数据库英文版第六版课后答案 (29)
数据库英文版第六版课后答案 (28)

7.14 Explain the distinctions among the terms primary key, candidate key, and superkey. Answer: A superkey is a set of one or more attributes that, taken collectively, allows us to identify uniquely an entity in the entity set. A superkey may contain extraneous attributes. If K is a superkey, then so is any superset of K. A superkey for which no proper subset is also a superkey is called a candidate key. It is possible that several distinct sets of attributes could
批注本地保存成功开通会员云端永久保存去开通
7 C H A P T E R
Database Design and the E-R
Model
This chapter introduces the entity-relationship model in detail. A significant change in the 6th edition is the change in the E-R notation used in the book. There are several alternative E-R notations used in the industry. Increasingly, however, the UML class diagram notation is used instead of the traditional E-R notation used in earlier editions of the book. Among the reasons is the wide availability of UML tools, as well as the conciseness of the UML notation compared to the notation with separate ovals to represent attributes. In keeping with this trend, we have changed our E-R notation to be more compatible with UML.
数据库系统概念(databasesystemconcepts)英文第六版课后练习题答案第8章

数据库系统概念(databasesystemconcepts)英文第六版课后练习题答案第8章C H A P T E R8Relational Database DesignExercises8.1Suppose that we decompose the schema R=(A,B,C,D,E)into(A,B,C)(A,D,E).Show that this decomposition is a lossless-join decomposition if thefollowing set F of functional dependencies holds:A→BCCD→EB→DE→AAnswer:A decomposition{R1,R2}is a lossless-join decomposition ifR1∩R2→R1or R1∩R2→R2.Let R1=(A,B,C),R2=(A,D,E),and R1∩R2=A.Since A is a candidate key(see Practice Exercise8.6),Therefore R1∩R2→R1.8.2List all functional dependencies satis?ed by the relation of Figure8.17.Answer:The nontrivial functional dependencies are:A→B and C→B,and a dependency they logically imply:AC→B.There are 19trivial functional dependencies of the form?→?,where.C does not functionally determine A because the?rst and third tuples havethe same C but different A values.The same tuples also showB does notfunctionally determine A.Likewise,A does not functionally determineC because the?rst two tuples have the same A value and different Cvalues.The same tuples also show B does not functionally determine C.8.3Explain how functional dependencies can be used to indicate the fol-lowing:910Chapter8Relational Database DesignA one-to-one relationship set exists between entity sets student andinstructor.A many-to-one relationship set exists between entity sets studentand instructor.Answer:Let Pk(r)denote the primary key attribute of relation r.The functi onal dependencies Pk(student)→Pk(instructor)and Pk(instructor)→Pk(student)indicate a one-to-one relationshipbecause any two tuples with the same value for student must havethe same value for instructor,and any two tuples agreeing on instructor must have the same value for student.The functional dependency Pk(student)→Pk(instructor)indicates amany-to-one relationship since any student value which isrepeatedwill have the same instructor value,but many student values mayhave the same instructor value.8.4Use Armstrong’s axioms to prove the soundness of the union rule.(Hint:Use the augmentation rule to show that,if?→?,then?→??.Apply theaugmentation rule again,using?→?,and then apply the transitivityrule.)Answer:To prove that:if?→?and?→?then?→??Following the hint,we derive:→?given→??augmentation rule→??union of identical sets→?given→??augmentation rule→??transitivity rule and set union commutativity8.5Use Armstrong’s axioms to prove the soundness of the pseudotransitiv-ity rule.Answer:Pr oof using Armstrong’s axioms of the Pseudotransitivity Rule:if?→?and??→?,then??→?.→?given→??augmentation rule and set union commutativity→?given→?transitivity rule8.6Compute the closure of the following set F of functional dependenciesfor relation schema R=(A,B,C,D,E).Exercises 11A →BCCD →EB →DE →AList the candidate keys for R .Answer:Note:It is not reasonable to expect students to enumerate all of F +.Some shorthand representation of the result should be acceptable as long as the nontrivial members of F +are found.Starting with A →BC ,we can conclude:A →B and A →C .Since A →B and B →D ,A →D (decomposition,transitive)Since A →C D and C D →E ,A →E (union,decom-position,transi-tive)Since A →A ,we have (re?exive)A →ABC DE from the above steps (union)Since E →A ,E →ABC DE (transitive)Since C D →E ,C D →ABC DE (transitive)Since B →D and BC →C D ,BC →ABC DE (augmentative,transitive)Also,C →C ,D →D ,B D →D ,etc.Therefore,any functional dependency with A ,E ,BC ,or C D on the left hand side of the arrow is in F +,no matter which other attributes appear in the FD.Allow *to represent any set of attributes in R ,then F +is B D →B ,B D →D ,C →C ,D →D ,B D →B D ,B →D ,B →B ,B →B D ,and all FDs of the form A ?→?,BC ?→?,C D ?→?,E ?→?where ?is any subset of {A ,B ,C ,D ,E }.The candidate keys are A ,BC ,C D ,and E .8.7Using the functional dependencies of Practice Exercise8.6,compute thecanonical cover F c .Answer:The given set of FDs F is:-A →BCCD →EB →DE →AThe left side of each FD in F is unique.Also none of the attributes in the left side or right side of any of the FDs is extraneous.Therefore the canonical cover F c is equal to F .12Chapter8Relational Database Design8.8Consider the algorithm in Figure8.18to compute?+.Show that thisalgorithm is more ef?cient than the one presented in Figure8.8(Sec-tion8.4.2)and that it computes?+correctly.Answer:The algorithm is correct because:If A is added to result then there is a proof that?→A.T o see this,observe that?→?trivially so?is correctly part of result.IfA∈?is added to result there must be some FD?→?such that A∈?and?is already a subset of result.(Otherwise f dcountwould be nonzero and the if condition would be false.)A full proofcan be given by induction on the depth of recursion for an executionof addin,but such a proof can be expected only from students witha good mathematical background.If A∈?+,then A is eventually added to result.We prove this byinduction on the length of the proof of?→A using Armstrong’saxioms.First observe that if procedure addin is called with someargument?,all the attributes in?will be added to result.Also if aparticular FD’s fdcount becomes0,all the attributes in its tail willde?nitely be added to result.The base case of the proof,A∈??A∈?+,is obviously true b ecause the?rst call to addinhas the argument?.The inductive hypotheses is that if?→A canbe proved in n steps or less then A∈result.If there is a proof inn+1steps that?→A,then the last step was an application ofeither re?exivity,augmentation or transiti vity on a fact?→?proved in n or fewer steps.If re?exivity or augmentation was usedin the(n+1)st step,A must have been in result by the end of the n thstep itself.Otherwise,by the inductive hypothesis??result.Therefore the dependency used in proving?→?,A∈?willhave f dcount set to0by the end of the n th step.Hence A will beadded to result.To see that this algorithm is more ef?cient than the one presented inthe chapter note that we scan each FD once in the main program.Theresulting array a ppears has size proportional to the size ofthe givenFDs.The recursive calls to addin result in processing linear in the sizeof a ppears.Hence the algorithm has time complexity which is linear inthe size of the given FDs.On the other hand,the algorithm given in thetext has quadratic time complexity,as it may perform the loop as manytimes as the number of FDs,in each loop scanning all of them once.8.9Given the database schema R(a,b,c),and a relation r on the schema R,write an SQL query to test whether the functional dependency b→cholds on relation r.Also write an SQL assertion that enforces the func-tional dependency.Assume that no null values are present.(Althoughpart of the SQL standard,such assertions are not supported by anydatabase implementation currently.)Answer:Exercises13a.The query is given below.Its result is non-empty if and only ifb→c does not hold on r.select bfrom rgroup by bhaving count(distinct c)>1b.create assertion b to c check(not exists(select bfrom rgroup by bhaving count(distinct c)>1))8.10Our discussion of lossless-join decomposition implicitly assumed thatattributes on the left-hand side of a functional dependency cannot take on null values.What could go wrong on decomposition,if this property is violated?Answer:The natural join operator is de?ned in terms of the cartesian product and the selection operator.The selection operator,gives unknown for any query on a null value.Thus,the natural join excludes all tuples with null values on the common attributes from the?nal result.Thus, the decomposition would be lossy(in a manner different from the usual case of lossy decomposition),if null values occur in the left-hand side of the functional dependency used to decompose the relation.(Null values in attributes that occur only in the right-hand side of the functional dependency do not cause any problems.)8.11In the BCNF decomposition algorithm,suppose you usea functional de-pendency?→?to decompose a relation schema r(?,?,?)into r1(?,?) and r2(?,?).a.What primary and foreign-key constraint do you expect toholdon the decomposed relations?b.Give an example of an inconsistency that can arise due to anerroneous update,if the foreign-key constraint were not enforcedon the decomposed relations above.c.When a relation is decomposed into3NF using the algorithm inSection8.5.2,what primary and foreign key dependencies wouldyou expect will hold on the decomposed schema?14Chapter8Relational Database DesignAnswer:a.?should be a primary key for r1,and?should be the foreign keyfrom r2,referencing r1.b.If the foreign key constraint is not enforced,then a deletion of atuple from r1would not have a corresponding deletion from thereferencing tuples in r2.Instead of deleting a tuple from r,this would amount to simply setting the value of?to null in some tuples.c.For every schema r i(??)added to the schema because of a rule→?,?should be made the primary key.Also,a candidate key?for the original relation is located in some newly created relationr k,and is a primary key for that relation.Foreign key constraints are created as follows:for each relationr i created above,if the primary key attributes of r i also occur inany other relation r j,then a foreign key constraint is created fromthose attributes in r j,referencing(the primary key of)r i.8.12Let R1,R2,...,R n be a decomposition of schema U.Let u(U)be a rela-(u).Show thattion,and let r i= RIu?r11r21···1r nAnswer:Consider some tuple t in u.