!!!操作系统全英文期末考试题(带答案)
计算机专业英语期末复习题及参考答案

一单选题 (共10题,总分值30分 )1. hacker (3 分)A. 音频B. 应用软件C. 机器语言D. 软件测试E. 结构化程序设计F. 内存G. 功能测试H. 关系数据库I. 黑客J. 防火墙2. functional testing (3 分)A. 音频B. 应用软件C. 机器语言D. 软件测试E. 结构化程序设计F. 内存G. 功能测试H. 关系数据库I. 黑客J. 防火墙3. relational database (3 分)A. 音频B. 应用软件C. 机器语言D. 软件测试E. 结构化程序设计F. 内存G. 功能测试H. 关系数据库I. 黑客J. 防火墙4. firewall (3 分)A. 音频B. 应用软件C. 机器语言D. 软件测试E. 结构化程序设计F. 内存G. 功能测试H. 关系数据库I. 黑客J. 防火墙5. software testing (3 分)A. 音频B. 应用软件C. 机器语言D. 软件测试E. 结构化程序设计F. 内存G. 功能测试H. 关系数据库I. 黑客J. 防火墙6. audi (3 分)B. 应用软件C. 机器语言D. 软件测试E. 结构化程序设计F. 内存G. 功能测试H. 关系数据库I. 黑客J. 防火墙7. application software (3 分)A. 音频B. 应用软件C. 机器语言D. 软件测试E. 结构化程序设计F. 内存G. 功能测试H. 关系数据库I. 黑客J. 防火墙8. machine language (3 分)A. 音频B. 应用软件C. 机器语言D. 软件测试E. 结构化程序设计F. 内存G. 功能测试H. 关系数据库J. 防火墙9. memory (3 分)A. 音频B. 应用软件C. 机器语言D. 软件测试E. 结构化程序设计F. 内存G. 功能测试H. 关系数据库I. 黑客J. 防火墙10. structured programming (3 分)A. 音频B. 应用软件C. 机器语言D. 软件测试E. 结构化程序设计F. 内存G. 功能测试H. 关系数据库I. 黑客J. 防火墙二填空题 (共1题,总分值5分 )11. Microsoft Word XP is the current Window versionof Word, and documents created in Word XP can beeasily _________________________________Excel, Power Point and Access files. In the interface of Word, the_________________________________displays the name of the current application and name of the current document;the_________________________________lists the names of the menus available;the_________________________________gives the user quick access to frequently used editingfunctions; the_________________________________enables theuser to change left and right margin.toolbarrulertitle barmenu barincorporate into (5 分)三翻译题 (共10题,总分值50分 )12. hard disk (5 分)13. 集成开发环境(5 分)14. 通用串行总线(5 分)15. network security (5 分)16. software maintenance (5 分)17. electronic commerce (5 分)18. 广域网(5 分)19. 结构化查询语言(5 分)20. management information system (5 分)21. 面向对象编程(5 分)四阅读理解 (共1题,总分值15分 )22. The Internet, then known as ARPANET, wasbrought online in 1969, which initiallyconnected four major computers at universitiesin the southwestern US . The early Internet wasused by computer experts , engineers, scientists, and librarians. There was nothing friendly about it. There were no home or office personalcomputers in those days, and anyone who used it, whether a computer professional or an engineeror scientist or librarian, had to learn to use a very complex system.The Internet matured in the 1970's as a result of the TCP/IP architecture. As the commands for E-mail, FTP , and telnet were standardized, it became a lot easier for non-technical people to learn to use the nets. It was not easy by today' s standards by any means, but it did open up use of the Internet to many more people in universities in particular. Other departments besides the libraries, computer, physics, and engineering departments found ways to make good use of the nets -- to communicate with colleagues around the world and to share files and resources.In 1991, the first really friendly interface to the Internet was developed at the University of Minnesota. The University wanted to develop a simple menu system to access files and information on campus through their local network.Since the Internet was initially funded by the government, it was originally limited to research, education, and government uses. Commercial uses were prohibited unless they directly served the goals of research and education. This policy continued until the early 1990's, when independent commercial networks began to grow.(四) Choose the best answer according to Passage C.(根据上文的内容选择正确的答案。
计算机操作系统期末测试题及答案解析(两套)

操作系统期末试题1一、单项选择题(每题2分,共20分)1.在操作系统中,进程的最基本的特征是( A )。
A. 动态性和并发性 B.顺序性和可再现性C.与程序的对应性 D.执行过程的封闭性2.为了使系统中各部分资源得到均衡使用,就必须选择对资源需求不同的作业进行合理搭配。
这项工作是由( A )完成的。
A.作业调度 B. 进程调度C.用户自己D.管理人员3.虚拟存储器给用户提供了特大的地址空间。
实际上它是( C )。
A. 扩大物理内存容量 B.扩大物理外存容量C. 扩大逻辑内存容量 D.扩大逻辑外存容量4.引入缓冲技术的主要目的是( C )。
A. 改善用户编程环境 B.提高CPU的处理速度C.提高CPU与设备之间的并行程度 D.降低计算机的硬件成本5.在微内核结构的现代操作系统中,进程( A )。
A. 只是资源分配的单位 B.只是调度运行的单位C.既是资源分配的单位,又是调度运行的单位 D.失去作用6. (A)没有多道程序设计的特点。
A.dosB.unixB.windows D.os/27. 下列四个操作系统中,是分时系统的为(C)。
A.cp/mB.ms-dosC.unixD.windows nt8. 在分时系统中,时间片一定,(B),响应时间越长。
A.内存越多B.用户数越多C.后备队列D.用户数越少9. 用户要在程序一级获得系统帮助,必须通过(D)。
A.进程调度B.作业调度C.键盘命令D.系统调用10. 操作系统是一组(C)。
A.文件管理程序B.中断处理程序C.资源管理程序D.设备管理程序二、判断题(选择你认为正确的叙述划√,认为错误的划×并说明原因。
每题2分,共10分)1.用户程序应与实际使用的物理设备无关,这种特性就称作与设备无关性。
( )2.处理机调度可分为三级:高级、中级和低级。
在所有的系统中,都必须具备这三级调度。
( )3.信号量机制是一种有效的实现进程同步与互斥的工具。
信号量只能由PV 操作来改变。
操作系统期末考试题和答案

操作系统期末考试题和答案一、选择题(每题2分,共20分)1. 在操作系统中,进程和程序的主要区别是()。
A. 程序是静态的,进程是动态的B. 程序是动态的,进程是静态的C. 程序是操作系统的一部分,进程是用户的一部分D. 程序是用户的一部分,进程是操作系统的一部分答案:A2. 下列关于死锁的描述中,错误的是()。
A. 死锁是指两个或多个进程在执行过程中,因争夺资源而造成的一种僵局B. 死锁产生的原因是系统资源不足C. 死锁的四个必要条件是互斥、占有和等待、不可剥夺和循环等待D. 死锁可以预防,但无法避免答案:D3. 在分页存储管理中,页表的作用是()。
A. 将逻辑地址转换为物理地址B. 将物理地址转换为逻辑地址C. 存储进程的执行状态D. 存储进程的资源分配情况答案:A4. 虚拟内存技术的主要目的是()。
A. 提高CPU的利用率B. 提高内存的利用率C. 提高I/O设备的利用率D. 提高磁盘的利用率答案:B5. 在操作系统中,文件的逻辑结构通常采用()。
A. 顺序结构B. 链接结构C. 索引结构D. 树形结构答案:A6. 操作系统中,文件的物理结构通常采用()。
A. 顺序结构B. 链接结构C. 索引结构D. 树形结构答案:B7. 在操作系统中,文件的共享是指()。
A. 多个进程可以同时访问同一个文件B. 多个进程可以同时修改同一个文件C. 多个进程可以同时创建同一个文件D. 多个进程可以同时删除同一个文件答案:A8. 在操作系统中,文件的保护是指()。
A. 防止文件被非法访问B. 防止文件被非法修改C. 防止文件被非法删除D. 以上都是答案:D9. 在操作系统中,文件的组织方式通常采用()。
A. 顺序文件B. 随机文件C. 索引文件D. 以上都是答案:D10. 在操作系统中,文件的存取方式通常采用()。
A. 顺序存取B. 随机存取C. 直接存取D. 以上都是答案:D二、填空题(每题2分,共20分)1. 操作系统的主要功能包括______、______、文件管理、设备管理和______。
操作系统期末考试试题及答案PDF

操作系统期末考试试题及答案PDF一、单项选择题(每题2分,共20分)1. 在现代操作系统中,进程和程序的主要区别是()。
A. 进程是一个动态的概念,程序是一个静态的概念B. 进程是程序的执行过程,程序是进程的代码集合C. 进程是程序的代码和数据的集合,程序是进程的执行过程D. 进程是程序的代码集合,程序是进程的执行过程2. 在操作系统中,进程调度的目的是()。
A. 决定进程的执行顺序B. 提高CPU的利用率C. 保证进程的公平性D. 以上都是3. 下列关于死锁的描述,不正确的是()。
A. 死锁是指两个或多个进程在执行过程中,因争夺资源而造成的一种僵局B. 死锁产生的四个必要条件是互斥、占有和等待、不可剥夺、循环等待C. 死锁的预防方法是破坏占有和等待条件D. 死锁的避免方法是通过银行家算法来实现4. 在操作系统中,虚拟内存的主要作用是()。
A. 提高内存的访问速度B. 提高内存的利用率C. 扩大内存的容量D. 以上都是5. 下列关于文件系统的的说法,不正确的是()。
A. 文件系统是操作系统中负责管理文件的系统B. 文件系统提供了文件的创建、删除、读取和写入等操作C. 文件系统将文件存储在磁盘上,并且可以对文件进行加密D. 文件系统允许多个用户同时访问同一个文件6. 在操作系统中,分页管理方式的主要优点是()。
A. 减少了内存的碎片B. 简化了内存管理C. 提高了内存的利用率D. 以上都是7. 下列关于进程通信的说法,不正确的是()。
A. 进程通信是指进程之间交换信息的过程B. 进程通信的方式有共享内存、消息传递、信号量等C. 进程通信可以提高系统的并发性D. 进程通信会导致进程的阻塞8. 在操作系统中,中断处理程序的主要作用是()。
A. 处理硬件设备发出的中断信号B. 处理用户发出的中断信号C. 处理操作系统发出的中断信号D. 处理进程发出的中断信号9. 下列关于操作系统的用户界面的说法,不正确的是()。
操作系统习题(英文版)

操作系统习题(英文版)Chapter 1 – Computer Systems OverviewTrue / False Questions:1. T / F – The operating system acts as an interface between the computerhardware and the human user.2. T / F –One of the processor’s main functions is to exchange data withmemory.3. T / F –User-visible registers are typically accessible to systemprograms but are not typically available to application programs.4. T / F – Data registers are general purpose in nature, but may berestricted to specific tasks such as performing floating-point operations.5. T / F –The Program Status Word contains status information in the formof condition codes, which are bits typically set by the programmer as aresult of program operation.6. T / F – The processing required for a single instruction ona typicalcomputer system is called the Execute Cycle.7. T / F – A fetched instruction is normally loaded into the InstructionRegister (IR).8. T / F –An interrupt is a mechanism used by systemmodules to signalthe processor that normal processing should be temporarily suspended.9. T / F – To accommodate interrupts, an extra fetch cycle is added to theinstruction cycle.10. T / F –The minimum information that must be saved before theprocessor transfers control to the interrupt handler routine is theprogram status word (PSW) and the location of the current instruction.11. T / F – One approach to dealing with multiple interrupts is to disable allinterrupts while an interrupt is being processed.12. T / F – Multiprogramming allows the processor to make use of idle timecaused by long-wait interrupt handling.13. T / F – In a two-level memory hierarchy, the Hit Ratio is defined as thefraction of all memory accesses found in the slower memory.14. T / F – Cache memory exploits the principle of locality by providing asmall, fast memory between the processor and main memory.15. T / F – In cache memory design, block size refers to the unit of dataexchanged between cache and main memory16. T / F – The primary problem with programmed I/O is that the processormust wait for the I/O module to become ready and mustrepeatedlyinterrogate the status of the I/O module while waiting.Multiple Choice Questions:1. The general role of an operating system is to:a. Act as an interface between various computersb. Provide a set of services to system usersc. Manage files for application programsd. None of the above2. The four main structural elements of a computer system are:a. Processor, Registers, I/O Modules & Main Memoryb. Processor, Registers, Main Memory & System Busc. Processor, Main Memory, I/O Modules & System Busd. None of the above3. The two basic types of processor registers are:a. User-visible and Control/Status registersb. Control and Status registersc. User-visible and user-invisible registersd. None of the above4. Address registers may contain:a. Memory addresses of datab. Memory addresses of instructionsc. Partial memory addressesd. All of the above5. A Control/Status register that contains the address of the nextinstruction to be fetched is called the:a. Instruction Register (IR)b. Program Counter (PC)c. Program Status Word (PSW)d. All of the above6. The two basic steps used by the processor in instruction processingare:a. Fetch and Instruction cyclesb. Instruction and Execute cyclesc. Fetch and Execute cyclesd. None of the above7. A fetched instruction is normally loaded into the:a. Instruction Register (IR)b. Program Counter (PC)c. Accumulator (AC)d. None of the above8. A common class of interrupts is:a. Programb. Timerc. I/Od. All of the above9. When an external device becomes ready to be serviced by theprocessor, the device sends this type of signal to the processor:a. Interrupt signalb. Halt signalc. Handler signald. None of the above10. Information that must be saved prior to the processor transferringcontrol to the interrupt handler routine includes:a. Processor Status Word (PSW)b. Processor Status Word (PSW) & Location of next instructionc. Processor Status Word (PSW) & Contents of processor registersd. None of the above11. One accepted method of dealing with multiple interrupts is to:a. Define priorities for the interruptsb. Disable all interrupts except those of highest priorityc. Service them in round-robin fashiond. None of the above12. In a uniprocessor system, multiprogramming increases processorefficiency by:a. Increasing processor speedb. Taking advantage of time wasted by long wait interrupt handlingc. Eliminating all idle processor cyclesd. All of the above13. As one proceeds down the memory hierarchy (i.e., from inboardmemory to offline storage), the following condition(s) apply:a. Increasing cost per bitb. Decreasing capacityc. Increasing access timed. All of the above14. Small, fast memory located between the processor and main memoryis called:a. WORM memoryb. Cache memoryc. CD-RW memoryd. None of the above15. When a new block of data is written into cache memory, the followingdetermines which cache location the block will occupy:a. Block sizeb. Cache sizec. Write policyd. None of the above16. Direct Memory Access (DMA) operations require the followinginformation from the processor:a. Address of I/O deviceb. Starting memory location to read from or write toc. Number of words to be read or writtend. All of the aboveQuestions1.1,1.4,1.7,1.8Problems1.1,1.3,1.4,1.5,1.7Chapter 2 – Operating System OverviewTrue / False Questions:1. T / F –An operating system controls the execution of applications andacts as an interface between applications and the computer hardware.2. T / F – The operating system maintains information that can be used forbilling purposes on multi-user systems.3. T / F – The operating system typically runs in parallel with applicationpro grams, on it’s own special O/S processor.4. T / F –One of the driving forces in operating system evolution isadvancement in the underlying hardware technology.5. T / F – In the first computers, users interacted directly with thehardware and operating systems did not exist.6. T / F – In a batch-processing system, the phrase “control is passed to ajob” means that the processor is now fetching and executinginstructions in a user program.7. T / F –Uniprogramming typically provides better utilization of systemresources than multiprogramming.8. T / F –In a time sharing system, a user’s program is preempted atregular intervals, but due to relatively slow human reaction time thisoccurrence is usually transparent to the user.9. T / F –A process can be defined as a unit of activity characterized by asingle sequential thread of execution, a current state, and an associated set of system resources.10. T / F – A virtual memory address typically consists of a page numberand an offset within the page.11. T / F – Implementing priority levels is a common strategyforshort-term scheduling, which involves assigning each process in thequeue to the processor according to its level of importance.12. T / F – Complex operating systems today typically consist of a fewthousand lines of instructions.13. T / F – A monolithic kernel architecture assigns only a few essentialfunctions to the kernel, including address spaces, interprocesscommunication and basic scheduling.14. T / F –The hardware abstraction layer (HAL) maps between generichardware commands/responses and those unique to a specificplatform.Multiple Choice Questions:17. A primary objective of an operating system is:a. Convenienceb. Efficiencyc. Ability to evolved. All of the above18. The operating system provides many types of services to end-users,programmers and system designers, including:a. Built-in user applicationsb. Error detection and responsec. Relational database capabilities with the internal file systemd. All of the above19. The operating system is unusual i n it’s role as a control mechanism, inthat:a. It runs on a special processor, completely separated from therest of the systemb. It frequently relinquishes control of the system processor andmust depend on the processor to regain control of the systemc. It never relinquishes control of the system processord. None of the above20. Operating systems must evolve over time because:a. Hardware must be replaced when it failsb. Users will only purchase software that has a current copyrightdatec. New hardware is designed and implemented in the computersystemd. All of the above21. A major problem with early serial processing systems was:a. Setup timeb. Lack of input devicesc. Inability to get hardcopy outputd. All of the above22. An example of a hardware feature that is desirable in abatch-processing system is:a. Privileged instructionsb. A completely accessible memory areac. Large clock cyclesd. None of the above23. A computer hardware feature that is vital to the effective operation of amultiprogramming operating system is:a. Very large memoryb. Multiple processorsc. I/O interrupts and DMAd. All of the above24. The principle objective of a time sharing, multiprogramming system isto:a. Maximize response timeb. Maximize processor usec. Provide exclusive access to hardwared. None of the above25. Which of the following major line of computer system developmentcreated problems in timing and synchronization that contributed to the development of the concept of the process?a. Multiprogramming batch operation systemsb. Time sharing systemsc. Real time transaction systemsd. All of the above26. The paging system in a memory management system provides fordynamic mapping between a virtual address used in a program and:a. A virtual address in main memoryb. A real address in main memoryc. A real address in a programd. None of the above27. Relative to information protection and security in computer systems,access control typically refers to:a. Proving that security mechanisms perform according tospecificationb. The flow of data within the systemc. Regulating user and process access to various aspects of thesystemd. None of the above28. A common problem with full-featured operating systems, due to theirsize and difficulty of the tasks they address, is:a. Chronically late in deliveryb. Latent bugs that show up in the fieldc. Sub-par performanced. All of the above29. A technique in which a process, executing an application, is dividedinto threads that can run concurrently is called:a. Multithreadingb. Multiprocessingc. Symmetric multiprocessing (SMP)d. None of the aboveQUESTIONS2.1,2.3,2.4,2.7,2.10PROBLEMS2.1,2.2,2.3,2.4。
操作系统 期末试题及答案

