11140820244RemoveRestrict
2024版Removed

Socioeconomic Factors
Factors such as population density, economic development, and social inequality can affect the vulnerability of communities to the removed phenomenon Higher population density and economic development levels may increase exposure and susceptibility to its impacts
13
04
Response strategies and measures
2024/1/24
14
Preventive measure
要点一
Risk assessment
Identify potential risks and hazards that could lead to removed situations, and assess their likelihood and impact
要点二
Mitigation measures
Implement measures to reduce the likelihood or impact of removed events, such as improving safety procedures, enhancing security measures, and providing training and education
2024/1/24
12
Trend prediction and evaluation
数据移除的管理规则

数据移除的管理规则
1. 目的
数据移除是为了保护个人隐私和公司敏感信息,遵守相关法律法规,确保数据安全。
2. 适用范围
这份管理规则适用于所有公司的数据处理工作,包括但不限于个人信息、客户资料、财务数据等。
3. 移除原则
- 数据移除应当遵循合法、正当、必要的原则,对于无关数据应当及时移除。
- 移除的数据应当进行彻底清除,确保无法恢复。
4. 移除流程
- 制定数据移除计划,明确移除的对象、范围和时间节点。
- 由专人负责数据移除工作,避免数据泄露和错误操作。
- 移除后需进行审计和验证,确保数据已被完全清除。
5. 监管与追踪
- 建立数据移除的监管机制,定期进行数据移除情况的检查与评估。
- 对于重要数据的移除,需进行备案并留存相关记录。
6. 处罚与责任
- 对于违反数据移除规则的行为,将依据公司规定进行相应的处罚。
- 数据移除工作由相应部门负责,确保责任明确。
7. 周期性评估
- 定期进行数据移除管理规则的评估,根据实际情况进行修订和完善。
以上为公司数据移除的管理规则,希望全体员工严格遵守,确保数据安全和个人隐私的保护。
google removalcause类型

Google Removal Cause 类型1. 概述在使用Google搜索引擎时,可能会遇到一些搜索结果被移除或隐藏的情况。
这些移除或隐藏的搜索结果是根据一定的移除原因来实施的。
而这些移除原因,即Removal Cause类型,对于了解搜索结果的工作原理和管理方式至关重要。
本文将介绍Google Removal Cause类型的相关知识,帮助读者更好地理解Google搜索引擎的运作机制。
2. Removal Cause 简介Removal Cause 是Google搜索引擎用于管理搜索结果并决定是否移除或隐藏特定内容的一种标准。
这些标准是依据Google的政策和法律法规制定的,旨在保护用户的利益和维护搜索结果的公正性和合法性。
在用户搜索特定内容时,如果搜索结果涉及被移除或隐藏的内容,便会显示相应的Removal Cause类型,通知用户这些搜索结果被移除的原因。
3. Google Removal Cause 类型在Google搜索结果被移除或隐藏时,会显示不同的Removal Cause 类型。
以下是一些常见的Removal Cause类型:3.1 违反Google政策有些搜索结果涉及违反Google政策的内容,如色情、暴力、恶意软件等。
这些搜索结果可能会被移除或隐藏,并显示“违反Google政策”类型的Removal Cause。
3.2 违反法律法规一些搜索结果可能涉及违反法律法规的内容,如侵犯版权、诽谤、盗窃等。
这些搜索结果会根据相关法律法规被移除或隐藏,显示“违反法律法规”类型的Removal Cause。
3.3 隐私问题部分搜索结果涉及用户的个人隐私信息,例如唯一识别信息号码、通联方式号码、住宅区域等。
这些搜索结果会被移除或隐藏,显示“隐私问题”类型的Removal Cause。
3.4 误导性信息有些搜索结果可能包含误导性的信息,如虚假广告、欺诈行为等。
这些搜索结果会被移除或隐藏,并显示“误导性信息”类型的RemovalCause。
DBV系列铜球式阀门说明书

APPLICATIONS • Gas or liquid flow control
SPECIFICATIONS Service: Gases and liquids compatible with wetted materials. End Connections: 1/4 to 3˝ female NPT. Pressure Limits: -29˝ Hg to 600 psi (-736 mm Hg to 41 bar) WOG. Temperature limit: -40 to 365ºF (-40 to 185ºC). Wetted Materials: Body and body cap: Brass; Ball: Chrome plated brass; Stem: Brass; Seat and packing: PTFE. Other Materials: Body gland and stem nut: Brass; Handle cover: Rubber; Handle: steel.
2˝
4-13/32 [112.01] 5-7/16 [137.92] 1-31/32 [50.04] 4-13/64 [106.93]
2-1/2˝ 5-53/64 [148.08] 8-1/2 [215.90] 2-31/64 [62.99] 4-61/64 [125.98]
3˝
6-29/64 [163.83] 8-1/2 [215.90] 2-61/64 [74.93] 5-1/8 [130.05]
The Series DBV Brass Ball Valve is an economical hand lever ball valve ideal for commercial or general industrial use. The Series DBV is the ideal choice for a manual shut off valve, along with many other applications. Valve body, body cap and ball are made of a quality brass for great durability. Seats and stem packing are constructed of PTFE for long lasting service as well. Blowout-proof stem provides safety in the event of overpressure. Full port design allows for maximum Cv while still retaining minimal pressure drop.
数据移除的管理规则

数据移除的管理规则1. 引言在数字化世界中,数据是一种强大的资源,但也需要谨慎处理。
本规则旨在定义并规范数据移除的原则和流程,确保数据在移除过程中的安全和合规性。
2. 数据移除的定义数据移除是指从存储设备或媒体中永久性地删除数据的过程。
这包括但不限于硬盘、闪存驱动器、光盘、磁带和其他储存介质。
3. 数据移除的原则3.1 确定性原则数据移除应当是确定性的,即一旦执行,数据应当被永久性地删除,不能被恢复或访问。
3.2 安全性原则数据移除应当是安全的,应避免在移除过程中数据泄露。
3.3 合规性原则数据移除应当符合相关的法律法规和政策要求,包括但不限于数据保护法、隐私法等。
4. 数据移除的流程4.1 数据移除申请数据移除需提交书面申请,申请中应明确需移除的数据类型、数据量、数据存储位置等信息。
4.2 数据移除评审数据移除申请需经过资讯科技部门评审,评审内容包括但不限于数据的敏感性、法规要求、移除方式等。
4.3 数据移除执行数据移除需由专业人员执行,执行过程需遵循相关流程和技术指南。
4.4 数据移除验证数据移除后,需通过相关技术手段验证数据是否已被完全移除,无法恢复。
4.5 数据移除记录需将数据移除的过程和结果进行记录,以便日后审计和复查。
5. 数据移除的方法5.1 物理销毁对于涉密或者重要的数据,可以选择物理销毁的方式,包括碎片化、磁化等。
5.2 工具擦除使用数据擦除工具覆盖原始数据,使数据无法恢复。
5.3 专业服务对于大型数据中心,可以选择专业的数据销毁服务,以节省时间和资源。
6. 结论本规则为公司提供了数据移除的原则和流程,以确保数据移除的确定性、安全性和合规性。
所有员工都应当遵循本规则,以保护公司的利益和客户的隐私。
gitguardian 扫描规则

gitguardian 扫描规则GitGuardian 扫描规则是用于检测代码仓库中可能存在的敏感信息或漏洞的一套规则集合。
该规则集旨在帮助开发团队更好地保护其代码和敏感信息的安全性。
1. API 密钥规则:该规则用于检测代码中是否包含 API 密钥,如 AWS 密钥、Google Cloud 密钥等。
API 密钥的泄露可能导致黑客获取权限并滥用 API。
2. 密码规则:该规则用于检测代码中是否包含硬编码的密码。
硬编码密码的存在可能导致攻击者轻易获取敏感信息或实施未授权访问。
3. 秘密文件规则:该规则用于检测代码中是否包含公开的秘密文件,例如`.env` 文件或其他包含敏感数据和凭证的文件。
这些文件的泄露可能暴露服务器或网站的敏感信息。
4. 加密密钥规则:该规则用于检测代码中是否包含加密密钥或证书。
加密密钥的泄露可能导致数据泄露或信息被篡改。
5. 数据库连接字符串规则:该规则用于检测代码中是否包含数据库连接字符串,如 MySQL、MongoDB 或 PostgreSQL 等。
数据库连接字符串的泄露可能导致数据库的未经授权访问或数据泄露。
6. 配置文件规则:该规则用于检测代码中是否包含配置文件,例如`config.xml` 或 `settings.py` 等。
这些配置文件的泄露可能导致服务器设置和应用程序配置的泄露。
7. 文件路径规则:该规则用于检测代码中是否包含敏感路径,例如`/etc/passwd` 或 `C:\Windows\System32`。
敏感路径的访问可能导致系统被黑客入侵或代码被滥用。
以上是 GitGuardian 扫描规则的几个示例,通过使用这些规则,开发团队能够及时发现并修复潜在的安全漏洞,从而确保代码和敏感信息的安全性。
disablerestrictedpermissions -回复

