data protection & migration new-阳光教材
Dell Data Protection Security Tools 安装指南说明书

Installation of Dell Data Protection | Security Tools after point of sale on Dell Latitude™, Optiplex™ and Precision SystemsInstallation GuideAugust 2013IntroductionDell Data Protection | Security Tools (DDP | ST) enables local management and provisioning of Dell’s advanced authentication hardware and self-encrypting drives and provides new policy options to better secure your Dell endpoints.Dell Data Protection | Security Tools CompatibilityDell Data Protection | AccessDell Data Protection | Access (DDP | A) is not compatible with DDP | ST. As both products manage your advanced authentication hardware and self-encrypting drives (SEDs), you cannot run bothsimultaneously. If you would like to install DDP | ST, you will need to uninstall DDP | A. For anumbered list use the “Number ed(1)” style.Dell Data Protection | Encryption 7.2.xDell Data Protection | Encryption (DDP | E) version 7.2.x is compatible with DDP | ST, but you will not realize the full potential of DDP | ST with DDP | E 7.2.x. Dell recommends that you upgrade to DDP | E8.x to enable full, integrated remote management of your authentication policy within the DDP | Eremote console.Dell Data Protection | Encryption 8.xDell Data Protection | Encryption 8.x was designed to work with and augment the features of DDP | ST.The DDP | E remote management console provides the ability to remotely manage all of theauthentication policies which can be locally managed within the DDP | ST local console.Installation of DDP | ST on a Platform with DDP | AIf you attempt to install DDP | ST on a system that has DDP | A installed, you will receive an errormessage advising you of the incompatibility with DDP | A. This error message provides basic guidance for uninstalling DDP | A. Following acknowledgement of this error message, the installation will abort.More detailed instructions are provided here.Prior to uninstalling DDP | A, you must deprovision any hardware managed by DDP | A. Note: If using some encryption products, such as DDP | E 7.2.x or Microsoft Bitlocker™, you will also need to stop or pause your encryption policy.© 2013 Dell Inc. Confidential. All rights reserved. Reproduction of this material in any manner whatsoeverwithout the express written permission of Dell Inc. is strictly forbidden. For more information, contact Dell.Dell, the DELL logo, and the DELL badge are trademarks of Dell Inc. All other trademarks are properties ofDeprovisioning DDP|A managed hardware includes the fingerprint reader, smart card reader, bios passwords, TPM and the self-encrypting drive. If you have not used DDP | A, you may uninstall DDP |A and restart the DDP | ST installation process.Deprovision DDP | A Managed HardwareLaunch DDP | A and click on the Advanced Tab.Select Reset System. This will require that you enter any provisioned credentials to verify your identity.After DDP | A verifies the credentials, DDP | A will perform the following actions:1. Remove all provisioned credentials from Dell ControlVault ™ if present2. Remove Dell ControlVault ™ owner password, if present3. Remove all provisioned fingerprints from integrated fingerprint reader, if present4. Remove all BIOS passwords (BIOS System, BIOS Admin, and HDD passwords), and5. Clear the Trusted Platform Module6. Remove the DDP | A Credential ProviderOnce these devices are deprovisioned, DDP | A will reboot the system to restore the Windows default Credential Provider.Uninstall DDP | AOnce your authentication hardware is deprovisioned, you can uninstall DDP|A. Navigate to Control Panel > Programs and Features and select Dell Data Protection | Access. Click “Uninstall” to launch the installer. When the installer finishes removing the files, click “Yes” to reboot.If using a self-encrypting drive, removing DDP | A will also unlock the SED and remove the pre-boot authentication.© 2013 Dell Inc. Confidential. All rights reserved. Reproduction of this material in any manner whatsoeverwithout the express written permission of Dell Inc. is strictly forbidden. For more information, contact Dell.Dell, the DELL logo, and the DELL badge are trademarks of Dell Inc. All other trademarks are properties of。
vSphere-Data-Protection-6.0部署及使用

vSphere-Data-Protection-6.0部署及使用vSphere Data Protection6.0部署及使用第 1页,共39页目录1概述 (4)2功能简介 (4)3安装部署 (4)3.1环境需求43.2部署流程43.2.1安装VDP虚拟机43.2.2配置DNS103.2.3配置VDP13第 2页,共39页3.2.4使用vSphere Web Client连接VDP设备 (25)4主要功能明细及验证 (26)4.1创建备份作业264.2执行备份作业334.3从备份中恢复虚拟机35第 3页,共39页1概述本文主要介绍vSphere Data Protection(VDP)的功能及安装部署流程,并在安装部署后针对其主要功能进行验证性测试,简要对比VDP较VDR的优势。
文中还将针对安装部署及使用过程中可能出现的问题进行标注说明。
2功能简介使用VDP可以针对虚拟机进行备份和恢复,将虚拟机整机或单个磁盘进行计划性的备份,在意外发生后,可以实现整机或单个文件级的恢复,从而保证用户数据的安全可用。
3安装部署3.1环境需求(1)ESXI:4.0及更高版本(2)VMware vCenter Server:5.1及更高版本(3)VDP通过VMware vSphere Web Client管理,故需要安装有安装Web Client 3.2部署流程3.2.1安装VDP虚拟机(1)下载“vSphereDataProtection-5.5.6-0.0TB.ova”或其他版本VDP的OV A文件;(2)通过vSphere Client或vSphere Web Client登录vCenter Server;(3)点击“文件”→“部署OVF模版(D…)”第 4页,共39页第 5页,共39页(4) 通过“浏览”选择VDP 的OV A 文件,点击“下一步≥”注意:这里需要登录到vCenter Server 进行模版部署,若直接登录主机部署VDP 模版则会出现如下错误:第 6页,共39页(5) 点击“下一步≥”(6) 点击“接受(A )”→“下一步”第 7页,共39页(7) 输入虚拟机名称,选择清单位置,点击“下一步≥”(8)选择存储位置,选择虚拟机磁盘格式为“Thin Provision”,点击“下一步≥”注意:如后期要扩充磁盘,这里必须要选择精简置备,并且磁盘有足够的空间用于扩充(9)配置VDP的网络信息,点击“下一步≥”第 8页,共39页(10)确认配置信息后,点击“完成”第 9页,共39页第 10页,共39页3.2.2 配置DNS为VDP 添加DNS 正向查找和反向查找记录 (1) 登录域控,点击“开始”→“管理工具”→“DNS”第 11页,共39页(2) 在DNS 管理器中,添加正向查找和反向查找(3)添加正向查找:(4)添加反向查找:第 12页,共39页3.2.3配置VDP(1)打开VDP电源第 13页,共39页(2)VDP启动后出现如下界面(3)根据提示,https://vdpip:8543/vdp-configure,通过浏览器登录VDP,这第 14页,共39页第 15页,共39页里默认密码为“changeme”(4) 点击“下一步”(5) 输入相关网络配置,点击“下一步”注意:这里如果未在域控中为VDP添加正向查找和反向查找会出现如下错误提示(6)选择时区,点击“下一步”第 16页,共39页第 17页,共39页(7)按要求输入VDP密码,点击“下一步”(8) 输入vCenter 用户名、密码等相关信息,点击“测试连接”第 18页,共39页注意:这里需要预先添加vCenter 权限和vCenter 的DNS 正反向记录,否则会有如下错误提示:(9)创建存储容量,这里选择后不能再更改(10)选择存储设备第 19页,共39页注意:在创建后备份初期,数据量会大量增加,这是正常现象,每个备份目标第一次都是完全备份,经过一次备份后增量备份功能才会发挥作用。
VMwarevSphereDataProtectionAdvanced5
产品介绍/1VMware vSphere Data Protection Advanced 是什么?vSphere Data Protection Advanced 是一款备份和恢复解决方案,它专为 vSphere 环境而设计,并由 EMC Avamar 提供支持。
它对 vSphere Data Protection (大多数版本的 vSphere 中都已提供)的功能进行了延展,提高了可扩展性,并增强了功能。
它平均能够在每个虚拟设备上备份 200 台虚拟机,因此,可以安全地保护包含数百台虚拟机的环境和远程办公室。
它不仅可提供无代理映像级备份到磁盘的功能,还可针对 Microsoft ® SQL Server ™、Exchange ™ 和 SharePoint ™ 提供客户机级应用一致性保护。
vSphere Data Protection Advanced 可通过高效利用网络的加密型复制功能将备份复制到一个或多个灾难恢复站点。
VMware vSphere Data Protection Advanced 5.8 有哪些新增的功能特性?• 可配置的并行备份:– 部署最多 8 个代理,并同时执行最多 24 个备份,以此来缩短备份时间,同时不影响网络、CPU 和内存使用情况– 使用 SCSI 热添加,以实现高效的数据传输• 随时随地访问并还原复制的备份:在主站点或灾难恢复站点访问复制的还原点并还原复制的备份• 支持 MS Exchange 数据库可用性组• 支持 SQL 集群备份• 支持 Linux LVM 和 EXT4• 支持每个 VMware vCenter Server ™ 中最多 20 个虚拟设备其他主要功能特性可扩展性 — 每个虚拟设备最多可存储 8 TB (约 200 个平均大小的虚拟机)的已消除重复数据的备份数据。
最多可在每台 vCenter Server 上部署 20 个虚拟设备。
Data Protector软件(解决方案、产品配置及注意事项)
HP Data Protector software:
HP Business Copy & Continuous Access
HP EVA and XP Disk Arrays
Disk-to-disk backup
(VTL, disk) HP Data Protector software:
Advanced Backup to Disk Virtual Tape Libraries (VTL) Disk Arrays
Windows(32/64 位)(Intel EM64T,AMD x64) HP-UX (HP-UX 11.31) Solaris Linux SuSE、Red Hat(Xeon64、AMD64)
磁盘代理
• • • • • • • • • • • • • • • •
11
介质代理
• • • • • • • • • • •
价格 支持 样板客户 功能
重要
4 2009年6月23日 星期二
如今保持业务连续 运转的动力
以消费者版本的价格获得 企业版本的功能
5
2009年6月23日 星期二
HP Data Protector 软件的样板客户已逾 22,000 家...这一数字仍在不断增加
Teves AG
6
2009年6月23日 星期二
B6963AA
NEW
B6953AA B6958BU
1x unlimited slots upgrade
B6965BA B6966AA
on-line backup LTU 1x system 1x system NEW manager-of-managers LTU B7038AA/DA/EA advanced backup to disk LTU 1x/10x/100 TB B6960EA functional extensions-manuals NDMP HP XP NEW B7023CA/DA zero downtime backup LTU 1x TB / 10x TB 1x TB / 10x TB B7026CA/DA instant recovery LTU B7027AA/DA 1x TB / 10x TB B7022BA/DA direct backup LTU open file backup media operations LTU
data protection act 2018 解读

