SonicWALL配置手册
SonicWall TZ570系列NGFW说明书

Highlights:• 5 GbE interfaces in a desktop form factor • SD-Branch ready• Secure SD-WAN capability • SonicExpress App onboarding • Zero-Touch Deployment• Single-pane-of-glass-management through cloud or firewall • SonicWall Switch, SonicWave Access Point and Capture Client integration • Built-in and expandable storage • Redundant power • High port density • Cellular failover • SonicOS 7.0 • TLS 1.3 support• Groundbreaking performance • High connection count • Fast DPI performance • Low TCOSonicWall TZ570 /570W/570PThe SonicWall TZ570 series, available in three models (TZ570, TZ570W, TZ570P) is the first desktop-form-factor next-generation firewall (NGFW) with 5 Gigabit Ethernet interfaces.Designed for mid-sized organizations and distributed enterprise with SD-Branch locations, the TZ570 series delivers industry-validated security effectiveness with best-in-class price-performance. TZ570 NGFWs address the growing trends in web encryption, connected devices and high-speed mobility by delivering a solution that meets the need for automated, real-time breach detection and prevention. The TZ570 is highly scalable, with high port density of 10 ports. It features both in-built and anexpandable storage of up to 256GB, that enables various features including logging, reporting, caching, firmware backup and more. An optionalsecond power supply provides added redundancy in case of failure. Deployment of TZ570 is furthersimplified by Zero-Touch Deployment, with the ability to simultaneously roll out these devices across multiple locations with minimal IT support. Built on next-gen hardware, itintegrates firewalling, switching and wireless capabilities, plus provides integration with Capture Client for seamless endpoint security.SonicOS and Security ServicesThe SonicOS architecture is at the core of TZ NGFWs. TZ570 is powered by the feature rich SonicOS 7.0operating system with new modern looking UX/UI, advanced security, networking and managementcapabilities. TZ570 features integrated SD-WAN , TLS 1.3 support, real-time visualization, high-speed virtual private networking (VPN) and other robust security features.Unknown threats are sent to SonicWall’s cloud-based Capture Advanced Threat Protection (ATP) multiengine sandbox for analysis. Enhancing Capture ATP is our patent-pending Real-Time Deep Memory Inspection (RTDMI™) technology. As one of Capture ATP’s engine, RTDMI detects and blocks malware and zero-day threats by inspecting directly in memory.By leveraging Capture ATP with RTDMI technology, in addition tosecurity services such as Reassembly-Free Deep Packet Inspection (RFDPI), Anti-virus and Anti-spyware Protection, intrusion preventionsystem, Application Intelligence and Control, Content Filtering Services, DPI-SSL, TZ series firewalls stop malware, ransomware and otherDeploymentsSmall to Medium size Business• Save space and money with an integrated gateway security solution with firewalling, switching and wireless capabilities •Reduce complexity and get the business runningwithout relying on IT personnel with easy onboarding using SonicExpress App and Zero-Touch Deployment, and easy management through a single pane of glass • Attain business continuity by providing failover to cellular connectivity • Protect network from attacks with a comprehensive security solution that incorporates VPN, IPS, CFS, AV and much more • Leverage high port density to power on multiple PoE devices such as IP phones and IP cameras • Boost employee productivity by blockingunauthorized access with traffic segmentation and access policiesSonicWall SwitchZero-T ouch Deployment CapableSonicWave Access PointZero-T ouch Deployment CapableCamera IP PhoneLaptopSmartphoneCapture Client Access SecurityEndpoint SecurityD istributed Enterprise with SD-Branches• Enhance customer experience and adapt to the changing business needs by enabling next-gen branch connectivity with SD-Branch • Drive business growth by investing in next-genappliances with multi-gigabit and advanced security features, to future-proof against the changing network and security landscape • Secure networks from the most advanced attacks with advanced security features and automatically block threats on decrypted traffic using protocols such as TLS 1.3• Leverage end-to-end network security withseamless integration of SonicWave access points, SonicWall Switches and Capture Client • Ensure seamless communication as stores talk to HQ via easy VPN connectivity which allows IT administrators to create a hub and spoke configuration for the safe transport of data between all locations • Improve business efficiency, performance and reduce costs by leveraging TZ570’s hardware and software enhancements, plus features such SD-WAN technology • Scale quickly and effortlessly with SonicExpress App and Zero-Touch Deployment • Ensure business continuity by providing failover to cellular connectivity • Maintain compliance with security features, and leverage built-in and expandable storage to store logs for audit purposesIPSec VPN clients (maximum)10 (500)SSL VPN licenses (maximum) 2 (200)Encryption/authentication DES, 3DES, AES (128, 192, 256-bit)/MD5, SHA-1, Suite B CryptographyKey exchange Diffie Hellman Groups 1, 2, 5, 14vRoute-based VPN RIP, OSPF, BGPRoute-based VPN Verisign, Thawte, Cybertrust, RSA Keon, Entrust and Microsoft CA for SonicWall-to-SonicWall VPN, SCEPVPN featuresDead Peer Detection, DHCP Over VPN, IPSec NAT Traversal, Redundant VPN Gateway,Route-based VPNGlobal VPN client platforms supported Microsoft ® Windows 10NetExtender Microsoft ® Windows 10, LinuxMobile ConnectApple ® iOS, Mac OS X, Google ® Android ™, Kindle Fire, Chrome OS, Windows 10SonicWall TZ570/570W/570P specifications- WAN X1 and X2 Port LEDs - X0–X7 RJ45 Port LEDs- X8 / X9 SFP/SFP+ Port LEDsSuperSpeed PortsLEDs -Security LED-Storage LEDPower InputConsole PortSonicWall TZ570/570W/570P specifications, continuedContent Filtering Service (CFS)HTTP URL, HTTPS IP, keyword and content scanning, Comprehensive filtering basedon file types such as ActiveX, Java, Cookies for privacy, allow/forbid lists Comprehensive Anti-Spam Service YesApplication Visualization YesApplication Control YesCapture Advanced Threat Protection YesDNS SecurityYesMajor regulatory complianceFCC Class B, FCC , ICESClass B, CE (EMC, LVD,RoHS), C-Tick, VCCI ClassB, UL/cUL, TUV/GS, CB,Mexico DGN notice byUL, WEEE, REACH, BSMI,KCC/MSIP, ANATELFCC P15E, ICES Class B,ISED/IC, CE (RED, RoHS),C-Tick, VCCI Class B, JapanWireless, UL/cUL, TUV/GS,CB, Mexico DGN notice byUL, WEEE, REACH, BSMI,NCC (TW) KCC/MSIP,SRRC, ANATELFCC Class A, ICES ClassA, CE (EMC, LVD, RoHS),C-Tick, VCCI Class A, UL/cUL, TUV/ GS, CB, MexicoDGN notice by UL, WEEE,REACH, BSMI, KCC/MSIP,ANATELSonicWall TZ570W specifications, continuedFrequency bands802.11a: 5.180-5.825 GHz; 802.11b/g: 2.412-2.472 GHz; 802.11n: 2.412-2.472 GHz,5.180-5.825 GHz; 802.11ac: 5.180-5.825 GHzOperating channels 802.11a: US and Canada 12, Europe 11, Japan 4, Singapore4, Taiwan 4; 802.11b/g: US and Canada 1-11, Europe 1-13, Japan (14-802.11b only); 802.11n (2.4 GHz): US and Canada 1-11, Europe 1-13, Japan 1-13; 802.11n (5 GHz): US and Canada 36-48/149-165, Europe 36-48, Japan 36-48, Spain 36-48/52-64; 802.11ac: US and Canada 36-48/149-165, Europe 36-48, Japan 36-48, Spain 36-48/52-64Transmit output power Based on the regulatory domain specified by the system administrator Transmit power control YesData rates supported 802.11a: 6, 9, 12, 18, 24, 36, 48, 54 Mbps per channel; 802.11b: 1, 2, 5.5, 11 Mbps per channel; 802.11g: 6, 9, 12, 18, 24, 36, 48, 54 Mbps per channel; 802.11n: 7.2, 14.4, 21.7, 28.9, 43.3, 57.8, 65, 72.2, 15, 30, 45, 60, 90, 120, 135, 150 Mbps per channel; 802.11ac: 7.2, 14.4, 21.7, 28.9, 43.3, 57.8, 65, 72.2, 86.7, 96.3, 15, 30, 45, 60, 90, 120, 135, 150, 180, 200, 32.5, 65, 97.5, 130, 195, 260, 292.5, 325, 390, 433.3, 65, 130, 195, 260, 390, 520, 585, 650, 780, 866.7 Mbps per channelModulation technology spectrum802.11a: Orthogonal Frequency Division Multiplexing (OFDM); 802.11b: Direct Sequence Spread Spectrum (DSSS); 802.11g: Orthogonal Frequency Division Multiplexing (OFDM)/Direct Sequence Spread Spectrum (DSSS); 802.11n: Orthogonal Frequency Division Multiplexing (OFDM); 802.11ac: Orthogonal Frequency DivisionMultiplexing (OFDM)1. Testing Methodologies: Maximum performance based on RFC 2544 (for firewall). Actual performance may vary depending on network conditions and activated services.2. Threat Prevention/GatewayAV/Anti-Spyware/IPS throughput measured using industry standard Spirent WebAvalanche HTTP performance test and Ixia test tools. Testing done with multiple flows through multiple port pairs. Threat Prevention throughput measured with Gateway AV, Anti-Spyware, IPS and Application Control enabled.3. VPN throughput measured using UDP traffic at 1280 byte packet size adhering to RFC 2544. All specifications, features and availability are subject to change.4. For rack mount, separate rack mount kit available.5. All TZ integrated wireless models can support either 2.4GHz or 5GHz band. For dual-band support, please use SonicWall's wireless access point products.SonicOS 7.0 Feature SummaryFirewall• Stateful packet inspection• Reassembly-Free Deep Packet Inspection • DDoS attack protection (UDP/ICMP/SYN flood)• IPv4/IPv6 support• Biometric authentication for remote access • DNS proxy• Full API support• SonicWall Switch