ip address and subnetting for new users - 015-DM
锐捷交换机实验手册

锐捷交换机实验手册四川华迪信息技术有限公司baby lai交换机配置新手篇:正确连接和初级配置第一步:利用电脑超级终端与交换机建立连接可进行网络管理的交换机上有一个“Console”端口,它是专门用于对交换机进行配置和管理的。
可以通过Console端口连接和配置交换机。
用Cisco自带的Console线,RJ-45端接入Cisco交换机Console口,Com口端接入电脑Com1或Com2口,必须注意的是要记清楚接入的是那个Com口。
按照步骤开启超级终端:开始-程序-附件-通讯-超级终端(图2)点击文件-新建连接(图3)输入超级终端名称,选择数据线所连端口(注意选择Com口时候要对应Console线接入电脑的Com口):图4确定-点击还原为默认值(图5)确定后开启交换机此时交换机开始载入IOS,可以从载入IOS界面上看到诸如IOS版本号,交换机型号,内存大小等数据当屏幕显示Press RETURN to get started的时候按回车就能直接进入交换机。
第二步:学习交换机的一些初级命令首先我们要知道Cisco配置界面分两种,一种是基于CLI(Command-line Interface命令行界面),一种是基于IOS(Internetwork Operting System互联网操作系统)。
暂时我们先探讨基于IOS的Cisco交换机。
基于IOS的交换机有三种模式,“>”用户模式,“#”特权模式,“(CONFIG)#”全局模式,在用户模式输入enable进入特权模式,在特权模式下输入disable回到用户模式,在特权模式下输入configure terminal进入全局模式。
在特权模式下输入disable回到特权模式下。
刚进入交换机的时候,我们处于用户模式,如:switch>。
在用户模式我们可以查询交换机配置以及一些简单测试命令。
在用户模式输入?号可以查询可以运行的命令。
出现命令过多不能全部显示可以用Enter键逐行显示,空格键整页翻动。
IP地址、子网掩码和域名知识

很明显,这些数字对于人来说不太好记忆。人们为了方便记忆,就将组成计算机的IP地址的32位二进制分成四段,每段8位,中间用小数点隔开,然后将每八位二进制转换成十进制数,这样上述计算机的IP地址就变成了:210.73.140.2。
二、IP地址的分类
*有限广播
前面提到的广播地址包含一个有效的网络号和主机号,技术上称为直接广播(directed boradcasting)地址。在网间网上的任何一点均可向其他任何网络进行直接广播,但直接广播有一个缺点,就是要知道信宿网络的网络号。
有时需要在本网络内部广播,但又不知道本网络网络号。TCP/IP规定,32比特全为"1"的网间网地址用于本网广播,该地址叫做有限广播地址(limited broadcast address)。
三、IP的寻址规则
1、网络寻址规则
A、网络地址必须唯一。
B、网络标识不能以数字127开头。在A类地址中,数字127保留给内部回送函数。
C、网络标识的第一个字节不能为255。数字255作为广播地址。
D、网络标识的第一个字节不能为"0","0"表示该地址是本地主机,不能传送。
2、主机寻址规则
A、主机标识在同一网络内必须是唯一的。
因此,迫切需要寻求新的技术,以应付网间网规模增长带来的问题。仔细分析发现,网间网规模的增长在内部主要表现为网络地址的增减,因此解决问题的思路集中在:如何减少网络地址。于是IP网络地址的多重复用技术应运而生。通过复用技术,使若干物理网络共享同一IP网络地址,无疑将减少网络地址数。
子网编址(subnet addressing)技术,又叫子网寻径(subnet routing),英文简称subnetting,是最广泛使用的IP网络地址复用方式,目前已经标准化,并成为IP地址模式的一部分。
如何设置局域网的IP地址和子网掩码

如何设置局域网的IP地址和子网掩码一、局域网的IP地址和子网掩码的概念和作用在探索如何设置局域网的IP地址和子网掩码之前,我们需要先了解局域网、IP地址和子网掩码的概念和作用。
1. 局域网(Local Area Network,LAN):局域网是指在一个相对较小的范围内,例如办公室、学校或家庭中的一组计算机和网络设备互相连接并共享资源的计算机网络。
它可以用于实现内部办公、文件共享、打印等功能。
2. IP地址(Internet Protocol Address):IP地址是计算机在互联网上的唯一标识,用于确定计算机之间的通信。
它由32位(IPv4)或128位(IPv6)二进制数组成,通常以点分十进制表示(例如192.168.0.1)。
在局域网中,每台计算机都需要有一个独立的IP地址,以便在局域网内进行通信。
IP地址由网络部分和主机部分组成,其中网络部分用于区分不同的网络,主机部分用于标识局域网中的具体计算机。
3. 子网掩码(Subnet Mask):子网掩码用于确定IP地址中哪部分是网络部分,哪部分是主机部分。
它和IP地址一起使用,用于在局域网中进行IP地址的分类和划分。
子网掩码也是32位(IPv4)或128位(IPv6)二进制数,通常与IP地址以同样的格式表示(例如255.255.255.0)。
子网掩码通过与IP地址进行逻辑与运算,可以将IP地址划分为网络地址和主机地址两部分,以便于路由器在局域网中正确转发数据包。
二、设置局域网的IP地址和子网掩码的步骤接下来,我们将介绍如何设置局域网的IP地址和子网掩码的步骤。
1. 确定网络需求和规划:在设置IP地址和子网掩码之前,我们需要先确定局域网的具体需求和规划。
例如,确定局域网所使用的IP地址范围、需要分配给每台计算机的IP地址数量等。
2. 登录网络设备管理界面:在设置IP地址和子网掩码之前,我们需要登录到网络设备的管理界面。
这通常需要使用路由器的登录用户名和密码。
网络IP地址的自动化配置技术

网络IP地址的自动化配置技术自动化配置网络IP地址是指通过使用特定的技术和协议,使计算机或其他网络设备能够自动获得可用的IP地址,并完成与网络的连接。
这项技术的发展和应用,大大简化了网络管理和配置的过程,提高了网络的灵活性和可扩展性。
本文将介绍几种常见的网络IP地址自动化配置技术。
一、动态主机配置协议(Dynamic Host Configuration Protocol,简称DHCP)DHCP是一种广泛使用的网络协议,用于分配和管理网络中计算机的IP地址、子网掩码、默认网关等网络配置信息。
通过DHCP服务器和客户端之间的通信,可以实现自动分配和更新IP地址的过程,极大地简化了网络管理员的工作。
DHCP客户端在启动时会发送DHCP请求,DHCP服务器则会回应并提供可用的IP地址。
这种方式可以有效避免IP地址冲突,使得网络设备能够快速地获得合适的IP地址,而无需手动配置。
二、零配置网络(Zeroconf)零配置网络也被称为“即插即用”网络,旨在使设备在无需网络管理员干预的情况下,能够自动发现、配置和连接到一个局域网或互联网。
零配置网络的核心技术是当设备加入网络时自动分配和配置IP地址。
比较常见的零配置网络技术有:1. 自动私有IP寻址(Automatic Private IP Addressing,简称APIPA):设备在未获取有效IP地址的情况下,会自动分配一个私有IP地址,例如在IPv4网络中的169.254.x.x网段。
这使设备能够在没有DHCP服务器的情况下进行通信。
2. 子网划分(Subnetting):在IPv6网络中,使用子网划分技术可以自动为设备分配唯一的IP地址,以适应网络拓扑结构的变化。
三、移动IP(Mobile IP)移动IP是一种网络协议,用于实现移动设备在不同网络之间切换时仍能保持连接不中断的功能。
该协议允许设备在切换网络时保持原有的IP地址,不会因网络切换而需要重新获取IP地址。
网络ip地址及子网划分(NetworkIPaddressandsubnetDivision)