data protection act 2018 解读
根据2023年12月28日的最新信息,Data Protection Act 2018是英国的一项数据保护法律。
以下是对该法律的解读:
1. 目的:Data Protection Act 2018的目的是确保个人数据的合理使用和保护。
它旨在落实欧洲联盟的《通用数据保护条例》(GDPR)并提供附加的规定和指导。
2. 数据主体权利:该法律赋予个人对其个人数据的一些基本权利,包括访问、更正、删除和限制处理等。
个人还有权利知晓他们的数据被如何处理以及有关数据处理活动的详细信息。
3. 数据处理者责任:Data Protection Act 2018要求数据处理者遵守严格的规则和标准来处理个人数据。
这包括合法性、透明性、目的限制、数据最小化、准确性和存储期限等原则。
4. 合法依据:数据处理必须有合法依据,例如数据主体的同意、履行合同、法律义务、公共利益或合法利益等。
该法律还规定了特殊类别的个人数据(如健康信息、种族或族裔信息等)的处理条件。
5. 数据传输和安全:Data Protection Act 2018要求数据处理者采取适当的技术和组织措施来保护个人数据免受未经授权的访问、意外损失或泄露。
此外,对于将个人数据传输到非欧洲经济区域的情况,必须确保适当的保护措施。
6. 数据保护监管机构:该法律设立了一个独立的数据保护监管机构,负责监督和执行数据保护规定。
在英国,这个机构是信息专员办公室(Information Commissioner's Office)。
1。
Data_Protector安装参考手册
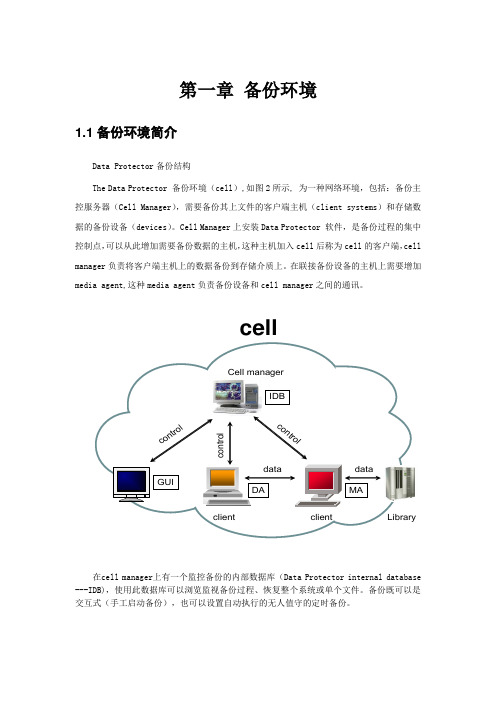
第一章 备份环境1.1备份环境简介Data Protector 备份结构The Data Protector 备份环境(cell ),如图2所示, 为一种网络环境,包括:备份主控服务器(Cell Manager ),需要备份其上文件的客户端主机(client systems )和存储数据的备份设备(devices )。
Cell Manager 上安装Data Protector 软件,是备份过程的集中控制点,可以从此增加需要备份数据的主机,这种主机加入cell 后称为cell 的客户端,cell manager 负责将客户端主机上的数据备份到存储介质上。
在联接备份设备的主机上需要增加media agent,这种media agent 负责备份设备和cell manager 之间的通讯。
Cell managerLibraryo n t r o l在cell manager 上有一个监控备份的内部数据库(Data Protector internal database ---IDB),使用此数据库可以浏览监视备份过程、恢复整个系统或单个文件。
备份既可以是交互式(手工启动备份),也可以设置自动执行的无人值守的定时备份。
第二章备份软件安装2.1 安装准备Cell Manager软件安装需求:PC Server (CPU P4,内存不小于512M)SCSI 卡(PCI LVD/SE接口)或光纤卡Windows 2000 server, Oracle 10g for windows,exchange,sqlserver 2000网络设置完毕:网卡配置完毕,网络连通,可以连接到服务器上(ping或telnet 到小型机执行成功)注意:由于备份软件的license和本地的IP地址相关联,所以安装之前最好确定本PC服务器的IP地址,以后不能随意更改,否则备份软件不能使用。
2.2安装过程:在备份PC服务器DL380光驱中插入DP 6.0 for windows光盘,安装程序自动启动选择Install Data Protector选择next选择I accept the terms in the license agreement选项,然后选择next输入口令(如果有口令)选择安装的路径,一般为默认路径安装;点击change,可以更改安装目录。
Data Protection Regulations

