iLTLChecker A probabilistic model checker for multiple DTMCs
写一篇是否想买一辆自动驾驶汽车的英语作文

写一篇是否想买一辆自动驾驶汽车的英语作文Title: Should I Buy a Self-Driving Car?With the rapid advancements in technology, self-driving cars have become a reality rather than just a futuristic concept. The idea of owning a car that can drive itself is both intriguing and intimidating. As a consumer, the decision to purchase aself-driving car is not an easy one. There are several factors to consider before making such a significant investment.One of the main advantages of self-driving cars is safety. Autonomous vehicles are equipped with sensors and cameras that can detect obstacles and react to potential dangers quicker than a human driver. This technology has the potential to reduce accidents caused by human error, such as distracted driving or impaired judgment. For individuals who prioritize safety above all else, a self-driving car may be an attractive option.Another benefit of self-driving cars is convenience. Imagine being able to relax or work during your daily commute instead of being stuck in traffic. Self-driving cars have the potential to improve traffic flow and reduce the time wasted in transit. They also eliminate the need for parking, as the car can drop you off at your destination and then find a parking spot on its own. Forbusy professionals or those with long commutes, this convenience factor can be a game-changer.However, there are also concerns and drawbacks associated with self-driving cars. One of the biggest issues is the potential for technical malfunctions. Like any technology, self-driving cars are not infallible and can experience glitches or errors that may compromise safety. There have been incidents where autonomous vehicles have crashed or failed to respond correctly to unexpected situations. For some consumers, this risk may outweigh the potential benefits of owning a self-driving car.Privacy is another major concern when it comes toself-driving cars. These vehicles are constantly collecting data on their surroundings and the behavior of the driver/passengers. This data is valuable to companies for improving their algorithms and providing personalized services, but it also raises questions about who has access to this information and how it is being used. As privacy concerns become more prevalent in our society, some individuals may be hesitant to embrace self-driving technology.Despite these concerns, the future of self-driving cars seems inevitable. Major car manufacturers and tech companies are investing heavily in autonomous vehicle technology, andgovernments are beginning to regulate and approve the use of self-driving cars on public roads. As this technology becomes more widespread, consumers will need to decide whether they are willing to embrace the future of transportation or stick with traditional vehicles.In conclusion, the decision to buy a self-driving car is a personal one that depends on individual preferences and priorities. Safety, convenience, and privacy are all factors that should be taken into consideration when weighing the pros and cons of autonomous vehicles. As the technology continues to evolve and improve, self-driving cars may become a common sight on our roads in the near future. Whether or not you choose to invest in this revolutionary technology is ultimately up to you.。
诺基亚电动自行车 Electropak 技术数据说明书
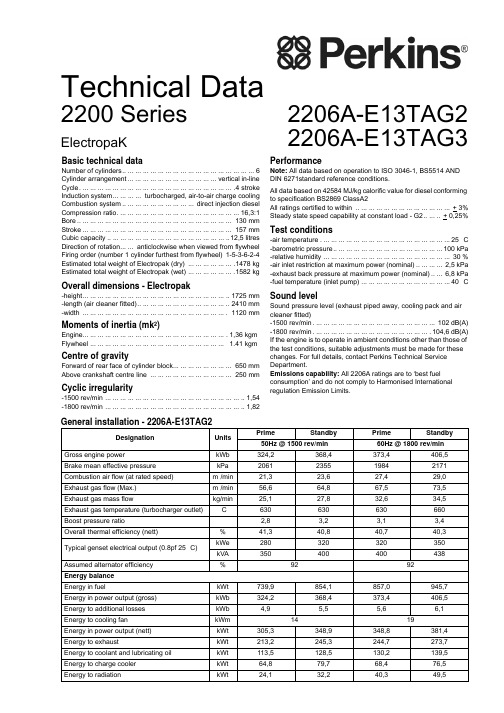
Technical DataBasic technical dataNumber of cylinders.. ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ...6 Cylinder arrangement... ... ... ... ... ... ... ... ... ... ... ...vertical in-line Cycle. ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... .4 stroke Induction system... ... ... ... turbocharged, air-to-air charge cooling Combustion system.. ... ... ... ... ... ... ... ... ... direct injection diesel Compression ratio. ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ...16,3:1Bore.. ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... 130 mm Stroke ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... 157 mm Cubic capacity .. ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ..12,5 litres Direction of rotation... ... anticlockwise when viewed from flywheel Firing order (number 1 cylinder furthest from flywheel)1-5-3-6-2-4Estimated total weight of Electropak (dry) ... ... ... ... ... ... .1478 kg Estimated total weight of Electropak (wet) ... ... ... ... ... ... .1582 kgOverall dimensions - Electropak-height... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ..1725 mm -length (air cleaner fitted).. ... ... ... ... ... ... ... ... ... ... ... ..2410 mm -width ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... . 1120 mmMoments of inertia (mk²)Engine... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... .1,36 kgm²Flywheel ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... 1.41 kgm²Centre of gravityForward of rear face of cylinder block... ... ... ... ... ... ... ... 650 mm Above crankshaft centre line ... ... ... ... ... ... ... ... ... ... ... 250 mmCyclic irregularity-1500 rev/min ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ..1,54-1800 rev/min ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ..1,82PerformanceNote:All data based on operation to ISO 3046-1, BS5514 AND DIN 6271standard reference conditions.All data based on 42584 MJ/kg calorific value for diesel conforming to specification BS2869 ClassA2All ratings certified to within .. ... ... ... ... ... ... ... ... ... ... ... ... + 3%Steady state speed capability at constant load - G2.. ... .. + 0,25%Test conditions-air temperature . ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ...25 °C -barometric pressure.. ... ... ... ... ... ... ... ... ... ... ... ... ... ...100 kPa -relative humidity ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... 30 %-air inlet restriction at maximum power (nominal).. ... ... ... 2,5 kPa -exhaust back pressure at maximum power (nominal).. ... 6,8 kPa -fuel temperature (inlet pump) ... ... ... ... ... ... ... ... ... ... ... ...40 °CSound levelSound pressure level (exhaust piped away, cooling pack and air cleaner fitted)-1500 rev/min. ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... 102 dB(A)-1800 rev/min. ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... .104,6 dB(A)If the engine is to operate in ambient conditions other than those of the test conditions, suitable adjustments must be made for these changes. For full details, contact Perkins Technical Service Department.Emissions capability: All 2206A ratings are to ‘best fuel consumption’ and do not comply to Harmonised International regulation Emission Limits.General installation DesignationUnits Prime Standby Prime Standby 50Hz @ 1500 rev/min60Hz @ 1800 rev/minGross engine powerkWb 324,2368,4373,4406,5Brake mean effective pressure kPa 2061235519842171Combustion air flow (at rated speed)m³/min 21,323,627,429,0Exhaust gas flow (Max.)m³/min 56,664,867,573,5Exhaust gas mass flowkg/min 25,127,832,634,5Exhaust gas temperature (turbocharger outlet)°C630630630660Boost pressure ratio2,83,23,13,4Overall thermal efficiency (nett)%41,340,840,740,3Typical genset electrical output (0.8pf 25 °C)kWe 280320320350kVA 350400400438Assumed alternator efficiency %9292Energy balance Energy in fuelkWt 739,9854,1857,0945,7Energy in power output (gross)kWb 324,2368,4373,4406,5Energy to additional losses kWb 4,95,55,66,1Energy to cooling fan kWm 1419Energy in power output (nett)kWt 305,3348,9348,8381,4Energy to exhaustkWt 213,2245,3244,7273,7Energy to coolant and lubricating oil kWt 113,5128,5130,2139,5Energy to charge cooler kWt 64,879,768,476,5Energy to radiationkWt24,132,240,349,5 - 2206A-E13TAG22200 Series2206A-E13TAG2 2206A-E13TAG3ElectropaKGeneral installationDesignation Units Prime Standby Prime Standby50Hz @ 1500 rev/min60Hz @ 1800 rev/min Gross engine power kWb368,4412,5373,4406,5 Brake mean effective pressure kPa2344263719842171 Combustion air flow (at rated speed)m³/min24,326,427,429,0 Exhaust gas flow (Max.)m³/min64,672,567,573,5 Exhaust gas mass flow kg/min28,130,932,634,5 Exhaust gas temperature (turbocharger outlet)°C630630660660 Boost pressure ratio3,23,53,13,4 Overall thermal efficiency (nett)%41,440,940,740,3Typical genset electrical output (0.8pf 25 °C)kWe320360320350 kVA400450400438Assumed alternator efficiency%9292Energy balanceEnergy in fuel kWt842,6958,2857,0945,7 Energy in power output (gross)kWb368,4412,5373,4406,5 Energy to additional losses kWb5,56,25,66,1 Energy to cooling fan kWm1419Energy in power output (nett)kWt348,9392,3348,8381,4 Energy to exhaust kWt252,6290,4244,7273,7 Energy to coolant and lubricating oil kWt127,3139,9130,2139,5 Energy to charge cooler kWt60,375,568,476,5 Energy to radiation kWt34,039,840,349,6 - 2206A-E13TAG3Rating definitionsPrime powerVariable load. Unlimited hours usage with an average load factor of 70% of the published Prime Power rating over each 24 hour period.A 10% overload is available for 1 hour in every 12 hours of operationStandby powerVariable load. Limited to 500 hours annual usage up to 300 hours of which may be continuous running, No overload is permittedCooling systemRadiatorFace area . ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ...1,238 m²Number of rows and materials . ... ... ... ... ... ... .1rows, aluminium Matrix density and material .. ... ... ... ..12 fins per inch, aluminium Width of matrix . ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... . 1048 mm Height of matrix ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... . 1100 mm Weight of radiator (dry). ... ... ... ... ... ... ... ... ... ... ... ... ... ..132 kg Pressure cap setting (min) ... ... ... ... ... ... ... ... ... ... ... ... ..70 kPa Charge coolerFace area.. ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ...1,006 m²Number of rows and materials . ... ... ... ... ... ... .1rows, aluminium Matrix density and material .. ... ... ... ..12 fins per inch, aluminium Width of matrix . ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... 915 mm Height of matrix ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... . 1100 mm Coolant pumpSpeed @ 1500 rev/min. ... ... ... ... ... ... ... ... ... ... ... 2056 rev/min Speed @ 1800 rev/min. ... ... ... ... ... ... ... ... ... ... ... 2468 rev/min Drive method. ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... .Gear FanDiameter ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... 927 mm Drive ratio.. ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ...0,92:1 Number of blades.. ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... .. 9 Material. ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... .composite Type.. ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... . pusher Cooling fan air flow @ 1500 rev/min. ... ... ... ... ... ... ...654 m³/min Cooling fan air flow @ 1800 rev/min. ... ... ... ... ... ... ...788 m³/min CoolantTotal system capacity ... ... ... ... ... ... ... ... ... ... ... ... ... . 51,4 litres Max. top tank temperature ... ... ... ... ... ... ... ... ... ... ... ... ..104 °C Temperature rise across engine... ... ... ... ... ... ... ... ... ... ... 10 °C Max. pressure in engine cooling circuit. ... ... ... ... ... ... ... ..70 kPa Max. permissible external system resistance ... ... ... ... ... ..30 kPa Max. static pressure head on pump.. ... ... ... ... ... ... ... ... ..30 kPa Coolant flow (min) against 30 kPa rstriction@ 1500 rev/min. ... ... ... ... ... ... ... ... ... ... ... ... ... ... .5,3 litres/sec @ 1800 rev/min. ... ... ... ... ... ... ... ... ... ... ... ... ... ... .6,7 litres/sec Thermostat operation range.. ... ... ... ... ... ... ... ... ... ... 87 to 98°C For details of recommended coolant specifications, refer to the Operation and Maintenance Manual for this engine model Duct allowanceDuct allowance 2206A-E13TAG2 - standbyMaximum additional retsriction (duct allowance) to cooling airflow and resultant minimum airflowEngine speedrev/minAmbient clear-ance inhibitedcoolant °CDuctallowancePam³/min 150059200563180059200716Duct allowance 2206A-E13TAG3 - standbyMaximum additional retsriction (duct allowance) to cooling airflow and resultant minimum airflowEngine speedrev/minAmbient clear-ance inhibitedcoolant °CDuctallowancePam³/min 150055200563180059200716Electrical system-type... ... ... ... ... ... ... ... ... ... ... ... ... ... ... .24 Volt negative earth Alternator type ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... .22SI -alternator voltage.. ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ..24V -alternator output ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ..70A Starter motor type.. ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ...39MT -starter motor voltage. ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ..24V -starter motor power... ... ... ... ... ... ... ... ... ... ... ... ... ... ... .7,8 kW Number of teeth on flywheel.. ... ... ... ... ... ... ... ... ... ... ... ... ..113 Number of teeth on starter pinion.. ... ... ... ... ... ... ... ... ... ... (11)Minimum cranking speed... ... ... ... ... ... ... ... ... ... ... 106 rev/min Starter solenoid maximum-pull-in current @ 0°C ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... 200A -hold-in current @ 0°C... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ..25A Cold start recommendations-5°C to -10°Coil... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ..SAE grade 15W40 Starter ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ...42MT Battery ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... 24 volts Max. breakaway current. ... ... ... ... ... ... ... ... ... ... ... ..1311 amps Cranking current ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... 588 amps Starting aids (ECM controlled)... ... ... ... ... ... ... ... ... ... ... ... none Min. mean cranking speed. ... ... ... ... ... ... ... ... ... ... .106 rev/min -11°C to -25°Coil... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... SAE grade 5W40 Starter ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ...42MT Battery ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... 24 volts Max. breakaway current. ... ... ... ... ... ... ... ... ... ... ... ..1585 amps Cranking current ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... 828 amps Starting aids (ECM controlled)... block heater 1,5kW (110V/240V) Min. mean cranking speed. ... ... ... ... ... ... ... ... ... ... .106 rev/min Notes:z Battery capacity is defined by the 20 hour ratez The oil specification should be for the minimum ambient temperature as the oil will not be warmed by the immersion heaterz Breakaway current is dependent on the battery capacity available. Cables should capable of handling transient current twice that of cranking current.Exhaust systemMaximum back pressure-1800 rev/min . ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... .10,0 kPa Exhaust outlet, internal diameter. ... ... ... ... ... ... ... ... ... . 123 mm Fuel systemInjection system... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ..MEUI Injector type. ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ..MEUI Governor type.. ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... electronic Governing conforms to ... ... ... ... ... ... ... ... .ISO 8528-5 Class G2 Injector pressure.. ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... .207 MPa Fuel lift pump-lift pump type.. ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... .gear driven -lift pump delivery @1500 rev/min... ... ... ... ... ... ... 480 litres/hour -lift pump delivery @1800 rev/min... ... ... ... ... ... ... 600 litres/hour -lift pump delivery pressure. ... ... ... ... ... ... ... ... ... ... ... ..621 kPa -max. suction head at pump inlet ... ... ... ... ... ... ... ... ... ... ... .3 m -max. static pressure head.. ... ... ... ... ... ... ... ... ... ... ... ... ... .4 m -max. fuel inlet temperature. ... ... ... ... ... ... ... ... ... ... ... ... ..55 °C -fuel filter spacing primary... ... ... ... ... ... ... ... ... ... ... .10 microns -fuel filter spacing secondary... ... ... ... ... ... ... ... ... ... ...2 microns Fuel specificationBS2869 Class A2 or BSEN590ASTM D975 Class 1D and class 2DNote:For further information on fuel specifications and restrictions, refer to the OMM, “Fluid Recommendations” for this engine model. Induction systemMaximum air intake restriction-clean filter... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ...2,5 kPa -dirty filter. ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ...6,4 kPa -air filter type ... ... ... ... ... ... ... . paper element - 15 inch diameterLubrication systemMaximum total system oil capacity ... ... ... ... ... ... ... ... ... .40 litres Minimum oil capacity in sump... ... ... ... ... ... ... ... ... ... ..32,5 litres Maximum oil capacity in sump.. ... ... ... ... ... ... ... ... ... ... .38 litres Maximum engine operating angles -front up, front down, right side, left side ... ... ... ... ... ... ... ... ... 7 °Lubricating oil-oil flow @ 1500 rev/min... ... ... ... ... ... ... ... ... ... ... 140 litres/min -oil flow @ 1800 rev/min... ... ... ... ... ... ... ... ... ... ... 172 litres/min -oil pressure at bearings @ 1500 rev/min. ... ... ... ... ... ... 310 kPa -oil pressure at bearings @ 1800 rev/min. ... ... ... ... ... ... 358 kPa -oil pressure at bearings (min).. ... ... ... ... ... ... ... ... ... ... 270 kPa -oil temperature (continuous operation) ... ... ... ... ... ... ... ..113 °C -oil consumption at full load as a % of fuel consumption.. ...0.15% Oil filter screen spacing. ... ... ... ... ... ... ... ... ... ... ... ... 30 microns Oil consumption as % of fuel consumption... ... ... ... ... ... ... ... 0,1 Sump drain plug tapping... ... ... ... ... ... ... ... ... ... ... ... .1 1/8 UNF Lubricating oil specification... ... ... ... ... ... API-CH4 - SAE15W-40 Recommended SAE viscosityEngine Oil ViscosityEMA LRG-1API CH-4 Viscosity GradeAmbient Temperature Minimum MaximumSAE 0W20-40 °C10 °CSAE 0W30-40 °C30 °CSAE 0W40-40 °C40 °CSAE 5W30-30 °C30 °CSAE 5W40-30 °C40 °CSAE 10W30-20 °C40 °CSAE 15W40-10 °C50 °C MountingsMaximum static bending moment at rear face of block. ...1356 Nm Fuel consumption2206A-E13TAG2 - 1500 rev/minLoad g/kWhr l/hr Standby19580 110% Prime power19577 100% Prime power19671 75% of Prime power19854 50% of Prime power203372206A-E13TAG3 - 1500 rev/minLoad g/kWhr l/hr Standby19490 110% Prime power19689 100% Prime power19781 75% of Prime power19962 50% of Prime power202422206A-E13TAG2 - 1800 rev/minLoad g/kWhr l/hr Standby19387 110% Prime power19588 100% Prime power19681 75% of Prime power19962 50% of Prime power205432206A-E13TAG3 - 1800 rev/minLoad g/kWhr l/hr Standby19387 110% Prime power19588 100% Prime power19681 75% of Prime power19962 50% of Prime power20543All fuel consumption figures are based on Nett powerAll information in the document is substantially correct at the time of printing but may be subsequently altered by the company.Distributed by2200 Series2206A-E13TAG22206A-E13TAG3Load acceptance TAG2 (cold) Initial load application: When engine reaches rated speed(15 seconds maximum after engine starts to crank)DescriptorUnits 50 Hz 60Hz % of prime power %6680Load (nett)kWm 184,8256Transient frequency deviation%<10<10Frequency recoverySeconds55Second load application: When engine reaches rated speed(5 seconds after initial load application)DescriptorUnits 50 Hz 60Hz % of prime power %7385Load (nett)kWm 204,4272Transient frequency deviation%<10<10Frequency recoverySeconds55TAG3 (cold) Initial load application: When engine reaches rated speed(15 seconds maximum after engine starts to crank)DescriptorUnits 50 Hz 60Hz % of prime power %5880Load (nett)kWm 185,6256Transient frequency deviation%<10<10Frequency recoverySeconds55Second load application: When engine reaches rated speed(5 seconds after initial load application)DescriptorUnits 50 Hz 60Hz % of prime power %6585Load (nett)kWm 208272Transient frequency deviation%<10<10Frequency recoverySeconds55The information shown above complies with the requirements of classification 3 and 4 of ISO 8528-12 and G2 operating limits stated in ISO 8528-5The above figures were obtained under the following test conditions:-minimum engine block temperature.. ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... . 45 °C -ambient temperature. ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ..15 °C -governing mode ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... isochronous -alternator efficiency... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... 92%-alternator inertia ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... 6,9 kgm²-under frequency roll off (UFRO) point set to. ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... 1 Hz below rated -UFRO rate set to... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... 2% voltage / 1% frequency LAM on/off.. ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ... ...off All tests were conducted using an engine which was installed and serviced to Perkins Engines Company Limited recommendations.Note:The general arrangement drawings shown in this data sheet are for guidance only. For installation purposes, latest versions should be requested from the Applications Dept., Perkins Engines Stafford, ST16 3UB United Kingdom.P u b l i c a t i o n N o . T P D 1687E 2. O c t o b e r 2008 P e r k i n s E n g i n e s C o m p a n y L i m i t e dPerkins Engines Company LimitedPeterborough PE1 5NA United Kingdom Telephone +44 (0) 1733 583000Fax +44 (0) 1733 。
福特猛禽皮卡英文菜单翻译中文菜单