integration• SD-WAN scalability• SD-WAN Usability Wizard1• SonicCoreX and SonicOS containerization1• Connections scalability (SPI, DPI, DPI SSL) Enhanced dashboard1• Enhanced device view• Top traffic and user summary• Insights to threats• Notification centerTLS/SSL/SSH decryption and inspection• TLS 1.3 with enhanced security1• Deep packet inspection for TLS/SSL/SSH • Inclusion/exclusion of objects, groupsor hostnames• SSL control• Enhancements for DPI-SSL with CFS• Granular DPI SSL controls per zone or rule Capture advanced threat protection2• Real-Time Deep Memory Inspection• Cloud-based multi-engine analysis• Virtualized sandboxing• Hypervisor level analysis• Full system emulation• Broad file type examination• Automated and manual submission• Real-time threat intelligence updates• Block until verdict• Capture ClientIntrusion prevention2• Signature-based scanning• Automatic signature updates• Bi-directional inspection• Granular IPS rule capability• GeoIP enforcement• Botnet filtering with dynamic list• Regular expression matchingAnti-malware2• Stream-based malware scanning• Gateway anti-virus• Gateway anti-spyware• Bi-directional inspection• No file size limitation• Cloud malware databaseApplication identification2• Application control• Application bandwidth management• Custom application signature creation• Data leakage prevention• Application reporting over NetFlow/IPFIX• Comprehensive application signature databaseTraffic visualization and analytics• User activity• Application/bandwidth/threat usage• Cloud-based analyticsHTTP/HTTPS Web content filtering2• URL filtering• Proxy avoidance• Keyword blocking• Policy-based filtering (exclusion/inclusion)• HTTP header insertion• Bandwidth manage CFS rating categories• Unified policy model with app control• Content Filtering ClientVPN• Secure SD-WAN• Auto-provision VPN• IPSec VPN for site-to-site connectivity• SSL VPN and IPSec client remote access• Redundant VPN gateway• Mobile Connect for iOS, Mac OS X, Windows,Chrome, Android and Kindle Fire• Route-based VPN (OSPF, RIP, BGP)Networking• PortShield• Jumbo frames• Path MTU discovery• Enhanced logging• VLAN trunking• Port mirroring (NS a 2650 and above)• Layer-2 QoS• Port security• Dynamic routing (RIP/OSPF/BGP)• SonicWall wireless controller• Policy-based routing (ToS/metric and ECMP)• NAT• DHCP server• Bandwidth management• A/P high availability with state sync• Inbound/outbound load balancing• High availability - Active/Standby withstate sync• L2 bridge, wire/virtual wire mode, tap mode,NAT mode• Asymmetric routing• Common Access Card (CAC) supportVoIP• Granular QoS control• Bandwidth management• DPI for VoIP traffic• H.323 gatekeeper and SIP proxy supportManagement, monitoring and support• Capture Security Appliance (CS a) support• Capture Threat Assessment (CTA) v2.0• New design or template• Industry and global average comparison• New UI/UX, Intuitive feature layout1• Dashboard• Device information, application, threats• Topology view• Simplified policy creation and management• Policy/Objects usage statistics1• Used vs Un-used• Active vs Inactive• Global search for static data• Storage support1• Internal and external storage management1• WWAN USB card support (5G/LTE/4G/3G)• Network Security Manager (NSM) support• Web GUI• Command line interface (CLI)• Zero-Touch registration & provisioning• CSC Simple Reporting1• SonicExpress mobile app support• SNMPv2/v3• Centralized management and reporting withSonicWall Global Management System (GMS)2• Logging• Netflow/IPFix exporting• Cloud-based configuration backup• BlueCoat security analytics platform• Application and bandwidth visualization• IPv4 and IPv6 management• CD management screen• Dell N-Series and X-Series switchmanagement including cascaded switchesDebugging and diagnostics• Enhanced packet monitoring• SSH terminal on UIWireless• SonicWave AP cloud management• WIDS/WIPS• Rogue AP prevention• Fast roaming (802.11k/r/v)• 802.11s mesh networking• Auto-channel selection• RF spectrum analysis• Floor plan view• Topology view• Band steering• Beamforming• AirTime fairness• Bluetooth Low Energy• MiFi extender• RF enhancements and improvements• Guest cyclic quotaIntegrated Wireless (TZ570W only)• 802.11ac Wave 2 wireless• Dual-band (2.4 GHz and 5.0 GHz)• 802.11 a/b/g/n/ac wireless standards• Wireless intrusion detection and prevention• Wireless guest services• Lightweight hotspot messaging• Virtual access point segmentation• Captive portal• Cloud ACLProduct SKUTZ570 with 1-year TotalSecure Essential Edition02-SSC-5651 TZ570W with 1-year TotalSecure Essential Edition02-SSC-5649 TZ570P with 1-year TotalSecure Essential Edition02-SSC-5653 TZ570 High Availability02-SSC-5694 TZ570P High Availability02-SSC-5655 TZ570 with 3-year Secure Upgrade Plus Essential Edition02-SSC-5661 TZ570W with 3-year Secure Upgrade Plus Essential Edition 02-SSC-5663 TZ570P with 3-year Secure Upgrade Plus Essential Edition02-SSC-5667Services for SonicWall TZ570SKU Essential Protection Service Suite - Capture ATP, Threat Prevention, Content Filtering, Anti-Spam and 24x7 Support (1-year)02-SSC-5137 Capture Advanced Threat Protection for TZ570 (1-year)02-SSC-5083 Gateway Anti-Virus, Intrusion Prevention and Application Control (1-year)02-SSC-5155 Content Filtering Service (1-year)02-SSC-5119 Comprehensive Anti-Spam Service (1-year)02-SSC-5101 24x7 Support (1-year)02-SSC-5065Services for SonicWall TZ570W SKU Essential Protection Service Suite - Capture ATP, Threat Prevention, Content Filtering, Anti-Spam and 24x7 Support (1-year)02-SSC-5149 Capture Advanced Threat Protection for TZ570W (1-year)02-SSC-5095 Gateway Anti-Virus, Intrusion Prevention and Application Control (1-year)02-SSC-5167 Content Filtering Service (1-year)02-SSC-5131 Comprehensive Anti-Spam Service (1-year)02-SSC-5113 24x7 Support (1-year)02-SSC-5077Services for SonicWall TZ570P SKU Essential Protection Service Suite - Capture ATP, Threat Prevention, Content Filtering, Anti-Spam and 24x7 Support (1-year)02-SSC-5143 Capture Advanced Threat Protection for TZ570P (1-year)02-SSC-5089 Gateway Anti-Virus, Intrusion Prevention and Application Control (1-year)02-SSC-5161 Content Filtering Service (1-year)02-SSC-5125 Comprehensive Anti-Spam Service (1-year)02-SSC-5107 24x7 Support (1-year)02-SSC-5071Accessories SKU SonicWall TZ670/570 Series FRU Power Supply02-SSC-3078 SonicWall TZ670/570 Series Rack Mount Kit02-SSC-3112 SonicWall 32GB Storage Module for TZ670/570 Series02-SSC-3114 SonicWall 64GB Storage Module for TZ670/570 Series02-SSC-3115 SonicWall 128GB Storage Module for TZ670/570 Series02-SSC-3116 SonicWall 256GB Storage Module for TZ670/570 Series02-SSC-3117 SonicWall Micro USB Console Cable for TZ670/570 Series02-SSC-5173 10GB-SR SFP+ Short Reach Fiber Module Multi-Mode No Cable01-SSC-9785 10GB-LR SFP+ Long Reach Fiber Module Single-Mode No Cable01-SSC-9786 10GB SFP+ Copper with 1M Twinax Cable01-SSC-9787 10GB SFP+ Copper with 3M Twinax Cable01-SSC-9788 1GB-SX SFP Short Haul Fiber Module Multi-Mode No Cable01-SSC-9789 1GB-LX SFP Long Haul Fiber Module Single-Mode No Cable01-SSC-9790 1GB-RJ45 SFP Copper Module No Cable01-SSC-9791 SonicWall SFP+ 10GBASE-T Transceiver Copper RJ45 Module02-SSC-1874Regulatory model numbersTZ570APL62-0F7 TZ570W APL62-0F8 TZ570P APL63-0F9About SonicWallSonicWall delivers Boundless Cybersecurity for the hyper-distributed era and a work reality where everyone is remote, mobile and unsecure. By knowing the unknown, providing real-time visibility and enabling breakthrough economics, SonicWall closes the cybersecurity business gap for enterprises, governments and SMBs worldwide. For more information, visit .。
SonicWall NSa 4650 5650 6650 快速入门指南说明书
说明 无链路。 以 1 Gbps、100 Mbps 或 10 Mbps 的速率链接。 流量已激活。
LAN 旁路 LED LED 颜色
关 稳定的绿光
稳定的黄光
说明
已禁用 LAN 旁路,端口彼此隔离。
LAN 旁路已设防,但未激活。直到断电/重启等事件发生 时,才会隔离端口,从而激活旁路。
LAN 旁路处于活动状态,端口连接在一起。如果电源发生 故障,LED 将显示为关闭,但旁路仍处于活动状态。
8 使用设置向导
此 SonicOS 设置向导将帮助您快速配置 SonicWall 设备,以保护互联网连接 安全。 使用设置向导的步骤如下: 1 使用 192.168.1.0/24 子网中的静态 IP 地址(如 192.168.1.20)配置管理计算机上的
本地连接 IPv4 属性,并将子网掩码设置为 255.255.255.0。 您的计算机能通过 MGMT 接口连接至 SonicOS。 2 在计算机的 Web 浏览器中,输入默认的 MGMT IP 地址: http://192.168.1.254 3 在初始屏幕中,单击第一个链接 To launch the SonicWall Setup Guide, click here(如 需启动 SonicWall 设置指南,请单击此处)可启动 SonicOS 设置向导。 4 这将打开 SonicOS 设置指南。单击 NEXT(下一步)。
注:在“有线模式”下运行时,防火墙的 MGMT 接口用于本地管理。如需启 用远程管理和动态安全服务以及应用程序智能更新,必须配置 WAN 接口 (与有线模式接口分离)用于互联网连接。
• Tap Mode (1-Port Tap)(分接模式(1 端口分接))- 防火墙使用单个接口连接并接 收来自相邻交换机 SPAN 端口的镜像数据包。与“有线模式”中的“检测模式”相似, 但只有单一端口且不在流量的物理路径中。如果 Tap 模式在设置向导中不可用, 您可以稍后在 SonicOS 管理界面中进行配置。
SonicWALL系列设备配置下
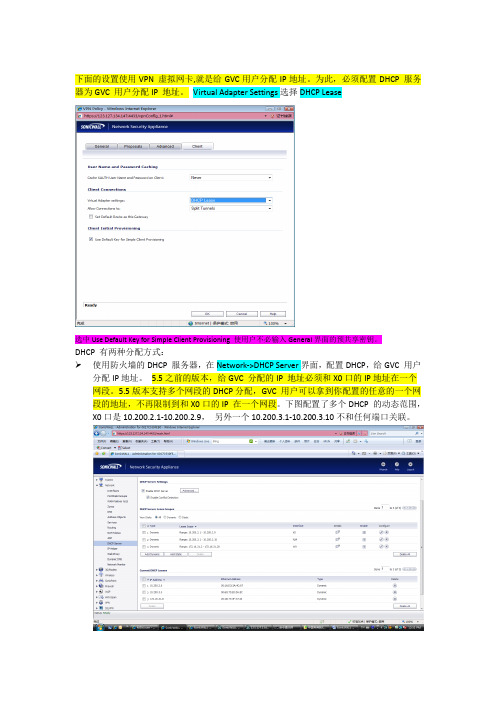
下面的设置使用VPN 虚拟网卡,就是给GVC用户分配IP地址。
为此,必须配置DHCP 服务器为GVC 用户分配IP 地址。
Virtual Adapter Settings选择DHCP Lease选中Use Default Key for Simple Client Provisioning 使用户不必输入General界面的预共享密钥。
DHCP 有两种分配方式:使用防火墙的DHCP 服务器,在Network->DHCP Server界面,配置DHCP,给GVC 用户分配IP地址。
5.5之前的版本,给GVC 分配的IP 地址必须和X0口的IP地址在一个网段。
5.5版本支持多个网段的DHCP分配,GVC 用户可以拿到你配置的任意的一个网段的地址,不再限制到和X0口的IP 在一个网段。
下图配置了多个DHCP 的动态范围,X0口是10.200.2.1-10.200.2.9,另外一个10.200.3.1-10.200.3.10不和任何端口关联。
配置完这个界面之后,需要配置VPN->DHCP Over VPN 界面,选择Use Internal DHCP Server, For Global VPN ClientRelay Agent IP(Optional)是可选的配置。
DHCP 服务器可以分配任意的网段给GVC用户。
Relay Agent IP就是那个网段中的一个保留的IP地址,不会分配给GVC用户。
当DHCP 请求到达DHCP服务器时,DHCP服务器知道要分配这个网段的地址给GVC用户。
DHCP服务器可以是防火墙本身的DHCP服务器,可以是专门的DHCP服务器,也可以是和防火墙互联的L3交换机,L3交换机一般都支持DHCP服务器的功能。
第二种DHCP,见下图。
使用VPN->DHCP over VPN->Configure界面,用内网的DHCP 服务器给用户分配IP地址。
Relay Agent IP(Optional)是可选的配置。
SonicWall NSsp 13700 快速入门指南说明书

