Firebird数据库的中文参考资料
firebird数据库语法

firebird数据库语法Firebird数据库是一种开源的关系型数据库管理系统,它采用SQL 语言进行数据操作和管理。
本文将介绍Firebird数据库的语法和用法,帮助读者更好地了解和使用Firebird数据库。
一、Firebird数据库的基本概念Firebird数据库是基于关系模型的数据库系统,它由多个表组成,每个表包含多个列,用于存储和管理数据。
Firebird数据库使用SQL语言进行数据的增删改查操作,可以灵活地满足各种应用程序的需求。
二、Firebird数据库的表操作在Firebird数据库中,可以使用CREATE TABLE语句创建表,语法如下:CREATE TABLE 表名(列1 数据类型,列2 数据类型,...);例如,创建一个名为"students"的表,包含"id"和"name"两列,数据类型分别为整数和字符串,可以使用以下语句:CREATE TABLE students(id INTEGER,name VARCHAR(50));三、Firebird数据库的数据插入操作在Firebird数据库中,可以使用INSERT INTO语句向表中插入数据,语法如下:INSERT INTO 表名 (列1, 列2, ...)VALUES (值1, 值2, ...);例如,向"students"表中插入一条数据,可以使用以下语句:INSERT INTO students (id, name)VALUES (1, '张三');四、Firebird数据库的数据查询操作在Firebird数据库中,可以使用SELECT语句查询表中的数据,语法如下:SELECT 列1, 列2, ...FROM 表名WHERE 条件;例如,查询"students"表中所有数据,可以使用以下语句:SELECT id, nameFROM students;五、Firebird数据库的数据更新操作在Firebird数据库中,可以使用UPDATE语句更新表中的数据,语法如下:UPDATE 表名SET 列1 = 值1, 列2 = 值2, ...WHERE 条件;例如,将"students"表中id为1的记录的name更新为"李四",可以使用以下语句:UPDATE studentsSET name = '李四'WHERE id = 1;六、Firebird数据库的数据删除操作在Firebird数据库中,可以使用DELETE FROM语句删除表中的数据,语法如下:DELETE FROM 表名WHERE 条件;例如,删除"students"表中id为1的记录,可以使用以下语句:DELETE FROM studentsWHERE id = 1;七、Firebird数据库的数据排序操作在Firebird数据库中,可以使用ORDER BY子句对查询结果进行排序,语法如下:SELECT 列1, 列2, ...FROM 表名ORDER BY 列 [ASC|DESC];其中,ASC表示升序排序,DESC表示降序排序。
关于SQLite 与 FireBird 利弊分析

关于SQLite 与FireBird 利弊分析关于SQLite 与FireBird 利弊分析经查阅网上资料:一、关于数据库简介:SQLite 主页:SQLite诞生于2000年5月,这几年增长势头迅猛无比,目前版本是3.3.8。
SQLite的特点如下:1、无需安装配置,应用程序只需携带一个动态链接库。
2、非常小巧,For Windows 3.3.8版本的DLL文件才374KB。
3、ACID事务支持,ACID即原子性、一致性、隔离性、和持久性(Atomic、Consistent、Isolated、和Durable)。
4、数据库文件可以在不同字节顺序的机器间自由的共享,比如可以直接从Windows移植到Linux或MAC。
5、支持数据库大小至2TB。
6、sqlite无疑是最小的一个,单文件程序,只有400k,而它生成的数据库文件也是单文件。
它支持大部份SQL92标准,不过遗憾的是不支持外键与存储过程Firebird 嵌入服务器版(Embedded Server)主页:从Interbase开源衍生出的Firebird,充满了勃勃生机。
虽然它的体积比前辈Interbase缩小了几十倍,但功能并无阉割。
为了体现Firebird短小精悍的特色,开发小组在增加了超级服务器版本之后,又增加了嵌入版本,最新版本为2.0。
Firebird的嵌入版有如下特色:1、数据库文件与Firebird网络版本完全兼容,差别仅在于连接方式不同,可以实现零成本迁移。
2、数据库文件仅受操作系统的限制,且支持将一个数据库分割成不同文件,突破了操作系统最大文件的限制,提高了IO吞吐量。
3、完全支持SQL92标准,支持大部分SQL-99标准功能。
4、丰富的开发工具支持,绝大部分基于Interbase的组件,可以直接使用于Firebird。
5、支持事务、存储过程、触发器等关系数据库的所有特性。
6、可自己编写扩展函数(UDF)。
7、firebird其实并不是纯粹的嵌入式数据库,embed版只是其众多版本中的一个。
FireBird - Quick Start Guide

Firebird Quick Start Guide}What is in the kit?IBPhoenix PublicationsFirebird Quick Start GuideThis section is an introduction for the complete newcomer to a few essentials for getting off to a quick start with a Firebird binary kit. For the fine details of configuring and running your server and tuning your installation, please refer to Chapters 4-6 of the Using Firebird manual, distributed on the IBPhoenix CD.What is in the kit?All of the kits contain all of the components needed to install the Firebird server:• the Firebird server executable• a client library located on the server machine• the command-line tools• the standard user-defined function libraries• a sample database• the C header files (not needed by beginners!)• release notes—ESSENTIAL READING!Default disk locationsThe following table describes the default disk locations for the components on Windows and Linux. Information is provided in two version contexts:• versions prior to Firebird 1.5• versions from Firebird 1.5 onward❖These differences are important. Versions prior to Firebird 1.5 use many of the same locations, component names and resource links as InterBase 6.x and prior versions of InterBase. Hence, itis not possible to run both a Firebird server and an InterBase server on the same machine withthese versions.In the major codebase revision starting at v.1.5, the old hard links to InterBase artifacts were removed and many of the major components were renamed. Firebird 1.5 may permit a running InterBase® server to be present. It is a certain objective for Firebird 2.Table 1: Components of the Firebird installationPlatform Component File Name Default Location32-bit and64-bit Windows Firebird server Pre v.1.5ibserver.exev.1.5 and onwardfbserver.exec:\Program Files\Firebird\binCommand-linetoolsgbak.exe, gfix.exe,gstat.exe, etc.c:\Program Files\Firebird\bin Sample database Employee.gdb c:\Program Files\Firebird\examplesUser-definedfunction (UDF)librariesib_udf.dll & ib_utils.dllfbudf.dll c:\Program Files\Firebird\udfWindows NT, 2000, XP Firebird client Pre v.1.5gds32.dllv.1.5 and onwardgds32.dll, linkingthrough to xxxxx.dllc:\Winnt\System32Windows 9x,ME Firebird client As above c:\WindowsPlatform Component File Name Default LocationLinux and possibly other UNIX distros Firebird server Pre v.1.5ibserverv.1.5 and onwardfbserver/opt/interbase/binTBACommand-linetoolsgbak, gfix, gstat, etc.Pre v.1.5v.1.5 and onward/opt/interbase/binTBASample database employee.gdbPre v.1.5v.1.5 and onward/opt/interbase/binTBAUDF libraries Pre v.1.5ib_udf.sov.1.5 and onwardib_udf.sofbudf.so/opt/interbase/udfTBAFirebird client Pre v.1.5libgds.so.0 (binary)libgds.so (symlink)v.1.5 and onwardTBA/usr/libTable 1: Components of the Firebird installationFirebird Quick Start Guide}Installing Firebird Installing FirebirdInstallation drivesFirebird server—and any databases you create or connect to—must reside on a hard drive that is physically connected to the host machine. You cannot locate components of the server, or any database, on a mapped drive, a filesystem share or a network filesystem.✰You can mount a read-only database on a CD-ROM drive but you cannot run Firebird server from one.Installation script or programAlthough it is possible to install Firebird by a filesystem copying method—such as “untarring” a snapshot build file or decompressing a structured WinZip “.zip” file—it is strongly recommended that you use the distributed release kit the first time you install Firebird. The Windows executable installation script, the Linux rpm (RedHat Package Manager) program and the official tar.gz for other Posix platforms perform some essential setup tasks. Provided you follow the instructions correctly, there should be nothing for you to do upon completion but log in and go!Windows platformsOn server platforms—Windows NT, 2000 and XP—the Firebird service will be running when the installation completes. Next time you boot up your server machine, it will be started automatically. To find out how to start and stop the server manually, see Running Firebird on Windows, p. 54 chapter 4 of Using Firebird.The non-server Windows platforms—Windows 95, 98 and ME—do not support services. The installation will start Firebird server as an application, protected by another application known as the Guardian. If the server application should terminate abnormally for some reason, the Guardian will attempt to restart it.✰A copy of the client library—gds32.dll—will have been installed in your system directory.Posix platformsIn all cases, read the release notes that pertain to the version of Firebird that you are going to install. There may be significant variations from release to release of any Posix operating system, especially the open source ones. Where possible, the build engineers for each Firebird version have attempted to document any known issues.!If you do not find a copy of the release notes in your kit, go back to the Downloads page of the Firebird website at and download a copy from there.If you have a Linux distribution that supports rpm installs, consult the appropriate platform documentation for instructions about using RedHat Package Manager. In most distributions you will have the choice of performing the install from a command shell or through a GUI interface.For Linux distributions that cannot process rpm programs, and for the various UNIX flavors, use the “.tar.gz” kit. You will find detailed instructions in the release notes.Shell scripts have been provided. In some cases, the release notes may instruct you to modify the scripts and make some manual adjustments.Testing your installationIf everything works as designed, the Firebird server process will be running on your server upon completion of the installation. It will start up automatically whenever you restart your server.At this point, it is assumed that you will use the recommended TCP/IP protocol for your Firebird client/server network.! For information about using NetBEUI protocol in an all-Windows environment, refer to Chapter 6, Network Configuration in the Using Firebird manual.❖IPX/SX networks are not supported by FirebirdPinging the serverUsually, the first thing you will want to do once installation is complete is ping the server. This just gives you a reality check to ensure that your client machine is able to see the host machine in your network. For example, if your server’s IP address in the domain that is visible to your client is 192.13.14.1, go to a command shell and type the commandping 192.13.14.1substituting this example IP address for the IP address that your server is broadcasting.