(u)implies that t[R i]∈r i,1≤i≤n.Thus,Note that r i= Rit[R1]1t[R2]1...1t[R n]∈r11r21...1r nBy the de?nition of natural join,t[R1]1t[R2]1...1t[R n]= ?(??(t[R1]×t[R2]×...×t[R n]))where the condition?is satis?ed if values of attributes with the samename in a tuple are equal and where?=U.The cartesian productof single tuples generates one tuple.The selection process is satis?edbecause all attributes with the same name must have the same valuesince they are projections from the same tuple.Finally,the projectionclause removes duplicate attribute names.By th e de?nition of decomposition,U=R1∪R2∪...∪R n,which meansthat all attributes of t are in t[R1]1t[R2]1...1t[R n].That is,t is equalto the result of this join.Since t is any arbitrary tuple in u,u?r11r21...1r n8.13Show that the decomposition in Practice Exercise8.1is not a dependency-preserving decomposition.Answer:The dependency B→D is not preserved.F1,the restrictionof F to(A,B,C)is A→ABC,A→AB,A→AC,A→BC,Exercises 15A →B ,A →C ,A →A ,B →B ,C →C ,AB →AC ,AB →ABC ,AB →BC ,AB →AB ,AB →A ,AB →B ,AB →C,AC (same as AB ),BC (same as AB ),ABC (same as AB ).F 2,the restriction of F to (C ,D ,E )is A →ADE ,A →AD ,A →AE ,A →DE ,A →A ,A →D ,A →E ,D →D ,E (same as A ),AD ,AE ,DE ,ADE (same as A ).(F 1∪F 2)+is easily seen not to contain B →D since the only F D in F 1∪F 2with B as the left side is B →B ,a trivial FD .We shall see in Practice Exercise 8.15that B →D is indeed in F +.Thus B →D is not preserved.Note that C D →ABC DE is also not preserved.A simpler argument is as follows:F 1contains no dependencies with D on the right side of the arrow.F 2contains no dependencies withB on the left side of the arrow.Therefore for B →D to be preserved theremustbe an FD B →?in F +1and ?→D in F +2(so B →D would follow by transitivity).Since the intersection of the two schemes isA ,?=A .Observe thatB →A is not in F +1since B +=B D .8.14Show that it is possible to ensure that a dependency-preserving decom-position into 3NF is a lossless-join decomposition by guaranteeing that at least one schema contains a candidate key for the schema being decom-posed.(Hint :Show that the join of all the projections onto the schemas of the decomposition cannot have more tuples than the original relation.)Answer:Let F be a set of functional dependencies that hold on a schema R .Let ?={R 1,R 2,...,R n }be a dependency-preserving 3NF decompo-sition of R .Let X be a candidate key for R .Consider a legal instance r of R .Let j = X (r )1 R 1(r )1 R 2(r ) (1)R n (r ).We want to prove that r =j .We claim that if t 1and t 2are two tuples in j such that t 1[X ]=t2[X ],then t 1=t 2.To prove this claim,we use the following inductive argument –Let F ′=F 1∪F 2∪...∪F n ,where each F i is the restriction of F to the schema R i in ?.Consider the use of the algorithm given in Figure 8.8to compute the closure of X under F ′.We use induction on the number of times that the f or loop in this algorithm is executed.Basis :In the ?rst step of the algorithm,result is assigned to X ,and hence given that t 1[X ]=t 2[X ],we know that t 1[result ]=t 2[result ]is true.?Induction Step :Let t 1[result ]=t 2[result ]be true at the end of thek th execution of the f or loop.Suppose the functionaldependency considered in the k +1th execution of the f or loop is ?→?,and that ??result .??result implies that t 1[?]=t 2[?]is true.The facts that ?→?holds for some attribute set Ri in ?,and that t 1[R i ]and t 2[R i ]are inR i (r )imply that t 1[?]=t 2[?]is also true.Since ?is now added to result by the algorithm,we know that t 1[result ]=t 2[result ]is true at theend of the k +1th execution of the f or loop.16Chapter8Relational Database DesignSince?is dependency-preserving and X is a key for R,all attributes in Rare in result when the algorithm terminates.Thus,t1[R]=t2[R]is true,that is,t1=t2–as claimed earlier.Our claim implies that the size of X(j)is equal to the size of j.Notealso that X(j)= X(r)=r(since X is a key for R).Thus we haveproved that the size of j equals that of /doc/826273026.htmling the result of PracticeExercise8.12,we know that r?j.Hence we conclude that r=j.Note that since X is trivially in3NF,?∪{X}is a dependency-preservinglossless-join decomposition into3NF.8.15Give an example of a relation schema R′and set F′of functional depen-dencies such that there are at least three distinct lossless-join decompo-sitions of R′into BCNF.Answer:Given the relation R′=(A,B,C,D)the set of functionaldependencies F′=A→B,C→D,B→C allows three distinctBCNF decompositions.R1={(A,B),(C,D),(B,C)}is in BCNF as isR2={(A,B),(C,D),(A,C)}R2={(A,B),(C,D),(A,C)}R3={(B,C),(A,D),(A,B)}8.16Let a prime attribute be one that appears in at least one candidate key.Let?and?be sets of attributes such that?→?holds,but?→?does not hold.Let A be an attribute that is not in?,is not in?,and forwhich?→A holds.We say that A is transitively dependent on?.Wecan restate our de?nition of3NF as follows:A relation schema R is in3NF with respect to a set F of functional dependencies if there are nononprime attributes A in R for which A is transitively dependent on akey for R.Show that this new de?nition is equivalent to the original one.Answer:Suppose R is in3NF according to the textbook de?nition.Weshow that it is in3NF according to the de?nition in the exercise.Let A bea nonprime attribute in R that is transitively dependent on a key?forR.Then there exists??R such that?→A,?→?,A∈?,A∈,and?→?does not hold.But then?→A violates the textbookde?nition of3NF sinceA∈?implies?→A is nontrivialSince?→?does not hold,?is not a superkeyA is not any candidate key,since A is nonprimeExercises17 Now we show that if R is in3NF according to the exercise de?nition,it is in3NF according to the textbook de?nition.Suppose R is not in3NF according the the textbook de?nition.Then there is an FD?→?that fails all three conditions.Thus→?is nontrivial.is not a superkey for R.Some A inis not in any candidate key.This implies that A is nonprime and?→A.Let?be a candidate key for R.Then?→?,?→?does not hold(since?is not a superkey), A∈?,and A∈?(since A is nonprime).Thus A is transitively dependent on?,violating the exercise de?nition.8.17A functional dependency?→?is called a partial dependency if thereis a proper subset?of?such that?→?.We say that?is partially dependent on?.A relation schema R is in second normal form(2NF)if each attribute A in R meets one of the following criteria:It appears in a candidate key.It is not partially dependent on a candidate key.Show that every3NF schema is in2NF.(Hint:Show that every partial dependency is a transitive dependency.)Answer:Referring to the de?nitions in Practice Exercise8.16,a relation schema R is said to be in3NF if there is no non-prime attribute A in R for which A is transitively dependent on a key forR.We can also rewrite the de?nition of2NF given here as:“A relation schema R is in2NF if no non-prime attribute A is partially dependent on any candidate key for R.”To prove that every3NF schema is in2NF,it suf?ces to show that if a non-prime attribute A is partially dependent on a candidate key?,thenA is also transitively dependent on the key?.Let A be a non-prime attribute in R.Let?be a candidate key for R.Suppose A is partially dependent on?.From the de?nition of a partial dependency,we know that for someproper subset?of?,?→A.Since,?→?.Also,?→?does not hold,sin ce?is acandidate key.Finally,since A is non-prime,it cannot be in either?or?.Thus we conclude that?→A is a transitive dependency.Hence we have proved that every3NF schema is also in2NF.8.18Give an example of a relation schema R and a set of dependencies suchthat R is in BCNF but is not in4NF.18Chapter8Relational Database DesignAnswer:R(A,B,C)A→→BExercises19result:=?;/*fdcount is an array whose i th element contains the number of attributes on the left side of the i th FD that arenot yet known to be in?+*/for i:=1to|F|dobeginlet?→?denote the i th FD;fdcount[i]:=|?|;end/*appears is an array with one entry for each attribute.The entry for attribute A is a list of integers.Each integeri on the list indicates that A appears on the left sideof the i th FD*/for each attribute A dobeginappears[A]:=NI L;for i:=1to|F|dobeginlet?→?denote the i th FD;if A∈?then add i to appears[A];endendaddin(?);return(result);procedure addin(?);for each attribute A in?dobeginif A∈result thenbeginresult:=result∪{A};for each element i of appears[A]dobeginfdcount[i]:=fdcount[i]?1;if fdcount[i]:=0thenbeginlet?→?denote the i th FD;addin(?);endendendendFigure8.18.An algorithm to compute?+.。
(完整版)数据库课后题参考答案
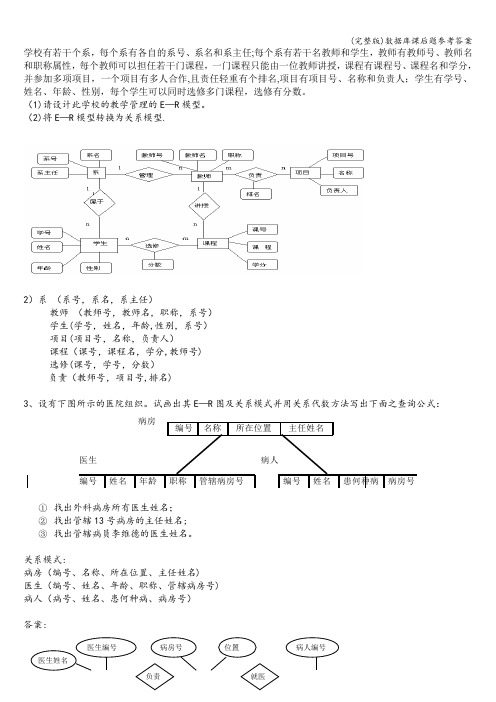
(完整版)数据库课后题参考答案学校有若干个系,每个系有各自的系号、系名和系主任;每个系有若干名教师和学生,教师有教师号、教师名和职称属性,每个教师可以担任若干门课程,一门课程只能由一位教师讲授,课程有课程号、课程名和学分,并参加多项项目,一个项目有多人合作,且责任轻重有个排名,项目有项目号、名称和负责人;学生有学号、姓名、年龄、性别,每个学生可以同时选修多门课程,选修有分数。
(1)请设计此学校的教学管理的E —R 模型。
(2)将E —R 模型转换为关系模型.2)系 (系号,系名,系主任)教师 (教师号,教师名,职称,系号) 学生(学号,姓名,年龄,性别,系号) 项目(项目号,名称,负责人)课程(课号,课程名,学分,教师号) 选修(课号,学号,分数) 负责(教师号,项目号,排名)3、设有下图所示的医院组织。
试画出其E —R 图及关系模式并用关系代数方法写出下面之查询公式:病房医生 病人图3-1 某医院人员组织关系框图 编号 名称所在位置主任姓名编号姓名患何种病 病房号编号 姓名年龄职称管辖病房号① 找出外科病房所有医生姓名; ② 找出管辖13号病房的主任姓名; ③ 找出管辖病员李维德的医生姓名。
关系模式:病房(编号、名称、所在位置、主任姓名)医生(编号、姓名、年龄、职称、管辖病房号) 病人(病号、姓名、患何种病、病房号)答案:就医病房号医生编号病人编号医生姓名位置负责①、''(外科位置医生姓名=∏σ() ②、'13'(=∏病房号主任姓名σ(病房))③、''(李维德病人姓名医生姓名=∏σ()第三章 习题一、单项选择题1、如果要在Windows 平台上运行DB2应用程序访问运行在UNIX 上的数据库服务器,需要在Windows 上安装那种产品?( )A DB2 企业服务器版B DB2 个人版C DB2 连接器D DB2 运行时客户端 答案:D2、下面那种产品不允许远程的客户端应用程序连接到该服务器?( ) A DB2 快速版 B DB2 个人版C DB2 企业服务器版D DB2 工作组服务器版 答案:B3、一个软件公司要开发一个需要访问DB2 for Linux 和DB2 for z/OS 的应用程序.下面那个产品最能满足这种需求?( )A DB2企业服务器版B DB2工作组服务器版C DB2连接器企业版D DB2通用开发版 答案:D4、下面那种产品不被认为是DB2服务器? ( ) A DB2快速版B DB2工作组服务器版C DB2个人版D DB2企业服务器版 答案:C5、下面那两种工具可以向数据库发出SQL语句进行查询? ()A 命令窗口B 命令中心C 命令行处理器D 命令处理器E 控制中心答案:B、C6、下面那种情况下,健康中心会发出报警:()A 表中的一行被删除B 运行LOAD工具C 当性能指标超过了预先定义的范围D 一条SQL语句由于语法错误而没有执行成功,并报错.答案:C二、填空题:1.DB2工具①可以用来在DB2中调度SQL脚本定期执行。
数据库系统概念(英文精编版.第六版)