6 使用本機管理進行初始設定和註冊
1 使用 192.168.1.x 子網路 (例如 192.168.1.100) 上的靜態 IP 位址設定您的電腦,並將網路遮罩設為 255.255.255.0。
2 使用隨附的乙太網路線,將 MGMT 介面連線至您的 電腦。
3 在網頁瀏覽器中前往 https://192.168.1.254 並使用預 設認證登入: Username (使用者名稱):admin Password (密碼):password
備註:當連線到 MGMT 介面時,若是沒有先在介面 設定中設定預設閘道,將無法連線至網際網路或其他 外部目的地。 7 按一下 Register (註冊) 並輸入您的 MySonicWall 認證,
以註冊您的 NSsp。 提示:從 SonicOS/X 註冊設備時,必須設定用於 WAN 介 面 的 DNS 設 定 值。若 為 DHCP WAN 類 型,則 DNS 已自動設定。
SonicWall 交換器
網路存取交換器
擷取用戶端
端點安全性
Cloud App Security
安全雲端應用程式
Capture Security Center
單一窗格管理,採用 Zero-Touch 部署
備註:隨附的電源線經核准僅供特定國家或地區使用。使用電源線之前,務必先確認其額定電 壓且經核准可供您所在位置使用。電源線僅供交流電源安裝使用。請參閱 NSsp 13700 安全、法 規和法律資訊文件,瞭解其他安全資訊。 有遺漏的項目? 請透過下列資訊聯絡 SonicWall 技術支援: https:///support/contact-support
X20 X23
10/5/2.5GE SFP+ 連接埠和 LED: 琥珀色燈長亮 = 以 10G、5G 或 2.5G 連線,琥珀色燈閃爍 = 動作中 綠燈長亮 = 以 1G 或更低速度連線,閃爍綠燈 = 動作中 熄滅 = 無連線
sonicwall ssl vpn 配置手册
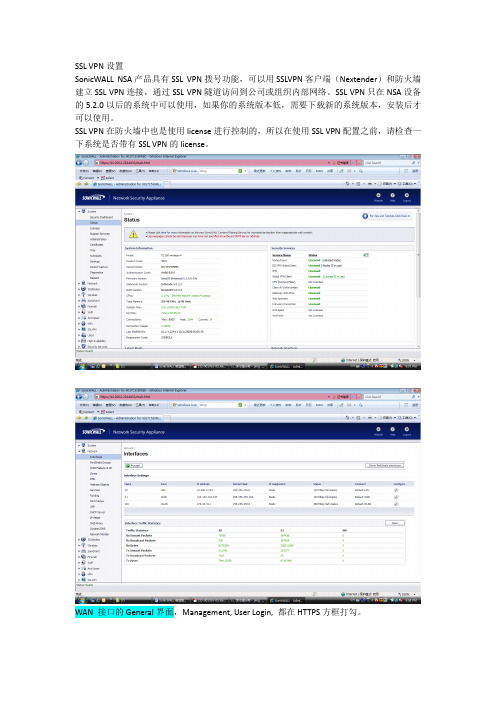
SSL VPN设置SonicWALL NSA产品具有SSL VPN拨号功能,可以用SSLVPN客户端(Nextender)和防火墙建立SSL VPN连接,通过SSL VPN隧道访问到公司或组织内部网络。
SSL VPN只在NSA设备的5.2.0以后的系统中可以使用,如果你的系统版本低,需要下载新的系统版本,安装后才可以使用。
SSL VPN在防火墙中也是使用license进行控制的,所以在使用SSL VPN配置之前,请检查一下系统是否带有SSL VPN的license。
WAN 接口的General界面,Management, User Login, 都在HTTPS方框打勾。
选择SSL VPN->Client Setting.在Interface下拉框中,使用X0(LAN口)作为SSL VPN服务口,同时在WAN安全区域允许SSL VPN接入,点WAN是红色的按钮变成绿色。
需要注意到是,Nextender的地址范围要和内网接口(本例是X0 LAN)的地址范围一致。
这个地址范围不要和其它机器冲突。
(你可以启用防火墙的另外一个没有使用的端口做SSL VPN 服务接口,那么你在Interface界面选择那个接口,IP 地址池范围就是那个接口网段的地址)NetExtender Client Settings是配置客户端的细致的设置。
Create Client Connection Profile:可以使NetExtender Client客户端软件自动保存成功连接的配置,下次连接,直接选择这个连接的参数,不用手工再次输入了。
点击SSL VPN->Client Routes菜单下,把需要访问的服务器网段地址或服务器地址添加进去。
Client Route界面把允许SSL VPN用户访问的主机地址和网段加入即可。
防火墙自动创建SSL VPN到各个安全区域的规则,本例是SSL VPN用户访问LAN Primary Subnet,就是LAN口的整个网段,自动生成的防火墙规则在Firewall->Access Rules, SSL VPN->LAN界面可以看到。
SonicWALL TZ Series产品说明说明书

