HttpWatch 7.0 帮助文档整理
client帮助文档

前言超文本传输协议(HTTP)也许是当今互联网上使用的最重要的协议了。
Web服务,有网络功能的设备和网络计算的发展,都持续扩展了HTTP协议的角色,超越了用户使用的Web 浏览器范畴,同时,也增加了需要HTTP协议支持的应用程序的数量。
尽管包提供了基本通过HTTP访问资源的功能,但它没有提供全面的灵活性和其它很多应用程序需要的功能。
HttpClient就是寻求弥补这项空白的组件,通过提供一个有效的,保持更新的,功能丰富的软件包来实现客户端最新的HTTP标准和建议。
为扩展而设计,同时为基本的HTTP协议提供强大的支持,HttpClient组件也许就是构建HTTP客户端应用程序,比如web浏览器,web服务端,利用或扩展HTTP协议进行分布式通信的系统的开发人员的关注点。
1. HttpClient的范围基于HttpCore[/httpcomponents-core/index.html]的客户端HTTP运输实现库基于经典(阻塞)I/O内容无关2. 什么是HttpClient不能做的HttpClient 不是一个浏览器。
它是一个客户端的HTTP通信实现库。
HttpClient的目标是发送和接收HTTP报文。
HttpClient不会去缓存内容,执行嵌入在HTML页面中的javascript 代码,猜测内容类型,重新格式化请求/重定向URI,或者其它和HTTP运输无关的功能。
第一章基础1.1 执行请求HttpClient 最重要的功能是执行HTTP方法。
一个HTTP方法的执行包含一个或多个HTTP 请求/HTTP响应交换,通常由HttpClient的内部来处理。
而期望用户提供一个要执行的请求对象,而HttpClient期望传输请求到目标服务器并返回对应的响应对象,或者当执行不成功时抛出异常。
很自然地,HttpClient API的主要切入点就是定义描述上述规约的HttpClient接口。
这里有一个很简单的请求执行过程的示例:HttpClient httpclient = new DefaultHttpClient();HttpGet httpget = new HttpGet("http://localhost/");HttpResponse response = httpclient.execute(httpget);HttpEntity entity = response.getEntity();if (entity != null) {InputStream instream = entity.getContent();int l;byte[] tmp = new byte[2048];while ((l = instream.read(tmp)) != -1) {}}1.1.1 HTTP请求所有HTTP请求有一个组合了方法名,请求URI和HTTP协议版本的请求行。
安卓HttpClient+Jsoup+Httpwatch模拟登陆正方教务获取信息
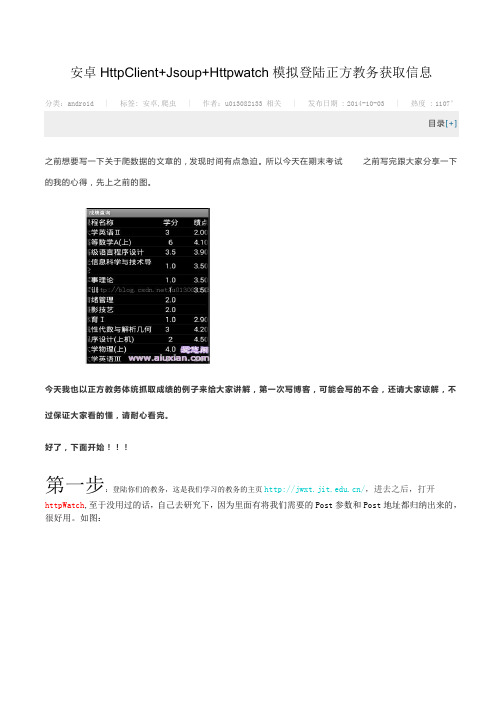
安卓HttpClient+Jsoup+Httpwatch模拟登陆正方教务获取信息分类: android | 标签: 安卓,爬虫| 作者: u013082133 相关| 发布日期 : 2014-10-03 | 热度 : 1107°目录[+]之前想要写一下关于爬数据的文章的,发现时间有点急迫。
所以今天在期末考试之前写完跟大家分享一下的我的心得,先上之前的图。
今天我也以正方教务体统抓取成绩的例子来给大家讲解,第一次写博客,可能会写的不会,还请大家谅解,不过保证大家看的懂,请耐心看完。
好了,下面开始!!!第一步:登陆你们的教务,这是我们学习的教务的主页/,进去之后,打开httpWatch,至于没用过的话,自己去研究下,因为里面有将我们需要的Post参数和Post地址都归纳出来的,很好用。
如图:进去之后你会看见HttpWatch刷刷的,出来一大片数据,当然我们的从当中挑选出有用的数据。
如图,我们打开上栏中的第一列标签,就是横线的地方。
首先我们来观看下数据,请求方法:post,状态值:302,请求的URL:/default2.aspx。
然后,我们来观察下面大圈圈中的数据,这里是Post所带的参数,里面有__ViewStat(我也不知道是什么,不过一起带着Post就好了,这里有个情况,我等会在下面讲,先用绿色标记),Button的值(乱码),lbLanguage(不管,先记下),RadioButtonList1(单选按钮:学生...),TextBox1:账号,TextBox2:密码。
Ok.......下面我们来看一下Button和lbLanguage和RadioButtonList1具体的值,下面的标签打开Stream,如图:看,里面有一些不认识的参数的值。
Button="" ,lbLanguage="",RadioButtonList1="%D1%A7%C9%FA",哦了。
TRSWCM7.0Fix自动更新手册

内容协作平台Array TRS WCMFIX自动更新手册V 7.0北京拓尔思信息技术股份有限公司Beijing TRS Information Technology Co., Ltd.版权说明本手册由北京拓尔思信息技术股份有限公司(以下简称TRS公司)出版,版权属TRS公司所有。
未经出版者正式书面许可,不得以任何方式复制本文档的部分或全部内容。
©北京拓尔思信息技术股份有限公司版权所有。
保留所有权利。
是北京拓尔思信息技术股份有限公司的注册商标。
关于本手册本手册旨在指导TRS WCM V7.0用户完成WCM的FIX自动更新。
读者对象本手册读者对象为使用TRS WCM V7.0的使用者。
用户反馈TRS公司感谢您使用TRS 产品。
如果您发现本手册中有错误或者产品运行不正确,或者您对本手册有任何意见和建议,请及时与TRS公司联系。
您的意见将是我们做版本修订时的重要依据。
目录第1章概述 (1)1.1 背景 (1)1.2 适用版本 (1)第2章FIX自动更新 (2)2.1 环境准备 (2)2.1.1 更新过程中确保应用不重启 (2)2.1.2 服务器部署Ant (2)2.2 更新FIX步骤 (2)2.2.1 在线更新 (3)2.2.2 离线更新 (3)2.3 更新FIX过程解读 (3)2.3.1 更新检测页面 (3)2.3.2 更新标识含义 (4)2.3.3 更新结果信息 (5)2.3.4 冲突文件信息 (5)2.3.5 手工部署操作信息 (6)第3章常见问题 (7)3.1 在更新过程中关掉页面或者更新完后未做手工操作、冲突文件比较等怎么办? (7)3.2 在离线更新的模式下,向服务器端请求的时间很久怎么办? (7)第1章概述1.1 背景TRSWCMV7_Build1015_6612_20130506 版本发布后,维护过程中问题的处理都以FIX包的方式提供,而项目手工更新FIX会带来一系列的问题:更新不完整、数据库脚本需要手工执行、多个FIX需要依次手工操作、项目定制的冲突文件无法智能化检测等问题,为了避免这些问题,产品组提供了自动更新FIX工具。
iwr命令用法-概述说明以及解释

iwr命令用法-概述说明以及解释1.引言1.1 概述概述:在计算机科学领域中,iwr命令是一个强大的工具,用于进行网络请求和获取网络上的数据。
该命令是PowerShell中的一个内置命令,可用于发送HTTP、HTTPS、FTP等协议的请求,并获取返回的数据。
它可以用于自动化任务、数据采集、网页爬虫等多种应用场景。
iwr命令提供了一种简便的方式来与网络进行交互。
通过发送HTTP 请求,我们可以从远程服务器获取数据,也可以向服务器发送数据。
它支持GET、POST、PUT、DELETE等常用的HTTP请求方法,并可以通过自定义HTTP头部和请求体来满足各种需求。
此外,iwr命令还支持对FTP 服务器进行文件传输操作。
除了基本的请求功能,iwr命令还提供了一些高级用法。
它可以与PowerShell的其他命令和模块进行结合,实现更加复杂的操作。
例如,可以通过iwr命令下载远程文件,并对其进行处理或解析。
还可以使用iwr 命令与API进行对接,实现自动化数据采集和处理。
然而,虽然iwr命令功能强大,但也存在一些局限性。
首先,它依赖于网络连接,如果网络不稳定或不可用,可能会导致请求失败。
其次,对于一些复杂的请求场景,iwr命令可能无法满足需求,需要借助其他工具或编程语言来完成。
另外,使用iwr命令进行大规模的请求时,需要注意机器的性能和网络负载,避免影响其他正常的网络请求。
尽管如此,iwr命令在网络请求和数据获取方面仍具有广泛的应用前景。
随着互联网的快速发展和数据的日益重要,对于网络数据的获取和处理需求也越来越高。
使用iwr命令可以简化这一过程,提高效率,为后续的数据分析和挖掘提供便利。
总的来说,iwr命令是一个功能丰富的网络请求工具,它的简单易用和强大灵活使其成为众多开发者和系统管理员的首选工具之一。
通过深入了解iwr命令的用法,我们可以更好地利用它在各种场景下进行网络请求和数据获取。
在不断改进和学习的过程中,我们可以更好地应对日益增长的网络数据需求,推动科技的进步和应用的创新。
IIS 7开发与管理完全参考手册说明书

图书基本信息书名:《IIS 7开发与管理完全参考手册》13位ISBN编号:978730220377310位ISBN编号:7302203776出版时间:2009-7出版社:清华大学出版社作者:[美] Ken Schaefe,Jeff Cochran页数:799译者:颜炯版权说明:本站所提供下载的PDF图书仅提供预览和简介以及在线试读,请支持正版图书。
更多资源请访问:前言WindowsServer2008是微软公司最新开发的服务器操作系统,提供了全新的InternetInformationServices7.0。
IIS7.0的基本工作机制已经进行了全新的设计,是一个完全模块化的Web服务器,易于部署,易于配置,因而大大提高了产品的可用性。
安全性和性能,同时,IIS7.0与紧密结合,大大扩展了IIS 的功能。
此外,IIS7.0还提供了全新的FTP服务程序,并提供了对FastCGI的支持,还具备了全新的实时诊断和错误定位功能。
因此,对于IIS管理人员和开发人员来说,为了充分利用IIS7.0的新特性,必须深入掌握更多的新知识。
本书正是基于上述原因编写的。
本书介绍了IIS7.0的新特性,并关注如何最有效地利用IIS7.0的新特性。
通过学习本书的内容,读者可以掌握如何部署。
使用和管理IIS7.0,并且学会如何在企业级系统中操作IIS7.0。
本书面向的主要读者是IIS管理人员以及应用IIS的技术人员。
因此,本书不仅仅关注IIS的各项功能,也不仅仅关注于如何利用某个图形用户界面或命令行管理工具配置这些功能,更重要的是:本书详细解释了IIS各项功能的内部工作原理,这样,当系统发生错误时,读者可以迅速找到错误的根源。
此外,因为许多IIS管理人员需要具备将常用过程自动化的能力,所以,本书的某些章节讨论了如何通过编程方式完成IIS管理工作,同时,还给出了大量的代码示例。
本书还介绍了在应用IIS过程中与高可用性。
WebFarm,以及IIS扩展等有关的内容,并且用一章的篇幅介绍如何进行错误定位和诊断。
WES7 定制手册
Windows Embedded Standard 2011 CTP2 Lab ManualWindows Embedded Standard 2011 – CTP2 Lab ManualTable of Contents1 Preparing to Use Windows Embedded Standard 2011 ...................................................................... 5 1.1 1.2 1.3 1.4 1.5 1.6 Introduction .............................................................................................................................. 5 Related Windows 7 Documentation .......................................................................................... 5 Minimum Device Hardware Requirements ................................................................................ 5 Release Notes ........................................................................................................................... 5 Install Windows Embedded Standard 2011 Toolkit .................................................................... 6 1.5.1 1.6.1 1.6.2 1.7 1.7.1 1.7.2 2 2.1 Open Windows Embedded Standard 2011 Toolkit Help .................................................. 6 Make Your Utility Disk Bootable ..................................................................................... 7 Add Image Builder Wizard to Your Utility Disk ................................................................ 7 Create a Windows PE Utility Disk with Image Configuration Editor ................................. 8 Create a Custom Windows PE Image .............................................................................. 8 Create a Utility Drive ................................................................................................................. 7Create a Windows Preinstallation Environment Utility Drive (Optional) ..................................... 8Build Windows Embedded Standard 2011 Images ............................................................................ 9 Build a Windows Embedded Standard 2011 Image with Image Builder Wizard .......................... 9 2.1.1 2.1.2 2.2 2.2.1 2.2.2 2.2.3 2.2.4 2.2.5 2.2.6 2.2.7 Build a Thin Client Image with Embedded Enabling Features .......................................... 9 Build an Image with Embedded Core Only .................................................................... 11 Build a Thin Client Image with Custom Settings ............................................................ 11 Add Update Packages to a Distribution Share (Optional) .............................................. 14 Add Third-Party Software (Optional) ............................................................................ 15 Run a Custom Script (Optional) .................................................................................... 16 Add Third-Party Drivers (Optional) ............................................................................... 17 Make Your Install Fully Unattended (Optional) ............................................................. 17 Create Image Builder Wizard Disk from Answer File (optional) ..................................... 24Build a Windows Embedded Standard 2011 Image Using Image Configuration Editor ............. 113Deploy an Image ............................................................................................................................ 25 3.1 Prepare and Capture an Image for Deployment ...................................................................... 25 3.1.1 3.1.2 3.2 3.2.1 3.2.2 Sysprep the Image........................................................................................................ 25 Capture the Image Into a Windows Image (.wim) File................................................... 25 Prepare your Destination Device .................................................................................. 26 Apply an Image to Your Device’s Hard Drive ................................................................. 27Page 2Deploy an Image Using ImageX ............................................................................................... 26©2009 Microsoft. All Rights Reserved.Windows Embedded Standard 2011 – CTP2 Lab Manual3.2.3 3.3 3.3.1 3.3.2 4 4.1Shut Down the Destination Device ............................................................................... 27 Start Image Builder Wizard with your Image ................................................................ 28 Customize a Captured Image ........................................................................................ 29Deploy an Image Using Image Builder Wizard.......................................................................... 27Service an Image ............................................................................................................................ 31 Service an Image with Image Configuration Editor and DISM................................................... 31 4.1.1 4.1.2 4.1.3 4.2 4.2.1 4.2.2 4.2.3 4.2.4 4.2.5 4.2.6 4.3 4.4 Create a Configuration Set using Image Configuration Editor........................................ 31 Install using your Configuration Set .............................................................................. 32 Test your image ........................................................................................................... 34 Mount your image ....................................................................................................... 34 Add sample packages ................................................................................................... 34 Adding a Package Using DISM ...................................................................................... 35 Unmount and Commit Changes .................................................................................... 35 Redeploy and Verify ..................................................................................................... 35 Add a Language Pack (optional).................................................................................... 35Service an Image with DISM .................................................................................................... 34Install Updates with WUSA...................................................................................................... 36 Service an Image with Package Scanner .................................................................................. 36 4.4.1 4.4.2 4.4.3 Package Enumeration................................................................................................... 37 Find Applicable Updates ............................................................................................... 37 Scavenging ................................................................................................................... 375Additional Windows Embedded Standard 2011 Labs ...................................................................... 39 5.1 Suppress OOBE ....................................................................................................................... 39 5.1.1 5.1.2 5.2 5.2.1 5.2.2 5.2.3 5.2.4 5.2.5 5.3 5.3.1 5.3.2 5.4 Create an Answer File .................................................................................................. 