福特猛禽皮卡英文菜单翻译中文菜单gauge mode (衡量模式) → gauge detail (衡量细节) → trans temp (变速箱的温度)trip(行程) → trip a 时间、每加仑耗油量、行驶的路程、平均每加化行驶的英里数→ trip bfuel economy (燃料经济) → fuel econ 燃油经济→ duration 持续的时间→ instant mpg 每加仑行驶的英里数truck apps (汽车应用) → off road 越野模式→ offroad camera 越野前摄像头→ information 信息→ 4*4 system 4*4模式→ advance trac 电子稳定系统→to active front camera→ eld (坡)→ hill descent contral 陡坡缓降控制系统trailer 拖车→ trailer disconnected 拖车断开→ change active trailer 改变拖车→ A →accumlated miles 累计英里→ gain:10.0 output 输出→ default trailer 默认拖车→ no active traile 没有拖车→ new traile 新的拖车→ connection checklist 链接清单→select type of trailer 选装拖车的类型→ conventional 传统→ fifth wheel 备用胎→ gooseneck 鹅颈→ delete trailer 删除拖车→ confirm delete 确认删除→ a are you sure?确认删除→ no stored traulers 没有储存拖车→ information screen 信息屏幕→ tow / hall 拖→ trailer brake controuer→ rename trailer 重命名拖车→ no stored trailer 没有存储拖车→ reset trailer mileage 重置拖车里程→default trailer 默认拖车settings(设置)→ driver assist 驾驶员辅助→trailer brake mode 拖车制动模式→ electric 电动→ elect over hydraulic 电气液压→ trailer sway control 挂车摆控制→ vehicle 车辆→ auto lamp pelay 灯光的延迟→10 second 延迟的时间→ DTE calculation 数据终端设备的计算→ normal history used 正常使用的历史→ towing history used 拖拽使用的历史→ easy entry exit 方便出入→ on 开 off 关→ lock 锁→ autolocka 自动锁,键盘锁→ autounlock 自动解锁→ unlocking 解锁→ one stage 第一阶段 ......→ menu control 菜单控制→ standard 标准→ mernory 内存→ oil life reset 油耗清零→ set to 100% 选装100%→ remote start 远程控制→climate control 气候控制→ front defrost 前方解冻→ rear defrost 后方解冻→ driver seat 司机座椅→ passenger seat 乘客座椅→ heater - a/c -auto 自动加热→ last setting 最后一项设置→ duration 持续时间→ quiet start 安静的开始→ wipers 雨刷→ courtesy wipe 前雨刷→ on / off→ mykey 钥匙→ create mykey 创建钥匙→hold ok to create mykey?→ language 语言→ english 英语→ francais 法语→ espcuol→ unit 单位→ english 英里→ metric 公里→ system reset 系统重置→ hold ok to reset system to factory default 恢复原厂设置。
让ModelCHECK规范您的设计

让ModelCHECK规范您的设计“ModelCHECK真的为我们解决了大问题,它规范了我们的设计,大幅提高了设计准确性,提高了设计效率。
使我们的设计更加完美。
可以说ModelCHECK是我们设计者的保护神”;这是某家电集团设计部X经理在一次总结会上的讲话。
但就在一个月前,他还经常为设计拖期和下游的模具部门和加工部门投诉而头疼。
这倒底是为什么呢?首先我们来了解一下该公司的设计情况。
该公司使用Pro/Engineer作为设计工具,使用IntraLink作为设计协同与数据管理系统。
设计的模式有两种:一、自行设计,即设计任务由本部门工程师完成。
二、外包设计,即将设计任务交给其他设计公司来做。
但下游的模具和加工仍然由本公司来完成。
由于设计任务比较繁重和不同专业的设计,该公司已经发展了许多优秀的设计公司。
以上两种模式在总设计中大致各占一半。
所有的设计数据都要进入IntraLink中进行管理。
接下来我们来看一下。
设计部遇到的主要问题。
1. 模型信息不全完整的设计,不仅仅包括产品的几何形状,还包括与之相关其他信息,如非尺寸参数(包括材料、规格、创建者、部门等等)、命名规则等信息。
,虽然为了规范设计,公司设定了各类设计模板。
尤其对于外包设计,都要求使用标准的模板进行设计。
但却没有办法保证所有的设计人员都是用了模板,即使使用了模板也无法保证他在设计过程中没有更改模板。
因此仍然需要花费大量的时间检查和修改模型。
而且一旦发现问题由于模型信息不全,很难直接找到创建者或者修改者。
从而浪费了大量的时间和精力。
正如X经理所说:“模型看起来都一样,但要检查和修改这些“一样的模型”,或者找到模型原来的设计者,甚至要花上比设计还要长的时间。
”2. 模型的质量无法保证虽然产品的设计周期越来越短,但通过努力大部分设计都能按期交付。
但是交付的设计模型,却不断接到模具部门和加工部门的投诉。
由于模型本身的质量不过关,导致后续的分模和加工编程无法进行。
Probabilistic model checking of an anonymity system