Data Protection Regulationsare laws designed to protect the personal data of individuals and ensure that organizations handling this data do so in a responsible and ethical manner. These regulations aim to protect the privacy and security of personal information, which includes things like names, addresses, phone numbers, financial details, and more. In this article, we will delve into the importance of data protection regulations, how they affect individuals and organizations, and the key principles that guide their implementation.One of the main reasons why data protection regulations are essential is to prevent unauthorized access to personal information. In today's digital age, where data is stored and shared online, there is an increased risk of data breaches and cyber-attacks. These regulations help to set standards for the collection, storage, and processing of personal data, ensuring that organizations have appropriate security measures in place to safeguard this information.Furthermore, data protection regulations also give individuals greater control over their personal data. These laws typically require organizations to obtain explicit consent before collecting and using personal information, as well as providing individuals with the right to access, correct, and delete their data. This empowers individuals to make informed decisions about how their data is used and gives them the ability to hold organizations accountable if they misuse or mishandle their information.For organizations, compliance with data protection regulations is not just a legal requirement, but also a way to build trust with their customers. By demonstrating a commitment to protecting personal data and following best practices for data security, organizations can enhance their reputation and establish credibility with consumers. This can lead to increased customer loyalty and a competitive advantage in the marketplace.The key principles that underpin data protection regulations include transparency, accountability, and privacy by design. Transparency requires organizations to be open and honest about how they collect, use, and share personal data, ensuring that individuals are aware of the purposes for which their information is being processed. Accountabilityholds organizations responsible for safeguarding personal data and requires them to implement robust security measures to prevent data breaches. Privacy by design encourages organizations to consider data protection and privacy from the outset of any new project or initiative, rather than as an afterthought.In conclusion, data protection regulations play a crucial role in protecting the privacy and security of personal information in today's digital world. By setting standards for the collection, storage, and processing of data, these regulations help to prevent unauthorized access and misuse of personal data. They also give individuals greater control over their information and empower them to make informed decisions about how their data is used. For organizations, compliance with data protection regulations is not just a legal obligation, but a way to build trust with customers and enhance their reputation. By adhering to the key principles of transparency, accountability, and privacy by design, organizations can demonstrate their commitment to data protection and earn the trust of their stakeholders.。
data protection clause条款

data protection clause条款摘要:I.数据保护条款概述A.数据保护条款的定义B.数据保护条款的重要性II.数据保护条款的主要内容A.个人数据的收集与使用1.数据收集的合法性2.数据使用的限制B.个人数据的安全保障1.数据安全措施的实施2.数据访问控制C.个人数据的权利与救济1.数据主体的权利2.救济措施的提供III.数据保护条款在国际贸易中的应用A.跨境数据传输1.数据跨境传输的原则2.数据跨境传输的协议B.跨国企业的数据保护问题1.跨国企业的数据保护挑战2.跨国企业如何遵守数据保护条款IV.我国的数据保护条款法规发展A.我国数据保护条款的立法现状B.我国数据保护条款的改革趋势正文:随着互联网的普及和大数据时代的到来,数据保护问题日益突出,数据保护条款作为保护个人数据安全的重要法律手段,越来越受到各国的重视。
数据保护条款,顾名思义,是指在合同、协议或其他法律文件中,关于保护个人数据的一系列规定。
它规定了数据的收集、使用、存储、传输等环节应遵循的原则和方法,以确保个人数据的安全、隐私得到保护。
数据保护条款的重要性体现在以下几个方面:首先,个人数据是个人信息的载体,涉及个人的隐私、名誉、财产等诸多权益,因此需要特殊的法律保护。
其次,数据保护条款有助于规范数据处理者的行为,提高数据安全水平,防止数据泄露、滥用等风险。
最后,数据保护条款是国际贸易中数据跨境传输的基础,有助于促进国际合作和数据自由流动。
数据保护条款的主要内容包括个人数据的收集与使用、个人数据的安全保障以及个人数据的权利与救济。
在个人数据的收集与使用方面,数据收集应遵循合法、正当、必要的原则,数据使用应受限,不能用于未经授权的目的。
在个人数据的安全保障方面,数据处理者应采取技术措施和其他必要措施,确保数据安全,防止数据泄露、损毁、篡改。
在个人数据的权利与救济方面,数据主体享有知情权、访问权、更正权、删除权等一系列权利,并有权获得救济,包括赔偿损失、恢复名誉等。
Data protection for sap oralce 安装
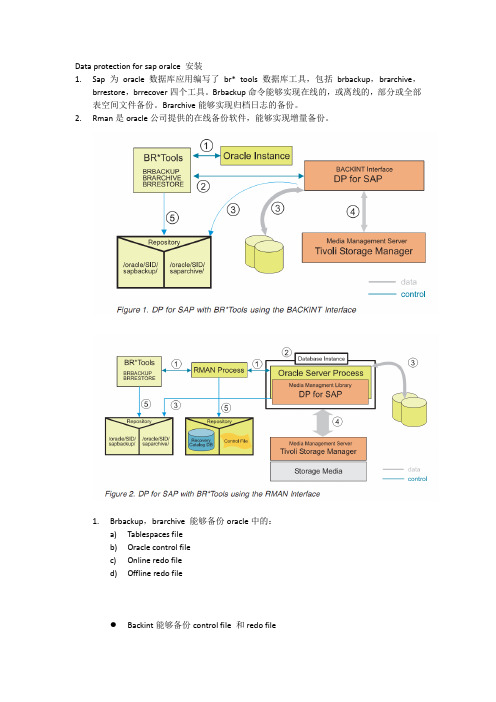
Data protection for sap oralce 安装1.Sap 为oracle数据库应用编写了br* tools 数据库工具,包括brbackup,brarchive,brrestore,brrecover四个工具。
Brbackup命令能够实现在线的,或离线的,部分或全部表空间文件备份。
Brarchive能够实现归档日志的备份。
2.Rman是oracle公司提供的在线备份软件,能够实现增量备份。
1.Brbackup,brarchive 能够备份oracle中的:a)Tablespaces fileb)Oracle control filec)Online redo filed)Offline redo fileBackint能够备份control file 和redo file●使用rman和它的共享库文件能够实施数据库增量备份。
●TDR中的prole组件安装过程2.软件预要求TSM SERVER,ORACLE,sap r3,TSM client已经按照好3.软件文件名格式:<version>-TIV-TSMERPORA-<platform>a)使用root用户登录oracle所在的机器b)Tdr的bit版本必须和oracle的一致。
i.如果使用RMAN,则编辑init<SID>.sap文件,插入以下语句backup_dev_type=rman_utilrman_parms="ENV=(XINT_PROFILE=<path>/init<SID>.utl,PROLE_PORT=<portnumber>,&BR_INFO)"ProLE的portnumber 号可以在/etc/services文件中查看。
以tdpr3ora 或tdpr3ora64命名。
ii.如果没有使用RMAN,则cd $ORACLE_HOME/rdbms/libln -s /usr/tivoli/tsm/tdp_r3/ora/libtdp_r3.<ext> /usr/lib/libobk.<ext>ln -s /usr/lib/libobk.<ext> $ORACLE_HOME/lib/libobk.<ext>4.安装完成后,在/etc/initab 文件中将看到ProLE的启动项。
Dell Data Protection 控制台用户指南.pdf_1700898517.963764