网络ip地址及子网划分(Network IP address and subnet Division)International rules: divide all IP addresses into A, B, C, D, E.Class a address: range 0~127, 0 is reserved and represents all IP addresses, and 127 is reserved address, and is used for testing loopback. Thus, the range of class a addresses is actually between 1~126. Such as: 10.0.0.1, the first paragraph number is the network number, and the remaining three paragraph number is the number of the local computer. Converted to 2, a class a IP address consists of 1 bytes of network address and 3 bytes of host address. The highest address of the network address must be "0", and the address ranges from 0.0.0.1 to 126.0.0.0. The available class a network has 126, each network capable of hosting more than 100 million hosts (2 of the 24 party hosts). Using subnet masks to make a distinction: 255.0.0.0.Class B address: ranges from 128-191, such as 172.168.1.1, the first and second segment numbers to network numbers, and the remaining 2 segment numbers are the numbers of the local computers. 2 hexadecimal conversion, consisting of a B class IP address by 2 bytes 2 bytes of the network address and the host address, the highest network address must be "10", the address range from 128.0.0.0 to 191.255.255.255. The available B class network has 16382, each network can accommodate more than 60 thousand hosts. Using subnet masks to make a distinction: 255.255.0.0.Class C address: ranges from 192-223, such as 192.168.1.1, first, second, and third. The number is the network number, and the last remaining number is the number of the local computer.Converted to 2, a C class IP address consists of 3 bytes of network address and 1 bytes of host address. The highest point of the network address must be "110"". Range from 192.0.0.0 to 223.255.255.255. C class network can reach more than 209, each network can accommodate 254 hosts. Using subnet masks to make a distinction: 255.255.255.0.Class D address: ranges from 224-239, class IP, D address, the first byte starts with '1110', and it is a reserved address. It does not point to specific networks, and this class of addresses is currently used in multicast (Multicast). A multicast address used to address a set of computers at a time that identifies a set of computers that share the same protocol.Class E address: ranges from 240-254 to 11110, reserved for future use. All zero ("0.0.0.0") addresses correspond to the current host. The full 1 IP address ("255.255.255.255") is the broadcast address of the current subnet.In the daily network environment, basically all use B, C two kinds of address, and ADE these 3 kinds of addresses are not playing, may be used.From the above description, you can see a lot of friends will make mistakes, is the beginning of the 192 set IP address B address, although the network communication in the LAN is not affected, but in fact is a division of behavior is not standardized.Brief description: subnet mask subnet mask is a 32 bit address, to shield a portion of the IP address to distinguish networkID and host identity, and that the IP address is in the LAN, or in remote online.With the above IP address as an example to illustrate, such as a C class, IP address 192.168.0.1, subnet mask for255.255.255.0 (conversion 2 hexadecimal, 255 in 2 hexadecimal, said 8 1, that is, all accounted for). The wording says that the network address of this C class IP address is 192.168.0, and the host address is 1.In so many network IP, the international regulation has a part of IP address is used for our local area network, that is, private network IP, not used in public network, their scope is:10.0.0.0 to 10.255.255.255172.16.0.0 to 172.31.255.255192.168.0.0 to 192.168.255.255Next, let's discuss the problem of network partitioning at once.If you give a C class of IP address segment:192.168.0.1-192.168.0.254, where 192.168.0 this belongs to the network number, and 1~254 indicates that the network segment can accommodate up to 254 mainframe computers. All we have to do now is to divide the 254 hosts again and distinguish them.The 192.168.0.1-192.168.0.254 default subnet mask used for 255.255.255.0, 0 of them in the 2 band said in 8, 0. so the 8position is not to occupy the network number, 8 times 2 is said to have 256 address, remove a header (network address) and a tail (host address), said there are 254 computer hosts, so we want to divide these 254 words, is to occupy the last 8 0 in a few.If the first 0. is occupied, then the subnet mask represented by the 2 hexadecimal is 11111111.11111111.11111111.10000000. Converting to 10 decimal is 255.255.255.128, so how much should the computer host be then? Is actually very simple, is the 7 of 2 (the original 2 is no longer the 8 times square), 7 =128 2, so if the subnet mask is 255.255.255.128, the class C address can be divided into 2 networks, each network has a maximum of 128 hosts. 192.168.0.1-192.168.0.127 is one, and192.168.0.128-192.168.0.255 is second.For example, if the IP or C address range is192.168.0.1-192.168.0.254, if the 255.255.255.192 subnet mask (which is the last 8 for the host, occupied 2, 2 hexadecimal 11111111.11111111.11111111.11000000), then the number of host computer that segment is 2 ^ 6 =64 Taiwan, a total of 2. 2 Party =4 segment. The first segment is 192.168.0.1-192.168.0.63, the second segment is 192.168.0.64-192.168.0.127, the third segment is 192.168.0.127-192.168.0.191, and the fourth segment is 192.168.0.192-192.168.0.254.From these 2 examples, we can sum up a rule, that is, the host is occupied by N digits, then there are 2 N sub networks, and there are 2 8-N times the number of hosts.Finally, a brief description of the B class address subnetdivision method. If you have a B class address segment and the 172.16.0.0-172.168.255.255 subnet mask is 255.255.0.0, you now need to segment this segment into subnets. Without dividing the subnet, there is only one network, which contains 2 of the 16 sides and more than 60 thousand hosts. Therefore, if you need to subnetting, network address host address needs to borrow.A caseThe first step is to convert 172.16.0.0 255.255.0.0 to binary, 1010110000010000, 00000000, 00000000128+32+8+4=172, 161111111111111111, 00000000, 00000000255.255.0.0.If the network address host address asked to borrow 2 bit words, then, the subnet mask is: 111111111111111100000000255.255.192.0 11000000, because by 2, there are 2 times of 2, is divided into 4 networks, each network had 14 times the 2 host addresses.172.16.0.1-172.16.63.254172.16.64.1-172.16.127.254172.16.128.1-172.16.191.254172.16.192.1-172.16.254.254In two casesIf the B class address 172.16.0.0-172.16.255.255 255.255.0.0 needs to be divided into smaller subnets, the network addressborrows a total of 10 digits from the host address,Decimal 172.16.0.0 255.255.0.0Binary 1010110000010000, 0000000000000000, 128+32+8+4=172 161111111111111111, 0000000000000000After borrowing 10 digits, the subnet mask in binary is: 11111111.11111111.11111111.11000000. In decimal notation, that's 255.255.255.192. Well, there are 2 of the 10 square networks in total, and 2 of the 6 addresses in each network. Using decimal to represent so many addresses, should be as follows (because there are 2 of the 10 party, too many, can not write one by one).6 in front:172.16.0.1-172.16.0.63172.16.0.64-172.16.0.127172.16.0.128-172.16.0.191172.16.0.192-172.16.0.254172.16.1.1---172.16.1.63172.16.1.64-172.16.1.127The last 6:172.16.254.128-172.16.254.191172.16.254.192-172.16.254.255172.16.255.1-172.16.255.63172.16.255.64-172.16.255.127One hundred and seventy-two16.255.128-172.16.255.191172.16.255.192-172.16.255.255从这2个例子中可以看出,划分B类子网地址,其实和划分C类子网地址是一样的,只不过划分C类的时候,是将第四段地址划分,而划分B类的时候,可以划分第三段,也可以划分第四段。
江西电信BRAS(华为ME60、MA5200G)配置规范

3.2.2.1 GE 用做上连接口....................................................... 23 3.2.2.2 GE 用做下联接口....................................................... 23 3.2.2.3 GE 拨号下联子接口(dot1Q) .............................................. 24 3.2.2.4 GE 拨号下联子接口(QinQ) ............................................... 24 3.2.2.5 GE 专线下联子接口..................................................... 25 3.2.2.6 接口 uRPF ............................................................ 26 3.2.2.7 hold-time 配置 ......................................................... 26 3.2.2.8 配置范例 ............................................................. 27 3.3 MULTI-VR(CONTEXT)配置 ......................................................................................................... 28
IP地址与网络上的其他系统有冲突解决方案

IP地址与网络上的其他系统有冲突怎么办?1.IP地址与网络上的其它系统有冲突. 设置成为由DHCP自动获取出现您所描述的错误提示,应该是网卡所设置的IP地址与网络上的另外一台电脑,或者其他网络设备的IP地址发生冲突,所谓冲突也就是使用了相同的地址,错误提示中的00:20:ED:9E:55:B6就是另外那台电脑或者网络设备的MAC地址。
如果您的电脑在一个局域网内,并且网卡IP地址是通过局域网的服务器自动分配的,在Windows 2000等操作系统上,可以单击“开始”按钮,选择“附件”中的“命令提示符”,在命令行状态下输入“ipconfig /renew”,让系统释放当前的IP地址,重新获得一个新的地址。
在Windows 98中,则可以单击“开始”按钮,选择“运行”,键入“winipcfg”,并在出现的对话框上选择释放当前IP,然后重新获取一个。
若您的IP地址是设置为固定IP地址的,如果是您自己设置的,可以另外设置一个,如果是由管理员分配的,那么您需要联系管理员,报告IP地址冲突的问题,要求更换IP地址或找出产生冲突的电脑进行修正。
如果您在单机情况下使用电脑,那么您需要检查自己所使用的设备中哪一个设备是冲突的原因,例如ADSL调制解调器的IP地址是否与您的网卡IP地址相同等。
IP地址在每个网络中只能是唯一的,如果重复了则发生IP冲突,就无法正常连入网络了。
你可以手动进行修改,步骤如下:在windowsXP或windows2000中:单击开始--设置--网络和拨号连接,在出现的网络和拨号连接窗口中右键单击“本地连接”,在出现的快捷菜单里选择“属性”命令,出现“本地连接”属性对话框,在“常规”选项卡中,中间的“此连接使且下列组件”列表框,选中“Internet协议(TCP/IP)”单击“属性”按钮,在出现的“Internet协议(TCP/IP)属性”对话框中选择“常规”选项卡中的“使用下列IP地址”单选按钮,然后就可以在下面的文本框中填写需要的IP地址,子网埯码及默认网关了。
IP地址的子网划分和子网掩码

IP地址的子网划分和子网掩码IP地址是互联网中常用的网络协议,用于标识网络上的设备。
网络管理员需要将IP地址分配给各个设备,以实现网络通信。
在这个过程中,子网划分和子网掩码扮演着重要的角色。
本文将详细介绍IP地址的子网划分和子网掩码的概念、原理及应用。
一、IP地址的基本概念IP地址(Internet Protocol Address)是一个用于标识通信节点或者主机地址的数值,由32位二进制数组成。
为了方便人们使用,IP地址通常被表示为四组用点分隔的十进制数(例如192.168.0.1)。
二、子网划分的概念与原理子网划分(Subnetting)是指将一个大的IP地址空间划分成若干个较小的子网,以便更有效地管理和利用IP地址。
通过子网划分,可以将网络划分成不同的子网,每个子网可以包含一定数量的IP地址。
子网划分的原理基于IP地址的二进制表示。
在IPv4中,32位的IP地址被分为网络部分和主机部分,其中网络部分用于标识网络,主机部分用于标识设备。
子网掩码则决定了IP地址中哪些位属于网络部分,哪些位属于主机部分。
三、子网掩码的概念与作用子网掩码(Subnet Mask)是一个32位的二进制数,用于将IP地址中的网络部分和主机部分进行分隔。
在二进制表示中,子网掩码中的1表示网络部分,0表示主机部分。
子网掩码的作用是定义了网络地址的范围,以及主机地址在网络中的唯一性。
通过与IP地址进行AND运算,可以判断一个IP地址属于哪一个子网。
四、子网划分和子网掩码的应用子网划分和子网掩码在网络管理和划分中发挥着重要的作用。
通过合理地划分子网,可以提高网络的安全性、管理性和性能。
在实际应用中,通过合理地选择子网掩码,网络管理员可以根据需求将IP地址按照不同的规模分配给各个子网。
例如,一个较大的网络可以划分成多个子网,不同的子网可以服务于不同的部门或者地区。
此外,子网划分和子网掩码还可以用于实现网络隔离和VLAN的划分。
什么是IP地址

