ali-application
CA Clarity

Studio 内容管理 ........................................................................................................................................................11 Microsoft Project Interface ........................................................................................................................................11 与 VersionOne 集成 ...................................................................................................................................................12 智能部分 .................................................................................................................................................................... 12 Apache Tomcat 日志分析..........................................................................................................................................13
Journal Papers

166-A, St: 9, Chaklala Scheme IIIRawalpindi, PakistanEmail: khayam@.pkSyed Ali KhayamA SSISTANT P ROFESSORNUST Institute of Information Technology (NIIT)National University of Sciences & Technology (NUST)Rawalpindi, PakistanFebruary 2007 to dateR ESEARCH I NTERESTSProtocol and application design for sensor, mobile ad hoc, and infrastructure wireless networks, performance evaluation of network architectures and protocols, modeling and simulation of complex networking phenomena, detection and spread prevention of self-propagating malicious codesE DUCATIONPh.D. Michigan State University (MSU) – Electrical EngineeringGraduation: December 2006Academic Advisor: Professor Hayder RadhaResearch Lab: Wireless and Video Communications (WAVES) Lab, MSUM.S. MSU – Electrical EngineeringGraduation: May 2003Academic Advisor: Professor Hayder RadhaResearch Lab: Wireless and Video Communications (WAVES) Lab, MSUB. E. National University of Sciences & Technology (NUST), Pakistan – Computer SystemsEngineeringGraduation: November 1999R ESEARCH/A CADEMIC P UBLICATIONS A ND P ATENTSBook Chapter(s)Syed Ali Khayam and Hayder Radha, “MAC Layer Wireless Channel Modeling,” Multimedia over Wireless and IP Networks, Elsevier Science, March 2007.Journal PapersSyed Ali Khayam and Hayder Radha, “Modeling Worm Propagation over Vehicular Ad Hoc Networks,”to appear in SAE Transactions − Special Issue on Selected Papers from SAE World Congress 2006.Syed Ali Khayam,Hayder Radha, Selin Aviyente, and John R. Deller, Jr., “Markov and Multifractal Wavelet Models for Wireless MAC-to-MAC Channels,” to appear in Elsevier Performance Evaluation Journal, vol. 64, no. 4, pp. 298−314, May 2007.Syed Ali Khayam,Shirish Karande, Muhammad U. Ilyas, and Hayder Radha, “Header Detection to Improve Multimedia Quality over Wireless Networks,” IEEE Transactions on Multimedia, vol. 9, no. 2, pp.377−385, February 2007.Syed Ali Khayam and Hayder Radha, “Using Signal Processing Techniques to Model Worm Propagation over Wireless Sensor Networks,” IEEE Signal Processing, vol. 23, no. 2, pp. 164−169, March 2006.Syed Ali Khayam and Hayder Radha, “Linear-Complexity Models for Wireless MAC-to-MAC Channels,”ACM Wireless Networks (WINET) – Special Issue on Selected Papers from MSWiM’03, vol. 11, no. 5, pp.543−555, September 2005.Syed Ali Khayam, Shirish Karande, Hayder Radha, and Dmitri Loguinov, “Performance Analysis and Modeling of Errors and Losses over 802.11b LANs for High-Bitrate Real-time Multimedia,” Elsevier/EURASIP Signal Processing: Image Communication, vol. 18, no. 47, pp. 575—595, August 2003.Conference/Workshop/Magazine PapersSyed Ali Khayam and Hayder Radha, “On the Impact of Ignoring Markovian Channel Memory on Analysis of Wireless Systems,” to appear in IEEE International Conference on Communications (ICC), June 2007.Syed Ali Khayam and Hayder Radha, “Using Session-Keystroke Mutual Information to Detect Self-Propagating Malicious Codes,” to appear in IEEE International Conference on Communications (ICC), June 2007.Shirish Karande, Syed Ali Khayam, Yongju Cho, Kiran Misra, Hayder Radha, Jaegon Kim, and Jin-Woo Hong, “On Channel State Inference and Prediction using Observable Variables in 802.11b Networks,”to appear in IEEE International Conference on Communications (ICC), June 2007.Yongju Cho, Syed Ali Khayam, Shirish Karande, Hayder Radha, Jaegon Kim, and Jin-Woo Hong, “A Multi-tier Model for BER Prediction over Residual Wireless Channels,” International Conference on Information Sciences & Systems (CISS), March 2007.Syed Ali Khayam, Shirish Karande, Muhammad U. Ilyas, and Hayder Radha, “Improving Wireless Multimedia Quality using Header Detection with Priors,” IEEE International Conference on Communications (ICC), June 2006.Syed Ali Khayam and Hayder Radha, “Constant-Complexity Models for Wireless Channels,” IEEE Infocom, April 2006.Syed Ali Khayam and Hayder Radha, “Modeling Worm Propagation over Vehicular Ad Hoc Networks,”SAE World Congress, April 2006.Aparna Gurijala and Syed Ali Khayam, “Encryption Effects on Compression Efficiency of Still Images,”SPIE Newsroom Magazine, February 2006.Aparna Gurijala, Syed Ali Khayam, Hayder Radha, and John R. Deller, Jr., “On Encryption-Compression Trade-off of Pre/Post-Filtered Images,” SPIE Conference on Mathematics of Data/Image Coding, Compression, and Encryption (MDICCE), August 2005.Syed Ali Khayam and Hayder Radha, “A Topologically-Aware Worm Propagation Model for Wireless Sensor Networks,” IEEE ICDCS International Workshop on Security in Distributed Computing Systems (SDCS), June 2005.Syed Ali Khayam, Muhammad U. Ilyas, Klaus Pörsch, Shirish Karande,and Hayder Radha, “A Statistical Receiver-based Approach for Improved Throughput of Multimedia Communications over Wireless LANs,” IEEE International Conference on Communications (ICC), May 2005.Syed Ali Khayam, Selin Aviyente, and Hayder Radha, “On Long-Range Dependence in High-Bitrate Wireless Residual Channels,” International Conference on Information Sciences and Systems(CISS), March 2005.Syed Ali Khayam and Hayder Radha, “Analyzing the Spread of Active Worms over VANET,” ACM Mobicom International Workshop on Vehicular Ad Hoc Networks (VANET), October 2004.Syed Ali Khayam and Hayder Radha, “Markov-based Modeling of Wireless Local Area Networks,” ACM Mobicom International Workshop on Modeling, Simulation and Analysis of Wireless and Mobile Systems (MSWiM), September 2003.Syed Ali Khayam, Shirish Karande, Michael Krappel, and Hayder Radha, “Cross-Layer Protocol Design for Real-time Multimedia Applications over 802.11b Networks,” IEEE International Conference on Multimedia and Expo (ICME), July 2003.Shirish Karande, Syed Ali Khayam, Michael Krappel, and Hayder Radha, “Analysis and Modeling of Errors at the 802.11b Link-Layer,” IEEE International Conference on Multimedia and Expo(ICME), July 2003.M. Usman Ilyas, Syed Ali Khayam, Omer Suleman, and Shahid Masud, “A Configurable Platform for Simulating Multiprocessor-based System-on-Chip,” International Symposium on Wireless Systems and Networks (ISWSN), May 2003.Syed Ali Khayam, Shoab A. Khan, and Sohail Sadiq, “A Generic Integer Programming Approach to Hardware/Software Codesign,” IEEE International Multi-topic Conference (INMIC), December 2001.Syed Ali Khayam and Mudassar Farooq, "Voice and Video over IP: Challenges and the Existing Infrastructure," International Workshop on Distributed Computing, Communications and Applications (IWDCCA), January 2000.Ph.D. DissertationSyed Ali Khayam, “Wireless Channel Modeling and Malware Detection using Statistical and Information-Theoretic Tools,” December 2006.M.S. ThesisSyed Ali Khayam, “Analysis and Modeling of Errors and Losses over 802.11b LANs,” May 2003.Patents PendingSyed Ali Khayam and Hayder Radha, “Mobile Network System for Malware Monitoring,” filed to the United States Patents and Trademarks Office, application # PCT/US2006/021501, June 2005.Syed Ali Khayam and Hayder Radha, “Self-Propagating Malware Detection using Session-Keystroke Correlation,” submitted to the MSU Office of Intellectual Property Rights, January 2007.Shirish Karande, Syed Ali Khayam, Yongju Cho, Kiran Misra, Hayder Radha, Jaegon Kim, and Jin-Woo Hong, “Channel State Inference and Prediction using Observable Variables in 802.11b Networks,”submitted to the MSU Office of Intellectual Property Rights, September 2006.Syed Ali Khayam and Hayder Radha, “Worm Detection at Network Endpoints using Information-Theoretic Traffic Perturbations,” submitted to the MSU Office of Intellectual Property Rights, February 2006.Syed Ali Khayam, Shirish Karande, and Hayder Radha, “Header Estimation to Improve Multimedia Quality over Wireless Networks,” submitted to the MSU Office of Intellectual Property Rights, February 2006.Technical Report(s)Syed Ali Khayam, “The Discrete Cosine Transform: Theory and Application,” WAVES lab technical report, May 2004.P ROFESSIONAL A FFILIATIONSSession ChairIEEE International Conference on Communications (ICC) 2007− Computer and Communications Network Security SymposiumReviewerIEEE/ACM Transactions on Networking, IEEE Transactions on Wireless Communications, IEEE Transactions on Multimedia, IEEE Journal on Selected Topics in Signal Processing, IEEE Signal Processing Letters, EURASIP Journal on Wireless Communications & Networking (JWCN), Elsevier Performance Evaluation Journal, Journal of Communications and Networks (JCN) IEEE International Conference on Communications (ICC) 2007, IEEE Consumer Communications & Networking Conference (CCNC) 2007, IEEE Wireless Communications & Networking Conference (WCNC) 2006MemberIEEE, ACM,Pakistan Engineering Council (PEC)H ONORS/A WARDSInvited to chair a technical paper session at the IEEE International Conference on Communications (ICC) 2007, Computer and Communications Network Security SymposiumSelected to serve on the review panels of many prestigious journals and conferencesResearch paper on Markov models for wireless channels was selected in the top 9% papers of ACM MSWiM 2003 and was invited to be submitted as a journal paper to ACM WINET journalResearch paper on worm propagation modeling over vehicular networks in SAE World Congress 2006 was invited to appear in SAE TransactionsResearch paper on encryption-compression tradeoffs of image coding systems in SPIE MDICCE 2005 was invited to appear in SPIE Newsroom MagazineReceived a rating of 4.0 from 38 out of the total 40 students in the Electronic Design andInstrumentation Lab Course taught at MSUJournal paper on linear-complexity wireless channel models was one of ACM WINET’s five most downloaded articles in February/March 2006Opinion paper on “Faculty Hiring program of Pakistan Higher Education Commission” was selected as the finalist of the Virtual Think Tank of Pakistan − National Policy Dialog CompetitionRecipient MSU Research Enhancement Award to attend IEEE Infocom 2006Recipient of Pakistan HEC Partial Ph.D. Support Scholarship to complete Ph.D. studies at MSURecipient of Pakistan HEC Split Ph.D. Scholarship to pursue Ph.D. studies at MSURecipient of NUST Split M.S. Scholarship to pursue Masters studies at MSUMade key technical contributions to research proposals that were submitted to NSF CyberTrust Program in 2004 and 2007: For the first proposal, after peer-review the NSF funded the 3 year project in August 2004; the second proposal is still under reviewMade key technical contributions to a research proposal submitted to MSU CyberSecurity Initiative: MSU funded the 2 year project in August 2003Selected to serve as Graduate Representative on the MSU Engineering College Advisory Committee in 2004/2005E XPERIENCE I N A CADEMIASummer 2002 to present MSU – Research Assistant, Wireless and VideoCommunications (WAVES) Lab, MSUSpring 2002, Summer 2003, Spring 2004 MSU – Teaching AssistantE XPERIENCE I N I NDUSTRYOctober 2000 to AugustCommunications Enabling Technologies – Design Engineer 2001 Lead a team which designed layer controller of a VoIP chipLead a team which developed an IPSec security framework April 1999 to July 1999 Communications Enabling Technologies – InternR EFERENCESHayder Radha, Professor, MSU (radha@)John R. Deller, Jr., Professor, MSU (deller@)Dmitri Loguinov, Assistant Professor, Texas A&M University (TAMU) (dmitri@)。
师大美食推荐移动应用系统的设计与实现-毕业论文