Dell Data Protection 控制台用户指南加密状态身份验证注册Password Manager版本 1.10© 2016 Dell Inc.Dell Data Protection | Encryption、Dell Data Protection | Endpoint Security Suite、Dell Data Protection | Endpoint Security Suite Enterprise、Dell Data Protection | Security Tools 和 Dell Data Protection | Cloud Edition 整套文件中使用的注册商标和商标:Dell™ 和 Dell 徽标、Dell Precision™、OptiPlex™、ControlVault™、Latitude™、XPS®和 KACE™ 是 Dell Inc.的商标。
Cylance®和 Cylance 徽标是 Cylance, Inc.在美国和其他国家/地区的注册商标。
McAfee®和 McAfee 徽标是 McAfee, Inc.在美国和其他国家/地区的商标或注册商标。
Intel®、Pentium®、Intel Core Inside Duo®、Itanium®和 Xeon®是 Intel Corporation 在美国和其他国家/地区的注册商标。
Adobe®、Acrobat®和 Flash®是 Adobe Systems Incorporated 的注册商标。
Authen Tec®和 Eikon®是 Authen Tec 的注册商标。
AMD®是 Advanced Micro Devices, Inc.的注册商标。
Microsoft®、Windows®和 Windows Server®、Internet Explorer®、MS-DOS®、Windows Vista®、MSN®、ActiveX®、Active Directory®、Access®、ActiveSync®、BitLocker®、BitLocker To Go®、Excel®、Hyper-V®、Silverlight®、Outlook®、PowerPoint®、OneDrive®、SQL Server®和 Visual C++®是 Microsoft Corporation 在美国和/或其他国家/地区的商标或注册商标。
data protection clause条款

Data Protection ClauseIntroductionIn today’s digital age, data protection has become a critical concern for individuals and organizations alike. With the increasing reliance on technology and the collection and processing of personal data, it is essential to have robust data protection measures in place. This is where a data protection clause comes into play. A data protection clause is a contractual provision that outlines the rights and obligations of parties when it comes to the collection, use, and safeguarding of personal data. In this article, we will delve into the key aspects of a data protection clause and its importance in ensuring data privacy.Scope and PurposeThe data protection clause sets out the scope and purpose of the clause in a contract. It defines the types of personal data that will be collected and processed, the purposes for which the data will be used, and the parties involved. The clause should clearly state that the collection and processing of personal data will be in accordance with applicable data protection laws and regulations.Data Collection and ProcessingThe data protection clause should specify how personal data will be collected and processed. It should outline the methods of data collection, such as through online forms, cookies, or directinteractions with individuals. Additionally, it should state the lawful basis for collecting and processing personal data, such as consent or legitimate interests.The clause should also address the purpose of data processing. This may include providing services to the individual, fulfilling contractual obligations, or complying with legal requirements. It should be made clear that personal data will not be used for any other purposes without obtaining additional consent from the individual.Data Retention and StorageThe data protection clause should outline the retention and storage of personal data. It should specify the duration for which personal datawill be stored and the criteria used to determine the retention period. This ensures that personal data is not kept for longer than necessary.Furthermore, the clause should address the security measures implemented to protect personal data. This may include encryption, access controls, regular backups, and monitoring systems. The aim is to prevent unauthorized access, loss, or alteration of personal data.Data Subject RightsA crucial aspect of a data protection clause is the recognition of data subject rights. These rights empower individuals to have control over their personal data. The clause should inform individuals of their rights, such as the right to access, rectify, and delete their personal data. It should also provide information on how individuals can exercise these rights, such as by contacting a designated data protection officer.Data TransfersIf personal data is transferred to a third party, whether within or outside the country, the data protection clause should address this issue. It should state the safeguards implemented to ensure the security and confidentiality of personal data during the transfer. This may include the use of standard contractual clauses, binding corporate rules, or adherence to an approved code of conduct.Breach NotificationIn the event of a data breach, the data protection clause should outline the procedures for notifying the affected individuals and the relevant authorities. The clause should specify the timeframe within which the breach will be reported and the information that will be provided to the affected individuals. This ensures transparency and allows individualsto take appropriate measures to protect themselves.Compliance and AuditsTo ensure compliance with data protection laws and regulations, the data protection clause should include provisions for audits and assessments. It should state that the parties will cooperate in conducting audits to assess compliance with the clause and applicable data protection laws. This helps in identifying and rectifying any non-compliance issues.ConclusionA data protection clause is an essential component of contractsinvolving the collection and processing of personal data. It establishes the rights and obligations of parties and ensures compliance with data protection laws and regulations. By including a comprehensive and well-drafted data protection clause, organizations can demonstrate their commitment to data privacy and build trust with individuals.。
data protection clause条款

数据保护条款是指在合同中特定的用来保护数据安全和隐私的条款。
在今天信息爆炸的时代,数据保护越来越成为人们关注的焦点。
数据保护条款的内容通常包括了个人数据保护、数据使用、数据安全和数据流转等方面的规定。
下面将从几个方面分析数据保护条款的重要性以及如何编写一份完善的数据保护条款。
一、数据保护条款的重要性1. 保护个人隐私权在信息化社会,个人的隐私数据被泄露已经成为一个严重的问题。
数据保护条款的制定可以有效地保护个人的隐私权,防止个人数据被滥用。
2. 遵守相关法律法规越来越多的国家和地区出台了相关的数据保护法律法规,要求企业在处理个人数据的过程中必须遵守相关规定。
而制定数据保护条款就是为了让企业遵守这些法律法规,保证数据的合法、合规使用。
3. 保护企业利益在商业活动中,企业获取和使用大量的数据,这些数据可能包含了商业机密和重要信息。
通过数据保护条款的规定,可以有效地保护企业的数据安全,并防止其被不法分子窃取和篡改。
二、如何编写数据保护条款1. 确定适用范围首先要确定数据保护条款适用的范围。
这包括了条款适用的对象,如个人数据、企业数据等;以及适用的业务范围,如电子商务、金融服务等。
2. 明确数据的收集和使用在数据保护条款中,需要明确规定数据的收集和使用方式。
包括了数据的获取途径、获取目的、使用范围等方面的规定,以确保数据的合法、合规使用。
3. 确保数据安全数据泄露和数据安全问题是当前互联网时代中的一大难题。
数据保护条款中需要明确规定数据的存储和传输安全措施,以保障数据不会被未经授权的获取和利用。
4. 规定数据流转和共享在商业活动中,数据的流转和共享是非常普遍的。
但是在数据保护条款中需要对数据的流转和共享进行规范。
需要明确规定数据流转和共享的条件、方式和限制,以保证数据的安全和合法使用。
5. 确定责任和违约责任数据保护条款中需要明确规定各方对数据保护的责任和义务,以及违约责任和违约后的处理方式。
这有利于明确各方的权利和义务,以及在发生纠纷时的处理方式。
VMwarevSphereVDP安装部署