操作系统期末试题及答案一、选择题(每题5分,共20题,答案请写在括号内)1. 操作系统的作用是什么?(a)连接软硬件之间的桥梁(b)保护计算机免受恶意软件的攻击(c)提供用户与计算机之间的交互界面(d)加强计算机网络的安全性2. 下面哪个不是操作系统的常见类型?(a)Windows(b)Linux(c)Mac OS(d)Internet Explorer3. 操作系统的内核负责什么功能?(a)用户界面(b)文件管理(c)进程管理(d)硬件设备驱动4. 以下哪个不是操作系统中的进程调度算法?(a)先来先服务(b)最短作业优先(c)轮转调度(d)最大剩余时间优先5. 内存管理中,虚拟内存的作用是什么?(a)提供给用户一个纯净的运行环境(b)增加系统的安全性(c)实现程序的地址隔离(d)加速程序的运行速度6. 操作系统中,进程通信的方式包括以下哪些?(a)共享内存(b)消息传递(c)信号量(d)所有上述方式7. 文件系统是用来管理什么的?(a)硬盘空间(b)内存空间(c)CPU资源(d)网络带宽8. 下面哪个不是操作系统的特征?(a)并发性(b)共享性(c)可靠性(d)简单性9. 以下哪个不属于处理机调度算法?(a)先来先服务(b)最短作业优先(c)最低优先权优先(d)最小执行时间优先10. 操作系统中,死锁是指什么情况?(a)一个进程的资源不足(b)多个进程相互等待对方释放资源(c)进程执行时间过长(d)进程之间的通信中断11. 操作系统中,缺页中断的发生会导致什么结果?(a)进程被挂起(b)进程被强制停止(c)页面被置换到辅存中(d)进程的优先级降低12. 下面哪个不属于操作系统的外存管理策略?(a)按需调入(b)置换算法(c)文件分配(d)缓存管理13. 操作系统中,中断处理程序的作用是什么?(a)保存现场并执行中断服务例程(b)清除中断标志(c)释放已占用的资源(d)中断优先级的调度14. 在时间片轮转调度算法中,轮转周期越大,响应时间会越_____。
计算机专业英语试题含答案

计算机专业英语试题2Ⅰ. Vocabulary(词汇)(30分)(一).Translate the following words and expressions into Chinese(写出下列词组的汉语。
)(共10分,每题1分)1.operating system2.white box testing3.hard disk4.management information system5.electronic commerce6.relational database7.software engineering8. software maintenance9. menu bar10.network security(二).Fill in the blanks with the corresponding English abbreviations.(根据汉语写出相应的英语缩写。
) (共10分,每题1分)1.只读存储器 2.广域网3.传输控制协议 4.文件传送[输]协议5.通用串行总线 6.面向对象编程7.集成开发环境 8.结构化查询语言9.数据库管理系统 10.开放系统互连(三)Match the following words and expressions in the left column with those similar in meaning in the right column.(将左列的词汇与右列相应的汉语匹配。
)(10分,每空1分)1. application software a. 音频2. machine language b. 应用软件3. structured programming c. 机器语言4. functional testing d. 软件测试5. memory e. 结构化程序设计6. relational database f. 内存7. firewall g. 功能测试8. software testing h. 关系数据库9. hacker i. 黑客10. audio j. 防火墙1. 6.2. 7.3. 8.4. 9.5. 10.Ⅱ. Comprehension(阅读理解)(一)Fill in the blanks with suitable words or expressions from the list given below, and change the form wherenecessary. (从下面方框中选择合适的词或表达,以其适当的形式填空。
操作系统全英文期中考试题(带答案)
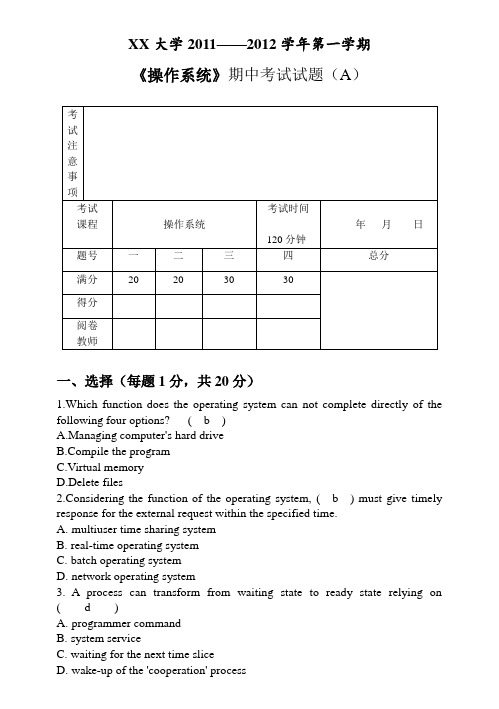
XX大学2011——2012学年第一学期《操作系统》期中考试试题(A)一、选择(每题1分,共20分)1.Which function does the operating system can not complete directly of the following four options? ( b )A.Managing computer's hard drivepile the programC.Virtual memoryD.Delete files2.Considering the function of the operating system, ( b ) must give timely response for the external request within the specified time.A.multiuser time sharing systemB.real-time operating systemC.batch operating systemwork operating system3. A process can transform from waiting state to ready state relying on ( d )A.programmer commandB.system serviceC.waiting for the next time sliceD.wake-up of the 'cooperation' process4.As we all know,the process can be thought of as a program in execution.We can deal with the the problem about ( b ) easier after importing the concept of process.A.exclusive resourcesB.shared resourcesC.executing in orderD.easy to execute5.CPU-scheduling decisions may take place under the following circumstances except which one?(D )A.When a process switches from the running state to the waiting stateB.When a process switches from the running state to the ready stateC.When a process switches from the waiting state to the ready stateD.When a process switches from the ready state to the waiting state6.In the four common CPU scheduling algorithm, Which one is the best choice for the time-sharing system in general?( C )A.FCFS scheduling algorithmB.Priority scheduling algorithmC.Round-robin scheduling algorithmD.Shortest-job-first scheduling algorithm7.If the initial value of semaphore S is 2 in a wait( ) and signal( ) operation,its current value is -1,that means there are ( B ) processes are waiting。
(最新整理)操作系统期末考试试题和答案及评分

操作系统期末考试试题和标准答案及评分标准
编辑整理:
尊敬的读者朋友们: 这里是精品文档编辑中心,本文档内容是由我和我的同事精心编辑整理后发布的,发布之前我们对 文中内容进行仔细校对,但是难免会有疏漏的地方,但是任然希望(操作系统期末考试试题和标准 答案及评分标准)的内容能够给您的工作和学习带来便利。同时也真诚的希望收到您的建议和反馈, 这将是我们进步的源泉,前进的动力。 本文可编辑可修改,如果觉得对您有帮助请收藏以便随时查阅,最后祝您生活愉快 业绩进步,以 下为操作系统期末考试试题和标准答案及评分标准的全部内容。
B. 磁盘 C. 对象 D.多道程序
3.一般来说,为了实现多道程序设计,计算机最需要( )。
A.更大的内存
B.更多的外设
C。更快的 CPU
D。更先进的终端
4.在下面的 I/O 控制方式中,需要 CPU 干预最少的方式是( )。
A.程序 I/O 方式
B。中断驱动 I/O 控制方式
C。直接存储器访问 DMA 控制方式 D。I/O 通道控制方式
B。选择一个主存中的进程调出到外存
C.选择一个外存中的进程调入到主存 D.将一个就绪的进程投入运行
8.如果允许不同用户的文件可以具有相同的文件名,通常采用( )来保证按名存取的安全。
A。重名翻译机构
B.建立索引表
C。建立指针
D.多级目录结构
9.文件控制块不包括( )。
A.文件名 B。文件访问权限说明 C。文件物理位置信息 D。磁盘坏块信息
5.在进程状态转换时,下列( )转换是不可能发生的.
A.就绪态→运行态
B.运行态→就绪态
C。运行态→阻塞态
D。阻塞态→运行态
操作系统全英文期末考试题(带答案)

一.选择题〔20分,每题1分〕1. Generally speaking, which one is not the major concern for a operating system in the following four options?( D )A.Manage the computerB.Manage the system resourcesC.Design and apply the interface between user's program and computer hardware systemD.High-level programming language complier2.The main disadvantage of batch system is ( C )A.CPU utilization is lowB.Can not concurrentck of interactionD.Low degree of automation3.A process transforms from waiting state to ready state is caused by the ( B )A.Interrupt eventB.Process schedulingC.Create a process for a programD.Waiting for some events4.The concurrent process is refers to ( C )A.The process can be run in parallelB.The process can be run in orderC.The process can be run in the same timeD.The process can not be interrupted5.In multi-process system, in order to ensure the integrity of public variables, the processes should be mutually exclusive access to critical areas. The so-called critical area is ( D )A.A bufferB.A date areaC.Synchronization mechanismD.A program6.The orderly use of resources allocation strategy can destroy the condition ( D ) to avoid deadlock.A.Mutual exclusiveB.Hold and waitC.No preemptionD.Circular waiter's applications use the system resources to complete its operation by the support and services of ( C )A.clicking the mouseB.Keyboard commandC.System callD.Graphical user interface8.There are four jobs arrived at the same time and the execution time of each job is 2h. Now they run on one processor at single channel,then the average turnaround time is ( B )9.Among the job scheduling algorithms, ( B ) is related to the job's estimated running time.A.FCFS scheduling algorithmB.Short-job-first scheduling algorithmC.High response ratio algorithmD.Balanced scheduling10.In memory management, the purpose of using the overlay and swapping is ( C )A.Sharing main memoryB.Expanding main memory physicallyC.Saving main memory spaceD.Improving CPU utilization11.In the page-replacement algorithm,which one can cause the Belady phenomenon? ( A )A.FIFOB.LRUC.CLOCKINGD.OPT12.The following description of the system in safe state,which one is correct?( B )A.It must cause deadlock if the system is in insecure stateB.It may cause deadlock if the system is in insecure stateC.It may cause deadlock if the system is in secure stateD.All are wrong13.Generally, when we talk about"Memory Protection", the basic meaning is ( C )A.Prevent hardware memory from damagingB.Prevent program from losing in memoryC.Prevent the cross-border call between programsD.Prevent the program from being peeped14.The actual capacity of virtual memory is equal to ( B )A.The capacity of external memory(disk)B.The sum of the capacity of external memory and main memoryC.The space that the CPU logical address givesD.The smaller one between the option B and C15.Physical file's organization is determined by ( D )A.ApplicationsB.Main memory capacityC.External memory capacityD.Operating system16.A computer system is configured with two plotters and three printers,in order to properly drive these devices,system should provide ( C ) device driver program.17.When there are fewer number of channels in system ,it may cause "bottlenecks".To solve this problem,which of the follow options is not the effective way?( A )A.improving the speed of CPUing the virtual device technologyC.Adding some hardware buffer on the devicesD.Increasing the path between devices and channels18.When I/O devices and main memory are exchanging data, it can be achieved without CPU's frequently intervention,this way of exchanging data is called ( C )A.PollingB.InterruptsC.Direct memory accessD.None of them19.The following description of device management, which one is not correct?( B )A.All external devices are managed by the system in uniformB.Channel is a software of controlling input and outputC.The I/O interrupt events from the I/O channel are managed by device managementD.One of the responsibility of the operating system is to use the hardware effectively20.The operating system used ( A ), it realized a mechanism that we can use more space to save more time.A.SPOOLINGB.Virtual storageC.ChannelD.Overlay二.填空题〔20分,每空1分〕1.Software may trigger an interrupt by executing a special operation called a system call .(P7)2.If there is only one general-purpose CPU,then the system is a single-processor system.(p12)3. A process can be thought of as a program in execution. (p79)4.As a process executes,it changes state.Each process may be in one of the following states:new,running,waiting,ready or terminated .(p83)5.Long-term(job) scheduling is the selection of processes that will beallowed to contend for the CPU.And Short-term(CPU) scheduling is the selection of one process from the ready queue. (p116)6.The process executing in the operating system may be either independent processes or cooperating processes. Cooperating processes require an interprocess communication mechanism to communicate with each other.Principally,communication is achieved through two schemes: share memory and message passing. (p116)7.In modern operating systems, resource allocation unit is process, processor scheduling unit is thread .(p127)8.Most modern operating systems provide kernel support for threads;among these are Windows,as well as Solaris and Linux .(p146)scheduling is the basis of multiprogrammed operating systems.(p153)10.The FCFS algorithm is nonpreemptive;the RR algorithm is preemptive.11.Sometimes,a waiting process is never again able to change state,because the resources it has requested are held by other waiting processes.This situation is called deadlock . (p245)12.The main purpose of a computer system is to execute programs.These programs,together with the data they access,must be in main memory(at least partially) during execution.(P274)13. The various memory-management algorithms differ in may aspects.In comparing different memory-management strategies,we use the follow considerations:Hardware support,Performance,Fragmentation,Relocation, Swapping,Sharing and protection . (p310)14.A process is thrashing if it is spending more time paging than executing.15.Virtual memory is a technique that enables us to map a large logical address space onto a smaller physical memory.(p365)16.When we solve the major problems of page replacement and frame allocation,the proper design of a paging system requires that we consider page size,I/O,locking,process creation,program structure,and other issues.(p366) 17.The operating system abstracts from the physical properties of its storage devices to define a logical storage unit,the file . (p373)18.Since files are the main information-storage mechanism in most computer system,file protection is needed.(p408)19.The seek time is the time for the disk arm to move the heads to the cylinder containing the desired sector.(P457)20.The hardware mechanism that enables a device to notify the CPU is called an interrupt .(p499)三.简答题〔30分,每题6分〕1.What is the operating system?What role does the operating system play in a computer?开放题,解释操作系统概念,操作系统可以完成哪些根本功能?关键词:a.治理系统资源,操纵程序运行,改善人机界面,为其他应用软件提供支持。
操作系统英文样题

