川大《数据结构》第二次作业
2022年四川大学计算机科学与技术专业《数据结构与算法》科目期末试卷A(有答案)

2022年四川大学计算机科学与技术专业《数据结构与算法》科目期末试卷A(有答案)一、选择题1、将两个各有N个元素的有序表归并成一个有序表,其最少的比较次数是()。
A.NB.2N-1C.2ND.N-12、从未排序序列中依次取出一个元素与已排序序列中的元素依次进行比较,然后将其放在已排序序列的合适位置,该排序方法称为()排序法。
A.插入B.选择C.希尔D.二路归并3、以下数据结构中,()是非线性数据结构。
A.树B.字符串C.队D.栈4、在下列表述中,正确的是()A.含有一个或多个空格字符的串称为空格串B.对n(n>0)个顶点的网,求出权最小的n-1条边便可构成其最小生成树C.选择排序算法是不稳定的D.平衡二叉树的左右子树的结点数之差的绝对值不超过l5、向一个栈顶指针为h的带头结点的链栈中插入指针s所指的结点时,应执行()。
A.h->next=sB.s->next=hC.s->next=h;h->next=sD.s->next=h-next;h->next=s6、排序过程中,对尚未确定最终位置的所有元素进行一遍处理称为一趟排序。
下列排序方法中,每一趟排序结束时都至少能够确定一个元素最终位置的方法是()。
Ⅰ.简单选择排序Ⅱ.希尔排序Ⅲ.快速排序Ⅳ.堆排Ⅴ.二路归并排序A.仅Ⅰ、Ⅲ、Ⅳ B.仅Ⅰ、Ⅱ、Ⅲ C.仅Ⅱ、Ⅲ、Ⅳ D.仅Ⅲ、Ⅳ、Ⅴ7、下列选项中,不能构成折半查找中关键字比较序列的是()。
A.500,200,450,180 B.500,450,200,180C.180,500,200,450 D.180,200,500,4508、每个结点的度或者为0或者为2的二叉树称为正则二叉树。
n个结点的正则二叉树中有()个叶子。
A.log2nB.(n-1)/2C.log2n+1D.(n+1)/29、有关二叉树下列说法正确的是()。
A.二叉树的度为2B.一棵二叉树的度可以小于2C.二叉树中至少有一个结点的度为2D.二叉树中任何一个结点的度都为210、对n个记录的线性表进行快速排序为减少算法的递归深度,以下叙述正确的是()。
数据结构与算法分析习题及参考答案
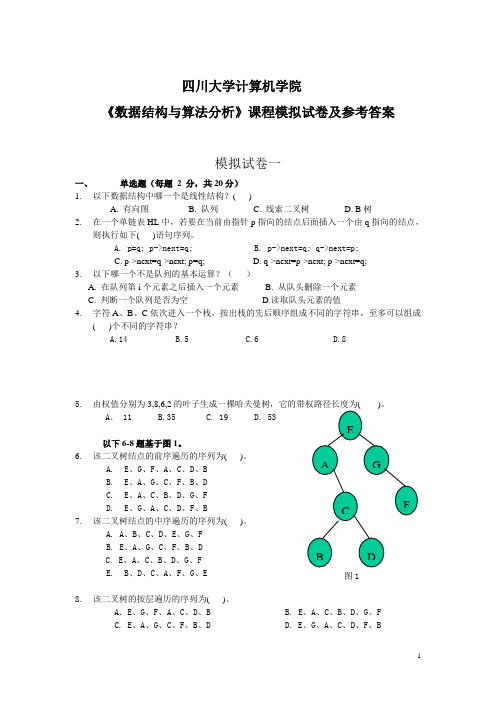
四川大学计算机学院《数据结构与算法分析》课程模拟试卷及参考答案模拟试卷一一、单选题(每题2 分,共20分)1.以下数据结构中哪一个是线性结构?( )A. 有向图B. 队列C. 线索二叉树D. B树2.在一个单链表HL中,若要在当前由指针p指向的结点后面插入一个由q指向的结点,则执行如下( )语句序列。
A. p=q; p->next=q;B. p->next=q; q->next=p;C. p->next=q->next; p=q;D. q->next=p->next; p->next=q;3.以下哪一个不是队列的基本运算?()A. 在队列第i个元素之后插入一个元素B. 从队头删除一个元素C. 判断一个队列是否为空D.读取队头元素的值4.字符A、B、C依次进入一个栈,按出栈的先后顺序组成不同的字符串,至多可以组成( )个不同的字符串?A.14B.5C.6D.85.由权值分别为3,8,6,2A. 11 B.35 C. 19 D. 53以下6-8题基于图1。
6.该二叉树结点的前序遍历的序列为( )。
A.E、G、F、A、C、D、BB.E、A、G、C、F、B、DC.E、A、C、B、D、G、FD.E、G、A、C、D、F、B7.该二叉树结点的中序遍历的序列为( )。
A. A、B、C、D、E、G、FB. E、A、G、C、F、B、DC. E、A、C、B、D、G、FE.B、D、C、A、F、G、E8.该二叉树的按层遍历的序列为( )。
A.E、G、F、A、C、D、B B. E、A、C、B、D、G、FC. E、A、G、C、F、B、DD. E、G、A、C、D、F、B9.下面关于图的存储的叙述中正确的是( )。
A.用邻接表法存储图,占用的存储空间大小只与图中边数有关,而与结点个数无关B.用邻接表法存储图,占用的存储空间大小与图中边数和结点个数都有关C. 用邻接矩阵法存储图,占用的存储空间大小与图中结点个数和边数都有关D.用邻接矩阵法存储图,占用的存储空间大小只与图中边数有关,而与结点个数无关10.设有关键码序列(q,g,m,z,a,n,p,x,h),下面哪一个序列是从上述序列出发建堆的结果?( )A. a,g,h,m,n,p,q,x,zB. a,g,m,h,q,n,p,x,zC. g,m,q,a,n,p,x,h,zD. h,g,m,p,a,n,q,x,z二、填空题(每空1分,共26分)1.数据的物理结构被分为_________、________、__________和___________四种。
数据结构第二次作业答案

数据结构第二次作业答案一、单项选择题1. C2. B3. A4. A5. D6. A7. D 8. C 9. D 10. C 11. D 12. C 13. A二、填空题1. 存储2. 先进先出3. 栈顶指针4. 队尾5. 一6. 局部变量7. 表尾8. 重数9. 3 10. 6 11. 6 12. 2h+1-1三、判断题1. 错2. 对3. 对4. 对5. 错6. 对7. 对8. 错9. 错四、运算题1.叶子结点数: 5单分支结点数:3两分支结点数:2三分支结点数:12.元素 34 56 58 63 94比较次数 2 1 3 4 43.左子树为空的所有单支结点:15,23,42,44右子树为空的所有单支结点:304.插入时造成不平衡的结点个数:45.结点 a b c d e出度 1 1 2 1 2入度 2 2 1 1 16.(1) 1,3,4,6,5,2 (3分)(2) 1,3,2,4,5,6 (3分)五、算法分析题1.利用"栈"作为辅助存储,将队列中的元素逆置(即相反次序放置)。
2.(1) q = q->lLink(2) return 1(3) return 03.1→21→32→34.(1) return PT(2) (PT=ParentPtr(BT->right,BT,X))(3) return NULL 或return 0六、算法设计题1.float poly(float x, float A[], int n) { if(!n) return A[0];else return x*poly(x, A, n-1)+A[n];}2.int BTreeHeight(BinTreeNode* BT){if(BT==NULL)//对于空树,返回-1并结束递归return –1;else{//计算左子树的高度int h1=BTreeHeight(BT->left); //计算右子树的高度int h2=BTreeHeight(BT->right); //返回树的高度if(h1>h2) return h1+1;else return h2+1;}}3.int BTreeLeafCount(BinTreeNode* BT){if(BT==NULL) return 0;else if(BT->left==NULL && BT->right==NULL) return 1;else return BTreeLeafCount(BT->left)+BTreeLeafCount(BT->right);}数据结构第三次作业答案一、单项选择题1. D2. A3. B4. C5. C6. A7. B 8. C 9. C 10. A 11. A 12. D 13. C二、填空题1. 2i+12. 最大值3. 20.54. 右子树5. 16. 右单旋转7. 2(n-1)8. 29. n-1 10. 高 11. 直接插入三、判断题1. 错2. 对3. 对4. 对5. 错6. 对7. 错8. 对四、运算题1.(1) 1,5,6,4,3,2(2) 1,5,3,2,6,42.顶点: 0 1 2 3 4 5 6路径长度: 0 16 10 14 25 21 313.拓扑序列:1,3,6,0,2,5,4,74.所有关键活动:<0,1>5,<1,3>10,<3,4>9,<4,5>12关键路径长度:365.(1)归并路数:5 (2)需要归并躺数:2答案解释:(1) 设归并路数为k,初始归并段个数m = 80,根据归并趟数计算公式S = ⎡log k m⎤ = ⎡log k80⎤ = 3得:k3≥80。