NE T WORK SECURIT YNetwork security and control is accomplished through a robust and flexible platform*Card not included. See /us/tz190cards.html for supported 3G PCMCIA Type II cards and analog modem PCMIA cards. retail/POSdeploymentsApplicationsSonicWALL TZ 150 SeriesIdeal for home and small offices, the TZ 150 Series integrates a deep packet inspection firewall, IPSec 3DES/AES VPN and 802.11b/g secure wireless capabilities in an easy-to-use, low cost platform.■ Compact form factor includes a single Ethernet WAN portand four-port auto-MDIX LAN switch■ Supports gateway anti-virus, anti-spyware, intrusionprevention and content filtering for true layered security■ Designed to exceed the performance requirements oftypical business DSL and cable broadband servicesSonicWALL TZ 180 SeriesDesigned as a complete Unified Threat Management (UTM) platform delivering business-class protection to small, remote and branch office networks, the TZ 180 Series features an integrated 5-port auto-sensing MDIX switch and configurable optional port.■ Exceptionally fast Unified Threat Management (UTM)performance on networks running gateway anti-virus, anti-spyware and intrusion prevention■ Integrated 802.11b/g wireless LAN with WPA2 supportdelivers increased security and flexibility as well as greater range for wireless users■ Inter-zone scanning combines with Unified ThreatManagement protection to eliminate threats no matter where they originate—inside or outside the network■ The TZ 180 delivers twice the UTM scanning speed as theTZ 170 and provides compelling new features such as a security dashboard for real-time threat monitoring and WPA2 supportSonicWALL TZ 190 SeriesThe flagship of the SonicWALL TZ Series, the TZ 190 is a high-performance security platform that integrates a Type II PC Card slot for WAN backup for small networks with mission-critical needs. The TZ 190 also includes automated failover/failback, a deep packet inspection firewall and optional 802.11b/g wireless LAN access. Building on the capabilities of the TZ 180 Series, the TZ 190 Series provides additional functionality including:■ Rapidly establish secure 3G wireless broadbandnetwork access in an instant without the need for a fixed Internet connection■ Adherence to PCI standards make this the ultimatesolution for retail point-of-sale merchants and service providers who require secure transmission of customer information■ Modular design enables the use of a wide range ofPC cards (3G, analog modem) for greater usage flexibilityWireless LANVPNInternetWired LAN TZ 150 WirelessCorporate HeadquartersVPNInternetWired LAN Wireless LANCorporate HeadquartersTZ 180 Wireless3G WirelessDial-upWireless LANVPNEthernetWired LAN Corporate HeadquartersTZ 190WirelessInternetORSonicWALL TZ 190。
SonicWALL配置手册--

SonicWALL防火墙标准版配置SonicWall标准版网络向导配置 (1)SonicWall标准版规则向导配置 (11)SonicWall标准版一般规则向导配置 (11)SonicWall标准版服务器规则向导配置 (21)SonicWall标准版一般规则直接配置 (25)SonicWall标准版服务器1对1 NAT配置 (29)SonicWall标准版透明模式配置 (31)SonicWall标准版网络向导配置首次接触SonicWALL防火墙设备,我们将电源接上,并开启电源开关,将X0口和你的电脑相连(注:请用交叉线),SonicWALL防火墙默认的IP地址为192.168.168.168,我们也可以通过setuptool.exe这个小工具探知SonicWALL防火墙的IP地址。
如图所示:页脚内容1当网线和电源等都连接好之后,我们设置一下本机的IP地址,以便和SonicWALL防火墙处于同一个网段。
如图所示:设置好IP地址后,我们在IE浏览器的地址栏输入SonicWALL防火墙的IP地址,页脚内容2点next,提示我们是否修改管理员密码,页脚内容3暂时不修改,点next,提示我们修改防火墙的时区,我们选择中国的时区。
页脚内容4点next,提示我们设置WAN口的地址获取类型,这时候,我们需要和ISP相联系,并选择相关的类型,这里以静态地址为例:页脚内容5我们点next,输入相关的信息,IP地址、掩码、网关、DNS服务器等,如果不知道此处该如何设置,请和你的ISP联系。
页脚内容6点next,提示我们设置LAN口的IP和掩码,我们根据自己的规划和网络的实际情况设置,此处我没有修改。
页脚内容7点next,防火墙询问我们在LAN口是否开启DHCP server的功能,并是否是默认的网段,我们可根据实际情况做调整,决定开始或关闭,以及网段地址等,如下图:页脚内容8点next,防火墙将把前面做的设置做一个摘要,以便我们再一次确认是否设置正确,如果有和实际不符的地方,可以点back返回进行修改。
SonicWall SonicOS 6.5系统设置管理指南说明书

SonicWall™ SonicOS 6.5 系统设置管理目录关于设置您的 SonicOS 系统 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .13关于 SonicOS 管理界面 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13配置基本设置 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .16关于设备 | 基本设置 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17配置防火墙名称 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18更改管理员名称和密码 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19配置登录安全 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19配置多管理员访问 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22启用增强的审核记录支持 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26配置管理界面 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26配置前板管理界面(仅限 SuperMassive 防火墙) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31配置客户端证书验证 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32检查证书过期 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35配置 SSH 管理 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36配置高级管理选项 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36手动下载 SonicPoint 镜像 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38选择语言 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39管理 SNMP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .41关于设备 | SNMP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41关于 SNMP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41设置 SNMP 访问权限 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42将 SNMP 配置为服务并添加规则 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50关于 SNMP 日志 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50管理证书 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .51关于证书 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51关于数字证书 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51关于证书和证书请求表 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52导入证书 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54删除证书 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56生成证书签名请求 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56配置简单证书注册协议 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 60配置时间设置 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .62关于设备 | 时间 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 62设置系统时间 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 62配置 NTP 设置 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 64设置日程 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .66关于日程 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 66SonicWall SonicOS 6.5 管理指南关于设备 | 日程 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 66添加自定义日程 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67修改日程 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 68删除自定义日程 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69关于管理用户 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .72关于用户管理 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 72使用本地用户和群组进行验证 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 73使用 RADIUS 进行身份验证 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 76使用 LDAP/Active Directory/eDirectory 验证 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 76关于单点登录 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 80安装单点登录代理和/或终端服务代理 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 90关于多管理员支持 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 107配置多管理员支持 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 108配置用于管理用户的设置 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .111用户 | 设置 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 111配置用户验证和登录设置 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 112配置用户会话 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 120自定义 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 123配置 RADIUS 身份验证 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 129配置 SonicWall 以支持 LDAP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 134关于对多个 LDAP 服务器的扩展支持 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 140关于从 LDAP 导入和镜像 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 141关于增强版 LDAP 测试 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143配置 SonicOS 以使用 SonicWall SSO 代理 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 143管理身份验证分区 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .165关于身份验证分区 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 165关于用户身份验证分区 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 166关于子分区 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 167关于分区间用户漫游 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 169关于身份验证分区选择 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 170关于对多个 LDAP 服务器的扩展支持 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172每个分区的 DNS 服务器和分割 DNS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172关于 RADIUS 身份验证 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 172从非分区配置升级 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173配置身份验证分区和策略 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173显示和过滤用户/分区 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 173配置和管理分区 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 175配置分区选择策略 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 186配置进行身份验证分区的服务器、代理和客户端 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 189配置本地用户和群组 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .191配置本地用户 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 191SonicWall SonicOS 6.5 管理指南添加本地用户 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 192编辑本地用户 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 197从 LDAP 导入本地用户 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 198配置访客管理员 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 198配置本地群组 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 199创建或编辑本地群组 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 200从 LDAP 导入本地群组 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 208按 LDAP 位置设置用户成员身份 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 208管理访客服务 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .209用户 | 访客服务 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 209全局访客设置 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 209访客配置文件 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 210管理访客帐户 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .213用户 | 访客帐户 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 213查看访客帐户统计 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 213添加访客帐户 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 215启用访客帐户 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 221启用访客帐户自动删除 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 221编辑访客帐户 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 221删除访客帐户 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 221打印帐户详细信息 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 222配置接口 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .224关于接口 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 225物理和虚拟接口 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 225 SonicOS 安全对象 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 227透明模式 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 228 IPS 探查器模式 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 228 Firewall Sandwich . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 230 HTTP/HTTPS 重定向 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 230在接口上启用 DNS 代理 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 230网络 | 接口 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 230显示/隐藏 PortShield 接口(仅限 IPv4) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 232接口设置 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 233接口流量统计 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 233配置接口 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 234配置静态接口 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 234配置路由模式 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 239在接口上启用带宽管理 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 241配置透明 IP 模式下的接口(连接 L3 子网) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 242配置无线接口 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 245配置 WAN 接口 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 248SonicWall SonicOS 6.5 管理指南配置链路聚合和端口冗余 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 255配置虚拟接口(VLAN 子接口) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 259配置 IPS 探查器模式 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 260配置安全服务(统一威胁管理) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 263配置有线和 Tap 模式 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 264带有链路聚合的有线模式 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 267二层桥接模式 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 267配置二层桥接模式 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 283非对称路由 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 290配置 IPv6 接口 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29131 位网络 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 291PPPoE 未编号接口支持 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 292PortShield 配置接口 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .295网络 | PortShield 群组 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 295关于 PortShield . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 295 X -系列交换机的 SonicOS 支持 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 296管理端口 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 305配置 PortShield 群组 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 313设置故障切换和负载均衡 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .319网络 | 故障切换和负载均衡 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 319关于故障切换和负载均衡 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 319故障切换和负载均衡的工作原理 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 320多个 WAN (MWAN) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 321网络 | 故障切换和负载均衡 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 321配置故障切换和负载均衡组 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 324配置群组成员的探测设置 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 327配置网络区域 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .329关于区域 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 329区域的工作方式 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 330预定义区域 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 330安全类型 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 331允许接口信任 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 331对区域启用 SonicWall 安全服务 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 331网络 | 区域 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 332区域设置表 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 333添加新区域 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 333配置访客访问的区域 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 335配置用于开放式验证和社交登录的区域 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 338配置 WLAN 区域 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 338删除区域 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 340配置有线模式 VLAN 转换 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .341SonicWall SonicOS 6.5 管理指南网络 | VLAN 转换 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 341关于 VLAN 转换 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 341创建和管理 VLAN 映射 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 342配置 DNS 设置 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .349网络 | DNS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 349关于分割 DNS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 351管理 DNS 服务器 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 352 DNS 和 IPv6 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 357 DNS 和 IPv4 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 358配置 DNS 代理设置 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .361网络 > DNS 代理 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 362关于 DNS 代理 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 363启用 DNS 代理 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 365配置 DNS 代理设置 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 367监控 DNS 服务器状态 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 367监控分割 DNS 服务器状态 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 368查看和管理静态 DNS 缓存条目 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 369查看 DNS 代理缓存条目 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 370配置路由通告和路由策略 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .372关于路由 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 372关于度量和管理距离 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 373路由通告 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 374 ECMP 路由 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 374基于策略的路由 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 375基于策略的 TOS 路由 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 375基于 PBR 度量值的优先级 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 376基于策略的路由和 IPv6 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 377 OSPF 和 RIP 高级路由服务 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 377丢弃隧道接口 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 384网络 | 路由 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 384网络 | 路由 > 设置 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 384网络 | 路由 > 路由策略 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 385网络 | 路由 > 路由通告 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 386网络 | 路由 > OSPFv2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 387网络 | 路由 > RIP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 388网络 | 路由 > OSPFv3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 389网络 | 路由 > RIPng . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 391配置路由 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 392按度量值设置路由的优先级 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 392为通过路由公告学习的默认路由配置度量值 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 393配置路由通告 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 393配置静态和基于策略的路由 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 394SonicWall SonicOS 6.5 管理指南。
SonicWALL配置手册--
SonicWALL配置手册--SonicWALL防火墙标准版配置SonicWall标准版网络向导配置 (1)SonicWall标准版规则向导配置 (7)SonicWall标准版一般规则向导配置 (7)SonicWall标准版服务器规则向导配置 (12)SonicWall标准版一般规则直接配置 (15)SonicWall标准版服务器1对1 NAT配置 (18)SonicWall标准版透明模式配置 (19)SonicWall标准版网络向导配置首次接触SonicW ALL防火墙设备,我们将电源接上,并开启电源开关,将X0口和你的电脑相连(注:请用交叉线),SonicWALL 防火墙默认的IP地址为192.168.168.168,我们也可以通过setuptool.exe这个小工具探知SonicW ALL防火墙的IP地址。
如图所示:当网线和电源等都连接好之后,我们设置一下本机的IP地址,以便和SonicWALL防火墙处于同一个网段。
如图所示:设置好IP地址后,我们在IE浏览器的地址栏输入SonicWALL防火墙的IP地址,点next,提示我们是否修改管理员密码,暂时不修改,点next,提示我们修改防火墙的时区,我们选择中国的时区。
点next,提示我们设置W AN口的地址获取类型,这时候,我们需要和ISP相联系,并选择相关的类型,这里以静态地址为例:我们点next,输入相关的信息,IP地址、掩码、网关、DNS服务器等,如果不知道此处该如何设置,请和你的ISP联系。
点next,提示我们设置LAN口的IP和掩码,我们根据自己的规划和网络的实际情况设置,此处我没有修改。
点next,防火墙询问我们在LAN口是否开启DHCP server的功能,并是否是默认的网段,我们可根据实际情况做调整,决定开始或关闭,以及网段地址等,如下图:点next,防火墙将把前面做的设置做一个摘要,以便我们再一次确认是否设置正确,如果有和实际不符的地方,可以点back返回进行修改。
Dell SonicWALL NSA系列下一代防火墙用户手册说明书