操作系统英文样题TestTrue / False Questions:1.T / F – An operating system controls the execution ofapplications and acts as an interface betweenapplications and the computer hardware.2.T / F – The operating system maintains informationthat can be used for billing purposes on multi-usersystems.3.T / F – The principal responsibility of the operatingsystem is to control the execution of processes.4.T / F – When one process spawns another, the spawningprocess is referred to as the child process and thespawned process is referred to as the parent process.5.T / F – The less-privileged processor execution mode isoften referred to as kernel mode.6.T / F – One kind of system interrupt, the trap, relates toan error or exception condition in the currentlyrunning process.7.T / F – The Process Image refers to the binary form ofthe program code.8.T / F – A typical UNIX system employs two Runningstates, to indicate whether the process is executing inuser mode or kernel mode.9.T / F – The short-term scheduler may limit the degreeof multiprogramming to provide satisfactory service to the current set of processes.10.T / F – The long-term scheduler is invoked wheneveran event occurs that may lead to the suspension orpreemption of the currently running process.11.T / F – In a multiprogramming system, main memoryis divided into multiple sections: one for the operating system (resident monitor, kernel) and one for the set of processes currently being executed.12.T / F – In the Dynamic Partitioning technique ofmemory management, compaction refers to shifting the processes into a contiguous block, resulting in all the free memory aggregated into in a single block.13.T / F – In a memory system employing paging, thechunks of a process (called frames) can be assigned to available chunks of memory (called pages).14.T / F – A memory system employing segmentationconsists of a number of user program segments thatmust be of the same length and have a maximumsegment length.15.T / F – The condition known as thrashing occurs whenthe majority of the processes in main memory require repetitive blocking on a single shared I/O device in the system.16.T / F – A Page Fault occurs when the desired pagetable entry is not found in the Translation Lookaside Buffer (TLB).17. T / F – Double buffering refers to the concept ofusing two buffers to alternatively fill and empty in order to facilitate the buffering of an I/O request.18. T / F – A pile file refers to the least complicatedform of file organization, where data are collected in sorted order and each record consists of one burst of data.19. T / F – In the general indexed file structure, thereare no key fields and variable-length records are allowed.20. T / F – Typically, an interactive user or a processhas associated with it a current directory, oftenreferred to as the working directory.21. T / F – In a uniprocessor machine, concurrent processescannot be overlapped; they can only be interleaved.22. T / F –In indirect addressing, as applied to message passing,messages are sent to a temporary shared data structuretypically known as a mailbox.23. T / F – Deadlock can be defined as the periodic blocking of aset of processes that either compete for system resources or communicate with each other.24. T / F – A reusable resource is one that can be safely used byonly one process at a time and is not depleted by that use.Multiple Choice Questions:1.A primary objective of an operating system is:a.Convenienceb.Efficiencyc.Ability to evolved.All of the above2.The operating system provides many types of servicesto end-users, programmers and system designers,including:a.Built-in user applicationsb.Error detection and responsec.Relational database capabilities with the internalfile systemd.All of the above3.The behavior of a processor can be characterized by examining:a.A single process traceb.Multiple process tracesc.The interleaving of the process tracesd.All of the above4.There are a number of conditions that can lead to process termination, including:a.Normal completionb.Bounds violationc.Parent terminationd.All of the above5.A Memory Table is an O/S control structure that is used by the O/S to:a.Manage I/O devicesb.Manage processesc.Provide information about system filesd.None of the above6.The type of scheduling that involves the decision to adda process to those that are at least partially in main memory and therefore available for execution is referred to as:a.Long-term schedulingb.Medium-term schedulingc.I/O schedulingd.None of the above7.In terms of frequency of execution, the short-term scheduler is usually the one that executes:a.Most frequentlyb.Least frequentlyc.About the same as the other schedulersd.None of the above8.A problem with the largely obsolete Fixed Partitioningmemory management technique is that of:a.Allowing only a fixed number of Processesb.Inefficient use of memoryc.Internal fragmentationd.All of the above9.An actual location in main memory is called a(n):a.Relative addressb.Logical addressc.Absolute addressd.None of the above10.The situation that occurs when the desired page tableentry is not found in the Translation Lookaside Buffer (TLB) is called a:a.TLB missb.TLB hitc.Page faultd.None of the above11.In a combined paging/segmentation system, a user’saddress space is broken up into a number of:a.Segments or pages, at the discretion of theprogrammerb.Fixed-size pages, which are in turn broken downinto variable-sized segmentsc.Variable-sized Segments, which are in turnbroken down into fixed-size pagesd.All of the above12. An example of a block-oriented I/O device is:a. CD-ROMb. Printerc. Modemd. All of the above13. Sequential files are optimal in scenariosinvolving:a. Applications that require frequent queriesb. Applications that require the processing ofall records in the filec. Applications that require infrequent updatesd. All of the above14. In a tree-structured directory, the series ofdirectory names that culminates in a file name is referred to as the:a. Pathnameb. Working directoryc. Symbolic named. None of the above15. In order to implement mutual exclusion on a critical resourcefor competing processes, only one program at a time should be allowed:a. In the critical section of the programb. To perform message passingc. To Exhibit cooperationd. None of the above16. A resource that can be created and destroyed is called a:a. Reusable resourceb. Producible resourcec. Consumable resourced. All of the above17. A condition of policy that must be present for a deadlock tobe possible is:a. Mutual exclusionb. Hold and waitc. No preemptiond. All of the above18. In deadlocked process recovery, selection criteria forchoosing a particular process to abort or rollback includes designating the process with the:a. Most estimated time remainingb. Lowest priorityc. Least total resources allocated so fard. All of the aboveFill-In-The-Blank Questions:1. The portion of the operating system that selectsthe next process to run is called the_______________.2. When the O/S creates a process at the explicitrequest of an existing process, the action isreferred to as _______________________.3. A process that cannot execute until some eventoccurs is said to be in the _______________ state.4. In a system that implements two suspend states,a process that has been swapped out of mainmemory and into secondary memory and that isalso awaiting an event is in the________/________ state.5. The task of assigning processes to the processoror processors over time, in a way that meetssystem objectives is called _______________.6. _______________-term scheduling is part of thesystem swapping function.7. _______________ is a scheduling policy in whichthe process with the shortest expectedprocessing time is selected next, but there is nopreemption.8.The task of subdividing memory between the O/S andprocesses is performed automatically by the O/S and iscalled ___________________.9.The phenomenon, in which there is wasted spaceinternal to a partition due to the fact that the block ofdata loaded is smaller than the partition, is referred to as ___________________.10.In the Dynamic Partitioning technique of memorymanagement, the process of shifting processes so they occupy a single contiguous block in memory is called ___________________.11.In a system that employs a paging memorymanagement scheme, the ___________________ shows the frame location for each page of the process.12.The situation where the processor spends most of itstime swapping process pieces rather than executinginstructions is called _______________.13.Most virtual memory schemes make use of a specialhigh-speed cache for page table entries, called a_______________.14. The term _______________ refers to the speedwith which data moves to and from the individual I/O device.15. A hard drive is an example of a_______________-oriented I/O device.16. The disk scheduling algorithm that implementsexactly 2 subqueues in a measure to avoid theproblem of “arm stickiness” is the_________________ policy.17. The file directory information element that holdsinformation such as the permitted actions on the file (e.g., reading, writing, executing, etc.) is the ______________ information element.18. Typically, an interactive user or a process hasassociated with it a current directory, oftenreferred to as the ______________.19. The data structure or table that is used to keeptrack of the portions assigned to a file is referred to as a ______________.20. UNIX employs ______________, which is acontrol structure that contains the keyinformation needed by the operating system for a particular file.21. The situation where Process 1 (P1) holds Resource 1 (R1),while P2 holds R2, and P1 needs R2 to complete and P2needs R1 to complete is referred to as _______________.22. When only one process is allowed in its critical code sectionat a time, then _______________ is enforced.23. A monitor supports _____________ by the use of conditionvariables that are contained within the monitor and accessible only within the monitor.24. All deadlocks involve conflicting needs for resources by_________ or more processes.。
Linux操作系统考试题库及答案

Linux操作系统考试题库及答案一、单项选择题1. Linux操作系统的创始人是()。
A. Bill GatesB. Linus TorvaldsC. Steve JobsD. Richard Stallman答案:B2. 在Linux系统中,查看当前路径的命令是()。
A. pwdB. lsC. cdD. mkdir答案:A3. 在Linux系统中,以下哪个命令用于查看文件内容?()A. catB. grepC. findD. touch答案:A4. 在Linux系统中,以下哪个命令用于创建目录?()A. touchB. mkdirC. rmdirD. rm答案:B5. 在Linux系统中,以下哪个命令用于删除文件?()A. mkdirB. rmdirC. rmD. touch答案:C6. 在Linux系统中,以下哪个命令用于查找文件?()A. grepB. findC. catD. ls答案:B7. 在Linux系统中,以下哪个命令用于查看当前登录用户?()A. whoB. userC. usersD. whoami答案:A8. 在Linux系统中,以下哪个命令用于查看系统运行时间和平均负载?()A. uptimeB. topC. psD. free答案:A9. 在Linux系统中,以下哪个命令用于查看磁盘空间使用情况?()A. dfB. duC. lsD. pwd答案:A10. 在Linux系统中,以下哪个命令用于查看网络配置?()A. ifconfigB. netstatC. routeD. all of the above答案:D二、多项选择题1. 在Linux系统中,以下哪些命令用于文本编辑?()A. viB. nanoC. emacsD. gedit答案:ABC2. 在Linux系统中,以下哪些命令用于文件权限管理?()A. chmodB. chownC. chgrpD. ls答案:ABC3. 在Linux系统中,以下哪些命令用于进程管理?()A. psB. topC. killD. free答案:ABC4. 在Linux系统中,以下哪些命令用于网络管理?()A. ifconfigB. netstatC. pingD. route答案:ABCD5. 在Linux系统中,以下哪些命令用于磁盘管理?()A. dfB. duC. fdiskD. mount答案:ABCD三、判断题1. Linux是一个开源的操作系统。
操作系统英文版课后习题答案整理word文档良心出品