❖If you get a timeout message, study the Using Firebird manual—Chapter 6, Network Configuration, and Chapter 7, Troubleshooting Connections—for further instructions.Note that if you are connecting to the server from a local client—that is, a client running on the same machine as the server— you can ping the virtual TCP/IP loopback server:ping localhost —or— ping 127.0.0.1Checking that the Firebird server is runningAfter installation, Firebird server should be running as a service on Windows NT, 2000 or XP or on Linux. Windows NT4, 2000 and XPFor the Windows server platforms, start the Services applet on the Control Panel.Firebird Server and The GuardianThis illustration shows the Services applet display on Windows NT 4. The appearance may vary from one Windows server edition to another.The GuardianIf the Guardian is running (as shown in the screenshot, over) it may have a different service name because of version changes.✰On Windows 2000 and XP, the Guardian is a convenience rather than a necessity, since these two operating systems have the facility to watch and restart services. It is recommended that youkeep Guardian active for other platforms if a SYSDBA is not available to restart the servermanually in the event that it is stopped for some reason.Windows Control Panel appletEarlier distributions of Firebird for Windows kits installed the InterBase Manager applet into theControl Panel of operating systems that support services. It was omitted from Firebird 1.0 because a number of Firebird-specific ‘Firebird [Server] Manager’ implementations became available throughopen source channels. Whilst the applet is not essential, it does provide a convenient way to start and stop the service.If you want a Firebird Manager applet and youdo not find one installed in the Control Panel ofyour Windows server, download the Delphisource code from the addons branch of theFirebird CVS tree or a compiled version from.The Control Panel applet will be similar inappearance to the illustration.Windows 9x or MEOn Windows 9x or ME Firebird server should be running as an application, monitored by the Guardian. The Guardian’s icon should appear in the tray with a green graphic. If the icon is flashing or showing as a red graphic, it indicates that Guardian is either attempting to start the server or has failed.If you used an installation kit that installed but did not automatically start the Guardian and the Firebird server, you can set it up as follows:1Locate the executable file for the Guardian program (ibguard.exe) and create a shortcut for it in the Startup area of your machine’s Start Menu.2Open the Properties dialog of the shortcut and go to the field where the command line is.3Edit the command line so it reads as follows:ibguard.exe -a4Save and close the Properties dialog.5Double-click on the shortcut to start the Guardian. The Guardian will proceed to start ibserver.exe.The Guardian should start up automatically next time you boot your Windows 9x or ME machine.❖There is currently no Control Panel applet which will detect the Firebird server application running on these non-server Windows versions.Posix serversUse the top command in a command shell to inspect the running processes interactively. If Firebird is running, you should see one process named ibguard (this is Guardian), one main and zero or more child processes named ibserver or fbserver—which one depends on the distribution of Firebird which you have installed.The following screenshot shows the output of top, restricted by grep to show only processes with names starting with the characters ‘ib’, i.e.top -A | grep ibFirebird Quick Start Guide}Other things you need✰If your Firebird server uses the Classic architecture, the process name is gds_inet_server. There will be one instance of this process running for each connection. Use top -A | grep gds tolook at them.Other things you needA network address for the server• If you are on a managed network, get the server’s IP address from your system administrator• If you have a simple network of two machines linked by a crossover cable, you can set up your server with any IP address you like except 127.0.0.1 (which is reserved for a local loopback server) and, of course, the IP address which you are using for your client machine. If you know the “native” IPaddresses of your network cards, and they are different, you can simply use thoseFirebird Quick Start Guide}Other things you need • If you are intending to try out a single-machine installation of both client and server, you should use the local loopback server address—localhost, with the IP address 127.0.0.1NOTE On Windows, it is possible to connect locally to the server, without using a local TCP/IPloopback. This is not a TCP/IP connection and it is not a thread-safe way to connect to a localserver. For using single instances of the command-line tools (gsec, gbak, etc.) it works just fine. Default user name and passwordThe SYSDBA user has all privileges on the server. The installation program will install the SYSDBA user with the password masterkey.✰Actually, it is masterke, since all characters after the eighth one are ignored.If your server is exposed to the Internet at all, you should change this password immediately using the gsec command-line utility.How to change the SYSDBA passwordYou need to be logged into the operating system as Superuser (root on Linux) to run gsec. Let’s say you decide to change the SYSDBA password to icuryy4me1Go to a command shell on your server and change to the directory where the command-line utilities are located. Refer to Table 1 (above) to find this location.2Type the following (it is case-sensitive on all platforms except Windows):gsec -user sysdba -password masterkeyYou should now see the shell prompt for the gsec utility:GSEC>3Type this commandGSEC> modify sysdba -pw icuryy4me4Press ENTER. The new password icuryy4me is now encrypted and saved and masterkey is no longer valid.5 5. Now quit the gsec shell:GSEC> quit✰Because Firebird ignores all characters in a password past the eighth character, icuryy4m will work, as will icuryy4monkeys.An Admin toolThe Firebird kit does not come with a GUI admin tool. It does have a set of command-line tools, executable programs which are located in the ./bin directory of your Firebird installation.The range of excellent GUI tools available for use with a Windows client machine is too numerous to describe here. A few GUI tools written in Borland Kylix, for use on Linux client machines, are also in various stages of completion.Inspect the Downloads > Contributed > Admin Tools page at for all of the options.✰You can use a Windows client to access a Linux server and vice-versa.Connecting to the sample databaseIn the ./examples directory of your Firebird installation is a sample database named employee.gdb. You can use this database to “try your wings”.❖If you are running the server on Windows XP or ME, be sure to rename this test database to employee.fdb to get around the System Restore utility, which targets files with a .gdb extension.There is more information about this problem in the release notes.Server name and pathIf you move the sample database, be sure you move it to a hard disk that is physically attached to your server machine. Shares, mapped drives or (on Unix) mounted SMB (Samba) filesystems will not work. The same rule applies to any databases that you create.There are two elements to a TCP/IP connection string: the server name and the disk/filesystem path. Its format is as follows:For a Linux server: servername:/filesystem-path/database-fileExample on a Linux or other Posix server named serverxyz:serverxyz:/opt/interbase/examples/employee.gdbFor a Windows server:servername:D:\filesystem-path\database-fileserverxyz:C:\Program Files\Firebird\examples\employee.gdbThe CONNECT statementConnecting to a Firebird database always requires the user to “log in” using a user name and a valid password—widely referred to as a log-in or login. Any user other than SYSDBA or root (on Posix systems only) needs also to have permissions to objects inside a database. For simplicity here, we will look at logging in as SYSDBA using the password masterkey.Using isqlThere are several different ways to connect to a database using isql. One way is to start isql in its interactive shell:Go to the ./bin directory of your Firebird installation and, at that prompt, type the command isqlC:\Program Files\Firebird\bin>isql uUse CONNECT or CREATE DATABASE to specify a databaseSQL>CONNECT "C:\Program Files\Firebird\examples\Employee.gdb" user'SYSDBA' password 'masterkey'; u❖In isql, make sure that every statement ends with a semicolon. If you forget, the prompt will change from SQL>to CON> and you won’t be able to continue until you type in thesemicolon and press u again.