CISSP笔记
信息系统项目管理师考试笔记重点难点

信息系统工程治理师考试笔记重点难点1.计算机根本构成:运算器、操纵器、存储器、输入设备、输出设备。
2.并行性是指计算机系统具有能够同时进展运算或者操作的特性,包含同时性与并发性。
3.根本思想:时间重叠、资源重叠、资源共享。
4.传统串行方式:优:操纵简洁,节约设备缺:执行指令速度慢,功能部件利用率低。
5.流水线处理机:优:程序执行时间短,功能部件利用率高缺:增加硬件,操纵过程较简单。
6.并行处理机SIMD 一个操纵器CU,N 个处理单元PE,一个互连网络IN 。
7.并行处理机要紧特点:⑴ 单指令流多数据流方式工作。
⑵ 使用资源重复方法引入空间因素。
⑶ 以某一类算法为背景的专用计算机。
⑷ 并行处理机的争论务必与并行算法争论亲热结合。
⑸ 异构型多处理系统。
8.多处理机系统构成MIMD:N个处理机+1个处理机存储器互联网络〔PMIN〕。
9.多处理机系统特点:⑴ 构造敏捷并行处理机处理单元很多;多处理机有较强通用性,适用多样算法,处理单元数量较少。
⑵ 程序并行性并行处理。
11.RISC与CISC 比较要紧特点如下:⑴ 指令数目较少,通常选用使用频度最高的一些简洁指令。
⑵ 指令长度固定,指令格式种类少,寻址方式种类少。
⑶ 大多数指令可在一个机器周期内完成。
⑷ 通用存放器数量多,只有存数/取数指令访问存储器,其余指令无关存放器之间进展操作。
两者要紧区分在于设计思想上。
12.存储系统分类:高速缓冲存储器〔Cache,双极半导体〕主存储器〔MOS 半导休,又称内存储器,包含高速缓存与主存〕关心存储器。
13.存储器的层次:高速缓存-主存,主存-辅存。
14.主存的根本构成:双极型 MOS 型〔由存储体、地址译码器、驱动器、I/O 操纵、片选操纵、读/写操纵〕。
15.存储器的要紧技术指标:存储容量、存取速度〔访问时间、存储周期 TM〕TM>TA、读出时间 TM>TW、写入时间、牢靠性、MTBF 平均故障间隔时间。
CISSP知识点汇总(更新至近4000条)

Division B
Division A
The Red Book
ITSEC 信息技术安全评估 准则
CTCPEC FC
Common Criteria
通用准则Common Criteria 国 际标准,从功能和保证角度来评 估构建进入系统的安全控制的有
EAL1 EAL2 EAL3 EAL4 EAL5 EAL6 EAL7 Certification 认证 Accreditltiprogramming 多程序 Multitasking 多任务 Multithreading 多线程
Multiprocessing 多处理器
process isolation 进程隔离 操作系统提供的保护机制。提 供封装、共享资源时分多用、 命名区分、虚拟存储器映射。
内存管理的目标
3 The Biba Model
4 The Clark-Wilson Model
三元组:主体、软件TP、客 体
5 Access Control Matrix 6 The Information Flow Model 信息流模型 这种模型限制在自己的流中,信 息以不违背安全策略的方式流入 或流出实体
引用监视器(Reference Monitor): RM的功能是根据访问控制数据库的定义,对抽象系统中所有使用者对目标的访问进行控制。
安全内核(Security Kernel):安全内核由TCB的硬件、软件和固件部分加上引用监视器所构成, 我们可以这样来区分安全内核和引用监视器:引用监视器和安全内核的功能是相同的, 但引用监视器是执行访问控制功能的抽象模型,而安全内核则是使用在各种系统中的具体实现。 1.提供隔离 2.完整可靠 3.足够小,可验证 引用监视器RM是概念,抽象的机器,协调所有主机对对象间的访问;安全内核是硬件,是TCB中执行RM的部分,TCB中除安全内核外还有其他安全机
cissp读书笔记系列

cissp读书笔记系列【篇一:cissp aio读书笔记02@gaoyan】cissp aio(第五版)读书笔记第1、2章多为了解知识点,读者了解即可,出考题几率很小。
第三章信息安全与风险管理1、安全管理包括风险管理、信息安全策略、措施、标准、指导原则、基准、信息分类、安全组织和安全教育。
2、安全管理的功能包括确定目标、范围、策略、优先级和战略。
管理层的职责是为其负责的资源和整个公司提供保护。
这些资源的形式包括人力、资本、硬件与信息。
3、制订安全计划应该使用自顶向下的方式。
启动、支持和指导来自最高管理层,该计划向下到达中级管理层,然后再到普通职员。
无论采用何种形式,安全管理者都需要清晰的报告结构、对职责的理解以及测试和监控功能,以便保证不会由于缺少交流而导致计划流产。
4、为了实现管理层的安全指标,应当利用:行政管理性控制、技术性控制、物理性控制。
5、行政管理性控制包括:开发和发布策略、标准、措施和指导原则;风险管理;人员的筛查;指导安全意识培训;实现变更控制措施。
6、技术性控制(也称为逻辑性控制)包括:实现和维护访问控制机制;密码和资源管理;身份标识和身份验证方法;安全设备;基础设施的配置。
7、物理性控制包括:控制个人对设施和不同部门的访问;锁定系统;去除不必要的软驱和光驱;保护设施的周边;检测入侵;环境控制。
8、安全规划可以分为3个不同的领域:战略规划、战术规划和操作规划。
战略规划可能包含以下目标:◆确保风险被正确理解并得到合理解决;◆保证遵守法律法规;◆使整个组织机构的安全责任一体化;◆建立一个成熟的模型,从而实现持续的完善;◆将安全作为一项业务成就,以吸引更多的客户。
操作规划示例:◆执行安全风险评估;◆不允许执行降低生产能力的安全变更;◆维护和实现控制;◆长期扫描脆弱性并提供补丁程序;◆跟踪策略遵守情况。
9、cobit分为4个领域:计划与组织、获取与实现、交付与支持、监控与评估。
cobit的组件包括:执行摘要、管理指导原则、架构、控制目标、实现工具集以及审计指导原则。
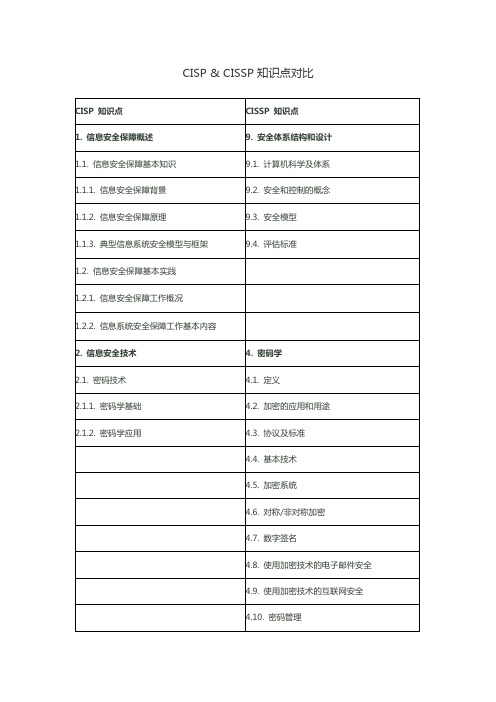
CISP & CISSP 知识点对比
4.7. 数字签名
4.8. 使用加密技术的电子邮件安全
4.9. 使用加密技术的互联网安全
4.10. 密码管理
4.11. PKI
4.12. 密码分析和攻击
4.13. 输出问题
2.2. 访问控制与审计监控
1. 访问控制
2.2.1. 访问控制模型
1.1. 授权和认证
2.2.2. 访问控制技术
CISP & CISSP 知识点对比
CISP 知识点
CISSP 知识点
1. 信息安全保障概述
9. 安全体系结构和设计
1.1. 信息安全保障基本知识
9.1. 计算机科学及体系
1.1.1. 信息安全保障背景
9.2. 安全和控制的概念
1.1.2. 信息安全保障原理
9.3. 安全模型
1.1.3. 典型信息系统安全模型与框架
9.4. 评估标准
1.2. 信息安全保障基本实践
1.2.1. 信息安全保障工作概况
1.2.2. 信息系统安全保障工作基本内容
2. 信息安全技术
4. 密码学
2.1. 密码技术
4.1. 定义
2.1.1. 密码学基础
4.2. 加密的应用和用途
2.1.2. 密码学应用
4.3. 协议及标准
4.4. 基本技术
4.5. 加密系统
3.3.1. 基本安全管理措施
3.8. 预防措施
3.3.2. 重要安全管理过程
5.信息安全治理和风险管理
5.2风险管理工具和实
5.3规划和组织
4. 信息安全工程
4.1. 信息安全工程原理
4.1.1. 安全工程理论背景
4.1.2. 安全工程能力成熟度模型
CISSP复习笔记(可打印修改)

1.安全管理基础概念1.标识组织的所有信息资产2.分析安全风险3.定义安全的重要性,随时有警觉的心4.对安全管理有实施的计划2. 安全所要具备的要素1、CIAC 机密性避免资产被未经过授权的人存取包括授权的和非授权的A 可用性及时而稳定的获取资源I 完整性避免未经授权的人做修改和经授权的人做未经允许的修改3.IT安全需要1.功能面(防火墙的功能就是过滤)2.确保功能可以达到(通过Log file也确定是否正确)3.首先定义安全策略()4.安全考量1.技术面2.组织架构3.公司文化4.管理5.业务运营6.风险5.安全政策成功因素1.最重要的是高层主管支持2.与工作相融合不能有冲突的部分3.思考以下部分(业务流程、技术流程呢个、管理流程)4.具体的实现(隐私权()、身份管理(对主管进行调查确信可信任)、应用程序、基础架构、管理)6.安全问题解决思考1.不同的需求都考虑在范围内2.ERP->VPN->CRM(客户关系管理)->ERP3.必须要求一致性7.实施安全政策1.软硬件配置标准(例如防毒、防火墙)2.变更(例如文件的销毁,用户的注册等等)3.基线(最小的安全等级和一致性、例如windows 2003必须打哪些补丁)以上三个都有强制性4.可有可无的标准(TCSEC和ITSEC规划等等他们的差别是TCSEC主要是系统、ITSEC 加入网络)8.如何做好安全管理1.定义角色和责任1.一起定义角色和责任(最高层主管、信息安全专家、owners(拥有者)、管理员、用户)2.雇佣人员事要注意(验证员工的工作履历、验证员工学历、签署合约、对高层进行背景调查)3.离职慎重处理(有两种情况第一个是自愿离职可以给一定缓冲时间、第二个是公司开除不要留任何缓冲时间)4.工作方面的事项(重要的工作项目要分工(避免私下串通)、定期工作轮换(舞弊的安全问题)、强制性休假)5.确保公司一定程度的安全(内部和外部的审计、高层做不定期的抽查以及安全措施和改进的地方、渗透测试、安全意识宣传(让公司了解安全重要)、技能培训、更深入的培训(让他们知道什么是密码学))2. 分级制度1.重要性(标识重要资产、等级高的进行保护、增加企业的优势、保护法律诉讼文件、根据等级来进行优先恢复减小公司损失)2.方向(公务类别、竞争对手有关的类别、公司财务有关的类别)3.谁来实施分级(拥有者来进行分级:足够的知识、要了解法律要求、讲求一直性、分级标准定义、加密和解密还有过期性(销毁程序等))4.注意事项(贴上警告标签、定期严查重要的资料例如备份、资料删除的时候要注意是否被彻底删除干净、遵循适当的删除策略)3.风险管理和分析1.风险管理目的(找出威胁来源,让风险做到可以接受的)2.风险如何形成(威胁和弱点共同存在)例如公司没有安装防火墙就属于公司的弱点,网络上的黑客就是对公司的威胁,如果黑客利用公司的弱点进行攻击成功,那么就有一个风险3.风险分析重要性(在企业内部标识风险,及时做好防御措施、考虑法律法规)4.新的威胁的产生(新的技术、文化的改变、新产品的出现)5.成功关键要素(1.高层主管的支持、2.成立风险评估小组、3.寻找人员加入小组)6.公司现有状况可以做到的程度7.风险分析类型(定量(数字化)、定性(情景以高中低来进行划分))CISSP复习笔记-第2章信息安全治理与风险管理2.1 安全基本原则2.1.1可用性(availability)∙确保授权的用户能够对数据和资源进行及时的和可靠的访问∙措施:回滚、故障切换配置∙反面:破坏(destruction)2.1.2 完整性(integrity)∙保证信息和系统的准确性和可靠性,并禁止对数据的非授权更改∙措施:配置管理(系统完整性)、变更控制(进程完整性)、访问控制(物理的和技术的)∙反面:篡改(alteration)2.1.3 机密性(confidentiality)∙确保在数据处理的每一个交叉点上都实施了必要级别的安全保护并阻止未经授权的信息披露∙措施:访问控制(物理的和技术的)∙反面:披露(disclosure)∙肩窥(shoulder surfing),社会工程(social engineering)2.2 安全定义∙脆弱性(vulnerability):缺少安全措施或采用的安全措施有缺陷∙威胁(threat):利用脆弱性带来的潜在危险∙风险(risk):威胁主体利用脆弱性的可能性以及相应的业务影响∙暴露(exposure):造成损失的实例∙控制(control)或对策(countermeasure):消除或降低潜在的风险2.3 控制类型∙按类型分:管理控制(软控制)、技术控制(逻辑控制)、物理控制∙按功能分o威慑性(deterent):威慑潜在攻击者o预防性(preventive):避免意外事件的发生o纠正性(corrective):意外事件发生后修补组件或系统,例如计算机映像o恢复性(recovery):使环境恢复到正常的操作状态,例如数据备份o检测性(detective):帮助识别以外活动和潜在入侵者o补偿性(compensating):提供可替代的控制方法2.4 安全框架2.4.1 ISO/IEC 27000系列∙组织安全规划的必要组成部分∙英国标准7799(British Standard 7799,BS7799)∙信息安全管理体系(Information Security Management System,ISMS)∙ISO/IEC 27000:世界上从全盘考虑的安全控制管理的最佳行业实践o戴明环:计划-执行-检查-处理,Plan-Do-Check-Action,PDCA2.4.2 企业架构框架∙汇总安全规划中所列出的要求,并将之集成到公司现有业务结构中2. Zachman框架∙John Zachman开发,用于定义和理解商业环境∙二维模型o横向为5W1H:什么(数据)、如何(功能)、哪里(网络)、谁(人)、何时(时间)、为何(动机)o纵向为不同的视角:计划人员、所有者、设计人员、建设人员、实施人员、工作人员3. 开放群组架构框架(The Open Group Architecture Framework,TOGAF)∙开放群组(Open Group)开发,用于定义和理解商业环境∙业务架构、数据架构、应用程序架构、技术架构4. 面向军事的架构框架∙美国国防部架构框架(Department of Defense Architecture Framework,DoDAF)∙英国国防部架构框架(British Ministry of Defense ArchitectureFramework,MoDAF)5. 企业安全架构∙舍伍德的商业应用安全架构(Sherwood Applied Business SecurityArchitecture,SABSA):风险驱动的企业安全架构,将安全映射到商业计划,与Zachman框架相似∙满足服务水平协议(Service Level Agreement,SLA)2.4.3 安全控制开发∙关注要落实到位的控制目标,以达成安全规划和企业架构所列出的目标∙信息及相关技术的控制目标(Control Objectives for Information and related Technology,CobiT):一组控制目标集,用来作为IT治理的框架,由ISACA和ITGI开发,分成4个领域o计划和组织(plan and organize)o获得与实现(acquire and implement)o交付与支持(deliver and support)o监控与评价(monitor)∙SP 800-53:由NIST开发的用于保障美国联邦系统安全的控制集2.4.4 COSO框架∙发起组织委员会(Committee Of Sponsoring Organizations)1985年开发,用来处理财务欺诈活动并汇报,应对萨班斯-奥克斯利法案(Sarbanes-Oxley Act,SOX)2.4.5 流程管理开发∙安全控制是工具,流程是如何使用这些工具∙信息技术基础设施库(Information Technology Infrastructure Library,ITIL):IT服务管理的最佳实践的事实标准∙六西格玛:摩托罗拉开发,目标是在生产过程中识别和消除缺陷∙能力成熟度模型集成(Capability Maturity Model Integration)2.7 风险评估和分析2.7.6 定量(Quantitative)分析∙自动风险分析:减少风险分析任务的手动难度,进行快速计算∙单一损失期望(Single Loss Expectany,SLE)∙暴露因子(Exposure Factor,EF)∙资产价值×EF=SLE∙年发生比率(Annualized Rate of Occurrence)∙年度损失期望(Annual Loss Expectancy)∙SLE×ARO=ALE∙因为数据本身多少会有一些主观性,因此无法做到完全客观∙不确定性:对估计缺乏信心的程度2.7.7 定性(Qualitative)分析∙Delphi技术:匿名投票∙定性和定量的目标都是评估公司面临的实际风险并给出威胁的严重程度等级(severity level),注意与定性分析给出的风险评级区分开2.7.8 保护机制∙实现防护措施前的ALE - 实现防护措施后的ALE - 防护措施每年的成本= 防护措施对公司的价值2.7.10 总风险与剩余风险∙威胁×脆弱性×资产价值=总风险∙总风险×控制间隙=剩余风险∙总风险-对策=剩余风险2.7.11 处理风险∙转移:买保险∙规避:终止引入风险的活动∙缓解:把风险降低至可接受的级别∙接受2.8 策略、标准、基准、指南和流程∙策略:高级管理层(或是选定的董事会和委员会)制定的一个全面声明,它规定安全在组织机构内所扮演的角色,分规章性策略、建议性策略、指示性策略∙标准:强制性的活动、动作或规则,可以为策略提供方向上的支持和实施∙基准:所需要的最低保护级别∙指南:没有应用特定标准时向用户、IT人员、运营人员及其他人员提供的建议性动作和操作指导∙流程:为达到特定目标而应当执行的详细的、分步骤的任务2.9 信息分类∙商业公司:机密(confidential)、隐私(private)、敏感(sensitive)、公开(public)∙军事机构:绝密(top secret)、秘密(secret)、机密(confidential)、敏感但未分类(Sensitive But Unclassified,SBU)、未分类(unclassified)2.11 安全指导委员会2.11.2 数据所有者∙对特定信息的子集和应用负最终责任2.11.3 数据看管员∙负责数据的保护与维护工作2.11.17 人员安全∙职责分离:预防性管理措施∙岗位轮换:检测性管理措施∙强制休假:检测性管理措施CISSP复习笔记-第2章信息安全治理与风险管理2.1 安全基本原则2.1.1可用性(availability)∙确保授权的用户能够对数据和资源进行及时的和可靠的访问∙措施:回滚、故障切换配置∙反面:破坏(destruction)2.1.2 完整性(integrity)∙保证信息和系统的准确性和可靠性,并禁止对数据的非授权更改∙措施:配置管理(系统完整性)、变更控制(进程完整性)、访问控制(物理的和技术的)∙反面:篡改(alteration)2.1.3 机密性(confidentiality)∙确保在数据处理的每一个交叉点上都实施了必要级别的安全保护并阻止未经授权的信息披露∙措施:访问控制(物理的和技术的)∙反面:披露(disclosure)∙肩窥(shoulder surfing),社会工程(social engineering)2.2 安全定义∙脆弱性(vulnerability):缺少安全措施或采用的安全措施有缺陷∙威胁(threat):利用脆弱性带来的潜在危险∙风险(risk):威胁主体利用脆弱性的可能性以及相应的业务影响∙暴露(exposure):造成损失的实例∙控制(control)或对策(countermeasure):消除或降低潜在的风险2.3 控制类型∙按类型分:管理控制(软控制)、技术控制(逻辑控制)、物理控制∙按功能分o威慑性(deterent):威慑潜在攻击者o预防性(preventive):避免意外事件的发生o纠正性(corrective):意外事件发生后修补组件或系统,例如计算机映像o恢复性(recovery):使环境恢复到正常的操作状态,例如数据备份o检测性(detective):帮助识别以外活动和潜在入侵者o补偿性(compensating):提供可替代的控制方法2.4 安全框架2.4.1 ISO/IEC 27000系列∙组织安全规划的必要组成部分∙英国标准7799(British Standard 7799,BS7799)∙信息安全管理体系(Information Security Management System,ISMS)∙ISO/IEC 27000:世界上从全盘考虑的安全控制管理的最佳行业实践o戴明环:计划-执行-检查-处理,Plan-Do-Check-Action,PDCA2.4.2 企业架构框架∙汇总安全规划中所列出的要求,并将之集成到公司现有业务结构中2. Zachman框架∙John Zachman开发,用于定义和理解商业环境∙二维模型o横向为5W1H:什么(数据)、如何(功能)、哪里(网络)、谁(人)、何时(时间)、为何(动机)o纵向为不同的视角:计划人员、所有者、设计人员、建设人员、实施人员、工作人员3. 开放群组架构框架(The Open Group Architecture Framework,TOGAF)∙开放群组(Open Group)开发,用于定义和理解商业环境∙业务架构、数据架构、应用程序架构、技术架构4. 面向军事的架构框架∙美国国防部架构框架(Department of Defense Architecture Framework,DoDAF)∙英国国防部架构框架(British Ministry of Defense ArchitectureFramework,MoDAF)5. 