Organizations of all sizes depend on their networks to access internal and external mission-critical applications. As advances in networking continueto provide tremendous benefits, organizations are increasingly challenged by sophisticated and financially-motivated attacks designed to disrupt communication, degrade performance and compromise data. Malicious attacks penetrate outdated stateful packet inspection firewalls with advanced application layer exploits. Point products add layers of security, but are costly, difficult to manage, limited in controlling network misuse and ineffective against the latest multipronged attacks.By utilizing a unique multi-core design and patented Reassembly-Free Deep Packet Inspection® (RFDPI) technology*, the Dell™ SonicWALL™ Network Security Appliance (NSA) Series of Next-Generation Firewalls offers complete protection without compromising network performance. The low latency NSA Series overcomes the limitations of existing security solutions by scanning the entirety of each packet for current internal and external threats in real-time. The NSA Series offers intrusion prevention, malware protection, and application intelligence, control and visualization, while delivering breakthrough performance. With advanced routing, stateful high-availability and high-speed IPSec and SSL VPN technology, the NSA Series adds security, reliability, functionality and productivity to branch offices, central sites and distributed mid-enterprise networks, while minimizing cost and complexity.Comprised of the Dell SonicWALL NSA 220, NSA 220 Wireless-N, NSA 250M, NSA 250M Wireless-N, NSA 2400, NSA 3500 and NSA 4500, the NSA Series offers a scalable range of solutions designed to meet the network security needs of any organization.Network SecurityAppliance SeriesNext-Generation Firewall• Next-Generation Firewall• Scalable multi-core hardware andReassembly-Free Deep PacketInspection• Application intelligence, controland visualization• Stateful high availability and loadbalancing• High performance and loweredtco• Network productivity• Advanced routing services andnetworking• Standards-based Voice over IP(VoIP)• Dell Sonicwall clean Wireless• onboard Quality of Service (QoS)• Integrated modules support• Border Gateway Protocol (BGP)support• More concurrent SSL VPN sessionsFeatures and benefitsNext-Generation Firewall features integrate intrusion prevention, gateway anti-virus, anti-spyware and URL filtering with application intelligence and control, and SSL decryption to block threats from entering the network and provide granular application control without compromising performance.Scalable multi-core hardware and Reassembly-Free Deep Packet Inspection scans and eliminates threats of unlimited file sizes, with near-zero latency across thousands of connections at wire speed.Application intelligence, control and visualization provides granular control and real-time visualization of applications to guarantee bandwidth prioritization and ensure maximum network security and productivity. Stateful high availability and load balancing features maximize total network bandwidth and maintain seamless network uptime, delivering uninterrupted access to mission-critical resources, and ensuring that VPN tunnels and other network traffic will not be interrupted in the event of a failover. High performance and lowered tcoare achieved by using the processingpower of multiple cores in unison todramatically increase throughput andprovide simultaneous inspectioncapabilities, while lowering powerconsumption.Network productivity increases becauseIT can identify and throttle or blockunauthorized, unproductive andnon-work related applications and websites, such as Facebook® or YouTube®,and can optimize WAN traffic whenintegrated with Dell SonicWALL WANAcceleration Appliance (WXA) solutions.Advanced routing services andnetworking features incorporate 802.1qVLANs, multi-WAN failover, zone andobject-based management, loadbalancing, advanced NAT modes, andmore, providing granular configurationflexibility and comprehensive protectionat the administrator’s discretion.Standards-based Voice over IP (VoIP)capabilities provide the highest levels ofsecurity for every element of the VoIPinfrastructure, from communicationsequipment to VoIP-ready devices suchas SIP Proxies, H.323 Gatekeepers andCall Servers.Dell SonicWALL clean Wirelessoptionally integrated into dual-bandwireless models or via Dell SonicWALLSonicPoint wireless access pointsprovides powerful and secure 802.11a/b/g/n 3x3 MIMO wireless, and enablesscanning for rogue wireless accesspoints in compliance with PCI DSS.onboard Quality of Service (QoS)features use industry standard 802.1pand Differentiated Services Code Points(DSCP) Class of Service (CoS)designators to provide powerful andflexible bandwidth management that isvital for VoIP, multimedia content andbusiness-critical applications.Integrated modules support on NSA250M and NSA 250M Wireless-Nappliances reduce acquisition andmaintenance costs through equipmentconsolidation, and add deploymentflexibility.Border Gateway Protocol (BGP)support enables alternate networkaccess paths (ISPs) if one path fails.More concurrent SSL VPN sessions addscalability, while extending End PointControl to Microsoft® Windows® devicesensures anti-malware and firewalls areup-to-date.Best-in-class threat protection Dell SonicWALL deep packetinspection protects against network risks such as viruses, worms, Trojans, spyware, phishing attacks, emerging threats and Internet misuse. Application intelligence and control adds highly controls to prevent data leakage and manage bandwidth at the application level.The Dell SonicWALL Reassembly-Free Deep Packet Inspection (RFDPI) technology utilizes Dell SonicWALL’s multi-corearchitecture to scan packets in real-time without stalling traffic in memory.This functionality allows threats to be identified and eliminated over unlimited file sizes and unrestricted concurrent connections, without interruption.The Dell SonicWALL NSA Series provides dynamic network protection through continuous, automated security updates, protecting against emerging and evolving threats, without requiring any administrator intervention.Dynamic security architectureand managementMobile users32Application intelligence and control Dell SonicWALL Application Intelligence and Control provides granular control, data leakage prevention, and real-time visualization of applications to guarantee bandwidth prioritization and ensure maximum network security and productivity. An integrated feature of Dell SonicWALL Next-Generation Firewalls, it uses Dell SonicWALL RFDPItechnology to identify and control applications in use with easy-to-use pre-defined application categories (such as social media or gaming)—regardless of port or protocol. Dell SonicWALL Application Traffic Analytics provides real-time and indepth historical analysis of data transmitted through the firewall including application activities by user.1Dell SonicWALL clean VPNDell SonicWALL Clean VPN™ secures the integrity of VPN access for remote devices including those running iOS or Android by establishing trust for remote users and these endpoint devices and applying anti-malware security services, intrusion prevention and application intelligence and control to eliminate the transport of malicious threats• The SonicWALL NSA 2400 is ideal for branch office and small- to medium-sized corporate environments concerned about throughput capacity and performance • The SonicWALL NSA 220, NSA 220 Wireless-N, NSA 250M and NSA 250M Wireless-N are ideal for branch office sites in distributed enterprise, small- to medium-sizedbusinesses and retail environmentscentralized policy managementThe Network Security Appliance Series can be managed using the SonicWALL Global Management System, which provides flexible, powerful and intuitive tools to manage configurations, viewreal-time monitoring metrics andintegrate policy and compliancereporting and application traffic analytics,all from a central location.Server Anti-Virusand Anti-SpywareServers anti-threatprotectionVPNVPNClientRemoteAccessUpgradeServiceWeb siteand contentusage control Enforced ClientAnti-Virusand Anti-SpywareClient PCs anti-threat protectionFlexible, customizable deployment options –NSA Series at-a-glanceEvery SonicWALL Network Security Appliance solution delivers Next-Generation Firewall protection, utilizing a breakthrough multi-core hardware design and Reassembly-Free Deep Packet Inspection for internal and external network protection without compromising network performance. Each NSA Series product combineshigh-speed intrusion prevention, file and content inspection, and powerful application intelligence and controlwith an extensive array of advanced networking and flexible configuration features. The NSA Series offers an accessible, affordable platform that is easy to deploy and manage in a wide variety of corporate, branch office and distributed network environments.• The SonicWALL NSA 4500 is ideal for large distributed and corporate central-site environments requiring high throughput capacity and performance • The SonicWALL NSA 3500 is idealfor distributed, branch office and corporate environments needing significant throughput capacity and performanceSecurity services andupgradesGateway Anti-Virus,Anti-Spyware, IntrusionPrevention and ApplicationIntelligence and controlService delivers intelligent,real-time network security protectionagainst sophisticated application layerand content-based attacks includingviruses, spyware, worms, Trojans andsoftware vulnerabilities such as bufferoverflows. Application intelligence andcontrol delivers a suite of configurabletools designed to prevent data leakagewhile providing granular application-level controls along with tools enablingvisualization of network traffic.Enforced client Anti-Virusand Anti-spyware (McAfee)working in conjunction withDell SonicWALL firewalls,guarantees that allendpoints have the latest versions ofanti-virus and anti-spyware softwareinstalled and active.content Filtering Serviceenforces protection andproductivity policies byemploying an innovativerating architecture, utilizingadynamic database to block up to 56categories of objectionable webcontent.Analyzer is a flexible, easyto use web-basedapplication traffic analyticsand reporting tool thatprovides powerful real-time andhistorical insight into the health,performance and security of the network.Virtual Assist is a remotesupport tool that enablesa technician to assumecontrol of a PC or laptopfor the purpose of providingremote technical assistance. Withpermission, the technician can gaininstant access to a computer using aweb browser, making it easy to diagnoseand fix a problem remotely without theneed for a pre-installed “fat” client.Dynamic Support Servicesare available 8x5 or 24x7depending on customerneeds. Features includeworld-class technicalsupport, crucial firmware updates andupgrades, access to extensive electronictools and timely hardware replacementto help organizations get the greatestreturn on their Dell SonicWALLinvestment.Global VPN clientUpgrades utilize a softwareclient that is installed onWindows-based computersand increase workforce productivity byproviding secure access to email, files,intranets, and applications for remoteusers.provide clientlessLinux-based systems. With integratedSSL VPN technology, Dell SonicWALLfirewall appliances enable seamless andsecure remote access to email, files,intranets, and applications from a varietyof client platforms via NetExtender, alightweight client that is pushed onto theuser’s machine.SonicWALL Mobile connect™,a single unified client app forApple® iOS and Google®Android™, provides smartphone andtablet users superior network-levelaccess to corporate and academicresources over encrypted SSL VPNconnections.comprehensive Anti-SpamService (CASS) offerssmall- to medium-sizedbusinesses comprehensiveprotection from spam andviruses, with instant deployment overexisting Dell SonicWALL firewalls. CASSspeeds deployment, eases administrationand reduces overhead by consolidatingsolutions, providing one-click anti-spamservices, with advanced configuration injust ten minutes.Deep Packet Inspection for of SSL-Encrypted traffic (DPI-SSL) transparentlydecrypts and scans both inbound andoutbound HTTPS traffic for threats usingDell SonicWALL RFDPI. The traffic is thenre-encrypted and sent to its originaldestination if no threats or vulnerabilitiesare discovered.Denial of Service attack prevention 22 classes of DoS, DDoS and scanning attacksKey exchange K ey Exchange IKE, IKEv2, Manual Key, PKI (X.509), L2TP over IPSec Route-based VPN Yes (OSPF, RIP)Certificate support Verisign, Thawte, Cybertrust, RSA Keon, Entrust, and Microsoft CA for Dell SonicWALL-to-Dell SonicWALL VPN, SCEP Dead peer detection Yes DHCP over VPN Yes IPSec NAT TraversalYes Redundant VPN gatewayYesGlobal VPN client platforms supported Microsoft Windows 2000, Windows XP, Microsoft Vista 32/64-bit, Windows 7 32/64-bitSSL VPN platforms supportedMicrosoft Windows 2000 / XP / Vista 32/64-bit / Windows 7, Mac 10.4+, Linux FC 3+ / Ubuntu 7+ / OpenSUSEMobile Connect platforms supported iOS 4.2 and higher, Android 4.0 and higherSecurity servicesDeep Packet Inspection Service Gateway Anti-Virus, Anti-Spyware, Intrusion Prevention and Application Intelligence and Control Content Filtering Service (CFS) HTTP URL,HTTPS IP, keyword and content scanning ActiveX, Java Applet, and cookie blocking bandwidth management on filtering categories, allow/forbid lists Gateway-enforced Client Anti-Virus and Anti-Spyware McAfee Comprehensive Anti-Spam Service Supported Application Intelligence Application bandwidth management and control, prioritize or block application and Control by signatures, control file transfers, scan for key words or phrasesDPI SSL Provides the ability to decrypt HTTPS traffic transparently, scan this traffic for threats using Dell SonicWALL’s Deep Packet Inspection technology (GAV/AS/IPS/ Application Intelligence/CFS), then re-encrypt the traffic and send it to its destination if no threats or vulnerabilities are found. This feature works for both clients and workingIP Address assignment Static, (DHCP, PPPoE, L2TP and PPTP client), Internal DHCP server, DHCP relay NAT modes1:1, 1:many, many:1, many:many, flexible NAT (overlapping IPs), PAT, transparent modeVLAN interfaces (802.1q) 25352550200Routing OSPF, RIPv1/v2, static routes, policy-based routing, MulticastQoS Bandwidth priority, maximum bandwidth, guaranteed bandwidth, DSCP marking, 802.1pIPv6Yes AuthenticationXAUTH/RADIUS, Active Directory, SSO, LDAP, Novell, internal user database, Terminal Services, Citrix Internal database/single sign-on users 100/100 Users150/150 Users250/250 Users300/500 Users1,000/1,000 UsersVoIPFull H.323v1-5, SIP, gatekeeper support, outbound bandwidth management, VoIP over WLAN, deep inspection security, full interoperability with most VoIP gateway and communications devicesSystemZone security Yes SchedulesOne time, recurring Object-based/group-based management Yes DDNSYesManagement and monitoring Web GUI (HTTP, HTTPS), Command Line (SSH, Console), SNMP v3: Global management with Dell SonicWALL GMSLogging and reporting Analyzer, Local Log, Syslog, Solera Networks, NetFlow v5/v9, IPFIX with extensions, real-time visualizationHigh availabilityOptional Active/Passive with State SyncLoad balancing Yes, (Outgoing with percent-based, round robin and spill-over); (Incoming with round robin,random distribution, sticky IP, block remap and symmetrical remap)StandardsTCP/IP, UDP, ICMP, HTTP, HTTPS, IPSec, ISAKMP/IKE, SNMP, DHCP, PPPoE, L2TP, PPTP, RADIUS, IEEE 802.3Wireless standards802.11 a/b/g/n, WPA2, WPA, TKIP, 802.1x, EAP-PEAP, EAP-TTLS WAN acceleration supportYesFlash memory32 MB compact Flash 512 MB compact Flash3G wireless/modem * With 3G/4G USB adapter or modem — With 3G/4G USB adapter or modemPower supply 36W external Single 180W ATX power supplyFansNo fan/1 internal fan 2 internal fans 2 fansPower input10-240V, 50-60Hz Max power consumption 11W/15W 12W/16W 42W 64W 66W Total heat dissipation 37BTU/50BTU 41BTU/55BTU 144BTU 219BTU 225BTUCertificationsVPNC, ICSA Firewall 4.1 EAL4+, FIPS 140-2 Level 2, VPNC, ICSA Firewall 4.1, IPv6 Phase 1, IPv6 Phase 2Certifications pending EAL4+, FIPS 140-2 Level 2, IPv6 Phase 1, IPv6 Phase 2 —Form factor 1U rack-mountable/ 1U rack-mountable/ 1U rack-mountable/ and dimensions 7.125 x 1.5 x 10.5 in/ 17 x 10.25 x 1.75 in/ 17 x 13.25 x 1.75 in/18.10 x 3.81 x 26.67 cm 43.18 x 26 x 4.44 cm 43.18 x 33.65 x 4.44 cmWeight 1.95 lbs/0.88 kg/ 3.05 lbs/1.38 kg/ 8.05 lbs/ 3.65 kg 11.30 lbs/ 5.14 kg2.15 lbs/0.97 kg3.15 lbs/1.43 kg WEEE weight V 3.05 lbs/1.38 kg/4.4 lbs/2.0kg/ 8.05 lbs/ 3.65 kg 11.30 lbs/5.14 kg3.45 lbs/1.56 kg4.65 lbs/2.11 kgMajor regulatoryF CC Class A, CES Class A, CE, C-Tick, VCCI, Compliance MIC, UL, cUL, TUV/GS, CB, NOM, RoHS, WEEE Environment 40-105° F, 0-40° C 40-105° F, 5-40° CMTBF 28 years/15 years 23 years/14 years 14.3 years 14.1 years 14.1 yearsHumidity5-95% non-condensing 10-90% non-condensingcertificationsSpecificationsTesting methodologies: Maximum performance based on RFC 2544 (for firewall). Actual performance may vary depending on network conditions and activated services. Full DPI Performance/Gateway AV/Anti-Spyware/IPS throughput measured using industry standard Spirent WebAvalanche HTTP performance test and Ixia test tools. Testing done with multiple flows through multiple port pairs. Actual maximum connection counts are lower when Next-Generation Firewall services are enabled. VPN throughput measured using UDP traffic at 1280 byte packet size adhering to RFC 2544. Supported on the NSA 3500 and higher. Not available on NSA 2400. *USB 3G card and modem are not included. See http://www.Dell /us/products/cardsupport.html for supported USB devices. The Comprehensive Anti-Spam Service supports an unrestricted number of users but is recommended for 250 users or less. With Dell SonicWALL WXA Series Appliance.Network Security Appliance 3500 01-SSC-7016NSA 3500 TotalSecure* (1-year) 01-SC-7033Network Security Appliance 450001-SSC-7012NSA 4500 TotalSecure* (1-year) 01-SC-7032Network Security Appliance 2400 01-SSC-7020NSA 2400 TotalSecure* (1-year) 01-SC-7035Network Security Appliance 250M 01-SSC-9755Network Security Appliance 250M Wireless-N 01-SSC-9757 (US/Canada)Network Security Appliance 250M TotalSecure* 01-SSC-9747Network Security Appliance 250M Wireless-N TotalSecure*01-SSC-9748 (US/Canada)Network Security Appliance 220 01-SSC-9750Network Security Appliance 220 Wireless-N 01-SSC-9752 (US/Canada)Network Security Appliance 220 TotalSecure* 01-SSC-9744Network Security Appliance 220 Wireless-N TotalSecure*01-SSC-9745 (US/Canada)For more information on Dell SonicWALL network security solutions, please visit .*Includes one-year of Gateway Anti-Virus, Anti-Spyware, Intrusion Prevention, andApplication Intelligence and Control Service, Content Filtering Service and Dynamic Support 24x7.Security Monitoring Services from Dell SecureWorks are available for thisappliance Series. For more information, visit /secureworks。
SonicWALL CDP 上线手册

