Fortinet-飞塔防病毒解决方案白皮书
飞塔防火墙03-部署防病毒

如何启用防病毒——保护内容表与策略
• 启用防病毒 • 设置超过阈 值的文件就 不再进行病 毒扫描(推 荐1M) • 是否过滤掉 超过阈值的 文件 • 防火墙策略 中调用
如何启用防病毒——测试防病毒是否启用
• 找到 • 点击右上角
• 点击此处
如何启用防病毒——报警信息
config antivirus service "http" set port 80 set port 8080 set scan-bzip2 disable set uncompnestlimit 12 set uncompsizelimit 10 end
在缓冲过程传递部分数据给用户——用户 舒适选项
防病毒
Course 201 v4.0
UTM菜单项——病毒检查
与病毒检测相关的菜单项
如何启用防病毒——查看病毒列表
进入“反病毒>配置>病毒列表”,查看病毒列表。 FortiGuard病毒定义列表在每次FortiGate设备接收到新的AV定义时进行更新。 FortiGuard中心病毒信息大全中FortiGate设备可以查看检测到的病毒、蠕虫、 特洛伊木马以及其他网络威胁的信息描述。
• 系统>维护>FortiGuard——设置 自动升级
如果你购买了推送式升级服 务的话,则可以选择该选项
通常FortiGate会自动寻找升级服务器 ,但是在此处可以指定升级服务器
如何设置病毒库升级——手工升级
• 系统>状态>许可证信息
如何设置非标准端口的病毒扫描
• 防病毒系统只扫描已知的端 口 (e.g. “http” = tcp/80) • 但是,它可以添加其他端口 • 仅仅当一个命令被触发的时 候才会激活 (文件传输)
飞塔硬件防火墙FGT30-100
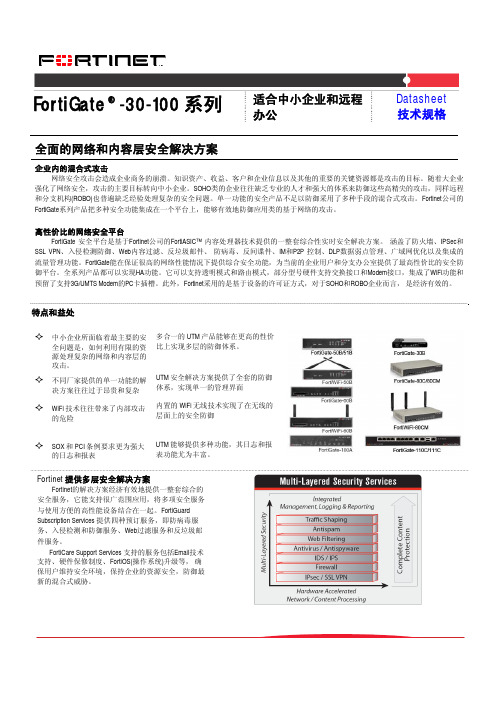
FortiGate® -30-100 系列适合中小企业和远程办公 Datasheet 技术规格全面的网络和内容层安全解决方案企业内的混合式攻击网络安全攻击会造成企业商务的崩溃。
知识资产、收益、客户和企业信息以及其他的重要的关键资源都是攻击的目标。
随着大企业强化了网络安全,攻击的主要目标转向中小企业。
SOHO类的企业往往缺乏专业的人才和强大的体系来防御这些高精尖的攻击,同样远程和分支机构(ROBO)也普遍缺乏经验处理复杂的安全问题。
单一功能的安全产品不足以防御采用了多种手段的混合式攻击。
Fortinet公司的FortiGate系列产品把多种安全功能集成在一个平台上,能够有效地防御应用类的基于网络的攻击。
高性价比的网络安全平台FortiGate 安全平台是基于Fortinet公司的FortiASIC™ 内容处理器技术提供的一整套综合性实时安全解决方案。
涵盖了防火墙、IPSec和SSL VPN、入侵检测防御、Web内容过滤、反垃圾邮件、防病毒、反间谍件、IM和P2P 控制、DLP数据弱点管理、广域网优化以及集成的流量管理功能。
FortiGate能在保证很高的网络性能情况下提供综合安全功能,为当前的企业用户和分支办公室提供了最高性价比的安全防御平台。
全系列产品都可以实现HA功能。
它可以支持透明模式和路由模式,部分型号硬件支持交换接口和Modem接口,集成了WiFi功能和预留了支持3G/UMTS Modem的PC卡插槽。
此外,Fortinet采用的是基于设备的许可证方式,对于SOHO和ROBO企业而言,是经济有效的。
特点和益处中小企业所面临着最主要的安全问题是,如何利用有限的资源处理复杂的网络和内容层的攻击。
多合一的UTM产品能够在更高的性价比上实现多层的防御体系。
不同厂家提供的单一功能的解决方案往往过于昂贵和复杂UTM安全解决方案提供了全套的防御体系,实现单一的管理界面WiFi技术往往带来了内部攻击的危险内置的WiFi无线技术实现了在无线的层面上的安全防御SOX和PCI条例要求更为强大的日志和报表UTM能够提供多种功能,其日志和报表功能尤为丰富。
FortiClient 和 Fortinet 安全基础架构的集成高级端点保护白皮书说明书

WHITE PAPERFigure 1: When deployed as part of the Fortinet Security Fabric, FortiClient can take advantage of threat-intelligence sharing to expand network visibility, detect attacks in real time, and coordinate threat response.Integrated Endpoint and Network Security Open Ecosystem Array A critical starting point to integrating endpoint and network security is an integrated, openecosystem of security solutions. Woven together to scale and adapt as business demandschange, the Security Fabric enables companies to address the full spectrum of challengesacross the expanding attack surface. Accordingly, part of the Fortinet Security Fabric,FortiClient works alongside common antivirus (AV) and endpoint detection and response (EDR)solutions. For example, users of Microsoft Windows Defender can augment their endpointprotection with FortiClient capabilities such as sandbox integration and VPN support.Endpoint Visibility and ManagementFortiClient integrates endpoint and network security, providing seamless visibility andcontrol across and between all endpoints, enforcing conditional access, and deliveringautomated threat response. It provides end-to-end visibility for both hosts and endpointdevices to help organizations harden endpoints and boost their security posture.Specifically, FortiClient simplifies endpoint management by centralizing key security tasks,identifying vulnerabilities, and correlating events to improve incident reporting. Followingare the ways FortiClient integrates endpoint and network security to provide transparentvisibility and management:Telemetry-based risk awarenessFortiClient establishes risk awareness by sharing real-time endpoint telemetry with networksecurity through the Fortinet Security Fabric. As part of this process, FortiAnalyzer collectslogs from FortiClient and other network components and incorporates global threatintelligence from FortiGuard Labs into a single pane of glass.Vulnerability managementFortiClient includes vulnerability scanning that allows IT infrastructure teams to discover andprioritize unpatched vulnerabilities. FortiClient also creates an applications inventory. Thisnot only provides visibility into software license utilization but also helps identify potentiallyunwanted applications and outdated applications for which patching support may not beavailable. All of this results in a reduced endpoint attack surface.Centralized provisioning and monitoringFortiClient allows IT infrastructure teams to deploy endpoint security software and performcontrolled upgrades to thousands of clients in just minutes, avoiding the time drain associated with manual deployment and minimizing human error. This seamless process is aided by FortiClient API integration with Microsoft Active Directory.Alert verificationIntegration between FortiClient and other security elements across the Security Fabric enables cross-referencing of events with network traffic. This feature helps to verify and triage alerts, enhancing the “signal-to-noise” ratio for incident reporting. As a result, IT infrastructure teams spend less time investigating false positives and are able to focus on identifying actual threats more accurately.Proactive risk managementOrganizations can augment their FortiClient endpoint security with an optional subscription to the FortiGuard Security Rating Service. The Security Rating Service helps IT infrastructure leaders improve their security in measurable ways and report their risk posture to executive management, boards of directors, and auditors. The Security Rating Service helps organizations understand where they stand in relation to peer organizations and accepted standards and provides actionable insights that IT infrastructure leaders can take to improve theorganization’s risk posture.Secure Remote AccessFortiClient offers IT infrastructure teams a powerful toolset for securing access by remote users, including conditional access empowered through endpoint and network integration and streamlined virtual private network (VPN 0 access) (Figure 2).Figure 2: FortiClient supports both IPsec and SSL VPN connections to provide secure remote access to remote users and branch offices.The FortiClient console allows administrators to provision VPN configurations and endpoint users to set up new VPN connections, saving time and reducing configuration errors.Conditional access empowered through endpoint and network integrationLeveraging conditional access capabilities in FortiClient, the IT infrastructure team is able to control endpoint access dynamically through virtual groups to determine access rights. Thus, as an example, only users in a finance group can retrieve information from the organization’s financial database. Yet, users in sales or engineering groups are unable to do so. Accordingly, FortiGate next-generation firewalls (NGFWs) retrieve and use FortiClient virtual groups to create firewall policies that enforce conditional access. This process is automatable since FortiGate NGFWs and FortiClient are integrated within the Security Fabric.Security enforcement also extends beyond virtual group access by automating conditional access: If an endpoint is out of compliance according to a preset condition (e.g., the device lacks a critical iOS or Android patch for a specified timeframe), FortiClient will assignthe user to a security-risk virtual group. By virtue of this designation, FortiGate NGFWs deny access to all resources except for internet connectivity. Once a user installs the required patch, FortiClient removes the user from the security-risk group, thereby restoring previous access rights.Streamlined VPN accessSecure sockets layer (SSL)/transport layer security (TLS) and IPsec VPN features inFortiClient provide secure and reliable access to corporate networks and applicationsfrom virtually any internet-connected remote location. FortiClient simplifies the remoteuser experience with built-in auto-connect and always-up VPN capability. Integration withFortiAuthenticator allows network teams to add two-factor authentication for additionalaccess security. In addition, FortiClient integrates with Microsoft Active Directory to facilitateauthentication and VPN logins using Active Directory credentials.Proactive Threat Response FortiClient leverages machine learning (ML)-based anti-malware, exploit prevention, web filtering, and sandbox integration to proactively protect endpoint devices. Here, FortiClient shares real-time threat intelligence across and between all endpoints and network securitycomponents to enable enterprisewide protection, regardless of where the threat is firstdiscovered. Threat-intelligence sharing facilitates automated responses, containingoutbreaks in near real time—thereby reducing time to containment and resolution.Automated remediationFortiClient automatically quarantines suspect devices to limit the spread of infection toother parts of the network. It also supports automatic patching for software applications andoperating systems, even when the endpoint is offline. These features help IT infrastructureleaders to ensure compliance with increasingly strict data privacy standards and industryregulations.Web filteringFortiClient delivers web security, web content filtering, and granular Software-as-a-Service(SaaS) control. In this case, it monitors browser and web application activity and enforcespolicies. FortiClient web filtering supports a variety of user devices, including Windows, Mac,iOS, Android, and Chromebook. Additionally, with FortiClient, IT infrastructure teams can seta consistent policy for devices when they are on and off the network. This enables them toavoid the time and expense needed to deploy and manage a third-party web filtering solutionor web proxy tools.Sandbox integrationFortiClient submits unknown or suspicious objects to FortiSandbox for detailed analysis.Once FortiSandbox identifies the threat, it notifies all FortiClient-protected endpoints andother security elements within the Security Fabric (Figure 3). This proactive approachallows IT infrastructure leaders to pinpoint and block unknown and zero-day threatsquickly and easily. ConclusionFortiClient facilitates deep integration between endpoint security and network security, especially when deployed as part of the FortinetSecurity Fabric. This integration strengthens not only endpoint security but also network security. At the same time, automation of endpoint security workflows and threat-intelligence sharing enables IT infrastructure leaders to streamline operations. This helps them deal with the cybersecurity skills shortage.65Copyright © 2019 Fortinet, Inc. All rights reserved. Fortinet , FortiGate , FortiCare and FortiGuard , and certain other marks are registered trademarks of Fortinet, Inc., and other Fortinet names herein may also be registered and/or common lawtrademarks of Fortinet. All other product or company names may be trademarks of their respective owners. Performance and other metrics contained herein were attained in internal lab tests under ideal conditions, and actual performance and other results may vary. Network variables, different network environments and other conditions may affect performance results. Nothing herein represents any binding commitment by Fortinet, and Fortinet disclaims all warranties, whether express or implied, except to the extent Fortinet enters a binding written contract, signed by Fortinet’s General Counsel, with a purchaser that expressly warrants that the identified product will perform according to certain expressly-identified performance metrics and, in such event, only the specific performance metrics expressly identified in such binding written contract shall be binding on Fortinet. For absolute clarity, any such warranty will be limited to performance in the same ideal conditions as in Fortinet’s internal lab tests. Fortinet disclaims in full any covenants, representations, and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise revise this publication without notice, and the most current version of the publication shall be applicable. Fortinet disclaims in full any covenants, representations, and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise revise this publication without notice, and the most current version of the publication shall be October 18, 2019 12:47 AM In addition to the above, FortiClient gives IT infrastructure teams end-to-end risk visibility based on threat-intelligence sharing and full control of security policies and responses. At the same time, it offers flexible, powerful remote access security with conditional admission and VPN support. Finally, FortiClient delivers proactive threat response with integrated, automated remediation, sandbox integration, web filtering, and interoperability with common AV and EDR solutions.Figure 3: By integrating with the Security Fabric, FortiClient automates the process of quarantining suspicious or compromised endpoints.1James Hasty, et al., “Advanced Endpoint Protection Test Report ,” NSS Labs, March 5, 2019. 2“Security Value Map: Advanced Endpoint Protection (AEP),” NSS Labs, March 2019. 3Jim Parise, “Heads Up: Cybercriminals Are Businesspeople ,” CFO, August 2, 2019.4Dionisio Zumerle, “The Long-Term Evolution of Endpoints Will Reshape Enterprise Security ,” Gartner, May 1, 2019.5“Empower Security Analysts Through Guided EDR Investigation: Bridging The Gap Between Detection And Response ,” Forrester, May 2019.6 Navanwita Sachdev, “The many motives of hackers and how much your data is worth to them ,” The Sociable, July 1, 2019.。
飞塔产品整体解决方案