disablerestrictedpermissions -回复什么是受限权限(Restricted Permissions)?受限权限(Restricted Permissions)是一种机制,旨在限制某些应用程序或用户对操作系统或系统资源的访问权限。
这种权限限制是为了提高计算机和网络的安全性而采取的措施,可以防止恶意软件或未经授权的访问,保护用户的隐私和数据安全。
在计算机和移动设备的操作系统中,每个应用程序都被分配了一组权限。
这些权限用于确定应用程序可以执行的特定操作。
权限的具体范围和级别根据操作系统和设备的不同而有所差异。
例如,在移动设备上,应用程序可能会请求访问相机、联系人、位置或存储设备等权限。
这些权限的授予或拒绝由用户决定。
然而,有些应用程序可能会滥用所授予的权限。
它们可能未经授权地访问用户的个人信息、跟踪位置、监视通信,甚至可能对系统造成破坏或拖慢性能。
为了避免这些问题,操作系统引入了受限权限机制。
受限权限的工作原理是,将某些敏感功能或系统资源的访问权限限制在应用程序内部。
这样,即使应用程序被恶意软件或未经授权的用户攻击,其对系统和用户数据的访问也将受到限制。
通常,操作系统会在应用程序安装时明确询问用户是否授予某些权限。
用户可以选择接受或拒绝权限请求,并可以在之后的时间内随时修改这些设置。
受限权限的实现依赖于操作系统的安全机制。
操作系统会监视应用程序的权限使用,并确保其不会超出或滥用其授予的权限。
这意味着,即使应用程序请求了某个权限,但操作系统发现其实际使用该权限的频率或方式不正常,也可以限制或撤销该权限。
这种监控和控制机制有助于防止应用程序的滥用行为。
受限权限对于保护用户数据、隐私和系统安全至关重要。
它给予用户更大的控制权,使其能够主动选择哪些权限可以被应用程序访问。
然而,用户也需要对权限请求进行审慎决策并监控应用程序的行为。
同时,开发者也需要对其应用程序进行详尽测试,确保权限的使用始终在合理和正常的范围内。
linux restrict参数

linux restrict参数【原创实用版】目录1.Linux restrict 参数简介2.restrict 参数的作用3.restrict 参数的语法和使用方法4.restrict 参数的实例分析5.restrict 参数的安全性考虑正文1.Linux restrict 参数简介Linux restrict 参数是 Linux 内核中的一个安全特性,它用于限制进程对某些系统资源的访问。
这个特性在 Linux 2.2.16 之后被引入,旨在提供一种更加细粒度的资源访问控制。
2.restrict 参数的作用restrict 参数的主要作用是限制进程对某些系统资源的访问。
通过使用 restrict 参数,系统管理员可以更加精确地控制进程对系统资源的访问权限,从而提高系统的安全性。
3.restrict 参数的语法和使用方法restrict 参数的语法如下:```<macro> <restrict> <resource>```其中,`<macro>`表示一个宏,用于表示要限制的系统资源,如`mknod`、`open`、`read`等;`<restrict>`表示 restrict 关键字;`<resource>`表示要限制的系统资源。
例如,要限制一个进程创建特殊文件的权限,可以使用以下参数:```restrict mknod /dev/myfile cmajor 100```4.restrict 参数的实例分析下面通过一个具体的实例来分析 restrict 参数的使用:假设有一个进程 P,它需要访问`/dev/mem`文件。
如果直接对这个文件进行读写操作,可能会导致系统崩溃。
为了保证系统的安全性,可以使用 restrict 参数来限制进程 P 对`/dev/mem`文件的访问。
首先,创建一个设备文件`/dev/mem_限制`,并设置其访问权限:```mknod /dev/mem_限制 cmajor 100chmod 600 /dev/mem_限制```然后,修改进程 P 的访问权限,使其只能通过`/dev/mem_限制`访问`/dev/mem`文件:```restrict mknod /dev/mem cmajor 100```这样,进程 P 只能通过`/dev/mem_限制`文件访问`/dev/mem`文件,从而保证了系统的安全性。
ADEPT产品说明书

