Computing the lattice of all fixpoints of a fuzzy closure operator
庞加莱 关于数学创造(翻译)

庞加莱关于数学创造(翻译)庞加莱关于数学创造(翻译)2010-11-15 15:37:21昨天刘未鹏在日志中提到庞加莱关于数学创造的文章,顺手译成了中文,如下:Mathematical Creation数学创造How is mathematics made? What sort of brain is it that can compose the propositions and systems of mathematics? How do the mental processes of the geometer or algebraist compare with those of the musician, the poet,the painter, the chess player? In mathematical creation which are the key elements? Intuition? An exquisite sense of space and time? The precision of a calculating machine?A powerful memory? Formidable skill in following complex logical sequences? A supreme capacity for concentration? 数学是由什么构成的?哪种类型的大脑能够创造数学的定理和系统?几何学家或是代数学家的思维活动和音乐家、是人画家和象棋选手有什么不同?数学创造中,哪些是关键元素?直觉?空间和时间的精确感觉?机器一般的计算准确性?超强的记忆力?复杂逻辑推导的超强技能?极好的注意力?The essay below, delivered in the first years of this century as a lecture before the Psychological Society in Paris, is the most celebrated of the attempts to describe what goes on in the mathematician's brain. Its author, Henri Poincaré, cousin of Raymond, the politician, was peculiarly fitted to undertake the task. One of the foremost mathematicians of all time, unrivaled as an analyst and mathematical physicist, Poincaré was known also as a brilliantly lucid expositor of the philosophy of science. These writings are of the first importance as professional treatises for scientists and are at the same time accessible, in large part, to the understanding of the thoughtful layman.下面的文章,是本世纪(20世纪)初期在巴黎心理学会上做的一次报告,是描述关于数学家大脑如何运转的最著名的尝试。
有效质量 英语

有效质量英语Effective MassThe concept of effective mass is a fundamental principle in physics that has far-reaching implications in various fields, from semiconductor technology to particle physics. Effective mass is a crucial parameter that describes the behavior of particles, particularly in the context of their interaction with external forces or fields.At its core, effective mass is a measure of the "apparent" or "effective" mass of a particle, which can differ from its actual or rest mass. This difference arises due to the complex interactions between the particle and its surrounding environment, such as the potential energy fields or the crystal structure of a material.In the case of a free particle, such as an electron in a vacuum, its effective mass is equal to its rest mass. However, when a particle is subjected to a potential energy field or is embedded within a material, its effective mass can deviate significantly from its rest mass. This phenomenon is particularly evident in semiconductor materials, where the effective mass of charge carriers (electrons and holes) plays a crucial role in determining the material's electronic andoptical properties.In semiconductor materials, the periodic potential created by the crystal lattice can significantly modify the effective mass of charge carriers. This modification is a result of the complex interactions between the charge carriers and the periodic potential, which can be described using the principles of quantum mechanics.The effective mass of charge carriers in semiconductors is a key parameter that determines the mobility, conductivity, and other important characteristics of the material. For example, in the design of electronic devices such as transistors and integrated circuits, the effective mass of charge carriers is a critical factor in optimizing device performance and efficiency.Moreover, the concept of effective mass extends beyond the realm of semiconductor physics. In particle physics, the effective mass of particles, such as subatomic particles or quasiparticles, is crucial for understanding their behavior and interactions within complex systems. For instance, the effective mass of particles in high-energy physics experiments can provide insights into the fundamental nature of matter and the forces that govern the universe.One of the most fascinating aspects of effective mass is its ability to exhibit exotic and counterintuitive behavior. In certain materials, suchas graphene or topological insulators, the charge carriers can exhibit an effective mass that is negative or even diverges to infinity. These unusual effective mass properties can lead to the emergence of novel physical phenomena, such as the quantum Hall effect or the formation of Dirac or Weyl fermions.The study of effective mass has also been instrumental in the development of cutting-edge technologies, such as quantum computing and spintronics. In these fields, the manipulation and control of the effective mass of charge carriers or spin-polarized particles are crucial for the realization of advanced devices and the exploration of quantum mechanical effects.In conclusion, the concept of effective mass is a fundamental principle in physics that has far-reaching implications across various disciplines. From semiconductor technology to particle physics, the effective mass of particles plays a vital role in understanding and predicting the behavior of complex systems. As scientific research continues to push the boundaries of our understanding, the study of effective mass will undoubtedly remain a crucial area of investigation, with the potential to unlock new frontiers in our quest to unravel the mysteries of the physical world.。
Exact algorithms for the minimum latency problem

Exact algorithms for the minimum latency problemBang Ye Wu∗,Zheng-Nan Huang,Fu-Jie ZhanDept.of Computer Science and Information Engineering,Shu-Te University,YenChau,Kaohsiung,Taiwan824,R.O.C.Key words:algorithms,minimum latency problem,dynamic programming,branch and bound1IntroductionLet G=(V,E,w)be an undirected graph with positive weight w(e)on each edge e∈E. Given a starting vertex s∈V and a subset U⊂V as the demand vertex set,the minimum latency problem(MLP)asks for a tour P starting at s and visiting each demand vertex at least once such that the total latency of all demand vertices is minimized,in which the latency of a vertex is the length of the path from s to thefirst visit of the vertex.The MLP is an important problem in computer science and operations research,and is also known as the delivery man problem or the traveling repairman problem.Similar to the well-known traveling salesperson problem(TSP),in the MLP we are asked tofind an“optimal”way for routing a server passing through the demand vertices.The difference is the objective functions.The latency of a vertex can be thought of as the delay of the service.In the MLP we care about the total delay(service quality),while the total length(service cost)is concerned in the TSP.The MLP on a metric space is NP-hard and also MAX-SNP-hard[4].Polynomial time algorithms are only known for very special graphs,such as paths[1,6],edge-unweighted trees[9],trees of diameter3[4],trees of constant number of leaves[8],or graphs with similar structure[12].Even for caterpillars(paths with edges sticking out),no polynomial time algorithm has been reported.In a recent work,it is shown that the MLP on edge-weighted trees is NP-hard[11].Due to the NP-hardness,many works ∗corresponding author(bangye@.tw)have been devoted to the approximation algorithms[2,3,4,7,8],and the current best approximation ratio is3.59[5].More references to exact and approximation algorithms can be found in those papers.“Dynamic programming”(DP)and“branch-and-bound”(B&B)are two popular strate-gies used to exactly solve NP-hard problems without exhaustive search.As pointed out in [12],the MLP can be exactly solved by a dynamic programming algorithm.However,the algorithm is still very time-consuming.By designing non-trivial lower bound functions and using a technique combining the advantages of both DP and B&B,we developed a series of exact algorithms for the MLP.Experimental results on both random and real data are also reported in this paper.The results show that our algorithm is much more efficient than the DP algorithm and the B&B algorithm,and we believe that the technique can be also applied to some other problems.2PreliminariesIn this paper,a graph is a simple and connected graph with a nonnegative weight on each edge.Throughout this paper,the input graph is G,and n is the number of nodes of graph G.An origin(starting vertex)is a given vertex of G.A tour is a route from the origin and visiting each vertex at least once.A subtour is a partial or a complete tour starting at the origin.Let H be a subgraph or a subtour.The set of vertices of H is denoted by V(H).For u,v∈V(G),we use d G(u,v)to denote the length of the shortest path between u and v on G.For a subtour P,d P(u,v)denotes the distance from thefirst visit of u to thefirst visit of v in P,and w(P)denotes the length of P.Definition1:Let P be a subtour starting at s on graph G.For a demand vertex v visited by P,the latency of v is defined as d P(s,v),which is the distance from the origin to thefirstvisit of v on P.The latency of a tour P is defined by L(P)=v∈Ud P(s,v),in which U isthe demand vertex set.In general,the input graph of a MLP may be any simple connected graph with nonnegative edge weights,and the demand vertex set does not necessarily include all the vertices.Ametric graph is a complete graph with edge weights satisfying the triangle inequality.By a simple reduction,we may assume that the input graph is always a metric graph and all the vertices are the demand vertices.Let G=(V,E,w)be the underlying graph and U⊂V be the demand vertex set.Wefirst compute the metric closure¯G=(U,U×U,¯w)of G,in which the weight on each edge is the shortest path length of the two endpoints in G.For any tour ¯P on¯G,we can construct a corresponding tour P on G by simply replacing each edge in¯P with the corresponding shortest path on G.It is easy to see that L(P)≤L(¯P).Conversely, given any tour P on G,we can obtain a tour¯P on¯G by eliminating all vertices not in U. Since the edge weight is the shortest path length,we have L(¯P)≤L(P).Consequently the minimum latencies of the two graphs are the same.Furthermore,if there exists an O(T(n)) time exact or approximation algorithm for the MLP on metric graphs,the MLP on general graphs can be solved in O(T(n)+f(n))time with the same performance guarantee,in which f(n)is the time complexity for computing the all-pairs shortest path length.In the remaining paragraphs,we assume that the input graph G is a metric graph and each vertex is a demand vertex.It should also be noted that the optimal tour never visits the same vertex twice in a metric graph.3Algorithms3.1Pure dynamic programmingTofind the optimal tour of a MLP,a brute force algorithm checking all permutations of the vertices except for the origin will takeΩ((n−1)!)time.In[12],it was pointed out that the MLP can be solved in O(n22n)time by a dynamic programming algorithm.For the completeness,we briefly explain the algorithm in the following.Definition2:Let P be a subtour on graph G.Define a cost function c(P)=L(P)+ (n−|V(P)|)w(P),i.e.,c(P)is the total latency of the visited vertices plus the length of P multiplied by the number of vertices not been visited.Let P1and P0be two routes such that the last vertex of P1is thefirst vertex of P0.We use P1//P0to denote the route obtained by concatenating P1and P0.For a subtour P,we say that P has configuration(R,v),in which R=V(P)and v is the last vertex of P. The dynamic programming algorithm is based on the following property which can be easily shown by definition.It also explains the reason why we define the cost function c in such a way.Claim1:Let P1and P2be subtours with the same configuration and c(P1)≤c(P2).If Y2=P2//P0is a complete tour,i.e.,P0is a route starting at the last vertex of P2and visiting all the remaining vertices,then Y1=P1//P0is also a tour and L(Y1)≤L(Y2).Tofind the minimum latency,by Claim1,we only need to keep one subtour for each possible configuration.The dynamic programming algorithm starts at the subtour containing only the origin and computes the best subtour for each configuration in the order that the number of the visited vertex is from small to large.The time complexity then follows that there are O(n2n)configurations and we generate O(n)subtours when a subtour is extended by one vertex.3.2Dynamic programming with pruningTo make the program more efficient,we introduce a pruning technique in the DP algorithm, which is similar to the one used in a typical branch-and-bound algorithm.While the program is running,we always record an upper bound(UB)of the optimal,which is the latency of some feasible tour.For each generated subtour P,we compute a lower bound of P,which is an under estimate of any complete tour containing P as a prefix.If the lower bound of a subtour is no less than UB,we can prune the subtour without affecting the optimality of the final solution.The key points are how we compute the UB and how we estimate the lower bound of a subtour.A pure DP algorithm does not generate any complete tour until it reaches the configura-tions consisting of the set of all vertices.To get an upper bound,we employ a simple greedy algorithm to build a tour.The greedy algorithm uses the“nearest vertexfirst”strategy. Beginning with a subtour containing only the origin,we repeatedly augment the subtour by one vertex until all vertices are included.At each iteration,we choose the vertex which isnearest to the stopping vertex of the subtour and has not been visited.Obviously,such a tour can be computed in O(n2)time.In addition to the initial stage,our algorithm uses the greedy method to build a tour whenever a new subtour is generated,and keep the current best solution.Algorithm DPwP MLPInput:A metric graph G=(V,E,w)and an origin s∈V.Output:The latency of the optimal tour.//Q i is a queue for storing the generated subtours consisting of i vertices.1:Initiate Q1,and insert subtour(s)into Q1.2:Get an upper bound UB of the optimal.3:For i←1to n−1do4:For each subtour P in Q i do5:compute an upper bound UB from P;6:if UB <UB7:UB←UB ;8:For each vertex v not in V(P)do9:generate a subtour P =P//(v);10:if there exists a subtour with the same configuration in Q i+111:keep the one with better c(·)value;12:else13:compute a lower bound LB of P ;14:if LB<UB then insert P into Q i+1;15:Output UB as the minimum latency.At Step10,we need to search a configuration in Q i+1.In a typical DP algorithm, such a step can be implemented by employing an array,of which each element is for one configuration.By suitably encoding the configurations,the search can be done in only one memory access.However,such a simple method is not suitable for our algorithm since it requires to check every configuration,and this is what we want to avoid.Because of the large size of the queue,a good data structure should be used.In our program,we use an AVL tree.In the next section,we shall present the experimental results,and it shows that the improvement is very significant,compared to a link list implementation.As in a typical B&B algorithm,the lower bound function is a key point to the efficiency of the algorithm.The running time depends heavily on two factors:the number of the generated subtours and the time to compute a lower bound of a subtour.A lower bound function eliminating many subtours may be bad if it suffers from a long computation time.In the following,let G=(V,E,w)be the input metric graph and s be the origin.Let P be a subtour stopping at a vertex r and Y=P//P0be the best tour consisting of P as its prefix. Let¯V=V−V(P),¯n=|¯V|,and P0=(v0=r,v1,v2...,v¯n).Remember that the best tour never visits a vertex twice in a metric graph.A function is a LB function of P if the latency of Y is lower bounded by the value of the function.We begin with a simple observation.For any1≤i≤¯n,by the triangle inequality,we haved Y(s,v i)=w(P)+d Y(r,v i)≥w(P)+w(r,v i).Therefore,L(Y)≥L(P)+¯ni=1(w(P)+w(r,v i))=L(P)+¯n w(P)+¯ni=1w(r,v i)=c(P)+v∈¯Vw(r,v). The following property is obvious,and we omit the proof.Claim2:The function B1(P)=c(P)+v∈¯Vw(r,v)is a LB function of P and can becomputed in O(n)time.Next,we generalize the simple idea.Let l i(r,v)be the length of the shortest i-edges path between vertices r and v.Thereby an i-edges path is a path consisting of exactly i different edges.Wefirst show the following property.Lemma3:For any vertices r and v,l i(r,v)≤l j(r,v)if i<j.Proof:It is sufficient to show that l i(r,v)≤l i+1(r,v).Let Q=(r,u1,u2,...,u i+1=v) be the shortest(i+1)-edges path.Then Q =(r,u2,...,u i+1)is an i-edges path,and w(Q )≤w(Q)since w(r,u2)≤w(r,u1)+w(u1,u2)by the triangle inequality.By the definition of li,we have l i(r,v)≤w(Q ),and this completes the proof.Note that l1(r,v)is exactly w(r,v)by definition.By the monotonic property of l i,it is natural to use a more general l i as the lower bound function.In the next theorem,we establish a family of lower bound functions.Note that the function B1coincides with the one in Claim 2.Theorem4:Let k≥1.The functionB k(P)=c(P)+v∈¯V l k(r,v)−k−1i=1maxv∈¯V{l k(r,v)−l i(r,v)}is a LB function of P and can be computed in O(kn)time if the value l i(r,v)is available for any1≤i≤k and any v∈¯V.Proof:Clearly l i(r,v i)≤d Y(r,v i)since d Y(r,v i)is the length of an i-edges path while l i(r,v i)is the minimum among all possible such paths.Furthermore,by Lemma3,we have l i(r,v)≤d Y(r,v j)for any j≥i,and therefore,for k≥1,L(Y)=c(P)+¯ni=1d Y(r,v i)≥c(P)+¯ni=1l i(r,v i)≥c(P)+k−1i=1l i(r,v i)+¯ni=kl k(r,v i)(1)For i<k,we rewritel i(r,v i)=l k(r,v i)−(l k(r,v i)−l i(r,v i)) in Eq.(1),and obtainL(Y)≥c(P)+¯ni=1l k(r,v i)−k−1i=1(l k(r,v i)−l i(r,v i))≥c(P)+v∈¯V l k(r,v)−k−1i=1maxv∈¯V{l k(r,v)−l i(r,v)}Finally the time complexity is obviously O(kn).Although it is very time-consuming to compute l k even for small k,we compute the values only once in a preprocessing stage.As a subtour is generated,we need only O(kn)time to obtain a lower bound.We summarize the time complexity of the algorithm in the next theorem.Theorem5:The algorithm DPwP MLP with lower bound function B k runs in O(n k+1+ n2T)time,in which T is the number of generated subtours.Proof:To employ B k as the lower bound function,we compute l i(u,v)for any1≤i≤k and each vertex pair(u,v)in a preprocessing stage.Since l i(u,v)is the length of the shortest i-edges path and an i-edges path containing exactly i−1intermediate vertices,all these values can be computed in O(n k+1)time by exhaustively checking all possible permutations.For each generated subtour,at Step5–7,we compute a feasible tour and update the upper bound if necessary,and it takes O(n2)time.For searching the configuration in Q i+1at Step 10,by employing an AVL tree,we perform O(log|Q i+1|)comparisons of configurations.Since there are at most n2n configurations,the number of comparisons is O(n).A configuration consists of a vertex and a set of up to n paring two configurations takes O(n) time.Therefore,the total time for searching the AVL trees is O(n2T),in which T is the total number of generated subtours.For Step13,by Theorem4,the time for computing the lower bounds of all subtours is O(knT).For Step14,since inserting an element into the AVL tree has the same time complexity as the searching,the total time for all the insertions is also O(n2T).In summary, the time complexity of the algorithm is therefore O(n k+1+n2T).4The experimental resultsWe implemented the algorithms in C language and investigated their practical performances. All the tests were performed on personal computers,each of which is equipped with an Intel Pentium IV2.4GHz CPU and256M bytes memory.Two types of test data were used: random data and real data.For each test case,the running time includes all the steps except for generating or calculating the input distances.4.1Random dataThe random data were generated artificially with edge weights drawn from uniform distribu-tion.All the edge weights are integers between1and1024.In Table1,we summarize the maximum running time for each program in the tests on random data.Algorithm DPP(i) denote the algorithm DPwP MLP with lower bound function B i.For the sake of compari-Table1:The maximum running time in the random data tests(seconds,K=1000)BF10.5K165K-------DP 1.45 3.278.3817.740.096.812.5K*--DPP L 1.07 2.7725.299.4367 4.07K8.41K--DPP(1)0.300.50 2.03 4.1911.343.781.018011.7K* DPP(2)0.220.38 1.44 2.947.6629.154.6166302 DPP(3)0.170.280.91 2.03 5.2717.737.2128247 DPP(4)0.250.47 1.00 2.06 4.9111.125.896.6176 DPP(5) 1.45 2.56 4.928.0313.722.740.5105165B&B(1) 1.80 3.9115.055.7161 1.77K 2.97K 6.50K-Table2:The maximum number of generated subtours in random data tests(M=106)n=18 1.1M0.23M0.12M0.11M789896985514.8M n=2110.5M 2.96M 1.99M 1.32M0.83M0.51M593M n=23-9.17M7.35M 6.51M 4.51M 3.26M-son,we also implemented the brute-force method(labeled by BF)and the branch-and-bound method(labeled by B&B(1),using the lower bound function B1).The BF computes the op-timal solution by simply checking all the possible permutations.The B&B(1)program is similar to DPP(1)except that it does not merge the subtours with the same configuration. It uses the depth-first strategy to choose the subtour to be extended,and the chosen subtour is augmented by each of the vertices not been visited yet.In fact,we also implemented the branch-and-bound method with B i,i>1.But their behaviors are similar,and we only list B&B(1)for comparison.Algorithm DPP L is the same as DPP(1)but using a link list instead of an AVL tree as the data structure for storing the configurations.Basically at least one hundred data instances were used for each problem size.But,for BF and DP,only few instances are tested because their performances almost do not vary with the input data of the same number of vertices.Some cells in the table are marked with “-”to indicate that we did not complete the tests on these cases because some data instances took too long to complete.A“*”in a cell indicates that the long running time is caused by“disk swap”in the virtual memory system.In Table2,we list the maximum number of subtours generated by each program for some typical values of n.Table3:The running time in the real data tests(seconds)Ulysses160.090.080.090.130.330.45 Ulysses22 3.40 3.53 3.50 3.42 5.5554.47 Gr2454.4751.5443.6434.4130.23285.17 Fri2639.6137.6432.7526.0927.41257.60 4.2Real dataIn addition to the random data,we also used real data to test the performances of the algorithms.The data instances are chosen from TSPLIB[10]for the sake of their problem sizes.The results are shown in Table3.Note that the number appeared in the name indicates the number of vertices for each instance.In fact,we have also performed some other tests on partial data drawn from larger instances in TSPLIB.The results are similar.Roughly speaking,problems with25–26vertices can be solved in paring with the results of random data,the performances are much better.The reason may be that the real data are more structured and therefore the bad cases rarely happen.5Discussion and concluding remarksBy the experimental results and some other observations in our development,we make the following conclusions.•The algorithm DPwP MLP takes the advantages of both the dynamic programming and the branch-and-bound strategies,and significantly improves the performance.•Using a good data structure such as the AVL tree in our program is very important.The reason is obvious by knowing the numbers of the generated subtours(Table2).•For small integers j>i,DPP(j)is better than DPP(i)when n exceeds some value.•Theoretically,we can improve the lower bound by restricting that the i-edge path can only visit the vertices in¯V.But it suffers from a long computation time and therefore has a worse performance.In fact,we have tried several other lower bound functions.Some of them eliminate much more subtours than B1but has a worse performance.References[1]F.Afrati,S.Cosmadakis,C.Papadimitriou,G.Papageorgiou,and N.Papakostantinou,The complexity of the traveling repairman problem,Theoretical Informatics and Appli-cations,20(1)(1986)79–87.[2]A.Archer and D.P.Williamson,Faster approximation algorithms for the minimum la-tency problem,in Proc.14th ACM-SIAM Symposium on Discrete Algorithms(SODA 2003),2003pp.88–96.[3]S.Arora and G.Karakostas,Approximation schemes for minimum latency problems,SIAM put.,32(5)(2003)1317-1337.[4]A.Blum,P.Chalasani,D.Coppersmith,B.Pulleyblank,P.Raghavan,and M.Sudan,Theminimum latency problem,in Proc.26th ACM Symposium on the Theory of Computing (STOC’94),1994pp.163–171.[5]K.Chaudhuri,B.Godfrey,S.Rao,and K.Talwar,Paths,Trees,and Minimum LatencyTours,in Proc.44th Symposium on Foundations of Computer Science(FOCS2003),2003 pp.36–45.[6]A.Garcia,P.Jodr´a,and J.Tejel,A note on the traveling repairmen problem,Networks,40(1)(2002)27–31.[7]M.Goemans and J.Kleinberg,An improved approximation ratio for the minimum latencyproblem,Math.Program.,82(1998)114–124.[8]E.Koutsoupias,C.Papadimitriou and M.Yannakakis,Searching afixed graph,in Proc.23nd Colloquium on Automata,Languages and Programming,Lecture Notes in Comput.Sci.,Vol.1099,1996,pp.280–289.[9]E.Minieka,The delivery man problem on a tree network,Ann.Oper.Res.,18(1989)261–266.[10]G.Reinelt,TSPLIB—a traveling salesman problem library,ORSA puting,3(1991)376–384.See also http://www.iwr.uni-heidelberg.de/groups/comopt/software-/tsplib95/.[11]R.Sitters,The minimum latency problem is NP-hard for weighted trees,in Proc.9thInternational IPCO Conference,Lecture Notes in Comput.Sci.,Vol.2337,2002,pp.230–239.[12]B.Y.Wu,Polynomial time algorithms for some minimum latency problems,Inf.Process.Lett.,75(5)(2000)225–229.11。
算法导论 第三版 第22章 答案 英

