasurementChapter 9Measurement ScalesIII The Sources and Collection of Data Chapter 10Exploring Secondary DataChapter 11Survey Methods: Communicating withRespondentsChapter 12Instruments for RespondentCommunicationChapter 13Observational Studies Chapter 14ExperimentationIV Analysis and Presentation of DataChapter 15Data Preparation and Description Chapter 16Exploring, Displaying, and ExaminingDataChapter 17Hypothesis TestingChapter 18Measures of AssociationChapter 19Multivariate Analysis: An Overview Chapter 20Presenting Results: Written and OralReportsA set of over 20 business cases including McDonalds,Xerox, Ramada. NCR is included as a separate section.n addition there is an extensive set of appendices including Core Business Reference Sources (both printed and electronic) and Selected Statistical Tables.The CD-Rom that accompanies the text includes the Glossary, data files, PowerPoint presentations, and exhibits index and the Business reference Sources.There is also an I nstructor’s Resource Guide and an Instructor’s Videotape Supplement that accompany the text but these were not available to the reviewer.The content as such is both predictable for a text of this type and relatively comprehensive. On the quantitative side topics such as exploratory data analysis are covered,as are data presentation methods, inferential statistics and hypothesis testing, correlation, regression and measures of association and multivariate analysis.Somewhat strangely, one of the appendices covers decision theory, which seems somewhat out of place whilst another covers ‘advanced’ nonparametric tests which could more usefully be covered in the main text.However, there are a number of areas from OR which would add value to the text: the basics of project management in a research project context; the use of cognitive mapping to help scope a research project; an introduction to systems thinking; an introduction to multi-criteria decision analysis in the context of complex decision making.Each chapter in the text follows a standard structure and format.The chapter starts with a “Bringing research to life” case study/vignette. This is a case study that develops throughout the text and involves two individuals who start working together on a specific research project: a customer service manager in an I T business and a freelance consultant/researcher brought in to help the business undertake research into customer attitudes and satisfaction. The two individuals are deliberately stereotyped and as opposites. The (female) manager is portrayed at having excellent person-to-person skills, aswell as personal skills, has little quantitative background and is a great believer in qualitative information. The (male) consultant/researcher is introduced as an anally-retentive anorak/geek who surrounds himself with all the latest IT gadgetry and is obsessed with hard data and analysis. As the case study unfolds on a chapter-by-chapter basis it develops predictably into a mutual improved understanding of the two polarised perspectives in terms of business and management decision-making. Fortunately, the authors resisted the temptation to have the two characters ride off into the sunset together!. From a student learning perspective, the developing case study probably works very well. It helps business students (who in my experience at least have little expressed interest in robust quantitative analysis and modelling) understand the role and contribution of such techniques in the wider research and decision making process. I t also helps the more specialist maths/stats/OR student appreciate that to a manager such tools and techniques do not occupy a central position of importance in their universe but are – at best – a means to an end of problem solving and decision making.Throughout each chapter use is also made of:•Snapshots which are short, focussed illustrations on real-world applications supporting that part of the text. These are helpful in reinforcing the message that organisations actually use these approachesand techniques•Tips, which are practical ideas at actually applying specific concepts and techniques•Case illustrations which use extracts from company literature and reports to highlight approaches and techniquesEach chapter concludes with a list of key terms which are defined in a separate end-of-text glossary; a list of the case examples used in the chapter; discussion questions; suggestions as to which of the cases included at the end of the text can be used to test understanding of the chapter; reference notes; further reading.The material generally is easy to read and is presented in a logical and structured manner. The use of cases, illustrations etc centrally helps break up the text as well as bring it to life in terms of its practical application to organisations. Inevitably, however, given the US focus of the text, some of the case study illustrations will mean little to UK students.The chapters that focus on the more quantitative aspects of the research process are well-written and the role of, and need for, quantitative approaches is generally well-explained. The use of illustrative data sets, calculations and computer output helps the student appreciate why these techniques are needed, how they can be used and how they can be evaluated and assessed.So, is the text worth buying/recommending?Well, I shall be buying a copy for my bookshelf. There’s a lot of material that can be used to bring a sense of reality to what can very often be quite abstract concepts and techniques and the huge number of case study illustrations will be a useful resource for my own teaching. Recommending it to students, however, is a different matter. It’s difficult to see from a UK context where such a text would find a suitable home.Business students who need a “good” text, particularly on the wider use of quantitative techniques in business decision making, would probably do better with a UK publication that better matched a typical syllabus and with one that was less concerned with “research” as such.Maths/Stats/OR students would probably find that the text contained little new in the way of “theory” although it certainly would be useful as a supplementary text at helping them better understand the role of that theory and the quantitative analyst in business decision making. This is where the text does particularly well but it is unlikely to be enough to persuade undergraduate students to buy it.Note: The McGraw Hill website details an 8th edition of this text with a later publication date and a different ISBN. The table of contents is identical although the page length is shorter at 640pp. It is not clear how this edition varies from that reviewed here.。
2020智慧树知道网课《医学遗传学(XXX)》章节测试满分答案

2020智慧树知道网课《医学遗传学(XXX)》章节测试满分答案.Chapter 1 Test1.(5 points) The object of study in medical ics is ______.A。
ic diseasesB。
Molecular diseasesXXXD。
XXXE。
ic diseases2.(5 points) ic diseases refer to diseases caused by ______.A。
XXXB。
XXXC。
XXX XXXD。
XXXE。
"Three-toxic" substances3.(5 points) XXX ______.A。
n exposureXXXXXXD。
Chemical poisoningE。
Heavy smoking4.(5 points) The occurrence of cleft lip is primarily determined by ______.A。
ic factorsB。
Environmental factorsXXXD。
XXX factorsXXX factors play a role in the occurrence5.(5 points) XXX ______.A。
XXX factorsB。
Environmental factorsXXXD。
XXXXXX factors play a role in the occurrence6.(5 points) XXX from n to n. A。
FalseB。
True7.(5 points) XXX.A。
TrueB。
False8.(5 points) XXX.A。
FalseB。
True9.(5 points) XXX.A。
TrueB。
False10.(5 points) XXX genes. A。
TrueB。
FalseChapter 2 Test1.(5 points) The cis-regulatory elements do not include______.A。
透镜焦距公式
2011-11-15
第一周第二次
页码,9/32
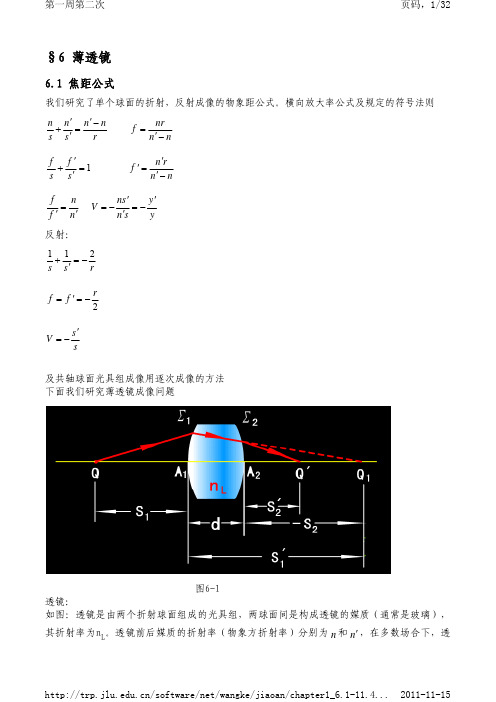
以上三条光线中任选两条做图,出射后的交点即为像点 P 求轴上物点的像或任意入射光线的共轭线,可利用焦面的性质 这种作图一般用于联合光具组中间成像时作图用,(目的为了保证入射光线经光具组的路径 连续) 物:
1区 实物——5区 缩小的倒立的实象(在2倍焦距处成等大倒立实像) 2区 实物——6区 放大的倒立的实象 3区 实物——1,2,3区 放大的正立的虚象 4区 虚物——4区 缩小的正立的实象 … 5区 … 6区 (同学们可总结凹透镜成像规律,用作图法)
f n n L n n n L r1 r2 n n L n n n L r1 r2
f
f n f n 这是薄透镜焦距公式
/software/net/wangke/jiaoan/chapter1_6.1-11.4...