---文档均为word文档,下载后可直接编辑使用亦可打印---摘要随着人们生活水平的提升,美食推荐的应用逐渐走入人们的视野,越来越多的人通过选择这些应用订餐。
但是,这些应用往往忽视了用户个性化的需求,推荐的美食千篇一律。
针对这一情况,研发了师大美食推荐移动应用系统。
本系统包括两大部分:移动应用端和云推送端。
其中,移动应用端是基于安卓平台开发,用户可以在手机应用上看到师大周边的各类美食。
云推送端可以根据用户的饮食习惯每日给用户个性化推荐美食。
通过在师大的测试表明,本系统可以有效帮助同学了解并适应学校周边的美食分布,解决学生吃饭选择困难的问题。
该论文有图20幅,表3个,参考文献18篇。
关键词:美食推荐动应用系统移动应用系统美食推荐Food Recommended Robile Application SystemDesign and ImplementationAbstractWith the improvement of people’s living standards, food recommendation applications walks into people's vision. More and more people choose to order foods by these applications on the phone. However, these applications tend to ignore the user personal requirement and the food they recommend follows the same pattern. In view of this situation, we development this mobile phone application of food recommendation. The system consists of two parts: mobile applications and cloud platform. The mobile application is based on the Android mobile phone by which users can see all kinds of food around the university. The cloud platform can recommend delicious food every day accord to user's eating habits. After rigorous testing,this application can help to adapt to the food distribution around the university and can solve the difficult problem of choosing food for the students.Key Words:Food Recommendation Mobile Application System; Mobile Application System; Food Recommendation图清单表清单1 绪论1.1 课题背景随着生活水平的提升,人们对于美食的要求也愈发多样,很多美食推荐软件也如雨后春笋般出现在应用市场。
PHP开发调用阿里云短信验证码的代码-直接可用

PHP开发调⽤阿⾥云短信验证码的代码-直接可⽤1:最低要求 PHP 5.62:安装了composer3:阿⾥云composer镜像地址命令(如果设置过就不需要):composer config -g repo.packagist composer https:///composer/4:安装 SDK 核⼼库 OpenAPI : Alibaba Cloud SDK for PHP 作为依赖项:composer require alibabacloud/darabonba-openapi5:阿⾥云短信SDK安装包命令(官⽅地址:https:///api-tools/sdk/Dysmsapi):composer require alibabacloud/dysmsapi-20170525 2.0.8<?php// This file is auto-generated, don't edit it. Thanks.namespace lib;use AlibabaCloud\SDK\Dysmsapi\V20170525\Dysmsapi;use AlibabaCloud\SDK\Dysmsapi\V20170525\Models\SendSmsRequest;use Darabonba\OpenApi\Models\Config;class aliyunSms{private static $accessKeyId = 'LTAI5t7AC3RH3333pZTDCaA3';//accessKeyIdprivate static $accessKeySecret = 'ihDUcyqNZvNYXASfLtijI33333NSk';//accessKeySecretprivate static $signName = 'xxxx技有限公司';//签名private static $templateCode = 'SMS_228533331';//模板代码/*** 使⽤AK&SK初始化账号Client* @param string $accessKeyId* @param string $accessKeySecret* @return Dysmsapi Client*/private static function createClient($accessKeyId, $accessKeySecret){$config = new Config([// 您的AccessKey ID"accessKeyId" => $accessKeyId,// 您的AccessKey Secret"accessKeySecret" => $accessKeySecret]);// 访问的域名$config->endpoint = "";return new Dysmsapi($config);}/*** @param string $phoneNumbers ⼿机号* @param string $code 验证码* @return void*/// public static function main($args)private static function main($phoneNumbers, $code){$client = self::createClient(self::$accessKeyId, self::$accessKeySecret);$sendSmsRequest = new SendSmsRequest(["templateParam" => "{\"code\":\"{$code}\"}","phoneNumbers" => "{$phoneNumbers}","signName" => self::$signName,"templateCode" => self::$templateCode]);$ali_res = $client->sendSms($sendSmsRequest);if ($ali_res->body->code == 'OK' && $ali_res->body->bizId != NULL) {return true;}switch ($ali_res->body->code) {case 'isv.BUSINESS_LIMIT_CONTROL':exception('短信发送频繁,请稍候再试');//tp的抛出错误,换成你⾃⼰的报错break;case 'isv.TEMPLATE_PARAMS_ILLEGAL':exception('短信验证码不符合变量规范');//tp的抛出错误,换成你⾃⼰的报错break;case 'isv.MOBILE_NUMBER_ILLEGAL':exception('⼿机号不正确,⽆法发送短信');//tp的抛出错误,换成你⾃⼰的报错break;}//少见的错误,记录下来//log_err($ali_res->body, '发送短信发⽣错误', 'ali_sms');//换成你的exception($ali_res->body->message);//tp的抛出错误,换成你⾃⼰的报错// 以下是阿⾥云短信正确和失败返回的数据,以作参考// 失败演⽰返回数据/* object(AlibabaCloud\SDK\Dysmsapi\V20170525\Models\SendSmsResponseBody)#81 (6) {["bizId"] => NULL["code"] => string(24) "isv.SMS_TEMPLATE_ILLEGAL"["message"] => string(38) "模板不合法(不存在或被拉⿊)"["requestId"] => string(36) "21A90D61-2D5E-533D-BFE7-9D16F8312A0E"["_name":protected] => array(4) {["bizId"] => string(5) "BizId"["code"] => string(4) "Code"["message"] => string(7) "Message"["requestId"] => string(9) "RequestId"}["_required":protected] => array(0) {}}*/// 成功返回数据演⽰/* object(AlibabaCloud\SDK\Dysmsapi\V20170525\Models\SendSmsResponseBody)#81 (6) {["bizId"] => string(20) "839015438514162136^0"["code"] => string(2) "OK"["message"] => string(2) "OK"["requestId"] => string(36) "EA37C2B7-E427-59F8-8B7C-06AD846A5439"["_name":protected] => array(4) {["bizId"] => string(5) "BizId"["code"] => string(4) "Code"["message"] => string(7) "Message"["requestId"] => string(9) "RequestId"}["_required":protected] => array(0) {}}*/}//发短信public static function sendSms($phoneNumbers, $code){$res = self::main($phoneNumbers, $code);return $res;}}此代码只需要修改命名空间和阿⾥云accessKeyId等相关信息,即可使⽤~exception是TP的错误异常抛出,我是做了全局的异常托管,并且在所有报错的地⽅调⽤此⽅法就能终端代码,报出错误,你只需要换成你的中断代码返回错误即可。
APP 应用程序Application的缩写