Probabilistic Model Checking ofan Anonymity SystemVitaly ShmatikovSRI International333Ravenswood AvenueMenlo Park,CA94025U.S.A.shmat@AbstractWe use the probabilistic model checker PRISM to analyze the Crowds system for anonymous Web browsing.This case study demonstrates howprobabilistic model checking techniques can be used to formally analyze se-curity properties of a peer-to-peer group communication system based onrandom message routing among members.The behavior of group mem-bers and the adversary is modeled as a discrete-time Markov chain,and thedesired security properties are expressed as PCTL formulas.The PRISMmodel checker is used to perform automated analysis of the system and ver-ify anonymity guarantees it provides.Our main result is a demonstration ofhow certain forms of probabilistic anonymity degrade when group size in-creases or random routing paths are rebuilt,assuming that the corrupt groupmembers are able to identify and/or correlate multiple routing paths originat-ing from the same sender.1IntroductionFormal analysis of security protocols is a well-establishedfield.Model checking and theorem proving techniques[Low96,MMS97,Pau98,CJM00]have been ex-tensively used to analyze secrecy,authentication and other security properties ofprotocols and systems that employ cryptographic primitives such as public-key en-cryption,digital signatures,etc.Typically,the protocol is modeled at a highly ab-stract level and the underlying cryptographic primitives are treated as secure“black boxes”to simplify the model.This approach discovers attacks that would succeed even if all cryptographic functions were perfectly secure.Conventional formal analysis of security is mainly concerned with security against the so called Dolev-Yao attacks,following[DY83].A Dolev-Yao attacker is a non-deterministic process that has complete control over the communication net-work and can perform any combination of a given set of attacker operations,such as intercepting any message,splitting messages into parts,decrypting if it knows the correct decryption key,assembling fragments of messages into new messages and replaying them out of context,etc.Many proposed systems for anonymous communication aim to provide strong, non-probabilistic anonymity guarantees.This includes proxy-based approaches to anonymity such as the Anonymizer[Ano],which hide the sender’s identity for each message by forwarding all communication through a special server,and MIX-based anonymity systems[Cha81]that blend communication between dif-ferent senders and recipients,thus preventing a global eavesdropper from linking sender-recipient pairs.Non-probabilistic anonymity systems are amenable to for-mal analysis in the same non-deterministic Dolev-Yao model as used for verifica-tion of secrecy and authentication protocols.Existing techniques for the formal analysis of anonymity in the non-deterministic model include traditional process formalisms such as CSP[SS96]and a special-purpose logic of knowledge[SS99].In this paper,we use probabilistic model checking to analyze anonymity prop-erties of a gossip-based system.Such systems fundamentally rely on probabilistic message routing to guarantee anonymity.The main representative of this class of anonymity systems is Crowds[RR98].Instead of protecting the user’s identity against a global eavesdropper,Crowds provides protection against collaborating local eavesdroppers.All communication is routed randomly through a group of peers,so that even if some of the group members collaborate and share collected lo-cal information with the adversary,the latter is not likely to distinguish true senders of the observed messages from randomly selected forwarders.Conventional formal analysis techniques that assume a non-deterministic at-tacker in full control of the communication channels are not applicable in this case. Security properties of gossip-based systems depend solely on the probabilistic be-havior of protocol participants,and can be formally expressed only in terms of relative probabilities of certain observations by the adversary.The system must be modeled as a probabilistic process in order to capture its properties faithfully.Using the analysis technique developed in this paper—namely,formalization of the system as a discrete-time Markov chain and probabilistic model checking of2this chain with PRISM—we uncovered two subtle properties of Crowds that causedegradation of the level of anonymity provided by the system to the users.First,if corrupt group members are able to detect that messages along different routingpaths originate from the same(unknown)sender,the probability of identifyingthat sender increases as the number of observed paths grows(the number of pathsmust grow with time since paths are rebuilt when crowd membership changes).Second,the confidence of the corrupt members that they detected the correct senderincreases with the size of the group.Thefirstflaw was reported independently byMalkhi[Mal01]and Wright et al.[W ALS02],while the second,to the best ofour knowledge,was reported for thefirst time in the conference version of thispaper[Shm02].In contrast to the analysis by Wright et al.that relies on manualprobability calculations,we discovered both potential vulnerabilities of Crowds byautomated probabilistic model checking.Previous research on probabilistic formal models for security focused on(i)probabilistic characterization of non-interference[Gra92,SG95,VS98],and(ii)process formalisms that aim to faithfully model probabilistic properties of crypto-graphic primitives[LMMS99,Can00].This paper attempts to directly model andanalyze security properties based on discrete probabilities,as opposed to asymp-totic probabilities in the conventional cryptographic sense.Our analysis methodis applicable to other probabilistic anonymity systems such as Freenet[CSWH01]and onion routing[SGR97].Note that the potential vulnerabilities we discovered inthe formal model of Crowds may not manifest themselves in the implementationsof Crowds or other,similar systems that take measures to prevent corrupt routersfrom correlating multiple paths originating from the same sender.2Markov Chain Model CheckingWe model the probabilistic behavior of a peer-to-peer communication system as adiscrete-time Markov chain(DTMC),which is a standard approach in probabilisticverification[LS82,HS84,Var85,HJ94].Formally,a Markov chain can be definedas consisting in afinite set of states,the initial state,the transition relation such that,and a labeling functionfrom states to afinite set of propositions.In our model,the states of the Markov chain will represent different stages ofrouting path construction.As usual,a state is defined by the values of all systemvariables.For each state,the corresponding row of the transition matrix de-fines the probability distributions which govern the behavior of group members once the system reaches that state.32.1Overview of PCTLWe use the temporal probabilistic logic PCTL[HJ94]to formally specify properties of the system to be checked.PCTL can express properties of the form“under any scheduling of processes,the probability that event occurs is at least.”First,define state formulas inductively as follows:where atomic propositions are predicates over state variables.State formulas of the form are explained below.Define path formulas as follows:Unlike state formulas,which are simplyfirst-order propositions over a single state,path formulas represent properties of a chain of states(here path refers to a sequence of state space transitions rather than a routing path in the Crowds speci-fication).In particular,is true iff is true for every state in the chain;is true iff is true for all states in the chain until becomes true,and is true for all subsequent states;is true iff and there are no more than states before becomes true.For any state and path formula,is a state formula which is true iff state space paths starting from satisfy path formula with probability greater than.For the purposes of this paper,we will be interested in formulas of the form ,evaluated in the initial state.Here specifies a system con-figuration of interest,typically representing a particular observation by the adver-sary that satisfies the definition of a successful attack on the protocol.Property is a liveness property:it holds in iff will eventually hold with greater than probability.For instance,if is a state variable represent-ing the number of times one of the corrupt members received a message from the honest member no.,then holds in iff the prob-ability of corrupt members eventually observing member no.twice or more is greater than.Expressing properties of the system in PCTL allows us to reason formally about the probability of corrupt group members collecting enough evidence to success-fully attack anonymity.We use model checking techniques developed for verifica-tion of discrete-time Markov chains to compute this probability automatically.42.2PRISM model checkerThe automated analyses described in this paper were performed using PRISM,aprobabilistic model checker developed by Kwiatkowska et al.[KNP01].The toolsupports both discrete-and continuous-time Markov chains,and Markov decisionprocesses.As described in section4,we model probabilistic peer-to-peer com-munication systems such as Crowds simply as discrete-time Markov chains,andformalize their properties in PCTL.The behavior of the system processes is specified using a simple module-basedlanguage inspired by Reactive Modules[AH96].State variables are declared in thestandard way.For example,the following declarationdeliver:bool init false;declares a boolean state variable deliver,initialized to false,while the followingdeclarationconst TotalRuns=4;...observe1:[0..TotalRuns]init0;declares a constant TotalRuns equal to,and then an integer array of size,indexed from to TotalRuns,with all elements initialized to.State transition rules are specified using guarded commands of the form[]<guard>-><command>;where<guard>is a predicate over system variables,and<command>is the tran-sition executed by the system if the guard condition evaluates to mandoften has the form<expression>...<expression>, which means that in the next state(i.e.,that obtained after the transition has beenexecuted),state variable is assigned the result of evaluating arithmetic expres-sion<expression>If the transition must be chosen probabilistically,the discrete probability dis-tribution is specified as[]<guard>-><prob1>:<command1>+...+<probN>:<commandN>;Transition represented by command is executed with probability prob,and prob.Security properties to be checked are stated as PCTL formulas (see section2.1).5Given a formal system specification,PRISM constructs the Markov chain and determines the set of reachable states,using MTBDDs and BDDs,respectively. Model checking a PCTL formula reduces to a combination of reachability-based computation and solving a system of linear equations to determine the probability of satisfying the formula in each reachable state.The model checking algorithms employed by PRISM include[BdA95,BK98,Bai98].More details about the im-plementation and operation of PRISM can be found at http://www.cs.bham. /˜dxp/prism/and in[KNP01].Since PRISM only supports model checking offinite DTMC,in our case study of Crowds we only analyze anonymity properties offinite instances of the system. By changing parameters of the model,we demonstrate how anonymity properties evolve with changes in the system configuration.Wright et al.[W ALS02]investi-gated related properties of the Crowds system in the general case,but they do not rely on tool support and their analyses are manual rather than automated.3Crowds Anonymity SystemProviding an anonymous communication service on the Internet is a challenging task.While conventional security mechanisms such as encryption can be used to protect the content of messages and transactions,eavesdroppers can still observe the IP addresses of communicating computers,timing and frequency of communi-cation,etc.A Web server can trace the source of the incoming connection,further compromising anonymity.The Crowds system was developed by Reiter and Ru-bin[RR98]for protecting users’anonymity on the Web.The main idea behind gossip-based approaches to anonymity such as Crowds is to hide each user’s communications by routing them randomly within a crowd of similar users.Even if an eavesdropper observes a message being sent by a particular user,it can never be sure whether the user is the actual sender,or is simply routing another user’s message.3.1Path setup protocolA crowd is a collection of users,each of whom is running a special process called a jondo which acts as the user’s proxy.Some of the jondos may be corrupt and/or controlled by the adversary.Corrupt jondos may collaborate and share their obser-vations in an attempt to compromise the honest users’anonymity.Note,however, that all observations by corrupt group members are local.Each corrupt member may observe messages sent to it,but not messages transmitted on the links be-tween honest jondos.An honest crowd member has no way of determining whether6a particular jondo is honest or corrupt.The parameters of the system are the total number of members,the number of corrupt members,and the forwarding probability which is explained below.To participate in communication,all jondos must register with a special server which maintains membership information.Therefore,every member of the crowd knows identities of all other members.As part of the join procedure,the members establish pairwise encryption keys which are used to encrypt pairwise communi-cation,so the contents of the messages are secret from an external eavesdropper.Anonymity guarantees provided by Crowds are based on the path setup pro-tocol,which is described in the rest of this section.The path setup protocol is executed each time one of the crowd members wants to establish an anonymous connection to a Web server.Once a routing path through the crowd is established, all subsequent communication between the member and the Web server is routed along it.We will call one run of the path setup protocol a session.When crowd membership changes,the existing paths must be scrapped and a new protocol ses-sion must be executed in order to create a new random routing path through the crowd to the destination.Therefore,we’ll use terms path reformulation and proto-col session interchangeably.When a user wants to establish a connection with a Web server,its browser sends a request to the jondo running locally on her computer(we will call this jondo the initiator).Each request contains information about the intended desti-nation.Since the objective of Crowds is to protect the sender’s identity,it is not problematic that a corrupt router can learn the recipient’s identity.The initiator starts the process of creating a random path to the destination as follows: The initiator selects a crowd member at random(possibly itself),and for-wards the request to it,encrypted by the corresponding pairwise key.We’ll call the selected member the forwarder.The forwarderflips a biased coin.With probability,it delivers the request directly to the destination.With probability,it selects a crowd member at random(possibly itself)as the next forwarder in the path,and forwards the request to it,re-encrypted with the appropriate pairwise key.The next forwarder then repeats this step.Each forwarder maintains an identifier for the created path.If the same jondo appears in different positions on the same path,identifiers are different to avoid infinite loops.Each subsequent message from the initiator to the destination is routed along this path,i.e.,the paths are static—once established,they are not altered often.This is necessary to hinder corrupt members from linking multiple7paths originating from the same initiator,and using this information to compromise the initiator’s anonymity as described in section3.2.3.3.2Anonymity properties of CrowdsThe Crowds paper[RR98]describes several degrees of anonymity that may be provided by a communication system.Without using anonymizing techniques, none of the following properties are guaranteed on the Web since browser requests contain information about their source and destination in the clear.Beyond suspicion Even if the adversary can see evidence of a sent message,the real sender appears to be no more likely to have originated it than any other potential sender in the system.Probable innocence The real sender appears no more likely to be the originator of the message than to not be the originator,i.e.,the probability that the adversary observes the real sender as the source of the message is less thanupper bound on the probability of detection.If the sender is observed by the adversary,she can then plausibly argue that she has been routing someone else’s messages.The Crowds paper focuses on providing anonymity against local,possibly co-operating eavesdroppers,who can share their observations of communication in which they are involved as forwarders,but cannot observe communication involv-ing only honest members.We also limit our analysis to this case.3.2.1Anonymity for a single routeIt is proved in[RR98]that,for any given routing path,the path initiator in a crowd of members with forwarding probability has probable innocence against collaborating crowd members if the following inequality holds:(1)More formally,let be the event that at least one of the corrupt crowd members is selected for the path,and be the event that the path initiator appears in8the path immediately before a corrupt crowd member(i.e.,the adversary observes the real sender as the source of the messages routed along the path).Condition 1guarantees thatproving that,given multiple linked paths,the initiator appears more often as a sus-pect than a random crowd member.The automated analysis described in section6.1 confirms and quantifies this result.(The technical results of[Shm02]on which this paper is based had been developed independently of[Mal01]and[W ALS02],be-fore the latter was published).In general,[Mal01]and[W ALS02]conjecture that there can be no reliable anonymity method for peer-to-peer communication if in order to start a new communication session,the initiator must originate thefirst connection before any processing of the session commences.This implies that anonymity is impossible in a gossip-based system with corrupt routers in the ab-sence of decoy traffic.In section6.3,we show that,for any given number of observed paths,the adversary’s confidence in its observations increases with the size of the crowd.This result contradicts the intuitive notion that bigger crowds provide better anonymity guarantees.It was discovered by automated analysis.4Formal Model of CrowdsIn this section,we describe our probabilistic formal model of the Crowds system. Since there is no non-determinism in the protocol specification(see section3.1), the model is a simple discrete-time Markov chain as opposed to a Markov deci-sion process.In addition to modeling the behavior of the honest crowd members, we also formalize the adversary.The protocol does not aim to provide anonymity against global eavesdroppers.Therefore,it is sufficient to model the adversary as a coalition of corrupt crowd members who only have access to local communication channels,i.e.,they can only make observations about a path if one of them is se-lected as a forwarder.By the same token,it is not necessary to model cryptographic functions,since corrupt members know the keys used to encrypt peer-to-peer links in which they are one of the endpoints,and have no access to links that involve only honest members.The modeling technique presented in this section is applicable with minor mod-ifications to any probabilistic routing system.In each state of routing path construc-tion,the discrete probability distribution given by the protocol specification is used directly to define the probabilistic transition rule for choosing the next forwarder on the path,if any.If the protocol prescribes an upper bound on the length of the path(e.g.,Freenet[CSWH01]),the bound can be introduced as a system parameter as described in section4.2.3,with the corresponding increase in the size of the state space but no conceptual problems.Probabilistic model checking can then be used to check the validity of PCTL formulas representing properties of the system.In the general case,forwarder selection may be governed by non-deterministic10runCount goodbad lastSeen observelaunchnewstartrundeliver recordLast badObserve4.2Model of honest members4.2.1InitiationPath construction is initiated as follows(syntax of PRISM is described in section 2.2):[]launch->runCount’=TotalRuns&new’=true&launch’=false;[]new&(runCount>0)->(runCount’=runCount-1)&new’=false&start’=true;[]start->lastSeen’=0&deliver’=false&run’=true&start’=false;4.2.2Forwarder selectionThe initiator(i.e.,thefirst crowd member on the path,the one whose identity must be protected)randomly chooses thefirst forwarder from among all group mem-bers.We assume that all group members have an equal probability of being chosen, but the technique can support any discrete probability distribution for choosing for-warders.Forwarder selection is a single step of the protocol,but we model it as two probabilistic state transitions.Thefirst determines whether the selected forwarder is honest or corrupt,the second determines the forwarder’s identity.The randomly selected forwarder is corrupt with probability badCbe next on the path.Any of the honest crowd members can be selected as the forwarder with equal probability.To illustrate,for a crowd with10honest members,the following transition models the second step of forwarder selection: []recordLast&CrowdSize=10->0.1:lastSeen’=0&run’=true&recordLast’=false+0.1:lastSeen’=1&run’=true&recordLast’=false+...0.1:lastSeen’=9&run’=true&recordLast’=false;According to the protocol,each honest crowd member must decide whether to continue building the path byflipping a biased coin.With probability,the forwarder selection transition is enabled again and path construction continues, and with probability the path is terminated at the current forwarder,and all requests arriving from the initiator along the path will be delivered directly to the recipient.[](good&!deliver&run)->//Continue path constructionPF:good’=false+//Terminate path constructionnotPF:deliver’=true;The specification of the Crowds system imposes no upper bound on the length of the path.Moreover,the forwarders are not permitted to know their relative position on the path.Note,however,that the amount of information about the initiator that can be extracted by the adversary from any path,or anyfinite number of paths,isfinite(see sections4.3and4.5).In systems such as Freenet[CSWH01],requests have a hops-to-live counter to prevent infinite paths,except with very small probability.To model this counter,we may introduce an additional state variable pIndex that keeps track of the length of the path constructed so far.The path construction transition is then coded as follows://Example with Hops-To-Live//(NOT CROWDS)////Forward with prob.PF,else deliver13[](good&!deliver&run&pIndex<MaxPath)->PF:good’=false&pIndex’=pIndex+1+notPF:deliver’=true;//Terminate if reached MaxPath,//but sometimes not//(to confuse adversary)[](good&!deliver&run&pIndex=MaxPath)->smallP:good’=false+largeP:deliver’=true;Introduction of pIndex obviously results in exponential state space explosion, decreasing the maximum system size for which model checking is feasible.4.2.4Transition matrix for honest membersTo summarize the state space of the discrete-time Markov chain representing cor-rect behavior of protocol participants(i.e.,the state space induced by the abovetransitions),let be the state in which links of the th routing path from the initiator have already been constructed,and assume that are the honestforwarders selected for the path.Let be the state in which path constructionhas terminated with as thefinal path,and let be an auxiliary state. Then,given the set of honest crowd members s.t.,the transi-tion matrix is such that,,(see section4.2.2),i.e.,the probability of selecting the adversary is equal to the cumulative probability of selecting some corrupt member.14This abstraction does not limit the class of attacks that can be discovered using the approach proposed in this paper.Any attack found in the model where indi-vidual corrupt members are kept separate will be found in the model where their capabilities are combined in a single worst-case adversary.The reason for this is that every observation made by one of the corrupt members in the model with separate corrupt members will be made by the adversary in the model where their capabilities are combined.The amount of information available to the worst-case adversary and,consequently,the inferences that can be made from it are at least as large as those available to any individual corrupt member or a subset thereof.In the adversary model of[RR98],each corrupt member can only observe its local network.Therefore,it only learns the identity of the crowd member imme-diately preceding it on the path.We model this by having the corrupt member read the value of the lastSeen variable,and record its observations.This cor-responds to reading the source IP address of the messages arriving along the path. For example,for a crowd of size10,the transition is as follows:[]lastSeen=0&badObserve->observe0’=observe0+1&deliver’=true&run’=true&badObserve’=false;...[]lastSeen=9&badObserve->observe9’=observe9+1&deliver’=true&run’=true&badObserve’=false;The counters observe are persistent,i.e.,they are not reset for each session of the path setup protocol.This allows the adversary to accumulate observations over several path reformulations.We assume that the adversary can detect when two paths originate from the same member whose identity is unknown(see sec-tion3.2.2).The adversary is only interested in learning the identity of thefirst crowd mem-ber in the path.Continuing path construction after one of the corrupt members has been selected as a forwarder does not provide the adversary with any new infor-mation.This is a very important property since it helps keep the model of the adversaryfinite.Even though there is no bound on the length of the path,at most one observation per path is useful to the adversary.To simplify the model,we as-sume that the path terminates as soon as it reaches a corrupt member(modeled by deliver’=true in the transition above).This is done to shorten the average path length without decreasing the power of the adversary.15Each forwarder is supposed toflip a biased coin to decide whether to terminate the path,but the coinflips are local to the forwarder and cannot be observed by other members.Therefore,honest members cannot detect without cooperation that corrupt members always terminate paths.In any case,corrupt members can make their observable behavior indistinguishable from that of the honest members by continuing the path with probability as described in section4.2.3,even though this yields no additional information to the adversary.4.4Multiple pathsThe discrete-time Markov chain defined in sections4.2and4.3models construc-tion of a single path through the crowd.As explained in section3.2.2,paths have to be reformulated periodically.The decision to rebuild the path is typically made according to a pre-determined schedule,e.g.,hourly,daily,or once enough new members have asked to join the crowd.For the purposes of our analysis,we sim-ply assume that paths are reformulated somefinite number of times(determined by the system parameter=TotalRuns).We analyze anonymity properties provided by Crowds after successive path reformulations by considering the state space produced by successive execu-tions of the path construction protocol described in section4.2.As explained in section4.3,the adversary is permitted to combine its observations of some or all of the paths that have been constructed(the adversary only observes the paths for which some corrupt member was selected as one of the forwarders).The adversary may then use this information to infer the path initiator’s identity.Because for-warder selection is probabilistic,the adversary’s ability to collect enough informa-tion to successfully identify the initiator can only be characterized probabilistically, as explained in section5.4.5Finiteness of the adversary’s state spaceThe state space of the honest members defined by the transition matrix of sec-tion4.2.4is infinite since there is no a priori upper bound on the length of each path.Corrupt members,however,even if they collaborate,can make at most one observation per path,as explained in section4.3.As long as the number of path reformulations is bounded(see section4.4),only afinite number of paths will be constructed and the adversary will be able to make only afinite number of observa-tions.Therefore,the adversary only needsfinite memory and the adversary’s state space isfinite.In general,anonymity is violated if the adversary has a high probability of making a certain observation(see section5).Tofind out whether Crowds satisfies16。
bilArabi数字组件用户说明书