川大《计算机应用基础》第二次作业答案

川大《计算机应用基础》第二次作业答案*单顶爲棒3L亞大案兵to个屮飘・2.0 «■, Hiuo-im.柞毎中孫绐叫的琵吨中”只自一顷启荷合閘目轻卓1 .屯子工停中时申元稱的默认叔?9 ____________ .R、数宇B. 文本仁日酹D.華刖#乙用碣电子二柞卿P的厅号逆行地号萱定__________ <A. 数字#B. TSC. 砖V手圧宾今D. 字母或皈字3.Exce 2010主界五窗口中爺绸栏上时&隹tfl茅来向单元钳人_____________ .4.敌宁氐袁字D W #4.?FExrel 2QLW.鐘AE7宇咋淘W幡用时,需曙辅人的畫訐宇符扉’九逗号氐分号仁甲引总#D.飕引号5.枉Excel工"谢生界面已不包含谶项卡足______________ .C. 睹人D. iM6.Exce XHO_U恵辽件的軸认扛屋名为_____ .A. JjQtR. xlsx VC. ppLXt>. Jpeg7.在Emd 20m 霍定一^单元悟笛存人的公士y=L計2+7:则当发单元框处于舖崔曲舸蟲M丙容为A.13+2+7B.-13*2+7^C.33D.=33S.当跖Extel MID中的分變匸总时「廖季宪按仝经宇段对sae農困孑 ____________ -A. 求诩B. 洁谨U曲D.貝沛宀弘在Excel 201OP, 表讲行排强L存"排序羽话惟中S0瞎權启的排序超字蚀I限制沖—A, 1*TR” 2半C. 孙D”任总扌*量裂艮£E U 第Y典 旧何鱼M-H S &蛊仪W 5LE"怨一I长只・S E 舌徵図播, 观盟一題E 盂餾翼・<ft 空規第«{?•竄Inr 阳 Y担Qir L e K'曲ID .8IQHtecm^-Y®968但I 635床丫B幕佝型,Ga甲喷*H O I O 0CDV<圮離G卷晅览々日4|朋葩HOTON 】u3d 」9M0d 出・9T田盟星奴畐ilz B OLT盘•畐fWU 三S蛊田岁罰期毀柏習・9Q飾事1.IX 貝£&盟舉壽直&早空料fWJK姐 &借畜1K D 9.&&料團姿少s fr半昼诃»床,爸<HOTOCUodJWMOdln To圧半星対-S 5^ I td+七< 、d + _h u 1+ 宅c s d+ 宅x w壬普g y r x fe s 養 w s f i c s f e Z +4I V N ±< > s+suN +E O 珊越妁迅g 父to R W I T Y 棚HBrnoIOZ -u -o d m 、—£00翼・署・t B i s n - k te r w e k % 妖te R 帛第出 15工一:&暑・£住半博 ¥L V 5L et «< od lt ・二o d tti 龙E fe R ・IC is G卷建星也u妙HOIOZ M u一•二ft o ^ 港z・我二-f r o s ^-o vx f i .o ^19•在PowerPoint 2010中,対幻灯片的車新排序,浓!)0删!除等操咋,以及亩视荃休构忠部持別有用的观劇是A. 幻灯片視图B. 幻灯片刘比腿“c. xmsD. 备注页规圉20. ^PowerPoint 2010中,设昌幻灯片背貝格式的填充选项中包含A. 宁体・宁号、做色、风格B・廿模板.幻灯片版式C•纯色.新变.图片和纹理毎“D.壳度对比度和馆和度21•按照网书信号危廊延迟,从<1弓戊排净正昶的星A. 易理网、B. JS硕C. 城域网、广域网、城理网城域冈、广减网7 广域网、局域网局域网、广减网22.以下頑于无经按入旦联网的__________ .A. GPRS/CDMAB. 3GC. WLAND. 肛上都杲723. QQS ____ •A. AD5US?丄网软件B. 即时通(5聊天软件“D. 办公枚件24. 当丽我国的互联网主要以科护和教育为目的.从爭詐经兰性的活动。
四川大学网络教育《数据结构》第二次作业答案

首页- 我的作业列表- 《数据结构》第二次作业答案欢迎你,你的得分:76.0完成日期:2014年01月09日18点12分说明:每道小题括号里的答案是您最高分那次所选的答案,标准答案将在本次作业结束(即2014年03月13日)后显示在题目旁边。
一、单项选择题。
本大题共25个小题,每小题2.0 分,共50.0分。
在每小题给出的选项中,只有一项是符合题目要求的。
若有序表为(b, c, d, e, f, g, q, r, s, t),则在二分查找关键字b的过程中,先后进行比较的关键字依次为()。
1( A )f,c,bf,d,bg,c,bg,d,b在对n个关键字进行直接选择排序的过程中,每一趟都要从无序区选出最小关键字元素,则在进行第i趟排序之前,无序区中元素的个数为()。
2( D )ii+1n-in-i+1若用邻接矩阵表示一个有向图,则其中每一列包含的″1″的个数为()。
3( A )图中每个顶点的入度图中每个顶点的出度图中每个顶点的度图中连通分量的数目一散列表长度m为100,采用除留余数法构造散列函数,即H(K)=K%P (P<=m),,为使散列函数具有较好的性能,P的选择应是()。
4( D )991009793二维数组A[8][9]按行优先顺序存储,若数组元素A[2][3]的存储地址为1087,A[4][7]的存储地址为1153,则数组元素A[6][7]的存储地址为()。
5( A )1207120912111213对关键字序列(56, 23, 78, 92, 88, 67, 19, 34)进行增量为3的一趟希尔排序的结果为()。
6( D )(19, 23, 56, 34, 78, 67, 88, 92) )(23, 56, 78, 66, 88, 92, 19, 34)(19, 23, 34, 56, 67, 78, 88, 92)(19, 23, 67, 56, 34, 78, 92, 88对线性表,在下列哪种情况下应当采用链表表示?( )7( A )经常需要随机地存取元素经常需要进行插入和删除操作表中元素需要占据一片连续的存储空间表中元素的个数不变一个栈的输入序列为1 2 3,则下列序列中不可能是栈的输出序列的是( )。
四川大学网络学院-数据结构课程设计-参考答案

四川大学《数据结构》课程设计实验项目及内容提要(实验任选一个完成)
试读3页
数据结构实验报告
实验名称: Huffman编码(二叉树应用)
提交文档学生姓名:
提交文档学生学号:
同组成员名单:无
指导教师姓名:
指导教师评阅成绩:
指导教师评阅意见:
.
.
