IOS Press External Memory Algorithms for String Problems
黑莓手机错误代码详解blackberry系统错误提示

黑莓手机错误代码详解blackberry系统错误提示黑莓手机错误代码详解 blackberry系统错误提示希望国内的黑莓用户对黑莓手机出错提示有个很好的认识,从而来解决问题。
101 Previous startup failed当jvm启动过程中,前一个启动的项目失败了,设备已经被重置。
这个错误表明jvm在启动时找到“启动进行中”这个标志位已经设置了,当前屏幕信息为:有意停止“系统继续重置”这个死循环,来纠正系统当前不正确的启动操作102 Invalid code in filesystem在文件系统中发现无效的代码。
手持设备的系统检查.cod文件的变动时,在一些.cod文件中检测到这个问题。
他肯可能是表明生成过程中发生了错误,即在cod文件中存在一个有问题的签名。
如果一些用户操作设备导致这个问题的发生,文件系统的代码被破坏,复位的周期将是连续循环的。
唯一的恢复方法是擦去设备并且恢复一个新的系统。
103 Cannot find starting address找不到启动的地址,用于启动系统的引导cod文件找不到。
这个错误表明一个用于引导系统的cod文件没有安装到设备上,或者格式不正确。
104 Uncaught:非预期:《java模块名》jvm诊断出一个非预期的java代码异常错误抛出,程序可以继续执行,或者手持设备可以用桌面管理器连是USB线安装一个程序调试器来查看这些错误信息。
事件日志里应该包含了异常错误的信息105 Example, DbRecSize( %d ) -> %d举例,DbRecSize( %d ) ->%d文件系统API已经为一种特定的操作返回一种错误状态码,他可能表明在jvm 上存在一个无效的或者错误的文件系统106 Graphics system error图形系统错误,在设备的图形系统里一个错误发生并被检测到107 operator new() called在jvm里,操作new()回调一个c++类,该函数代码没有被正确的从VMRamObject对象来继承,新操作符需要被正确的继承。
苹果手机设置虚拟内存的方法

苹果手机设置虚拟内存的方法
苹果手机都可以越狱,越狱后就可以设置虚拟内存,把你的手机的可用率放大到最大化吧!以下就是店铺把你所求知识技巧手把手教会!欢迎观看!
苹果手机设置虚拟内存
iOS 10 系统的越狱到来的确让人感到兴奋,但是也有不少用户称iOS 10 系统的内存不够用,导致应用闪退。
1. 通过iFile 文件管理器进入需要修改的文件的路径/System/Library/LaunchDaemons
2. 找到需要修改的文件:com.apple.jetsamproperties.N56.plist(找不到 N56 文件的锋友可以修改 N61),点击该文件,并按照下图方式修改数值:
需要提到的是,在修改之前最好先备份文件。
修改之后点击储存并退出,然后重启 iPhone,重新越狱,再次进入文件管理器。
3. 进入路径 sbin,找到 dynamic_pager 文件,文件如下图所示:点击运行之后后会出现如下提示:
点击“继续”后出现下图代码:
点击右上角的完成,退出文件管理,重启iPhone,并进入越狱模式,再次进入文件管理器,进入路径:/var/vm 查看是否出现下图中显示的swapfile0 文件。
如果此文件生成,则代表虚拟内存开启成功。
苹果手机设置虚拟内存的方法将本文的Word文档下载到电脑,方便收藏和打印推荐度:点击下载文档文档为doc格式。
内存报错解决方法(Memory error resolution)

内存报错解决方法(Memory error resolution)然后关闭并停止Windows管理规范服务。
删除WINNT \ System32 \ WBEM \库文件夹中的所有文件。
(在删除前请创建这些文件的备份副本。
)打开”服务和应用程序”,单击服务,然后打开并启动Windows 管理规范服务。
当服务重新启动时,将基于以下注册表项中所提供的信息重新创建这些文件:hkey_local_machine \软件\微软\ \\”MOFs CIMOM WBEM下面搜集几个例子给大家分析:例一:即浏览器出现”0x0a8ba9ef”指令引用的”0x03713644”内存,或者”0x70dcf39f”指令引用的”0x00000000”内存。
该内存不能为“读”。
要终止程序,请单击”确定”的信息框,单击”确定”后,又出现”发生内部错误,您正在使用的其中一个窗口即将关闭”的信息框,关闭该提示信息后,即解决方法浏览器也被关闭:1、开始-运行窗口,输入“regsvr32 actxprxy .dll”回车,接着会出现一个信息对话框”中的DllRegisterServer actxprxy.dll中成功”,确定。
再依次运行以下命令。
(这个方法有人说没必要,但重新注册一下那些。
DLL对系统也没有坏处,反正多方下手,能解决问题就行。
)regsvr32 Shdocvw.dllregsvr32 OLEAUT32.DLLregsvr32 actxprxy.dll中regsvr32 mshtml.dllmsjava.dll regsvr32regsvr32 browseui.dllregsvr32 urlmon.dll2、修复或升级IE浏览器,同时打上系统补丁。
看过其中一个修复方法是,把系统还原到系统初始的状态下升级到了建议将IE 6。
例二:有些应用程序错误:“0x7cd64998”指令参考的”0x14c96730”内存。
该内存不能为“读”。
IOS恢复系统出现各种错误的原因及解决办法

IOS恢复系统出现各种错误的原因及解决办法未知错误2:发生原因:Apple 以外的其他公司(“第三方”)制造的安全软件可能阻止iTunes 和其他Apple 应用程序与Apple 服务器或PC 上的资源之间的通信。
解决办法: 1、电脑的时间、日期、时区设置正确2、用管理员登录电脑3、暂停使用或关闭安全软件未知错误5:发生原因:没有进入dfu模式解决办法:按照刷机操作进入dfu模式再刷。
未知错误6:发生原因:未正常进入降级模式或USB故障等导致发生此错误。
解决办法:1、更新itunes2、重新进入dfu模式回复3、检查usb状况是否良好4、换电脑未知错误错误9:发生原因:如果设备与USB 总线意外断开且通信停止,就会出现此错误。
在恢复过程中手动断开设备连接时会出现这种情况。
解决方法:1、可通过执行USB 隔离故障诊断、使用其他USB 基座接口电缆、尝试其他USB 端口、在另一台电脑上恢复或者通过消除第三方安全软件的冲突来解决此问题。
2、更换数据线3、先恢复能用的固件,再刷你想要的固件。
未知错误13、14发生原因:错误14的发生常常是USB接口的不稳定或者第三方软件冲突引起的。
解决方法:1、换其他地方下载的官方或自制固件试试,不少人因此解决问题2、检查usb接口3、关闭或暂停使用第三方安全软件未知错误20、21发生原因:尝试将iPhone、iPad 或iPod touch 的软件降级会导致此错误。
解决办法:让手机进入dfu模式重新恢复自制固件。
未知错误23解决办法:1、官方固件放到此目录下:C:\Documents and Settings\用户名\Application Data\Apple Computer\iTunes\iPhone Software Updates目录中,如果没有可以自己建立2、进入dfu模式重新恢复未知错误28发生原因:USB供电不足或者硬件问题解决办法:1、换usb接口2、重新进dfu模式刷机3、过段时间再刷4、内存坏了未知错误29发生原因:硬件或者电池原因解决办法:送修未知错误1002发生原因:基带或者chip损坏解决方法:送修。
开机提示内存错误常见错误代码及解决方法!