Our assessmenttheir Arabic language proficiency level and rate ofprogress through ongoing formative assessmentdelivered via the bilArabi digital component. This isachieved through enjoyable and engaging onlineactivities and quizzes, which extend learning beyondthe classroom and reinforce Arabic languagelearning.Teachers can also view detailed assessment data onour bilArabi digital platform. They can then use thisintelligence to inform the development ofdifferentiated teaching and learning strategies, todrive student performance and overall confidencecommunicating in Arabic.Teachers have the tools at their fingertips tomaximise student success in national exams throughregular and personalised feedback and targetedsupport for improvement, facilitating a smoothprogression to higher-level study.Data-driven instructionThe bilArabi digital component hosts aGradebook that teachers can use for ongoingformative assessment and to view performancedata. Performance data analysis can then be usedto differentiate learning in the classroom andimprove results.Write-in student’s bookLevels 1-9Native and non-native strandseBookTeacher GuideDigital LearningProfessional Development TrainingKey component overviewKey course components include:AssessmentWe hope you and your studentswill love Arabic language learningwith bilArabi from Pearson!Teacher supportTeachers are supported from the outset with in-depth implementationtraining, and ongoing professional development delivered byPearson experts.bilArabi’s Teacher’s Book with detailed lesson plans and links tocorresponding student book pages help educators to plan and deliverlessons with confidence and ease.Student supportChildren have access to both a print and digital Student’sBook, which contain ‘parent engagement’ sections. Thiseffectively extends learning beyond the classroom andactively involves parents in the child’s Arabic languagelearning development.To find out more,email:********************************Our supportSupport at each step of the learning journeyWe appreciate that bilArabi offers a new and unique way of teaching andlearning Arabic in the classroom, with an inquiry-based, student-centeredapproach. So we’ve worked hard to create a truly blended learning programmethat offers support for teachers and students at each stage.Pearson PresentsFor the love of ArabicIntroducing bilArabiBringing Arabic language learning to life!A program based on modern learning standards, enriched with children's literature, and a catalyst for higher thinking skills.BilArabi was developed to make learning Arabic fun, purposeful, effective, and scalable to all levels.The curriculum presents the Arabic language in a modern, contemporary way and applies best practice pedagogy harnessed from latest findings in the fields of education, language learning, linguistics and educational psychology.We believe that learning Arabic should be fun, easy, and meaningful for the learner, the teacher and the parents as well. We believe that in Arabic there is beauty, depth, and flexibility that can accommodate and channel every new knowledge, science and idea in this world. We believe that we need to show our children all that is possible in Arabic and we believe that bilArabi is the best tool to do so.Blended-LearningChildren can access their Student eBook through the bilArabi digital component, and can also take part in online practice activities, such as quizzes to test their Arabic language knowledge and understanding.As such, the course truly offers a blended-learning approach suits both traditional and more technologically advanced schools. It helps teachers to support students to achieve their potential and seamlessly progress to the next level of learning, through the effective integration of print and digital content and activities.Why bilArabi?••in children.• and techniques in the classrooms.••Our standardsOur contentLiterature-basedA mix of photos and illustrations, plus interactive videos engages students in ArabicMore than just an Arabic language learning programmeWith a comprehensive range of informational and literature reading texts, children are fully immersed in reading and writing from the beginning of the course, helping them to become better readers, writers and thinkers. Engaging stories completely engage students in the Arabic language, accelerating language proficiency and progress.bilArabi has a vibrant look and feel that uses a blend of illustrations and real-life photos to engage students with the course content. More photos are used in the upper grades to fit with the needs of these age groups.The design of the programme provides a seamless linkbetween the print and digital components, helping students focus on learning activities and teachers deliver lessons with ease; improving the overall learning and teaching experience. It also includes links to a range of Arabic songs, games and stories designed to support language acquisition, developed by our Partner Makooky, a well-known quality provider of edutainment for children in the Middle East.bilArabi is a rich curriculum that offers more than just language learning, with content that aims to develop a passion for Arabic history and culture, and inspire trust in a bright future for the language. The course also includes 21st Century Skills to prepare students for high-stakes exams and the workplaceage acquisition, where learning t schools and countries.。
英语单词的重音规则

英语单词的重音规则 LELE was finally revised on the morning of December 16, 2020七大特殊单词重音规则1. 英语中派生词的重音和词根重音一致。
派生词就是一些有同样词根的词。
比如: act, active, actively com'pare com'parison2. 带有下列后缀的词:-ary, -ery, -ory, -ism, -ist, -mony, -ment, -ary等,重音通常在第一个音节上。
例如:customary scientist slavery factory realism3. 带下列前缀的词:a-, ab-, ac-, ad-, al-, be-, con-, de-, dis-, em-, en-, in-, mis-, re-, trans-, un-重音通常在第二音节上。
例如: a'bout ab'duce ac'cede ad'mire be'long con'sult de'tect dis'like4. 带下列后缀的词:-aim, -ain, -cur, -eem, -duce, -ere, -firm, -gn, -oin, -oke, -ose, -pt, -rce, -self, -ume重音通常在第二音节。
contain occur sincere design confirm5. 带下列后缀的词:-ade, -ain, -ee, -eer, -esque, -ette, -ique, -ine, -oon重音通常在最后一个音节。
这些词一般都是从法语中借来的词。
例如: emplo'yee an'tique maga'zine ci'gar volun'teer gaso'line6. 带下列后缀的词:-eous, -ial, -ian, -ic, -ics, -ient, -ion, -ious, -ish, -it, -liar, -sive, -tal, -uous重音通常在倒数第二音节上。
Save Cart by Mozaca 用户指南说明书

Multiple Save Cart Pro by MozacaOverview:Save Cart by Mozaca apps brings your customer’s shopping experience to the next level. While standard checkout’s main purpose is to purchase items with one session flow, Save Cart by Mozaca apps provides your customer’s possibilities save your cart for later or create multiplied cards into the menu“My Saved Carts” for keeping full control on multiple purchases. This feature helps manage multiple shopping cards by giving them unique names. It also provides information about the number of items, total price, date created for each cart. You can also preview each cart with items without leaving the current cart and print the contained cart out. Customers can simply go to the “my save cart” from my account options or from the customer profile drop-down on the top right corner for managing saved cards. For creating a new cart “save cart”buttons located on the mini cart pop-up and on the shopping cart itself. We also understand that you have custom CSS on your end so we are keeping as little as possible styling with this extension so it can be simply adapted for your store. Features:●save multiple carts●customers can print carts●manage all saved carts customer account●replace a current cart with a saved cartHow It Works:Simply enable the extension from the store backend and your customers will have the possibility to save their shopping carts.Live Extension Demo:Click hereHave a question or technical support with our Extension?Please reach us by email.Locations on website: 1.- Shopping Cart2.- Account Options3.- Profile Drop-DownInstallation:1.Unpack the .zip file you’ve downloaded.2.Connect to the server where the website source folder is located with FTPor SFTP client.3.Go to the Magento root folder.4.Create folders Mozaca/SaveCart in<Magento root folder>/app/code/5.Copy extension files to folder:<Magento root folder>/app/code/Mozaca/SaveCart6.Run command from the Magento root folderphp bin/magento setup:upgradephp bin/magento setup:static-content:deployConfigurations:There is no configuration in the control panel.。
沃尔沃英文缩写含义清单-20150604

第 1 页,共 76 页
AME AMEC AMK AMP AMPPE AMS AMTD ANC ANOM ANOVA ANS ANSI ANX AO AOC AOS AP APD APEAL APEL APG API APP APQP APR APS AQL AQS AR ARB ARL ARM ARO ARP ARPA ARS AS ASA ASAP ASC ASDM ASESO ASIC ASIL ASM ASN ASP ASR ASSY ASTA ASTM AT ATACQ ATC ATEO ATI ATM ATP
Advanced Manufacturing Engineering After Market Executive Committee W ork Environment Committee After Market Program After Market Pre-Program Engineering Application Management Services Advanced Manufacturing Technology and Development Active Noise Cancellation Analysis Of Means Analysis Of Variation Alarm Notification System American National Standards Institute Automotive Network Exchange Application Owner Active On-demand Coupling A.Attribute utomotivePrototype Occupancy Sensor Process 3. Accelerator 1 2. Annual Pedal Availability Performance Data Automotive Performance Execution & Layout Study Assessment for Prior Experience & Learning Arizona Proving Ground Application Program Interface Availability Performance Program Advanced Product Quality Planning Annual Percentage Rate Affordable Personel Structure Accepted Quality Level Air Quality Sensor Application Ready Architecture Review Board Analytical Road Loads Accelerated Revitalization Management Assembly Receive Order 1. Application Recovery Plan 2. Abrasive Resistant Paint Advanced Research Projects Agency 1. Active Rear Steering 2. Active Roll Stabilization 1. Automatic Synchronizer 2. Automatic System After Sales Analysis As Soon As Possible 1.Adaptive Steering Column 2. Active Short Cut Air Bag System Diagnostic Module Automotive Safety Engineering Standards Office Application Specified Integrated Circuit A Safety Integrity Level 1.utomotive Automative Strategy Meeting 2. Active Safety Management Advanced Shipping Notice Active Server Pages Attribute Status Report Assembly Active Safety Test Arena American Society for Testing And Material Automatic Transmission Answers To All Car Questions Automatic Temperature Control Automatic Transmission Engineering Office Advanced Technical Information 1.Antenna Module 2. Antenna Tuner Module Affordable Target Process
Model Checking说明书

$#
Given an abstraction function h : S Sh, the concrete states are grouped and mapped into abstract states :
Mh
h
h h Preservation Theorem ?
M
27
%
If M has partial behavior of N, we say that “N simulates M”: M N
generate initial abstraction
Mh
model check
Mh |=
Mh |=
generate counterexample Th
stop
Th check if counterexample spurious Th is not spurious
35
$*
Counterexample-Guided Abstraction Refinement C, SpecC, Verilog
11
Determines Patterns on Infinite Traces
Atomic Propositions a
a
a
a
a
Boolean Operations
Temporal operators
a Xa Fa Ga aUb
“a is true now” “a is true in the neXt state” “a will be true in the Future” “a will be Globally true in the future” “a will hold true Until b becomes true”
ABB 6英寸SCH10AC管道猪和嘴部维护和操作手册说明书