提交报告时间: 2020 年 3 月 26 日
目录
一、概述 (1)
二、系统分析 (1)
三、概要设计 (2)
四、详细设计 (4)
4.1 赫夫曼树的建立 (4)
4.1.1 选择选择parent 为0 且权值最小的两个根结点的算
法 (5)
4.1.2 统计字符串中字符的种类以及各类字符的个数 (7)
4.1.3构造赫夫曼树 (8)
4.2赫夫曼编码 (10)
4.2.1赫夫曼编码算法 (10)
4.2.2建立正文的编码文件 (11)
4.3代码文件的译码 (12)
五、运行与测试 (14)
六、总结与心得 (14)
参考文献................................. 错误!未定义书签。
附录..................................... 错误!未定义书签。
软件 数据结构 中期考试091109 (含部分答案)
四川大学期中考试试题(闭卷)(2009~2010学年第1学期)课程号: 311036030 课程名称:数据结构与算法分析任课教师:孙界平、张卫华适用专业年级:软件工程 2008级学号:姓名:考试须知四川大学学生参加由学校组织或由学校承办的各级各类考试,必须严格执行《四川大学考试工作管理办法》和《四川大学考场规则》。
有考试违纪作弊行为的,一律按照《四川大学学生考试违纪作弊处罚条例》进行处理。
四川大学各级各类考试的监考人员,必须严格执行《四川大学考试工作管理办法》、《四川大学考场规则》和《四川大学监考人员职责》。
有违反学校有关规定的,严格按照《四川大学教学事故认定及处理办法》进行处理。
题号一(40%) 二(40%) 三(20%) 卷面成绩得分阅卷教师阅卷时间注意事项:1. 请务必将本人所在学院、姓名、学号、任课教师姓名等信息准确填写在试卷和答题纸上。
2. 考试结束,请将试卷和答题纸一并交给监考老师。
一、单项选择题(本大题共40小题,每小题1分,共40分)提示:在每小题评阅教师得分列出的备选项中只有一个是符合题目要求的,请将其代码填写在下表中。
错选、多选或未选均无分1 2 3 4 5 21 22 23 24 256 7 8 9 10 26 27 28 29 3011 12 13 14 15 31 32 33 34 3516 17 18 19 20 36 37 38 39 401. A solution is efficient ifa) it solves a problem within the require resource constraints.b) it solves a problem within human reaction time.c) it solves a problem faster than other known solutions.d) a and b.*e) a and c.f) b and c.2. Assume that P contains n elements. The number of sets in the powerset of P isa) nb) n^2*c) 2^nd) 2^n - 1e) 2^n + 13. R is an equivalence relation on set S if it is ( )*a) reflexive, symmetric, transitive.b) reflexive, antisymmetric, transitive.c) symmetric, transitive.d) antisymmetric, transitive.e) irreflexive, symmetric, transitive.f) irreflexive, antisymmetric, transitive.4. Mathematical induction is most like ( )a) iteration.*b) recursion.c) branching.d) divide and conquer.5. Pick the growth rate that corresponds to the most efficient algorithm as n gets large: ( )a) 5n*b) 20 log nc) 2n^2d) 2^n6. Asymptotic analysis refers to: ( )a) The cost of an algorithm in its best, worst, or average case.*b) The growth in cost of an algorithm as the input size grows towardsinfinity.c) The size of a data structure.d) The cost of an algorithm for small input sizes7. For an air traffic control system, the most important metric is: ( )a) The best-case upper bound.b) The average-case upper bound.*c) The worst-case upper bound.d) The best-case lower bound.e) The average-case lower bound.f) The worst-case lower bound.8. The best case for an algorithm refers to: ( )a) The smallest possible input size.*b) The specific input instance of a given size that gives the lowest cost.c) The largest possible input size that meets the required growth rate.d) The specific input instance of a given size that gives the greatest cost.9. Here is a series of C++ statements using the list ADT in the book. ( )L1.append(10);L1.append(20);L1.append(15);If these statements are applied to an empty list, the result will looklike:a) < 10 20 15 >*b) < | 10 20 15 >c) < 10 20 15 | >d) < 15 20 10 >e) < | 15 20 10 >f) < 15 20 10 | >10. Finding the element in an array-based list with a given key value requires worst case time:a) O(1).b) O(log n).*c) O(n).d) O(n^2).11. In the linked-list implementation presented in the book, a header node is used: ( )*a) To simplify special cases.b) Because the insert and delete routines won't work correctly without it.c) Because there would be no other way to make the current pointer indicate the first element onthe list.12. When we say that a list implementation enforces homogeneity, we mean that: ( )a) All list elements have the same size.*b) All list elements have the same type.c) All list elements appear in sort order.13. All operations on a stack can be implemented in constant time except: ( )a) Pushb) Popc) The implementor's choice of push or pop (they cannot both be implemented in constant time).*d) None of the above.14. Recursion is generally implemented using ( )a) A sorted list.*b) A stack.c) A queue.15. The height of a binary tree is: ( )a) The height of the deepest node.b) The depth of the deepest node.*c) One more than the depth of the deepest node.16. A full binary tree is one in which: ( )*a) Every internal node has two non-empty children.b) all of the levels, except possibly the bottom level, are filled.17. The relationship between a full and a complete binary tree is: ( )a) Every complete binary tree is full.b) Every full binary tree is complete.*c) None of the above.18. The correct traversal to use on a BST to visit the nodes in sorted order is: ( )a) Preorder traversal.*b) Inorder traversal.c) Postorder traversal.19. When a pointer requires 4 bytes and a data element requires 12 bytes, the linked listimplementation requires less space than the array-based list implementation when the array would be: ( )*a) less than 1/4 full.b) less than 1/3 full.c) less than half full.d) less than 2/3 full.e) less than 3/4 full20. When every node of a full binary tree stores an 8-byte data field and two 4-byte child pointers,the overhead fraction is approximately: ( )a) one quarter.b) one third.*c) one half.d) two thirds.e) three quarters.f) none of the above.21. Assume a BST is implemented so that all nodes in the left subtree of a given node have valuesless than that node, and all nodes in the right subtree have values greater than or equal to that node. ( )When implementing the delete routine, we must select as its replacement:a) The greatest value from the left subtree.*b) The least value from the right subtree.c) Either of the above.22. When implementing heaps and BSTs, which is the best answer? ( )a) The time to build a BST of n nodes is O(n log n),and the time to build a heap of n nodes is O(n log n).b) The time to build a BST of n nodes is O(n),and the time to build a heap of n nodes is O(n log n).*c) The time to build a BST of n nodes is O(n log n),and the time to build a heap of n nodes is O(n).d) The time to build a BST of n nodes is O(n),and the time to build a heap of n nodes is O(n).23. Huffman coding provides the optimal coding when: ( )a) The messages are in English.b) The messages are binary numbers.*c) The frequency of occurrence for a letter is independent of its context within the message.d) Never.24. The primary ADT access functions used to traverse a general tree are: ( )a) left child and right siblingb) left child and right child*c) leftmost child and right siblingd) leftmost child and next child25. We use the parent pointer representation for general trees to solve which problem? ( )a) Shortest pathsb) General tree traversal*c) Equivalence classesd) Exact-match query26. As K gets bigger, the ratio of internal nodes to leaf nodes: ( )*a) Gets smaller.b) Stays the same.c) Gets bigger.d) Cannot be determined, since it depends on the particular configuration of the tree.27. A sequential tree representation is best used for: ( )*a) Archiving the tree to disk.b) Use in dynamic in-memory applications.c) Encryption algorithms.d) It is never better than a dynamic representation.28. The most space efficient representation for general trees will typically be: ( )a) List of children*b) Left-child/right siblingc) A K-ary tree.29. A sorting algorithm is stable if it: ( )a) Works for all inputs.