Michelle Bodnar, Andrew Lohr April 12, 2016
Exercise 22.1-1 Since it seems as though the list for the neighbors of each vertex v is just an undecorated list, to find the length of each would take time O(out − degree(v )). So, the total cost will be v∈V O(outdegree(v )) = O(|E | + |V |). Note that the |V | showing up in the asymptotics is necessary, because it still takes a constant amount of time to know that a list is empty. This time could be reduced to O(|V |) if for each list in the adjacency list representation, we just also stored its length. To compute the in degree of each vertex, we will have to scan through all of the adjacency lists and keep counters for how many times each vertex has appeared. As in the previous case, the time to scan through all of the adjacency lists takes time O(|E | + |V |). Exercise 22.1-2 The adjacency list representation: 1 : 2, 3 2 : 1, 4, 5 3 : 1, 6, 7 4:2 5:5 6:3 7 : 3.
铝的晶格常数-体弹模量及弹性常数分子模拟

铝的晶格常数-体弹模量及弹性常数分子模拟CCCalculation of material lattice constant and bulk modulus 2012 Calculation of materiallatticeconstantand bulk modulusSummary :Aluminum is one of the world's most used metals, the calculated aluminum lattice constant and bulk modulus can be used to improve the performance of the aluminum consequently make better use of aluminum. In virtue of molecular dynamics simulation software ,we can solve the lattice constant . By the derivative of the lattice con s tant, the bulk modulus can be obtained. The elastic constants of a material display the elasticity and we can use the software material studio to simulate and get them. The simulation results match the experimental values. Key words:Aluminum, lattice constant, bulk modulus, elastic constant , simulation.Introduction:In materials science, in order to facilitate analysis about the way in which the crystal particles are arranged, the basic unit can be removed from the crystal lattice as a representative (usually the smallest parallel hexahedron) as a compositionunit of dot matrix, called a cell (i.e. solid State Physics "original cell" concept); lattice constant (or so-called lattice constant) refers to the side length of the unit cell, in other words, the side length of each parallel hexahedral cells. Lattice constant is an important basic parameters of crystal structure. Figure A is the basic form of the lattice constant.Figure ALattice constant is a basic structural parameter,which has a direct relationship with the bondings between the atoms ,of the crystal substance. It reflects the changes in the internal composition of the crystal of the lattice constant, force state changes, etc.The bulk modulus (K or B) of a substance measures thesubstance's resistance touniform compression. It isdefined as the ratio of theinfinitesimal pressure increaseto the resulting relative decreaseof the volume. Its base unit is thepascal. Figure B describes theeffect of bulk modulus.Figure BThe bulk modulus canbe formally defined by theequation:where is pressure, isvolume, and denotes thederivative of pressure withrespect to volume.Our research object isaluminum,whose atomicnumber is 13 and relative massis 27.The reserves of aluminumranks only second to ferrumcompared with other metallicelements. Aluminum andaluminum alloy are consideredthe most economic andapplicable in many applicationfields as a consequence of theirexcellent properties. What’smore,increased usage ofaluminum will result fromdesigners' increased familiaritywith the metal and solution tomanufacturing problems thatlimit some applications.The crystal structure of aluminum is face-centered cubic. The experimental value of lattice constant and bulk modulus are 0.0.40491nm and 79.2Gpa. Computing theory and methods:Our simulation is on the basis that aluminum is offace-centered cubic crystal structure. We can get the exact value of lattice constant in virtue of molecular dynamics simulation software. Then by the derivation of lattice constant for energy E,we obtain bulk modulus.To start with ,compile a script for the use of operation and simulation in lammps. We set periodicboundary conditions in the script and create an analog box,whose x ,y ,z coordinate values are all confined to [0,3].Run the script in lammps, calculating the potential energy,kinetic energy as well as the nearest neighbor atoms for each atom. Finally put out the potential energy function of aluminum.Extract the datas under the linux system produced by lammps to continue the computation by means of matlab,from which we can get the lattice constant through several times of matching.Figure CFigure C——the curve shows the relationship between cohesive energy and lattice constant,which is what we get in the process of computing in matlab,points out the lattice constant corresponding with the least cohesive energy. The horizontal ordinate of the rock bottom stand for the lattice constant of aluminum which can be clearly located as 0.40500nm.Since we have obtained the lattice constant,we simulated the visualization of aluminu’s crystal structure. Figure D is what we get through the visualization.Figure DThe bulk modulus is defined as:As for cubic cell,the formula can be transformed into the following pattern:The bulk modulus can be calculated with the formula above combined with the latticeconstant. Finally,the bulk modulus is 78.1Gpa.Besides,to enrich our research, we have calculated the elastic constants of aluminum. Because of the symmetry of face-centered cubic,aluminum only has three elastic constants. To reach the target ,we have to establish a cell of aluminum in the software material studio in the first place and then transform it into a primitive cell. Figure E and figure F are the cell and the primitive cell we have established during the simulation .Figure EFigure FIt comes to the CASTEP step after the geometry optimization. We managed to makeE cut=350eV andK points=16*16*16 ,both of which are extremely importantand also sensitive to the calculation of elastic constant,after several trials. Figure G is the primitive cell that has been through the geometry optimization.Figure GThe calculated results are as follows:C11=106.2GpaC12=60.5GpaC44=28.7Gpa Correspondingly ,the experimental range of the three elastic constants are listed below:C11=108~112GpaC12=61.3~66GpaC44=27.9~28.5GpaAs we can see,although a little outside of the value range of the experimental standards, our results are right within the error range.Conclusion:Our group has calculated the lattice constant and bulk modulus of aluminum,both of which coincide with the experimental value,by means of lammps and matlab. Moreover ,we have found out that bulk modulus has a close relationshipwith temperature. As lattice constant haven’t made any change under small change of temperature while the energy of the material have changed,so we concluded that temperature change can influence bulk modulus as a consequence of the change of cohesive energy change resulting from temperature change.There are still problems in our research as you can see that the three elastic constants are a little out of the value range. But this group is the one closest to the experimental value. Our group have concluded that the errors result from the script which can affect the accuracy of the simulation.Besides,the most valuable thing we have learned is that we must seek the solutions and never give up in face of difficulties.References:[1]材料科学基础(胡赓祥、蔡珣、戎咏华上海交通大学出版社)[2]Ayton, Gary; Smondyrev, Alexander M; Bardenhagen, Scott G; McMurtry, Patrick; Voth, Gregory A.“Calculating the bulk modulus for a lipid bilayer with none quilibrium molecular dynamics simulation". Biophysical Society. 2002.[3]Cohen, Marvin (1985).CCCalculation of material lattice constant and bulk modulus 2012 "Calculation of bulk modulus ofdiamond and zinc-blende solids". Phys. Rev. B 32: 7988–7991. [4] Watson, I G; Lee, P D; Dashwood, R J; Young, P . Simulation of the Mechanical Properties of an Aluminum Matrix Composite using X-ray Microtomography: Physical Metallurgical and Materials Science. Springer Science & Business Media. 2006. [6] Ashley, Steven. Aluminum vehicle breaks new ground. Engineering--Mechanical Engineering. Feb 1994. [7] Sanders, Robert E, Jr; Farnsworth, David M. Trends in Aluminum Materials Usage forElectronics. Metallurgy. Oct2011.附文:lammps脚本units metalboundary p p patom_style atomicvariable i loop 20variable x equal 4.0+0.01*$ilattice fcc $xregion box block 0 3 0 3 0 3 create_box 1 boxcreate_atoms 1 boxpair_style adppair_coeff * * AlCu.adp Almass 1 27neighbor 1 binneigh_modify every 1 delay 5 check yes variable p equal pe/108variable r equal 108/($x*3)^3 timestep 0.005thermo 10compute 3 all pe/atomcompute 4 all ke/atomcompute 5 all coord/atom 3dump 1 all custom 100 dump.atom id xs ys zs c_3 c_4 c_5dump_modify 1format"%d %16.9g %16.9g %16.9g%16.9g %16.9g %g"min_style sdminimize 1.0e-12 1.0e-12 1000 1000print "@@@@ (latticeparameter,rho,energy per atom):$x$r $p"clearnext ijump in.al至于代码的含义,可参考其它资料或查询lammps官网manual。
Lecture14_Lattice_Structures
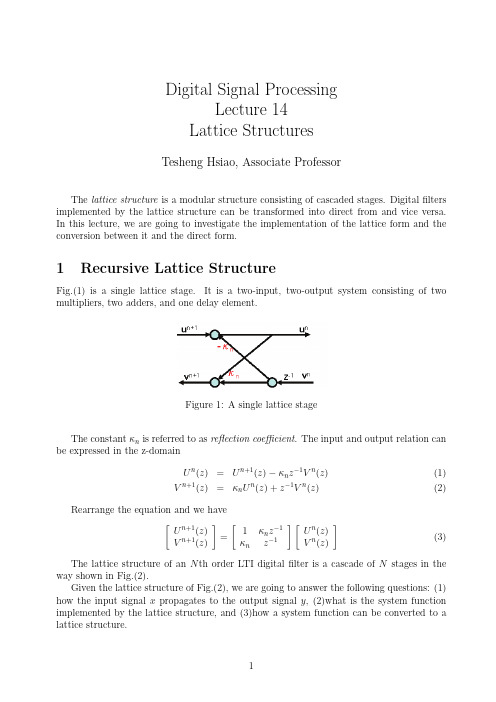
Digital Signal ProcessingLecture 14Lattice StructuresTesheng Hsiao,Associate ProfessorThe lattice structure is a modular structure consisting of cascaded stages.Digital filters implemented by the lattice structure can be transformed into direct from and vice versa.In this lecture,we are going to investigate the implementation of the lattice form and the conversion between it and the direct form.1Recursive Lattice StructureFig.(1)is a single lattice stage.It is a two-input,two-output system consisting of two multipliers,two adders,and one delayelement.Figure 1:A single lattice stageThe constant κn is referred to as reflection coefficient .The input and output relation can be expressed in the z-domainU n (z )=U n +1(z )−κn z −1V n (z )(1)V n +1(z )=κn U n (z )+z −1V n (z )(2)Rearrange the equation and we have[U n +1(z )V n +1(z )]=[1κn z −1κn z −1][U n (z )V n (z )](3)The lattice structure of an N th order LTI digital filter is a cascade of N stages in the way shown in Fig.(2).Given the lattice structure of Fig.(2),we are going to answer the following questions:(1)how the input signal x propagates to the output signal y ,(2)what is the system function implemented by the lattice structure,and (3)how a system function can be converted to a lattice structure.Figure2:Recursive lattice structure•Lattice FilteringThe output of the lattice structure can be calculated in a recursive way.Assume that the system is at initial rest;hence v n[−1]=0,n=0,1,···,N−1.From Fig.(2),for each time step k≥0,we haveinitial conditions:v n[−1]=0,n=0,1,···,N−1for k=0,1,2,···u N[k]=x[k]for n=N−1to0u n[k]=u n+1[k]−κn v n[k−1]v n+1[k]=κn u n[k]+v n[k−1]endv0[k]=u0[k]y[k]=N∑n=0λn v n[k]end•The system function of the lattice structureLetP n(z)=U n(z)U0(z),Q n(z)=V n(z)V0(z),n=0,1,2,···,NHence,Eq.(3)can be rewritten as[P n+1(z) Q n+1(z)]=[1κn z−1κn z−1][P n(z)Q n(z)],n=0,1,2,···,N−1(4) =[1κnκn1][P n(z)z−1Q n(z)],n=0,1,2,···,N−1(5)Note thatU0(z)=V0(z),P0(z)=Q0(z)=1,X(z)U0(z)=P N(z),Y(z)U0(z)=N∑n=0λn Q n(z)Therefore the system function H (z )isH (z )=Y (z )X (z )=∑N n =0λn Q n (z )P N (z )(6)If we expand Eq.(4),we obtain [P n (z )Q n (z )]=[1κn −1z −1κn −1z −1]···[1κ0z −1κ0z −1][11],n =0,1,···,N (7)It is clear from Eq.(7)that P n (z )and Q n (z )are polynomials of z −1of order n .From Eq.(6),P N (z )is the denominator of H (z )while ∑N n =0λn Q n (z )is the numerator ofH (z ).Note that the number of parameters in the lattice structure (κn ,n =0,···N −1and λn ,n =0,···,N )is the same as the number of coefficients of an N th order rational function.In summary,the system function H (z )can be determined by applying Eq.(4)recur-sively to find P n (z )and Q n (z ),n =1,2,···,N ,given Q 0(z )=P 0(z )=1.Then use Eq.(6)to determine H (z ).•Convert the direct form to the lattice structureLet P n (z )=p n 0+p n 1z −1+···+p n n z−n and Q n (z )=q n 0+q n 1z −1+···+q n n z −n ;From Eq.(7),we have [P 1(z )Q 1(z )]=[1κ0z −1κ0z −1][11]=[1+κ0z −1κ0+z −1][P 2(z )Q 2(z )]=[1κ1z −1κ1z −1][1+κ0z −1κ0+z −1]=[1+(κ0+κ0κ1)z −1+κ1z −2κ1+(κ1κ0+κ0)z −1+z −2]...=...Hence we conclude by induction that p n n =κn −1and q n n =1for n =0,1,2,···,N .Moreover we have the following lemma.Lemma 1Q n (z )=z −n P n (z −1),n =0,1,···,NProof:This lemma can be proved by induction.The n =0case is trivialFor n =1,P 1(z )=1+κ0z −1and Q 1(z )=κ0+z −1.Thus the equality holds.Suppose that the equality holds for n =k ,i.e.Q k (z )=z −k P k (z −1).Equivalently,z −k Q k (z −1)=P k (z )For n =k +1,from Eq.(4)we haveP k +1(z )=P k (z )+κk z −1Q k (z )Q k +1(z )=κk P k (z )+z −1Q k (z )Thereforez −(k +1)P k +1(z −1)=z −k −1P k (z −1)+κk z −k Q k (z −1)=z −1Q k (z )+κk P k (z )=Q k +1(z )Thus,by mathematical induction Q n (z )=z −n P n (z −1)for n =0,1,···,NQ.E.D.Assume that κn =1for all n .If we inverse Eq.(5),we have[P n (z )z −1Q n (z )]=11−κ2n[1−κn −κn 1][P n +1(z )Q n +1(z )],n =0,1,···,N −1Hence,P n(z )=P n +1(z )−κn Q n +1(z )1−κ2n ,n =N −1,N −2,···,0(8)Let H (z )=B (z )A (z )=∑N n =0b n z −n 1−∑N n =1a n z −n ,where A (z )andB (z )are polynomials of z −1.Since p n n =κn −1for all n ,thereflection coefficients κn ’s can be determined recur-sively by first setting P N (z )=A (z )and Q N (z )=z −N P N (z −1).Then κN −1=p N N is determined.Applying Eq.(8)and Lemma 1recursively to find P n (z ),κn ’s can be determined successively.To determine λn ,we observe that the coefficient of z −N in the numerator must beλN since B (z )=∑Nn =0λn Q n (z )and q N N =1.Therefore λN =b N .We can removeλN Q N (z )from B (z ),resulting in a (N −1)th order polynomial,and determine λN −1by taking advantage of the property q n n =1for all n .The whole process continuous until all λn ’s are determined.In summaryP N =A (z ),S N =B (z ),λN =b Nfor n =N −1to 0κn =p n +1n +1Q n +1(z )=z −(n +1)P n +1(z −1)P n (z )=P n +1(z )−κn Q n +1(z )1−κ2nS n (z )=S n +1(z )−λn +1Q n +1(z )λn =s n nend•Stability of the Lattice Structure Form Eq.(4),we haveP 1(z )=1+κ0z −111is stable if and only if |κ0|<1.Since the lattice structure is a cascade of N similar stages,the stability of the filter can be verified easily as follows.Lemma 2The lattice structure in Fig.(2)is stable if and only if |κn |<1for all n .2All-pole SystemsAn all-pole system has no nonzero zeros,i.e.the system function is H (z )=1A (z ).In thelattice structure in Fig.(2),if λ0=1and λn =0for n >0,thenH (z )=∑N n =0λn Q n (z )P N (z )=1P N (z )Hence the all-pole system has a simpler lattice structure shown in Fig.(3).Figure 3:The lattice Structure for an all-pole systemOne interesting feature of the lattice structure in Fig.(3)is that the system function from x to v N is an all-pass system.This can be seen as follows.H all (z )=V N (z )X (z )=Q N (z )P N (z )=z −N P N (z −1)P N (z )If z 0is a pole of H all (z ),then 1/z 0must be a zero of H all (z )and vice versa.Due to the symmetry of poles and zeros,H all (z )is indeed an all-pass system.3Nonrecursive lattice structureIf H (z )=B (z ),i.e an FIR filter,the lattice structure becomes nonrecursive.We will explore its properties in this section.We would like to maintain the symmetric structure in Fig.(2)or Fig.(3)because previous results (e.q.Lemma 1)can be applied directly by doing so.In other words,Eq.(1)and Eq.(2)must hold for each stage.If H (z )is FIR,then G (z )=H −1(z )is an all-pole system.If we implement the all-pole system G (z )in the lattice form of Fig.(3),we haveG (z )=1H (z )=1P N (z )=U 0(z )U N (z )By exchanging its input and output,we get the desired FIR system.Note that in this FIR lattice structure,signals flow from u 0to u N .Hence Eq.(3)should be used to compute the signal propagation from stage to stage.The corresponding lattice structure is shown in Fig.(4).Notice that the structure is nonrecursive.The system function implemented by the nonrecursive lattice structure can be constructed in the same way as the recursive lattice structure:P 0(z )=Q 0(z )=1for n =1to N [P n (z )Q n (z )]=[1κn −1z −1κn −1z −1][P n −1(z )Q n −1(z )]endH(z)=P N(z)Figure4:Nonrecursive Lattice StructureTo convert from a system function to the nonrecursive lattice structure,the algorithm is similar to that of the recursive version:P N=B(z)=1+b1z−1+···+b N z−Nfor n=N to1κn−1=p nnQ n(z)=z−n P n(z−1)P n−1(z)=P n(z)−κn−1Q n(z)1−κ2n−1endNote that from Lemma1,p n0=q nn=1for all n.Therefore the coefficient of the constantterm in H(z),i.e.b0,must be1.If b0=1,an intuitive approach is to divide B(z)by b0. However,if b N=b0,as in the case of the linear phasefilter,this will result inκN−1=1, and again we will run into trouble in computing the reflection coefficients.A preferable way is to implement the FIR system H′(z)=1+(B(z)−b0)in a lattice structure and subtract 1−b0from its output.The idea is shown in Fig.(5)Figure5:Nonrecursive lattice structure for b0=1If we apply Lemma2to the nonrecursive lattice structure,we observe that B(z)is a minimum phase system if and only if|κn|<1for all n.If B(z)=P N(z)is a minimum phase system,then the system function from x=u0to v N,i.e.Q N(z),becomes a maximum phase system according to Lemma1,i.e.all its zeros are outside the unit circle.Afinal remark of this lecture:According to Lemma2,each stage of the stable(or minimum phase)lattice structure is an attenuator,i.e.it does not amplify the signals.Thisproperty gives the lattice structure great computational stability and this is the primary reason that the lattice structure is implemented.However,the price for this property is the complex computation of the signalflow.。
