【A3】Bitcoin Isnt Broken
BITCOIN

In the end,I want to finish my speech with a song of John Lennon.
That's all,thank you!
The second way is transaction.
• You can exchang it in a bitcoin trading platform just like stock exchange. • Its' price changes as the amount of exchange.
Bitcoin
26%
7%
20%
50%
A new kind of currency
Contents
• 1、What is a bitcoin? How to get it? • 2、Features • 3、Current situation
Definition
Bitcoin is an open source peer-to-peer payment network and digital currency introduced in 2009 . It's principle: cryptography and decentralized network.
The first way is mining.
• The actual mining of Bitcoins is by a purely mathematical • process. • You must download a operational programme ,register some special websites of bitcoin,write your register name and password in the operational programme and then start the programme,the rest of work is the computers.
罗技G系列外设宏命令编程参考文档

罗技G系列外设宏命令编程参考文档————————————————————————————————作者: ————————————————————————————————日期:G-series Lua API 参考文档V8.5预览与概述手册目录手册目录.......................................................................................................................... (2)内容预览.............................................................................................................................3参考文档.......................................................................................................................... (4)标准Lua 5.1库................................................................................................................... 40附录A...............................................................................................................................41内容预览G-seriesLuaAPI 参考手册是一套使用Lua 脚本编程语言描述并且为G-series 系列游戏键盘提供高级脚本功能。
解密比特币
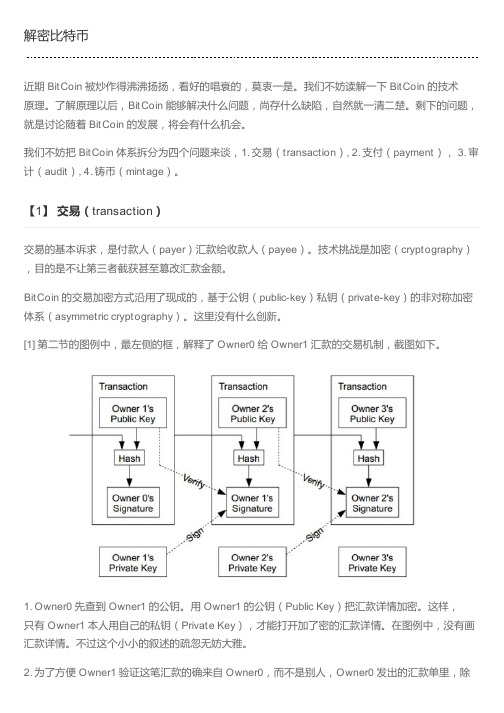
了有加了密的汇款详情,还有 Owner0 的数字签名(Signature)。
Owner1 拿到汇款时,为了验证这笔汇款的确来自 Owner0,他可以用 Owner0 的公钥,来验证汇款单中 Owner0 的数字签名。
3. Owner0 发出汇款单时,汇款单不仅仅投递到 Owner1,而且还要广而告之,任何人只要愿意参与 BitCoin 审计,都可以收到全球所有人发出的所有汇款单。
4. 沿用 1、2、3 的原理,Owner1 给 Owner2 汇款,然后 Owner2 给 Owner3 汇款。
BitCoin 通过Hash 机制,把涉及同一枚 BitCoin 的所有汇款交易(Tranaction)串连起来,目的是为了追查重复付款(double spending)的欺诈行为。
【2】支付(payment)当付款人(payer)向收款人(payee)发出汇款交易(transaction)后,支付过程(payment)并没有完成。
直到收款人签收了汇款以后,支付过程才正式结束。
在收款人接受汇款以前,他必须确认汇款人没有重复付款(double spending)。
这就类似于我们接受纸币前,最好验证一下纸币是不是假钞一样。
BitCoin 验证重复付款的办法,是靠群众检举。
当收款人收到汇款时,他把汇款单广而告之。
审计站点收到广而告之的汇款单时,会检查汇款单中涉及的 BitCoin,是否出现在其它汇款单中,是否被重复付款。
如果出现这种重复付款,审计站点会检举,并通知收款人拒绝签收汇款。
BitCoin 保证重复付款的行为,能够被检举,但是不能保证能够被当场抓获。
[2] 假设了一个场景,1. 骗子开设了两个账号,A 和 B。
他先把一枚 BitCoin 由账号 A 汇款到账号 B,账号 B 立刻签收。
账户 B 签收汇款前,没有把汇款单广而告之。
2. 然后骗子去 C 的网店买东西,他把同一枚 BitCoin 由账号 A 汇款到账号 C。
斑马技术公司DS8108数字扫描仪产品参考指南说明书

比特币最大交易网破产的机会

比特币最大交易网破产的机会李燕02月25日17:32 分享到:77比特币网络金融财经2月24日,MtGox已删除其官方Twitter上所有的帖子今天上午开始,MtGox网站已经无法打开。
曾经是全球最大的比特币交易平台MT.GOX由于系统漏洞损失大量比特币无法弥补客户损失而申请破产保护。
2月24日,MtGox已删除其官方Twitter上所有的帖子今天上午开始,MtGox网站已经无法打开。
曾经是全球最大的比特币交易平台MT.GOX由于系统漏洞损失大量比特币无法弥补客户损失而申请破产保护。
而包括中国比特币交易网站BTC China在内的世界多家比特币交易网站,专门就“MT.GOX破产”发表了联合声明。
据《华尔街日报》稍早前的报道,比特币交易所Mt.Gox的CEO Mark Karpeles已经在博客中宣布退出比特币基金会。
本人并没有透露离开的原因。
外界猜测这和Mt.Gox接连不断出现的安全漏洞有一定的关系。
据了解,Mt.Gox目前面临一系列长期的技术问题。
这些问题去年夏季就已开始出现,当时Mt.Gox暂停了客户提取美元。
2014年2月7日,位于日本、世界上最早创建的这个MtGox比特币交易平台对外称,由于软件故障,暂停比特币提现。
2月10日,MtGox发布公告称恢复提取现金,但停止提取比特币;随后又公告称“比特币存在漏洞”,导致其提现出现双重交易,因此暂停了提取比特币。
从2月20日至21日,MtGox的比特币价格从260多美元,最低跌至91美元,后又回升至140美元左右。
而其他的交易平台,比特币价格仍然在500多美元,但由于投资者信心受到影响,价格也普遍下跌10%~20%。
Mt.Gox曾在发表的声明中称:“比特币软件中存在一个漏洞,黑客可以利用该漏洞修改交易信息,比如让一个本来已经发生的比特币交易看起来像没发生……这会导致系统重新发送比特币……”受Mt.Gox破产的影响,比特币的价格出现了较大波动,25日中国国内比特币的交易价格在3700—3000元人民币之间剧烈震荡。
Indradrive 系列 故障代码