*b) Does not change the relative ordering of records with identical key values.c) Always sorts in the same amount of time (within a constant factor) for a given input size.30. Which sorting algorithm does not have any practical use? ( )a) Insertion sort.*b) Bubble sort.c) Quicksort.d) Radix Sort.e) a and b.31. When sorting n records, Insertion sort has worst-case cost: ( )a) O(log n).b) O(n).c) O(n log n).*d) O(n^2)e) O(n!)f) None of the above.32. When sorting n records, Quicksort has worst-case cost: ( )a) O(log n).b) O(n).c) O(n log n).*d) O(n^2)e) O(n!)f) None of the above.33. When sorting n records, Mergesort has worst-case cost: ( )a) O(log n).b) O(n).*c) O(n log n).d) O(n^2)e) O(n!)f) None of the above.34. When sorting n records, Selection sort will perform how many swaps in the worst case? ( )a) O(log n).*b) O(n).c) O(n log n).d) O(n^2)e) O(n!)f) None of the above.35. A poor result from which step causes the worst-case behavior for Quicksort? ( )*a) Selecting the pivotb) Partitioning the listc) The recursive call36. In the worst case, the very best that a sorting algorithm can do when sorting n records is: ( )a) O(log n).b) O(n).*c) O(n log n).d) O(n^2)e) O(n!)f) None of the above.37. The basic unit of I/O when accessing a disk drive is: ( )a) A byte.*b) A sector.c) A cluster.d) A track.e) An extent.38. The most time-consuming part of a random access to disk is usually: ( )*a) The seek.b) The rotational delay.c) The time for the data to move under the I/O head.39. The simplest and most commonly used buffer pool replacement strategy is: ( )a) First in/First out.b) Least Frequently Used.*c) Least Recently Used.40. The sorting algorithm used as a model for most external sorting algorithms is: ( )a) Insertion sort.b) Quicksort.*c) Mergesort.d) Radix Sort.二、问答题(本大题共8小题,每小题5分,共40分)。
《数据结构》四川大学_期终复习试题+答案

四川大学“精品课程”计算机科学与技术专业(本科)《数据结构与算法分析》课程考试说明与模拟试卷第一部分考试说明数据结构与算法分析》是计算机科学与技术专业统设的一门重要的必修专业基础课,它主要研究数据的各种逻辑结构和在计算机中的存储结构,还研究对数据进行的插入、查找、删除、排序、遍历等基本运算或操作以及这些运算在各种存储结构上具体实现的算法。
由于本课程的主教材采用C++语言描述算法,期末卷面考试也采用C++语言描述,因而要求在做平时作业和上机实验操作时用C++开发工具(如:Visual C++或C++ Builder或Borland C++)。
下面按照主教材中各章次序给出每章的具体复习要求,以便同学们更好地进行期末复习。
第一章绪论重点掌握的内容:1. 数据结构的二元组表示,对应的图形表示,序偶和边之间的对应关系。
2. 集合结构、线性结构、树结构和图结构的特点。
3. 抽象数据类型的定义和表示方法。
4. 一维和二维数组中元素的按下标和按地址的访问方式以及相互转换,元素地址和数组地址的计算,元素占用存储空间大小和数组占用存储空间大小的计算。
5. 普通函数重载和操作符函数重载的含义,定义格式和调用格式。
6. 函数定义中值参数和引用参数的说明格式及作用,函数被调用执行时对传送来的实际参数的影响。
7. 算法的时间复杂度和空间复杂度的概念,计算方法,数量级表示。
8. 一个简单算法的最好、最差和平均这三种情况的时间复杂度的计算。
对于本章的其余内容均作一般掌握。
第二章线性表重点掌握的内容:1. 线性表的定义及判别和抽象数据类型的描述,线性表中每一种操作的功能,对应的函数名、返回值类型和参数表中每个参数的作用。
2. 线性表的顺序存储结构的类型定义,即List类型的定义和每个域的定义及作用。
3. 线性表的每一种运算在顺序存储结构上实现的算法,及相应的时间复杂度。
4.链接存储的概念,线性表的单链接和双链接存储的结构,向单链表中一个结点之后插入新结点或从单链表中删除一个结点的后继结点的指针链接过程。
数据结构II试卷B答案年月

东北大学继续教育学院数据结构II 试卷(作业考核线上) B 卷(共 10 页)一、单选题(每小题2分,共10小题,20分)[ A ] 1.抽象数据类型的三个组成部分分别为A.数据对象、数据关系和基本操作B.数据元素、逻辑结构和存储结构C.数据项、数据元素和数据类型D.数据元素、数据结构和数据类型[ D ] 2.下列各式中,按增长率由小至大的顺序正确排列的是A.n,n!,2n ,n3/2 B.n3/2,2n,n logn,2100C.2n,log n,n logn,n3/2 D.2100,logn, 2n, n n[ A ] 3. 已知指针p和q分别指向某单链表中第一个结点和最后一个结点。
假设指针s指向另一个单链表中某个结点,则在s所指结点之后插入上述链表应执行的语句为A. q->next=s->next;s->next=p;B. s->next=p;q->next=s->next;C. p->next=s->next;s->next=q;D. s->next=q;p->next=s->next;[ C ] 4.二维数组A[20][10]采用行优先的存储方法,若每个元素占2个存储单元,且第1个元素的首地址为200,则元素A[8][9]的存储地址为A.374 B.576C.378 D.580[ B ] 5.设有一个顺序栈的入栈序列是a、b、c,则3个元素都出栈的可能不同排列个数为A.4 B.5C. 6D. 7[ D ] 6. 设树T的度为4,其中度为1,2,3和4的结点个数分别为4,2,1,1 则T中的叶子数为A.5 B.6C.7 D.8[ C ] 7.以下说法不正确的是A.无向图中的极大连通子图称为连通分量B.连通图的广度优先搜索中一般要采用队列来暂存刚访问过的顶点C.图的深度优先搜索中一般要采用栈来暂存刚访问过的顶点D.有向图的遍历不可采用广度优先搜索[ B ] 8. 假设在构建散列表时,采用线性探测解决冲突。
2019级春数据结构第二次作业

题号题目内容答案答题时间1"空串与空格串是相同的,这种说法____。
A.正确B.不正确"B02"串是一中特殊的线性表,其特殊性体现在____。
A.可以顺序存储B.数据元素是一个字符C.可以链接存储D.数据元素可以是多个字符"B03"设有两个串p和q,求q在p中首次出现的位置的运算称作____。
A.连接B.模式匹配C.求子串D.求串长"B04"设串s1=’ABCDEFG’,s2=’PQRST’,函数con (x,y)返回x和y串的连接串,subs(s,i,j)返回串s的从序号i的字符开始的j个字符组成的子串,len(s)返回串s的长度,则con (subs (s1,2,len (s2)), subs (s1,len (s2),2))的结果串是____。
A.BCDEFB.BCDEFGC.BCPQRSTD.BCDEFEF"D05"常对数组进行的两种基本操作是____。
A.建立与删除B.索引和修改C.对数据元素的存取和修改D.查找与索引"C06"二维数组M的成员是6个字符(每个字符占一个存储单元,即一个字节)组成的串,行下标i的范围从0到8,列下标j的范围从0到9,则存放M 至少需要①_ _个字节;M 数组的第8列和第5行共占②____个字节。
A.90B.180C.240D.540E.108F.114G.54H.60"DE07"二维数组A中,每个元素的长度为3个字节,行下标i从0到7,列下标j从0到9,从首地址SA开始连续存放在存储器内,存放该数组至少需要的字节数是____。
A.80B.100C.240D.270"C08"由于二叉树中每个结点的度最大为2,所以二叉树是一种特殊的树,这种说法____。
A.正确B.错误"B09"假定在一棵二叉树中,双分支结点数为15,单分支结点数为30个,则叶子结点数为个。
川大软件数据结构选择题库

_______________________________ 少年易学老难成,一寸光阴不可轻-百度文库一Chapter 1 Data Structures and Algorithms: Instructor's CD questions1.The primary purpose of most computer programs isa)to perform a mathematical calculation.*b) to store and retrieve information.c)to sort a collection of records.d)all of the above.e)none of the above.2.An integer is aa)) simple typeb)aggregate typec)composite typed)a and be)none of the above3.A payroll records is aa)simple typeb)aggregate typec)composite type*d) a and b e) none of the above4.Which of the following should NOT be viewed as an ADT?a)listb)integerc)array*d) none of the above5.A mathematical function is most like a*a) Problemb)Algorithmc)Program6.An algorithm must be or do all of the following EXCEPT:a)correctb)composed of concrete steps*c) ambiguousd)composed of a finite number of stepse)terminate7.A solution is efficient ifa.it solves a problem within the require resource constraints.b.it solves a problem within human reaction time.1_______________________________ 少年易学老难成,一寸光阴不可轻-百度文库_______ c.it solves a problem faster than other known solutions.d.a and b.*e. a and c.f. b and c.8.An array isa)A contiguous block of memory locations where each memory location storesa fixed-length data item.b)An ADT composed of a homogeneous collection of data items, each data item identified by a particular number.c)a set of integer values.*d) a and b.e)a and c.f)b and c.9.Order the following steps to selecting a data structure to solve a problem.(1)Determine the basic operations to be supported.(2)Quantify the resource constraints for each operation.(3)Select the data structure that best meets these requirements.(4)Analyze the problem to determine the resource constraints that anysolution must meet.a)(1, 2, 3, 4)b)(2, 3, 1, 4)c)(2, 1, 3, 4)*d) (1, 2, 4, 3)e) (1, 4, 3, 2)10.Searching for all those records in a database with key value between 10 and 100 is known as:a) An exact match query.*b) A range query.c)A sequential search.d)A binary search.Chapter 2 Mathematical Preliminaries: Instructor's CD questions1.A set has the following properties:a)May have duplicates, element have a position.b)May have duplicates, elements do not have a position.c)May not have duplicates, elements have a position.