SonicWALL CDP 上线手册网域万通技术部目录1.客户机使用要求 (3)2.查看CDP设备当前IP (3)3.Web方式配置你的CDP (3)4.安装CDP软件 (5)5.注册你的CDP到Mysonicwall账户 (6)6.设定CDP备份策略 (10)7.个人用户备份数据举例 (12)8.个人用户备份Outlook 邮件 (14)9.备份Server级的网络应用 (15)10.常见问题 (15)1.客户机使用要求SonicW ALL CDP产品的管理软件和个人使用CDP备份的Agent软件,可以安装在Windows XP, 2000, 2000 Server or 2003 Server上同时客户机要配有至少10/100 Base-T 以太网网卡。
2.查看CDP设备当前IP新的CDP设备初始IP为192.168.168.169/24。
将客户机IP地址配置为同一网段,用IE 浏览器输入:https://192.168.168.169,先对CDP进行网络配置。
注意:如果发现无法登录CDP,同时也无法ping 通192.168.168.169,可通过设备后面的串口登录设备,查看设备当前IP地址。
串口速率显示当前设备IP地址3.Web方式配置你的CDP(1).IE浏览器输入:https://192.168.168.169输入用户名:admin 密码:password ,可选多种语言界面点击login 登录(2).登陆到管理窗口后,查看功能Network—Setting ,修改CDP网卡IP地址为当前公司局域网地址,使CDP设备可以上网更新新的Firmware。
Default Gateway 为当前网络网关Name Servers 为DNS服务器配置好如图(3). 为确保配置无误,可在Network—Connectivity里面进行网络测试为保证后续设备可以注册到Mysonicwall账户和升级,可选择Ping Register Server 测试,Ping通如图:(4).升级CDP硬件Firmware网络连接无误后,应首先将CDP升级到最新版本的硬件内核点击System—Upgrade 进行硬件内核升级升级过程如下:升级完成后,在System—Status页面可查看当前设备Firmware版本4.安装CDP软件(1).CDP设备使用之前,要注册到Mysonicwall账户,并得到Register Code(激活Mysonicwall账户过程请参照相关文档)▪登录 https://网站,输入你之前注册成功的Mysonicwall账户和密码。
SONICWALL SonicWALL 网络安全设备系列 说明书

灵活和可自定义的部署选项——NSA 系列一览
每一种 SonicWALL NSA 网络安全设 备解决方案都采用了突破性多核硬件 设计以及具有专利的免重组深度包检 测(RFDPITM)技术,针对各种内部 和外部网络保护,提供新一代统一威 胁管理保护,而无需牺牲网络性能。 每一款 NSA 系列产品都融合了高速入 侵防御、文档和内容检测、强大的应 用智能服务控制以及众多先进的、具 有高度灵活性的网络和配置功能。 NSA 系列所采用的平台不仅易用性 强,而且价格合理,便于在各种类型 的企业、分支机构和分布式网络环境 中部署和管理。
强制客户端和服务器防病毒及反间谍软件利用一 个单一的集成客户端为笔记本电脑、台式机及服务 器提供全面的病毒及间谍软件防护,同时还能提供 网络范围内的防病毒及反间谍软件策略、定义及软 件更新的自动强制。
内容过滤服务通过采用创新性的评级架构,利用动 态数据库阻止 56 类令人讨厌的 Web 内容,从而实 现保护及生产力策略的强制。
NSA 系列克服了现有安全解决方案的各种局限性,它能实时地对每一个数据包执行 整体扫描,以检测当前出现的内部及外部威胁。依靠高速多核处理平台,NSA 系列 能执行深度包检测功能,同时不会影响关键网络及应用的性能。
NSA 系列采用了新一代统一威胁管理(UTM)技术来抵御各种攻击,同时具有入 侵防御、防病毒及反间谍软件功能以及 SonicWALL 应用智能服务的应用层控制功 能。NSA 系列利用先进的路由、全状态高可用性以及高速 IPSec 和 SSL VPN 技术 让您的分支机构、中央区域及分布式中小型企业网络倍添安全性、可靠性、功能性 及生产力,同时还将成本及复杂程度降到最低。
■ SonicWALL NSA 4500 是那些需要 高吞吐量和高性能的企业中心站点 和大规模分布式环境的理想选择。
SonicWall Mobile Connect 5.0 用户指南说明书

适用于 Android 的 SonicWall® Mobile Connect 5.0用户指南目录Mobile Connect 简介 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4 Mobile Connect 的工作原理 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4 Mobile Connect 5.0 中的新功能 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4其他功能信息 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5支持的平台 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6 Android 产品支持 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6SonicWall 设备支持 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7需要的网络信息 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7安装和连接 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .8安装 Mobile Connect . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8创建和保存连接 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9创建防火墙或 SMA 100 系列/ SRA 连接 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10创建 SMA 1000 系列/ E 级 SRA 连接 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12启动连接 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13连接到防火墙或 SMA 100 系列/ SRA 设备 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13连接到 SMA 1000 系列/ E 级 SRA 设备 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16配置客户端证书 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22带有 SMA 1000 系列/ E 级 SRA 的客户端证书 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22带有 SMA 100 系列/ SRA 的客户端证书 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 24使用 Mobile Connect 小组件 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26安装并使用快速设置磁贴 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26安装快速设置磁贴 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26使用快速设置磁贴 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28使用应用程序快捷方式 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29设置、书签和文件 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .30设置概述 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 30设置部分 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 31支持部分 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32SMA 1000 系列/ E 级 SRA 的附加设置 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33 URL 控制语法和参数 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34使用 addprofile 命令 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34使用 connect 命令 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35使用 disconnect 命令 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36使用 callbackurl 命令参数 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 36使用书签 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38显示和过滤书签 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 38支持的书签类型 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39使用文件 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42SonicWall Mobile Connect for Android 5.0 用户指南文件类型和策略 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 44应用程序访问控制 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .47关于应用程序访问控制 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 47登录并注册设备 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 48控制应用程序行为 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50连接后查看应用程序列表 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51关于学习模式(仅限管理员) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52监控和故障排除 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .53监控 Mobile Connect . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53 Mobile Connect 故障排除 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56失败的终端控制检查 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57常规故障排除 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 58SonicWall 支持 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .59关于本文档 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 60SonicWall Mobile Connect for Android 5.0 用户指南1Mobile Connect 简介适用于 Android 的 SonicWall® Mobile Connect 这款应用程序可使 Android 设备建立与受 SonicWall 安全设备保护的专用网络之间的安全移动连接。
SonicWall SonicOS 6.5 快速設定手冊说明书

SonicWall™ SonicOS 6.5 快速設定目錄使用 SonicWall 快速設定指南 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4關於快速設定指南 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4在 NAT 啟用時設定固定 IP 位址 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4啟動指南 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5瀏覽指南 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6使用設定指南 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .7設定指南 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7存取設定指南 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9部署方案(僅限無線平台) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9變更管理員密碼 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10時區 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10設定模組化裝置類型 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11設定 3G/4G/LTE . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11設定數據機 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14WAN 容錯移轉撥號連線 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14WAN 網路模式 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15LAN 設定 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 20LAN DHCP 設定 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21調控網域註冊 (僅限無線平台) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22WLAN Radio 設定 (僅限無線平台) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22WLAN 安全設定 (僅限無線平台) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 26WPA/WPA2 模式設定 (僅限無線平台) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27WLAN VAP (虛擬存取點) 設定 (僅限無線平台) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28連接埠指派 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 29設定摘要 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 33設定指南已完成 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 34使用 PortShield 介面指南 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .35 PortShield 介面指南 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 35使用公用伺服器指南 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .39公用伺服器指南 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 39公用伺服器類型 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 40私人網路 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 41伺服器公用資訊 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 42公用伺服器設定摘要 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43使用 VPN 指南 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .45 VPN 指南 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45設定站台對站台 VPN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 45SonicOS 6.5 快速設定建立 WAN GroupVPN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 51使用無線指南 (僅限無線平台) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .56無線指南 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 56調控網域註冊 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57無線 LAN 設定 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 57 WLAN Radio 設定 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 59 WLAN 安全設定 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 62 WPA 模式設定 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 63 WLAN VAP (虛擬存取點) 設定 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 65 WLAN VAP(虛擬存取點)設定 - 建立 VAP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 65 WLAN VAP(虛擬存取點)設定 > WLAN 子網路和區域 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 66無線設定摘要 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67使用 App Rule 指南 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .69 App Rule 指南 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 69應用程式規則原則類型 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 70使用 WXA 設定指南 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .78 WXA 設定指南 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 78入門 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 79介面頁面 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 80啟用加速頁面 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 82群組頁面 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 82 WXA 頁面 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83加速元件 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 84 VPN 頁面 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85路由頁面 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85完成頁面 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 86已簽署 SMB 的 WFS 設定指南 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 86選擇專屬 WXA . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87啟用延伸支援 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87網域詳細資料 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 88加入網域 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89設定共用 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 90設定本機檔案伺服器 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 90設定遠端檔案伺服器 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 91新增網域記錄 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 92完成頁面 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 93SonicWall 支援 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .95關於本文件 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 96SonicOS 6.5 快速設定SonicOS 6.5 快速設定1使用 SonicWall 快速設定指南•第 4 頁「關於快速設定指南」•第 4 頁「在 NAT 啟用時設定固定 IP 位址」•第 5 頁「啟動指南」•第 6 頁「瀏覽指南」關於快速設定指南快速設定提供易於使用的設定指南幫助您進行初始原則和安全性的建立。
SonicWALL PRO 1260产品说明说明书

Easy-to-use wizards simplify even the most complicated tasks, including initial device configuration, VPN set-up and public server configuration
Dead Peer Detection DHCP Over VPN IPSec NAT Traversal Redundant VPN Gateway
30+ Mbps* 25 5 (Upgradeable to 50)
DES, 3DES, AES (128, 192, 256-bit) MD5, SHA-1 Manual Key, PKI (X.509), IKE Yes Yes Verisign®, Thawte, Baltimore, RSA Keon, Entrust®, and Microsoft® CA for SonicWALL-to-SonicWALL VPN Yes Yes Yes, NAT_Tv00 and v03 Yes
Award-winning Global Management System (GMS) provides comprehensive management and reporting tools for simplified configuration, enforcement and management of global security policies, VPN and services, all from a central location
sonicwall快速安装手册配置