❖Although single quote symbols are the “norm” for delimiting strings in Firebird, double quote symbols were used with the database path string in the above example. This is sometimesnecessary with some of the command-line utilities where the path string contains spaces. Singlequotes should work for paths that do not contain spaces.At this point, isql will inform you that you are connected:DATABASE "C:\Program Files\Firebird\examples\Employee.gdb", User: sysdba SQL>You can now continue to play about with the employee.gdb database. The characters isql stand for interactive SQL [utility]. You can use it for querying data, getting information about the metadata, creating database objects, running data definition scripts and much more.To get back to the command prompt typeSQL> QUIT;For more information about isql, see chapter 10, Interactive SQL Utility (isql) (p. 152 of Using Firebird). Using a GUI clientGUI client tools usually take charge of composing the CONNECT string for you, using server, path, user name and password information that you type into prompting fields. Use the elements as described in the preceding topic.✰• It is quite common for such tools to expect the entire server + path as a single string• Remember that file names and commands on Linux and other Posix command shells arecase-sensitiveFirebird Quick Start Guide}Creating a database using isqlCreating a database using isqlThere is more than one way to create a database using isql. Here, we will look at one simple way to create a database interactively—although, for your serious database definition work, you should create and maintain your metadata objects using data definition scripts. There is a complete chapter in the Using Firebird manual discussing this topic.Starting isqlTo create a database interactively using the isql command shell, you need to be working on the server. Get to a command prompt in Firebird’s ./bin directory and start isql as follows:C:\Program Files\Firebird\bin>isql uUse CONNECT or CREATE DATABASE to specify a databaseThe CREATE DATABASE statementNow, you can create your new database interactively. Let’s suppose that you want to create a database named test.fdb and store it a directory named “data” on your D drive:SQL> CREATE DATABASE 'D:\data\test.fdb' page_size 8192 user 'SYSDBA' password 'masterkey'; uThe database will be created and, after a few moments, the SQL prompt will reappear. You are now connected to the new database and can proceed to create some test objects in it.To verify that there really is a database there, type in this query:SQL> SELECT * FROM RDB$RELATIONS; uThe screen will fill up with a large amount of data! This query selects all of the rows in the system table where Firebird stores the metadata for tables. An “empty” database is not empty—it contains a database which will become populated with metadata as you begin creating objects in your database.To get back to the command prompt typeFirebird Quick Start Guide}Performing a client-only installSQL> QUIT;For more information about isql, see chapter 10, Interactive SQL Utility (isql) (p. 152 of Using Firebird). Performing a client-only installEach remote client machine needs to have the client library—libgds.so on Posix clients, gds32.dll on Windows clients—that matches the release version of the Firebird server.Firebird versions from 1.5 onward require an additional client library named libfb.so or fb32.dll which contains the full library. In these newer distributions, the “gds” named files are distributed to maintain compatibility with third-party products which need these files. Internally, the libraries will “jump” to the correct access points in the renamed libraries.Some extra pieces are also needed for the client-only install.WindowsAt the time of publication, no compact installation program was available to assist with installing the client pieces on a Windows client. If you are in the common situation of running Windows clients to a Linux or other Posix Firebird server, you need to download the full Windows installation kit that corresponds to the version of Firebird server you install on your Linux or other server machine.Fortunately, once you have the kit, the Windows client-only install is easy to do. Run the installation program, just as though you were going to install the server—but select the CLIENT ONLY option from the install menu. Linux and some other Posix clientsA small-footprint client install program for Linux clients is not available either. Additionally, some Posix flavors—even within the Linux constellation—have somewhat idosyncratic requirements for filesystem locations. For these reasons, not all *x distributions for Firebird even contain a client-only install option.For most Linux flavors, the following procedure is suggested for Firebird versions lower than 1.5. Log in as root for this.1Look for libgds.so.0 in /opt/interbase/lib on the server where Firebird server is installed. Copy it to /usr/lib on the client.2Create the symlink libgds.so for it, using the following command:ln -s /usr/lib/libgds.so.0 /usr/lib/libgds.so3Copy the interbase.msg file to /opt/interbase4In system-wide default shell profile, or using setenv() from a shell, create the INTERBASE environment variable and point it to /opt/interbase, to enable the API routines to locate the messages.Other things worth knowingThis chapter finishes with a small, eclectic collection of things other Firebird ‘newbies’ wished they had known about when they began.Firebird SQLEvery database management system has its own idiosyncrasies in the ways it implements SQL. Firebird adheres to the SQL standard more rigorously than any other RDBMS except possibly its “cousin”, InterBase®. Developers migrating from products that are less standards-compliant often wrongly suppose that Firebird is quirky, whereas many of its apparent quirks are not quirky at all.String delimiter symbolStrings in Firebird are delimited by a pair of single quote symbols—'I am a string'—(ASCII code 39 NOT 96). If you used earlierversions of Firebird’s relative, InterBase®, you might recall that double and single quotes were interchangeable as string delimiters. Double quotes cannot be used as string delimiters in Firebird.Double-quoted identifiersBefore the SQL-92 standard, it was not legal to have object names (identifiers) in a database that duplicated keywords in the language, were case-sensitive or contained spaces. SQL-92 introduced a single new standardto make any of them legal, provided that the identifiers were defined within pairs of double-quote symbols (ASCII 34) and were always referred to using double-quote delimiters.The purpose of this “gift” was to make it easier to migrate metadata from non-standard RDBMSs to standards-compliant ones. The down-side is that, if you choose to define an identifier in double quotes, its case-sensitivity and the enforced double-quoting will remain mandatory.Firebird does permit a slight relaxation under a very limited set of conditions: if the identifier which was defined in double-quotes 1) was defined as all upper-case, 2) is not a keyword and 3) does not contain any spaces, then it can be used in SQL unquoted as long as it is used in all upper-case.Unless you have a compelling reason to define quoted identifiers, it is usually recommended that you avoid them. Firebird happily accepts a mix of quoted and unquoted identifiers—so there is no problem including that keyword which you inherited from a legacy database, if you need to.