开机提示内存错误常见错误代码及解决方法!下面是小编收集整理的一些常见的内存可能发生的错误代码和简单解决办法,一起来看看吧!为什么开机提示内存错误1.开机提示“CMOSMemorySizeMismatch”【故障表现】开机启动时,提示“CMOSMemorySizeMismatch 信息。
【故障分析】从提示信息来看,是BIOS发现主板上的内存与CMOS中存放的数值不同,所发产生此错误信息。
【故障处理】启动计算机,进入BIOS设置程序,正确设置后保存退出即可。
2.开机提示“Memorytestfail”【故障表现】开机自检时,屏幕出现“Memorytestfail”,并给出“pressF1continue,orDELtosetup”提示信息。
【故障分析】该错误提示信息,表示检测内存时出现故障。
引起该故障多半是由于使用了不同品牌或不同工作频率的内存条,从而导致兼容性问题,亦有可能是内存插槽出现问题。
【故障处理】根据可能引起故障的不同原因,可通过下面的方法解决。
⑴按照提示信息,按“F1”键继续启动计算机,如果可以正常进入系统,但发现显示的内容容量比实际安装的内存条容量要少,则说明该故障完全是由于多个内存条之间的不兼容引起的,可以通过使用同品牌同频率的内存来解决此问题。
⑵若按“F1”键不能正常进入系统,则说明内存发生严重的故障。
先应对单根内存条进行测试排除单个内存条故障。
然后再组合多根内存条进一步测试,找出不兼容的内存条。
⑶若确定所使用的内存条并不存在兼容问题,则需要进一步检查内存及主板上的内存插槽是否有损坏,因为这些问题也可能引起该故障。
3.开机提示“pressESCtoskipmemorytest”【故障表现】开机后会对内存进行很多次检测,并给出“pressESCtoskipmemorytest”提示信息,按“ESC”键可跳过内存检测,继续启动计算机。
【故障分析】多次检测内存并出现提示信息,是因为CMOS中没有启用快速加电自检功能。
bios出错英文提示信息

bios出错英文提示信息以下是店铺整理的bios出错英文提示信息大全,供大家参考和学习.Drive A error 驱动器A错误System halt 系统挂起Keyboard controller error 键盘控制器错误Keyboard error or no keyboard present 键盘错误或者键盘不存在BIOS ROM checksum error BIOS ROM校验错误Single hardisk cable fail 当硬盘使用Cable选项时硬盘安装位置不正确FDD Controller Failure BIOS 软盘控制器错误HDD Controller Failure BIOS 硬盘控制器错误Driver Error 驱动器错误Cache Memory Bad, Do not Enable Cache 高速缓存Cache损坏,不能使用Error: Unable to control A20 line 错误提示:不能使用A20地址控制线Memory write/Read failure 内存读写失败Memory allocation error 内存定位错误CMOS Battery state Low CMOS没电了Keyboard interface error 键盘接口错误Hard disk drive failure 加载硬盘失败Hard disk not present 硬盘不存在Floppy disk(s) fail (40) 软盘驱动器加载失败,一般是数据线插反,电源线没有插接,CMOS内部软驱设置错误CMOS checksum error-efaults loaded. CMOS校验错误,装入缺省(默认)设置Detecting floppy drive A media... 检测软驱A的格式Drive media is : 1.44Mb1.2Mb 720Kb 360K 驱动器格式是1.44Mb、12Mb、720kb、360kb的一种DISK BOOT FAILURE, INSERT SYSTEM DISK AND PRESS ENTER 磁盘引导失败,插入系统盘后按任意键继续Invalid partition table 无效的分区表Error loading operating system 不能装入引导系统Missing operating system 系统引导文件丢失Invalid system disk 无效的系统盘Disk I/O error, Replace the disk and press any key. 磁盘I/O错误,替换磁盘后按任意键,当C盘系统文件丢失或被破坏时出现。
苹果Crash日志

安装Xcode提示错误:An unknown error occurred. See the install log for more details.解决方法:只需把时间改为2013即可1、ios应用crash的四种类型程序崩溃: 可能是最常见的,经常发生于内存访问出错,异常,或者其他的程序错误内存不足:系统因为没有足够的内存满足程序需求从而杀死程序出现这种日志.它不同于其他日志的是它没有程序各线程的堆栈信息. Rather than be concerned about what part of your code was executing at the time of termination, you should investigate your memory usage patterns and your responses to low memory warnings. Memory usage of each process is reported in terms of number of memory pages, which as of this writing are 4KB each.强制退出:异常代码 0xdeadfa11. 这出现在用户在程序界面按下关机键知道出现"移动滑块关机",然后长按Home键.用户之所以这么做,很可能因为你的程序无响应,当然也不一定.响应超时: 异常代码 0x8badf00dios应用crash的四种类型2、如何获取crash logiPhone真机上Crash文件的存储路径为:Mac OS X:~/Library/Logs/CrashReporter/MobileDevice/windows xp:C:Documents and Settings<USERNAME>Application DataApple CommputerLogsCrashReporterMobileDevice<DEVICE_NAME>Windows vista or 7:C:Users<USERNAME>AppDataRoamingApple CommputerLogsCrashReporterMobileDevice<DEVI CE_NAME>我们走xcode的organizer的device log中获取相应应用的crash信息文件选中我们关注的应用app,找到关心的异常时间的crash记录,点击右键,选择"Reveal Log in Finder"保存到dSYM文件目录下。
iphone无法读源文件或磁盘解决方法

iphone无法读源文件或磁盘解决方法标题:解决iPhone无法读源文件或磁盘的问题当您在使用iPhone时,可能会遇到无法读取源文件或磁盘的情况。
这可能是由于多种原因引起的,包括但不限于系统错误、文件损坏、存储空间不足等。
本文将为您提供详细的解决方案,帮助您顺利解决问题。
一、了解问题的可能原因1. 系统错误:iPhone的操作系统可能会出现一些错误,导致设备无法正确识别和读取某些文件或磁盘。
2. 文件损坏:如果文件本身已经损坏或被病毒感染,那么iPhone就无法正常读取这些文件。
3. 存储空间不足:当iPhone的存储空间不足时,它可能无法加载新的文件或应用程序,从而导致无法读取源文件或磁盘的问题。
二、检查并修复系统错误1. 重启设备:这是最简单也最常用的解决方法。
只需长按电源键,然后滑动屏幕上的滑块来关闭设备。
等待几秒钟后,再次按下电源键重新启动设备。
2. 更新操作系统:确保您的iPhone运行的是最新版本的操作系统。
打开“设置”应用,点击“通用”,然后选择“软件更新”。
如果有可用的更新,按照提示进行安装。
3. 恢复出厂设置:如果以上方法都无法解决问题,您可以考虑恢复出厂设置。
请注意,这将删除设备上的所有数据和设置,因此在此之前,请确保备份重要信息。
三、处理损坏的文件1. 使用专业的文件修复工具:有许多第三方软件可以帮助您修复损坏的文件。
例如,Disk Drill是一款强大的数据恢复和文件修复工具,可以轻松修复各种类型的文件。
2. 手动删除损坏的文件:如果您知道哪些文件是损坏的,可以尝试手动删除它们。
打开“文件”应用,找到并选中要删除的文件,然后点击右下角的垃圾桶图标。
四、释放存储空间1. 删除不需要的应用程序:打开“设置”应用,选择“通用”,然后点击“iPhon e存储”。
在这里,您可以看到每个应用程序占用的空间,以及最近未使用的应用程序。
点击一个应用程序,然后点击“删除应用”以将其卸载。
memory previous uncorrectable memory error

memory previous uncorrectable
memory error
"Memory previous uncorrectable memory error" 是一个计算机错误消息,通常表示系统检测到了以前发生的无法纠正的内存错误。
这个错误可能是由硬件问题或软件问题引起的。
当计算机系统检测到内存错误时,它会尝试纠正错误。
如果错误无法纠正,系统会记录下来并显示错误消息。
"Memory previous uncorrectable memory error" 错误消息表示系统已经检测到了一个以前发生的无法纠正的内存错误。
这个错误可能是由以下原因引起的:
1. 内存故障:内存芯片可能出现故障,导致数据损坏或丢失。
2. 内存兼容性问题:某些内存模块可能与计算机系统不兼容,导致内存错误。
3. 硬件故障:其他硬件组件,如主板或处理器,可能出现故障,导致内存错误。
4. 软件问题:某些软件程序可能会导致内存错误,例如内存泄漏或缓冲区溢出。
要解决这个问题,可以尝试以下步骤:
1. 检查内存:使用内存检测工具检查内存是否存在故障。
2. 更换内存:如果内存存在故障,尝试更换内存模块。
3. 检查硬件:检查其他硬件组件是否存在故障。
4. 更新驱动程序:确保所有硬件驱动程序都是最新的。
5. 运行杀毒软件:扫描计算机以查找恶意软件。
6. 重新安装操作系统:如果以上步骤都无法解决问题,可以尝试重新安装操作系统。
如果你不确定如何解决这个问题,建议联系计算机制造商或技术支持人员寻求帮助。
几种outofmemory的解决方法