*d) May not have duplicates, elements do not have a position._______________________________ 少年易学老难成,一寸光阴不可轻-百度文库2.A sequence has the following properties:a)) May have duplicates, element have a position.b)May have duplicates, elements do not have a position.c)May not have duplicates, elements have a position.d)May not have duplicates, elements do not have a position.3.For set F, the notation |P| indicatesa)) The number of elements in Pb)The inverse of Pc)The powerset of F.d)None of the above.4.Assume that P contains n elements. The number of sets in the powerset of P isa)nb)n A2*c) 2A nd)2A n - 1e) 2A n + 15.If a sequence has n values, then the number of permutations for that sequence will bea)nb)n A2c)n A2 - 1d)2A n*e) n!6.If R is a binary relation over set S, then R is reflexive if*a) aRa for all a in S.b)whenever aRb, then bRa, for all a, b in S.c)whenever aRb and bRa, then a = b, for all a, b in S.d)whenever aRb and aRc, then aRc, for all a, b, c in S.7.If R is a binary relation over set S, then R is transitive ifa)aRa for all a in S.b)whenever aRb, then bRa, for all a, b in S.c)whenever aRb and bRa, then a = b, for all a, b in S.*d) whenever aRb and aRc, then aRc, for all a, b, c in S.8.R is an equivalence relation on set S if it isa)) reflexive, symmetric, transitive.b)reflexive, antisymmetric, transitive.c)symmetric, transitive.少年易学老难成,一寸光阴不可轻-百度文库d)antisymmetric, transitive.e)irreflexive, symmetric, transitive.f)irreflexive, antisymmetric, transitive.9.For the powerset of integers, the subset operation defines *a) a partial order.b)a total order.c)a transitive order.d)none of the above.10.log nm is equal toa) n + m*b) log n + log mc)m log nd)log n - log m11.A close-form solution isa) an analysis for a program.*b) an equation that directly computes the value of a summation.c) a complete solution for a problem.12.Mathematical induction is most likea) iteration.*b) recursion.c)branching.d)divide and conquer.13.A recurrence relation is often used to model programs witha)for loops.b)branch control like "if" statements.*c) recursive calls.d) function calls.14.Which of the following is not a good proof technique.a) proof by contradiction.*b) proof by example.c) proof by mathematical induction.15.We can use mathematical induction to:a) Find a closed-form solution for a summation.*b) Verify a proposed closed-form solution for a summation.c) Both find and verify a closed-form solution for a summation._______________________________ 少年易学老难成,一寸光阴不可轻-百度文库一Chapter 3 Algorithm Analysis: Instructor's CD questions1.A growth rate applies to:a)the time taken by an algorithm in the average case.b)the time taken by an algorithm as the input size grows.c)the space taken by an algorithm in the average case.d)the space taken by an algorithm as the input size grows.e)any resource you wish to measure for an algorithm in the average case.*f) any resource you wish to measure for an algorithm as the input size grows.2.Pick the growth rate that corresponds to the most efficient algorithm as n gets large:a) 5n*b) 20 log nc)2nA2d)2A n3.Pick the growth rate that corresponds to the most efficient algorithm when n =4.a)5nb)20 log nc)2nA2*d)2A n4.Pick the quadratic growth rate.a)5nb)20 log n*c) 2nA2d) 2An5.Asymptotic analysis refers to:a) The cost of an algorithm in its best, worst, or average case.*b) The growth in cost of an algorithm as the input size grows towards infinity.c)The size of a data structure.d)The cost of an algorithm for small input sizes6.For an air traffic control system, the most important metric is:a)The best-case upper bound.b)The average-case upper bound.c)) The worst-case upper bound.d)The best-case lower bound._______________________________ 少年易学老难成,一寸光阴不可轻-百度文库__________e)The average-case lower bound.f)The worst-case lower bound.7.When we wish to describe the upper bound for a problem we use:a)) The upper bound of the best algorithm we know.b)The lower bound of the best algorithm we know.c)We can't talk about the upper bound of a problem because there can alwaysbe an arbitrarily slow algorithm.8.When we describe the lower bound for a problem we use:a)The upper bound for the best algorithm we know.b)the lower bound for the best algorithm we know.c)The smallest upper bound that we can prove for the best algorithm that could possibly exist.*d) The greatest lower bound that we can prove for the best algorithm that could possibly exist.9.When the upper and lower bounds for an algorithm are the same, we use:a)big-Oh notation.b)big-Omega notation.*c) Theta notation.d)asymptotic analysis.e)Average case analysis.f)Worst case analysis.10. When performing asymptotic analysis, we can ignore constants and low order terms because:*a) We are measuring the growth rate as the input size gets large.b)We are only interested in small input sizes.c)We are studying the worst case behavior.d)We only need an approximation.11.The best case for an algorithm refers to:a) The smallest possible input size.*b) The specific input instance of a given size that gives the lowest cost.c)The largest possible input size that meets the required growth rate.d)The specific input instance of a given size that gives the greatest cost.12.For any algorithm:a)) The upper and lower bounds always meet, but we might not know what they are.少年易学老难成,一寸光阴不可轻-百度文库b)The upper and lower bounds might or might not meet.c)We can always determine the upper bound, but might not be able to determine the lower bound.d)We can always determine the lower bound, but might not be able to determine the upper bound.13.If an algorithm is Theta(f(n)) in the average case, then it is: a) Omega(f(n)) in the best case.*b) Omega(f(n)) in the worst case.c) O(f(n)) in the worst case.14.For the purpose of performing algorithm analysis, an important property ofa basic operation is that:a)It be fast.b)It be slow enough to measure.c)Its cost does depend on the value of its operands.*d) Its cost does not depend on the value of its operands.15.For sequential search,a) The best, average, and worst cases are asymptotically the same.*b) The best case is asymptotically better than the average and worst cases.c)The best and average cases are asymptotically better than the worst case.d)The best case is asymptotically better than the average case, and the average case is asymptotically better than the worst case.Chapter 4 Lists, Stacks and Queues: Instructor's CD questions1.An ordered list is one in which:a) The element values are in sorted order.