❖Some database admin tools enforce double-quoting of ALL identifiers by default. Try to choose a tool which makes double-quoting optional.Apostrophes in stringsIf you need to use an apostrophe inside a Firebird string, you can “escape” the apostrophe character by preceding it with another apostrophe.For example, this string will give an error:'Joe's Emporium'because the parser encounters the apostrophe and interprets the string as ‘Joe’ followed by some unknown keywords.To make this a legal string, double the apostrophe character:'Joe''s Emporium'Notice that this is TWO single quotes, not one double-quote.Concatenation of stringsThe concatenation symbol in SQL is two ‘pipe’ symbols (ASCII 124, in a pair with no space between). In SQL, the ‘+’ symbol is an arithmetic operator and it will cause an error if you attempt to use it for concatenating strings. The following expression prefixes a character column value with the characters ‘Reported by:’:'Reported by: ' || LastNameTake care with concatenations. Be aware that Firebird will raise an error if your expression attempts to concatenate two or more char or varchar columns whose potential combined lengths would exceed the maximum length limit for a char or a varchar (32 Kb).See also the note below, Expressions involving NULL, about concatenating in expressions involving NULL.Division of an integer by an integerFirebird accords with the SQL standard by truncating the result (quotient) of an integer/integer calculation to the next lower integer. This can have bizarre results unless you are aware of it.For example, this calculation is correct in SQL:1 / 3 = 0If you are upgrading from a RDBMS which resolves integer/integer division to a float quotient, you will need to alter any affected expressions to use a float or scaled numeric type for either dividend, divisor, or both.For example, the calculation above could be modified thus in order to produce a non-zero result:1.000 / 3 = 0.333Expressions involving NULLIn SQL, NULL is not a value. It is a condition, or state, of a data item, in which its value is unknown. Because it is unknown, null cannot behave like a value. When you try to perform arithmetic on NULL, or involve it with values in other expressions, the result of the operation will always be NULL. It is not zero or blank or an “empty string” and it does not behave like any of these values.So—here are some examples of the types of surprises you will get if you try to perform calculations and comparisons with NULL:1 +2 +3 + NULL = NULLif (a = b) thenMyVariable = 'Equal'elseMyVariable = 'Not equal';will return ‘Not equal’ if both a and b are null.if (a <> b) thenMyVariable = 'Not equal'elseMyVariable = 'Equal';will also return ‘Not equal’ if both a and b are null.FirstName ||' ' || LastNamewill return NULL if either FirstName or LastName is NULL.BackupFirebird comes with its own utility for backing up and restoring your databases. Its name is gbak and it can be found in the ./bin directory of your Firebird installation. Firebird databases can be backed up whilst users are connected to the system and going about their normal work. The backup will be taken from a snapshot of the database state at the time the backup began.Regular backups and occasional restores using gbak should be a scheduled part of your database management activity.❖Do not use external proprietary backup utilities or file-copying tools such as WinZip, tar, copy, xcopy, etc., on a database which is running. Not only will the backup be unreliable, but thedisk-level blocking used by these tools can corrupt a running database."Study the warnings in the next section about database activity during restores!。
常用嵌入式数据库概览

Berkeley DB概述Berkeley DB是由美国Sleepycat Software公司开发的一套开放源码的嵌入式数据库的程序库(database library),它为应用程序提供可伸缩的、高性能的、有事务保护功能的数据管理服务。
Berkeley DB为数据的存取和管理提供了一组简洁的函数调用API接口。
它是一个经典的C-library模式的toolkit,为程序员提供广泛丰富的函数集,是为应用程序开发者提供工业级强度的数据库服务而设计的。
其主要特点如下:嵌入式(Embedded):它直接链接到应用程序中,与应用程序运行于同样的地址空间中,因此,无论是在网络上不同计算机之间还是在同一台计算机的不同进程之间,数据库操作并不要求进程间通讯。
Berkeley DB为多种编程语言提供了API接口,其中包括C、C++、Java、Perl、Tcl、Python 和PHP,所有的数据库操作都在程序库内部发生。
多个进程,或者同一进程的多个线程可同时使用数据库,有如各自单独使用,底层的服务如加锁、事务日志、共享缓冲区管理、内存管理等等都由程序库透明地执行。
轻便灵活(Portable):它可以运行于几乎所有的UNIX和Linux系统及其变种系统、Windows 操作系统以及多种嵌入式实时操作系统之下。
它在32位和64位系统上均可运行,已经被好多高端的因特网服务器、台式机、掌上电脑、机顶盒、网络交换机以及其他一些应用领域所采用。
一旦Berkeley DB被链接到应用程序中,终端用户一般根本感觉不到有一个数据库系统存在。
可伸缩(Scalable):这一点表现在很多方面。
Database library本身是很精简的(少于300KB的文本空间),但它能够管理规模高达256TB的数据库。
它支持高并发度,成千上万个用户可同时操纵同一个数据库。
Berkeley DB能以足够小的空间占用量运行于有严格约束的嵌入式系统,也可以在高端服务器上耗用若干GB的内存和若干TB的磁盘空间。
用firebird自带的工具的管理数据库
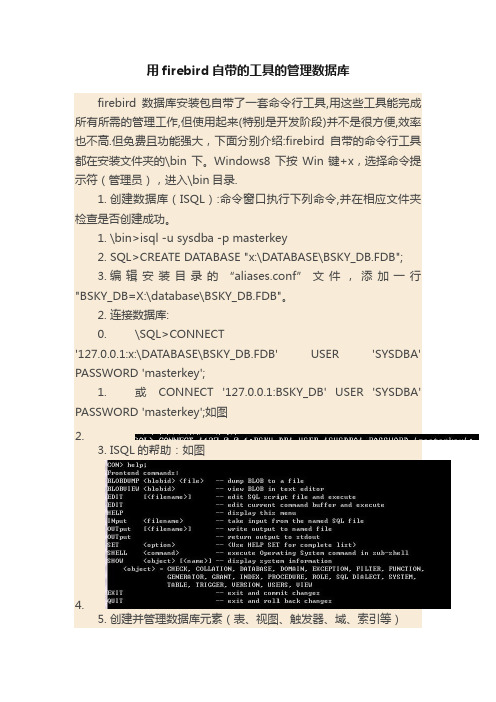
用firebird自带的工具的管理数据库firebird数据库安装包自带了一套命令行工具,用这些工具能完成所有所需的管理工作,但使用起来(特别是开发阶段)并不是很方便,效率也不高.但免费且功能强大,下面分别介绍:firebird自带的命令行工具都在安装文件夹的\bin下。
Windows8下按Win键+x,选择命令提示符(管理员),进入\bin目录.1.创建数据库(ISQL):命令窗口执行下列命令,并在相应文件夹检查是否创建成功。
1.\bin>isql -u sysdba -p masterkey2.SQL>CREATE DATABASE "x:\DATABASE\BSKY_DB.FDB";3.编辑安装目录的“aliases.conf”文件,添加一行"BSKY_DB=X:\database\BSKY_DB.FDB"。
2.连接数据库:0.\SQL>CONNECT'127.0.0.1:x:\DATABASE\BSKY_DB.FDB' USER 'SYSDBA' PASSWORD 'masterkey';1.或CONNECT '127.0.0.1:BSKY_DB' USER 'SYSDBA' PASSWORD 'masterkey';如图2.3.ISQL的帮助:如图4.5.创建并管理数据库元素(表、视图、触发器、域、索引等)0.域:其实就是自己重新定义的数据类型,好处是容易阅读和统一修改。
例:1.SQL>CREATE DOMAIN EMAIL_ADDRESS AS2.CON>VARCHAR(255) CHARACTER SET NONE3.COLLATE NONE;4.CREATE DOMAIN KEY_ID AS INTEGER NOT NULL;5.CREATE DOMAIN KEY_NAME AS VARCHAR(40) CHARACTER SET NONE COLLATE NONE;6.SQL>CREATE DOMAIN NORM_BLOB AS BLOB SUB_TYPE 0 SEGMENT SIZE 80;7.显示域:8.SQL>SHOW DOMAINS;9.EMAIL_ADDRESS KEY_ID10.KEY_NAME NORM_BLOB1.表:用域来创建表比直接用原始数据类型方便以后管理。
firedac 开发手册 中文

firedac 开发手册中文摘要:1.引言2.Firedac 简介3.Firedac 的特点4.Firedac 的安装与配置5.Firedac 的基本使用方法6.Firedac 的高级功能7.Firedac 的应用案例8.Firedac 的常见问题及解决方案9.总结正文:【引言】Firedac 是一款非常强大的数据访问组件,它可以帮助开发者快速高效地访问各种数据库。
无论是在桌面应用、Web 应用还是移动应用中,Firedac 都能提供稳定可靠的数据访问服务。
本文将对Firedac 进行详细介绍,包括其特点、安装与配置、基本使用方法和高级功能等。
【Firedac 简介】Firedac(Firebird Data Access Component)是一个用于访问Firebird 数据库的 .NET 数据访问组件。
它基于Firebird 数据库引擎,提供了丰富的功能,允许开发者轻松地创建、编辑、查询和删除数据库中的数据。
Firedac支持多种编程语言,如C#、、Delphi 和Python 等。
【Firedac 的特点】1.高度可定制的界面2.支持多种数据库类型3.强大的数据处理能力4.易于集成到现有项目中5.跨平台支持【Firedac 的安装与配置】1.下载Firedac 安装包2.安装Firedac3.配置Firedac,包括设置数据源、连接字符串等【Firedac 的基本使用方法】1.创建数据库连接2.创建数据表对象3.添加、修改、删除和查询数据4.数据验证与数据处理【Firedac 的高级功能】1.数据分页2.数据排序3.数据过滤4.数据导入与导出5.事务处理【Firedac 的应用案例】1.桌面应用:使用Firedac 访问数据库,实现员工信息管理2.Web 应用:使用Firedac 实现在线订单管理3.移动应用:使用Firedac 实现用户数据统计与分析【Firedac 的常见问题及解决方案】1.无法连接到数据库2.数据处理错误3.性能问题【总结】Firedac 是一款功能强大的数据访问组件,它可以帮助开发者快速高效地访问各种数据库。
firebird与flamerobin使用教程

firebird与flamerobin使用教程一、下载相关软件1.1 下载firebird:到其主页下载:/,下载最新版本的,并且是win32平台下的。
1.2 下载flamerobin:到其主页下载:,下载windows平台上的版本。
二、安装软件1、安装firebird,双击下载的软件,一直点”next”安装就行,最后一步,选择运行firebird。
2、安装flamerobin,双击下载的软件,一直点”next”安装就行,最后一步,选择运行flamerobin。
三、使用flamerobin3.1打开flamerobin,其初始界面如图表1所示。
图表 13.2新建数据库1)在“Localhost”上击鼠标右键,选择“Create a new database”。
弹出“CreateNew Database”对话框,如图表 2所示。
图表 22)点击”Database path”右边的按钮,弹出“Select database file”对话框,选择好路径,输入用户名。
如我选择的是:f:\student.fdb。
firebird默认的DBA的名称为:SYSDBA,密码:masterkey。
输入之后如图表 3所按钮创建数据库。
示。
最后单击“Create”3)创建好的数据库如所图表4所示。
图表 43.3注册已有的数据库1)保证有一个已经创建好的数据库,如在E盘上有一个student.fdb数据库。
2)在localhost上右击鼠标,如下图所示。
3)选择”Register existing database....”,打开如下图所示的窗口。
点这里选择数据库点击“Database path”右边的按钮,打开一个窗口选择数据库,输入用户服务名:SYSDBA,密码:masterkey。
选择“Save”按钮。
注册好的数据库如下图所示。
3.4连接数据库双击数据库名,就可以连接数据。
连接成功后如图表5所示。
图表 53.5创建表4)在”Tables”上击右键,选择“Create new…”,弹出如图6所示的创建表的窗口图表 65)输入创建表的sql语句,如图表7所示。
FireBird数据库在企业小型应用系统开发中的优势

库 It ra e 同 出 一 源 , “ 费 、 源 、 平 台 ” 据 库 。 Fr neb s 是 免 开 跨 数 i e
格 式 完 全 相 同 , 用 修 改 。一 个 Fr br 不 i i e d数 据 库 服 务 器 能 够 管
理 多 个 独 立 数据 库 , 一 数据 库 同 时 可支 持 多个 客 户 端 。硬 件 每 需 求 低 , 既可 在 最 常见 硬 件 环 境 ,也 可 在 较 差 的 硬 件 环 境 工 作 , 件 要 求仅 取 决 于 用 户 数 量 。该 数 据库 可 分成 多个 物 理 文 硬
件 , 个 文 件 大 小 依 赖 于 操 作 系 统 限 制 , 支 持 多 变体 系 结 构 每 还
( GA ) M 。
Bi r d数 据 库 在 开 发 小型 系统 中 独 具 优 势 ,对 于 企 业 级 单 机 和 实时 处 理 应 用 系统 , 功 能 并 不 比 大 型 商 业 数 据 库 差 , 有 自 其 并 己 的特 点 。 本 文通 过 介 绍 我 公 司 考 勤 系 统 Fr r i Bi e d数 据 库 的 实际 应 用 ,说 明 了该 数 据 库 在 企 业 /、 应 用 系统 开 发 中 的优 J型
r
斟学 坝察 1
L2 0 0 8芷簟 5期 J
赵艳 霞
( 天津东方海陆集装箱码头有 限公 司 天津 305 ) 0 4 6
Firebird(火鸟)数据库v3.0.3.32900官方版

Firebird(⽕鸟)数据库v3.0.3.32900官⽅版firebird数据库是由Borland公司研发的⼀款跨平台关系型数据库系统,它基于开源的Interbase6.0,拥有数据视图、触发器、事物处理以及存储过程等⼤型关系数据库的所有特性,在稳定性和兼容性上也有良好的扎实基础,在⽂件的⼤⼩上也只有简单的⼗⼏兆,且⾼度可定制,客户端的分发也很简单,只需要⼀个dll应⽤程序扩展⽂件,既能作为多⽤户环境下的数据库服务器运⾏,也提供嵌⼊式数据库的实现,由单数据库升级到企业级的应⽤过程中为中⼩型企业在数据库的管理上提供了⼀个易于使⽤的⼯具。
⽽firebird管理⼯具其实就是针对这款软件系统进⾏图形化管理的⼯具,Firebird数据库⾃⾝拥有⼀套⾃带的命令⾏⼯具,即使不通过图形化管理⼯具的使⽤也能完成对数据的管理功能,同时⼀个数据库服务器能够管理多个独⽴的数据库,每⼀个数据库可⽀持多个客户端连结,能够提供⼤部分SQL-99的标准功能,深受⼴⼤⽤户的喜爱与青睐。
本站为您提供下载,有需要的⽤户可以在本站下载!注:下载包中有Firebird数据库安装包以及数据库使⽤说明,安装包在未使⽤时请⽤户不要轻易删除以及更改⽂件类型。
安装教程1、在本站下载好压缩包,将⽂件解压,双击运⾏“Firebird-3.0.2.32703_0_x64.exe”程序,弹出语⾔选择框,选择“English”英语语⾔种类,点击“ok”开始安装;⼩提⽰:下载包中32位和64位不同安装版本的firebird数据库,⽤户可以根据⾃⼰操作系统的位数⾃定义安装对应位数的数据库版本;Firebird(⽕鸟)数据库 v3.0.3.32900官⽅版⼤⼩:16MB语⾔:简体中⽂类别:数据库类类型:国产软件授权:免费软件时间:2019/7/14官⽹:环境:Windows10, Windows8, Windows7, WinVista, Win2003, WinXP, Win2000安全检测:⽆插件360通过腾讯通过⾦⼭通过瑞星通过89% 11%8.9分本地下载⾼速下载需优先下载⾼速下载器,提速50%相关软件firebird数据库是由Borland公司研发的⼀款跨平台关系型数据库系统,它基于开源的Interbase6.0,拥有数据视图、触发器、事物处理以及存储过程等⼤型关系数据库的所有特性,在稳定性和兼容性上也有良好的扎实基础,在⽂件的⼤⼩上也只有简单的⼗⼏兆,且⾼度可定制,客户端的分发也很简单,只需要⼀个dll应⽤程序扩展⽂件,既能作为多⽤户环境下的数据库服务器运⾏,也提供嵌⼊式数据库的实现,由单数据库升级到企业级的应⽤过程中为中⼩型企业在数据库的管理上提供了⼀个易于使⽤的⼯具。