39 Using your answer file with Image Builder Wizard ........................................................ 39 Hide boot screens ........................................................................................................ 40 Use Shell Launcher ....................................................................................................... 40 Remove Windows branding ......................................................................................... 41 Replace the startup screen background image ............................................................. 41 Add Message Blockers.................................................................................................. 42 Install from Image Builder Wizard directly to UFD : ...................................................... 44 Install from Image Builder Wizard to Hard Drive, ImageX to UFD: ................................. 44Using a Custom Shell and Custom Branding............................................................................. 40Build a USB bootable Windows Embedded 2011 image ........................................................... 44Create Custom Templates for IBW .......................................................................................... 46©2009 Microsoft. All Rights Reserved. Page 3Windows Embedded Standard 2011 – CTP2 Lab Manual5.4.1 5.4.2Creating Templates ...................................................................................................... 46 Using Custom Templates in IBW ................................................................................... 46©2009 Microsoft. All Rights Reserved.Page 4Windows Embedded Standard 2011 – CTP2 Lab Manual1 Preparing to Use Windows Embedded Standard 20111.1 IntroductionWelcome to Windows Embedded Standard 2011. This lab manual is a guide to help you use and evaluate Windows Embedded Standard 2011. In addition to preparation steps, such as toolkit installation, this manual includes labs for key scenarios such as building an image, deploying an image and servicing an image. The labs are most easily followed in the order presented. You can also chose labs individually based on your interests and previous experience with Windows Embedded, but please note that several lab scenarios assume you have the output of an earlier lab scenario.1.2 Related Windows 7 DocumentationWindows Embedded Standard 2011 is based on Windows 7; therefore much of the Windows 7 documentation can be used as reference material. • Windows 7 Automated Installation Kit (Windows AIK) online documentation /downloads/details.aspx?FamilyID=f1bae135-4190-4d7c-b19319123141edaa&displaylang=en Windows 7 Technical Library on Microsoft TechNet /enus/library/dd349342.aspx Windows Developer Center for Windows 7 /enus/windows/dd433113.aspx• •1.3 Minimum Device Hardware RequirementsYou must have the following minimum hardware to be able to build a Windows Embedded Standard 2011 image on your device: • • • • • 1 GHz x86 or amd64 processor 1 GB of flash or hard drive space (4 GB recommended) 512 MB of RAM (1 GB recommended for amd64 devices) 900 MHz CPU or equivalent At least one of the following bootable media types: • • • • Bootable DVD-ROM drive Bootable USB 2.0 port and a USB Flash Drive (UFD) with 4 GB free space, or access to a local networkBIOS supporting Windows Preinstallation Environment (Windows PE) 3.0 Minimum hardware requirements, particularly RAM requirements, may be greater depending on the size and type of feature packages selected.1.4 Release NotesAlthough every attempt has been made to provide workarounds and additional usage notes for scenarios that are affected by known issues in the pre-release versions of Windows Embedded Standard 2011, we strongly recommend that you refer to the release notes provided with this release before beginning any of the labs described in this manual. ©2009 Microsoft. All Rights Reserved. Page 5Windows Embedded Standard 2011 – CTP2 Lab Manual1.5 Install Windows Embedded Standard 2011 ToolkitYou can install Windows Embedded Standard 2011 Toolkit on your development computer from a DVD or from setup files downloaded from Microsoft Connect. 1. Run Setup.exe • If you have the Windows Embedded Standard 2011 Toolkit DVD, installation should begin when you insert the DVD into the DVD drive. If it doesn’t start automatically, the Setup.exe file can be found at: <DVD Drive>:\WindowsEmbeddedStudio.msi. 2. On the Setup Type page, do one of the following: • To install the tools and distribution share to the default location, select Complete. The default locations are: • • • 3. 32-bit operating system: [System Drive]:\Program Files\Windows Embedded Standard 2011 64-bit operating system: [System Drive]:\Program Files(x86)\Windows Embedded Standard 2011To install the tools and distribution share to a different location, select Custom.Follow the instructions in the installation wizard to complete the installation process.1.5.1 Open Windows Embedded Standard 2011 Toolkit HelpThe Windows Embedded Standard 2011 Toolkit Help contains more detailed information on many of the topics and steps contained in this manual. To access the Windows Embedded Standard 2011 Toolkit Help: 1. Start Image Configuration Editor on your development computer • 2. From the Start menu, click Programs, click Windows Embedded Standard 2011, and then click Image Configuration Editor.On the toolbar, click the Help icon to launch Help.©2009 Microsoft. All Rights Reserved.Page 6Windows Embedded Standard 2011 – CTP2 Lab Manual1.6 Create a Utility DriveIf your device is able to boot from a DVD, you can use the Windows Embedded Standard 2011 DVD appropriate to your device’s architecture to install the OS image directly to your device. Otherwise you can create a bootable USB drive by using the DiskPart tool and then loading the USB Drive with Image Builder Wizard (IBW) or WindowsPreinstallation Environment (WinPE). Diskpart supports the partitioning and formatting of a USB Flash Device (UFD) as a bootable device. A USB drive with a minimum of 4 GB is recommended for a utility drive loaded with Image Builder Wizard.1.6.1 Make Your Utility Disk Bootable1. 2. Attach your USB drive to your development computer. From a Windows Vista, Windows 7 or Windows Preinstallation (Windows PE) 3.0 environment, run the DiskPart tool by typing the following at a command prompt: diskpart Note: The version of the DiskPart tool provided by Windows Vista, Windows 7 and Windows PE 2.0, 2.1 and 3.0 supports the partitioning and formatting of a UFD as a bootable device. Previous versions of the DiskPart tool, including the version provided by Windows XP, do not fully support partitioning and formatting a UFD to be bootable and should not be used. 3. Use the DiskPart tool to determine the disk number and device size to be used for the next step by typing the following at the DiskPart prompt: list disk 4. Use the DiskPart tool to partition and format the drive and make it bootable. At the DiskPart prompt, type the following, replacing <disk_number> with the disk number of the USB drive: select clean create select active format assign exit disk <disk_number> part pri part 1 fs=ntfs quickYour USB drive is now bootable.1.6.2 Add Image Builder Wizard to Your Utility DiskThe Image Builder Wizard disks provide the ability to quickly generate a new IBW disk in the event IBW has been serviced or new packages have been added to the distribution share. To generate an Image Builder Wizard Disk:©2009 Microsoft. All Rights Reserved.Page 7Windows Embedded Standard 2011 – CTP2 Lab Manual 1. Start Image Configuration Editor on your development computer • 2. 3. 4. 5. 6. From the Start menu, selectPrograms, selectWindows Embedded Standard 2011, then selectImage Configuration Editor.On the Tools menu, select Media Creation, then select Create IBW Disk Enter the desired distribution share to be copied. Select your USB drive as the target folder. Select the desired disk architecture. Click OK.1.7 Create a Windows Preinstallation Environment Utility Drive (Optional)In some instances, you may want to create a utility disk that includes the Windows Preinstallation Environment (Windows PE). Windows PE is a lightweight version of Windows used mainly for deployment. You may prefer to use Windows PE instead of Image Builder Wizard if your USB drive is smaller than 2 GB, if you have space limitations on your device or if your device requires custom drivers that you will install on a custom version of Windows PE.1.7.1 Create a Windows PE Utility Disk with Image Configuration EditorThe Windows PE Utility Disk feature of the Media Creation tool in Image Configuration Editor provides the ability to quickly generate a Windows PE disk for gathering information about your target device or for deploying an image using Image Builder Wizard. The generated disk includes TAP.exe, ImageX and Package Scanner. To generate a Windows PE utility disk: 1. 2. Create a bootable utility disk (section 1.6.1 above). Start Image Configuration Editor on your development computer • 3. 4. 5. 6. 7. From the Start menu, selectPrograms, selectWindows Embedded Standard 2011, then selectImage Configuration Editor.On the Toolsmenu, selectMedia Creation, then selectCreate PE Image. Enter a target folder on your development computer to which the binaries will be copied. Select the desired disk architecture. Click OK. Copy the contents of the ISO sub-folder from the target folder on your development computer to the root directory of your bootable utility disk.1.7.2 Create a Custom Windows PE ImageSee the topic “Create a Custom Windows PE Image” in the Windows Embedded Standard 2011 Toolkit Help for more information about creating a custom Windows PE Image and gathering other files to add to the bootable USB drive you created in section 1.6.1.©2009 Microsoft. All Rights Reserved.Page 8Windows Embedded Standard 2011 – CTP2 Lab Manual2 Build Windows Embedded Standard 2011 Images2.1 Build a Windows Embedded Standard 2011 Image with Image Builder WizardImage Builder Wizard (IBW) is a tool you can use to create, configure and install Windows Embedded Standard 2011 on your device. The wizard runs directly on your device and guides you through a set of configuration choices. After you make your selections, the wizard creates and installs Windows Embedded Standard 2011 onto the device. You can further customize the installation or you can capture it to an image file and deploy it to other devices. In this lab, you will use IBW on your device to create different Windows Embedded Standard 2011 images. You can follow the steps provided in this lab to create the following variations: • • An image that can be used for a thin client device. A “minboot” image that contains only the base packages (referred to as Embedded Core).2.1.1 Build a Thin Client Image with Embedded Enabling FeaturesTo build a thin client image using IBW: 1. Start Image Builder Wizard on your device by either: • • Start the wizard from your Windows Embedded Standard 2011 DVD, your ISO image, or the USB drive prepared in section 1.6 Boot your device into Windows PE and run setup.exe from another location (USB drive, network share, etc.). Note: Image Builder Wizard will setup and install Windows Embedded Standard 2011. It’s important to make sure you are running the wizard on your device itself and not on your development computer. 2. On the first page, select Build an Image This option starts IBW and allows you to choose packages, drivers and languages to include in your image. You can optionally start from a template. 3. 