Abstract Computing the Closest Point to a Circle

Computing the Closest Point to a CirclePinaki MitraNIMC,AliporeCalcutta,Indiae-mail:pinaki m@Asish Mukhopadhyay∗School of Computer Science University of Windsor,Windsor,Canada e-mail:asishm@uwindsor.caS.V.RaoDepartment of Computer Science&Engineering Indian Institute of Technology,Guwahati,India e-mail:svrao@iitg.ernet.inAbstractIn this paper we consider the problem of computing theclosest point to the boundary of a circle among a setS of n points.We present two algorithms to solve this problem.One algorithm runs in O(n3)prepro-cessing time and space and O(log2n)query time.The other algorithm runs in O(n1+ )preprocessing time and O(n log n)space and O(n2/3+ )query time.Thus we ex-hibit a trade-offbetween preprocessing and query times For dimensions d≥3we present an algorithm with O(n d/2 + )preprocessing time to report an approx-imate closest point to the boundary of d-dimensional query sphere R in O(n1−1/(d+1)+ )query time.1IntroductionThe problem of preprocessing a set S,of n points in the plane to determine the closest point to a query line was initially addressed by Cole and Yap[2],who obtained a solution with preprocessing time and space in O(n2)and query time in O(log n).Lee and Ching[6]obtained the same result using geometric duality.In[8]an algorithm was presented with O(n log n)preprocessing time and space and O(n0.695)query time.The space complexity was improved to O(n)in a subsequent result by Mi-tra and Chaudhuri[9].In[10],the simplicial partition technique of[7]was used to improve the query time to O(n1/2+ )for arbitrary >0,with preprocessing time and space in O(n1+ )and O(n log n)respectively.In this paper,we consider a natural extension of the above problem-determining a point in S that is closest to the boundary of a query circle.Ourfirst algorithm precomputes all higher order Voronoi diagrams.The preprocessing time and space complexities of this algo-rithm are in O(n3),while the query time is in O(log2n). We propose another algorithm that uses the simplicial partition idea of Matousek[7].The preprocessing time and space complexities of this algorithm are in O(n1+ )∗Research supported by an NSERC Operating Grant and O(n log n)respectively,while the query time is in O(n2/3+ ).The second approach generalizes to higher dimen-sions.Here,however,point location turns out to be a bottleneck.Recently,some attempts have been made to overcome this problem by computing an approxi-mate nearest neighbor in higher dimensions[4].Tak-ing a cue from this,for dimension d≥3,we propose an algorithm thatfinds an approximate closest point, according to two different approximation schemes,with preprocessing time in O(n d/2 + )and query time in O(n1−1/(d+1)+ ).2Geometric Insight for High Preprocessing and Low Query AlgorithmIn a preprocessing step,we compute all higher order Voronoi diagrams.The cost of this is in O(n3)[11].The main idea of the query procedure is a binary search on the pre-computed higher-order Voronoi diagrams.Let the query circle have centre at p and radius a. Algorithm Query(R)pute the nearest neighbor of p from V or1(S)and check if its distance from p is less than a.If not, we report the nearest neighbor of p as the answer to the query since in this case all points of S lies outside or on the boundary of the circle R.Stop.pute the furthest neighbor of p from V or n(S)and check if its distance from p is greater than a.If not,we report the furthest neighbor as the answer to the query since in this case all points of S lies inside or on the boundary of the circle R.Stop.3.Perform a binary search within the interval(1...n).Compute n/2 -th nearest neighbor of pfrom V or n/2 and determine its distance from p.If it is equal to a this point is the answer to our query.If it is greater than a recurse in the interval1(1... n/2 ).Otherwise,if it is less than a recursein the interval n/2 ...n.Thus determine the k-th and(k+1)-th nearest neighbors s and t of p such that(dist(p,s)<a)and(dist(p,t)>a).4.For each of the the two points s and t determinedin Step III,we compute the absolute difference of their distance from p and a.The point having the least value of the absolute difference is the answer to our query.Thus we have the following theorem.Theorem1Given a set S of n points,the closest point from the boundary of a query circle R can be computed in O(log2n)time with O(n3)preprocessing time and space.In the next section,we propose an alternate algo-rithm based on the simplicial partition technique of Ma-tousek[7]to improve the preprocessing time.3Simplicial PartitionsA simplicial partition of S is a collection of pairsΨ(S)={(S1,t1),(S2,t2),...,(S r,t r)}(1) where the S i’s are mutually disjoint subsets of S whose union is S,and each t i is a tetrahedron that contains S i (see Fig.1).A simplicial partition isfine if|S i|≤2∗n/r for each i.For a given simplicial partitionΨ(S),the crossing number of a plane Q is the number of tetrahedrons of Ψ(S)that the plane properly intersects.The crossing number ofΨ(S)is the maximum crossing number over all planes that intersect the simplicial partition.The following theoretically important result by Ma-tousek[7]shows how to construct afine simplicial par-tition with a low crossing number.Theorem2For any given set S of n d-dimensional points and a parameter r,1≤r≤n,afine simplicial partition of size r,with O(r1−1/d)crossing number,ex-ists.Further,for any given >0,such a simplicial partition can be constructed in time O(n1+ ).Figure1:Plane Q cuts a simplicial partition.We lift the set S of n points and the query circle R,onto the surface of a paraboloid[3]z=x2+y2.S denotes the lifted set of points and R the plane through the image of the query circle.Points inside the circle R gets mapped to one halfspace and points outside the ring R gets mapped to the other halfspace.We construct afine simplicial partition of S of size r with crossing number O(r2/3).What is important for our problem is that each tetrahedron that is not intersected by R , traps a set of points whose projections lie completely inside or outside the query circle.We use the simplicial partition of the lifted set of points to create a r-way partition tree on the set of points S,keeping with each subset of points the corre-sponding tetrahedron that enclosed their lifted images in3-space.4Algorithmic DetailsThe constructibility of afine simplicial partition in3-space with a low crossing number implies that the pro-jections of the point sets enclosed by at least r−O(r2/3) simplices are not intersected by a query circle R.For the remaining at most O(r2/3)simplices that are inter-sected by S ,we proceed recursively on the respective partitions of the projections of the point sets enclosed by these tetrahedra.The preprocessing phase of the algorithm maintains both the nearest neighbor and furthest neighbor Voronoi diagrams of the point set corresponding to each node of the partition tree.Then preprocess each of the Voronoi diagram using the algorithm of Kirkpatrick[5]to per-form point location.Given a query circle R with center p and radius a, we answer the closest point query,using the following algorithm.Algorithm Q1.Initialize q to(∞,∞),the nearest point to the thequery ring.2.If the tetrahedron associated with the node of thepartition tree lies below R ,use the furthest neigh-bor Voronoi diagram of the projection of the point set inside the tetrahedron to detect the region in which the center p lies.Let t1be the point asso-ciated with this region.In Fig.2a,since p lies in V(p i)the closest point to the boundary of R is p i and thus t1=p i.If the absolute difference of the distance of t1from p and a is less than that of q update q to t1.3.If the tetrahedron associated with the node of thepartition tree lies above R ,use the nearest neigh-bor Voronoi diagram of the projection of the point set inside the quadrilateral to detect the region in2(b)(a)Figure 2:(a)Furthest neighbor Voronoi diagram is queried when the tetrahedron lies below R .(b)Nearest neighbor Voronoi diagram is queried when the tetrahe-dron lies above R .which the center p lies.Let t 2be the point asso-ciated with this region.In Fig.2b,since p lies in V (p j )the closest point to the boundary of R is p j and thus t 2=p j .If the absolute difference of the distance of t 2from p and a is less than that of q update q to t 2.4.If the tetrahedron associated with the node of the partition tree intersects R we recurse on the sub-trees rooted at that node of the partition tree.The complexity of the algorithm is summarized in the following theorem.Theorem 3Given a set S of n points and a query cir-cular circle R the closest point from the boundary of R in the set S can be answered in O (n 2/3+ )query time with O (n 1+ )preprocessing time and O (n log n )prepro-cessing space.The approach of the previous section extends to higher dimensions in exactly the same way.5Approximate nearest pointIf an approximate closest point is acceptable,we can avoid point location in higher dimensional Voronoi di-agrams required for an exact solution.We preprocess each partitioned point set using Clarkson’s [1]random-ized algorithm for the nearest neighbor query.For a set S of n points in d -dimension we can preprocess this setin O (n d/2 +)time to perform nearest neighbor query in O (log n )time.Now,for the furthest point query in the preprocessing phase we will maintain the furthest point from each point in the simplicial partition.For a partition with m points this computation can be easily done using any brute force algorithm in O (m 2)time in any dimension.Given a query sphere,if the whole par-tition lies completely inside,we will use the algorithm of Clarkson to compute the nearest neighbor q of the(a)(b)Figure 3:Diagram for the worst case:(a)first approxi-mation (b)second approximation.center p .Then use this furthest neighbor of q as an approximate furthest neighbor of p .Fig.3a illustrates the worst case situation if we adopt this approach.In this diagram we see that the actual furthest neighbor of p ,i.e.,t is at a distance which is almost 3times the distance of p from the reported fur-thest neighbor s .The constant of approximation can be improved if we increase the preprocessing overhead by maintaining the furthest neighbor of each data point in each of the 2d quadrants around that point.Again for a partition with m points this computation can be easily done using any brute force algorithm in O (m 2)time in any dimension.Now given the query circle we locate the nearest neigh-bor q of the center p .Then from O (2d )furthest points maintained for q we choose the one which is at maxi-mum distance from p .For fixed d thus we have to spend an additional O (1)time besides the O (log n )time near-est neighbor query.Fig.3b illustrates the worst case situation if we adopt this approach.In this diagram we see that the actual furthest neighbor of p ,i.e.,t is at a distance which is almost √5times the distance of p from the reported furthest neighbor s .Now if we try to bound the error of approximation from the boundary of the query sphere the error ratio is roughly (a −l/2− 1)/(a −kl/2+ 2),where k =3in the first approximation and k =√5in the second approximation.Thus for a >>l we have constant ap-proximation.But for values of a close to kl/2the error of approximation is high.The time complexity of preprocessing each partition using Clarkson’s algorithm [1]would dominate the time complexity of construction of the partition tree.Fol-lowing a similar analysis as done for two dimension,we establish the following theorem.Theorem 4Given a set of n points and a query sphere R in d dimensions,an approximate nearest neighbor from the boundary of the sphere can be computed inO (n 1−1/(d +1)+ )query time with O (n d/2 +)prepro-cessing.36ConclusionsIn this paper we have shown that the results of Mitra and Chaudhuri[9]can be generalized to answer the cir-cle query problem.We have presented two algorithms one with high preprocessing and low query time and the other one with low preprocessing and high query time. References[1]K.L.Clarkson.A randomized algorithm forclosest-point queries.SIAM put.,17:830–847,1988.[2]R.Cole and C.K.Yap.Geometric retrieval prob-lems.In Proc.24th Annu.IEEE Sympos.Found.Comput.Sci.,pages112–121,1983.[3]H.Edelsbrunner and R.Seidel.Voronoi diagramsand arrangements.Discrete Comput.Geom.,1:25–44,1986.[4]Piotr Indyk and Rajeev Motwani.Approximatenearest neighbors:Towards removing the curse of dimensionality.In Proc.30th Annu.ACM Sympos.Theory Comput.,page to appear,1998.[5]D.G.Kirkpatrick.Optimal search in planar sub-divisions.SIAM put.,12(1):28–35,1983. [6]D.T.Lee and Y.T.Ching.The power of geometricduality rm.Process.Lett.,21:117–122,1985.[7]J.Matouˇs ek.Efficient partition trees.DiscreteComput.Geom.,8:315–334,1992.[8]P.Mitra.Finding the closest point to a queryline.In G.Toussaint,editor,Snapshots in Compu-tational Geometry,volume II,pages53–63.1992.[9]P.Mitra and B.B.Chaudhuri.Efficiently com-puting the closest point to a query line.Pattern Recognition Letters,19:1027–1035,1998.[10]Asish ing simplicial paritions todetermine a closest point to a query line.Pattern Recognition Letters,24:1915–1920,2003.[11]F.P.Preparata and putationalGeometry:An Introduction.Springer-Verlag,3rd edition,October1990.4。
半导体物理与器件英语