几个小型数据库的比较

几个小型数据库的比较Access,MSDE 2000,Embedded Firebird,SQLite等都是可以免费再分发(free redistributable)的数据库。
相比而言,MSDE 2000 显著缺点是需要安装,最大优点是和服务器端的SQL Server 编程模型一致,开发便利。
Access的显著缺点是功能较少,不支持事务等常用功能,最大优点是简单、多数开发者都很熟悉,部署也很方便。
SQLite支持事务,也是一款单文件数据库,比较不足的是 .NET Data Provider 还不是很成熟。
Firebird则同时具有:单文件、部署简单不需安装(只需XCOPY 两个文件)、支持事务、存储过程、触发器,.NET Data Provider比较稳定成熟等优点。
这个星球上的数据库实在不胜枚举,这里只列一些我接触过的常见的。
可以稍微夸张点说,有交互的应用,起码得用一下数据保存,即便是自定义结构的数据保存,还是最常见的INI、XML等,都可以算是“数据库”,真正点的,如DBase系列、FoxBase、FoxPro、MSAccess、InterBase、MS SQL Server、Oracle、DB2等,这些是商业化的数据库,前面几个只能算是数据库,后面几个是RMDBS(关系型数据库管理系统)。
对应商业化的,有开源的:SQLite、SimpleSQL、Berkely DB、Minosse、Firebird( 前身是是Borland公司的InterBase)、PostgreSQL、MySQL 等。
□SQLite:大家可以看我的SQLite系列随笔,C编写的,可以跨操作平台,支持大部分ANSI SQL 92,它是嵌入式的轻量级关系形数据库引擎,只需要一个DLL,体积为250k,数据库也只是一个文件,零配置,便可工作。
既然开源,你甚至可以把它嵌入你的程序中。
核心开发人员只有一个,最近加入了另外一个,也就是2个人而已,实在佩服,目前发展到3.1.0,相当高效稳定,有开源驱动在上有其 Data Provider for SQLite :https:///projects/adodotnetsqlite/。
第8章 Delphi数据库及SQL基础

第8章数据及SQL基础8.1简介Firebird特性介绍Firebird是一个全功能的,强大高效的,轻量级,免维护的数据库。
它很容易让您从单用户,单数据库升级到企业级的应用。
给中小型企业提供了一个很好的工具,一些需要小的数据库的软件!8.1.1数据库特点1.Firebird是一个真正的关系数据库,支持存储过程、视图、触发器、事务等大型关系数据库的所有特性;2.Firebird支持SQL92的绝大部分命令,并且支持大部分SQL99命令,新版Firebird 2.0对SQL99的支持更完整;3.Firebird源码基于成熟的商业数据库InterBase,有良好的稳定性,与InterBase有良好的兼容性;4.不用考虑授权费用(免费),不用当心将来有一天你或你的客户因为使用盗版而被数据库开发商告上法庭;5.发布简易,安装文件只有几M,且高度可定制,客户端的分发也很简单,只需一个DLL文件;6.Firebird的嵌入式服务器版本,不用安装,直接运行,基于单机开发首选;7.Firebird的运行效率非常高;8.具备高度可移植性,可在Linux,Unix,MacOS,Windows,Solaris系统下运行,而且数据库格式完全一样,不用修改;9.开发环境支持良好,Delphi,C++Builder不用通过ODBC连接,直接用原生开发接口开发基于Firebird的程序。
8.1.2数据库功能1.Domains 域2.TABLES 表3.VIEWS 视图4.TRIGGERS 触发器5.EXCEPTIONS 异常6.PROCEDURES 存储过程7.GENERATORS 生成子8.INDICES 索引Domains 域作用:域对象可以帮助我们在基本数据类型的基础上扩展很多有用的数据类型。
1、逻辑数据类型boolean(取值范围0或1)有两种方法实现布尔逻辑类型。
方法之一:使用整数0和1代表逻辑真和假。
create domain boolean as smallint default 0 check(value in (0,1));方法之二:使用字符'0'和'1'代表逻辑真和假。
5款主流开源数据库的比较

5款主流开源数据库的⽐较开源数据库使得信息处理的成本降低,强有⼒的数据库解决⽅案进⼊更多的企业,特别是中⼩型企业。
同时,随着开源数据库在功能上的⽇益强⼤和完善,以及⼈们对其了解的深⼊,开源数据库在中⼩型企业中将会有更⼴泛地应⽤。
下⾯,笔者为⼤家介绍5款主流开源数据库软件,也许它正是你正在使⽤的,也许是你关注的,在这⾥,你可以了详细了解它们的技术优势。
1、MySQL 作为当今最流⾏的开源数据库之⼀,MySQL数据库为⽤户提供了⼀个相对简单的解决⽅案,适⽤于⼴泛的应⽤程序部署,能够降低⽤户的TCO。
MySQL是⼀个多线程、结构化查询语⾔(SQL)数据库服务器。
MySQL的执⾏性能⾼,运⾏速度快,容易使⽤。
MySQL包括以下⼏个关键优势: ◆可靠的性能和服务MySQL向公众提供所有数据库服务器软件的早期版本,都是利⽤开放源码进⾏为期⼏个⽉的测试之后才发布作为⽣产之⽤。
◆易于使⽤和部署MySQL的结构体系易于定制,运⾏速度快,其独特的多存储引擎结构为企业客户提供了灵活性,为数据库管理系统带来紧致性和稳定性,易于部署。
◆⾃由获得源码可以随时访问MySQL源代码,其策略确保了⾃由性,避免锁定某家公司或平台。
◆跨平台⽀持MySQL可⽤于20多种不同平台,包括主要的Linux系统、Mac OS X、Unix和Windows ◆可信赖的开发⼒量MySQL拥有⼤量的⽤户基础,也拥有⾼素质、有经验的开发团队。
◆满⾜企业需求MySQL结构体系简单易⽤,运⾏速度极快,能够处理企业数据库绝⼤多数的应⽤需求。
2008年12⽉8⽇,Sun Microsystems公司宣布,正式对外提供MySQL 5.1软件 —— 这是全球最受欢迎的开源数据库MySQL的⼀个极其重要的新版本。
MySQL 5.1 GA版现通过以下三种模式提供,以满⾜不同⽤户的各种特殊需求: ◆MySQL Community Server —— Sun的MySQL 数据库的免费开源版。
firebird

FireBird是一种小巧的关系型数据库,它有多种版本,包括服务器版(象MySQL),单机版(象Access)以及嵌入式(象SQLite)。
而且不管是服务器版还是嵌入式版它都完整支持视图、触发器、存储过程等SQL高级特性。
问题是它提供的C API“不太友好”,不容易掌握(特别是我),所以我一直只会在C++Builder 里编程使用FireBird(因为FireBird源于Borland的InterBase,VCL库自带了InterBase的组件),直到有一天我发现了IBPP...IBPP是一个FireBird/Interbase数据库API的C++包装,使用起来也比较简单,只要把IBPP源码目录里的"core/all_in_one.cpp"加入工程,在代码中包含头文件"ibpp.h",最后根据操作系统预定义一个IBPP_WINDOWS或IBPP_UNIX的宏即可。
另外,当然还要安装FireBird客户端,如果只是学习,我们可以下载嵌入式版本。
IBPP首先要找到FireBird的动态库,在Windows下,IBPP在下面的路径中查找:∙在程序目录下查找fbembed.dll∙在程序目录下查找fbclient.dll∙依据DefaultInstance注册表键值查找fbclient.dll∙在系统定义位置查找fbclient.dll∙在系统定义位置查找gds32.dllFireBird主页:IBPP主页:关于FireBird的中文教程我推荐姚启红编著的《Borland InterBase7.0 应用开发指南》(网上一找一大堆)。
例一,基本应用1.#include <iostream>2.#include <ibpp.h>ing namespace std;4.5.//数据库名,根据你的情况更改。
6.const char* g_szDBName = "d:\\test.fdb";7.//服务器名,针对服务器版本。
FireBird数据库使用指南

FireBird数据库使用指南一、FireBird数据库简介Firebird是一个跨平台的关系数据库系统,目前能够运行在Windows、linux和各种Unix 操作系统上,提供了大部分SQL-99标准的功能。
它既能作为多用户环境下的数据库服务器运行,也提供嵌入式数据库的实现。
Firebird提供良好的并发性,高效的执行,强大的语言支持存储过程和触发器。
从1981年起,它已经被许多商业公司运用于许多的产品系统中。
Firebird脱胎于Borland公司的开源版数据库Interbase6.0,是一个完全非商业化的产品,用C和C++开发。
由于与interbase的血缘关系,大部分interbase的开发工具可以直接应用到Firebird开发中。
Firebird和原Borland的InterBase有着相同的血脉,其作为一个开源项目在2000年7月25日前遵循InterBase Public License V.1.0协议。
Firebird 使用Mozilla Public License v.1.1许可证发行。
Firebird特性介绍:firebird是一个全功能的,强大高效的,轻量级,免维护的数据库。
它很容易让您从单用户,单数据库升级到企业级的应用。
一个firebird数据库服务器能够管理多个独立的数据库,每一个数据库同时可支持多个客户端连结。
总之:它是一个开源的,强大在,可以自由使用的数据库(即使是商业上的使用)关键特性:支持原子性,并发性,隔离性等概念。
MGA:支持事务的多个版本功能,存储过程:使用PSQL(Procedure SQL),你可以创建强大的存储过程来处理服务上的所有数据,你可以使用select Stored Procedure的形式,使用存储过程,以得到一个虚拟的表结构的结果。
这样的话,你就可以很容易的在报表中使用它。
事件:存储过程和触发器可以引发事件,这个事件可以被客户端程序监听到生成子:生成子也称为序列,它可以很容易的实现自动增加的字段。
Firebird-File-Metadata-Security

Firebird File and Metadata SecurityGeoff Worboys7 December 2005 – Document version 0.5Table of ContentsIntroduction (3)Background (3)The Problem (4)The Solution (5)Difficulties (5)Protecting User Data (5)Embedded Firebird Server (8)Other Forms of Obscurity (9)Acceptable Low Security (9)Choosing Obscurity (9)The Philosophical Argument (10)Conclusions (10)Acknowledgements (10)Appendix A: Document History (11)Appendix B: Use of This Document (12)IntroductionIf you stumble on this page and don't know about Firebird, see this link: This article discusses the security of Firebird database files and in particular access to the metadata stored in those files. It has been written in response to frequent questions on the Firebird lists concerning these issues. The article avoids technical specifics. To discover how to secure files in your particular operating system refer to relevant documentation for that operating system, to discover how to apply user and object security in Firebird databases refer to documentation available from the Firebird website (noted above) or buy The Firebird Book by Helen Borrie.BackgroundFor an application (user) to access a Firebird database it must connect to the Firebird server process. On receiving a connect request the server process will authenticate the user credentials against the server users defined in the security database. If authentication is successful the server will allow the application access to any database that it requests and then use the roles and privileges defined in that database to provide fine grained access control to objects in that database.At no time does the user connecting to the database require direct access to the database file itself. All access goes through the server process, which accesses the database file as needed to fulfil requests. It is the server that restricts or allows access to the logged-in user, according to the permissions defined for that user in that database.Every Firebird server installation has a “SYSDBA” user, this user has unrestricted access to any database avail-able to that server. Database specific privileges are effectively ignored when the database is accessed using SYSDBA. When you first copy a database onto a server you can use SYSDBA to customise the privileges according to the users and requirements of the server. However it also means that, if I have direct access to a database file, I can copy that file from a server where I may not know the SYSDBA password onto a different server where I do know the SYSDBA password and so gain unrestricted access to the database.As you can see from this description, Firebird security is predicated on the assumption that the Firebird server process will be running in an adequately secure environment. Firebird itself takes no precautions to provide external security. Once a person has physical access to a database file there is no effective way to prevent that user from reading all data (and metadata) within that file.This means that, for reasonable security, installations should ensure that the database files are adequately secured. In most cases this means that the Firebird server process should run as its own specific operating system user and only that user (and probably the administrator/root user) should have direct operating system access to the database files. The database files should not be located in directories that are accessible from the network, or by any local users other than specifically authorised personnel.For the security to be effective it is also preferred that the server computer is stored in a secure location to prevent physical tampering that could permit unauthorised users to access the hard disk from beyond the strictures of the operating system.However, the above explanation does not necessarily help developers who, having written databases for distri-bution and installation to remote sites, may wish to protect the intellectual property carried in their databases. Such