Atomicity of updates
Failures
may lead to inconsistencies (1) account_A = account_A – 100 (2) account_B = account_B + 100
Example:
Concurrent access by multiple users
Exercises
Computer users interacts with data in the _______ level A. physical B. logical C. view D. all of the above Application users interact with data in the _______ level. A. physical B. logical C. view D. all of the above How the data are actually stored is called _______ A. Physical level B. Logical level C. View level D. Conceptual level
property is called ( )
A. Data inconsistency C. Data isolation B. Data redundancy D. Data integrity
1.3 View of Data
Hierarchy of Abstraction Levels
Three Abstraction Levels of Data
机械工业出版社
本课程学习内容
关系数据模型 关系数据库语言
数据库技术与应用——VisualFoxPro6.0篇课后练习题答案

<<数据库技术与应用——Visual FoxPro 6.0篇>>练习题答案第1章练习题答案1、数据定义、数据操纵2、文件系统阶段、数据库系统阶段3、属性、字段、元组、记录4、关键字5、域6、属性、属性到域的映象7、关系、关系8、投影9、选择运算、投影运算10、连接运算、自然连接三、简答题1、答:数据库(DataBase)是被长期存放在计算机内、有组织的、可以表现为多种形式的可共享的数据集合。
数据库管理系统(DataBase Management System,简称DBMS)是计算机系统软件,它的职能是有效地组织和存储数据、获取和管理数据,接受和完成用户提出的访问数据的各种请求。
数据库系统是指拥有数据库技术支持的计算机系统,它可以实现有组织地、动态地存储大量相关数据,提供数据处理和信息资源共享服务。
数据库系统是指在计算机系统中引入数据库后的系统,一般由数据库、数据库管理系统(及其开发工具)、应用系统、数据库管理员和用户构成。
2、答:关系是一张二维表,每个关系有一个关系名。
在计算机中,一个关系可以存储为一个文件。
在Visual FoxPro中,一个关系就是一个表文件。
元组是二维表中水平方向的行,有时也叫做一条记录。
属性是二维表中垂直方向的列,有时也叫做一个字段。
3、答:数据库系统由四部分组成:硬件系统、系统软件、数据库应用系统和各类人员。
4、答:常用的数据模型有层次模型、网状模型和关系模型。
层次模型的特点是:形状象一棵倒立的树,有且仅有一个结点无父结点,这个结点称为根结点,其他结点有且仅有一个父结点。
网状模型的特点是:形状象一张网,允许一个以上的结点无父结点,一个结点可以有多于一个的父结点。
关系模型的特点是:在关系中,数据的逻辑结构是一张二维表。
该表满足每一列中的分量是类型相同的数据;列的顺序可以是任意的;行的顺序可以是任意的;表中的分量是不可再分割的最小数据项,即表中不允许有子表;表中的任意两行不能完全相同。
数据库课后习题答案(仅供参考)

第1章数据库基础知识答案一、简答题1.(张红超提供)DB:数据库(Datebase,DB)是按照一定的方式组织的、存储在外部存储设备上的、能为多个用户共享的、与应用程序相互独立的相关数据集合。
DBMS:数据库管理系统(Database Management System,DBMS)是对数据库中数据资源进行统一管理和控制的软件,它提供数据定义、数据操作、数据库管理、数据库建立和维护以及通信等功能。
DBS:数据库系统(Database System,DBS)是由计算机系统、数据库及其描述机构、数据库管理系统和有关人员组成,是由这几个方面组成的具有高度组织性的总体。
区别:数据库就是存放数据的仓库,数据库管理系统就是用来管理数据库的,其中数据库系统是一个通称,包括数据库、数据库管理系统、数据库管理人员等的统称,是最大的范畴。
2.(张红超提供)(1) 实体(Entity)是现实世界客观存在并可相互区别的事物可以是具体的人、事、物或抽象的概念(某次活动,某种思想)。
(2) 属性(Attribute)实体所具有的特性或特征。
一个实体可以由若干个属性来刻画。
分“型”属性名和“值”取值。
(3)主码(Primary Key,关键字)唯一标识实体的属性或属性组称为主码。
3.(张红超提供)(1)需求分析:收集和分析数据库所有用户的信息需求和处理需求。
(2)概念结构设计:对用户需求进行综合、归纳与抽象,把用户的信息要求统一到一个整体逻辑结构中,通常用E-R图表示概念模型。
这是数据库设计的关键。
(3)逻辑结构设计:将概念模型转换为某个DBMS所支持的数据模型(如关系模型),形成数据库的模式和外模式。
(4)物理设计:确定数据库的物理结构并对其评价(时间效率和空间效率)物理设计的结果是形成数据库的内模式。
(5)数据库实施:在计算机系统上建立起实际数据库结构、装入数据、测试、试运行的过程。
(6)数据库运行和维护:数据库投入运行标志着开发任务的基本完成和维护工作的开始。
数据库课后习题答案

数据库课后习题答案第一章1.数据(DB):数据实际上是描述事物的符号纪录。
2.数据库: 数据库实际上是长期存储在计算机内的有组织的、可共享的数据集合。
3.从文件系统的视角上看去,文件是无结构的,文件只是一个字节流,因此,我们经常把文件叫做流式文件,实际上文件的数据是有结构的,数据的结构需要程序员通过编写程序来建立和维护。
4.数据库应用可以分为两大类:联机事务处理(OLTP),联机分析处理(OLAP).联机事务处理解决了组织结构业务自动化问题,而联机分析处理帮助管理层更好的分析组织结构的运站情况。
5. 数据库管理系统(DBMS):数据库管理系统是一类重要的软件,由一组程序组成。
其主要功能是完成对数据库的定义、数据操作。
提供给用户一个简明的接口,实现事务处理等。
6.数据库管理系统的基本功能:数据的定义功能数据操作功能数据库的运行和管理数据库的建立和维护功能7.数据库管理系统由两大部分组成:查询处理器存储管理器8.层次结构:应用层语言翻译层数据存取层数据存储层操作系统数据库9. 数据库系统:数据库系统是基于数据库的计算机应用的系统,有四部分组成数据库数据管理系统应用系统用户。
10. 数据库管理员的职责:(1)决定数据库中要存储的数据及数据结构(2)决定数据库的存储结构和存取策略(3)保证数据的安全性和完整性(4)监控数据库的使用和运行(5)数据库的改进和重组重构11.数据模型的三要素:数据结构数据操作完整性约束12. 数据结构是所研究的对象的类型的集合,这些对象是数据库的组成成分,他们包含两类:一类是与数据之间联系有关的对象。
一类是与数据之间联系有关的对象。
13. 数据操作:数据库主要有检索和更新(插入、删除、修改)两大类操作。
14.在关系模型中任何关系都要满足实体完整性和参照完整性。
15.三种数据模型:概念模型逻辑模型物理模型逻辑模型中有:层次模型网状模型关系模型面向对象模型对象关系模型其中层次模型和网状模型统称为非关系模型。
数据库系统概念(database system concepts)英文第六版 课后练习题 答案 第25章