什么是IP地址IP地址称作网络协议地址,是分配给主机的一个32位地址,由4个字节组成,分为动态IP地址和静态IP地址两种。
接下来小编为大家整理了什么是IP地址,希望对你有帮助哦!IP地址(Internet Protocol Address)是一种在Internet上的给主机编址的方式,也称为网际协议地址。
由32位二进制数组成,为便于使用,常以XXX.XXX.XXX.XXX形式表现,每组XXX代表小于等于255的10进制数。
例如202.96.155.9。
Internet中,IP地址是唯一的。
目前IP技术可能使用的IP地址最多可有约42亿个。
骤看可能觉得很难会用尽,但由于早期编码上的问题,使很多编码实际上被丢空或不能使用。
加上因特网的普及,使每个家庭都至少有一部电脑,连同公司的电脑,以及连接每个网络的服务器,长此下去,专家担心随着Internet的发展,将不够用。
所以相应的科研组织正在研究128位的IP地址,其IP地址数量最高可达3.402823669 × 1038 个,地球上的每一粒沙子都可以拥有自己的IP地址,这种新版的IP地址技术叫IPv6。
An IP address (Internet Protocol address) is a unique number that devices use in order to identify and communicate with each other on a network utilizing the Internet Protocol standard. Any participating device —including routers, computers, time-servers, internet FAX machines, and some telephones —must have its own unique address. This allows information passed onwards on behalf of the sender to indicate where to send it next, and for the receiver of the information to know that it is the intended destination.The numbers currently used in IP addresses range from 1.0.0.0 to 255.255.255.255, though some of these values are reserved for specific purposes. This does not provide enough possibilities for every internet device to have its own permanentnumber. Subnet routing, Network Address Translation and the Dynamic Host Configuration Protocol (DHCP) server all allow local networks to use the same IP addresses as other networks elsewhere though both are connected to the Internet. Devices such as network printers, web servers and email servers are often allocated static IP addresses so they can always be found.IP addresses are conceptually similar to phone numbers, except they are used in LANs (Local Area Network), WANs (Wide Area Network), or the Internet. Because the numbers are not easy for humans to remember, the Domain Name System provides a service analogous to an address book lookup called "domain name resolution" or "name resolution". Special DNS servers on the internet are dedicated to performing the translation from a domain name to an IP address and vice versa.More detailThe Internet Protocol (IP) knows each logical host interface by a number, the IP address. On any given network, this number must be unique among all the host interfaces that communicate through this network. Users of the Internet are sometimes given a host name in addition to their numerical IP address by their Internet service provider.The IP addresses of users browsing the World Wide Web are used to enable communications with the server of the Web site. Also, it is usually in the header of email messages one sends. In fact, for all programs that utilize the TCP/IP protocol, the sender IP address and destination IP address are required in order to establish communications and send data.Depending on one's Internet connection the IP address can be the same every time one connects (called a static IP address), or different every time one connects, (called a dynamic IPaddress). In order to use a dynamic IP address, there must exist a server which can provide the address. IP addresses are usually given out through a server service called DHCP or the Dynamic Host Configuration Protocol. If a static address is used, it must be manually programmed into parameters of the device's network interface.Internet addresses are needed not only for unique enumeration of hosted interfaces, but also for routing purposes, therefore a high fraction of them are always unused or reserved.The unique nature of IP addresses makes it possible in many situations to track which computer — and by extension, which person — has sent a message or engaged in some other activity on the Internet. This information has been used by law enforcement authorities to identify criminal suspects; however dynamically-assigned IP addresses can make this difficult.IP version 4AddressingIn version 4 of the Internet protocol (IPv4), the current standard protocol for the Internet, IP addresses consist of 32 bits, which makes for 4,294,967,296 (over 4 billion) unique host interface addresses in theory. If all of these were used, that would be around one IP address per 21.3 square meters, or 70 square feet, of land. In practice, because addresses are allocated in blocks, many unused addresses are unavailable (much like unused phone numbers in a sparsely-populated area code), so that there is some pressure to extend the address range via IP version 6 (see below).IPv4 addresses are commonly expressed as a dotted quad, four octets (8 bits) separated by periods. The host known as currently has the number 3482223596,written as 207.142.131.236 in base-256: 3482223596 equals 207×2563 142×2562 131×2561 236×2560. (Resolving the name to its associated number is handled by Domain Name System servers.)IPv4 addresses were originally divided into two parts: the network and the host. A later change increased that to three parts: the network, the subnetwork, and the host, in that order. However, with the advent of classless inter-domain routing (CIDR), this distinction is no longer meaningful, and the address can have an arbitrary number of levels of hierarchy. (Technically, this was already true any time after the advent of subnets, since a site could elect to have more than one level of subnetting inside a network number.)AssignmentEach interface of a device is assigned, at least theoretically, a unique IP address. In practice, some interfaces may be unnumbered, and many addresses are not globally unique.The actual assignment of an address is not arbitrary. The fundamental principle of routing, that addresses encode information about a device's location within a network, implies that an address assigned to one part of a network will not function in another part of the network. A hierarchical structure, standardized by CIDR and overseen by the Internet Assigned Numbers Authority (IANA) and its Regional Internet Registries (RIRs), manages the assignment of Internet address worldwide. Each RIR maintains a publically searchable WHOIS database that provides information about IP address assignments; information from these databases plays a central role in numerous tools which attempt to locate IP addresses geographically.ExhaustionSome private IP address space has been allocated via RFC 1918. This means the addresses are available for any use by anyone and therefore the same RFC 1918 IP addresses can be reused. However they are not routable on the Internet. They are used extensively due to the shortage of registerable addresses. Network address translation (NAT) is required to connect those networks to the Internet.While a number of measures have been taken to conserve the limited existing IPv4 address space (such as the use of NAT and Private Addressing), the number of 32-bit IP addresses is not sufficient to accommodate the long-term growth of the Internet. For this reason, the plan is that the Internet 128-bit IPv6 addressing scheme will be adopted over the next 5 to 15 years.IP version 5What would be considered IPv5 existed only as an experimental non-IP real time streaming protocol called ST2, described in RFC 1819. In keeping with standard UNIX release conventions, all odd-numbered versions are considered experimental, and this version was never intended to be implemented; the protocol was not abandoned. RSVP has replaced it to some degree.IP version 6In IPv6, the new (but not yet widely deployed) standard protocol for the Internet, addresses are 128 bits wide, which, even with generous assignment of netblocks, should suffice for the foreseeable future. In theory, there would be exactly 2128, or about 3.403 × 1038 unique host interface addresses. If the earth were made entirely out of 1 cubic millimeter grains of sand, then you could give a unique address to each grain in 300 million planets the size of the earth. This large address space will besparsely populated, which makes it possible to again encode more routing information into the addresses themselves.AddressingA version 6 address is written as eight 4-digit hexadecimal numbers separated by colons. For readability, addresses may be shortened in two ways. Within each colon-delimited section, leading zeroes may be truncated. Secondly, one string of zeroes (and only one) may be replaced with two colons (::). For example, all of the following addresses are equivalent:1080:0000:0000:0000:0000:0034:0000:417A1080:0:0:0:0:34:0:417A1080::34:0:417AGlobal unicast IPv6 addresses are constructed as two parts: a 64-bit routing part followed by a 64-bit host identifier.Netblocks are specified as in the modern alternative for IPv4: network number, followed by a slash, and the number of relevant bits of the network number (in decimal). Example: 12AB::CD30:0:0:0:0/60 includes all addresses starting with 12AB00000000CD3.IPv6 has many improvements over IPv4 other than just bigger address space, including autorenumbering and mandatory support for IPsec.。
通信外文翻译---了解 TCPIP 寻址和子网配置基础知识