ns y ns y
1 1 2 s s r f f s s r 2
V
及共轴球面光具组成像用逐次成像的方法 下面我们研究薄透镜成像问题
图6-1 透镜: 如图:透镜是由两个折射球面组成的光具组,两球面间是构成透镜的媒质(通常是玻璃), 其折射率为nL。透镜前后媒质的折射率(物象方折射率)分别为 n 和 n ,在多数场合下,透
s x f s x f ,
(实物),否则 (实象)。 s, s 也可以从 F , F 算起
代入物象距公式得xx'=ff',这便是薄透镜公式的牛顿公式。
焦距公式: 物象距公式: 横向放大率公式: 薄透镜的横向放大率分别为:
V1
所以
ns1 nL s
V2
f1 f1 1 s s 1
Vyondys 53 (golodirsen) 产品说明书

Vyondys 53™ (golodirsen)(Intravenous)Document Number: IC-0520 Last Review Date: 08/08/2023Date of Origin: 01/06/2020Dates Reviewed: 01/2020, 08/2020, 09/2020, 08/2021, 08/2022, 08/2023I.Length of AuthorizationCoverage will be for 6 months and may be renewed.II.Dosing LimitsA.Quantity Limit (max daily dose) [NDC Unit]:•Vyondys 53 100 mg/2 mL single-dose vial: 35 vials per 7 daysB.Max Units (per dose and over time) [HCPCS Unit]:•350 billable units (3500 mg) every 7 daysIII.Initial Approval CriteriaCoverage is provided in the following conditions:Universal Criteria 1,9•Patient is not on concomitant therapy with other DMD-directed antisense oligonucleotides(e.g., eteplirsen, casimersen, viltolarsen, etc.); AND•Patient is not on concomitant therapy with delandistrogene moxeparvovec-rokl; AND•Serum cystatin C, urine dipstick, and urine protein-to-creatinine ratio (UPCR) are measured prior to starting therapy and periodically during treatment; AND •Patient had an inadequate response, or has a contraindication or intolerance, to viltolarsen;ANDDuchenne Muscular Dystrophy (DMD) † Ф1-15•Patient has a confirmed mutation of the DMD gene that is amenable to exon 53 skipping;AND•Patient has been on a stable dose of corticosteroids, unless contraindicated or intolerance, for at least 6 months; AND•Patient retains meaningful voluntary motor function (e.g., patient is able to speak, manipulate objects using upper extremities, ambulate, etc.); AND•Patient is receiving physical and/or occupational therapy; AND•Baseline documentation of one or more of the following:o Dystrophin levelo Timed function tests (e.g., 6-minute walk test [6MWT], time to stand [TTSTAND], time to run/walk 10 meters [TTRW], time to climb 4 stairs [TTCLIMB], etc.)o Upper limb function (ULM) testo North Star Ambulatory Assessment (NSAA) scoreo Forced Vital Capacity (FVC) percent predicted† FDA Approved Indication(s); ‡ Compendia Recommended Indication(s); Ф Orphan Drug IV.Renewal Criteria 1-15Coverage may be renewed based upon the following criteria:•Patient continues to meet the universal and other indication-specific relevant criteria such as concomitant therapy requirements (not including prerequisite therapy), performancestatus, etc. identified in section III; AND•Absence of unacceptable toxicity from the drug. Examples of unacceptable toxicity include: severe hypersensitivity reactions, kidney toxicity (e.g., glomerulonephritis, persistentincrease in serum cystatin C, proteinuria, etc.), etc.; AND•Patient has responded to therapy compared to pretreatment baseline in one or more of the following (not all-inclusive):o Increase in dystrophin levelo Improvement in quality of lifeo Stability, improvement, or slowed rate of decline in one or more of the following: ▪Timed function tests (e.g., 6-minute walk test [6MWT], time to stand [TTSTAND], time to run/walk 10 meters [TTRW], time to climb 4 stairs [TTCLIMB], etc.) ▪Upper limb function (ULM) test▪North Star Ambulatory Assessment (NSAA) score▪Forced Vital Capacity (FVC) percent predictedV.Dosage/Administration 1Duchenne Muscular Dystrophy Administer 30 mg/kg intravenously once weekly.VI.Billing Code/Availability InformationHCPCS Code:•J1429 – Injection, golodirsen, 10 mg; 1 billable unit = 10 mgNDC:•Vyondys 53 100 mg/2 mL single-dose vial: 60923-0465-xxVII.References1.Vyondys 53 [package insert]. Cambridge, MA; Sarepta Therapeutics, Inc.; February 2021.Accessed July 2023.2.Topaloglu H, Gloss D, Moxley RT 3rd, et al. Practice guideline update summary:Corticosteroid treatment of Duchenne muscular dystrophy: Report of the GuidelineDevelopment Subcommittee of the American Academy of Neurology. Neurology. 2016 Jul12;87(2):238.3.Bushby K, Finkel R, Birnkrant DJ, et al. Diagnosis and management of Duchennemuscular dystrophy, part 1: diagnosis, and pharmacological and psychosocial management.Lancet Neurol; 2010 Jan; 9(1):77‑93.4.Bushby K, Finkel R, Birnkrant DJ, et al. Diagnosis and management of Duchennemuscular dystrophy, part 2: implementation of multidisciplinary care. Lancet Neurol; 2010Jan; 9(2):177-189.5.Kinane TB, Mayer OH, Duda PW, et al. Long-Term Pulmonary Function in DuchenneMuscular Dystrophy: Comparison of Eteplirsen-Treated Patients to Natural History.Journal of Neuromuscular Diseases 5 (2018) 47–58.6.Muntoni F, Frank D, Sardone V, et al. Golodirsen Induces Exon Skipping Leading toSarcolemmal Dystrophin Expression in Duchenne Muscular Dystrophy Patients WithMutations Amenable to Exon 53 Skipping (S22.001). Neurology Apr 2018, 90 (15Supplement) S22.0017.Institute for Clinical and Economic Review. Deflazacort, Eteplirsen, and Golodirsen forDuchenne Muscular Dystrophy: Effectiveness and Value. Final Evidence Report. August15, 2019 https:///wp-content/uploads/2020/10/ICER_DMD-Final-Report_081519-2-1.pdf. Accessed July 2023.8.Khan N, Eliopoulos H, et al on behalf of the Eteplirsen Investigators and the CINRG DNHSInvestigators. Eteplirsen Treatment Attenuates Respiratory Decline in Ambulatory andNon-Ambulatory Patients with Duchenne Muscular Dystrophy. J. Neuromuscular Dis, vol.6, no. 2, pp. 213-225, 2019.9.Frank DE, Schnell FJ, Akana C, et al. Increased dystrophin production with golodirsen inpatients with Duchenne muscular dystrophy. Neurology. 2020 May 26;94(21):e2270-e2282.doi: 10.1212/WNL.0000000000009233. Epub 2020 Mar 510.Birnkrant DJ, Bushby K, Bann CM, et al. Diagnosis and management of Duchennemuscular dystrophy, part 1: diagnosis, and neuromuscular, rehabilitation, endocrine, andgastrointestinal and nutritional management. Lancet Neurol 2018; 17:251.11.Birnkrant DJ, Bushby K, Bann CM, et al. Diagnosis and management of Duchennemuscular dystrophy, part 2: respiratory, cardiac, bone health, and orthopaedicmanagement. Lancet Neurol 2018; 17:347.12.Servais L, Mercuri E, Straub V, et al.; SKIP-NMD Study Group. Long-Term Safety andEfficacy Data of Golodirsen in Ambulatory Patients with Duchenne Muscular DystrophyAmenable to Exon 53 Skipping: A First-in-human, Multicenter, Two-Part, Open-Label,Phase 1/2 Trial. Nucleic Acid Ther. 2022 Feb;32(1):29-39. doi: 10.1089/nat.2021.0043. Epub 2021 Nov 17.13.Moxley RT 3rd, Ashwal S, Pandya S, et al. Practice parameter: corticosteroid treatment ofDuchenne dystrophy: report of the Quality Standards Subcommittee of the AmericanAcademy of Neurology and the Practice Committee of the Child Neurology Society.Neurology. 2005;64:13–20.14.Gloss D, Moxley RT 3rd, Ashwal S, Oskoui M. Practice guideline update summary:Corticosteroid treatment of Duchenne muscular dystrophy: Report of the GuidelineDevelopment Subcommittee of the American Academy of Neurology. Neurology. 