18
FortiGate中型设备
适合中型企业和大型企业分支机构的安全设备
FGT-1240B
• 高性能多功能安全 • 更高性价比和同级别更高接口密度
FGT-1000C FGT-800C FGT-600C FGT-300C FGT-200B FGT-200B-POE
主要好处:
✓ 高速防火墙和 IPSec VPN 性能 ✓ 高速应用控制 ✓ 加速的 IPS/AV 性能 ✓ 板载存储器,用于 WAN 优化、本地报 告和归档*
数据库安全
FortiDB
数据库安全审计
安全云服务
FortiGuard 实时安全云 服务网络
终端访问安全
FortiClient
终端访问安全
统一安全管理
FortiAuthenticator
统一认证管理
FortiManager
集中安全管理
FortiAnalyzer
集中安全审计
7
7
Fortinet实现网络安全的全方位立体防御
FGT-240D
4 Gbps 6us 3.2M
FGT-280D (-POE)
4Gbps 2us 3.2M
每秒新建会话 IPSec VPN
IPS (HTTP) 防病毒 (代理/流 )
22k 450 Mbps
950 Mbps 300/700Mbps
22k 450 Mbps
950 Mbps 300/700Mb ps 40 x GE RJ45
300-600 Series Mid Range
800-1000 Series
3000 Series
5000 Series High End
PoE, High Density GE
FORTINET FortiGate 产品技术手册

美国FORTINET 公司系列产品技术手册V4.0版2004年7月北京办事处地址:北京市海淀区中关村南大街2号数码大厦B座903室 邮编100086 电话:(010)8251 2622 传真:(010)8251 2630网站:Fortinet 内部资料2004年目 录1. 公司介绍.................................................................................................................................................................4 1.1 公司背景............................................................................................................................................................4 1.2 产品简介............................................................................................................................................................4 1.3 关键技术............................................................................................................................................................4 1.4 总裁介绍............................................................................................................................................................5 1.5 业务范围 (5)2. 产品系列介绍 (6)2.1 F ORTI G ATE -50A................................................................................................................................................7 2.2 F ORTI G ATE -60...................................................................................................................................................7 2.3 F ORTI G ATE -100.................................................................................................................................................7 2.4 F ORTI G ATE -200.................................................................................................................................................8 2.5 F ORTI G ATE -300.................................................................................................................................................8 2.6 F ORTI G ATE -400.................................................................................................................................................9 2.7 F ORTI G ATE -500.................................................................................................................................................9 2.8 F ORTI G ATE -800...............................................................................................................................................10 2.9 F ORTI G ATE -1000............................................................................................................................................10 2.10 F ORTI G ATE -3000............................................................................................................................................10 2.11 F ORTI G ATE -3600............................................................................................................................................11 2.12 F ORTI G ATE -4000............................................................................................................................................12 2.13 F ORTI G ATE -5000............................................................................................................................................13 2.14 F ORTI M ANAGER 系统. (13)3. 产品功能和特点 (14)3.1 病毒防火墙新理念........................................................................................................................................14 3.2 F ORTI G ATE 系列.............................................................................................................................................14 3.3 基于网络的防病毒........................................................................................................................................15 3.4 分区域安全管理的特色...............................................................................................................................15 3.5 VPN 功能..........................................................................................................................................................15 3.6 防火墙功能.....................................................................................................................................................16 3.7 独特的内容过滤.............................................................................................................................................16 3.8 基于网络IDS 的/IDP 功能.............................................................................................................................16 3.9 VPN 远程客户端软件....................................................................................................................................17 3.10F ORTI ASIC F 技术和ORTI OS 操作系统 (17)3.10.1 高性能并行处理................................................................................................17 3.10.2 实时体系结构...................................................................................................17 3.10.3 实时内容级智能................................................................................................17 3.10.4 提供分区间安全的虚拟系统支撑.......................................................................18 3.10.5 高可用性(HA)...................................................................................................18 3.11 F ORTI G ATE 提供整体解决方案. (18)4.FORTIGATE 防火墙典型应用方案..................................................................................................................19 4.1 中小型企业防火墙应用...............................................................................................................................19 4.2 中大型企业防火墙应用...............................................................................................................................20 4.3 分布型企业防火墙应用...............................................................................................................................21 4.4 校园网安全部署应用....................................................................................................................................22 5. 销售许可证和认证证书. (23)5.1 公安部硬件防火墙销售许可证..................................................................................................................23 5.2公安部病毒防火墙销售许可证 (23)5.3中国信息安全产品测评认证中心 (24)5.4计算机世界推荐产品奖 (24)5.5中国 (24)5.6ICSA认证证书 (25)5.7在美国获奖 (26)6.技术支持方式 (27)6.1北京办事处技术支持 (27)6.1.1 技术支持、售后服务及人员培训 (27)6.1.2 服务组织结构 (27)6.1.3 技术咨询和培训 (27)6.2F ORTI P ROTECT防护服务中心 (27)6.3F ORT P ROTECT安全防护小组 (28)6.4F ORTI P ROTECT推进式网络 (28)7.说明 (29)7.1附件:公司与产品介绍资料 (29)7.2联系我们 (29)Fortinet 内部资料2004年1.公司介绍1.1 公司背景美国Fortinet(飞塔)公司是新一代的网络安全设备的技术引领厂家。
FortiGate 100D参数白皮书

1 年的硬件保修
90 天的 FortiCare Web 技术支持
90 天的软件升级
售后支持指南请参阅 /support/support/support.html
FortiGate100D 是为中小企业设计的
UTM 构建安全的 VPN 体系
FortiOS 4.3 创造安全的新概念
FortiOS 4.3 作为 FortiGate 的核心, 是以安全、性能和可靠为目标开 发的。该专用系统采用了强大的 FortiASIC 芯片提高安全性和性能。 FortiOS 可以实现多种安全功能, 如防火墙、VPN、入侵检测与防 御、反恶意软件、反垃圾邮件、 web 过滤、应用控制、数据防泄漏 和终端系统控制。
防病毒吞吐(代理/流扫描) 虚拟域(缺省/最大) 支持 AP 数 支持 FortiToken 数 不限用户数 高可用性
FortiGate-100D
22 22 16 1/2 1 16GB
2500/1000/200Mbps 37us
290Kpps 2.5M 22K
10,000/5000 450Mbps 1500/1500
虚拟专用网(VPN) ICSA 认证(IPSec) PPTP, IPSec, L2TP, GRE SSL VPN***
SSL VPN 支持通道和代理模式 SSL VPN 用户界面自定义 支持 DES, 3DES, AES 256 加密算法, SHA-1 / MD5 认证 SCEP 简单证书登记协议 OCSP 在线证书状态协议 Hub and Spoke 星型 VPN DPD 通道状态检测 NAT 穿越,XAUTH 认证 静态 VPN,动态拨号 VPN 支持
虚拟域为安全服务提供商提供解决方案
虚拟域可以将FortiGate划分出若干逻辑的 虚拟设备,每个虚拟设备可以单独设置路 由、防火墙策略、内容层的防病毒、IPS等功 能。安全服务商可以为多个企业组织部署一 个FortiGate,将其划分成若干逻辑设备分配给 不同的企业组织,并且为其设置相应逻辑设 备的管理权限,这样每个被服务的企业可以 单独地管理安全设置,查看相应的日志信 息。
FortiGate 100D参数白皮书

虚拟域为安全服务提供商提供解决方案
虚拟域可以将FortiGate划分出若干逻辑的 虚拟设备,每个虚拟设备可以单独设置路 由、防火墙策略、内容层的防病毒、IPS等功 能。安全服务商可以为多个企业组织部署一 个FortiGate,将其划分成若干逻辑设备分配给 不同的企业组织,并且为其设置相应逻辑设 备的管理权限,这样每个被服务的企业可以 单独地管理安全设置,查看相应的日志信 息。
用户对于可疑恶意软件威胁保证响应时间的需求,
Fortinet还可以提供FortiGuard防病毒安全订阅服务的 “高级响应” 服务级别。与用户购买的服务保证协
议(SLA)一起,这
种高级服务合同可为用户提供一个直接联系Fortinet全球威胁科研团队的渠道。
标准FortiCare支持服务 包括以下服务内容:
1 年的硬件保修
90 天的 FortiCare Web 技术支持
90 天的软件升级
售后支持指南请参阅 /support/support/support.html
FortiGate100D 是为中小企业设计的
UTM 构建安全的 VPN 体系
技术指标
硬件参数 10/100/1000 (总接口数) 最大网络接口数 10/100/1000 LAN(交换接口) USB(客户端/服务器) RJ-45 串口 内部存储
系统性能 防火墙吞吐量(1518/512/64UDP) 网络延时 防火墙吞吐量 PPS
并发会话
新建会话 防火墙策略数(全局/虚拟域) IPSec 吞吐量(512 字节) 网关到网关的 IPSec VPN 通道数 (全局/虚拟域) 客户端到网关 IPSec VPN 通道数 SSL VPN 用户数(推荐最大) SSL VPN 吞吐量 IPS 吞吐
Fortinet技术白皮书