企业安全架构∙舍伍德的商业应用安全架构(Sherwood Applied Business SecurityArchitecture,SABSA):风险驱动的企业安全架构,将安全映射到商业计划,与Zachman框架相似∙满足服务水平协议(Service Level Agreement,SLA)2.4.3 安全控制开发∙关注要落实到位的控制目标,以达成安全规划和企业架构所列出的目标∙信息及相关技术的控制目标(Control Objectives for Information and related Technology,CobiT):一组控制目标集,用来作为IT治理的框架,由ISACA和ITGI开发,分成4个领域o计划和组织(plan and organize)o获得与实现(acquire and implement)o交付与支持(deliver and support)o监控与评价(monitor)∙SP 800-53:由NIST开发的用于保障美国联邦系统安全的控制集2.4.4 COSO框架∙发起组织委员会(Committee Of Sponsoring Organizations)1985年开发,用来处理财务欺诈活动并汇报,应对萨班斯-奥克斯利法案(Sarbanes-Oxley Act,SOX)2.4.5 流程管理开发∙安全控制是工具,流程是如何使用这些工具∙信息技术基础设施库(Information Technology Infrastructure Library,ITIL):IT服务管理的最佳实践的事实标准∙六西格玛:摩托罗拉开发,目标是在生产过程中识别和消除缺陷∙能力成熟度模型集成(Capability Maturity Model Integration)2.7 风险评估和分析2.7.6 定量(Quantitative)分析∙自动风险分析:减少风险分析任务的手动难度,进行快速计算∙单一损失期望(Single Loss Expectany,SLE)∙暴露因子(Exposure Factor,EF)∙资产价值×EF=SLE∙年发生比率(Annualized Rate of Occurrence)∙年度损失期望(Annual Loss Expectancy)∙SLE×ARO=ALE∙因为数据本身多少会有一些主观性,因此无法做到完全客观∙不确定性:对估计缺乏信心的程度2.7.7 定性(Qualitative)分析∙Delphi技术:匿名投票∙定性和定量的目标都是评估公司面临的实际风险并给出威胁的严重程度等级(severity level),注意与定性分析给出的风险评级区分开2.7.8 保护机制∙实现防护措施前的ALE - 实现防护措施后的ALE - 防护措施每年的成本= 防护措施对公司的价值2.7.10 总风险与剩余风险∙威胁×脆弱性×资产价值=总风险∙总风险×控制间隙=剩余风险∙总风险-对策=剩余风险2.7.11 处理风险∙转移:买保险∙规避:终止引入风险的活动∙缓解:把风险降低至可接受的级别∙接受2.8 策略、标准、基准、指南和流程∙策略:高级管理层(或是选定的董事会和委员会)制定的一个全面声明,它规定安全在组织机构内所扮演的角色,分规章性策略、建议性策略、指示性策略∙标准:强制性的活动、动作或规则,可以为策略提供方向上的支持和实施∙基准:所需要的最低保护级别∙指南:没有应用特定标准时向用户、IT人员、运营人员及其他人员提供的建议性动作和操作指导∙流程:为达到特定目标而应当执行的详细的、分步骤的任务2.9 信息分类∙商业公司:机密(confidential)、隐私(private)、敏感(sensitive)、公开(public)∙军事机构:绝密(top secret)、秘密(secret)、机密(confidential)、敏感但未分类(Sensitive But Unclassified,SBU)、未分类(unclassified)2.11 安全指导委员会2.11.2 数据所有者∙对特定信息的子集和应用负最终责任2.11.3 数据看管员∙负责数据的保护与维护工作2.11.17 人员安全∙职责分离:预防性管理措施∙岗位轮换:检测性管理措施∙强制休假:检测性管理措施CISSP复习笔记-第3章访问控制3.1 访问控制概述∙主体:用户、程序、进程∙客体:计算机、数据库、文件、目录、窗口、打印队列、接口、设备(一般不将程序或进程视为客体)3.3 身份标识、身份验证、授权与可问责性∙确保可问责性的唯一方法是主体能够被唯一标识,并且主体的动作被记录在案3.3.1 身份标识与身份验证∙三种因素可用于身份验证o某人知道的内容:密码、PIN、认知密码、图形验证码o某人所拥有的物品:钥匙、证件、tokeno某人的身份:基于物理特征,生物测定学(biometrics)∙强(双因素)身份验证:至少包含三种因素中的二种∙安全身份o唯一性:每个用户必须具有用于问责的唯一IDo非描述性:任何凭证都不应当表明账户的目的o签发:上述元素由权威机构提供,用于证明身份∙一对一:验证/认证(verification/authentication),一对多:识别(identification)身份管理(Identity Manageme,IdM)∙目录o基于X.500标准和某种协议,例如轻量级目录访问协议(Lightweight Directory Access Protocol,LDAP)o Windows环境会登入域控制器(Domain Controller,DC),它的数据库中运行一个层次化的活动目录服务(Active Directory,AD)o问题:由于不是使用必要的客户端软件创建,因此无法管理许多遗留设备和应用程序∙目录在身份管理中的角色o所有资源信息、用户属性、授权资料、角色、潜在的访问控制策略及其他内容都存储在目录中o元目录:从不同的来源收集必要信息并将它们保存在一个中央目录内,需要定期与身份存储库同步o虚拟目录:与元目录相似,可以替代元目录,虚拟目录中没有数据,只是只想驻留实际数据的位置∙Web访问管理(Web Access Management,WAM)o用户与基于Web的企业资源之间的主要网关o通常WAM工具还提供单点登录功能3.3.2 密码管理∙密码同步∙自助式密码重设∙辅助式密码重设∙遗留单点登录∙账户管理∙用户指配(user provisioning):为响应业务过程而创建、维护、删除存在于一个或多个系统、目录、应用程序中的用户对象与属性∙用户资料更新∙联合身份(federated identity):以在两个或多个地点链接一名用户的独特身份为基础,因而不需要同步或合并目录信息,是公司和客户能更加方便地访问分布式资源1. 访问控制和标记语言∙服务供应标记语言(Service Provisioning Markup Language,SPML):允许驻留在一个组织或者多个组织上的应用程序之间交换供应数据,允许用户算理,允许位于不同平台上的服务供应集成和互操作∙可拓展访问控制标记语言(Extensible Access Control Markup Language,XACML):用来向Web服务和其他企业应用程序提供的资产表述安全策略和访问权限2. 生物测定学∙误拒率(False Rejection Rate,FRR):1类错误,误报率∙误受率(False Acceptance Rate,FAR):2类错误,漏报率∙交叉错误率(Crossover Error Rate):FRR=FAR,也称相等错误率(Equal Error Rate)∙指纹:曲线、分叉、微小特征∙手掌扫描:沟槽、脊状突起、折缝∙手部外形:手掌和手指的长度、宽度、外形∙视网膜扫描:眼球后方视网膜上血管的图案,类似测眼压,用户体验最差∙虹膜扫描:图案、分叉、颜色、环状、光环、皱纹,光学部件必须放置于合适的位置,以保证阳光没有照入光圈中∙动态签名:签名过程中引起的物理移动转换成电信号∙动态击键:输入具体短语时产生的电信号∙声纹:不同人语音模式存在的微小差别∙面部扫描:骨骼结构、鼻梁、眼眶、额头、下颚形状∙手形拓扑:整个手形及其弯曲部分的不同起伏形状3. 密码∙限幅级别(clipping level):登陆失败次数的上限5. 一次性密码(One-Time Passwd,OTP)∙同步令牌:基于时间或计数器,令牌和身份验证服务器必须共享用于加密和解密的相同安全密钥∙异步令牌:基于挑战/响应机制8. 存储卡∙门禁卡,磁条卡9. 智能卡∙本身包含微处理器和集成电路∙接触式:银行卡;非接触式:公交卡∙不容易被复制、篡改3.3.3 授权1. 访问准则∙基于组、基于物理或逻辑位置、基于时间段或时间间隔、基于事务5. Kerberos∙一个身份验证协议∙20世纪80年代中期作为MIT的“Athena”项目的一部分设计出来∙Windows 2000及以上操作系统的默认身份验证方法∙分布式环境中单点登录的一个示例,异构网络的一个实际标准∙使用对称密码学∙容易遭受密码猜测攻击∙主要组件o密钥分发中心(Key Distribution Center,KDC):保存了所有用户和服务的秘密密钥,Kerberos环境内最重要的组件,提供身份验证服务以及密钥分发功能o委托人(Principal):KDC为每个委托人提供一个账户,并与之共享一个秘密密钥,可以是用户、应用程序或网络服务o票证授予服务(Ticket Granting Service,TGS):发放服务票证(Service Ticket,ST)o身份验证服务(AuthenticationService,AS):发放票证授予票证(Ticket Granting Ticket,TGT)o域(Realm):在一个域内KDC对于所有用户、应用程序和网络服务来说都是可信任的身份验证服务器∙身份验证过程:参考16. SESAME(Secure European System for Application in a Multi-vendor Environment)∙使用对称和非对称密钥∙目的是拓展Kerberos的功能和弥补它的缺陷3.4 访问控制模型3.4.1 自主访问控制(Discretionary Access Control,DAC)∙资源的所有者能够指定哪些主体能够访问该资源∙身份型∙最常用方法:访问控制列表(Access Control List,ACL)∙大多数操作系统基于DAC模型∙反面:非自主访问控制(Non-discretionary Access Control,NDAC),通过中央授权来决定哪些主体可以访问对应的客体3.4.2 强制访问控制(Mandatory Access Control,MAC)∙安全标签:也称敏感度标签,绑定在主体和客体上o分类:遵循层次化结构,如秘密、绝密、机密等o类别:与部门或项目等对应起来∙系统接收到一个队客体的访问请求时,根据你主体的安全许可、客体的分类以及操作系统的安全策略做出决策,主体安全许可必须大于等于客体的分类3.4.3 角色型访问控制(Role-Based Access Control,RBAC)∙集中管理的控制方式∙雇员流动性高的公司最适合使用的访问控制系统∙非自主访问控制的一种3.5 访问控制技术和方法∙规则型访问控制(rule-based access control):不一定是身份型的∙限制性用户接口:数据库视图,只在键盘上提供某些键∙访问控制矩阵(access control matrix)o功能表:特定主体对所有客体的访问权限,矩阵中的行o访问控制列表:所有主体对特定客体的访问权限,矩阵中的列3.6 访问控制管理3.6.1 集中式访问控制管理∙AAA:Authentication,Authorization,Audit∙密码身份验证协议(Password Authentication Protocol,PAP)∙挑战握手身份验证协议(Challenge Handshake Authentication Protocol,CHAP)∙可拓展身份验证协议(Extensible Authentication Protocol,EAP)∙远程身份验证拨号用户服务(Remote Authentication Dial-In UserService,RADIUS)∙终端访问控制器访问控制系统(Terminal Access Controller Access Control System,TACACS)o TACACS:身份验证和授权过程组合在一起o拓展TACACS(Extended TACACS,XTACACS):身份验证、授权和审计过程分开o TACACS+:采用拓展双因素用户身份验证的XTACACS∙Diameter:解决漫游、移动IP、PPP以太网、VoIP及传统AAA协议无法跟上的其他技术3.9 访问控制实践∙客体重用:将先前包含一个或多个客体的介质重新分配给主体,介质要先擦除、消磁∙发射安全:阻止入侵者通过侦听设备从电磁波中获取信息,例如TEMPEST技术3.10 访问控制监控3.10.1 入侵检测系统(Intrusion Detection System,IDS)∙网络型IDS(Network-based IDS,NIDS)∙主机型IDS(Host-based IDS,HIDS)∙特征型IDS:模式匹配,状态匹配∙异常型IDS:统计异常型,协议异常型,流量异常型,规则型3.11 对访问控制的几种威胁∙字典攻击∙蛮力攻击o战争拨号(wardialing):使用大量电话号码,以试图找到一个调制解调器来获得未授权访问∙登陆欺骗∙网络钓鱼o网址嫁接(pharming):实施DNS中毒(DNS poisoning)攻击,将受害者重定向至一个看似合法的、其实是伪造的Web站点o鱼叉:专门针对特定人的钓鱼CISSP复习笔记-第4章安全架构和设计4.2 系统架构∙ISO/IEC 42010:2007:IEEE推荐的软件密集型系统架构描述4.3 计算机架构4.3.1 中央处理单元(Central Processing Unit,CPU)∙算术逻辑单元(Arithmetic Logic Unit,ALU)∙控制单元∙通用寄存器:用于保存变量和临时结果∙特殊寄存器o程序计数器o栈指针o程序状态字(Program Status Word,PSW):保存各种不同的条件位,其中一个条件位指出CPU应在用户模式(问题状态),还是在特权模式(内核模式(kernel mode)或监管模式(supervisor mode))工作∙地址总线(address bus):CPU通过地址总线与RAM和其他I/O设备建立连接∙数据总线(data bus):读/写的数据被放在数据总线上4.3.2 多重处理∙多核CPU的对称模式和非对称模式4.3.3 操作系统架构1. 进程管理∙协调式多任务处理(cooperative multitasking):要求处理器自愿地释放所使用的资源∙抢占式多任务处理(preemptive multitasking):操作系统能否控制进程使用某一资源的时间∙进程:拥有各自的存储器空间、栈和程序计数器∙中断:进程通过中断知道何时能与CPU通信∙可屏蔽中断(maskable interrupt):分配给不是十分重要的事件,程序可以选择是否忽略∙不可屏蔽中断(non-maskable interrupt):程序无法忽略2. 线程管理∙线程:当进程有具体活动需要操作系统执行时而生成的指令集3. 进程调度∙死锁:两个进程互相需要对方当前占用的资源才能完成任务4. 进程活动∙采用以下方法可以实施进程隔离o对象封装:APIo共享资源的时分复用o命名区分:PIDo虚拟地址空间映射(virtual address space mapping)5. 存储器管理∙CPU寄存器>高速缓存器>主存储器>(交换空间>)磁盘存储∙基寄存器(base register)和界限寄存器(limit register)确定进程地址空间4.3.4 存储器类型1. 随机存取存储器(Random Access Memory,RAM)∙动态RAM(Dynamic RAM,DRAM):使用电容和晶体管,电容中的数据必须不断进行动态刷新,位值才不会莫名其妙地消失,刷新需要时间,因此比静态RAM 慢∙静态RAM(Static RAM,SRAM):不使用电容、只用晶体管,在RAM芯片中占更大面积,比DRAM快、比DRAM贵。
CISSP学习笔记(中文)

注:此文档为我第一次看完all in one整理出来的,没什么框架,仅仅是一些知识点,里面很大部分内容来源于书中章节结尾的“快速提示”和文中的关键术语。
望各位大大勿喷,有错误的地方还望包涵,谢谢!第二章信息安全治理与风险管理1.安全的目标是对数据和资源提供可用性,完整性和机密性保护2.脆弱性指的是缺少防护措施或防护措施存在能够被利用的缺陷3.威胁时某人或某物有意或无意地利用某种脆弱性并导致资产损失的可能性4.风险是威胁主体利用脆弱性的可能性及相应的潜在损失5.对策,也叫防护措施或者控制措施,能够缓解风险6.控制可以是行政性的,技术性的或物理性的,能够提供威慑性,防御性,检测性,纠正性或恢复性保护7.补偿控制室由于经济或业务功能性原因而采用的备选控制8.CobiT是控制目标架构,允许IT治理9.ISO/IEC2701是建立,实施,控制和改进信息安全管理体系的标准10.ISO/IEC27000系列源自BS7799,是国际上有关如何开发和维护安全计划的最佳实践11.企业架构框架用来为特定开发架构和呈现视图信息12.信息安全管理体系(ISMS)是一套策略,流程和系统的集合,用来管理ISO/IEC27001中列出的信息资产所面临的风险13.企业安全架构是企业结构的额子集,描述当前和未来的安全过程,体系和子单元,以确保战略一致性14.蓝图是把技术集成进入业务流程的功能性定义15.企业架构框架用来构建最符合组织需求和业务驱动力的单一架构16.Zachman是企业架构框架,SABSA是安全企业架构框架17.COSO是治理模型,用来防止公司环境内出现欺诈18.ITIL是一套IF服务管理的最佳实践19.六格西玛用来识别进程中的缺陷,从而对进程进行改进20.企业安全架构应该配合战略调整,业务启用,流程改进和安全有效性等21.NIST800-53的控制类别分为:技术性的,管理性的和操作性的22.OCTAVE是团队型的,通过研讨会而管理风险的方法,通常用于商业部门23.安全管理应该由顶而下进行(从高级管理层向下至普通职员)24.风险可以转移,规避,缓解和接受25.威胁X脆弱性X资产价值=总风险26.总风险X控制间隙=剩余风险27.风险分析有下列4个主要目标:1、确定资产及其价值;2、识别脆弱性和威胁;3、量化潜在威胁的肯呢关系与业务影响;4、在威胁的影响和对策的成本之间达到预算的平衡28.失效模式及影响分析(Failure Modes and Effect Analysis,FMEA)是一种确定功能,标识功能失效以及通过结构化过程评估失效原因和失效影响的方法29.故障树分析是一种有用的方法,用于检测复杂环境和系统中可能发生的故障30.定量风险分析会尝试为分析中的各个组件指派货币价值31.纯粹的定量风险分析是不可能的,因为定性项无法被精确量化32.在执行风险分析时,了解不确定性程度非常重要,因为它表明团队和管理层对于分析数据的信任程度33.自动化风险分析工具可以减少风险分析中的手动工作量。
CISSP培训笔记

CISSP 最新学习笔记此文就是我班2014年高分考生袁同学在准备CISSP考试过程中得边瞧书边整理得一个学习笔记,整理得非常细致到位,特借此供各位备考学员参考。
第1章节到第10章节主要就是学习all in one第六版资料时笔记;第11章到18章节主要就是在学习完all in one后做cccure网站上面练习题后,补充得知识点;第19章到25章节为学习officeial guide教材后补充得知识点;最后第26章就是总复习时作actual练习题时补充得知识点。
在瞧书3遍all in one后,主要补充学习了pre guide得学习笔记,cccure练习题与official guide进行知识点得补充,最后总复习阶段(1周左右)以本复习笔记为基础,配合actual 练习题进行。