4. Accept the End User License Agreement (EULA). The Choose the way you want to build your image page allows you to start from a template or from a blank configuration. In this exercise, select the Thin Client template and click Next. Select a language, time and currency format and keyboard or input method to install on the final image. These selections are for the primary language of your image. You can add additional languages later. Click Next to continue. The Summary of Drivers and Features page shows a summary of the drivers to be installed, detected devices and feature packages in your template. Check the Modify Drivers and Modify Features checkboxes and click Next.5.6.©2009 Microsoft. All Rights Reserved.Page 9Windows Embedded Standard 2011 – CTP2 Lab Manual 7. On the Find and Select Drivers page, choose one of the following options and click Next to continue: • • The Automatically detect devices option detects the drivers on your device and attempts to find drivers for them. The Choose a PMQ option makes it possible for you to import a device list from a previously generated PMQ file. As with Windows Embedded XP, TAP.exe is used to generate this PMQ file. The Do not select additional drivers option includes only the drivers in Embedded Core. Your image will still be bootable but drivers for non-boot-critical devices may not be installed.•8.The Confirm drivers to be installed page shows drivers that will be installed as well as the devices that were detected on your computer for which we do not have drivers. Click Browse if you want to add custom drivers. Click Next to continue. On the Please select Feature Packagesto include in your image page you can add additional features to your configuration. Because you started from the Thin Client template, several packages have been preselected for you. Choose any additional packages you wish to include.9.10. Determine which type of write filters you want to use for your thin client and select the appropriate feature packages. To use File Based Write Filter (FBWF) and Registry Filter, select: • • OR To use Enhanced Write Filter (EWF), Hibernate Once Resume Many (HORM) and Registry Filter, select: • • • Embedded Enabling Features\Enhanced Write Filter with HORM Embedded Enabling Features\Registry Filter Boot Environments\Enhanced Write Filter Boot Environment Note: Although EWF can be used without HORM, using HORM requires EWF. Adding EWF in IBW (without an answer file) will configure all existing volumes to be protected in RAM-REG mode; however EWF will be disabled for all of them. 11. Click the Resolve Dependencies button. If a pop-up window asks you to choose between multiple packages, make the following selections: a. If you are installing HORM, select Embedded Windows 7 Boot Environment, otherwise select the Windows 7 Boot Environment. • • • Select Windows Embedded Standard Startup Screens. Select Windows Explorer. Select Standard Windows USB Stack. Embedded Enabling Features\File Based Write Filter (FBWF) Embedded Enabling Features\Registry Filter©2009 Microsoft. All Rights Reserved.Page 10Windows Embedded Standard 2011 – CTP2 Lab Manual b. Resolve all other dependencies, then click Done. Click Next to continue.12. The Summary of Drivers and Features page gives you a final overview of packages and drivers to be installed. If you are satisfied with your selections, click Next. 13. Select the disk or partition where you would like to install the image, then click Next to begin installation and set up of the customized Windows Embedded Standard 2011 image on your device. 14. To enable Embedded Enabling Features after installation is complete, open a command prompt on your device and run the following commands: • For FBWF and Registry Filter: fbwfmgr /enable fbwfmrg /addvolume c: • For EWF, HORM and Registry Filter: ewfmgr c: -enable ewfmgr c: -activatehorm 15. Once HORM has been activated, it should be tested: a. b. c. d. e. f. Reboot so that EWF is enabled. Start Internet Explorer Enable hibernation by typing the following at a command prompt: powercfg –h on Reboot and device should resume from hibernation. Make changes and reboot your device again Verify your device state returns to that of step d above and that the changes made in step e were not retained.2.1.2 Build an Image with Embedded Core OnlyA Windows Embedded Standard 2011 image that contains just the Embedded Core package is described as a “minboot” image. To build an Embedded Core (eCore) image using Image Builder Wizard, follow the steps in section 2.1.1 Build a Thin Client Image with Embedded Enabling Features with the following changes: 1. 2. At step 4, choose the Minimum Configuration template Complete steps 10 and 15 only if you want to enable write filters.2.2 Build a Windows Embedded Standard 2011 Image Using Image Configuration Editor2.2.1 Build a Thin Client Image with Custom Settings1. Start Image Configuration Editor on your development computer. • From the Start menu, selectPrograms, selectWindows Embedded Standard 2011, then selectImage Configuration Editor.©2009 Microsoft. All Rights Reserved.Page 11Windows Embedded Standard 2011 – CTP2 Lab Manual 2. On the File menu, select Distribution Share, then navigate to the desired distribution share. The default distribution share locations are: • On a development computer running a 32-bit operating system: • • • x86 distribution share: C:\Program Files\Windows Embedded Standard 2011\DS amd64 distribution share: C:\Program Files\Windows Embedded Standard 2011\DS64On a development computer running a 64-bit operating system: • • x86 distribution share: C:\Program Files(x86)\Windows Embedded Standard 2011\DS amd64 distribution share: C:\Program Files(x86)\Windows Embedded Standard 2011\DS643. 4.On the File menu, click New Answer File. By default, the Embedded Edition package is added to this new answer file. This is the Embedded Core package. Add Driver Packages a. On the File menu, click Import then select Import PMQ to add device drivers using a PMQ file. In the Messages pane, in the Import PMQ tab, you can review the results of mapping the devices in a PMQ file to driver packages. • • Successfully mapped devices will be listed. To view the package in the answer file that the device was mapped to, double-click the device name. The warning icons denote devices that were not mapped to driver packages. If you need support for these devices, see section 2.2.3 Note: For more information on how to generate a PMQ file, refer to the Windows Embedded Standard 2011 Help topic “How to Generate a .PMQFile Using Target Analyzer”. b. In the Distribution Share pane, under Packages/Driver, you can add additional driver packages. Double-click any driver package (leaf node in the tree) to add it to your answer file. In the Distribution Share pane, expand the Packages/FeaturePack node. Expand the Browsers/Internet Explorer 8 node, right-click on Internet Explorer 8 Browser and select Add to Answer File. Expand the Graphics and Multimedia node, right-click on Windows Media Player 12 and selectAdd to Answer File. Expand the Remote Connections node, right-click on Remote Desktop Connectionand select Add to Answer File.5.Add Feature Packages a. b. c. d.6.Determine which type of write filters you want to use for your thin client. In the Distribution Share pane, under Packages/FeaturesPack, right-click on the appropriate feature packages and select Add to Answer File. To use File Based Write Filter (FBWF) and Registry Filter, select:©2009 Microsoft. All Rights Reserved.Page 12Windows Embedded Standard 2011 – CTP2 Lab Manual • • OR To use Enhanced Write Filter (EWF), Hibernate Once Resume Many (HORM) and Registry Filter, select: • • • Embedded Enabling Features\Enhanced Write Filter with HORM Embedded Enabling Features\Registry Filter Boot Environments\Enhanced Write Filter Boot Environment Note: Although EWF can be used without HORM, using HORM requires EWF. Adding EWF in IBW (without an answer file) will configure all existing volumes to be protected in RAM-REG mode; however EWF will be disabled for all of them. 7. To add language packs, in the Distribution Share pane, expand the Packages/LanguagePack/en-US node. Right-click the English (US) Language Pack package and select Add to Answer File. Add additional language packs the same way. To change Internet Explorer 8 settings: a. b. c. d. e. f. In theAnswer File pane, click on theInternet Explorer 8 Browser package. In the Settings pane, change Filter View to “4 Specialize”. In the Settings pane, click on the Value column to update the value for each of the following settings: Set Home_Page to /embedded SetIEWelcomeMsg to false Save your answer file. Embedded Enabling Features\File Based Write Filter (FBWF) Embedded Enabling Features\Registry Filter8.You have now changed the way Internet Explorer behaves by using Image Configuration Editor’s settings UI. You can change additional settings in your answer file the same way. 9. To resolve dependencies, from the Validate menu, select Add Required Packages. a. If there are any errors listed in the Validation tab of the Messages pane that state “Dependencies of the source package are not satisfied,” double-click the error message and use the Resolve Dependencies dialogue box to satisfy all required package dependencies. • If you are asked to choose between two USB stacks, choose “Bootable Windows USB Stack” only if you are using the USB Boot Embedded Enabling Feature and enabling a USB bootable image (see section 5.3). Otherwise choose “Standard Windows USB Stack.” If you are asked to choose between two boot environment packages, choose “Enhanced Write Filter Boot Environment” if you are installing HORM with EWF. Otherwise choose “Windows Boot Environment”.•b.Warnings that state “Optional Dependencies exist for the source package” are acceptable and may be ignored. Page 13©2009 Microsoft. All Rights Reserved.。
性能测试常用监控工具简介

一、 LINUX监控工具--NMON
NMON简介
● Nmon是一种在Aix与Linux操作系统上 广泛使用的监控与分析工具
● Nmon所记录的信息非常全面 ● Nmon可以产生数据文件与图形化结果
NMON监控内容
● cpu占用率 ● 内存使用情况 ● 磁盘I/O速度、传输和读写比率 ● 文件系统的使用率 ● 网络I/O速度、传输和读写比率、错误统计率与传输包的大小 ● 消耗资源最多的进程 ● 计算机详细信息和资源 ● 页面空间和页面I/O速度 ● 用户自定义的磁盘组 ● 网络文件系统
Spotlight on oracle监控top session
TopSessions面板可以查看当前哪个session当前占用了大量的资源;单 击session列表,会在session Information中显示该会话的所有详细信息 ,可以查看执行计划,判断是否存在全表扫描
Spotlight on oracle监控top sql
● 举例:./nmon –F test.nmon –s 5 –c 1000
NMON生成数据文件
● nmon analyser生成数据文件 ● 需要将nmon analyser的宏安全模式调至低
NMON数据文件分析
NMON数据文件分析
主要关注TAB: ● SYSSUM ● CPU_ALL ● CPU_SUMM ● DISK_SUMM ● DISKBUSY ● MEM ● NET
Jconsole启动
服务器端启动:
在catalina.sh的JAVA_OPTS参数中添加-Djava.awt.headless=true 在Xshell的参数选项中,将X11连接选中:
Jconsole启动
远程连接:
WEB知识-HttpWatch工具简介
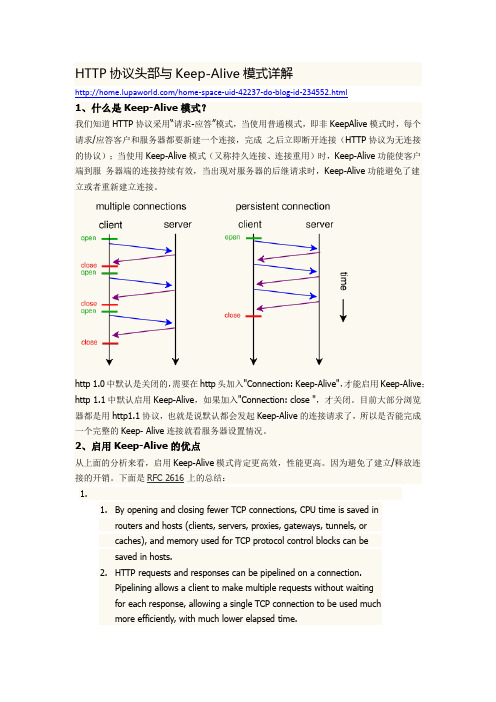
HTTP协议头部与Keep-Alive模式详解/home-space-uid-42237-do-blog-id-234552.html1、什么是Keep-Alive模式?我们知道HTTP协议采用“请求-应答”模式,当使用普通模式,即非KeepAlive模式时,每个请求/应答客户和服务器都要新建一个连接,完成之后立即断开连接(HTTP协议为无连接的协议);当使用Keep-Alive模式(又称持久连接、连接重用)时,Keep-Alive功能使客户端到服务器端的连接持续有效,当出现对服务器的后继请求时,Keep-Alive功能避免了建立或者重新建立连接。
http 1.0中默认是关闭的,需要在http头加入"Connection: Keep-Alive",才能启用Keep-Alive;http 1.1中默认启用Keep-Alive,如果加入"Connection: close ",才关闭。
目前大部分浏览器都是用http1.1协议,也就是说默认都会发起Keep-Alive的连接请求了,所以是否能完成一个完整的Keep- Alive连接就看服务器设置情况。
2、启用Keep-Alive的优点从上面的分析来看,启用Keep-Alive模式肯定更高效,性能更高。
因为避免了建立/释放连接的开销。
下面是RFC 2616上的总结:1.1.By opening and closing fewer TCP connections, CPU time is saved inrouters and hosts (clients, servers, proxies, gateways, tunnels, orcaches), and memory used for TCP protocol control blocks can besaved in hosts.2.HTTP requests and responses can be pipelined on a connection.Pipelining allows a client to make multiple requests without waitingfor each response, allowing a single TCP connection to be used muchmore efficiently, with much lower elapsed time.work congestion is reduced by reducing the number of packetscaused by TCP opens, and by allowing TCP sufficient time todetermine the congestion state of the network.tency on subsequent requests is reduced since there is no timespent in TCP's connection opening handshake.5.HTTP can evolve more gracefully, since errors can be reported withoutthe penalty of closing the TCP connection. Clients using futureversions of HTTP might optimistically try a new feature, but ifcommunicating with an older server, retry with old semantics afteran error is reported.RFC 2616(P47)还指出:单用户客户端与任何服务器或代理之间的连接数不应该超过2个。