几种outofmemory的解决方法Out of Memory(内存溢出)是指应用程序在运行过程中尝试申请的内存量超出了系统所能提供的最大内存限制。
当应用程序无法获取所需的内存空间时,会导致程序崩溃或出现异常。
为了解决 Out of Memory 的问题,可以采取以下几种方法:1. 检查内存泄漏:内存泄漏是指程序中分配的内存没有得到释放,导致内存占用不断增加。
通过使用内存分析工具,如 Java VisualVM、Eclipse Memory Analyzer等,可以检测到内存泄漏的问题并进行修复。
2. 增加堆内存:可以通过修改应用程序的启动参数,增加 Java 虚拟机(JVM)的堆内存大小。
通过修改 -Xmx 参数,可以增加最大堆内存的大小,例如将 -Xmx 设置为 2GB,即可将最大堆内存增加到 2GB。
3.优化代码逻辑:检查应用程序的代码逻辑,确保不会产生无限循环、重复创建对象等导致内存消耗过大的问题。
例如,可以使用缓存对象、避免频繁创建临时对象等方式来减少内存的使用。
4.使用内存分页:可以将内存中的数据分页加载,将数据分为多个页面进行处理,每次只加载当前需要的页面。
这样可以减少一次性加载大量数据造成的内存压力。
5. 使用软引用或弱引用:软引用和弱引用是 Java 中的两种特殊引用类型,它们可以在内存不足时自动释放被引用对象的内存空间。
通过使用软引用或弱引用,可以减少内存的消耗。
6.使用内存缓存:将经常使用的数据缓存在内存中,避免频繁的磁盘读写操作。
通过使用内存缓存,可以提高数据的读取速度,并减少对物理内存的消耗。
7.分析内存使用情况:使用工具分析内存使用情况,找出内存占用过多的原因。
通过监控内存使用情况,可以发现内存泄漏、内存占用过大的问题,并进行及时的优化。
8.压缩数据:对于大量的数据存储,可以采取数据压缩的方式来减少内存的消耗。
例如,使用压缩算法对图片、文件等数据进行压缩,可以减少内存的使用量。
IPHONE刷机ITUNES提示的错误代码以及解决方案

IPHONE刷机ITUNES提示的错误代码以及解决方案在使用iTunes刷机过程中,有时会遇到各种错误代码。
下面是一些常见的错误代码以及解决方案:1. 错误代码1:该错误通常表示与iTunes服务器的通信问题。
解决方法包括检查电脑的网络连接、暂时关闭防火墙和安全软件,尝试使用不同的USB端口或连接线,以及更新iTunes至最新版本。
2.错误代码9:这个错误通常发生在更新或还原过程中,可能是由于USB连接问题、安全软件干扰或硬件问题引起的。
解决方法包括更换USB 连接线、暂时关闭防火墙和安全软件,尝试使用不同的电脑或USB端口,以及尝试使用恢复模式或DFU模式进行还原。
3.错误代码14:该错误通常表示与USB连接相关的问题。
解决方法包括更换USB端口、更换USB连接线、尝试使用不同的电脑,以及确保USB端口和连接线没有损坏或松动。
4.错误代码21:这个错误可能是由于安全软件或防火墙的干扰引起的。
解决方法包括暂时关闭防火墙和安全软件,尝试使用不同的电脑或USB端口,以及确保网络连接稳定。
5.错误代码40:该错误通常表示与USB连接问题有关。
解决方法包括更换USB端口、更换USB连接线,确保USB端口和连接线没有损坏或松动,以及尝试使用不同的电脑进行刷机。
6.错误代码2001:这个错误通常表示与硬件问题有关。
解决方法包括更换USB连接线、尝试使用不同的电脑或USB端口,以及确保USB端口和连接线没有损坏或松动。
7. 错误代码3194:该错误通常表示设备无法连接到iTunes服务器。
解决方法包括检查电脑的hosts文件,确保没有被修改,尝试使用不同的电脑或网络,以及确保网络连接稳定。
8.错误代码4013:这个错误通常发生在更新或还原过程中,可能是由于硬件问题引起的。
解决方法包括更换USB连接线、尝试使用不同的电脑或USB端口,以及确保USB端口和连接线没有损坏或松动。
9. 错误代码9006:该错误通常表示与网络连接问题有关。
ios如何扩展内存

Word 文档1 / 1 ios 如何扩展内存ios 系统的没有虚拟内存对于大部分宠爱玩游戏的果粉来说是个内伤,在ios 完善越狱后很多果粉都在查找增加虚拟内存的教程。
接下来学习啦我就给大家介绍ios 完善越狱后如何增加虚拟内存的〔方法〕..ios 系统如何扩展内存的方法:(1)下载附件把 com.apple.virtualMemory.plist 放在 /private/var/preferences com.apple.dynamic_pager.plist 放在/System/Library/LaunchDaemons(2)打开 /System/Library/LaunchDaemons/com.apple.SpringBoard.plist 文件进行修改(修改前请备份一份出来,以便以后呀还原)"'是增加下面两行代码,增加这两行上去别改其他地方的代码"'com.apple.dynamic_pager修改完按保存(3)进入/private/var 看下有没vm 的文件夹,假如没新建一个vm 文件夹(vm 文件夹确定要小写 大写的就不行),设置权限设置成图片这样按确定(4)全部完成后,重启手机,/private/var/vm 出现swapfile0就说明胜利 如图这教程开启的是128M 虚拟内存,够用了。
临时还没有512M 虚拟内存教程.. 假如觉得不好,把 com.apple.virtualMemory.plist 和 com.apple.dynamic_pager.plist 删除,把com.apple.SpringBoard.plist 还原就可以了 设置VM 文件夹权限教程先在Cydia 安装 openSSH 电脑安装 iFunBOX 安装好后 iFunBOX 进入,/private/var 右键vm 文件夹权限。
iPhone储存空间无法加载怎么办iPhone储存空间不显示解决方法
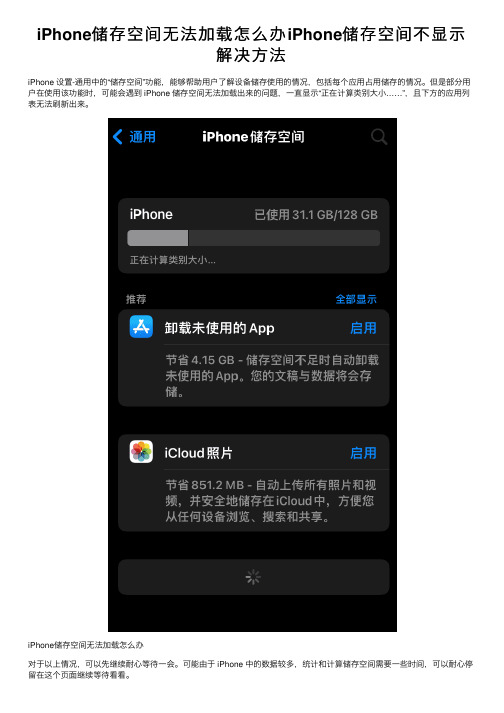
iPhone储存空间⽆法加载怎么办iPhone储存空间不显⽰
解决⽅法
iPhone 设置-通⽤中的“储存空间”功能,能够帮助⽤户了解设备储存使⽤的情况,包括每个应⽤占⽤储存的情况。
但是部分⽤户在使⽤该功能时,可能会遇到 iPhone 储存空间⽆法加载出来的问题,⼀直显⽰“正在计算类别⼤⼩……”,且下⽅的应⽤列表⽆法刷新出来。
iPhone储存空间⽆法加载怎么办
对于以上情况,可以先继续耐⼼等待⼀会。
可能由于 iPhone 中的数据较多,统计和计算储存空间需要⼀些时间,可以耐⼼停留在这个页⾯继续等待看看。
如果较长时间仍然没有刷新出来:
1.打开飞⾏模式和低电量模式,再回到“iPhone 储存空间”界⾯查看。
2.在 iOS 15 以及更新系统中,前往设置-App Store-个性化推荐中,点击“清除 App 使⽤数据”,然后再回到“iPhone 储存空间”界⾯查看。
3.尝试重启您的设备,如果重启设备后“iPhone 储存空间”仍然⽆法加载,则前往 iPhone 设置-蜂窝⽹络,在应⽤列表中找到“设置”,并关闭其联⽹权限,再重启设备。
重启完之后,回到“iPhone 储存空间”查看。
操作完毕后,再打开“设置”应⽤的联⽹权限(不会影响到后续“储存空间”的加载),以免⽆法使⽤其它需要联⽹的功能。
iPhone 提示磁盘空间不足问题解决办法