SonicWALL 防火墙配置Tunnel Interface VPN简介: SonicWALL 防火墙配置 Tunnel Interface VPN本文适用于:涉及到的 Sonicwall 防火墙Gen5: NSA E7500, NSA E6500, NSA E5500, NSA 5000, NSA 4500, NSA 3500, NSA 2400, NSA 240Gen5 TZ 系列: TZ 100 /W,TZ 200/ W, TZ 210/ Wireless固件/软件版本: SonicOS 5.5.0.0 增强版以及更新版本服务: Route Based VPN(Tunnel Interface VPN)功能与应用使用 Tunnel Interface VPN(基于路由的 VPN)的两个优势:1. 将网络拓扑的配置从 VPN Policy 中独立出来2. 网络流量的路由更加灵活,用户可以自定义 VPN 流量路径配置步骤配置 TZ210W1. 进入 VPN->Settings 页面,点击 Add 按钮2. 在 General 选项卡,Policy Type 选择 Tunnel Interface,IPSec Primary Gateway Name or Address 中输入 VPN 对端的 WAN 口地址,本例中为192.168.160.2433. 在 Proposals 选项卡,VPN 两端保持一致4.进入 Network->Routing 页面,点击 Add 按钮添加一条路由策略,在 Destination选择Create new address object…,如图所示:Interface 选择之前在 VPN->Settings 页面添加的 VPN Policy5. 点击 OK 完成配置6. 配置完成的路由策略如图所示配置 NSA35001. 进入 VPN->Settings 页面,点击 Add 按钮2. 在 General 选项卡,Policy Type 选择 Tunnel Interface,IPSec Primary GatewayName or Address 中输入VPN 对端的WAN 口地址,本例中为192.168.160.2523.进入 Network->Routing 页面,点击 Add 按钮添加一条路由策略,在 Destination选择Create new address object…,如图所示:Interface 选择之前在 VPN->Settings 页面添加的 VPN Policy4. 点击 OK 完成配置5. 配置完成的路由策略如图所示SonicWall防火墙快速安装手册声明:本手册是由深圳市福义轩信息技术有限公司制作,未经深圳市福义轩信息技术有限公司授权严禁传播,一经发现深圳市福义轩信息技术有限公司将保留法律手段.1、将本机网卡地址配置为192.168.168.X (192.168.168.168除外)、子网掩码为:255.255.255.0 网关和DNS暂时不用配置。
为SonicWALL 路由器 配置无线连接 说明书

为SonicWALL路由器配置无线连接无线网络是一把双刃剑。
WLAN对雇员和访客给予授权,但是他们同样也带来了安全风险。
当一系列的无线策略和设备在部署时,有一个非常常见的解决方案,那就是部署SonicWALL 无线设备防火墙。
而本文就是你在配置SonicWALL无线设备时所必须了解的内容。
在这些事例中,我们将使用一台SonicWALL TZ 170 SP无线设备作为范例,因为该型号是我们平时最常遇到的无线路由器,不过这些步骤同样也适用于其他SonicWALL TZ无线设备。
SonicWALL TZ无线路由器SonicWALL的TZ无线路由器提供了很多非无线路由器上所没有的功能。
另外,为了保护局域网,还提供了无线网络攻击检测服务,可以帮助监控未经授权的存取,以及对无线AP 的盗用,以及独立的防火墙来保护无线局域网的无线通讯。
IPSec加密连同WPA一起,对客户端和AP之间的无线通讯进行加密。
如果希望,客户服务可以被配置为热点信息。
另外,SonicWALL无线路由器拥有的一个功能是分布式的WLAN 支持,可以支持SonicPoint卫星AP。
SonicWALL无线路由器支持802.11b和802.11g标准。
在绝大多数SonicWALL设备的安装中,它都是作为AP向网络客户端提供无线连接。
而路由器则通过一个传统的UTP线缆连接到网络上。
为了帮助阻止未经授权的网络访问,无线客户端必须经过SonicWALL的用户级别审核。
该设备同时也支持一系列的安全协议,比如WEP,WPA,以及WPA-EAP。
选择AP的放置位置要配置一个无线网络,选择好无线AP的位置是第一步。
SonicWALL列出了一些优化无线性能的推荐措施:尽可能在离网络中心最近的位置放置无线AP。
这样可以避免无线信号的大幅度衰减。
将AP放置在合适的位置,以尽可能的减少AP发送无线电波到客户端之间所需穿越的墙体或天花板的数目。
尽可能尝试将无线设备放置在每个单元的覆盖范围之内。
SonicWall NSA系列网络安全应用机产品说明说明书

The SonicWall Network Security Appliance (NSA) series providesmid-sized networks, branch offices and distributed enterprises with advanced threat prevention in a high-performance security platform. Combining next-generation firewall technology withour patented* Reassembly-Free Deep Packet Inspection (RFDPI) engine on a multi-core architecture, the NSA series offers the security, performance and control organizations require. Superior threat prevention and performanceNSA series next-generation firewalls (NGFWs) integrate advanced security technologies to deliver superior threat prevention. Our patented single-pass RFDPI threat prevention engine examines every byte of every packet, inspecting both inbound and outbound traffic simultaneously. The NSA series leverages on-box capabilities including intrusion prevention, anti-malware and web/URL filtering in addition to cloud-based SonicWall Capture multi-engine sandboxing service to block zero-day threats at the gateway. Unlike other security products that cannot inspect large files for hidden threats, NSA firewalls scan files of any size acrossall ports and protocols. The security architecture in SonicWall NGFWs has been validated as one of the industry’s best for security effectiveness by NSS Labs for five consecutive years. Further, SonicWall NGFWs provide complete protection by performingfull decryption and inspection of TLS/SSL and SSH encrypted connections as well as non-proxyable applications regardless of transport or protocol. The firewall looks deep inside every packet (the header and data) searching for protocol non-compliance, threats, zero-days, intrusions, and even defined criteria to detect and prevent hidden attacks that leverage cryptography, block encrypted malware downloads, cease the spread of infections, and thwart command and control (C&C) communications and data exfiltration. Inclusion and exclusion rules allow total control to customize which traffic is subjected to decryption and inspection based on specific organizational compliance and/or legal requirements. When organizations activate deep packet inspection functions such as intrusion prevention, anti-virus, anti-spyware, TLS/SSL decryption/inspection and others on their firewalls, network performance often slows down, sometimes dramatically. NSA series firewalls, however, feature a multi-core hardware architecture that utilizes specialized security microprocessors. Combined with our RFDPI engine,this unique design eliminates the performance degradation networks experience with other firewalls.In today’s security environment, it’s not enough to rely on solely on outside parties for threat information. That’s why SonicWall formed its own in-house Capture Labs threat research team more than 15 years ago. This dedicated team gathers, analyzes and vets data from over one million sensors in itsSonicWall Network SecurityAppliance (NSA) seriesIndustry-validated security effectiveness and performance formid-sized networksBenefits:Superior threat preventionand performance• Patented reassembly-free deeppacket inspection technology• On-box and cloud-based threatprevention• TLS/SSL decryption and inspection• Industry-validated securityeffectiveness• Multi-core hardware architecture• Dedicated Capture Labs threatresearch teamNetwork control and flexibility• Powerful SonicOS operating system• Application intelligence and control• Network segmentation with VLANs• High-speed wireless securityEasy deployment, setup andongoing management• Tightly integrated solution• Centralized management• Scalability through multiplehardware platforms• Low total cost of ownershipCapture Threat Network. SonicWall also participates in industry collaboration efforts and engages with threat research communities to gather and share samples of attacks and vulnerabilities. This shared threat intelligence is usedto develop real-time countermeasures that are automatically deployed to our customers’ firewalls.Network control and flexibilityAt the core of the NSA series is SonicOS, SonicWall’s feature-rich operating system. SonicOS provides organizations with the network control and flexibility they require through application intelligence and control, real-time visualization, an intrusion prevention system (IPS) featuring sophisticated anti-evasion technology, high-speed virtual private networking (VPN) and other robust security features.Using application intelligence and control, network administrators can identify and categorize productive applications from those that are unproductive or potentially dangerous, and control that traffic through powerful application-level policies on both a per-user and a per-group basis (along with schedules and exception lists). Business-critical applications can be prioritizedand allocated more bandwidthwhile non-essential applications arebandwidth-limited. Real-time monitoringand visualization provides a graphicalrepresentation of applications, users andbandwidth usage for granular insightinto traffic across the network.For organizations requiring advancedflexibility in their network design,SonicOS offers the tools to segmentthe network through the use of virtualLANs (VLANs). This enables networkadministrators to create a virtualLAN interface that allows for networkseparation into one or more logicalgroups. Administrators create rules thatdetermine the level of communicationwith devices on other VLANs.Built into every NSA series firewall is awireless access controller that enablesorganizations to extend the networkperimeter securely through the use ofwireless technology. Together, SonicWallfirewalls and SonicWave 802.11ac Wave2 wireless access points create a wirelessnetwork security solution that combinesindustry-leading next-generation firewalltechnology with high-speed wireless forenterprise-class network security andperformance across the wireless network.Easy deployment, setup andongoing managementLike all SonicWall firewalls, the NSAseries tightly integrates key security,connectivity and flexibility technologiesinto a single, comprehensive solution.This includes SonicWave wirelessaccess points and the SonicWall WANAcceleration Appliance (WXA) series,both of which are automatically detectedand provisioned by the managingNSA firewall. Consolidating multiplecapabilities eliminates the need topurchase and install point products thatdon’t always work well together. Thisreduces the effort it takes to deploy thesolution into the network and configureit, saving both time and money.Ongoing management and monitoringof network security are handled centrallythrough the firewall or through theSonicWall Global Management System(GMS), providing network administratorswith a single pane of glass from whichto manage all aspects of the network.Together, the simplified deploymentand setup along with the ease ofmanagement enable organizations tolower their total cost of ownership andrealize a high return on investment.SonicWallSonicWave 432iSonicWall NSA 5600The SonicWall NSA 2600 is designed to address the needs of growing small organizations, branch offices and school campuses.The SonicWall NSA 3600 is ideal for branch office and small- to medium-sized corporate environments concerned aboutthroughput capacity and performance.Dual fansPower8 x 1GbEports1GbEmanagementConsoleDualDual fansPower2 x 10GbE12 x 1GbE1GbEmanagement4 x 1GbESFP portsConsoleDualDual fansPower2 x 10GbE 12 x 1GbE1GbEmanagement 4 x 1GbESFP portsConsoleDual The SonicWall NSA 4600 secures growing medium-sizedorganizations and branch office locations with enterprise-class features and uncompromising performance.The SonicWall NSA 5600 is ideal for distributed, branch office and corporate environments needingsignificant throughput.Dual fansPower2 x 10GbE12 x 1GbE 1GbEmanagement4 x 1GbE SPF portsConsole DualNetwork Security Appliance 6600The SonicWall NSA 6600 is ideal for large distributed andcorporate central site environments requiring high throughputcapacity and performance.Dual hotswappable fansPower4 x 10GbE8 x 1GbE 1GbEmanagement 8 x 1GbE SFP ports ConsoleDualReassembly-Free Deep Packet Inspection engineThe SonicWall Reassembly-Free Deep Packet Inspection (RFDPI) is a single-pass, low latency inspection system that performs stream-based, bi-directional traffic analysis at high speed without proxying or buffering to effectivelyuncover intrusion attempts and malwaredownloads while identifying application traffic regardless of port and protocol. This proprietary engine relies onstreaming traffic payload inspection to detect threats at Layers 3-7, and takesnetwork streams through extensive andrepeated normalization and decryption in order to neutralize advanced evasion techniques that seek to confusedetection engines and sneak malicious code into the network.Once a packet undergoes thenecessary pre-processing, including SSL decryption, it is analyzedagainst a single, proprietary memory representation of three signature databases: intrusion attacks, malware and applications. The connection state is then advanced to represent the positionof the stream relative to these databases until it encounters a state of attack, or other “match” event, at which point a pre-set action is taken.In most cases, the connection is terminated and proper logging andnotification events are created. However, the engine can also be configured for inspection only or, in case of application detection, to provide Layer 7 bandwidth management services for the remainder of the application stream as soon as the application is identified.Flexible, customizable deployment options – NSA series at-a-glanceEvery SonicWall NSA firewall utilizes a breakthrough, multi-core hardware design and RFDPI for internal and external network protection without compromising network performance. NSA series NGFWs combine high-speed intrusion prevention, file and content inspection, and powerful application intelligence and control with anextensive array of advanced networking and flexible configuration features. The NSA series offers an affordable platform that is easy to deploy and manage in a wide variety of large, branch office and distributed network environments.NSA series as central-site gatewayNSA series as in-line NGFW solutionPacket Packet assembly-based processSonicWall stream-based architectureCompetitive proxy-based architecture When proxy becomes full or content too large,files bypass scanning.Reassembly-free Deep Packet Inspection (RFDPI)Reassembly-free packet scanning eliminates proxy and content size limitations.Inspection timeLessMoreInspection capacityMinMaxCapture LabsThe dedicated, in-house SonicWall Capture Labs threat research team researches and develops counter-measures to deploy to customer firewalls for up-to-date protection. The team gathers data on potential threats from several sources including our award-winning network sandboxing service, Capture Advanced Threat Protection, as well as more than 1 million SonicWall sensors located around the globe that monitor traffic for emerging threats. Itis analyzed via machine learning using SonicWall's Deep Learning Algorithmsto extract the DNA from the code to see if it is related to any known forms of malicious code.SonicWall NGFW customers benefit from continuously updated threat protection around the clock. New updates take effect immediately without reboots or interruptions. The signatures resident on the appliances are designed to protect against wide classes of attacks, covering tens of thousands of individual threats with a single signature.In addition to the countermeasureson the appliance, NSA appliances alsohave access to SonicWall CloudAV,which extends the onboard signatureintelligence with over 20 millionsignatures. This CloudAV database isaccessed by the firewall via a proprietary,light-weight protocol to augment theinspection done on the appliance. WithCapture Advanced Threat Protection,a cloud-based multi-engine sandbox,organizations can examine suspiciousfiles and code in an isolated environmentto stop advanced threats such as zero-day attacks.Advanced threat protection SonicWall Capture Advanced Threat Protection Service is a cloud-based multi-engine sandbox that extends firewall threat protection to detect and prevent zero-day threats. Suspicious files are sent to the cloud for analysis with the option to hold them at the gateway until a verdict is determined. Themulti-engine sandbox platform, which includes virtualized sandboxing, full system emulation and hypervisor level analysis technology, executes suspicious code and analyzes behavior. When afile is identified as malicious, a hash is immediately created within Capture and later a signature is sent to firewalls to prevent follow-on attacks.The service analyzes a broad rangeof operating systems and file types, including executable programs, DLL, PDFs, MS Office documents, archives, JAR and APK.Capture provides an at-a-glance threatanalysis dashboard and reports, whichdetail the analysis results for files sent tothe service, including source, destinationand a summary plus details of malwareaction once detonated.ProtectionCollectionClassificationCountermeasureL A B SGlobal management and reporting For highly regulated organizations wanting to achieve a fully coordinated security governance, compliance and risk management strategy, SonicWall Global Management System (GMS®) provides administrators a unified, secure and extensible platform to manage SonicWall firewalls, wireless access points and Dell X-Series switches through a correlated and auditable workstream process. GMS enables enterprises to easily consolidate the management of security appliances, reduce administrativeand troubleshooting complexities,and govern all operational aspects ofthe security infrastructure, includingcentralized policy management andenforcement; real-time event monitoring;user activities; application identifications;flow analytics and forensics; complianceand audit reporting; and more. GMS alsomeets the firewall’s change managementrequirements of enterprises through aworkflow automation feature. With GMSworkflow automation, all enterprises willgain agility and confidence in deployingthe right firewall policies, at the righttime and in conformance to complianceregulations. Available in software, cloudand virtual appliance options, GMSprovides a coherent way to managenetwork security by business processesand service levels, dramaticallysimplifying lifecycle management of youroverall security environments comparedto managing on a device-by-devicebasis.Port Expansion Scalability SonicWall GMS Secure Compliance EnforcementFeaturesAround-the-clock security updates New threat updates are automatically pushed to firewalls in the field with active security services, and take effectimmediately without reboots or interruptions.Bi-directional raw TCP inspection The RFDPI engine is capable of scanning raw TCP streams on any port bi-directionally preventing attacks that they tosneak by outdated security systems that focus on securing a few well-known ports.Extensive protocol support Identifies common protocols such as HTTP/S, FTP, SMTP, SMBv1/v2 and others, which do not send data in raw TCP, anddecodes payloads for malware inspection, even if they do not run on standard, well-known ports.Firewall• Stateful packet inspection• Reassembly-Free Deep PacketInspection• DDoS attack protection (UDP/ICMP/SYNflood)• IPv4/IPv6 support• Biometric authentication for remoteaccess• DNS proxy• Threat APISSL/SSH decryption and inspection1• Deep packet inspection for TLS/SSL/SSH • Inclusion/exclusion of objects, groups orhostnames• SSL ControlCapture advanced threat protection1• Cloud-based multi-engine analysis• Virtualized sandboxing• Hypervisor level analysis• Full system emulation• Broad file type examination• Automated and manual submission• Real-time threat intelligence updates • Auto-block capabilityIntrusion prevention1• Signature-based scanning• Automatic signature updates• Bidirectional inspection• Granular IPS rule capability• GeoIP enforcement• Botnet filtering with dynamic list• Regular expression matchingAnti-malware1• Stream-based malware scanning• Gateway anti-virus• Gateway anti-spyware• Bi-directional inspection• No file size limitation• Cloud malware database Application identification1• Application control• Application traffic visualization• Application component blocking• Application bandwidth management• Custom application signature creation• Data leakage prevention• Application reporting over NetFlow/IPFIX• User activity tracking (SSO)• Comprehensive application signaturedatabaseWeb content filtering1• URL filtering• Anti-proxy technology• Keyword blocking• Bandwidth manage CFSrating categories• Unified policy model with app control• Content Filtering ClientVPN• Auto-provision VPN• IPSec VPN for site-to-site connectivity• SSL VPN and IPSec client remote access• Redundant VPN gateway• Mobile Connect for iOS, Mac OSX, Windows, Chrome, Android andKindle Fire• Route-based VPN (OSPF, RIP, BGP)Networking• PortShield• Jumbo frames• IPv6• Path MTU discovery• Enhanced logging• VLAN trunking• RSTP (Rapid Spanning Tree protocol)• Port mirroring• Layer-2 QoS• Port security• Dynamic routing (RIP/OSPF/BGP)• SonicWall wireless controller• Policy-based routing (ToS/metric andECMP)• NAT• DHCP server• Bandwidth management• Link aggregation (static and dynamic)• Port redundancy• A/P high availability with state sync• A/A clustering• Inbound/outbound load balancing• L2 bridge, wire/virtual wire mode,tap mode• 3G/4G WAN failover• Asymmetric routing• Common Access Card (CAC) supportWireless• MU-MIMO• Floor plan view• Topology view• Band steering• Beamforming• AirTime fairness• MiFi extender• Guest cyclic quotaVoIP• Granular QoS control• Bandwidth management• DPI for VoIP traffic• H.323 gatekeeper and SIP proxy supportManagement and monitoring• Web GUI• Command line interface (CLI)• SNMPv2/v3• Centralized management and reporting• Logging• Netflow/IPFix exporting• Cloud-based configuration backup• BlueCoat Security Analytics Platform• Application and bandwidth visualization• IPv4 and IPv6 Management• Dell X-Series switch managementincluding cascaded switches1Requires added subscription.Testing Methodologies: Maximum performance based on RFC 2544 (for firewall). Actual performance may vary depending on network conditions and activated services.Threat Prevention/GatewayAV/Anti-Spyware/IPS throughput measured using industry standard Spirent WebAvalanche HTTP performance test and Ixia test tools. Testing done with multiple flows through multiple port pairs. Threat Prevention throughput measured with Gateway AV, Anti-Spyware, IPS and Application Control enabled.VPN throughput measured using UDP traffic at 1280 byte packet size adhering to RFC 2544. All specifications, features and availability are subject to change.For every 125,000 DPI connections reduced, the number of available DPI SSL connections increases by 750.Active/Active Clustering and Active/Active DPI with State Sync require purchase of Expanded License.Performance optimized mode can provide significant increases in performance without major impact to threat prevention efficacy.*Future use. All specifications, features and availability are subject to change.NSA series ordering information*Please consult with your local SonicWall reseller for a complete list of supported SFP and SFP+ modules© 2018 SonicWall Inc. ALL RIGHTS RESERVED. SonicWall is atrademark or registered trademark of SonicWall Inc. and/or its affiliates SonicWall, Inc.1033 McCarthy Boulevard | Milpitas, CA 95035 Regulatory model numbers:NSA 2600–1RK29-0A9NSA 3600–1RK26-0A2NSA 4600–1RK26-0A3NSA 5600–1RK26-0A4NSA 6600–1RK27-0A5About UsSonicWall has been fighting the cyber-criminal industry for over 25 years, defending small, medium size businesses and enterprises worldwide. Our combination of products and partners has enabled a real-time cyber defense solution tuned to the specific needs of the more than 500,000 businesses in over 150 countries, so you can do more business with less fear.。
SonicWall SuperMassive Series 产品说明说明书