tomcat7.0运行过程解析

tomcat7.0运行过程解析一、接口和类概况.apache.catalina .Lifecycle接口:表示组件生命周期(1)签名:public interface Lifecycle(2) 基本流程:NEW-->init(INITIALIZING-->INITIALIZED)-->start(STARTING_PREP-->STARTING-->STARTED)-->stop(STOPPING_PREP-->STOPPING-->STOPPED)-->destroy(DESTROYING-->DESTROYED)Start,stop分三个阶段,init,destroy分两个阶段。
(2)阶段之间的跳转关系图(来自源代码):(3)声明的方法:public void addLifecycleListener(LifecycleListener listener)public LifecycleListener[] findLifecycleListeners();public void removeLifecycleListener(LifecycleListener listener);public void init() throws LifecycleException;public void start() throws LifecycleException;public void stop() throws LifecycleException;public void destroy() throws LifecycleException;public LifecycleState getState();public String getStateName();.apache.catalina.util. LifecycleSupport类:为Lifecycle的实现提供支持,简化Lifecycle的实现(1)签名:public final class LifecycleSupport(2)构造函数:public LifecycleSupport(Lifecycle lifecycle) {super();this.lifecycle = lifecycle;}(3)已实现public void addLifecycleListener(LifecycleListener listener)public LifecycleListener[] findLifecycleListeners()public void fireLifecycleEvent(String type, Object data)public void removeLifecycleListener(LifecycleListener listener).apache.catalina.util.LifecycleBase 类:实现了Lifecycle接口,完成大部分通用业务(1)签名:public abstract class LifecycleBase implements Lifecycle(2)重要成员:private LifecycleSupport lifecycle = new LifecycleSupport(this); 利用它完成Lifecycle接口的实现private volatile LifecycleState state = LifecycleState.NEW; 初始状态(3)定义抽象方法initInternal,startInternal,stopInternal,destroyInternal(4)实现了生命周期方法init,start,stop,destroy,并在实现内部分别调用对应的initInternal,startInternal,stopInternal,destroyInternal方法,以便子类可以增加个性化的业务逻辑(5)把生命周期方法执行的过程分阶段,并调用阶段设置方法setStateInternal设置相应阶段,在setStateInternal的内部调用fireLifecycleEvent(lifecycleEvent, data)来触发生命周期事件.apache.catalina.util.LifecycleMBeanBase 类:实现对Lifecycle对象的JMX管理(1)签名:public abstract class LifecycleMBeanBase extends LifecycleBase implements MBeanRegistration(2)主要是在initInternal中调用register(this, getObjectNameKeyProperties());在destroyInternal中调用unregister(oname)。
NetWeaver7.0配置手册

ERP软件部 NetWeaver7.0配置手册-初级版本 <内测版本>目录1.简介 (4)1.1目的 (4)1.2范围 (4)1.3定义、首字母缩写词和缩略语 (4)1.4参考资料 (4)1.5概述 (4)2.配置NETWEAVER (4)2.1为什么需要配置? (4)2.2BOUNCYCASTLE JCE (4)2.3更新ORACLE驱动 (6)2.4调整JVM参数 (7)3.配置系统运行日志 (9)4.安装部署FMIS服务端程序 (11)4.1配置FMIS数据源 (11)4.2更新FMIS服务程序包 (15)4.3部署FMIS服务程序包 (15)4.4卸载FMIS (16)5.常见问题(FAQ) (18)5.1为什么? (18)5.2为什么? (18)5.3为什么? (19)5.4为什么? (19)5.5如何? (19)6.附录A:如何 (19)NetWeaver7.0配置手册-初级1.简介本文档包括了NetWeaver7.0的配置管理以及日常维护过程中会出现的部分的解决方法。
1.1目的1.2范围NetWeaver7.01.3定义、首字母缩写词和缩略语1.4参考资料1.5概述2.配置NetWeaver进行配置前,请确认NetWeaver已经启动。
确认方式:http://IP:端口/nwa 可正常访问。
2.1为什么需要配置?因为需要配置…2.2bouncycastle JCEFMIS 服务端借助bouncycastle JCE完成数据的加密解密功能。
复制bcprov-jdk14-137.jar,bcmail-jdk14-137.jar至JRE的lib\ext目录中。
例如:D:\j2sdk1.4.2_19\jre\lib\ext注:如何判断NetWeaver的java.ext.dirs目录?访问 http://IP:端口/sap/monitoring/SystemInfo,点击Instance的server的VM的SystemProperties,在打开的页面中查找“java.ext.dirs”。
抓包工具-HttpWatch(功能详细介绍)

抓包⼯具-HttpWatch(功能详细介绍) HttpWatch是功能强⼤的⽹页数据分析⼯具,集成在IE⼯具栏,主要功能有⽹页摘要、cookies管理、缓存管理、消息头发送/接收,字符查询、POST数据、⽬录管理功能和报告输出。
HttpWatch是⼀款能够收集并显⽰深层信息的软件,它不⽤代理服务器或⼀些复杂的⽹络监控⼯具,能够在显⽰⽹页的同时显⽰⽹页请求和回应的⽇志信息,甚⾄可以显⽰浏览器缓存和IE之间的交换信息,集成在IE⼯具栏。
(HttpWatch⼯具需要下载安装,这⾥就不详说了,直接搜索百度就ok了) HTTP基础知识之HTTP消息格式 当⽤户使⽤浏览器访问某个URL地址、提交表单数据时,浏览器会⽣成请求消息发送给服务器,服务器收到请求后,将⽣成的响应消息返回给浏览器。
浏览器发出的请求信息和服务器返回的响应信息统称为HTTP消息。
HTTP消息有着严格的格式。
⼀个完整的请求消息包括:⼀个请求⾏、若⼲消息头及实体内容,其中⼀些消息头和实体内容是可选的,消息头和实体内容之间使⽤空⾏隔开,下⾯是HTTP请求消息内容:(Request-Line) GET /get.do?prod=wmail_lbp&ver=1&uid=nt@&domain=&mobUser=0&callback=themeHandler.callback&rnd=0.13562542999267713 HTTP/1.1 Accept application/javascript, */*;q=0.8Accept-Encoding gzip, deflateAccept-Language zh-CNConnection Keep-AliveCookie starttime=; logType=Host Referer /User-Agent Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0)HTTP请求消息内容 ⼀个完整的响应消息包括:⼀个状态⾏、若⼲消息头及实体内容。
Httpwatch使用说明

Httpwatch使用说明一、概述:HttpWatch强大的网页数据分析工具.集成在Internet Explorer工具栏.包括网页摘要.Cookies管理.缓存管理.消息头发送/接受.字符查询.POST 数据和目录管理功能.报告输出HttpWatch 是一款能够收集并显示页页深层信息的软件。
它不用代理服务器或一些复杂的网络监控工具,就能够在显示网页同时显示网页请求和回应的日志信息。
甚至可以显示浏览器缓存和IE之间的交换信息。
集成在Internet Explorer工具栏。
二、基本功能介绍启动Httpwatch从IE的“查看”—“浏览器栏”—“HttpWatch”启动HttpWatch。
如下图所示:以下是HttpWatch程序界面以下用登录业务基础平台http://test-sxgs-sys2:9080/platfo rm/home来展示Httpwatch:用户名为:kejiAdmin 密码为:1点击“Record”后,在IE打开需要录制的网址, 业务基础平台http://test-sxgs-sys2:9080/platform/home,输入用户名,密码后完成登录操作1. Overview(概要)表示选定某个信息显示其概要信息如上图所示:Display URL:http://test-sxgs-sys2:9080/platform/ho meResult:200请求的URL是http://test-sxgs-sys2:9080/platform/hom e ,返回的Htpp状态代码结果200,表示成功;Started At 2012-Jan-20 10:19:53.792 (local time) C ompleted表示为:请求开始时间(实际记录的是本机的时间)HTTP Request Unconditional request sent for http:/ /test-sxgs-sys2:9080/platform/home Completed表示为:Http请求,当浏览器向Web服务器发出请求时,它向服务器传递了一个数据块,也就是请求信息Http Response Headers and content returnedHttp响应,当浏览器接受到web服务器返回的信息时2. timeChart从timeChart,我们可以一目了然的看到那些请求花费的时间较长,一般柱状的长短表示从请求到接受共花费的时间,我们重点需要优化那些柱状较长的部分,当然我们也可以点击time列,按请求时间排到序,直接找出请求时间最长的部分。
AWStats中文帮助文档

AWStats 的配置指令和选项主设置(必须设置)LogFile"LogFile"包含要分析的日志文件,可以使用绝对路径或者相对路径(对awstats.pl而言)。
比如:LogFile = /var/log/apache2/access_log如果需要设定动态的文件名(比如日志文件名中含有该日志生成的日期),可以使用标签(tags):tags 含义%YYYY-n n小时前的年(四位,比如2006)%YY-n n小时前的年(两位,比如06)%MM-n n小时前的月(比如01)%MO-n n小时前的月(比如Jan)%DD-n n小时前的天(比如03)%HH-n n小时前的小时(比如03)%NS-n n小时前的秒(自1970年0:00以来,只精确到天,比如1136332800,是格林威治时间2006年1月4日的零点)%WM-n n小时前的周(week in month,值为01-05)(注意,文档与实际并不一致,文档中值为1-5,可能是个bug)%Wm-n n小时前的周(week in month,值为0-4)%WY-n n小时前的周(week in year,值为01-52)%Wy-n n小时前的周(week in year,值为00-51)%DW-n n小时前的天(day in week,值为1-7,1=sunday,如果需要使得1=monday,减去24小时就可以了。
)%Dw-n n小时前的天(day in week,值为0-6,0=sunday,如果需要使得0=monday,减去24小时就可以了。
)比如:LogFile = /var/log/apache2/access_log.%YYYY-24-%MM-24-%DD-24.txt还可以使用管道:LogFile = gzip -d如果有多个日志文件需要分析(比如做了负载均衡),可以这样:LogFile = "/pathtotools/logresolvemerge.pl *.log |"LogType日志的类型:W web日志M mail日志F ftp日志比如:LogT ype=WLogFormat日志的格式:1 Apache 或者Lotus Notes/Domino 的combined日志格式2 老的IIS的日志格式3 Webstar的native日志格式4 Apache 或者Squid 的common日志格式我们还可以自己指定日志格式,下表是日志格式的各个字段%host客户端的主机名或者IP地址%lognamequot Authenticated login/user with format: "alex"%logname Authenticated login/user with format: alex%time1 日期,格式为[dd/mon/yyyy:hh:mm:ss +0000] 或[dd/mon/yyyy:hh:mm:ss]%time2 日期,格式为yyyy-mm-dd hh-mm-ss%time3 日期,格式为Mon dd hh:mm:ss 或Mon dd hh:mm:ss yyyy%time4 日期,格式为dddddddddd(unix的时间戳)%methodurl 方法和url,格式为:"GET /index.html HTTP/x.x"%methodurlnoprot 方法和url,格式为:"GET /index.html"%method 方法,格式为:GET%url URL,格式为:/index.html%query 查询的字符串(Query string) ( URLWithQuery 选项要用)%code 返回的状态码Return code status (with format for web log: 999)%bytesd 文档的大小(字节)%refererquot Referer page,格式为:"/from.htm"%referer Referer page,格式为:/from.htm%uaquot User agent,格式为:"Mozilla/4.0 (compatible, ...)"%ua User agent,格式为:Mozilla/4.0_(compatible...)%gzipin mod_gzip comdivssion input bytes: In:XXX%gzipout mod_gzip comdivssion output bytes & ratio: Out:YYY:ZZpct.%gzipratio mod_gzip comdivssion ratio: ZZpct.%deflateratio mod_deflate comdivssion ratio with format: (ZZ)%email EMail sender (for mail log)%email_r EMail receiver (for mail log)%virtualname Web sever virtual hostname. Use this tag when same log contains data of several virtual web servers. AWStats will discard records not in SiteDomain nor HostAliases%cluster If log file is provided from several computers (merged by logresolvemerge.pl), this tag define field of cluster id.%other 如果日志文件有一些字段不被上面的列表包括,使用%other比如:LogFormat= 1LogFormat="%host %other %logname %time1 %methodurl %code %bytesd %refererquot %uaquo t"LogSeparator日志各个字段间的分隔符比如:LogSeparator=" "DNSLookupDNS反查,可取的值如下:0 不用DNS反查1 完全启用DNS反查2 DNS反查只从静态的DNS的缓存中取得比如:DNSlookup=2DirData统计结果存放的目录。
2Question 用户指南说明书

2Question UserGuide2Question User Guide ................................................................................................................................... Introduction 31. ................................................................................................................................... Getting Started 32. ................................................................................................................................... 4Top menubar ................................................................................................................................... 5Main Screen ................................................................................................................................... Playing a branching database 73. ................................................................................................................................... Lesson Ideas 84.Introduction -2Question is a tool for creating branching (binary) databases.A branching database is sometimes referred to as a binary tree or a key.Branching databases are a way of classifying a groups of objects.A branching database id a way to identify an object by answering a series of simple questions and yes/no questions.When using in class, start by doing lots of sorting and classifying activities with the children and thinking about the different ways you could sort your objects. You can use the images within the 2Question resources area of Purple Mash.There are some teaching ideas in the Lesson Ideas section of this guide.You can also fin examples branching databases in the teachers section. You can print off the image banks to go with the databases to try them out.FruitVegetablesMy friendsMusical instrumentsGetting Started -2.1Top menubarNew FileOpen a saved fileSave the current datePrint the graph and dataExport the graph and data as an imageShare the file to a displayboard or blog, create a QR code or link, set as a 2Do or send by 2Email. See the Generating Share Links Guide for more information about these features.Play: Once the table has been created it can be played to identify and object. See Playing a branching database for details2.2Main ScreenWhen you open a new file, the screen will look like this:This is the first question of the database. Click on the 'Click to Edit' box to open the editorFill in the Question Text and wording for the answer choices; this will usually be 'yes' and 'no'. You have the following additional options:Add sound from the sound picker. This includes the ability to record your own sound or upload from your device.Add an image; this could be an image of the final object or something that represents the choice made. For example, if the question was 'Does it have teeth?', the image could be some teeth. Thisadds interest to the look of the database. Images can be selected from clip-art , drawn usingthe paint tools or uploaded from your device or the device web-cam .Add additional notes; perhaps some more information about the question or the feature that the question asks about.Once you click 'OK', branches will be added to the database and you can add further questions until you are left with just one item (the end of a branch).Tick the check-box 'This is a final answer and the answer choice boxes will disappear. Put the answer into the box that says 'Question Text'.Repeat this process until all items have been classified.Add a title and Save the database, it is now ready to 'Play'.Once a database has been saved, it can be 'played' to identify an item. Click the Play button and answer each of the questions as they are presented until the answer is reached.There is a unit within the Computing Scheme of Work about Branching databases: Unit 2.4 -Questioning.This can be used with your class or adapted to children of different ages.There are example materials PDFs that can be printed and used for off-line activities.Fruits examples:How could we sort the fruits into groups?Fruits that have a skinFruits that have pipsFruits that have a stoneFruits that are roundMy friends examples:Think about the children in class, how could you sort them?Boys and girlsChildren with long hairChildren with short hairChildren with blue eyesChildren with brown eyesGuess What? Now