l.lWhat are the three main purpo ses of an op erat ing system? ⑴ In terface betwee n the hardware and user; (2) man age the resource of hardware and software; (3) abstracti on of resource;Answer:• To provide an environment k>r a computer user to< execute programs on computtr hardware in a ccnvenient and efficient manner• Tb 吕 lk>cat 特 the 艺t?parattz resources of the compuler as nteded to strive the prtjblem given* The allocation p TOCESS should be as fair and efficient as possible.• Asa ct>ntroJ p a>gram it serves two major functions : (1) sup ervision of the execution of user programs to p re vent errors and improper use of the computer, and (2) manage ment of the «p erat it) JI and control of [/O devices.1.2 List the four steps that are necessary to run a program on a completely dedicated machine. Prep rocess ing > Process ing > Linking > Executi ng.Answer乩 Reserve machine time*b. Manually load program into memory.c. Load starting address and begin execution.d.Monitor and control execution of program fnim ct>nsoie.1.6 Define the esse ntial prop erties of the follow ing types of op erat ing systems: a. Batch b. In teractive c. Time shari ng d. Real time e. Network f. DistributedAnswerBatch. Jobs with similar needs are batched together and run through the computer as a grcup by anoperator or automatic job st^quencer.[咆jrformHrk :电 is increased by atteiTipting to keep CPU andI/O devices busv 試 all times throughoff-lineoperation, Kptx?ling, and multiprogramming* Batch is good for executing large jobs that netxlinteraction; it can be siubmilted and picked up laterInteractive. Thkin J of many short transactiorifd where the results ofthe next transaction may be unpredictable. Response rirne needs to be short (seconds] since the user submils and w^iih For the result.Time sharing. This systems u&es 匚n scheduling and mLiltiprt)gramming toprtividt* economical interactive of a system. The CP 匚 占w 让 chem rap idly fn>nn one user to another Instead of havinga job defined by spooled card images^ each program re^dsa” b. c.its next control card from the terminal, and output is normally printed immediately to the screen. Real time. Often usvd in a dedicated application, tliis system reads information fram sensors and mustrespond within a fixed amount of time to ensure correct performance- Network.Distributed .This system distributes computation arntmg se¥t?ral physical prtxzesKors, Theprt>cesst>rs do not share memory or a cltKk. Instead, each prixessor has its t>wn kxzal memory. They communicate with each other through various communicatitm lines, such as a high-speed bus or telephone line.1.7 hardware. When is it approp riate for the op erat ing system to forsake this principle and to waste " resources? Why is such a system not really wasteful?Answer Single*user systems shtiuId maximize use of the systenn for the user. A GUI might “waste" CPU cy<les, but it optimizes the user's interaction with the system.2.2 How does the distinction between monitor mode and user mode function as a rudimentary form of p rotecti on (security) system?亠 ■ ■Answer; By establishing a set of privileged instructions that can be executed only when in the mt>niu)r mode, the operating system is assured of ct^ntrolling the entire system at all times.2.3 What are the differe nces betwee n a tra p and an in terru pt? What is the use of each fun cti on?Answer An interrupt is a ha rd w a re-genera ted change-of-flow within the system. An interrupt handler is summoned to deal with the c<iuse oF the interrupt; control is then re*turned to the interrupted context and instruction. A trap is a sof t wa re-genera ted in terru p 匕 An interrupt can bv usvd to signal the coiTipJctk*n of an [/O to obviate the need fnr du\ icy poiling. A trap can be used to call operating system routines or to catch arithmetic errors.2.5 Which of the follow ing in structi ons should be p rivileged? a. Set value of timer. b. Read the clock. c. Clear memory.d. Turn off i nterru pts.e. Switch from user to mon itor mode.d. Wehave stressed the n eed for an op erat ing system to make efficie ntuse of the comp ut ing3OS Exercise BookClass No. NameAnswer: The following instructions should be privileged: a. Set value of timer. b. Clear memory. c. Turn off interruptacL Switch from user to monitor mode.2.8 Protect ing the op erati ng system is crucial to en suri ng that the comp uter system op erates correctly. P rovisi on of this p rotecti on is the reas on beh ind dual-mode op erati on, memory pr otecti on, and the timer. To allow maximum flexibility, however, we would also like to p lace mini mal con stra ints on the user. The followi ngis a list of op erati ons thatof in structi ons that must be p rotected? a. Change to user mode. b. Change to mon itor mode. c. Read from mon itor memory. d. Write into mon itor memory.e. Fetch an in structi on from mon itor memory.f. Tur n on timer in terru pt.g. Turn off timer in terru pt.Answen The minimal set of instructions that must be protected are:Read from monitor memory* Write into monitor me mor v.*Turn off timer interrupt.3.6 List five services p rovided by an op erat ing system. Exp lain how each p rovides convenience to the users. Explainalso in which cases it would be impossible for user-levelpr ograms to p rovide these services.Answer:are no rmally p rotected.What is the minimal seta. Change to monitor mod 匕b. c.Program execution. The operating system loads the contents (or sections) of a file into memory and begins its execution. A user-level pm呂ram could not be trusted to properly allocate CPU time.I/O' op e rat ions. Disks, tapes, serial lines^ and other devices must be communicated with at a \ ery low level. The user need only specify the device and the operation to perform on it, while the system converts that request into device- or controller-specific commands. User-level programs cannot be trusted to only access devices they should have access to nnd to only access them when they art otherwise unused.File-system manipulation. There arv many details in file creation, deletion, alkKation, and naming that users should not have to perform. Blocks of disk spact? are used by files and must be tracked.Deleting a file requires removing the name file information and freeing the 说[located bk>cks.[Protections must also be checked to assure prtiper file access. User prt^grams could neither ensure adherence tct protection methexJs nor be trusted to allocate only free blocks and deallocate blocks on file deletion.Communications. Message passing between systems requires messages be turned into packets of information, sent to the network contnUlei; transmitted across a communications medium, and reassembled by the destination system. Packet ordering and data correction must take place. Again, user programs might not coordinate access to the network device, or they might reevi^T packets destined for other processes. • Error detection. Error detection occurs at both the hardware and sofirware levels. At the hardware le\-el, all data transfers must be inspected to ensure that data have not been c(>rrupted in transit AU data on media must bi checked to be sure they have not changed since they were written to the media. At the software level, media must be checked for data consistency;for instance, do the number of allt>cated and unallocated blocks of storage match the total number on the device. There, errors are frequently prexzess-independent (for instance, the corruption of data on a disk), so there must be a global program (ttiE op erating system) that handles all type 吕 of errors. Also, by having errors processed by the operating system, p rocesses need not contain code to catch and correct all thE errors possible on a syst Em.3.7What is the purpose of system calls?Answer System ualls(J1U>W user-lewl lii request ices uf tl咤uperdting sv;»-tem.3.10 What is the purpose of system programs?jVnswcr: Evstem p rograms can be thought of bundlcz^ uf useful systctu oils. Tbevprovide basic functicrahty to users and so users de not need to write their own programs to sol、忙common problems.4.1MS-DOS pr ovided no means of con curre nt pr ocess ing. Discuss three major comp licati ons that con curre nt p rocess ing adds to an op erat ing system.5OS Exercise BookClass No. NameAnswer:A method of time sharing must be implemented to allow each of several processes to have access to the systen'i. This method inxoJvcs the prompt ion of processes that do not voluntarily giA-e up the CPU (by using A system cal], for instance) <ind the kernel being reentrant (so more than one prtxzess may be executing kernel code concurrently).Processes and system resources must hav E protections and must be prciteck?d frtiTn each other Any given process must be limited in the amount of memory it can use and the operations it can perform on devices like disks.Care must be taken in the kernel to pre\ ent deadkxzks between processe 鬲 so prcicesses aren't waiting for each other's allcxated rest>urces.4.6full at any one time. Modify the algorithm to allow all buffers to be utilized fully.Answer No answer.5.1 P rovide two p rogram ming exa mp les of multithread ing givi ng imp rove p erforma nee over a sin gle-threaded soluti on.Answer (1) A server that services each request in a sep a rate thread. (2) A paral* lelized application such as matrix multi plication where different p arts of the matrix may be worked on in parallel. (3) An interactive GUI program such as a dibugger where a thread is used to monitor user input, another thread represents the running flppHcation, and a third thread monitors performance.5.3 What are two differences between user-level threads and kernel-level threads? Under what circumsta nces is one type better tha n the other?r■Answer Context switching between user tlireads is quite similar tG switching between kernel threads, although it is dependent on the threads library and how it maps user threads to kernel threads. In general, context switching between user threads involves taking a user thread of its LWP and replacing it with another thread. This act typically involves saving and restoring the st^te of the registers.6.3 Con sider the follow ing set of p rocesses, with the len gth of the CPU-burst time give n in millisec on ds: P rocessP1 P2 P3 F4 P5The p rocessesare assumed to have arrived in the orderThe correct p roducer— con sumer algorithm in Secti on 4.4 allows only n-1 buffers to beBurst 10 1 2 1 5Time P riority 3 1 3 4 2P1, P2, P3, P4, P5, all at time 0.a.Draw four Gantt charts illustrati ng the executi on of these p rocesses using FCFS, SJF, a nonpreemp tive p riority (a smaller p riority n umber imp lies a higher p riority), and RR (qua ntum = 1) scheduli ng.b.What is the tur narou nd time of each pr ocess for each of the scheduli ng algorithms in part a?c.What is the wait ing time of each p rocess for each of the scheduli ng algorithms in p art a?d.Which of the schedules in p art a results in the mini mal average wait ing time (over all pr ocesses)?An swer:AnswerThe four Gantt charts area.b- Turnaround timeFCFS円101113卩414 卩519RR■19274SJF191 ^riority18196Waiting time (turnaround time minus burst time)FCFS RR卩210Ih11卩413卩514 SJF214Prit^ritv•J61618d. Shortest Job First6.4 Suppose that the followingpr ocess will run the listed amou nt of time. In an sweri ng the questi ons, use nonpreemp tivescheduli ng and base all decisi ons on the in formati on you have at the time the decisi onp rocesses arrive for execution at the times in dicated. Each70.110.4a. What is the average tur narou nd time for these p rocesses with the FCFS scheduli ng algorithm?b. What is the average turnaround time for these processes with the SJF scheduling algorithm?c. The SJF algorithm is supp osed to impr ove p erforma nee, but no tice that we chose to run p rocessP1 at time 0 because we did not know that two shorter p rocesses wouldarrive soon. Comp ute what the average turn arou nd time will be if the CPU is left idle for the first 1 un it and the n SJF scheduli ng is used. Remember that p rocesses and P2 are wait ing duri ng this idle time, so their wait ing time may in crease. This algorithm could be known as future-k no wledge scheduli ng.Answer; a. 10,53b. 9.53c. 6.86Remember that turnaround time LS finishing time minus arrival time^ so you have h) subtract the arrival times to compute the turnaround times. F 匚FS is 11 if yw forget subtract arrival time.6.10 Explain the differe nces in the degree to which the follow ing scheduli ng algorithms discrim in ate in favor of short p rocesses: a. FCFS b. RRc. Multilevel feedback queuesAnswen孔 FCFS —discriminates against sliort jobs since any short jobs arriving after long jobs will have a kmger waiting time.b. RR 一treats all jobs equally (giving them eqiiaL bursts of CPU time) so short Qbm will be able toleave the system faster since they will finish first.c. Multilevel feedback queues —work similar to the RR algorithm —they discriminate favorably towardshort jt>bs.7.7 Show that, if the wait and sig nal op erati ons are not executed atomically, then mutual exclusi on may be violated.Answer No answer,must be made.ClassOS Exercise BookNo.NameAi rhal rimeBuist 1 i[uvPi7.8 The Slee pin g-Barber Pr oblem. A barbersho p con sists of a wait ing room with n chairsand the barber room containing the barber chair. If there are no customers to be served,the barber goes to slee p. If a customer en ters thebarbersho p and all chairs are occu pi ed,then the customer leaves the sho p.lf the barber is busy but chairs are available, the nthe customer sits in one of the free chairs. If the barber is aslee p, the customer wakes up the barber. Write a p rogram to coord in ate the barber and the customers.Answer: Please refer to the supporting Web site for source code solution.8.2 Is it possible to have a deadlock involving only one single process? Explain your answer.Answer No. This follows directly from the hold-and-wait condition.8.4 Con sider the traffic deadlock dep icted in Figure 8.11.a. Show that the four n ecessary con diti ons for deadlock in deed hold in this exa mple.b. State a sim pie rule that will avoid deadlocks in this system.Answer No answerCon Sider the follow ing snap shot of a system:Allocati onMax AvailableA B C DA B C D A B C D P0 0 0 1 2 0 0 1 2 1 5 2 0P1 1 0 0 0 1 7 5 0 P2 13 54 2 35 6P 3 0 6 3 2 0 6 5 2P40 0 1 40 6 5 6An swer the follow ing questi ons using th e ban kera. What is the content of the matrix Need?b. Is the system in a safe state?c. If a request from p rocess immediately?Answer:A. Deadlock cannot occur because preempticin exists.b. Yes. A process may never acquire all the resources 让 needs if they are continuously preempted by aseries of reqviests such as those of process C.9.5 Given memory partitions of 100K, 500K, 200K, 300K, and 600K (in order), how would each of the First-fit, Best-fit, and Worst-fit algorithms place processes of 212K, 417K, 112K,and 426K (in order)? Which algorithm makes the most efficie nt use of memory?8.13 s algorithm:P1 arrives for (0,4,2,0), can the request be gran ted9OS Exercise BookClassNo. NameAnswer:212K is put in 500K partition 417K is put in BOOK partidon112K is put in 288K partition (new partition 288K = 500K = 212K) e. 426 K must wa 让212K 仏 put in 300K partidon 417K is put in 500K partition1I2K is put in 2nOK parti tin n 426K put in 600K partidon212K is put in 600K partition417K is put in 500K partitio 口 112K is put in 388K partidon 426K must waitIn this example. Best-fit turns out to be the best9.8 Con Sider a logical address sp ace of eight p ages of 1024 words each, mapped onto a physical memory of 32 frames.a. How many bits are there in the logical address?b. How many bits are there in the p hysical address?Answera. Logical addrej^s: 13 bitsb.卩hvsical address: 15 bits9.16 Con Sider the follow ing segme nt table: Segme nt Base Len gtha. First-fit:d ・ f. Best-fit:8- h* k. Worst-fit:m. n.600 14 100 580 96What are the p hysical addresses for the follow ing logical addresses? a. 0,430 b. 1,10 c. 2,500 d. 3,400 e. 4,112Answena. 219 + 43(1-649illegal reference, trap ki Dpvra ting systemillegal reference, trap tu op grating system10.2 Assume that you have a page referenee string for a process with m frames (initiallyall emp ty). The p age refere nee stri ng has len gth p with n disti net p age n umbers occur init. For any p age-re pl aceme nt algorithms,a. What is a lower bou nd on the n umber of p age faults?b. What is an upper bou nd on the n umber of p age faults?Answer a. tr b.卩10.11 Con Sider the follow ing p age refere nee stri ng: 1, Z 3, 4, 2,1,5, 6, Z 1,2, 3, 7, 6, 3, Z 1, Z 3, 6.How many p age faults would occur for the follow ing repl aceme nt algorithms, assum ing one, two, three, four, five, six, or seve n frames? Remember all frames are in itially emp ty, so your first uni que p ages will all cost one fault each.LRU rep laceme nt FIFO rep laceme nt Op timal rep laceme nt0 1 2 3 4219 2300 90 1327 1952 b. 2300 + 10 = 2310c. d. 1327 + 400= 17271111.7 Explain the purp ose of the openAnswer :■ The open operatit>n informs the system that the named file is about to become active^* Tlie cloiie «peration informs the system that tlie named file is no longer in active use by the user who issued the 匚lose operation.11.9 Give an example of an application in which data in a file should be accessed in the followi ng order: a. Seque ntially b. Ran domlyAnsiver :Print the content of the file.Print the content of record /. This record can be found using hashing or index techniques.11.12 theseusers to be able to access one file.a. How would you sp ecify this p rotecti on scheme in UNIX?b. Could you suggest ano ther pr otecti on scheme that can be used more effectively for this purpose tha n the scheme p rovided by UNIX?Answera. There are two methods for achieving this:Answer:ClassOS Exercise BookNo.NameNumber of framesLRU FIFO Optimal12 3 48-5 00 8 6 4and close op erati ons.a. b. Con sider a system that supports 5000 users. Suppose that you want to allow 4990 ofi. Create an access list with the names of all 4990ii. Put these 4990 users in one group and set the group access accordingly. This scheme cannot alwaysbe implemented since user groups are restricted by th# system.b. The univErse access information applies to all users unless their name appears in the access-controlHst with different access permission. With this scheme you simply put the names of the remaining ten users in the access control list but no access privileges alh)wcd.■r2Tl _Consider _a filecurrently consisting of 100 blocks.__Assume that _the file control block(ande in dex block, in the case of i ndexed allocati on) is already in memory. Calculate how any disk I/O op erati ons are required for con tiguous, li nked, and in dexed (sin gle-level) locati on strategies, if, for one block, the follow ing con diti ons hold. In thecase, assume that there is no room to grow in the beg inning, but there to be added is stored inAnswer198 9813.2 Con Sider the follow ing I/O see narios on a sin gle-user PC.a. A mouse used with a grap hieal user in terfaeeb. A tape drive on a multitask ing op erat ing system (assume no device p realloeati on is available) e. A disk drive containing user filesd. A gra phics eard with direet bus conn eeti on, aeeessible through memory-ma pped I/OFor each of these I/O see narios, would you desig n the op erat ing system to use bufferi ng, spo oli ng, eaehi ng, or a comb in ati on? Would you use p olled I/O, or in terru pt-drive n I/O? Give reas ons for your choices.teon tiguousalloeati onis room to grow in the end. Assume that the block in formatio nmemory.a. The block is added at the beg inning.b. The block is added in the middle. e. The block is added at the end.d. The block is removed from the begi nning.e. The block is removed from the middle.f. T he block is removed from the end.ContiffljQus LinkedIndexeda. b.201 101 52 3 52 10013OS Exercise BookClass No. NameAnswenA mouse used with a graphical user interfaceBuffering may bt? needed to record mouse movement during times when higher- priority op erations aretaking place. Spooling and caching are inap propriat 巳 Interrupt driven I/O is m 〔>st appropriate^ A t 日pe drive on a multitasking operating system (assume no device preallocation is availabl £) Buffering may be needed to manage through put difference behveen the tape drive and the souro? or destination of the I/O, C 白匚hing can bv used to hold copies of daU that resides on the tape, for faster access. Spooling could be used to stage data to the device when multiple users desire to read from or write to it. Interrupt driven I/G is likely to allow the best performance. A disk drive containing user filesBuffering can be used to hold data while in transit from user space to the disk, and visa versa. Caching can be used to hold disk-resident data for impmvtd performance. Spociling is not necessary because disks are shared-access devices. Interrupt- driven I/O is best for devices such as disks that transfer data at slow rates-A graphics card with direct bus connection, accessible through memory-rnapped I/O 'Buffering may be needed to control multiple access and for performance (doublebuffering can be used to hold the next screen image while displaying the current one). Caching and 5pooling are not necessary^ due to IH E fast and shared-access natures of the device. Folling and in term pts are only useful for input and for I/O completion detection, neither of which is needed for a memory^mapped device.14.2Suppose that a disk drive has 5000 cylinders,numbered 0 to 4999. The drive is currentlyserving a request at cylinder 143, and the previous request was at cylinder 125. The queue of pending requests, in FIFO order, is86, 1470, 913, 1774, 948, 1509, 1022, 1750, 130Start ing from the curre nt head p ositi on, what is the total dista nee (in cyli nders) that the disk arm moves to satisfy all the pending requests, for each of the follow ing diskscheduli ng algorithms? a. FCFS b. SSTF c. SCAN d. LOOK e. C-SCANa. b.d.Answer:a. The FCFS schedule bi 143, 86, 1470, 913, 1774, 94S, 1509, 1022, 1750, 130. The tntal seekdistance is 7081.b. The SSTF schedule is 143, 130, 86, 913, 948, 1D22, 1470, 1509, 1750, 1774. The total seekdistance is 1745.c. The SCAN schedule is 143, 913, 94«, 1022,1470, 1509, 1750, 1774, 4999,130, 86. The total seekdistance is 9769.The LCX)K scheduJe is 143, 913, 94H, 1022, 1470, 1509, 1750, 1774, 130, H6. The total seekdistance is 3319.e. The C-SCAN schedule is 143,913,948,1022,1470,1509.1750,1774,4999;130. Thetotal seek distance is 9813.{Bonus.} The C-LOOK schedule is 143” 913,94& 1022,1470,1509,1750,1774,86,130. The tohal seek distance is 3363.1.1 1.62.3 2.53.7 6.3 6。
操作系统全英文期末考试题