Error MessagesF9001 Error internal function call.F9002 Error internal RTOS function callF9003 WatchdogF9004 Hardware trapF8000 Fatal hardware errorF8010 Autom. commutation: Max. motion range when moving back F8011 Commutation offset could not be determinedF8012 Autom. commutation: Max. motion rangeF8013 Automatic commutation: Current too lowF8014 Automatic commutation: OvercurrentF8015 Automatic commutation: TimeoutF8016 Automatic commutation: Iteration without resultF8017 Automatic commutation: Incorrect commutation adjustment F8018 Device overtemperature shutdownF8022 Enc. 1: Enc. signals incorr. (can be cleared in ph. 2) F8023 Error mechanical link of encoder or motor connectionF8025 Overvoltage in power sectionF8027 Safe torque off while drive enabledF8028 Overcurrent in power sectionF8030 Safe stop 1 while drive enabledF8042 Encoder 2 error: Signal amplitude incorrectF8057 Device overload shutdownF8060 Overcurrent in power sectionF8064 Interruption of motor phaseF8067 Synchronization PWM-Timer wrongF8069 +/-15Volt DC errorF8070 +24Volt DC errorF8076 Error in error angle loopF8078 Speed loop error.F8079 Velocity limit value exceededF8091 Power section defectiveF8100 Error when initializing the parameter handlingF8102 Error when initializing power sectionF8118 Invalid power section/firmware combinationF8120 Invalid control section/firmware combinationF8122 Control section defectiveF8129 Incorrect optional module firmwareF8130 Firmware of option 2 of safety technology defectiveF8133 Error when checking interrupting circuitsF8134 SBS: Fatal errorF8135 SMD: Velocity exceededF8140 Fatal CCD error.F8201 Safety command for basic initialization incorrectF8203 Safety technology configuration parameter invalidF8813 Connection error mains chokeF8830 Power section errorF8838 Overcurrent external braking resistorF7010 Safely-limited increment exceededF7011 Safely-monitored position, exceeded in pos. DirectionF7012 Safely-monitored position, exceeded in neg. DirectionF7013 Safely-limited speed exceededF7020 Safe maximum speed exceededF7021 Safely-limited position exceededF7030 Position window Safe stop 2 exceededF7031 Incorrect direction of motionF7040 Validation error parameterized - effective thresholdF7041 Actual position value validation errorF7042 Validation error of safe operation modeF7043 Error of output stage interlockF7050 Time for stopping process exceeded8.3.15 F7051 Safely-monitored deceleration exceeded (159)8.4 Travel Range Errors (F6xxx) (161)8.4.1 Behavior in the Case of Travel Range Errors (161)8.4.2 F6010 PLC Runtime Error (162)8.4.3 F6024 Maximum braking time exceeded (163)8.4.4 F6028 Position limit value exceeded (overflow) (164)8.4.5 F6029 Positive position limit exceeded (164)8.4.6 F6030 Negative position limit exceeded (165)8.4.7 F6034 Emergency-Stop (166)8.4.8 F6042 Both travel range limit switches activated (167)8.4.9 F6043 Positive travel range limit switch activated (167)8.4.10 F6044 Negative travel range limit switch activated (168)8.4.11 F6140 CCD slave error (emergency halt) (169)8.5 Interface Errors (F4xxx) (169)8.5.1 Behavior in the Case of Interface Errors (169)8.5.2 F4001 Sync telegram failure (170)8.5.3 F4002 RTD telegram failure (171)8.5.4 F4003 Invalid communication phase shutdown (172)8.5.5 F4004 Error during phase progression (172)8.5.6 F4005 Error during phase regression (173)8.5.7 F4006 Phase switching without ready signal (173)8.5.8 F4009 Bus failure (173)8.5.9 F4012 Incorrect I/O length (175)8.5.10 F4016 PLC double real-time channel failure (176)8.5.11 F4017 S-III: Incorrect sequence during phase switch (176)8.5.12 F4034 Emergency-Stop (177)8.5.13 F4140 CCD communication error (178)8.6 Non-Fatal Safety Technology Errors (F3xxx) (178)8.6.1 Behavior in the Case of Non-Fatal Safety Technology Errors (178)8.6.2 F3111 Refer. missing when selecting safety related end pos (179)8.6.3 F3112 Safe reference missing (179)8.6.4 F3115 Brake check time interval exceeded (181)Troubleshooting Guide | Rexroth IndraDrive Electric Drivesand ControlsI Bosch Rexroth AG VII/XXIITable of ContentsPage8.6.5 F3116 Nominal load torque of holding system exceeded (182)8.6.6 F3117 Actual position values validation error (182)8.6.7 F3122 SBS: System error (183)8.6.8 F3123 SBS: Brake check missing (184)8.6.9 F3130 Error when checking input signals (185)8.6.10 F3131 Error when checking acknowledgment signal (185)8.6.11 F3132 Error when checking diagnostic output signal (186)8.6.12 F3133 Error when checking interrupting circuits (187)8.6.13 F3134 Dynamization time interval incorrect (188)8.6.14 F3135 Dynamization pulse width incorrect (189)8.6.15 F3140 Safety parameters validation error (192)8.6.16 F3141 Selection validation error (192)8.6.17 F3142 Activation time of enabling control exceeded (193)8.6.18 F3143 Safety command for clearing errors incorrect (194)8.6.19 F3144 Incorrect safety configuration (195)8.6.20 F3145 Error when unlocking the safety door (196)8.6.21 F3146 System error channel 2 (197)8.6.22 F3147 System error channel 1 (198)8.6.23 F3150 Safety command for system start incorrect (199)8.6.24 F3151 Safety command for system halt incorrect (200)8.6.25 F3152 Incorrect backup of safety technology data (201)8.6.26 F3160 Communication error of safe communication (202)8.7 Non-Fatal Errors (F2xxx) (202)8.7.1 Behavior in the Case of Non-Fatal Errors (202)8.7.2 F2002 Encoder assignment not allowed for synchronization (203)8.7.3 F2003 Motion step skipped (203)8.7.4 F2004 Error in MotionProfile (204)8.7.5 F2005 Cam table invalid (205)8.7.6 F2006 MMC was removed (206)8.7.7 F2007 Switching to non-initialized operation mode (206)8.7.8 F2008 RL The motor type has changed (207)8.7.9 F2009 PL Load parameter default values (208)8.7.10 F2010 Error when initializing digital I/O (-> S-0-0423) (209)8.7.11 F2011 PLC - Error no. 1 (210)8.7.12 F2012 PLC - Error no. 2 (210)8.7.13 F2013 PLC - Error no. 3 (211)8.7.14 F2014 PLC - Error no. 4 (211)8.7.15 F2018 Device overtemperature shutdown (211)8.7.16 F2019 Motor overtemperature shutdown (212)8.7.17 F2021 Motor temperature monitor defective (213)8.7.18 F2022 Device temperature monitor defective (214)8.7.19 F2025 Drive not ready for control (214)8.7.20 F2026 Undervoltage in power section (215)8.7.21 F2027 Excessive oscillation in DC bus (216)8.7.22 F2028 Excessive deviation (216)8.7.23 F2031 Encoder 1 error: Signal amplitude incorrect (217)VIII/XXII Bosch Rexroth AG | Electric Drivesand ControlsRexroth IndraDrive | Troubleshooting GuideTable of ContentsPage8.7.24 F2032 Validation error during commutation fine adjustment (217)8.7.25 F2033 External power supply X10 error (218)8.7.26 F2036 Excessive position feedback difference (219)8.7.27 F2037 Excessive position command difference (220)8.7.28 F2039 Maximum acceleration exceeded (220)8.7.29 F2040 Device overtemperature 2 shutdown (221)8.7.30 F2042 Encoder 2: Encoder signals incorrect (222)8.7.31 F2043 Measuring encoder: Encoder signals incorrect (222)8.7.32 F2044 External power supply X15 error (223)8.7.33 F2048 Low battery voltage (224)8.7.34 F2050 Overflow of target position preset memory (225)8.7.35 F2051 No sequential block in target position preset memory (225)8.7.36 F2053 Incr. encoder emulator: Pulse frequency too high (226)8.7.37 F2054 Incr. encoder emulator: Hardware error (226)8.7.38 F2055 External power supply dig. I/O error (227)8.7.39 F2057 Target position out of travel range (227)8.7.40 F2058 Internal overflow by positioning input (228)8.7.41 F2059 Incorrect command value direction when positioning (229)8.7.42 F2063 Internal overflow master axis generator (230)8.7.43 F2064 Incorrect cmd value direction master axis generator (230)8.7.44 F2067 Synchronization to master communication incorrect (231)8.7.45 F2068 Brake error (231)8.7.46 F2069 Error when releasing the motor holding brake (232)8.7.47 F2074 Actual pos. value 1 outside absolute encoder window (232)8.7.48 F2075 Actual pos. value 2 outside absolute encoder window (233)8.7.49 F2076 Actual pos. value 3 outside absolute encoder window (234)8.7.50 F2077 Current measurement trim wrong (235)8.7.51 F2086 Error supply module (236)8.7.52 F2087 Module group communication error (236)8.7.53 F2100 Incorrect access to command value memory (237)8.7.54 F2101 It was impossible to address MMC (237)8.7.55 F2102 It was impossible to address I2C memory (238)8.7.56 F2103 It was impossible to address EnDat memory (238)8.7.57 F2104 Commutation offset invalid (239)8.7.58 F2105 It was impossible to address Hiperface memory (239)8.7.59 F2110 Error in non-cyclical data communic. of power section (240)8.7.60 F2120 MMC: Defective or missing, replace (240)8.7.61 F2121 MMC: Incorrect data or file, create correctly (241)8.7.62 F2122 MMC: Incorrect IBF file, correct it (241)8.7.63 F2123 Retain data backup impossible (242)8.7.64 F2124 MMC: Saving too slowly, replace (243)8.7.65 F2130 Error comfort control panel (243)8.7.66 F2140 CCD slave error (243)8.7.67 F2150 MLD motion function block error (244)8.7.68 F2174 Loss of motor encoder reference (244)8.7.69 F2175 Loss of optional encoder reference (245)Troubleshooting Guide | Rexroth IndraDrive Electric Drivesand Controls| Bosch Rexroth AG IX/XXIITable of ContentsPage8.7.70 F2176 Loss of measuring encoder reference (246)8.7.71 F2177 Modulo limitation error of motor encoder (246)8.7.72 F2178 Modulo limitation error of optional encoder (247)8.7.73 F2179 Modulo limitation error of measuring encoder (247)8.7.74 F2190 Incorrect Ethernet configuration (248)8.7.75 F2260 Command current limit shutoff (249)8.7.76 F2270 Analog input 1 or 2, wire break (249)8.7.77 F2802 PLL is not synchronized (250)8.7.78 F2814 Undervoltage in mains (250)8.7.79 F2815 Overvoltage in mains (251)8.7.80 F2816 Softstart fault power supply unit (251)8.7.81 F2817 Overvoltage in power section (251)8.7.82 F2818 Phase failure (252)8.7.83 F2819 Mains failure (253)8.7.84 F2820 Braking resistor overload (253)8.7.85 F2821 Error in control of braking resistor (254)8.7.86 F2825 Switch-on threshold braking resistor too low (255)8.7.87 F2833 Ground fault in motor line (255)8.7.88 F2834 Contactor control error (256)8.7.89 F2835 Mains contactor wiring error (256)8.7.90 F2836 DC bus balancing monitor error (257)8.7.91 F2837 Contactor monitoring error (257)8.7.92 F2840 Error supply shutdown (257)8.7.93 F2860 Overcurrent in mains-side power section (258)8.7.94 F2890 Invalid device code (259)8.7.95 F2891 Incorrect interrupt timing (259)8.7.96 F2892 Hardware variant not supported (259)8.8 SERCOS Error Codes / Error Messages of Serial Communication (259)9 Warnings (Exxxx) (263)9.1 Fatal Warnings (E8xxx) (263)9.1.1 Behavior in the Case of Fatal Warnings (263)9.1.2 E8025 Overvoltage in power section (263)9.1.3 E8026 Undervoltage in power section (264)9.1.4 E8027 Safe torque off while drive enabled (265)9.1.5 E8028 Overcurrent in power section (265)9.1.6 E8029 Positive position limit exceeded (266)9.1.7 E8030 Negative position limit exceeded (267)9.1.8 E8034 Emergency-Stop (268)9.1.9 E8040 Torque/force actual value limit active (268)9.1.10 E8041 Current limit active (269)9.1.11 E8042 Both travel range limit switches activated (269)9.1.12 E8043 Positive travel range limit switch activated (270)9.1.13 E8044 Negative travel range limit switch activated (271)9.1.14 E8055 Motor overload, current limit active (271)9.1.15 E8057 Device overload, current limit active (272)X/XXII Bosch Rexroth AG | Electric Drivesand ControlsRexroth IndraDrive | Troubleshooting GuideTable of ContentsPage9.1.16 E8058 Drive system not ready for operation (273)9.1.17 E8260 Torque/force command value limit active (273)9.1.18 E8802 PLL is not synchronized (274)9.1.19 E8814 Undervoltage in mains (275)9.1.20 E8815 Overvoltage in mains (275)9.1.21 E8818 Phase failure (276)9.1.22 E8819 Mains failure (276)9.2 Warnings of Category E4xxx (277)9.2.1 E4001 Double MST failure shutdown (277)9.2.2 E4002 Double MDT failure shutdown (278)9.2.3 E4005 No command value input via master communication (279)9.2.4 E4007 SERCOS III: Consumer connection failed (280)9.2.5 E4008 Invalid addressing command value data container A (280)9.2.6 E4009 Invalid addressing actual value data container A (281)9.2.7 E4010 Slave not scanned or address 0 (281)9.2.8 E4012 Maximum number of CCD slaves exceeded (282)9.2.9 E4013 Incorrect CCD addressing (282)9.2.10 E4014 Incorrect phase switch of CCD slaves (283)9.3 Possible Warnings When Operating Safety Technology (E3xxx) (283)9.3.1 Behavior in Case a Safety Technology Warning Occurs (283)9.3.2 E3100 Error when checking input signals (284)9.3.3 E3101 Error when checking acknowledgment signal (284)9.3.4 E3102 Actual position values validation error (285)9.3.5 E3103 Dynamization failed (285)9.3.6 E3104 Safety parameters validation error (286)9.3.7 E3105 Validation error of safe operation mode (286)9.3.8 E3106 System error safety technology (287)9.3.9 E3107 Safe reference missing (287)9.3.10 E3108 Safely-monitored deceleration exceeded (288)9.3.11 E3110 Time interval of forced dynamization exceeded (289)9.3.12 E3115 Prewarning, end of brake check time interval (289)9.3.13 E3116 Nominal load torque of holding system reached (290)9.4 Non-Fatal Warnings (E2xxx) (290)9.4.1 Behavior in Case a Non-Fatal Warning Occurs (290)9.4.2 E2010 Position control with encoder 2 not possible (291)9.4.3 E2011 PLC - Warning no. 1 (291)9.4.4 E2012 PLC - Warning no. 2 (291)9.4.5 E2013 PLC - Warning no. 3 (292)9.4.6 E2014 PLC - Warning no. 4 (292)9.4.7 E2021 Motor temperature outside of measuring range (292)9.4.8 E2026 Undervoltage in power section (293)9.4.9 E2040 Device overtemperature 2 prewarning (294)9.4.10 E2047 Interpolation velocity = 0 (294)9.4.11 E2048 Interpolation acceleration = 0 (295)9.4.12 E2049 Positioning velocity >= limit value (296)9.4.13 E2050 Device overtemp. Prewarning (297)Troubleshooting Guide | Rexroth IndraDrive Electric Drivesand Controls| Bosch Rexroth AG XI/XXIITable of ContentsPage9.4.14 E2051 Motor overtemp. prewarning (298)9.4.15 E2053 Target position out of travel range (298)9.4.16 E2054 Not homed (300)9.4.17 E2055 Feedrate override S-0-0108 = 0 (300)9.4.18 E2056 Torque limit = 0 (301)9.4.19 E2058 Selected positioning block has not been programmed (302)9.4.20 E2059 Velocity command value limit active (302)9.4.21 E2061 Device overload prewarning (303)9.4.22 E2063 Velocity command value > limit value (304)9.4.23 E2064 Target position out of num. range (304)9.4.24 E2069 Holding brake torque too low (305)9.4.25 E2070 Acceleration limit active (306)9.4.26 E2074 Encoder 1: Encoder signals disturbed (306)9.4.27 E2075 Encoder 2: Encoder signals disturbed (307)9.4.28 E2076 Measuring encoder: Encoder signals disturbed (308)9.4.29 E2077 Absolute encoder monitoring, motor encoder (encoder alarm) (308)9.4.30 E2078 Absolute encoder monitoring, opt. encoder (encoder alarm) (309)9.4.31 E2079 Absolute enc. monitoring, measuring encoder (encoder alarm) (309)9.4.32 E2086 Prewarning supply module overload (310)9.4.33 E2092 Internal synchronization defective (310)9.4.34 E2100 Positioning velocity of master axis generator too high (311)9.4.35 E2101 Acceleration of master axis generator is zero (312)9.4.36 E2140 CCD error at node (312)9.4.37 E2270 Analog input 1 or 2, wire break (312)9.4.38 E2802 HW control of braking resistor (313)9.4.39 E2810 Drive system not ready for operation (314)9.4.40 E2814 Undervoltage in mains (314)9.4.41 E2816 Undervoltage in power section (314)9.4.42 E2818 Phase failure (315)9.4.43 E2819 Mains failure (315)9.4.44 E2820 Braking resistor overload prewarning (316)9.4.45 E2829 Not ready for power on (316)。
比特币被盗数10万枚 Mt. Gox关闭系管理不善