APP(应用程序,Application的缩写)编辑应用程序(外语缩写:App;外语全称:Application)。
APP指的是智能手机的第三方应用程序。
比较著名的应用商店有苹果的App Store,谷歌的Google Play Store,诺基亚的Ovi store,还有黑莓用户的BlackBerry App World,微软的Marketplace等。
最近两年,app分发成为各大互联网巨头的新“行当”,在手机厂商和专业应用下载平台的夹击下,不但没有被挤成“夹心饼干”,反而成了可口的“驴肉火烧”。
以百度手机助手为例,其打破传统应用分发的下载套路,从娱乐和社交的角度去“再造”应用分发平台,开创了一个值得圈点的应用市场新模式,也让我们看到了APP快消化品牌运作的趋势。
[1] A中文名应用软件外文名Application外语缩写App格式ipa、pxl、deb、apk等主流系统iOS、Android、WindowsPhone应用商店App Store、Marketplace等目录1介绍2手机操作系统3用途4开发5开发语言6营销7前景8应用▪基本介绍▪发展现状▪优势因素9国内APP管理1介绍编辑iOS系统格式有ipa,pxl,deb;Android系统格式有:apk;诺基亚的S60系统格式有sis,sisx,jar;微软的WindowsPhone 7、WindowsPhone 8系统格式为xap;黑莓平台为zip。
一开始应用[2] 只是作为一种第三方应用的合作形式参与到互联网商业活动中去的,随着互联网越来越开放化,应用作为一种萌生与iphone的盈利模式开始被更多的互联网商业大亨看重,一方面可以积聚各种不同类型的网络受众,另一方面借助APP平台获取流量,其中包括大众流量和定向流量。
2手机操作系统编辑主流的手机操作系统有:苹果系统版本iOS[3]安卓Android微软windowsphone塞班系统版本Symbian3用途编辑随着智能手机和iPad等移动终端设备的普及,人们逐渐习惯了使用应用客户端上网的方式,而目前国内各大电商,均拥有了自己的应用客户端,这标志着,应用客户端的商业使用,已经开始初露锋芒。
爱立信告警百科
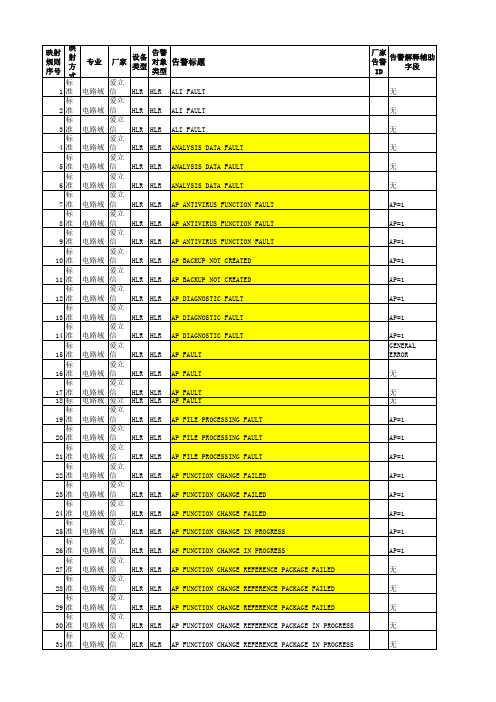
映 告警 射 专业 厂家 设备 对象 告警标题 类型 方 类型 式 标准 电路域 爱立信HLR HLR ALI FAULT 标准 电路域 爱立信HLR HLR ALI FAULT 标准 电路域 爱立信HLR HLR ALI FAULT 标准 电路域 爱立信HLR HLR ANALYSIS DATA FAULT 标准 电路域 爱立信HLR HLR ANALYSIS DATA FAULT 标准 电路域 爱立信HLR HLR ANALYSIS DATA FAULT 标准 电路域 爱立信HLR HLR AP ANTIVIRUS FUNCTION FAULT 标准 电路域 爱立信HLR HLR AP ANTIVIRUS FUNCTION FAULT 标准 电路域 爱立信HLR HLR AP ANTIVIRUS FUNCTION FAULT 标准 电路域 爱立信HLR HLR AP BACKUP NOT CREATED 标准 电路域 爱立信HLR HLR AP BACKUP NOT CREATED 标准 电路域 爱立信HLR HLR AP DIAGNOSTIC FAULT 标准 电路域 爱立信HLR HLR AP DIAGNOSTIC FAULT 标准 电路域 爱立信HLR HLR AP DIAGNOSTIC FAULT 标准 电路域 爱立信HLR HLR AP FAULT 标准 电路域 爱立信HLR HLR AP FAULT 标准 电路域 爱立信HLR HLR AP FAULT 标准 电路域 爱立信HLR HLR AP FAULT 标准 电路域 爱立信HLR HLR AP FILE PROCESSING FAULT 标准 电路域 爱立信HLR HLR AP FILE PROCESSING FAULT 标准 电路域 爱立信HLR HLR AP FILE PROCESSING FAULT 标准 电路域 爱立信HLR HLR AP FUNCTION CHANGE FAILED 标准 电路域 爱立信HLR HLR AP FUNCTION CHANGE FAILED 标准 电路域 爱立信HLR HLR AP FUNCTION CHANGE FAILED 标准 电路域 爱立信HLR HLR AP FUNCTION CHANGE IN PROGRESS 标准 电路域 爱立信HLR HLR AP FUNCTION CHANGE IN PROGRESS 标准 电路域 爱立信HLR HLR AP FUNCTION CHANGE REFERENCE PACKAGE 标准 电路域 爱立信HLR HLR AP FUNCTION CHANGE REFERENCE PACKAGE 标准 电路域 爱立信HLR HLR AP FUNCTION CHANGE REFERENCE PACKAGE 标准 电路域 爱立信HLR HLR AP FUNCTION CHANGE REFERENCE PACKAGE 标准 电路域 爱立信HLR HLR AP FUNCTION CHANGE REFERENCE PACKAGE 标准 电路域 爱立信HLR HLR AP LOG STATISTICS 标准 电路域 爱立信HLR HLR AP LOG STATISTICS 标准 电路域 爱立信HLR HLR AP LOG STATISTICS 标准 电路域 爱立信HLR HLR AP MESSAGE STORE WARNING 标准 电路域 爱立信HLR HLR AP MESSAGE STORE WARNING 标准 电路域 爱立信HLR HLR AP MESSAGE STORE WARNING 标准 电路域 爱立信HLR HLR AP NOT AVAILABLE 标准 电路域 爱立信HLR HLR AP NOT AVAILABLE 标准 电路域 爱立信HLR HLR AP NOT AVAILABLE 标准 电路域 爱立信HLR HLR AP NOT REDUNDANT 标准 电路域 爱立信HLR HLR AP NOT REDUNDANT 标准 电路域 爱立信HLR HLR AP NOT REDUNDANT 标准 电路域 爱立信HLR HLR AP NOT REDUNDANT 标准 电路域 爱立信HLR HLR AP PROCESS REINITIATED 标准 电路域 爱立信HLR HLR AP PROCESS REINITIATED 标准 电路域 爱立信HLR HLR AP PROCESS REINITIATED 标准 电路域 爱立信HLR HLR AP PROCESS STOPPED 标准 电路域 爱立信HLR HLR AP PROCESS STOPPED 标准 电路域 爱立信HLR HLR AP PROCESS STOPPED 标准 电路域 爱立信HLR HLR AP PROCESS STOPPED 标准 电路域 爱立信HLR HLR AP REBOOT 标准 电路域 爱立信HLR HLR AP REBOOT 标准 电路域 爱立信HLR HLR AP REBOOT 标准 电路域 爱立信HLR HLR AP SOFT FUNCTION CHANGE FAILED 标准 电路域 爱立信HLR HLR AP SOFT FUNCTION CHANGE FAILED 标准 电路域 爱立信HLR HLR AP SOFT FUNCTION CHANGE FAILED 标准 电路域 爱立信HLR HLR AP SOFT FUNCTION CHANGE IN PROGRESS 标准 电路域 爱立信HLR HLR AP SOFT FUNCTION CHANGE IN PROGRESS 标准 电路域 爱立信HLR HLR AP SYSTEM ANALYSIS 标准 电路域 爱立信HLR HLR AP SYSTEM ANALYSIS
Alfresco介绍
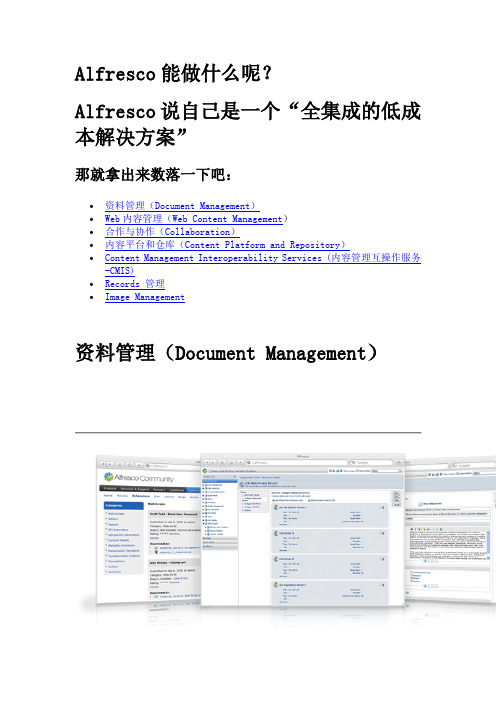
Alfresco能做什么呢?Alfresco说自己是一个“全集成的低成本解决方案”那就拿出来数落一下吧:∙资料管理(Document Management)∙Web内容管理(Web Content Management)∙合作与协作(Collaboration)∙内容平台和仓库(Content Platform and Repository)∙Content Management Interoperability Services (内容管理互操作服务-CMIS)∙Records 管理∙Image Management资料管理(Document Management)一些很贵的也很复杂的企业资料管理系统(ECM)已经不少了。
不过人们往往更习惯使用那些每天都用的简单的熟悉的工具,比如:共享驱动器(shared drives)和微软Office(Microsoft Office).Alfresco 资料管理(Document Management)在对内容的接受,共享和存储方面,可以更好的让用户使用自己常用的工具容易的建立自己的内容应用,包括检索和版本化管理等重要功能。
共享驱动器(Shared drive)Alfresco的资料库和一个共享在网络上的驱动器一样。
你可以保留使用任何你知道的或者喜欢的编辑工具来编辑资料。
从Microsoft Office 到Open Office, Dreamweaver 或者 AutoCAD,而不用安装其他的程序或者需要重新学习。
无论是自己还是公司需要的功能都可以满足,包括存储,版本化管理,共享,检索和审计。
对MS Office的集成(Integration with Microsoft Office)Alfresco集成了MS Office 和 Open Office。
所以你可以一如既往的使用你自己的office环境,在不需要再学习的情况下,你和你的公司就可以得到存储,版本化管理,共享,检索和很简单的就集成了工作流的审计功能。
PREARRIVAL INFORMATION JEBEL ALI