play some games!Use the pictures of the fruit to play a game.Put the images faced up on the desk, choose a fruit (but leave the card in place).Tell the children you are going to have some fruit for lunch can they guess which fruit you have chosen.Tell the children they can ask you 1 question at a time about the fruit you have chosen but you are only allowed to answer yes or no.Lesson Ideas -Example questions:Is your fruit orange (eliminates the orange straight away!)Is your fruit long (That takes care of the banana!)Do you usually eat the skin on the fruit? (The lemon is out!)Is your usually bought as a bunch? (Possibly the grapes!)You could play similar games using images of the children.Let the children play 'Guess Who?' games with photographs of themselves or using their Purple Mash avatars. Play in small groups with images of the children on the table.Try making a fruit branching database using the example picture cards, arrows and yes/no cardsUse the 6 fruit images.Use the blank boxes to write your questions and the yes no card and arrows to display your database.Write your own questions in the blank boxes.Using yes and no answers, create a branching database with the pictures (there are some yes/no cards for you to print out too).Think about the game you have just been playing, guessing the fruit.Start with a question which will group the fruits into 2 groups. For example, is your fruit green? To make a well functioning branching database, the questions should split the remaining choices into equal groups (or as equal as possible), this means that, on average, you will get to the correct answer in the fewest steps.Use the cards to help you make your branching database on the floor.Test your branch, get a child to choose a picture of a fruit, use the questions to find out what it is.。
Eaton Foreseer 7 设备配置工具指南说明书

Foreseer 7 Device ConfigurationUtility GuideForeseer 7.0 Device Configuration Utility GuidePublication date 1/2018Copyright © 2018 by Eaton Corporation. All rights reserved. Specifications contained herein are subject to change without notice.Power Xpert and Foreseer are registered trademarks of Eaton Corporation.EATON CORPORATION - CONFIDENTIAL AND PROPRIETARY NOTICE TO PERSONS RECEIVING THIS DOCUMENT AND/OR TECHNICAL INFORMATION THIS DOCUMENT, INCLUDING THE DRAWING AND INFORMATION CONTAINED THEREON, IS CONFIDENTIAL AND IS THE EXCLUSIVE PROPERTY OF EATON CORPORATION, AND IS MERELY ON LOAN AND SUBJECT TO RECALL BY EATON AT ANY TIME. BY TAKING POSSESSION OF THIS DOCUMENT, THE RE- CIPIENT ACKNOWLEDGES AND AGREES THAT THIS DOCUMENT CANNOT BE USED IN ANY MANNER ADVERSE TO THE INTERESTS OF EATON, AND THAT NO PORTION OF THIS DOCUMENT MAY BE COPIED OR OTHERWISE REPRO- DUCED WITHOUT THE PRIOR WRITTEN CONSENT OF EATON. IN THE CASE OF CONFLICTING CONTRACTUAL PROVI- SIONS, THIS NOTICE SHALL GOVERN THE STATUS OF THIS DOCUMENT.DISCLAIMER OF WARRANTIES AND LIMITATION OF LIABILITYThe information, recommendations, descriptions and safety notations in this document are based on Eaton Corporation’s (“Eaton”) experience and judgment and may not cover all contingencies. If further information is required, an Eaton sales office should be consulted. Sale of the product shown in this literature is subject to the terms and conditions outlinedin appropriate Eaton selling policies or other contractual agreement between Eaton and the purchaser. THERE ARE NO UNDERSTANDINGS, AGREEMENTS, WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING WARRANTIES OF FITNESS FOR A PARTICULAR PURPOSE OR MERCHANTABILITY, OTHER THAN THOSE SPECIFICALLY SET OUT IN ANY EXIST- ING CONTRACT BETWEEN THE PARTIES. ANY SUCH CONTRACT STATES THE ENTIRE OBLIGATION OF EATON. THE CONTENTS OF THIS DOCUMENT SHALL NOT BECOME PART OF OR MODIFY ANY CONTRACT BETWEEN THE PAR- TIES.In no event will Eaton be responsible to the purchaser or user in contract, in tort (including negligence), strict liability or otherwise for any special, indirect, incidental or consequential damage or loss whatsoever, including but not limited to damage or loss of use of equipment, plant or power system, cost of capital, loss of power, additional expenses in the use of existing power facilities, or claims against the purchaser or user by its customers resulting from the use of the information, recommendations and descriptions contained herein.ContentsIntroduction (4)Interactive Device Installation (4)To install a new Device on the Foreseer Local Server: (4)Configuring a Serial Connection (5)To configure a Direct Serial Connection at the Foreseer Server: (5)To edit a device: (5)Configuring the Message Manager (6)Setup (6)SNMP Resend Parameters (9)Required Connections (10)Trusted Message Manager Connections (10)Menu Reference (11)Administration Menu (11)Configuration Menu (11)IntroductionYou can use the Device Config utility to:• Add or modify devices from the Foreseer configuration in a running ForeseerServer. You can add “driver allowed” channels as well.• Modify an existing device or to add a channel to a device, you must first load itsdriver. In this context, loading a device's driver disables that device in the Foreseerservice. When you unload the driver in the Device Config utility that driver is re-enabled in the Foreseer service. You can only load a single driver in the DeviceCon- fig utility at a time.• Add channel message settings for Message Management.Interactive Device InstallationTo install a new Device on the Foreseer Local Server:1. Select the Start Server Configuration command in the Configuration menu.The ********SERVER CONFIGURATION MODE******** message appears in thewindow’s title bar.NoteIf an administrative password is required to configure the server, adialog box will appear in which you must provide that password.2. Right-click the local server, then select the Install Device command to accessthe initial Device Installation dialog box.3. Locate the previously completed Configuration Checklist for the new equipment,then click Next.4. Choose the Select the device from a list option and click Next. The Devicemust be correctly wired and running in a normal operational mode in order tosuccessfully connect to it.5. Select the device from the list, then click Next.6. Accept the suggested name for the Device or enter another unique description,observing the character limitations, and then click Next to continue.7. Specify whether the interface between the Server and the Device is a N etworkor direct Serial connection and then select the appropriate type for that option.NoteTCP/IP Protocol must be installed on the Server PC regardless of thetype of Device connection. When utilizing a ConnectUPS NetworkAdapter (Powerware UPS products only), specify a UDP/IP connection.TCP VIM II is only used to install legacy Liebert equipment.8. In the settings dialog box that appears, enter the requested additionalinformation and then click Next. Continue to enter communications informationand click Next until requested. When the display returns to the DeviceInstallation dialog box, click OK followed by Next to continue.9. In the Identification dialog box, verify that the information displayed about the De-vice corresponds to the information recorded on the Configuration Checklist. Ifnot, Cancel the installation and recheck the Device. If the displayed Deviceinformation is correct, click Next.10. With the target Device and the interface connection defined, click Finish tocomplete the installation. The new equipment will appear in the Tree View.ImportantIf the installation is unsuccessful, or the Device information does notappear in the Identification window, click Back and check that allconfiguration entries are proper and that hardware connections with theequipment are correct. After verifying the configuration and connections,once again attempt to install the Device. Contact Eaton Corporation'sForeseer Technical Support if Device installation problems persist.11. Install any additional Devices using the same p rocedure.12. With all Devices properly installed click No in response to the Install AnotherDevice? prompt to terminate the installation process.13. Select End Server Configuration in the Configuration menu to restore normalForeseer Server operation.Configuring a Serial ConnectionThe Device's Port Settings must be specified if a Direct Serial or VIM II connection isused. Either choice requires that you specify the Serial Communications Port and itssettings.To configure a Direct Serial Connection at the Foreseer Server:1. Accept the displayed Port or select one of the Ports currently available from thelist.2. If you wish to change the port settings, click the Change Settings button to dis-play the named port's Properties dialog box containing additional serial interfaceparameters.3. Click OK to enable the displayed Port Settings and return to the DeviceInstallation Wizard.The process for entering the necessary configuration settings for a VIM II DirectSerial Connection is similar. After specifying the communications Port and DeviceSet- tings for the VIM II, you are prompted to specify the VIM II Address and Port.Click OK to enable the displayed parameters and return to the Device InstallationWizard.You can modify any existing device using the Device Config utility. The following gen-eral procedure can be used for modifying device or channel properties or adding achannel.To edit a device:1. Right-click the device in the Tree and then choose Load Driver. The device andits channel icons will turn purple.2. • To modify the device properties, right-click the device and choose Properties.• To modify a channel's properties, right-click the channel and choose Proper-ties.• To add a Channel, right-click the device and choose Add Channel.3. When you've finished, right-click the device and choose Unload Driver. You cannow load the driver for another device that you wish to configure.4. When you're finished configuring devices, select End Server Configurationfrom the Configuration menu.Configuring the Message ManagerThere are four configuration tasks for the message manager within the ForeseerServer:Setup Defines which devices or individual channels sendalerts through Message Management as well asthe configuration for various alarms and actions.You can also define the SNMP behavior.Configure Required Connections: Identifies which Foreseer systems are required to be connected to this Server in instances where the Client normally performs Message Management functions. If any one of the listed systems becomes disconnected from the Server, Foreseer Message Management begins its messaging routine to alert personnel of alarms.Setup SNMP Properties Sets global SNMP resend properties.Trusted Connections Defines a set of trusted machines that are permit-ted to connect to the Message Manager.Use this to configure Message Manager settings for the server, devices, or individual channels.1. Select the Setup command from the Administration > Message Managementsubmenu.2. Right-click any server, device, or channel in the list, and then click Edit. You canalso multi-select.3. For individual channels, you can set whether or not to use the default NotificationList (this checkbox is under the Default tab). For channels, devices, and servers you can set behavior for Critical and Cautionary alarms, as well as when an alarm is acknowledged or normal status is attained. Note that you can select theseindividually or use multi-select. You can specify:• The notification list to use.• Whether to send a message if required connections are missing.• Parameters for Alpha Messages. You can either choose to use the standard message and configure it with the checkboxes or select Use Custom Message (under Alpha Message). If you are using the standard message, you canselect to include the Server Name, Device Name, Channel Name, as well asa user defined message.If you choose Use Custom Message, you have access to all of the Message Manager variables. Click Edit the Custom Message to access the message editor dialog box.