The SonicWall SuperMassive Series is SonicWall’s next-generation firewall (NGFW) platform designed for large networks to deliver scalability, reliability and deep security at multi-gigabit speeds with near zero latency.Built to meet the needs of enterprise, government, education, retail, healthcare and service provider, the SuperMassive Series is ideal for securing distributed enterprise networks, data centers and service providers.The combination of SonicWall’s SonicOS operating system, patented* Reassembly-Free Deep Packet Inspection® (RFDPI) technology and massively multi-core, highly scalable hardware architecture, the SuperMassive 9000 Series deliver industry-leading application control, intrusion prevention, malware protection and TLS/SSL decryption and inspection at multi-gigabit speeds. The SuperMassive Series is thoughtfully designed with power, space and cooling (PSC) in mind, providing the leading Gbps/watt NGFW in the industry for high performance packet and data processing, application control and threat prevention.The SonicWall RFDPI engine scans every byte of every packet across all ports, delivering full content inspection of the entire stream while providing high performance and low latency. This technology is superior to proxy designs that reassemble content using sockets bolted to anti-malware programs, which are plagued with inefficiencies and the overhead of socket memory thrashing, which leads to high latency, low performance and file size limitations. The RFDPI engine delivers full content inspection to eliminate various forms of malware before they enter the network and provides protection against evolving threats — without file size, performance or latency limitations.The RFDPI engine also performs full decryption and inspection of TLS/SSL and SSH encrypted traffic as well asnon-proxyable applications, enabling complete protection regardless of transport or protocol. It looks deep inside every packets (the header and data part) searching for protocol non-compliance, threats, zero-days, intrusions, and even defined criteria to detect and prevent attacks hidden inside encrypted traffic, cease the spread of infections, and thwart command and control (C&C) communications and data exfiltration. Inclusion and exclusion rules allow total control to customize which traffic is subject to decryption and inspection based on specific organizational compliance and/or legal requirements. Application traffic analytics enablethe identification of productive and unproductive application traffic in real time, and traffic can then be controlled through powerful application-level policies. Application control can be exercised on both a per-user and per-group basis, along with schedules and exception lists. All application, intrusion prevention and malware signatures are constantly updated by the SonicWall Capture Labs threats research team. Additionally, SonicOS, an advanced purpose-built operating system, provides integrated tools that allowfor custom application identification and control.SonicWall SuperMassive SeriesUncompromising, high-performance, next-generation firewall protection foryour enterprise network.Benefits:• Get complete breach preventionincluding high performanceintrusion prevention, lowlatency malware protection andcloud-based sandboxing• Gain full granular applicationidentification, controland visualization• Find and block hidden threats withdecryption and inspection of TLS/SSL and SSH encrypted traffic,without performance problems• Scale security performance for10/40 Gbps data centers• Adapt to service-level increasesand ensure network servicesand resources are availableand protected*U.S. Patents 7,310,815; 7,600,257; 7,738,380; 7,835,361SuperMassive 9000 SeriesSeries lineupThe SonicWall SuperMassive 9000 Series features 4 x 10-GbE SFP+, up to 12 x 1-GbE SFP , 8 x 1-GbE copper and 1 GbEmanagement interfaces, with an expansion port for an additional 2 x 10- GbE SFP+ interfaces (future release). The 9000 Series features hot-swappable fan modules and power supplies.SuperMassive 9000 Seriesdisplay port interface4 x 10-GbE SFP+ ports 8 x 1-GbE SFP ports 8 x 1-GbEportsDual USB ports LCD Dual hot-Expansion bay Two hot-swappable,Dual hot-Expansion bayTwo hot-swappable,SD card for future usedisplayport interface SFP+ ports12 x 1-GbE 2 x 80Gb 8 x 1-GbE ports LCDcontrolsReassembly-Free Deep Packet Inspection engineRFDPI is a single-pass, low latency inspection system that performs stream-based, bi-directional traffic analysis at high speed without proxying or buffering to effectively uncover intrusion attempts, malware and identify application traffic regardless of port and protocol. This proprietary engine relies on streaming traffic payload inspection in order to detect threats at Layers3-7. The RFDPI engine takes network streams through extensive and repeated normalization and decryption in orderto neutralize advanced obfuscation andevasion techniques that seek to confusedetection engines and sneak maliciouscode into the network.Once a packet undergoes the necessarypre-processing, including TLS/SSLdecryption, it is analyzed against a singleproprietary memory representationof multiple signature databases:intrusion attacks, malware, botnet andapplications. The connection stateis then advanced to represent theposition of the stream relative to thesedatabases until it encounters a state ofattack, or other “match” event, at whichpoint a preset action is taken. In mostcases, the connection is terminatedand proper logging and notificationevents are created. However, the enginecan also be configured for inspectiononly or, in the case of applicationdetection, to provide Layer 7 bandwidthmanagement services for the remainderof the application stream as soon as theapplication is identified.PacketPacket assembly-based processSonicWall stream-based architecture Competitive proxy-based architectureWhen proxybecomes full orcontent too large,files bypassscanning.Reassembly-free Deep Packet Inspection (RFDPI)Reassembly-free packetscanning eliminates proxyand content size limitations.Inspection timeLess MoreInspection timeLess MoreInspection capacityMin MaxExtensible architecture for extremescalability and performanceThe RFDPI engine is purposely designedwith a keen focus on providing securityscanning at a high level of performance,to match both the inherently paralleland ever growing nature of networktraffic. When combined with multi-coreprocessor systems, this parallelism-centric software architecture scales upperfectly to address the demands ofdeep packet inspection (DPI) at hightraffic loads. The SuperMassive platformrelies on processors that, unlike x86,are optimized for packet, crypto andnetwork processing while retainingflexibility and programmability in thefield — a weak point for ASICs systems.This flexibility is essential when new codeand behavior updates are necessaryto protect against new attacks thatrequire updated and more sophisticateddetection techniques. Another aspectof the platform design is the uniqueability to establish new connectionson any core in the system, providingultimate scalability and the ability todeal with traffic spikes. This approachdelivers extremely high new sessionestablishment rates (new conn/sec) whiledeep packet inspection is enabled — akey metric that is often a bottleneck fordata center deployments.Advanced threat protection SonicWall Capture Advanced Threat Protection Service1 is a cloud-based multi-engine sandbox that extends firewall threat protection to detect and prevent zero-day threats. Suspicious files are sent to the cloud for analysis with the option to hold them at the gateway until a verdict is determined. Themulti-engine sandbox platform, which includes virtualized sandboxing, full system emulation and hypervisor level analysis technology, executes suspicious code and analyzes behavior. When afile is identified as malicious, a hash is immediately created within Capture and later a signature is sent to firewalls to prevent follow-on attacks.The service analyzes a broad rangeof operating systems and file types, including executable programs, DLL, PDFs, MS Office documents, archives, JAR and APK.Capture provides an at-a-glance threat analysis dashboard and reports, which detail the analysis results for files sent to the service, including source, destination and a summary plus details of malwareaction once detonated.Capture LabsThe dedicated, in-house SonicWall Capture Labs threats researchteam researches and develops countermeasures to deploy to customer firewalls for up-to-date protection. The team gathers data on potential threat data from several sources including our award-winning network sandboxing service, Capture Advanced Threat Protection, as well as more than 1 million SonicWall sensors located around the globe that monitor traffic for emerging threats. It is analyzed via machine learning using SonicWall's Deep Learning Algorithms to extract the DNA from the code to see if it is related to any known forms of malicious code. SonicWall NGFW customers with the latest security capabilities are provided continuously updated threat protection around the clock. New updates take effect immediately without rebootsor interruptions. The signatures onthe appliances protect against wideclasses of attacks, covering up to tensof thousands of individual threats with asingle signature.In addition to the countermeasures onthe appliance, SuperMassive firewallsalso have access to the SonicWallCloudAV1, which extends the onboardsignature intelligence with tens ofmillions of signatures, and growingby millions annually. This CloudAVdatabase is accessed by the firewall viaa proprietary, lightweight protocol toaugment the inspection done on theappliance. With Capture AdvancedThreat Protection1, a cloud-based multi-engine sandbox, organizations canexamine suspicious files and code in anisolated environment to stop advancedthreats such as zero-day attacks.Protection CollectionClassificationCountermeasureL A B S1 Requires added subscriptionApplication intelligence and control Application intelligence informs administrators of application traffic traversing their network so they can schedule application controls based on business priority, throttle unproductive applications and block potentially dangerous applications. Real-time visualization identifies traffic anomalies as they happen, enabling immediate countermeasures against potential inbound or outbound attacks or performance bottlenecks.SonicWall Application Traffic Analytics1 provide granular insight into application traffic, bandwidth utilization and security threats, as well as powerful troubleshooting and forensicscapabilities. Additionally, secure single sign-on (SSO) capabilities ease the user experience, increase productivity and reduce support calls. Management of application intelligence and controlis simplified by the intuitive web-based interface.Global management and reportingFor highly regulated organizations wanting to achieve a fully coordinated security governance, complianceand risk management strategy,the optional SonicWall Global Management System1 (GMS®) provides administrators a unified, secure and extensible platform to manage SonicWall firewalls, wireless access points and switches through a correlated and auditable workstream process. GMS enables enterprises to easily consolidate the managementof security appliances, reduce administrative and troubleshooting complexities, and govern all operational aspects of the security infrastructure, including centralized policy management and enforcement; real-time event monitoring; user activities; application identifications; flow analytics and forensics; compliance and audit reporting; and more. GMS also meets the firewall change management requirementsof enterprises through a workflowautomation feature. With GMS workflowautomation, all enterprises will gainagility and confidence in deploying theright firewall policies, at the right timeand in conformance to complianceregulations. GMS provides a coherentway to manage network security bybusiness processes and service levels,dramatically simplifying lifecyclemanagement of your overall securityenvironments as compared to managingon a device-by-device basis.• Centralizedmanagement• Error-free policymanagement• Strong access control• Comprehensiveaudit trails• PCI, HIPAA, SOXreport templates• Lower operating costsPort Expansion ScalabilitySonicWall GMS Secure Compliance EnforcementBenefits1 Requires added subscription1 Requires added subscriptionFirewall• Stateful packet inspection• Reassembly-Free DeepPacket Inspection• DDoS attack protection(UDP/ICMP/SYN flood)• IPv4/IPv6 support• Biometric authentication forremote access• DNS proxy• Threat APISSL/SSH decryption and inspection2• Deep packet inspection for TLS/SSL/SSH • Inclusion/exclusion of objects, groupsor hostnames• SSL ControlCapture advanced threat protection2• Cloud-based multi-engine analysis• Virtualized sandboxing• Hypervisor level analysis• Full system emulation• Broad file type examination• Automated and manual submission • Real-time threat intelligence updates • Auto-block capabilityIntrusion prevention2• Signature-based scanning• Automatic signature updates• Bi-directional inspection engine• Granular IPS rule set• GeoIP enforcement• Botnet filtering with dynamic list• Regular expression matchingAnti-malware2• Stream-based malware scanning• Gateway anti-virus• Gateway anti-spyware• Bi-directional inspection• No file size limitation• Cloud malware database Application identification2• Application control• Application traffic visualization• Application component blocking• Application bandwidth management• Custom application signature creation• Data leakage prevention• Application reporting overNetFlow/IPFIX• User activity tracking (SSO)• Comprehensive applicationsignature databaseWeb content filtering2• URL filtering• Anti-proxy technology• Keyword blocking• Bandwidth management forCFS categories• Unified policy model with app control• Content Filtering ClientVPN• Auto-provision VPN• IPSec VPN for site-to-site connectivity• SSL VPN and IPSEC client remote access• Redundant VPN gateway• Mobile Connect for iOS, Mac OSX, Windows, Chrome, Android andKindle Fire• Route-based VPN (OSPF, RIP, BGP)Networking• Dynamic LAG using LACP• PortShield• Jumbo frames• Path MTU discovery• Enhanced logging• VLAN trunking• Port mirroring• Layer-2 QoS• Port security• Dynamic routing (RIP/OSPF/BGP)• SonicWall wireless controller1• Policy-based routing(ToS/metric and ECMP)• NAT• DHCP server• Bandwidth management• Link aggregation (static and dynamic)• Port redundancy• A/P high availability with state sync• A/A clustering• Inbound/outbound load balancing• L2 bridge, wire/virtual wire mode, tapmode, NAT mode• 3G/4G WAN failover (not onSuperMassive 9800)• Asymmetric routing• Common Access Card (CAC) supportWireless• MU-MIMO• Wireless planning tool• Band steering• Beamforming• AirTime fairness• MiFi extender• Guest cyclic quotaVoIP• Granular QoS control• Bandwidth management• DPI for VoIP traffic• H.323 gatekeeper and SIP proxy supportManagement and monitoring• Web GUI• Command-line interface (CLI)• SNMPv2/v3• Centralized management and reportingwith SonicWall Global ManagementSystem (GMS)2• Logging• Netflow/IPFix exporting• Cloud-based configuration backup• BlueCoat security analytics platform• Application and bandwidth visualizer• IPv4 and IPv6 Management• LCD management screen• Dell X-Series switch management11 Not supported on SonicOS 6.2.7.72 Requires added subscriptionSuperMassive 9000 Series system specificationsTesting Methodologies: Maximum performance based on RFC 2544 (for firewall). Actual performance may vary depending on network conditions and activated services. Full DPI/Gateway AV/Anti-Spyware/IPS throughput measured using industry standard Spirent WebAvalanche HTTP performance test and Ixia test tools. Testing done with multiple flows through multiple port pairs. VPN throughput measured using UDP traffic at 1280 byte packet. Applies to SuperMassive 9200, 9400 and 9600. SuperMassive 9800 UC APL certification is pending. Supported on SonicOS 6.1 and 6.2. For every 125,000 DPI connections reduced, the number of available DPI SSL connections increases by 750. *Future use. All specifications, features and availability are subject to change.SuperMassive 9000 Series ordering information*Please consult with a SonicWall SE for a complete list of supported SFP and SFP+ modules.© 2017 SonicWall Inc. ALL RIGHTS RESERVED. SonicWall is atrademark or registered trademark of SonicWall Inc. and/or its affiliates in the U.S.A. and/or other countries. All other trademarksand registered trademarks are property of their respective owners.SonicWall, Inc.5455 Great America Parkway | Santa Clara, CA 95054 Refer to our website for additional information. About UsSonicWall has been fighting the cyber-criminal industry for over 25 years, defending small, medium size businesses and enterprises worldwide. Our combination of products and partners has enabled a real-time cyber defense solution tuned to the specific needs of the more than 500,000 global businesses in over 150 countries, so you can do more business with less fear.Datasheet-SuperMassive-US-VG-MKTG476。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
S o n i c W A L L防火墙标准版配置
SonicWall标准版网络向导配置 (1)
SonicWall标准版规则向导配置 (7)
SonicWall标准版一般规则向导配置 (7)
SonicWall标准版服务器规则向导配置 (12)
SonicWall标准版一般规则直接配置 (15)
SonicWall标准版服务器1对1 NAT配置 (19)
SonicWall标准版透明模式配置 (20)
SonicWall标准版网络向导配置
首次接触SonicWALL防火墙设备,我们将电源接上,并开启电源开关,将X0口和你的电脑相连(注:请用交叉线),SonicWALL防火墙默认的IP地址为192.168.168.168,我们也可以通过setuptool.exe这个小工具探知SonicWALL防火墙的IP地址。
如图所示:
当网线和电源等都连接好之后,我们设置一下本机的IP地址,以便和SonicWALL防火墙处于同一个网段。
如图所示:
设置好IP地址后,我们在IE浏览器的地址栏输入SonicWALL防火墙的IP地址,
点next,提示我们是否修改管理员密码,
暂时不修改,点next,提示我们修改防火墙的时区,我们选择中国的时区。
点next,提示我们设置WAN口的地址获取类型,这时候,我们需要和ISP相联系,并选择相关的类型,这里以静态地址为例:
我们点next,输入相关的信息,IP地址、掩码、网关、DNS服务器等,如果不知道此处该如何设置,请和你的ISP联系。
点next,提示我们设置LAN口的IP和掩码,我们根据自己的规划和网络的实际情况设置,此处我没有修改。
点next,防火墙询问我们在LAN口是否开启DHCP server的功能,并是否是默认的网段,我们可根据实际情况做调整,决定开始或关闭,以及网段地址等,如下图:
点next,防火墙将把前面做的设置做一个摘要,以便我们再一次确认是否设置正确,如果有和实际不符的地方,可以点back返回进行修改。
按照我们前面的设置,防火墙开启了NAT 模式——即在LAN内的PC访问WAN外的互连网时,将转换其IP地址为WAN口地址。
点apply,设置生效。
并需要重起防火墙,点restart重起。
当把配置做好以后,我们将防火墙的X1口接到ISP进来的网线上,将X0口接到内网交换机上。
这时,我们可以找一个内网的机器,测试是否可以访问外网:
SonicWall标准版规则向导配置
SonicWall标准版一般规则向导配置
当我们做如上的配置后,此时的策略是默认允许内网的所有机器可以任意的访问外网,为了符合公司的安全策略,我们如果要相关的安全策略,限制一些访问的协议。
通常有两种做法:一种是先限制所有的协议,在逐步开放需要访问的协议;另一种是先开放所有的协议,在逐步禁止不能访问的协议。
我们以第二种方式为例。
选择firewall,
我们可以点右上角的rule wizard,也可以直接点add,以使用规则向导为例:
点next,我们选择规则类型,public server rule我们在DMZ或者LAN有服务器,需要对外发布,——即允许来自WAN口的PC可以访问我们的服务器而做的端口映射。
而general rule则是前面强调的针对LAN或DMZ区访问外网的权限控制。
我们以此为例,选择general rule。
点next,选择我们需要控制的协议和服务,此处我们选择web,
点next,选择针对的web的执行的动作,由于默认已经有一条规则允许内网可以任意的访
问外网,我们为控制内网的访问权限,选择deny,同时还有TCP连接超时的时间,默认是15分钟,可根据需要做修改。
如无特殊要求,可使用默认设置。
点next,此处设置此规则的源接口和源IP地址,根据需要做一配置,我们此处选择LAN的192.168.168.12做规则控制。
点next,此处选择规则生效的目的接口和目的IP地址,*表示任意的地址。
点next,此处设置规则生效的时间,默认是一直生效,可根据需要修改时间。
点next,相关的规则设置的选项已经设置好了。
点apply,规则生效,在规则列表的最上面一条,即是我们刚才通过规则向导设置的规则。
SonicWall标准版服务器规则向导配置
假如我们在DMZ区或者LAN区还有一些服务器需要对外发布,那么,我们也需要添加相关的规则,以允许来自外网的访问。
以web服务为例,通过规则向导来配置,如下:
点rule wizard,
点next,选择public server rule
点next,我们选择需要对外发布的服务类型,此处选择web,输入服务器的IP地址,并选择其所处的接口,此处选择LAN口,
点next,
点apply,规则生效
我们可以看到,在规则列表中的第4条即为我们添加的规则。
在我们添加这条规则的背后,服务器的IP地址被映射成了WAN口的地址,并自动添加了相关的NAT配置。
SonicWall标准版一般规则直接配置
通过前面的向导配置,我们可以发现,添加一般规则时,其配置过程相对复杂,因为,我们可以直接添加策略,而不用通过向导配置。
如下,
在firewall 界面,的access rules下,直接点add:
我们以禁止内网IP为192.168.168.12的PC不允许访问外网的ftp服务为例,在action 处,选择deny,在service处选择ftp,source处选择LAN口的,在地址段处添写IP,192.168.168.12,
在destination处选择WAN口,地址保留*号,表示任意地址。
如果我们不需要做进一步的设置,如规则生效时间,带宽等,可直接点OK生效,如果需要做进一步设置,选advanced,修改我们需要设置的时间,
如果要做带宽限制,选择bandwidth,将enable勾选,并输入相关的带宽控制要求。
(注:由于本条规则deny,所以带宽控制不可用)
点OK,规则生效。
规则列表中的第2条即为我们添加的规则。
SonicWall标准版服务器1对1 NAT配置
如果我们有多余的公网IP地址,并且希望服务器可以单独拥有一个公网IP地址,即我们需要对服务器做1对1的NAT时,我们需要通过如下的配置来实现:
点network,选择 one-to-one NAT,我们勾选enable one-to-one NAT
点add,
在弹出的界面中,我们输入相关的服务器IP和公网IP,在range length处,我们可以添入相关的数字,如果只有1个服务器,添1,如果添入的数字为其他数字如5,则,私网地址处,将从我们添入的地址开始,公网地址处,也将从我们添入的公网地址开始,一一对应,并递增直到段的长度结束。
点OK后,NAT生效。
如下图。
在做完1对1的NAT后,我们选择到firewall界面,选择access rules,来添加相关的规则,
同样可通过rule wizard来做向导配置,其界面如前所述。
SonicWall标准版透明模式配置
如果需要将防火墙部署成透明模式,在我们登陆防火墙时,在弹出的向导设置页面选择cancel,
输入默认的帐号密码
点login,然后选择networks
我们点LAN对应的编辑条,并在IP地址处输入给予防火墙的IP地址,并把掩码做相应的修改,以符合实际情况。
点OK,配置生效。
此时,我们选择WAN口的模式,选择透明模式,
选择后生效,
点WAN口的编辑图标,修改WAN口的网关地址,以便可以和其他网络进行通讯。
点intranet,
在这里,如果我们选择第二个选项,点add后,添加的IP将属于LAN,其于的IP属于WAN 口;如果我们选择第三个选项,点add后,添加的IP将属于WAN,其于的IP属于LAN口。
我们可以选择一个添加比较简单的选项。
以选择第二个选项为例。
点add,添加属于LAN口的IP,
点OK,添加的IP生效。
如果还有别的地址需要添加,我们可以点add,进一步添加。
即完成网络方面的配置,如果需要做规则等,可通过前面的叙述配置。