目录一、Chapter 3:Security management practices (3)1、1 安全管理 (3)1、2 风险管理 (4)1、3 Policies、standards、baselines、guidelines、procedures (6)1、4 Classification (7)1、5 employee (7)二、chapter 4:Access Control (7)2、1 Identification, Authentication(= Validating), and Authorization(标识、认证、授权) (8)2、2 Access Control Models(访问控制模型) (10)2、3 Access Control Techniques and Technologies(方法与技术) (10)2、4 Access Control Administration(访问控制管理) (11)2、5 Access Control Methods(访问控制方法) (11)2、6 Access Control Type (12)2、7 access control practices (13)2、8 Access Control Monitoring (13)2、9 A few threats to access control (14)三、Chapter 5:Security Models and Architecture (14)3、1 Computer Architecture (14)3、2 Operation System Architecture (17)3、3 System architecture (17)3、4 安全模型 (18)3、5 运行得安全模式security modes of operation (20)3、6 Systems Evaluation Methods (21)3、7 A Few Threats to Security Models and Architectures (22)四、Chapter 6:Physical Security (22)4、1 Planning process (23)4、2 Protecting assets (24)4、3 Internal Support Systems (25)4、4 Environmental issues (26)4、5 Perimeter security (27)五、Chapter 7:Telecommunications and Networking Security (28)5、1 开放系统模型 (29)5、2 TCP/IP (30)5、3 Type of transmission (30)5、4 LAN Networking (31)5、5 介质访问技术Media access technology (32)5、6 LAN Protocols (32)5、7 Networking Device (33)5、8 Networking services and protocols (34)5、9 MAN、WAN (36)5、10 远程访问remote access (38)5、11 wireless technologies (40)六、Chapter 8:Cryptography (42)6、1 加密方法methods of encryption (43)6、2 对称算法得类型Type of symmetric methods (44)6、3 非对称算法得类型 (45)6、4 Message Integrity hash MD5 SHA (46)6、5 PKI-Public Key infrastructure (49)6、6 链路加密与端到端加密 (49)6、7 E-mail标准 (49)6、8 Internet security (50)6、9 Attack (51)七、Chapter 9:Business Continuity Planning (51)7、1 Make BCP Part of the Security Policy and Program (52)7、2 业务连续性计划得需求 (53)7、3 Recovery Strategies恢复策略 (54)7、4 Developing Goals for the Plans (56)7、5 testing and revising the plan测试与修改计划 (56)八、Chapter 10:Law, investigation and Ethics (57)8、1 Computer Crime Investigations (58)九、Chapter 11:Application and system development (60)9、1 Database Management (61)9、2 System Development (63)9、3 Application Development Methodology (65)9、4 攻击 (67)十、Chapter 12:Operation Security (68)10、1 Security Operations and Product Evaluation (69)10、2 Network and Resource Availability (70)10、3 Email security (70)10、4 Hack and Attack Methods (71)十一、Cccure security management (72)十二、Cccure AC (73)十三、Cccure CPU (75)十四、Cccure AP (76)十五、Cccure encryption (78)十六、Cccure telecommunication (79)十七、Cccure OS运行安全 (80)十八、Cccure 法律 (82)十九、official guide 法律 (83)二十、official guide BCP (83)二十一、official guide 安全管理 (83)二十二、official guide AP (83)二十三、official guide密码 (85)二十四、official guide Network (86)二十五、official guide OS (87)25、1 Information Protection Environment (87)二十六、Actual (88)26、1 One day (88)26、2 two (92)26、3 three (96)一.Chapter 3:Security management practices记住几个公式P65ARO就是年发生概率,10年发生一次,则ARO=1*0、1SLE就是发生一次造成得损失,如37500,那么ALE=0、1*37500=3750EF(暴露因素)*sset value = SLESLE*ARO=ALE(年损失期望)Data owner等多种角色得职责商业公司与政府得集中分级(4、5)1.1 安全管理1. 安全管理需要自顶向下(T op-Down approach)得来进行,高层引起足够得重视,提供足够得支持、资金、时间与资源。
CISSP重点

CISSP重点通过做题归纳出CISSP重点考察的知识点Ch1. Information Security Governance and Risk Management1、CobiT与ITIL关系The Control Objectives for Information and related Technology (CobiT) is a framework developed by the Information Systems Audit and Control Association (ISACA) and the IT Governance Institute (ITGI). It defines goals for the controls that should be used to properly manage IT and ensure IT maps to business needs, not specifically just security needs.The Information Technology Infrastructure Library (ITIL) is the de facto standard of best practices for IT service management. A customizable可定制framework, ITIL provides the goals, the general activities necessary to achieve these goals, and the input and output values for each process required to meet these determined goals. ITIL provides steps for achieving IT service management goals as they relate to business needs.In essence, CobiT addresses "what is to be achieved," while ITIL addresses "how to achieve it." In order to achieve many of the objectives addressed in CobiT, an organization can use ITIL, which provides process-level steps for achieving IT service management objectives.CobiT can be used as a model for IT governance. Actually, Committee of Sponsoring Organizations of the Treadway Commission (COSO) is a model for corporate governance. CobiT is derived from the COSO framework. You can think of CobiT as a way to meet many of the COSO objectives, but only from the IT perspective.2、欧洲Privacy法案(Safe Harbor欧洲安全港)The Safe Harbor requirements were created to harmonize the data privacy practices of the U.S. with the European Union's stricter privacy controls, and to prevent accidental information disclosure and loss. The framework outlines how any entity that is going to move private data to and from Europe must go about protecting it.The Health Insurance Portability and Accountability Act (HIPAA) provides a framework and guidelines to ensure security, integrity, and privacy when handling confidential medical information within the U.S.3、安全机构Security steering committee is responsible for making decisions on tactical and strategic security issues within the enterprise.Security policy committee is a committee chosen by senior management to produce security policies. The steering committee does not directly create policies but reviews and approves them if acceptable.安全指导委员会不会直接新建策略,而是审查和批准可接受的策略。
CISSP最新培训班详细笔记(110页)

CISSP最新培训班详细笔记(110页)CISSP 最新学习笔记此文是我班2014年高分考生袁同学在准备CISSP考试过程中的边看书边整理的一个学习笔记,整理的非常细致到位,特借此供各位备考学员参考。
第1章节到第10章节主要是学习all in one第六版资料时笔记;第11章到18章节主要是在学习完all in one后做cccure网站上面练习题后,补充的知识点;第19章到25章节为学习officeial guide教材后补充的知识点;最后第26章是总复习时作actual练习题时补充的知识点。
在看书3遍all in one后,主要补充学习了pre guide的学习笔记,cccure练习题和official guide进行知识点的补充,最后总复习阶段(1周左右)以本复习笔记为基础,配合actual 练习题进行。
目录一. Chapter 3:Security management practices (5)1.1 安全管理 (5)1.2 风险管理 (6)1.3 Policies、standards、baselines、guidelines、procedures (7)1.4 Classification (8)1.5 employee (9)二. chapter 4:Access Control (10)2.1 Identification, Authentication(= Validating), and Authorization(标识、认证、授权) (10)2.2 Access Control Models(访问控制模型) (12)2.3 Access Control Techniques and T echnologies(方法和技术) (13)2.4 Access Control Administration(访问控制管理) (13)2.5 Access Control Methods(访问控制方法) (14)2.6 Access Control Type (15)2.7 access control practices (15)2.8 Access Control Monitoring (15)2.9 A few threats to access control (16)三. Chapter 5:Security Models and Architecture (17)3.1 Computer Architecture (17)3.2 Operation System Architecture (20)3.3 System architecture (20)3.4 安全模型 (21)3.5 运行的安全模式security modes of operation (23)3.6 Systems Evaluation Methods (23)3.7 A Few Threats to Security Models and Architectures (24)四. Chapter 6:Physical Security (26)4.1 Planning process (26)4.2 Protecting assets (28)4.3 Internal Support Systems (28)4.4 Environmental issues (29)4.5 Perimeter security (31)五. Chapter 7:T elecommunications and Networking Security (33)5.1 开放系统模型 (33)5.2 TCP/IP (34)5.3 Type of transmission (35)5.4 LAN Networking (35)5.5 介质访问技术Media access technology (36)5.6 LAN Protocols (37)5.7 Networking Device (37)5.8 Networking services and protocols (39)5.9 MAN、WAN (40)5.10 远程访问remote access (43)5.11 wireless technologies (44)六. Chapter 8:Cryptography (47)6.1 加密方法methods of encryption (48)6.2 对称算法的类型Type of symmetric methods (49)6.3 非对称算法的类型 (50)6.4 Message Integrity hash MD5 SHA (51)6.5 PKI-Public Key infrastructure (54)6.6 链路加密和端到端加密 (54)6.7 E-mail标准 (54)6.8 Internet security (55)6.9 Attack (56)七. Chapter 9:Business Continuity Planning (57)7.1 Make BCP Part of the Security Policy and Program (58) 7.2 业务连续性计划的需求 (58)7.3 Recovery Strategies恢复策略 (59)7.4 Developing Goals for the Plans (61)7.5 testing and revising the plan测试和修改计划 (61)八. Chapter 10:Law, investigation and Ethics (63)8.1 Computer Crime Investigations (64)九. Chapter 11:Application and system development (66)9.1 Database Management (66)9.2 System Development (68)9.3 Application Development Methodology (71)9.4 攻击 (72)十. Chapter 12:Operation Security (74)10.1 Security Operations and Product Evaluation (74) 10.2 Network and Resource Availability (76)10.3 Email security (76)10.4 Hack and Attack Methods (77)十一. Cccure security management (79)十二. Cccure AC (80)十三. Cccure CPU (82)十四. Cccure AP (84)十五. Cccure encryption (86)十六. Cccure telecommunication (88)十七. Cccure OS运行安全 (89)十八. Cccure 法律 (91)十九. official guide 法律 (92)二十. official guide BCP (93)二十一. official guide 安全管理 (93)二十二. official guide AP (94)二十三. official guide密码 (96)二十四. official guide Network (97)二十五. official guide OS (99)25.1 Information Protection Environment (99)二十六. Actual (100)26.1 One day (100)26.2 two (104)26.3 three (108)一.Chapter 3:Security management practices记住几个公式ARO是年发生概率,10年发生一次,则ARO=1*0.1SLE是发生一次造成的损失,如37500,那么ALE=0.1*37500=3750EF(暴露因素)*sset value = SLESLE*ARO=ALE(年损失期望)Data owner等多种角色的职责商业公司和政府的集中分级(4、5)1.1 安全管理1. 安全管理需要自顶向下(T op-Down approach)的来进行,高层引起足够的重视,提供足够的支持、资金、时间和资源。
CISSP K笔记

K書筆記本-Information Security & Risk Management (01)資訊安全是近來幾年相當受到觀注的領域,Jason自投入業界至今也在三年前轉往這個領域當然在這個領域中也有不少的挑戰,而Jason近來也在正在準備這方面的挑戰為了讓自已和廣大的鄉民們也能一同的討論,Jason將讀過的資料轉化後貼到自已的blog中跟大家一起討論Information Security的組成可由Availability(可用性)、Integrity(完整性、一致性)、Confidentiality(機密性)所構成而每個構成安全的特性中個別又包含了不同層面的涵意:Availability:可用性避免服務中斷。
Intregint:避免得到授權或未經授權者做任何規範外的變更,並且保持資訊內外的一致。
Confidentiality:保護授權機密性這麼說似乎相當的模糊,不過,透過下列的說明大家應該比較能夠明瞭:Availability又分為Timely(即時)及 Reliable(可信任),要用的時侯馬上可以用,並且可以被信任的機制或處理流程。