2016 Feb2;86(5):465-72. Doi: 10.1212/WNL.0000000000002337. Reaffirmed on January 22, 2022.15.Darras BT, Urion DK, Ghosh PS. Dystrophinopathies. GeneReviews./books/NBK1119/. Initial Posting: September 5, 2000; Last Revision: January 20, 2022. Accessed on July 18, 2023.Appendix 1 – Covered Diagnosis CodesG71.01 Duchenne or Becker muscular dystrophyAppendix 2 – Centers for Medicare and Medicaid Services (CMS)Medicare coverage for outpatient (Part B) drugs is outlined in the Medicare Benefit Policy Manual (Pub. 100-2), Chapter 15, §50 Drugs and Biologicals. In addition, National Coverage Determination (NCD), Local Coverage Articles (LCAs) and Local Coverage Determinations (LCDs) may exist and compliance with these policies is required where applicable. They can be found at: https:///medicare-coverage-database/search.aspx. Additional indications may be covered at the discretion of the health plan.Medicare Part B Covered Diagnosis Codes (applicable to existing NCD/LCA/LCD): N/AJurisdiction Applicable State/US Territory ContractorE (1) CA, HI, NV, AS, GU, CNMI Noridian Healthcare Solutions, LLCF (2 & 3) AK, WA, OR, ID, ND, SD, MT, WY, UT, AZ Noridian Healthcare Solutions, LLC5 KS, NE, IA, MO Wisconsin Physicians Service Insurance Corp (WPS)6 MN, WI, IL National Government Services, Inc. (NGS)Jurisdiction Applicable State/US Territory ContractorH (4 & 7) LA, AR, MS, TX, OK, CO, NM Novitas Solutions, Inc.8 MI, IN Wisconsin Physicians Service Insurance Corp (WPS) N (9) FL, PR, VI First Coast Service Options, Inc.J (10) TN, GA, AL Palmetto GBA, LLCM (11) NC, SC, WV, VA (excluding below) Palmetto GBA, LLCL (12) DE, MD, PA, NJ, DC (includes Arlington &Novitas Solutions, Inc.Fairfax counties and the city of Alexandria in VA)K (13 & 14) NY, CT, MA, RI, VT, ME, NH National Government Services, Inc. (NGS)15 KY, OH CGS Administrators, LLC。
EMAGE-2D使用说明书

Users’ Manual for EMAGE-2D Laurel Industrial Company, Inc.Table of ContentsChapter 1 System Overview (3)1.1 Brief Description of Main Features of EMAGE-2D (3)1.2 Requirement for Computer System (4)1.3 Install and Run EMAGE-2D (4)Chapter 2 Data Manipulation and Analysis (7)2.1 Data Input (7)2.2 Brief Description about Data Manipulation Toolbar (10)2.3 Viewing Data (11)2.4 Data Manipulation (17)2.5 Saving Data (27)Chapter 3 RRI 2-D Inversion (31)3.1 Choose Data for RRI Inversion (31)3.2 Initial Model Construction (32)3.3 Set RRI Inversion Parameter (35)3.4 Save RRI files (39)3.5 Run RRI Inversion (40)3.6 Retrieve Inversion Result (41)Chapter 4 RM2D Inversion (44)4.1 Brief Description about Model Manipulation Toolbar (44)4.2 Data Selection for RM2D Inversion (46)4.3 Set RM2D Starting Model (47)4.4 Model Display and Modification (49)4.5 Set RM2D Inversion Parameters (52)4.6 Save RM2D Files (53)4.7 Run RM2D Inversion (55)4.8 Retrieve Inversion Result (56)Chapter 5 PW2D Forward (58)5.1 Introduction to Finite Element Modeling (58)5.2 Frequency Definition (61)5.3 Mesh Initialization (61)5.4 Model Display and Manipulation (62)5.5 Set Model 1-D Background (63)5.6 Boundary Extension (63)5.7 Set Site Location (64)5.8 Clear Current Model (65)5.9 Save PW2D Files (65)5.10 Run PW2D Forward (66)5.11 Retrieve PW2D Forward Result (67)Appendix: Software Document for RM2D inversion (68)References (78)Disclaimer (79)Chapter 1 System Overview1.1 Brief Description of Main Features of EMAGE-2DEMAGE-2D is a MT/AMT data processing and modeling software package, which can be divided into four modules including Data Manipulation and Analysis, RRI Inversion, RM2D Inversion and PW2D Forward. Below is a brief introduction to the major features of each module.1.Data Manipulation and Analysis∙Viewing data parameters such as apparent resistivity, impedance phase, coherency, skew, strike, polar diagram, Bostick transform etc. ∙Impedance rotation∙Data interpolation∙Frequency and site selection∙TE/TM mode definition∙Static shift analysis and correction∙Duplicate site handle2.RRI Inversion∙Data selection for inversion∙Starting model construction∙Set inversion parameters∙Save RRI files and run RRI∙Retrieve and display inversion result3.RM2D Inversion∙Data selection for inversion∙Starting model construction∙Model manipulation∙Set inversion parameters∙Save RM2D files and run RM2D∙Retrieve and display inversion result4.PW2D Forward∙Frequency selection for forward problem∙Model construction and manipulation∙Auto padding for the extension of model boundary∙Save PW2D files and run PW2D∙Retrieve and display forward calculation result1.2 Requirement for Computer SystemEMAGE-2D is a window application that can be run on Window 95/98, Window NT 4.0. It is recommended to run EMAGE-2D on a high performance computer because of the computational intensity of 2-D inversion and forward algorithm.1.Minimum RequirementCPU: Pentium 200Memory: 32 megabytesHard Disk: 100 megabytes free spaceDisplay: support 800X600 resolution under 256-color mode2.Recommended RequirementCPU: Pentium-II 400Memory: 128 megabytesHard Disk: 500 megabytes free spaceDisplay: support 1024X768 resolution under 16 bites color mode1.3 Install and Run EMAGE-2DEMAGE-2D InstallationInsert the EMAGE-2D CDROM into your computer‟s CDROM drive, then run the file setup.exe so the installation wizard will be launched. It will guide you through the entire installation procedure.When you begin the setup program, you will be presented the Choose Destination Location dialog (figure 1.1) which gives you chance to specify which folder to install EMAGE-2D.EMAGE-2D executable and all other supported files will be automatically copied into this folder by installation wizard. The default folder isC:\EMAGE-2D. If you hope to change it, click Browse button, then the Choose Folder dialog (figure 1.2) will be displayed on the screen. You can specify the EMAGE-2D installation folder on it, then click OK button to return Choose Destination Location dialog in which you can click Next button to begin to copy files.Figure 1.1 Choose Destination Location DialogFigure 1.2 Choose Folder DialogIf your operation system is Window NT, you also need run ntdrv.exe under subfolder “NTDRV” in the EMAGE-2D folder to install dongle driver on your machine.Run EMAGE-2DEMAGE-2D can only be run on the machine on which the hardware key (dongle) supplied with EMAGE-2D is installed. In order to install dongle, it is better shut down your computer first, then attach the dongle to the parallel printer port of your computer. You can attach the 25-pin connector of the printer to the other end of the key. After making sure the dongle is installed properly, click EMAGE-2D item on the Program submenu of Start menu on your computer to launch EMAGE-2D. You also can double click EMAGE-2D.EXE in the directory where EMAGE-2D is installed to run it.Chapter 2 Data Manipulation and Analysis2.1 Data InputEMAGE-2D supports Z file format of EH4, RES file format of MT-1 and the output of PW2D forward output as input data at present time.1.EH4 Data InputFor EH4 data, there are two ways to prepare input data. Below is step by step description about how to input EH4 data into EMAGE-2D.1)Using @(or @l)File as Input DataFigure 2.1 Open EH4 @ Files Dialog(1)Create a working directory in your hard disk.(2)For high frequency data, copy @ file and the impedance files (the files preceded by Z) of your survey data from your EH4 instrument into the working directory; For low frequency data copy @l and the impedance files (the files preceded by W) into the working directory. (3)Select Open EH4 @ file…in File menu, then Open EH4 @ file dialog (figure 2.1) will be popup on the screen. When Auto Selectcheckbox is checked, EMAGE-2D will determine whether the data is high or low frequency data according to the file name. Sometime you may rename @ or @l file for some reasons. In this case, EMAGE-2D has no idea about the data type, so you need set it manually. High Freq and Low Freq radio button will be enabled after Auto Check is unchecked. If the data to be input is high frequency data, High Freq should be checked, otherwise, Low Freq should be checked.