Fortinet技术白皮书Version 5.02006.03目录1.公司介绍 (5)2.产品定位 (5)2.1产品理念 (5)2.2产品概述 (6)2.3系统结构 (6)3.功能列表 (7)4.FORTIGATE系列性能 (9)4.1F ORTI G A TE-50A (9)4.2F ORTI G A TE-60 (9)4.3F ORTI W I F I-60 (10)4.4F ORTI G A TE-100 (10)4.5F ORTI G A TE-100A (10)4.6F ORTI G A TE-200 (11)4.7F ORTI G A TE-200A (11)4.8F ORTI G A TE-300 (11)4.9F ORTI G A TE-300A (12)4.10F ORTI G ATE-400 (12)4.11F ORTI G ATE-400A (13)4.12F ORTI G ATE-500 (13)4.13F ORTI G ATE-500A (13)4.14F ORTI G ATE-800 (14)4.15F ORTI G ATE-800F (14)4.16F ORTI G ATE-1000A/FA2 (15)4.17F ORTI G ATE-3000 (15)4.18F ORTI G ATE-3600 (16)4.19F ORTI G ATE-5020 (16)4.20F ORTI G ATE-5050 (17)4.21F ORTI G ATE-5140 (17)4.其他产品 (19)4.1F ORTI M ANAGER-集中安全管理平台 (19)4.2F ORTI C LIENT-主机安全软件 (19)4.3F ORTI A NALYZER-集中日志报告系统 (19)4.4F ROTI R EPORTER -安全分析报告软件 (19)4.5F ORTI M AIL -高性能邮件安全平台 (19)5.FORTIGUARD 安全服务系统 (21)5.1F ORTI P ROTECT -全球安全防护服务体系 (21)5.3F ORTI G UARD入侵检测和防御服务 (21)5.4F ORTI G UARD W EB内容过滤服务 (21)5.5F ORTI G UARD反垃圾邮件服务 (21)6. FORTINET产品特色 (21)6.1F ORTINET提供了网络安全的整体解决方案 (21)6.2F ORTINET产品技术领先 (22)6.3F ORTINET产品功能齐全 (22)6.4F ORTINET产品线完善 (22)6.5F ORTI G A TE产品应用面广适合各种领域 (22)6.6F ORTINET设计的ASIC独特 (22)6.7F ORTI G A TE作为防病毒网关产品支持多种I NTERNET协议 (22)6.8F ORTI G A TE支持中文管理界面 (22)6.9F ORTINET有高端产品适合运营服务供应商应用 (23)6.10F ORTINET服务体系完善 (23)6.11F ORTI G ATE产品性价比高 (23)6.12F ORTINET产品可以为企业带来良好的投资回报率 (23)6.13F ORTINET产品在中国得到广泛应用 (23)6.14F ORTINET获得多项国家权威机构论证证书和销售许可证 (23)6.15F ORTINET产品在中国业界获得多项奖项 (23)7.竞争分析 (25)1.F ORTI G ATE作为防火墙产品与其它同类产品相比优势突出 (25)2.F ORTINET在网络安全市场上竞争对手甚少 (25)3.F ORTINET公司引领统一威胁管理市场潮流 (25)4.市场需要UTM的理由 (25)8. 销售许可 (26)9.典型应用 (27)9.1中小型企业防火墙应用 (27)9.2中大型企业防火墙应用 (28)9.3分布型企业防火墙应用 (28)9.4校园网络安全部署应用 (29)10.成功案例 (30)10.1应用案例1 (30)10.2应用案例2 (30)10.3应用案例3 (31)10.4应用案例4 (32)10.5应用案例5 (32)10.6应用案例6 (33)10.7应用案例7 (34)11.核心技术 (37)11.1技术要点 (37)11.2病毒防火墙新理念 (37)11.3基于网络的IDP功能 (37)11.4集成VPN的安全网关 (37)11.5ASIC加速和实时操作系统 (37)11.6独特的内容过滤 (38)11.7动态威胁防御系统 (38)11.8分区域安全管理 (38)12.技术支持 (39)1.公司介绍美国Fortinet(飞塔)公司是新一代网络安全防御技术的前锋,引导着网络信息安全发展的潮流。
Fortinet-飞塔BYOD+解决方案白皮书

使用Fortinet解决方案应对BYOD带来的问题和挑战介绍携带自己的办公设备(BYOD:Bring Your Own Device)一直是倍受争议话题,如何在员工使用BYOD在生产效率的提高与BYOD给企业带来安全风险之间实现最佳的平衡。
许多员工已经在使用自己的设备进行工作。
最近的一项行业调查表明,将近75%的员工已经使用自有设备访问与工作相关的数据。
目前一代的员工将BYOD看作一种权利,安全行业的专家也将BYOD视为他们最关心的安全问题之一,在政策与技术之间寻找平衡点确保个人设备以一种可实施的方式进行使用是非常具有挑战性的。
本文将探究一些与BYOD使用相关的优势,也提出一些BYOD在部署方面的关键安全问题。
最后,探讨基于网络的BYOD 部署以及和为什么网络是BYOD实施的最好场所。
BYOD带来的安全挑战BYOD有很多直观的优势:提高了生产率,降低生产成本,提高了员工的认可。
虽说这些好处相当具有吸引力,随之也有很多与部署BYOD环境相关的严重挑战。
与BYOD相联系的挑战可以迫使公司机构严格评估其安全状况和基础设施,必须考虑应对以下每一个挑战。
失控许多员工发现,对于移动设备往往不同于如同桌面设备必须遵守严格的公司政策。
利用这个政策的空白,许多员工使用其移动设备访问视频流文件和其他应用程序,这些应用程序的使用有悖于公司的标准政策。
随着移动设备提供了一种可以绕过公司规定的应用程序访问限制和员工行为准则,对企业网络的带宽造成了压力且降低了生产率。
增加了数据丢失的潜在可能性由于移动设备的使用不受传统的实体企业的规定的限制,潜在的数据丢失显著增加。
移动设备的用户面临的威胁包括恶意软件感染的风险,因疏忽或是恶意共享关键业务数据,甚至是移动设备丢失或被盗。
此外,公共环境中还存在以窃取无防护数据为唯一目的的流氓无线网络。
设备间不一致的安全政策另一个挑战是公司机构因不同的移动设备而不能指定有效统一的移动设备安全访问管理政策。
Fortinet-飞塔IPS入侵防御解决方案白皮书

1.系统威胁导言今天各个组织所面临的最大的苦恼是,如何描述所遇到的攻击和购买什么样的技术手段来发防御它们。
例如:“应用层”究竟意味着什么,“蠕虫攻击、蠕虫和恶意软件有什么区别”。
“应用”或者称为“应用层”是最容易混乱的概念了。
例如,谁是“应用层”攻击的制造者?或者说制造商的产品具有“应用层”防护能力,意味着什么?从某种意义上讲,OSI的七层模型仅仅是对网络通讯进行模块化描述(见图1)。
换句话说,它仅仅是停留在网络通讯的模型层面上,而对实际通讯(比如电子邮件、web浏览器和SAP)等没有什么实际作用。
即使象“SMTP”和“HTTP”这些通常被当作典型“应用层”的,实际上也是要确保高级别层次的应用能够和各种环境进行通讯。
但是,更为复杂的是,确实确实有一些“网络层应用”是符合七层协议的,比如说Telnet和FTP。
但是这些协议却更加深入地证明了“应用层”这个概念是多么地容易被误解的或错误地使用。
OSI的模型从信息安全角度来看这表明什么呢?与该文章相关的关键点在于:●在解释“应用层的攻击”和“应用层的防御”的概念时候一定要小心,尤其是在市场材料中使用。
目前没有定义好的或通用的概念。
●OSI的“应用层”确实是和网络层和传输层有所区别的,他们主要体现于网络通讯。
例如,攻击对以下应用仍旧是有危害的:各种工具类应用的代码和命令(比如浏览器、web服务器、数据库),各种可以重新封包或修改的软件(比如Word和SAP),以及个人数据(比如个人保健信息等)。
最有效和最精确的方法是:面向通讯的攻击和防御方法,面向文件的攻击和防御方法,面向数据的攻击和防御方法。
2. 攻击的生命周期分析与前面讨论概念不同的是,本章节将清楚地描述攻击工作方式。
和澄清“应用层”和“基于网络”的概念一样,讨论攻击的方法和作用对采用什么样的手段阻止它们是非常重要的。
我们认为攻击一般是由以下四步组成的:1、传递是指一个攻击如何从源到目标的。
本地执行的攻击往往是要靠手工导入和加载执行感染文件的。
Fortinet-飞塔NGFW下一代网络安全防御白皮书

FORTINET-下一代网络安全防御下一代网络安全防御1FORTINET-下一代网络安全防御目录概览 ............................................................................................................................................................................... 3 简介 ............................................................................................................................................................................... 4 企业与服务提供商面临的安全挑战.............................................................................................................................. 5 旧有的威胁从未远离 ............................................................................................................................................. 5 加速演变的新威胁................................................................................................................................................. 5 基于 web 的攻击增加数据泄漏的损失 ................................................................................................................ 5 Web2.0 应用 ........................................................................................................................................................ 6 传统防火墙不再有效 ..................................................................................................................................... 6 迁移到下一代网络 ......................................................................................................................................... 7 安全演进的下一步:新一代安全平台 .......................................................................................................................... 7 下一代安全技术 .................................................................................................................................................... 7 应用控制 ........................................................................................................................................................ 8 入侵检测系统(IPS) .................................................................................................................................. 11 数据丢失防御(DLP) ................................................................................................................................. 13 网页内容过滤............................................................................................................................................... 15 双栈道 IPv4 与 IPv6 支持.............................................................................................................................. 16 集成无线控制器 ........................................................................................................................................... 16 集中管理 ...................................................................................................................................................... 17 核心安全技术 ...................................................................................................................................................... 18 防火墙 - 状态流量检测与数据包过滤 ..................................................................................................... 18 虚拟专用网 (VPN)........................................................................................................................................ 18 URL 过滤 ....................................................................................................................................................... 19 反病毒/反间谍软件 ..................................................................................................................................... 20 反垃圾邮件 .................................................................................................................................................. 22 结论 ............................................................................................................................................................................. 23 关于 Fortinet ................................................................................................................................................................ 24 关于 FortiOS................................................................................................................................................................. 242FORTINET-下一代网络安全防御概览自从几年以前Gartner提出“下一代防火墙”的概念以来,许多网络安全厂商争先恐后将下一代防火墙作 为所生产防火墙产品的一个种类,但这却造成了不同的结果。
Fortinet飞塔 Fortigate 防火墙 功能介绍

Fortinet飞塔Fortigate 防火墙功能介绍集成了一个5个端口的交换机,免除使用外5个端口的交换机,免除使用外接HUBFortiGate-60CWAN 链接,支持冗余的互联网连接,集成了一个病毒防火墙对小型办公室是理想的解决办法。
FortiGate的特点是双可以自动由For了流量控制,增强了网络流量能力。
FortiGate 在容量、速率、和性价比方面对小型商务,远程商店、宽带通信点都是理想的。
FortiGate或交换机,使得联网的设备直接连接到对小型办公和分支机构企业提供All-in-One保护。
FortiGate 病毒防火墙是专用的基于ASIC的硬件产品,在网络边界处提供了实时的保护。
基于Fortinet的FortiASIC? 内容处理器芯片,FortiGate平台是业界唯一能够在不影响网络性能情况下检测病毒、蠕虫及其他基于内容的安全威胁,甚至象Web过滤这样的实时应用的系统。
系统还集成了防火墙、VPN、入侵检测、内容过滤和流量控制功能,实现具有很高性价比、方便的和强有力的解决方案。
双DMZ端口对web 或邮件服务器提供了额外的网络区域,和对网络流量的增加的控制具有单个安全和接入策略无线接入点增加tiProtectTM网络实现攻击数据库的更新,它提供持续的升级,以保护网络不受最新的病毒,蠕虫,木马及其他攻击,随时随地的受到安全保护。
产品优势:1.提供完整的网络保护:综合了基于网络的病毒防御,Web和EMail内容过滤,防火墙,VPN,动态入侵检测和防护,流量管理和反垃圾邮件功能检测和防止1300多种不同的入侵,包括DoS和DDoS攻击,减少了对威胁的暴露基于ASIC的硬件加速,提供优秀的性能和可靠性2.保持网络性能的基础下,在邮件,文件转送和实时Web流量中消除病毒,蠕虫,和灰色软件/间谍软件的威胁3.自动下载更新病毒和攻击数据库,同时可以从FortiProtectTM网主动“推送”更新容易管理和使用—通过图形化界面初始建立,快速简便地配置指南指导管理通过FortiManagerTM集中管理工具,管理数千个FortiGate设备。
Fortinet与NTT合作白皮书:保护企业网络和物理资产说明书