Integrity則有”Prevent unauthorized modification by unauthorized people.(避免未經授權者做任何未經授權的變更)”、”Prevent unauthorized modification by authorized people.(避免授權者做任何未經授權的變更)”及”Maintain internal and external consistency.(維持內部與外部的一致性)”Confidentiality則是”Prevent intentional or unintentional unauthorized disclosure.(確保有意或無意的散播)”身為一個資訊安全人員應該確保以上三點的完整架構,當然在不同的領域環境之下,一定有特別著重的部份,但三者一定缺一不可就像是經典電影中的對白:我身為一個汽車維修人員,身上帶著起子算得上是合情合理吧~!雖然談到資安大家所想的就是抓駭客、防止被入侵、中毒事件,但是對於資安人員來看,可不止是如此的簡單而以但是也不可不否認,台灣在資安所著重的路份確實相當的薄弱,試問沒有賺錢的公司會想導入資安嗎?台灣的教育之下也不是以安全為第一考量針對(ISC)2所提出的資安十大領域之中,可以很明確的看出6.5分管理2.5分科技及1分法律,這樣才能達成十分安全資安人員首重道德,對於其道德良知的看重勝過其它因素,若資安人員沒有約束自已的能力,那麼對於客戶的安全怎麼會重視呢?K書筆記本-Information Security & Risk Management (02)上一篇中談論到了資安的構面,但是實際的作法應該如何運作會在下面的幾個K書筆記本中與大家討論即然談論到了資安,就不能不討論到資安管理(Information Security Mamagement)的內容在The Official (ISC)2 Guide to the CISSP CBK(Common body of knowledge)中提到的資訊安全管理應該包含:Governance Structure(治理結構)、Policies(政策)、Standards(標準)、Procedures(程序)、Baselines(基礎線)、Guidelines(指引方針)當然談到了資安治理那麼IT的安全需求呢(IT Security Requirements)?對於一個完整的資安解決方案又該如何做起?這個又是一種考量的基礎,在尋找一個IT安全結構下應該由兩種需求來考量:Functional Requirements(軟體需求)、Assurance Requirements(保障需求)Functional Requirements: Defines the security behavior of the control measure. Selected based on risk assessment.軟體需求:控制措施運作狀態的特性。
Cissp考试 AllInOne全书重点笔记

对称加密:DES标准-DEA加密算法:64位:56位加密,8位奇偶校验,16轮计算1.ECB电子密码本:最快捷,一般用来加密数据库,短小的引用加密,容错,长消息会发生重复导致破解难度下降2.CFB密文反馈:前一组加密结果作为下一组加密的IV3.CBC密码分组链接(很重要):前一组加密结果与下一组明文进行异或,然后再加密4.OFB输出反馈:用于加密下一组明文的值来自于密钥流3DES:48轮加密,时间比DES长3倍EEE3:3个密码,加密,加密,加密EEE2:2个密码,加密,加密,加密(1,3用同一个密码)EDE2:2个密码,加密,解密,加密(1,3用同一个密码)AES标准-Rijndeal算法128位-10轮计算192位-12轮计算256位-14轮计算blowfish分组加密RC4最常用的流密码(目前已被破解)用于SSLRC5分组加密RC5-32/12/16 64位分组,12轮运算,128位密码(16个字节)非对称加密:Diffie-hellman 主要用于密钥交换有限域内离散对数RSA 加密,数字签名,密钥交换分解大因数为原始大质数的难度ELGamal 加密,数字签名,密钥交换有限域内计算离散对数ECC 椭圆曲线,同等密钥长度下效率最高,消息完整性散列算法:MAC:1.HMAC(用消息+对称秘钥一起做MAC),只有拥有对称秘钥的接收方才能正确计算出同样的MAC2.CBC-MAC(用密码分组链接加密的最后一组结果作为MAC)散列算法:MD4 128位散列MD5 128散列,比MD4复杂SHA 160位散列,应用在DSA数字签名算法内DSA:非对称加密,只用作数字签名DSS数字签名标准(美国)SHA生成160位散列,然后用(DSA,RSA,ECC)加密,加密以后的结果用作数字签名PKI公钥基础设施:一般用户生成公钥+私钥,向RA请求验证用户身份,RA验证用户身份以后提交给CA,CA创建公钥证书(证书包含用户公钥以及身份,证书时间戳等信息)以及签名发送给请求者ca发放的证书用ca自身的私钥加密,用户用ca的公钥(任何人都可以得到)解密,用来验证证书发放机构ca的身份,从而验证证书的有效性+完整性。
CISSP Review Notes

THIS STUDY GUIDE WAS GREATLY IMPROVED BY HENRY GUZ MANIN JANUARY2005THANKS FOR YOUR CONTRIBUTIONJanuary2006:Thanks to Intensified for his correction about CSMA/CA being used on WLAN and NOT CSMA/CD as it was specified.Good catch!!Access ControlTelecommunications&Network SecuritySecurity Management PracticesApplication and System DevelopmentCryptographySecurity Architecture and ModelsOperations SecurityBCP and DRPLaw,Investigation,and EthicsPhysical SecurityAccess ControlAccess control protects the system s and resources from unauthorized access,and,usually determ ines the level of authorization.Subject-Entity requiring access to an object–user or process.(Active).Object-Entity to which access is requested–file,process.(Passive).Access control consists of the following primary areasIdentificationAuthenticationAuthorizationAccountabilityThe last three of these are largely com prised of‘logical access controls’.IdentificationBiometrics Very sophisticated and accurate,but expensive.Type1error Rejection on authorized individuals–false reject rate(FRR)Type2error Acceptance of individual that should be rejected(FAR)CER Crossover error rate–point at which false acceptance equals false rejection–expressed as a percentage.Important m easurement of biometric system’s accuracy.The lower the better.Other barriers to widespread adoption of biometrics include user acceptance,enrollment tim e and throughput.Collected biometric images are stored in a corpus.Effectiveness versus Acceptance of biometric devicesOrder of Effectiveness Order of AcceptancePalm scan Iris scanHand geom etry Keystroke dynamicsIris scan Signature dynamicsRetina pattern Voice verificationFingerprint Facial recognitionVoice verification FingerprintFacial Recognition Palm scanSignature Dynamics Hand GeometryKeystroke Dynamics Retina PatternAuthenticationThe three general types of authentication areSom ething a person knows.Som ething a person has.Som ething a person is.Strong authentication requires two of these three(two-factor authentication). PasswordsPasswords are the m ost com monly used,but also considered one of the weakest.A cognitive passwords is information only you should know,like your m other’s m aiden nam e.One-time PasswordsThere are two types of one-tim e password–synchronous and asynchronous.One-tim e passwords are usually generated by a token device that com municates with anauthentication service.Synchronous–Token device synchroniz es with authentication server via a tim e based or event based synchronization.Token device and auth server share the sam e secret key.Asynchronous–Uses a challenge-response schem e to com munication with theauthentication server.Other authentication mechanismsPrivate key–digitally signing a m essage.Passphrase–transformed into a virtual passwordMem ory card–holds information but does not process it.ATM card.Sm art card–capability of processing information.AuthorizationThe system knows who you are(authentication)and m ust now decide if you can carry out the requested actions.This is where authorization com es into play.Access criteria is the crux of authorizationAccess criteria types can be broken up intoRolesGroupsPhysical or logical(network)locationTim e of dayTransaction typeAll access criteria should default to“no access”.Need to know principleManagement’s job is to determ ine the“need to know”.Adm inistrator job is to configure access control and security m echanisms to fullfil the need to know requirements.Single Sign-on MechanismsScripting Batch files containing logic details.Insecure.High m aintenance recording and m aintaining scripts.KerberosKerberos is a single sign-on system that uses sym metric key cryptography(DES)and end to end encryption.Kerberos eliminates the need for transm itting passwords over the network.In order to implem ent Kerberos,all software in use m e be Kerberoscom patible or,“kerberized”.The com ponents of Kerberos areKDC Key distribution center.Holds user’s and services’keys.The foundation of kerberos is the client and server’s trust in the KDC.The KDC actually consists of a ticket granting service and authentication server.Principals Entities requiring KDC services–users,apps or services.The KDC and each principal share a secret key.Ticket Tickets are created by the KDC and given to a principle when that principle needs to authenticate to another principle.Realm A“realm”is the set of com ponents and principles that the KDC provides services for.AS Authentication service–this is part of the KDC.Kerberos Authentication ProcessThe client trusts the KDC and the services trust the KDC due to their secret keys.An overview of the process when a client wan’t to use a service via Kerberos isThe client sends its user id and the nam e of the requested service to the KDC.The KDC provides a session key for the client and service to use.One is encrypted with the user secret key and the other with the service secret key.The KDC generates a service ticket containing both session keys.This ticket is sent back to the client.The user enters their password and if the password is correct,the client converts it into the necessary key to decrypt the client session key in the ticket.The client decrypts the client portion of the ticket to get the session key and sends the ticket on to the service.The service uses its own private key to decrypt the session key.The user and service are now authenticated to each other and com municate withencrypted data via the session key.Secret key Shared between KDC and a principle.Session key Shared between two principles.Kerberos weaknessKerberos has a number of weaknesses that can m ake it vulnerable to attack.Som e of these areThe KDC is a single point of failure.The secret keys are tem porarily stored on user’s workstations,in m emory,etc.Session keys are decrypted and reside on user’s workstations.Vulnerable to password guessing.Does not protect network traffic.When a user changes password,the KDC database needs to be updated with a new corresponding secret key.Replay attacks can be used against Kerberos.Secure European System for Applications in a Multiuser Environment.Sesam e is a single sign-on system designed to address som e of the kerberos weaknesses.It uses public key cryptography for distribution of secret keys and supports MD5and CRC32hashing.Still vulnerable to password guessing.Sesam e uses the Needham-Schroeder protocol.No local processing.Thin clients for the user to login to the network just to be able to use the com puter.Kryptoknight is another single sign-on protocol similar to Kerberos.The m ain difference is that there is a peer-to-peer relationship am ong parties and the KDC.An access control m odel is a fram ework that dictates how subjects access objects.There are three m ain types of access control m odel m andatory access control,discretionary access control and role-based access control.The creator of a file is the‘owner’and can grant ownership to others.Access control is at the discretion of the owner.Most com mon implem entation is through access control lists.Discretionary access control is required for the Orange Book “C”Level.Much m ore structured.Is based on security labels and classifications.Access decisions are based on clearance level of the data and clearancelevel of the user,and,classification of the object.Rules are m ade by m anagement,configured by the adm inistrators and enforced by the operating system.Mandatoryaccess control is required for the Orange Book“B”Level.Continually adm inistered set of controls by role within organization.Access rights assigned to roles–not directly to users.Roles are tighter controlled than groups-a user can only have one role.Can use different types of RBACRole-based Role within organization.Task-based Specific task assigned to the user.Lattice-based Upper and Lower boundsAccess Control Techniques and TechnologiesOnce a com pany decides on the access control m odel to use,the technologies andtechniques to implement that m odel need to be determ inedRole-based Can be used with MAC–Labels assigned to roles.Or with non-discretionary controls such as NT Groups.Rule-based Example-Router or firewall rules–user cannot change.