according to Federal Register / Vol. 77, No. 58 / Monday, March 26, 2012 / Rules and Regulations Date of issue: 07/28/2017Version: 1.007/28/2017EN (English)Page 11.1. IdentificationProduct form : Mixture Product name: ADEPTOther means of identification: EPA Reg. No. 400-4771.2. Recommended use and restrictions on useRecommended use : Insect growth regulatorRestrictions on use: Agriculture,For professional users only1.3. SupplierMacDermid Agricultural Solutions, Inc. 245 Freight StreetWaterbury, CT 06702 - USA T 1-866-761-9397**********************1.4. Emergency telephone numberEmergency number: FOR 24-HOUR MEDICAL EMERGENCY ASSISTANCE CALL PROPHARMA: 1-866-303-6952 or +1-651-603-3432 FOR 24-HOUR CHEMICAL EMERGENCY (Spill, leaks, fire, exposure or accident) call CHEMTREC: 1-800-424-9300 or +1-703-527-38872.1. Classification of the substance or mixtureGHS-US classification Acute toxicity (inhal.), Category 4H332 Harmful if inhaled Serious eye damage/eye irritation, Category 2B H320 Causes eye irritation Carcinogenicity, Category 1AH350 May cause cancerSpecific target organ toxicity — Repeated exposure, Category 2 H373 May cause damage to organs through prolonged or repeated exposure Hazardous to the aquatic environment — Acute Hazard, Category 1H400 Very toxic to aquatic lifeHazardous to the aquatic environment — Chronic Hazard, Category 1 H410 Very toxic to aquatic life with long lasting effects Combustible DustMay form combustible dust concentrations in airFull text of H statements : see section 162.2. GHS Label elements, including precautionary statementsGHS-US labellingHazard pictograms (GHS-US):GHS07GHS08GHS09Signal word (GHS-US) : DangerHazard statements (GHS-US): May form combustible dust concentrations in air H320 - Causes eye irritation H332 - Harmful if inhaled H350 - May cause cancerH373 - May cause damage to organs through prolonged or repeated exposure H400 - Very toxic to aquatic lifeH410 - Very toxic to aquatic life with long lasting effectsPrecautionary statements (GHS-US) : P201 - Obtain special instructions before useP202 - Do not handle until all safety precautions have been read and understoodP260 - Do not breathe dustP261 - Avoid breathing dustP264 - Wash hands, forearms and face thoroughly after handlingP271 - Use only outdoors or in a well-ventilated areaP273 - Avoid release to the environmentP280 - Wear eye protection, protective glovesP304+P340 - If inhaled: Remove person to fresh air and keep comfortable for breathingP305+P351+P338 - If in eyes: Rinse cautiously with water for several minutes. Remove contactlenses, if present and easy to do. Continue rinsingP308+P313 - If exposed or concerned: Get medical advice/attentionP312 - Call a doctor if you feel unwellP314 - Get medical advice/attention if you feel unwellP337+P313 - If eye irritation persists: Get medical advice/attentionP391 - Collect spillageP405 - Store locked upP501 - Dispose of contents/container to hazardous or special waste collection point, inaccordance with local, regional, national and/or international regulation2.3. Other hazards which do not result in classificationNo additional information available2.4. Unknown acute toxicity (GHS US)25.64% of the mixture consists of ingredient(s) of unknown acute toxicity (Oral)26.9% of the mixture consists of ingredient(s) of unknown acute toxicity (Dermal)25.64% of the mixture consists of ingredient(s) of unknown acute toxicity (Inhalation (Dust/Mist))3.1. SubstancesNot applicable3.2. Mixtures*Chemical name, CAS number and/or exact concentration have been withheld as a trade secretFull text of hazard classes and H-statements : see section 16SECTION 4: First-aid measures4.1. Description of first aid measuresFirst-aid measures general : Never give anything by mouth to an unconscious person. If you feel unwell, seek medicaladvice (show the label where possible).First-aid measures after inhalation : Call a poison center or a doctor if you feel unwell. Remove victim to fresh air and keep at rest ina position comfortable for breathing.First-aid measures after skin contact : Remove affected clothing and wash all exposed skin area with mild soap and water, followedby warm water rinse.First-aid measures after eye contact : IF IN EYES: Rinse cautiously with water for several minutes. Remove contact lenses, if presentand easy to do. Continue rinsing.First-aid measures after ingestion : Rinse mouth. Do NOT induce vomiting. Obtain emergency medical attention.4.2. Most important symptoms and effects (acute and delayed)Symptoms/effects : May cause damage to organs through prolonged or repeated exposure.Symptoms/effects after inhalation : May cause cancer by inhalation.Symptoms/effects after eye contact : Causes eye irritation.4.3. Immediate medical attention and special treatment, if necessaryTreat symptomatically.5.1. Suitable (and unsuitable) extinguishing mediaSuitable extinguishing media : Foam. Dry powder. Carbon dioxide. Water spray. Sand.Unsuitable extinguishing media : Do not use a heavy water stream.5.2. Specific hazards arising from the chemicalFire hazard : Combustible Dust. Burning produces irritating, toxic and noxious fumes. Dust may formexplosive mixture in air.Reactivity : No dangerous reactions known.5.3. Special protective equipment and precautions for fire-fightersFirefighting instructions : Use water spray or fog for cooling exposed containers. Exercise caution when fighting anychemical fire. Prevent fire fighting water from entering the environment.Protection during firefighting : Do not enter fire area without proper protective equipment, including respiratory protection.Wear a self contained breathing apparatus.6.1. Personal precautions, protective equipment and emergency proceduresGeneral measures : Avoid contact with skin, eyes and clothing. Avoid creating or spreading dust. Do not breathedust. Use personal protective equipment as required.6.1.1. For non-emergency personnelProtective equipment : Refer to section 8.2.Emergency procedures : Evacuate unnecessary personnel.6.1.2. For emergency respondersProtective equipment : Refer to section 8.2.Emergency procedures : Ventilate area.6.2. Environmental precautionsPrevent entry to sewers and public waters. Do not allow to enter drains or water courses.6.3. Methods and material for containment and cleaning upFor containment : Avoid generating dust. Contain and collect as any solid.Methods for cleaning up : On land, sweep or shovel into suitable containers. Minimize generation of dust. Store awayfrom other materials.6.4. Reference to other sectionsSection 13: disposal information. Section 7: safe handling. Section 8: personal protective equipment.7.1. Precautions for safe handlingPrecautions for safe handling : Provide good ventilation in process area to prevent formation of vapour. Obtain specialinstructions before use. Do not handle until all safety precautions have been read andunderstood. Avoid contact with skin, eyes and clothing. Avoid creating or spreading dust. Donot breathe dust. Use personal protective equipment as required.Hygiene measures : Do not eat, drink or smoke when using this product. Wash hands and other exposed areas withmild soap and water before eating, drinking or smoking and when leaving work.7.2. Conditions for safe storage, including any incompatibilitiesStorage conditions : Keep container tightly closed.Incompatible products : Strong bases. Strong acids. Strong oxidizers.Incompatible materials : Sources of ignition. Direct sunlight.Storage area : Store in dry, cool, well-ventilated area.8.1. Control parameters8.2. Appropriate engineering controlsAppropriate engineering controls : Avoid dispersal of dust in the air (ie, clearing dust surfaces with compressed air). Emergencyeye wash fountains and safety showers should be available in the immediate vicinity of anypotential exposure. Provide local exhaust or general room ventilation.Environmental exposure controls : Prevent leakage or spillage.8.3. Individual protection measures/Personal protective equipmentPersonal protective equipment : Avoid all unnecessary exposure.Hand protection : Wear suitable gloves resistant to chemical penetration. barrier laminate. Butyl rubber. nitrilerubber gloves. neoprene gloves. Viton.Eye protection : Chemical goggles or safety glasses.Respiratory protection : Wear appropriate mask.Other information : Do not eat, drink or smoke during use.SECTION 9: Physical and chemical properties9.1. Information on basic physical and chemical propertiesPhysical state : SolidAppearance : Powder.Colour : white to yellowOdour : FaintOdour threshold : No data availablepH : 7.97 ca.; concentration 10 g/lMelting point : No data availableFreezing point : No data availableBoiling point : No data availableFlash point : No data availableRelative evaporation rate (butylacetate=1) : No data availableFlammability (solid, gas) : Non flammable.Vapour pressure : No data availableRelative vapour density at 20 °C : No data availableRelative density : No data availableDensity : 18.7 lb/cu. ft.Solubility : Dispersible.Log Pow : No data availableAuto-ignition temperature : No data availableDecomposition temperature : No data availableViscosity, kinematic : No data availableViscosity, dynamic : No data availableExplosive limits : No data availableExplosive properties : No data availableOxidising properties : No data available9.2. Other informationNo additional information available10.1. ReactivityNo dangerous reactions known.10.2. Chemical stabilityDust may form flammable and explosive mixture with air.10.3. Possibility of hazardous reactionsHazardous polymerization will not occur.10.4. Conditions to avoidDirect sunlight. Extremely high or low temperatures.10.5. Incompatible materialsStrong acids. Strong bases. Strong oxidizers.10.6. Hazardous decomposition productsCarbon monoxide. Carbon dioxide.11.1. Information on toxicological effectsLikely routes of exposure : Inhalation; Skin and eye contactAcute toxicity : Inhalation: Harmful if inhaled.Skin corrosion/irritation : Not classified(Not irritating to skin)Serious eye damage/irritation : Causes eye irritation.Respiratory or skin sensitisation : Not classified(No sensitizing reaction was observed for guinea pigs) Germ cell mutagenicity : Not classifiedCarcinogenicity : May cause cancer.Reproductive toxicity : Not classifiedSpecific target organ toxicity (single exposure) : Not classified: May cause damage to organs through prolonged or repeated exposure. Specific target organ toxicity (repeatedexposure)Aspiration hazard : Not classifiedSymptoms/effects after inhalation : May cause cancer by inhalation.Symptoms/effects after eye contact : Causes eye irritation.SECTION 12: Ecological information12.1. Toxicity12.2. Persistence and degradability12.3. Bioaccumulative potential12.4. Mobility in soilADEPTEcology - soil Not established.12.5. Other adverse effectsOther information : Avoid release to the environment.13.1. Disposal methodsWaste disposal recommendations : Dispose in a safe manner in accordance with local/national regulations.Ecology - waste materials : Avoid release to the environment.Department of Transportation (DOT)In accordance with DOTNon-Bulk (<= 882 pounds / 400 Kg) NOT REGULATEDBulk (>882 pounds / 400 Kg) :Transport document description : UN3077 ENVIRONMENTALLY HAZARDOUS SUBSTANCE, SOLID, N.O.S. (Diflubenzuron),9, IIIUN-No.(DOT) : UN3077Proper Shipping Name (DOT) : ENVIRONMENTALLY HAZARDOUS SUBSTANCE, SOLID, N.O.S. (Diflubenzuron)Packing group (DOT) : III - Minor DangerHazard labels (DOT) : 9 - Class 9 (Miscellaneous dangerous materials)Dangerous for the environment : YesMarine pollutant : YesAdditional informationEmergency Response Guide (ERG) Number : 171Other information : No supplementary information available.Transport by seaIMDGTransport hazard class(es) (IMDG) : 9:Marine pollutant : YesUN-No. (IMDG) : 3077Transport document description (IMDG) : UN 3077 ENVIRONMENTALLY HAZARDOUS SUBSTANCE, SOLID, N.O.S. (Diflubenzuron),9, III, MARINE POLLUTANTClass (IMDG) : 9 - Miscellaneous dangerous substances and articlesPacking group (IMDG) : III - substances presenting low dangerEmS-No. (Fire) : F-AEmS-No. (Spillage) : S-FAir transportIATATransport hazard class(es) (IATA) : 9:Marine pollutant : YesUN-No. (IATA) : 3077Transport document description (IATA) : UN 3077 ENVIRONMENTALLY HAZARDOUS SUBSTANCE, SOLID, N.O.S. (Diflubenzuron),9, IIIClass (IATA) : 9 - Miscellaneous Dangerous GoodsPacking group (IATA) : III - Minor Danger15.1. US Federal regulationsAll components of this product are listed, or excluded from listing, on the United States Environmental Protection Agency ToxicSubstances Control Act (TSCA) inventory except for:CAS-No. 85586-07-8 1.5%Sulfuric acid, mono-C12-14 (even numbered)-alkyl esters,sodium saltsChemical(s) subject to the reporting requirements of Section 313 or Title III of the Superfund Amendments and Reauthorization Act (SARA) of1986 and 40 CFR Part 372.N-[[(4-chlorophenyl)amino]carbonyl]-2,6-difluorobenzamide CAS-No. 35367-38-5 25%This chemical is a pesticide product registered by the United States Environmental Protection Agency and is subject to certain labeling requirements under federal pesticide law. These requirements differ from the classification criteria and hazard information required for safety data sheets (SDS), and for workplace labels of non-pesticide chemicals. The hazard information required on the pesticide label is reproduced below. The pesticide label also includes other important information, including directions for use.:EPA Registration Number 400-477FIFRA Signal Word CAUTIONFIFRA Hazard Statement Causes moderate eye irritation. Avoid contact with eyes or clothing.FIFRA Other This pesticide is toxic to aquatic invertebrates. For terrestrial uses, do notapply directly to water or to areas where surface water is present or tointertidal areas below the mean high water mark. Drift or runoff from treatedareas may be hazardous to aquatic invertebrate organisms in neighboringareas. Do not contaminate water when disposing of equipment wastewateror rinsate.15.2. International regulationsCANADA15.3. US State regulationsCalifornia Proposition 65 - This product contains, or may contain, trace quantities of a substance(s) known to the state ofCalifornia to cause cancer, developmental and/or reproductive harmSECTION 16: Other informationData sources : ACGIH (American Conference of Government Industrial Hygienists).Component Supplier SDSs.European Chemicals Agency (ECHA) C&L Inventory database. Accessed athttp://echa.europa.eu/web/guest/information-on-chemicals/cl-inventory-database.Krister Forsberg and S.Z. Mansdorf, "Quick Selection Guide to Chemical Protective Clothing",Fifth Edition.Manufacturer Information.National Fire Protection Association. Fire Protection Guide to Hazardous Materials; 10thedition.Occupational Health Guide for chemical Substances - Vol. II, September, 1978.OSHA 29CFR 1910.1200 Hazard Communication Standard.Chemical Substance Inventory. Accessed at/oppt/existingchemicals/pubs/tscainventory/howto.html.Other information : None.Full text of H-statements:H228 Flammable solidH302 Harmful if swallowedH315 Causes skin irritationH318 Causes serious eye damageH319 Causes serious eye irritationH320 Causes eye irritationH332 Harmful if inhaledH335 May cause respiratory irritationH350 May cause cancerH373 May cause damage to organs through prolonged or repeated exposureH400 Very toxic to aquatic lifeH410 Very toxic to aquatic life with long lasting effectsAbbreviations and acronyms:ATE: Acute Toxicity EstimateCAS (Chemical Abstracts Service) numberEC50: Environmental Concentration associated with a response by 50% of the test population.GHS: Globally Harmonized System (of Classification and Labeling of Chemicals).LD50: Lethal Dose for 50% of the test populationOSHA: Occupational Safety & Health AdministrationSTEL: Short Term Exposure LimitsTSCA: Toxic Substances Control ActTWA: Time Weighted AverageNFPA health hazard : 2 - Materials that, under emergency conditions, can causetemporary incapacitation or residual injury.NFPA fire hazard : 2 - Materials that must be moderately heated or exposed torelatively high ambient temperatures before ignition canoccur.NFPA reactivity : 0 - Normally stable, even under fire exposure conditions,and not reactive with water.SDS Prepared by: The Redstone Group, LLC.6077 Frantz RdSuite 206Dublin, Ohio, USA 43016614.923.7472This information is based on our current knowledge and is intended to describe the product for the purposes of health, safety and environmental requirements only. It should not therefore be construed as guaranteeing any specific property of the product。
基线配置核查题库