Understanding TCPIP addressing and subnetting basics ⏹INTRODUCTIONWhen you configure the TCP/IP protocol on a Microsoft Windows computer, an IP address, subnet mask, and usually a default gateway are required in the TCP/IP configuration settings.To configure TCP/IP correctly, it is necessary to understand how TCP/IP networks are addressed and divided into networks and subnetworks. This article is intended as a general introduction to the concepts of IP networks and subnetting. A glossary is included at the end of article.Back to the top⏹MORE INFORMATIONThe success of TCP/IP as the network protocol of the Internet is largely because of its ability to connect together networks of different sizes and systems of different types. These networks are arbitrarily defined into three main classes (along with a few others) that have predefined sizes, each of which can be divided into smaller subnetworks by system administrators. A subnet mask is used to divide an IP address into two parts. One part identifies the host (computer), the other part identifies the network to which it belongs. To better understand how IP addresses and subnet masks work, look at an IP (Internet Protocol) address and see how it is organized.Back to the top●IP addresses: Networks and hostsAn IP address is a 32-bit number that uniquely identifies a host (computer or other device, such as a printer or router) on a TCP/IP network.IP addresses are normally expressed in dotted-decimal format, with four numbers separated by periods, such as 192.168.123.132. To understand how subnet masks are used to distinguish between hosts, networks, and subnetworks, examine an IP address in binary notation.For example, the dotted-decimal IP address 192.168.123.132 is (in binary notation) the 32 bit number 110000000101000111101110000100. This number may be hard to make sense of, so divide it into four parts of eight binary digits.These eight bit sections are known as octets. The example IP address, then, becomes 11000000.10101000.01111011.10000100. This number only makes a little more sense, so for most uses, convert the binary address into dotted-decimal format (192.168.123.132). The decimal numbers separated by periods are the octets converted from binary to decimal notation.For a TCP/IP wide area network (WAN) to work efficiently as a collection of networks, the routers that pass packets of data between networks do not know the exact location of a host for which a packet of information is destined. Routers only know what network the host is a member of and use information stored in their route table to determine how to get the packet to the destination host's network. After the packet is delivered to the destination's network, the packet is delivered to the appropriate host.For this process to work, an IP address has two parts. The first part of an IP address is used as a network address, the last part as a host address. If you take the example 192.168.123.132 and divide it into these two parts you get the following: 192.168.123. Network.132 Host-or-192.168.123.0 - network address.0.0.0.132 - host address.Back to the top●Subnet maskThe second item, which is required for TCP/IP to work, is the subnet mask. The subnet mask is used by the TCP/IP protocol to determine whether a host is on the local subnet or on a remote network.In TCP/IP, the parts of the IP address that are used as the network and host addresses are not fixed, so the network and host addresses above cannot be determined unless you have more information. This information is supplied in another 32-bit number called a subnet mask. In this example, the subnet mask is 255.255.255.0. It is not obvious what this number means unless you know that 255 in binary notation equals 11111111; so, the subnet mask is:11111111.11111111.11111111.0000000Lining up the IP address and the subnet mask together, the network and host portions of the address can be separated:11000000.10101000.01111011.10000100 -- IP address (192.168.123.132)11111111.11111111.11111111.00000000 -- Subnet mask (255.255.255.0)The first 24 bits (the number of ones in the subnet mask) are identified as the network address, with the last 8 bits (the number of remaining zeros in the subnet mask) identified as the host address. This gives you the following:11000000.10101000.01111011.00000000 -- Network address (192.168.123.0) 00000000.00000000.00000000.10000100 -- Host address (000.000.000.132)So now you know, for this example using a 255.255.255.0 subnet mask, that the network ID is 192.168.123.0, and the host address is 0.0.0.132. When a packet arrives on the 192.168.123.0 subnet (from the local subnet or a remote network), and it has a destination address of 192.168.123.132, your computer will receive it from the network and process it.Almost all decimal subnet masks convert to binary numbers that are all ones on the left and all zeros on the right. Some other common subnet masks are: Decimal Binary255.255.255.192 1111111.11111111.1111111.11000000255.255.255.224 1111111.11111111.1111111.11100000Internet RFC 1878 (available from ) describes the valid subnets and subnet masks that can be used on TCP/IP networks.Back to the top●Network classesInternet addresses are allocated by the InterNIC ( ), theorganization that administers the Internet. These IP addresses are divided into classes. The most common of these are classes A, B, and C. Classes D and E exist, but are not generally used by end users. Each of the address classes has a different default subnet mask. You can identify the class of an IP address by looking at its first octet. Following are the ranges of Class A, B, and C Internet addresses, each with an example address:Class A networks use a default subnet mask of 255.0.0.0 and have 0-127 as their first octet. The address 10.52.36.11 is a class A address. Its first octet is 10, which is between 1 and 126, inclusive.Class B networks use a default subnet mask of 255.255.0.0 and have 128-191 as their first octet. The address 172.16.52.63 is a class B address. Its first octet is 172, which is between 128 and 191, inclusive.Class C networks use a default subnet mask of 255.255.255.0 and have 192-223 as their first octet. The address 192.168.123.132 is a class C address. Its first octet is 192, which is between 192 and 223, inclusive.In some scenarios, the default subnet mask values do not fit the needs of the organization, because of the physical topology of the network, or because the numbers of networks (or hosts) do not fit within the default subnet mask restrictions. The next section explains how networks can be divided using subnet masks.Back to the topSubnettingA Class A, B, or C TCP/IP network can be further divided, or subnetted, by a system administrator. This becomes necessary as you reconcile the logical address scheme of the Internet (the abstract world of IP addresses and subnets) with the physical networks in use by the real world.A system administrator who is allocated a block of IP addresses may be administering networks that are not organized in a way that easily fits these addresses. For example, you have a wide area network with 150 hosts on three networks (in different cities) that are connected by a TCP/IP router. Each of these three networks has 50 hosts. You are allocated the class C network 192.168.123.0. (For illustration, this address is actually from a range that is not allocated on the Internet.) This means that you can use the addresses 192.168.123.1 to 192.168.123.254 for your 150 hosts.Two addresses that cannot be used in your example are 192.168.123.0 and 192.168.123.255 because binary addresses with a host portion of all ones and all zeros are invalid. The zero address is invalid because it is used to specify a network without specifying a host. The 255 address (in binary notation, a host address of all ones) is used to broadcast a message to every host on a network. Just remember that the first and last address in any network or subnet cannot be assigned to any individual host.You should now be able to give IP addresses to 254 hosts. This works fine if all 150 computers are on a single network. However, your 150 computers are on three separate physical networks. Instead of requesting more address blocks for each network, you divide your network into subnets that enable you to use one block of addresses on multiple physical networks.In this case, you divide your network into four subnets by using a subnet maskthat makes the network address larger and the possible range of host addresses smaller. In other words, you are 'borrowing' some of the bits usually used for the host address, and using them for the network portion of the address. The subnet mask 255.255.255.192 gives you four networks of 62 hosts each. This works because in binary notation, 255.255.255.192 is the same as 1111111.11111111.1111111.11000000. The first two digits of the last octet become network addresses, so you get the additional networks 00000000 (0), 01000000 (64), 10000000 (128) and 11000000 (192). (Some administrators will only use two of the subnetworks using 255.255.255.192 as a subnet mask. For more information on this topic, see RFC 1878.) In these four networks, the last 6 binary digits can be used for host addresses.Using a subnet mask of 255.255.255.192, your 192.168.123.0 network then becomes the four networks 192.168.123.0, 192.168.123.64, 192.168.123.128 and 192.168.123.192. These four networks would have as valid host addresses: 192.168.123.1-62192.168.123.65-126192.168.123.129-190192.168.123.193-254Remember, again, that binary host addresses with all ones or all zeros are invalid, so you cannot use addresses with the last octet of 0, 63, 64, 127, 128, 191, 192, or 255.You can see how this works by looking at two host addresses, 192.168.123.71 and 192.168.123.133. If you used the default Class C subnet mask of 255.255.255.0, both addresses are on the 192.168.123.0 network. However, if you use the subnet mask of 255.255.255.192, they are on different networks; 192.168.123.71 is on the 192.168.123.64 network, 192.168.123.133 is on the 192.168.123.128 network.Back to the top●Default gatewaysIf a TCP/IP computer needs to communicate with a host on another network, it will usually communicate through a device called a router. In TCP/IP terms, a router that is specified on a host, which links the host's subnet to other networks, is called a default gateway. This section explains how TCP/IP determines whether or not to send packets to its default gateway to reach another computer or device on the network.When a host attempts to communicate with another device using TCP/IP, it performs a comparison process using the defined subnet mask and the destination IP address versus the subnet mask and its own IP address. The result of this comparison tells the computer whether the destination is a local host or a remote host.If the result of this process determines the destination to be a local host, then the computer will simply send the packet on the local subnet. If the result of the comparison determines the destination to be a remote host, then the computer will forward the packet to the default gateway defined in its TCP/IP properties. It is then the responsibility of the router to forward the packet to the correct subnet.Back to the top●TroubleshootingTCP/IP network problems are often caused by incorrect configuration of the threemain entries in a computer's TCP/IP properties. By understanding how errors in TCP/IP configuration affect network operations, you can solve many common TCP/IP problems.Incorrect Subnet Mask: If a network uses a subnet mask other than the default mask for its address class, and a client is still configured with the default subnet mask for the address class, communication will fail to some nearby networks but not to distant ones. As an example, if you create four subnets (such as in the subnetting example) but use the incorrect subnet mask of 255.255.255.0 in your TCP/IP configuration, hosts will not be able to determine that some computers are on different subnets than their own. When this happens, packets destined for hosts on different physical networks that are part of the same Class C address will not be sent to a default gateway for delivery. A common symptom of this is when a computer can communicate with hosts that are on its local network and can talk to all remote networks except those that are nearby and have the same class A, B, or C address. To fix this problem, just enter the correct subnet mask in the TCP/IP configuration for that host.Incorrect IP Address: If you put computers with IP addresses that should be on separate subnets on a local network with each other, they will not be able to communicate. They will try to send packets to each other through a router that will not be able to forward them correctly. A symptom of this problem is a computer that can talk to hosts on remote networks, but cannot communicate with some or all computers on their local network. To correct this problem, make sure all computers on the same physical network have IP addresses on the same IP subnet. If you run out of IP addresses on a single network segment, there are solutions that go beyond the scope of this article.Incorrect Default Gateway: A computer configured with an incorrect default gateway will be able to communicate with hosts on its own network segment, but will fail to communicate with hosts on some or all remote networks. If a single physical network has more than one router, and the wrong router is configured as a default gateway, a host will be able to communicate with some remote networks, but not others. This problem is common if an organization has a router to an internal TCP/IP network and another router connected to the Internet.⏹REFERENCESTwo popular references on TCP/IP are:"TCP/IP Illustrated, V olume 1: The Protocols," Richard Stevens, Addison Wesley, 1994"Internetworking with TCP/IP, V olume 1: Principles, Protocols, and Architecture," Douglas E. Comer, Prentice Hall, 1995It is strongly recommended that a system administrator responsible for TCP/IP networks have at least one of these references available.●GlossaryBroadcast address -- An IP address with a host portion that is all ones.Host -- A computer or other device on a TCP/IP network.Internet -- The global collection of networks that are connected together and sharea common range of IP addresses.InterNIC -- The organization responsible for administration of IP addresses on the Internet.IP -- The network protocol used for sending network packets over a TCP/IP network or the Internet.IP Address -- A unique 32-bit address for a host on a TCP/IP network or internetwork.Network -- There are two uses of the term network in this article. One is a group of computers on a single physical network segment; the other is an IP network address range that is allocated by a system administrator.Network address -- An IP address with a host portion that is all zeros.Octet -- An 8-bit number, 4 of which comprise a 32-bit IP address. They have a range of 00000000-11111111 that correspond to the decimal values 0- 255.Packet -- A unit of data passed over a TCP/IP network or wide area network.RFC (Request for Comment) -- A document used to define standards on the Internet.Router -- A device that passes network traffic between different IP networks.Subnet Mask -- A 32-bit number used to distinguish the network and host portions of an IP address.Subnet or Subnetwork -- A smaller network created by dividing a larger network into equal parts.TCP/IP -- Used broadly, the set of protocols, standards and utilities commonly used on the Internet and large networks.Wide area network (WAN) -- A large network that is a collection of smaller networks separated by routers. The Internet is an example of a very large WAN.了解TCPIP 寻址和子网配置基础知识⏹简介在 Microsoft Windows 计算机上配置 TCP/IP 协议时,TCP/IP 配置设置中需要 IP 地址和子网掩码,通常还需要一个默认网关。
IP地址冲突的解决方法的方法