半导体物理与器件英语Semiconductor Physics and DevicesThe field of semiconductor physics and devices is a crucial aspect of modern technology, as it underpins the development of a wide range of electronic devices and systems that have transformed our daily lives. Semiconductors, which are materials with electrical properties that lie between those of conductors and insulators, have been the backbone of the digital revolution, enabling the creation of integrated circuits, transistors, and other essential components found in smartphones, computers, and a myriad of other electronic devices.At the heart of semiconductor physics is the study of the behavior of electrons and holes within these materials. Electrons, which are negatively charged particles, and holes, which are the absence of electrons and carry a positive charge, are the fundamental charge carriers in semiconductors. The interactions and movement of these charge carriers within the semiconductor lattice structure are governed by the principles of quantum mechanics and solid-state physics.One of the fundamental concepts in semiconductor physics is theenergy band structure. Semiconductors have a unique energy band structure, with a filled valence band and an empty conduction band separated by an energy gap. The size of this energy gap determines the semiconductor's electrical properties, with materials having a smaller energy gap being more conductive than those with a larger gap.The ability to manipulate the energy band structure and the behavior of charge carriers in semiconductors has led to the development of a wide range of electronic devices. The most prominent of these is the transistor, a fundamental building block of modern electronics. Transistors are used to amplify or switch electronic signals and power, and they are the essential components in integrated circuits, which are the heart of digital devices such as computers, smartphones, and various other electronic systems.Another important class of semiconductor devices are diodes, which are two-terminal devices that allow the flow of current in only one direction. Diodes are used in a variety of applications, including power supplies, rectifiers, and light-emitting diodes (LEDs). LEDs, in particular, have become ubiquitous in modern lighting and display technologies, offering improved energy efficiency, longer lifespan, and enhanced color quality compared to traditional incandescent and fluorescent light sources.Semiconductor devices are not limited to electronic applications; they also play a crucial role in optoelectronics, a field that deals with the interaction between light and electronic devices. Photodetectors, such as photodiodes and phototransistors, are semiconductor devices that convert light into electrical signals, enabling a wide range of applications, including imaging, optical communication, and solar energy conversion.The development of semiconductor physics and devices has been a continuous process, driven by the relentless pursuit of improved performance, efficiency, and functionality. Over the past several decades, we have witnessed remarkable advancements in semiconductor technology, with the miniaturization of devices, the introduction of new materials, and the development of innovative device architectures.One of the most significant trends in semiconductor technology has been the scaling of transistor dimensions, often referred to as Moore's Law. This observation, made by Intel co-founder Gordon Moore in 1965, predicted that the number of transistors on a microchip would double approximately every two years, leading to a dramatic increase in computing power and a corresponding decrease in device size and cost.This scaling has been achieved through a combination ofadvancements in fabrication techniques, material engineering, and device design. For example, the use of high-k dielectric materials and the implementation of FinFET transistor architectures have allowed for continued scaling of transistor dimensions while maintaining or improving device performance and power efficiency.Beyond the scaling of individual devices, the integration of multiple semiconductor components on a single integrated circuit has led to the development of increasingly complex and capable electronic systems. System-on-a-chip (SoC) designs, which incorporate various functional blocks such as processors, memory, and input/output interfaces on a single semiconductor die, have become ubiquitous in modern electronic devices, enabling greater functionality, reduced power consumption, and improved overall system performance.The future of semiconductor physics and devices holds immense promise, with researchers and engineers exploring new materials, device architectures, and application domains. The emergence of wide-bandgap semiconductors, such as silicon carbide (SiC) and gallium nitride (GaN), has opened up new possibilities in high-power, high-frequency, and high-temperature electronics, enabling advancements in areas like electric vehicles, renewable energy systems, and communication networks.Additionally, the integration of semiconductor devices with otheremerging technologies, such as quantum computing, neuromorphic computing, and flexible/wearable electronics, is paving the way for even more transformative applications. These developments have the potential to revolutionize fields ranging from healthcare and transportation to energy and communication, ultimately enhancing our quality of life and shaping the technological landscape of the future.In conclusion, the field of semiconductor physics and devices is a cornerstone of modern technology, underpinning the development of a vast array of electronic devices and systems that have become indispensable in our daily lives. The continuous advancements in this field, driven by the relentless pursuit of improved performance, efficiency, and functionality, have been instrumental in driving the digital revolution and shaping the technological landscape of the21st century. As we move forward, the future of semiconductor physics and devices promises even more remarkable innovations and transformative applications that will continue to shape our world.。
2006-Computational thinking_中英对照_

C
omputational thinking builds on the power and limits of computing processes, whether they are executed by a human or by a machine. Computational methods and models give us the courage to solve problems and design systems that no one of us would be capable of tackling alone. Computational thinking confronts the riddle of machine intelligence: What can humans do better than computers? And What can computers do better than humans? Most fundamentally it addresses the question: What is computable? Today, we know only parts of the answers to such questions.
2 / 6 Computational Thinking – Jeannette M. Wing Just as the printing press facilitated the spread of the three Rs, what is 力培养。和出版社促进了3个 R(阅读,书写和算术Reading, Writing appropriately incestuous about this vision is that computing and &Arithmetic)的传播相类似,计算机和使用电脑促进了计算机思维 computers facilitate the spread of computational thinking. Computational thinking involves solving problems, designing 的传播。 systems, and understanding human behavior, by drawing on the 计算机思维采纳计算机科学的基本理念,可运用于问题的解决 concepts fundamental to computer science. Computational thinking includes a range of mental tools that reflect the breadth of the field of ,系统设计和理解人类行为。计算机思维包含了一定范围内的思维 computer science. 工具,反映出计算机科学领域的广泛性。 Having to solve a particular problem, we might ask: How difficult 在解决一个问题时,我们会问:这有多难?怎样做是最佳的方 is it to solve? and What’s the best way to solve it? Computer science rests on solid theoretical underpinnings to answer such questions 法?计算机思维站在坚实的理论地基上给予这样的问题精确的答案 precisely. Stating the difficulty of a problem accounts for the 。问题的难度要说取决于机器的能力-用来解决问题的计算工具。 underlying power of the machine—the computing device that will run the solution. We must consider the machine’s instruction set, its 要考虑机器的指令,资源的约束和运行环境。 resource constraints, and its operating environment. In solving a problem efficiently, we might further ask whether an 为了有效率地解决问题,我们也许要进而问道,貌似的解决方 approximate solution is good enough, whether we can use randomization to our advantage, and whether false positives or false 案是不是最好的呢,我们可以随机化优势吗,是否允许主动错误或 negatives are allowed. Computational thinking is reformulating a seemingly difficult problem into one we know how to solve, perhaps 者被动错误。计算机思维通过简化,嵌入,转换或者模拟,将看来 by reduction, embedding, transformation, or simulation. 困难的问题转化为可以解决的问题。 Computational thinking is thinking recursively. It is parallel processing. It is interpreting code as data and data as code. It is type checking as the generalization of dimensional analysis. It is recognizing both the virtues and the dangers of aliasing, or giving someone or something more than one name. It is recognizing both the cost and power of indirect addressing and procedure call. It is judging a program not just for correctness and efficiency but for aesthetics, and a system’s design for simplicity and elegance.
1Departamento de Matem'atica, Pontif'icia Universidade Cat'olica do Rio de Janeiro