•Restricted interfacesMenus and shells–ATM m achineDatabase viewsPhysically constrained interfaces.•Access Control MatrixTable of subjects and objects indicating access.•Capability TablesSpecifies the access a certain subject has to specific objects.Corresponds to arow in the access control m atrix.Bound to subject.Access Control ListsBound to object.List of subjects authorized to access a specific object,and,the level of access/authorization.•Content-dependantDatabase views are a good example–access is based on the data content itself.•Context-dependantAccess is based on location,tim e of day,previous access history,etc.Access Control AdministrationAccess control adm inistration is either centralized,decentralized or a hybrid of the two.Examples of centralized access control technologies includeRADIUS Rem ote Authentication Dial-In User ually used for dialup.Access server requests user login credentials and forwards to a backend RADIUS server.Can use callback for additional security.TACACS(Terminal Access Controller Access Control System).There are several types of TACACSTACACS Com bines its authentication and authorization processes.Passwords arestatic.XTACACS Separates authentication,authorization and accounting processes.TACACS+XTACACS with two-factor user authentication.Supports tokenauthentication.Security DomainA security dom ain is defined as a“realm of trust”.Subjects and objects share com monsecurity policies and procedures and are m anaged by the sam e system.Also used within operating system s and applications to protect system files or processes.It can also be defined as the com plete set of resources available to a user.Access Control MethodsThere are three broad categories of access control layersAdm inistrativeTechnicalPhysicalPolicies and procedures Guidelines+standards+baselinesPersonnel controls Hiring,firing,promotions,transfers,separation of duties,rotation of duties,forced vacation.Supervisory structures Clear lines of reporting.Awareness TrainingSecurity Testing Drills,penetration testing,queries to em ployees,interviews,reviews.Network segregation.Perimeter security.Com puter controls.Work area separation.Data backups.Cabling.System Access–See previous access control m echanisms.Network architecture–Logical controls can provide segregation and protection of an environment.I/P address ranges,subnets,routing between networks,etc.Network Access–Logical network access controls–routers,switches,NICs,bridges.Encryption and ProtocolsControl Z one–Technical and physical control.Surrounds and protects network devices that em it electrical signals.TEMPEST related.Access Control TypesEach control m ethod can also perform different functionality.The functionality types are PreventativeDetectiveCorrectiveDeterrentRecoveryCom pensatingFor examplePreventative-AdministrativePolicies and procedures,effective hiring practices,background checks,data classification, security awareness training.Preventative-PhysicalBiometrics,badges,swipe cards,guards,dogs,m otion detectors,fences,m antraps,locks and alarms.Preventative-TechnicalPasswords,biometrics,sm art cards,encryption,call-back system s,database views,antivirus software,ACLs,firewalls,IDSAuditingAuditing capabilities ensure that users are held accountable for their actions,verify that policies are enforced,deter improper actions and are an investigative tool.There are3m ain types of audit toolAudit reductionVariance detectionAttack-signature detectionAudit data m ust be protected from unauthorized viewing and m odif ication.Access Control PracticesThe following tasks should be carried out regularlyDeny access to undefined or anonymous accountsLimit and m onitor adm inistration accountsSuspend access after a number of failed loginsRem ove accounts as soon as som eone leaves an organization.Format Access Control ModelsThe Bell LaPadula m odel is built on state m achine concepts and focuses on confidentiality.The objective of this m odel is to ensure that the initial state is always secure and that transitions always result in a secure state.Bell LaPadula defines asecure state through3m ultilevel propertiesSimple Security Policy No read up–a lower level subject cannot read a higher level object.Protecting confidentiality.Security*(star)property No write down–do not allow confidential information to be written to a local level,where a lower level subject will be able to view it.Discretionary Security Property Uses a discretionary access control m atrix tom anage exceptions.The Biba m odel is lattice based and focuses on integrity m ore than confidentiality.Biba specifies the following three axiomsSimple Integrity Axiom No read down.A higher level subject cannot read information from a lower level.This prevents higher level reports and data being corrupted by lower level(and less trustworthy)information.Integration*(Star)Axiom No write up.A subject cannot write data above itssecurity level–higher level data m ight be com promised by lower level,less trustworthy data.A subject at one integrity level cannot invoke a subject at a higher integrity levelwas developed after the Biba m odel and ensures integrity.The Clark-Wilson Model utilizes separation of duties to ensure that authorized users do not m ake unauthorized changes to data.In this way task are divided into different parts and different subjects each do different parts.Often tim es subjects under the Clark-Wilson Model cannot access data directly,but m ust instead go through a program or other third party,which helps to ensure the subject has the proper classification.This m odel has em p hasis on internal and external consistency.Clark-Wilson uses well form ed transactions,separation of duties and the labeling of subjects and objects with programs to m aintain integrity.Security properties are partly defined through five certification ru les,suggesting the check that should be conducted so that the security policy is consistent with the application requirements.CDI–Constrained Data Item A data item whose integrity m ust be preserved.IVPS–Initial Verification Procedures Confirm that all CDIs are in a valid integrity state when the IVP is run.TP–Transformation Procedure Manipulates the CDIs through a well-formedtransaction,which transforms a CDI from one valid integrity state to another.UDI–Unconstrained Data Item Data item s outside of the control area such as input information.Any TP that takes a UDI as input m ust either convert the UDI into a CDI or reject the UDI and perform no transaction at all.Unauthoriz ed disclosure of informationThere are several ways in which information can be inadvertently disclosed.The follow item s are related to information disclosureObject Reuse Reassigning m edia to a subject when m edia m ight still contain som e residual information.Make sure m edia is cleaned.Degaussing works best.Object reuse controls are required for TCSEC B2and above.Emanation Picking up radiation em itted by devices.Can use TEMPEST technology to block.TEMPEST is very expensive,som e alternatives areWhite Noise–Unif orm spectrum of random electrical signals used to disguise realdata.Z ones–Control z ones.Access Control MonitoringKeeping track of who attem pts to access specific resources,access control m onitoring is an important detective m echanism usually carried out by intrusion detection system s Network Based IDS Monitors network,or a segm ent of the network(passive).Known as NIDS.Placem ent of sensors is a critical part of configuring a network based IDS.Place a sensor on the outside firewall to detect attacks and inside the firewall to detect invasions.Another factor to consider is that the network traffic should never exceed the IDS threshold,or the IDS m ay just start to drop packets.Host-Based Monitors a specific system,such as your critical servers.Intrusion detection system s have two m ain m ethods of operationKnowledge/Signature based This type of IDS looks for known attacks and istherefore weak vs new attacks.There are less false alarms.This type of IDS m ay also fail to detect“slow”attacks extended over a long period of tim e.Behavior based/Statistical IDS This type of IDS detects deviations from expected behavior of users and system s.May use expert system s.Detects new attacks anddoesn’t rely on a database of signatures to be updated,but,can cause m ore falsepositives.Relational