concerns may include specifically the metadata (table structures and relationships, stored procedures and triggers) but may also include specific data carried in some tables. These concerns represent the main purpose of this article.The ProblemA developer creates a database (and usually an accompanying client application) for installation on servers at remote sites. At such sites it is usual for a person at that site to have full access to the computer on which the Firebird server is running – in order to be able to perform backups and other maintenance tasks. As described in the background information, direct access to the database file provides the ability to gain full and unrestricted access to all the information in the database – both data and metadata.In such cases the developer may not trust the users at these remote sites to keep the intellectual property repre-sented by the database confidential. The fear may be that the users will reverse-engineer the database for their own purposes, or that these remote sites will fail to maintain the security necessary to prevent unauthorised access to the database.This leads to the common questions on the Firebird lists along the lines of:“I want to—”“—protect my database design (table structures, stored procedures, triggers etc.) from all users of the database at a remote installation. How can I do this with Firebird?”“I want to—”“—stop any users at a remote installation from accessing these particular tables of data. They contain pro-prietary information used internally by the application.”Firebird (at least to v1.5) provides no built-in encryption facilities. The simple answer to both of these questions is that it cannot be done using the current capabilities of Firebird. A user who can get direct access to the file gains access to all details within that file.In the first instance no workaround is feasible because the server itself must be able to read the metadata. In the second instance it may be possible to implement client side encryption/decryption features, but then you will lose the ability to make effective use of database indexes and search facilities – and key management remains a major problem (more below).The SolutionThere is really only one possible solution to these requests: Host the database and server at your own site and let the clients connect to your server remotely, through dial-up or Internet facilities etc. Terminal server (Windows or Linux/Unix) capabilities could be a useful way to implement such requirements.In this way you maintain control over the database file and can restrict access to the various features and struc-tures of your database using the usual Firebird internal security features (roles and privileges, etc.). DifficultiesIt is worth pointing out that there are difficulties even in this situation, if your intention is to protect the structure of your database.Needs of the Access LayerVarious database development libraries interrogate metadata, such as primary key, domain and similar structural information, in order to make development of client applications easier. Consequently, you may discover that you cannot prevent users from accessing metadata without also preventing your application from gathering the information that it requires.This may mean that you will need to choose between allowing metadata details to escape from your server via a sophisticated data access interface and spending the considerable extra time it takes to develop an application using a less sophisticated access library.“Leaking” by Inference and DeductionThere is also the issue that most client applications inherently “leak” structural information about the database with which they interact. It is very rare for a database-centric application to have an interface that does not reveal many details about the table structures that it uses.Some details may be hidden behind views and selectable stored procedures, but defining such features purely to try and hide structural information is an exercise in frustration. It is probably futile, anyway, since some details will escape, whatever you try.Protecting User DataBefore continuing with other discussions relating to encryption of Firebird data, I do want to highlight that it is possible for users to protect their databases with encryption. This does not help developers who want to hide information from legitimate users, but it may help to meet the requirements of customers wanting to increase the security of their databases.In some office situations it may not be practicable to locate the Firebird server computer in a truly secure envi-ronment. During times when the office is attended the likelihood that anyone will be able to access the computerto copy the database files (or steal the computer or hard disk to get the files later) may be quite low. However out of normal working hours (nights and weekends) it may be a different matter. Someone could gain access to the office, take the hard disk out of your computer (or take the entire computer) and take it away to access the database.EncryptionWhile Firebird itself provides no built-in encryption features there are some excellent products that do. You could install software that creates an encrypted volume on your computer and locate the database file (and any other confidential data) on that volume. When the computer is shut down all data exists in an encrypted file and cannot be accessed without the key. When you start the computer you have to mount the encrypted volume and supply the secret key before the data can be accessed. This additional, and necessarily manual, step in the start up process may be inconvenient but it can provide excellent security for unattended computer systems. Software with these capabilities includes: TrueCrypt (), Bestcrypt from Jetico (www.jetico. com) and PGPDisk (/products/pgpdisk/ – note that this link goes to an old freeware version, that site has links to newer commercial versions of the product). There are others but the last two are ones that I have used myself.Why doesn't Firebird provide encryption?Because of the needs described above it is common for users to request that Firebird should, in a future version, add the ability to encrypt metadata, selected user data, or even the entire database. Not being a Firebird core developer, I cannot say categorically that it will not happen. However, the issue is not really whether encryption is practicable or useful, but a matter of whether key management would provide a solution to the problems we are examining.Encryption can only be as good as the secret key required for decryption. It can be worse but it cannot be better. There are several excellent encryption algorithms available that could be used. When good encryption is used, attacks are likely to be against the key rather than against the encryption itself.How could encryption work?So let's look at how things would work if Firebird were to encrypt the metadata in a database...Before the database could be accessed the secret key would need to be supplied. Giving the decryption key to the user would be pointless, simply bringing us back to the original problem. So, presumably, whenever the customer restarts the server they would call the developer who would then dial in and enter the needed key. Even if this were practicable, it is not necessarily going to solve the problem. For example; the customer could install some monitoring software on their server to detect the key as it is entered.There are hardware based solutions to provide a key to a decryption process. But again this would need to be in possession of the client, and if we don't trust the client we cant stop them from using it to gain access to the database from another server where the SYSDBA password is known.Firebird is an open source product. If the encryption facilities were built in, or open source plug-in libraries were used, it would be feasible for users to build their own versions of the server or plug-in that not only performed the necessary encryption and decryption to access the protected database but also output the key, or simply output the decrypted details directly. The developer, not being in control of the server, can neither detect nor prevent such activity.You might consider building your own version of the Firebird server with the decryption key hidden in the executable. However, decompilers are available. It would not take long to discover the key simply by comparing the decompiled versions of your custom Firebird build with the