FRFRA/IA A 1/ 10 Customer Plant ABB Contract No. Customer Contract No.MANUAL AND MAINTENANCE INSTRUCTIONPIG AND LIPS6” SCH10ACA 14/09/2020 First issue A. CAILLOT C. PIERCETh. DELECLUSERev.E tat/ Status DateObjet de la révision/ Description of the modificationABB PI CellierEtabli par/ Written byABB PI CellierVérifié par/ Checked byDate/VisaABB PI CellierApprouvé par/ Approved byDate/VisaClient/CustomerApprouvé par/ Approved byDate/VisaCe document est la propriété exclusive de ABB France Division Process Automation Activité Cellier. Il est interdit d’en faire usage ou de lecommuniquer sans autorisation préalable.This document belongs to ABB France Division Process Automation Activity Cellier. It is prohibited to use or transmit it without our prior consent.CONTENTS1.FOREWORD (4)1.1CONFORMITY (4)2.AFTER-SALES SERVICE (4)2.1PRODUCTS HANDLED BY THE EQUIPMENT (4)2.2PIGGED LINES (5)2.3GUARANTEE (5)3.TECHNICAL DATA (5)4.MAINTENANCE (6)5.PIG SIZE (6)6.PIG DAMAGE (6)7.PIG STORAGE (7)8.AIR PRESSURES (7)9.TYPICAL PROBLEMS WITH THE BUILD OF A PIGGED LINE (7)9.1INTERNAL WELDS NOT SMOOTHED (7)9.2PIPE JOINING (7)9.3ROUGH INTERNAL PIPE FINISH (8)9.4FLANGES NOT PROPERLY LINED UP (8)9.5PIPE SUPPORTS (8)10.REFERENCE DOCUMENTS (8)11.DATASHEET PIG (9)12.PIG INSPECTION SHEET (10)1. FOREWORD1.1 CONFORMITYYou have purchased an ABB France I.A. Cellier Activity product.This operating manual provides the operator with appropriate instructions for safe and correct operation and to facilitate the maintenance. This manual must have been read and understood by every individual given the task of transporting, installing, commissioning, maintaining operating and repairing the equipment and be available to the operating personal at all times.2. AFTER-SALES SERVICEOur after-sales service will provide you with all technical information on ABB France I.A. Cellier Activity products and their applications. Should you have any questions regarding our products, please contact :ABB FranceDivision Industrial Automation– Cellier ActivityService Après-Vente produitsParc d'Activités des Combaruches73100 Aix Les BainsEmail:*****************Tel : +33 (0) 479350565Fax : +33 (0) 4798837712.1 PRODUCTS HANDLED BY THE EQUIPMENTThe equipment has been designed to handle certain products. Typically these products are : ▪Petroleum oils and additives.▪Paints.▪Water.The transfer of any products other than those defined above can be harmful to users or to the equipment (solvent with a low flash point, overheated products, aggressive/corrosi ve products etc….)In case of doubt, contact ABB France I.A. Cellier Activity.2.2 PIGGED LINESThe equipment has been designed for ABB pigged lines.The equipement can be used in other makes of pigged line but the following items must be carefully checked :▪The internal diameter of the pigged line,▪The pigged lancher/receiver and pigged valves used on the pigged line,▪The instrumentation of the pigged line,▪The construction method of the pigged line (no penetrating welds and no internal sharp edges), ▪The assembly method of the pigged line and the pipe (flange and pipe connections perfctly aligned),▪The piping and equipement supports,▪The pig detection method and equipment.2.3 GUARANTEEABB Cellier assume no liability for damage or malfunctions resulting from failure to comply with the installation, operating or maintenance instructions.Parts subject to wear are not guaranteed.Guarantee claims must be made by quoting ABB Cellier order number immediately on detecting the defect and within the scope of warranty obligations mentioned in the purchase contract.The guarantee does not cover damage resulting directly or indirectly from :▪Inappropriate use.▪Non-compliance with our storage instructions.▪Faulty equipment or facilities connected to the product.▪Vibrations generated by external units (sample : pumps) and transmitted to the product.▪Incorrect cables and wiring.▪Use of non-genuine spare parts and accessories from ABB France I.A. Cellier Activity.▪Modification of our product without prior written approval from ABB France I.A. Cellier Activity. 3. TECHNICAL DATAThese operating instructions concern the following ranges of pig :▪E ither monobloc, requiring in this case the complete replacement of the pig (mainly 2”),▪Dismountable, requiring the replacement of only the lips after the dismantling of the pig.General technical data regarding the pig can be found in the following attached documents : ▪Data sheet n° C48003763.4. MAINTENANCEIn all casespreventive maintenance is necessary with the pig replacement. It will be more difficult to replace a damaged or too worn pig than a normally worn pig. The pig lifetime is specific to each installation. The pig replacement periodicity can be defined after a few months operation by frequently checking during this period (say once every two weeks) the state of wear of the pig lips. The attached sheet can be used to record the findings line by line.It is also possible to observe signs which indicate that a pig is worn such as :▪ Pig detections in launching/receiving stations are not stable during product pumping. ABB Cellierprogrammed control systems give warnings if this happens during an automatic sequence.▪ Pigs can be sucked out of the launching station by the product. ABB Cellier programmed controlsystems give warnings if this happens during an automatic sequence.▪ Demisters become full of product more quickly. This can also be observed by regularly monitoringthe levels in the demisters and noting the frequency with which the emptying is necessary.▪ Pig sequences take longer. ABB Cellier programmed control systems give warnings if the piggingoperation is too long.5. PIG SIZEThe following table can be used to determine if a worn pig can be re-used or if the pig / lips need to be replaced.6. PIG DAMAGEA normally worn pig lip will show even signs of wear on the whole circumference and the tip of the lip will be point and not flat as for a brand new pig lip. However if the lips is cut, split or has lumps missing then this is a sign that something is wrong with the build of the line (if the pigs are always in this condition when changed) or that an incident has happened during the pig operation which has led to the lips being damaged.7. PIG STORAGEThe mechanical characteristics of pig material (lips and bodies) can be adversely affected if stored for a long time (more than 6 months) in humid conditionsStorage under the following conditions will help to eliminate such effects and the resulting reduction in their working life :▪Stored in sealed, opaque bags, anti UV with humidity absorber.▪Labelled with the delivery date.▪Temperature between 15°C and 35°C.▪Out of direct light.▪Inside.8. AIR PRESSURESThe air pressure used for pigging can sometimes be the cause of damage if it is set too high. The pressure is set using a manual pressure regulator on the air supply line to each launching and receiving station. It can be necessary to increase the pressure in case a pig becomes blocked but the pressure must always be reduced to a suitable operating pressure. The actual required pressure depends greatly on the line configuration and the products pigged. If the pressure is set too high then the pigs will travel very fast in an empty line condition (pig positioning or at the end of transfers for example). A high pressure will also increase the compressed air consumption and increase may result in increased cycle times as the decompression time will be longer.Normal operating pressures are between 2 to 4 bars.9. TYPICAL PROBLEMS WITH THE BUILD OF A PIGGED LINE9.1 INTERNAL WELDS NOT SMOOTHEDAfter welding a flange onto the pipe it is necessary to grind the internal weld bead to a smooth finish at the same internal diameter as the pipe. This will prevent pig lip damage as the pig passes over the weld. This cause is usually found immediately after construction during the commissioning phase and is not a cause of sudden damage after a period of satisfactory operation.9.2 PIPE JOININGPipe joining is done using the sleeve junction method with no penetration welding, to ensure that the pipe junction will not cause damage to the pigs. If the internal edges of the pipes at the cut end are not de-burred and rounded off then the pig lips will be damaged. If the pipes are not spot welded face to face but with a gap then this could also cause the pig lips to be damaged. If the internal pipe diameter tolerances are not tight enough then two adjacent lengths of pipe could have different internal diameters meaning that a smooth transition from one pipe to another is not possible and consequently the lips will be damaged. This cause is usually found immediately after construction during the commissioning phase and is not a cause of sudden damage after a period of satisfactory operation.9.3 ROUGH INTERNAL PIPE FINISHNot all pipe specifications require the same smooth internal finish as used for pigged lines. The use of such pipes could lead to abnormally fast wearing out of pig lips. The same is true if the pipes have been poorly protected during the storage/construction phase. The pipes delivered must come with protective end caps and are internally oiled before packing. They should be kept in this condition up until the moment they are required for construction and as far as possible stored in a covered/protected area.9.4 FLANGES NOT PROPERLY LINED UPWhen making flanged connections on a pigged line two (2” & 3” lines) or four (4” & 6” lines) centering pins are installed. These pins ensure that the flange bores are lined up so that the pig passage is smooth and it does not come up against a shoulder. Flange connections are used when installing pig stations or valves in a pigged line. Depending on the installation method the centering pins could have been removed and replaced by normal bolts. If this is the case then it is necessary to make sure that M16 bolts have been used for 2”, 3” & 4” lines and M20 bolts have been used for 6” lines, to check the fla nge to flange line up and to check that the bolts are tight. Periodic flange tightness checks should be performed (every two to three months).9.5 PIPE SUPPORTSDue to the pigging process and the vibrations caused by the movement of pigs, especially through the bends, it is important that the pipe supports are frequent enough and correctly installed. If this is not the case then the shocks resulting from pig movement and loose pipes could cause the flange connections to come loose and, in extreme circumstances, the pipes to be damaged. A damaged pipe, with a dent for example could cause the pig lip to be damaged. Periodic support fixing checks should be performed (every two to three months).10. REFERENCE DOCUMENTS▪C48003763 : Datasheet Pig▪Pig Inspection Sheet.FRFRA/IA A 9/ 10 Customer Plant ABB Contract No. Customer Contract No.11. DATASHEET PIG12. PIG INSPECTION SHEETPig Line Diameter : ....................................... Pig Line Reference : ..................................... Pig Line Length : ………………………………Date : ........... Signature : ...............................。
汽车配件说明书

Indicators................................ 131 Shift Lever Positions ................. 131 Shift Lock Release..................... 134
奇思妙想的英语作文 螃蟹车

奇思妙想的英语作文螃蟹车## Crab-Bot.The Crab-Bot is an amphibious vehicle concept that seeks to take inspiration from the crustacean of the same name. This design is intended to combine the maneuverability and adaptability of a crab with the speed and efficiency of a car. The following response will discuss the specific features and benefits of this unique vehicle.Locomotion and Design:Just like the crab it takes inspiration from, the Crab-Bot would feature eight independently-controlled legs. This arrangement would provide exceptional stability andtraction on both land and underwater. Each leg would have multiple joints, allowing for a wide range of motion and the ability to navigate uneven or slippery surfaces. The body of the vehicle would be lightweight and streamlined,designed to reduce drag and maximize agility.Amphibious Capabilities:One of the key features of the Crab-Bot is its amphibious capabilities. The vehicle would be fully sealed and equipped with a powerful propulsion system that would allow it to transition seamlessly between land and water. The legs would be designed to function as both walking and swimming appendages, providing locomotion in both environments. This versatility would make the Crab-Bot an ideal vehicle for coastal areas, disaster relief operations, and exploration of aquatic terrains.Sensory Systems and Autonomy:To operate effectively in diverse environments, theCrab-Bot would be equipped with an array of sensors, including cameras, sonar, and infrared detectors. These sensors would provide the vehicle with a comprehensive view of its surroundings, allowing it to navigate autonomouslyor with remote control. The Crab-Bot could be programmedwith specific tasks or missions and then operate independently, making it suitable for tasks such as underwater exploration or search and rescue operations.Advantages of the Crab-Bot:The Crab-Bot concept offers several unique advantages:Exceptional Maneuverability and Traction: The eight independently-controlled legs provide unparalleled agility and stability on both land and underwater.Amphibious Capabilities: The ability to seamlessly transition between land and water makes the Crab-Bot ideal for coastal environments and amphibious operations.Versatility: The Crab-Bot can be adapted for various applications, including transportation, exploration, and search and rescue.Autonomous Capabilities: The advanced sensory systems and autonomy features allow the Crab-Bot to operateindependently or with remote control.## 螃蟹车。
波斯奇运动汽车:模型与配置指南说明书

The models featured in this publication are approved for road use in Germany. Some items of equipment are available as extra-cost options only. The availability of models and options may vary from market to market due to local restrictions and regulations. For information on standard and optional equipment, please consult your Porsche Centre. All information regarding construction, features, design, performance, dimensions, weight, fuel consumption and running costs is correct to the best of our knowledge at the time of going to print (04/2018). Porsche reserves the right to alter speci cations, equipment and delivery scopes without prior notice. Colours may di er from those illustrated. Errors and omissions excepted.Sportscar Together.CayenneCayenne Turbo Cayenne E-HybridDesign.Cayenne TurboCayenne E-HybridCayenne Turbo837465121New light strip with three-dimensional ‘PORSCHE’ logo 2‘e-hybrid’ model designation with corona in Acid Green on the tailgate 3New taillights with LED technology with three-dimensional lighting graphics and integrated four-point brake lights 4 21-inch Exclusive Design wheel with wheel arch extension in exterior colour Porsche Exclusive Manufaktur5 Roof spoiler painted in exterior colour 6New rear apron with horizontal contouring and accentuated wide look 7Rear apron in exterior colour 8 21-inch AeroDesign wheels with wheel arch extensions in exterior colour6471231L ED main headlights with matrix beamincluding PDLS Plus2Slats with black (high-gloss) inlaysin the air intakes – only in conjunctionwith exterior package in black(high-gloss)3N ew front apron with largecentral air intake4‘Power dome’ on bonnet5Independent Turbo front apronwith signi cantly larger air intakes6M ixed tyres7D ouble-row Turbo front lightsin LED bre optics541231Porsche Communication Management(PCM) with full-HD 12-inch touchscreendisplay including online navigation module2A scending centre console with grab handles3Sports seats in front (18-way, electric)with integrated headrests4Multifunction Sports steering wheelwith gearshi paddlesCayenne S1Porsche Communication Management (PCM) with full-HD 12-inch touchscreen display including online navigation module 2 Centre console with Direct Touch Control 3 High-resolution displays4Multifunction sports steering wheel with gearshi paddles 5 Mode switch (Sport Chrono Package)6Trim in aluminium, wood or carbon. Image features trim in black (high-gloss)7Sport Chrono clock Cayenne E-Hybrid 433352176Cayenne E-Hybrid.Cayenne Turbo.Cayenne S.Cayenne.Cayenne Turbo, Cayenne S and CayenneCayenne E-HybridDriveand chassis.Cayenne Turbo5641273Cayenne E-Hybrid 1 3.0-litre V6 combustion engine 2Power electronics 3Electric motor 4High-voltage cable 5 On-board charger 6 Vehicle charge port 7 High-voltage batteryCayenne E-HybridCayenne TurboCayenneE FD C B ACayenneCayenne S12Cayenne Turbo1Cayenne Turbo4215310951271211863413Comfort and infotainment.Cayenne Turbo1265Seats | Comfort and infotainment2312 131236558917441Burmester® two-way centre speaker 2 3D surround speaker 3Tweeter (air motion transformer, AMT)4 Midrange speaker 5 Bass speaker 6Tweeter 7 Two-way 3D surround speaker 8Burmester® active subwoofer with 400-watt class D digital ampli er 9B urmester® 21-channel, 1,055-watt digital ampli er1223461 BOSE® centre speaker2 Tweeter3 Midrange speaker 4Bass speaker 5 Bass-midrange speaker 6 Surround speaker 7 BOSE® 14-channel, 710-watt digital ampli er 8 BOSE® passive subwoofer 7815Porsche Connect.Lighting and assistance systems.1 2122 11。
酒吧调酒师速查表说明书