$SERVER_NAME$ - returns the server issuing the alarm$DEVICE_NAME$ - returns the name of the device issuing the alarm. $CHANNEL_NAME$ - returns by the name of the channel$ALARM_MSG$ - returns the alarm message.$DATE$ - returns the current date.$SERIAL#$ - returns the serial number of the device that issued the alarm. $ACKED_BY$ - returns the user name that acknowledged the alarm. $CHANNEL_VALUE$ - returns the current value of the channel.$CHANNEL_UNITS$ - returns the units used by the channel.$ALARM_VALUE$ - returns the channel value at the time of the alarm. $ALARM_STATE$ - returns the current state of the alarm.$ALARM_PRIORITY$ - returns the alarm priority.$ACK_NOTE$ - returns the text, if any, that was entered as a note when the alarm was acknowledged.• The command line to use for the Command Line service. This allows youto change the command line issued for each alarm state or status.Once these are configured, you can copy the settings to the other alarm orstatus tabs using the buttons at the bottom of the dialog box.Figure 1. Channel Message Settings Dialog Box4. If you are also configuring SNMP traps, click the SNMP tab:a. For both Critical Alarm and Cautionary Alarm, select one of the 25 prede-fined traps or leave the setting at Do not send a Trap.b. Set the Alarm Events parameters. You can choose to also send a trap onalarm acknowledgement or return to normal.5. Click OK.Figure 2. SNMP SettingsSNMP Resend ParametersThrough this dialog box you can globally set the trap resend behavior. These settingsapply to all channels, devices, and server for which SNMP traps are configured. Toaccess it, select the SNMP Properties command from the Administration >Message Management submenu.Required Connections1. Select the Configure Required Connection command from the Administration> Message Management submenu to display the Required Connection Set-tings dialog box.Figure 4. Required Connection Strings2. Click on the Add button to access the Enter Client IP Address dialog box.3. Furnish either the Foreseer Message Management host network address orcomputer name and click OK.4. Check the box preceding the address to enable server access by t hat client.5. Specify the Startup Delay during which the server will ignore any clients thatbe- come disconnected. This delay is in effect whenever the server is initialized,or when modifications have been made to the system.6. Repeat the process to add other Foreseer clients to the list.7. Click OK to accept the displayed settings.Trusted Message Manager ConnectionsWhen setting up the Message Manager on client machines, you must define themas having trusted IP addresses or machine names. To access the dialog box, selectthe Trusted Connections command from the Administration > MessageManagement submenu. Click the Add button to add machines to the list. Select anentry and click Remove to delete it. Use the Edit button to change an entry.11Figure 5. Trusted Message Manager ConnectionsMenu ReferenceAdministration MenuLogin/LogoffIf a password is set for administering the Foreseer serv er, you'll need to enter it configure that server. Login pro- vides a way to authenticate to the server with the pass- word while logoff removed those credentials from your De- vice Config utility session.Message ManagementYou can use this submenu to configure Message Man agement . Message Management establishes an automatic escalation procedure in response to user-specified alarms. When an alarm is detected, Foreseer calls each person in the appropriate Notification List in the order shown until the alert is acknowledged. The Status portion of the Message Management window reports the notification is being performed and its ongoing progress. If every- one on the List is called without receiving an acknowledgement, Foreseer can repeat the entire procedure until the alarm is acknowledged, thereby ensuring a response.Unload/Load DriverBy default, all devices are shown in the Device Config utili ty tree with white icons. Loading the driver for anindividual device disables that device in a running Foreseer service so that it can be modified. When you are finished configuring the device, unloading the driver re-enables it (with the changes to its configuration) in the Foreseer service. You must unload the driver to configure a device and you can only unload one driver at a time. That is, you cannot simultaneously configure more than one device.Configuration MenuStart/End Server ConfigurationCertain configuration functions are only available when in Server Configuration mode. Configuring backups is only available when not in Server Configuration mode. Functions that are only available in Server Configuration mode are:• Install Device (Device right-click menu and Configuration menu)• Add Channel (Device right-click menu and Configurationmenu).。
SM7文件系统知识库引导说明书
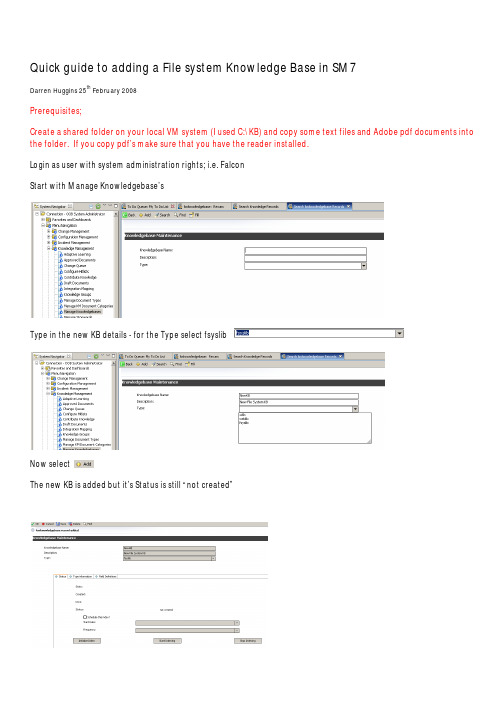
Quick guide to adding a File system Knowledge Base in SM7Darren Huggins 25th February 2008Prerequisites;Create a shared folder on your local VM system (I used C:\KB) and copy some text files and Adobe pdf documents into the folder. If you copy pdf’s make sure that you have the reader installed.Login as user with system administration rights; i.e.FalconStart with Manage Knowledgebase’sType in the new KB details -for the Type select fsyslibNow selectThe new KB is added but it’s Status is still “not created”Next we need direct it to the share we created earlier and indicate the document types we will include.Go back to the Status tab –set a schedule if required indexingSave the KB recordThen select Initialize IndexOK the recordRe-open and the KB should now be onlineNow start indexing and once it has finished there should be a number of records available (fyi –I have noticed that performance drops off a bit while the file system is being indexed)The KB should be accessible by other users; I use Joe Employee to search documents and my NewKB returns the recordThis has been designed for demonstration purposesonly and has NOT been tested in production environments. Please use as appropriate.。
DtHealth 7.0的安装与配置

东华医疗DtHealth7.0 安装与配置说明书版本历史目录1.简介 (4)1.1.版本 (4)1.2.参考文献 (4)1.3.先决条件 (4)2.IIS安装 (4)3.1.Windows 2008 (4)3.2.Windows XP (7)3.3.Win 7 (8)3.安装、配置数据库管理软件 (9)3.1.安装数据库管理软件 (9)3.2.配置数据库管理软件 (14)3.2.1.配置fdbms和cache.cpf (14)3.2.2.拷贝cache.key (17)4.配置CSP (18)5.配置IIS (19)5.1.Windows XP (19)5.2.1.建立dthealth虚拟目录 (19)5.2.2.修改执行权限 (22)5.2.3.模块映射 (22)5.2.Windows 2008/WIN 7 (25)5.2.1.建立dthealth虚拟目录 (25)5.2.2.添加模块映射 (26)5.2.3.启用【目录浏览】 (29)5.2.4.共享设置 (31)5.3.建立其他产品的虚拟目录 (33)6.修改DtHealth系统配置 (33)7.配置组件编辑器 (34)8.滚执行记录自动任务 (35)9.配置Medtrak和LabTrak (37)9.1.配置Medtrak (37)9.1.1.配置medtrak.ini (37)9.1.2.设置快捷方式 (37)9.1.3.运行时常见问题 (38)9.2.配置LabTrak (39)9.2.1.配置labtrak.ini (39)9.2.2.设置快捷方式 (39)9.2.3.运行 (39)1.简介本文档介绍了东华医疗标准版DtHealth 7.0的安装与配置步骤1.1.版本ENSEMBLE 20101.2.参考文献无1.3.先决条件1.Windows 2008 Server/Win 7/Windows 2003 server/Windows XP2.Web Server software3.部分产品需要安装.netframework4.02.IIS安装3.1.Wind ows 20081.检查是否安装好了IIS,可去【管理工具】的【服务管理器】中查看,如图所示2.如果没有安装好了IIS,可以通过【添加角色】安装注意:必须使用Administrator用户进行安装3.如果是开发服务器,可以关闭防火墙,或者指定cache可以通过防火墙3.2.Wind ows XP1.检查是否安装好了IIS,可去【控制面板】->【管理工具】中查看,如图所示2.如果没有安装好了IIS,可以通过【程序和功能】-【打开和关闭Windows功能】安装3.3.Win 71.检查是否安装好了IIS,可去【控制面板】->【管理工具】中查看,如图所示2.如果没有安装好了IIS,可以通过【程序和功能】-【打开和关闭Windows功能】安装3.安装、配置数据库管理软件3.1.安装数据库管理软件注意:1.安装Ensemble/Cache之前必须先安装IIS2.Windows 2008和WIN 7中安装Cache 2010前需要先更改区域与语言设置:设置美国,英语(美国),安装完成后在改回当前设置(xp、2003和Win7不需要此操作)3.安装版本64位:ensemble-2010.2.8.1104-win_x64.execache-2010.2.8.1104-win_x64.exe32位:ensemble-2010.2.8.1104-win_x86.execache-2010.2.8.1104-win_x64.exeEnsemble的默认安装目录为C:\Intersystems\Ensemble,在本文中约定为$Ensemble$(Cache的默认安装目录为C:\Intersystems\Cache,同理约定为$Cache$,后面不再单独描述)3.1.1.选择接受条款,点击【下一步】3.1.2.确定Ensemble服务实例名称3.1.3.确定安装路径3.1.4.选择”自定义”类型的安装模式3.1.5.选择“Unicode”3.1.6.确定数据库服务端口和管理WEB页面端口,默认不变3.1.7.确定安装的角色,选择Minimal3.1.8.中间会提示是否需要停止IIS服务,选择【是】3.2.配置数据库管理软件3.2.1.配置fdbms和cache.cpf1.关闭数据库管理软件2.将【数据库管理软件配置】中的fdbms文件夹拷贝到$Ensemble$(或$Cache$)\mgr下3.拷贝标准版文件夹DtHealth制定机器中,本文约定标准版所在目录为$DTHEALTH$4.将cache_2010_ensemble.cpf文件放置$Ensemble$;或将cache_2010_cache.cpf文件放置$Cache$下,然后备份原来的cache.cpf,并将新拷入的文件更名为cache.cpf 5.打开cache.cpf,修改路径与实际物理路径相符合。
HttpWatch测试工具理解文档V1.0

HttpWatch7.0工具使用理解文档V1.0*修订类型分为A - ADDED M - MODIFIED D –DELETED注:对该文件内容增加、删除或修改均需填写此记录,详细记载变更信息,以保证其可追溯性目录1HttpWatch介绍 (1)1.1概述 (1)1.2版本 (1)2HttpWatch环境搭建 (2)2.1安装 (2)2.2启动HttpWatch (5)2.3HttpWatch7.0新功能介绍 (10)3HttpWatch功能介绍 (15)4HttpWatch自动化应用 (24)4.1自动化测试概述 (24)4.2HttpWatch自动化架构 (24)4.2.1控制类 (25)4.2.2插件类 (25)4.2.3日志类 (25)4.2.4属性类 (25)4.3Ruby自动化控制HttpWatch (26)4.3.1概述 (26)4.3.2录制 (27)4.3.3Watir驱动浏览器 (28)4.3.4保存日志文件 (28)4.3.5打开日志文件 (29)4.3.6访问日志文件数据 (29)5注意事项 (31)1HttpWatch介绍1.1概述HttpWatch是强大的网页数据分析工具.集成在Internet Explorer和FireFox工具栏,包括网页摘要Cookies管理、缓存管理、消息头发送/接受、字符查询、POST 数据和目录管理功能、报告输出。
HttpWatch 是一款能够收集并显示网页深层信息的软件。
它不用代理服务器或一些复杂的网络监控工具,就能够在显示网页同时显示网页请求和返回的日志信息。
甚至可以显示浏览器缓存和IE之间的交换信息。
集成在Internet Explorer和FireFox工具栏。
只需要选择相应的网站,软件就可以对网站与浏览器之间的请求和回复的通讯情况进行分析并在同一界面显示其相应的日志记录。
每一个HTTP记录都可以详细分析其Cookies、消息头、字符查询等信息。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
1Getting StartedOpening the HttpWatch Browser Plug-inYou can display the HttpWatch plug-in in the lower part of the Internet Explorer (IE) or Firefox window by following the instructions shown below:Opening the HttpWatch Plug-in in IE 6Click on the HttpWatch toolbar button:or select it from the View menu:If neither of these options is available please restart Windows and try again. The plug-in can also be opened using Shift+F2 (see Using Keyboard Shortcuts).Opening the HttpWatch Plug-in in IE 7 or 8Click on the HttpWatch toolbar button which is normally on a hidden part of the IE Command Bar. You need to click on the toolbar chevrons (>>) before clicking on the HttpWatch button:or by selecting it from the Tools->Toolbars->Explorer Bar menu:If neither of these options is available please restart Windows and try again. The plug-in can also be opened using Shift+F2 (see Using Keyboard Shortcuts).The position of the HttpWatch button on the Command Bar can be changed using the Tools->Toolbars->Customize... menu item:If you move the HttpWatch toolbar button up:It can then be accessed more easily in IE:Opening the HttpWatch Plug-in in Firefox 2.0 - 3.6Click on the HttpWatch Tools menu item or status bar icon:If neither of these options is available please restart Firefox and check that HttpWatch is not disabled in Tools->Add-ons. The plug-in can also be opened using Shift+F2 (see Using Keyboard Shortcuts).Recording HTTP and HTTPS trafficOnce you have HttpWatch displayed in the browser, press the Record button to start recording HTTP requests.If you are using the free Basic Edition then extended HTTP information is only displayed for sites in the Alexa Top 20 or .HttpWatch includes an offline log file viewer known as HttpWatch Studio. It can be started from the HttpWatch program group under the Start menu or by double clicking on a .hwl file.2What's newNew in Version 7.0Page Level EventsPage level time charts now include lines to indicate when events were raised during the loading of a page:Improved Grouping of Requests during Page LoadRequests occurring after the page onload event are now grouped with the requests recorded during the initial loading of the page:HttpWatch Detects and Highlights Potential ProblemsHttpWatch now examines each request and issues warnings where problems relating to performance, security or functionality are detected. Requests that have warnings are highlighted with a new Warning column marker:and a new request level Warnings tab shows the details of each potential problem:There's also a new Warning tab in the Summary window that summarizes the occurrence of each type of warning in a page or set of selected requests:Customizable Grid ControlsRight clicking on a grid's column headers opens a customization menu:For example, you may want to increase the font size if you