Pre arrival information for Jebel Ali PortWish to advise you that, we “Inchcape Shipping Services” has been appointed as agents for your good vessels upcoming call to Jebel Ali Port for cargo operations.Kindly find below pre-arrival info along with ISPS requirements attached for your arrival Jebel Ali Port.Appreciate to keep us advised about your updated ETA in Jebel Ali.We are pleased to provide you with the following.Pre arrival information for Jebel Ali Port - Ref: ISS/Pre-arrival / J.Ali / Ver01 022009.Pls note, JEA Port Maintains Security Level-01.Prior to arrival all vessels, regardless of tonnage, should provide Jebel Ali Port Control with the following information:a) Name of the vesselb) Port of Registry – Please send us this on priority so that we can register your good vessel with the local Port.c) Name of the Masterd) Gross tonnagee) LOA.f) Arrival Draftg) Cargo to discharge/loadh) Voyage Numberi) Pilot boarding arrangementsj) Number of crew indication the number of deck crew available for maneuveringk) Health informationl) Last port of callk) if any security / arm and ammunition on boardi) any special requirement such as Fresh water supply, Main Engine Immobilization, sludge disposal, lifeboat lowering etc to be arranged at Jebel Ali Port.j) Berthing preference, port side or starboard sideCommunicationThe Port Radio station maintains continuous listening watch on VHF Channel 16 The Port Emergency Channel is VHF 18A On coming within VHF range of Jebel Ali Port Control, vessel should establish VHF Contact for the purpose of updating the estimated time of arrival and at least two hours notice in the Pilot Boarding Area Should be given.Vessels are warned that VHF channels are monitored and tape recorded, any misuse of VHF channels will be reported tothe proper authoritiesMarine InformationMinimum RequirementsIn the interest of avoiding delays, all vessels calling Jebel Ali should comply with the following minimum requirements andbe fitted with:(I) Fully operational radar(ii) Fully operational VHF radio with normal marine channels.(iii) Sufficient crew to handle tug line and mooring efficiently.(iv) Efficient propulsion and deck machinery.(v) Efficient and adequate moorings to secure vessel safely.(vi) Efficient signaling equipment(vii) Fully operational tachometer, rudder and helm indicators.(viii) Efficient mooring stations communications system(ix) Efficient anchor windlass and anchorsIf any of the above requirements cannot be complied with, the Harbour Master should be advised prior to arrival via Jebel Ali Port ControlPilot Boarding AreaThe Pilot Boarding Area is located north of the channel entrance. The centre of this area is in position 25deg 09'Nand 54deg 54É with a radius of one mile.Please send us the following documents by email or fax. Our fax No +971 4 3345622.(a) Copy of Ship's Registry-(b) Copy of crew list with S/book numbers / Date of issue / Expiry + Passport Numbers / Date of Issue & Date of expiry to be incorporated – ( A Blank Copy of Crew-list attached here for your ready reference & use).(c) Last Port Clearance copy, Original MUST be on board. Kindly ensure that destination mentioned as Jebel Ali & total no.of crew should match with on arrival crew list(d) International Ship Security Certificate copy(e) Stowage plan(f) – A Separate Passengers List – Indicating Full Names & Passport Details of the Security Guards Travelling with the vessel if not holding seaman’s book. If security personal are holding seaman’s book request to put their names on crew list.(g) - Weapons Declaration on vessel’s letterhead duly Signed/Stamped by Master/Chief Officer.Pls keep the Original Weapons Declaration Letter Duty Signed/Stamped by Master/Ch.Officer) ready for collection by the ISPS Duty Security Officer in Charge who will board thevessel on ship’s arrival in JEA Port.(h) –Weapons Declaration on Carrier’s Letterhead.Same will also be collected by the same ISPS Duty Security Officer in Charge who will visit the vessel on ship’s arrival at JEA Port(Specimen Weapons on Carriers Letterhead attached).Very Important message for vessels carrying Weapons and Armed Security On Board a Merchant Vessel:We have attached here ’Procedures for Armed Security On board Merchant Vessels’’ issued by Security Department of Jebel Ali Ports, Customs & Free Zone Corporation for your Perusal, Ready Reference & ComplianceRe: Fresh Water Supply Cost at JEA Port & Disclaimer for same as Follows:Fresh Water available at Jebel Ali Port @ AED 13.5/- ( US$ 3.5 ) PMTon – ( ROE: US$ 1/- = AED 3.66 ).Fresh Water supplied to the vsls by the Dubai Electricity and Water Authority-(DEWA) through quay pipe linesand the cost is based on quantity supplied as evidenced by the shore meter reading, irrespective of the quantityreceived on board. This cannot be disputed.A) Four copies of crew list (duly signed / stamped original) in attached format.B) Three copies of ships registryC) Original last Port clearance + 2 copiesD) One copy of ships particulars.Our Boarding agent shall collect above documents to register the vessel inward and outward clearance.No Immigration / Customs Officials will come on board for inspection.Re: Crew Shore Leave/Passes & Requirements for Same:- Ship Crew can apply for Shore Passes only after two-(02)-hours of Vessel Registered with Local Port Immigration Authority.- Crew Shore-leave not permitted after 19:00-hrs LT.- Shore-leavers Must Return back to the vessel by or before 23:00-hrs-LT on same day.Shore Leave/Passes Requirements:Original Passport and Seaman’s Book + 02-Ppt Size Photographs required at theImmigration .Shore Leave is subject to CID/immigration Authorities Approval.- According to Local Authorities’ Rules & Regulation,Only Crew/Passengers Listed onCrew-list-(subject to CID approval) will be allowed to go for shore leave.Passport size photograph to be available for shore liberty for each person. In case of photograph not available thensame can be arranged through photograph booth available at Jebel Ali while making a payment of AED 15/- in the slotMachine for 4 photographs - ROE: US$ 1/- = AED: 3.66.Pls be guided & kindly advise all ship-crew / shore leavers accordinglyRe: Passengers/Security Guards Shore LeavePls be advised that Only Valid Seamen Book & Passport Holders will be permitted to go for ashore leave, provided, they are on the Crew-list.Crew / Passengers Holding Only Passports, but No Seamen-Books will be considered as passengers & they mustbe On a separate Passengers List - None Seamen-Book Holders will not be permitted to go for shore leaveby the Local Immigration Authorities.Please have the following documents ready on arrival for inward clearance.A) Four copies of crew list (duly signed / stamped original) in attached format.B) Three copies of ship registryC) Original Last port clearance + 2 copiesD) One copy of ships particulars.Please note our 24 Hours contact no. at Jebel Ali Port - +971 56 6865476We have also attached ISPS check list for Jebel Ali Port.Please acknowledge & confirm this message with attachments well received.Best Regards,。
springboot操作阿里云OSS实现文件上传,下载,删除功能

springboot操作阿⾥云OSS实现⽂件上传,下载,删除功能⽬录1.需求2. 阿⾥云OSS购买和配置3. Springboot操作OSS4.运⾏项⽬测试API接⼝参考资料:学会看⽂档,并实际运⽤也是⼀种习惯和技能下⾯就来简单⼊门⼀下,⽤当下⽐较热门的Springboot 去操作阿⾥云OSS⽂件存储。
1.需求(没踩过下⾯的坑的⼩伙伴可以直接跳过这⼀章节)问题简述⾸先,我在之前⾃⼰做⼀些开源⼩项⽬案例中遇到⼀些⽂件上传下载的问题,⽐如在本机⽂件上传和下载都可以正常使⽤,通过将⽂件上传到Springboot项⽬的根⽬录下,按⽇期分⽂件夹,⽂件访问也很⽅便,可以直接返回⽂件相对路径地址,并直接可以访问。
问题然⽽,这种⽅式存在弊端,因为当项⽬打包(jar包)部署阿⾥云学⽣机后,出现类似io.NotFoundException...(No Such Directory)的问题,,⽽如果打war包部署到tomcat则没问题,可以正常使⽤,经过排查很久,找出问题所在:因为jar打包封装后是不能改变其内部⽬录结构的,也就是说,按⽇期分类的⽂件上传⽂件夹,如果当需要创建新⽇期的⽂件夹的时候,是⽆法在jar包中新增⽂件夹的,这时候就会出现IO异常问题。
⽽对于放在tomcat中的war包,当tomcat运⾏的时候会⾃动解压war包,其在服务器上是存在真实路径的。
解决⽅案⽅案⼀:我在⽹上找了⼀种⽅法,是通过打完jar包部署后,给springboot项⽬static下的⽂件上传⽂件夹单独分离出来(相当于是以相对路径换绝对路径),访问的时候直接相当通过服务器上和jar包同级⽬录下新建⼀个⽂件上传⽂件夹。
⽅案⼆:直接将⽂件上传到服务器指定路径下的⽂件上传位置,这种⽅式也相当于直接使⽤绝对路径。
⽅案三:在服务器上使⽤FastDFS和Nginx搭建分布式⽂件存储,这种⽅式⽐较复杂,⽽且学⽣及本来内存和带宽就⼩,在⾃⼰电脑的虚拟机可以试试这种⽅案,还是挺好⽤的,学⽣服务器就算了。
HSF分布式开发框架

HSF 初体验目录一句话形容HSF 0HSF安装 0Ali-Tomcat安装 0Pandora安装 0环境配置 0提供HSF服务 0创建Web项目 0添加maven依赖 (1)编写需要发布的服务 (2)配置Spring (3)消费HSF服务 (4)添加spring配置 (4)编写测试代码 (5)打包测试 (5)实践 (6)一句话形容HSFHSF就好比人体的血管,它是阿里内部各个系统通信的基础软件。
HSF安装先了解下HSF应用的运行环境。
如图:首先,应用运行在潘多拉(Pandora)容器中,容器又通过Ali-Tomcat启动。
Ali-Tomcat安装下载并解压Ali-Tomcat即可。
Pandora安装下载并解压Pandora到Ali-Tomcat的deploy目录即可。
到此,HSF的运行环境就安装完毕。
环境配置//TODO configserver 绑定提供HSF服务创建Web项目首先用idea(或者eclipse,这里以idea为例)创建一个maven web项目。
File -> New Project -> Maven -> Create from archetype -> maven-archetype-webapp -> 连续Next 项目目录结构如图:添加maven依赖在项目pom.xml中添加如下依赖:<dependencies><dependency><groupId>org.springframework</groupId><artifactId>spring-web</artifactId><version>3.1.1.RELEASE</version></dependency><dependency><groupId>com.taobao.hsf</groupId><artifactId>hsf.app.spring</artifactId><version>2.1.0.7</version><scope>provided</scope></dependency><dependency><groupId>javax.servlet</groupId><artifactId>javax.servlet-api</artifactId><version>3.0.1</version><scope>provided</scope></dependency></dependencies>=编写需要发布的服务创建需要发布的服务接口,com.taobao.edas.test.SampleServicepublic interface SampleService {String echo(String str);}SampleService服务提供了一个echo的方法调用。
Flex System IB6131 InfiniBand Switch 产品指南说明书