Database SecurityRelational database security is a growing area of concern.The following are areasrelating to database technology and securitySchema Description of the database and its ually written using a DDL.Cardinality Number of rows in a table.Degree Number of columns in a table.Domain The set of all allowable values an attribute can take.Entity Integrity&Referential IntegrityView-Virtual table defined from other tables that is used to restrict access,hideattributes and provide content-dependant access.Views help implem ent least privilege and need to know principles.To protect against“inference attacks”,databases m ay have a m inimum query set size and prohibit query of“all but one”tuples.Highly secure system s m ay also em ploycontext dependant access control where the tuples a user can read are based on those already read.ThreatsThe m ain categories of threat to access control m echanisms areDictionary attack.Brute force attack.Spoofing at login–fake login screen to capture details.A“trusted path”can m it igate login spoofing.The following m easures are used to com pensate for internal and external accessviolationsBackupsRAIDFault toleranceBusiness continuity planningInsuranceTopTELECOMMUNICATIONS&NETWORK SECURITYOpen Systems Interconnect(OSI)modelDeveloped early1980s and introduced in1984•Application|Presentation|ApplicationSession|____________Transport<-->Host to HostNetwork<-->Internet Layer.Data Link|Physical|Network Access Layer.“Each protocol at a specific OSI layer com municates with a protocol that operates at the sam e OSI layer on another com puter.This happens through encapsulation”The protocols,technologies and com puters that operate within the OSI m odel are called open systems.Application LayerThe application layer works closest to the user and handled m essage exchanges,terminal sessions,etc.The application does not include the actual applications,but the protocols(APIs)that support the applications.Examples of protocols running in the application layer includeSMTP,HTTP,LPD,FTP,WWW,Telnet,TFTPPresentation LayerThe presentation layer received data from the application layer and puts it into a form at that all com puters using the OSI m odel can understand.The presentation layer is not concerned with the m eaning of data,but the correct syntax and form at.The presentation layer can often be considered a“translator”.This layer also handles encryption and com pression.ASCII,JPEG,TIF,GIF,Encryption,Com pression,MIDI,MPEGSession LayerWhen two com puters need to com munication,or transfer information,a connectionsession needs to be set up between them.The session layer is responsible forestablishing a connection,m aintaining it during data transfer and releasing it when done.The session layer works in3phasesConnection establishmentData TransferConnection releaseCom mon protocols at the session layer areSSL,NFS,SQL,RPCTransport LayerWhen two com puters are going to com municate,they m ust first agree on how m uch information each will send at a tim e,how to determ ine if data was lost in order toretransmit and other parameters.The com puters agree on these parameters through a process at the transport layer,OSI layer4.The transport layer helps provide m ore reliable data transfer,error correction and flow control.It assem bles data into a stream for transm itting over the network,and handledm ultiplexing if necessary.The transport layer also handles the teardown of virtualcircuits and the m ultiplexing of upper layer applications.TCP,UDP,SPXNetwork LayerThe m ain responsibility of the network layer is to insert information into the packet’s header so that it can be properly routed.Routing protocols build and m aintain their tables at this layer.The protocols at this layer do not ensure packet delivery–they rely on the transport layer for that.Protocols operating at this level includeIP,ICMP,RIP(Routing information protocol),OSPF(Open shortest path first),BGP(Border gateway protocol)and Internet group m anagement protocol(IGMP)Most routers also run in the network layer.Data Link LayerAs data travels down the ISO stack it com es to a point where it needs to be translated into LAN or WAN binary form at for line transm ission.This happens at the data link layer.The data link layer is where the operating system knows what form at the data fram e m ust be in to transm it over Token Ring,Ethernet,FDDI,ATM,etc.Network cards bridge the data link and physical layer.The data link layer actuallyconsists of two sub layersMedia Access Control(MAC)Logical Link Control(LLC)Protocols operating in the data link layer includeSLIP,PPP,RARP,L2F,L2TP,ISDN ARPBridges operate in the data link layer.Physical LayerThe physical layer converts bits into voltage for transm ission.This layer controlssynchronization,data rates,line noise and physical m edium access.Protocols operating in the physical layer includeRS232,SONET,HSSI,X.21Repeaters operating in the physical layer.OSI defines6basic security services to secure OSI com municationsAuthenticationAccess ControlData confidentialityData integrityNon-repudiationLogging and MonitoringIn addition,the OSI m odel defines8security m echanisms.A security m echanism is a control that is implemented in order to provide the6basic security servicesEnciphermentDigital SignaturesAccess ControlData IntegrityAuthenticationTraffic PaddingRouting ControlNotarizationTCP/IPI/P is a network layer protocol and provides datagram routine services.Two m ain protocols work at the transport layer,TCP and UDP.TCP Handshake1.Host--------SYN--------->Host B<-----SYN/ACK----->---------ACK-------->The TCP/IP m odel has4layersApplicationHost to hostInternetNetwork AccessThe TCP/IP m odel layers correspond to the ISO m odel layers as followsApplication Application,presentation,session.Host to Host TransportInternet NetworkNetwork Access Data Link,PhysicalThe Host-to-host layer handlesTCP-Virtual Circuit,sequenced,slower,m ore reliableUDP-“Best effort”,connectionless.Internet layerI/P-No guarantee of delivery,delivery in sequence or only once.ARP-I/P to MACRARP-MAC to I/PICMPThe I/P header contains a protocol field.Som e com mon protocols are-ICMP–IGMP6-TCP17–UDPWithin the I/P protocol suite,when an application form ats data for sending overthe network,it is a message.At the transport layer,TCP works on the data and it is now a segment i.Thesegm ent is passed to the network layer.The network layer adds addressing and routine and the bundle is now called adatagram.The datagram is passed off to the data link layer which fram es the datagram witha header&trailer.It is now called a frame.TCP UDPApplication Layer Message MessageTransport Layer Segm ent PacketNetwork Layer Datagram DatagramData Link Layer Fram e Fram eClass A Unauthoriz ed access of restricted network services.Also called“login abuse”. Refers to legitim ate users accessing network services that should be restricted to them.Class B Unauthoriz ed use of a network for non-business purposes.Class C EavesdroppingClass D DOS and other disruptionsClass E Network Intrusion.Refers to the use of unauthorized access to break into the network from the outside.Classic cases are spoofing,piggybacking and backdoor exploitation.Class F Probing.An active variation of eavesdropping.Additional Attacks SYN attacks,Buffer Overflow,Teardrop attack and Sm urf.Common Session Hi-jacking attacks•IP Spoofing attacks.•TCP sequence number attacks.•Other fragmentation attacks–using fragmented packets to hide true contact. NETWORKINGMost of the differences between LAN and WAN take place at the data link layer“Two LANs connected by a router is an internetwork,not a bigger LAN.Each LAN has its own addressing schem e and broadcast and com munication m echanisms.If they are connected by different data link technologies such a fram e relay of X.25then we are looking at a WAN”Usually a bus or star topologyIEEE802.3standardShared m edia–all devices take turns and detect collisionsUses broadcast and collision dom ainsCSMA/CD access m ethod(Carrier Sense Multiple Access with Collision Detection)Uses coaxial or twisted pair.Common Implementationses coaxial cable.Max length of185m eters and provides up to 10mbs es BNC connectors.es thicket coaxial cable.Longer cable segm ents and lessinterference.10baseT Twisted-pair copper wiring.RJ45connectors,usually in a star topology with a hub or switch.Fast Ethernet Regular ethernet running at100mbps over twister pair wiring.Ethernet Types Table10base2,ThinNet Co-Axial10mbps10base5,ThickNet Co-Axial10mbps10base-T UTP10mbps100base-FX,Fast UTP100mbps1000base-T UTP1,000mbps802.5standard,originally developed by IBMSignal travels in a logical ringEach com puter is connected to a hub called a Multistation Access Unit(MAU) 16mbps capacityActive Monitor–removes fram es that are continually circulatingBeaconing–attem pts to work around errors.Fiber Distributed Data InterfaceDeveloped by ANSIHigh speed token-passing m edia access technologySpeed of100mbvps–usually used as a backbone network using fiber optics.Fault tolerance–second counterrotating ring.Can be used up to100kms,so popular in MANsCDDI(copper distributed data interface)is a version that can be used locally.802.8standard.CABLINGLAN Media Standard CharacteristicsEthernet802.3Shared m ediaBroadcast&Collision DomainsCSMA/CDCoaxial or twisted cable10mbps–1gbpsToken Ring802.5Devices connect to center MAUToken-passing access m ethodTransm ission speeds of4-16m pbsActive m onitor and beaconing FDDI802.8Token-passing access m ethodDual counter rotating ring–fault tolerance100mbps over fiber-opticLong distance at high speed*CDDI works over UTPBandwidth Size of pipeData Rate Am ount of dataCoaxialCopper core surrounded by shielding layer。