C H A P T E R25Advanced Data Types and New ApplicationsPractice Exercises25.1What are the two types of time,and how are they different?Why doesit make sense to have both types of time associated with a tuple?Answer:A temporal database models the changing states of someaspects of the real world.The time intervals related to the data storedin a temporal database may be of two types-valid time and transactiontime.The valid time for a fact is the set of intervals during which the factis true in the real world.The transaction time for a data object is the set oftime intervals during which this object is part of the physical database.Only the transaction time is system dependent and is generated by thedatabase system.Suppose we consider our sample bank database to be bitemporal.Only the concept of valid time allows the system to answer queries suchas-“What was Smith’s balance two days ago?”.On the other hand,queries such as-“What did we record as Smith’s balance two daysago?”can be answered based on the transaction time.The differencebetween the two times is important.For example,suppose,three daysago the teller made a mistake in entering Smith’s balance and correctedthe error only yesterday.This error means that there is a differencebetween the results of the two queries(if both of them are executedtoday).25.2Suppose you have a relation containing the x,y coordinates and namesof restaurants.Suppose also that the only queries that will be askedare of the following form:The query specifies a point,and asks if thereis a restaurant exactly at that point.Which type of index would bepreferable,R-tree or B-tree?Why?Answer:The given query is not a range query,since it requires onlysearching for a point.This query can be efficiently answered by a B-treeindex on the pair of attributes(x,y).12Chapter25Advanced Data Types and New Applications25.3Suppose you have a spatial database that supports region queries(withcircular regions)but not nearest-neighbor queries.Describe an algo-rithm tofind the nearest neighbor by making use of multiple regionqueries.Answer:Suppose that we want to search for the nearest neighbor of apoint P in a database of points in the plane.The idea is to issue multipleregion queries centered at P.Each region query covers a larger area ofpoints than the previous query.The procedure stops when the result ofa region query is non-empty.The distance from P to each point withinthis region is calculated and the set of points at the smallest distance isreported.25.4Suppose you want to store line segments in an R-tree.If a line segment isnot parallel to the axes,the bounding box for it can be large,containinga large empty area.•Describe the effect on performance of having large bounding boxes on queries that ask for line segments intersecting a given region.•Briefly describe a technique to improve performance for such queries and give an example of its benefit.Hint:You can divide segmentsinto smaller pieces.Answer:Large bounding boxes tend to overlap even where the regionof overlap does not contain any information.The followingfigure:Rshows a region R within which we have to locate a segment.Notethat even though none of the four segments lies in R,due to the largebounding boxes,we have to check each of the four bounding boxes toconfirm this.A significant improvement is observed in the follwoingfigure:Practice Exercises3Rwhere each segment is split into multiple pieces,each with its own bounding box.In the second case,the box R is not part of the boxes indexed by the R-tree.In general,dividing a segment into smaller pieces causes the bounding boxes to be smaller and less wasteful of area. 25.5Give a recursive procedure to efficiently compute the spatial join of tworelations with R-tree indices.(Hint:Use bounding boxes to check if leaf entries under a pair of internal nodes may intersect.)Answer:Following is a recursive procedure for computing spatial join of two R-trees.SpJoin(node n1,node n2)beginif(the bounding boxes of n1and n2do not intersect)return;if(both n1and n2are leaves)output all pairs of entries(e1,e2)such thate1∈n1and e2∈n2,and e1and e2overlap;if(n1is not a leaf)NS1=set of children of n1;elseNS1={n1};if(n1is not a leaf)NS1=set of children of n1;elseNS1={n1};for each ns1in NS1and ns2in NS2;SpJoin(ns1,ns2);end25.6Describe how the ideas behind the RAID organization(Section10.3)canbe used in a broadcast-data environment,where there may occasionally be noise that prevents reception of part of the data being transmitted.4Chapter25Advanced Data Types and New ApplicationsAnswer:The concepts of RAID can be used to improve reliability ofthe broadcast of data over wireless systems.Each block of data that isto be broadcast is split into units of equal size.A checksum value iscalculated for each unit and appended to the unit.Now,parity data forthese units is calculated.A checksum for the parity data is appendedto it to form a parity unit.Both the data units and the parity unit arethen broadcast one after the other as a single transmission.On reception of the broadcast,the receiver uses the checksums to verify whether each unit is received without error.If one unit is foundto be in error,it can be reconstructed from the other units.The size of a unit must be chosen carefully.Small units not only requiremore checksums to be computed,but the chance that a burst of noisecorrupts more than one unit is also higher.The problem with usinglarge units is that the probability of noise affecting a unit increases;thus there is a tradeoff to be made.25.7Define a model of repeatedly broadcast data in which the broadcastmedium is modeled as a virtual disk.Describe how access time anddata-transfer rate for this virtual disk differ from the correspondingvalues for a typical hard disk.Answer:We can distinguish two models of broadcast data.In the caseof a pure broadcast medium,where the receiver cannot communicatewith the broadcaster,the broadcaster transmits data with periodic cy-cles of retransmission of the entire data,so that new receivers can catchup with all the broadcast information.Thus,the data is broadcast in acontinuous cycle.This period of the cycle can be considered akin to theworst case rotational latency in a disk drive.There is no concept of seektime here.The value for the cycle latency depends on the application,but is likely to be at least of the order of seconds,which is much higherthan the latency in a disk drive.In an alternative model,the receiver can send requests back to the broadcaster.In this model,we can also add an equivalent of disk accesslatency,between the receiver sending a request,and the broadcasterreceiving the request and responding to it.The latency is a function ofthe volume of requests and the bandwidth of the broadcast medium.Further,queries may get satisfied without even sending a request,sincethe broadcaster happened to send the data either in a cycle or basedon some other receivers request.Regardless,latency is likely to be atleast of the order of seconds,again much higher than the correspondingvalues for a hard disk.A typical hard disk can transfer data at the rate of1to5megabytes persecond.In contrast,the bandwidth of a broadcast channel is typicallyonly a few kilobytes per second.Total latency is likely to be of the orderof seconds to hundreds or even thousands of seconds,compared to afew milliseconds for a hard disk.25.8Consider a database of documents in which all documents are keptin a central database.Copies of some documents are kept on mobilePractice Exercises5 computers.Suppose that mobile computer A updates a copy of docu-ment1while it is disconnected,and,at the same time,mobile computer B updates a copy of document2while it is disconnected.Show how the version-vector scheme can ensure proper updating of the central database and mobile computers when a mobile computer reconnects. Answer:Let C be the computer onto which the central database is loaded.Each mobile computer(host)i stores,with its copy of each document d,a version-vector–that is a set of version numbers V d,i,j, with one entry for each other host j that stores a copy of the document d,which it could possibly update.Host A updates document1while it is disconnected from C.Thus, according to the version vector scheme,the version number V1,A,A is incremented by one.Now,suppose host A re-connects to C.This pair exchanges version-vectors andfinds that the version number V1,A,A is greater than V1,C,A by1,(assuming that the copy of document1stored host A was updated most recently only by host A).Following the version-vector scheme, the version of document1at C is updated and the change is reflected by an increment in the version number V1,C,A.Note that these are the only changes made by either host.Similarly,when host B connects to host C,they exchange version-vectors,and host Bfinds that V1,B,A is one less than V1,C,A.Thus,the version number V1,B,A is incremented by one,and the copy of docu-ment1at host B is updated.Thus,we see that the version-vector scheme ensures proper updating of the central database for the case just considered.This argument can be very easily generalized for the case where multiple off-line updates are made to copies of document1at host A as well as host B and host C.The argument for off-line updates to document2is similar.。
数据库系统概念(英文精编版.第六版)
Attributes
Attribute Domain
The set of allowed values for each attribute is called the domain of the attribute
The special value null is a member of every domain
Instructor_schema = (ID, name, dept_name, salary)
r(R) is a relation on the relation schema R
We use lowercase names for relations.
Example: instructor (Instructor _schema)
2.5 Relational Query Languages
2.6 Relational Operations
Chapter 2: Relational Model
教学目的:
熟悉关系数据模型
教学重点:
简单属性、多值属性、复合属性
关系、关系模式、码等概念 关系模式图 关系代数的操作
?简单属性多值属性复合属性?关系关系模式码等概念?关系模式图?关系代数的操作?教学难点
Chapter 2: Relational Model
2.1 Structure of Relational Databases 2.2 Database Schema 2.3 Keys 2.4 Schema Diagrams
referenced relation
Exercise: 找出左图里面
存在的其他外码、参照关 系和被参照关系
数据库系统概念第六版课后习题部分答案2s
数据库系统概念第六版课后习题部分答案2sC H A P T E R2Introduction to the Relational ModelPractice Exercises2.1Consider the relational database of Figure??.What are the appropriateprimary keys?Answer:The answer is shown in Figure2.1,with primary keys under-lined.2.2Consider the foreign key constraint from the dept name attribute of in-structor to the department relation.Give examples of inserts and deletes tothese relations,which can cause a violation of the foreign key constraint.Answer:Inserting a tuple:(10111,Ostrom,Economics,110,000)into the instructor table,where the department table does not have thedepartment Economics,would violate the foreign key constraint.Deleting the tuple:(Biology,Watson,90000)from the department table,where at least one student or instructortuple has dept name as Biology,would violate the foreign key con-straint.employee(person name,street,city)works(person name company name,salary)company(company name,city)Figure2.1Relational database for Practice Exercise2.1.12Chapter2Introduction to the Relational Model2.3Consider the time slot relation.Given that a particular time slot can meetmore than once in a week,explain why day and start time are part of theprimary key of this relation,while end time is not.Answer:The attributes day and start time are part of the primary keysince a particular class will most likely meet on several different days,and may even meet more than once in a day.However,end time is notpart of the primary key since a particular class that starts at a particulartime on a particular day cannot end at more than one time.2.4In the instance of instructor shown in Figure??,no two instructors havethe same name.From this,can we conclude that name can be used as asuperkey(or primary key)of instructor?Answer:No.For this possible instance of the instructor table the namesare unique,but in general this may not be always the case(unless theuniversity has a rule that two instructors cannot have the same name,which is a rather unlikey scenario).2.5What is the result of?rst performing the cross product of student andadvisor,and then performing a selection operation on the result with thepredicate s id=ID?(Using the symbolic notation of relational algebra,this query can be written as?s id=I D(student×advisor).)Answer:The result attributes include all attribute values of studentfollowed by all attributes of advisor.The tuples in the result are asfollows.For each student who has an advisor,the result has a rowcontaining that students attributes,followed by an s id attribute identicalto the students ID attribute,followed by the i id attribute containing theID of the students advisor.Students who do not have an advisor will not appear in the result.Astudent who has more than one advisor will appear a correspondingnumber of times in the result.2.6Consider the following expressions,which use the result ofa relationalalgebra operation as the input to another operation.For each expression,explain in words what the expression does.a.?year≥2009(takes)1studentb.?year≥2009(takes1student)c. ID,name,course id(student1takes)Answer:a.For each student who takes at least one course in2009,displaythe students information along with the information about whatcourses the student took.The attributes in the result are:ID,name,dept name,tot cred,course id,section id,semester,year,gradeb.Same as(a);selection can be done before the join operation.c.Provide a list of consisting ofExercises3ID,name,course idof all students who took any course in the university.2.7Consider the relational database of Figure??.Give an expression in therelational algebra to express each of the following queries:a.Find the names of all employees who live in city“Miami”.b.Find the names of all employees whose salary is greater than$100,000.c.Find the names of all employees who live in“Miami”and whosesalary is greater than$100,000.Answer:a. name(?city=“Miami”(employee))b. name(?salary>100000(employee))c. name(?city=“Miami”∧salary>100000(employee))2.8Consider the bank database of Figure??.Give an expression in therelational algebra for each of the following queries.a.Find the names of all branches located in“Chicago”.b.Find the names of all borrowers who have a loan in branch“Down-town”.Answer:a. branch name(?branch city=“Chicago”(branch))b. customer name(?branch name=“Downtown”(borro w er1loan))。
数据库系统概论第六版课后答案