一.选择题(20分,每题1分)1. Generally speaking, which one is not the major concern for a operating system in the following four options( D )the computerthe system resourcesand apply the interface between user's program and computer hardware systemprogramming language complier2.The main disadvantage of batch system is ( C )A.CPU utilization is lowB.Can not concurrentck of interactionD.Low degree of automation3.A process transforms from waiting state to ready state is caused by the ( B )A.Interrupt eventB.Process schedulingC.Create a process for a programD.Waiting for some events4.The concurrent process is refers to ( C )A.The process can be run in parallelB.The process can be run in orderC.The process can be run in the same timeD.The process can not be interrupted5.In multi-process system, in order to ensure the integrity of public variables, the processes should be mutually exclusive access to critical areas. The so-called critical area is ( D )A.A bufferB.A date areaC.Synchronization mechanismD.A program6.The orderly use of resources allocation strategy can destroy the condition ( D ) to avoid deadlock.A.Mutual exclusiveB.Hold and waitC.No preemptionD.Circular waiter's applications use the system resources to complete itsoperation by the support and services of ( C )A.clicking the mouseB.Keyboard commandC.System callD.Graphical user interface8.There are four jobs arrived at the same time and the execution time of each job is 2h. Now they run on one processor at single channel,then the average turnaround time is ( B )9. the job scheduling algorithms, ( B ) is related to the job's estimated running time.A.FCFS scheduling algorithmB.Short-job-first scheduling algorithmC.High response ratio algorithmD.Balanced scheduling10.In memory management, the purpose of using the overlay and swapping is ( C )A.Sharing main memoryB.Expanding main memory physicallyC.Saving main memory spaceD.Improving CPU utilization11.In the page-replacement algorithm,which one can cause the Belady phenomenon ( A )A.FIFOB.LRUC.CLOCKINGD.OPT12.The following description of the system in safe state,which one is correct( B )A.It must cause deadlock if the system is in insecure stateB.It may cause deadlock if the system is in insecure stateC.It may cause deadlock if the system is in secure stateD.All are wrong13.Generally, when we talk about"Memory Protection", the basic meaning is ( C )A.Prevent hardware memory from damagingB.Prevent program from losing in memoryC.Prevent the cross-border call between programsD.Prevent the program from being peeped14.The actual capacity of virtual memory is equal to ( B )A.The capacity of external memory(disk)B.The sum of the capacity of external memory and main memoryC.The space that the CPU logical address givesD.The smaller one between the option B and C15.Physical file's organization is determined by ( D )A.ApplicationsB.Main memory capacityC.External memory capacityD.Operating system16.A computer system is configured with two plotters and three printers,in order to properly drive these devices,system should provide ( C ) device driver program.17.When there are fewer number of channels in system ,it may cause "bottlenecks".To solve this problem,which of the follow options is not the effective way( A )A.improving the speed of CPUing the virtual device technologyC.Adding some hardware buffer on the devicesD.Increasing the path between devices and channels18.When I/O devices and main memory are exchanging data, it can be achieved without CPU's frequently intervention,this way of exchanging data is called ( C )A.PollingB.InterruptsC.Direct memory accessD.None of them19.The following description of device management, which one is not correct( B )A.All external devices are managed by the system in uniformB.Channel is a software of controlling input and outputC.The I/O interrupt events from the I/O channel are managed by device managementD.One of the responsibility of the operating system is to use the hardware effectively20.The operating system used ( A ), it realized a mechanism that we can use more space to save more time.A.SPOOLINGB.Virtual storageC.ChannelD.Overlay二.填空题(20分,每空1分)1.Software may trigger an interrupt by executing a special operation called a system call .(P7)2.If there is only one general-purpose CPU,then the system is a single-processor system.(p12)3. A process can be thought of as a program in execution. (p79)4.As a process executes,it changes process may be in one of the following states:new,running,waiting,ready or terminated .(p83)5.Long-term(job) scheduling is the selection of processes that will beallowed to contend for the Short-term(CPU) scheduling is the selection of one process from the ready queue. (p116)6.The process executing in the operating system may be either independent processes or cooperating processes. Cooperating processes require an interprocess communication mechanism to communicate with each ,communication is achieved through two schemes: share memory and message passing. (p116)modern operating systems, resource allocation unit is process, processor scheduling unit is thread .(p127)modern operating systems provide kernel support for threads;among these are Windows,as well as Solaris and Linux .(p146)scheduling is the basis of multiprogrammed operating systems.(p153)FCFS algorithm is nonpreemptive;the RR algorithm is preemptive. ,a waiting process is never again able to change state,because the resources it has requested are held by other waiting situation is called deadlock . (p245)main purpose of a computer system is to execute programs,together with the data they access,must be in main memory(at least partially) during execution.(P274)13. The various memory-management algorithms differ in may comparing different memory-management strategies,we use the follow considerations:Hardwaresupport,Performance,Fragmentation,Relocation,Swapping,Sharing and protection . (p310)14.A process is thrashing if it is spending more time paging than executing.15.Virtual memory is a technique that enables us to map a largelogical address space onto a smaller physical memory.(p365)16.When we solve the major problems of page replacement and frame allocation,the proper design of a paging system requires that we consider page size,I/O,locking,process creation,program structure,and other issues.(p366)17.The operating system abstracts from the physical properties of its storage devices to define a logical storage unit,the file . (p373)18.Since files are the main information-storage mechanism in most computer system,file protection is needed.(p408)19.The seek time is the time for the disk arm to move the heads to the cylinder containing the desired sector.(P457)20.The hardware mechanism that enables a device to notify the CPU is called an interrupt .(p499)三.简答题(30分,每题6分)1.What is the operating systemWhat role does the operating system play in a computer开放题,解释操作系统概念,操作系统可以实现哪些基本功能关键词:a.管理系统资源,控制程序运行,改善人机界面,为其他应用软件提供支持。
操作系统答案(全)

[英文原版]操作系统_精髓与设计原理_第6版答案翻译Keys of Operating Systems Internals and Design Principles6th Edition第一章计算机系统概述复习题:1.1、列出并简要地定义计算机的四个主要组成部分。
答:主存储器,存储数据和程序;算术逻辑单元,能处理二进制数据;控制单元,解读存储器中的指令并且使他们得到执行;输入/输出设备,由控制单元管理。
1.2、定义处理器寄存器的两种主要类别。
答:用户可见寄存器:优先使用这些寄存器,可以使机器语言或者汇编语言的程序员减少对主存储器的访问次数。
对高级语言而言,由优化编译器负责决定把哪些变量应该分配给主存储器。
一些高级语言,如C语言,允许程序言建议编译器把哪些变量保存在寄存器中。
控制和状态寄存器:用以控制处理器的操作,且主要被具有特权的操作系统例程使用,以控制程序的执行。
1.3、一般而言,一条机器指令能指定的四种不同操作是什么?答:这些动作分为四类:处理器-寄存器:数据可以从处理器传送到存储器,或者从存储器传送到处理器。
处理器-I/O:通过处理器和I/O模块间的数据传送,数据可以输出到外部设备,或者从外部设备输入数据。
数据处理,处理器可以执行很多关于数据的算术操作或逻辑操作。
控制:某些指令可以改变执行顺序。
1.4、什么是中断?答:中断:其他模块(I/O,存储器)中断处理器正常处理过程的机制。
1.5、多中断的处理方式是什么?答:处理多中断有两种方法。
第一种方法是当正在处理一个中断时,禁止再发生中断。
第二种方法是定义中断优先级,允许高优先级的中断打断低优先级的中断处理器的运行。
1.6、内存层次的各个元素间的特征是什么?答:存储器的三个重要特性是:价格,容量和访问时间。
1.7、什么是高速缓冲存储器?答:高速缓冲存储器是比主存小而快的存储器,用以协调主存跟处理器,作为最近储存地址的缓冲区。
1.8、列出并简要地定义I/O操作的三种技术。
操作系统期末考试及参考答案