VMwarevSphereVDP安装部署VMware vSphere VDP安装部署⼀、VDP是什么vSphere Data Protection (VDP) 是⼀个基于磁盘的备份和恢复解决⽅案,可靠且易于部署。
vSphere Data Protection 与VMwarevCenter Server完全集成,可以对备份作业执⾏有效的集中式管理,同时将备份存储在经过重复数据消除的⽬标存储中。
⼀、vSphere Data Protection 具有以下优势:1 针对所有虚拟机提供快速有效的数据保护,甚⾄可保护那些已关闭或在物理主机之间移动的虚拟机。
2 在所有备份上使⽤智能重复数据消除,从⽽可极⼤地减少备份数据所消耗的磁盘空间。
3 通过使⽤更改数据块跟踪和VMware 虚拟机快照,降低了备份虚拟机的成本,最⼤程度地缩短了备份窗⼝。
4 可实现轻松备份,⽆需在每个虚拟机上安装第三⽅代理。
5 可以作为集成组件简单直接地安装到vSphere 中,可通过Web 门户进⾏管理。
6 对vSphere Data Protection 配置的直接访问已集成到标准的vSphere Web Client 中。
7 使⽤检查点和回滚机制保护备份。
8 从基于Web 的界⾯中,通过最终⽤户启动的⽂件级恢复 (诸多限制)⼆、提供Windows 和Linux ⽂件的简化恢复。
映像级备份和恢复VMware 映像备份的优势包括:1 提供虚拟机的完整映像备份,⽽与来宾操作系统⽆关2 如果⾼效传输⽅法SCSI 热添加可⽤并且已获得适当许可,则会利⽤该功能,这样可避免通过⽹络拷贝整个VMDK 映像3 从映像级备份中提供⽂件级恢复4 在vSphere Data Protection 应⽤装置保护的所有 .vmdk ⽂件内部以及各⽂件之间执⾏重复数据消除5 使⽤更改数据块跟踪实现更快的备份和恢复6 通过重复数据消除和压缩数据,最⼤程度地减少⽹络流量7 ⽆需在每个虚拟机中管理备份代理8 ⽀持并⾏备份和恢复,以实现出⾊的吞吐量重要说明:虚拟机映像备份的最佳做法是在每个虚拟机上安装VMware ⼯具。
Data Protector产品介绍及许可方案说明书

Product FlyerThe Benefits ofCapacity-Based Licensing:+ Allows for multiple backup copies without increased license costs+ Is a highly scalable and affordable “pay as you-grow”license model+ Enables easy prediction of future license needs witha simpler licensing model+ Allows backup administrators to utilize Data Protector capabilities more fully with expanded featureavailability+ Flexible integrations to easily adapt backup to changing environment requirements+ Introduction of subscription licenses for better cost control, moving from CapEx to OpEx.Data Protector Licenseand Upgrade OverviewThe Data Protector licensing model has evolved to align with our customers’ ever-changing IT environments—hybrid infrastruc-tures, rapidly growing volumes and sources of data, and the com-plexities of operating these systems. The following information will provide you with an overview of the new simplified licensing and pricing models for Data Protector and should help you identify which would be the most suitable for your organization.Why Upgrade?Chances are that the backup processes beingrun have not really changed much in a few yearsor everything seems is to be running fine. Maybethere is some new backup capability requiredin another part of the environment, but that isbeing taken care of with a different, targetedproduct. There is also just the effort and timerequired to be able to validate and install the newupgraded version, something that there neverseems to be enough of. Also, as data backup it-self is not going to drive the business to greaterprofitability or create a better market positiondue to some new or innovative technologyintroduction there is the old saying that couldbe applied, “If it’s not broken, don’t fix it…”.But the reality is that things will have changed,as they always do when dealing with high-tech. Applications have developed; new ap-plications are being introduced; data volumehas increased while backup windows havedecreased; the type of storage is transitioningto a greater hybrid model; and the wider IT envi-ronment is not only evolving but coming underincreasing threat of attack from cyber criminals,not to mention ransomware.So, isn’t it time to re-evaluate your backup envi-ronment? Old, traditional complex, multi licenseinstallations have been replaced with simpler,“All you can eat” capacity and socket licenses.This simplified licensing enables better costvisibility and control, easier compliance, andreduced management.■New functionality can boost performanceand reduce storage use.■In-depth reporting can simplify auditingand compliance and give greater insightto backup operations and optimizations.■Benefit from the latest applicationintegrations and version support.■The latest security updates will deliverthe best defenses against cyber attacksensuring your data backups are fullyprotected as the last line of defenseagainst threats.New Editions of Data Protectorwith Built-In CapabilitiesThe simplified, all inclusive licenses were intro-duced when two new editions of OpenT ext™Data Protector were launched: OpenText™Data Protector Express, specifically designedfor virtual environments, and OpenT ext™ DataProtector Premium for hybrid (virtual and physi-cal) environments. Both editions offer integratedreporting through Data Protector’s web-baseduser interface. With advanced reporting nowbuilt-in, in addition to integrated automationProduct FlyerData Protector License and Upgrade Overviewand monitoring, Data Protector offers all the key tools that businesses need to efficiently man -age their end-to-end backup environment from a single console. Current Data Protector cus -tomers can upgrade to the latest release and migrate to one of the new editions to maximize capabilities and simplify licensing.Now, a third product offering is available using the same front-end, capacity based licens-ing. OpenText™ Data Protector for Cloud Workloads provides backup and recovery ca -pabilities for Microsoft 365, as well as offering wider backup coverage for many hypervisors, clouds and adds container backup to the list.In addition, both Data Protector Premium and Data Protector for Cloud Workloads are now available with subscription pricing.■ Data Protector Express , featuringsocket based pricing, is designed forhighly virtual environments and offered at an optimal price. It includes agentless protection for VMware and Hyper-V workloads and advanced VM recovery features such as granular recovery (GRE), Power On, Live Migrate, and zero downtime backup (ZDB) integration. Standard reporting and analytics are included in the Express edition.■ Data Protector Premium , featuringcapacity-based pricing, is intended for enterprises that need a unified backup and disaster recovery solution forphysical, virtual, and hybrid environments. Data Protector Premium includes the full functionality of Data Protectorincluding software encryption, software deduplication, Block Based Backup, integrations with IT operations tools such as OpenT ext Business ValueDashboard and Operations Orchestration, and integrations with mission-criticalapplications, cloud and storage platforms. Advanced reporting and analytics areincluded in the Premium edition.Table 1. Data Protector Edition Comparison ■ Data Protector for Cloud Workloads , isthe newest addition to the Data Protector lineup and is available for all companies looking for backup protection for Microsoft 365 applications, or who have a wide range of hypervisors or containers to backup, and want to have flexibility in their choice of cloud providers for their storage needs. Licensed in the same way Data Protector Premium based on front-end capacity, both Data Protector Premium and Data Protector for Cloud Workloads capacity licenses are available as a perpetual license or as a subscription for maximum cost flexibility and control.Why Capacity-Based Licensing with Data Protector Premium?■ Scalable —easy to acquire additionalcapacity■ Affordable —pay-as-you-grow licensingmodel■ Predictable —pricing based on yourcurrent and future storage and compute requirements■ Simplified —simplifies management,reduces errors and ensures that you always have what is needed for your environment■ Comprehensive —modernize yourData Protector environment with thelatest advanced backup and recovery capabilities at an optimal priceThe following table illustrates the simplicity, and fully inclusive nature of the capacity-based license. Not only does it simplify cost control, but it provides the full backup capabilities toadd extra value to your backup environment. These capabilities are something that would have required extra licenses, and payment for before. Maybe the extra functionality was dis -regarded due to increased cost but with the Premium capacity license everything is avail-able so that the full benefits and improvements for your backup operations can be discovered.Now Is the Time to Upgrade Y our Data Protector EnvironmentMake the most of your investment in Data Protector and upgrade to take advantage of the latestcapabilities—new features, new integrations and new licensing. See some of the value you will get from your current version when you move to the latest version of Data Protector, and whenyou add Data Protector for Cloud Workloads to your backup environment:Continued on next pageIt’s Easy to Update Y our LicenseContact your local OpenT ext™ sales repre-sentative and let them know you’re interested in upgrading to Data Protector Express or Premium with capacity-based licensing, or if you want to find out more about adding Data Protector for Cloud Workloads to your environ -ment.. Your representative will provide a quote to move you from your existing license to a new license.FAQs about upgrading:Q. I have capacity-based licensing for DataProtector 10.02 or prior—do I need to change my licensing to the Premium edition to get access to the functionality of version 10.10 and on?A.While most functionality is the same there are some differences. Specifically MS SCOM management pack and advanced, fully fea-tured reporting is not included in standard capacity based license (CBL). Encryption is only included in CBL from version 10.10. Also, future releases of Data Protector Pre-mium may contain functionality that is only available with the Premium license so it may be advantageous to discuss moving to Premium with your sales contact.Q.Icurrently have Traditional licenses and would like to move to Data Protector Pre-mium. How do I do this?A.We have a license exchange program al -lowing you to exchange your Traditional licenses for Data Protector Premium li-censes. This exchange will review both the product and maintenance components of the license. Please contact your sales rep for information on this.Q.Ihave multiple copies of my backups, some replicated to another data center, others to the cloud, do I need to license the amount of storage consumed by each copy?A.Data Protector Premium is licensed by TB of front-end capacity protected: i.e., the aggre -gate amount of source data being backed up from all systems; you do not need addi -tional licenses for additional copies of yourbackups.Note: Earlier versions of a release series may not have all capabilities listedFor more information about Data Protector visit the website at: /dataprotector/opentext。
Dell Data Protection Security Tools 安裝指南说明书