比特币被盗数10万枚 Mt. Gox关闭系管理不善这样解释:“所有新铸造成的比特币,以及每一笔交易,都通过互联网公开记录和证实。
这种记录被称作blockchain,它有助于确保系统安全,避免欺诈和滥用。
比特币无法复制或伪造。
”确实,比特币很难复制或伪造,不幸的是它并不难窃取。
如果你自己不注意,比特币很容易丢失。
交易安全至关重要。
系统漏洞被忽略系统漏洞在2月7日显现,Mt.Gox强行停止了比特币提现业务。
在2月10日发布的一份新闻声明中,该公司表示停止提现是因为软件漏洞可能导致人们进行欺诈交易。
这则声明引起了比特币领域的批评。
WizTechnologies公司首席技术官杰森·毛里斯(JasonMaurice)表示,马克·卡普勒斯缺乏互联网安全意识。
他指出,卡普勒斯早在去年10月就已经承认了系统漏洞存在。
毛里斯解释说:“马克认识到了问题存在,但却误解了安全问题的严重性,也没有及时采取补救措施。
到2014年2月,他认识到漏洞已经非常严重,并提出了相应的解决方案,但为时已晚,损失已经发生。
他忽略了软件方面一个价值数百万美元的漏洞,任何一位称职的软件工程师都应当立即认识到问题的严重性。
任何金融机构都应当配备一支高素质的安全团队来发现这些漏洞,但马克全靠自己。
真是奇怪。
”毛里斯和他的好友一共损失了价值4万美元的比特币,他们一直在研究这家公司到底出了什么问题。
“根据我们对比特币交易情况的分析,Mt.Gox不仅仅因为软件漏洞损失货币,而且有可能无意中丢弃了一些比特币。
这种不专业的做法真是难以置信。
”他说。
上文提到的Mt. Gox前员工表示,Mt. Gox员工直到前一周周五才知道了比特币大量消失的情况。
“Mt.Gox将90%的比特币冷藏起来,也就是文档钱包和USB钥匙。
他们从银行租来了保险柜,需要重启交易账户时,他们就把比特币取出来,将它们输入系统里。
然而,在冷藏和交易完成这个过程之间,没有任何财务对账。
TD信息元素详解