normal, unencrypted version.Various database products do exist which purport to provide strong encryption. Perhaps the encryption is strong but, unless the key management is in place to support this feature, the encryption is not going to achieve the desired effect. It may encourage you to believe you are protected, but you need to study the key management to discover if this is really true.The painful truth is that, once you lose control of the hardware on which the encryption and decryption takes place, all bets are off. If the decryption key cannot be kept reliably secure then even good encryption becomes little more than security by obscurity.Limiting the distribution of dataSome people request encryption of the database data so that they can try and limit the dissemination of data. They are happy for the particular authorised user to see the data, but they wish to limit that user's ability to distribute the data to other people.Just imagine for a moment that all the key management problems described above have been solved, so that it has become impractical for the user to just copy the database. In such cases the user would simply write a small program that extracted the data they were interested in (from the legitimately installed server) and copied that data to its own file or database.I guess it is possible that Firebird might provide some form of application authentication system in the future that may make it possible to limit this form of data extraction, however most of the same problems exist. If you do not control the server you cannot prevent the user from installing a version of the server that does not require the authentication.Removing SYSDBA accessAt various times people have suggested that removing SYSDBA access to a database could be the solution. The idea behind it is that, when the database is moved to a new server where the SYSDBA password is known, it will not help the person because SYSDBA does not have access anyway. Some have reported limited success in this respect by creating an SQL role name of SYSDBA and making sure it does not have access to the database objects.However it does not really solve the problem. The database file can be viewed with a hex viewer or similar utility and the list of available user names discovered. (Discovering the owners of the database objects would be particularly useful.) Once known, these names can be added to the new server and used directly.An even simpler workaround might be to use the embedded version of Firebird server (see below) or to compile your own version of the Firebird server that ignores security constraints.Custom names for SYSDBAThere has been some suggestion about allowing the SYSDBA user name to be changed. This may offer some limited protection against brute-force network attacks against the SYSDBA password, since such attacks would need to guess both the user name and its password, but it does not help protect the system from a person with direct access to the database file.Deleting stored procedure and trigger source codeWhen you write and define a stored procedure or trigger for a Firebird database, the server stores an almost complete copy of the procedure source code along with a “compiled” copy referred to as BLR (Binary Language Representation). It is the BLR that is executed by the server, the source code is not used.Some developers attempt to protect at least some of their database metadata by deleting the source code from the database before distributing the database (a simple direct update against the relevant metadata table fields).I recommend that you don't do this for two reasons...1.BLR is a fairly simplistic encoding of the source code. It would not be difficult to decode the BLR backto a human readable form. Such a decoding would be without comments and formatting, but the SQL that goes into a stored procedure or trigger is rarely so complicated that this would cause much of a problem.Hence the protection offered by the removal of source code is not very significant.2.The source code can be useful for other purposes. It allows fixes to be applied directly to the databasewithout needing to bring in the full source from elsewhere (and then remembering to remove it again when the fix is applied). The source code is also used by various utilities, such as my own DBak application – an alternative backup program to “gbak”. I have not bothered to write my own BLR decoder at this stage, so DBak relies on the availability of the source code in order to be able to build a DDL script to reconstructa database.Embedded Firebird ServerThere is a special version of the Firebird server referred to as “embedded”. This is a special client library that includes the server itself. When an application links to this library it loads the server and allows direct access to any database that is accessible on the local computer. This version of the server does not use a security database. The user name specified during the “logon” (no password authentication occurs) is used to manage user access to database objects (via SQL permissions) but if that user name is SYSDBA (or the owner of the database) then unrestricted access is possible.The features of embedded are useful for developers wanting to create easy to distribute single-user applications that do not need security.From that brief description it appears that having an embedded server client installed on a server hosting other databases could present itself as a major security risk. In reality the risk is no greater than if the embedded client did not exist.When an application loads the embedded server, the server operates in the application (and therefore the user's) security context. This means that the embedded server will only be able to access database files that the user could access directly through the operating system. Giving an untrusted user access to install programs on a secure server is bad news in any case, but provided you have specified appropriate file permissions on secure databases, the embedded server itself is no threat.The threat comes from all the other things that the user could install.The fact that the embedded server exists only serves to highlight what is possible given direct access to a database file, especially in an open source environment. If it did not already exist then it would certainly be possible for someone to compile an equivalent capability.Other Forms of ObscurityVarious other forms of security by obscurity have been proposed. Such things as special events that fire on login and log off to call user functions to prevent or deny access. Such features may offer some limited use for closed source systems, where the obscurity of the implementation helps to hide exactly how information is being protected. But for an open source system the work around for such hacks is to simply build your own version of the server that bypasses the event or code which is preventing access. It is difficult to offer obscurity in an open source system.Consider also what happens when you distribute your compiled executables. Compiled programs are great ex-amples of obscurity. No encryption is used (usually), all steps of the code are there to be analysed by anyone with the time and knowledge and, indeed, there are decompilers available to assist with this process. Once a person discovers what libraries your code was compiled with, isolating the results to only your own “secret”code makes the whole process much faster. Have you written to Borland, Microsoft or whoever requesting that they somehow encrypt their compiled binaries?Acceptable Low SecurityMy comments so far have been directed at the idea of strong security and I guess the concept of security by obscurity has been written with some contempt. However at times weak security is all that you want. Sometimes the data is just not that valuable. You want to stop the casual browser and make it at least inconvenient for the more advanced thief.I have used such schemes myself in various places. Often there is no point in throwing Twofish, AES or whatever at such schemes because those are all about strong encryption. They are heavy with processing overhead and complication relating to keeping the security strong. A simple XOR against some known string (the key) may be sufficient. If the key can be discovered by the thief then it does not matter whether you have used weak or strong encryption, the game is over anyway.Choosing ObscurityThe thing about security by obscurity is that it must be obscure! If Firebird were to