(4)Click OK button on the dialog to begin inputting data.(5)When an impedance file in @ or @l does not exist in the current directory, a warning message will be given to indicate that this file does not exist in the current directory and inquire whether to continue without it or quit to check the data.2)Edit EH4 line definition file (EH4 File) as input data.Figure 2.2 Open EH4 File Dialog(1)Create a working directory in the hard disk, then copy the impedance files preceded by Z or W into the working directory.(2)Use text editor such as Notepad in Windows or Edit on Dos promptmode to create a line definition file with an extension of EH4. If you use word processor such as Word to create line definition file, be sure save it as pure text format. Below is an example to demonstrate the format of EH4 line definition file.Line 1 Format: EH4Line 2 This is an example of line definition file for EH4 dataLine 3 There are three sites in the data setLine 4 Data:Line 5 Ztest.001 X: 0 Y: 0 Z: 0Line 6 Ztest.002 X: 30 Y: 0 Z: 0Line 7 Ztest.003 X: 60 Y: 0 Z: 0Line 1 always is “Format: EH4”, indicating that the input data is EH4 data. After that, you can write any number of comment lines (such line 2 and line 3 in above example). The “Data:” line (line 4 in above example) after comment lines indicates the lines below are the data lines that will be taken as input by EMAGE-2D. Each site takes one line consisting of the impedance file name and coordinates for the site.(3)Click Open EH4 File in File menu to popup Open EH4 File dialog (figure 2.2). Open EH4 data line definition file to input data.2.MT-1 Data Input(1)Create a working directory in the hard disk, then copy the RES files output by MT-1 processing program into the working directory.(2)Use text editor such as Notepad in Windows or Edit on Dos prompt mode to create a line definition file with an extension of MT1. If you use word processor such as Word to create line definition file, be sure save it as pure text format. Below is an example to demonstrate the format of MT-1 data line definition file.Line 1 Format: MT-1Line 2 This is an example of line definition file for MT-1 dataLine 3 Data:Line 4 Demo1.res X: 0 Y: 0 Z: 400Line 5 Demo2.res X: 1000 Y: 0 Z: 510Line 6 Demo3.res X: 2000 Y: 0 Z: 450Line 1 always is “Format: MT-1”, indicating that the input data is MT-1 data. After that, you can write any number of comment lines (line 2 in above example). The “Data:” line (line 3 in above example) after comment lines indicates the lines below are the data lines that will be taken as input by EMAGE-2D. Each site takes one line, consisting of the impedance file name and coordinates for the site.Figure 2.3 Open MT-1 File Dialog(3)Click Open MT-1 File in File menu then popup Open MT-1 File dialog (figure 2.3). Open MT-1 data line definition file to input data. 3.PW2D Forward Calculation Data InputDetailed description about how to input PW2D data is discussed in Chapter 5.2.2 Brief Description about Data Manipulation ToolbarFigure 2.4 Data Manipulation ToolbarIn order to edit and display the input data, user need to access the controls on the Data Manipulatio n Toolbar (figure 2.4). When data input has been done, the toolbar will be enabled. Below are brief descriptions about themain functions of the controls from left to right in the toolbar.Plot Button:Click it to refresh the content in plot area.Edit Button:Any graphical edit operation cannot be functioned unless this button is checked.Mask Button:This button is used to control whether or not to display the disabled frequencies. When it is checked , the disabled frequencies will not be displayed, otherwise, the disabled frequencies will be displayed in gray color.Static Shift Button:This button is used control to display the data without static shift correction or corrected data. If it is unchecked, the displayed data will be raw data without static correction, otherwise, corrected data will be displayed. Another function of this button is for static correction operation. Static shift correction operation is allowed only if the button is checked. Interpolation Button:It is used to control if display raw data or interpolated data. If this button is unchecked, raw data will be displayed, otherwise you can view and edit the interpolated data.Switch Button:When this button is checked, you can switch XY and YX mode impedance (rotate±90 °) frequency by frequency.Plot Type Selection List Box:Can be used to select different parameters to view and edit.Site Selection List Box:Set the selected site as current site, so you can view and edit the parameters of the current site.2.3 Viewing DataEMAGE-2D can display twenty-first type of parameter about the data set (figure 2.5)1.Site Location MapSelect this item to display Site Location Map. After data input is completed, EMAGE-2D will display Site Location Map in plot area(figure 2.6). A triangle sign represents each site. The impedance file name of the site taken as site name is displayed above or below it. If you hope not to display site name on the map, click Show Site Name in Site Location Map in Data Manipulation menu to uncheck it.Figure 2.5 Plot Type In Selection List BoxFigure 2.6 Site Location Map2.Apparent Resistivity CurveThe apparent resistivity curve of current site will be displayed in plot area when user selects Apparent Resistivity item in Plot Type Selection list box (figure 2.7). For raw data, XY and YX mode are represented as rectangle and triangle signs respectively. If interpolated data is displayed, XY and YX model will be shown by red and blue dot respectively. Mask, Static Shift and Interpolation button on the Data Manipulation toolbar can be used to control the display mode of apparent resistivity curve.∙When Mask button is checked, the disabled frequencies will not be shown, otherwise, the disabled frequencies will be displayed in gray color.∙When Static Shift button is checked, the data after static shift correction will be displayed, otherwise the uncorrected data will be shown.