信息元素功能性定义作者:李欣目录目录 (1)信息元素功能性定义 (11)1 核心网信息元素 (11)1.1 CN Information elements (11)1.2 CN Domain System Information (11)1.3 CN Information info (11)1.4 IMEI (11)1.5 IMSI (GSM-MAP) (11)1.6 Intra Domain NAS Node Selector (11)1.7 Location Area Identification (12)1.8 NAS message (12)1.9 NAS system information (GSM-MAP) (12)1.10 Paging record type identifier (12)1.11 PLMN identity (12)1.12 PLMN Type (12)1.13 P-TMSI (GSM-MAP) (12)1.14 RAB identity (12)1.15 Routing Area Code (12)1.16 Routing Area Identification (13)1.17 TMSI (GSM-MAP) (13)2 UTRAN 移动信息元素 (13)2.1 Cell Access Restriction (13)2.2 Cell identity (13)2.3 Cell selection and re-selection info for SIB3/4 (13)2.4 Cell selection and re-selection info for SIB11/12 (13)2.5 Mapping Info (14)2.6 URA identity (14)3 UE 信息元素 (14)3.1 Activation time (14)3.2 Capability Update Requirement (14)3.3 Cell update cause (15)3.4 Ciphering Algorithm (15)3.5 Ciphering mode info (15)3.6 CN domain specific DRX cycle length coefficient (15)3.7 CPCH Parameters (15)3.8 C-RNTI (15)3.9 DRAC system information (15)3.10 Void (16)3.11 Establishment cause (16)3.12 Expiration Time Factor (16)3.13 Failure cause (16)3.14 Failure cause and error information (16)3.15 Initial UE identity (16)3.16 Integrity check info (16)3.17 Integrity protection activation info (17)3.18 Integrity protection Algorithm (17)3.19 Integrity protection mode info (17)3.20 Maximum bit rate (17)3.21 Measurement capability (17)3.22 Paging cause (17)3.23 Paging record (17)3.24 PDCP capability (17)3.25 Physical channel capability (18)3.26 Protocol error cause (18)3.27 Protocol error indicator (18)3.28 RB timer indicator (18)3.29 Redirection info (18)3.30 Re-establishment timer (18)3.31 Rejection cause (18)3.32 Release cause (18)3.33 RF capability FDD (19)3.34 RLC capability (19)3.35 RLC re-establish indicator (19)3.36 RRC transaction identifier (19)3.37 Security capability (19)3.38 START (19)3.39 Transmission probability (19)3.40 Transport channel capability (20)3.41 UE multi-mode/multi-RAT capability (20)3.42 UE radio access capability (20)3.43 UE Timers and Constants in connected mode (21)3.44 UE Timers and Constants in idle mode (21)3.45 UE positioning capability (21)3.46 URA update cause (21)3.47 U-RNTI (21)3.48 U-RNTI Short (21)3.49 UTRAN DRX cycle length coefficient (21)3.50 Wait time (21)3.51 UE Specific Behavior Information 1 idle (21)3.52 UE Specific Behavior Information 1 interRAT (22)4 无线承载信息元素 (22)4.0 Default configuration identity (22)4.1 Downlink RLC STATUS info (22)4.2 PDCP info (22)4.3 PDCP SN info (22)4.4 Polling info (22)4.5 Predefined configuration identity (23)4.6 Predefined configuration value tag (23)4.7 Predefined RB configuration (23)4.8 RAB info (23)4.9 RAB info Post (23)4.10 RAB information for setup (23)4.11 RAB information to reconfigure (24)4.12 NAS Synchronization indicator (24)4.13 RB activation time info (24)4.14 RB COUNT-C MSB information (24)4.15 RB COUNT-C information (24)4.16 RB identity (24)4.17 RB information to be affected (24)4.18 RB information to reconfigure (25)4.19 RB information to release (25)4.20 RB information to setup (25)4.21 RB mapping info (25)4.22 RB with PDCP information (25)4.23 RLC info (25)4.24 Signaling RB information to setup (26)4.25 Transmission RLC Discard (26)5 传输信道信息元素 (26)5.1 Added or Reconfigured DL TrCH information (26)5.2 Added or Reconfigured UL TrCH information (27)5.3 CPCH set ID (27)5.4 Deleted DL TrCH information (27)5.5 Deleted UL TrCH information (27)5.6 DL Transport channel information common for all transport channels (27)5.7 DRAC Static Information (27)5.8 Power Offset Information (28)5.9 Predefined TrCH configuration (28)5.10 Quality Target (28)5.11 Semi-static Transport Format Information (28)5.12 TFCI Field 2 Information (28)5.13 TFCS Explicit Configuration (28)5.14 TFCS Information for DSCH (TFCI range method) (29)5.15 TFCS Reconfiguration/Addition Information (29)5.16 TFCS Removal Information (29)5.17 Void (29)5.18 Transport channel identity (29)5.19 Transport Format Combination (TFC) (29)5.20 Transport Format Combination Set (29)5.21 Transport Format Combination Set Identity (29)5.22 Transport Format Combination Subset (29)5.23 Transport Format Set (29)5.24 UL Transport channel information common for all transport channels (30)6 物理信道信息元素 (30)6.1 AC-to-ASC mapping (30)6.2 AICH Info (30)6.3 AICH Power offset (30)6.4 Allocation period info (30)6.5 Alpha (30)6.6 ASC Setting (30)6.7 Void (31)6.8 CCTrCH power control info (31)6.9 Cell parameters Id (31)6.10 Common timeslot info (31)6.11 Constant value (31)6.12 CPCH persistence levels (31)6.13 CPCH set info (31)6.14 CPCH Status Indication mode (31)6.15 CSICH Power offset (32)6.16 Default DPCH Offset Value (32)6.17 Downlink channelisation codes (32)6.18 Downlink DPCH info common for all RL (32)6.19 Downlink DPCH info common for all RL Post (32)6.20 Downlink DPCH info common for all RL Pre (32)6.21 Downlink DPCH info for each RL (32)6.22 Downlink DPCH info for each RL Post (33)6.23 Downlink DPCH power control information (33)6.24 Downlink information common for all radio links (33)6.25 Downlink information common for all radio links Post (33)6.26 Downlink information common for all radio links Pre (33)6.27 Downlink information for each radio link (33)6.28 Downlink information for each radio link Post (33)6.29 Void (33)6.30 Downlink PDSCH information (33)6.31 Downlink rate matching restriction information (34)6.32 Downlink Timeslots and Codes (34)6.33 DPCH compressed mode info (34)6.34 DPCH Compressed Mode Status Info (34)6.35 Dynamic persistence level (34)6.36 Frequency info (34)6.37 Individual timeslot info (35)6.38 Individual Timeslot interference (35)6.39 Maximum allowed UL TX power (35)6.40 Void (35)6.41 Midamble shift and burst type (35)6.42 PDSCH Capacity Allocation info (35)6.43 PDSCH code mapping (36)6.44 PDSCH info (36)6.45 PDSCH Power Control info (36)6.46 PDSCH system information (36)6.47 PDSCH with SHO DCH Info (36)6.48 Persistence scaling factors (36)6.49 PICH Info (36)6.50 PICH Power offset (37)6.51 PRACH Channelisation Code List (37)6.52 PRACH info (for RACH) (37)6.53 PRACH partitioning (37)6.54 PRACH power offset (37)6.55 PRACH system information list (37)6.56 Predefined PhyCH configuration (38)6.57 Primary CCPCH info (38)6.58 Primary CCPCH info post (38)6.59 Primary CCPCH TX Power (38)6.60 Primary CPICH info (38)6.61 Primary CPICH Tx power (38)6.62 Primary CPICH usage for channel estimation (38)6.63 PUSCH info (38)6.64 PUSCH Capacity Allocation info (38)6.65 PUSCH power control info (39)6.66 PUSCH system information (39)6.67 RACH transmission parameters (39)6.68 Radio link addition information (39)6.69 Radio link removal information (39)6.70 SCCPCH Information for FACH (39)6.71 Secondary CCPCH info (39)6.72 Secondary CCPCH system information (40)6.73 Secondary CPICH info (40)6.74 Secondary scrambling code (40)6.75 SFN Time info (40)6.76 SSDT cell identity (40)6.77 SSDT information (40)6.78 STTD indicator (40)6.79 TDD open loop power control (41)6.80 TFC Control duration (41)6.81 TFCI Combining Indicator (41)6.82 TGPSI (41)6.83 Time info (41)6.84 Timeslot number (41)6.85 TPC combination index (41)6.86 TSTD indicator (41)6.87 TX Diversity Mode (41)6.88 Uplink DPCH info (41)6.89 Uplink DPCH info Post (42)6.90 Uplink DPCH info Pre (42)6.91 Uplink DPCH power control info (42)6.92 Uplink DPCH power control info Post (42)6.93 Uplink DPCH power control info Pre (42)6.94 Uplink Timeslots and Codes (42)6.95 Uplink Timing Advance (42)6.96 Uplink Timing Advance Control (43)7 测量信息元素 (43)7.1 Additional measurements list (43)7.2 Cell info (43)7.3 Cell measured results (43)7.4 Cell measurement event results (44)7.5 Cell reporting quantities (44)7.6 Cell synchronization information (44)7.7 Event results (44)7.8 FACH measurement occasion info (45)7.9 Filter coefficient (45)7.10 HCS Cell re-selection information (45)7.11 HCS neighboring cell information (45)7.12 HCS Serving cell information (45)7.13 Inter-frequency cell info list (46)7.14 Inter-frequency event identity (46)7.15 Inter-frequency measured results list (46)7.16 Inter-frequency measurement (46)7.17 Inter-frequency measurement event results (47)7.18 Inter-frequency measurement quantity (47)7.19 Inter-frequency measurement reporting criteria (47)7.20 Inter-frequency measurement system information (47)7.21 Inter-frequency reporting quantity (47)7.22 Inter-frequency SET UPDATE (48)7.23 Inter-RAT cell info list (48)7.24 Inter-RAT event identity (48)7.25 Inter-RAT info (48)7.26 Inter-RAT measured results list (48)7.27 Inter-RAT measurement (49)7.28 Inter-RAT measurement event results (49)7.29 Inter-RAT measurement quantity (49)7.30 Inter-RAT measurement reporting criteria (49)7.31 Inter-RAT measurement system information (50)7.32 Inter-RAT reporting quantity (50)7.33 Intra-frequency cell info list (50)7.34 Intra-frequency event identity (50)7.35 Intra-frequency measured results list (50)7.36 Intra-frequency measurement (50)7.37 Intra-frequency measurement event results (51)7.38 Intra-frequency measurement quantity (51)7.39 Intra-frequency measurement reporting criteria (51)7.40 Intra-frequency measurement system information (51)7.41 Intra-frequency reporting quantity (52)7.42 Intra-frequency reporting quantity for RACH reporting (52)7.43 Maximum number of reported cells on RACH (52)7.44 Measured results (52)7.45 Measured results on RACH (52)7.46 Measurement Command (52)7.47 Measurement control system information (53)7.48 Measurement Identity (53)7.49 Measurement reporting mode (53)7.50 Measurement Type (53)7.51 Measurement validity (53)7.52 Observed time difference to GSM cell (53)7.53 Periodical reporting criteria (53)7.54 Primary CCPCH RSCP info (54)7.55 Quality measured results list (54)7.56 Quality measurement (54)7.57 Quality measurement event results (54)7.58 Quality measurement reporting criteria (54)7.59 Quality reporting quantity (54)7.60 Reference time difference to cell (54)7.61 Reporting Cell Status (55)7.62 Reporting information for state CELL_DCH (55)7.63 SFN-SFN observed time difference (55)7.64 Time to trigger (55)7.65 Timeslot ISCP info (55)7.66 Traffic volume event identity (55)7.67 Traffic volume measured results list (55)7.68 Traffic volume measurement (55)7.69 Traffic volume measurement event results (56)7.70 Traffic volume measurement object (56)7.71 Traffic volume measurement quantity (56)7.72 Traffic volume measurement reporting criteria (56)7.73 Traffic volume measurement system information (56)7.74 Traffic volume reporting quantity (56)7.75 UE internal event identity (56)7.76 UE internal measured results (57)7.77 UE internal measurement (57)7.78 UE internal measurement event results (57)7.79 UE internal measurement quantity (57)7.80 UE internal measurement reporting criteria (57)7.81 Void (58)7.82 UE Internal reporting quantity (58)7.83 UE Rx-Tx time difference type 1 (58)7.84 UE Rx-Tx time difference type 2 (58)7.85 UE Transmitted Power info (58)7.86 UE positioning Ciphering info (58)7.87 UE positioning Error (58)7.88 UE positioning GPS acquisition assistance (59)7.89 UE positioning GPS almanac (59)7.90 UE positioning GPS assistance data (59)7.91 UE positioning GPS DGPS corrections (59)7.92 UE positioning GPS ionospheric model (59)7.93 UE positioning GPS measured results (59)7.94 UE positioning GPS navigation model (60)7.95 UE positioning GPS real-time integrity (60)7.96 UE positioning GPS reference time (60)7.97 UE positioning GPS UTC model (61)7.98 UE positioning IPDL parameters (61)7.99 UE positioning measured results (61)7.100 UE positioning measurement (61)7.101 UE positioning measurement event results (61)7.102 Void (62)7.103 UE positioning OTDOA assistance data for UE-assisted (62)7.104 Void (62)7.105 UE positioning OTDOA measured results (62)7.106 UE positioning OTDOA neighbor cell info (62)7.107 UE positioning OTDOA quality (63)7.108 UE positioning OTDOA reference cell info (63)7.109 UE positioning position estimate info (64)7.110 UE positioning reporting criteria (64)7.111 UE positioning reporting quantity (64)7.112 T ADV info (65)8 其它信息元素 (65)8.1 BCCH modification info (65)8.2 BSIC (65)8.3 CBS DRX Level 1 information (65)8.4 Cell Value tag (65)8.5 Inter-RAT change failure (65)8.6 Inter-RAT handover failure (66)8.7 Inter-RAT UE radio access capability (66)8.8 Void (66)8.9 MIB Value tag (66)8.10 PLMN Value tag (66)8.11 Predefined configuration identity and value tag (66)8.12 Protocol error information (66)8.13 References to other system information blocks (66)8.14 References to other system information blocks and scheduling blocks (67)8.15 Rplmn information (67)8.16 Scheduling information (67)8.17 SEG COUNT (67)8.18 Segment index (67)8.19 SIB data fixed (67)8.20 SIB data variable (67)8.21 SIB type (67)8.22 SIB type SIBs only (67)9 ANSI-41 Information elements (68)10 Multiplicity values and type constraint values (68)信息元素功能性定义消息是由多个信息元素组合而成,信息元素根据其功能的不同划分为:核心网域信息元素、UTRAN 移动信息元素、UE 信息元素、无线承载信息元素、传输信道信息元素、物理信道信息元素和测量信息元素。
GRBL错误代码