数据库系统概论第六版课后答案第1章数据库系统概述一、填空题1. 在关系数据库中,一个元组对应表中。
解: 一个记录 (一行)2. 常用的数据模型有:、、和面向对象模型。
解: 关系模型,层次模型,网状模型3. 用二维表来表示实体及实体之间联系的数据模型是。
解: 关系模型4. 关系模型数据库中最常用的三种关系运算是、、。
解: 选择运算,投影运算,连接运算5. 在数据库系统中,数据的最小访问单位是。
解: 字段(数据项)6. 对表进行水平方向的分割用的运算是。
解: 选择运算7. 数据结构、和称为数据模型的三要素。
解: 数据操作,数据约束条件8. 关系的完整性约束条件包括完整性、完整性和完整性三种。
解: 用户定义,实体,参照二、单项选择题1. 对数据库进行规划、设计、协调、维护和管理的人员,通常被称为(D )。
A. 工程师B. 用户C. 程序员D. 数据库管理员2. 下面关于数据(Data)、数据库(DB)、数据库管理系统(DBMS)与数据库系统(DBS)之间关系的描述正确的是( B )。
A. DB包含DBMS和DBSB. DBMS包含DB和DBSC. DBS包含DB和DBMSD. 以上都不对3. 数据库系统的特点包括( D )。
A. 实现数据共享,减少数据冗余B. 具有较高的数据独立性、具有统一的数据控制功能C. 采用特定的数据模型D. 以上特点都包括4. 下列各项中,对数据库特征的描述不准确的是( D )。
A. 数据具有独立性B. 数据结构化C. 数据集中控制D. 没有冗余5. 在数据的组织模型中,用树形结构来表示实体之间联系的模型称为 ( D )。
A. 关系模型B. 层次模型C. 网状模型D. 数据模型6. 在数据库中,数据模型描述的是 ( C ) 的集合。
A. 文件B. 数据C. 记录D. 记录及其联系7. 在关系数据库中,关系就是一个由行和列构成的二维表,其中行对应( B )。
A. 属性B. 记录C. 关系D. 主键8. 关系数据库管理系统所管理的关系是( C )。
(完整版)数据库课后题参考答案

学校有若干个系,每个系有各自的系号、系名和系主任;每个系有若干名教师和学生,教师有教师号、教师名和职称属性,每个教师可以担任若干门课程,一门课程只能由一位教师讲授,课程有课程号、课程名和学分,并参加多项项目,一个项目有多人合作,且责任轻重有个排名,项目有项目号、名称和负责人;学生有学号、姓名、年龄、性别,每个学生可以同时选修多门课程,选修有分数。
(1)请设计此学校的教学管理的E-R 模型。
(2)将E-R 模型转换为关系模型。
2)系 (系号,系名,系主任)教师 (教师号,教师名,职称,系号) 学生(学号,姓名,年龄,性别,系号) 项目(项目号,名称,负责人)课程(课号,课程名,学分,教师号) 选修(课号,学号,分数) 负责(教师号,项目号,排名)3、设有下图所示的医院组织。
试画出其E-R 图及关系模式并用关系代数方法写出下面之查询公式:病房医生 病人图3-1 某医院人员组织关系框图 编号 名称所在位置主任姓名编号姓名患何种病 病房号编号 姓名年龄职称管辖病房号① 找出外科病房所有医生姓名;② 找出管辖13号病房的主任姓名; ③ 找出管辖病员李维德的医生姓名。
关系模式:病房(编号、名称、所在位置、主任姓名) 医生(编号、姓名、年龄、职称、管辖病房号) 病人(病号、姓名、患何种病、病房号)答案:①、''(外科位置医生姓名=∏σ) ②、'13'(=∏病房号主任姓名σ(病房))③、''(李维德病人姓名医生姓名=∏σ)第三章 习题一、单项选择题1、如果要在Windows 平台上运行DB2应用程序访问运行在UNIX 上的数据库服务器,需要在Windows 上安装那种产品?( )A DB2 企业服务器版B DB2 个人版C DB2 连接器D DB2 运行时客户端 答案:D2、下面那种产品不允许远程的客户端应用程序连接到该服务器?( ) A DB2 快速版 B DB2 个人版C DB2 企业服务器版D DB2 工作组服务器版 答案:B 3、一个软件公司要开发一个需要访问DB2 for Linux 和DB2 for z/OS 的应用程序。
《Access习题集》第6版答案-全