Operational Technology, Secure no MoreWHITE PAPERSecure your cyber and physical assetswith Fortinet and NTTThe mindsetthe same vulnerabilities.Challenges of OT cybersecurityProtecting converged OT/ITThe rise in recent cyberattacks on industrial production facilities highlights the difficulties faced by OT teams.The new realities of OT/IT network convergence necessitate a new cybersecurity approach based on the real world.It’s not that we can’t connect the dots. We can’t see the dots.The head of the US National Security Agency and Cyber Criminal Command in March 2021.3““House dividedAccept the new realitiesConverge OT/IT networks to match threatsOutdated cybersecurity toolsCybersecurity skills gapComplacencyThe tsunami on the horizonA converged OT/IT security requires a common strategy and an integrated approach. Unfortunately, in most organizations, OT and IT teams are separated and report to different CXOs.OT/IT teams need to set aside old notions that air-gapped networks provide good protection, especially whencoupled with firewalls. Today, sophisticated intruders can access OT networks through endpoints such as sensors, gauges, laptops, or even USB devices. Enterprises need to fortify firewalls with web apps firewalls, anomaly detection, AI/ML real-time monitoring and alerts.Cybersecurity threats are a great equalizer that does not differentiate between IT and OT environments. Enterprises need to adapt their security teams and posture to meet the daily threats.Security teams are overwhelmed by the high attack frequency and lack of funding or the threat detection and response tools needed to perform their work efficiently.The pool of available security talent is getting smaller, and OT teams have to compete against better-funded and more attractive opportunities.Despite the known insider risks, 54% of organizations do not have an insider risk response plan!4The arrival of 5G will revolutionize factory floors, thereby expanding the industrial surface of attack. Furthermore, the worldwide electric grid is about to experience a massive surge of demand driven by demand for renewable energy and electric vehicles (EVs). Morgan Stanley anticipates renewables in the U.S. growing to 60% of energy generation and EVs making up 33% of the market by 2040.5Fortinet and NTT have you coveredSecuring your connected universe requires a holistic view of cybersecurity risks, a new matching security posture and architecture, and an integrated physical and cyber protection solution. Fortinet and NTT managed security solutions offer all the elements enterprises need for a converged OT/ITcybersecurity protection. NTT’s services include 24/7 monitoring, detection and response to potential threats. The managed services free your IT teams to focus on business initiatives.Understand risksAdopt a comprehensive security postureNTT security consulting services identify security vulnerabilities associated with the OT and IT networks and map the risk to the operational level. Several bodies establish standards for guiding the industry, including the National Institute of Standards and Technology , theEuropean Union’s Directive on Security of Network and Information Systems (NIS Directive), and the International Electrotechnical Commission (IEC 62443). The standard benchmarks help identify risks and how they relate to OT environments. Fortinet is an active contributing member of industry standards groups, including NIST. These benchmarks and the identified risks guide organizations in prioritizing steps that can quickly reduce risks and maintain operational uptime.A robust security posture offers access management, protection for all assets and visibility into the entire edge-to-cloud environment, including industrial IoT endpoints. Fortinet and NTT managed security solutions provide the tools enterprises need to secure their cyber and physical footprints. Authenticated access to all endpoints and computers is an essential part of Fortinet’s security architecture. NTT security solutions offer visibility into the security network state by passively observing the OT network, creating an updated and comprehensive inventory of everynetwork segment, device, application version, connectivity between devices and security score. Also, NTT performs real-time behavior analytics that identifies normal and abnormal activities. These capabilities enhance the harmful malware and othermanagement (SIEM) to record allcommands and activities.ongoing operations.Fortinet Security FabricPurdue enterprise referencearchitecture modelBroad visibility of the entire digital attack surface to better manage risk Integrated solution that reduces the complexity of supporting multiple point productsAutomated workflows to increase speed of operations and responseFabric Management CenterOpenEcosystemFortiGuard ThreatIntelligence1. October 2020. Cybersecurity & Infrastructure Security Agency, “Alert AA20-275A).”2, 4. Code42 December 2020. “code42 Data Exposure Report.” 3. WSJ PRO Cybersecurity March 26, 2021. “NSA Chief Says Recent Hacks Expose Limits of U.S. Cyber Protections.”5. CNBC PRO March 31, 2021. “Electric grid spending is an “overlooked” opportunity, says Morgan Stanley.”Sources:NTT and Fortinet partner together to provide a wide range of expertise to help organizations protect their OT/IP networks and operations:The Fortinet-NTT partnership enables organizations to protect their converged OT systems from IT networks’ endemic threats while reducing disruptions and lowering operating expenses. Fortinet and NTT help their customers assess, design, plan, implement and manage their converged OT/IT plans. The offerings includemanaged services for monitoring and management to keep customers’ OT/IT environments safe from bad actors.Fortinet provides the technology solution through the Fortinet Security Fabric, an integrated and automated security architecture that delivers visibility, control and real-time traffic analysis to neutralize threats proactively.NTT offers managed services that protectcustomers’ data and infrastructure. The managed services cover monitoring and managed security services that reduce risks and minimize the impact of malicious cyberattacks.NTT provides business and technology advisory services delivered by cybersecurity experts with industry-specific knowledge of OT networks. NTT teams also bring regional experience that enables clients to plan and execute their cybersecurity journey with minimal to no business risks.NTT offers the OT Cybersecurity ExcellenceCenter to identify best fit technologies, implement and monitor systems for ongoing integrity and protection.The rising and more sophisticated cyber threats require new OT/IT converged cybersecurity strategies that protect digital assets, defend against threats and rapidly recover from successful attacks.““Next stepsFor additional information on how to start your journey to a converged OT and IT cybersecurity operations, visit and explore how you can protect your cyber and physical assets.。
Fortinet-飞塔应用控制(上网行为管理)及流量控制解决方案白皮书

应用及流量控制白皮书基本于深度检测的应用监控和管理互联网经过十几年的高速发展,已经成为人们工作、生活中不可缺少的一部分。
聊天软件、网页视频、P2P下载、网上炒股、VoIP语音等丰富多彩的互联网应用给我们带来便利的同时,也带来了很多问题,如员工上班时间使用与工作无关的应用严重影响了工作效率、P2P下载让原本有限的带宽资源更加紧张等,如何对互联网应用进行监视和控制、如何提高带宽利用率已成为大多数企业急待解决的问题。
目前互联网上的应用很多都在浏览器中或其它应用程序中运行,很多应用还可以使用多种端口传输,因此,通过在防火墙上禁止或允许应用的TCP和UDP端口来控制应用的方法已不再有效。
FortiOS的深度检测功能可以基于包特征识别应用,阻止有害应用、保障正常应用的同时,还可以对每个单独的应用进行限速和认证。
FortiOS 的应用控制功能结合基于内容的UTM功能——包括入侵检测、防病毒、信息漏洞防护等,可以为企业提供深层次的、最全面的安全防护。
FortiOS应用控制传统防火墙只能通过源/目的IP地址、端口识别网络流量,并通过这些属性来对流量进行控制。
但如果需要对某种应用产生的流量进行控制,传统的方法则无能为力。
每种应用产生的流量都有其相应的独一无二的特征值,FortiOS应用控制功能可以识别出这些特征值,并通过特征来定位流量是来自哪种应用。
应用控制功能基于入侵保护系统的协议解码器实现,相比入侵保护功能,应用控制功能界面更友好、功能更丰富。
目前,FortiOS的可以识别1000种以上的应用、服务及协议。
FortiOS应用控制技术可以提供用户网络内各种应用占用网络带宽情况的图形报表。
通过分析可视化图形报表,可对非法的应用进行阻止,对允许通过的应用进行流量限制、病毒检测、入侵保护或其它可以针对应用开启的UTM功能。
应用程序使用排行榜根据当前流量情况实时展现,除了可显示应用的流量、会话排名外,还可以显示应用流量对应的源、目的IP地址。
Fortinet整体安全解决方案

骇客
入侵 蠕虫
病毒 间谍软件
僵尸网络 垃圾邮件
恶意 URL Web 过滤
恶意 App
高级持续性威胁
防火墙
VPN
IPS
反恶意软件
反垃圾邮件
应用控制
高级威胁防御
Layer 1-2
内容& 应用 (Layer 3-7)
不断增长的性能需求
8
Increasing Damage
Fortinet 优势 – 安全
FortiGuard Labs 威胁研究
单一 管理控制台
管理
通用平台 支持所有型号 按需部署,无论形态与位置 统一的一致性策略
防火墙 VPN 应用控制 IPS Web 过滤 反恶意软件 WAN 加速
整合的基础设施
敏感信息防泄漏
WiFi 控制器 高级威胁防御 SaaS 网关
更快更强壮地 应对威胁, 降低风险发生带来 的危害 更少的 管理开销, 更简单 运维基础设施
17
FortiGate NGFW产品线
FortiGuard
FortiOS 性能 & 接口
FortiGate 30 – 90
FortiGate 100 – 900
FortiGate 1000 – 5000
低端桌面式
中端机架式(1-2U)
万兆及超万兆(2U以上)
18
FortiGate低端桌面系列
FG-94D-POE FWF-90D/POE
入侵防御 服务
Web 安全 服务
数据库安全 服务
+ 其他威胁情报共享来源
漏洞管理 服务
IP 信誉 服务
全球Fortinet设备 足迹
9
Fortinet技术产品安全解决方案白皮书说明书