GRBL错误代码GRBL Error List"error:1" : _("G-code words consist of a letter and a value. Letter was not found."),"error:2" : _("Numeric value format is not valid or missing an expected value."),"error:3" : _("Grbl '$' system command was not recognized or supported."),"error:4" : _("Negative value received for an expected positive value."),"error:5" : _("Homing cycle is not enabled via settings."),"error:6" : _("Minimum step pulse time must be greater than 3usec"),"error:7" : _("EEPROM read failed. Reset and restored to default values."),"error:8" : _("Grbl '$' command cannot be used unless Grbl is IDLE. Ensures smooth operation during a job."),"error:9" : _("G-code locked out during alarm or jog state"),"error:10" : _("Soft limits cannot be enabled without homing also enabled."),"error:11" : _("Max characters per line exceeded. Line was not processed and executed."),"error:12" : _("(Compile Option) Grbl '$' setting value exceeds the maximum step rate supported."),"error:13" : _("Safety door detected as opened and door state initiated."),"error:14" : _("(Grbl-Mega Only) Build info or startup line exceeded EEPROM line length limit."),"error:15" : _("Jog target exceeds machine travel. Command ignored."),"error:16" : _("Jog command with no '=' or contains prohibited g-code."),"error:20" : _("Unsupported or invalid g-code command found in block."),"error:21" : _("More than one g-code command from same modal group found in block."),"error:22" : _("Feed rate has not yet been set or is undefined."),"error:23" : _("G-code command in block requires an integer value."),"error:24" : _("Two G-code commands that both require the use of the XYZ axis words were detected in the block."),"error:25" : _("A G-code word was repeated in the block."),"error:26" : _("A G-code command implicitly or explicitly requires XYZ axis words in the block, but none were detected."),"error:27" : _("N line number value is not within the valid range of 1 - 9,999,999."),"error:28" : _("A G-code command was sent, but is missing some required P or L value words in the line."),"error:29" : _("Grbl supports six work coordinate systems G54-G59. G59.1, G59.2, and G59.3 are not supported."),"error:30" : _("The G53 G-code command requires either a G0 seek or G1 feed motion mode to be active. A different motion was active."), "error:31" : _("There are unused axis words in the block and G80 motion mode cancel is active."),"error:32" : _("A G2 or G3 arc was commanded but there are no XYZ axis words in the selected plane to trace the arc."),"error:33" : _("The motion command has an invalid target. G2, G3, and G38.2 generates this error, if the arc is impossible to generate or if the probe target is the current position."),"error:34" : _("A G2 or G3 arc, traced with the radius definition, had a mathematical error when computing the arc geometry. Try either breaking up the arc into semi-circles or quadrants, or redefine them with the arc offset definition."),"error:35" : _("A G2 or G3 arc, traced with the offset definition, is missing the IJK offset word in the selected plane to trace the arc."), "error:36" : _("There are unused, leftover G-code words that aren't used by any command in the block."),"error:37" : _("The G43.1 dynamic tool length offset command cannot apply an offset to an axis other than its configured axis. The Grbl default axis is the Z-axis."),"error:38" : _("An invalid tool number sent to the parser"),"ALARM:1" : _("Hard limit triggered. Machine position is likely lost due to sudden and immediate halt. Re-homing is highly recommended."), "ALARM:2" : _("G-code motion target exceeds machine travel. Machine position safely retained. Alarm may be unlocked."), "ALARM:3" : _("Reset while in motion. Grbl cannot guarantee position. Lost steps are likely. Re-homing is highly recommended."), "ALARM:4" : _("Probe fail. The probe is not in the expected initial state before starting probe cycle, where G38.2 and G38.3 is not triggered and G38.4 and G38.5 is triggered."),"ALARM:5" : _("Probe fail. Probe did not contact the workpiece within the programmed travel for G38.2 and G38.4."),"ALARM:6" : _("Homing fail. Reset during active homing cycle."),"ALARM:7" : _("Homing fail. Safety door was opened during active homing cycle."),"ALARM:8" : _("Homing fail. Cycle failed to clear limit switch when pulling off. Try increasing pull-off setting or check wiring."), "ALARM:9" : _("Homing fail. Could not find limit switch within search distance. Defined as 1.5 * max_travel on search and 5 * pulloff on locate phases."),"Hold:0" : _("Hold complete. Ready to resume."),"Hold:1" : _("Hold in-progress. Reset will throw an alarm."),"Door:0" : _("Door closed. Ready to resume."),"Door:1" : _("Machine stopped. Door still ajar. Can't resume until closed."),"Door:2" : _("Door opened. Hold (or parking retract) in-progress. Reset will throw an alarm."), "Door:3" : _("Door closed and resuming. Restoring from park, if applicable. Reset will throw an alarm."),。
凶猛的比特币