*b) Each element a position within the list.2.An ordered list is most like a:a)set.b)bag.c)) sequence.3.As compared to the linked list implementation for lists, the array-based listimplementation requires:a)More spaceb)Less space*c) More or less space depending on how many elements are in the list._______________________________ 少年易学老难成,一寸光阴不可轻-百度文库4.Here is a series of C++ statements using the list ADT in the book.L1.append(10);L1.append(20);L1.append(15);If these statements are applied to an empty list, the result will look like:a)< 10 20 15 >*b) < | 10 20 15 >c)< 10 20 15 | >d)< 15 20 10 >e)< | 15 20 10 >f)< 15 20 10 | >5.When comparing the array-based and linked implementations, the array-based implementation has:a)) faster direct access to elements by position, but slower insert/delete from the current position.b)slower direct access to elements by position, but faster insert/delete from the current position.c)both faster direct access to elements by position, and faster insert/delete from the current position.d)both slower direct access to elements by position, and slower insert/delete from the current position.6.For a list of length n, the linked-list implementation's prev function requiresworst-case time:a)O(1).b)O(log n).*c) O(n).d) O(n A2).7.Finding the element in an array-based list with a given key value requiresworst case time:a)O(1).b)O(log n).*c) O(n).d) O(n A2).8.In the linked-list implementation presented in the book, a header node isused:*a) To simplify special cases._______________________________ 少年易学老难成,一寸光阴不可轻-百度文库一b)Because the insert and delete routines won't work correctly without it.c)Because there would be no other way to make the current pointer indicatethe first element on the list.9.When a pointer requires 4 bytes and a data element requires 4 bytes, thelinked list implementation requires less space than the array-based list implementation when the array would be:a)less than 1/4 full.b)less than 1/3 full.*c) less than half full.d)less than 第full.e)less than 34 fullf)never.10.When a pointer requires 4 bytes and a data element requires 12 bytes, thelinked list implementation requires less space than the array-based list implementation when the array would be:a)) less than 1/4 full.b)less than 1/3 full.c)less than half full.d)less than 2/3 full.e)less than 34 fullf)never.11.When we say that a list implementation enforces homogeneity, we meanthat:a) All list elements have the same size.*b) All list elements have the same type.c) All list elements appear in sort order.12.When comparing the doubly and singly linked list implementations, we findthat the doubly linked list implementation*a) Saves time on some operations at the expense of additional space.b)Saves neither time nor space, but is easier to implement.c)Saves neither time nor space, and is also harder to implement.13. We use a comparator function in the Dictionary class ADT:a)to simplify implementation.*b) to increase the opportunity for code reuse.c) to improve asymptotic efficiency of some functions.14.All operations on a stack can be implemented in constant time except:少年易学老难成,一寸光阴不可轻-百度文库a) Pushb)Popc)The implementor's choice of push or pop (they cannot both be implementedin constant time).*d) None of the above.15.Recursion is generally implemented usinga) A sorted list.*b) A stack.c) A queue.Chapter 5 Binary Trees: Instructor's CD questions1.The height of a binary tree is:a)The height of the deepest node.b)The depth of the deepest node.*c) One more than the depth of the deepest node.2.A full binary tree is one in which:*a) Every internal node has two non-empty children.b) all of the levels, except possibly the bottom level, are filled.3.The relationship between a full and a complete binary tree is:a)Every complete binary tree is full.b)Every full binary tree is complete.*c) None of the above.4.The Full Binary Tree Theorem states that:a)) The number of leaves in a non-empty full binary tree is one more than the number of internal nodes.b)The number of leaves in a non-empty full binary tree is one less than the number of internal nodes.c)The number of leaves in a non-empty full binary tree is one half of the number of internal nodes.d)The number of internal nodes in a non-empty full binary tree is one half of the number of leaves.5.The correct traversal to use on a BST to visit the nodes in sorted order is:a) Preorder traversal.*b) Inorder traversal.c) Postorder traversal.6. When every node of a full binary tree stores a 4-byte data field,10少年易学老难成,一寸光阴不可轻-百度文库two 4-byte child pointers, and a 4-byte parent pointer, theoverhead fraction is approximately:a)one quarter.b)one third.c)one half.d)two thirds.*e) three quarters.f) none of the above.7.When every node of a full binary tree stores an 8-byte data field and two 4-byte child pointers, the overhead fraction is approximately:a)one quarter.b)one third.*c) one half.d)two thirds.e)three quarters.f)none of the above.8.When every node of a full binary tree stores a 4-byte data field and theinternal nodes store two 4-byte child pointers, the overhead fraction is approximately:a)one quarter.b)one third.*c) one half.d)two thirds.e)three quarters.f)none of the above.9.If a node is at position r in the array implementation for a complete binarytree, then its parent is at:a)) (r - 1)/2 if r > 0b)2r + 1 if (2r + 1) < nc)2r + 2 if (2r + 2) < nd)r - 1 if r is evene)r + 1 if r is odd.10.If a node is at position r in the array implementation for a complete binarytree, then its right child is at:a)(r - 1)/2 if r > 0b)2r + 1 if (2r + 1) < n*c) 2r + 2 if (2r + 2) < nd)r - 1 if r is evene)r + 1 if r is odd.11_______________________________ 少年易学老难成,一寸光阴不可轻-百度文库—11.Assume a BST is implemented so that all nodes in the left subtree of agiven node have values less than that node, and all nodes in the rightsubtree have values greater than or equal to that node. Whenimplementing the delete routine, we must select as its replacement:a) The greatest value from the left subtree.*b) The least value from the right subtree.c) Either of the above.12.Which of the following is a true statement:a)In a BST, the left child of any node is less than the right child, and in a heap, the left child of any node is less than the right child.*b) In a BST, the left child of any node is less than the right child, but in a heap, the left child of any node could be less than or greater than the right child.c)In a BST, the left child of any node could be less or greater than the right child, but in a heap, the left child of any node must be less than the right child.d)In both a BST and a heap, the left child of any node could be either less than or greater than the right child.13.When implementing heaps and BSTs, which is the best answer?a)The time to build a BST of n nodes is O(n log n), and the time to build a heap of n nodes is O(n log n).b)The time to build a BST of n nodes is O(n), and the time to build a heap of n nodes is O(n log n).*c) The time to build a BST of n nodes is O(n log n), and the time to build a heap of n nodes is O(n).d) The time to build a BST of n nodes is O(n), and the time to build a heap of n nodes is O(n).14.The Huffman coding tree works best when the frequencies for letters area) Roughly the same for all letters.*b) Skewed so that there is a great difference in relative frequencies for various letters.15.Huffman coding provides the optimal coding when:a)The messages are in English.b)The messages are binary numbers.