∙When Interpolation Button is checked, the interpolated data will be displayed, otherwise the raw data will be shown.Figure 2.7 Apparent Resistivity Curve3.Impedance Phase CurveThe impedance phase curve of current site will be displayed in plot areawhen you select Impedance Phase item in Plot Type Selection list box. For raw data, XY and YX mode are represented as rectangle and triangle signs respectively. If the interpolated data is displayed, XY and YX model will be shown by red and blue dot respectively. The display mode of impedance phase curve controlled by Mask and Interpolation button is the same as that of apparent resistivity.4.StrikeThe strike curve of current site will be displayed in plot area when you select Strike item in Plot Type Selection list box. The display mode of strike curve controlled by Mask and Interpolation button is the same as that of apparent resistivity.5.SkewThe skew curve of current site will be displayed in plot area when you select Skew item in Plot Type Selection list box. The display mode of skew curve controlled by Mask button is the same as that of apparent resistivity.6.CoherencyThe coherency curve of current site will be displayed in plot area when you select Mult Coh (E, H) item in Plot Type Selection list box. The data of XY mode and YX mode is represented as rectangle and triangle signs respectively. The display mode of coherency curve controlled by Mask button is the same as that of apparent resistivity.There is no coherency data in the MT-1‟s RES file, so EMAGE-2D set them to 1 in order to be compatible with EH-4 data.7.Polar DiagramThe polar diagram of current site will be displayed in the plot area when you select Polar Diagram item in Plot Type Selection list box (figure 2.8). The polar of each frequency is contained in a rectangle where the frequency value is printed on upper part of the rectangle. Red polar and blue polar are principal impedance and auxiliary impedance components respectively.Figure 2.8 Polar Diagram8.Bostick TransformThe relation between impedance and frequency can be transformed to the relation between resistivity and depth by Bostick transform, roughly reflecting the earth resistivity distribution versus depth.The Bostick transform curve of current site will be displayed in plot area when you select Bostick Transform item in Plot Type Selection list box. For raw data, XY and YX mode are represented as rectangle and triangle signs respectively. If the interpolated data is displayed, XY and YX model will be shown by red and blue dot respectively. The display mode of Bostick transform curve controlled by Static Shift and Interpolation button is the same as apparent resistivity.Cross SectionsIn order to view cross section of the data, you need to define profile first. If you want to show the cross section of TM or TE mode data, you shoulddefine the mode of each site also. A detailed description about how to define profile and TM/TE mode is presented later in this manual. EMAGE-2D can show twelve types of cross sections (table 2.1).Table 2.1 The type of cross section Item in the listbox of plot typeApparent resistivity in XY mode App. Resistivity Freq Section-RhoXY Impedance phase in XY mode Phase Freq Section-PhsXYApparent resistivity in YX mode App. Resistivity Freq Section-RhoYX Impedance phase in YX mode Phase Freq Section-PhsYXApparent resistivity in TM mode App. Resistivity Freq Section-RhoTM Impedance phase in TM mode Phase Freq Section-PhsTMApparent resistivity in TE mode App. Resistivity Freq Section-RhoTE Impedance phase in TE mode Phase Freq Section-PhsTEBostick resistivity in XY model Bostick Depth Section-BostXYResBostick resistivity in YX model Bostick Depth Section-BostYXResBostick resistivity in TM model Bostick Depth Section-BostTMResBostick resistivity in TE model Bostick Depth Section-BostTERes Static shift and Interpolation buttons on Data Manipulation toolbar can be used to control display manner of cross section. When Static Shift button is checked, the data you have seen is statically corrected data, otherwise uncorrected data is shown. Interpolation button acts similar way, checked for interpolated data, unchecked for raw data.EMAGE-2D will create default color scale for each type of cross section according to data value. If you want set it manually, click Set Color Scale For Contour in Data Manipulation menu and popup Set Color Scale For Contour dialog (figure 2.9). Double-click any item in Scale List box, the scale value will appear in Enter Color Scale Value so you can modify it manually. Default Color Scale checkbox gives you the option to use default color scale or not. If you check Blank No Data Area, the area without data will be blanked.Static Correction Reference CurveIn order to display static correction reference curve, you need also define profile first. After that, click Static Correction Reference Curve to display it. Please refer to Static Shift Correction section later in this manual for thedetailed discussion about it.Figure 2.9 Set Color Scale For Contour Dialog2.4 Data ManipulationMost of data edit operation will need to access Data Manipulation menu and Data Manipulation toolbar. If no explicit indication, submenu mentioned in this chapter refers to the item in Data Manipulation menu and toolbar is taken for Data manipulation toolbar.1.Duplicate Sites HandleIf there are duplicates sites whose X and Y coordinates are same, Check Duplicate Sites submenu will be enabled. Select it and popup Check Duplicate Sites modeless dialog (figure 2.10). When the dialog is displayed on the screen, you can do other operation outside the dialog so it is convenient to check duplicate sites‟ data quality while dealing with them.The first group of duplicate sites found by EMAGE-2D will be appear in Duplicate Sites list box when you open the dialog first time. EMAGE-2D will search another group of duplicate sites if there are ones when you click Find Next button. Select Restart will search duplicate sites again from very beginning. If you decide delete some site, highlight the site name in list box, then click Delete button to delete it. Sometime it may bebetter to combine duplicate sites into a new site. Click Combine… button to bring Input Combined Site Name dialog (figure 2.11) up. Put site name in Combined Site Name as the name of the new site. If you hope to delete the old sites after combination, please check Delete Old Sites checkbox. After click OK button, the combined site will display in Duplicate Site list box of Check Duplicate Sites dialog. It is recommended to disable bad frequencies of duplicate sites before doing combination.Figure 2-10 Check Duplicate Sites DialogFigure 2-11 Input Combined Site Name Dialog2.Fix ImpedanceIn MT/AMT theory, the impedance is calculated under right-handed coordinate system. If the orientation of electrical or magnetic sensors isnot set this way, the calculation of skew and polar will be incorrect, the auxiliary impedance component of polar and skew will be anomaly big. If the orientation of some site is suspected not being set properly, EMAGE-2D will fix it automatically. Sometime EMAGE-2D will make wrong decision because of the noise in the data and the complexity of the earth. In this case, you need fix it manually by check the skew and polar diagram. When the skew and auxiliary impedance component is too big, you can click Fix Impedance submenu to fix it.3.Vector Versus Tensor Data of EH4Vector impedance is not stable as the polarizing direction of incident electromagnetic field varies with time. This is the very reason why we often use tensor impedance for data interpretation in MT. When the measure time is short such as EH4 survey, the polarization may not change too much. It may be acceptable to use vector data for interpretation. In field survey, it is not unusual to have good data in one direction but bad in another direction due to culture noise. It maybe causes both XY and YX mode data noisy if you use tensor impedance data because the calculation of tensor data will use both direction data. As for vector impedance data, you only need electrical field in one direction and magnetic field in the perpendicular direction to get vector data in this direction. In this case, you may get good data in one direction for interpretation. This is why both vector and tensor data are contained in impedance file of EH4 data. It is recommended to use tensor impedance if the data of both