新B ooming Bitcoinoo ing B凶猛的比特币文/见习记者 张程比特币自2009年诞生至今,币值已经上涨了数万倍,今年6月7日更是突破2万元的大关。
一串数字组成的电子货币为何有如此大的能量?作为金融危机遗产的比特币在支持者的眼中代表着未来。
2008年始于美国次贷危机的全球金融危机,让人们对于金融机构、货币发行者的信用产生了深深的质疑。
金融机构肆意扩张信用、滥用担保引发了一场不可收拾的全球金融危机,各国央行为抵挡金融危机又纷纷采取量化宽松政策,导致了货币的超发和贬值。
金融机构犯的错最后不得不由民众买单。
这使得人们开始寻求一种去中心化的、更为可靠的新货币体系。
在此背景之下,2008年10月31日,即雷曼兄弟银行倒闭后的一个多月,一位自称“中本聪”的人在一封邮件中宣称发现了一种新的去中心化的货币体系,并在这个邮件上附上了《比特币:一种点对点的电子现金系统》的白皮书,大致介绍了其构想。
翌年1月3日,在位于芬兰的一个小型服务器上,中本聪“挖”出了比特币的第一个区块——创世区块,宣告比特币的诞生。
中本聪在创世区块中写下了当天泰晤士报头版的标题:“Chancellor onbrink of second bailout for banks" (财政大臣站在第二次救助银行的边缘)。
这句话不仅证明了比特币产生的时间,也嘲讽了旧的货币体系。
比特币是什么比特币是一种建立在密码学基础上的电子现金支付系统,相比于以货币发行机构为中心的传统货币体系,比特币通过机制的巧妙设计,实现了去中心化。
传统的电子货币为了保证不发生“双重支付”等欺诈问题,在交易的过程中需要一个中心机构对货币进行检验。
这种制度之下,货币的运行就依赖于中心机构。
比特币通过引入“时间戳服务器”的机制,即在每次交易之后便在比特币后面加一个时间戳,并在全网进行广播,类似于一个“全网公开的账本”,从而防止了这种问题的出现。
每次交易之后形成的时间戳会纳入区块中,这样就形成了链形的区块链。
bitcoin比特币介绍