基线配置核查题库基线配置核查是一项重要的安全措施,用于确保计算机系统和网络的安全性。
基线配置是指为了满足特定安全标准而对系统进行的一系列配置操作。
在基线配置核查中,我们需要检查系统是否按照安全要求进行了正确的配置,并对可能存在的安全风险进行评估。
以下是一些常见的基线配置核查题目,用于帮助我们评估系统的安全性:1. 系统是否定期更新补丁和安全补丁?是否存在未安装的关键补丁?2. 是否启用了强密码策略?密码长度、复杂性要求是否符合安全标准?3. 是否禁用了默认的管理员账户?是否配置了独立的管理员账户?4. 是否启用了账户锁定功能,限制了登录尝试次数?5. 是否启用了防火墙,并配置了适当的规则来限制网络流量?6. 是否禁用了不必要的服务和端口,以减少系统的攻击面?7. 是否配置了安全审计功能,记录了系统关键事件的日志?8. 是否配置了安全的文件和文件夹权限,限制了敏感数据的访问?9. 是否禁用了自动运行的功能,限制了恶意软件的传播?10. 是否安装了有效的防病毒软件,并定期更新病毒库?通过回答这些问题,我们可以评估系统的安全配置程度,并发现潜在的安全风险。
如果发现了配置不当或存在漏洞的情况,我们应该及时采取措施进行修复,以确保系统的安全性。
基线配置核查是保障系统和网络安全的重要一环,它可以帮助我们发现系统配置不当或存在漏洞的问题,及时采取措施进行修复,以防止潜在的安全威胁。
通过定期进行基线配置核查,可以确保系统按照安全要求进行了正确的配置,提高系统的安全性和稳定性。
在进行基线配置核查时,我们需要关注系统的各个方面,包括操作系统、网络设备、应用程序等。
同时,我们也需要不断学习和了解最新的安全威胁和防护技术,以提高我们的核查能力。
总结起来,基线配置核查是保障系统安全的重要一环,通过回答一系列的问题,可以评估系统的安全配置程度,发现潜在的安全风险,并及时采取措施进行修复。
通过定期进行基线配置核查,可以提高系统的安全性和稳定性,防止潜在的安全威胁。
去除停用词流程

去除停用词流程下载温馨提示:该文档是我店铺精心编制而成,希望大家下载以后,能够帮助大家解决实际的问题。
文档下载后可定制随意修改,请根据实际需要进行相应的调整和使用,谢谢!并且,本店铺为大家提供各种各样类型的实用资料,如教育随笔、日记赏析、句子摘抄、古诗大全、经典美文、话题作文、工作总结、词语解析、文案摘录、其他资料等等,如想了解不同资料格式和写法,敬请关注!Download tips: This document is carefully compiled by theeditor. I hope that after you download them,they can help yousolve practical problems. The document can be customized andmodified after downloading,please adjust and use it according toactual needs, thank you!In addition, our shop provides you with various types ofpractical materials,such as educational essays, diaryappreciation,sentence excerpts,ancient poems,classic articles,topic composition,work summary,word parsing,copy excerpts,other materials and so on,want to know different data formats andwriting methods,please pay attention!去除停用词流程一、准备工作阶段。
在进行去除停用词之前,需要做好充分的准备。
单位招聘考试EPC初级(试卷编号221)

单位招聘考试EPC初级(试卷编号221)1.[单选题]以下子网掩码正确的是?A)00000000-11111111-11110000-0000000000000000-11111111-11110000-00000000B)11011101-1101111-11101010-0000100011011101-1101111-11101010-00001000C)11111111-11111111-11111000-0000000011111111-11111111-11111000-00000000答案:C解析:32.[单选题]设定本局的信令点编码用于()协议的寻址。
A)SCCPB)RANAPC)GTPD)MTP3答案:D解析:3.[单选题]uMAC系统是基于()协议版本开发。
A)R5B)R6C)R7D)R8答案:D解析:4.[单选题]ZXUN-xGW GGSN新增动态地址池后会自动生成ACL。
由于全局ACL条目有限制,需要合理规划地址池。
下列地址段配置生成ACL最少的是( )。
The ZXUN-xGW GGSN will generate an ACL when a new local IP pool is added. Since the global number of ACL entries is limited, we need to plan the IP pool reasonably. On the following address segment, the number of ACL entries is the least: ( ).A)segment 10.123.1.0 10.123.1.255 mask 255.255.255.0 cpulocation 2/1B)segment 10.123.1.1 10.123.1.254 mask 255.255.255.0 cpulocation 2/1C)segment 10.123.1.1 10.123.1.255 mask 255.255.255.0 cpulocation 2/1D)segment 10.123.1.2 10.123.1.255 mask 255.255.255.0 cpulocation 2/1答案:A解析:5.[单选题]不可达定时器应该略比MS使用的()计时器长。
Clearswift SECURE Email Gateway说明书