考试试卷:A√卷、B卷(请在选定项上打√)考试形式:闭、开√卷(请在选定项上打√),允许带 入场考试日期: 年 月 日,考试时间: 120 分钟 任任课教师:__诚信考试,沉着应考,杜绝违纪。
考生姓名:学号:所属院系:_题序1-701234总分得分评卷人注意:本考卷分P a r t1、P a r t2两部分,第一部分为选择题共70分;第二部分为问答题共30分。
选择题答案请填入以下表格,只答在题目上的不给分。
问答题答案请写在答题纸上。
题号12345678910 1-1011-2021-3031-4041-5051-6061-70Part One: Multiple Choice Questions (one mark each.)Choose the best answer for the following questions. There is only one best answer for each question.1.Operating systems provide certain levels of interfaces. However, is in general not provided by OS.A. Application programming interface (API)B. Command line interpreterC. Graphic user interface (GUI)D. System call2. A distributed system could be _________.A. A client-server systemB. A peer-to-peer systemC. A clustering systemD. All the above3.When operating system says Resource, it could beA.Memory spaceB.Global variableswork bandwidthD.All the abovepared to the OSes with microkernel, the monolithic counterpart sometimes shows advantage in .A. ScalabilityB. ModularityC. PerformanceD. Readability5.Which of the functionalities listed below must be supported by the operating system for handheld devices.A. Batch programmingB. Virtual memoryC. Time sharingD. Networking6.Which of the following types of operating systems has the best job throughput ?A. Time sharingB. InteractiveC. BatchD. Real time7. A CPU scheduler focuses on __________ scheduling.A. mixture-termB. short-termC. medium-termD. long-term8.The context-switch causes overhead by OS. The action affects many objects, but is not included.A. registerB. global variableC. stackD. memory9.Which of the following process state transitions is impossible to happen?A. from ready state to running stateB. from ready state to waiting stateC. from running state to ready stateD. from waiting state to ready state10. A process will change its state from “waiting” to “ready” when _____.A.it has been selected for execution by schedulerB.the event it had been waiting for has occurredC.its time slice is finishedD.it waits for some event11.The main difference between a process and a program is that _________.A. a process has its life cycle while a program has not.B. a program has its life cycle while a process has not.C. a program can own resources while a process cannot.D. a process can own resources while a program cannot.ing the program shown as following:#include <sys/types.h>#include <stdio.h>#include <unistd.h>int value = 10;int main() {pid_t pid;pid = fork();value += 10;if(pid == 0) { /* child process */value += 5; }else if (pid > 0) { /* parent process */wait(NULL);printf("PARENT: value = %d", value); /* LINE A */exit(0);}}Which string will be output at Line A?A. PARENT: value =20B. PARENT: value =10C. PARENT: value =15D. PARENT: value =2513. A semaphore array in Linux is often used as ______.A. a kind of direct communicationB. a kind of low-level communicationC. a kind of symmetrical communicationD. a kind of inter-process communication14.Which of the following statement is true ?A. Sometimes multithreading does not provide better performance than a single-threaded solutionB. Sometimes multithreading does the same performance as a single-threaded solutioC. Sometimes multithreading provides better performance than a single-threaded solutionD. All the above are true15.Threads in a process share the _________.A. Stack memoryB. Heap memoryC. Register valuesD. Global variables16.In general, multithreading shows some features benefiting user applications. Even though an operatingsystem does not support multithreading, those features could be brought with by use of __________.A. One to One ModelB. Kernel level threadC. User level threadD. None17.Which of the following scheduling algorithms could result in starvation ?A. First come first servedB. Round robinC. Shortest job firstD. Highest response_ratio next18.Consider a variant of the RR scheduling algorithm in which the entries in the ready queue are pointers tothe PCBs. If there are two pointers to the same PCB:A. It would not be the RR algorithm and be illegal.B. The time slice would have to be adjusted in order to rebalance the CPU load.C. The pointed process always gains twice the CPU time.D. The time interrupt should be smart enough which makes the OS kernel more complicated.19.Suppose the system is dominated by processes with short burst-time, ____ is the most appropriate choice.A. Multilevel queuesB. Multilevel feedback queuesC. First come first servedD. Round robin20.Sometimes two scheduling criteria are conflict with each other, and not satisfied both. Which of thefollowing pairs of scheduling criteria are ALWAYS non-conflicting?A. CPU utilization and response timeB. Average turnaround time and average waiting timeC. Average turnaround time and maximum waiting timeD. I/O device utilization and CPU utilization21.Talking about the scheduling for CPU burst cycle vs I/O burst cycle, which statement is true.A. A scheduler does not care the process either in CPU burst cycle or I/O burst cycleB. A process is either CPU burst or I/O burstC. A process with CPU burst cycle is preferredD. A process with I/O burst cycle is preferredFor the next 3 questions, considering the following set of processes, with the length of the CPU-burst time given in milliseconds:Process Arrival time Burst timeP103P225P341P454P58122.For the FCFS scheduling algorithm, the average waiting time is_____.A. 14/5B. 25/5C. 44/5D. 33/523.For the SJF scheduling algorithm, the average waiting time is _____.A. 11/5B. 22/5C. 41/5D. 30/524.For the Round Robin (quantum is 2) scheduling algorithm, the average waiting time is ___.A. 44/5B. 34/5C. 29/5D. 15/525.The critical section in an OS is ________.A. a process schedulerB. a data sectionC. a synchronization mechanismD. a segment of code26.Which of the following statements is incorrect regarding Busy Waiting?A. Busy waiting makes worse CPU throughput.B. Busy waiting could be avoided by proper CPU scheduling.C. Busy waiting does not just come with Critical Section Problem.D. If a solution to the Critical Section Problem causes busy waiting, the solution is incorrect.27.Which of the following statements is correct?A. Critical section is a piece of code in a process for mutual exclusion.B. Critical section is a piece of code in a process for process synchronization.C. Critical section is a piece of code in a process for inter-process communication.D. Critical section is a piece of code in a process for accessing critical (shared) resources.28.For two-process Critical Section(CS) problem solution, the Progress condition does not mean thatA. Only processes wish to enter the section are the candidates.B. If and only if there are some processes wish to enter the critical section, the Progress condition applies.C.The decision to enter the critical section should be made within limited time, even though there exists aprocess running in its critical section.D. A process is allowed to enter its critical section many times while the others keep waiting.29.Which one of the following statements is correct about spinlock?A. Spinlock is appropriate for single-processor systemsB. Spinlock is often used in multiprocessor systemsC.Spinlock could be used in single-processor systemsD. Spinlock is not often used in multiprocessor systems30.Which one of the following statements is correct about synchronization primitives ?A. The primitive could be implemented by disabling interrupts, even in single-processor systems.B. The primitive could not implemented by disabling interrupts, neither in single-processor systems nor inmultiprocessor systems.C. The primitive could only be implemented by disabling interrupts for multiprocessor systems.D. If used in user-level programs, the primitive could be implemented by disabling interrupts.31.Hope the server limits its number to be concurrently connected no more than N clients. One solution willbeA. A semaphore for resource sharing purpose, with the initial value NB. A semaphore for resource sharing purpose, with the initial value 1C. A semaphore for synchronization purpose, with the initial value ND. A semaphore for synchronization purpose, with the initial value 132.Which one of the following is not the necessary condition for a deadlock to occur?A. StarvationB. Mutual exclusionC. Hold and waitD. NO Preemption33.Which of the following methods can prevent the deadlock from the very beginning?A. Resource allocation in an increasing order of enumerationB. Banker’s algorithmC. Deadlock detectionD. Deadlock avoidance34.Consider the following snapshot of a system:Allocation Max AvailableABCD ABCD ABCD0 0 1 2 0 0 1 2 1 5 2 0P1 0 0 0 1 7 5 0P1P1 3 5 423 5 620 6 3 2 0 6 5 2P3P0 0 1 4 0 6 5 64Which one is the safe sequence for the system?A. < P0, P3, P4, P2, P1>B. < P1, P2, P4, P3, P0>C. < P2, P0, P4, P1, P3>D. < P4, P3, P1, P2, P0>35.The address binding could be by the way ofA. The variables in source codes converted to the binaryB. The variables in source codes compiled into object modulesC. Several object modules are linked together into a single programD. All the above36.An unsafe state implies ________.A. the existence of deadlockB. that deadlock will eventually occurC. that some unfortunate sequence of events might lead to a deadlockD. The scenario that the Dining Philosophers Problem described37.In a real computer system, neither the resources available nor the demands of processes for resources areconsistent over long periods (months). Resources break or are replaced, new processes come and go, new resources are bought and added to the system. If deadlock is controlled by the banker’s algorithm, which of the following changes can be made safely (without introducing the possibility of deadlock) ?A. Increase the number of processes.B. Increase Max for one process (the process needs more resources than allowed, it may want more)C. Increase Available (new resources added).D. Decrease Available (resource permanently removed from system)38.Which of the following memory management method helps to share a code segment across processes?A. Contiguous memory allocationB. Pure segmentationC. Pure pagingD. None of above39.Which of the following memory management method has no impact in terms of internal fragmentation?A. Two-level pagingB. SegmentationC. PagingD. Linux paging strategy40.To apply the demand paging memory management, the CPU with powerful MMU is a must. However,is NOT a necessity.A. InterruptB. Present bit defined in the segment table entryC. TLBD. Page table41.Assume that you are monitoring the rate at which the pointer in the clock algorithm (which indicates thecandidate page for replacement) moves. What can you say about the system if you notice the pointer is moving fast ?A. the program is accessing a large number of pages simultaneouslyB. the operation finding candidate pages for replacement is efficientC. the virtual memory system is extremely efficientD. that indicates many of the resident pages are not being accessed42.Suppose that a machine provides instructions that can access memory locations using the one-levelindirect addressing scheme. How many page faults incurred when all of the pages of a program are currently non-resident and the first instruction of the program is an indirect memory load operation ?A. 3B. 2C. 1D. 043. A certain computer provides its users with a virtual-memory space of 232bytes. The computer has 218bytes of physical memory. The virtual memory is implemented by paging, and the page size is 4096 bytes.A user process generates the virtual address 11123456, actually its page number is ___A. 69923B. 2715C. 1110D. 1112345644.Consider a demand-paging system with the following time-measured utilizations:CPU utilization 20%Paging disk 97.7%Other I/O devices 5%Which of the following will improve CPU utilization ?A. Increase the degree of multiprogrammingB. Decrease the degree of multiprogrammingC. Install a faster CPUD. Install a bigger paging disk45.Which of the following indicates that the system performs wellA. A process suffers deadlockB. A process suffers starvationC. A process suffers bad turnaround timeD. A process suffers thrashing46.Virtual memory management with paging does not requireA. the page replacementB. to process the page fault interruptC. to load some code or data into the contiguous memory spaceD. none of the above47.In order for a virtual memory management performing well, it is preferred thatA. processes do not have too much I/O operationsB. the program size should not be bigger than the whole memory spaceC. there are some large size contiguous memory spaceD. the locality of processes is well featuredFor the next 2 questions, consider a paging system with the page table stored in memory.48.If a memory reference takes 200 nanoseconds, how long does a paged memory reference take ?A. 200 nanoseconds + the time to process the page entries which is a bit over 200 nanosecondsB. depends, sometimes 400 nanoseconds, and sometimes 200 nanosecondsC.200 nanosecondsD. 400 nanoseconds49.If we add TLBs, and 75 percent of all page-table references are found in the TLBs, what is the effectivememory reference time ? (Assume that finding a page-table entry in the TLBs takes zero time, if the entry is there.)A. 250 nanosecondsB. 350 nanosecondsC. 400 nanosecondsD. 200 nanoseconds50.If an OS is not facilitated with virtual memory management, thenA. A process has to be loaded fully in memory before execution and kept staying in memoryB. A process does not have to be loaded fully in memory before execution, neither does stay in memoryC. A process does not have to be loaded fully in memory before execution, however has to stay in memoryduring executionD. A process has to be loaded fully in memory before execution, however does not have to stay in memoryduring executionFor the next 3 questions, assume that five memory partitions are of size 100KB, 500KB, 200KB, 300KB, and 600KB (in order). The processes of 212KB, 417KB, 112KB and 426KB(in order) are applied to be put in place.51.If the first-fit algorithm is equipped, the process of 112KB will be put in the partition withA. 200KBB. 300KBC. 500KBD. 600KB52.If the best-fit algorithm is equipped, the process of 112KB will be put in the partition withA. 500KBB. 200KBC. 300KBD. 600KB53.If the worst-fit algorithm is equipped, the process of 112KB will be put in the partition withA. 500KBB. 200KBC. 300KBD. 600KB54.Which of the following designs is not to share a file located in a remote machine.A. Maintaining several replicasB. IP address followed by a pathC. URLD. Virtual address55. A file’s attributes vary from one operating system to another, but typically consist ofA. File nameB. SectorsC. TypeD. The name of the creating program56.The per-process open-file table isA. unique and maintained by OS for all usersB. one of OS data structure for better performance of file system managementC. claimed by each process and for its own purposeD. an accounting data structure to tell how many files opened by the process57.As to the way accessing data of a file,A. The sequential manner is better than the random one.B. The random access is better than the sequential one.C. Both the sequential and the random access are the right way.D. Either the sequential or the random access is replaced by DBMS.58.Which of the following design is practical by operating systems.A. Automatically open a file while referenced for the first time, and close the file when the job terminates.B. The user has to open and close the file explicitly.C. The user has to open the file explicitly, but the file is closed automatically when the job terminates.D. All the above59.Regarding the file access permission, which of the following statements is NOT correct.A. The “Cloud” providing SaaS is an example facilitated the file system to write once but read many timesB. Some file systems are read only, not allowing any write operation.C. Some file systems are dedicated to write only once but read many timesD. The web site providing search service is an example facilitated the file system to write once but read manytimesB flash drive is popular nowadays. Usually it is not formatted withA. btrfsB. ISO 9660C. FA TD. EXT261.None of the disk-scheduling disciplines could avoid starvation, except ____.A. FCFSB. SSTFC. C-SCAND. C-LOOK62.Overheads are always associated with an interrupt service, resulting in worse performance. However, theydo not include the cost of ________A. saving process stateB. executing the instruction just next the interrupt pointC. restoring process stateD. flushing the instruction pipeline63.Look at the fact that requests are not usually uniformly distributed. For example, a cylinder containing thefile system FAT can be expected to be accessed more frequently than a cylinder that only contains files.And the fact that file systems typically find data blocks via an indirection table, such as a FAT in DOS.Which of the following ways would take advantage of this indirection to improve disk performance ?A. Keep the metadata in the nearest corner of cylindersB. Cache the metadata in primary memoryC. Back up the metadataD. Redesign the file system by discarding the indirection64.Which scheme of disk array provides no data redundancy ?A. RAID 3B. RAID 0C. RAID 1D. RAID 265.Suppose that a disk drive has 5000 cylinders, numbered 0 to 4999. The drive is currently serving arequest at cylinder 143, and the previous request was at cylinder 125. The queue of pending requests, in FIFO order, is86, 1470, 913, 1774, 948, 1509, 1022, 1750, 130Starting from the current head position, what is the sequence of cylinder number that the disk arm moves to satisfy all the pending requests, for the SSTF algorithms?A. 143, 913, 948, 1022, 1470, 1509, 1750, 1774, 4999, 130, 86B. 143, 913, 948, 1022, 1470, 1509, 1750, 1774, 130, 86C. 143, 130, 86, 913, 948, 1022, 1470, 1509, 1750, 1774D. 143, 86, 1470, 913, 1774, 948, 1509, 1022, 1750, 13066.Some file systems allow disk storage to be allocated at different levels of granularity. For example, a filesystem could allocate 4KB of disk space as a single block, or as four 1024-byte blocks. Do you think the example isA. Absolutely nonsenseB. Probably true, but it is only for academic researchC. Practical, because there exists a popular file system using the schemeD. Absolutely true, all file systems use the scheme67.Which of the following statements is wrong from the operating system view?A. Memory sometimes is used as a diskB. Memory sometimes is used as read onlyC. Memory sometimes is used as a USB flash driveD. Memory sometimes is used as a disk cache68. A logical address is ________A. the address in an object fileB. the address in an executable fileC. the address in a CPU instruction together with operatorD. All the above69. A file system uses a scheme with support for extents. A file is a collection of extents, with each extentcorresponding to a contiguous set of blocks. This file system is calledA. Contiguous allocationB. Linked allocationC.Indexed allocationD. None of above70.Which reason does not make sense: The operating system generally treats removable disks as shared filesystems but assigns a tape drive to only one application at a time, becauseA. Disks have fast random-access time, so they give good performance for interleaved access streams. Bycontrast, tapes have high positioning timeB. The owner of the Tape cartridge may wish to store the cartridge off-site (far away from the computer) tokeep a copy of the data safe from a fire at the location of the computerC. Historically tape cartridges are often used to send large volumes of data from a producer to the consumer.Such a tape cartridge is reserved for that particular data transferD. None of abovePart Two: (30 marks)1. ( 12 marks) Consider the following set of processes, with the length of the CPU-burst time given in milliseconds:Process Burst Time PriorityP1 10 3P2 1 1P3 2 3P4 1 4P5 5 2The processes are assumed to have arrived in the order P1, P2, P3, P4, P5, all at time 0. Suppose it is used FCFS, SJF, a non-preemptive priority (a smaller priority number implies a higher priority), and RR (quantum = 1) scheduling.a. What is the turnaround time of each process for each of the scheduling algorithms ?b. Which of the schedules results in the minimal average waiting time (over all processes)?2. ( 6 marks) Lamport's bakery algorithm is intended to improve the safety in the usage of shared resources among multi ple threads by means of mutual exclusion, briefed as following.1 lock(integer i) {2 Choosing[i] = true;3 Number[i] = 1 + max(Number[1], ..., Number[NUM_THREADS]);4 Choosing[i] = false;5 f f o r (j = 1; j <= NUM_THREADS; j++) {6 // Wait until thread j receives its number:7 w w h i l e (Choosing[j]) { /* nothing */ }8 // Wait until all threads with smaller numbers or with the same9 // number, but with higher priority, finish their work:10 w w h i l e ((Number[j] != 0) && ((Number[j], j) < (Number[i], i))) {11 /* nothing */12 }13 }14 }15 //critical section16 unlock(integer i) {17 Number[i] = 0;18 }1920 Thread(integer i) {21 w w h i l e (true) {22 lock(i);23 // The critical section goes here...24 unlock(i);25 // n o n-c r i t i c a l s e c t i o n...26 }27 }(1) Suppose Thread(i) and Thread(j) are running concurrently, will they occasionally get the same Number[] ?i.e. Number[i] == Number[j]. If so, please give a scenario.(2) If the Choosing array is not applied, i.e. Line 2, Line 4 and Line 7 are deleted, will the algorithm conflict with Critical Section Requirements of Mutual Exclusion, Progress and Bounded Waiting. If so, please give a scenario.3. ( 4 marks) Assume we have a demand-paged memory. The page table is held in registers. It takes 8 milliseconds to service a page fault if an empty page is available or the replaced page is not modified, and 20 milliseconds if the replaced page is modified. Memory access time is 100 nanoseconds. Assume that the page to be replaced is modified 70 percent of the time. What is the maximum acceptable page-fault rate for an effective access time of no more than 200 nanoseconds?4. ( 8 marks) The EXT2 file system defines an index array with 15 pointers to locate all data blocks of a file.(1) The first 12 items of the index array accommodate the locations of the first 12 data block.(2) The 13th item points to an index block called the indirect block, which contains index entries, each being a pointer to a data block.(3) The 14th item points to an index block containing entries, where each entry is a pointer to yet another indirect block as described in (2).(4) The 15th item points to an index block containing entries where each entry is a pointer to another index block as described in (3).Suppose the EXT2 data block is of size 4096 bytes, and an index entry is of size 4 bytes. Please answer how would be the maximal size of a file ?操作系统试卷参考答案和评分标准Part 1. Answer Sheet:(每小题1分,共计70分)12345678910A D D C C CB B B B11121314151617181920A A D D D C C C C B21222324252627282930A A A D D D D CB B31323334353637383940A A A A D C CB B B41424344454647484950A AB BC CD D A A51525354555657585960A B C D A B C D A B61626364656667686970A B B B C C C D D DPart 2.1.Answer: 12 分a. Turnaround time(共10分,错1个扣0.5分)FCFS RR SJF PriorityP1 10 19 19 16P211 2 1 1P3 13 7 4 18P4 14 4 2 19P5 19 14 96b. Shortest Job First(2分)2.Answer: 6 分(2小题各 3 分)(1) Number[i] = 1 + max(Number[1], ..., Number[NUM_THREADS]);This line of statement is not an atomic operation.If there is a breakout by the scheduler before and after the assignment operation, “=”, it may result in the snapshot, in which Number[i] == Number[j](2) Demo/* we have no choosing mechanism.Pi Pj*/->reg = max(.....) + 1;->reg = max(...) + 1;->set number[j] = reg;->for(index = 0; index < n; index++)->run when index == i;->while((number[index]!=0&&(number[index,index]< number[j,j]));/******* NOTE! the process i hasn't set number[i],so thecondition is false *********/-> enter critical section->set number[i] = reg;->while((number[index]!=0 && (number[index],index) < number[i],i)));/*-------------------------------------------------------------*//** here we can conclude that Pi can enter critical section as well as Pj **/3.Answer: 4 分0.2 _sec = (1 − P) ×0.1 _sec + (0.3P) ×8 millisec + (0.7P) ×20 millisec0.1 = −0.1P + 2400 P + 14000 P0.1 =16,400 PP =0.000006(答案正确的,给4分。
(完整word版)操作系统英文版课后习题答案整理(word文档良心出品)