CISSP 笔记 Access Control
Access Controls OverviewAccess controls are security features that control how users andsystems communicate andinteract with other systems and resources.Access control is a broad term that covers several different types of mechanisms thatenforce access control features on computer systems, networks, and informationSecurity PrinciplesAICIdentification, Authentication, Authorization, and AccountabilityIdentification describes a methodof ensuring that a subject (user, program, or process) is the entity it claims to be. To be properly authenticated, the subject is usually required to provide a second piece to thecredential setLogical access controls are technical tools used for identification, authentication, authorization, and accountability.Identification and AuthenticationThree general factors can be used for authentication: something a person knows, something a personhas,and something a person is.Strong authentication contains two out of these three methods: something a personknows, has, or is. This is also referred to as two-factor authentication.Creating or issuing secure identities should include three key aspects: uniqueness, nondescriptive, and issuanceIdentity ManagementIdentity management is a broad and loaded term that encompassesthe use of different products to identify, authenticate, and authorize users through automated meansthe term also includes user account management, access control, password management, single sign-on functionality, managing rights and permissions for user accounts, and auditing and monitoring all of these itemsFor the CISSP exam, the following are the types of technologies you should be aware of:•Directories•Web access management•Password management•Legacy single sign-on•Account management•Profile updateDirectoriesThe objects within the directory are managed by a directory service. The directory service allows an administrator to configure and manage how identification, authentication, authorization, and access controltake place within the network and on individual systems.In a Windows environment, when you log in, you are logging in to a domain controller (DC), which has a hierarchical directory in its database. The database is runninga directory service (Active Directory), which organizes the network resources and carriesout user access control functionality. So once you successfully authenticate to the DC,certain network resources will be available to you (print service, file server, e-mail server, and so on) as dictated by the configuration of AD.The directory service keep all of these entities organized by using namespacesEach directory service has a way of identifying and naming the objects theywill manage.In databases based on the X.500 standard that are accessed by LDAP, the directory service assigns distinguished names (DNs) to each object.DN is made up of a common name (cn) and domain components (dc)Directories’Role in Identity ManagementA directory used for IdM is specialized database software that has been optimized for reading and searching operations.It is the main component of an identity management solutionA meta-directory gathers the necessary information from multiple sources and stores it in one central directory.A virtual directory plays the same role and can be used instead of a meta-directory.The difference between the two is that the meta-directory physically has the identitydata in its directory, whereas a virtual directory does not and points to where the actualdata resideWeb Access ManagementWeb access management (WAM) software controlswhat users can access when using a web browser to interact with web-based enterpriseassets.The WAM software is the main gateway between users and the corporateweb-basedresources. It is commonly a plug-in for a web server, so it works as a front-end processWAM tools usually also provide a single sign-on capability so that once a user is authenticated at a web site, she can access different web-based applications and resources without having to log in multiple times.Cookies id used to keep the state of a web accessPassword Management∙Password SynchronizationPassword synchronization technologies can allow a user to maintain just one password across multiple systems∙Self-Service Password ResetSome products are implemented to allow users to reset their own passwords.∙Assisted Password ResetSome products are created for help-desk employeeswho need to work with individuals when they forget their password∙Legacy Single Sign-OnAn SSO technology allows a user to authenticate one time andthen access resources in the environment without needing to re-authenticateWith password synchronization, a producttakes the user’s password and updates each user account on each different system andapplication with that one password.So in SSOenvironments, the SSO software intercepts the login prompts from network systemsand applications and fills in the necessary identification and authentication information for the user.An SSO solution may also provide a bottleneck or single point of failure. If the SSO server goes down, users are unable to access network resources. This is why it’s a goodidea to have some type of redundancy or fail-over technology in place.it can be expensive to implement, especially in larger environments. Many times companies evaluate purchasing this type of solution and find out it istoo cost-prohibitiveThe otherissue is that it would mean all of the users’credentials for the company’s resources arestored in one location∙Account ManagementAccount management deals with creating user accounts on all systems, modifying the account privileges when necessary, and decommissioning the accounts when they are no longer needed.The automated workflow component is common in account management products that provide IdM solutions. Not only does this reduce the potential errors that can takeplace in account management, each step (including account approval) is logged andtracked. This allows for accountability and provides documentation for use in backtracking if something goes wrong.∙ProvisioningAn account management process.from the creation of an anccout to an decommission.User provisioning refers to the creation, maintenance, and deactivation of user objects and attributes as they exist in one or more systems, directories, or applications, inresponse to business processes.User provisioning software may include one or more ofthe following components: change propagation, self-service workflow, consolidateduser administration, delegated user administration, and federated change controlsummaryDirectories are built to containuser and resource information. A metadata directory pulls identity information that resides in different places within the network to allow IdM processes to only have to getthe needed data for their tasks from this one location. User managementtools allow forautomated control of user identities through their lifetimes and can provide provisioning.A password management tool is in place so that productivity is not slowed down by a forgotten password. A single sign-on technology requires internal users to only authenticate once for enterprise access. Web access management tools provide a single sign-onservice to external users and control access to web-based resources.Profile UpdateThere can be a plethora of information ona user that is captured (e-mail address, home address, phone number, panty size, andso on). When this collection of data is associated with the identity of a user, we call it aprofile.The profile should be centrally located for easier management. IdM enterprise solutions have profile update technology that allows an administrator to create, makechanges, or delete these profiles in an automated fashion when necessaryFederationIdentity federation is based upon linking a user’s otherwise distinct identitiesat two or more locations without the need to synchronize or consolidate directory information.Web porta ls functions are parts of a website that act as a point of access to information.A portal presents information from diverse sources in a unified manner.used and integrated in many web-based federated identity management processes and products today.Access Control and Markup LanguagesXML is a universal and foundational standard that provides a structurefor other independent markup languages to be built from and still allow for interoperabilityThe Service Provisioning Markup Language (SPML)allows for the exchange of provisioning data between applicationsThis markup language allows for the integration and interoperation of service provisioning requests across