directions is good.You can switch between tensor and vector data by click Show EH4Vector Data submenu. If vector data is being used, a check sign will appear on the left of the submenu. By the way, if you have done rotation on the data, the data will be tensor because there is no way to rotate vector data.4.Site and Frequency Selection(1)Site SelectionThere are two ways to select sites into current data set.Figure 2.12 Data Selection DialogThe first one is to select sites on Data Selection dialog. Select Data Selection submenu to bring up Data Selection dialog (figure 2.12). A site will be selected into the current data set if you highlight it in Site Name list box, unhighlight it will delete it from the current data set. Clicking site name in the list box will switch between selection and deletion. You can select or delete all sites by clicking Select All Sites button. If all sites are already selected, clicking Select All Sites button will delete all sites, otherwise all sites will be selected. Actually, deleted sites will not be considered it in data analysis, display and interpretation process. You can include it later by reselecting it.The second way for site selection can be done though Site Location Map.A triangle sign represents each site. When Site location Map is shown, check Edit button on the toolbar first. Clicking the site sign will switch between selection and deletion. The selected sites are printed in blue color,deleted ones in gray color.(2)Frequency SelectionThere are three ways to select frequency.The first one is to do it in Data Selection dialog that is similar to site selection. Highlight a frequency in Frequency list box of the dialog (figure 2.12) to enable it, unhighlight it to disable it. Every frequency contained in any site will be listed in Frequency list box. It is not necessary to have all sites have same frequencies. If you enable or disable any frequency in the list box, this frequency will be enabled or disabled from the sites that have the data of this frequency. Select All Freq button can also be used to enable or disable all frequencies in the way which is similar to Select All Sites button for site selection.Figure 2-13 Frequency Auto-Selection DialogThe second way is to select frequencies automatically in Frequency Auto-Selection dialog. Selecting Frequency Auto-Selection submenu to popup Frequency Auto-Selection dialog (figure 2.13). Input cut-off value in Select Freq. By Coh(>=)so the frequencies will be disable automatically when their coherencies are below this value. Similarly, the frequencies will also be disabled when their skews are greater than the value in Select Freq. By Skew (<=).In other hand, you are provided an option to select frequencies for the current site or all sites in Site Selection radio button group and to select frequencies for which mode data in ModeSelection radio button group.The third way is to select frequencies on apparent resistivity, impedance phase and coherency curves. Interpreter normally needs to analyze data site by site during interpretation process and delete bad frequencies. Below are some suggestions for frequency selection.∙Coherency: It is recommended to delete the frequencies which coherency is below 0.6.∙Skew: Theoretically speaking, skew is a measure of the three dimensionality of the resistivity distribution near the site. But the noise in data will also make it big. When the skew of one frequency is much bigger than that of the rest, it is possible to be caused by noise and need to be deleted.∙Smoothness: Apparent resistivity and impedance should be smooth and continuous for high quality data. The outliers should be deleted before interpretation.To select frequencies this way, you need check Edit button on the toolbar first, then click left and right buttons of mouse to enable or disable frequencies XY and YX mode data respectively.5.Profile DefinitionIn order to display cross section, calculate static shift correction reference and prepare data for 2D inversion, you need define profile first. There are two methods to define profile in EMAGE-2D.(1)Define Profile in Data Selection DialogSelect beginning and ending site of the profile in Starting Site and Ending Site respectively in Data Selection dialog (figure 2.12), then click OK to complete profile definition. After that, a black line will be plotted in Site Location Map to indicate the orientation of the profile.(2)Define Profile in Site Location MapCheck Edit button in the toolbar and hold down Ctrl key in your computer keyboard, then click at the starting position of the profile on the map andmove mouse cursor while keeping left button of the mouse down. When the cursor has been moved to the ending position of the profile you hope to put, release mouse button to finish profile definition.6.Impedance RotationThe impedance of XY and YX mode will be same if the geology is one-dimensional. For non-1D geology, the data of XY and YX mode will be different. The impedance tensor can be rotated mathematically to any other orthogonal axis orientation. If the geology is truly two-dimensional this rotation will reach an angle such that auxiliary impedance become zero and the principal impedance becomes the principal impedance. This angle yields the impedance strike once it has been determined which of the XY or YX components reflects the impedance for the electrical field which is parallel to the strike. When we can rotate impedance so that X direction is perpendicular to the strike of the structure. The XY and YX components are defined as TM and TE mode respectively. If we undertake 1-D interpretation, it is better use the data of TE mode because 1-D inversion result of TE data is closer to the real geology than that of TM data. For 2-D inversion, usually it is best to use the combination of TE and TM data. If you choose one direction of data to do 2-D interpretation, it is widely argued that in 2-D model the goal should to match the TM curve, as it has higher lateral resolution and is less affected by 3-D distortions then the TE mode.There are five types of rotation implemented in EMAGE-2D(1)Analytic RotationImpedance can be rotated to principal axes, which is a related but different concept from the strike of structure, by analytic rotation. In two-dimensional geology, both strike and tip of structure are principal axes. Interpreter should refer to the geology and other kind information to determine if impedance is rotated to strike or tip.(2)Zxy Maximum RotationRotate impedance to one of two principal axes so that the apparent resistivities of X direction (ρx y) are always greater than those of Y direction (ρy x).。
分子诊断学遗传性疾病的分子诊断

simultaneously:同时地;
multiplex:多样化; exon:外显子;
deletion:缺失
01
02
Phenylketonuria is an inborn error of metabolism resulting from a deficiency of phenylalanine hydroxylase. There are many techniques that can be used to mutation screening, such as PCR-STR, PCR-SSCP, PCR-RFLP, PCR-DGCE, and so on.
主要是由于肝内苯丙氨酸羟化酶(phenylalanine hydroxylase, PAH)严重缺失所致的苯丙氨酸代谢异常,为常染色体隐性遗传病 临床表现:智力障碍、色素减少、尿特殊气味及神经和精神症状
分子诊断方法:
1
PCR-STR连锁分析
2
PCR-RFLP
3
多重ASPCR法 PCR-DGGE法
Phenylketonuria:苯丙酮尿 phenylalanine hydroxylase:苯基丙氨酸羟化酶
Cystic fibrosis(CF) is caused by mutations in the CFTR gene. Five tests are most frequently used: resctriction enzyme analysis, the heteroduplex analysis, ARMS, reverse hybridization and OLA.