Flex System IB6131 InfiniBand SwitchProduct Guide (withdrawn product)The Flex System IB6131 InfiniBand Switch is designed to offer the performance you need to support clustered databases, parallel processing, transactional services, and high-performance embedded I/O applications, helping to reduce task completion time and lower the cost per operation. The switch supports 40 Gbps QDR InfiniBand and can be upgraded to 56 Gbps FDR InfiniBand.The Flex System IB6131 InfiniBand Switch can be installed in the Flex System chassis, which provides a high bandwidth, low latency fabric for Enterprise Data Centers (EDC), high-performance computing (HPC), and embedded environments. When used in conjunction with IB6132 InfiniBand QDR and FDR dual-port mezzanine I/O cards, these switches will achieve significant performance improvements resulting in reduced completion time and lower cost per operation.Figure 1 shows the switch module.Figure 1. Flex System IB6131 InfiniBand SwitchDid you know?This switch is designed for low latency, high bandwidth, and computing efficiency for performance-driven server and storage clustering applications. The switch supports full bisectional bandwidth, and, when combined with the InfiniBand 56 Gbps FDR adapter, your organization can achieve efficient high-performance computing by providing maximum bandwidth and off-loading from the CPU protocol processing and data movement overhead, such as Remote Direct Memory Access (RDMA) andSend/Receive semantics, allowing more processor power for the application.Flex System, a new category of computing and the next generation of Smarter Computing, offers intelligent workload deployment and management for maximum business agility. This chassis delivers high-speed performance complete with integrated servers, storage, and networking for multiple chassis management in data center compute environments. Furthermore, its flexible design can meet the needs of varying workloads with independently scalable IT resource pools for higher utilization and lower cost per workload. While increased security and resiliency protect vital information and promote maximum uptime, the integrated, easy-to-use management system reduces setup time and complexity, providing a quicker path to a return on investment (ROI).Click here to check for updatesFigure 2. Location of the switch bays in the Flex System Enterprise ChassisFigure 3. Logical layout of the interconnects between I/O adapters and I/O modulesThe Flex System IB6131 InfiniBand Switch can be installed in bays 1, 2, 3, and 4 of the Enterprise Chassis.A supported InfiniBand adapter card must be installed in the corresponding slot of the compute node (slot A1 when modules are installed in bays 1 and 2 or slot A2 when switches are in bays 3 and 4).With compute nodes that have an integrated dual-port 10 GbE network interface controller (NIC), these switches can only be installed in bays 3 and 4, because integrated NIC's ports are routed to bays 1 and 2 with a specialized periscope connector, and the InfiniBand adapter card in slot A1 cannot be installed. However, when needed, the periscope connector can be replaced with an InfiniBand adapter card. In this case, the integrated NIC will be disabled, and the InfiniBand switches can be used in bays 1 and 2.The following table shows the connections between the adapters installed in the compute nodes other than x222 to the switch bays in the chassis.Table 3. Adapter to I/O bay correspondenceI/O adapter slot in the server Port on the adapter Corresponding I/O module bayin the chassisSlot 1Port 1Module bay 1Port 2Module bay 2 Slot 2Port 1Module bay 3Port 2Module bay 4Slot 3(full-wide compute nodes only)Port 1Module bay 1 Port 2Module bay 2Slot 4(full-wide compute nodes only)Port 1Module bay 3 Port 2Module bay 4The following table shows the connections between the adapters installed in the x222 compute nodes to the switch bays in the chassis.Table 4. x222 InfiniBand adapter to I/O bay correspondenceCompute node IB6132D 2-port FDR InfiniBand Corresponding I/O module bay in the chassis Upper compute node Upper Port 1Module bay 4Lower compute nodeLower Port 1Module bay 3The following table lists the InfiniBand I/O adapters that are supported by the IB6131 InfiniBand Switch.Table 5. Supported InfiniBand I/O adapter cardsDescriptionPart numberFeature code (x-config / e-config)Support for IB6131switch Flex System IB6132 2-port FDR InfiniBand Adapter 90Y3454A1QZ / None Yes Flex System IB6132 2-port QDR InfiniBand Adapter NoneNone / 1761Yes Flex System IB6132D 2-port FDR InfiniBand Adapter90Y3486A365 / A365YesThe adapters are installed in slots in each compute node. Figure 4 shows the locations of the slots in thex240 M5 Compute Node. The positions of the adapters in the other supported servers are similar.Figure 4. Location of the I/O adapter slots in the Flex System x240 M5 Compute NodeConnectors and LEDsFigure 5. Front panel of the Flex System IB6131 InfiniBand SwitchPopular configurationsFigure 6 shows the use of the Flex System IB6131 InfiniBand switches to route two InfiniBand FDR ports on the dual-port expansion card installed in slot 2 of the compute node. Each compute node has two InfiniBand ports, and two IB6131 switches are installed in bays 3 and 4 of the Enterprise Chassis. The connections between the adapter card and the modules are internal to the chassis. No cabling is needed.Figure 6. Using IB6131 InfiniBand Switch with dual-port InfiniBand FDR adapter cardsThe following table lists the solution components.Table 6. Components used when connecting the adapter to the InfiniBand switchesDescription QuantityPart number/machinetype1 to 149532-x4x Flex System x240 M5 with EN4172 2-port 10Gb EthernetAdapter90Y3454Flex System IB6132 2-port FDR InfiniBand Adapter 1 per server8721-A1x Flex System Enterprise Chassis195Y3309Flex System Fabric EN4093R 10Gb Scalable Switch290Y3450Flex System IB6131 InfiniBand Switch290Y3462Flex System IB6131 InfiniBand Switch (FDR Upgrade)290Y34703m FDR InfiniBand Cable Up to 18 per IB6131switchRelated publicationsTrademarksLenovo and the Lenovo logo are trademarks or registered trademarks of Lenovo in the United States, other countries, or both. A current list of Lenovo trademarks is available on the Web athttps:///us/en/legal/copytrade/.The following terms are trademarks of Lenovo in the United States, other countries, or both:Lenovo®Flex SystemLenovo ServicesSystem x®Other company, product, or service names may be trademarks or service marks of others.。
阿里分布式缓存Tair技术介绍

TAIR在阿里的应用
• • 缓存,降低对后端数据库的访问压力, 会员,session,库存,购物车,优惠等 数据存储,允许部分数据丢失 • 离线数据导入,在线访问 • 读取低延迟,不能有毛刺
内存型 临时存储
M
F
SSD 快速导入 极速查询
SSD 持久化需求
L
R
内存型 丰富数据结构
• 通用kv存储,交易快照,安全风控等 • 存储黑白单数据,读qps很高 • 计数器功能,更新非常频繁,数据不可丢失
1%
Memory Management
Other 20% Locking
15%
优化前 • • • •
优化后 细粒度锁(fine-grained locks) 无锁数据结构(lock-free data structures) CPU本地数据结构(per-CPU data structures) 读拷贝更新(RCU)
业务解决方案—内存网格
中心
• 场景 • 读写量超大 • 大量本地计算 • 高性能计算快速IO • 方案 • 数据本地性 • 读穿透 • Write Through • Write Behind/merge • 多单元replication
Application Application
单元
Application
异地多活与单元化 24*365的稳定性 为了更好的体验
• 弹性扩展与资源调度
异地多活与单元化
单元A
机房 统一接入层 应用层 机房 统一接入层 应用层
中心机房
机房 统一接入层 应用层
单元B
机房 统一接入层 应用层
中间件
中间件
中间件
中间件
TAIR
TRADEMARKELECTRONICAPPLICATIONSYSTEM(TEAS)

TRADEMARK ELECTRONIC APPLICATION SYSTEM (TEAS) Welcome to United States Patent and Trademark Office (USPTO) e-TEAS TUTORIALTo use e-TEAS successfully, please follow the steps outlined below. For additional general trademark information, please telephone the Trademark Assistance Center, at 703-308-9000. If you need help in resolving glitches or need answers to technical questions, you can email us at ******************. Please include your telephone number, so we can talk to you directly, if necessary.STEP 1: Determine (1) what mark you want to register, and the form thereof (i.e., either words only or stylized wording and/or design; and (2) the goods to which the mark is (or will be) applied, or the services in connection with which the mark is (or will be) used. For assistance with the goods and/or services, check the USPTO Goods/Services Manual.STEP 2: Use the Trademark Electronic Application System (TESS) to search the USPTO database, to determine whether a confusingly similar mark is already registered, or whether a pending application for a confusingly similar mark has been filed, for related goods and/or services.STEP 3:Based on your search results from TESS (STEP 2), check the status of any potentially conflicting application or registration through the Trademark Application and Registration Retrieval (TARR) system.STEP 4: In light of all of the information above, re-assess whether it makes sense to seek registration. Please be aware that once you file your application, we do not cancel the filing or refund the fee, unless the application fails to satisfy minimum filing requirements. The fee is a processing fee, which the USPTO does not refund, even if no registration ultimately issues after the substantive review by the examining attorney. STEP 5: If the mark you wish to register consists of stylized wording or a design, then first create a GIF or JPG image file of the mark, and save onto your local drive. e-TEAS cannot be used for filing a stylized or design mark if no GIF or JPG image file exists. Similarly, if you will be filing the application based on actual use in commerce (i.e., you have already sold goods or rendered services under this specific mark), create a GIF or JPG im age file of the “specimen” of use, i.e., either scan or digitally photograph a sample of how the mark actually appears; e.g., a tag or label for goods or an advertisement for services. (However, because submission of a specimen is not required at the time of filing, lack of an image file for the specimen will not preclude filing an initial application through e-TEAS). NOTE: You do not have to create a special electronic file for a “word only” (i.e., not stylized or design) mark, or for an “intent-to-use” application ( i.e., where you have not yet sold goods or rendered services under this specific mark, but you have a bona fide intention to use the mark at some point in the future.STEP 6: Access the front page of the TEAS site. If necessary, click on the links to the Frequently Asked Questions about Trademarks and the TEAS Technical and Policy Hints. STEP 7: Click on the designated link to access the list of available e-TEAS forms.STEP 8: Click on the link for Trademark/Servicemark Application, Principal Register. STEP 9: Answer the series of YES and NO questions on the first page of the Form Wizard. When finished, click on the NEXT button at the bottom of the page, to pull up a form tailored to the specific requirements for this particular filing.STEP 10: Enter information in the appropriate fields in the form. You must enter information in all of the fields containing a red asterisk, as these fields are considered mandatory to receive an application filing date. However, you should enter all available information at this time, since failure to do so, although not preventing filing, may delay approval of the application and require later submission of the information to the assigned examining attorney.STEP 11: If you are the proper signatory of the application, you will “sign” the completed application by entering any combination of alpha/numeric characters that has been specifically adopted to serve the function of the signature, preceded and followed by the forward slash (/) symbol. Acceptable "signatures" could include: /john doe/; /jd/; or /123-4567/. No “pre-approval” from the USPTO of the “electronic signature” is required, nor must the “electronic signature” even be consistent from one filing to the next.If you are not the proper signatory, proceed to the Validate Form function, at STEP 12. The application may still be verified to check for missing information or errors even if the signature and date signed fields are left blank. STEP 19will permit you, if appropriate, to send the application to another party for signature.STEP 12: Upon completing the application, click on the “Validate Form” button at the end of the form. If you did not enter information for a mandatory field, an “error” screen will pop up. You must then re-access the initial form to enter the required information. You can continue the application process only by eliminating all error messages. Clicking the “Reset Form” button will totally clear all entries in the form.For fields that are not considered mandatory, but for which an entry should be made, a “warning” screen will pop up. If an entry was not made simply due to oversight, you can again re-access the form to enter information by clicking on “Go Back.” However, you can by-pass a “warning” and continue the application submission process by clicking onthe “Continue” button, if the piece of information is not known at this time and it is more critical to receive a filing date than to wait for that data.STEP 13: Before submitting the application, double-check your work by clicking on the icons within the Validation Page (to view the application data in various formats):∙Input: this presents the data in a simple “table” format (i.e., field name on the left, data on the right, with no “boilerplate” text).∙Drawing: the mark will appear in the middle of the page, either as typed words, or as the image previously attached. Print out this page to ensure that the resulting image is correct, i.e., the entire mark is visible, in clear black-and-white (no gray tones), and not greater than 4x4 inches. (Because of different monitor settings, it is not always possible to determine this simply by viewing the image on-line. We are concerned only with how the image actually “prints out”). If you determine that the image is not acceptable, then you must create a new image file, re-attach the file within the form, and repeat the steps outlined above.∙Specimen (only appears for a use-based application): the specimen image (which, unlike the drawing image, may be in color) should be viewable. Print out this page to ensure that the entire specimen has been captured. (Because of different monitor settings, it is not always possible to determine this simply by viewing the image on-line. We are concerned only with how the image actually “prints out”). If you determine that the image is not acceptable, then you must create a new image file, re-attach the file within the form, and repeat the steps outlined above.∙Scannable format: this shows all of the data as associated with tagged data fields, which permits the USPTO to upload the information directly into our databases and avoid manual data entry errors.∙Text form: this presents the application data in a narrative, paragraph-type format. STEP 14: Print the information accessed from any of these icons for your records simply by using the print function within the standard browser.STEP 15: If any of the information being viewed is incorrect, close the page, to return to the main Validation Page. Then, click on the “Go Back to Modify” button at the bottom of the Validation Page, to access the original application form. You can then correct any errors. Because a change has been made to the form, you must re-validate the application,again using the Validate Form button. At this point, you may resume the process at the Validation Page.STEP 16: Enter the address to which the USPTO is to email the acknowledgment; e.g., either a personal em ail address or a “docketing” email address specifically established to track application filings. (The USPTO no longer mails paper filing receipts for electronically submitted applications).STEP 17: Re-enter the email address, to ensure delivery of the acknowledgment. (An inconsistent entry will result in a pop-up box asking for another entry of the address). STEP 18: Read and check the box within the “Important Notice” section at the bottom of the Validation Page. This confirms that you understand that once you file an application, we will not cancel the filing or refund the fee, unless the application fails to satisfy minimum filing requirements. The fee is a processing fee, which we do not refund even if we cannot issue a registration after our substantive review.STEP 19: To save the electronic file to a local drive (either to pull up to continue work at a later time, or to forward to another party, either for review or signature), click on the “Download Portable Form” button at the bottom of the V alidation Page.STEP 20: If ready to file, click on the PAY/SUBMIT button. If paying by deposit account, shortly after clicking the PAY/SUBMIT button, a screen comes up that says “SUCCESS! We have received your application and assigned serial number ________.” Within 24 hours, an email acknowledgment, containing both the assigned serial number and a complete summary of all data (but for any images), will also be sent to the email address provided at STEP 16. For your records, print out copies of the SUCCESS screen and the email acknowledgment.If paying by credit card, clicking on the PAY/SUBMIT button will bring up a screen to enter the appropriate credit card information. After properly entering the credit card information, submission can be completed to the USPTO. Shortly after successful transmission, a screen comes up that says “SUCCESS! We have received your application and assigned serial number ________.” Again, within 24 hours, an email acknowledgment, containing both the assigned serial number and a complete summary of all data (but for any images), will also be sent to the email address provided at STEP 16. For your records, print out copies of the SUCCESS screen and the email acknowledgment.STEP 21: If after successful filing you discover an error, follow the steps outlined in the email acknowledgment for submission of a “preliminary amendment.”STEP 22: Follow the status of the prosecution of the application through the Trademark Application and Registration Retrieval (TARR)system, or call 703-305-8747 (Monday-Friday, 6:30 a.m. to 12 midnight, EST). However, do NOT attempt to check status until at least 45 days after submission, to allow sufficient time for our databases to be updated.。
GATE-WAY