With email still being the primary business collaboration tool, organizations need to ensure that the content and information they send and receive is both appropriate and permitted to enter or leave the organization. The Clearswift SECURE Email Gateway (SEG) helps to secure against critical information data loss; protecting the intellectual property and brand reputation of your organization and ensuring compliance with current regulations and standards.Clearswift’s award-winning deep-content inspection capabilities facilitate the competitive advantages inherent in open and safe communications; transforming email from a high-risk communication channel to one tailored exactly to your organization’s needs.The Gateway scans emails for sensitive content, and based on a granular organizational policy it provides the necessary flexibility to permit multiple behaviours, depending on the senders and recipients of the message. The Clearswift Adaptive Redactionfunctionality allows for content to be dynamically modified to make the content safe rather than having to stop and block and forcea remediation.Inbound threat protectionFeaturing integrated, cloud-assisted Kaspersky and / or Sophos anti-virus, with automatic updates every fifteen minutes toprovide the latest protection. These technologies are supplemented with zero-hour anti-malware and active code detection to ensure that no malware comes in, or goes out, via email. Targeted ransomware and spyware attacks typically use email with commonly used Office and PDF files as a means to deliver a payload. If these exploits manage to reach the desktop they will be run with the user privileges of the recipient, which could provide access to sensitive data. So as an addition to standardanti-malware features the Structural Sanitization feature permits macro’s, scripts and Active/X to be removed from messages, PDF and Office file formats significantly reducing the risk of targeted ransomware and spyware attacks being successful.Message Sanitization is able to remove URLs, attachments and HTML from messages to ensure there is no potential riskfrom that message.Best-of-Breed spam detectionThe new Clearswift SECURE Email Gateway comes with a completely redesigned anti-spam engine incorporating thebest-of-breed Mailshell component. This reduces the amount of spam reaching the end-user and the number of false positives.DMARC, SPF and DKIM support enables yet further spam reduction and with an Outlook Spam Reporter included, spam can be monitored, registered and eliminated. Featuring a new multi-layer spam defence mechanism using IP reputations, greylisting, signatures, SPF, RBL, recipient authentication and machine learning (Bayesian) engines to provide > than 99.9% detection rates, the SEG is able to drastically reduce the amount of time users spend managing their inboxes and significantly reduces theeffect of malware contained in spam.Context-aware content inspection policiesFlexible policies and context-aware content inspection mean you no longer have to choose between free-flowing communications and unacceptable risk. Flexible policy is the key to any real-world deployment. If the policy is too restrictive then people either cannot work effectively, or they find ways to get around their security policy.Adaptive RedactionClearswift’s unique Adaptive Redaction features permit the content of messages and attachments to be modified dynamically based on policy. The Data Redaction feature allows information to flow when before it would have been blocked. Customers can create policies to change specific words and phrases in messages and documents with “*” characters to make the content safe.This can apply to Credit Card numbers, Social Security details, Project codes, individual names or any custom value.Figure 1. Clearswift Adaptive Redaction: Data RedactionThe Document Sanitization feature can remove outstanding revision changes, clearing history and fast-save data that can also hold embarrassing critical information being accidentally disclosed. Document properties, such as “Author”, “Organization” and “Status” can be completely removed or bespoke properties can be preserved.DATA REDACTIONAdaptive RedactionOriginal Email with attachmentsEmail after Adaptive RedactionAdaptive Data Loss PreventionData loss is one of today’s biggest organizational concerns. Be it the latest designs, customer details or private employee information, the loss of intellectual property can ruin a company, both from a financial and reputational perspective.To reduce the chances of accidental data loss, the SECURE Email Gateway is able to control messages based on their content and their context. Context is provided through integration with Active Directory or LDAP, so policy can be applied to a specific individual or group (or the whole organization). The content of the message is checked through looking for text in the message body, subject line and also attachments, against 180 predefined policies.Policies consist of standard words, phrases or regular expressions, which can be used to look for complex alphanumeric patterns. These patterns could be used to identify an organization’s assets, such as credit cards, IBAN numbers, social security numbers, and many more.These phrases can be combined using Boolean and positional operators to create examples such as: • Credit .FOLLOWEDBY=1. Card• Confidential .AND. (Project .OR. Material)• C hecking for policy violations can also take place within image content such as screen shots, attachments and embedded content in documents.ComplianceStaying within the bounds of a regulatory framework is very important. To help you maintain compliance, the SECURE Email Gateway includes standard templates and dictionaries for common terms that may indicate a data breach.The Gateways are supplied with customisable dictionaries for GLBA, HIPAA, SEC and SOX to save deployment time. Organizations that must adhere to PCI and PII regulations can use a custom dictionary and the special ‘credit card’ and ‘social security’ tokens. Customers can augment the standard dictionaries with ones that may be more applicable.Organizations that must adhere to PCI and PII regulations, such as the EU GDPR, can use a custom dictionary and any of the more than 200+ pre-configured PCI and PII tokens to simplify policy definition and enforcement. Customers can augment the standard dictionaries with ones that may be more applicable.Some information will always need to be shared and email encryption is another important capability of the Gateway, ensuring that regulations relating to sensitive data sent over the internet are protected using strong encryption. The HITECH Act in the US and the EU’s General Data Protection Regulation make it clear that sensitive data must be encrypted when sent via email; the SECURE Email Gateway supports a number of different encryption mechanisms to provide flexibility as required.Email encryptionWith TLS as standard, and cost options to provide either S/MIME, PGP and password protected files or Web portal-based encryption, the Email Gateway offers a variety of options to cater for customer requirements. Whichever you choose, the Gateway allows sensitive data to be delivered securely, in seconds, using the optimal format for the recipient.Management and reportingThe user interface of the Gateway is powerful, yet simple to use. With roles based administration, automation and policy re-use, it’s quick and easy to build policy, manage violations, track messages and report on trends and behaviour. In this way, valuable insight is provided without consuming valuable admin resource.Deep content inspectionTrue file-type detection that recognizes files by signature and not by extension allows the Clearswift SECURE Email Gateway to understand files accurately. Compressed file archives are opened and the contents examined in real-time; embedded documents are discovered, and content is scanned in depth, to ensure data leakage is kept at bay.Flexible deployment optionsYou decide how you want to buy and deploy the Clearswift SECURE Email Gateway, either as a pre-installed hardware appliance, as a software image that can be loaded on a choice of hardware platforms, or alternatively virtualized in a VMware / Hyper-V environment. The Clearswift SECURE Email Gateway is also available as a Cloud solution using providers such as AWS and Azure or from Clearswift (regional offerings) as hosted virtual servers where you maintain control of the platform, but with the convenience and benefits of a Cloud delivery model.About ClearswiftClearswift is trusted by organizationsglobally to protect their criticalinformation, giving them the freedomto securely collaborate and drivebusiness growth. Our uniquetechnology supports a straightforwardand ‘adaptive’ data loss preventionsolution, avoiding the risk of businessinterruption and enabling organizationsto have 100% visibility of their criticalinformation 100% of the time.Clearswift operates world-wide, havingregional headquarters in Europe, AsiaPacific and the United States. Clearswifthas a partner network of more than 900resellers across the globe.More information is available atUK - International HQClearswift Ltd1310 WatersideArlington Business ParkTheale, Reading, BerkshireRG7 4SATel : +44 (0) 118 903 8903Fax : +44 (0) 118 903 9000Sales: +44 (0) 118 903 8700Technical Support: +44 (0) 118 903 8200Email:*******************AustraliaClearswift (Asia/Pacific) Pty LtdLevel 17 RegusCoca Cola Place40 Mount StreetNorth Sydney NSW 2060AustraliaTel: +61 2 9424 1200Technical Support: +61 2 9424 1210Email:*******************.auGermanyClearswift GmbHIm Mediapark 8D-50670 CologneGermanyTel: +49 (0)221 828 29 888Technical Support: +49 (0)800 1800556Email:******************JapanClearswift K.KShinjuku Park Tower N30th Floor3-7-1 Nishi-ShinjukuTokyo 163-1030JapanTel: +81 (3)5326 3470TechnicalSupport************Email:**********************United StatesClearswift Corporation309 Fellowship Road, Suite 200Mount Laurel, NJ 08054United StatesTel: +1 856-359-2360Technical Support: +1 856 359 2170Email:******************.comIntuitive web-based interface Ease of use and no requirement to learn complex syntax or Linuxcommands.Multi-gateway consolidated reporting Consolidated reporting view of user’s activities for easier analysis andsharing of management data.Multi-gateway message tracking Enables a view of where messages came from, how they wereprocessed and where they went across multi-gateways, complete withmanual or scheduled export capability.Centralized SYSLOG, SCOM, SNMP, SMTP Alerting Consolidate to a central SIEM, or use SCOM, SNMP or SMTP management alerts for a ‘lights out’ data centre deployment.* Cost Option。
安全数据表(SDS)单号:1796009-ENG-06,发布日期:1998年2月18日,修订日期:2
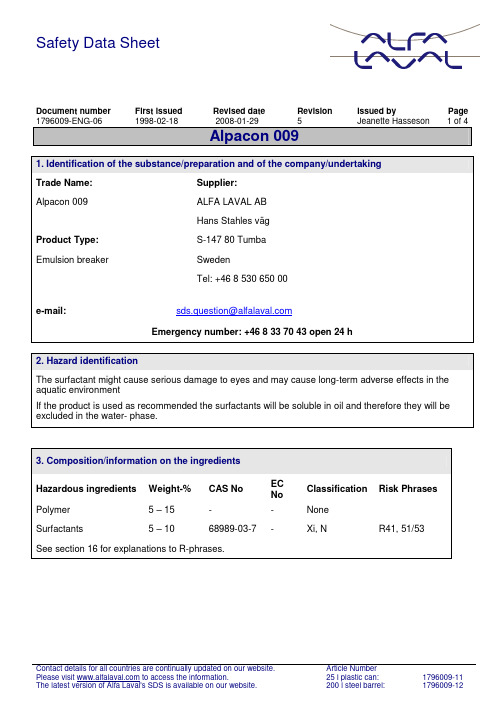
Safety Data SheetDocument number First issued Revised date Revision Issued by Page 1796009-ENG-06 1998-02-18 2008-01-29 5 Jeanette Hasseson 1 of 4Alpacon 0091. Identification of the substance/preparation and of the company/undertakingTrade Name: Supplier:Alpacon 009 ALFA LAVAL ABHans Stahles vägProduct Type: S-147 80 TumbaEmulsion breaker SwedenTel: +46 8 530 650 00e-mail:Emergency number: +46 8 33 70 43 open 24 h2. Hazard identificationThe surfactant might cause serious damage to eyes and may cause long-term adverse effects in the aquatic environmentIf the product is used as recommended the surfactants will be soluble in oil and therefore they will be excluded in the water- phase.3. Composition/information on the ingredientsHazardous ingredients Weight-% CAS No ECNoClassification Risk PhrasesPolymer 5 – 15 - - NoneSurfactants 5 – 10 68989-03-7 - Xi, N R41, 51/53 See section 16 for explanations to R-phrases.4. First –aid measuresFirst aid – Inhalation Move to fresh air.First aid – Skin contact Wash off with plenty of water.First aid – Eye contact Rinse immediately with tepid water for several minutes. Proceedthe rinse during transport to hospital.Obtain medical attention.First aid – Ingestion Rinse mouth and drink at least 1-2 glasses of water. Do notinduce vomiting.Obtain medical attention.5. Fire- fighting measuresExtinguishing media All extinguishing media are suitable.Special hazards of product The product is not flammable. In case of fire the product mightform hazardous gases as NOx and COx.Protective equipment for fire fighting Not applicable.Fire –fight If the fire is extinguished with water environmental dangeroussubstances might be entering the environment.6. Accidental release measuresPersonal precautions Wear suitable goggles and gloves.Environmental precautions Prevent spills from reaching sewage, wells and watercourses. Spillage Absorb spills with sand, earth or other inert material. Collect andremove for destruction.Large spillage Contact local authority7. Handling and storageHandling Do not mix with other chemicals. Use recommended personalprotection according to section 8.Storage Store in a closed container.8. Exposure control / personal protectionRespiratory protection Appropriate ventilation. Provide facilities for rinsing eyes.Skin protection Protective gloves of nitrile.Eye protection Safety goggles.Ingestion Do not eat or drink during use. Wash hands before eating.9. Physical and chemical propertiesPhysical state Clear liquid.Colour Slightly yellow.Odour Weak smell.Density at 20 °C (g/ml) 1.025± 0.005.pH (as is) at 20 °C 7-9°brix 17.8±0.6.Viscosity at 25 °C (SP01/20 rpm) (cP) 1368±130.Cloud point during heating (°C) 50ºC.Flash point >100 º C10. Stability and reactivityStability The product is stable under normal conditions, but it decomposesat high temperatures.Conditions to avoid Extreme heatMaterials to avoid None knownHazardous decomposition products None known if the product is handled as recommended. In caseof fire the product might form hazardous gases as NOx and COx.11. Toxicological informationSkin At prolonged or frequently use of the product blush might occur.Eyes The product might cause serious damage to eyes.Consumption Low acute toxicity . Might be irritating to mucous membrane.LD50 oral rat 4500mg/kgSkin irritation test rabbit Slightly irritatingEye irritation test rabbit Strongly irritatingSensibillisation Not allergenicGen toxicity Not mutagenic12. Ecological informationLC50 96h (fish) >100mg/lNOEC 96 h (fish) > 100mg/lEC50 48h (Daphnia magna) > 100mg/lNOEC 48 h (Daphnia magna) > 100 mg/lDegradation No readily bodegradable13. Disposal considerationsDisposal of product: State and local disposal regulations may differ from federaldisposal regulations. Always dispose in accordance with federal,state and local requirements.Disposal of containers: Containers should be reused or disposed of by landfill orincineration as appropriate.14. Transport informationNot classified as a hazardous substance according to transport regulations.15. Regulatory informationLabel Symbol(s): XiIrritantRisk Phrases: R36 Irritating to eyes.R52/53 Harmful to aquatic organisms, may cause long-termadverse effects in the aquatic environment.Safety Phrases: S39 Wear eye/ face protection.16. Other informationExplanations to R-phrases in section 2 R41 Risk of serious damage to eyes.R51/53 Toxic to aquatic organisms, may cause long-term adverse effects in the aquatic environment.See also product label for product applications.Important changes have been made in section: 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12 and 15.DISCLAIM OF RESPONSIBILITYAlfa Laval provides the information contained herein in good faith but makes no representation as to its comprehensiveness or accuracy. This document is only a guide to the potential hazards of the product. All individuals working with or around the product should be properly trained. Persons coming into contact with the product must be capable of exercising their own independent judgment concerning the conditions or methods of handling, storage and usage of the product. Alfa Laval will not be responsible for claims, losses, or damages of any kind resulting from the information provided in this Safety Data Sheet or the use, handling, storage or disposal of the product. Alfa Laval makes no representations or warranties, either express or implied, including without limitation any warranties of merchantability or fitness for a particular purpose with respect to the information set out herein or the product to which the information refers.。
nmi detected please consult -回复