按照合成速率降低的珠蛋白类型分为α、β、γ、δ地中海贫血
α-地中海贫血( α -thalassemia) α0地贫是α链完全不能合成者 α+地贫是部分α链合成者
MODULE GUIDE

International Finance7 BSP 0354 Academic Year - 2010/11Semester - A Module Leader – Edward KerrContents:1. Contact details for the module leaders (and teaching team)2, Module aimsThe aim of the International Finance Module is to:understand the financial problems specific to multi-nationalcompanies, together with the associated theory;understand techniques for managing these problems.3. Format of deliveryOne hour Lecture and one hour Seminar each week4. Use of StudyNetSTUDYNET is a virtual learning environment (VLE) developed by the University of Hertfordshire to assist student learning. It provides access to web-pages, lecture notes and other learning materials as well as e-mail facilitiesEach week, tutorial answers and/or additional materials will be uploaded to STUDYNET.You should visit the module site regularly during the week. This will indeed by our major source of communication.The site will be used to announce any unavoidable changes such as room/time of tutorials etc.Please note that it is the student‟s responsibility to access additional informationand/or notices relating to this module from StudyNet.W here to find what you want on Studynet:∙Module Guide in Module Information–∙DMD (Definitive Module Document.) in Module Information∙Reading list in Module Guide in Module Information∙Lecture slides in Teaching materials∙Assignment details in Module Guide in Module Information∙Grading criteria in Module Guide in Module Information∙Seminar groups in Module Information5. (a) Weekly programme to include: (provisional and subject to change)It will be noted that many of the Seminars include a discussion of topics arising from the Lectures and Text Book readings. In order to act as a focus for this activity, a number of specific questions are given at the end of the PowerPoint presentation for each Lecture.5. (b) Reading:Essential Text:Buckley, AMultinational FinanceFT Prentice-Hall5th Edition - 2004ISBN: 0-273-68209-1Other Texts:As advised by Module Tutor during Lecture Sessions6. (a) Assessment Detail (100% coursework. No examination)There is a 2-part assessment, part 1 carries 80%, part 2 carries 20%.PART 1 (80% weighting)This part of the assessment requires the preparation of TWO reports, each of which carries40 marks.:∙Report # 1:This is a report of an academic nature, which invites students to critically evaluateInternational Financial theory. It will be due for submission not later than 23.30 on MON 06 DEC 10.∙Your Assignment is to answer the following question:"The recognition, measurement and management of Exposure and Risk is one ofthe primary roles of the Treasurer of an Multi-National Company.Explain the Exposures and Risks that the Treasurer would need to recognise, theways in which the Treasurer would seek to measure them and the contribution thateffective management of these Risks and Exposures would make to CompanyProfit."REPORT: This is an individual report.WORD LIMIT: 2,500 words.FORMAT: Present this report as a Management Report, suitable for presentation toa member of the Board of Directors of your Company. Students are advised toensure that there is a clear concise conclusion / recommendation - reports that donot contain this will be penalised.OTHER ADVICE: Students are invited to illustrate their submissions with charts,diagrams and suitable calculations where these would serve to add to the clarity ofthe report and the points being made within the report.∙Report # 2:This is a more practical piece of work, which will take the form of a written analysis of aCase Study. It will be due for submission not later than 23.30 on MON 17 JAN 11.The following aspects are common to both pieces of work:∙The upper word limit is 2,500 words∙This is an INDIVIDUAL report. Whilst students are invited to discuss theassignment between themselves, the submitted report MUST be individually-prepared∙Credit will be given for clearly-argued reports, with the argument being supported by appropriate evidence and theory. Clear conclusions and, if appropriate,recommendations MUST be given. Students who do not include these features intheir reports can expect to receive poor marks∙Reports should be appropriately structured. Advice will be given on this. These are reports not essays∙Reports must be submitted via the Submission Box on StudyNet by the deadline date / time. This copy will be considered to be the definitive submission. There arepenalties for late submission∙We may ask for an additional hard-copy version of the report∙We expect to report marks and feedback within 14 days of submission, but this cannot be guaranteedPART 2 (20% weighting):This part of the assessment requires the completion of TWO “Class Tests”. These will be of a Multiple-Choice nature and will be similar to the Test Banks in Buckley.At least six weeks‟ notice will be given of the date of each Class Test - attendance at each Class Test is compulsoryPASSING THE MODULE:To pass the Module, it is necessary to score at least 50% across the totality of the Module assessments. It is not necessary to pass each element of assessment.6 (b) This is the likely Module Workload for this particular module,6. (c) Deferral/Referral AssessmentThe detail of refer/refer coursework will be on StudyNet by 3rd May 2011, at thelatest.Hand in DateThe submission date for all referred/deferred coursework assessments will be 27thJune 2011. This deadline relates to semester A, semester B and semester A/Breferred/deferred coursework.7. (a) FeedbackFeedback from assessed coursework assignments will be normally provided usingthe UHBS …Assessment Feedback Form' which will provide feedback on manyaspects of your work. If work has been submitted electronically then similarfeedback may be supplied via the StudyNet feedback system.Formative and/or general feedback may also be given in class time.7. (b) UHBS reserves the right to use electronic means to identify plagiarism.8. The grading criteria for this module can be found in Appendix A.9. Useful resources for support with your modules▪Academic Skills Unit (ASU) /go/asu▪Information HertfordshireInformation Hertfordshire Toolkit for Business and may help you choose thebest sources for different types of business information and include Onlinetutorials and quizzes .▪Student contract /go/asu10. Note - All aspects of the module are potentially examinable.The information given in this Module Guide is believed correct, but the Business Schoolreserves the right, at its discretion, and for any reason, to make changes to the Guide,syllabus and/or module without prior notice.University of Hertfordshire Business SchoolModule Guide 2010-11APPENDIX A GENERIC GRADING CHARACTERISTICS OF POSTGRADUATE WORKHOW YOUR POSTGRADUATE WORK WILL BE ASSESSEDThe university records all assessed (ie summative) marks on a 0-100 numeric grade system. Not all work is amenable to being marked reliably using such fine grading. In such cases, the use of the following 27 point scale is recommended.** Grades above 90 (eg 92, 95, 98) should only be awarded for work of truly exceptional quality and are likely to be used very sparingly.。
芯片测试仪设备操作指南说明书