解决iphone 提示空间不足的解决方案方法一:如果你熟悉Linux,其实是比较好办的。
就是把占用空间比较多的目录挪到第二个分区上,然后建立一个符号链接链回来即可。
比如,移动照片文件的目录。
前提是能够通过SSH 登录到iPhone 上,最简单的可能只需要几条命令:# mkdir /private/var/DCIM# cp -r /DCIM/* /private/var/DCIM/# mv /DCIM /DCIM.backup# ln -s /private/var/DCIM /DCIM重启动一下,没啥问题就可以把DCIM.backup 目录删掉。
有人说你咋这么费劲? mv 一步再ln 一步不就搞定了? 我的机器上会提示你权限不足(估计是和下面说的小陷阱有关)。
土鳖一点吧,管用就成。
还有个小陷阱,如果你挪动了应用程序相关的目录,你会发现应用程序不干活了。
这时候需要修改一下/etc/fstab 文件。
默认的是这样的:# cat /etc/fstab/dev/disk0s1 / hfs rw 0 1/dev/disk0s2 /private/var hfs rw, noexec 0 2修改为:# cat /etc/fstab/dev/disk0s1 / hfs rw 0 1/dev/disk0s2 /private/var hfs rw 0 2方法二:用boss tool解决1.如果你有无线网络,你可以开启installer,在Utilities栏目下找到BossTool,然后点击install安装即可。
2.你可以使用iBus在软件列表页的“最新软件”栏目下找到BossTool,点击后,iBus将会自动安装到你的iPhone中。
当然,你也可以下载并解压缩BossTool,然后使用iBus或者iBrickr直接安装pxl文件即可。
安装并开启BossTool,在初始界面中可以看见“Free Disk Space”、“iPod Wiper”和“Jailbreak Prep”三个选项。
iphone开启原生虚拟内存教程-iphone6 虚拟内存

com.apple.SBUserNotification
com.apple.chatkit.clientcomposeserver.xpc
com.apple.UIKit.statusbarserver
com.apple.dynamic_pager
com.apple.aps.alertprovider.xpc
本文格式为 Word 版,下载可任意编辑,页眉双击删除即可。
HideUntilCheckIn ResetAtClose
com.apple.springboard.UIKit.migserver ResetAtClose
com.apple.springboard.blockableservices ResetAtClose
ResetAtClose
com.apple.bulletinboard.observerconnection com.apple.bulletinboard.publisherconnection
com.apple.icfcaboard ResetAtClose
第5页共5页
RunAtLoad
ThrottleInterval 5 UserName mobile
第4页共5页
本文格式为 Word 版,下载可任意编辑,页眉双击删除即可。
看了“iphone 开启原生虚拟内存教程”还想看: 1.怎样启用虚拟内存 2.ios 虚拟内存优化怎么设置 3.ios 虚拟内存优化有什么用 4.系统内存不够用虚拟内存大小修改步骤 5.iPhone4S 清理“垃圾”容量的方法
com.apple.springboard.alerts ResetAtClose
com.apple.springboard.carditemscontroller com.apple.springboard.icongeneration
苹果刷机出现未知错误-35 -5000分析解决方法

未知错误-35或-5000:问题的表现:当iTunes尝试下载音乐时,如果iTunes Music文件夹或其中某个文件夹的权限不正确,或者文件夹不存在或在其位置上出现不完整的替身,则可能发生一些错误,包括“-5000”和“-35”。
将显示以下警告之一:“由于发生错误,无法查看已购买的音乐(-5000 错误)。
”“错误(-35)”“iTunes Store 中发生错误。
请稍后再试。
”当您尝试从iTunes Store 下载购买的歌曲时可能会发生此类情况。
在Mac OS X 中,iTunes 可能出现此问题。
解决方法:(1)首先,请确认iTunes Music 文件夹是否存在。
如果此文件夹不存在,请参阅“iTunes:移动iTunes Music 文件夹”以了解创建新文件夹的步骤。
如果此文件夹的位置上出现替身,请验证其能否正常工作。
(2)修改iTunes Music 文件夹的权限。
此文件夹通常位于“音乐”文件夹下的iTunes 文件夹中(~/音乐/iTunes/iTunes Music)。
(3)使用Finder1.使用管理员帐户登录。
2.找到iTunes Music 文件夹。
如果您不确定iTunes Music 文件夹的位置,请启动iTunes 并打开iTunes 菜单中的“偏好设置”,然后点按“高级”。
此时您就会看到iTunes Music 文件夹的位置。
3.选择iTunes Music 文件夹。
4.在文件菜单上,选取显示简介。
5.点按显示三角形以打开“简介”窗口中的“所有权和权限”部分。
6.将权限设置如下(系统可能提示您输入管理员帐户密码):所有者:“读与写”权限群组:“只读”权限其他:“只读”权限点按“应用到包含的项”按钮。
关闭“显示简介”窗口。
7.点按“应用到包含的项”按钮。
8.关闭“显示简介”窗口。
高级:使用终端1.打开“终端”(/应用程序/实用工具)。
警告:此步骤包括通过在“终端”应用程序中输入命令来修改权限设置。
iphone 菊花门解决方法(越狱用户)

此方法针对越狱用户
iphone摄像头最近出现一个现象:菊花门,打开摄像头,始终显示菊花界面,无法实际打开。
后来某一天突然自己就好了,又能正常使用,经过多次验证,找到一个解决办法,步骤如下:
首先你是越狱,而且手机未拆机修过安装ifile,进入打开
/System/Library/CoreServices/SpringBoard.app找到N**AP.list,*号是两个数字,用属性编辑器打开后找到front-facing-camera,设置其值为false(根据系统版本不同有的直接是滑按钮使其关闭)。
继续用ifile找到目录:/private/var/mobile/Media/PhotoData,清空此目录内所有文件,退出ifile。
不要做其他任何操作,重启手机。
重启后,打开相册,会显示空白,不要着急,也不要删除任何文件,一会儿会恢复,否则有白苹果风险,退出相册,打开相机,后置摄像头显示正常。
再次用ifile将N**AP.plist的front-facing-camera值设为true后重启,再次打开摄像头,前置摄像头工作正常。
以上步骤在我手机上已经多次验证有效。
iOS-OOM(out-of-memery)