WHITE PAPERFortinet Technology Cybersecurity Solutions Bolstering Protection Against Advanced Cyber Threats While Optimizing Cost and EfficiencyThe Fortinet Security Fabric delivers a broad, integrated, and automated security solution with end-to-end integration that brings centralized visibility and control spanning the entire organization. A wide array of Fortinet cybersecurity tools integrates seamlessly into the Security Fabric, along with dozens of third-party solutions delivered by Fabric Partners. Additionally, an open ecosystem and extensive application programming interface (API) tools give technology companies options regarding the integration of other tools. This provides flexibility for an ever-changing threat landscape and a rapidly evolving marketplace.The Security Fabric is built on the foundation of FortiGate Next-Generation Firewalls (NGFWs) and artificial intelligence (AI)-powered threat intelligence from FortiGuard Labs. FortiManager and FortiAnalyzer, along with tools for security orchestration, automation, and response (SOAR) integrate seamlessly to enable a strategic and coordinated responseto advanced threats. FortiClient and FortiEDR advanced endpoint security tools and FortiNAC network access control protect endpoints and IoT devices at the network edge. Physical security can be added to the Fabric with FortiCamera and FortiRecorder.The Fortinet Security Fabric enables technology companies to move from a tactical stance toward cybersecurity to a strategic one. Companies can make informed decisions about best practices based on real-time information and advanced analytics. And an automated approach to security processes, threat response, and compliance reporting maximizes operational efficiency while improving security.Figure 1: The Fortinet Security Fabric.CloudSecurityOpenEcosystemFortiGuardThreatIntelligenceSecureNetworkingManufacturing floor cybersecurityIT and OT are increasingly co-dependent, and many technology companies were early adopters of this trend. Supervisory control and data acquisition (SCADA) systems are often based on older technology, and connection to the internet wasnot envisioned when they were designed. As a result, many SCADA systems have vulnerabilities that are not easily fixed. Compounding the risk, IoT devices that measure and convey critical information at the manufacturing facility are often headless, meaning that security patches cannot be applied.To protect these critical but vulnerable systems, plant managers and security teams need to achieve centralized visibility into the entire cybersecurity infrastructure, from IT to OT. They must also be able to segment the network according to business need and centrally control both wired and wireless networks.The Fortinet Security Fabric provides centralized visibility and control acrossthe IT and OT systems of technology companies. FortiGate NGFWs, includingthe FortiGate Rugged Series for different environmental needs, provide the foundation for integration of OT into the security architecture. The intent-based segmentation capabilities included in FortiGate NGFWs enable IT and OT networks to be intelligently segmented to support zero-trust access and prevent lateral movement of threats. FortiNAC helps companies track and protect their IoT devices. Further, SOAR tools and FortiAnalyzer help organizations automate security response strategically, improving efficiency and helping stop threats thatNearly three-fourths (74%) of workers say they want to continue to work remotely following the pandemic, regardless of their business’s hybrid work plans.7move at machine speed.The Fortinet Security Fabric enables technology companies with manufacturing operations to integrate the security architecture across IT and OT environments, unlocking automation and optimizing operational efficiency. This can protect the manufacturing floor against both targeted and recycled threats and minimize production disruptions that impact the bottom line.Remote workforceThe start of the pandemic sent tech company employees home and IT teams scrambled to support and secure a fully remote workforce. Even though companies are shifting to hybrid and even going back to fully on-site work models, there are still many remote or frequently traveling workers.To preserve employee productivity, users need the same access in a residence, an airport, or a hotel room that they would have if they were sitting in a company office. Yet, providing such access introduces cybersecurity risk—especially for companies that operate with a perimeter-based approach to security. To provide secure remote access, companies must adopt a holistic approach to cybersecurity that includes a zero-trust approach to access, making no distinction between “trusted” internal traffic and traffic from the outside. Robust network segmentation must be bolstered by behavior-based ways to detect when user accounts and devices are compromised.Our work-from-anywhere (WFA) solution enables technology companies to provide extensive access to remote workers while protecting network segments that specific employees do not need. Fortinet Zero Trust Network Access (ZTNA) safely connects users to applications no matter where the user is located and no matter where the application is hosted. FortiAuthenticator and FortiToken identity and access management solutions help companies limit access to authorized users. FortiGate intent-based segmentation enables the network to be divided according to business need, enabling zero-trust access. Advanced endpoint protection tools, such as FortiEDR (endpoint detection and response) and FortiClient, help prevent infiltration through the endpoint devices used by remote workers.These Fortinet solutions enable technology companies to provide full and secure access to remote workers while protecting corporate assets against attacks from remote locations.Secure branch networksTechnology companies often have small and large branch offices around the world. Many have large overseas locations that are involved in resource-intensive work like R&D—often in coordination with managers residing at headquarters. Secure and reliable connections between these sites and headquarters are often critical for time-sensitive projects.The multiprotocol label switching (MPLS) infrastructure that traditionally provided connectivity to branch offices is expensive, cumbersome, and difficult to scale. As hybrid-cloud networks grow, network traffic increases, and workers at branch locations frequently notice latency in cloud-based services. And as companies struggle when they try to prioritize traffic, the latency can apply to a company’s most-critical applications.In response to these problems, companies are rapidly adopting software-defined wide-area networks (SD-WAN), which enable network traffic to travel on the public internet. To keep such a network secure, SD-WAN technology should ideally be integrated with the cybersecurity infrastructure—and with the networking infrastructure at the branch.Fortinet Secure SD-WAN technology is included in FortiGate NGFWs, enablinghighly secure and cost-effective connections on the public internet, but also over a virtual WAN (vWAN) within select public clouds. At the branch, Fortinet SD-Branch solutions extend the SD-WAN solution to the access layer. This enables secure networking at branches and consistent security coverage from the internet to the wireless network, down through the switching infrastructure.Fortinet solutions for secure branches enable companies to provide secure, high-performance networking with branches, with multiple choices for routing of traffic depending on volume. This helps support network performance at branches while protecting the network against intrusions that enter through branch locations.The vast majority (98%) of security professionals report that relying on multiple cloud providers creates additional security challenges.8Multi-cloud securityTechnology organizations were early adopters of cloud-based services, and most now operate in multiple public and private clouds. And in many cases, their most valuable and sensitive data is contained within this hybrid-cloud infrastructure. As organizations adopt services across this distributed architecture, the default is to leverage the built-in cybersecurity tools offered by each cloud provider.However, these solutions do not communicate with one another, and indeed have different underlying structures. The result can be multiple security silos—one for each cloud provider, one for the private cloud infrastructure, and one for the corporate data center. This makes centralized visibility and automation impossible. The result can be team members being pulled away from strategic projects to do manual work when compliance audit reports are due.To address this lack of visibility and operational inefficiency, organizations must unify the security architecture from the hybrid cloud to the data center. Policy management must be consistent across the board, and threat intelligence should be made available across the company in real time.Fortinet Cloud Security solutions accomplish these objectives by providing a single-pane-of-glass view of the entire cloud infrastructure. They feature native integration with all major public cloud providers, broad protection to cover all elements of the attack surface, and management and automation features that enable consistent, timely threat detection and response through automation.Fortinet enables technology companies to protect disparate cloud-based applications and infrastructure in a consistent way—with multiple layers of cybersecurity protection. As a result, technology companies can confidently deploy any service in any cloud at any time.Fortinet DifferentiatorsIntegrated platformThe Fortinet Security Fabric is built on a flexible platform based on FortiOS, a purpose-built operating system. On this foundation, technology companies can build an end-to-end, integrated security architecture from the data center to the network edge to multiple clouds. Multiple Fortinet tools integrate into the Security Fabric, and third-party solutions canbe added seamlessly via Fabric Connectors. Other third-party products can be integrated with a Fortinet open API and a library of API tools.High performance and low latencyFortiGate NGFWs provide the industry’s best performance during secure sockets layer/transport layer security (SSL/TLS) inspection and experience extremely low latency rates—even in demanding technology industry networks. With 95% oftraffic now encrypted across Google,9 this ensures that a necessary function does not impact operations.Branch location networking and securityFortinet offers comprehensive Secure SD-WAN technology, along with cybersecurity infrastructure for branch locations that eliminates the need for expensive MPLS bandwidth, provides optimal security, and improves network performance.Insider threat protectionFortinet delivers a comprehensive and multilayered solution to guard against insider threats with identity and access management supplemented by NAC, intent-based segmentation, deception technology, and user and entity behavior analytics (UEBA)—all integrated for centralized visibility and control.Robust threat intelligenceFortiGuard Labs delivers near-real-time protection based on threat intelligence from a large global network of firewalls andan AI-powered self-evolving detection system (SEDS). This results in extremely accurate, real-time identification of zero-day and unknown threats before they can cause problems on a network.ConclusionTechnology companies deliver digital innovation to their customers, but their brands can be tarnished quickly if their products lack quality, have technical glitches, or do not have adequate cybersecurity protection. By helping to thwart the tactics of a variety of threat actors, the Fortinet Security Fabric helps prevent these outcomes. As a result, technology organizations can focus on what they do best: innovate and delight customers.1 “2021 Cost of a Data Breach Report,” Ponemon Institute and IBM Security, July 28, 2021.2 “The Ultimate List of Internet of Things Statistics for 2022,” FindStack, February 15, 2022.3 “Understand the risk of IoT vulnerabilities in the remote work era,” SC Magazine, February 4, 2022.4 “2021 Cost of a Data Breach Report,” Ponemon Institute and IBM Security, July 28, 2021.5 “How Tech Companies Can Boost Cyber Defenses: Building a Cyber-First Culture,” eWeek, September 20, 2021.6 “Intellectual Property Enforcement,” U.S. Department of State, April 26, 2021.7 “Top cybersecurity statistics, trends, and facts,” CSO, October 7, 2021.8 “Multi-cloud environments creating additional security challenges,” HelpNetSecurity, July 15, 2021.9 “Google Transparency Report,” Google, accessed April 19, 2022. Copyright © 2022 Fortinet, Inc. All rights reserved. Fortinet, FortiGate, FortiCare and FortiGuard, and certain other marks are registered trademarks of Fortinet, Inc., and other Fortinet names herein may also be registered and/or common law trademarks of Fortinet. All other product or company names may be trademarks of their respective owners. Performance and other metrics contained herein were attained in internal lab tests under ideal conditions, and actual performance and other results may vary. Network variables, different network environments and other conditions may affect performance results. Nothing herein represents any binding commitment by Fortinet, and Fortinet disclaims all warranties, whether express or implied, except to the extent Fortinet enters a binding written contract, signed by Fortinet’s General Counsel, with a purchaser that expressly warrants that the identified product will perform according to certain expressly-identified performance metrics and, in such event, only the specific performance metrics expressly identified in such binding written contract shall be binding on Fortinet. For absolute clarity, any such warranty will be limited to performance in the same ideal conditions as in Fortinet’s internal lab tests. Fortinet disclaims in full any covenants, representations, and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise revise this publication without notice, and the most current version of the publication shall be applicable.April 28, 2022 8:01 AM。
Fortinet云安全解决方案白皮书说明书