第一章数据库基础知识一、填空题1.管理、数据资源2.采集、存储、分类、传输3.文件管理、数据库系统、分布式数据库系统4.数据库、数据库管理系统、硬件、软件和相关人员,数据库管理系统5.层次模型6.关系模型7.现实世界数据特征8.层次模型、网状模型、关系模型、数据结构、关系模型9.需求分析、概念结构设计、逻辑结构设计、物理结构设计、数据库实施和数据库运行与维护10.所有属性都是不可分的基本数据项11.关键字/候选键12.元组13.网状结构14.模式、外模式、内模式15.存储模式16.概念模型17.数据结构化,数据独立性、数据共享性、数据完整性18.用户自定义完整性19.插入和删除异常、更新异常20.面向对象方法、OO 方法二、选择题1.B2.B3.A4.D5.D6.C7.D8.D9.A 10.B 11.C 12.D 13.A 14.C 15.C 16.C 17.B 18.B19.A 20.A 21.C 22.C 23.B 24.C 25.B 26.D 27.D 28.D 29.C 30.AD 31.A 32.A 33.D 34.B 35.B36.C 37.D 38.D39.C 40.D 41.B42.B 43.C 44.B 45.B46.B 47.B 48.B 49.D 50.B三、判断题1.对2。
对3。
错4。
错5。
对6。
错7。
错8。
错9。
对10。
对四、问答题1.参考答案R∩S R∪SR-S R×S2.请根据以下E-R图导出关系表参考答案:1)职工(职工号,姓名,性别,出生日期,部门号)部门(部门号,部门名,电话,地址)2)图书(书号,书名,作者,出版社,出版日期,价格)读者(读者编号,姓名,性别,职业,电话)借阅(读者编号,书号,借阅日,归还日)3.参考答案:属于第二范式,可分解为第三范式:教师(教师编号,姓名,职称,系别)院系(系别,系主任)或教师(教师编号,姓名,职称,院系编号)院系(院系编号,系别,系主任)4.参考答案:2NF,分解为以下的3NF第二章ACCESS概述一、填空1.office2.对象,窗口3.表,查询,窗体,报表,宏,accdb4.查询5.报表6.空数据库,模板7.客户端数据库,Web数据库8.Access Services9.压缩和修复数据库10.Access选项、第三章表的创建与管理一、填空题1.对象(50)2.表结构3.字段名4.255、空格5.常规属性、查阅属性6.关联7.父表中8.主键、字段、多个字段9.系统定义、用户定义10.OLE、超级链接、附件11.速度、查询12.单个字段、多个字段13.6553514.数据表视图、设计视图15.一个、多个16.空值、重复值17.一对一、一对多、多对多18.数据19.计算/超级链接/附件20.文本21.货币22.备注23.一个24.有效性规则25.双精度型26.表27.是/否28.主键/主关键字29.输入掩码、有效性规则30.格式属性31.数据32.外键33.关联字段34.一对一35.一、多36.设计视图37.一对多、多对多38.常规39.选择、投影40.选择筛选、按窗体筛选、高级筛选41.记录42.外键43.表间、实施参照完整性、级联删除相关记录44.同一数据库45.自动46.主表、子表47.字段定义、属性定义48.共同字段、数据类型二、选择题第四章查询设计一、填空题1.计算、条件检索2.查询3.表、查询4.动态数据集合、数据来源5.选择查询、交叉表查询、参数查询、操作查询、SQL查询6.查询准则7.同行、不同行8.选择查询9.窗体、报表10.两个、两个、字段11.行标题、列标题12.准确性、有效性13.数据资源14.GROUP BY(分组)15.数据定义、数据查询16.查询设计视图17.逻辑18.Date()-[参加工作时间]<365 19.数据来源20.数据保持同步21.查询向导、设计视图22.多表查询、单表查询23.简单查询向导、交叉表查询向导、查找重复项查询向导、查找不匹配项查询向导24.选择查询、参数查询25.查询、准则、数据来源26.查询设计视图(题干为“则用户可以在查询的中加入”)27.查询设计视图28.查询设计视图29.生成表查询、追加查询、更新查询、删除查询30.算术、逻辑、特殊31.双引号32.方括号33.两个34.选择查询35.参数36.生成表查询37.删除查询38.检索数据、查询结果39.Len([姓名])=240.Month([出生日期])=841.Year(date( ))-year([参加工作时间])>1042.Like “计算机*”43.Mid([学号],3,2)=“07”44.>60 and <10045.任意单个字符46.任意字符串47.IS NULL48.IS NOT NULL49.IN (“教授”, “讲师”),[“教授”or “讲师”]50.Date ( )二、选择题1.C 2.C 3.D 4.C 5.C 6.A 7.A 8.B 9.D 10.C 11.D 12.A 13.A 14.D 15.B 16.C 17.C 18.A19.C20.B21.D22.B23.C24.C25.C26.B27.D28.B29.B30.D31.A32.D33.B34.A35.D36.D37.D38.B39.D40.D41.C42.B43.C44.B45.B46.C47.D48.C49.A50.B51.C52.C53.A54.D55.B56.D57.B58.A59.A60.C61.C62.A63.B64.A65.D66.B67.C三、判断题1.F 2.T 3.F 4.T 5.F 6.F7.F8.F9.F10.T11. F12.T13. F14.T15. F第五章报表设计一、填空题1.表,查询2.报表打印3.记录输入的先后4.报表页眉,页面页眉,主体,页面页脚,报表页脚5.设计,分组和汇总,分组和排序6.报表页眉,每一7.直线,矩形8. 49.不能10.可以11.页面页眉12.表,查询13.窗体,报表(注:12和13题,题干重复了,经验证,4种对象都可以另存为“报表”)14.报表设计,报表,空报表,向导,标签15.本题无明确答案,题干有问题,应该是“同一主报表中最多可同时添加3个子报表对象”16.计算,组页脚,报表页脚(注:第一个空有些同学会填“文本框”,文本框是最常用的计算控件,但不是唯一的可实现计算功能的控件)17.页面设置,打印预览二、单选题1. D2. D3. B4. C5. A6. A7. D8. D9.D(注:如果没有分组,则有“纵栏式”、“表格式”和“两端对齐”三种布局;如果存在分组,则有“递阶”、“块”和“大纲”等布局方式。
数据库英文版第六版课后答案

数据库英文版第六版课后答案Chapter 1: IntroductionQuestions1.What is a database?A database is a collection of organized and structured data stored electronically in a computer system. It allows users to efficiently store, retrieve, and manipulate large amounts of data.2.What are the advantages of using a database system?–Data sharing and integration: A database system allows multiple users to access and share data simultaneously.–Data consistency and integrity: A database system enforces rules and constraints to maintain the accuracy and integrity of the data.–Data security: A database system provides access control mechanisms to ensure that data is accessed by authorized users only.–Data independence: A database system separates the data from the application programs that use it, allowing for easier applicationdevelopment and maintenance.Exercises1.Discuss the advantages and disadvantages of using a database system.Advantages:–Data sharing and integration–Data consistency and integrity–Data security–Data independenceDisadvantages:–Cost: Database systems can be expensive to set up and maintain.–Complexity: Database systems require a certain level of expertise to design, implement, and manage.–Performance overhead: Database systems may introduce some overhead in terms of storage and processing.Overall, the advantages of using a database system outweigh the disadvantages in most cases, especially for large-scale applications with multiple users and complex data requirements.Chapter 2: Relational Model and Relational Algebra Questions1.What is a relation? How is it represented in the relational model?A relation is a table-like structure that represents a set of related data. It is represented as a two-dimensional table with rows and columns, where each row corresponds to a record and each column corresponds to a attribute or field.2.What is the primary key of a relation?The primary key of a relation is a unique identifier for each record in the relation. It is used to ensure the uniqueness and integrity of the data.Exercises1.Consider the following relation:Employees (EmpID, Name, Age, Salary)–EmpID is the primary key of the Employees relation.–Name, Age, and Salary are attributes of the Employees relation.2.Write a relational algebra expression to retrieve the names of all employees whose age is greater than 30.π Name (σ Age > 30 (Employees))Chapter 3: SQLQuestions1.What is SQL?SQL (Structured Query Language) is a programming language designed for managing and manipulating relational databases. It provides a set of commands and statements that allow users to create, modify, and query databases.2.What are the main components of an SQL statement?An SQL statement consists of the following main components:–Keywords: SQL commands and instructions.–Clauses: Criteria and conditions that specify what data to retrieve or modify.–Expressions: Values, variables, or calculations used in SQL statements.–Operators: Symbols used to perform operations on data. Exercises1.Write an SQL statement to create a table called。
数据库课后习题答案(全)

第1章数据库系统概述习题参考答案1.1 数据处理和数据库应用的例子:电话公司使用数据库存储客户基本信息、客户的每次通话信息以及雇员基本信息、雇员业绩信息等。
典型的数据处理包括电话收费、生成客户长途电话话单、计算雇员工资等图书馆使用数据库存储图书资料信息、读者基本信息、图书借阅信息等。
典型的数据处理包括新书登记、处理读者借还图书等税务局使用数据库存储纳税人(个人或公司)信息、纳税人缴纳税款信息等。
典型的数据处理包括纳税、退税处理、统计各类纳税人纳税情况等。
银行使用数据库存储客户基本信息、客户存贷款信息等。
典型的数据处理包括处理客户存取款等。
超市使用数据库存储商品的基本信息、会员客户基本信息、客户每次购物的详细清单。
典型的数据处理包括收银台记录客户每次购物的清单并计算应交货款。
1.2 DBMS是数据库管理系统的简称,是一种重要的程序设计系统。
它由一个相互关联的数据集合和一组访问这些数据的程序组成。
数据库是持久储存在计算机中、有组织的、可共享的大量数据的集合。
数据库中的数据按一定的数据模型组织、描述和存储,可以被各种用户共享,具有较小的冗余度、较高的数据独立性,并且易于扩展。
数据库系统由数据库、DBMS(及其开发工具)、应用系统和数据库管理员组成。
数据模型是一种形式机制,用于数据建模,描述数据、数据之间的联系、数据的语义、数据上的操作和数据的完整性约束条件。
数据库模式是数据库中使用数据模型对数据建模所产生设计结果。
对于关系数据库而言,数据库模式由一组关系模式构成。
数据字典是DBMS维护的一系列内部表,用来存放元数据。
所谓元数据是关于数据的数据。
1.3 DBMS提供如下功能:(1)数据定义:提供数据定义语言DDL,用于定义数据库中的数据对象和它们的结构。
(2)数据操纵:提供数据操纵语言DML,用于操纵数据,实现对数据库的基本操作(查询、插入、删除和修改)。
(3)事务管理和运行管理:统一管理数据、控制对数据的并发访问,保证数据的安全性、完整性,确保故障时数据库中数据不被破坏,并且能够恢复到一致状态。
数据库英文版第六版课后答案(32)