1.1What are the three main purposes of an operat ing system?⑴ In terface betwee n the hardware and user;(2) man age the resource of hardware and software;(3) abstracti on of resource;Answer;•Tb provide an environment ksr a computer user to execute programs on computer h日rchvare in n convenient and efficient manner.•Tb allocate the separate resources of the computer as needed to st)ke the problem given.The allcxation prtxzess should b? as fair and efficient as possible.•Asa control program it serves two major functions; (1) supervision of the execution 由user programs to prevent errors and improper use of the computer, and (2) management of the operatioji and control of I/O devices.1.2 List the four steps that are necessary to run a program on a completely dedicated machine. Preprocessing > Process ing > Linking > Executi ng.Answer:乩Reserxe machine time*b* Manually load program into memory.u Load starting address and begin exe匚Lition.cL Monitor and control execution of program fr(im console.b. In teractivec. Time shar ingd. Real timee. Networkf. DistributedAnswera” Batch, Jobs w计h similar reeds are batched together and run through the computer as a group by ^r\operator or automatic jc)b s^quenc^r. [^rformanct? i$ incr^a^ed by atteiTipting to keep CPU 3nd I/O devices busv 311 timesi through buffering, off-line operation^ spooling, and multiprogramming. Batch is good for executing 】arge jobs thjit need little interacticm; it can be submitted and piuked up later.b. Interactive. This system is cumpofied of m^nv short transactions where the results of thenext transactiiin may be unpredictablen Respond time needs tn be short (sectwids) since the user submits and waik for the result.u Time sharing. This systems u 船呂匚Pl sch<*duling ^nd multi programming to pmvidu eConoiniCcil interactive use of 蛊system. The CPL switches rapidly iri>m one user tn another Instead of having a job defined by spcxiled card images^ each program readsits next control card from the terminab and output is normally printed immediately to the screen.(_L Real time. Often tisvci in a dedicated application, this system reads information from sensors and must respond within a fixed amount of time to ensure correct performance.work.f.Distributed .This system distributes computation among several physical processors” TheprtKessors do not share menion- or a clock. Instead, each pnxzessor has its own kxzalmemory. They communicate with each other through various communication lines f such asa high-speed bus or telephone line.1.7 Wehave stressed the need for an operating system to make efficient use of the computing hardware. When is it appropriate for the operating system to forsake this principle and to waste ” resources? Why is such a system not really wasteful?Answer Single-user systems should maximize use of the system for the user A GUImight "xvastc * GPL' cycles, but it optimizes the user T s interaction with the system.2.2 How does the distinction between monitor mode and user mode function as a rudimentary form of protecti on (security) system?Answer: By establishing a set of privileged instructions that can be executed only when in tlie m(snitnr mt)de f the tiperating system is assured of controlling the entire system at all times.2.3 What are the differences between a trap and an interrupt? What is the use of eachfun cti on?Answer An interrupt is a ha rd \ v a re-^en era ted change-of-flow within the system. An interrupt handler is summoried to deal with the cause oF the interrupt; control is then re turned to the interrupted context and instruction. A trap is a software-j;enerated interrupt. An interrupt can be uwd to signal the compJrtio n “f an I/O obviate the nevd for polling. A trap can be used ti> call operating svstem routines or to catch arithmetic errors.2.5 Which of the follow ing in structi ons should be privileged?a. Set value of timer.b. Read the clock.c. Clear memory.d. Turn off interrupts.e. Switch from user to monitor mode.3OS Exercise BookClass No. NameAnswer: The following instructions should be privileged:Set value of timer,b.Clear memory.Jc.Turn off interrupts.d.Switch from user to monitor mode*2.8 Protecting the operating system is crucial to ensuring that the computer system operates correctly. Provision of this protection is the reason behind dual-mode operation, memory protection, and the timer. To allow maximum flexibility, however, we would also like to place mini mal con stra ints on the user.The following is a list of operations that are normally protected. What is the minimal setof in structi ons that must be protected?a. Change to user mode.b. Change to mon itor mode.c. Read from mon itor memory.d. Write into mon itor memory.e. Fetch an instruction from monitor memory.f. Tur n on timer in terrupt.g. Turn off timer interrupt.Answer: The minimal 5et of instructions that must be protected are:a.Change to monitor mtxle.b.Read from moni tor memory*c.Write into monitor me mor v.Jd.Turn off timer interrupt3.6 List five services provided by an operat ing system. Explain how each provides convenience to the users. Explain also in which cases it would be impossible for user-level programs to provide these services.Answer;«Program execution. The operating system loads thv contents (or sections) of a file into menidry and begins its execution. A user-level program could not be trusted to properly allocate CPU time.•I/O operations. Disks, tapes, serial lines;and other devices must be communicated with ata very low level. The user need only specify the dev ice and the operation to perform (in it,while the system converts that request into <ie\r ict^ or contr<i11er-spec i fit commands.User-level pnjgrams cannot be trusted to only access devices they should have access to and to only access them when they otherwise unused.«File-system manipulation, fhere are manv details in file creation, deletion/ alkKation, and naming that users should not have to perform. Blocks of disk space are used by files and must be tracked, deleting a file requires remo\ ing the name file information and freeing the <ilkx:ated blocky I^ratections must also be checked to assure proper file access. User prc^grams could neither ensure adherence to protect]on methcxis nor be trusted to allocate only free block吕and deallocate bkxzks on file deletion.J•Communications. Message passing between systems requires messages be turned into packets of information, sent to the network controller, trannmitted across a community tk>ns medium, and reassembled by the destination system.卩acket ordering and data correction must take place. Again, user program吕might not c(sordinate ac cess to the network dev ice, or they might receive packets destined tor other processes^»Error detection. Error detection (occurs at both the hardware and soFtwart? levels. At tlie hardware level, all data transfers must be inspected to ensure that data hax e not beencorrupted in transit All data on media must be checked to be sure they have not changed since they uritten to the media. At the software level, media must bechecked for data ccnsistencj^; for instance, do the number of allocated and unallocated blocks of storage match the total number on the device. There, errors are frequently pnxzess-independent (for instance, the 匚omiption of data on a disk)5 sc there must be a global program (the operating system) that handles all h pes of errors. Also, by having errors pmc essed by the operating system, processes need not contain code to catch and ccjrrect all the ernjrs possible on a system.3.7 What is the purpose of system calls?Answer; Sv>ttn'. dlltnv ustr-levtl lu request str\ ices nt 11 it? uperating svs-tem.3.10 What is the purpose of system programs?J V USWCE Svstcm programs can be thought of as bundle!ti of useful system oils. Thev r provide bcisic functidcaliU users and sci users do not need to wnte their cwn programs to s<>k r e comnicMi problems,4.1 MS-DOS provided no means of con curre nt process ing. Discuss three major complicati onsthat con curre nt process ing adds to an operat ing system.5OS Exercise BookClass No. NameAnswer:*A method of time sharing must be implemented to allow each of several prcxzesses to have access to the system. This method involves the preemption of processes that do notvoluntarily give up the CPU (by using a system ca1]r for instance) and the kernel being reentrant (so more than one prtxzess may be executing kernel code concurrently).・[Vocesses and system resources must have protections and must be protected from each other. Any given process must be limited in the amount of memory it can use and tlie ope Mt ions 让can perform on devices like di^ks.•Care must be taken in the kernel to prevent deadkxzks between prucesses, so processesaren*t waiting for each other's allocated rest>urces,4.6 The correct producer —consumer algorithm in Section 4.4 allows only n-1 buffers to befull at any one time. Modify the algorithm to allow all buffers to be utilized fully.Answer: No answer.5.1 Provide two program ming examples of multithread ing givi ng improve performa nee overa sin gle-threaded soluti on.Answer (1) A Web server that services each request in a separate Lliread. (2) A parallelized application such as matrix multiplication where different parts of the matrix may be worked on in parallel. (3) An intEivictin GUI program such as a debugger where a thread is used to monitor user input, another thread represents the running application, and a third thread monitors performance.5.3 What are two differences between user-level threads and kernel-level threads? Underwhat circumsta nces is one type better tha n the other?Answer: Context switching between user threads is quite sinniliir to switching between kernel threads, although it is dependent on the threads library and how it maps user threads to kernel threads. In general, context switching between user threads involves taking a user thread of its LWP and replacing it with another thread. This act typically involves saving and restoring the stttte of the registers.6.3 Consider the following set of processes, with the length of the CPU-burst time given inmillisec on ds:Process Burst Time PriorityP1103P211P323F414P552The processes are assumed to have arrived in the order P l, F2, F3, F4, P5, all at time 0.a.Draw four Gantt charts illustrati ng the executi on of these processes using FCFS, SJF, a non preemptive priority (a smaller priority n umber implies a higher priority), and RR (qua ntum = 1) scheduli ng.b.What is the turnaround time of each process for each of the scheduling algorithms in part a?c.What is the waiting time of each process for each of the scheduling algorithms in part a?d.Which of the schedules in part a results in the minimal average waiting time (over all processes)?An swer:Answer;a.The four Gantt charts areb.Turnaround timeFCFS RR SJF Priority101919 16112 1 113 741814421919149 6 匚Waiting time (turnaround time minus burst time)FCFS RR SJF Priority卩】0996Pz10100心115216P*133118Ps14941d. Shortest Job First6.4 Suppose that the following processes arrive for execution at the times indicated. Eachprocess will run the listed amou nt of time. In an sweri ng the questi ons, use non preemptive scheduling and base all decisions on the information you have at the time the decisionmust be made.PtXKCSS Ai ri\ al Time Burst Time0.087OS Exercise BookClass No. NameP20.44l.D1a. What is the average turnaround time for these processes with the FCFS scheduling algorithm?b. What is the average turnaround time for these processes with the SJF scheduling algorithm?c. The SJF algorithm is supposed to improve performa nee, but no tice that we chose to run process P1 at time0 because we did not know that two shorter processes would arrive soon. Compute what the average turnaround time will be if the CPU is leftidle for the first 1 un it and the n SJF scheduli ng is used. Remember that processes P1 and P2 are wait ing dur ing this idle time, so their wait ing time may in crease. Thisalgorithm could be known as future-k no wledge scheduli ng.Answera.10.53b.9.53c.6,86Remember that turnaround time LS finishing time minus arrival time, so have to subtract the arrival tinier to compute thu turnaround times. FCFS is 11 if you forget to subtract arrival time.6.10 Explain the differences in the degree to which the following scheduling algorithms discrim in ate in favor of short processes:a.FCFSb.RRc.Multilevel feedback queuesAnswer:a.FCFS—discriminates against short jobs since any short jobs arriving after long jobs willhave a longer waiting time.b.RR一treats all jobs equally (giving them equal bursts of CPU time) so short jobs will beable to leave the system faster since they will finish first.c.Multilevel feedback queues—work similar to the RR algorithm—thev discriminatefa^r i>rably toward slusrt jobs.7.7 Show that, if the wait and sig nal operati ons are not executed atomically,then mutual exclusi on may be violated.Answer No answer.7.8 The Sleepi ng-Barber Problem. A barbershop con sists of a wait ing room with n chairs and the barber room containing the barber chair. If there are no customers to be served,the barber goes to sleep. If a customer en ters the barbershop and all chairs are occupied,then the customer leaves the shop .If the barber is busy but chairs are available, the nthe customer sits in one of the free chairs. If the barber is asleep, the customer wakes up the barber. Write a program to coord in ate the barber and the customers.Answer: Please refer to the support ing Web s its for source code solution,8.2 Is it possible to have a deadlock involving only one single process? Explain your answer.Answer Ncx I'his folknvs directly from the hold-and-wait condition.8.4 Con sider the traffic deadlock depicted in Figure 8.11.a. Show that the four n ecessary con diti ons for deadlock in deed hold in this example.b. State a simple rule that will avoid deadlocks in this system.Answer No answer.8.13 Con sider the follow ing sn apshot of a system:Allocati on Max AvailableA B C D A B C D A B C DP00 0 1 20 0 1 2 1 5 2 0P1 1 0 0 0 1 7 5 0P2 1 3 5 4 2 3 5 6P30 6 3 20 6 5 2P40 0 1 40 6 5 6An swer the follow ing questi ons using th e ban ker s algorithm:a.What is the content of the matrix Need?b.Is the system in a safe state?c.If a request from process P1 arrives for (0,4,2,0), can the request be gran tedimmediately?Answer;A. Deadlcx^k cannot ixrcur because preemption exists,b. Yes. A process may never acquire all the resources 让needs if they are continuouslypreempted by a series of requests such as those of process C.9.5 Given memory partitions of 100K, 500K, 200K, 300K, and 600K (in order), how would each of the First-fit, Best-fit, and Worst-fit algorithms place processes of 212K, 417K, 112K,and 426K (in order)? Which algorithm makes the most efficie nt use of memory?Answer:a. First-fit:b* 212K is put in 500K partitionc. 417K is put in 600K partitiond* 112K is put in 288K partition (new partition 288K = 500K - 212K)e.426K must waitf.Best-fit:g.212K is put in 300K partition9OS Exercise BookClass No. Nameh.417K is put in 500K partitioni.112K is put in 200K partitionj.426K is put in 600K partitionk.Worst-fit:L 212K is put in 600K partitionm. 417K is put in 500K partitionn. 112K is put in 388K partitionc 426K must waitIn this example, Best-fit turns out to be the bE%t*9.8 Con sider a logical address space of eight pages of 1024 words each, mapped onto a physicalmemory of 32 frames.a. How many bits are there in the logical address?b. How many bits are there in the physical address?Answera,l.ogica) address: 13 bitsb.Physical address: 15 bitsJ9.16 Con sider the follow ing segme nt table:Segme nt Base Len gth02196001230014290100313275804195296What are the physical addresses for the follow ing logical addresses?a. 0,430b. 1,10c. 2,500d. 3,400e. 4,112Answer:a.219 + 430 = 649b.2300 + 10 = 2510u ill亡月ed reference, trap ki operating systemd.1327 -b 400 = 1727e.illegal reference, trap to operating system10.2 Assume that you have a page referenee string for a process with m frames (initiallyall empty). The page refere nee stri ng has len gth p with n disti net page n umbers occur init. For any page-replacement algorithms,a. What is a lower bou nd on the n umber of page faults?b. What is an upper bou nd on the n umber of page faults?Answer:a* nb»p1, 2, 3, 4, 2, 1,5, 6, 2, 1,2, 3, 7, 6, 3, 2, 1, 2, 3, 6.How many page faults would occur for the following replacement algorithms, assuming one, two, three, four, five, six, or seven frames? Remember all frames are initially empty, so your first unique pages will all cost one fault each.LRU replaceme ntFIFO replaceme ntOptimal replaceme nt11OS Exercise BookClassNo.NameNumbei of frames1 2 3 4 5 6 711.7 Expla in the purpose of the ope n and close operati ons.Answer :» The o[fen operation informs the system that the named file is about to bect>me active^ * Tlie cluse operation informs the system that the named file )s nt> lunger in active use by the user who issued the dose operation.11.9 Give an example of an application in which data in a file should be accessed in the followi ng order: a. Seque ntially b. Ran domlyAnswer :a. Print the 匚 on tent of the file,b. Print the content of record /. This record can be found using hashing or index tech niques.11.12 Con sider a system that supports 5000 users. Suppose that you want to allow 4990 of these users to be able to access one file.a. How would you specify this protection scheme in UNIX?b. Could you suggest ano ther protecti on scheme that can be used more effectively for this purpose tha n the scheme provided by UNIX?Answer:a. There are twc methods for achieving this : L Create an access control list withtlu? names of all 4990 users.ii. Put these 4990 users in one ^roup and set the group access accordingly. This scheme cannot always be implemented since user groups are restricted by the system. b. The universe access information applies to all users unless their name appears in the access-control list with different access permission. With this scheme you simply put the names of the remaining ten users in the access control list but \v 让h no access pri\ ileges allovcexfLRUFIFOOptimal 20 20 20 18 18 15 15 16 11 10 14 8 8 10 7 7 10 7 7 77Answer12.1 Consider a file currently consisting of 100 blocks. Assume that the file control block (andthe index block, in the case of indexed allocation) is already in memory. Calculate howmany disk I/O operations are required for contiguous, linked, and indexed (single-level)allocati on strategies, if, for one block, the follow ing con diti ons hold. In thecon tiguousallocati on case, assume that there is no room to grow in the beg inning, but there is room to grow in the end. Assume that the block in formatio n to be added is stored in memory.a. The block is added at the beg inning.b. The block is added in the middle.c. The block is added at the end.d. The block is removed from the begi nning.e. The block is removed from the middle.f. The block is removed from the end.AnswerLinked Indexeda. 201 1 1b. 1015211 3 1d. 198 1 0e. 9852 0f. 0 100 013.2 Con sider the follow ing I/O sce narios on a sin gle-user PC.a. A mouse used with a graphical user in terfaceb. A tape drive on a multitasking operating system (assume no device preallocation is available)c. A disk drive containing user filesd. A graphics card with direct bus conn ecti on, accessible through memory-mappedI/OFor each of these I/O scenarios, would you design the operating system to use buffering, spooli ng, cachi ng, or a comb in ati on? Would you use polled I/O, or in terrupt-drive n I/O? Give reas ons for your choices.Answer:a. A mouse used with a graphical user interfaceBuffering may be needed to record mouse movement during times when higher- priority operations are taking place. Spooling and caching are inappropriate. Inter rupt driven I/O is most appropriate^b” A tape drive on a multitasking operating system (assume no device preAlkxzation is available)Buffering may be needed to manage throughput d让ferEria? behveen the tape drive and the sounzt? or destination of the I/O, C臼匚hing can be used to hold copies of that resides on the tape, for faster access. Spooling could be used to stage data to the device whenmultiple users desire to read from or write to it” Interrupt driven [/O is likely to allow the best performance.13OS Exercise BookClass No. Name匸* A disk drive containing user tilesBuffering can be used to hold data while in transit from user space to the disk, and visaversa. Caching can be used to hold disk-resident data for improved perfor mance.Spoc^ling is not necessary because disks are shared-access devices. Interrupt- driven T/O is best for devices such as disks that transfer data at slow rates,d. A graphics card w让h direct bus coi^nection, accessible through mem<irv-mapped I/OBuffering may be needed to control multiple access and for performance (doublebuffering can be used to hold the next screen image while displaying the current tme). Caching and spooling are not necessary r due to the fast and shared-access natures of the device. Polling and interrupts are only useful for input and for【/O completion detec tion f neither of which is needed for a mem()r y-ma pped device.14.2 Suppose that a disk drive has 5000 cylinders, numbered 0 to 4999. The drive is currently serving a request at cylinder 143, and the previous request was at cylinder 125. The queue of pending requests, in FIFO order, is86, 1470, 913, 1774, 948, 1509, 1022, 1750, 130Start ing from the curre nt head positi on, what is the total dista nee (in cyli nders) thatthe disk arm moves to satisfy all the pending requests, for each of the follow ingdiskscheduli ngalgorithms?a. FCFSb. SSTFc. SCANd. LOOKe. C-SCANAnswer:乩The FCFS schedule is 143f 86f 1470, 913, 1774, 948, 1509, 1022, 1754), 130. The total seek distance is 7081.b. The SSTF schedule is 143, 130, 86. 913, 948, 1022, 1470, 1509. 1750r 1774. The total seekdistance is 1745.€. The SCAN schedule is 143, 913, 94«f1022f 1470, 1509,1750f 1774, 4999,130, 86. The to怙1 seek distance is 9769.d.The LOOK schedule is 143, 913, 948,1022, 1470,1509,1750,177< 130,86. The total seekdistance is 3319*e.The C-SCAN schedule is 143f 913,948,1022J 470,1509.1750,1774,4999,8& 130. The totalseek distance is 9813.f.(Bonus.) The C-LOOK schedule is 143,913,94& 1022,1470,1509.1750,1774, 86,130. Thetotal seek distance is 3363.1.1 1.62.3 2.53.7 6.3 6。
英文版计算机试题及答案