wallet
Wallet address example:
1DZYaCj3HbFq6A5PG6oskHFnnso9kao2o
Bitcoin Mining
Bitcoin Mining
SO MUCH
What is Bitcoin?
• They creat:
• No central
• No borders
• Anonymous
•
------Bitcoin
freedom
ECDSA
The principle of trading Bitcoin
• Wallet private key and public key
Paul Krugman
• So buying into Bitcoin has, at least so far, been a good investment.
• But does that make the experiment a success? Um, no. What we want from a monetary system isn’t to make people holding money rich; we want it to facilitate transactions and make the economy as a whole rich. And that’s not at all what is happening in Bitcoin
founder
creat
geeks
Bitcoin in 2009
broken格式 -回复

broken格式-回复[broken格式]是一种在互联网上广泛使用的文字格式,它常常被用来调侃或者模仿某种语气、态度或格式。
这种格式常常以中文的形式出现,一篇1500-2000字的文章将详细讲解如何使用和写作[broken格式],并且从中探讨其流行原因。
第一步:了解[broken格式]的定义和背景[broken格式],又称损坏/断句/断章/损幅...格式,是表达特定情感或者强调的一种文字调侃格式。
它主要通过对文本进行“断句”或者“损坏”的形式来表达幽默、讽刺或者夸张的效果。
这种格式通常采用标点符号的乱用、断句的错误或者不合逻辑,使得读者在阅读时能够感受到一种有趣的破绽感。
[broken格式]起源于网络文化的表达方式,尤其是在社交媒体和论坛上广泛流行。
它的流行源于人们对于传统文字表达方式的调侃和对于新颖、有趣表达方式的追求。
[broken格式]通常被用作调侃、嘲笑特定人物或者现象的手段,它在互联网上被广泛使用,并成为年轻一代的文化符号之一。
第二步:分析[broken格式]的使用范围和形式[broken格式]的使用范围非常广泛,可以被运用在各种不同的主题和话题中。
从日常生活、娱乐、体育到时事新闻和社会问题等领域,只要是能引起人们共鸣或者关注的话题,[broken格式]就能发挥作用。
它的形式也非常多样化,可以通过错字、断句、标点乱用、重复、叠加等方式进行表达。
在使用[broken格式]时,人们常常通过扭曲传统的语法和表达方式来制造一种错乱感或者反讽效果。
例如,在夸赞某个事物时,采用多次重复同一语词或者伪装成对它的不满来表达。
这样的表达形式能够带给读者一种意想不到的反差,增加话题的趣味性同时也能够达到强调、讽刺、调侃的效果。
第三步:分析[broken格式]的流行原因[broken格式]之所以在网络上迅速流行,可以归因于以下几个原因:1. 幽默性:[broken格式]能够制造出令人捧腹大笑的效果,通过与传统的语法和表达方式的冲突,给人一种出人意料的幽默感。
btc-密码学原理

比特币系统(BTC)中的密码学原理其实加密货币是不加密的,区块链上所有的交易内容都是公开的,包括账户的地址,转账的金额,都是公开的。
比特币中用到了密码学的两个功能:一个是哈希[1],另外一个是签名[2]。
哈希大家应该都比较熟悉哈希函数的工作原理,密码学中用到的哈希函数被称为crypto-graphic hash function。
它有两个重要的性质:一个叫做collision resistance.这个地方的collision是指哈希碰撞。
如果有两个输入x, y且x ≠y ,hash函数是H(v),但是H(x) = H(y)。
这就叫做哈希碰撞[3]。
两个不同的输入算出来的哈希值是相等的。
哈希碰撞是很常见的。
像我们使用哈希表的过程中就会遇到hash碰撞。
不同的输入可能会被映射到hash表中的同一个位置。
一般来说哈希碰撞是不可避免的。
因为输入空间是远远大于输出空间的,比如说我们有256位的hash值。
那输出空间有多大呢。
所有hash值的可能性就是2的256次方,输出空间就只有这么大。
但是输入空间可以是无限大的。
所以它是有任意多样的可能性。
按照鸽笼原理的话。
必然会出现有两个输入被映射到同一个输出的情况。
所以我们这里说的collision resistance 并不会出现哈希碰撞。
有的上管这个性质叫做collision free。
这个说法我不是特别喜欢。
因为它对人很容易造成误解。
好像是碰撞不会发生。
实际上碰撞是客观存在的。
它这个意思是实际上没有什么高效的方法,人为的去制造哈希碰撞。
就给定一个x,没有什么好的办法,你能找到另外一个y,使得H(x) 和H(y)的哈希值恰好相等。
没有什么高效的方法去找。
你硬要找的话可以用蛮力求解的方法。
比如说这个x和y,你就遍历所有输入的可能性。
然后看看哪一个算出来的哈希值正好相等。
这种叫做brute-froce。
遍历所有的取值,最后找了一个哈希值恰好碰撞在一起。
如果输入空间比较大。
Bitcoin and its Imperfection

Sen Wang, Group B
Outline
• Basic Introduction to Bitcoin • Imperfection of Bitcoin • Improvement to Bitcoin • Summary
Basic Introduction to Bitcoin
• 2. Bitcoin is a total bubble ?
• Maybe. But you can buy a villa with a rare tulip, you can only buy a cheap car with a Bitcoin (about 100,000 yuan)
• 3. Latest news:
• Lightening network has been deployed on Bitcoin last week
• Every miner should calculate a very hard math problem (Hash collision) to prove its loyalty • Electricity Bitcoin costs is over 159 countries • Biggest mine pool owns 2672PH/s
• 1.Totally decentralized. No middle man; No one can control • 2.Distributed ledger • 3.Everyone can mine Bitcoin • 4.Most security database human ever builds
ቤተ መጻሕፍቲ ባይዱ
bitcoin bug

• But there remain plenty of true believers in digital currencies. They point out that prices are still well above where they were in 2016. And interest from institutional investors is still strong enough for analysts to want to make sense of the cryptophenomenon.
• 但数字货币仍然有很多忠实信徒。他们指 出,目前的价格仍远高于2016年的水平。
机构投资者仍然兴趣十足,让分析师想要 弄明白这种加密货币现象
• The latest bank to take a shot is Barclays, which devotes a lot more of its “Equity Gilt Study 2018” to the impact of
• 投机泡沫很难模型化——非理性行为要怎 么用理性的方法来评估呢?但巴克莱巧妙 地运用了传染病来作类比。泡沫始于少数 资产所有者(“受感染者”)。新买家被 吸引过来(受到感染),因为他们见证了 价格上涨,担心错失良机。很大一部分人 口是免疫的,永远不会受影响。
• Buyers use a combination of the current price and an extrapolation of the recent increase in price to estimate their expected target value. The faster the price rises, the wilder investors’ hopes and the more the infection spreads. Eventually the market runs out of potential participants and the price rise slows. Once it starts to fall, holders lose hope of big gains and start to sell. The epidemic dies out.
比特币存在的缺陷