Dell Data Protection Security Tools 安裝指南 v1.12註、警示與警告:「註」表示可以幫助您更有效地使用產品的重要資訊。
:「警示」表示有可能會損壞硬體或導致資料遺失,並告訴您如何避免發生此類問題。
:「警告」表示可能的財產損失、人身傷害或死亡。
© 2017 Dell Inc. All rights reserved.Dell、EMC 與其他商標均為 Dell Inc. 或其子公司的商標。
其他商標為其各自所有者的商標。
Registered trademarks and trademarks used in the Dell Data Protection Encryption, Endpoint Security Suite, Endpoint Security Suite Enterprise, and Dell Data Guardian suite of documents: Dell TM and the Dell logo, Dell Precision TM, OptiPlex TM, ControlVault TM, Latitude TM, XPS®, and KACE TM are trademarks of Dell Inc. Cylance®, CylancePROTECT, and the Cylance logo are registered trademarks of Cylance, Inc. in the U.S. and other countries. McAfee® and the McAfee logo are trademarks or registered trademarks of McAfee, Inc. in the US and other countries. Intel®, Pentium®, Intel Core Inside Duo®, Itanium®, and Xeon® are registered trademarks of Intel Corporation in the U.S. and other countries. Adobe®, Acrobat®, and Flash® are registered trademarks of Adobe Systems Incorporated. Authen Tec® and Eikon® are registered trademarks of Authen Tec. AMD® is a registered trademark of Advanced Micro Devices, Inc. Microsoft®, Windows®, and Windows Server®, Internet Explorer®, MS-DOS®, Windows Vista®, MSN®, ActiveX®, Active Directory®, Access®, ActiveSync®, BitLocker®, BitLocker To Go®, Excel®, Hyper-V®, Silverlight®, Outlook®, PowerPoint®, OneDrive®, SQL Server®, and Visual C++® are either trademarks or registered trademarks of Microsoft Corporation in the United States and/or other countries. VMware® is a registered trademark or trademark of VMware, Inc. in the United States or other countries. Box® is a registered trademark of Box. DropboxSM is a service mark of Dropbox, Inc. Google TM, Android TM, Google TM Chrome TM, Gmail TM, YouTube®, and Google TM Play are either trademarks or registered trademarks of Google Inc. in the United States and other countries. Apple®, Aperture®, App StoreSM, Apple Remote Desktop TM, Apple TV®, Boot Camp TM, FileVault TM, iCloud®SM, iPad®, iPhone®, iPhoto®, iTunes Music Store®, Macintosh®, Safari®, and Siri® are either servicemarks, trademarks, or registered trademarks of Apple, Inc. in the United States and/or other countries. GO ID®, RSA®, and SecurID® are registered trademarks of Dell EMC. EnCase TM and Guidance Software® are either trademarks or registered trademarks of Guidance Software. Entrust® is a registered trademark of Entrust®, Inc. in the United States and other countries. InstallShield® is a registered trademark of Flexera Software in the United States, China, European Community, Hong Kong, Japan, Taiwan, and United Kingdom. Micron® and RealSSD® are registered trademarks of Micron Technology, Inc. in the United States and other countries. Mozilla® Firefox® is a registered trademark of Mozilla Foundation in the United States and/or other countries. iOS® is a trademark or registered trademark of Cisco Systems, Inc. in the United States and certain other countries and is used under license. Oracle® and Java® are registered trademarks of Oracle and/or its affiliates. Other names may be trademarks of their respective owners. SAMSUNG TM is a trademark of SAMSUNG in the United States or other countries. Seagate® is a registered trademark of Seagate Technology LLC in the United States and/or other countries. Travelstar® is a registered trademark of HGST, Inc. in the United States and other countries. UNIX® is a registered trademark of The Open Group. VALIDITY TM is a trademark of Validity Sensors, Inc. in the United States and other countries. VeriSign® and other related marks are the trademarks or registered trademarks of VeriSign, Inc. or its affiliates or subsidiaries in the U.S. and other countries and licensed to Symantec Corporation. KVM on IP® is a registered trademark of Video Products. Yahoo!® is a registered trademark of Yahoo! Inc. This product uses parts of the 7-Zip program. The source code can be found at . Licensing is under the GNU LGPL license + unRAR restrictions (/license.txt).章1: 簡介 (5)概觀 (5)章2: 要求條件 (6)驅動程式 (6)用戶端必備項目 (6)軟體 (7)硬體 (8)語言支援 (10)驗證選項 (10)互通性 (11)取消提供及解除安裝 Dell Data Protection | Access (11)取消提供 DDP|A 管理的硬體 (11)解除安裝 DDP|A (12)初始化 TPM (12)清除所有權及啟動 TPM (12)章3: 安裝與啟動 (13)安裝 DDP | Security Tools (13)啟動 DDP | Security Tools (14)章4: 適用 Administrators (17)變更系統管理員密碼與備份位置 (17)設定加密與開機前驗證 (19)變更加密與開機前驗證設定 (21)設定驗證選項 (22)設定登入選項 (22)設定密碼管理員驗證 (24)設定復原問題 (26)設定指紋掃描驗證 (26)設定一次性密碼驗證 (27)設定智慧卡註冊 (28)設定進階權限 (29)智慧卡與生物辨識服務 (選用) (30)管理使用者的驗證 (30)新增新使用者 (31)註冊或變更使用者認證 (31)移除一個已註冊的認證 (33)移除使用者註冊的所有認證 (33)章5: 解除安裝工作 (34)解除安裝 DDP | Security Tools (34)章6: 復原 (36)目錄3自我復原,Windows 登入復原問題 (36)自我復原,PBA 復原問題 (37)自我復原,一次性密碼 (38)章7: 詞彙表 (40)4目錄簡介Dell Data Protection | Security Tools 為 Dell 電腦管理員與使用者提供安全和身分保護。
data protection by design and by default