IntroductionVirtualization is generally the first step when business paces from traditional data center onto the cloud migration journey. Cloud by definition is a pool of API resources that can be rapidly provisioned or released through cloud service providers’ APIs for enabling ubiquitous, elastic, scalable, on-demand access to a shared pool of configurable compute, networking, and storage resources. The nature of “software-defined” everything in the cloud makes it easier to implement with great privileges and yet come even greatresponsibility for security implementation. Cloud migration is not a one-way street, and it’s very common to see hybrid cloud deployments based on business workloads coexisting in the enterprise both on premise and at hosted cloud providers.Securing Your Public and Hybrid CloudScale and Segment Cloud Security on DemandFortinet Cloud Security enables organizations to securely and elastically scale protection to their private, public, and hybrid cloud infrastructure and workloads, and to segment both within the cloud andbetween endpoints, enterprisenetworks, and the cloud.FIGURE 1: SECURITY FOR THE CLOUDSecurity Paradigm ShiftUnlike an organization independently building a data center infrastructure, cloud-based infrastructure as a service (IaaS) is built and aggregated through pools of resources and is designed to be elastic to scale with organizational demand. The leasing and subscription model changes how security is designed and implemented, as cloud consumption transitions from traditional CAPEX to OPEX in the public cloud. The security paradigm shifted from protecting a big-perimeterFIGURE 2: SECURITY PARADIGM SHIFTEDwalled garden to micro-segmented security control of business workloads. IT infrastructure becomes shifted from end-to-end complete data center ownership to owning just enough for the workload to operate in the cloud. IT architecture becomes shifted from static approaches to elastic capacity with on-demand metering consumption. This paradigm shift applies to both cloud ingress/egress (northbound-southbound) and lateral (eastbound-westbound) network traffic flow.According to Gartner’s strategic planning assumptions on “How to Make Cloud IaaS More Secure Than Your Data Center”:n n Through 2020, workloads that exploit public cloud IaaScapabilities to improve security protection will suffer at least 60% fewer security incidents than those in traditional data centers.n n Through 2020, 95% of cloud security failures will be thecustomer’s fault.n n Through 2020, 99% of vulnerabilities exploited will continueto be ones known of by security and IT professionals for atleast one year.As the cloud IaaS technology continues to evolve and mature, the majority of the security responsibility falls on how thebusiness secures and governs the applications and data on cloud IaaS.Well-defined Roles in Securing the Public CloudFor securing the public cloud, it is imperative to follow the “Shared Responsibility” model as espoused by industry groups like the Cloud Security Alliance (CSA) and providers including Amazon AWS and Microsoft Azure. These can be divided into two components — Security OF the Cloud and Security IN the Cloud .Security OF the Cloud comprises what the cloud provider, such as AWS and Azure, will provide. This represents literally all data center components for the cloud IaaS.FIGURE 3: SHARED RESPONSIBILITY - REDUCE SECURITY COST + MAINTAIN FLEXIBILITY , ACCESS, AND CONTROLSecurity IN the Cloud comprises what cloud tenants are responsible for implementing with their security solutions.Legacy security technologies coming into the cloud are still using appliance-based solutions, host-based agents, and manual audits. To achieve a truly consistent security posture in the cloud, businesses need to make the new mentality shift to move critical data away from the monolithic host-centric security model and start leveraging components available from public cloud-based web services. Rather than simply acquiring standalone security appliance that introduce security management challenges, they should instead consider cloud security solutions with centralized management and visibility across all deployment nodes. Point solutions today withoutextensions into cloud APIs are due to fail when they hit the point of scaling elastically in the cloud.Fortinet Security Solutions for Public CloudsCloud deployment is not meant to replicate what it’s done in the traditional data center. Fortinet has purposefully built cloud appliances for Amazon Web Services (AWS) CloudFormation or Microsoft Azure Resource Manager (ARM) templates to take advantage of cloud API-driven functionalities.The Fortinet Security Fabric-ready APIs fully support AWS and Azure and help extend the security intelligence across the cloud. Fortinet further embraces AWS Auto Scaling web services to provide better capacity planning through automation.With a global presence across all regions in public clouds,Fortinet further helps customers and partners meet their security goal of providing applications and data close to their geographical user bases. Geopolitical compliance can be further provided through Fortinet FortiOS intelligence and reporting.Fortinet Security Fabric for the CloudThe Fortinet Security Fabric extends Fortinet’s cloud securitysolutions across the entire enterprise attack surface.Virtualization is a core component of the security fabric that enables applications and data to be delivered efficiently in an on-demand manner through software-defined orchestration. Business workloads can be replicated and automated through preconfigured templates to increase agility and high availability.It is also critical to have single-pane-of-glass management and to own the control plane over cloud resource abstraction, so that businesses can embrace this new dynamic, automated, services-oriented architecture and improve control and visibility in varying cloud deployments.FIGURE 4: FORTINET SECURITY FABRIC FOR CLOUD SECURITYFortinet supports on-demand hourly and annual metering subscriptions in the cloud marketplace, as well as bring your own license (BYOL) for perpetual consumption. As clouds are driven by the need to reduce CAPEX and OPEX expenditures. Fortinet provides the broadest set of service-driven portfolios that can be deployed in micro-segmented clouds without compromising holistic security intelligence.The key principles of cloud security implementation in the Fortinet Security Fabric are:n n Scalable – high-performance firewalls and network securityappliances that scale from IoT to branch offices to the enterprise campus to the hybrid cloudn n Aware – integrated with underlying cloud infrastructure tobe aware of dynamic changes in the cloud environment and to provide seamless protectionn n Secure – micro-segmentation and internal segmentation inthe hybrid cloud extended with end-to-end segmentation across the entire attack surfacen n Actionable – integrated into SIEM and other analytics inprivate and public clouds, with the ability to orchestrate changes to FortiGate and other Fortinet security policy/posture automatically in response to incidents and eventsn n Open – built on an extensible platform with programmaticAPIs (REST and JSON) and other interfaces to integrate with hypervisors, SDN controllers, cloud management, orchestration tools, and software-defined data center and cloudHybrid IT InfrastructureA hybrid cloud that mixes on-premise data centers/private clouds with public clouds requires rigorous management. Fortinet helps organizations build a cohesive securityinfrastructure that is easy to deploy, manage, and extend. Using the fabric-ready API framework, Fortinet seamlessly integrates orchestration and automation to work across the mixed cloud environments. This increased agility, flexible consumption, and automation help DevOps teams own the control plane and respond to changes in the cloud environment more efficiently. Fortinet helps maintain consistency in security posture across clouds with a familiar look and feel in tools and resources. By extending the data center with consistent management,organizations can get enterprise-grade performance and security in the data center and in the cloud, as well as meet changing business needs with greater flexibility and capacity on demand.FortiGate Security PlatformThe FortiGate family of physical and virtual security appliances provides the foundation for securing private and public cloud environments. High-end physical FortiGate appliances provide highly scalable north-south data center firewall and network security protection at the edge or core of the private cloud. Virtual FortiGate appliances provide north-south protection for public clouds, as well as east-west segmentation within and across the hybrid cloud.All FortiGate physical and virtual security appliances share a common FortiOS firmware with consolidated multi-function security, from firewall to intrusion prevention to next-genfirewall to anti-malware to web filtering, and more, and receive consistent FortiGuard threat and content updates fromFortinet’s fully in-house FortiGuard Labs threat research team.Fortinet Virtual AppliancesIn addition to the flagship FortiGate platform, nearly a dozen other Fortinet security and networking solutions are available, not just as physical appliances but also as virtual appliances,from web application security to sandboxing to analytics to application delivery, for deployment in private and public cloud environments.Agile Software-Defined SecurityFortinet’s Security Fabric for the clouds enables orchestration and automation of both physical and virtual FortiGate security appliances in the hybrid cloud. Through a rich set of RESTful and other programmatic APIs, FortiGate appliances can be tightly orchestrated and automated with leading software-defined cloud platforms.Orchestration in the Public CloudFortiGate security solutions are tightly orchestrated with leading public clouds like AWS and Azure to provide on-demand provisioning, pay-as-you-go pricing, elastic auto-scaling, and unified security analytics that enhance protection and visibility in the public cloud environment.Single-Pane-of-Glass Visibility and ControlA workload should have the same secure and compliant posture regardless of whether it is running in a private cloud or public cloud, or whether it may migrate from one to another in a hybrid strategy. Fortinet’s central management solutions, including FortiManager and FortiAnalyzer, provide a single consolidated view of security policies, governance reporting, and event monitoring regardless of physical, virtual, or cloud infrastructure, and across private, public, and hybrid clouds.ConclusionRapid enterprise adoption of private and public clouds is driving the evolution of cloud security. Agile and elastic cloud security solutions need to fundamentally scale protection and segmentation within and across cloud environments. Fortinet’s FortiGate security platform and cloud security solutions secure private, public, and hybrid clouds, and extend protection seamlessly via the Fortinet Security Fabric across the entire enterprise from IoT to data center to cloud.Copyright © 2016 Fortinet, Inc. All rights reserved. Fortinet , FortiGate , FortiCare and FortiGuard , and certain other marks are registered trademarks of Fortinet, Inc., and other Fortinet names herein may also be registered and/or common law trademarks of Fortinet. All other product or company names may be trademarks of their respective owners. Performance and other metrics contained herein were attained in internal lab tests under ideal conditions, and actual performance and other resultsmay vary. Network variables, different network environments and other conditions may affect performance results. Nothing herein represents any binding commitment by Fortinet, and Fortinet disclaims all warranties, whether express or implied, GLOBAL HEADQUARTERS Fortinet Inc.899 Kifer RoadSunnyvale, CA 94086United StatesTel: +/salesEMEA SALES OFFICE 905 rue Albert Einstein Valbonne06560, Alpes-Maritimes, FranceTel +33 4 8987 0500APAC SALES OFFICE 300 Beach Road 20-01The Concourse Singapore 199555Tel: +65.6513.3730LATIN AMERICA SALES OFFICE Paseo de la Reforma 412 piso 16Col. Juarez C.P . 06600 México D.F.Tel: 011-52-(55) 5524-8428。
Fortinet 技术白皮书_CN

l 增加对关键资源的监视。 l 研究有效的安全策略并培训用户。
解决方案对于每一个公司肯定是不同的,而 IT 专业人员必须充分分析和 理解他们的安全需求,确定究竟什么是他们试图保护的。一个完整有效的安 全方案不仅包括最新的安全技术,而且要考虑到公司的预算、社会和文化层 面的因素。
许多黑客正监视着软件提供商的补丁公告,并 对补丁进行简单的逆向工 程,由此来发现漏洞。图 1 举例说明了一个已知漏洞及相应补丁的公布到该 漏洞被利用之间的天数。需要注意的是,对于最近的一些攻击,这一时间已 经大大缩短了。
IT 和安全人员不仅需要担心已知安全威胁,他们还不得不集中精力来防 止各种被称之为“零小时”(zero-hour)或“零日”(zero-day)的新的未知 的威胁。为了对抗这种新的威胁,安全技术也在不断进化,包括深度包检测 防火墙、应用网关防火墙、内容过滤、反垃圾邮件、SSL VPN、基于网络的 防病毒和入侵防御系统( IPS)等新技术不断被应用。但是黑客的动机正在 从引起他人注意向着获取经济利益转移,我们可以看到一些更加狡猾的攻击 方式正被不断开发出来,以绕过传统的安全设备,而社会工程(social engineering)陷阱也成为新型攻击的一大重点。
描,并在它们加载以前就将它们关闭 – 这就导致即使有了最新的 病毒特征码,事实上它们还是不能被检测出来。 企业单纯依靠给予主机的防病毒软件和给操作系统和应用程序打补丁 的方法会使它们的内部系统面临很高的安全风险。随着业务中使用了越来越 多的面向全球且需要持续运行的关键应用,停机来更新操作系统补丁、病毒 特征码和应用升级变得越来越困难。而公司的 Web、Email、电子商务、数 据库、应用等服务器由于长时间不打补丁会很容易在新的攻击方式下暴露出 它们的漏洞。仅仅依靠基于主机的防病毒软件的另一个缺点是,事实上有害 代码在被每一个主机的安全软件检测和阻挡之前就已经进入了公司的网络, 这就大大威胁了企业关键业务系统和网络应用。
Fortinet MSSP 合作伙伴解决方案白皮书说明书