are using HttpWatch in a demonstration:New Data Columns in the Request GridThere's now more than thirty columns to choose from in the main request grid covering almost every data item that is available in HttpWatch:Customizable CSV ExportThe CSV output now can now be customized to include the data fields that you need:Data Tips Help You Understand The Recorded DataData tips are now displayed when you hold the mouse pointer over an item such as an HTTP status code:Or a header value saving you the trouble of looking up what the value means:New Icon Based Type ColumnThe new icon based type column saves space and provides an instant visual marker for different types of content. The data tip shows the underlying mime type:Coloring of Result Column ValuesThe result column now uses red to indicate errors and gray for (Cache):More Information About CookiesThe cookie tab now displays the HttpOnly and Secure flags for each cookie; including cookie values that were sent to the server. The source column shows whether the cookie value was returned from the server, set by Javascript or saved in the cookie store by a previous session:Improved Support For HAR FilesHTTP Archive (HAR files) can now be:∙Saved as HttpWatch log files (.hwl)∙Open using the HttpWatch automation interface∙Re-exported in CSV or XML formatsImproved Automation InterfaceThe automation interface allows HttpWatch to be controlled from programs written in almost any programming language (e.g. C#, , Ruby, Javascript). In version 7.0, this interface has been extended with new classes, properties and methods to support:∙Page level events∙Warnings∙Export of customized CSV output∙HTTP Archive (HAR) filesImage dimensionsThe documentation is also improved with a new format and object relationship diagrams:Uploaded File Type on POST Data tabThe content type of uploaded files is now shown in a separate column in the POST Data tab:3Version HistoryVersion 7.0.23∙Fixed: HAR files with a BOM marker can now be opened in HttpWatch∙Fixed: An access violation occurred when attempting to open a HAR file with no page groups∙Fixed: More than three fractional digits are now accepted for the seconds value in ISO8601 date/time strings when importing HAR filesVersion 7.0.22∙Improved: Added a 'Using Ruby' section to the HttpWatch Automation Reference help file ∙Fixed: Corrected typos and broken links in help files∙Fixed: An error message is no longer displayed by HttpWatch when nesting Firefox within a tab using the URL 'chrome://browser/content/browser.xul'Version 7.0.21∙Fixed: The error 'Invalid Seek offset' could be displayed when opening a log file in HttpWatch Basic EditionVersion 7.0∙New: Page event timings are now displayed in the the time chart with tooltips∙New: Added 'Page Events' to page summary window∙Improved: Requests that occur before and after the page load event now appear in a single page group∙New: Added a warning column that displays a ! for any request where a warning was issued (see Warnings section below for more information). The tool tip for the ! displays a short summary of the warnings found on the request∙New: Added a Warnings tab to display the warnings found on a request∙New: The summary window now contains a Warnings tab∙New: Right clicking on a column heading in the main grid displays a content menu of customization options∙New: Added Tools->Warnings dialog that can be used to disable individual warnings. Also available from the context menu on a warning∙New: The columns used in the main grid can be changed using the 'Select Columns' option in the grid header context menu∙New: Columns can be reordered by dragging∙New: The font used in the main grid can be changed using the 'Font...' option in the header context menu. If you choose a larger font the grid text, headings and data tips are scaled up making it useful for demos∙New: Tooltips have been added to all grid column headers to explain what the grid is displaying∙New: Data tips display explanations of certain data values (e.g. result codes) and HTTP header names∙New:Send by Email, Export CSV, Export HAR and Export XML are now available for HAR files in HttpWatch Studio∙New: Added a Type column to the POST Data tab to show the content type of uploaded files ∙New: The Result column value for failing request is colored red and (Cache) results are grayed∙New: Secure, HttpOnly and Source columns added to Cookie grid∙New: Added Tools->Options->CSV Export to allow customization of fields in CSV export files∙New: The Type column now uses icons to indicate content type. The text based column is still available as the 'Content Type' column in the Select Columns window∙New: Can now save a HAR file as a HWL file∙Changed: Has a new version 7.x HWL file format∙Changed: Renamed 'Performance' summary tab to 'Network'∙Changed: Can no longer load HWL files saved with HttpWatch version 4.x4Plug-in for Internet Explorer and FirefoxUsing the HttpWatch Plug-inWhen HttpWatch is installed, it adds a plug-in to Internet Explorer and Firefox that can be used to record and view HTTP requests. The plug-in window can be opened by clicking on the HttpWatch icon(see Getting Started ).The HttpWatch plug-in window consists of three sections:ToolbarThe toolbar is displayed at the top of the window and contains buttons that are used to control HttpWatchRequest GridThis displays a scrollable list of HTTP requests that have been recorded by HttpWatch.Request ViewSelecting an item in the requests grid causes the lower part of the HttpWatch window to display detailed information about that item. The size of this region can be adjust by dragging the horizontal line that separates it from the requests grid.Recording HTTP requests with HttpWatchThe basic steps required to control logging are as follows:1.In Internet Explorer or Firefox open the HttpWatch window by clicking on the icon or byselecting it from the menu (See Getting Started).2.Click the Record button to start recording HTTP requests.e the browser to interact with the web site you want to examine. Whilst doing this,you can close the HttpWatch window and it will carry on logging requests in thebackground.4.Individual requests can be viewed by selecting them in the request grid.5.The log can be emptied using the Clear button or logging can be halted with the Stopbutton.You can avoid logging certain types of requests by using the filter. For example, if you are only interested in the pages returned by a site and not the images you would do the following:1.Open the Filter dialog by clicking on the Filter button.2.Enable filtering by clicking on the Enable filtering check box3.Control the type of HTTP request that is logged by clicking on the Content is: checkbox and clicking on the first check box marked text/html.This will restrict HttpWatch to only recording HTTP requests that return HTML content. For more information see Using the Filter.Saving the LogThe Save button in HttpWatch allows the log to be saved as a .hwl file and loaded into HttpWatch Studio at a later date (See Save button ). The log can also be exported as an XML or CSV file.4.1Toolbar ButtonsThe main toolbar is used to control HttpWatch and contains the following buttons:∙Record∙Stop∙Clear∙View∙Summary∙Find∙Filter∙Save∙Print∙Tools∙LicenseRecordClicking this button will start recording requests in the HttpWatch.StopClicking this button will stop requests being logged.ClearClicking this button clears the contents of the log.ViewClicking this button will open the View menu and display menu items that control the appearance and behavior of the HttpWatch request grid.SummaryClicking this item shows or hides the Summary View.FindClicking this button will open the Find dialog and allow text to be quickly located anywhere in the log of requests.FilterClicking this button will open the Filter dialog and allow requests to be filtered by content type.SaveClicking this item saves the complete log to an HttpWatch log file (.hwl). The Open using HttpWatch Studio checkbox can be used to automatically load the log file into the HttpWatch Studio after it has been saved.The arrow on the toolbar next to this button provides access to Export to CSV... , Export to XML..., Export to HAR... and Send by Email...HttpWatch log files can be reopened using File->Open in HttpWatch Studio or by double clicking on a .hwl file.If you are using HttpWatch Professional Edition, the files you save can be viewed in HttpWatch Basic Edition and you can view the complete contents of files saved in HttpWatch BasicEdition. For more information about transferring log files please see Basic vs Professional Edition.PrintClicking this item opens the Print dialog.ToolsClicking this button will open the Tools menu and display menu items that allow cookies and cache entries to be cleared.LicenseClick this button to set or change the HttpWatch license key.4.2View MenuThe View menu offers the following commands:4.3 Tools MenuThe Tools menu offers the following commands:4.4Options DialogOptions Dialog TabsThe options dialog contains three tabs that can be used to configure the HttpWatch plug-in:1.General2.Recording3.CSV ExportGeneral OptionsThe General tab of the Options dialog contains the following options to configure HttpWatch:Clear log when recording startsIf this check box is selected the log is automatically cleared whenever recording is started interactively.Confirm Cache and Cookie ClearingThis controls whether a confirmation dialog is displayed when one of the clearing options is used on the Tools menu.Use shortcut keys in Internet Explorer / FirefoxClear this check box if you want to disable the use of shortcut keys in the browser. You may need to do this if an HttpWatch shortcut key clashes with a shortcut key used by a web application.Allow shortcut keys that open HttpWatchClear this check box if one of the shortcuts that open HttpWatch (e.g. Shift+F2 for Dock) is interfering with the use the keyboard shortcuts provided by the browser or a web applicationOnly allow other shortcut keys if HttpWatch is openWhen this check box is enabled, shortcut keys that do not open HttpWatch will only be processed if the HttpWatch plugin window is visible. By clearing this option you could perform an action like starting recording (Ctrl+F2) without opening HttpWatch.Recording OptionsUse Record button to start recordingThis is the default setting when you install HttpWatch. Recording is only started when you click on the record button and will continue until the Stop button is clicked.Start Recording when HttpWatch is openedIf this option is enabled HttpWatch will automatically start recording as soon as the Plug-in window is opened.Stop Recording when HttpWatch is closedThis options causes HttpWatch to stop recording when the Plug-in window is closedAutomatically Record when IE/Firefox StartsUsing this options enables automatic recording in HttpWatch, unless the browser was started using the automation interface's New method. The automatic record and saving settings are used when the next instance of the browser starts.Confirmation MessageEnabling this check box causes a confirmation message to be displayed to the user when the browser starts asking them whether they want to proceed with automatic HttpWatch recording. This setting can only be disabled in HttpWatch Professional Edition.Save Log file when IE/Firefox closes or every N minutesThis option can be used to automatically save the HttpWatch log file when the browser exits or after a period of time specified in minutes.If the value in minutes is set to 0 the log file is only written out when IE or Firefox exits. No log file is written out if the log is empty.Write Log files toAutomatically saved log files are written to this location. The following locations are support:∙Local directories, e.g. C:\LOGFILES∙Network paths, e.g. \\DEVSERVER\LOGFILES∙The temporary directory for the current user. Leave the field blank to do thisThe file name is automatically