iOS-OOM(out-of-memery)Jetsam管理的⼀种crash机制,通过Signal⽆法捕捉到Jetsam,iOS不⽀持交换空间,⽆RAM和DISK之间的映射,这是因为移动端⼤多数设备均为闪存。
Jetsam crash⽇志{"bug_type":"298","timestamp":"2020-10-19 11:27:59.22 +0800","os_version":"iPhone OS 14.0.1 (18A393)","incident_id":"48A5344C-34D3-4FD1-BAF3-EAFBC1F15842"} {"crashReporterKey" : "ed5786382fe57f1c8c847aa1995b4ae301ff1eea","kernel" : "Darwin Kernel Version 20.0.0: Fri Aug 28 23:07:00 PDT 2020; root:xnu-7195.0.46~9\/RELEASE_ARM64_T8020","product" : "iPhone11,6","incident" : "48A5344C-34D3-4FD1-BAF3-EAFBC1F15842","date" : "2020-10-19 11:27:59.22 +0800","build" : "iPhone OS 14.0.1 (18A393)","timeDelta" : 89,"memoryStatus" : {"compressorSize" : 66687,"compressions" : 1574450,"decompressions" : 920590,"zoneMapCap" : 1441710080,"largestZone" : "vm pages array","largestZoneSize" : 11223040,"pageSize" : 16384,"uncompressed" : 177283,"zoneMapSize" : 127418368,"memoryPages" : {"active" : 54456,"throttled" : 0,"fileBacked" : 32811,"wired" : 52390,"anonymous" : 75798,"purgeable" : 1361,"inactive" : 53082,"free" : 4344,"speculative" : 1071}},"largestProcess" : "XXXApp","genCounter" : 1,"processes" : [{"uuid" : "213c33d7-a2a9-333e-b1e8-293fa1f3a4ce","states" : ["daemon","idle"],"age" : 1406544508698,"purgeable" : 0,"fds" : 25,"coalition" : 486,"rpages" : 75,"priority" : 0,"physicalPages" : {"internal" : [1,62]},...rpages代表页的⼤⼩,pageSize" : 16384,为当前设备页框的⼤⼩4KB通过 rpages * pageSize 就能得出当前app被杀掉时占⽤的内存## Jetsam机制它可以理解为操作系统为了控制内存资源过度使⽤⽽采⽤的⼀种管理机制。
iphone设备总是提示存储空间不足怎么办