bartender cheat sheet This bartender cheat sheet includes an easy list of popular drinks. It's a short cut to creating your favorite cocktails! Toget started, make sure you have some basic cocktail tools!This guide contains affiliate links, which means I’ll receive a commission if you Click on the photos to access my all time favorite products!Jigger Boston ShakerHawkthorneStrainer Julep Strainer Juicer Fine Mesh Straineramaretto sour1 1/2 ounces amaretto liqueur3/4 ounce lemon juice1 ounce simple syrup1/2 ounce egg white (optional) americano1 1/2 ounces Campari1 1/2 ounces sweet vermouthClub soda, to top aperol spritz2 ounces Aperol3 ounces proseccoclub soda, to top apple martini1 1/2 ounces vodka1/2 ounce sour apple schnapps1/2 ounce lemon juice black russian2 ounces vodka1 ounce coffee liqueurbloody mary1 1/2 ounces vodka4 ounces tomato juice2 dashes Tabasco sauce2 dashes Worcestershire sauce1 pinch ground black pepper1 pinch smoked paprika cable car1 1/2 ounces spiced rum3/4 ounce orange curaçao1/2 ounce simple syrup1 ounce lemon juice chocolate martini1 1/2 ounces Chocolate Liqueur1/2 ounce Vodka1 1/2 ounces Creme de Cacao2 1/2 ounces Heavy Cream cosmopolitan1 1/2 ounces citrus vodka1 ounce orange liqueur1/2 ounce lime juice1 dash cranberry juicefrench 752 ounces gin 3/4 ounce lemon juice 3/4 ounce simple syrup 2 ounces Champagne daiquiri 2 ounces light rum 1 ounce lime juice 1/2 ounce s imple syrup dark 'n' stormy 2 ounces dark rum 3 ounces ginger beer 1/2 ounce lime juice espresso martini 2 ounces vodka 1/2 ounce coffee liqueur 1 ounce espresso1/2 ounce simple syrup (optional)fizz 2 ounces gin 3/4 ounce lemon juice 3/4 ounce simple syrup 1 egg white (optional) Club soda, to topgimlet2 ounces gin3/4 ounce lime juice3/4 ounce simple syrup gin and tonic2 ounces gin4 ounces tonic water greyhound2 ounces vodka4 ounces grapefruit juice hurricane2 ounces light rum2 ounces dark rum1 ounce lime juice1 ounce orange juice1/2 ounce passion fruit juice1/2 ounce simple syrup1 tablespoon grenadine kamikaze1 1/2 ounces vodka1 ounce triple sec1 ounce fresh lime juicelemon drop martini2 ounces vodka1/2 ounce triple sec1 ounce lemon juice1/2 ounce simple syruplong island1/2 ounce gin1/2 ounce light rum1/2 ounce vodka1/2 ounce blanco tequila1/2 ounce triple sec1ounce sour mixCola, to topmai tai1 ounce light rum1 ounce dark rum3/4 ounce lime juice1/2 ounce orange curaçao1/2 ounce orgeat syrup manhattan2 ounces bourbon or rye1 ounce sweet vermouth2 dashes Angostura bittersmargarita2 ounces blanco tequila1/2 ounce orange liqueur1 ounce lime juice1/2 ounce agave syrup martini (gin)2 ounces gin1/2 ounce dry vermouthDash of orange bitters (optional) martini (vodka)2 ounces vodka1/2 ounce dry vermouthDash of orange bitters (optional) mint julep4 to5 mint leaves2 sugar cubes2 1/2 ounces bourbon whiskey mojito6 mint leaves2 teaspoons sugar2 ounces light rum3/4 ounce lime juiceClub soda, to topmoscow mule2 ounces vodka1/2 ounce lime juice3 ounces ginger beer mudslide1 ounces vodka1 ounce coffee liqueur1 1/2 ounces Irish cream liqueur negroni1 ounce gin1 ounce campari1 ounce sweet vermouth old fashioned1 sugar cube2 dashes Angostura bitters2 ounces rye or bourbonpiña colada2 ounces light rum1 1/2 ounces cream of coconut2 ounces pineapple juicepisco sour2 ounces pisco1 ounce lime juice1/2 ounce simple syrup1 egg white (optional)rusty nail1 1/2 ounces Scotch whisky3/4 ounce Drambuie screwdriver2 ounces vodka5 ounces orange juice seabreeze1 1/2 ounces vodka3 ounces cranberry juice1 1/2 ounces grapefruit juice sex on the beach1 1/2 ounces vodka1/2 ounce peach schnapps1 1/2 ounces orange juice1 1/2 ounces cranberry juice sidecar1 1/2 ounces cognac1 ounce orange liqueur3/4 ounce lemon juice, freshly squeezedwhiskey sour 2 ounces bourbon 3/4 ounce lemon juice 1/2 ounce simple syrup 1/2 ounce egg white (optional)vesper 3 ounces gin 1 ounce vodka 1/2 ounce Lillet blanc tom collins 2 ounces London Dry gin 1 ounce lemon juice 1/2 ounce simple syrup Club soda, to top tequila sunrise 2 ounces blanco tequila 4 ounces orange juice 1/2 ounce grenadine sloe gin 1 1/2 ounces sloe gin 1 ounce lemon juice 3/4 ounce simple syrup Club soda, to topLOOKING FOR MORE TIPS?Check out my 'Cocktail Basics'series on YouTube. Just click here!bartender cheat sheet ©Homebody Eats @HOMEBODYEATS @HOMEBODY.EATS @HOMEBODY EATS white russian 2 ounces vodka 1 ounce coffee liqueur splash of heavy cream FOLLOW ALONG FOR MORE FUN!。
Mack Trucks 诊断系统说明书

FREQUENTLY ASKED QUESTIONSWho should buy Truck Diagnostic System?Truck Diagnostic System was designed specifically to meet the needs of Mack fleets. Mack dealerships may see value in having Truck Diagnostic System in their shop, but there is no intention of making it a required tool at this time.How is Truck Diagnostic System different from Premium Tech Tool?Truck Diagnostic System satisfies the demand by customers for a light tool that can do light diagnostics, minor parameter changes and generate vehicle reports. It’s a very fast light tool, but does not have the capabilities for doing warranty work.Who is the target market for Truck Diagnostic System?It was developed primarily for fleets that have light diagnostic needs and want vehicle trip reporting capabilities. Why Noregon?As part of our connected vehicle strategy, Mack Trucks is determined to work with best-in-class partners to develop easy to use and highly integrated solutions. Truck Diagnostics System is the latest example of this philosophyAre the parameter changes password protected?Yes, if a fleet chooses to setup password protection on their trucks’ programmable parameters, Truck Diagnostic System will prompt for that password to be entered prior to allowing parameters to be changes. Premium Tech Tool is required initially to establish or change an existing password on the truck.What’s the difference between Truck Diagnostic System and Premium Tech Tool?Truck Diagnostic System is a very fast, light tool that quickly displays truck fault codes within one minute while Premium Tech Tool supports the need for more in-depth diagnostics and extensive parameter changes. See Comparison Chart for specifics.Does Truck Diagnostic System replace Premium Tech Tool?No, there are a number of differences between Truck Diagnostic System and PTT. Three primary advantages to Premium Tech Tool are its guided diagnostics, software programming and ability to be used for warranty work. Do I need internet access for Truck Diagnostic System?No, internet access is not needed with Truck Diagnostic System. Only a 90 day license verification is required. What trucks will Truck Diagnostic System work on?Truck Diagnostic System is designed for Mack EPA2007, EPA2010, and EPA2014 trucks.Will I need to purchase a second Truck Diagnostic System license if I own Volvo trucks?No, a single license will allow a fleet to read Volvo and Mack trucks.Should I buy the stand-alone system or the JPRO Command Module?The functionality of the Truck Diagnostic System stand-alone or Command Module for JPRO® Commercial Fleet Diagnostics is the same. Use of the Command Module requires the purchase of the JPRO® Commercial Fleet Diagnostics which has additional functionality, including other OEMs. Questions about the JPRO® Commercial Fleet Diagnostics systems should be directed to Noregon.Where can I find more information?For more information visit the “Parts and Service” section of www.MackTruck .How much does it cost? And are there any volume discounts?Both the stand-alone system and the JPRO Command Module have an annual MSRP of $450. For more information on volume discounts, please contact Noregon at 844-804-2293 or visit.Is Truck Diagnostics System a one-time purchase?Truck Diagnostic System is an annual subscription.What does it cost to update Truck Diagnostic System?Updates to Truck Diagnostic System are provided free of charge as long as the annual subscription is active.If I buy Truck Diagnostic System do I need anything else?Yes, Truck Diagnostic System is a software program. A PC or laptop, 9 pin connector and a RP1210A compliant adapter is need.Can Truck Diagnostic System perform vehicle tests such as cylinder cut outs?Yes, Truck Diagnostic System can perform manual Cylinder Cut Out, DPF Regeneration and Learned Data Reset.What OEM applications come with Truck Diagnostic System?Truck Diagnostic System does not come with any bundled OEM software applications.Can Truck Diagnostic System adjust user-configurable parameters?Truck Diagnostic System has the capability to read user-configurable vehicle parameters and it can set Road Speed Limit, Cruise Control Enable, Idle Shutdown, Cruise Control Max Set Speed and Cruise Control Min Speed on Resume.Can Truck Diagnostic System clear Fault Codes?Yes, Truck Diagnostic System has the ability to clear both active and inactive fault codes. Truck Diagnostic System can also clear proprietary Mack and Volvo PPID and PSID faults.Can Truck Diagnostic System perform ECU reprogramming?Due to security and safety concerns, Truck Diagnostic System does not allow the reprograming of ECUs. If you require ECU reprogramming you will need to use the Premium Tech Tool application.Do I need OEM software in order for Truck Diagnostic System to work?No Truck Diagnostic System is a stand-alone tool.How does Truck Diagnostic System diagnose aftertreatment issues?Truck Diagnostic System allows you to see the overall health of the aftertreatment system in one simple screen. The user can easily see values such as Soot Level, DPF Lamp status, Engine derate as it relates to Aftertreatment and current Regeneration Status. The user can see if there are conditions inhibiting regeneration from taking place. Additionally, the user can start and monitor the DPF Regeneration process using Truck Diagnostic System.System requirements and troubleshooting:What kind of computer do I need to run Truck Diagnostic System?Noregon recommends using a Panasonic Toughbook CF-53 or Panasonic Toughbook CF-31 but Truck Diagnostic System will work on a current PC running Microsoft XP, Vista Business, Windows 7, or Windows 8. Does Truck Diagnostic System work on a PC running Windows 7 or Windows 8?Truck Diagnostic System will work on a PC running Microsoft Windows Vista, Microsoft Windows XP Service Pack 3, Windows 7 or Windows 8.Do you offer free technical phone support?Yes.Does Truck Diagnostic System include any OEM troubleshooting manuals?Truck Diagnostic System will search your PC for all installed OEM troubleshooting manuals and these will be available for viewing directly within the application. Truck Diagnostic System does not come with any troubleshooting manuals.。
迈阿迪Transit Connect车载挂车装备说明说明书

Transit Connect: I ncluded with Class I Trailer TowPackage – Option Code 53TNote: S ee chart at right for the weight-carrying capacity of this hitch receiver.(This capacity also is shown on a label affixed to each receiver.)Factory-Installed Trailer Hitch Receiver OptionsTransit Connect Model Van/Wagon (Option Code) (53T)Trailer Wiring Harness (4-Pin) X Trailer Wiring Module X Hitch Receiver X Trailer Sway ControlXTrailer Towing PackageNotes: • C ontent may vary depending on model, trim and/orpowertrain. See your dealer for specific content information.• T railer Towing Package recommended for all light trucksthat will be used for towing to help ensure easy, proper connection of trailer lights.Frontal Area is the total area in square feet that a moving vehicle and trailer exposesto air resistance. The chart above shows the maximum trailer frontal area that must be considered for a vehicle/trailer combination. Exceeding these limitations may significantly reduce the performance of your towing vehicle.Frontal Area Limitations/VehicleConsiderations WithTransit Connect20 sq. ft.All ApplicationsFrontal Area Considerations2018 Transit ConnectWeight-Carrying Max. Trailer Max. Tongue LoadVehicle Capacity (lbs.)(1)(l b s.)Transit Connect2,000 200(1) Hitch receivers do not include a hitch ball or ball mounting. You are responsible for obtaining the proper hitch ball, ballmounting, and other appropriate equipment to tow both the trailer and its cargo load.Refer to the Trailer Towing Selector chart for Maximum Loaded Trailer Weights for this vehicle.Hitch Receiver Weight CapacityTRAILER TOWING SELECTORAFTER YOU BUY Before heading out on a trip, check your vehicle’s Owner’s Manual for break-in and severe-duty maintenance schedules (do not tow a trailer until your vehicle has been driven at least 1,000 miles). Be sure to have your fully-loaded vehicle (including passengers) and trailer weighed so asnot to exceed critical weight limits. If any of these limits are exceeded, cargo should be removed from the vehicle and/ or trailer until all weights are within the specified limits.BEFORE YOU BUY If you are selecting a vehicle that will be used for towing, you should determine the approximate weight of thetrailer you intend to tow, including the weight of any additional cargo and fluids that you will be carryingin the trailer. Also, be sure the vehicle has the proper optional equipment. Keep in mind that performance can be severely affected in hilly terrain when the minimum acceptable powertrain combination is selected. Consider purchasing a vehicle with a more powerful engine.BrakesMany states require a separate braking system ontrailers with a loaded weight of more than 1,500pounds. For your safety, Ford Motor Companyrecommends that a separate functional brakesystem be used on any towed vehicle, includingthose dolly-towed or towbar-towed. There areseveral basic types of brake systems designed toactivate trailer brakes:1. E lectronically Controlled Brakes usuallyprovide automatic and manual control of trailerbrakes. They require that the tow vehicle beequipped with a controlling device and additionalwiring for electrical power. These brakes typicallyhave a control box installed within reach ofthe driver and can be applied manually orautomatically.2. E lectric-Over-Hydraulic (EOH) TrailerBrakes are operated by an electrically poweredpump that pressurizes a hydraulic fluid reservoirbuilt into the trailer’s brake system. Many ofthe available EOH trailer brake models arecompatible with the Ford factory installed, dash-integrated Trailer Brake Controller (TBC).3. S urge Brakes are independent hydraulic brakesactivated by a master cylinder at the junction ofthe hitch and trailer tongue. They are notcontrolled by the hydraulic fluid in the towvehicle’s brake system, and the tow vehicle’shydraulic system should never be connecteddirectly to the trailer’s hydraulic system.Be sure your trailer brakes conform to all applicablestate regulations. See Towing Safely for All Vehicleson the next page for additional braking information.Trailer LampsMake sure the trailer is equipped with lights thatconform to all applicable government regulations.The trailer lighting system should not be connecteddirectly to the lighting system of the vehicle. Seea local recreational vehicle dealer or rental traileragency for correct wiring and relays for the trailerand heavy-duty flashers.Safety Chains– A lways use safety chains when towing. Safetychains are used to retain connection betweenthe towing and towed vehicle in the event ofseparation of the trailer coupling or ball– C ross chains under the trailer tongue to preventthe tongue from contacting the ground if aseparation occurs. Allow only enough slack topermit full turning – be sure they do not drag onthe pavement– W hen using a frame-mounted trailer hitch,attach the safety chains to the frame-mountedhitch using the recommendations supplied by thehitch manufacturer– S ee your vehicle’s Owner’s Manual for safetychain attachment information– F or rental trailers, follow rental agencyinstructions for hookup of safety chainsTrailer Wiring Harness– S ome vehicles equipped with a factory-installedTrailer Tow Package include a trailer wiringharness and a wiring kit– T his kit includes one or more jumper harnesses(to connect to your trailer wiring connector) andinstallation instructionsWeight DistributionFor optimum handling and braking, the load must be properly distributed Keep center of gravity low for best handlingApproximately 60% of the allowable cargo weight should be in the front half of the trailer and 40% in the rear (within limits of tongue load or king pin weight) Load should be balanced from side-to-side to optimize handling and tire wear Load must be firmly secured to prevent shifting during cornering or braking, which could result in a sudden lossof controlBefore StartingBefore setting out on a trip, practice turning, stopping and backing up your trailer in an area away from heavy traffic Know clearance required for trailer roof Check equipment (make a checklist) Backing UpBack up slowly, with someone spotting near the rear of the trailer to guide you Place one hand at bottom of steering wheel and move it in the direction you want the trailer to goMake small steering inputs – slight movement of steering wheel results in much greater movement in rear of trailer TurningWhen turning, be sure to swing wide enough to allow trailer to avoid curbs and other obstructions.BrakingAllow considerably more distance for stopping with trailer attached Remember, the braking system of the tow vehicle is rated for operation at the GVWR, not GCWRIf your tow vehicle is an F-150, F-Series Super Duty®, Transit or Expedition and your trailer has electric brakes, the optional Integrated Trailer Brake Controller (TBC) assists in smooth and effective trailer braking by powering the trailer’s electric or electric-over-hydraulic brakes with proportional output based on the towing vehicle’s brake pressure If your trailer starts to sway, applybrake pedal gradually. The slidinglever on the TBC should be used onlyfor manual activation of trailer brakeswhen adjusting the gain. Misuse, suchas application during trailer sway,could cause instability of trailer and/ortow vehicleTowing On HillsDownshift the transmission to assistbraking on steep downgrades and toincrease power (reduce lugging) whenclimbing hillsWith TorqShift® transmission, selecttow/haul mode to automaticallyeliminate unwanted gear search whengoing uphill and help control vehiclespeed when going downhillParking With A TrailerWhenever possible, vehicles withtrailers should not be parked on agrade. However, if it is necessary, placewheel chocks under the trailer’s wheels,following the instructions below.Apply the foot service brakes and holdHave another person place the wheelchocks under the trailer wheels on thedowngrade sideOnce the chocks are in place, releasebrake pedal, making sure the chockswill hold the vehicle and trailerApply the parking brakeS hift automatic transmission into park,or manual transmission into reverseWith 4-wheel drive, make sure thetransfer case is not in neutral (ifapplicable)Starting Out Parked OnA GradeApply the foot service brake and holdStart the engine with transmission inpark (automatic) or neutral (manual)Shift the transmission into gear andrelease the parking brakeRelease the brake pedal and move thevehicle uphill to free the chocksApply the brake pedal while anotherperson retrieves the chocksAcceleration And PassingThe added weight of the trailer candramatically decrease the accelerationof the towing vehicle – exercise caution.When passing a slower vehicle, be sureto allow extra distance. Remember, theadded length of the trailer must clearthe other vehicle before you can pullback inSignal and make your pass on levelterrain with plenty of clearanceIf necessary, downshift for improvedaccelerationDriving With An AutomaticOverdrive TransmissionWith certain automatic overdrivetransmissions, towing – especiallyin hilly areas – may cause excessiveshifting between overdrive and the nextlower gear.To eliminate this condition and achievesteadier performance, overdrive can belocked out (see vehicle Owner’s Manual)I f excessive shifting does not occur, useoverdrive to optimize fuel economyOverdrive may also be locked out toobtain engine braking on downgradesWhen available, select tow/haul modeto automatically eliminate unwantedgear search and help control vehiclespeed when going downhillDriving With Cruise ControlTurn off the cruise control with heavyloads or in hilly terrain. The cruisecontrol may turn off automaticallywhen you are towing on long, steepgrades. Use caution while driving onwet roads and avoid using cruise controlin rainy or winter weather conditions.Tire PressureUnderinflated tires get hot and mayfail, leading to possible loss ofvehicle controlOverinflated tires may wear unevenlyand compromise traction and stoppingcapabilityTires should be checked often forconformance to recommended coldinflation pressuresSpare Tire UseA conventional, identical full-size sparetire is required for trailer towing (mini,compact and dissimilar full-size sparetires should not be used; alwaysreplace the spare tire with a new roadtire as soon as possible).On The RoadAfter about 50 miles, stop in aprotected location and double-check:Trailer hitch attachmentLights and electrical connectionsTrailer wheel lug nuts for tightnessEngine oil – check regularly through-out tripHigh Altitude OperationGasoline engines lose power by 3-4%per 1,000 ft. elevation. To maintainperformance, reduce GVWs and GCWsby 2% per 1,000 ft. elevation starting atthe 1,000 ft. elevation point.Powertrain/Frontal AreaConsiderationsThe charts in this Guide show theminimum engine size needed to movethe GCW of tow vehicle and trailer.Under certain conditions, however, (e.g.,when the trailer has a large frontal areathat adds substantial air drag or whentrailering in hilly or mountainous terrain)it is wise to choose a larger engineSelecting a trailer with a low-drag,rounded front design will help optimizeperformance and fuel economyNote: F or additional trailering informationpertaining to your vehicle, refer to thevehicle Owner’s Manual.Towing a trailer is demanding on your vehicle, your trailer and your personal driving skills.Follow some basic rules that will help you tow safely and have a lot more fun.Photography, illustrations and informationpresented herein were correct when approvedfor publishing. Ford Motor Company reservesthe right to discontinue or change at any timethe specifications or designs without incurringobligation. Some features shown or describedare optional at extra cost. Some options arerequired in combination with other options.Consult your dealer for the latest, mostcomplete information on models, features,prices and availability.Many of the recreational vehicles shown inthis brochure are modified or manufacturedby companies other than Ford MotorCompany. Ford assumes no responsibility forsuch modifications or manufacturing./towing-guides. TOWING SAFELY FOR ALL VEHICLES。
DECA GUIDE 2020-21 PENALTY POINT CHECKLIST说明书