IP地址冲突的解决方法的方法IP地址是计算机在网络中的唯一标识符,它允许我们连接到互联网并与其他设备进行通信。
然而,有时候会发生IP地址冲突的情况,这会导致网络连接问题和通信故障。
本文将介绍几种解决IP地址冲突的方法,帮助您解决这个常见的网络问题。
一、IP地址冲突的原因分析在解决IP地址冲突之前,我们先了解一下造成冲突的原因。
IP地址冲突通常发生在多台计算机或设备在同一个网络上使用相同的IP地址时。
这可能是由于以下几个原因导致的:1.手动配置错误:网络管理员或用户手动配置IP地址时输入错误,导致多台设备使用了相同的IP地址。
2.DHCP分配冲突:当使用动态主机配置协议(DHCP)时,DHCP 服务器错误地分配了相同的IP地址给多个设备。
3.网络断开重连:当计算机或设备从一个网络断开连接并重新连接到另一个网络时,它可能会与已经存在的设备使用同一个IP地址。
了解了IP地址冲突的原因后,我们可以使用以下方法来解决这个问题。
二、解决IP地址冲突的方法1.手动重新配置IP地址当发现了IP地址冲突时,一种简单有效的方法是手动重新配置冲突的设备的IP地址。
首先,您需要检查网络上的其他设备是否使用了相同的IP地址。
然后,打开冲突设备的网络设置,将IP地址更改为一个未被其他设备使用的唯一地址,确保子网掩码等其他设置也正确配置。
这种方法需要手动操作,适用于小型网络或个人设备。
但是,当网络规模较大或设备众多时,手动重新配置将变得不可行。
2.通过DHCP服务器自动分配IP地址在大型网络环境中,使用动态主机配置协议(DHCP)可以更方便地管理IP地址。
通过启用DHCP服务器,您可以让网络中的设备自动获取IP地址,从而避免手动配置导致的冲突。
要解决IP地址冲突,您可以关闭设备上的DHCP功能,然后重新启动设备,它将自动向DHCP服务器请求并获得一个新的唯一IP地址。
这种方法适用于企业网络和大型组织。
3.重启路由器和设备有时,IP地址冲突可能是由于网络设备之间的通信故障导致的。
subnet的中文意思是什么

subnet的中文意思是什么subnet的中文意思是什么看到subnet这个词汇可能不少学生会觉得都比较陌生,subnet 有子网络的意思,那么现在就一起subnet的知识吧,希望能够帮到大家!subnet的中文意思英汉解释n. 子网络,分支网络参考例句:1. View card information, can see IP, gateway, subnet yards.查看网卡信息,可以看IP,网关,子网码。
2. The subnet mask helps your computer define the difference between the two addresses.子网路遮罩帮助您的电脑定义在这二个位址之间的差。
3. You entered an invalid subnet mask. The subnet mask has to be contiguous. Please enter a valid mask.您输入一个无效的子网掩码。
子网掩码必须是相邻的。
请输入一个有效的掩码。
subnet的网络释义subnet子网; 子线网; 子网路; 子網路;Resource Subnet资源子网; 资源网;logical subnet逻辑子网;subnet ID子网号; 子网ID; 子网路位址;screened subnet屏蔽子网; 加幕子网;subnet的双语例句The network gateway is determined by ANDing the packet destination with the subnet mask.网路闸道器以封包目的地和子网路遮罩进行AND运算来加以决定。
You cannot create a single scope that contains the IP address range and subnet mask you specified.您无法创建一个包含指定ip地址范围和子网掩码的单一作用域。
IP ADDRESS AND SUBNET MASK

页面 12
2020/12/22
六、子网、子网掩码
Hale Waihona Puke • 子网子网就是把一个大网分割开来而生成的较小网络。 在Internet或TCP/IP网络中,通过路由器连接的网段 就是子网,同一子网的IP地址必具有相同的网络地址。
• 子网掩码
子网掩码也是一组32位的二进制数,形式上与IP地 址一样。同一子网中的子网掩码相同,它用于屏蔽IP地 址的一部分以区别网络ID和主机ID,判断目的主机的 IP地址是在本局域网还是在远程网。
八、子网的划分
• 子网编址方法
将IP地址的主机号部分进一步划分成子网部分和主机 部分
从标准IP地址的主机号部分从左向右“借”位并把它 们指定为子网号部分
在“借”用时必须给主机号部分剩余2位 在“借”用时至少要借用2位
页面 16
2020/12/22
默认C类子网掩码 255.255.255.0
11111111 11111111
,主机号为21
页面 11
2020/12/22
IP分配需注意的问题
1.小型网络使用C类地址,中型网络使用B类地址,大型网络 使用A类地址
2.主机 连接到同一网络中所有主机的IP地址共享同一netid
3.路由器 路由器可以连接多个物理网络 每个连接都拥有自己的IP地址 每个连接IP地址的netid应与这个网络的netid相同
192.168.0.2 202.113.26.0 127.2.0.1
主机号
页面 6
2020/12/22
四、 IP地址的分类
• 二进制形式
页面 7
2020/12/22
• 点分式
地址 类型 A类 B类 C类 D类 E类
IP地址冲突的原因及解决方法的影响

IP地址冲突的原因及解决方法的影响IP地址冲突是指在局域网中存在多台设备使用相同的IP地址,从而导致网络通信出现故障或不稳定。
本文将分析引起IP地址冲突的原因,并提供一些解决方法。
同时,还将探讨IP地址冲突对网络的影响。
1. 原因分析IP地址冲突可能出现在任何一个局域网中,以下是引起冲突的主要原因:1.1 配置错误当管理员手动为设备配置IP地址时,可能会由于疏忽或错误而导致IP地址重复。
这可能发生在新设备添加到网络中,或者在更改网络配置时。
1.2 动态主机配置协议(DHCP)故障使用DHCP服务器为设备动态分配IP地址时,如果DHCP服务器存在故障或被配置错误,可能会分配相同的IP地址给多个设备,从而引发冲突。
1.3 网络设备故障网络设备(如路由器、交换机等)也可能引起IP地址冲突。
例如,设备固件更新或配置更改后,设备没有正确识别其他设备的IP地址。
2. 解决方法以下是解决IP地址冲突的几种常见方法:2.1 静态IP地址配置管理员可以手动为每个设备配置唯一的静态IP地址,确保不会发生地址冲突。
这种方法需要仔细管理和规划,以避免配置错误。
2.2 DHCP服务器管理在使用DHCP服务器分配IP地址时,确保DHCP服务器的配置正确无误。
提供足够的IP地址池大小,以避免地址资源耗尽,并设置合理的租期时间。
2.3 网络设备识别和排查定期检查网络设备的固件更新,确保设备能够正常识别其他设备的IP地址。
在配置更改后,测试设备的通信功能,以确保没有产生冲突。
2.4 网络监控和报警系统安装网络监控和报警系统,定期检查并识别IP地址冲突。
通过及时报警和排查,减少IP冲突对网络带来的不良影响。
3. IP地址冲突的影响IP地址冲突可能导致以下问题:3.1 网络不稳定当多个设备试图使用相同的IP地址时,会导致冲突并阻碍相应设备的正常通信。
这会导致网络不稳定,严重影响网络的正常运行。
3.2 通信故障IP地址冲突会干扰设备之间的通信。
电脑独立IP搭建解决网络连接问题的有效方法

电脑独立IP搭建解决网络连接问题的有效方法在当今数字化社会中,互联网已经成为人们日常生活中不可或缺的一部分。
而在使用互联网时,我们经常会遇到网络连接问题,导致我们无法正常上网。
而搭建独立IP地址是一种解决网络连接问题的有效方法。
本文将为您介绍搭建独立IP地址的步骤及方法,并探讨其解决网络连接问题的价值。
一、搭建独立IP地址的步骤要搭建独立IP地址,我们需要按照以下步骤进行操作:1.了解IP地址的概念和作用:IP地址是互联网协议(Internet Protocol)的缩写,是网络中设备的唯一标识。
它的作用是在互联网上准确定位电脑或其他设备,从而实现网络通信。
2.选择合适的服务提供商:在搭建独立IP地址前,需要选择合适的服务提供商。
我们可以根据自己的需求选择不同类型的服务提供商,如云服务提供商、VPS(Virtual Private Server)提供商等。
3.注册账号并购买IP地址服务:在服务提供商的官方网站上注册账号,并根据自己的需求购买IP地址服务。
4.配置IP地址:购买IP地址服务后,服务提供商会提供一些配置信息,如IP地址、子网掩码、网关等。
我们需要将这些配置信息输入到电脑的网络设置中,从而完成IP地址的配置。
5.测试连接:在完成IP地址配置后,我们可以进行网络连接的测试,确保能够正常访问互联网。
二、独立IP地址解决网络连接问题的价值搭建独立IP地址可以有效解决以下网络连接问题:1.解决IP冲突问题:在大多数情况下,我们使用的是动态IP地址,即每次连接互联网时,都会被分配一个新的IP地址。
然而,当多个设备使用同一个网络时,可能会出现IP地址冲突的问题,导致网络连接异常。
通过搭建独立IP地址,我们可以避免IP地址冲突问题,确保网络连接稳定。
2.提高网络连接速度:与共享IP地址相比,独立IP地址可以为用户提供更快的网络连接速度。
这是因为共享IP地址的连接速度取决于同时使用同一IP地址的用户数量,而独立IP地址能够避免这种问题,提高网络连接速度。
如何解决局域网IP地址冲突的文章