data protection by design and bydefaultData protection by design and by default (DPbD) is a concept that refers to embedding data protection and privacy safeguards into the design and operation of information systems, technologies, business processes, and organizational structures. This means that data protection measures should be taken into account from the initial conception of a project, rather than being bolted on as an afterthought.DPbD involves considering and addressing the data protection risks and impacts of an initiative in advance, including ensuring that only the necessary data is collected and processed, that the data is accurate and up-to-date, and that the data is kept secure and protected against unauthorized access and disclosure. DPbD should also ensure that individuals have control over their personal data, that data subject rights can be effectively exercised, and that privacy is maintained throughout the lifecycle of the data.The concept of DPbD is reflected in the GDPR, which requires organizations to integrate data privacy considerations into their operations, systems, and services by default, and to ensure that personal data is protected throughout the data processing lifecycle. Failure to implement DPbD can result in significant fines and reputational damage for organizations.。
data protection act 2018 解读 -回复

data protection act 2018 解读-回复关于《数据保护法2018》的解读引言:《数据保护法2018》(Data Protection Act 2018)是英国议会于2018年通过的一项法律,旨在确保个人数据得到妥善保护和合理处理。
该法律对于个人数据的收集、存储、传输、处理等方面做出了明确的规定,同时也规定了处理违规行为的处罚措施。
本文将从以下几个方面逐步解读《数据保护法2018》。
第一部分:背景和目的[200-300字]首先,了解背景和目的是理解《数据保护法2018》的重要前提。
随着数字技术的快速发展和互联网的普及,个人数据的泄露和滥用成为了一个严重的问题。
为了保护个人隐私,维护数据安全,英国政府决定制定《数据保护法2018》。
该法旨在确保个人数据得到适当的处理和保护,同时促进数字经济的发展。
第二部分:重要概念解析[400-500字]在理解《数据保护法2018》的具体规定之前,有必要清楚几个重要的概念。
首先,个人数据是指任何与特定个人相关的信息,例如姓名、地址、手机号码等。
其次,个人数据的控制者是决定个人数据如何处理的实体,例如公司或政府机构。
第三,处理个人数据需要遵循六项原则,即合法性、目的限制、数据最小化、准确性、存储限制和机密性。
最后,数据主体是指个人数据所属的个人,他们有权了解自己的个人数据如何被处理和使用。
第三部分:个人数据的收集和处理[400-500字]《数据保护法2018》对于个人数据的收集和处理做出了明确规定。
首先,个人数据只能在合法和公正的基础上进行收集,并且只能用于特定的目的。
处理个人数据必须遵循数据控制者和数据主体之间的合同和法律义务。
同时,个人数据的处理需要经过数据主体的明确同意,除非有法律明确规定的例外。
在处理个人数据时,必须采取合理的安全措施,防止数据的滥用、泄露或遗失。
第四部分:数据主体的权利[300-400字]《数据保护法2018》赋予了数据主体一系列的权利,以保护他们的个人数据。
cdp是什么

cdp是什么:
持续数据保护。
CDP(Continuous Data Protection,持续数据保护)技术是对传统数据备份技术的一次革命性的重大突破。
传统的数据备份解决方案专注在对数据的周期性备份上,因此一直伴随有备份窗口、数据一致性以及对生产系统的影响等问题。
CDP为用户提供了新的数据保护手段,系统管理者无须关注数据的备份过程(因为CDP系统会不断监测关键数据的变化,从而不断地自动实现数据的保护),而且仅仅当灾难发生后,简单地选择需要恢复到的时间点即可实现数据的快速恢复。
该项技术通过在操作系统核心层中植入文件过滤驱动程序,来实时捕获所有文件访问操作。
对于需要CDP连续备份保护的文件,当CDP管理模块经由文件过滤驱动拦截到其改写操作时,则预先将文件数据变化部分连同当前的系统时间戳(System Time Stamp)一起自动备份到CDP存储体。
从理论上说,任何一次的文件数据变化都会被自动记录,因而称之为持续数据保护。
dpa分析报告