54 | DECA GUIDE 2020-21PENAL TY POINT CHECKLISTCHECKED PENAL TY POINTSASSESSED PAGE NUMBER1. The Written Statement of Assurances and Academic Integritymust be signed by all participants and the chapter advisor andplaced in front of the written entry.15____________2.Entries submitted in an official DECA written event folio. Folios are available from Shop DECA. No markings, tape or othermaterial should be attached to the folio. One photocopy orthe original typed document must be submitted. Participantsmay keep a copy for use in the presentation.5____________3. Sheet protectors may not be used.5____________4. Limited to the number of pages specified in the guidelines(plus the title page and the table of contents).____________ 5 (per page)____________5. All pages are numbered in sequence starting with theexecutive summary and ending with the final page of theappendix. Do not use separate sheets between sections oras title pages for sections.5____________6. Entry must be typed. Handwritten corrections, notes, chartsand graphs will be penalized.5____________7. Paper is 8½ inches x 11 inches. No fold-outs, attachments ortabs used.5____________8. The written entry follows the outline in the Written EntryGuidelines for the event. Additional subsections are permittedin the body of the written entry.5____________9. Written entry must be printed single-sided.5____________A check indicates that the item has been examined.A circled number indicates that an infraction has been noted.A page number indicates the location of the infraction.____________0To complete this form, all that needs to be done is to click in the box in the "checked" column, and a total will be calculated at the bottom. Only click if penalties are needed to be assigned. Note: Answer 4 requires a number input (5 points per page per penalty assessment). If no penalties are to assigned, leave the form blank. Please fill in your name at the bottom to verify your scores.Please print your name as validation of this form。
spyglass-高级lint-check

Richest set of built-in syntax checks2350+ built-in rules for Verilog, VHDL, V2K, SystemVerilog and mixed languageLint, Openmore, Morelint standards575+ lint, coding style, IP-reuse rulesSTARC, STARC2002, STARCAD21, STARC 2005Recognized industry standard rules from consortium of top 11 semiconductor companies in Japan500+ rules for best practices, coding guidelines, IP-reuse, etc.
Source: I.B.S. Inc.
Source: Gartner
SoC Development Cost
Typical Impact Of Poorly Coded RTL
Chip killer bugs/escapesFixing the problems late in design cycle delays scheduleCombinational loops, non tri-state nets cause functional failureIncorrect FSM behavior causes functional failureLong time to complete verificationIncomplete coverage - Only as complete as your set of simulation vectorsCreating test vectors/assertions is time-consuming and complexSynthesis/simulation mismatch, incomplete initialization cause verification delaysPoor area, power, testability and timing of the chipUnintended redundant logic, use of complex FSM’s lead to poor QoRNo predictability in the design process to hit the market windowDesign reviews are manual, ad-hoc and subjectiveA chip company identified 10+ structural issues that would take 2 to 4 days each to identify and fix in the normal implementation flow
latent class model