iphone设备总是提示存储空间不足怎么办
当发现设备总是提示存储空间不足,我们第一反应便是寻找可删除的程序或所存储的东西,总是忽略了各个程序的缓存文件系统日志其实也是很占设备的存储空间!下面店铺就为大家介绍一下该如何解决这个问题吧。
如果你的设备已经越狱,便可选择利用插件iCleaner(Pro)帮帮忙!iCleaner是一款强大的清理内存的插件,你可以利用它对iOS系统的垃圾文件都清理掉。
安装前须知>>
►设备需完美越狱
►插件支持:iOS7.0.x
►需要添加源地址:/(免费)
安装教程>>
1.打开Cydia图标,然后点选右下角的搜索选项,输入「iCleaner」进行搜索。
若第一次搜索不到,可重返变更选项,点击左上方的刷新选项,待刷新完毕再次进行搜索即可。
2.找到该插件之后,点击右上方的“安装”并确认,便会自动进入安装程序。
待安装完毕后直接回到Cydia界面即可。
设置使用说明>>
成功安装后返回主桌面,便会看到「iCleaner」插件的图标,点击进入后看到工具最下方栏目分别是:更多选项,清理功能(主要功能所在)以及设置(包括语言等等)。
而在在清理功能页面,点击右上角的「Clean」即会对所列项目进行缓存文件清理(根据一般用户只要将信息选项设定为关闭,其余的设定都保持默认即可进行清理)
当然,你需要理解的是,清理的用意是释放「存储空间」而不是「清理 RAM」也不是「设备加速」。
因此,清理后设备对设备的运行速度影响不大。
iphone设备总是提示存储空间不足怎么办将本文的Word文档下
载到电脑,方便收藏和打印推荐度:点击下载文档文档为doc格式。
注销iPhoneCPU降频代码,果粉收藏必备
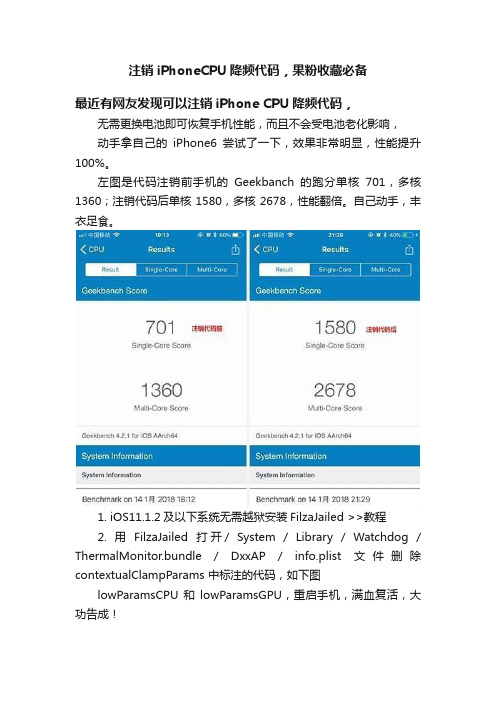
1. iOS11.1.2及以下系统无需越狱安装FilzaJailed >>教程
2. 用FilzaJailed打开/ System / Library / Watchdog / ThermalMonitor.bundle / DxxAP / info.plist文件删除contextualClampParams 中标注的代码,如下图
无需更换电池即可恢复手机性能而且不会受电池老化影响
注销iPhoneCPU降频代码,果粉收藏必备
最近有网友发现可以注销iPhone CPU降频代码,
无需更换电池即可恢复手机性能,而且不会受电池老化影响,
动手拿自己的iPhone6尝试了一下,效果非常明显,性能提升100%。
左图是代码注销前手机的Geekbanch的跑分单核701ቤተ መጻሕፍቲ ባይዱ多核1360;注销代码后单核1580,多核2678,性能翻倍。自己动手,丰衣足食。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Fundamenta Informaticae XXI(2001)1001–10171001 IOS PressExternal Memory Algorithms for String Problems∗Kangho RohSchool of Computer Science and Engineering,Seoul National University,Seoul,Koreakhroh@theory.snu.ac.krMaxime Crochemore†Institut Gaspard-Monge,Universit´e de Marne-la-Vall´e e,Paris,FranceDepartment of Computer Sciences,King’s College London,London,United KingdomMaxime.Crochemore@univ-mlv.frCostas S.IliopoulosDepartment of Computer Sciences,King’s College London,London,United Kingdomcsi@Kunsoo Park‡School of Computer Science and Engineering,Seoul National University,Seoul,Koreakpark@theory.snu.ac.krAbstract.In this paper we present external memory algorithms for some string problems.Exter-nal memory algorithms have been developed in many research areas,as the speed gap between fastinternal memory and slow external memory continues to grow.The goal of external memory algo-rithms is to minimize the number of input/output operations between internal memory and externalmemory.These years the sizes of strings such as DNA sequences are rapidly increasing.However,externalmemory algorithms have been developed for only a few string problems.In this paper we considerfive string problems and present external memory algorithms for them.They are the problems offinding the maximum suffix,string matching,periodfinding,Lyndon decomposition,andfindingthe minimum of a circular string.Every algorithm that we present here runs in a linear number ofI/Os in the external memory model with one disk,and they run in an optimal number of disk I/Os inthe external memory model with multiple disks.Keywords:External memory algorithm,maximum suffix,string matching,periodfinding,Lyndondecomposition,minimum of a circular stringAddress for correspondence:Kunsoo Park,School of Computer Science and Engineering,Seoul National University,Seoul 151-744,Korea∗A preliminary version of this paper appeared in the proceedings of17th Australasian Workshop on Combinatorial Algorithms.†Partially granted by CNRS.‡Supported by FPR05A2-341of21C Frontier Functional Proteomics Project from Korean Ministry of Science&Technology.1002K.Roh,M.Crochemore,C.S.Iliopoulos,and K.Park/External Memory Algorithms for String Problems1.IntroductionData sets in many applications are often too big tofit into main memory.In such applications it is important that algorithms take into account the memory constraints of the system[33,38].In most modern systems the memory is organized into a hierarchy.At the top level,fast internal memory which is expensive and has low storage capacity is located.At the bottom level,slower external memory which is cheap and has high storage capacity is located.Therefore the input/output communication(or simply I/O)between two levels in memory hierarchy can be a bottleneck in massive data set applications. One approach to optimizing performance is to develop algorithms that minimize I/Os between internal memory and external memory.These algorithms are referred to as external memory algorithms or more simply EM algorithms.Early work in external memory algorithms focused on fundamental problems such as sorting,matrix multiplication,and FFT[1,30,39,3].More recently,research on EM algorithms has moved towards solving graph and geometric problems[7].Work on graph problems includes transitive closure computa-tions,some graph traversal problems,and memory management for maintaining connectivity information and paths on graphs[36,29,19].String algorithmics is an important subject in algorithm research,and its applications include text processing,sequence analysis,information retrieval,DNA sequencing,etc.These years the sizes of strings such as DNA sequences are rapidly increasing.For example,the human genome sequence is too long to be loaded into the main memory of most computers.Thus external memory algorithms are necessary for string problems.However,external memory algorithms have been developed for only a few string problems:string B-trees by Ferragina and Grossi[16,17],string sorting by Arge-Ferragina-Grossi-Vitter[3],suffix trees by Farach-Ferragina-Muthukrishnan[15]and Clark and Munro[8],dictionary matching by Ferragina and Luccio[18].In this paper we present external memory algorithms for the followingfive string problems:1)finding the maximum suffix of a string[11,12],2)string matching[6,12,20,21,26,34],3)finding the period of a string[10,11],4)Lyndon decomposition of a string[2,14,25],5)finding the minimum of a circular string[5,24,35].These are well-studied and fundamental problems in string algorithmics.Wefirst give two external memory algorithms for the maximum suffix problem:one uses four mem-ory blocks and requires6 NB I/O operations,and the other uses six memory blocks and4 NBI/Ooperations,where N is the size of the given string and B is the block transfer size.Hence there is a tradeoff between memory blocks and I/O operations.Our algorithms for the remaining four problems are based on the maximum suffix algorithms;they incorporate in their algorithms either the maximum suffix algorithms directly or variations of the maximum suffix algorithms.Every algorithm we present in this paper runs in a linear number of I/Os in the external memory model with one disk.We also consider the external memory model with multiple disks.Every algorithm that we present runs in an optimal number of disk I/Os in the external memory model with multiple disks.These results with previous external memory algorithms for string problems are just the beginning of a new research area,i.e.,that of developing external memory algorithms for string problems.Many in-teresting problems in string algorithmics[22,23,13]can be considered for external memory algorithms.The remainder of the paper is organized as follows.Section2introduces the external memory model and the string problems that we consider in this paper.Section3presents the maximum suffix problem and two external memory algorithms that solve it.Section4and Section5give a string matching algo-rithm and a periodfinding algorithm based on the maximum suffix algorithm,respectively.We considerK.Roh,M.Crochemore,C.S.Iliopoulos,and K.Park /External Memory Algorithms for String Problems 1003the Lyndon decomposition problem in Section 6and the problem of finding the minimum of a circular string in Section 7.We conclude in Section 8.2.Preliminaries 2.1.External memory modelWe describe a simple but reasonably accurate model of the memory system [38].In this model,there are 2kinds of memory.One is internal memory and the other is external memory (disk).The internal memory and CPU are very fast,and disk access is slow.In order to amortize this access time for a larger amount of data,the disk reads or writes a large collection of contiguous data items at once.The collection of contiguous data items is called a block [38,7].In order to model the behavior of the I/O system,we can capture the main properties of the memory system as follows [38].