MechanicsOscillationsElliptical Oscillation of a String PendulumDESCRIPTION OF ELLIPTICAL OSCILLATIONS OF A STRING PENDULUM AS THE SU-PERIMPOSITION OF TWO COMPONENTS PERPENDICULAR TO ONE ANOTHER.UE1050121 06/15 MEC/UDFig. 1: Experiment set-upGENERAL PRINCIPLESDepending on the initial conditions, a suitable suspended string pendulum will oscillate in such a way that the bob’s motion describes an ellipse for small pendulum deflections. If the motion is resolved into two perpendicu-lar components, there will be a phase difference between those components.This experiment will investigate the relationship by measuring the oscillations with the help of two perpendicularly mounted dynamic force sensors. The amplitude of the components and their phase difference will then be evaluated. The phase shift between the oscillations will be shown directly by displaying the oscillations on a dual-channel oscilloscope.Three special cases shed light on the situation:a) If the pendulum swings along the line bisecting the two force sensors, the phase shift φ = 0°.b) If the pendulum swings along a line perpendicular to that bisecting the two force sensors, the phase shift φ = 180°.c) If the pendulum bob moves in a circle, the phase shift φ =oscillation directions of the string pendulum under in-vestigationLIST OF EQUIPMENT1 SW String Pendulum Set 1012854 (U61025)1 SW Stand Equipment Set 1012849 (U61022)1 SW Sensors Set @230 V 1012850 (U61023-230) or1 SW Sensors Set (@115 V 1012851 (U61023-115) 1 USB Oscilloscope 2x50 MHz 1017264 (U112491)SET-UP∙Screw the stand rods with both external and internal threads into the outer threaded sockets of the base plate. ∙Extend both rods by screwing rods with external thread only onto the ends of them.∙Attach double clamps near the top of both stand rods and turn them to point inwards so that the slots are vertical and facing one another.∙Attach both springs from the spring module to the lugs on the cross bar (angled side).∙Hang the large loop of string from the lug on the flat side.Fig. 3 Assembly of spring module∙Connect the springs and vector plate to the hook of a dynamic force sensor with a small loop of string and care-fully pull everything taut.∙Attach the force sensor with the screw tightened by hand. ∙Attach the second force sensor in the same way.Fig. 4 Attachment of dynamic force sensors to spring module∙Pull the string through the eyelet of the spring module (in the middle of the metal disc).∙Thread the end of the string through the two holes of the length adjustment slider.Fig. 5 Set up of string3B Scientific GmbH, Rudorffweg 8, 21031 Hamburg, Germany, ∙Clamp the cross bar into the slots of the two double clamps, suspend a weight from the end of the string and set up the height of the pendulum using the length ad-justment slider.Fig. 6 Attachment of cross bar in double clamp ∙ Connect the force sensors to the inputs for channels A and B of the MEC amplifier board.∙ Connect outputs A and B of the MEC control unit to channels CH1 and CH2 of the oscilloscope.EXPERIMENT PROCEDURE∙Set the oscilloscope time base time/div to 1 s, select a vertical deflection for channels CH1 and CH2 of 50 mV DC and set the trigger to “Edge” mode, “Normal” sweep, “Source CH1” and “Slope +”.∙Slightly deflect the string pendulum and allow it to oscil-late in a plane which bisects the alignment of the two force sensors (oscillation path a in Fig. 2). Observe the oscilloscope trace and save it.∙Slightly deflect the string pendulum and allow it to oscil-late in a plane which is perpendicular to the one which bi-sects the two force sensors (oscillation path b in Fig. 2). Observe the oscilloscope trace and save it.∙Slightly deflect the string pendulum and allow it to oscil-late in a circle (oscillation path c in Fig. 2). Observe the oscilloscope trace and save it.SAMPLE MEASUREMENT AND EVALUA-TIONWhen the pendulum is oscillating in the plane of the bisecting angle between the sensors, the two sensors will experience symmetric loading (oscillation path a in Fig. 2). The signals from the two force sensors will be in phase, i.e. the phase shift between them will be φ= 0° (Fig. 7).Fig. 7: Oscillation components for a string pendulum swingingalong the line bisecting the two force sensorsWhen the pendulum is oscillating in the plane perpendicular to the bisecting angle between the sensors, the two sensors will experience asymmetric loading (oscillation path b in Fig. 2). The signals from the two force sensors will be wholly out of phase, i.e. the phase shift between them will be φ= 180° (Fig. 8).Fig. 8: Oscillation components for a string pendulum swingingalong the line perpendicular to that bisecting the two force sensorsThe circular oscillation is a superimposition of the oscillations along the plane of the bisecting angle between the sensors and the angle perpendicular to it with a phase shift of φ = 90°(Fig. 9).Fig. 9: Oscillation components for a string pendulum describ-ing a circle。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Year 1964 1965 1966 1967 1968 Total
Number 17 13 15 15 12 72
10
Types of Statistical Figure
⑴Bar Diagram、 ⑵Circle Diagram ⑶Percentage bar chart、 ⑷Line Graph ⑸ histogram ⑹ scatter gram (7)…
Frequency distribution Table Groups (1) 129~ 132~ 135~ 138~ 141~ 144~ 147~ 150~ 153~ 156~ 159~162 Total Number (2) 2 2 8 20 26 25 20 9 3 2 1 118 Meadians of Groups (3) 130.5 133.5 136.5 139.5 142.5 145.5 148.5 151.5 154.5 157.5 160.5 —
1
The maximum width of the man skull (mm)
2
Chapter2 Data Description
MBA课程 数据分析技术与方法
3
•
Geysers, is a kind of hot springs. Sometimes its injection interval is not stable. "Old Faithful" geyser is in Yellowstone National Park in Ohio (Ohio) State which is one of the world's most famous geyser. Visitors hope not to wait too long of the fountain eruption.
2:06
1min41s
5ve statistical analysis
Descriptive statistics analyzes a various features of a set of
data, so that we can describe the characteristics of samples even of the population.
What are the differences among those concepts?
16
Pie Diagram
The area of a circle represents a group of data as a whole, while the ratio of a circle sector area and the whole circle represents each percentage component of data.
6
Statistical Table
1 2 3 4 5 6 7 8 9 10 Wang XX Li XX Zhang X X Li XX Li XX Liu X X Chen X X Wang X X Chen X X Wu XX 30 42 18 26 22 29 19 22 25 23 Worker Cadres Student Worker Worker Teacher Peasant Worker Worker Worker
Pie Diagram of 40 students’ standing jumping scores
1point2.5% 2points15% 3points25% 4points32. 5% 5points25%
17
Difference between the two kinds of charts
30
20
10
Frequency
Std. Dev = 48.43 Mean = 435.8 0 300.0 350.0 400.0 375.0 425.0 450.0 500.0 525.0 550.0 600.0 325.0 475.0 575.0 N = 120.00
选择反应时间
13
A frequency distribution table for 118 13-yearold girls’ Height (cm)
Weights 13. 54% 18.22% 1.82% 41.67% 32.64% 24.75% 100%
Table Body
Table Feet
Source: China Statistical Yearbook
9
Modified Example for Statistical Table
Table 2-15 Third group of patients Survival and death yearly (Original Table)
The basic structure of tables:
title, headings, lines, numbers, and notes.
7
Statistical Table for 40 students’ Standing Jumping Scores
Scores 1 2 3 4 5
Number 1 6 10 13 10
5
statistical table and statistical graph
are two important methods of statistical description. They are not only simple, straightforward, easy to understand and accept, but also are ease of comparison and analysis. For the same facts, the narrative text may need to be long-winded explanation, while tables or charts can be clear at a glance.
Time Interval 58min 82min
Predict time of next eruption 7:33am 8:54am
8:59
10:12 11:46
1min51s
4min33s 1min42s
58min
89min 58min Lunch Time
9:57am
11:41am 12:44am
14
30
20
10
This figure shows a trend. There are more numbers in the middle and less in both side, and it is almost symmetry. We call it follow Gaussian distributions
Table 2-16 1964~1968Death Ratio of acute myocardial infarction (Modified Table) Death Patients In Acute Hospital Stage 8 7 5 4 7 6 6 6 4 4 30 27 Death Ratio(%) In Acute Hospital Stage 47.1 41.2 38.5 30.8 46.7 40.0 40.0 40.0 33.3 33.3 41.7 37.5
Here are standing long jump scoring records of 40 students : 2,4,3,5,3,5,4,4,3,5 1,5,3,3,2,4,3,5,4,4 4,5,2,3,2,5,4,5,2,3 4,4,3,5,2,4,5,4,3,4 1. From the above data, can you tell the exact number of students who got 4 points? 2. If a student scores 3 points, can you quickly figure out his level in the class?
• Under the same conditions, pressive strength, caliber, length of products. • Length and weights of the same kind of organism; • Measurement error of the same object;
11
Bar Diagram Chart:
15 13
Bar Diagram: Combined by Strips of equal width or length.
10 6 5 1 0
1分 2分
10
10
3分
4分
5分
12
Population Distribution with Histogram
Histogram
•
Every 40 to 126 minutes, Old Faithful erupts. Yellowstone staff are always able to accurately predict the next eruption time.
Start Time 6:35 7:32
Duration 1min55s 4s
8
Header
2006, China's land situation
Unit:1000 hectares
Type Arable Land Forest Inland water area Lawn Spendable Lawn Others Total
Area 13004 17491 1747 40000 31333 23758 96000