Session
映射管理
Cache
管理(历史k线等)
数据转发 处理器
数据接收 缓冲区
断线重连 处理器
负载均 衡处理 器
权限 认证
状 态 检 测
V4(Decode/Encode)
网关转发 数据方案
Client C1 C2 C3 . . . S1 S2 S3 S4 S5 S6 S7 S8 . . .
方案一
创建通道 Y
转发数据
aplication
数据流
aplication ->gateway-> outerSpace
outerSpace
转发数据
Y 数据包
aplication
GateWay S1-L1 S2-L1 S3-L1 S1-SIF S2-SIF S3-SIF S1-L2 S2-L2 S3-L2 Application
LEVEL-1
SIF
LEVEL-2
网关转发 数据方案
Client C1 C2 C3 . . . S1 S2 S3 S4 S5 S6 S7 S8 . . .
GATE-WAY架构设计初稿
概要
• • • • 网关作用 网关架构 网关转发数据方案 数据流
网关作用
一.转发 把不同种类的外部系统请求转发给不同的业务系统。
二.简化外部系统 Gateway是为阻隔复杂度向外蔓延而生的,它把复杂的 实现封装起来,为其他模块或系统提供一个简单易用的接口。
网关架构之
方案二
GateWay S1-L1 S2-L1 S3-L1 S1-SIF S2-SIF S3-SIF S1-L2 S2-L2 S3-L2 Application
LEVEL-1
Salesforce Process Builder用户指南说明书

Contents Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17About This Guide . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17 Overview of Process Builder Components . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17 Using Process Builder . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18 Advanced Scripting and Setting Up Searching . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18 Sample Applications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18 Reference Material . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19 Assumptions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19 Conventions Used in This Guide . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19 Viewing Documentation Online . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20 For More Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20Chapter 1 Overview of iPlanet Process Manager . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21 Workflow in Business Processes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21 Designing a Process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22 Performing Tasks in a Process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23 Administering Processes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26 Summary of Process Manager Components . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26 Chapter 2 Introduction to Process Builder . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29 About Processes and Process Builder . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29 What is a Process? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29 What is Process Builder? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30 Who Should Use Process Builder? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32 What is a Process Instance? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32 About Applications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33 Creating an Application . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33 Deploying an Application . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34 Sample Applications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34 Starting Process Builder . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34 The preferences.ini File . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35 Starting Process Builder on Windows NT . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 363Starting Process Builder on Solaris . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36Using Process Builder . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37 Process Builder Applications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39Application Tree View . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41Process Map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42Map Palette . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42Messages Window . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44Main Toolbar . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45Menu Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 46HTML Page Editor Toolbar . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 49 Chapter 3 Planning an Application . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51 Planning Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51Planning the Process Map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52 Entry Points . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52User Activities . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53Automated Activities . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53Custom Activities . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53Subprocesses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54Decision Points . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54Parallel Processing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54Exit Points . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55Transitions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55Notifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55Exceptions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56 Planning Assignments . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56 Planning Groups and Roles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57Planning for Monitoring . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58Planning Delegations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58 Determining the Data Requirements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58 File Attachments . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 59 Planning Forms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 59 Planning Access to Forms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 60 Planning Custom Scripts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 60 Planning Searches . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 60 Planning Deployment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 61 4Process Manager Builder’s Guide• May 2000Chapter 4 Creating an Application . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 63 Application Creation Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 64 Getting Information from the Administrator . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 65 Creating a New Application . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 65 The New Application Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 66 Setting Application Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67 The Application Properties Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67 Using Sample Applications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 70 Applications and the Corporate Directory . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 71 Setting Your Corporate Directory . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 72 Deleting an Application . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 73Chapter 5 Designing a Process Map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 75 Drawing the Process Map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 76 Saving a Process Map to a File . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 76 Adding Items with the Palette . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 78 Deleting Items . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 80 Entry Points . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 80 User Activities . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 81 Setting Activity Expirations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 82 Setting Activity Assignments . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 84 Using Parallel Approval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85 Automated Activities . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87 Subprocesses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89 Connecting the Parent and Child Process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 93 Custom Activities . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 93 Using a Custom Activity . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 94 Custom Activity Inspector Window . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 94 Inspector Window After Setting a Custom Activity . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96 Adding a Custom Palette . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 98 Exception Manager . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100 Default Exception Manager . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100 Creating an Exception Manager . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100 Exception Manager Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 101 Decision Points . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 102 Split-Join (Parallel Processing) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 104 Properties of a Parallel Process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 104 Adding a Parallel Process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 104 Notifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 106 Notification Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 106Contents5Built-in Email Notification Scripts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 107 Exit Points . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 107 Transitions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108 Types of Transitions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108Adding a Transition . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109Transition Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 109Example Using a True/False Field . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 110 Chapter 6 Defining Groups and Roles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 113Groups and Roles Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 113 Default Groups and Roles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 115 Creating Groups and Roles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 116 The Create a New Role or Group Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 116The Application Group Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 119The Corporate Group Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 122The Dynamic Group Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 125The Field Role Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 128 Prioritizing Groups and Roles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 129 Deleting Groups and Roles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 130 Chapter7 Defining Data Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 131 Data Field Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 131 Creating a Data Field . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 132 The Create a New Data Field Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 133 Setting Field Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 135 Custom Data Fields with Predefined Class IDs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 136 CheckBox . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 136Computed . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 137Date . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 137DateTime . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 137Digital Signature . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138File Attachment . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138Password . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 141Radio Buttons . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 142Select List . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143TextArea . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143TextField . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 144URL . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 145 6Process Manager Builder’s Guide• May 2000UserPicker Widget . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 146 Custom Data Fields with Your Own Class ID . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 147 Predefined Data Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 147 Address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 147 Name . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 149 Telephone . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 150 Deleting Data Fields . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 151 Setting Up the Content Store . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 151 The Content Store Inspector Window . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 152 Troubleshooting the Content Store . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 153Chapter8 Designing Forms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 155 Planning Forms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 155 Creating Forms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 156 Modifying Forms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 160 Using Process Builder’s Form Editor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 160 Using an External Editor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 160 Using the HTML Page Editor Toolbar . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 161 Using the Edit, Insert and Format Menus . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 162 Using Right-Mouse-Button Menu Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 163 Changing Field Properties for a Form . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 164 Hints for Setting Field Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 165 Accessing the Data Dictionary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 165 Using Scripts to Validate User Input . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 165 Adding a Banner to Forms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 166 Setting Access to Forms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 166 Forms for Assignees . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 168 Forms for Monitoring the Process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 168 Forms for the Administrator . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 168 Setting Access to an Entry Point . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 169Chapter9 Using Scripts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171 Overview of Scripts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171 Kinds of Scripts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 171 When to Use Scripts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173 About Writing Scripts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 174 Predefined Scripts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 174 Assignment Scripts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 174 Completion Scripts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 177Contents7Verification Scripts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 177Email Notification Scripts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 177Initialization and Shutdown Scripts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179 Creating Scripts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 179 The Script Editor Window . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 181Setting a Script as a Template . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 182 Using Client-side Scripts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 183 Chapter10 Deploying an Application . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 187Before You Deploy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 187 Set up and Configure Process Manager . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 188Deploy Subprocesses First . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 188Save the Process Map, If Desired . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 188Fix Application Errors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 188 Steps for Deploying an Application . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 188 The Deploy Application Dialog Box . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 190 Revising a Deployed Application . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 192 Summary of Allowed Revisions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 193Deployed Applications Compared with Local Copies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 195Using a Backup of a Local Application . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 195Saving a Local Application to Another Name . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 195 Redeploying an Application . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 196 Chapter11 Advanced Techniques for Scripting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 197 Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 197 Getting Information about the Current Process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 198 Getting and Setting Data Field Values . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 198Getting Data Field Values in Decision Point and Automation Script Transitions . . . . . . . . . . . . . 200 Getting Information about Users and their Attributes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .200 Finding Users and Accessing their Attributes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .200Modifying User Attributes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 201Adding and Deleting Users . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 202 Accessing the Content Store . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 202 Example of Accessing a Stored Item . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 203Storing Files in the Content Store . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 205 Logging Error and Informational Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 206 Verifying Form Input . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 207 Verifying Form Input with Client-Side JavaScript . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 208Verifying Form Data in Completion Scripts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 212 8Process Manager Builder’s Guide• May 2000。
三星手机内各文件夹的功能和含义.doc