*c) The frequency of occurrence for a letter is independent of its context within the message.d) Never.12_______________________________ 少年易学老难成,一寸光阴不可轻-百度文库一Chapter 6 Binary Trees: Instructor's CD questions1.The primary ADT access functions used to traverse a general tree are: a) left child and right siblingb) left child and right child*c) leftmost child and right siblingd) leftmost child and next child2.The tree traversal that makes the least sense for a general treeis:a) preorder traversal*b) inorder traversalc) postorder traversal3.The primary access function used to navigate the general tree when performing UNION/FIND is:a)left childb)leftmost childc)right childd)right sibling*e) parent4.When using the weighted union rule for merging disjoint sets, the maximum depth for any node in a tree of size n will be:a) nearly constant*b) log nc)nd)n log ne)n A25.We use the parent pointer representation for general trees to solve which problem?a)Shortest pathsb)General tree traversal*c) Equivalence classesd) Exact-match query6. When using path compression along with the weighted union rule for merging disjoint sets, the average cost for any UNION or FIND operation in a tree of size n will be:*a) nearly constantb)log nc)nd)n log n13_______________________________ 少年易学老难成,一寸光阴不可轻-百度文库一7.The most space efficient representation for general trees will typically be:a) List of children*b) Left-child/right siblingc) A K-ary tree.8.The easiest way to represent a general tree is to:a) convert to a list.*b) convert to a binary tree.c) convert to a graph.9.As K gets bigger, the ratio of internal nodes to leaf nodes:a)) Gets smaller.b)Stays the same.c)Gets bigger.d)Cannot be determined, since it depends on the particular configuration of the tree.10.A sequential tree representation is best used for:*a) Archiving the tree to disk.b)Use in dynamic in-memory applications.c)Encryption algorithms.d)It is never better than a dynamic representation.Chapter 7 Internal Sorting: Instructor's CD questions1.A sorting algorithm is stable if it:a) Works for all inputs.*b) Does not change the relative ordering of records with identical key values.c) Always sorts in the same amount of time (within a constant factor) for a given input size.2.Which sorting algorithm does not have any practical use?a) Insertion sort.*b) Bubble sort.c)Quicksort.d)Radix Sort.e)a and b.3.When sorting n records, Insertion sort has best-case cost:a)O(log n).14_______________________________ 少年易学老难成,一寸光阴不可轻-百度文库*b) O(n).c)O(n log n).e)O(n!)f)None of the above.4.When sorting n records, Insertion sort has worst-case cost:a)O(log n).b)O(n).c)O(n log n).*d) O(n A2)e)O(n!)f)None of the above.5.When sorting n records, Quicksort has worst-case cost:a)O(log n).b)O(n).c)O(n log n).*d) O(n A2)e)O(n!)f)None of the above.6.When sorting n records, Quicksort has average-case cost:a)O(log n).b)O(n).c)) O(n log n).d)O(n A2)e)O(n!)f)None of the above.7.When sorting n records, Mergesort has worst-case cost:a)O(log n).b)O(n).*c) O(n log n).d)O(n A2)e)O(n!)f)None of the above.8.When sorting n records, Radix sort has worst-case cost:a)O(log n).b)O(n).c)O(n log n).d)O(n A2)e)O(n!)15少年易学老难成,一寸光阴不可轻-百度文库*f) None of the above.9.When sorting n records with distinct keys, Radix sort has a lower bound of:a)Omega(log n).b)Omega(n).*c) Omega(n log n).d)Omega(n A2)e)Omega(n!)f)None of the above.10.Any sort that can only swap adjacent records as an average case lower bound of:a)Omega(log n).b)Omega(n).c)Omega(n log n).*d) Omega(n A2)e)Omega(n!)f)None of the above.11.The number of permutations of size n is:a)O(log n).b)O(n).c)O(n log n).d)O(n A2)*e) O(n!)f)None of the above.12.When sorting n records, Selection sort will perform how many swaps in the worst case?a) O(log n).*b) O(n).c)O(n log n).d)O(n A2)e)O(n!)f)None of the above.13.Shellsort takes advantage of the best-case behavior of which sort?*a) Insertion sortb)Bubble sortc)Selection sortd)Shellsorte)Quicksortf)Radix sort16_______________________________ 少年易学老难成,一寸光阴不可轻-百度文库_______________14.A poor result from which step causes the worst-case behavior for Quicksort?*a) Selecting the pivotb)Partitioning the listc)The recursive call15.In the worst case, the very best that a sorting algorithm can do when sorting n records is:a)O(log n).b)O(n).*c) O(n log n).d)O(n A2)e)O(n!)f)None of the above.Chapter 8 File Processing and External Sorting: Instructor's CD questions1.As compared to the time required to access one unit of data frommain memory, accessing one unit of data from disk is:a)10 times faster.b)1000 times faster.c)1,000,000 time faster.d)10 times slower.e)1000 times slower.*f) 1,000,000 times slower.2.The most effective way to reduce the time required by a disk-based program is to:a) Improve the basic operations.*b) Minimize the number of disk accesses.c)Eliminate the recursive calls.d)Reduce main memory use.3.The basic unit of I/O when accessing a disk drive is:a)A byte.*b) A sector.c)A cluster.d)A track.e)An extent.4.The basic unit for disk allocation under DOS or Windows is:a)A byte.b)A sector.*c) A cluster.17少年易学老难成,一寸光阴不可轻-百度文库d) A track.e) An extent.5.The most time-consuming part of a random access to disk is usually: *a) The seek.b)The rotational delay.c)The time for the data to move under the I/O head.6.The simplest and most commonly used buffer pool replacement strategy is:a)First in/First out.b)Least Frequently Used.*c) Least Recently Used.7.The C++ programmer's view of a disk file is most like:a)) An array.b)A list.c)A tree.d)A heap.8.In external sorting, a run is:a)) A sorted sub-section for a list of records.b)One pass through a file being sorted.c)The external sorting process itself.9.The sorting algorithm used as a model for most external sorting algorithms is:a)Insertion sort.b)Quicksort.*c) Mergesort.d) Radix Sort.10.Assume that we wish to sort ten million records each 10 bytes long (for a total file size of 100MB of space). We have working memory of size 1MB, broken into 1024 1K blocks. Using replacement selection and multiway merging, we can expect to sort this file using how many passes through the file?a)About 26 or 27 (that is, log n).b)About 10.c)4.*d) 2.Chapter 9 Searching: Instructor's CD questions18少年易学老难成,一寸光阴不可轻-百度文库1.Which is generally more expensive?a) A successful search.*b) An unsuccessful search.2.When properly implemented, which search method is generally the most efficient for exact-match queries?a)Sequential search.b)Binary search.c)Dictionary search.d)Search in self-organizing lists*e) Hashing3.Self-organizing lists attempt to keep the list sorted by:a) value*b) frequency of record accessc) size of record4.The 80/20 rule indicates that:a) 80% of searches in typical databases are successful and 20% are not.