如何解决局域网IP地址冲突的文章解决局域网IP地址冲突的方法局域网(IP地址的缩写是IP,全称是Internet Protocol Address),是指在一个较小的范围内互联的多个计算机组成的网络。
在局域网中,每个计算机都需要拥有唯一的IP地址,以便实现网络通信。
然而,由于IP地址的数量有限,有时候会出现IP地址冲突的情况,即两个或更多计算机拥有相同的IP地址。
这会导致网络通信故障和数据传输错误。
因此,解决局域网IP地址冲突是网络管理员和用户需要面对的问题。
一、发现IP地址冲突当局域网中出现IP地址冲突时,会出现一些特定的问题,如无法访问特定的网站或网络资源,文件传输错误,打印机无法正常工作等。
要解决这些问题,首先需要能够发现IP地址冲突的存在。
以下是几种常用的方法:1. Ping命令:在Windows操作系统中,可以通过使用Ping命令来检测IP地址是否冲突。
打开命令提示符窗口,输入"ping IP地址"(将IP地址替换为具体的IP地址),如果出现回复超时或其他错误提示,则可能存在IP地址冲突。
2. IP扫描工具:使用专门的IP扫描工具可以扫描局域网中的所有IP地址,并显示已分配和冲突的IP地址。
3. 网络管理软件:一些网络管理软件可以自动检测和报告IP地址冲突,提供更方便的管理和解决方法。
二、解决IP地址冲突一旦发现局域网中存在IP地址冲突,需要立即采取措施解决。
以下是几种常用的解决方法:1. 手动更改IP地址:将冲突的计算机的IP地址手动更改为一个未被使用的IP地址。
首先确定可以使用的未被分配的IP地址范围,然后逐个更改冲突的计算机的IP地址。
2. DHCP服务器:如果局域网中使用了动态主机配置协议(DHCP),则可以调整DHCP服务器的设置,以确保每个计算机都能够获得一个唯一的IP地址。
3. 静态IP地址管理:对于需要固定IP地址的计算机,可以设置静态IP地址。
确保每个计算机被分配了不同的静态IP地址,以避免冲突。
解决网络IP地址冲突的方法

解决网络IP地址冲突的方法网络IP地址冲突是在同一局域网中由于存在相同的IP地址而导致的通信故障。
随着互联网的普及和网络设备的增加,IP地址冲突已经成为了一个常见的问题。
本文将介绍一些解决网络IP地址冲突的方法,以帮助用户解决这一问题。
1. 动态IP分配与静态IP分配相结合动态IP分配是指通过DHCP服务器自动分配IP地址给网络设备,而静态IP分配则是手动设置固定的IP地址。
结合使用这两种方式可以有效减少IP地址冲突的概率。
对于常用的设备可以采用静态IP分配,确保每个设备都有独立的IP地址;对于临时连接的设备,可以使用动态IP分配,让DHCP服务器自动分配可用的IP地址。
2. 检查IP地址是否重复当发生IP地址冲突时,首先需要检查是否存在重复的IP地址。
这可以通过使用网络管理工具或者ping命令来实现。
如果发现有多个设备使用相同的IP地址,可以手动更改其中一个设备的IP地址,确保每个设备都有唯一的地址。
3. 使用子网掩码进行划分通过合理设置子网掩码,将局域网划分为多个子网,可以有效减少IP地址冲突的可能性。
子网掩码用于确定一个IP地址的网络部分和主机部分。
通过将不同的设备分配到不同的子网中,可以避免同一个子网中存在相同的IP地址。
4. 使用网络管理软件网络管理软件可以帮助快速定位并解决IP地址冲突问题。
这些软件通常提供可视化的网络拓扑图,可以清楚地显示出每个设备的IP地址,从而方便管理员进行管理。
当发生IP地址冲突时,网络管理软件会及时发出警报,并提供解决方案。
5. 重新启动网络设备有时,重启网络设备也可以解决IP地址冲突的问题。
当一个设备重新加入网络时,DHCP服务器会重新分配可用的IP地址。
通过重新启动设备,可以重新获取IP地址,从而避免冲突。
总结:网络IP地址冲突是一个常见而又令人头疼的问题。
借助动态IP分配与静态IP分配相结合、检查IP地址是否重复、使用子网掩码进行划分、使用网络管理软件以及重新启动网络设备等方法,我们可以有效地解决IP地址冲突,确保网络通信的顺利进行。
ip冲突的简单解决方法

ip冲突的简单解决方法IP冲突的简单解决方法。
IP地址冲突是指在同一网络中出现了两台或两台以上计算机使用了相同的IP地址,这样就会导致网络通信出现故障,给网络管理带来诸多不便。
那么,面对IP地址冲突问题,我们应该如何解决呢?下面就为大家介绍几种简单的解决方法。
首先,我们可以通过查看IP地址的分配情况来确认是否存在IP地址冲突。
在Windows系统中,我们可以通过“cmd”命令来打开命令提示符窗口,然后输入“ipconfig/all”命令来查看当前计算机的IP地址、子网掩码、网关等信息。
通过比对不同计算机的IP地址,我们可以很快确认是否存在IP地址冲突的情况。
确认存在IP地址冲突后,我们可以通过修改IP地址的方式来解决冲突。
在Windows系统中,我们可以通过进入“控制面板”-“网络和 Internet”-“网络和共享中心”-“更改适配器设置”来找到网络连接,然后右键点击选择“属性”,在弹出的窗口中选择“Internet 协议版本 4(TCP/IPv4)”并点击“属性”,在弹出的窗口中选择“使用下面的IP地址”,然后修改IP地址和子网掩码,最后点击“确定”来保存设置。
通过这种方式,我们可以很方便地修改计算机的IP地址,从而解决IP地址冲突的问题。
除了修改IP地址,我们还可以通过重启路由器或交换机来解决IP地址冲突的问题。
在网络中,路由器和交换机负责为计算机分配IP地址,当出现IP地址冲突时,我们可以尝试重启路由器或交换机,让其重新为计算机分配IP地址,从而解决IP地址冲突的问题。
需要注意的是,在重启路由器或交换机之前,我们需要提前通知网络中的其他用户,以免造成不必要的影响。
此外,我们还可以通过使用IP地址分配器来解决IP地址冲突的问题。
IP地址分配器可以自动为计算机分配可用的IP地址,避免出现IP地址冲突的情况。
在网络中,我们可以部署DHCP服务器来实现IP地址的自动分配,让网络中的计算机可以方便地获取可用的IP地址,避免出现IP地址冲突的问题。
IP地址与子网掩码