generated and contains the date/time, user name and computer name. See Automatic Recording for more information.Automatically purge log files older then N daysIf this option is selected any log files older than the specified value in days are deleted from the directory used for automatic saving. The deletion occurs just before a new log file automatically saved by HttpWatch. Only log files written by the same user on the same computer will be deleted. If any other HttpWatch log files are present in the directory they will not be deleted.CSV Export OptionsThe same fields as HttpWatch request grid:Select this option to use the columns from the request grid as CSV export fields.These fields:Select this option to manually configure which fields should be used for CSV export. Once the option is selected you can setup the fields using the Change and Reset buttons.Change...Clicking on this button opens the CSV field selection dialog. You can then choose exactly which fields should be included in the CSV output.ResetClick this button to copy the list of fields in the HttpWatch request grid into the list of manually selected fields.The same data as HttpWatch version 6.x and earlierThis options causes CSV export to use the same format as previous versions of HttpWatch.4.5Using Keyboard ShortcutsKeyboard shortcuts in HttpWatchTo do this Press thisOpen a docked HttpWatch window Shift+F2Close the HttpWatch window Shift+F8Undock the HttpWatch window Shift+F3Hide/Show the HttpWatch window Shift+F7Start recording Ctrl+F2Stop recording Ctrl+F3Clear all requests Ctrl+DelOpen Filter dialog Ctrl+F9Hide/Show the Summary window Shift+F9Hide/Show the Properties window Shift+F12Turn on filter Ctrl+F7Turn off filter Ctrl+F8Previous highlight Ctrl+Up ArrowNext highlight Ctrl+Down Arrow Save Ctrl+Shift+SExport to XML Ctrl+Shift+XExport to CSV Ctrl+Shift+C Collapse All Ctrl+Shift+Left Arrow Expand All Ctrl+Shift+Right Arrow Clear Cache and All Cookies Alt+DelClear Cache Alt+CClear All Cookies Alt+KOpen the Options window Alt+OOpen the Warnings window Alt+W5HttpWatch StudioUsing HttpWatch StudioHttpWatch Studio is a standalone viewer for HttpWatch files. It can be started from the Windows Start menu under the HttpWatch program group or by double clicking on a .hwl file.The HttpWatch Studio window consists of four sections:MenuThe toolbar is displayed at the top of the window and contains buttons that are used to control HttpWatch Studio. For more information see Menus.ToolbarThe toolbar is displayed at the top of the window and contains buttons that are used to control HttpWatch Studio. For more information see Toolbar Buttons.Request GridThis displays a scrollable list of HTTP requests that have been recorded by HttpWatch. For more information see Requests Grid.Request ViewSelecting an item in the requests grid causes the lower part of the HttpWatch window to display detailed information about that item. The size of this region can be adjust by dragging the horizontal line that separates it from the requests grid. For more information see Request View.5.1 MenusFile menuEdit menuView menuTools menuWindow menuHelp menuFile menu commandsThe File menu offers the following commands:Edit menu commandsThe Edit menu offers the following commands:View menu commandsThe View menu offers the following commands:Group By Page Controls whether requests should be grouped by pageTools menu commandsThe Tools menu offers the following commands:Window menu commandsThe Window menu offers the following commands: Cascade Arranges windows in an overlapped fashion.Help menu commandsThe Window menu offers the following commands:5.2Toolbar Buttons∙Open∙Save∙Print∙Print Preview∙Summary∙Properties∙Filter∙LicenseOpenClicking this item opens an HttpWatch log file (.hwl) in HttpWatch Studio.Clicking this item saves the complete log to an HttpWatch log file (.hwl). The Open using HttpWatch Studio checkbox can be used to automatically load the log file into the HttpWatch Studio after it has been saved.The arrow on the toolbar next to this button provides access to Export to CSV... , Export to XML..., Export to HAR... and Send by Email...HttpWatch log files can be reopened using File->Open in HttpWatch Studio or by double clicking on a .hwl file.If you are using HttpWatch Professional Edition, the files you save can be viewed in HttpWatch Basic Edition and you can view the complete contents of files saved in HttpWatch Basic Edition. For more information about transferring log files please see Basic vs Professional Edition.PrintClicking this item opens the Print dialog.Pint PreviewClicking this item opens the Print Preview window.SummaryClicking this item shows or hides the Summary View.PropertiesClicking this item shows or hides the Properties Window.FindClicking this button will open the Find dialog a nd allow text to be quickly located anywhere in the log of requests.Clicking this button will open the Filter dialog and allow requests to be filtered by content type. LicenseClick this button to set or change the HttpWatch license key.6Using HttpWatchThis section describes how to use and configure HttpWatch:HttpWatch User InterfaceUsing the FilterConfiguring Content EditorsWorking with SAP URLsSilent Install of HttpWatch6.1User InterfaceThe HttpWatch user interface in HttpWatch Studio and the plug-in for Internet Explorer and Firefox have four main sections:1. ToolbarThe toolbar is displayed at the top of the window and contains buttons that are used to control HttpWatch. For more information see Toolbar Buttons.2. Request GridThis displays a scrollable list of HTTP requests that have been recorded by HttpWatch. For more information see Requests Grid.3. Request ViewSelecting an item in the requests grid causes the lower part of the HttpWatch window to display detailed information about that item. The size of this region can be adjust by dragging the horizontal line that separates it from the requests grid. For more information see Request View.4. Summary ViewClicking on the Summary toolbar button or selecting multiple items in the requests grid opens a window that displays summary data. For more information see Summary View.Request GridWhat is the Request Grid?The upper part of the HttpWatch window displays a scrollable list of captured HTTP/HTTPS requests and is automatically updated in the HttpWatch plug-in as you access a web site. Clicking on a column heading will cause the data to be sorted in ascending order based on data in that column. A second click on the same column will reverse the sort order and display the data in descending order.Details of the currently selected item are displayed in the request view. If you selected more than one request or a page heading then a summary of the recorded data is displayed in the Summary View.For more information on the way data is displayed please refer to these sections:Page GroupingPage Level Time ChartsData ColumnsThe columns used by the grid can be changed using the Select Columns dialog. These columns are displayed by default:StartedThe time at which the request was started by the browser. This is an offset in hours, minutes and seconds from the first entry in the log.TimeThe time in seconds to complete the request. This is measured from when the browser first started processing the request until the last byte of data is read from the response.Time ChartA graphical bar chart representation of each request relative to other requests in the same page. This column can be hidden using the 'Time Chart Column' option on the view menu. The timing bars and events lines shown in this column are described in Page Level Time Charts! (Warnings)HttpWatch detects possible problems in each recorded request. An exclamation mark is displayed in this column if one or more warnings were assigned to a request.SentThis is total number of bytes sent by the browser in the HTTP request message. It includes the size of the HTTP request headers and any POST data (e.g. form values or uploaded files).ReceivedThis is total number of bytes downloaded by the browser while reading the HTTP response and includes both the size of the HTTP headers and content. For commonly encountered result values you can interpret this value as follows:200For an HTTP OK response this value is the size of HTTP response headersThe HTTP method that was used when the request was sent.ResultIf the request was successful then the HTTP status code will be shown here, e.g. 200 for OK, 404 for page not found, 403 permission denied or 304 if a requested resource has not been modified. In cases where the content was read from the cache without contacting the HTTP server, this column contains '(Cache)'.The value 'Aborted' in this column indicates that the browser cancelled the HTTP operation before it completed. This can occur if images are being downloaded when you click on a link to a different page.TypeThis shows an icon representing the type of content that was downloaded. The tooltip for each entry displays the underlying mime type, e.g. 'text/html'.URLThe address of the web content being accessed, e.g. /default.asp. HttpWatch can reformat SAP portal URLs into an easier to read format. See for Working with SAP URLs more details.Page GroupingGrouping of Recorded RequestsThe Request Grid is grouped by page unless there is no page grouping information available or grouping as been disabled using the 'Group By Page' option on the view menu.Please refer to the sections below that describe the numbered items in this screen shot:1. Expanded Page GroupThis page group starts at 0:00.000 in the log file and contains 12 requests. The page header shows the title of the page and displays a '-' symbol that can be used to collapse the group. The summary line at the end of the group shows that the page took 3.671 seconds to download, The blue color of the page header indicates that this is a normal page load.The structure and color scheme used in the time chart for the page are described in Page Level Time Charts.2. Expanded Dynamic Page GroupThis page group starts at 0:23.649 in the log file and the yellow color of the page header indicates that this was a dynamic change to a previously loaded page. Dynamic page groups are usually the result of AJAX calls or modifications made by Javascript functions or event handlers.3. Collapsed Page GroupThis page group has been collapsed using the +/- control. The page header shows the page title, total time and the number of requests.4. Ungrouped RequestsSome requests do not directly relatePage Level Time ChartHttpWatch Time ChartsColored bars are displayed in the time chart column of the Request Grid to show the relative timing of requests making up a page and the different phases of an HTTP request, e.g. connect, send, etc. Vertical lines are also included to show where certain page level events occurred.The screen shot below shows a time chart from the Google Mail home page:Request TimingsThe colored horizontal bars are described below:ColorTiming NameDescriptionBlocked The Blocked time includes any pre-processing time (such as cache lookup) and the time spent waiting for a network connection to become available. IE 7 and Firefox 2 will only create a maximum of two concurrent network connections per host name (i.e.) and will queue up requests until a network connection is available. Often the Blocked time is the most significant factor in the download time of images embedded in a web page.DNS Lookup DNS Lookup is the time required to resolve a host name (e.g. ) into a numeric IP address (e.g. 216.239.59.99).Connect Connect is the time required to create a TCP connection to the web server (or proxy). If a secure HTTPS connection is being used this time includes the SSL handshake process. Keep-Alive connections are often used to avoid the overhead of repeatedly connecting to the web server.Send Send is the time required to send the HTTP request message to the server and will depend on the amount。