*b) 80% of the searches in typical databases are to 20% of the records.c) 80% of records in typical databases are of value, 20% are not.5.Which of the following is often implemented using a self-organizing list? *a) Buffer pool.b)Linked list.c)Priority queue.6.A hash function must:a)) Return a valid position within the hash table.b)Give equal probability for selecting an slot in the hash table.c)Return an empty slot in the hash table.7.A good hash function will:a)Use the high-order bits of the key value.b)Use the middle bits of the key value.c)Use the low-order bits of the key value.*d) Make use of all bits in the key value.8.A collision resolution technique that places all records directlyinto the hash table is called:a)Open hashing.b)Separate chaining.*c) Closed hashing.d) Probe function.19少年易学老难成,一寸光阴不可轻-百度文库9.Hashing is most appropriate for:a)In-memory applications.b)Disk-based applications.*c) Either in-memory or disk-based applications.10.Hashing is most appropriate for:a)) Range queries.b)Exact-match queries.c)Minimum/maximium value queries.11.In hashing, the operation that will likely require more record accesses is: *a) insertb) deleteChapter 10 Indexing: Instructor's CD questions1.An entry-sequenced file stores records sorted by:a)Primary key value.b)Secondary key value.*c) Order of arrival.d) Frequency of access.2.Indexing is:a) Random access to an array.*b) The process of associating a key with the location of a corresponding data record.c) Using a hash table.3.The primary key is:a)) A unique identifier for a record.b)The main search key used by users of the database.c)The first key in the index.4.Linear indexing is good for all EXCEPT:a)Range queries.b)Exact match queries.*c) Insertion/Deletion.d)In-memory applications.e)Disk-based applications.5.An inverted list provides access to a data record from its:a) Primary key.20______________________________ 少年易学老难成,一寸光阴不可轻-百度文库*b) Secondary key.c) Search key.6.ISAM degrades over time because:a) Delete operations empty out some cylinders.*b) Insert operations cause some cylinders to overflow.c) Searches disrupt the data structure.7.Tree indexing methods are meant to overcome what deficiency in hashing? *a) Inability to handle range queries.。
2009-2010《数据结构与算法》试卷及答案

四川大学期末考试试题(闭卷)(2009~2010学年第2学期)课程号: 311036030 课程名称:数据结构与算法(B卷)任课教师:孙界平杨秋辉张卫华适用专业年级:软件工程 2009级学号:姓名:考试须知四川大学学生参加由学校组织或由学校承办的各级各类考试,必须严格执行《四川大学考试工作管理办法》和《四川大学考场规则》。
有考试违纪作弊行为的,一律按照《四川大学学生考试违纪作弊处罚条例》进行处理。
四川大学各级各类考试的监考人员,必须严格执行《四川大学考试工作管理办法》、《四川大学考场规则》和《四川大学监考人员职责》。
有违反学校有关规定的,严格按照《四川大学教学事故认定及处理办法》进行处理。
题号一(30%) 二(10%) 三(15%) 四(20%) 五(25%) 卷面成绩得分阅卷时间注意事项:1. 请务必将本人所在学院、姓名、学号、任课教师姓名等信息准确填写在试题纸和添卷纸上;2. 请将答案全部填写在本试题纸上;3. 考试结束,请将试题纸、添卷纸和草稿纸一并交给监考老师。
一、单项选择题(本大题共15小题,每小题2分,共30分)提示:在每小题列评阅教师得分出的四个备选项中只有一个是符合题目要求的,请将其代码填写在答题纸上。
错选、多选或未选均无分。
1. A mathematical function is most like a ( A )(A) Problem(B) Algorithm(C) Program(D) Code2. A recurrence relation is often used to model programs with ( C )(A) for loops.(B) branch control like "if" statements.(C) recursive calls.(D) function calls.3. For an air traffic control system, the most important metric is: ( C )(A) The best-case upper bound.(B) The average-case upper bound.(C) The worst-case upper bound.(D) The best-case lower bound.4. For a list of length n, the linked-list implementation's prev() function requires worst-case time: ( C )(A) O(1).(B) O(log n).(C) O(n).(D) O(n2).5. Assume a BST is implemented so that all nodes in the left subtree of a given node have values less than that node, and all nodes in the right subtree have values greater than or equal to that node. When implementing the delete routine, we must select as its replacement: ( B )(A) The greatest value from the left subtree.(B) The least value from the right subtree.(C) Either of the above.(D) The root.6. The primary ADT access functions used to traverse a general tree are: ( C )(A) left child and right sibling(B) left child and right child(C) leftmost child and right sibling(D) leftmost child and next child7. A sorting algorithm is stable if it: ( B )(A) Works for all inputs.(B) Does not change the relative ordering of records with identical key values.(C) Always sorts in the same amount of time (within a constant factor) for a given input size.(D) Most efficient.8. When sorting n records, Quicksort has worst-case cost: ( D )(A) O(log n).(B) O(n).(C) O(n log n).(D) O(n2)9. The basic unit of I/O when accessing a disk drive is: ( B )(A) A byte.(B) A sector.(C) A cluster.(D) A track.10. The sorting algorithm used as a model for most external sorting algorithms is: ( C )(A) Insertion sort.(B) Quicksort.(C) Mergesort.(D) Radix Sort.11. Which of the following is often implemented using a self-organizing list? ( A )(A) Buffer pool.(B) Linked list.(C) Priority queue.(D) B-Tree12. An entry-sequenced file stores records sorted by: ( C )(A) Primary key value.(B) Secondary key value.(C) Order of arrival.(D) Frequency of access.13. The primary difference between a B-tree and a B+-tree is: ( A )(A) The B+-tree store records only at the leaf nodes.(B) The B+-tree has a higher branching factor.(C) The B+-tree is hight balanced.(D) The B+-tree is smaller.14. The goal of a topological sort is to: ( B )(A) Sort all of the graph vertices by value.(B) Sort all of the graph vertices so that each vertex is listed prior to any others that depend onit.(C) Sort all of the graph vertices by distance from the source vertex.(D) None of the above.15. Which is a good example of a greedy algorithm? ( B )(A) Floyd's all-pairs shortest path algorithm.(B) Prim's minimal-cost spanning tree algorithm.(C) Depth-first search.(D) T opological sorting.二、判断题(本大题共5小题,每小题2分,共10分)提示:正确打T,错误打F,评阅教师得分将其结果填写在答题纸上。
数据结构和其算法第二次作业

数据结构和其算法第二次作业在学习计算机科学的道路上,数据结构和算法就像是基石,为我们构建起高效、稳定的程序大厦提供了坚实的支撑。
这次的第二次作业,让我对数据结构和算法有了更深入的理解和体会。
我们先来谈谈数据结构。
数据结构是指数据元素之间的关系和组织方式。
常见的数据结构有数组、链表、栈、队列、树和图等。
数组是一种最简单也最常用的数据结构。
它就像是一排整齐排列的盒子,每个盒子都有一个固定的位置,通过索引可以快速访问其中的元素。
但是,数组的长度一旦确定就很难改变,如果要插入或删除元素,可能会涉及到大量的数据移动,效率较低。
链表则不同,它像是一串珠子,每个珠子通过指针连接到下一个珠子。
链表的插入和删除操作非常方便,只需要修改指针的指向即可,但访问特定位置的元素就需要从头开始遍历,速度相对较慢。
栈是一种“后进先出”的数据结构,想象一下往一个桶里放东西,最后放进去的会最先被拿出来。
栈在函数调用、表达式求值等场景中发挥着重要作用。
队列则是“先进先出”,就像排队买票,先来的先得到服务。
它常用于任务调度、消息传递等方面。
树是一种层次结构的数据结构,比如二叉树、二叉搜索树等。
二叉搜索树的特点是左子树的所有节点值小于根节点值,右子树的所有节点值大于根节点值,这使得查找、插入和删除操作的效率都比较高。
图则是由顶点和边组成,可以用来表示各种复杂的关系,比如交通网络、社交关系等。
说完数据结构,再来说说算法。
算法是解决特定问题的一系列步骤。
好的算法应该具有正确性、可读性、健壮性和高效性等特点。
比如排序算法,常见的有冒泡排序、插入排序、选择排序、快速排序和归并排序等。
冒泡排序就像水里的泡泡,每次比较相邻的两个元素,如果顺序不对就交换位置,一轮下来最大的元素就“浮”到了末尾。
插入排序则是将待排序的元素依次插入到已排序的部分中。
选择排序是每次选择未排序部分的最小元素放到已排序部分的末尾。
快速排序是一种分治的算法,通过选择一个基准元素,将数组分成两部分,然后对这两部分分别进行排序。
数据结构2014(全英文) 四川大学期末考试试题

四川大学期末考试试题(闭卷)A (2013 ——2014 学年第 2 学期)
课程号:课序号:1 课程名称:数据结构(in English ) 任课教师:成绩:
适用专业年级:13电子商务学生人数:159印题份数:160学号:姓名:
2 题间不留空,一般应题卷分开教务处试题编号:
教务处试题编号:
四川大学期末考试试题(闭卷)B (2013 ——2014 学年第 2 学期)
课程号:402079030课序号:0,1 ,2 课程名称:数据结构任课教师:黄勇成绩:
适用专业年级:13电子商务学生人数:159印题份数:160学号:姓名:
注:1试题字迹务必清晰,书写工整。
本题 2 页,本页为第 1 页
2 题间不留空,一般应题卷分开教务处试题编号:
four railway carriages numbered {1,2,3,4 }, which
Programming Questions.(2*10=20)
Write a program that finds the height of a binary tree.
Write an algorithm to delete the i th element in the queue.
本题 2 页,本页为第 2 页
教务处试题编号:。