WHITE PAPERExecutive SummaryAs the threat landscape becomes more advanced and cybersecurity talent becomesmore scarce, partnering with a managed security service provider (MSSP) is anincreasingly attractive option for many organizations. In order to take advantage ofthis opportunity, MSSPs must be able to cost-effectively deliver a broad range ofsecurity services. Having a plethora of unconnected point products on the back endworks against this goal. The Fortinet Security Fabric delivers a broad, integrated, andautomated security architecture that enables delivery of effective, comprehensivesecurity services with minimal cost and staff time. It even affords MSSPs anopportunity to expand into networking services, expanding their footprint at existingsites and growing a base of new clients.The cybersecurity skills shortage,1 coupled with the cost and hassle of maintaining 24×77 coverage of an increasingly complex infrastructure, have made MSSPs increasinglyattractive to companies of all sizes. One recent analysis projects that companies will spendmore than $58 billion on managed security services by 2024,2 reflecting more than a 14%annual growth rate.This trend represents an unprecedented opportunity for MSSPs. Providers with a broad set of offerings can increase their footprint at existingclient sites, and recruit new clients with the promise of being able to meet their current and future needs.3 But to take advantage of this growingmarket need, MSSPs must deliver the right mix of security services cost-effectively—and in ways that align with the business needs andpriorities of their target customers.Fortinet MSSP partners reduce risk and minimize the impact of cyberattacks by providing managed security and monitoring services toprotect enterprise data, infrastructure, and users—regardless of who, where, when, and how IT assets are accessed. They extend thesecurity operations of the enterprise by bridging people, skills, process, and technology.Fortinet offers a broad portfolio of integrated and automated security tools that cover network security, cloud security,4 application security,5access security, and network operations center (NOC) and security operations center (SOC) functions.6 The ability to bridge security andnetworking on the same platform is a big advantage for MSSPs, enabling them to offer a broad, single-provider solution and increasingaverage revenue per user (ARPU).Key MSSP Cybersecurity ChallengesVisibilityA lack of visibility is one reason that many businesses are turning to MSSPs for help in defending against attacks. They find themselves in this positionbecause over time, they have responded to the growth of the attack surface by deploying unconnected point products, resulting in a disaggregatedsecurity architecture. This lack of visibility increases risk, as the organization often does not even know when it has been attacked.8 Providing end-to-end visibility is an essential capability for MSSPs seeking to meet the service expectations of their target customers. In the absence of visibility, fast-moving intrusions may cause harm before a response can occur, negating all efforts to maintain an effective security posture.9 To deliver a value add to customers, MSSPs need to achieve end-to-end visibility across each customer’s environment and provide that visibility to them via a customer portal.Operational efficiencyThe point of a managed service is to take advantage of economies of scale to deliver services more cost-effectively than a customer could. But if the MSSP’s services are delivered inefficiently, they will not be profitable. Lack of integration across different security elements and architectural fragmentation increase operational inefficiencies. Without integration and automation, many securityworkflows must be managed manually.10 This certainly increases risk, but it can also slowDevOps cycles, degrade customer and employee experience, and increase administrativeoverhead and operational costs.End-to-end integration, on the other hand, enables the MSSP to deliver broad serviceswhile optimizing staff time and budgetary resources, maximizing margins and potentiallyincreasing ARPU. Silos are eliminated, and the MSSP’s customers receive the mostcomplete security protection possible.Breadth of offeringsOffering a broad suite of security services to customers enables an MSSP to meet theneeds of more current and potential customers. This potentially increases ARPU throughthe opportunity to upsell in specific accounts. It also enables the organization to competefor business from potential new customers that are looking for a comprehensive set ofservices under one umbrella.11Adding functionality via unintegrated point products results in technology sprawl witheach product operating in its own silo, which necessitates manual correlation withexisting services. Ironically, it could mean that customer accounts that leverage more services would be less profitable than those that use fewer services, inhibiting business growth. On the other hand, MSSPs whose offerings are powered by a broad, integrated, and automated security architecture can customize their offerings to each customer’s needs. And every newly added service on an account increases both ARPU and profits.Threat intelligence and analyticsIn today’s advanced threat landscape, customers need real-time access to robust threat intelligence to counter attacks that move at machine speed. In addition to a customer’s own security logs, many subscribe to threat-intelligence feeds pulled from large networksof firewalls around the world, but it is a challenge to aggregate this data across a fragmented security architecture in time to deliver adequate speed of response.Customers also expect data-driven advice from the professionals they are paying to manage their security infrastructure—a challenge for MSSPs operating in disaggregated environments. In such an environment, providing advice to customers is an expensive proposition, and the insights gained are less valuable due to inevitable human error in the analysis.Use CasesManaged Secure SD-WAN ServiceThe rapid growth of software-defined wide-area networking (SD-WAN) over the past few years12 affords MSSPs an incredible opportunity. MSSPs now have easy access to tools that can increase their footprint at customer sites by expanding into networking services. The opportunity is equally attractive to customers, as it enables them to scale their network traffic using the public internet without paying for new multiprotocol label switching (MPLS) bandwidth. But security is a big challenge for companies consideringSD-WAN, as network traffic moving on the public internet opens a big new element of the attack surface.Other SD-WAN offerings are often based on point products that are purchased and administered separately from a security solution. This can increase operating costs, reduce margins, degrade security, and reduce the overall quality of the service. FortiGate Secure SD-WAN combines complete security and robust networking performance in a single platform, enabling MSSPs to broaden their reach profitably. Such an offering also provides the potential for an MSSP to expand its services to secure networking at branch locations—again without adding additional point products. Fortinet SD-Branch includes FortiGate next-generation firewalls (NGFWs) combined with switching, wireless access, and network access control tools to provide complete connectivity and security protection at remote offices.Offering managed secure SD-WAN services powered by Fortinet brings a number of advantages to MSSPs: nn The opportunity to grow ARPU at existing customer sites by expanding into networking services to, from, and within branch locationsn The ability to grow this new business over time with a lack of expensive additional contracts and deployments required nn Operational efficiency and enhanced profitability by delivering the service via a fully integrated, multi-tenant toolsetnManaged SOC ServiceNot every company can afford to have a full-fledged SOC. Designing and building out the space,hiring a team, and providing 24×7 staffing and hardware and software maintenance on anongoing basis is an expensive proposition. Unfortunately, the cybersecurity skills shortagemeans that the problem is only getting worse.13That said, the enhanced security, visibility, and actionable insights that can be derivedfrom a SOC are important for the business. MSSPs can fill this gap by delivering a rangeof services from their own SOC. These services can be offered at specific levels or astailored services for individual customers’ needs.For example, many customers benefit from managed security information and eventmanagement (SIEM) services because of the deep visibility and analytics they provide.And managed detection and response services can leverage artificial intelligence(AI)-driven threat intelligence and indicators of compromise (IOC) feeds to add layersof protection to customer environments. Customers can even have their own log-incredential to view the analytics for themselves.The Fortinet Security Fabric, powered by FortiGate NGFWs, enables MSSPs to build afull-spectrum SOC with end-to-end integration across the entire architecture. Numerous“In the modern times we live in, formulating new strategies, and remedying existing security measures to combat the changing threat landscape, is of the utmost importance. Keeping this in mind, MSSPs serve as the Holy Grail solution that the cybersecurity realm needs today!”14security tools from Fortinet and third-party Fabric Partners integrate seamlessly into the Fabric. Additionally, the open architecture and robust representational state transfer application programming interface (REST API) enable MSSPs to integrate other solutions to fill niche needs or maximize investment in legacy tools.Delivering managed SOC services using the Fortinet Security Fabric brings these benefits to MSSPs:n n The ability to offer comprehensive services without managing a plethora of point productsn n The benefit of real-time, AI-powered threat intelligence along with other layers of protection against unknown threatsn n Operational efficiency and enhanced profitability by delivering the service via a fully integrated, multi-tenant toolse tFigure 1: A broad, integrated, and automated security architecture from Fortinet helps MSSPs deliver a wide range of services, including managed SD-WAN services, managed SOC services, and managed cloud security services.Managed Cloud Security ServiceThe explosion in the use of the public cloud by businesses of all sizes does not seem tobe slowing. In fact, Software-as-a-Service (SaaS) spending alone is expected to exceed$80 billion this year15—an annual growth rate of more than 17%. Unfortunately, the rapidadoption of sprawling cloud infrastructures increases security operations complexity fororganizations, and the result is often that cloud-based applications are vulnerable. Onekey driver of risk is the misconfiguration of cloud-based systems.16With the right infrastructure, MSSPs can offer comprehensive cybersecurity protectionfor all services running on multiple clouds. Alternatively, they can offer protection on anapplication-by-application basis using a Web Application Firewall (WAF)-as-a-Servicemodel. Both approaches can increase an MSSP’s footprint at customer sites. As theyoffer more cloud security services within an account, operational efficiencies derived fromend-to-end integration can increase their margins.17 Fortinet offers robust, cloud-native tools