Latent Class ModelsbyJay Magidson, Ph.D.Statistical Innovations Inc.Jeroen K. Vermunt, Ph.D.Tilburg University, the NetherlandsOver the past several years more significant books have been published on latent class and other types of finite mixture models than any other class of statistical models. The recent increase in interest in latent class models is due to the development of extended computer algorithms, which allow today's computers to perform latent class analysis on data containing more than just a few variables. In addition, researchers are realizing that the use of latent class models can yield powerful improvements over traditional approaches to cluster, factor, regression/segmentation, as well as to multivariable biplots and related graphical displays.What are Latent Class Models?Traditional models used in regression, discriminant and log-linear analysis contain parameters that describe only relationships between the observed variables. Latent class (LC) models (also known as finite mixture models) differ from these by including one or more discrete unobserved variables. In the context of marketing research, one will typically interpret the categories of these latent variables, the latent classes, as clusters or segments (Dillon and Kumar 1994; Wedel and Kamakura 1998). In fact, LC analysis provides a powerful new tool to identify important market segments in target marketing. LC models do not rely on the traditional modeling assumptions which are often violated in practice (linear relationship, normal distribution, homogeneity). Hence, they are less subject to biases associated with data not conforming to model assumptions. In addition, LC models have recently been extended (Vermunt and Magidson, 2000a, 2000b) to include variables of mixed scale types (nominal, ordinal, continuous and/or count variables) in the same analysis. Also, for improved cluster or segment description the relationship between the latent classes and external variables (covariates) can be assessed simultaneously with the identification of the clusters. This eliminates the need for the usual second stage of analysis where a discriminant analysis is performed to relate the cluster results to demographic and other variables.Kinds of Latent Class ModelsThree common statistical application areas of LC analysis are those that involve1)clustering of cases,2)variable reduction and scale construction, and3)prediction.This paper introduces the three major kinds of LC models:•LC Cluster Models,•LC Factor Models,•LC Regression Models.Our illustrative examples make use of the new computer program (Vermunt and Magidson, 2000b) called Latent GOLD®.LC Cluster ModelsThe LC Cluster model:•identifies clusters which group together persons (cases) who share similar interests/values/characteristics/behavior,•includes a K-category latent variable, each category representing a cluster. Advantages over traditional types of cluster analysis include:•probability-based classification: Cases are classified into clusters based upon membership probabilities estimated directly from the model,•variables may be continuous, categorical (nominal or ordinal), or counts or any combination of these,•demographics and other covariates can be used for cluster description.Typical marketing applications include:•exploratory data analysis,•development of a behavioral based and other segmentations of customers and prospects.Traditional clustering approaches utilize unsupervised classification algorithms that group cases together that are "near" each other according to some ad hoc definition of "distance". In the last decade interest has shifted towards model-based approaches which use estimated membership probabilities to classify cases into the appropriate cluster. The most popular model-based approach is known as mixture-model clustering, where each latent class represents a hidden cluster (McLachlan and Basford, 1988). Within the marketing research field, this method is sometimes referred to as “latent discriminant analysis” (Dillon and Mulani, 1999). Today's high-speed computers make these computationally intensive methods practical.For the general finite mixture model, not only continuous variables, but also variables that are ordinal, nominal or counts, or any combination of these can be included. Also, covariates can be included for improved cluster description.As an example, we used the LC cluster model to develop a segmentation of current bank customers based upon the types of accounts they have. Separate models were developed specifying different numbers of clusters and the model selected was the one that had the lowest BIC statistic.This criteria resulted in 4 segments which were named:1)Value Seekers (15% of customers),2)Conservative Savers (35% of customers),3)Mainstreamers (40% of customers),4)Investors (10% of customers).For each customer, the model gave estimated membership probabilities for each segment based on their account mix. The resulting segments were verified to be very homogeneous and to differ substantially from each other not only with respect to their mix of accounts, but also with respect to demographics, and profitability. In addition, examination of survey data among the sample of customers for which customer satisfaction data were obtained found some important attitudinal and satisfaction differences between the segments as well. Value seekers were youngest and a high percentage were new customers. Basic savers were oldest.Investors were the most profitable customer segment by far. Although only 10% of all customers, they accounted for over 30% of the bank’s deposits. Survey data pinpointed the areas of the bank with which this segment was least satisfied and a LC regression model (see below) on follow-up data related their dissatisfaction to attrition. The primary uses of the survey data was to identify reasons for low satisfaction and to develop strategies of improving satisfaction in the manner that increased retention.This methodology of segmenting based on behavioral information available on all customers offers many advantages over the common practice of developing segments from survey data and then attempting to allocate all customers to the different clusters. Advantages of developing a segmentation based on behavioral data include:•past behavior is known to be the best predictor of future behavior,•all customers can be assigned to a segment directly, not just the sample for which survey data is available,•improved reliability over segmentations based on attitudes, demographics, purchase intent and other survey variables (when segment membership is based on survey data,a large amount of classification error is almost always present for non-surveyedcustomers) .LC Factor ModelsThe LC Factor model:•identifies factors which group together variables sharing a common source of variation,•can include several ordinal latent variables, each of which contains 2 or more levels,•is similar to maximum likelihood factor analysis in that its use may be exploratory or confirmatory and factors may be assumed to be correlated or uncorrelated(orthogonal).Advantages over traditional factor analysis are:•factors need not be rotated to be interpretable,•factor scores are obtained directly from the model without imposing additional assumptions,•variables may be continuous, categorical (nominal or ordinal), or counts or any combination of these,•extended factor models can be estimated that include covariates and correlated residuals.Typical marketing applications include:•development of composite variables from attitudinal survey items,•development of perceptual maps and other kinds of biplots which relate product and brand usage to behavioral and attitudinal measures and to demographics,•estimation of factor scores,•direct conversion from factors to segments.The conversion of ordinal factors to segments is straightforward. For example, consider a model containing 2 dichotomous factors. In this case, the LC factor model provides membership classification probabilities directly for 4 clusters (segments) based on the classification of cases as high vs. low on each factor: segment 1 = (low, low); segment 2 = (low, high); segment 3 = (high, low) and segment 4 = (high, high). Magidson and Vermunt (2000) found that LC factor models specifying uncorrelated factors often fit data better than comparable cluster models (i.e., cluster models containing the same number of parameters).Figure 1 provides a bi-plot in 2-factor space of lifestyle interests where the horizontal axis represents the probability of being high on factor 1 and the vertical axis the probability of being high on factor 2. The variable AGE was included directly in the LC Factor model as a covariate and therefore shows up in the bi-plot to assist in understanding the meaning of the factors. For example, we see that persons aged 65+ are most likely to be in the (low, high) segment, as are persons expressing an interest in sewing. As a group, their (mean) factor scores are (Factor 1, Factor 2) = (.06, .67).Since these factor scores have a distinct probabilistic interpretation, this bi-plot represents an improvement over traditional biplots and perceptual maps (see Magidson and Vermunt 2000). Individual cases can also be plotted based on their factor scores.Figure 1: Bi-plot for life-style dataThe factor model can also be used to deal with measurement and classification errors in categorical variables. It is actually equivalent to a latent trait (IRT) model without the requirement that the traits be normally distributed.LC Regression ModelsThe LC Regression model, also known as the LC Segmentation model:• is used to predict a dependent variable as a function of predictors,• includes an R-category latent variable, each category representing a homogeneous population (class, segment),• different regressions are estimated for each population (for each latent segment),• classifies cases into segments and develops regression models simultaneously.Advantages over traditional regression models include:• relaxing the traditional assumption that the same model holds for all cases (R=1)allows the development of separate regressions to be used to target each segment,• diagnostic statistics are available to determine the value for R,Factor10.00.20.40.60.8 1.0Factor21.00.80.60.40.20.0AGECAMPINGHUNTINGFISHINGWINESKNITTINGSEWINGFITNESSTENNISGOLFSKIBIKINGBOATINGGARDENTRAVEL 18-2425-3435-4445-5455-6465+camp huntfish wines knit sew fitness tennis golf ski bikeboat gardentravel•for R > 1, covariates can be included in the model to improve classification of each case into the most likely segment.Typical marketing applications include:•customer satisfaction studies: identify particular determinants of customer satisfaction that are appropriate for each customer segment,•conjoint studies: identify the mix of product attributes that appeal to different market segments,•more generally: identify segments that differ from each other with respect to some dependent variable criterion.Like traditional regression modeling, LC regression requires a computer program. As LC regression modeling is relatively new, very few programs currently exist. Our comparisons between LC regression and traditional linear regression are based on the particular forms of LC regression that are implemented in the Latent GOLD® program. For other software see Wedel and DeSarbo (1994) and Wedel and Kamakura (1998). Typical regression programs utilize ordinary least squares estimation in conjunction with a linear model. In particular, such programs are based on two restrictive assumptions about data that are often violated in practice:1)the dependent variable is continuous with prediction error normally distributed,2)the population is homogeneous - one model holds for all cases.LC regression as implemented in the Latent GOLD® program relaxes these assumptions: 1) it accommodates dependent variables that are continuous, categorical (binary, polytomous nominal or ordinal), binomial counts, or Poisson counts,2) the population needs not be homogeneous (i.e., there may be multiple populations as determined by the BIC statistic).One potential drawback for LC models is that there is no guarantee that the solution will be the maximum likelihood solution. LC computer programs typically employ the EM or Newton Raphson algorithm which may converge to a local as opposed to a global maximum. Some programs provide randomized starting values to allow users to increase the likelihood of converging to a global solution by starting the algorithm at different randomly generated starting places. An additional approach is to use Bayesian prior information in conjunction with randomized starting values which eliminates the possibility of obtaining boundary (extreme) solutions and reduces the chance of obtaining local solutions. Generally speaking, we have achieved good results using 10 randomized starting values and small Bayes constants (the default option in the Latent GOLD program).In addition to using predictors to estimate separate regression model for each class, covariates can be specified to refine class descriptions and improve classification of cases into the appropriate latent classes. In this case, LC regression analysis consists of 3 simultaneous steps:1)identify latent classes or hidden segments2)use demographic and other covariates to predict class membership, and3)classify cases into the appropriate classes/segmentsDependent variables may also include repeated/correlated observations of the kind often collected in conjoint marketing studies where persons are asked to rate different product profiles. Below is an example of a full factorial conjoint study designed to assist in the determination of the mix of product attributes for a new product.Conjoint Case StudyIn this example, 400 persons were asked to rate each of 8 different attribute combinations regarding their likelihood to purchase. Hence, there are 8 records per case; one record for each cell in this 2x2x2 conjoint design based on the following attributes:•FASHION (1 = Traditional; 2 = Modern),•QUALITY (1 = Low; 2 = High),•PRICE (1 = Lower; 2 = Higher) .The dependent variable (RATING) is the rating of purchase intent on a five-point scale. The three attributes listed above are used as predictor variables in the model and the following demographic variables are used as covariates:•SEX (1 = Male; 2 = Female),•AGE (1 = 16-24; 2 = 25-39; 3 = 40+).The goal of a traditional conjoint study of this kind is to determine the relative effects of each attribute in influencing one’s purchase decision; a goal attained by estimating regression (or logit) coefficients for these attributes. When the LC regression model is used with the same data, a more general goal is attained. First, it is determined whether the population is homogeneous or whether there exists two or more distinct populations (latent segments) which differ with respect to the relative importance placed on each of the three attributes. If multiple segments are found, separate regression models are estimated simultaneously for each. For example, for one segment, price may be found to influence the purchase decision, while a second segment may be price insensitive, but influenced by quality and modern appearance.We will treat RATING as an ordinal dependent variable and estimate several different models to determine the number of segments (latent classes). We will then show how this methodology can be used to describe the demographic differences between these segments and to classify each respondent into the segment which is most appropriate. We estimated one- to four-class models with and without covariates. Table 1 reports the obtained test results. The BIC values indicate that the three-class model is the best model (BIC is lowest for this model) and that the inclusion of covariates significantly improves the model.Table 1: Test results for regression models for conjoint dataModelLog-likelihood BIC-valueNumber ofparametersWithout covariatesOne segment-440288467Two segments-4141831915Three segments-4087831223Four segments-4080834631With covariatesTwo segments-4088828418Three segments-4036824629Four segments-4026829340The parameter estimates of the three-class model with covariates are reported in Tables 2 and 3 and 4. As can be seen from the first row of Table 2, segment 1 contains about 50% of the subjects, segment 2 contains about 25% and segment 3 contains the remaining 25%. Examination of class-specific probabilities shows that overall, segment 1 is least likely to buy (only 5% are Very Likely to buy) and segment 3 is most likely (21% are Very Likely to buy).♦Table 2: Profile outputClass 1Class 2Class 3Segment Size0.490.260.25RatingVery Unlikely0.210.100.05Not Very Likely0.430.200.12Neutral0.200.370.20Somewhat Likely0.100.210.43Very Likely0.050.110.21♦Table 3: Beta's or parameters of model for dependent variableClass 1Class 2Class 3Wald p-value Wald(=)p-value Fashion 1.97 1.140.04440.19 4.4e-95191.21 3.0e-42Quality0.040.85 2.06176.00 6.5e-38132.33 1.8e-29Price-1.04-0.99-0.94496.38 2.9e-1070.760.68The beta parameter for each predictor is a measure of the influence of that predictor on RATING. The beta effect estimates under the column labeled Class 1 suggest that segment 1 is influenced in a positive way by products for which FASHION = Modern (beta = 1.97) and in negative way by PRICE = Higher (beta = -1.04), but not by QUALITY (beta is approximately 0). We also see that segment 2 is influenced by all 3 attributes, having a preference for those product choices that are modern (beta = 1.14), high quality (beta = .85) and lower priced (beta = -0.99). Members of segment 3 preferhigh quality (beta = 2.06) and the lower (beta = -.94) product choices, but are not influenced by FASHION.Note that PRICE has more or less the same influence on all three segments. The Wald (=) statistic indicates that the differences in these beta effects across classes are not significant (the p-value = .68 which is much higher than .05, the standard level for assessing statistical significance). This means that all 3 segments exhibit price sensitivity to the same degree. This is confirmed when we estimate a model in which this effect is specified to be class-independent. The p-value for the Wald statistic for PRICE is2.9x10-107 indicating that the amount of price sensitivity is highly significant.With respect to the effect of the other two attributes we find large between-segment differences. The predictor FASHION has a strong influence on segment 1, a less strong effect on segment 2, and virtually no effect on segment 3. QUALITY has a strong effect on segment 3, a less strong effect on segment 2, and virtually no effect on segment 1. The fact that the influence of FASHION and QUALITY differs significantly between the 3 segments is confirmed by the significant p-values associated with the Wald(=) statistics for these attributes. For example, for FASHION, the p-value = 3.0x10-42.The beta parameters of the regression model can be used to name the latent segments. Segment 1 could be named the “Fashion-Oriented” segment, segment 3 the “Quality-Oriented” segment, and segment 2 is the segment that takes into account all 3 attributes in their purchase decision.♦Table 4: Gamma's: parameters of model for latent distributionClass 1Class 2Class 3Wald p-valueSexMale-0.560.71-0.1524.47 4.9e-6Female0.56-0.710.15Age16-250.84-0.59-0.2453.098.1e-1126-40-0.320.59-0.2740+-0.520.010.51The parameters of the (multinomial logit) model for the latent distribution appear in Table 4. These show that females have a higher probability of belonging to the “Fashion-oriented” segment (segment 1), while males more often belong to segment 2. The Age effects show that the youngest age group is over-represented in the “Fashion-oriented”segment, while the oldest age group is over-represented in the “Quality oriented”Segment.ConclusionsWe introduced three kinds of LC models and described applications of each that are of interest in marketing research, survey analysis and related fields. It was shown that LC analysis can be used as a replacement for traditional cluster analysis techniques, as a factor analytic tool for reducing dimensionality, and as a tool for estimating separate regression models for each segment. In particular, these models offer powerful new approaches for identifying market segments.BIOSJay Magidson is founder and president of Statistical Innovations, a Boston based consulting, training and software development firm specializing in segmentation modeling. His clients have included A.C. Nielsen, Household Finance, and National Geographic Society. He is widely published on the theory and applications of multivariate statistical methods, and was awarded a patent for a new innovative graphical approach for analysis of categorical data. He taught statistics at Tufts and Boston University, and is chair of the Statistical Modeling Week workshop series. Dr. Magidson designed the SPSS CHAID™ and GOLDMineR® programs, and is the co-developer (with Jeroen Vermunt) of Latent GOLD®.Jeroen Vermunt is Assistant Professor in the Methodology Department of the Faculty of Social and Behavioral Sciences, and Research Associate at the Work and Organization Research Center at Tilburg University in the Netherlands. He has taught a variety of courses and seminars on log-linear analysis, latent class analysis, item response models, models for non-response, and event history analysisall over the world, as well as published extensively on these subjects. Professor Vermunt is developer of the LEM program and co-developer (with Jay Magidson) of Latent GOLD® .ReferencesDillon, W.R., and Kumar, A. (1994). Latent structure and other mixture models in marketing: An integrative survey and overview. R.P. Bagozzi (ed.), Advanced methods of Marketing Research, 352-388,Cambridge: Blackwell Publishers.Dillon, W.R.. and Mulani, N. (1989) LADI: A latent discriminant model for analyzing marketing research data. Journal of Marketing Research, 26, 15-29.Magidson J., and Vermunt, J.K. (2000), Latent Class Factor and Cluster Models, Bi-plots and Related Graphical Displays. Submitted for publication.McLachlan, G.J., and Basford, K.E. (1988). Mixture models: inference and application to clustering. New York: Marcel Dekker.Vermunt, J.K. & Magidson, J. (2000a). “Latent Class Cluster Analysis”, chapter 3 in J.A. Hagenaars and A.L. McCutcheon (eds.), Advances in Latent Class Analysis. Cambridge University Press.Vermunt, J.K. & Magidson, J. (2000b). Latent GOLD 2.0 User's Guide. Belmont, MA: Statistical Innovations Inc.Wedel, M., and DeSarbo, W.S (1994). A review of recent developments in latent class regression models. R.P. Bagozzi (ed.), Advanced methods of Marketing Research, 352-388, Cambridge: Blackwell Publishers. Wedel, M., and Kamakura, W.A. (1998). Market segmentation: Concepts and methodological foundations. Boston: Kluwer Academic Publishers.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
iLTLChecker:A Probabilistic Model Checker for Multiple DTMCs∗YoungMin Kwon and Gul AghaDepartment of Computer ScienceUniversity of Illinois at Urbana-Champaign{ykwon4,agha}@AbstractiLTL is a probabilistic temporal logic that can spec-ify properties of multiple discrete time Markov chains(DTMCs).In this paper,we describe two related tools:MarkovEstimator a tool to estimate a Markov transitionmatrix,and iLTLChecker,a tool to model check iLTL prop-erties of DTMCs.These tools work together to verify iLTLproperties of DTMCs.1iLTLCheckeriLTL[6]is a Linear Temporal Logic(LTL)[5]that canspecify temporal changes of expected rewards of a Markovprocess.Unlike existing probabilistic temporal logics suchas Probabilistic Computation Tree Logic(PCTL)[3]andContinuous Stochastic Logic(CSL)[1]which build a prob-ability space on the paths of computation and reason aboutthe probability space,iLTL specifies directly on the transi-tions of Probability Mass Function(pmf).iLTL captures the frequency interpretation of probabilityin large scale systems.Consider the following simple ex-ample:suppose that there is a Discrete Time Markov Chain(DTMC)of two states,say{a,b},and two transitions toother states with probability one.Suppose also that a pred-icateαis true in a but not in b.Because,this DTMC alter-nates states in every step,there are no path with consecutivesequences of a state.However,suppose that there are100nodes initially50in a state and50in b state.Then,thereare always50%of the nodes in a state or in b state and2(P[α]≥0.5)is true in iLTL.Model The model of iLTL is a set of DTMCs:Ii=1{X(i)},where X(i)=(S(i),M(i)),S(i)={s1,...,s n i}is a set of states,and M(i)∈I R n×n is a Markov transition matrix that specifies the state transitionFigure2.iLTLCheckercollision.The second graph of Figure1shows responses from the estimated model.Specification iLTL can specify temporal changes of ex-pected rewards of multiple DTMCs.A reward function (S→I R)can be regarded as benefit or cost associated with states.Let us consider the following examples of iLTL spec-ification.In this example we compare two DTMCs A= (S,M),B=(S,M ),where S={ready,run,wait}.•32P[A=ready]>P[B=ready]+0.1:in the steady state the availability,the probability that a process is in ready state,of DTMC A is at least10% larger than that of DTMC B.•P[A=ready]>P[B=ready]->2P[A=ready]+2*P[A=run]+2*P[A=wait]>P[B=ready]+2*P[B=run]+2*P[B=wait]: once the availability of A becomes larger than that of B,the expected energy consumption level of A is always larger than that of B.2ImplementationThe Markov chain estimator is implemented in Java1.4.2 and the goodness offit test method uses Matlab functions, although we are migrating the tester to Java.iLTL checker is implemented mostly in C using LAPACK Fortran li-brary for Matrix operations.Figure2is a snapshot of iLTLChecker[4].Figure2shows an iLTLChecker description.An iLTLChecker description has two blocks:a model block which describes a list of DTMCs and a specification block which describes iLTL specifications.Note that the model block of Figure2defines two DTMCs A and B with theFigure3.A counter examplesame set of states but different probability transition ma-trices.In the specification the inequality a is whether the availability of A is larger than that of B.Thefirst com-mented specification describes whether in the steady statea is true.For which the model checker returns true.Thesecond specification checks whether the witness of a(t)be-ing true for t=0,...,3is a sufficient condition for aa to be true always.The model checking result is falsewith a counter example x(A)(0)=[0.114,0.886,0]T and x(B)(0)=[0.114,0.8269,0.0591]T.Figure3shows probability transitions of the two DTMCs form the initial pmfs of the counter example.Note that for thefirst four steps the inequality a is true.But at thefifth step it becomes false and from then on it is true,as is proved by thefirst commented specification.If we add a(4)to the precondition of the specification then the model checker re-turns true.That is,(a∧X a∧X X a∧X X X a ∧X X X X a)->[]a is true.Thus,four consecu-tive witnesses of a is a sufficient condition that the expected availability of A is always larger than that of B.References[1] C.Baier,J.P.Katoen,and H.Hermanns.Approximate sym-bolic model checking of continuous-time markov chains.InCONCUR,LNCS1664,pages146–162,1999.[2]Crossbow Technology,Inc./.[3]H.Hansson and B.Jonsson.A logic for reasoning about timeand reliability.In Formal Aspects of Computing,volume6,pages512–535,1994.[4]iLTL Checker./∼ykwon.[5]Orna Lichtenstein and Amir Pnueli.Checking thatfinite stateconcurrent programs satisfy their linear specification.1984.[6]YoungMin Kwon and Gul Agha.Linear Inequality LTL(iLTL):A model checker for discrete time markov chains.In Int.Conf.on Formal engineering Methods.LNCS3308,Springer-Verlag,2004.2。