英文版计算机试题及答案一、选择题(每题2分,共20分)1. Which of the following is not a function of an operating system?A. Process managementB. Memory managementC. Data storageD. File management2. In a computer network, what does the term "bandwidth" refer to?A. The width of the network cableB. The maximum rate of data transferC. The number of users connectedD. The speed of the network processor3. What is the primary purpose of a firewall?A. To prevent unauthorized access to a networkB. To encrypt dataC. To manage network trafficD. To store user passwords4. Which of the following is a type of software used for creating and editing documents?A. Spreadsheet softwareB. Database softwareC. Word processing softwareD. Graphics software5. What is the term used to describe the process of converting data from one format to another?A. Data migrationB. Data transformationC. Data conversionD. Data translation6. What does the acronym "CPU" stand for in computing?A. Central Processing UnitB. Central Processing UnitC. Computer Processing UnitD. Computing Processing Unit7. What is the function of a router in a network?A. To connect multiple networksB. To store dataC. To provide power to devicesD. To print documents8. What is the process of finding and fixing errors in software called?A. DebuggingB. PatchingC. UpdatingD. Patching9. Which of the following is a type of computer virus that replicates itself by attaching to other programs?A. TrojanB. WormC. RansomwareD. Spyware10. What is the term for the graphical representation of data on a computer screen?A. Data visualizationB. Data representationC. Data graphingD. Data mapping二、填空题(每题2分,共20分)1. The _________ is the primary memory used by a computer to store data and instructions that are currently being processed.2. A _________ is a type of software that allows users to create and edit images.3. The process of converting analog signals to digital signals is known as _________.4. A _________ is a collection of data stored in a structured format.5. The _________ is a hardware component that connects a computer to a network.6. In computer programming, a _________ is a sequence of statements that perform a specific task.7. The _________ is a type of malware that hides its presence and waits for a trigger to activate.8. A _________ is a type of software that is designed to protect a computer from unauthorized access.9. The _________ is the process of organizing and managing data in a database.10. A _________ is a type of software that allows users tocreate and edit spreadsheets.三、简答题(每题10分,共30分)1. Describe the role of a server in a computer network.2. Explain the difference between a compiler and an interpreter in programming.3. Discuss the importance of data backup and recovery in a computing environment.四、编程题(每题15分,共30分)1. Write a simple program in Python that calculates the factorial of a given number.2. Create a function in Java that takes an array of integers and returns the largest number in the array.答案:一、选择题1. C2. B3. A4. C5. C6. A7. A8. A9. B10. A二、填空题1. RAM (Random Access Memory)2. Graphics software3. Analog-to-digital conversion4. Database5. Network interface card (NIC)6. Function or procedure7. Trojan8. Antivirus software9. Database management10. Spreadsheet software三、简答题1. A server in a computer network is a powerful computer or system that manages network resources, including hardware and software, and provides services to other computers on the network, such as file storage, web hosting, and print services.2. A compiler is a program that translates source codewritten in a programming language into machine code that a computer can execute. An interpreter, on the other hand, reads and executes the source code line by line without the need for a separate compilation step.3. Data backup and recovery are crucial in a computing environment to prevent data loss due to hardware failure, software bugs, or malicious attacks. Regular backups ensure that data can be restored to a previous state in case of corruption or deletion.四、编程题1. Python Program for Factorial Calculation:```pythondef factorial(n):if n == 0:return 1 else:。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
XX大学2011 ——2012 学年第一学期《操作系统》期末考试试题(A)一.选择题(20分,每题1分)1. Generally speaking, which one is not the major concern for a operating system in the following four options?( D )A.Manage the computerB.Manage the system resourcesC.Design and apply the interface between user's program and computer hardware systemD.High-level programming language complier2.The main disadvantage of batch system is ( C )A.CPU utilization is lowB.Can not concurrentck of interactionD.Low degree of automation3.A process transforms from waiting state to ready state is caused by the ( B )A.Interrupt eventB.Process schedulingC.Create a process for a programD.Waiting for some events4.The concurrent process is refers to ( C )A.The process can be run in parallelB.The process can be run in orderC.The process can be run in the same timeD.The process can not be interrupted5.In multi-process system, in order to ensure the integrity of public variables, the processes should be mutually exclusive access to critical areas. The so-called critical area is ( D )A.A bufferB.A date areaC.Synchronization mechanismD.A program6.The orderly use of resources allocation strategy can destroy the condition ( D ) to avoid deadlock.A.Mutual exclusiveB.Hold and waitC.No preemptionD.Circular waiter's applications use the system resources to complete its operation by the support and services of ( C )A.clicking the mouseB.Keyboard commandC.System callD.Graphical user interface8.There are four jobs arrived at the same time and the execution time of each job is 2h. Now they run on one processor at single channel,then the average turnaround time is ( B )A.1hB.5hC.2.5hD.8h9.Among the job scheduling algorithms, ( B ) is related to the job's estimated running time.A.FCFS scheduling algorithmB.Short-job-first scheduling algorithmC.High response ratio algorithmD.Balanced scheduling10.In memory management, the purpose of using the overlay and swapping is ( C )A.Sharing main memoryB.Expanding main memory physicallyC.Saving main memory spaceD.Improving CPU utilization11.In the page-replacement algorithm,which one can cause the Belady phenomenon? ( A )A.FIFOB.LRUC.CLOCKINGD.OPT12.The following description of the system in safe state,which one is correct?( B )A.It must cause deadlock if the system is in insecure stateB.It may cause deadlock if the system is in insecure stateC.It may cause deadlock if the system is in secure stateD.All are wrong13.Generally, when we talk about"Memory Protection", the basic meaning is ( C )A.Prevent hardware memory from damagingB.Prevent program from losing in memoryC.Prevent the cross-border call between programsD.Prevent the program from being peeped14.The actual capacity of virtual memory is equal to ( B )A.The capacity of external memory(disk)B.The sum of the capacity of external memory and main memoryC.The space that the CPU logical address givesD.The smaller one between the option B and C15.Physical file's organization is determined by ( D )A.ApplicationsB.Main memory capacityC.External memory capacityD.Operating system16.A computer system is configured with two plotters and three printers,in order to properly drive these devices,system should provide ( C ) device driver program.A.5B.3C.2D.117.When there are fewer number of channels in system ,it may cause "bottlenecks”. To solve this problem, which of the follow options is not the effective way?( A )A.improving the speed of CPUing the virtual device technologyC.Adding some hardware buffer on the devicesD.Increasing the path between devices and channels18.When I/O devices and main memory are exchanging data, it can be achieved without CPU's frequently intervention, this way of exchanging data is called ( C )A.PollingB.InterruptsC.Direct memory accessD.None of them19.The following description of device management, which one is not correct?( B )A.All external devices are managed by the system in uniformB.Channel is a software of controlling input and outputC.The I/O interrupt events from the I/O channel are managed by device managementD.One of the responsibility of the operating system is to use the hardware effectively20.The operating system used ( A ), it realized a mechanism that we can use more space to save more time.A.SPOOLINGB.Virtual storageC.ChannelD.Overlay二.填空题(20分,每空1分)1.Software may trigger an interrupt by executing a special operation called a system call .(P7)2.If there is only one general-purpose CPU, then the system is a single-processor system.(p12)3. A process can be thought of as a program in execution. (p79)4.As a process executes, it changes state. Each process may be in one of the following states: new, running, waiting, ready or terminated .(p83)5.Long-term(job) scheduling is the selection of processes that will be allowed to contend for the CPU. And Short-term(CPU) scheduling is the selection of one process from the ready queue. (p116)6.The process executing in the operating system may be either independent processes or cooperating processes. Cooperating processes require an interprocess communication mechanism to communicate with each other. Principally, communication is achieved through two schemes: share memory and message passing. (p116)7. In modern operating systems, resource allocation unit is process, processor scheduling unit is thread. (p127)8. Most modern operating systems provide kernel support for threads; among these are Windows, as well as Solaris and Linux. (p146)9. CPU scheduling is the basis of multiprogrammed operating systems. (p153)10. The FCFS algorithm is nonpreemptive; the RR algorithm is preemptive.11. Sometimes, a waiting process is never again able to change state, because the resources it has requested are held by other waiting processes. This situation is called deadlock . (p245)12. The main purpose of a computer system is to execute programs. These programs, together with the data they access, must be in main memory (at least partially) during execution. (P274)13. The various memory-management algorithms differ in many aspects. In comparing different memory-management strategies, we use the follow considerations: Hardware support, Performance, Fragmentation, Relocation, Swapping, Sharing and protection . (p310)14.A process is thrashing if it is spending more time paging than executing.15.Virtual memory is a technique that enables us to map a large logical address space onto a smaller physical memory.(p365)16.When we solve the major problems of page replacement and frame allocation,the proper design of a paging system requires that we consider page size,I/O,locking,process creation,program structure,and other issues.(p366) 17.The operating system abstracts from the physical properties of its storage devices to define a logical storage unit,the file . (p373)18.Since files are the main information-storage mechanism in most computer system,file protection is needed.(p408)19.The seek time is the time for the disk arm to move the heads to the cylinder containing the desired sector.(P457)20.The hardware mechanism that enables a device to notify the CPU is called an interrupt .(p499)三.简答题(30分,每题6分)1.What is the operating system?What role does the operating system play in acomputer?开放题,解释操作系统概念,操作系统可以实现哪些基本功能?关键词:a.管理系统资源,控制程序运行,改善人机界面,为其他应用软件提供支持。