various platforms.SPML is made up of three main entities: the Requesting Authority (RA), which is the entity that is making the request to set up a newaccount or make changes to an existing account; the Provisioning Service Provider(PSP), which is the software that responds to the account requests;and the Provisioning Service Target (PST), which is the entity that carries out the provisioning activitieson the requested system.Security Assertion Markup Language (SAML)It is an XML standard that allows the exchange of authentication and authorization data to be shared between security domainsSAML provides the authentication pieces to federated identitymanagement systemsto allow business-to-business (B2B) and business-to-consumer (B2C) transactions.Transmission of SAML data can take place over different protocol types,but a common one is Simple Object Access Protocol (SOAP). SOAP is a specification that outlineshow information pertaining to web services is exchanged in a structured mannerAn SOA is a way to provide independentservices residing on different systems in different business domains in one consistentmanner.Extensible Access Control Markup Language (XACML)XACML is used to express security policies and access rights to assetsprovided through web services and other enterprise applicationsXACML is both an access control policy language and a processing modelthat allows for policies to be interpreted and enforced in a standard manner.XACML uses a Subject element (requesting entity), a Resource element (requested entity), and an Action element (types of access)BiometricsBiometric sverifies an individual’s identity by analyzing a unique personal attribute or behavior, which is one of the most effective and accurate methods of verifying identificationBiometrics is typically broken up into two different categories. The first isthe physiologicalThe second category of biometrics is known as behavioralWhen a biometric system rejects an authorized individual, it is called a Type I error (false rejection rate)When the system accepts impostors who should be rejected it is called a Type II error(false acceptance rate).Using the CER as an impartial judgment of a biometric system helps create standards by which products from differentvendors can be fairly judged and evaluated∙Fingerprint∙Palm Scan∙Hand Geometry∙Retina Scan∙Iris Scan∙Signature Dynamics∙Keystroke Dynamics∙Voice Print∙Facial Scan∙Hand Topography used in conjunction with hand geometry. Passwords∙Password ManagementIf passwords are properly generated,updated, and kept secret, they can provide effective security.If an attacker is after a password, she can try a few different techniques:Electronic monitoringAccess the password fileBrute force attacksDictionary attacksSocial engineeringRainbow table∙Password CheckersA tool that used for find out the weakness of a password is called password checker.∙Password Hashing and EncryptionSalts are random values addedto the encryption process to add more complexity and randomness ∙Password Aging∙Limit Logon AttemptsCognitive PasswordCognitive passwordsare fact- or opinion-based information used to verify an individual’s identity.One-Time PasswordOne-time password generating tokens come in two general types: synchronous and asynchronous.The token device is the most common implementation mechanism for OTP and generates the one-time password for the user to submit to an authentication server.∙The Token DeviceThe token device, or password generator, is usually a handhelddevice that has an LCD display and possibly a keypad.The token device presents the user with a list of characters to be entered as a password whenlogging on to a computer. Only the token device and authentication service know themeaning of these characters.∙SynchronousA synchronous token device synchronizes with the authenticationservice by using time or a counter as the core piece of the authentication process. If the synchronization is time-based, the token device and the authentication service musthold the same time within their internal clocks. The time value on the token device anda secret key are used to create the one-time password.If the token device and authentication service use counter-synchronization,the user will need to initiate the creation of the one-time password by pushing a button on thetoken device. This causes the token device and the authentication service to advance tothe next authentication value.In either time- or counter-based synchronization, the token device and authenticationservice must share the same secret base key used for encryption and decryption.∙AsynchronousA token device using an asynchronous token–generating methodemploys a challenge/response scheme to authenticate the user.Cryptographic KeysAnother way to prove one’s identity is to use a private key by generating a digital signatureA digital signature isa technology that uses a private key to encrypt a hash value (message digest). The act ofencrypting this hash value with a private key is called digitally signing a message. PassphraseMemory CardsThe main difference between memory cards and smart cards is their capacity to processinformation. A memory card holds information but cannot process information. A smart cardholds information and has the necessary hardware and software to actuallyprocess that information.Smart CardAsmart cardhas the capability of processing information because it has a microprocessor and integrated circuits incorporated into the card itselfTwo general categories of smart cards are the contact and the contactless typesThe contact smart card has a gold seal on the face of the card. When this card is fully inserted into a card reader, electrical fingers wipe against the card in the exact positionthat the chip contacts are located. This will supply power and data I/O to the chip forauthentication purposesThe contactless smart card has an antenna wire that surroundsthe perimeter of the card. When this card comes within an electromagnetic field of thereader, the antenna within the card generates enough energy to power the internal chipThis fact and the complexity of the smart token make these cardsresistant to reverse-engineering and tampering methods。
Cissp系列读书笔记之访问控制

Cissp读书笔记系列之访问控制(Srxh1314出品)目录3.2安全原则 (4)3.3身份标识、身份验证、授权与可问责性 (4)3.3.1 身份标识与身份验证 (5)3.3.2 身份管理(Identity Management,IdM) (6)3.3.2密码管理 (7)SSO单点登入 (7)SGML准通用置标语言 (8)xml可扩展标记语言 (8)SOAP即简单对象访问协议 (8)实现问责制的四个步骤: (8)生物验证技术 (9)3.3.3授权 (9)Kerberos (9)SESAME (10)单点登入技术示例 (10)3.4访问控制模型 (11)3.4.1 自主访问控制 (11)3.4.2 强制访问控制 (11)3.4.3 角色型访问控制 (11)格型访问控制(Lattice-Based Access Control) (12)3.5 访问控制方法和技术 (12)3.5.1 规则型访问控制 (12)3.5.2 限制性用户接口 (12)3.5.3 访问控制矩阵 (13)3.6 访问控制管理 (13)3.6.1 集中式访问控制管理 (13)3.6.2 分散式访问控制管理. (14)3.7 访问控制方法 (15)3.7.1 访问控制层 (15)3.7.2 行政管理性控制 (16)3.7.3 物理性控制 (16)3.7.4 技术性控制 (16)3.8 可问责性 (16)3.8.1 审计信息的检查 (18)3.8.2 保护审计数据和日志信息 (18)3.8.3 击键监控 (18)3.9 访问控制实践 (18)信息的未授权泄漏 (18)3.10 访问控制监控 (19)3.10.1 入侵检测.. (19)3.10.2 入侵防御系统 (20)3.11 对访问控制的几种威胁 (20)3.11.1 字典攻击. (20)3.11.2 蛮力攻击. (20)3.11.3 登录欺骗 (21)3.11.4 网络钓鱼 (21)3.11.5 威胁建模 (22)小结 (22)快速提示 (23)3.2安全原则各种安全控制中3个主要的安全原则是:可用性完整性机密性3.2.1 可用性信息、系统和资源必须在时间上能够保证用户使用,这样才不会影响其工作效率。
CISSP要点-第六章物理安全与环境安全

第六章物理安全与环境安全物理安全是对环境风险和不可预知的人类活动的第一道防线。
通过环境设计预防犯罪结合了与其有关的物理环境和社会问题,以减少犯罪,降低对犯罪的恐惧。
在决定为物理安全分配适当的预算经费的时候。
应该先确定设施中的财产的价值和设施本身的价值。
自动的环境控制措施有助于减少损害程度,并能够加快恢复进程。
而手工的方法耗费时间、容易出错,而且需要人不断地注意。
需要对物理建筑使用的材料及建筑结构成分的防护特性做出评估,并评估它的效用、成本以及给公司带来的收益。
一些物理安全措施可能和人身生命安全相矛盾,需要注意到这个问题,要意识到人的生命总是比保护设施或其中的设备更加重要。
在为设施寻找建筑地点的时候,需要考虑到当地的犯罪率,发生自然灾害的几率,与医院、警察局、消防局、机场和铁路的距离。
供暖通风和空调系统(HVAC)应该为公司维持适当的温度和湿度。
并提供闭环的空气流通系统,保证正压力及通风。
湿度过高会造成腐蚀,而湿度过低会造成静电。
灰尘和空气的污染物会给计算机硬件造成不利影响,因此它们应该被控制在一个可以接受的水平上。
管理方面的措施包括对紧急:事件处理规程的演习和练习、仿真试验、文件的归档、检查和报告、对员工的预先筛选、解雇后的处理规程、责任的委托.、岗位轮换、安全意识培训。
紧急事件处理规程文档需要能够很容易地拿到,并需要定期检查和更新。
接近式身份验证装置可以是用户激活的(意思是由用户主动完成认证)或是系统激活的(意思是由系统主动完成认证)。
无线电收发器是一种不需要用户采取行动的接近式认证装置,读卡器向该设备传送一个信号,而该设备返回一个认证码。
外部的栅栏可能会花费很多成本而且影响美观,但是能够使建筑周围不那么拥挤并有助于设施的访问控制。
内部的隔间不能够忽视天花板。
因为入侵者可以搬开天花板,越过隔间进入到设施中的关键部位。
入侵检测设备包括运动探测器、闭路电视系统、振动探测器和光束探测器。
入侵检测设备比较敏锐,安装和监视费用很高,需要人的响应,会受误报警的干扰。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
4.3.3授权;
1. 访问规则:基于各种角色、组、位置、时间的事物处理的类型实施
不同的访问准则
2. 默认拒绝访问
3. 知其所需:最下权限访问原则
4. 单点登录:SSO
5. Kerberos:MIT设计出来的单点登录系统,使用对称密钥算法实现
6. SESAME :对Kerberos做了改进,基于对称和非对称的算法实现
7. 安全域:可以基于网络设备、地址段、用户、进程等划分层次化的
域环境
8. 目录服务:轻量级目录服务器,不用知道具体的主机在什么地方,
通过LDAP是实现访问
9. 瘦客户机
4.4 访问控制模型
访问控制模型是规定主体如何访问客体的一个架构,它使用访问控制技术和安全机制来实现模型的规则和目标。
3种模型:
自主访问控制
强制访问控制
非自主访问控制(角色型访问控制)
1、DAC:Discreationary Access Control:
基于用户,使用ACL实现授权访问,操作系统使用的就是DAC 模型。
No Access:不允许访问;
Write(W):可写;
Read(R):可读;
Delese(D):可删除;
Execute(E):可执行;
Change(C):可读、可写、可删除、可执行但是不能改变文件的ACL和所有者;
Full Coutrl 任何权限。
2、MAC:Mandatory Access control:
主体通过标签访问客体,操作系统通过对比主体和客体的安全标签和知其所需的原则来做出决策。
SE Linux,Trusted Solaris
3、PBAC:Role-based Access Control=nondiscreatiionary Access
Control
使用集中管理的方式实现主客体之间的互访,可以基于公司的资源来进行授权。
DAC:用户的所有者决定虽能访问资源,ACL用于实施安全策略。
MAC:通过严格的标签机制实现访问,系统决定是否可以访问。
PBAC:访问策略基于主体角儿和功能位置
4.5 访问控制方法和技术
4.5.1 规则型访问控制:
通过特定的规则来规定主体和客体之间可以做什么,不可以做什么。
不一定是基于身份的,可以基于各种各种各样的复杂的东西定义访问规则。
4.5.2限制性用户端口:
不允许请求没写功能、信息或访问特定的系统资源,限制性用户接口能够限制用户的访问行为。
限制性接口主要有一下三种:菜单、外壳、数据库试图和物理限制接口
4.5.3 访问控制矩阵
通过矩阵的方式实现访问控制的管理,主体、客体、能执行的动作
4.6访问控制管理。