数据库英⽂版第六版课后答案(32)C H A P T E R11Indexing and HashingThis chapter covers indexing techniques ranging from the most basic one tohighly specialized ones.Due to the extensive use of indices in database systems,this chapter constitutes an important part of a database course.A class that has already had a course on data-structures would likely be famil-iar with hashing and perhaps even B+-trees.However,this chapter is necessaryreading even for those students since data structures courses typically cover in-dexing in main memory.Although the concepts carry over to database accessmethods,the details(e.g.,block-sized nodes),will be new to such students.The sections on B-trees(Sections11.4.5)and bitmap indexing(Section11.9) may be omitted if desired. Exercises11.15When is it preferable to use a dense index rather than a sparse index?Explain your answer.Answer:It is preferable to use a dense index instead of a sparse indexwhen the?le is not sorted on the indexed?eld(such as when the indexis a secondary index)or when the index?le is small compared to the sizeof memory.11.16What is the difference between a clustering index and a secondary index?Answer:The clustering index is on the?eld which speci?es the sequentialorder of the?le.There can be only one clustering index while there canbe many secondary indices.11.17For each B+-tree of Practice Exercise11.3,show the steps involved in thefollowing queries:a.Find records with a search-key value of11.b.Find records with a search-key value between7and17,inclusive.Answer:With the structure provided by the solution to Practice Exer-cise11.3a:9798Chapter11Indexing and Hashinga.Find records with a value of11i.Search the?rst level index;follow the?rst pointer.ii.Search next level;follow the third pointer.iii.Search leaf node;follow?rst pointer to records with key value11.b.Find records with value between7and17(inclusive)i.Search top index;follow?rst pointer.ii.Search next level;follow second pointer.iii.Search third level;follow second pointer to records with keyvalue7,and after accessing them,return to leaf node.iv.Follow fourth pointer to next leaf block in the chain.v.Follow?rst pointer to records with key value11,then return.vi.Follow second pointer to records with with key value17.With the structure provided by the solution to Practice Exercise12.3b:a.Find records with a value of11i.Search top level;follow second pointer.ii.Search next level;follow second pointer to records with key value11.b.Find records with value between7and17(inclusive)i.Search top level;follow second pointer.ii.Search next level;follow?rst pointer to records with key value7,then return.iii.Follow second pointer to records with key value11,then return.iv.Follow third pointer to records with key value17.With the structure provided by the solution to Practice Exercise12.3c:a.Find records with a value of11i.Search top level;follow second pointer.ii.Search next level;follow?rst pointer to records with key value11.b.Find records with value between7and17(inclusive)i.Search top level;follow?rst pointer.ii.Search next level;follow fourth pointer to records with key value7,then return.iii.Follow eighth pointer to next leaf block in chain.iv.Follow?rst pointer to records with key value11,then return.v.Follow second pointer to records with key value17.Exercises99 11.18The solution presented in Section11.3.4to deal with nonunique searchkeys added an extra attribute to the search key.What effect could this change have on the height of the B+-tree?Answer:The resultant B-tree’s extended search key is unique.This results in more number of nodes.A single node(which points to mutiple records with the same key)in the original tree may correspond to multiple nodes in the result tree.Dependingon how they are organized the height of the tree may increase;it might be more than that of the original tree.11.19Explain the distinction between closed and open hashing.Discuss therelative merits of each technique in database applications.Answer:Open hashing may place keys with the same hash function value in different buckets.Closed hashing always places such keys together in the same bucket.Thus in this case,different buckets can be of different sizes,though the implementation may be by linking together?xed size buckets using over?ow chains.Deletion is dif?cult with open hashing as all the buckets may have to inspected before we can ascertain that a key value has been deleted,whereas in closed hashing only that bucket whose address is obtained by hashing the key value need be inspected.Deletions are more common in databases and hence closed hashing is more appropriate for them.For a small,static set of data lookups may be more ef?cient using open hashing.The symbol table of a compiler would be a good example.11.20What are the causes of bucket over?ow in a hash?le organization?Whatcan be done to reduce the occurrence of bucket over?ows?Answer:The causes of bucket over?ow are:-a.Our estimate of the number of records that the relation will have wastoo low,and hence the number of buckets allotted was not suf?cient.b.Skew in the distribution of records to buckets.This may happeneither because there are many records with the same search keyvalue,or because the the hash function chosen did not have thedesirable properties of uniformity and randomness.To reduce the occurrence of over?ows,we can:-a.Choose the hash function more carefully,and make better estimatesof the relation size.b.If the estimated size of the relation is n r and number of records perblock is f r,allocate(n r/f r)?(1+d)buckets instead of(n r/f r)buckets.Here d is a fudge factor,typically around0.2.Some space is wasted:About20percent of the space in the buckets will be empty.But thebene?t is that some of the skew is handled and the probability ofover?ow is reduced.11.21Why is a hash structure not the best choice for a search key on whichrange queries are likely?100Chapter11Indexing and HashingAnswer:A range query cannot be answered ef?ciently using a hashindex,we will have to read all the buckets.This is because key valuesin the range do not occupy consecutive locations in the buckets,they aredistributed uniformly and randomly throughout all the buckets.11.22Suppose there is a relation r(A,B,C),with a B+-tree index with searchkey(A,B).a.What is the worst-case cost of?nding records satisfying10using this index,in terms of the number of records retrieved n1and the height h of the tree?b.What is the worst-case cost of?nding records satisfying1050∧5n2that satisfy this selection,as well as n1and h de?ned above?c.Under what conditions on n1and n2would the index be an ef?cient way of?nding records satisfying10Answer:a.What is the worst case cost of?nding records satisfying10using this index,in terms of the number of records retrieved n1and the height h of the tree?This query does not correspond to a range query on the search key as the condition on the?rst attribute if the search key is a comparison condition.It looks up records which have the value of A between10and50.However,each record is likely to be in a different block, because of the ordering of records in the?le,leading to many I/O operation.In the worst case,for each record,it needs to traverse the whole tree(cost is h),so the total cost is n1?h.b.What is the worst case cost of?nding records satisfying1050∧5n2that satisfy this selection,as well as n1and h de?ned above.This query can be answered by using an ordered index on the search key(A,B).For each value of A this is between10and50,the system located records with B value between5and10.However,each record could is likely to be in a different disk block.This amounts to exe-cuting the query based on the condition on A,this costs n1?h.Then these records are checked to see if the condition on B is satis?ed.So, the total cost in the worst case is n1?h.c.Under what conditions on n1and n2would the index be an ef?cient way of?nding records satisfying10n1records satisfy the?rst condition and n2records satisfy the second condition.When both the conditions are queried,n1records are output in the?rst stage.So,in the case where n1=n2,no extra records are output in the furst stage.Otherwise,the records whichExercises101 dont satisfy the second condition are also output with an additionalcost of h each(worst case).11.23Suppose you have to create a B+-tree index on a large number of names,where the maximum size of a name may be quite large(say40characters) and the average name is itselflarge(say10characters).Explain how pre?x compression can be used to maximize the average fanout of nonleaf nodes. Answer:There arises2problems in the given scenario.The?rst prob-lem is names can be of variable length.The second problem is names can be long(maximum is40characters),leading to a low fanout and a correspondingly increased tree height.With variable-length search keys, different nodes can have different fanouts even if they are full.The fanout of nodes can be increased bu using a technique called pre?x compres-sion.With pre?x compression,the entire search key value is not stored at internal nodes.Only a pre?x of each search key which is suf?ceint to distinguish between the key values in the subtrees that it seperates.The full name can be stored in the leaf nodes,this way we dont lose any information and also maximize the average fanout of internal nodes. 11.24Suppose a relation is stored in a B+-tree?le organization.Suppose sec-ondary indices stored record identi?ers that are pointers to records on disk.a.What would be the effect on the secondary indices if a node splithappens in the?le organization?b.What would be the cost of updating all affected records in a sec-ondary index?c.How does using the search key of the?le organization as a logicalrecord identi?er solve this problem?d.What is the extra cost due to the use of such logical record identi?ers?Answer:a.When a leaf page is split in a B+-tree?le organization,a numberof records are moved to a new page.In such cases,all secondaryindices that store pointers to the relocated records would have tobe updated,even though the values in the records may not havechanged.b.Each leaf page may contain a fairly large number of records,andeach of them may be in different locations on each secondary index.Thus,a leaf-page split may require tens or even hundreds of I/Ooperations to update all affected secondary indices,making it a veryexpensive operation.c.One solution is to store the values of the primary-index search keyattributes in secondary indices,in place of pointers to the indexed102Chapter11Indexing and Hashingrecords.Relocation of records because of leaf-page splits then doesnot require any update on any secondary index.d.Locating a record using the secondary index now requires two steps:First we use the secondary index to?nd the primary index search-key values,and then we use the primary index to?nd the corre-sponding records.This approach reduces the cost of index updatedue to?le reorganization,although it increases the cost of accesingdata using a secondary index.11.25Show how to compute existence bitmaps from other bitmaps.Make sure that your technique works even in the presence of null values,by using a bitmap for the value null.Answer:The existence bitmap for a relation can be calculated by takingthe union(logical-or)of all the bitmaps on that attribute,including thebitmap for value null.11.26How does data encryption affect index schemes?In particular,how might it affect schemes that attempt to store data in sorted order?Answer:Note that indices must operate on the encrypted data orsomeone could gain access to the index to interpret the data.Otherwise,the index would have to be restricted so that only certain users could access it.To keep the data in sorted order,the index scheme would haveto decrypt the data at each level in a tree.Note that hash systems wouldnot be affected.11.27Our description of static hashing assumes that a large contiguous stretch of disk blocks can be allocated to a static hash table.Suppose you can allocate only C contiguous blocks.Suggest how to implement the hash table,if it can be much larger than C blocks.Access to a block should stillbe ef?cient.Answer:A separate list/table as shown below can be created.Starting address of?rst set of C blocksCStarting address of next set of C blocks2Cand so onDesired block address=Starting adress(from the table depending onthe block number)+blocksize*(blocknumber%C)For each set of C blocks,a single entry is added to the table.In thiscase,locating a block requires2steps:First we use the block number tond the actual block address,and then we can access the desired block.。
数据库英文版第六版课后答案 (29)