三星手机内各文件夹的功能和含义.doc三星手机内各文件夹的功能和含义1、Android_secure——软件主程序文件夹2、Alirpt——浏览器缓存文件夹3、91caiandar——黄历天气的文件夹4、Beintoo——水果忍者的文件夹5、Cache——高速缓冲存储器6、.deviceidInfo——设备身份信息,安卓智能手机里的deviceidInfo文件指的是:手机设备系统信息7、.dianru——蜻蜓FM收音机的文件夹。
8、.dir_com.qihoo.appstore——是360应用商店程序下载文件夹9、Lenovodata——联想手机恢复出厂设置预置文件10、.LeStore——联想乐商店缓存11、.mediacache——媒体缓存,在'我的电脑'右键'属性'-->'高级'-->'性能'->'高级'-->'虚拟内存'中将所有盘的虚拟内存设置为无分页文件,并选择“设置”后重启系统,就可以删除页面文件pagefile.sys。
就可以变小了,不要直接删除!12、.medieval_software——@WiFi万能钥匙的文件夹13、.privatedata——私人数据14、.UTSystemConfig——天猫的文件夹15、.wk——工作16、.wordeditor——文字编辑器17、——这个文件夹没用的,可以删除,不影响18、Android——安卓系统文件夹19、application_w——系统程序20、audiostat——音频属性21、autonavi——高德导航的文件夹22、autonavidata——高德地图数据的文件夹23、BaiduMapSdk——百度-地图-位置24、Baofeng——暴风影音的文件夹25、Bluetooth——蓝牙26、Books——书籍27、CallMaster——来电通的文件夹28、Camera——照相机;电影摄影机的文件夹29、Data——智能手机里的data是用来存储数据的30、DCIM——数码相机的文件夹。
RBS2001解析
RBS200基站简图 配电屏
电源架
电池组 电池组
A-BIS
PCM
DF
ALARM
RX
TX
RX
TX
RX
光端 TX
TRI
M1
E1
总线扩展 TG0-CELL0
M2
E2
TG1-CELL1
M3
E3
TG2-CELL2
xlx
RBS200原理
TRI-信令 A-BIS
BSC
TRI
LAPD
TG1
TRX TG2
TRX TG3
xlx
A-BIS PCM的时隙分配图(RBS200与RBS2000)
SYNC
TRXC0信令 TS0-3 TS4-7
SYNC
TRXC0信令/DXU信令 TS0-3 TS4-7
TTRRII
TRI信令
TRXC9信令 TS0-3 TS4-7
RBS200时的时隙分配(固定)
TRXC9信令 TS0-3 TS4-7
注:向下是 ON,向上是 OFF。
RTT---一块板对应于一个机架,目前的配置是每小区2个架,共 6个机架,所以共有6块RTT板,RILT-9---M1架、RILT-8---M2架 RILT-7---M3架、RILT-6----E1架、RILT-5----E2、RILT-4---E3架。 且分别对应于连接域上C1C2C3D1D2D3,通过这些接口再接至 每个机架上的B3接口,之后接载波单元。
MOMONITER--MOTRX MONITER;MORRX;MONITER; MORTX MONITER;MOTS MONITER;MOTF MONITER。
MOCONFIG--TRXC RRX RTX TS TF。 MOSIMULATION--TRXC RRX TX TS TF 。 接口标准:RS232---9 针串口 2 接 2、3 接 3,这两条一收一发, 以串行发送,第三条是 5 接 5,公共地线,RBS2000 中的 OMT 的串口线 标准也是 2 接 2,3 接 3,5 接 5。SITE MASTER 使用的串口标准为 2 接 3,3 接 2,5 接 5。
AXE平台介绍

•
•
•
与CP状态相关的指令
DPSWI
DPHAS DPSES DPPA I
交换CP两侧的状态SB-WO EX;EX SB-WO
HALT CP一侧。 分离备用侧。 SB-WO SB-HA; SB-WO SB-SE;
并边,命令SB-HA 或SB-SE侧进行更新。命令
下达后备用侧状态变成SB-UP, 最终CP-A 变成EX,CP-B 变 成SB-WO; DPWSP 查看CP状态;
•
• • • • • •
业务交换功能AM(SSFAM)提供智能业务交换功能;
业务控制功能AM(SCFAM)提供智能业务控制功能; 系统操作和维护AM(SYSOMAM)提供了系统级的操作和维护功能数据接入业务 AM; DASAM IUSAM 在 MSC/VLR里提供包括ISDN业务的主要速率接入和基本速率接入业务,ISDN IUSAM提供了ISDN的用户业务; (SOMAM)完成MSC/VLR里的ISDN应用的操作和维护功能; (DAGAM)为具有INTERNET业务功能的MSC/VLR提供INTERNET的 用户业务AM;
MDS MMS
移动数据子系统 移动交换子系统
MSS SHS DTS NMS OMS
移动性和无线子系统 短消息处理子系统 数据传送子系统 网络管理子系统 操作和维护子系统
AXE的系统结构
APT:交换部分,用来处理所有的电话交换功能。 APZ:控制部分 各自又由许多子系统组成,如:FMS、MCS、 CPS、SUS、TSS、OMS等,而每一子系统又由 若干功能块组成。其中核心部分为选组级GSS, 即交换部分,由TSM和SPM组成T-S-T的结构, 为双面结构。
Mechanical Structer
AliOSThings开发环境搭建