DPA分析报告一、背景介绍数据保护法案(Data Protection Act,简称DPA)是一项旨在保护个人数据的法律法规。
它规定了如何处理、存储和保护个人数据,以及数据主体的权利和隐私保护措施。
本报告旨在对DPA进行分析,以便更好地理解其内容和影响。
二、DPA的核心内容DPA主要包含以下核心内容:1. 数据处理原则DPA强调数据处理应遵循合法、公平、透明、目的限制、数据最小化、准确性、存储限制、安全性和责任制原则。
这些原则确保了个人数据的合理使用和保护。
2. 数据主体权利DPA赋予数据主体一系列权利,包括访问个人数据、更正不准确数据、删除数据、限制处理、数据可携带性和反对自动化决策等。
这些权利为数据主体提供了对其个人数据的控制权。
3. 数据处理责任者与数据处理者DPA明确了数据处理责任者和数据处理者的义务和责任。
数据处理责任者负责确保数据处理符合法律要求,并采取适当的安全措施。
数据处理者作为数据处理责任者的合作伙伴,需遵守其指示并确保数据安全。
4. 数据保护官(DPO)DPA要求某些组织任命数据保护官(DPO),负责监督数据保护事务,并与数据主体、数据处理责任者和监管机构进行沟通。
DPO的职责包括咨询、监督和报告等。
5. 数据传输和跨境流动DPA规定了个人数据传输和跨境流动的条件和限制。
在数据传输和跨境流动过程中,必须保证数据的合法性和安全性。
三、DPA的影响和意义DPA对个人数据的保护提供了明确的法律框架,对个人数据的合理使用和保护起到了重要作用。
它具有以下影响和意义:1. 保护个人隐私权DPA确保个人数据的合法性和透明性,保护个人隐私权。
个人数据只能在符合法律要求的情况下进行处理和使用,个人数据主体拥有对其个人数据的控制权。
2. 促进数据经济发展通过规范和保护数据的处理和跨境流动,DPA促进了数据经济的发展。
合法、安全的数据处理和传输有利于数据驱动的创新和商业发展。
3. 增强数据安全意识DPA强调数据处理责任者的安全责任,促使组织加强数据安全意识和保护措施,防止个人数据的泄露和滥用。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
什么是卷影复制服务(VSS)? 什么是卷影复制服务(VSS)? (VSS)
卷影复制服务 (VSS) 是 Windows Server 2003 中开始引 入的一项新服务, Vista。 入的一项新服务,它同样适用于 Windows Vista。它实质上是 一个框架,可推动应用程序、 一个框架,可推动应用程序、存储子系统与存储管理应用程序 之间的通信,以定义、保留和利用存储数据的时间点副本。 之间的通信,以定义、保留和利用存储数据的时间点副本。 卷影复制是一项服务, 卷影复制是一项服务,它提供文件系统更改跟踪和数据存 中诸如“以前的版本” 储,以支持 Windows Vista 中诸如“以前的版本”和“系统 还原”等功能。 还原”等功能。 简单地说,只要您对文件进行了更改, 简单地说,只要您对文件进行了更改,VSS 就会为文件 的已更改部分保留一个副本。 的已更改部分保留一个副本。只保存文件的已更改部分使得 能够有效地利用磁盘空间。 VSS 能够有效地利用磁盘空间。
• Vista 数据移植 Windows 轻松传送 数据移植—Windows
Placeholder-presentation title | 6 April, 2006 Lenovo Confidential | © 2006 Lenovo Page 3 of 12
为什么要做备份
• 为了防止可能发生的数据丢失问题,应定期进行备份并 为了防止可能发生的数据丢失问题, 维护这些备份 • Windows Vista 提供了一个新的备份和还原中心,这是 提供了一个新的备份和还原中心, 管理备份设置的集中位置,从而大大简化了此过程。 管理备份设置的集中位置,从而大大简化了此过程。在 备份和还原中心内, 备份和还原中心内,可以备份新的文件和文件夹或者备 份整个系统,可以从备份中还原文件, 份整个系统,可以从备份中还原文件,还可以制定备份 计划, 计划,使备份自动进行 • 注意:Windows Vista Starter 或 Windows Vista 注意: Home Basic 中不包括设置自动备份的功能
Placeholder-presentation title | 6 April, 2006 Lenovo Confidential | © 2006 Lenovo Page 16 of 12
为什么我找不到一些文件的卷影副本? 为什么我找不到一些文件的卷影副本?
有几个可能的原因: 有几个可能的原因: • 可能未打开那个硬盘的“系统保护”。如果没有打开“系 可能未打开那个硬盘的“系统保护” 如果没有打开“ 统保护” 无法创建卷影副本。 统保护”,Windows 无法创建卷影副本。 • 打开“系统保护”的步骤 打开“系统保护” –单击打开“系统”。 单击打开“ 单击打开 系统” –在左侧窗格中,单击“系统保护”。如果系统提示您输 在左侧窗格中, 在左侧窗格中 单击“系统保护” 入管理员密码或进行确认,请键入密码或提供确认。 入管理员密码或进行确认,请键入密码或提供确认。 –在“自动还原点”下,选择要打开“系统保护”的卷旁 选择要打开“系统保护” 在 自动还原点” 边的复选框,然后单击“确定” 边的复选框,然后单击“确定”。 • 文件可能是脱机文件。脱机文件是存储在共享网络文件夹 文件可能是脱机文件。 上的文件的副本。卷影副本对脱机文件不可用。 上的文件的副本。卷影副本对脱机文件不可用。如果计算 机位于公司网络上, 机位于公司网络上,网络管理员可能禁用了卷影副本
Placeholder-presentation title | 6 April, 2006 Lenovo Confidential | © 2006 Lenovo Page 13 of 12
什么是以前版本? 什么是以前版本?
• 以前版本是备份副本(使用备份文件向导备份的文件和文 以前版本是备份副本( 件夹的副本)或卷影副本( 件夹的副本)或卷影副本(Windows 自动保存为还原点一 部分的文件和文件夹的副本)。( )。(卷影副本可以是计算机 部分的文件和文件夹的副本)。(卷影副本可以是计算机 上的文件的副本或者网络计算机上的共享文件的副本。) 上的文件的副本或者网络计算机上的共享文件的副本。) 可以使用以前版本的文件还原意外修改、 可以使用以前版本的文件还原意外修改、删除或损坏的文 根据文件或文件夹的类型,可以打开、 件。根据文件或文件夹的类型,可以打开、保存到其它位 或者还原以前版本。 置,或者还原以前版本。
整个计算机
Windows Complete PC备份
首次设置计算机时,应该创建 Windows Complete PC 备份映像;
Placeholder-presentation title | 6 April, 2006 Lenovo Confidential | © 2006 Lenovo Page 7 of 12
存储备份的方法
• 可以将文件备份到以下任意存储类型
–硬盘(内部或外部) 硬盘(内部或外部) 硬盘 –其它可移动磁盘 其它可移动磁盘 –可写 DVD 和 CD 可写 –网络资源 网络资源
Placeholder-presentation title | 6 April, 2006 Lenovo Confidential | © 2006 Lenovo Page 8 of 12
Home Premium
Ultimate
手动备份和恢复用户文件
是
是
是
将用户文件备份到网络共享
否
是
是
自动备份用户文件
否
是
是
基于完整 PC 映像的备份和恢复
否
否
是
Placeholder-presentation title | 6 April, 2006 Lenovo Confidential | © 2006 Lenovo Page 5 of 12
Placeholder-presentation title | 6 April, 2006 Lenovo Confidential | © 2006 Lenovo Page 11 of 12
VSS处理流程 VSS处理流程
• VSS处理映射拷贝,需要协调各个模块来完成,从而保证 VSS处理映射拷贝 需要协调各个模块来完成, 处理映射拷贝, 创建出高保真的拷贝,进而实现数据的一致性, 创建出高保真的拷贝,进而实现数据的一致性,其具体 步骤如下图所示: 步骤如下图所示:
如何进入备份和还原中心
• 开始 控制面板 系统和维护 备份和还原中心
Placeholder-presentation title | 6 April, 2006 Lenovo Confidential | © 2006 Lenovo Page 6 of 12
备份文件和备份整个计算机
备份 个人文件 使用 备份文件向导 使用时间 应该定期备份您创建和修改的文件。最好在进 行任何系统更改前备份文件;
Placeholder-presentation title | 6 April, 2006 Lenovo Confidential | © 2006 Lenovo Page 2 of 12
课程目录
• Vista 数据保护 备份和还原中心 数据保护—备份和还原中心
–备份文件和备份计算机 备份文件和备份计算机 –存贮备份的方法 存贮备份的方法 –什么是卷影服务 什么是卷影服务 –卷影服务的原理 卷影服务的原理 –还原备份 还原备份 –完全备份演示 完全备份演示 –备份文件演示 备份文件演示 –还原文件演示 还原文件演示
Placeholder-presentation title | 6 April, 2006 Lenovo Confidential | © 2006 Lenovo Page 12 of 12
如何创建卷影副本
• 打开“系统保护”的步骤: 打开“系统保护”的步骤: –单击打开“系统” 单击打开“ 单击打开 系统” –在左侧窗格中,单击“系 在左侧窗格中, 在左侧窗格中 单击“ 统保护” 统保护”. 如果系统提示 您输入管理员密码或进行 确认, 确认,请键入密码或提供 确认。 确认。 –在“自动还原点”下,选 在 自动还原点” 择要打开“系统保护” 择要打开“系统保护”的 磁盘旁边的复选框, 磁盘旁边的复选框,然后 单击“确定” 单击“确定”。
Placeholder-presentation title | 6 April, 2006 Lenovo Confidential | © 2006 Lenovo Page 4 of 12
不同版本中的Vista备份功能之间的区别 不同版本中的Vista备份功能之间的区别 Vista
备份功能
Home Basic
数据保护和数据移植
--Vista --Vista Data Protection and Data Migration
Hosted By Author name – department Month/Year
Lenovo Confidential | © 2006 Lenovo
课程目录
• Vista 数据保护 备份和还原中心 数据保护—备份和还原中心 • Vista 数据移植—Windows 轻松传送 数据移植 Windows
• 可写光盘
–还可以将文件保存到 DVD 或 CD。确保光盘可写,即可以添加、 还可以将文件保存到 CD。确保光盘可写,即可以添加、 删除或更改内容。 删除或更改内容。
Placeholder-presentation title | 6 April, 2006 Lenovo Confidential | © 2006 Lenovo Page 9 of 12
Placeholder-presentation title | 6 April, 2006 Lenovo Confidential | © 2006 Lenovo Page 14 of 12
如何访问以前版本的文件和文件夹? 如何访问以前版本的文件和文件夹?