Robust Adaptive Polygonal Approximation of Implicit CurvesH´E LIO L OPES J O˜AO B ATISTA O LIVEIRA L UIZ H ENRIQUE DE F IGUEIREDODepartamento de Matem´a tica,Pontif´ıcia Universidade Cat´o lica do Rio de JaneiroRua Marquˆe s de S˜a o Vicente225,22453-900Rio de Janeiro,RJ,BrazilFaculdade de Inform´a tica,Pontif´ıcia Universidade Cat´o lica do Rio Grande do SulAvenida Ipiranga6681,90619-900Porto Alegre,RS,BrazilIMPA–Instituto de Matem´a tica Pura e AplicadaEstrada Dona Castorina110,22461-320Rio de Janeiro,RJ,Brazil Abstract.We present an algorithm for computing a robust adaptive polygonal approximation of an implicit curve in the plane.The approximation is adapted to the geometry of the curve because the length of the edges varies with the curvature of the curve.Robustness is achieved by combining interval arithmetic and automatic differentiation.Keywords:piecewise linear approximation;interval arithmetic;automatic differentiation;geometric modeling1IntroductionAn implicit object is defined as the set of solutions of anequation,where.For well-behaved functions,this set is a surface of dimensionin.Of special interest to computer graphics are implicitcurves()and implicit surfaces(),althoughseveral problems in computer graphics can be formulatedas high-dimensional implicit problems[2,3].Applications usually need a geometric model of theimplicit object,typically a polygonal approximation.Whileit is easy to compute polygonal approximations for para-metric objects,computing polygonal approximations forimplicit objects is a challenging problem for two main rea-sons:first,it is difficult tofind points on the implicit ob-ject[4];second,it is difficult to connect isolated points intoa mesh[5].In this paper,we consider the problem of computing apolygonal approximation for a curve given implicitly bya function,that is,In Section2we review some methods for approximatingimplicit curves,and in Section3we show how to computerobust adaptive polygonal approximations.By“adaptive”we mean two things:first,is explored adaptively,in thesense that effort is concentrated on the regions of that arenear;second,the polygonal approximation is adapted tothe geometry of,having longer edges where isflat andFigure1:Our algorithm in action for the ellipse given im-plicitly by.lem is to check the sign of at the vertices of the cell.If these signs are not all equal,then the cell must intersect (provided is continuous,of course).However,if the signs are the same,then we cannot discard the cell,because it might contain a small closed component of in its interior, or might enter and leave the cell through the same edge.In practice,the simplest solution to both problems is to use afine regular grid and hope for the best.Figure2shows an example of such full enumeration on a regular rectan-gular grid.The enumerated cells are shown in grey.The points where intersects the boundary of those cells can be computed by linear interpolation or,if higher accuracy is desired,by any other classical method,such as bisection. Note that the output of an enumeration is simply a set of line segments;some post-processing is needed to arrange these segments into polygonal lines.Full enumeration works well—provided afine enough grid is used—but it can be very expensive,because many cells in the grid will not intersect,specially if has components of different sizes(as in Figure2).If we take the number of evaluations of as a measure of the cost of the algorithm,then full enumeration will waste many eval-uations on cells that are far away from.Typically,if the grid has cells,then only cells will intersect. Thefiner the grid,the more expensive full enumeration is.Another popular approach to approximating an im-plicit curve is continuation,which starts at a point on the curve and tries to step along the curve.One simple contin-uation method is to integrate the Hamiltonian vectorfield Figure2:Full enumeration of the cubic curve given implic-itly by in the square.,combining a simple numerical integra-tion method with a Newton corrector[6].Another method is to follow the curve across the cells of a regular cellular decomposition of by pivoting from one cell to another, without having to compute the whole decomposition[2].Continuation methods are attractive because they con-centrate effort where it is needed,and may adapt the com-puted approximation to the local geometry of the curve,but they need starting points on each component of the curve; these points are not always available and may need to be hunted in.Moreover,special care is needed to handle closed components correctly.What we need is an efficient and robust method that performs adaptive enumeration,in which the cells are larger away from the curve and smaller near it,so that com-putational effort is concentrated where it is most needed. The main obstacle in this approach is how to decide reli-ably whether a cell is away from the curve.Fortunately, interval methods provide a robust solution for this problem, as explained in Section3.Moreover,by combining interval arithmetic with automatic differentiation(also explained in Section3),it is possible to reliably estimate the curvature of and thus adapt the enumeration not only spatially,that is,with respect to the location of in,but also geomet-rically,by identifying large cells where can be approxi-mated well by a straight line segment(see Figure3,left). The goal of this paper is to present a method for doing ex-actly this kind of completely adaptive approximation,in a robust way.Figure3:Geometric adaption(left)versus spatial adaption(right).3Robust adaptive polygonal approximationAs discussed in Section2,what we need for robust adaptive enumeration is some kind of oracle that reliably answers the question“Does this cell intersect?”.Testing the sign of at the vertices of the cell is an oracle,but not a reli-able one.It turns out that it is easier to implement oracles that reliably answer the complementary question“Is this cell away from?”.Such oracles test the absence of in the cell,rather than its presence,but they are just as effec-tive for reliable enumeration.We shall now describe how such absence oracles may be implemented and how to use them to compute adaptive enumerations reliably.3.1Inclusion functions and adaptive enumerationAn absence oracle for a curve given implicitly bycan be readily implemented if we have an inclusion function for,that is,a function defined on the subsets of and taking real intervals as values such thatIn words,is an estimate for the complete set of values taken by on.This estimate is not required to be tight: may be strictly larger than.Nevertheless,even if not tight,estimates provided by inclusion functions are sufficient to implement an absence oracle:If, then,that is,for all pointsin;this means that does not intersect.Note that this is not an approximate statement:is a proof that does not intersect.Once we have a reliable absence oracle,it is simple to write a reliable adaptive enumeration algorithm as follows: Algorithm1:explore:if thendiscardelseif thenoutputelsedivide into smaller piecesfor each,exploreStarting with a call to explore,this algorithm performs a recursive exploration of,discarding subregions of when it can prove that does not contain any part of the curve.The recursion stops when is smaller than a user-selected tolerance,as measured by its diameter or any equivalent norm.The output of the algorithm is a list of small cells whose union is guaranteed to contain the curve.In practice,is a rectangle and is divided into rect-angles too.A typical choice(which we shall adopt in the sequel)is to divide into four equal rectangles,thus gen-erating a quadtree[7],but it is also common to bisect perpendicularly to its longest size or to alternate the direc-tions of the cut[8].3.2An algorithm for adaptive approximation Algorithm1is only spatially adaptive,because all output cells have the same size(see Figure3,right).Geometricadaption requires that we estimate how the curvature of varies inside a cell.This can be done by using an inclusion function for the normalized gradient of,because this gradient is normal to.The inclusion function satisfies where is the normalized gradient of at the point:Figure4:Some automatic differentiation formulas.or computational differentiation.This simple technique has been rediscovered many times[9,23–25],but its use is still not widespread;in particular,applications of automatic dif-ferentiation in computer graphics are still not common[26].Derivatives computed with automatic differentiation are not approximate:the only errors in their evaluation are round-off errors,and these will be significant only when they already are significant for evaluating the function it-self.Like interval arithmetic,automatic differentiation is easy to implement[23,27]:instead of operating with single numbers,we operate with tuples of numbers,where is the value of the function and is the value of its partial derivative with respect to the-th variable.We extend the elementary operations and func-tions to these tuples by means of the chain rule and the elementary calculus formulas.Once this is done,deriva-tives are automatically computed for complicated expres-sions simply by following the rules for each elementary operation or function that appears in the evaluation of the function itself.In other words,any sequence of elementary operations for evaluating can be automati-cally transformed into a sequence of tuple operations that computes not only the value of at a point but also all the partial derivatives of at this point.Again,op-erator overloading simplifies the implementation and use of automatic differentiation,but it can be easily implemented in any language[27],perhaps aided by a precompiler[22].Figure4shows some sample automatic differentiation formulas for.Note how values on the left-hand side of these formulas(and sometimes on the right-hand side as well)are reused in the computation of partial derivatives on the right-hand side.This makes automatic differentiation much more efficient than symbolic differentiation:several common sub-expressions are identified and evaluated only once.We can take the formulas for automatic differentiation and interpret them over intervals:each is now an in-terval,and the operations on them are interval operations. This combination of automatic differentiation with interval arithmetic allows us to compute interval estimates of par-tial derivatives automatically,and is the last tool we needed to implement Algorithm2.3.5Implementation detailsWe implemented Algorithm2in C++,coding interval arith-metic routines from scratch and taking the automatic differ-entiation routines from the book by Hammer et al.[28].To test whether the curve isflat in a cell,we com-puted an interval estimate for the normalized gradient of inside.This gave a rectangle in. The test was implemented by testingwhether both sides of were smaller than.This is not the only possibility,but it is simple and worked well,exceptfor the non-obvious choice of the gradient tolerance.Our implementation of approx()computed the inter-section of with a rectangular cell by dividing alongits main diagonal into two triangles,and using classical bi-section on the edges for which the sign of at the vertices was different.As mentioned in Section3.2,this produces aconsistent polygonal approximation,even at adjacent cells that do not share complete edges.If the sign of was the same at all the vertices of, then we simply ignored;this worked well for the exam-ples we used.If necessary,the implementation of approxmay be refined by using the estimate to test whether the gradient of or one of its components is zero inside. If these tests fail,then can be safely discarded because cannot contain small closed components of and can-not intersect an edge of more than once:closed compo-nents must contain a singular point of,and double inter-sections imply that or vanish in.We did notfind these additional tests necessary in our experiments.3.6Examples of adaptive approximationFigures5–12show several examples of adaptive approxi-mations computed with our program.The examples shown on the left hand side of thesefigures were output by the ge-ometrically adaptive Algorithm2;the examples shown on the right hand side were output by the spatially adaptive Al-gorithm1.The two variants were computed with the same parameters:the region is,the re-cursion was stopped after levels of recursion(that is,the spatial tolerance was),and the tolerance for gra-dient estimates was.As mentioned in Section3.2,we set for the examples on the right hand side,to reduce geometric adaption to spatial adaption.Cells visitedCurve Geometric Spatial Ratio 53412245 6.6Bicorn94300 3.2 77091781 2.5Cubic128262 2.0 923717737.5Pisces logo280488 1.7 11745712121 1.6Taubin233446 1.9 Table1:Statistics for the curves in Figures5–12.The white cells of many different sizes reflect the spa-tial adaption.The grey cells of many different sizes reflect the geometric adaption.Inside each grey cell,the curve is approximated by a line segment.Table1shows some statistics related to these exam-ples.For each curve,we show the total number of cells vis-ited and the number of grey cells(we call also them leaves). We give these numbers for the geometrically adaptive Algo-rithm2and for the spatially adaptive Algorithm1,and also give their ratio for comparison.As can be seen in Table1, for all the examples tested Algorithm2was more efficient than Algorithm1,in the sense that it visited fewer cells and output fewer cells.4Related workEarly work on implicit curves in computer graphics concen-trated on rendering,and consisted mainly of continuation methods in image space.Aken and Novak[29]showed how Bresenham’s algorithm for circles can be adapted to render more general curves,but they only gave details for conics. Their work was later expanded by Chandler[30].These two papers contain several references to the early work on the rendering problem.More recently,Glassner[31]dis-cussed in detail a continuation algorithm for rendering.Special robust algorithms have been devised for alge-braic curves,that is,implicit curves defined by a polyno-mial equation.One early rendering algorithm was proposed by Aron[32],who computed the topology of the curve us-ing the cylindrical algebraic decomposition technique from computational algebra.He also described a continuation algorithm that integrates the Hamiltonian vectorfield,but is guided by the topological structure previously computed. More recently,Taubin[33]gave a robust algorithm for ren-dering a plane algebraic curve.He showed how to compute constant-width renderings by approximating the Euclidean distance to the curve.His work can be seen as a specialized interval technique for polynomials.Dobkin et al.[2]described in detail a continuation method for approximating implicit curves with polygonal lines.Their algorithm follows the curve across a regular triangular grid that is never fully built,but is instead tra-versed from one intersecting cell to another by reflection rules.Since the grid is regular,their approximation is not geometrically adaptive.Moreover,the selection of the grid resolution is left to the user and so the aliasing problems mentioned in Section2may still occur.Suffern[34]seems to have been thefirst to try to re-place full enumeration with adaptive enumeration.He pro-posed a quadtree exploration of the ambient space guided by two parameters:how far to divide the domain without trying to identify intersecting cells,and how far to go before attempting to approximate the curve in the cell.This heuris-tic method seems to work well,but of course its success de-pends on the selection of those two parameters,which must be done by trial and error.Shortly afterwards,Suffern and Fackerell[18]applied interval methods for the robust enumeration of implicit curves,and gave an algorithm that is essentially Algo-rithm1.Their work is probably thefirst application of interval arithmetic in graphics(the early work of Mudur and Koparkar[10]seems to have been largely ignored until then).In a course at SIGGRAPH’91,Mitchell[17]revisited the work of Suffern and Fackerell[18]on robust adaptive enumeration of implicit curves,and helped to spread the word on interval methods for computer graphics.He also described automatic differentiation and used it in ray trac-ing implicit surfaces.Snyder[13,19]described a complete modeling sys-tem based on interval methods,and included an approxima-tion algorithm for implicit curves that incorporated a global parametrizability criterion in the quadtree decomposition. This allowed his algorithm to produce an enumeration that hasfinal cells of varying size,but the resulting approxima-tion is not adapted to the curvature.Figueiredo and Stolfi[37]showed that adaptive enu-merations can be computed more efficiently by using tighter interval estimates provided by affine arithmetic.More recently,Hickey et al.[35]described a robust program based on interval arithmetic for plotting implicit curves and relations.Tupper[36]described a similar, commercial-quality,program.5ConclusionAlgorithm2computes robust adaptive polygonal approxi-mation of implicit curves.As far as we know,this is the first algorithm which computes a reliable enumeration that is both spatially and geometrically adaptive.The natural next step in this research is to attack im-plicit surfaces,which have recently become again an active research area[38].The ideas and techniques presented in this paper are useful for computing robust adaptive approx-imations of implicit surfaces.However,the solution will probably be more complex,because we will have to face more difficult topological problems,not only for the sur-face itself but also in the local approximation by polygons.We are also working on higher-order approximation methods for implicit curves based on a Hermite formula-tion.AcknowledgementsThis research was done while J.B.Oliveira was visit-ing the Visgraf laboratory at IMPA during IMPA’s sum-mer post-doctoral program.Visgraf is sponsored by CNPq, FAPERJ,FINEP,and IBM Brasil.H.Lopes is a mem-ber of the Matmidia laboratory at PUC-Rio.Matmidia is sponsored by FINEP,PETROBRAS,CNPq,and FAPERJ. L.H.de Figueiredo is a member of Visgraf and is partially supported by a CNPq research grant.References[1]H.Lopes,J.B.Oliveira,L.H.de Figueiredo,Robust adap-tive approximation of implicit curves,in:Proceedings of SIBGRAPI2001,IEEE Press,2001,pp.10–17.[2] D.P.Dobkin,S.V.F.Levy,W.P.Thurston,A.R.Wilks,Contour tracing by piecewise linear approximations,ACM Transactions on Graphics9(4)(1990)389–423.[3] C.M.Hoffmann,A dimensionality paradigm for surfaceinterrogations,Computer Aided Geometric Design7(6) (1990)517–532.[4]L.H.de Figueiredo,J.Gomes,Sampling implicit ob-jects with physically-based particle systems,Computers& Graphics20(3)(1996)365–375.[5]L.H.de Figueiredo,J.Gomes,Computational morphologyof curves,The Visual Computer11(2)(1995)105–112. [6] E.L.Allgower,K.Georg,Numerical Continuation Methods:An Introduction,Springer-Verlag,1990.[7]H.Samet,The Design and Analysis of Spatial Data Struc-tures,Addison-Wesley,1990.[8]R.E.Moore,Methods and Applications of Interval Analysis,SIAM,Philadelphia,1979.[9]R.E.Moore,Interval Analysis,Prentice-Hall,1966.[10]S.P.Mudur,P.A.Koparkar,Interval methods for processinggeometric objects,IEEE Computer Graphics&Applications 4(2)(1984)7–17.[11] D.L.Toth,On ray tracing parametric surfaces,ComputerGraphics19(3)(1985)171–179(SIGGRAPH’85Proceed-ings).[12] D.P.Mitchell,Robust ray intersection with interval arith-metic,in:Proceedings of Graphics Interface’90,1990,pp.68–74.[13]J.M.Snyder,Generative Modeling for Computer Graphicsand CAD,Academic Press,1992.[14]T.Duff,Interval arithmetic and recursive subdivision for im-plicit functions and constructive solid geometry,Computer Graphics26(2)(1992)131–138,(SIGGRAPH’92Proceed-ings).[15]W.Barth,R.Lieger,M.Schindler,Ray tracing general para-metric surfaces using interval arithmetic,The Visual Com-puter10(7)(1994)363–371.[16]J.B.Oliveira,L.H.de Figueiredo,Robust approximationof offsets and bisectors of plane curves,in:Proceedings of SIBGRAPI2000,IEEE Press,2000,pp.139–145.[17] D.P.Mitchell,Three applications of interval analysis incomputer graphics,in:Frontiers in Rendering course notes, SIGGRAPH’91,1991,pp.14-1–14-13.[18]K.G.Suffern,E.D.Fackerell,Interval methods in computergraphics,Computers&Graphics15(3)(1991)331–340. [19]J.M.Snyder,Interval analysis for computer graphics,Com-puter Graphics26(2)(1992)121–130(SIGGRAPH’92Pro-ceedings).[20]J.Stolfi,L.H.de Figueiredo,Self-Validated NumericalMethods and Applications,Monograph for21st Brazil-ian Mathematics Colloquium,IMPA,Rio de Janeiro, 1997,available at.[21]V.Kreinovich,Interval software,.[22] F.D.Crary,A versatile precompiler for nonstandard arith-metics,ACM Transactions on Mathematical Software5(2) (1979)204–217.[23]R.E.Wengert,A simple automatic derivative evaluation pro-gram,Communications of the ACM7(8)(1964)463–464.[24]L.B.Rall,The arithmetic of differentiation,MathematicsMagazine59(5)(1986)275–282.[25]H.Kagiwada,R.Kalaba,N.Rasakhoo,K.Spingarn,Numer-ical Derivatives and Nonlinear Analysis,Plenum Press,New York,1986.[26] D.Mitchell,P.Hanrahan,Illumination from curved re-flectors,Computer Graphics26(2)(1992)283–291(SIG-GRAPH’92Proceedings).[27]M.Jerrell,Automatic differentiation using almost any lan-guage,ACM SIGNUM Newsletter24(1)(1989)2–9. [28]R.Hammer,M.Hocks,U.Kulisch,D.Ratz,C++NumericalToolbox for Verified Computing,Springer-Verlag,Berlin, 1995.[29]J.V.Aken,M.Novak,Curve-drawing algorithms for rasterdisplays,ACM Transactions on Graphics4(2)(1985)147–169,corrections in ACM TOG,6(1):80,1987.[30]R.E.Chandler,A tracking algorithm for implicitly definedcurves,IEEE Computer Graphics and Applications8(2) (1988)83–89.[31] A.Glassner,Andrew Glassner’s Notebook:Going the dis-tance,IEEE Computer Graphics and Applications17(1) (1997)78–84.[32] D.S.Arnon,Topologically reliable display of algebraiccurves,Computer Graphics17(3)(1983)219–227(SIG-GRAPH’83Proceedings).[33]G.Taubin,Rasterizing algebraic curves and surfaces,IEEEComputer Graphics and Applications14(2)(1994)14–23.[34]K.G.Suffern,Quadtree algorithms for contouring functionsof two variables,The Computer Journal33(5)(1990)402–407.[35]T.J.Hickey,Z.Qju,M.H.V.Emden,Interval constraintplotting for interactive visual exploration of implicitly de-fined relations,Reliable Computing6(1)(2000)81–92. [36]J.Tupper,Reliable two-dimensional graphing methods formathematical formulae with two free variables,Proceedings of SIGGRAPH2001(2001)77–86.[37]L.H.de Figueiredo,J.Stolfi,Adaptive enumeration of im-plicit surfaces with affine arithmetic,Computer Graphics Fo-rum15(5)(1996)287–296.[38]R.J.Balsys,K.G.Suffern,Visualisation of implicit sur-faces,Computers&Graphics25(1)(2001)89–107.Figure5:Two circles:Figure7:“Clown smile”:.Geometric adaption(left)versus spatial adaption(right)for and.Figure8:Cubic:.Geometric adaption(left)versus spatial adaption(right)for and.Figure9:Pear:.Geometric adaption(left)versus spatial adaption(right)for and .Figure10:Pisces logo:.Geometric adaption(left)versus spatial adaption(right) for and.Figure11:Sextic approximating a Mig outline.(Algebraic curvefitted to data points computed with software by T.Tasdizen available at.)Geometric adaption(left)versus spatial adaption(right)for and .Figure12:Quartic from Taubin’s paper[33]:.Geometric adaption(left) versus spatial adaption(right)for and.。
pwscf说明书