AliOSThings开发环境搭建AliOS Things开发环境搭建1.安装aos环境1.1安装python,pip,gitsudo apt-get install -y python python-pip git1.2检查上述⼯具是否安装完成hanqi@hanqi-PC:~/Desktop$ pip -V && python -V && git --versionpip 9.0.1 from /usr/lib/python2.7/dist-packages (python 2.7)Python 2.7.13git version 2.11.01.3安装依赖库和aos-cubepython -m pip install setuptools wheel aos-cube1.4将aos命令添加到环境变量# 编辑vimvim ~/.bashrc# 在末尾添加export PATH="/home/hanqi/.local/bin/:$PATH"# 更新配置source ~/.bashrc1.5验证hanqi@hanqi-PC:~$ aos -hUsage: aos [OPTIONS] COMMAND [ARGS]...Options:-v, --verbose Verbose diagnostic output-vv, --very-verbose Very verbose diagnostic output--version Show the version and exit.-h, --help Show this message and exit.Commands:check Do code checkcreate Create project or componentdebug Start gdb serverdevices List devices on serial portsinstall Install components or toolslist List components and devicesmake Make aos program/componentmonitor Serial port monitoropen Open an example projectota OTA firmware management toolpack Pack and make a component packageremove Remove the installed component or packageupgrade Upgrade tools and componentsupload Upload aos image2.下载AliOS Things源码2.1Gitee阿⾥源码git clone https:///alios-things/AliOS-Things.git当git完毕之后会在home⽬录下多⼀个AloOS-Things的⽬录,⾥⾯就是AliOS Things源码,其⽬录结构如下hanqi@hanqi-PC:~$ cd AliOS-Things/hanqi@hanqi-PC:~/AliOS-Things$ lsapplication build components core include LICENSE NOTICE platform projects README.md README-zh.md test>3.编译源码3.1进⼊AliOS Things⽬录,清除配置编译hanqi@hanqi-PC:~/AliOS-Things$ aos make distcleanaos-cube version: 0.5.11Cleaning...Done3.2配置内核hanqi@hanqi-PC:~/AliOS-Things$ aos make menuconfig3.2.1配置模板⼯程(以helloworld为例)3.2.2配置⽬标板(以LinuxHost为例)3.3编译⼯程3.3.1开始编译,但报错aos make3.3.2因为缺少某个库⽂件导致报错,安装对应⽂件即可(使⽤了32位指令,电脑是64位的,⽆法直接编译执⾏32位机器指令) sudo apt-get install g++-multilib3.3.3再次编译即可,最终如下Build complete: helloworld_demo@linuxhost3.4执⾏程序编译完成后会⽣成out⽂件夹,在/home/hanqi/AliOS-Things/out/helloworld_demo@linuxhost/binary⽬录下会⽣成可执⾏⽂件,执⾏即可Build complete: helloworld_demo@linuxhosthanqi@hanqi-PC:~/AliOS-Things$ lsaos_config.h application build components core include LICENSE NOTICE out platform projects README.md README-zh.md testhanqi@hanqi-PC:~/AliOS-Things$ cd out/hanqi@hanqi-PC:~/AliOS-Things/out$ lsconfig helloworld_demo@linuxhosthanqi@hanqi-PC:~/AliOS-Things/out$ cd helloworld_demo@linuxhost/hanqi@hanqi-PC:~/AliOS-Things/out/helloworld_demo@linuxhost$ lsaos_all_components.mk auto_component binary config.mk includes libraries moduleshanqi@hanqi-PC:~/AliOS-Things/out/helloworld_demo@linuxhost$ cd binary/hanqi@hanqi-PC:~/AliOS-Things/out/helloworld_demo@linuxhost/binary$ lshelloworld_demo@linuxhost.bin helloworld_demo@linuxhost.map helloworld_demo@linuxhost_ota.bin.xz readme.txt helloworld_demo@linuxhost.elf helloworld_demo@linuxhost_map.csv helloworld_demo@linuxhost.stripped.elf helloworld_demo@linuxhost.hex helloworld_demo@linuxhost_ota.bin link.optshanqi@hanqi-PC:~/AliOS-Things/out/helloworld_demo@linuxhost/binary$ ./helloworld_demo@linuxhost.elfcpu num is 1Welcome to AliOS Thingsnano entry here!hello world! count 0hello world! count 1hello world! count 2hello world! count 3hello world! count 4hello world! count 5hello world! count 6^Chanqi@hanqi-PC:~/AliOS-Things/out/helloworld_demo@linuxhost/binary$。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
New York UniversityA private university in the public serviceSchool of Continuing and Professional Studies Application forThe American Language Institute Certificate of Eligibility 200 (I-20 Form)Room48CooperSquare,New York, NY 10003-7154Telephone: (212) 998-7040Fax: (212) 995-4135Email: ali@Dear International Applicant:Thank you for inquiring about New York University’s American Language Institute. All international students who plan to enrol in our full-time English as a Second Language program must obtain a student (F-1) visa. In order to receive a student (F-1) visa, you must begin by applying for a Certificate of Eligibility (I-20 Form). Please read the enclosed brochure and information before completing the application.To receive a Certificate of Eligibility (I-20 Form), you must submit the following:1) Completed application for Certificate of Eligibility (I-20 Form).2) Copy of passport.3) Affidavit of Support form signed by your financial sponsor.4) Original bank documents preferably in English or accompanied by an authorizedEnglish translation.5) Non-refundable application fee of $150.00. The acceptance material will be sent by express mailservice. Do not send cash or wire transfers. The fee must be in the form of a credit card charge(use the form on the last page), an international money order, a travellers check, or a check from a United States bank. The money order or check should be made payable to “New York University.”Upon receiving your application and original financial documents, an I-20 form will be mailedto you to apply for a student (F-1) visa at the nearest U.S. Embassy or Consulate. To allow forsufficient time to process and mail your admissions material, we advise you to submit your applicationat least six weeks before you wish to begin your studies. Students who are interested in NYU housing should apply at least three months before the beginning of each semester, as space is limited.Academic records are not required for admissions to this program.Please contact us if we can be of any further assistance. We look forward to receiving your completed application.Sincerely,Ms. Mary ChungInternational Student Advisorencl: ApplicationAffidavit of SupportBrochureW YORK UNIVERSITYNEW YORK UNIVERSITYA private university in the public serviceA private university in the public serviceSchool of Continuing and Professional StudiesAMERICAN LANGUAGE INSTITUTE48 Cooper Square, Room 200New York, NY 10003-7154Tel: (212) 998-7040Fax: (212) 995-4135Email: ali@APPLICATION FOR CERTIFICATE OF ELIGIBILITY (I-20 FORM) 20010-11You must enroll in a full-time English as Second Language program in order tomaintain student (F-1) status in the U.S.1. Name of Applicant(ACCORDING TO PASSPORT) Family Name Given Name Middle Name2.Sex: Female Male3. Date of Birth: Month Day Year4. Country of Birth:5. Country of Citizenship:6. Mailing Address (Home/Business): effective until / /7. Permanent Address in Home Country:(No express mail service to PO Box addresses)City State Country Postal Code City State Country Postal CodeAttn: (Name/Company/Agency) Telephone: Student’s E-mail:Telephone: Fax: E-mail:8. When do you wish to enroll? Fall (09/07/10-12/09/10)-Apply before 7/30. Summer Ses. 1 (05/16/11-06/30/11)-Apply before 04/08.Spring (01/18/11-04/28/11)-Apply before 12/14. Summer Ses. 2 (06/27/11-08/11/11)-Apply before 05/13.9. Are you or will you be attending another school in the U.S. before enrolling in the A.L.I.? Yes NoIf you are currently in the U.S. what kind of visa status do you have? ______ Do you want to change this status? Yes NoIf F-1, please list the name of your current school: Dates of attendance to Are you planning to leave the U.S. before beginning at NYU? Yes No If yes, when?10. Would you like to receive a NYU Housing Application? Yes No (Housing applications will be mailed separately)11. Family member or friend to be notified in case of emergency.Name Relation to You Telephone/FaxPLEASE READ THE FOLLOWING STATEMENT AND SIGN WHERE INDICATEDI understand that New York University reserves the right to refuse admission to any applicant who, in the University’s judgement, is not qualified. Similarly, in order to safeguard its ideals of scholarship, character and personal behavior, the University reserves the right to require the withdrawal of any student at any time for any reason deemed sufficient under the rules and practices of the University.I further understand that admission to New York University’s American Language Institute in no way implies admission for academic study for a degree or as a special student to any academic division of NYU. Applicant must be at least 18 years old to be considered for admission.I understand that the I-20 form is to be used only if I intend to enroll in the ALI at NYU. And I agree to pay a cancellation fee if I decide not to attend the American Language Institute at New York University after entering the U.S. with the I-20 form issued by this institution.I certify that the information given in this application is complete and accurate.ofapplicantSignatureDateA non-refundable application fee of US$150.00 must accompany your application. Payment of the fee must be made in the form of an international money order or check drawn from a US bank. Money order/check made payable to “New York University.”We suggest that you arrange for an additional set of original financial documents to be presented to the United States Embassy or Consulate.(PLEASE COMPLETE THE AFFADAVIT ON PAGE 2 →)AFFIDAVIT OF SUPPORT(Required for issuance of I-20 Form)YOU ARE REQUIRED TO CERTIFY THAT FUNDS ARE AVAILABLE FOR THE LENGTH OF YOUR PROGRAM AT NEW YORK UNIVERSITY’S AMERICAN LANGUAGE INSTITUTE, EXCLUSIVE OF TRAVEL EXPENSES. IN COMPUTING YOUR FINANCIAL RESOURCES, YOU SHOULD BEAR IN MIND THAT YOU WILL NOT BE PERMITTED TO WORK. COURSE AND ESTIMATED LIVING EXPENSES ARE LISTED BELOW. TUITION AND ALL RELATED FEES MUST BE PAID AT REGISTRATION.Intensive course at American English and Orientation (X30.9000)Fall 2010: September 7, 2010- December 9, 2010 Summer Ses. 1 2011: June 30, 2011 - July 28, 2011Spring 2011: January 18, 2011- April 28, 2011 Summer Ses. 2 2011: June 27, 2011 – August 11, 2011One TermCourse expenses (Fall or Spring) SummerTuition(Estimate) $4,820 $2,510 (for 6 weeks) | $4,000 (for 12 weeks)Mandatory University Fee 400 250†Hospital Insurance 710 710SCPS Registration Fee 20 20Technology Fee 88 88Books and materials 100 100‡Living expenses 6,000 3,000 (for 6 weeks) | $4,500 (for 12 weeks)Estimated total $12,136 $6,678 (for 6 weeks) | $9,668 (for 12 weeks)All dates and fees are subject to change without notice.†Hospitalization Insurance is required of all students who are not covered by personal/family insurance while in the U.S. The NYU Student Health Insurance Plan covers a minimum of $250,000 for illness and $250,000, for accident/injury for medical and hospital expenses, $15,000 for medical evacuation and $7,500 for repatriation. In addition, this Plan covers pre-exiting conditions as well as in-patient and out-patient mental health treatment. Students must provide proof of comparable personal/family health insurance to be waived from participation in this University Plan. These fees are estimated and are subject to change. ‡ Living expenses are estimated at $1,375.00 per month covering rent, food, transportation – exclusive of travel to/from the U.S., and clothing.Tuition Refund Policy: For withdrawals before 1st class, 100%; before 3rd class, 75%; for withdrawals after the third class, no refund.NYU housing rates from $6,000-11,000 per semester (Fall or Spring). Off-Campus housing is $800-1,200 per month at minimum.If your spouse and/or children will accompany you, please complete the following:(You must provide financial proof of an additional US $500.00 per month for your spouse and US $300.00 per month for each child.)Family Name Given Name Relationship Date of Birth Country of BirthTO BE COMPLETED BY THE APPLICANT’S FINANCIAL SPONSOR Fill in with typewriter or print in block letters in ink.)Please return this Affidavit of Support along with AN ORIGINAL OF ONE of the financial documents listed below:1. Bank Letter or Statement – Should be provided by the sponsor’s bank, indicating the minimum required amount for the desiredlength of study (in U.S. Dollars).2. Employment Letter – Indicates the sponsor’s position and **annual salary on company letterhead stationary. (**The sponsor’sannual salary should be at least 3 times the amount of the course and living expenses listed above.) If the sponsor is self-employed, a personal bank statement it required.)I hereby certify that I am able, willing and do promise to support my: (please check one)Daughter SelfSon EmployeeOther Student’s Name (Please include family and given name)with a minimum of $ _____________ $12,136 (Fall or Spring Term- 14 weeks)$6,678 (Summer Term-6 weeks) $9,668 (Summer Term-12 weeks)for his/her tuition, fees and living expenses at New York University’s American Language Institute/School of Continuing Education.I understand that the cost of study at New York University’s American Language Institute//School of Continuing Education includes the cost of tuition and estimated room, board and miscellaneous expenses. It does not include transportation to and from the US.Financial Sponsor’s Signature Print Name Email(Address)New York UniversityA private university in the public serviceSchool of Continuing and Professional StudiesThe American Language InstituteRoom200Square,Cooper48New York, NY 10003-7154Telephone: (212) 998-7040Fax: (212) 995-4135Email: ali@Charge Card Payment Authorization for ALI Application Fee Student’s Name: _______________________________________I authorize New York University to charge my credit card for the $150 ALI application fee. I understand that this fee is nonrefundable.Please type or print clearlyCredit card type (PLEASE CHECK ONE):□ Visa □ MasterCard □ American Express □ DiscoverCredit Card No.: _______________________________________________Expiration Date: Month _________ / Year___________Verification/Security Code: ______________Cardholder’s Name: ____________________________________________(As it appears on the credit card)Billing Address: ______________________________________________________________________________________________Email: _________________________ Telephone: ___________________Cardholder’s Signature: ________________________ Date: __________。