8.23
Why are certain functional dependencies called trivial functional dependencies? Answer: Certain functional dependencies are called trivial functional dependencies because they are satisfied by all relations. Use the definition of functional dependency to argue that each of Armstrong’s axioms (reflexivity, augmentation, and transitivity) is sound. Answer: The definition of functional dependency is: ␣ →  holds on R if in any legal relation r ( R), for all pairs of tuples t1 and t2 in r such that t1 [␣] = t2 [␣], it is also the case that t1 [] = t2 [].
8.22
Explain what is meant by repetition of information and inability to represent information. Explain why each of these properties may indicate a bad relational-database design. Answer: • Repetition of information is a condition in a relational database where the values of one attribute are determined by the values of another attribute in the same relation, and both values are repeated throughout the relation. This is a bad relational database design because it increases the storage required for the relation and it makes updating the relation more difficult, and can lead to inconsistent data if updates are done to one copy of the value, but not to another. • Inability to represent information is a condition where a relationship exists among only a proper subset of the attributes in a relation. This is bad relational database design because all the unrelated attributes must be filled with null values otherwise a tuple without the unrelated information cannot be inserted into the relation. • Inability to represent information can also occur because of loss of information which results from the decomposition of one relation into two relations, which cannot be combined to recreate the original relation. Such a lossy decomposition may happen implicitly, even without explicitly carrying out decomposition, if the initial relational schema itself corresponds to the decomposition.
数据库英文版第六版课后答案 (41)

building Packard Painter Taylor Watson Watson
room number 101 514 3128 100 120
157
158 Chapter 20 Data Warehousing and Mining
capacity
500 10 70 30 50
20.7 Explain why the nested-loops join algorithm (see Section 12.5.1) would work poorly on database stored in a column-oriented manner. Describe an alternative algorithm that would work better and explain why your solution is better. Answer: If the nested-loops join algorithm is used as is, it would require tuples for each of the relations to be assembled before they are joined. Assembling tuples can be expensive in a column store, since each attribute may come from a separate area of the disk; the overhead of assembly would be particularly wasteful if many tuples do not satisfy the join condition and would be discarded. In such a situation it would be better to first find which tuples match by accessing only the join columns of the relations. Sort-merge join, hash join, or indexed nested loops join can be used for this task. After the join is performed, only tuples that get output by the join need to be assembled; assembly can be done by sorting the join result on the record identifier of one of the relations and accessing the corresponding attributes, then resorting on record identifiers of the other relation to access its attributes.
数据库课后题答案

数据库课后题答案1)查询全体图书的图书号,书名,作者,出版社,单价。
SELECT * FROM 图书2)查询全体图书的信息,其中单价打8折,并且将该列设置别名为’打折价’ 。
SELECT 图书号,书名,作者,出版社,单价*0.8 ‘打折价’ FROM 图书3)显示所有借阅者的读者号,并去掉重复行。
SELECT DISTINCT 读者号FROM 借阅4)查询所有单价在20到30之间的图书信息。
SELECT * FROM 图书WHERE 单价BETWEEN 20 AND 305)查询所有单价不在20到30之间的图书信息。
SELECT * FROM 图书WHERE 单价NOT BETWEEN 20.00 AND 30.006)查询机械工业出版社、科学出版社、人民邮电出版社的图书信息SELECT * FROM 图书WHERE 出版社IN (‘机械工业出版社’, ‘科学出版社’, ‘人民邮电出版社’)7)查询既不是机械工业出版社、也不是科学出版社出版的图书信息SELECT * FROM 图书WHERE 出版社NOT IN (‘机械工业出版社’, ‘科学出版社’)8)查找姓名的第二个字符是’建’并且只有两三个字符的读者的读者号、姓名。
SELECT 读者号,姓名FROM 读者WHERE 姓名LIKE ‘_建_’9)查找姓名以’王’开头的所有读者的读者号、姓名。
SELECT 读者号,姓名FROM 读者WHERE 姓名LIKE ‘王%’10)查找姓名以’王’、’张’或’李’开头的所有读者的读者号、姓名。
SELECT 读者号,姓名FROM 读者WHERE 姓名LIKE ‘[王张李]%’11)查找姓名不是以’王’、’张’或’李’开头的所有读者的读者号、姓名。
SELECT 读者号,姓名FROM 读者WHERE 姓名NOT LIKE ‘[王张李]%’12)查询无归还日期的借阅信息。
SELECT * FROM 借阅WHERE 归还日期IS NULL13)查询有归还日期的借阅信息。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
8.20
68
Chapter 8 Relational Database Design
8.21
Normalize the following schema, with given constraints, to 4NF. books(accessionno, isbn, title, author, publisher) users(userid, name, deptid, deptname) accessionno → isbn isbn → title isbn → publisher isbn → → author userid → name userid → deptid deptid → deptname Answer: In books, we see that isbn → → title, publisher, author and yet, isbn is not a super key. Thus, we break books into books accnno(accessionno, isbn) books details(isbn, title, publisher, author) After this, we still have isbn → → author but neither is isbn a primary key of book details, nor are the attributes of book details equal to {isbn} ∪ {author}. Therefore we decompose book details again into books details1(isbn, title, publisher) books authors(isbn, author) Similarly, in users, deptid → deptname and yet, deptid is not a super key. Hence, we break users to users(userid, name, deptid) departments(deptid, deptname)
CHAPTER
8
Relational Database Design
This chapter presents the principles of relational database design. Undergraduates frequently find this chapter difficult. It is acceptable to cover only Sections 8.1 and 8.3 for classes that find the material particularly difficult. However, a careful study of data dependencies and normalization is a good way to introduce students to the formal aspects of relational database theory. There are many ways of stating the definitions of the normal forms. We have chosen a style which we think is the easiest to present and which most clearly conveys the intuition of the normal forms.
Exercises
8.19 Give a lossless-join decomposition into BCNF of schema R of Exercise 8.1. Answer: From Exercise 8.6, we know that B → D is nontrivial and the left hand side is not a superkey. By the algorithm of Figure 8.11 we derive the relations {( A, B , C , E ), ( B , D)}. This is in BCNF. Give a lossless-join, dependency-preserving decomposition into 3NF of schema R of Practice Exercise 8.1. Answer: First we note that the dependencies given in Practice Exercise 8.1 form a canonical cover. Generating the schema from the algorithm of Figure 8.12 we get R′ = {( A, B , C ), (C , D, E ), ( B , D), ( E , A)}. Schema ( A, B , C ) contains a candidate key. Therefore R′ is a third normal form dependency-preserving lossless-join decomposition. Note that the original schema R = ( A, B , C , D, E ) is already in 3NF. Thus, it was not necessary to apply the algorithm as we have done above. The single original schema is trivially a lossless join, dependency-preserving decomposition.
Exercises
69
We verify that there are no further functional or multivalued dependencies that cause violation of 4NF, so the final set of relations are:
books accnno(accessionno, isbn) books details1(isbn, title, publisher) books authors(isbn, author) users(userid, name, deptid) departments(deptid, deptname)
8.23
Why are certain functional dependencies called trivial functional dependencies? Answer: Certain functional dependencies are called trivial functional dependencies because they are satisfied by all relations. Use the definition of functional dependency to argue that each of Armstrong’s axioms (reflexivity, augmentation, and transitivity) is sound. Answependency is: ␣ →  holds on R if in any legal relation r ( R), for all pairs of tuples t1 and t2 in r such that t1 [␣] = t2 [␣], it is also the case that t1 [] = t2 [].
8.24
70
Chapter 8 Relational Database Design
Reflexivity rule: if ␣ is a set of attributes, and  ⊆ ␣, then ␣ → . Assume ∃ t1 and t2 such that t1 [␣] = t2 [␣] t1 [] = t2 [] since  ⊆ ␣ ␣ →  definition of FD Augmentation rule: if ␣ → , and ␥ is a set of attributes, then ␥ ␣ → ␥ . Assume ∃ t1 , t2 such that t1 [␥ ␣] = t2 [␥ ␣] t1 [␥ ] = t2 [␥ ] ␥ ⊆ ␥␣ t1 [␣] = t2 [␣] ␣ ⊆ ␥␣ t1 [] = t2 [] definition of ␣ →  t1 [␥ ] = t2 [␥ ] ␥ = ␥ ∪  ␥␣ → ␥ definition of FD Transitivity rule: if ␣ →  and  → ␥ , then ␣ → ␥ . Assume ∃ t1 , t2 such that t1 [␣] = t2 [␣] t1 [] = t2 [] t1 [␥ ] = t2 [␥ ] ␣ → ␥ 8.25 definition of ␣ →  definition of  → ␥ definition of FD
8.22
Explain what is meant by repetition of information and inability to represent information. Explain why each of these properties may indicate a bad relational-database design. Answer: • Repetition of information is a condition in a relational database where the values of one attribute are determined by the values of another attribute in the same relation, and both values are repeated throughout the relation. This is a bad relational database design because it increases the storage required for the relation and it makes updating the relation more difficult, and can lead to inconsistent data if updates are done to one copy of the value, but not to another. • Inability to represent information is a condition where a relationship exists among only a proper subset of the attributes in a relation. This is bad relational database design because all the unrelated attributes must be filled with null values otherwise a tuple without the unrelated information cannot be inserted into the relation. • Inability to represent information can also occur because of loss of information which results from the decomposition of one relation into two relations, which cannot be combined to recreate the original relation. Such a lossy decomposition may happen implicitly, even without explicitly carrying out decomposition, if the initial relational schema itself corresponds to the decomposition.