User’s Guide for Quantum ESPRESSO(version4.2.0)Contents1Introduction31.1What can Quantum ESPRESSO do (4)1.2People (6)1.3Contacts (8)1.4Terms of use (9)2Installation92.1Download (9)2.2Prerequisites (10)2.3configure (11)2.3.1Manual configuration (13)2.4Libraries (13)2.4.1If optimized libraries are not found (14)2.5Compilation (15)2.6Running examples (17)2.7Installation tricks and problems (19)2.7.1All architectures (19)2.7.2Cray XT machines (19)2.7.3IBM AIX (20)2.7.4Linux PC (20)2.7.5Linux PC clusters with MPI (22)2.7.6Intel Mac OS X (23)2.7.7SGI,Alpha (24)3Parallelism253.1Understanding Parallelism (25)3.2Running on parallel machines (25)3.3Parallelization levels (26)3.3.1Understanding parallel I/O (28)3.4Tricks and problems (29)4Using Quantum ESPRESSO314.1Input data (31)4.2Datafiles (32)4.3Format of arrays containing charge density,potential,etc (32)5Using PWscf335.1Electronic structure calculations (33)5.2Optimization and dynamics (35)5.3Nudged Elastic Band calculation (35)6Phonon calculations376.1Single-q calculation (37)6.2Calculation of interatomic force constants in real space (37)6.3Calculation of electron-phonon interaction coefficients (38)6.4Distributed Phonon calculations (38)7Post-processing397.1Plotting selected quantities (39)7.2Band structure,Fermi surface (39)7.3Projection over atomic states,DOS (39)7.4Wannier functions (40)7.5Other tools (40)8Using CP408.1Reaching the electronic ground state (42)8.2Relax the system (43)8.3CP dynamics (45)8.4Advanced usage (47)8.4.1Self-interaction Correction (47)8.4.2ensemble-DFT (48)8.4.3Treatment of USPPs (50)9Performances519.1Execution time (51)9.2Memory requirements (52)9.3File space requirements (52)9.4Parallelization issues (52)10Troubleshooting5410.1pw.x problems (54)10.2PostProc (61)10.3ph.x errors (62)11Frequently Asked Questions(F AQ)6311.1General (63)11.2Installation (63)11.3Pseudopotentials (64)11.4Input data (65)11.5Parallel execution (66)11.6Frequent errors during execution (66)11.7Self Consistency (67)11.8Phonons (69)1IntroductionThis guide covers the installation and usage of Quantum ESPRESSO(opEn-Source Package for Research in Electronic Structure,Simulation,and Optimization),version4.2.0.The Quantum ESPRESSO distribution contains the following core packages for the cal-culation of electronic-structure properties within Density-Functional Theory(DFT),using a Plane-Wave(PW)basis set and pseudopotentials(PP):•PWscf(Plane-Wave Self-Consistent Field).•CP(Car-Parrinello).It also includes the following more specialized packages:•PHonon:phonons with Density-Functional Perturbation Theory.•PostProc:various utilities for data postprocessing.•PWcond:ballistic conductance.•GIPAW(Gauge-Independent Projector Augmented Waves):EPR g-tensor and NMR chem-ical shifts.•XSPECTRA:K-edge X-ray adsorption spectra.•vdW:(experimental)dynamic polarizability.•GWW:(experimental)GW calculation using Wannier functions.The following auxiliary codes are included as well:•PWgui:a Graphical User Interface,producing input datafiles for PWscf.•atomic:a program for atomic calculations and generation of pseudopotentials.•QHA:utilities for the calculation of projected density of states(PDOS)and of the free energy in the Quasi-Harmonic Approximation(to be used in conjunction with PHonon).•PlotPhon:phonon dispersion plotting utility(to be used in conjunction with PHonon).A copy of required external libraries are included:•iotk:an Input-Output ToolKit.•PMG:Multigrid solver for Poisson equation.•BLAS and LAPACKFinally,several additional packages that exploit data produced by Quantum ESPRESSO can be installed as plug-ins:•Wannier90:maximally localized Wannier functions(/),writ-ten by A.Mostofi,J.Yates,Y.-S Lee.•WanT:quantum transport properties with Wannier functions.•YAMBO:optical excitations with Many-Body Perturbation Theory.This guide documents PWscf,CP,PHonon,PostProc.The remaining packages have separate documentation.The Quantum ESPRESSO codes work on many different types of Unix machines,in-cluding parallel machines using both OpenMP and MPI(Message Passing Interface).Running Quantum ESPRESSO on Mac OS X and MS-Windows is also possible:see section2.2.Further documentation,beyond what is provided in this guide,can be found in:•the pw forum mailing list(pw forum@).You can subscribe to this list,browse and search its archives(links in /contacts.php).Only subscribed users can post.Please search the archives before posting:your question may have already been answered.•the Doc/directory of the Quantum ESPRESSO distribution,containing a detailed de-scription of input data for most codes infiles INPUT*.txt and INPUT*.html,plus and a few additional pdf documents;people who want to contribute to Quantum ESPRESSO should read the Developer Manual,developer man.pdf.•the Quantum ESPRESSO Wiki:/wiki/index.php/Main Page.This guide does not explain solid state physics and its computational methods.If you want to learn that,you should read a good textbook,such as e.g.the book by Richard Martin: Electronic Structure:Basic Theory and Practical Methods,Cambridge University Press(2004). See also the Reference Paper section in the Wiki.This guide assume that you know the basic Unix concepts(shell,execution path,directories etc.)and utilities.If you don’t,you will have a hard time running Quantum ESPRESSO.All trademarks mentioned in this guide belong to their respective owners.1.1What can Quantum ESPRESSO doPWscf can currently perform the following kinds of calculations:•ground-state energy and one-electron(Kohn-Sham)orbitals;•atomic forces,stresses,and structural optimization;•molecular dynamics on the ground-state Born-Oppenheimer surface,also with variable cell;•Nudged Elastic Band(NEB)and Fourier String Method Dynamics(SMD)for energy barriers and reaction paths;•macroscopic polarization andfinite electricfields via the modern theory of polarization (Berry Phases).All of the above works for both insulators and metals,in any crystal structure,for many exchange-correlation(XC)functionals(including spin polarization,DFT+U,hybrid function-als),for norm-conserving(Hamann-Schluter-Chiang)PPs(NCPPs)in separable form or Ultra-soft(Vanderbilt)PPs(USPPs)or Projector Augmented Waves(PAW)method.Non-collinear magnetism and spin-orbit interactions are also implemented.An implementation offinite elec-tricfields with a sawtooth potential in a supercell is also available.PHonon can perform the following types of calculations:•phonon frequencies and eigenvectors at a generic wave vector,using Density-Functional Perturbation Theory;•effective charges and dielectric tensors;•electron-phonon interaction coefficients for metals;•interatomic force constants in real space;•third-order anharmonic phonon lifetimes;•Infrared and Raman(nonresonant)cross section.PHonon can be used whenever PWscf can be used,with the exceptions of DFT+U and hybrid functionals.PAW is not implemented for higher-order response calculations.Calculations,in the Quasi-Harmonic approximations,of the vibrational free energy can be performed using the QHA package.PostProc can perform the following types of calculations:•Scanning Tunneling Microscopy(STM)images;•plots of Electron Localization Functions(ELF);•Density of States(DOS)and Projected DOS(PDOS);•L¨o wdin charges;•planar and spherical averages;plus interfacing with a number of graphical utilities and with external codes.CP can perform Car-Parrinello molecular dynamics,including variable-cell dynamics.1.2PeopleIn the following,the cited affiliation is either the current one or the one where the last known contribution was done.The maintenance and further development of the Quantum ESPRESSO distribution is promoted by the DEMOCRITOS National Simulation Center of IOM-CNR under the coor-dination of Paolo Giannozzi(Univ.Udine,Italy)and Layla Martin-Samos(Democritos)with the strong support of the CINECA National Supercomputing Center in Bologna under the responsibility of Carlo Cavazzoni.The PWscf package(which included PHonon and PostProc in earlier releases)was origi-nally developed by Stefano Baroni,Stefano de Gironcoli,Andrea Dal Corso(SISSA),Paolo Giannozzi,and many others.We quote in particular:•Matteo Cococcioni(Univ.Minnesota)for DFT+U implementation;•David Vanderbilt’s group at Rutgers for Berry’s phase calculations;•Ralph Gebauer(ICTP,Trieste)and Adriano Mosca Conte(SISSA,Trieste)for noncolinear magnetism;•Andrea Dal Corso for spin-orbit interactions;•Carlo Sbraccia(Princeton)for NEB,Strings method,for improvements to structural optimization and to many other parts;•Paolo Umari(Democritos)forfinite electricfields;•Renata Wentzcovitch and collaborators(Univ.Minnesota)for variable-cell molecular dynamics;•Lorenzo Paulatto(Univ.Paris VI)for PAW implementation,built upon previous work by Guido Fratesi(ano Bicocca)and Riccardo Mazzarello(ETHZ-USI Lugano);•Ismaila Dabo(INRIA,Palaiseau)for electrostatics with free boundary conditions.For PHonon,we mention in particular:•Michele Lazzeri(Univ.Paris VI)for the2n+1code and Raman cross section calculation with2nd-order response;•Andrea Dal Corso for USPP,noncollinear,spin-orbit extensions to PHonon.For PostProc,we mention:•Andrea Benassi(SISSA)for the epsilon utility;•Norbert Nemec(U.Cambridge)for the pw2casino utility;•Dmitry Korotin(Inst.Met.Phys.Ekaterinburg)for the wannier ham utility.The CP package is based on the original code written by Roberto Car and Michele Parrinello. CP was developed by Alfredo Pasquarello(IRRMA,Lausanne),Kari Laasonen(Oulu),Andrea Trave,Roberto Car(Princeton),Nicola Marzari(Univ.Oxford),Paolo Giannozzi,and others. FPMD,later merged with CP,was developed by Carlo Cavazzoni,Gerardo Ballabio(CINECA), Sandro Scandolo(ICTP),Guido Chiarotti(SISSA),Paolo Focher,and others.We quote in particular:•Carlo Sbraccia(Princeton)for NEB;•Manu Sharma(Princeton)and Yudong Wu(Princeton)for maximally localized Wannier functions and dynamics with Wannier functions;•Paolo Umari(Democritos)forfinite electricfields and conjugate gradients;•Paolo Umari and Ismaila Dabo for ensemble-DFT;•Xiaofei Wang(Princeton)for META-GGA;•The Autopilot feature was implemented by Targacept,Inc.Other packages in Quantum ESPRESSO:•PWcond was written by Alexander Smogunov(SISSA)and Andrea Dal Corso.For an introduction,see http://people.sissa.it/~smogunov/PWCOND/pwcond.html•GIPAW()was written by Davide Ceresoli(MIT),Ari Seitsonen (Univ.Zurich),Uwe Gerstmann,Francesco Mauri(Univ.Paris VI).•PWgui was written by Anton Kokalj(IJS Ljubljana)and is based on his GUIB concept (http://www-k3.ijs.si/kokalj/guib/).•atomic was written by Andrea Dal Corso and it is the result of many additions to the original code by Paolo Giannozzi and others.Lorenzo Paulatto wrote the PAW extension.•iotk(http://www.s3.infm.it/iotk)was written by Giovanni Bussi(SISSA).•XSPECTRA was written by Matteo Calandra(Univ.Paris VI)and collaborators.•VdW was contributed by Huy-Viet Nguyen(SISSA).•GWW was written by Paolo Umari and Geoffrey Stenuit(Democritos).•QHA amd PlotPhon were contributed by Eyvaz Isaev(Moscow Steel and Alloy Inst.and Linkoping and Uppsala Univ.).Other relevant contributions to Quantum ESPRESSO:•Andrea Ferretti(MIT)contributed the qexml and sumpdos utility,helped withfile formats and with various problems;•Hannu-Pekka Komsa(CSEA/Lausanne)contributed the HSE functional;•Dispersions interaction in the framework of DFT-D were contributed by Daniel Forrer (Padua Univ.)and Michele Pavone(Naples Univ.Federico II);•Filippo Spiga(ano Bicocca)contributed the mixed MPI-OpenMP paralleliza-tion;•The initial BlueGene porting was done by Costas Bekas and Alessandro Curioni(IBM Zurich);•Gerardo Ballabio wrote thefirst configure for Quantum ESPRESSO•Audrius Alkauskas(IRRMA),Uli Aschauer(Princeton),Simon Binnie(Univ.College London),Guido Fratesi,Axel Kohlmeyer(UPenn),Konstantin Kudin(Princeton),Sergey Lisenkov(Univ.Arkansas),Nicolas Mounet(MIT),William Parker(Ohio State Univ), Guido Roma(CEA),Gabriele Sclauzero(SISSA),Sylvie Stucki(IRRMA),Pascal Thibaudeau (CEA),Vittorio Zecca,Federico Zipoli(Princeton)answered questions on the mailing list, found bugs,helped in porting to new architectures,wrote some code.An alphabetical list of further contributors includes:Dario Alf`e,Alain Allouche,Francesco Antoniella,Francesca Baletto,Mauro Boero,Nicola Bonini,Claudia Bungaro,Paolo Cazzato, Gabriele Cipriani,Jiayu Dai,Cesar Da Silva,Alberto Debernardi,Gernot Deinzer,Yves Ferro, Martin Hilgeman,Yosuke Kanai,Nicolas Lacorne,Stephane Lefranc,Kurt Maeder,Andrea Marini,Pasquale Pavone,Mickael Profeta,Kurt Stokbro,Paul Tangney,Antonio Tilocca,Jaro Tobik,Malgorzata Wierzbowska,Silviu Zilberman,and let us apologize to everybody we have forgotten.This guide was mostly written by Paolo Giannozzi.Gerardo Ballabio and Carlo Cavazzoni wrote the section on CP.1.3ContactsThe web site for Quantum ESPRESSO is /.Releases and patches can be downloaded from this site or following the links contained in it.The main entry point for developers is the QE-forge web site:/.The recommended place where to ask questions about installation and usage of Quantum ESPRESSO,and to report bugs,is the pw forum mailing list:pw forum@.Here you can receive news about Quantum ESPRESSO and obtain help from the developers and from knowledgeable users.You have to be subscribed in order to post to the list.Please browse or search the archive–links are available in the”Contacts”page of the Quantum ESPRESSO web site,/contacts.php–before posting: many questions are asked over and over again.NOTA BENE:only messages that appear to come from the registered user’s e-mail address,in its exact form,will be accepted.Messages”waiting for moderator approval”are automatically deleted with no further processing(sorry,too much spam).In case of trouble,carefully check that your return e-mail is the correct one(i.e.the one you used to subscribe).Since pw forum averages∼10message a day,an alternative low-traffic mailing list,pw users@,is provided for those interested only in Quantum ESPRESSO-related news,such as e.g.announcements of new versions,tutorials,etc..You can subscribe(but not post)to this list from the Quantum ESPRESSO web site.If you need to contact the developers for specific questions about coding,proposals,offersof help,etc.,send a message to the developers’mailing list:user q-e-developers,address.1.4Terms of useQuantum ESPRESSO is free software,released under the GNU General Public License. See /licenses/old-licenses/gpl-2.0.txt,or thefile License in the distribution).We shall greatly appreciate if scientific work done using this code will contain an explicit acknowledgment and the following reference:P.Giannozzi,S.Baroni,N.Bonini,M.Calandra,R.Car,C.Cavazzoni,D.Ceresoli,G.L.Chiarotti,M.Cococcioni,I.Dabo,A.Dal Corso,S.Fabris,G.Fratesi,S.deGironcoli,R.Gebauer,U.Gerstmann,C.Gougoussis,A.Kokalj,zzeri,L.Martin-Samos,N.Marzari,F.Mauri,R.Mazzarello,S.Paolini,A.Pasquarello,L.Paulatto, C.Sbraccia,S.Scandolo,G.Sclauzero, A.P.Seitsonen, A.Smo-gunov,P.Umari,R.M.Wentzcovitch,J.Phys.:Condens.Matter21,395502(2009),/abs/0906.2569Note the form Quantum ESPRESSO for textual citations of the code.Pseudopotentials should be cited as(for instance)[]We used the pseudopotentials C.pbe-rrjkus.UPF and O.pbe-vbc.UPF from.2Installation2.1DownloadPresently,Quantum ESPRESSO is only distributed in source form;some precompiled exe-cutables(binaryfiles)are provided only for PWgui.Stable releases of the Quantum ESPRESSO source package(current version is4.2.0)can be downloaded from this URL:/download.php.Uncompress and unpack the core distribution using the command:tar zxvf espresso-X.Y.Z.tar.gz(a hyphen before”zxvf”is optional)where X.Y.Z stands for the version number.If your version of tar doesn’t recognize the”z”flag:gunzip-c espresso-X.Y.Z.tar.gz|tar xvf-A directory espresso-X.Y.Z/will be created.Given the size of the complete distribution,you may need to download more packages and to unpack them following the same procedure(they will unpack into the same directory).Plug-ins should instead be downloaded into subdirectory plugin/archive but not unpacked or uncompressed:command make will take care of this during installation.Occasionally,patches for the current version,fixing some errors and bugs,may be distributed as a”diff”file.In order to install a patch(for instance):cd espresso-X.Y.Z/patch-p1</path/to/the/diff/file/patch-file.diffIf more than one patch is present,they should be applied in the correct order.Daily snapshots of the development version can be downloaded from the developers’site :follow the link”Quantum ESPRESSO”,then”SCM”.Beware:the develop-ment version is,well,under development:use at your own risk!The bravest may access the development version via anonymous CVS(Concurrent Version System):see the Developer Manual(Doc/developer man.pdf),section”Using CVS”.The Quantum ESPRESSO distribution contains several directories.Some of them are common to all packages:Modules/sourcefiles for modules that are common to all programsinclude/files*.h included by fortran and C sourcefilesclib/external libraries written in Cflib/external libraries written in Fortraniotk/Input/Output Toolkitinstall/installation scripts and utilitiespseudo/pseudopotentialfiles used by examplesupftools/converters to unified pseudopotential format(UPF)examples/sample input and outputfilesDoc/general documentationwhile others are specific to a single package:PW/PWscf:sourcefiles for scf calculations(pw.x)pwtools/PWscf:sourcefiles for miscellaneous analysis programstests/PWscf:automated testsPP/PostProc:sourcefiles for post-processing of pw.x datafilePH/PHonon:sourcefiles for phonon calculations(ph.x)and analysisGamma/PHonon:sourcefiles for Gamma-only phonon calculation(phcg.x)D3/PHonon:sourcefiles for third-order derivative calculations(d3.x)PWCOND/PWcond:sourcefiles for conductance calculations(pwcond.x)vdW/VdW:sourcefiles for molecular polarizability calculation atfinite frequency CPV/CP:sourcefiles for Car-Parrinello code(cp.x)atomic/atomic:sourcefiles for the pseudopotential generation package(ld1.x) atomic doc/Documentation,tests and examples for atomicGUI/PWGui:Graphical User Interface2.2PrerequisitesTo install Quantum ESPRESSO from source,you needfirst of all a minimal Unix envi-ronment:basically,a command shell(e.g.,bash or tcsh)and the utilities make,awk,sed. MS-Windows users need to have Cygwin(a UNIX environment which runs under Windows) installed:see /.Note that the scripts contained in the distribution assume that the local language is set to the standard,i.e.”C”;other settings may break them. Use export LC ALL=C(sh/bash)or setenv LC ALL C(csh/tcsh)to prevent any problem when running scripts(including installation scripts).Second,you need C and Fortran-95compilers.For parallel execution,you will also need MPI libraries and a“parallel”(i.e.MPI-aware)compiler.For massively parallel machines,or for simple multicore parallelization,an OpenMP-aware compiler and libraries are also required.Big machines with specialized hardware(e.g.IBM SP,CRAY,etc)typically have a Fortran-95compiler with MPI and OpenMP libraries bundled with the software.Workstations or“commodity”machines,using PC hardware,may or may not have the needed software.If not,you need either to buy a commercial product(e.g Portland)or to install an open-source compiler like gfortran or g95.Note that several commercial compilers are available free of charge under some license for academic or personal usage(e.g.Intel,Sun).2.3configureTo install the Quantum ESPRESSO source package,run the configure script.This is ac-tually a wrapper to the true configure,located in the install/subdirectory.configure will(try to)detect compilers and libraries available on your machine,and set up things accordingly. Presently it is expected to work on most Linux32-and64-bit PCs(all Intel and AMD CPUs)and PC clusters,SGI Altix,IBM SP machines,NEC SX,Cray XT machines,Mac OS X,MS-Windows PCs.It may work with some assistance also on other architectures(see below).Instructions for the impatient:cd espresso-X.Y.Z/./configuremake allSymlinks to executable programs will be placed in the bin/subdirectory.Note that both Cand Fortran compilers must be in your execution path,as specified in the PATH environment variable.Additional instructions for CRAY XT,NEC SX,Linux PowerPC machines with xlf:./configure ARCH=crayxt4./configure ARCH=necsx./configure ARCH=ppc64-mnconfigure Generates the followingfiles:install/make.sys compilation rules andflags(used by Makefile)install/configure.msg a report of the configuration run(not needed for compilation)install/config.log detailed log of the configuration run(may be needed for debugging) include/fft defs.h defines fortran variable for C pointer(used only by FFTW)include/c defs.h defines C to fortran calling conventionand a few more definitions used by CfilesNOTA BENE:unlike previous versions,configure no longer runs the makedeps.sh shell scriptthat updates dependencies.If you modify the sources,run./install/makedeps.sh or type make depend to updatefiles make.depend in the various subdirectories.You should always be able to compile the Quantum ESPRESSO suite of programs without having to edit any of the generatedfiles.However you may have to tune configure by specifying appropriate environment variables and/or command-line ually the tricky part is toget external libraries recognized and used:see Sec.2.4for details and hints.Environment variables may be set in any of these ways:export VARIABLE=value;./configure#sh,bash,kshsetenv VARIABLE value;./configure#csh,tcsh./configure VARIABLE=value#any shellSome environment variables that are relevant to configure are:ARCH label identifying the machine type(see below)F90,F77,CC names of Fortran95,Fortran77,and C compilersMPIF90name of parallel Fortran95compiler(using MPI)CPP sourcefile preprocessor(defaults to$CC-E)LD linker(defaults to$MPIF90)(C,F,F90,CPP,LD)FLAGS compilation/preprocessor/loaderflagsLIBDIRS extra directories where to search for librariesFor example,the following command line:./configure MPIF90=mpf90FFLAGS="-O2-assume byterecl"\CC=gcc CFLAGS=-O3LDFLAGS=-staticinstructs configure to use mpf90as Fortran95compiler withflags-O2-assume byterecl, gcc as C compiler withflags-O3,and to link withflag-static.Note that the value of FFLAGS must be quoted,because it contains spaces.NOTA BENE:do not pass compiler names with the leading path included.F90=f90xyz is ok,F90=/path/to/f90xyz is not.Do not use environmental variables with configure unless they are needed!try configure with no options as afirst step.If your machine type is unknown to configure,you may use the ARCH variable to suggest an architecture among supported ones.Some large parallel machines using a front-end(e.g. Cray XT)will actually need it,or else configure will correctly recognize the front-end but not the specialized compilation environment of those machines.In some cases,cross-compilation requires to specify the target machine with the--host option.This feature has not been extensively tested,but we had at least one successful report(compilation for NEC SX6on a PC).Currently supported architectures are:ia32Intel32-bit machines(x86)running Linuxia64Intel64-bit(Itanium)running Linuxx8664Intel and AMD64-bit running Linux-see note belowaix IBM AIX machinessolaris PC’s running SUN-Solarissparc Sun SPARC machinescrayxt4Cray XT4/5machinesmacppc Apple PowerPC machines running Mac OS Xmac686Apple Intel machines running Mac OS Xcygwin MS-Windows PCs with Cygwinnecsx NEC SX-6and SX-8machinesppc64Linux PowerPC machines,64bitsppc64-mn as above,with IBM xlf compilerNote:x8664replaces amd64since v.4.1.Cray Unicos machines,SGI machines with MIPS architecture,HP-Compaq Alphas are no longer supported since v.4.2.0.Finally,configure recognizes the following command-line options:--enable-parallel compile for parallel execution if possible(default:yes)--enable-openmp compile for openmp execution if possible(default:no)--enable-shared use shared libraries if available(default:yes)--disable-wrappers disable C to fortran wrapper check(default:enabled)--enable-signals enable signal trapping(default:disabled)and the following optional packages:--with-internal-blas compile with internal BLAS(default:no)--with-internal-lapack compile with internal LAPACK(default:no)--with-scalapack use ScaLAPACK if available(default:yes)If you want to modify the configure script(advanced users only!),see the Developer Manual.2.3.1Manual configurationIf configure stops before the end,and you don’tfind a way tofix it,you have to write working make.sys,include/fft defs.h and include/c defs.hfiles.For the latter twofiles,follow the explanations in include/defs.h.README.If configure has run till the end,you should need only to edit make.sys.A few templates (each for a different machine type)are provided in the install/directory:they have names of the form Make.system,where system is a string identifying the architecture and compiler.The template used by configure is also found there as make.sys.in and contains explanations of the meaning of the various variables.The difficult part will be to locate libraries.Note that you will need to select appropriate preprocessingflags in conjunction with the desired or available libraries(e.g.you need to add-D FFTW)to DFLAGS if you want to link internal FFTW).For a correct choice of preprocessingflags,refer to the documentation in include/defs.h.README.NOTA BENE:If you change any settings(e.g.preprocessing,compilationflags)after a previous(successful or failed)compilation,you must run make clean before recompiling,unless you know exactly which routines are affected by the changed settings and how to force their recompilation.2.4LibrariesQuantum ESPRESSO makes use of the following external libraries:•BLAS(/blas/)and•LAPACK(/lapack/)for linear algebra•FFTW(/)for Fast Fourier TransformsA copy of the needed routines is provided with the distribution.However,when available, optimized vendor-specific libraries should be used:this often yields huge performance gains. BLAS and LAPACK Quantum ESPRESSO can use the following architecture-specific replacements for BLAS and LAPACK:MKL for Intel Linux PCsACML for AMD Linux PCsESSL for IBM machinesSCSL for SGI AltixSUNperf for SunIf none of these is available,we suggest that you use the optimized ATLAS library:see /.Note that ATLAS is not a complete replacement for LAPACK:it contains all of the BLAS,plus the LU code,plus the full storage Cholesky code. Follow the instructions in the ATLAS distributions to produce a full LAPACK replacement.Sergei Lisenkov reported success and good performances with optimized BLAS by Kazushige Goto.They can be freely downloaded,but not redistributed.See the”GotoBLAS2”item at /tacc-projects/.FFT Quantum ESPRESSO has an internal copy of an old FFTW version,and it can use the following vendor-specific FFT libraries:IBM ESSLSGI SCSLSUN sunperfNEC ASLAMD ACMLconfigure willfirst search for vendor-specific FFT libraries;if none is found,it will search for an external FFTW v.3library;if none is found,it will fall back to the internal copy of FFTW.If you have recent versions of MKL installed,you may try the FFTW interface provided with MKL.You will have to compile them(only sources are distributed with the MKL library) and to modifyfile make.sys accordingly(MKL must be linked after the FFTW-MKL interface)MPI libraries MPI libraries are usually needed for parallel execution(unless you are happy with OpenMP multicore parallelization).In well-configured machines,configure shouldfind the appropriate parallel compiler for you,and this shouldfind the appropriate libraries.Since often this doesn’t happen,especially on PC clusters,see Sec.2.7.5.Other libraries Quantum ESPRESSO can use the MASS vector math library from IBM, if available(only on AIX).2.4.1If optimized libraries are not foundThe configure script attempts tofind optimized libraries,but may fail if they have been in-stalled in non-standard places.You should examine thefinal value of BLAS LIBS,LAPACK LIBS, FFT LIBS,MPI LIBS(if needed),MASS LIBS(IBM only),either in the output of configure or in the generated make.sys,to check whether it found all the libraries that you intend to use.If some library was not found,you can specify a list of directories to search in the envi-ronment variable LIBDIRS,and rerun configure;directories in the list must be separated by spaces.For example:./configure LIBDIRS="/opt/intel/mkl70/lib/32/usr/lib/math"If this still fails,you may set some or all of the*LIBS variables manually and retry.For example:./configure BLAS_LIBS="-L/usr/lib/math-lf77blas-latlas_sse"Beware that in this case,configure will blindly accept the specified value,and won’t do any extra search.。
Computational Fluid Dynamics