nmi detected please consult -回复「NMI detected, please consult」是计算机系统中的一种错误提示,它意味着计算机的处理器在执行指令时检测到了一个非法的操作或异常情况。
NMI(非屏蔽中断)是一种特殊类型的中断信号,具有最高的优先级,可用于处理系统中的严重错误或故障。
当计算机系统发生NMI错误时,处理器会立即停止当前的执行任务,并生成一个NMI信号,然后通知操作系统和其他相关硬件设备。
这个错误通常表示系统遇到了严重的问题,需要进行故障排除和修复,以维护系统的稳定运行。
要解决「NMI detected, please consult」错误,首先需要确定错误的来源。
有许多可能导致NMI错误的因素,包括硬件故障、驱动程序冲突、软件错误或操作系统问题等。
以下是一些可能的步骤:1. 检查硬件连接:首先,检查计算机的硬件连接是否正确。
确保所有插槽、插头和电缆都牢固连接,并检查硬件设备是否正常工作。
2. 查看系统日志:打开操作系统的事件查看器或系统日志,查找与NMI 错误相关的任何错误消息或警告。
这些信息可以提供关于错误发生的时间、位置和可能的原因的线索。
3. 更新驱动程序和固件:许多NMI错误是由于驱动程序或固件问题引起的。
确保已安装最新版本的驱动程序和固件,并及时更新它们以解决已知的问题。
4. 运行系统诊断工具:大多数计算机系统都提供了内置的诊断工具,可以扫描硬件故障并检测问题。
运行这些工具可以帮助确定是否存在硬件故障。
5. 检查内存和硬盘:使用内置的内存和硬盘测试工具对系统进行全面的扫描。
损坏的内存或硬盘驱动器可能会导致NMI错误。
6. 清理和冷却系统:过热可能会导致计算机系统发生故障。
确保计算机的散热器清洁,风扇正常工作,并且系统处于适当的通风环境中。
7. 检查电源供应:摆在控制你计算机正常运行的最常见问题之一是电源供应问题。
确保电源供应稳定,并检查电缆和连接是否完好无损。
Oracle Communications Solution Integrations RODOD

Oracle Communications Solution IntegrationsUnderstanding the RODOD Reference SolutionProduct ManagementMarch 2015Safe Harbor StatementThe following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into any contract. It is not a commitment to deliver any material, code, or functionality, and should not be relied upon in making purchasing decisions. The development, release, and timing of any features or functionality described for Oracle’s products remains at the sole discretion of Oracle.Generally Available ApplicationsInstallationScripts &ConfigurationReferenceExamples& BestPracticesRODODReferenceSolutionWhat is the RODOD Reference Solution?•NEW with RODOD & AIA Comms 11.4 •Unattended installation of RODOD reduces skillsets and timelines for a standard install•Reference Data illustrates configuration best practices •Try out new & existing RODOD features•Common API extensions provided as samples •Low Risk standard RODOD Configuration •Self-contained RODOD install* for wider access •Suitable for training, demos, pre-sales, requirements definition, evaluation•Suitable for developing integrations, extensions to 3rd party systems, development systems, adapt & extend•NEW Available via OTN•Used by Development internally. Previously available only through Oracle Communications Consulting. •Free for use with commercial license applications including demo & partner licenses•OTN content is free but provided as-is. Partners & End-users are responsible for support •Requirements to Use References •Understanding of RODOD & Oracle application install •Read & review our Reference Documentation to ensure application compatibility•Acquire commercial applications via paid license or partner and/or demonstration licenses •Understanding of Linux OS, scripting, file systems, permissionsSharing RODOD Best Practices with RODOD ReferencesTrained on RODOD References using Guided Learning Paths Deployed in Partner Labs Forms the basis of Solution Driven Design and the Standard Solution for BSS & OSS.Over 2 years using our tools & references on key projects.Courseware & Transfer of Information (TOI) built on top of RODOD References Best Practices & Guidelines built from real customer deployments.Who is using RODOD References?Available through Oracle Technology Network•Well established fordistributing Oracleproduct samples•Use MIT License Termsfor Reference content•Organized collateralaround our BSS & OSSsolutions and clear linksto products•Available to both end-customers and SIpartnersRODOD Reference Solution: Unattended Installation•RODOD “typical” topology •Single instance of each application,•Minimum 4 x 16GB VMs with OEL/RHEL•Optional AMP/OEM for discovery & monitoring •Optional Revenue Management Suite IP 1.1•OEL 6.5+ / RHEL•DB 11g per each application, optional DB RAC •OSM O2A deployed with Calculate Service Order (CSO)•WLS Domains for each of AIA, OSM, PDC, AMP•Optional WLS Clustering for AIA & OSM This installation is not secure by default. It is intended for demonstration, training, enablement on RODOD. Please consult the secure installation guide for each application when deploying with live customer data or on a live network.Media Server Execute Unattended Install Siebel CRM RMS (BRM & PDC) AIA 11.4 PIPsOSM with O2A Windows / Browsers Design StudioAMP/OEMRODOD Reference Solution Compatibility MatrixApplication Version SummarySiebel for Communications 8.1.1.14 / IP14 Open UI, Bulk opsBilling & Revenue Management 7.5 PS10 ECE, install with (optional) RMS Reference Solution Product Design Center 11.1.0.6AIA for Communications 11.4 11g-based Technology stack (certified)AIA for Communications Product Integration Packs 11.4 Corporate Accounts, Legal Entity Collections, Payment onOrder, New attributes on EBO for SOMOrder & Service Management 7.2.4.1 Large orders, OTMOrder & Service Management Cartridges for Order-to-Active (O2A) 2.1.0 Includes OTM and provides a Calculate Service Order(CSO) functionality. New sample SOMThe RODOD Reference Solution installs the latest certified applications based on AIA for Communications 11.4. The installation scripts are not certified for all combinations and do not provide upgrade(s).RODOD Reference Solution: New AIA 11.4 & AMP Features •Siebel Open UI with bulk order handling•Corporate Account Hierarchy•Legal Entities & Split Billing•Family Share Plans•Electronic Bill Presentment (EBP)•A charging use-case to illustrate RODOD-RMS integration •Discover RODOD stack from OEM Application Management Packs (AMP)•Offer design with PDC, BRM & Siebel•Plus core and legacy RODOD features for Order Capture, Order Delivery & Agent Assisted Billing & CareMost new features will include public recordings. The recordings are built based on the RODOD Reference Solution and can be followed step-for-step on the Reference Installation•Go to the OTN site for RODOD•Start with a review of our RODODcollateral before Reference installation •Download the install scripts & document packages •Review the installation presentation, Getting Started & install recordings •Install RODOD •Try-out RODOD features based on the User Guide and recordingsRODOD Reference Solution: Next StepsRODOD Reference What’s New RODOD Reference Installation Getting Started Guide TOI Install Recordings on Oracle UniversityInstallation GuideRODOD Reference Data & Use Cases RODOD Reference User GuideTOI User Demo Recordings on OUSafe Harbor StatementThe preceding is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into any contract. It is not a commitment to deliver any material, code, or functionality, and should not be relied upon in making purchasing decisions. The development, release, and timing of any features or functionality described for Oracle’s products remains at the sole discretion of Oracle.。
ruleremovetargetbyid 多个规则