•N =problem size (in units of data items),•M =internal memory size (in units of data items),•B =block transfer size (in units of data items),•D =number of disk drives.First we assume that D =1and there is just one CPU.We define a single I/O to be the process of reading or writing of a block (B contiguous items).The I/O complexity of an algorithm is the number of disk I/Os that the algorithm performs.We refer to O N B I/Os as “linear number of I/Os”in the external memory model with one disk.We also consider an external memory model with multiple disks.Vitter and Shriver introduced a practical parallel disk model which has D independent disk drives [39].In an I/O step,each of the D disks can transfer a block of size B simultaneously.When T (N )is the number of disk I/Os for an external memory model with one disk,T N D is the optimal number of disk I/Os in the model with multiple disks.2.2.Problem definitionsIn this paper we consider five string problems.All of these problems have linear time algorithms in the internal memory model.We will present an efficient external memory algorithm for every problem.We assume that there is an ordering on the alphabet Σ.The notation a ≺b means that character a is lexicographically smaller than character b .The notation a b means that a =b or a ≺b .The notations ‘≺’and ‘ ’can be extended to strings in a similar way.1Maximum Suffix.The maximum suffix of a string is the lexicographically largest suffix of the string.The maximum suffix problem is to find the maximum suffix of a given string.There are several ways that this computation can be done in internal memory.One may use suffix tree construction [28],suffix array construction [27],or factor automata construction [9].Crochemore and Perrin [12]gave a simple and elegant linear-time algorithm for the maximum suffix problem.1004K.Roh,M.Crochemore,C.S.Iliopoulos,and K.Park/External Memory Algorithms for String Problems 2String Matching.The string matching problem is tofind all occurrences of a pattern string in a text string.There are many string matching algorithms,e.g.,Knuth-Morris-Pratt(KMP)and Boyer-Moore(BM) algorithms[26,6].In this paper we consider string matching algorithms that require only constant additional memory space[12,11,20,21,34].3Period Finding.Let T[1..N]be a string.We call an integer p(1≤p≤N)a period of T if T[i]=T[i+p]for all1≤i≤N−p.The shortest period of T is called the period of T and denoted by per(T).The periodfinding problem is tofind per(T).There are some algorithms thatfind the period of a string[10,11].4Lyndon DecompositionFor a given string T,the Lyndon decomposition is a unique decomposition T=w1w2···w k with the following two properties.One is that the strings w1,w2,···,w k are non-increasing in lexico-graphic order.The other is that each w i is strictly less than any of its proper circular shift.Being circular means that string A of length n has n equivalent representations,namely A[i..n]A[1..i−1] for1≤i≤n,where A[1..0]is the empty string.A proper circular shift A[i..n]A[1..i−1]is a circular shift with i=1.Duval[14]gave an algorithm thatfinds the Lyndon decomposition of a string.Smyth and Iliopoulos[25]gave an alternative algorithm for Lyndon decomposition.5Minimum of Circular String.Let T[1..N]be a string.The minimum-of-circular-string problem is tofind the lexicographically smallest string among the N circular shifts of T.Shiloach[35]gave a linear-time algorithm that finds the minimum of a circular string.3.Maximum Suffix3.1.MS-decompositionA string T[1..N]has N suffixes.The maximum suffix of T is the lexicographically largest suffix among the N suffixes and is denoted by max(T).Let v=max(T)and u be the string such that T=uv.The string v can be written as w e w where |w|=per(v),e≥1,and w is a prefix of w.The sequence(u,w,e,w )is called the MS-decomposition of T,where MS stands for maximum suffix.An MS-decomposition of T=uw e w can be expressed by four integers(i,j,k,p)such thati=|u|,j=|uw e|,k=|w |,p=|w|.(1) The4-tuple(i,j,k,p)is called the MS-tuple of T.Example3.1.Let a string A be bbccbccbc.The maximum suffix of A is ccbccbc and its period is3.So the MS-decomposition of A is(bb,ccb,2,c),and the MS-tuple of A is(2,8,1,3)K.Roh,M.Crochemore,C.S.Iliopoulos,and K.Park /External Memory Algorithms for String Problems 10053.2.Internal memory algorithmAlgorithm 1is an internal memory maximum suffix algorithm,which is a modified version of the one in [12]so that its invariants can be clearly stated.It finds max (T )of a given string T and the period of max (T ).Theorem 3.1gives the main idea of Algorithm 1.For any string T and a character x ,max (T x )can be computed by Theorem 3.1.Theorem 3.1.[12]Let A be a string and (i,j,k,p )be the MS-tuple of A .Let x be a character and a character x be A [i +k +1].Then we havemax (Ax )= max (A )x,if x x max (A [j +1..j +k ]x ),if x ≺x.Example 3.2.We show an example for Theorem 3.1.See Figure 1.For a given string A =bbccbccbc ,the MS-tuple of A is (2,8,1,3)as shown in Example 3.1.In (a),the new character x =a is smaller than x =c .Therefore the maximum suffix of Ax becomes max (A )x =ccbccbca .In (b),the new character x =d is larger than x .Hence,max (Ax )is equal to max (cd ),which is d in this case.max(Ad)=max(cd)b b w w w’c b c c b c cd b b j j+k j j+k w w w’c b c c b c c ab b u A i+k ic c b c c b c a A b b u A i+k i (a)(b)b c c c c b c dAu w i i+k j+k jFigure 1.Example of Theorem 3.1Algorithm 1has four integers i,j,k ,and p and has a series of iterations.After an iteration,Algorithm 1maintains the following invariant.•max (T [i +1..N ])=max (T )•(0,j −i,k,p )is the MS-tuple of T [i +1..j +k ](i.e.,T [i +1..j +k ]is the maximum suffix of itself).The initial values of i,j,k ,and p are 0,1,0,and 1,respectively.The suffix T [i +1..N ]is the maximum suffix of T when j +k becomes N .Now we describe the details of an iteration.At the beginning of an iteration,we increase k by 1and compare T [i +k ]and T [j +k ].According to the ordering between T [i +k ]and T [j +k ],three cases can occur.In each case,the variables i,j,k ,and p are computed by Theorem 3.1.In case 1,T [i +k ]and T [j +k ]are the same (i.e.,the periodicity continues).If k <p ,the variables i,j,k ,and p are not changed.If k =p ,the variables i,j,k ,and p become i,j +k,0,and p ,respectively.Figure 2shows case 1.1006K.Roh,M.Crochemore,C.S.Iliopoulos,and K.Park /External Memory Algorithms for String Problems Algorithm 1Maximum suffix algorithmfunction MAXSUFFIX (T [1..N ])i =0,j =1,k =0,p =1for j +k <N dok =k +1if T [i +k ]=T [j +k ]thenif k =p then j =j +k,k =0fielse if T [i +k ] T [j +k ]thenj =j +k,k =0,p =j −ielsei =j,j =i +1,k =0,p =1fiod(T [i +1..N ]is the maximum suffix of T [1..N ])i+kT[i+k]=T[j+k]T[i+k]=T[j+k] and k<pT[i+k]=T[j+k]u w w w j+kw T[i+k]=T[j+k] and k=pu w w w i+k j+kFigure 2.Case 1In case 2,T [i +k ]is larger than T [j +k ].By Theorem 3.1,T [i +1..j +k ]is the maximum suffix of T [1..j +k ]and |T [i +1..j +k ]|becomes the period of itself.Therefore the variables i,j,k ,and p become i,j +k,0and j +k −i ,respectively.Figure 3shows this situation.In case 3,T [i +k ]is smaller than T [j +k ].In this case,max (T )and max (T [j +1..N ])are the same by Theorem 1.Thus,Algorithm 1finds the maximum suffix of T [j +1..N ]instead of that of T .The variables i,j,k ,and p become j,j +1,0,and 1,respectively.See Figure 4.Note that in case 1with k =p and case 2,the value of i +k decreases by k ,and the value of j +k decreases by k −1in case 3.After an iteration,the variable i +j +k increases by at least 1.Because i +j +k cannot be larger than 2N ,the time complexity of Algorithm 1is O (N )in internal memory.3.3.External memory algorithmFor a string T of length N ,suppose that T is composed of continuous blocks in external memory,that is T =b 1b 2···b N B .Algorithm 1runs in linear time in internal memory,but it is not an efficient algorithm in external memory.It was shown in [32]that the number of disk I/Os of Algorithm 1can be O (N ).K.Roh,M.Crochemore,C.S.Iliopoulos,and K.Park /External Memory Algorithms for String Problems 1007i+kT[i+k]>T[j+k]u j+kw Figure 3.Case 2T[i+k]<T[j+k]u j+ki+k Figure 4.Case 3We present an external memory algorithm which will be called EMMS (external memory maximum suffix)algorithm.Assume that the number of disks is one.We consider an external memory model with multiple disks later.EMMS maintains four memory blocks b I ,b I +K ,b J ,and b J +K .The initial value of each of them is the first block of T .While EMMS runs,b I and b J always have the blocks which are accessed by i and j ,respectively.b I +K and b J +K have the blocks which are accessed by i +k and j +k ,respectively,with one exception described below.We now describe the details of an iteration of EMMS.At the beginning of an iteration,variable k increases by 1.If i +k accesses the next block of b I +K after the increase of k ,EMMS reads the next block of b I +K to b I +K .Similarly,EMMS maintains b J +K .If case 1with k =p or case 2occurs,the values i +k and j become i and j +k respectively.When i +k decreases,there are three cases depending on the relation between b I and b I +K .Case X is that b I and b I +K are the same.Case Y is that b I +K is the next block of b I .Case Z is that b I +K is at least one block apart from b I .When case X or case Z occur,b I +K gets the block which is accessed by i +k .However,if case Y occurs,b I +K keeps the next block of b I (i.e.,the current block of b I +K ).This is the one exception mentioned above.In case 1with k <p ,EMMS does nothing.In case 3,i and i +k increase to j ,and j and j +k become j +1.Thus,b I and b I +K get the current block of b I .For b J and b J +K ,first b J gets the block accessed by j +1if it is not the current block of b J .Now the change for b J +K is the same as that of b I +K ,i.e.,there are three cases depending on the relation between b J and b J +K .Figure 5.Case Z1008K.Roh,M.Crochemore,C.S.Iliopoulos,and K.Park/External Memory Algorithms for String Problems Now we compute the number of disk I/Os.First we compute the maximum number of disk I/Os for i and i+k.Because b I gets the block of b J when i increases,i does not need disk I/Os.So we count disk I/Os for i+k only.The variable i+k can increase from1to N−1and it can decrease on the way.If case X or case Y occurs,no disk I/O is needed until i+k becomes equal to the current value of i+k before it decreases.For case Z,see Figure5.Let an integer a be i+k minus the position ofthe last character of b I.If case Z occurs,at most aB memory blocks can be reread until i+k becomesthe current value of itself.Hence,the maximum number of disk I/Os for i+k is N−1B +aBforall occurrences of case Z.Let an integerαbe the sum of all k’s of case Z,and let an integerβbe thenumber of case Z’s.We get N−1B +aB≤ N−1B+( aB+1)≤ N−1B+aB+β≤N−1B +kB+β≤ N−1B+ αB+β.The value ofβis at most αB+1because k is larger than Bwhen case Z occurs.Sinceαis at most N−1because j increases by k when i+k decreases by k andj is at most N−1,the maximum number of disk