Computational Fluid Dynamics Computational Fluid Dynamics (CFD) is a branch of fluid mechanics that uses numerical analysis and data structures to solve and analyze problems that involve fluid flows. It has become an integral part of engineering and science, playing a crucial role in the design and optimization of various systems and processes. However, despite its widespread use and importance, CFD also presents a number of challenges and limitations that need to be addressed. One of the main challenges of CFD is the accuracy of the simulations. While CFD models are based on mathematical equations that describe fluid flow, these equations are often simplified and approximated to make them solvable using numerical methods. As a result, the accuracy of CFD simulations heavily depends on the assumptions and simplifications made, as well as the quality of the input data. This can lead to discrepancies between the simulated results and real-world observations, making it crucial for engineers and scientists to carefully validate and calibrate their CFD models. Another challenge of CFD is the computational cost associated with solving complex fluid flow problems. CFD simulations require significant computational resources, especially for high-fidelity simulations that involve complex geometries, turbulent flows, and multiphase interactions. This often leads to long simulation times and high computational expenses, limiting thepracticality of using CFD for certain applications. As a result, researchers are constantly seeking ways to improve the efficiency of CFD solvers and algorithms, as well as exploring new computing technologies such as parallel processing and cloud computing to reduce the computational burden. In addition to accuracy and computational cost, CFD also faces challenges related to the validation and verification of its models. Validating CFD simulations against experimental data is essential for establishing the credibility of the results and ensuring their reliability for making design decisions. However, experimental validation can be costly and time-consuming, and it may not always be feasible for certain applications. This raises questions about the reliability of CFD predictions and the level of confidence that can be placed in the simulation results, especially in critical engineering applications such as aerospace and automotive design. Moreover, the complexity of fluid flow phenomena presents a significant challengefor CFD, particularly in simulating turbulent flows and multiphase flows. Turbulent flows are characterized by chaotic and unpredictable behavior, making them notoriously difficult to model and simulate accurately. Similarly, multiphase flows, which involve the interaction of different phases of matter such as gas-liquid or liquid-solid, pose significant challenges due to the complex interfacial dynamics and phase interactions. As a result, CFD practitioners often resort to empirical modeling and simplifications to tackle these complexities, which can introduce uncertainties and limitations in the simulation results. Despite these challenges, CFD continues to advance and evolve, driven by ongoing research and development efforts aimed at addressing its limitations. Researchers are exploring new modeling approaches, such as large eddy simulation (LES) and direct numerical simulation (DNS), to improve the accuracy of turbulent flow predictions. They are also investigating new numerical methods and algorithms, such as immersed boundary methods and lattice Boltzmann methods, to enhance the capability and efficiency of CFD solvers. Furthermore, the integration of machine learning and artificial intelligence techniques into CFD holds promise for improving the predictive accuracy and reliability of simulations, particularly in cases where traditional modeling approaches fall short. In conclusion, while CFD presents several challenges and limitations, it remains a powerful tool for understanding and predicting fluid flow behavior in a wide range of engineering and scientific applications. By addressing the accuracy, computational cost, validation, and complexity challenges, ongoing research and development efforts continue to push the boundaries of what is achievable with CFD, opening up new possibilities for innovation and discovery in the field of fluid mechanics. As CFD continues to evolve, it is essential for practitioners to remain vigilant in critically evaluating and improving the reliability of CFD simulations, ensuring that they provide meaningful and trustworthy insights for engineering design and decision-making.。
Lattice Gauge Fields and Discrete Noncommutative Yang-Mills Theory

Contents
1 Introduction and summary 2 Quantum field theory on noncommutative spaces 2.1 2.2 2.3 2.4 Sc . . . . . . . . . . . . . . . . . . . . . . . . . . Noncommutative Yang-Mills theory . . . . . . . . . . . . . . . . . . . . . . . Star-gauge invariant observables . . . . . . . . . . . . . . . . . . . . . . . . . The noncommutative torus . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2 6 6 9 10 13 14 15 17 23 26 27 31 33 34 38 40 41 44
J. Ambjørn1) ∗ , Y.M. Makeenko1) 2) † , J. Nishimura1) ‡ and R.J. Szabo1) §
1)
The Niels Bohr Institute Blegdamsvej 17, DK-2100 Copenhagen Ø, Denmark
2)
Institute of Theoretical and Experimental Physics B. Cheremushkinskaya 25, 117218 Moscow, Russia
2
geometry provides a natural framework to describe nonperturbative aspects of string theory [2, 5]. This belief is further supported by the fact that Matrix Theory [6] and the IIB matrix model [7], which are conjectured to provide nonperturbative definitions of string theories, give rise to noncommutative Yang-Mills theory on toroidal compactifications [8]. The particular noncommutative toroidal compactification is interpreted as being the result of the presence of a background Neveu-Schwarz two-form field, and it can also be understood in the context of open string quantization in D-brane backgrounds [9, 10]. Furthermore, in Ref. [11] it has been shown that the IIB matrix model with D-brane backgrounds is described by noncommutative Yang-Mills theory. The early motivation [12] for studying quantum field theory on noncommutative spacetimes was that, because of the spacetime uncertainty relation, the introduction of noncommutativity would provide a natural ultraviolet regularization. However, more recent perturbative calculations [13]–[16] have shown that planar noncommutative Feynman diagrams contain exactly the same ultraviolet divergences that their commutative counterparts do, which implies that the noncommutativity does not serve as an ultraviolet regulator. One therefore needs to introduce some other form of regularization to study the dynamics of noncommutative field theories. On the other hand, it has been found that the ultraviolet divergences in non-planar Feynman diagrams [16, 17] exhibit an intriguing mixing of ultraviolet and infrared scales, which can also be described using string-theoretical approaches [18, 19]. Heuristically, this UV/IR mixing can be understood in terms of the induced uncertainty relations among the spacetime coordinates. If one measures a given spacetime coordinate with some high precision, then the remaining spacetime directions will generally extend because of the smearing. Furthermore, noncommutative solitons which do not have counterparts in ordinary field theory have been discovered [20] for sufficiently large values of the noncommutativity parameters, and it has also been shown [19] that noncommutative Yang-Mills theory in four dimensions naturally includes gravity. In order to investigate further the non-trivial dynamics of noncommutative field theories, it is important therefore to develop a nonperturbative regularization of these theories. Such a program has been put forward in Refs. [11, 15, 19],[21]–[24] and it is similar to earlier works [25] based on the mapping between large N matrices and spacetime fields. In particular, in Ref. [22] a unified framework was presented which naturally interpolates between the two ways that noncommutative Yang-Mills theory has appeared in the context of matrix model formulations of string theory, namely the compactification of Matrix theory and the twisted large N reduced model. The model proposed was a finite N matrix model defined by the twisted Eguchi-Kawai model [26, 27] with a quotient condition analogous to the ones considered in Refs. [8, 28]. It was interpreted as a lattice formulation of noncommutative
bynormanchonacky,editorinchief诺曼chonacky,主编