ruleremovetargetbyid 多个规则如何使用"ruleremovetargetbyid"来删除多个规则。
Step 1: 了解ruleremovetargetbyid是什么首先,我们需要了解ruleremovetargetbyid是一个什么样的函数或方法。
ruleremovetargetbyid是一个用于删除规则的命令,它可以通过指定规则的id来删除特定的规则。
与其他删除规则的功能类似,ruleremovetargetbyid可以用于清理代码库中不需要的规则或进行规则管理。
Step 2: 定位要删除的规则的id在使用ruleremovetargetbyid之前,我们需要找到要删除的规则的id。
规则id通常由系统分配,并且可以在规则管理面板或相关文档中找到。
确保准确地找到了要删除的规则的id,以避免意外删除其他规则。
Step 3: 导入必要的库或环境在使用ruleremovetargetbyid之前,我们需要确保所需的库或环境已导入。
具体要求取决于您使用的编程语言或开发工具。
例如,在使用JavaScript编写的Web应用程序中,您可能需要导入相关的JavaScript 库或设置环境。
Step 4: 编写删除规则的代码在了解如何使用ruleremovetargetbyid之后,我们可以编写代码来删除多个规则。
以下是一个示例代码片段,展示了如何使用ruleremovetargetbyid来删除三个不需要的规则:var ruleIds = ["ruleId1", "ruleId2", "ruleId3"];for (var i = 0; i < ruleIds.length; i++) {ruleremovetargetbyid(ruleIds[i]);}在该示例代码中,我们将要删除的规则的id存储在一个数组中,并使用for循环遍历该数组。
nftables 删除规则

nftables 删除规则nftables是一个强大而灵活的Linux内核防火墙管理工具,它允许您创建、修改和删除防火墙规则,使您能够更好地保护您的系统和网络。
删除规则也是使用nftables非常重要的一部分,因为它允许您对防火墙策略进行动态调整。
要删除nftables规则,您需要知道规则的表、链和规则集。
表定义了规则存储的位置,链定义了规则的匹配条件,规则集定义了规则的具体操作。
首先,您可以使用nft list ruleset命令来查看当前nftables规则防火墙的配置。
nft list ruleset这将显示当前的nftables配置,包括表、链和规则集的详细信息。
要删除规则,您需要编辑或创建一个新的nftables配置文件,然后将其应用到防火墙中。
下面是一个简单的示例,显示了如何删除具有特定匹配条件的规则:```table ip my_table {chain my_chain {type filter hook input priority 0; policy accept;ip daddr 192.168.0.1 drop;}}delete rule ip my_table my_chain ip daddr 192.168.0.1 drop```这个示例中,我们定义了一个名为my_table的表,其中包含一个名为my_chain的链。
链的类型为filter,挂载在input钩子上,并且拥有优先级0和默认策略接受。
我们还定义了一个规则,该规则将目的IP地址为192.168.0.1的数据包丢弃。
在删除规则之前,我们首先需要确保规则存在。
我们可以使用nft list ruleset命令来查看规则的存在:```nft list ruleset```如果规则存在,我们可以使用delete rule语句将其从表中删除。
在上面的示例中,我们使用delete rule命令来删除具有特定匹配条件(目的IP地址为192.168.0.1)的规则。
excludedparties list system -回复

excludedparties list system -回复什么是排除名单系统(Excluded Parties List System)?排除名单系统(EPLS)是一种用于管理和保护政府采购过程的工具。
它是政府机构和组织用来确定哪些个人、公司或组织不得参与政府采购项目的系统。
这些被列入排除名单的实体可能因为诈骗、腐败、合同违规或其他违法行为而被禁止参与政府采购项目。
排除名单系统的目的是确保公共资源的合理和透明使用,保护政府采购过程的诚信,以及遏制腐败。
为什么需要排除名单系统?政府采购项目通常涉及大量的资金和资源。
如果腐败和不当行为得不到监管和控制,这些项目可能会受到损害,导致资金浪费和不公平竞争。
排除名单系统的引入旨在为政府采购项目提供更高的透明度和责任性。
通过禁止那些曾经从事违法行为的实体参与政府采购,排除名单系统能够帮助保护公共财产和利益。
如何建立排除名单系统?建立一个有效的排除名单系统需要政府机构和组织采取一系列的步骤。
首先,政府机构或相关组织需要对其政府采购政策进行审查和修改,以确保适当的排除名单制度的引入。
其次,他们需要明确制定具体的规则和标准,以决定哪些行为将使某个实体被列入排除名单。
这包括定义违规行为的范围、界定处罚机制和确定排除名单的期限。
然后,政府机构和组织需要建立一个数据库或系统来记录和管理排除名单。
这个系统需要能够被各个政府机构和相关组织访问,并能够及时更新和追踪排除名单中的信息。
这样一来,政府机构在进行采购前就可以查询并确认参与者是否被列入排除名单。
一个有效的排除名单系统还应该包括相应的申诉和上诉机制,以确保被列入排除名单的实体有机会辩护或申诉。
这有助于防止错误和不公正的列入排除名单。
其他需要考虑的因素:除了建立排除名单系统的步骤,还有一些其他因素需要考虑。
例如,政府机构和组织应该与其他国际组织和机构分享排除名单信息,以便更广泛地保护公共资源和利益。
此外,建立培训和教育计划,以帮助政府工作人员和供应商了解排除名单系统的操作和重要性也是非常重要的。
说明drop table时,restrict和cascade的区别。 -回复