I/Os for i+k becomes2 N−1B + N−1B+1≤3 NB.Similarly,we can compute the maximum number of disk I/Os for j and j+k.It is also bounded by3 NB .Thus,the I/O complexity of EMMS is6 NB.Now we present a modified version of EMMS which will be called mEMMS(modified EMMS).ItsI/O complexity is4 NB .The mEMMS algorithm maintains six memory blocks b I,b I+K,b J,b J+K,b I+B,and b J+B.While mEMMS runs,b I,b I+K,b J,and b J+K always have the blocks which are accessed by i,i+k,j,and j+k,respectively.The block b I+B may have the next block of b I or is null.Similarly, b J+B may have the next block of b J or is null.We now explain how mEMMS maintains b I+B.After an iteration,b I+B maintains the following invariant.If i+k accesses a block which is not b I(i.e.,i+k accesses a block to the right of b I),b I+B has the next block of b I.Otherwise,b I+B is null.The initial value of b I+B is null and that of i+k is0.While i keeps the current value,i+k can increase only by1when it increases.Thus,thefirst block which is accessed by i+k and is not b I, must be the next block of b I.b I+B gets the next block of b I when i+k accesses it,and keeps it until i increases and accesses a block which is not the current block of b I.When i accesses a block which is not b I,b I+B becomes null.The invariant for b I+B is satisfied.Similarly,mEMMS maintains b J+B.We compute the number of disk I/Os.When case Z occurs,b I+B always has the next block of b I.Therefore in case Z,at most aB −1memory blocks are reread until i+k becomes the current value.Thus,the maximum number of disk I/Os for i+k is N−1B +( aB−1)for all occurrences of caseZ.Hence,we get N−1B +( aB−1)≤ N−1B+aB≤ N−1B+aB≤ N−1B+kB≤N−1B + αB≤2 NB.Similarly,the maximum number of disk I/Os for j is also bounded by2 NB.Thus,the I/O complexity of mEMMS is4 NB.Now we consider an external memory model with multiple disks.Disk striping is a practical paradigm with multiple disks[37,38].Figure6shows an example with D=5and B=2.The input data items are striped across the disks,and I/Os are permitted only on entire stripes,one stripe at a time.For exam-ple,data items10to19can be accessed in one disk I/O time.Note that the effect of disk striping is that the multiple disks act as a single disk with a block of size DB.The disk striping paradigm can be applied to mEMMS easily.Because mEMMS maintains six memory blocks of size DB and four integers,we assume that the internal memory size M is largeenough to have them.Then,the I/O complexity becomes4 NDB .This is an optimal I/O complexity withthe external disk model with multiple disks.K.Roh,M.Crochemore,C.S.Iliopoulos,and K.Park /External Memory Algorithms for String Problems 1009D 0D 1D 2D 3D 4stripe 00123456789stripe 110111213141516171819stripe 220212223242526272829stripe 330313233343536373839The data layout on the multiple disks with D =5and B =2.Figure 6.Disk striping4.String MatchingMany string matching algorithms find the occurrences of a pattern P inside a text T by considering increasing positions in T .At each position met during the execution of an algorithm,a scan is done to decide whether the pattern occurs there or not,and a shift is made.Thus,these kinds of algorithms perform a series of scans and shifts,and so we refer to them as scan-and-shift algorithms .For instance,the Knuth-Morris-Pratt (KMP for short)is a scan-and-shift algorithm [26].The scan of the pattern against the text at a given position can be realized in several ways.But a scan from left to right is certainly most natural.KMP maintains an array (failure function)whose size is proportional to the length of P .Whenever KMP meets a mismatch while it performs a scan,it accesses the array.Thus,if the array is too big to be stored in internal memory and mismatches occur frequently,KMP cannot be efficient in external memory.The scan-and-shift algorithm in Figure 7scans T and P ,and it stops when it meets a mismatch.Let a string A be P [1..x ]when it meets a mismatch after x matches and b be the text character at the position where a mismatch occurs.In this situation,the best length of a shift is per (Ab ).But the pre-computation of all periods leads to the same problem as KMP has.Hence,we will compute an approximation of per (Ab )without pre-computation.A mismatch occurs hereTEXTPATTERN PATTERNb aA Shift: per(Ab)Figure 7.Scan-and-shift algorithm1010K.Roh,M.Crochemore,C.S.Iliopoulos,and K.Park /External Memory Algorithms for String Problemst1rpatterntext t+rFigure 8.Variables t and r4.1.String matching using maximum suffixWe present an external memory string matching algorithm,which will be called the EMSM (external memory string matching)algorithm.EMSM has a series of iterations which consist of a scan and a shift just like other scan-and-shift algorithms.A shift in an iteration consists of three steps.Consider a string Ab as in Figure 7.The first step is to compute the MS-decomposition of Ab .The second step is to compute the length of the shift.In the third step,the pattern is shifted to the right.EMSM maintains the following variables and memory blocks.The variables t and r are the pointers on T and P as shown in Figure 8.Two pointers t +r and r are used when EMSM performs a scan.The block b T has the block which is accessed by t in T .Two blocks b T +R and b R basically have the block accessed by t +r and r in T and P ,respectively,with one exception described below.Moreover,a memory block b R −B is used,which has the previous block of b R or is null .The reason why EMSM maintains this block is to avoid the problem that a variable accesses two adjacent blocks repeatedly.The way that EMSM maintains b R −B is described below.In the second step of the shift,EMSM uses two additional memory blocks.Now we describe an iteration.EMSM performs a scan to the right and compares T [t +r ]and P [r ].During the scan,if r accesses the next block of b R ,b R −B gets the current block of b R and b R gets the next block of b R .The scan is stopped when |P |matches are found or a mismatch occurs.If |P |matches are found (i.e.,the pattern P occurs at the position t +1of T ),let a string V be T [t +1..t +|P |+1].If a mismatch between T [t +r ]and P [r ](i.e.,r −1matches occur),let V be T [t +1..t +r ].The string V is the same as Ab in Figure 7.After the scan,EMSM performs a shift.For the first step of the shift,EMSM computes the MS-decomposition of V using EMMS or mEMMS.Let uw e w and (i,j,k,p )be the MS-decomposition and the MS-tuple of V .In the second step of the shift,EMSM computes the length of the shift which is an approxima-tion of per (V )[11].If u is a suffix of w ,the length of the shift is per (X )=|w |.Otherwise,it is max(|u |,min(|w e w |,|uw e |)).The value of max(|u |,min(|w e w |,|uw e |))is not the exact value of per (V )but it is equal to or larger than a half of the length of V [11].EMSM performs a test whether u is a suffix of w or not when |u |<|w |from the positions t +i and t +j to the left.During the test,two memory blocks,one for u and the other for w ,are used.In the third step,the pattern is shifted and t increases by the length of the shift.If u is a suffix of w ,EMSM doesn’t make comparisons between T [t +1..t +|V |−|w |]and P [1..|V |−|w |],which are of the form uw e −1w after the shift [11].The variables and the blocks are updated as follows.The variable r decreases to |X |−|w |+1.If u is not a suffix of w ,the variable r becomes 1.After the updates,K.Roh,M.Crochemore,C.S.Iliopoulos,and K.Park/External Memory Algorithms for String Problems1011w w w w’i TFigure9.An Overhanging Occurrence and a Periodif r accesses b R−B or b R after the decrease,b R keeps the current block.This is the exception for b R mentioned above.Otherwise,b R gets the block which is accessed by r and b R−B becomes null.If t+r accesses b T and b T+R is the next block of b T,b T+R keeps the current block.This is the exception for b T+R mentioned above and is similar to that for b I+B in EMMS.Now we compute the number of disk I/Os.The variable t needs NB disk I/Os because it monotoni-cally increases.Consider the variable t+r.When u is a suffix of w in an iteration,t+r can decrease byat most |V|2 .The number of disk I/Os for t+r is linear by a similar argument that the number of diskI/Os for i+k is linear in EMMS.To reduce the number of disk I/Os,the technique for i+k in mEMMS can be used for t+r(i.e.,EMSM keeps the next block of b T using an additional block).Similarly,we can show that the number of disk I/Os for r is linear.During the second step of shift,the number of diskI/Os is at most 2|u|B .Because|u|is smaller than the length of the shift and the sum of the lengths ofshifts of all iterations is smaller than N,the number of disk I/Os for the second step is linear.We can also show that the number of disk I/Os for the computation of the MS-decomposition is also linear.Hence, the I/O complexity of EMSM is linear.5.Period FindingIn this section we consider the problem of computing the period of a given string.When p is a period of string T of length N,the substring T[1..N−p]is both a proper prefix and suffix of T.Therefore if EMSM meets N−i+1consecutive matches when it performs a scan at the position i,i−1is a period of T.Figure9illustrates.Therefore we can modify the EMSM algorithm tofind all periods of T.The I/O complexity for periodfinding is the same as that of EMSM.6.Lyndon DecompositionAny string T can be written uniquely T=w1w2···w n with the following two properties.1.the strings w1,w2,···,w n are non-increasing in lexicographic order.2.each w i(1≤i≤n)is strictly less than any of its proper circular shifts.。