We shall not cease from explorationAnd the end of all our exploringWill be to arrive where we startedAnd know the place for the first time.—Four Quartets: Little Gidding, T.S. Elliott I spent a significant portion of my career as a physics professor. This was sufficiently long ago that I can claim to have been present at the beginning—the entry of com-puting into the physics teaching enterprise. In fact, this was less than a generation from the time that computers were first used in physics, thus it wasn’t entirely clear what the full scope and type of their applications would be. But it was fairly clear that they were surprisingly useful and their application was going to be fairly broad. What I don’t think any of us expected was the variety of tasks to which computers would be put nor the depth of the changes they would effect upon the ways we think about the physical world.T oday, a generation or so later, I’ve found occasion to re-visit this domain and be surprised all over again. The occa-sion is a decision I made as editor to make CiSE more relevant and useful to the physics education community. The surprise I found was how little had changed in the way physics is taught, even though enormous changes have oc-curred in the way physics—and other sciences, to say noth-ing of engineering—is done. Computational physics has actually become accepted as a “legitimate” mode of scien-tific investigation in its own right.CiSE’s association with physics education sprang from the magazine’s birth as the result of the marriage between IEEE Computational Science and Engineering (CSE) and the Amer-ican Institute of Physics’ Computers in Physics (CIP). The physics educational community was heavily invested in CIP,and at the time of the merger, CiSE started with a signifi-cant number of department editors drawn from that com-munity. CiSE’s content, like that of CIP before it, was deemed useful to those teaching physics.As time progressed, the interesting areas in scientific com-puting moved from the “garage” to the “factory,” and those with a major career investment in research moved along with this trend. But the way physics was taught, and I mean content rather than pedagogy, continued along pretty much the same. Clever new programming methods and algo-rithms were no longer needed as programming tools got more sophisticated. Ironically, this sophistication required more constant use than many instructors could afford to maintain their proficiency. At the same time, stand-alone products were no longer as easy to create as operating sys-tems became more complex, less transparent, and harder to work within. This meant that many educational users turned to boxed computational applications for instruction and some turned away entirely from trying to include serious computation in their courses. Consequently, computation stayed at the margins in mainstream physics curricular con-tent, and CiSE, now looking more like the old CSE than the old CIP, lost its usefulness for many physics instructors. Last year, I decided to make revisiting this venue a prior-ity. My first move was to convene a group of physics pro-fessors for whom computing hadn’t been marginalized, the purpose being an informal conversation to outline compu-tation issues in the undergraduate physics realm. This group had lots of ideas as well as lots of gripes and some laments about the state of computing in the curriculum. One pro-fessor, very prominent in this area, declared that the stan-dard introductory physics course content used methodology characteristic of the late 19th century—as if computing hadn’t happened at all.A C HANGE OF L ANDSCAPE AND AB ROADENED S COPEBy Norman Chonacky, editor in chiefI’VE PROMISED YOU THAT CISE WOULD BE BROADENING ITS SCOPE DURING MY TERM AS EDITOR IN CHIEF, AND THIS ISSUE MARKS THE START OF A NEW CHAPTER IN THIS EFFORT. SOMETIMES, IN SEEKING THE NEW, WE RE-ENCOUNTER THE OLD AND ARE SURPRISED BY WHAT WE’VE LEARNED:4Copublished by the IEEE CS and the AIP 1521-9615/06/$20.00 © 2006 IEEE C OMPUTING IN S CIENCE& E NGINEERINGJ ULY /A UGUST 20065From this meeting emerged the concept for a project and a possible role for CiSE in addressing these issues. The proj-ect was to build a community of common interest in the concept of bringing physics practice and physics educa-tional content closer together through computing. CiSE ’s role would be to enlarge our scope and presentation to more intentionally include the needs of this group of edu-cators for the purposes of facilitating their projects and in-creasing their numbers.This current issue is the first step in that direction. In it,you will find some of the usual—articles on state-of-the-art computational science topics such as neural networks and spectral analysis. But you’ll also find an article describing how software projects are being used in graduate training for computer scientists and software engineers. Another ar-ticle hints at the US National Science Digital Library’s abil-ity to foster computational physics education. We’re also experimenting with our article formats by introducing our first T echnical Note, a peer-reviewed article of smaller size and narrower content than our normal feature articles. This one happens to be a clever educational application that makes maximal use of modest resources, and it comes from a physics instructor laboring under stressful conditions: he’s from a university in Baghdad, Iraq.In the next issue, we’ll take a special look at computation in physics courses, and it will be the theme of the entire issue. Don’t miss it.N EW E DITORIAL B OARD M EMBERSMario Belloni is an associate professor of physics at Davidson College in North Carolina, where he also serves on its SACS Reaffirmation of Accreditation commit-tee. His research interests include mathematical methods,classical mechanics, electromagnetic theory, theoretical as-trophysics, and quantum mechanics. Belloni has a PhD and an MS in physics from the University of Connecticut.He is a member of the American Physical Society, theAmerican Association of Physics Teachers, and the Council on Undergraduate Research. He’ll serve as CiSE ’s new Book Review editor.Steven Gottlieb is a professor of physics at Indiana Univer-sity, where his research interests include elementary par-ticle theory—in particular, lattice QCD and computational physics. He has an AB in mathematics and physics from Cor-nell University and an MA and a PhD in physics from Prince-ton University. Gottlieb is a member of the AmericanPhysical Society and Sigma Xi, has served on the executive committee of the APS Division of Computational Physics,and is currently a division associate editor for Physical Review Letters . Contact him at sg AT .Rubin Landau is a professor of physics at Oregon State Uni-versity, where he also directs the university’s BS degree program in computational physics. His research interests in-clude theoretical/computational subatomic particle physics,high-performance computing, and computational science ed-ucation. Landau has a BS from Cornell University and a PhD from the University of Illinois. He serves on the executive com-mittee of the American Physical Society’s Division of Compu-tational Physics. He’ll serve as CiSE ’s new News editor.Greg Wilson is an adjunct professor in the Department of Computer Science at the University of Toronto, where he’s leading the development of a Web-based portal for managing undergraduate team programming projects. He also serves as a contributing editor to Doctor Dobb’s Journal .Wilson has a PhD in computer science from the University of Edinburgh. He served as a project mentor for Google’s 2005“Summer of Code.” Contact him via /~gvwilson.AMY NGVILLE &Google’s PageRank and Beyond about the science of Web page rankings. The book includes an extensive back-ground chapter designed to help general readers learn more about the math-ematics of search engines, and it contains several MATLAB codes and links to sample Web data sets. The philosophy throughout is to encourage readers to experiment with the ideas and algorithms in the text.Any business seriously interested in improving its rankings in the major search engines can benefit from the clear examples, sample code, and list of resources provided.“I don’t think there are any competitive books in print with the same depth and breadth on the topic of search engine ranking. The content is well-organized and well-written.”—Michael Berry, University of TennesseeCloth $35.00 0-691-12202-4Princeton University Press800-777-4726U.S.•Below is given annual work summary, do not need friends can download after editor deleted Welcome to visit againXXXX annual work summaryDear every leader, colleagues:Look back end of XXXX, XXXX years of work, have the joy of success in your work, have a collaboration with colleagues, working hard, also have disappointed when encountered difficulties and setbacks. Imperceptible in tense and orderly to be over a year, a year, under the loving care and guidance of the leadership of the company, under the support and help of colleagues, through their own efforts, various aspects have made certain progress, better to complete the job. For better work, sum up experience and lessons, will now work a brief summary.To continuously strengthen learning, improve their comprehensive quality. With good comprehensive quality is the precondition of completes the labor of duty and conditions. A year always put learning in the important position, trying to improve their comprehensive quality. Continuous learning professional skills, learn from surrounding colleagues with rich work experience, equip themselves with knowledge, the expanded aspect of knowledge, efforts to improve their comprehensive quality.The second Do best, strictly perform their responsibilities. Set up the company, to maximize the customer to the satisfaction of the company's products, do a good job in technical services and product promotion to the company. And collected on the properties of the products of the company, in order to make improvement in time, make the products better meet the using demand of the scene.Three to learn to be good at communication, coordinating assistance. On‐site technical service personnel should not only have strong professional technology, should also have good communication ability, a lot of a product due to improper operation to appear problem, but often not customers reflect the quality of no, so this time we need to find out the crux, and customer communication, standardized operation, to avoid customer's mistrust of the products and even the damage of the company's image. Some experiences in the past work, mentality is very important in the work, work to have passion, keep the smile of sunshine, can close the distance between people, easy to communicate with the customer. Do better in the daily work to communicate with customers and achieve customer satisfaction, excellent technical service every time, on behalf of the customer on our products much a understanding and trust.Fourth, we need to continue to learn professional knowledge, do practical grasp skilled operation. Over the past year, through continuous learning and fumble, studied the gas generation, collection and methods, gradually familiar with and master the company introduced the working principle, operation method of gas machine. With the help of the department leaders and colleagues, familiar with and master the launch of the division principle, debugging method of the control system, and to wuhan Chen Guchong garbage power plant of gas machine control system transformation, learn to debug, accumulated some experience. All in all, over the past year, did some work, have also made some achievements, but the results can only represent the past, there are some problems to work, can't meet the higher requirements. In the future work, I must develop the oneself advantage, lack of correct, foster strengths and circumvent weaknesses, for greater achievements. Looking forward to XXXX years of work, I'll be more efforts, constant progress in their jobs, make greater achievements. Every year I have progress, the growth of believe will get greater returns, I will my biggest contribution to the development of the company, believe inyourself do better next year!I wish you all work study progress in the year to come.。
Ergodic quantum computing

Dominik Janzing and Pawel Wocjan∗
IAKS Prof. Beth, Arbeitsgruppe Quantum Computing,
arXiv:quant-ph/0406235v1 30 Jun 2004
Universit¨ at Karlsruhe, Am Fasanengarten 5, 76 131 Karlsruhe, Germany June 30, 2004
1
Introduction
The question which control operations are necessary to achieve universal quantum computing is essential for quantum computing research. The standard model of quantum computation requires (1) preparation of basis states, (2) implementation of single and two-qubit gates and (3) single-qubit measurements in the computational basis. Meanwhile there are many proposals that reduce or modify the set of necessary control operations (see e.g. [1, 2, 3, 4, 5]). Common to all those models is that the program is encoded in a sequence of control operations. Here we consider a model which requires no control operations during the computation since the computation is carried out by the autonomous time evolution of a fixed
Solid State Electronic Devices

Solid State Electronic Devices : The Fundamentals and ApplicationsSolid state electronic devices are an essential part of modern technology. They are the basis for many electronic devices, such as computers, cell phones, and televisions. These devices are based on the principles of solid-state physics, which focuses on the study of materials and their properties.Solid state electronic devices, such as transistors, diodes, and integrated circuits, have revolutionized the way we live and work. They have made it possible to create smaller, faster, and more complex electronic devices. This article will explain the fundamental principles of solid-state electronic devices, their applications, and the future of solid-state electronics.The Physics ofSolid-state electronic devices are electronic components that are made from solid materials, such as semiconductor materials. A semiconductor material is one that has electrical conductivity between that of a conductor and an insulator. The most widely used semiconductor material is silicon, although other materials, such as germanium and gallium arsenide, are also used.The behavior of semiconductors is governed by their electronic properties, such as the energy band structure and the distribution of electrons and holes. These properties are determined by the arrangement of atoms in the crystal lattice structure of the material. The electronic properties of a semiconductor can be manipulated by doping it with impurities.Doping means intentionally introducing impurities or dopants into a semiconductor to modify its electrical properties. Two types of doping are used in semiconductors: n-type and p-type doping. N-type doping is the introduction of impurities with extra electrons, such as phosphorus or arsenic. P-type doping is the introduction of impurities with missing electrons, such as boron.When a semiconductor is doped with n-type impurities, it becomes an n-type semiconductor, which has a surplus of negatively charged electrons. When a semiconductor is doped with p-type impurities, it becomes a p-type semiconductor, which has a deficit of negatively charged electrons. The interaction between these two types of semiconductors is the basis of many solid-state electronic devices.The Applications ofSolid state electronic devices have many applications, from digital circuits to power electronics. They are used in the following applications:1. Digital CircuitsDigital circuits are circuits that use a binary system of 0s and 1s to represent information. Solid state electronic devices, such as diodes and transistors, are used to build digital circuits. Integrated circuits, which are made up of millions of transistors on a single chip, are used in digital circuits to perform billions of calculations in seconds.2. Power ElectronicsPower electronics involve the use of solid state electronic devices to convert electrical energy from one form to another. They are used in a wide range of applications, such as motor control, renewable energy systems, and electric vehicles. Power electronic devices, such as rectifiers, inverters, and DC-DC converters, are used in power electronics.3. OptoelectronicsOptoelectronics involves the use of solid state electronic devices to control and manipulate light. They are used in a wide range of applications, such as fiber optics, displays, and solar cells. Optoelectronic devices, such as LEDs, laser diodes, and photodetectors, are used in optoelectronics.The Future of Solid State ElectronicsSolid state electronics have come a long way since the invention of the transistor. However, there is still room for improvement. Future developments in solid state electronics will focus on the following areas:1. NanotechnologyNanotechnology involves the manipulation of matter on an atomic, molecular, and supramolecular scale. The use of nanotechnology in solid state electronics will lead to the development of smaller, faster, and more efficient devices.2. Quantum ComputingQuantum computing involves the use of quantum phenomena, such as superposition and entanglement, to perform calculations. The development of quantum computing will revolutionize the field of solid state electronics, leading to the development of new types of devices.3. Energy EfficiencyThe development of more energy-efficient solid state electronic devices is a priority, as the demand for energy continues to grow. The use of renewable energy sources, such as solar and wind power, will require the development of more efficient power electronic devices.ConclusionSolid state electronic devices have revolutionized the way we live and work. They are the basis for many electronic devices that we use every day. The principles of solid-state physics govern the behavior of these devices, and their applications are wide-ranging. The future of solid state electronics looks bright, with developments in nanotechnology, quantum computing, and energy efficiency leading the way.。
PLATON基操-计算堆积指数

PLATON基操-计算堆积指数(Packing Index)以下内容摘自《PLATON-MANUAL》Section 1.3.3.2。
《PLATON-MANUAL》可从以下地址下载:http://www.platonsoft.nl/PLATON-MANUAL.pdf1.3.3.2 − CALC K.P.I. − Calculate Solvent Accessible Volume + Packing Index.PLATON offers two options for the detection and analyses of solvent accessible voids in a crystal structure. The SOLV option is a faster version of the VOID option and recommended when only the solvent accessible volume is of interest. The additional expense in computing time with the VOID option is useful only when, in addition to the detection of solvent areas, a packing coefficient (Kitaigorodskii, 1961) is to be calculated (for which also the solvent inaccessible voids between atoms have to be considered) or when detailed unit cell sections are to be listed. The faster SOLV option is used implicitly as part of a SQUEEZE calculation and CIF-V ALIDATION (in order to report about incomplete structures).Some background information may be obtained from the paper: van der Sluis & Spek (1990 ) and Chapter 5. As a general observation it can be stated that crystal structures rarely contain solvent accessible voids larger than in the order of 25 Ang**3. However it may happen that solvent of crystallization leaves the lattice without disrupting the structure. This can be the case with strongly H-bonded structures around symmetry elements or framework structures such as zeolites.Packing IndexThe Kitaigorodskii type of packing index is calculated as a 'free' extra with the VOID calculation. Use the SOLV option when neither the packing index nor a map-section listing is needed. It should be remarked that structures have a typical packing index of in the order of 65 %. The missing space is in small pockets and cusps too small to include isolated atoms or molecules.The relevant keyboard instruction is:CALC VOID (PROBE radius [1.2]) (PSTEP n [6]/GRID s [0.2]) (LIST/LISTabc)The PROBE radius is taken by default as the van der Waals radius of Hydrogen.The GRID s is taken by default as 0.2 Angstrom.The PSTEP n should be such that n x s = radius for computational reasons.The LIST option produces a printout of the VOID grid. The default order of x,y&z in the listing may be managed manually with the LISTabc keyword where a,b,c can be X,Y,Z in any order. E.g. LISTXYZ has X section to section and Z horizontal.The horizontal grid has 130 steps as a maximum.译文如下:译文文档可从之前的推文《PLATON手册》中下载。