比特币存在的缺陷比特币(Bitcoin)是一种去中心化的数字货币,以区块链技术为基础,被誉为数字黄金。
但是,与传统的货币相比,比特币还存在着一些缺陷。
1. 性能瓶颈比特币是一种点对点的电子现金系统,但其处理交易的能力却受到限制。
比特币网络每分钟只能处理约7个交易,而Visa(维萨)信用卡每秒钟可以处理6000多笔交易,显示出比特币存在性能瓶颈的问题。
比特币的处理能力瓶颈主要源于其运行机制,比特币采用工作量证明机制(PoW),需要消耗大量的算力来完成区块的验证,这限制了大量的交易能在较短时间内被处理。
为解决这一问题,比特币社区提出了多项升级方案,如闪电网络和分片技术。
2. 交易费用高昂交易费用是指交易所需支付的手续费,也是比特币存在的另一个问题。
由于比特币处理速度较慢,需要在交易时付出较高的交易费用,以便更快地得到确认。
交易费用高昂的问题主要是由于比特币网络交易数量众多、区块大小有限、挖矿难度不断增加等原因造成的。
虽然比特币社区提出了多项解决方案,如SegWit、Lightning Network 等,但至今仍难以完全解决这一问题。
3. 治理机制不足比特币是一种去中心化的数字货币,没有中心机构控制其发行和流通。
然而,去中心化也带来了比特币治理机制不足的问题。
比特币社区缺乏共识机制,没有明确的规则和决策流程,导致社区内部经常出现分歧。
比特币社区提出了多种治理方案,如Bitcoin Improvement Proposal (BIP) 和User Activated Soft Fork (UASF) 等,以尝试在社区内达成共识。
然而这些方案也引发了一系列新的争议和分歧,导致比特币社区内部经常陷入僵局。
4. 安全性风险由于比特币是一种去中心化的数字货币,没有中心机构控制其发行和交易,因此存在着安全性的风险。
比特币钱包如果遭受黑客攻击,可能会导致比特币被盗窃或损失。
比特币的安全性问题主要源于其分布式数据库和密码学技术的安全性问题。
比特币核心数据结构

#[derive(PartialEq, Clone, Serializable, Deserializable)]
pub struct BlockHeader {
pub version: u32,
// 版本号,指定验证规则
pub previous_header_hash: H256, // 前一区块哈希
pub struct Block {
pub block_header: BlockHeader,
// 区块头部
pub transactions: Vec<Transaction>, // 交易列表
}
BlockHeader
区块头部定义如下:
c++版本实现定义:
/** Nodes collect new transactions into a block, hash them into a hash tree,
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
No, Bitcoin I sn’t Broken“Bitcoin Is B roken,” proclaimed声明,宣布,公告Ittay Eyal and Emin Gun Sirer, two Cornell康奈尔大学(美国纽约)computer scientists. In Bitcoin’s peer-to-peer process for processing transactions, computers called “miners” compete to竞相做某事solve a difficult mathematical problem, with the winner earning a reward. The researchers analyzed the rules of this process and concluded that it allows a minority 少数的of miners to collude 串通,勾结and gain more than their fair share of the rewards. In the long run从长远来看,终究, they suggest, this colluding minority could seize control of the Bitcoin network, negating否定,取消,使无效the benefits of its decentralized分散式的,分散化的,分散管理的,peer-to-peer architecture 体系结构.This is a clever analysis, but it falls far short of 差得很远,远未能proving that the decentralized cryptocurrency加密电子货币is fatally命中注定的,致命的,无可避免的flawed有缺陷的,有瑕疵的. In reality, the attack they outline is a relatively minor concern次要问题for Bitcoin miners, and shouldn't affect ordinary Bitcoin users at all.Bitcoin’s transaction clearing process operates like a virtual lottery虚拟彩票. Each miner makes a list of recent transactions交易, called a “block”块区, and then tries to solve a difficult mathematical problem that takes that block as an input投入. A correct solution works like a lottery ticket —it’s hard to find but easy to verify 验证,核实once it’s been found. The first miner to find a solution announces it to the rest of the miners to claim the prize. Within a few seconds, the other miners verify the ticket is valid有根据的,有效的, and then the process starts over, with miners creating a new block and trying to solve a new round of the puzzle.In the Cornell researchers’ attack, a minority of少数的evil miners collude in hopes of gaining an unfair advantage over everyone else其他人. Their strategy works like this: When an evil miner finds a winning lottery ticket, it shares it with the other evil miners but not with the rest of the network. The evil miners abandon the current round and start working on the next one. Meanwhile, the rest of the miners continue looking for a solution to the block the evil miners have solved. That gives the evil miners an unfair head start on the new round of the game.Eventually, one of the honest nodes will find a lottery ticket of its own and present it to the rest of the network for validation. The moment that happens, an evil node will present its own winning ticket to the network.Who gets the reward? It’s complicated, but in a nutshell简而言之,简单的说the winning ticket will most likely be the one that the majority of other miners see first. If two miners release tickets nearly simultaneously同时地, then some miners will hear about the honest miner’s ticket first and others will hear about the evil miner’s ticketinstead, making the outcome a tossup.抛硬币决定某事,没准的事To ensure that most nodes hear about the evil nodes' ticket, Eyal and Sirer propose 打算that the evil nodes set up a large number of fake miners whose only job is to listen for honest miners announcing their own tickets and then quickly disseminating 散播,传播the evil miners’ preferred ticket instead. In theory, a large enough network of fake miners should be able to ensure that the evil miners’ lottery ticket gets accepted close to 100 percent of the time. And even without that kind of trickery诡计, the researchers calculate that the colluding miners may be able to get their ticket recognized frequently enough that the strategy earns the colluding miners an unfair profit at the expense of other miners.The upshot结局,结果is that the honest miners waste a lot of their time trying to solve a problem that's already been solved. So the evil miners will win more than their share of the rewards. The researchers argue that honest miners will have a strong incentive动机to join the conspiracy阴谋集团. Over time有朝一日。
经过一段时间后, they say, the conspiracy will grow until it has gained a majority of the network’s computing power计算效率. And at that point在那时,在那个阶段, it will gain the de facto power 否决权to block and even reverse transactions submitted to提交the network.“I think it’s been overblown过分渲染by the media a lot,” says Bitcoin developer Mike Hearn of the paper. He says that Eyal and Sirer “hand-wave away” 没有充分考虑到many of the potential difficulties in carrying out their proposed attack. For example, he says, it would be hard to add a huge number of fake miners to the network without people noticing.Indeed, the biggest problems with their attack are social more than technological. Many Bitcoin miners have organized themselves into “pools” that combine their computing power and share the proceeds收益. The leaders of the major mining pools know each other. And if some miners started trying to corrupt the mining process, they would notice.It’s not hard for honest nodes to take countermeasures反抗手段,对策if they figure out what’s going on and which miners are part s of the conspiracy. If an evil miner and an honest miner both announce a lottery ticket around the same time, the honest nodes can always pick the ticket announced by the honest miner over the evil miner’s ticket.And the Cornell attack would be easy for honest miners to detect. Right now, it’s rare for two miners to announce solutions within seconds of each other. If that started to happen on a regular basis, it would be strong evidence that something fishy可疑的was going on. The more often it happened, the more data they’d have to help them identify who was honest and who was participating in the conspiracy. Honest miningpools could publish lists of their members to help flush out冲掉,排出,驱逐出来the impostor s.骗子,冒名顶替者“People have been coming up with complicated game theory博弈论attacks on the blockchain for quite a long time,” Hearn says. “This one is interesting but it’s not the biggest problem Bitcoin faces by any means.”Key word1.coinbase 比特币钱包2.加密电子货币加密电子货币(Cryptocurrency)3.比特币是经由一种称为“挖矿”的过程产生,参与者通过处理交易验证和记录来获取作为手续费的比特币,或取得新产出的比特币。