说明drop table时,restrict和cascade的区别。
-回复在关系型数据库系统中,DROP TABLE是一种命令,用于删除数据库中的表。
当我们执行DROP TABLE命令时,系统会要求用户确认该操作,因为表的删除是一个不可逆的操作。
在确认删除之前,我们可以选择使用RESTRICT或CASCADE来指定删除操作的行为。
RESTRICT和CASCADE是两种不同的约束类型,它们可以应用于DROP TABLE命令。
这两种约束的主要目的是确保数据的完整性和一致性。
下面我们将详细讨论RESTRICT和CASCADE的区别。
RESTRICT是DROP TABLE命令的默认行为。
当我们使用RESTRICT约束时,系统会检查是否存在与要删除的表相关联的外键约束。
如果存在外键约束,则系统会阻止删除操作,并给出一个错误消息。
假设我们有两个表:表A和表B。
表B是表A的外键约束。
如果我们尝试删除表A,并且使用RESTRICT约束,系统将检查表B是否引用了表A的主键。
如果是这样,系统将不允许删除表A,以遵守外键约束。
在这种情况下,我们可以首先删除对表A的所有引用,然后再删除表A。
CASCADE约束与RESTRICT约束不同。
当我们使用CASCADE约束时,系统将自动删除与要删除的表相关联的外键约束。
这意味着,不仅删除表A,还会同时删除引用表A的所有其他表。
CASCADE约束的作用是确保删除操作不会破坏数据的完整性和一致性。
以之前的例子为例,如果我们使用CASCADE约束来删除表A,系统会检查表B是否引用了表A的主键。
如果是这样,系统将自动删除表B,以遵守外键约束。
这样,我们可以在不手动删除引用表A的其他表的情况下,一次性删除表A及与之相关的所有表。
使用RESTRICT或CASCADE约束取决于我们对数据的处理方式。
如果我们希望手动处理数据完整性和一致性问题,我们可以选择使用RESTRICT 约束。
这样,系统会阻止任何可能破坏数据完整性的操作。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
学 0 0 0 0
0000
0 0
0 0
0 1
1 I/D S D CB
5
光标/字符移位
0 0 0 0 0 1 S/C R/L * *
6
功能
0 0 0 0 1 DL N F * *
7 8 9
置字符发生器地址 置数据存贮器地址 读忙标志和地址
院 0 0 0 1
001 0 1 BF
字符发生存贮器地址 显示数据存贮器地址
(2) 保存项目。如下图 4 所示,将项目保存到上一步专门建立的文件流水灯里边,
(3)
院 并且将项目的名称也命名为“流水灯”。
选择芯片。将目标芯片选择为 NXP/LPC2114。如图 5 所示。
(4)选择添加启动代码“Startup.s”文件,如图 6 所示。点击“是”,用来添加启动 代码。
韶关学院电子系-- HYQ
#define INT32S signed int
#define INT32U unsigned int
#define LedBus 0x3ff
/***************************/
//延时函数
void Delay(INT32U x)
{
while(x--);
}
韶 //延时函数结束
(1) Protues 放置元件与放置电源接地符号的选择。在左边的快捷图标中,按照 下图 14 指示,可使得系统处于放置元件还是处于放置电源符号状态。
韶关学院电子系-- HYQ
《嵌入式系统原理实验讲义》实验一 GPIO 输出控制实验
(2) 用鼠标点击图 14 的放置元件图标,在点 P 按钮,就可进入元件放置放置状 态。如图 15 所示。
韶关学院电子系-- HYQ
仿真。
《嵌入式系统原理实验讲义》实验一 GPIO 输出控制实验
六.思考题
韶 1.在完成本实验内容的基础上,将发光二极管接到 P1.16-P1.24。重新编程,实现流水
灯的显示模式如下:
关
其中,模式 1 的显示方式为:只让 D1 亮,然后以较快的速度往下移动,直到 D10。然后 D10 保持亮的状态,又从 D1 开始,亮到 D9。以此类推,直到全部都亮。要求灯往下沉的
6.执行菜单 Project/Rebuilt all target
files 命令。或者快捷图标
编译程
序。
编译之后,会在下边的输出窗口给出编
译的结果。如果没有错误,最后提示的结果
如下图 12 所示。如果存在错误 Error(s),则
一定要将错误排除,程序才能允许。如果提示有警告 Warrning(s),则要弄清楚引起警告的
韶关学院电子系-- HYQ
《嵌入式系统原理实验讲义》实验一 GPIO 输出控制实验
原因是什么。有些警告不影响系统运行。
7.打开 Protues 软件,设计仿真电路图。
韶 关 学 院
图 13 仿真电路图 图 13 中,U1 为 LPC2124 芯片。U2 为整排的发光二极管,名称为 LED-BARGARPH-GRN, RN1 为排阻,名称为 RX8。R1,R2 为电阻,名称为 RES。
(3) 在图 15 的元件库中,在 KeyWords 中输 入关键词,如 LPC2114 就可以找到元件。也可以先 找到元件种类,再到具体的元件列表中找到所需的 元件。
常用的元件类别如下: Capactors:电容。 Diodes:二极管 Inductors:电感 Microprocessors ICs:微处理器,MCS51、ARM7、 AVR 单片机等芯片。 Optelectronics:光电器件,发光二极管、数码 管、LCD 都包含在这里。
《嵌入式系统原理实验讲义》实验一 GPIO 输出控制实验
#include "LPC22XX.H"
#define INT8S signed char
#define INT8U unsigned char
#define INT16S signed short
#define INT16U unsigned short
韶
关
学
4.设计程序。在“流水灯.c”文件的编辑区里,输入程序。完整的程序见附录。 5.设置十六进制代码输出。鼠标放到左边的项目管理区 Project Workspace 下的 Target1,
院 点击右键,如图 10 所示,选择 Options for Target ‘Target 1’。如图 11 所示,选择 output,将 Create Hex File 选中。
院 寄存器选择。1:选择资料寄存器,0:选择指令寄存器
读写选择。1:读;0:写
使能选择。1:LCD 可读写。0:LCD 不可读写 数据端口的第 0 位 数据端口的第 1 位 数据端口的第 2 位 数据端口的第 3 位 数据端口的第 4 位 数据端口的第 5 位 数据端口的第 6 位 数据端口的第 7 位 背光电源正极,5V±5% 背光电源负极,0V
指令 4:显示开关控制。 D:控制整体显示的开与关,高电平表示开显示,低电平表示关显
示 C:控制光标的开与关,高电平表示有光标,低电平表示无光标 B:控制光标是否闪烁,
高电平闪烁,低电平不闪烁。
指令 5:光标或显示移位 S/C:高电平时移动显示的文字,低电平时移动光标。R/L,高向
左,低向右。
指令 6:功能设置命令 DL:高电平时为 4 位总线,低电平时为 8 位总线。 N:低电平时为
计数器地址
10 写数据到指令 7.8 所设地址 1 0
要写的数据
11 从指令 7.8 所设的地址读数据 1 1
读出的数据
指令 1:清显示,光标复位到地址 00H位置。指令 2:光标复位,光标返回到地址 00H。
指令 3:光标和显示模式设置 I/D:光标移动方向,高电平右移,低电平左移,S:屏幕上所
有文字是否左移或者右移。高电平表示有效,低电平则无效。
韶 YM1602 可显示 2 行的字符,每一行显示 16 个字符,整个屏幕可显示 32 个字符。屏
幕上每个显示位置都有地址。地址的安排如下表 1 所示,第一行为 80H-8FH,第二行为 C0H -CFH。要在液晶屏的某个位置上显示某个数码,必须先给液晶屏写入要显示的地址,再 写入显示内容的 ASCII 码数据。
韶
关
四.预习内容:寄存器 PINSELx,IOxPIN,IOxSET,IOxDIR,IOxCLR。P172-188
五.实验步骤
学 1. 在电脑硬盘上专门建立一个文件夹,如“流水灯”,用来存 放设计程序。 2. 打开 Keil Uv3 软件,建立工程文件“流水灯.uV2”。
(1) 点击菜单 Project/u Vision Project…,如图 3 所示。
} } }
韶 关 学 院
韶关学院电子系-- HYQ
《 嵌入式系统实验讲义》 实验二 液晶屏实验
实验二 液晶屏实验
一.实验目的 1. 掌握掌握 LPC2000 系列 ARM7 芯片与 LCD 的接口技术 2. 了解液晶显示模块的工作原理,掌握液晶的软件驱动程序设计
二.实验器材 PC 机,Keill uV3 和 Protues7.5 软件
学 时候,速度相对比其他模式快,但能用眼睛看到灯光往下流动。
七.注意事项 为提高实验的效果,到实验室做实验之前,各位同学必须先预习,写好预习报告,并且
要求先编译好程序,做好仿真电路图,用 u 盘带到实验室来给老师看效果。在实验室的时间
院 主要是修改程序,检查效果,讨论问题。
பைடு நூலகம்
//附录:流水灯.c
韶关学院电子系-- HYQ
三.实验任务 编写液晶屏 YM1602 的驱动程序,在液晶屏上显示英文字母、数字和标点符号。
四.实验原理 1.YM1602 概述
液晶屏 YM1602 是一种非常易用的字符型 LCD,可显示 ASCII 码对应的内容,如大小 写英文字母,0-9 的数字,标点符号等等。大写字母 A~Z 对应的 ASCII 编码为 41H~5AH, 小写字母 a~z 对应的 ASCII 码的编码为 61~7AH,数字 0~9 对应的编码为 30H~39H。
单行显示,高电平时双行显示。 F: 低电平时显示 5x7 的点阵字符,高电平时显示 5x10 的
《嵌入式系统原理》实验讲义
作者:洪远泉
韶 关 学 院
韶关学院电子系
《嵌入式系统原理实验讲义》实验一 GPIO 输出控制实验
实验一 GPIO 输出控制实验 一.实验目的
1. 熟悉 LPC2000 系列 ARM7 微控制器的 GPIO 的输出控制 2. 掌握 Keil uV3 和 Protues 软件的应用 3. 掌握 ARM7 的 C 语言编程方法 二.实验设备:PC 机,Keill uV3 和 Protues7.5 软件 三.实验任务 将 LPC2214 芯片的 P0.0-P0.9 口连接到发光二极管光 D1-D10 中,在 Keil uV3 平台下用 C 语言编程,实现流水灯的控制。流水灯点亮的状态如图 2 所示。
/**********************/
学 void LEDDATA(INT16U x)
{ IO0CLR=LedBus;//先将 LED 端口全部清零
IO0SET=x;
} /**********************/ int main(void) {
院
INT16U i=0,j;
GPIO_INIT();
/***********************/ //GPIO 初始化函数,P0.0-P0.9 设置为输出 IO 口
void GPIO_INIT(void)
关 { PINSEL0&=0xfff00000;//P0.0-P0.9 设为 IO 口,其他引脚的功能保持不变 IO0DIR|=0x000003ff;//P0.0-P0.9 设为输出口,其他引脚的方向保持不变 }