to bring MSSP customers’ entire distributed cloudinfrastructure together under a single umbrella, with consistent security protection, policymanagement, and configuration management. FortiGate VM brings the NGFW to avirtual machine form factor that works well for cloud environments, and the FortiWeb web application firewall (WAF) is available in several form factors as well, including SaaS. The FortiCASB cloud access security broker (CASB) service and the FortiCWP cloud workload protection (CWP) tool deliver visibility, compliance, threat protection, and configuration management across the cloud infrastructure.A managed cloud security service powered by Fortinet brings these advantages to MSSPs:nn Security tools native to each cloud bring a consistent set of security policies and practices to all customer cloud deploymentsn In-line, real-time threat intelligence in FortiWeb enables instant, automated response to security eventsnn Operational efficiency and enhanced profitability by delivering the service via a fully integrated, multi-tenant toolsetnFortinet Differentiators for MSSPsRobust, broad-based security products and services to enable a comprehensive menu of services for MSSP customers from a single platform. This can result in higher ARPU and broader revenue opportunities. At the same time, Fortinet Network Security Expert (NSE) training gives MSSPs a consolidated training model for a broad set of security and networking products under management—and a way to differentiate their services.Multiple product consumption models offer MSSPs and their customers the flexibility they need to secure their data, infrastructure, and applications in the most optimal way. Different Fortinet solutions are available in appliance, virtual machine, cloud, and SaaS form factors. MSSPs can also leverage special pricing programs such as pay-as-you-go and subscriptions, providing the flexibility to address different business models supporting their service offerings.Recognized leadership in network security, named a Leader in the Gartner Magic Quadrant for Network Firewalls,18 and scoring best among nine vendors in the NSS Labs Next-generation Firewall Security Value Map.19 This unparalleled performance enables MSSPs to reduce their capital expenses (CapEx) spend, and a smaller security and network footprint to deploy and manage lowers operational expenses (OpEx) costs.The ability to leverage investments in third-party products via integration through the Fabric Alliance, open APIs, and a robust REST API. This enables MSSPs with rapid scale to remove friction and increase the speed of service rollouts.Security solutions designed as multi-tenant from the ground up, enabling MSSPs to isolate but still manage multiple customer networks from a single console. This increases ARPU while improving operational efficiencies.ConclusionAs customers look to MSSPs to help them with seemingly intractable cybersecurity challenges, offering limited, cookie-cutter, or disconnected services is not a good way to build business. But MSSPs that base a broad set of services on the Fortinet Security Fabric have the opportunity to become a one-stop shop for security services—and a trusted advisor to a growing client base.Copyright © 2019 Fortinet, Inc. All rights reserved. Fortinet , FortiGate , FortiCare and FortiGuard , and certain other marks are registered trademarks of Fortinet, Inc., and other Fortinet names herein may also be registered and/or common law trademarks of Fortinet. All other product or company names may be trademarks of their respective owners. Performance and other metrics contained herein were attained in internal lab tests under ideal conditions, and actual performance and other results may vary. Network variables, different network environments and other conditions may affect performance results. Nothing herein represents any binding commitment by Fortinet, and Fortinet disclaims all warranties, whether express or implied, except to the extent Fortinet enters a binding written contract, signed by Fortinet’s General Counsel, with a purchaser that expressly warrants that the identified product will perform according to certain expressly-identified performance metrics and, in such event, only the specific performance metrics expressly identified in such binding written contract shall be binding on Fortinet. For absolute clarity, any such warranty will be limited to performance in the same ideal conditions as in Fortinet’s internal lab tests. Fortinet disclaims in full any covenants, representations, and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise revise this publication without notice, and the most current version of the publication shall be applicable. Fortinet disclaims in full any covenants, representations, and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise revise this publication without notice, and the most current version of the publication shall be November 18, 2019 9:37 PM 1Mekhala Roy, “Effects of cybersecurity skills shortage worsening, new study says ,” TechTarget, May 10, 2019.2“Managed Security Services Market is Expected to Exceed US$ 58 billion by 2024,” MarketWatch, February 27, 2019.3Christophe Voilque, “MSSP 2.0: How to Launch or Expand Managed Security Services with the Fortinet Security Fabric ,” Fortinet, March 27, 2019.4“Key Principles and Strategies for Securing the Enterprise Cloud: A Cloud Security Blueprint ,” Fortinet, December 3, 2018.5“Fortinet Web Application Security for the Cloud ,” Fortinet, March 19, 2019.6“Bridging the NOC-SOC Divide: Understanding the Key Architectural Requirements for Integration ,” Fortinet, August 23, 2018.7Scott Matteson, “To stay competitive, MSSPs need to grow and evolve ,” TechRepublic, January 16, 2019.8John Maddison, “The Problem with Too Many Security Options ,” Fortinet, May 9, 2019.9 Derek Manky, “The Evolving Threat Landscape—Swarmbots, Hivenets, Automation in Malware ,” CSO, August 29, 2018.10“Network Complexity Creates Inefficiencies While Ratcheting Up Risks: Understanding the Causes and Implications ,”Fortinet, June 1, 2019.11“Managed Security Services’ Value Is Scale ,” Channel Futures, May 14, 2019.12Andy Patrizio, “Enterprises are moving to SD-WAN beyond pilot stages to development ,” Network World, May 7, 2018.13Jon Oltsik, “Is the cybersecurity skills shortage getting worse?” CSO, May 10, 2019.14Rebecca James, “How Can MSSPs Thrive in the Growing Time of Complex Cyber Threats?” Infosecurity, October 29, 2019.15Louis Columbus, “Roundup Of Cloud Computing Forecasts And Market Estimates, 2018,” Forbes, September 23, 2018.16Asher Benbenisty, “Don’t Go Once More Unto the Breach: Fix Those Policy Configuration Mistakes ,” Infosecurity, October 30, 2018.17“Industry leaders struggle to balance digital innovation and security ,” Help Net Security, April 4, 2018.18“FortiGate Network Firewalls Give MSSPs Another Reason to Select Fortinet ,” Fortinet, September 24, 2019.19 “Independent Validation of Fortinet Solutions: NSS Labs Real-world Group Tests ,” Fortinet, January 2019.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
1.病毒问题目前,恶意软件感染率大幅增高,以窃取公司敏感数据和破坏重要用户用户记录的恶意软件会给企业造成巨大的损失,企业必须选择正确的防御方式来阻止恶意软件感染。
针对现在的Internet,恶意软件研究人员发现了大量的恶意软件活动,并评估每天都有数以千计的恶意软件变种在发布并传播。
与之形成强烈对比的是,只是在几年前,研究人员每天只能发现少量新的恶意软件。
研究人员预计随着Internet中大量的新恶意继续恶化,这种情况仅是大流行的初期阶段。
同时黑客发布越来越复杂的恶意软件——一些被设计为偷渡式安装并通过一台曾经是信任的主机或假冒他人进行分发。
这篇文档针对在网关处检测数据的网关防病毒架构设计,描述、比较并提出了一份最好的实践指南。
这种架构被设计对识别并阻止恶意软件内容进行高速数据检查,如:键盘记录器、后门程序、间谍软件、rootkit等其它形态的恶意软件。
将两种主流架构进行比较。
第一种方式是Fortinet利用定制硬件来加速文件重组和应用识别的代理方式,可提供更全面的文件分析。
第二种是基于数据流方式,在对数据包进行逐个检测。
以下内容将描述基于流方式虽然可提供最大化的性能,但性能提高的代价是低检测率,增加用户因检测失败而感染恶意软件的高风险。
值得注意的是Fortinet向正规的第三方认证中心(ICSA实验室)提交了Fortinet架构以确保100%的WildList防御(WildList是一个Internet上最活跃病毒的数据库。
列表每月更新,由维护,Fortinet是其成员之一)。
每月的ICSA测试证明FortiGate设备可提供100%的WildList保护。
另外,Fortinet 对恶意软件防御相比WildList进行了扩充,使用启发式分析和文件还原引擎动态的检测多形态病毒及新的恶意软件变种。
通过对Web、FTP下载/上传、邮件信息及IM(即时消息)等应用的数据传输进行扫描,FortiGate设备可对最流行的恶意软件进行阻止。
反之,没有一种目前的基于流网关经过认证或行业证明可提供100% WildList保护。
2.Fortinet方式——加速的内容分析Fortinet网络架构是利用专用的硬件架构,在不牺牲网络安全性和性能的前提下,正确快速的检测恶意内容。
使用深度文件分析和基于代理的应用引擎,FortiGate设备把文件提交给内容层、协议层和启发式分析层等多个层次,使系统能检查到最复杂的多形态恶意软件。
为了进一步增加检测正确性,代理方式在检测前可对文件解包或解密,使FortiGate设备能解决规避方法。
由于文件经常被有意的打包或加密,以逃避基于流的检测方式。
例如,黑客清楚基于流检测的运行原理后,故意的打包恶意软件以逃避基于流扫描的检测。
打包文件是指把文件压缩或归档为某种格式,如UPX、gzip、ZIP和RAR。
正常使用Web应用时,Web服务器通常会为了更快的在Internet上传输内容对文件压缩。
一旦接收到文件,浏览器将会自动解压文件并显示或执行。
因为组成一个文件的所有数据包必须被缓存并重组,而解包文件通常会消耗很高的性能,大多数基于流的防病毒引擎只能提供有限的数据包重组支持。
微软最近的一份报告指出,超过一半的新发现的恶意软件为了逃避和迷惑的原因,都被进行了打包。
事实上许多基于流的引擎只能支持有限的数据包重组,这意味着部署基于流的防病毒网关后,超过50%的最活跃的恶意软件可能未被发现而流入网络——网关重要的安全缺陷使用户更易被感染,带来了高风险。
图2 基于流的防病毒网关潜在安全缺陷3.文件分析和恶意代码检测检测恶意软件内容的第一步,也是最重要的步骤,是应用检测规则前要把整个文件进行重组。
一旦FortiGate收到数据,将执行解包、解密及文件还原程序,复原出真实的二进制文件。
而基于流的引擎因不能对文件解包、解密并还原为二进制格式,所以静态签名库只能对文件的内容进行推测。
这种方式将提高误判的可能性,并可能阻塞正常的流量或中断重要应用程序的运行。
图3 FortiGate透明截取传输中的文件进行检测因数据在两台主机间传输,当数据传输到请求文件下载的客户端时,FortiGate透明的截取文件分片。
一旦接收到所有的分片,FortiGate将重组成完整的文件进行分析。
如果发现文件经过打包,将调用解包程序对文件解压缩,以得到真实的内容。
如果发现文件经过加密,FortiGate系统将对文件仿真执行以解密文件,显示出文件的真实内容并进行精确的分析。
当大文件的解包和解密时,FortiGate将提供更高的检测及精确性级别,以确保重要应用程序的正确运行。
以下的章节将讨论一个FortiGate如何正确检测多形态病毒的实例,这种病毒专门为设计为逃避基于流的检测。
4.比较多形态病毒检测方法多形态病毒是专门用来逃避依靠静态文件特征检测病毒的方法,这种病毒加密病毒代码并自动执行解和文件转化程序。
当多形态病毒在主机间传播时,通过使用不同的加密算法和前一个版本的关键信息,转化程序改变文件结构形成病毒变种。
变种包括同样的病毒,但文件结构已被改变,所以相对以前的版本很少或没有留下可被识别的模板。
因为转化引擎可能产生上百万的新变种,依靠特征检测每一种变种效率将非常低,占用资源也很高。
只有通过先重组完整文件再应用仿真程序来解密并显示文件代码的方式才能正确高效的检测多形态病毒。
图4 逃避静态签名库检测的多形态病毒变种基于流的方法基于流的防病毒厂商可能辩解他们能轻松的编写签名库来匹配打包或加密的文件本身。
事实上,捕获所有的初始和变种病毒将使签名库数量变得不切合实际,数据包级的检测会面对可量化性及系统资源问题。
签名库数量越多,可利用系统资源就越少,基于流的方法将严重的影响性能。
举例来说,一种多形态病毒变异出1,000种不同的变种。
多形态病毒每感染一台主机,转化引擎都可能为每一种形态随机使用不同的加密或关键信息进行编码。
通过为每个文件形态编写签名库来正确捕获一个病毒,基于流的方法需要:1 (初始) + 1,000 (变种) = 1,001 (为检测一种病毒的签名)文件变种数量的另一个要素是打包方法,对于基于流的防病毒网关,将需要更高的检测一种病毒的签名库数量。
Fortinet的方法通过使用仿真引擎,FortiGate架构只需要一条签名检测同一个多形态病毒。
文件被重组和分析时,如果发现文件被加密,FortiGate将仿真文件执行,以前的加密代码被解密并分析。
这种状态下,不管文件架构如何变化,只需要检查一条文件签名,不需要为每一变体编一条签名。
图5 FortiGate设备执行文件重组图6 FortiGate仿真引擎解密文件发现病毒代码Fortinet基于代理的方法能提供高性能和高水平安全的更好的平衡。
使用加速文件分析的专用硬件,FortiGate设备在保护高性能和低延迟的同时,还能实现包含解包和仿真引擎的更深度文件分析。
图7 Fortinet代理架构和基于流的防病毒网关功能比较基于流的防病毒测试在一些Internet网关上使用基于流的检测方式作为主要的恶意软件检测引擎。
尽管这种方式能提供较高的性能,但使用基于流的方式检测恶意软件有很大的局限性。
基于流的扫描技术通常用来做IPS(入侵保护)系统,能最有效和最理想的执行深度包检测,发现那些明确包含在一个或一些数据包中发送的攻击。
对使用基于流引擎网关防病毒产品功能测试中,通过在FTP客户端和服务器间传输EICAR测试文件测试检测能力。
首先传输ZIP格式EICAR文件,可以正确检测并阻止。
但同一个EICAR文件在传输前使用常用打包软件打包或归档后,轻易的通过了基于流的防病毒引擎检测。
图8 阻止FTP传输EICAR文件在使用常打包和归档程序对文件打包后,文件没有被检测到,轻易的通过了基于流的网络防病毒产品,并可在客户端下载和执行。
图9 FTP传输RAR格式的EICAR文件使用常用的RAR格式,EICAR文件未被检测到,成功的发送到客户端。
在下一个测试中,使用BZ2格式打包文件。
BZ2是在Internet上传输文件的另一种常用打包格式。
图10 FTP传输BZ2格式的EICAR文件使用常用的BZ2格式,EICAR文件未被检测到,成功的发送到客户端。
5.专利技术的硬件加速只有通过数据包的关联与重组,一些最复杂的混合型威胁才能被发现。
为了补偿先进检测技术带来的性能延迟,Fortinet使用FortiASIC芯片来为特征扫描、加密/解密和SSL等功能提供硬件加速。
Fortinet拥有专利的紧凑模式识别语言(Compact Pattern Recognition Language,简称CPRL)与FortiASIC一起使用,提供比基于PC工控机的安全设备高出数倍的性能。
通过一些很巧妙的设计,FortiASIC 总能帮助用户在威胁到达之前完成更新,而不会停留在过期的阶段。
正如图形加速卡能加速复杂图形的显示一样,FortiASIC和CPRL能对病毒和攻击检测进行特征和模板匹配进行加速。
Fortinet的完全内容检测和重组技术与业界第一个硬件加速检测引擎(FortiASIC和CPRL语言)一起,提供了当今最先进的ASIC加速安全产品⏹多种FortiASIC处理器加速防病毒FortiASIC是构建Fortinet独有硬件平台的基础。
FortiASIC处理器是针对实际应用开发的系列产品,它们或能够达到高速的网络处理性能,或采用了智能的扫描引擎,能够对安全应用、内容层处理进行加速,降低对CPU等系统资源的占用。
FortiASIC技术涵盖与FortiOS这样的经过安全加固的操作系统集成,以达到高速处理和完善的安全体系。
防病毒技术采用了最新的FortiASIC网络处理器(NP)、内容层处理器(CP)和多核处理器(SP)进行加速。
其中内容层处理器(CP)可以对文件级的病毒过滤进行加速,是目前业内文件级病毒网关技术性能最好的产品之一。
FortiASIC-SP可以对病毒的流扫描技术进行加速,以应用到高吞吐、低延时的网络环境中。
⏹先进的启发式和异常检测为了针对未知的威胁和有害流量的检测与防护,Fortinet将多个前沿的检测技术组合在一起,提供了启发式扫描和异常检测。
启发式扫描技术用来增强防病毒、反垃圾邮件和其它相关的扫描活动。
当异常检测被IDS和IPS检测引擎使用时,通过高级技术和基于特征的技术相结合,对于使用IP碎片和协议受控方法攻击的检测能力就大大增强了。
先进的防病毒扫描技术:●文件分析●蠕虫检测●文件类型分析●流扫描●启发式检查Fortinet的防病毒扫描引擎结合了多种技术来检测已知的和尚未开发出特征码的新病毒。
检测未知病毒是通过复杂的启发式扫描技术来进行的,这些技术需要用到文件头和实际的包内容来完成。