implement some sort of encryption into its disk reads and writes then it would not be obscure because it is an open source project. It would take almost no time at all to recompile the source to discover the key being provided and everything is lost. So if you really needed this feature you would obtain the Firebird source, insert your own obscuring code into the disk read and write methods and compile your own variation of the Firebird server. (Such code could be discovered by decompiling the executable but it does take a fairly serious thief to try this.)Before you do this, try to work out whether it would actually solve your problem, if the user also takes a copy of the specially compiled executables along with the database; or if it remains possible for a user to extract the secrets directly from your running server.The Philosophical ArgumentThere is also the philosophical question of why you would choose an open source database server product to build a closed source database. Many people have contributed to the project in the firm belief that open source is the best way to provide software.But, more particularly, when it comes to the storage of users' data I am a firm believer that the users should insist on the ability to access their own data – which will often include the need to understand the structures and the processes you have built (the metadata). If you go out of business or become otherwise unavailable it may be of critical importance that the users can at least extract their own data (in appropriate formats) in order to be able to move to alternative systems.Can you trust the users to respect your intellectual property while you are still in business and available? Provide the necessary services and facilities and hopefully they will. If not, there is a good chance that there is little you can do to stop them.ConclusionsThe problem has been that too many people do not understand security and how difficult it is to do well. Regret-tably there have been many software products that have encouraged such misunderstandings by implementing obscurity rather than true security. Witness the number of companies around that provide “data recovery” ser-vices, by which they mean bypassing or breaking the supposed security of obscured data.Encryption is not a panacea for security. If you are not in control of the environment (the hardware, the operating system and all software running on that system) then you have no control over the security – regardless of what encryption schemes you may have in place. This is the situation when you distribute your database to remote server installations.If you really need to protect the data or metadata in your database then you will need to retain control of the database file and the environment in which it is accessed. No other solution will offer you the same level of security.AcknowledgementsI would like to thank the various people that have reviewed and commented on this article. I would also like to thank the many people that contribute to the Firebird support list, which is the source of much of the information that appears in this article.Appendix A:Document HistoryThe exact file history – starting at version 0.5 – is recorded in the manual module in our CVS tree; see http:// /cvs/?group_id=9028Revision HistoryN/A14 Feb 2005GW First edition.N/A11 Apr 2005GW The section on “Acceptable low security” was reviewed to try andhighlight simple XOR algorithms as weak to ensure that readers inves-tigate further if interested in this approach.N/A26 Apr 2005GW Additional section on Embedded server (and references to it). Movedfootnote into an italic note, footnotes don't work well with HTML.Added a TOC.N/A 4 Dec 2005GW Added reference to TrueCrypt. Added Use of this Document section.Added an Acknowledgements section.0.57 Dec 2005PV Moved Document History and Use of This Document into appendices.Added version number for use within the Firebird project. Added docu-ment to Firebird CVS repository.Appendix B:Use of This DocumentI have tried to make this document accurate at the time of writing but I cannot guarantee that there are no mistakes. Security is a complex subject, where security is important to your product or installation you should seek professional advice.I place no particular restrictions on the use of this document. You are free to reproduce, modify or translate this document. However, altered versions of the document should be annotated with the changes that have been made and the name of author of the change (so that my name is not associated with text that I did not write). —G.W.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
WHERE a.RDB$SYSTEM_FLAG = 0
AND d.RDB$FIELD_NAME = "RDB$FIELD_TYPE"
ORDER BY a.RDB$RELATION_NAME, b.RDB$FIELD_ID
十一、查找某表的所有字段及相关定义
SMALLINT:短整型,取值范围:-32768至32767,数值确定比较小时,可以使用,可以节省磁盘空间与提升效率
WHERE B.RDB$CONSTRAINT_TYPE = "PRIMARY KEY"
AND B.RDB$RELATION_NAME = "tablename"
AND A.RDB$INDEX_NAME = B.RDB$INDEX_NAME
ORDER BY A.RDB$FIELD_POSITION
INNER JOIN RDB$RELATION_FIELDS b
ON a.RDB$RELATION_NAME = b.RDB$RELATION_NAME
INNER JOIN RDB$FIELDS c
ON b.RDB$FIELD_SOURCE = c.RDB$FIELD_NAME
INNER JOIN RDB$TYPES d
and r1.RDB$INDEX_NAME = rind.RDB$INDEX_NAME
十四、添加主键等约束
alter table tablename add constraint PK_tablename primary key(FIELDname)
alter table tablename add constraint uq_FIELD unique(FIELDname) 或 alter table tablename add unique(FIELDname)
一、分页写法小例:
select first 10 templateid,code,name from template ;
select first 10 skip 10 templateid,code,name from template ;
select * from shop rows 1 to 10; --firebird2.0支持这种写法
十八、查指定表所有unique约束 和 主键约束
SELECT a.RDB$FIELD_NAME,b.rdb$constraint_name,b.rdb$constraint_type FROM RDB$INDEX_SEGMENTS a, rdb$relation_constraints b where a.RDB$INDEX_NAME=b.RDB$INDEX_NAME and b.RDB$RELATION_NAME='tablename'
然后
alter table tablename drop constraint 主键名 (主键名一般在隐藏的系统表中,每个约束一个名。)
十六、创建数据库
Create Database 'D:\Mydb.fdb' user 'sysdba' password 'masterkey' [default character set gbk]
火鸟Firebird数据库的中文参考资料
■firebird标准连接串
Driver=Firebird/InterBase(r) driver;Uid=SYSDBA;Pwd=masterkey;DbName=C:\document. and Settings\Administrator\桌面\data\demo.fdb;
NUMERIC:小数型,与DECIMAL类似,稍后讲它们的区别。
注意,当数据含小数部分时,请尽量用DECIMAL,因为浮点型有精度问题,除非数值特别大,才用浮点型!
DECIMAL与NUMERIC的区别:
比如,DECIMAL(5,2)与NUMERIC(5,2)所分别定义的字段,DECIMAL(5,2)指的是至少有5位数字,还可以更多!而NUMERIC(5,2)指的是,就是5位,不多也不少。
where r1.RDB$RELATION_NAME = "tablename"
and r1.RDB$CONSTRAINT_TYPE = "FOREIGN KEY"
and r1.RDB$CONSTRAINT_NAME = ref.RDB$CONSTRAINT_NAME
and ref.RDB$CONST_NAME_UQ = r2.RDB$CONSTRAINT_NAME
十七、查指定字段Not Null约束
SELECT a.rdb$trigger_name,b.rdb$constraint_name,b.rdb$constraint_type FROM RDB$CHECK_CONSTRAINTS a, rdb$relation_constraints b where a.rdb$constraint_name=b.rdb$constraint_name and b.rdb$constraint_type='NOT NULL' and b.RDB$RELATION_NAME='表名' and a.rdb$trigger_name='字段名'
INTEGER:长整型,取值范围:-2147483648至2147483647
FLOAT:单精度浮点型,取值范围:1.175*10[-38]至3.402*10[38]
DOUBLE PRECISION:双精度浮点型,取值范围:2.225*10[-308]至1.797*10[308]
DECIMAL:小数型,可指定有效位数最大为18位或小数点后18位。比如DECIMAL(5,2),就是指有5位数字,不含小数点,形如123.45
update RDB$RELATION_FIELDS
set RDB$DESCRIPTION = "描述信息"
where (RDB$RELATION_NAME = "SHOP") and
(RDB$FIELD_NAME = "CREDIT_BUY")
五、--显示字段注释
select RDB$FIELD_NAME,RDB$DESCRIPTION from RDB$RELATION_FIELDS
添加NOT NULL约束比较特殊
update RDB$RELATION_FIELDS set RDB$NULL_FLAG = 1 where (RDB$FIELD_NAME = 'FIELDNAME') and (RDB$RELATION_NAME = 'TN')
insert into RDB$RELATION_constraints values('NN_FIELD','NOT NULL','WFW','NO','NO','')
AND A.RDB$FIELD_SOURCE = B.RDB$FIELD_NAME
ORDER BY A.RDB$FIELD_POSITION
十二、查找某表的主键定义字段
select A.RDB$FIELD_NAME FROM RDB$INDEX_SEGMENTS A, RDB$RELATION_CONSTRAINTS B
SELECT A.RDB$FIELD_NAME, B.RDB$FIELD_TYPE, B.RDB$FIELD_LENGTH, B.RDB$FIELD_PRECISION, B.RDB$FIELD_SCALE
FROM RDB$RELATION_FIELDS A, RDB$FIELDS B
WHERE A.RDB$RELATION_NAME = "tablename"
■Firebird除了可见的表外,还隐藏了系统表具体可用(注意以下语句中的""中的文本区分大小写)
查询所有的表和视图(包括系统表和系统视图)
SELECT RDB$RELATION_NAME FROM RDB$RELATIONS;
这样我们就能看到rdb$开头的系统表,如约束信息表:
rdb$relation_constraints 及与其相关的 RDB$CHECK_CONSTRAINTS RDB$INDEX_SEGMEN$CONSTRAINT_NAME, rind.RDB$FIELD_NAME, r2.RDB$RELATION_NAME
FROM RDB$RELATION_CONSTRAINTS r1, RDB$RELATION_CONSTRAINTS r2, RDB$REF_CONSTRAINTS ref, RDB$INDEX_SEGMENTS rind
二、show
show tables;
show table tablename;
三、
D:\firebird2\bin>isql -u sysdba -p masterkey
connect "E:\company\xmwsoft\newxmwsoft\c2\db\cts2.fdb";
四、--更新字段注释
insert into RDB$CHECK_constraints values('NN_FIELD','FIELD')
十五、删除主键等约束
先查这个表的主键名
select RDB$CONSTRAINT_NAME from RDB$RELATION_CONSTRAINTS where RDB$CONSTRAINT_TYPE='PRIMARY KEY' and RDB$RELATION_NAME='tablename'