IP地址与子网掩码1、IP地址:我们知道,不同的物理网络技术有不同的编址方式;不同物理网络中的主机,有不同的物理网络地址。
网间网技术是将不同物理网络技术统一起来的高层软件技术。
网间网技术采用一种全局通用的地址格式,为全网的每一网络和每一主机都分配一个网间网地址,以此屏蔽物理网络地址的差异。
IP协议提供一种全网间网通用的地址格式,并在统一管理下进行地址分配,保证一个地址对应一台网间网主机(包括网关),这样物理地址的差异被IP层所屏蔽。
IP层所用到的地址叫做网间网地址,又叫IP地址。
它由网络号和主机号两部分组成,统一网络内的所有主机使用相同的网络号,主机号是唯一的。
IP地址是一个32为的二进制数,分成4个字段,每个字段8位。
由于二进制使用起来不方便,用户使用“点分十进制”方式表示。
IP地址唯一的标识出主机所在的网络和网络中位置的编号2、三类主要的网络地址:我们知道,从LAN到WAN,不同种类网络规模相差很大,必须区别对待。
因此按网络规模大小,将网络地址分为主要的三类,A类:A类地址用于少量的(最多27个)主机数大于216的大型网,每个A类网络可容纳最多224台主机;这类地址的特点是以0开头,第一字节表示网络号,第二、三、四字节表示网络中的主机号,网络数量少,最多可以表示126个网络号,每一网络中最多可以有16777214个主机号。
IP地址:第一字节。
第二字节。
第三字节。
第四字节0******* ******** ******** ********l—126 0—255 0—255 1—254B类地址用于主机数介于28~216之间数量不多不少的中型网,B类网络最多214个;这类地址的特点是以l0开头,第一、二字节表示网络号,第二、三字节表示网络中的主机号,最多可以表示16384个网络号,每一网络中最多可以有66534个主机号。
IP地址:第一字节第二字节第三字节第四字节10****** ********* ******** ********128一191 0—255 0—255 1—254C类地址用于每个网络只能容纳28台主机的大量小型网,C类网络最多221个。
2013年华为数通HCIE认证课程体系及考试大纲
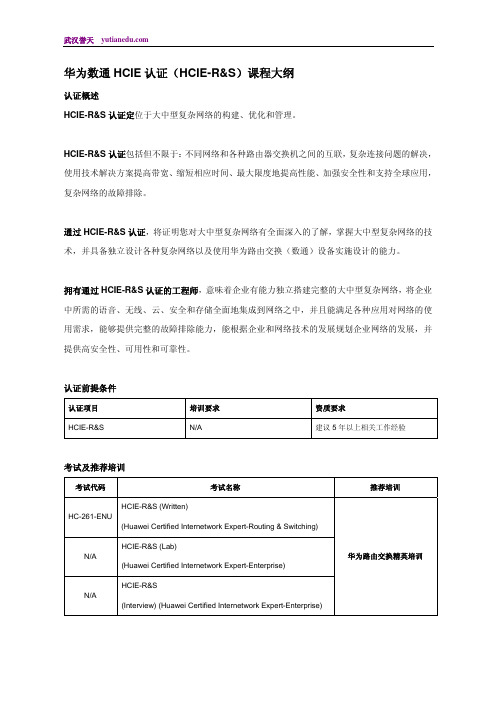
华为数通HCIE认证(HCIE-R&S)课程大纲认证概述HCIE-R&S认证定位于大中型复杂网络的构建、优化和管理。
HCIE-R&S认证包括但不限于:不同网络和各种路由器交换机之间的互联,复杂连接问题的解决,使用技术解决方案提高带宽、缩短相应时间、最大限度地提高性能、加强安全性和支持全球应用,复杂网络的故障排除。
通过HCIE-R&S认证,将证明您对大中型复杂网络有全面深入的了解,掌握大中型复杂网络的技术,并具备独立设计各种复杂网络以及使用华为路由交换(数通)设备实施设计的能力。
拥有通过HCIE-R&S认证的工程师,意味着企业有能力独立搭建完整的大中型复杂网络,将企业中所需的语音、无线、云、安全和存储全面地集成到网络之中,并且能满足各种应用对网络的使用需求,能够提供完整的故障排除能力,能根据企业和网络技术的发展规划企业网络的发展,并提供高安全性、可用性和可靠性。
认证前提条件认证项目培训要求资质要求HCIE-R&S N/A 建议5年以上相关工作经验考试及推荐培训考试代码考试名称推荐培训HCIE-R&S (Written)HC-261-ENU(Huawei Certified Internetwork Expert-Routing & Switching)HCIE-R&S (Lab)华为路由交换精英培训N/A(Huawei Certified Internetwork Expert-Enterprise)HCIE-R&SN/A(Interview) (Huawei Certified Internetwork Expert-Enterprise)认证考试考试费用HC-261-ENU HCIE-R&S(Written)300 USDHCIE-R&S(Lab)1200 USDHCIE-R&S(Interview)再认证随着网络技术的发展,华为认证的内容不定期进行更新或优化,通过再认证,可以保证认证的有效性;并表明认证与网络技术的最新发展趋势保持一致。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Cisco − IP Addressing and Subnetting for New UsersTable of ContentsIP Addressing and Subnetting for New Users (1)Document ID: 13788 (1)Introduction (1)Prerequisites (1)Requirements (1)Components Used (1)Additional Information (1)Conventions (2)Understanding IP Addresses (2)Network Masks (3)Understanding Subnetting (4)Examples (5)Sample Exercise 1 (6)Sample Exercise 2 (6)VLSM Example (7)VLSM Example (8)CIDR (9)Appendix (9)Sample Config (9)Host/Subnet Quantities Table (10)NetPro Discussion Forums − Featured Conversations (11)Related Information (11)IP Addressing and Subnetting for New Users Document ID: 13788IntroductionPrerequisitesRequirementsComponents UsedAdditional InformationConventionsUnderstanding IP AddressesNetwork MasksUnderstanding SubnettingExamplesSample Exercise 1Sample Exercise 2VLSM ExampleVLSM ExampleCIDRAppendixSample ConfigHost/Subnet Quantities TableNetPro Discussion Forums − Featured ConversationsRelated InformationIntroductionThis document will give you basic information you will need to configure your router for routing IP, such as how addresses are broken down and how subnetting works. You will learn how to assign each interface on the router an IP address with a unique subnet. And do not worry, we will show you lots of examples to help tie everything together.PrerequisitesRequirementsThere are no specific prerequisites for this document.Components UsedThis document is not restricted to specific software and hardware versions.Additional InformationIf definitions are helpful to you, use these vocabulary terms to get you started:Address T he unique number ID assigned to one host or interface in a network.••Subnet A portion of a network sharing a particular subnet address.Subnet mask A 32−bit combination used to describe which portion of an address refers to the subnet •and which part refers to the host.•Interface A network connection.If you have already received your legitimate address(es) from the InterNIC (Internet Network Information Center), you are ready to begin. If you are not planning on connecting to the Internet, we strongly suggest that you use reserved addresses from RFC 1918 .ConventionsFor more information on document conventions, see the Cisco Technical Tips Conventions.Understanding IP AddressesAn IP address is an address used to uniquely identify a device on an IP network. The address is made up of 32 binary bits which can be divisible into a network portion and host portion with the help of a subnet mask. The 32 binary bits are broken into four octets (1 octet = 8 bits). Each octet is converted to decimal and separated by a period (dot). For this reason, an IP address is said to be expressed in dotted decimal format (for example, 172.16.81.100). The value in each octet ranges from 0 to 255 decimal, or 00000000 − 11111111 binary.Here is how binary octets convert to decimal: The right most bit, or least significant bit, of an octet will hold a value of 20. The bit just to the left of that will hold a value of 21. This continues until the left−most bit, or most significant bit, which will hold a value of 27. So if all binary bits are a one, the decimal equivalent would be 255 as shown here:1 1 1 1 1 1 1 1128 64 32 16 8 4 2 1 (128+64+32+16+8+4+2+1=255)Here is a sample octet conversion when not all of the bits are set to 1.0 1 0 0 0 0 0 10 64 0 0 0 0 0 1 (0+64+0+0+0+0+0+1=65)And this is sample shows an IP address represented in both binary and decimal.10. 1. 23. 19 (decimal)00001010.00000001.00010111.00010011 (binary)These octets are broken down to provide an addressing scheme that can accommodate large and small networks. There are five different classes of networks, A to E. This document focuses on addressing classes A to C, since classes D and E are reserved and discussion of them is beyond the scope of this document. Note: Also note that the terms "Class A, Class B" and so on are used in this document to help facilitate the understanding of IP addressing and subnetting. These terms are rarely used in the industry anymore because of the introduction of classless interdomain routing (CIDR).Given an IP address, its class can be determined from the three high−order bits. Figure 1 shows the significance in the three high order bits and the range of addresses that fall into each class. For informational purposes, Class D and Class E addresses are also shown.Figure 1In a Class A address, the first octet is the network portion. Octets 2, 3, and 4 (the next 24 bits) are for the network manager to divide into subnets and hosts as he/she sees fit. Class A addresses are used for networks that have more than 65,536 hosts (actually, up to 16777214 hosts!).In a Class B address, the first two octets are the network portion. Octets 3 and 4 (16 bits) are for local subnets and hosts. Class B addresses are used for networks that have between 256 and 65534 hosts.In a Class C address, the first three octets are the network portion. Octet 4 (8 bits) is for local subnets and hosts − perfect for networks with less than 254 hosts.Network MasksA network mask helps you know which portion of the address identifies the network and which portion of the address identifies the node. Class A, B, and C networks have default masks, also known as natural masks, as shown here:Class A: 255.0.0.0Class B: 255.255.0.0Class C: 255.255.255.0An IP address on a Class A network that has not been subnetted would have an address/mask pair similar to: 8.20.15.1 255.0.0.0. To see how the mask helps you identify the network and node parts of the address, convert the address and mask to binary numbers.8.20.15.1 = 00001000.00010100.00001111.00000001255.0.0.0 = 11111111.00000000.00000000.00000000Once you have the address and the mask represented in binary, then identifying the network and host ID is easier. Any address bits which have corresponding mask bits set to 1 represent the network ID. Any address bits that have corresponding mask bits set to 0 represent the node ID.8.20.15.1 = 00001000.00010100.00001111.00000001255.0.0.0 = 11111111.00000000.00000000.00000000−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−net id | host idnetid = 00001000 = 8hostid = 00010100.00001111.00000001 = 20.15.1Understanding SubnettingSubnetting allows you to create multiple logical networks that exist within a single Class A, B, or C network. If you do not subnet, you will only be able to use one network from your Class A, B, or C network, which is unrealistic.Each data link on a network must have a unique network ID, with every node on that link being a member of the same network. If you break a major network (Class A, B, or C) into smaller subnetworks, it allows you to create a network of interconnecting subnetworks. Each data link on this network would then have a unique network/subnetwork ID. Any device, or gateway, connecting n networks/subnetworks has n distinct IP addresses, one for each network / subnetwork that it interconnects.To subnet a network, extend the natural mask using some of the bits from the host ID portion of the address to create a subnetwork ID. For example, given a Class C network of 204.15.5.0 which has a natural mask of 255.255.255.0, you can create subnets in this manner:204.15.5.0 − 11001100.00001111.00000101.00000000255.255.255.224 − 11111111.11111111.11111111.11100000−−−−−−−−−−−−−−−−−−−−−−−−−−|sub|−−−−By extending the mask to be 255.255.255.224, you have taken three bits (indicated by "sub") from the original host portion of the address and used them to make subnets. With these three bits, it is possible to create eight subnets. With the remaining five host ID bits, each subnet can have up to 32 host addresses, 30 of which can actually be assigned to a device since host ids of all zeros or all ones are not allowed (it is very important to remember this). So, with this in mind, these subnets have been created.204.15.5.0 255.255.255.224 host address range 1 to 30204.15.5.32 255.255.255.224 host address range 33 to 62204.15.5.64 255.255.255.224 host address range 65 to 94204.15.5.96 255.255.255.224 host address range 97 to 126204.15.5.128 255.255.255.224 host address range 129 to 158204.15.5.160 255.255.255.224 host address range 161 to 190204.15.5.192 255.255.255.224 host address range 193 to 222204.15.5.224 255.255.255.224 host address range 225 to 254Note: There are two ways to denote these masks. First, since you are using three bits more than the "natural" Class C mask, you can denote these addresses as having a 3−bit subnet mask. Or, secondly, the mask of 255.255.255.224 can also be denoted as /27 as there are 27 bits that are set in the mask. This second method is used with CIDR. Using this method, one of thse networks can be described with the notation prefix/length. For example, 204.15.5.32/27 denotes the network 204.15.5.32 255.255.255.224. When appropriate theprefix/length notation is used to denote the mask throughout the rest of this document.The network subnetting scheme in this section allows for eight subnets, and the network might appear as:Figure 2Notice that each of the routers in Figure 2 is attached to four subnetworks, one subnetwork is common to both routers. Also, each router has an IP address for each subnetwork to which it is attached. Each subnetwork could potentially support up to 30 host addresses.This brings up an interesting point. The more host bits you use for a subnet mask, the more subnets you have available. However, the more subnets available, the less host addresses available per subnet. For example, a Class C network of 204.17.5.0 and a mask of 255.255.255.224 (/27) allows you to have eight subnets, each with 32 host addresses (30 of which could be assigned to devices). If you use a mask of 255.255.255.240 (/28), the break down is:204.15.5.0 − 11001100.00001111.00000101.00000000255.255.255.240 − 11111111.11111111.11111111.11110000−−−−−−−−−−−−−−−−−−−−−−−−−−|sub |−−−Since you now have four bits to make subnets with, you only have four bits left for host addresses. So in this case you can have up to 16 subnets, each of which can have up to 16 host addresses (14 of which can be assigned to devices).Take a look at how a Class B network might be subnetted. If you have network 172.16.0.0 ,then you know that its natural mask is 255.255.0.0 or 172.16.0.0/16. Extending the mask to anything beyond 255.255.0.0 means you are subnetting. You can quickly see that you have the ability to create a lot more subnets than with the Class C network. If you use a mask of 255.255.248.0 (/21), how many subnets and hosts per subnet does this allow for?172.16.0.0 − 10101100.00010000.00000000.00000000255.255.248.0 − 11111111.11111111.11111000.00000000−−−−−−−−−−−−−−−−−| sub |−−−−−−−−−−−You are using five bits from the original host bits for subnets. This will allow you to have 32 subnets (25). After using the five bits for subnetting, you are left with 11 bits for host addresses. This will allow each subnet so have 2048 host addresses (211), 2046 of which could be assigned to devices.Note: In the past, there were limitations to the use of a subnet 0 (all subnet bits are set to zero) and all ones subnet (all subnet bits set to one). Some devices would not allow the use of these subnets. Cisco Systems devices will allow the use of these subnets when the ip subnet zero command is configured. ExamplesSample Exercise 1Now that you have an understanding of subnetting, put this knowledge to use. In this example, you are given two address / mask combinations, written with the prefix/length notation, which have been assigned to two devices. Your task is to determine if these devices are on the same subnet or different subnets. You can do this by using the address and mask of each device to determine to which subnet each address belongs.DeviceA: 172.16.17.30/20DeviceB: 172.16.28.15/20Determining the Subnet for DeviceA:172.16.17.30 − 10101100.00010000.00010001.00011110255.255.240.0 − 11111111.11111111.11110000.00000000−−−−−−−−−−−−−−−−−| sub|−−−−−−−−−−−−subnet = 10101100.00010000.00010000.00000000 = 172.16.16.0Looking at the address bits that have a corresponding mask bit set to one, and setting all the other address bits to zero (this is equivalent to performing a logical "AND" between the mask and address), shows you to which subnet this address belongs. In this case, DeviceA belongs to subnet 172.16.16.0.Determining the Subnet for DeviceB:172.16.28.15 − 10101100.00010000.00011100.00001111255.255.240.0 − 11111111.11111111.11110000.00000000−−−−−−−−−−−−−−−−−| sub|−−−−−−−−−−−−subnet = 10101100.00010000.00010000.00000000 = 172.16.16.0From these determinations, DeviceA and DeviceB have addresses that are part of the same subnet. Sample Exercise 2Given the Class C network of 204.15.5.0/24, subnet the network in order to create the network in Figure 3 with the host requirements shown.Figure 3Looking at the network shown in Figure 3, you can see that you are required to create five subnets. The largest subnet must support 28 host addresses. Is this possible with a Class C network? and if so, then how?You can start by looking at the subnet requirement. In order to create the five needed subnets you would need to use three bits from the Class C host bits. Two bits would only allow you four subnets (22).Since you need three subnet bits, that leaves you with five bits for the host portion of the address. How manyhosts will this support? 25 = 32 (30 usable). This meets the requirement.Therefore you have determined that it is possible to create this network with a Class C network. An example of how you might assign the subnetworks is:netA: 204.15.5.0/27 host address range 1 to 30netB: 204.15.5.32/27 host address range 33 to 62netC: 204.15.5.64/27 host address range 65 to 94netD: 204.15.5.96/27 host address range 97 to 126netE: 204.15.5.128/27 host address range 129 to 158VLSM ExampleIn all of the previous examples of subnetting you will notice that the same subnet mask was applied for all the subnets. This means that each subnet has the same number of available host addresses. You may need this in some cases, but, in most cases, having the same subnet mask for all subnets ends up wasting address space. For example, in the Sample Exercise 2 section, a class C network was split into eight equal−size subnets; however, each subnet did not utilize all available host addresses, which results in wasted address space. Figure 4 illustrates this wasted address space.Figure 4Figure 4 illustrates that of the subnets that are being used, NetA, NetC, and NetD have a lot of unused host address space. This may have been a deliberate design accounting for future growth, but in many cases this is just wasted address space due to the fact that the same subnet mask is being used for all the subnets.Variable Length Subnet Masks (VLSM) allows you to use different masks for each subnet, thereby using address space efficiently.VLSM ExampleGiven the same network and requirements as in Sample Exercise 2 develop a subnetting scheme using VLSM, given:netA: must support 14 hostsnetB: must support 28 hostsnetC: must support 2 hostsnetD: must support 7 hostsnetE: must support 28 hostDetermine what mask allows the required number of hosts.netA: requires a /28 (255.255.255.240) mask to support 14 hostsnetB: requires a /27 (255.255.255.224) mask to support 28 hostsnetC: requires a /30 (255.255.255.252) mask to support 2 hostsnetD*: requires a /28 (255.255.255.240) mask to support 7 hostsnetE: requires a /27 (255.255.255.224) mask to support 28 hosts* a /29 (255.255.255.248) would only allow 6 usable host addressestherefore netD requires a /28 mask.The easiest way to assign the subnets is to assign the largest first. For example, you can assign in this manner: netB: 204.15.5.0/27 host address range 1 to 30netE: 204.15.5.32/27 host address range 33 to 62netA: 204.15.5.64/28 host address range 65 to 78netD: 204.15.5.80/28 host address range 81 to 94netC: 204.15.5.96/30 host address range 97 to 98This can be graphically represented as shown in Figure 5:Figure 5Figure 5 illustrates how using VLSM helped save more than half of the address space.CIDRClassless Interdomain Routing (CIDR) was introduced to improve both address space utilization and routing scalability in the Internet. It was needed because of the rapid growth of the Internet and growth of the IP routing tables held in the Internet routers.CIDR moves way from the traditional IP classes (Class A, Class B, Class C, and so on). In CIDR , an IP network is represented by a prefix, which is an IP address and some indication of the length of the mask. Length means the number of left−most contiguous mask bits that are set to one. So network 172.16.0.0 255.255.0.0 can be represented as 172.16.0.0/16. CIDR also depicts a more hierarchical Internet architecture, where each domain takes its IP addresses from a higher level. This allows for the summarization of the domains to be done at the higher level. For example, if an ISP owns network 172.16.0.0/16, then the ISP can offer 172.16.1.0/24, 172.16.2.0/24,and so on to customers. Yet, when advertising to other providers, the ISP only needs to advertise 172.16.0.0/16.For more information on CIDR, see RFC 1518 and RFC 1519 .AppendixSample ConfigRouters A and B are connected via serial interface.Router Ahostname routera!ip routing!int e 0ip address 172.16.50.1 255.255.255.0!(subnet 50)int e 1 ip address 172.16.55.1 255.255.255.0!(subnet 55)int t 0 ip address 172.16.60.1 255.255.255.0!(subnet 60) int s 0ip address 172.16.65.1 255.255.255.0 (subnet 65)!S 0 connects to router Brouter ripnetwork 172.16.0.0Router Bhostname routerb!ip routing!int e 0ip address 192.1.10.200 255.255.255.240!(subnet 192)int e 1ip address 192.1.10.66 255.255.255.240!(subnet 64)int s 0ip address 172.16.65.2 (same subnet as router A's s 0)!Int s 0 connects to router Arouter ripnetwork 192.1.10.0network 172.16.0.0Host/Subnet Quantities TableClass B Effective Effective# bits Mask Subnets Hosts−−−−−−− −−−−−−−−−−−−−−− −−−−−−−−− −−−−−−−−−1 255.255.128.02 327662 255.255.192.0 4 163823 255.255.224.0 8 81904 255.255.240.0 16 40945 255.255.248.0 32 20466 255.255.252.0 64 10227 255.255.254.0 128 5108 255.255.255.0 256 2549 255.255.255.128 512 12610 255.255.255.192 1024 6211 255.255.255.224 2048 3012 255.255.255.240 4096 1413 255.255.255.248 8192 614 255.255.255.252 16384 2Class C Effective Effective# bits Mask Subnets Hosts−−−−−−− −−−−−−−−−−−−−−− −−−−−−−−− −−−−−−−−−1 255.255.255.1282 1262 255.255.255.192 4 623 255.255.255.224 8 304 255.255.255.240 16 145 255.255.255.248 32 66 255.255.255.252 64 2*Subnet all zeroes and all ones included. Thesemight not be supported on some legacy systems.*Host all zeroes and all ones excluded.NetPro Discussion Forums − Featured Conversations Networking Professionals Connection is a forum for networking professionals to share questions, suggestions, and information about networking solutions, products, and technologies. The featured links are some of the most recent conversations available in this technology.NetPro Discussion Forums − Featured Conversations for RPService Providers: MPLSVirtual Private Networks: ServicesVirtual Private Networks: SecurityRelated Information•IP Subnet Calculator ( registered customers only)•IP Routing Protocols Support PageSubnet Zero and the All−Ones Subnet••Host and Subnet QuantitiesIP Subnet Calculation & Design Online Documentation••Technical Support − Cisco SystemsAll contents are Copyright © 1992−2005 Cisco Systems, Inc. All rights reserved. Important Notices and Privacy Statement. Updated: Sep 26, 2005Document ID: 13788。
