European Community under the “Information Society Technologies”
新视野第4册 课本单词
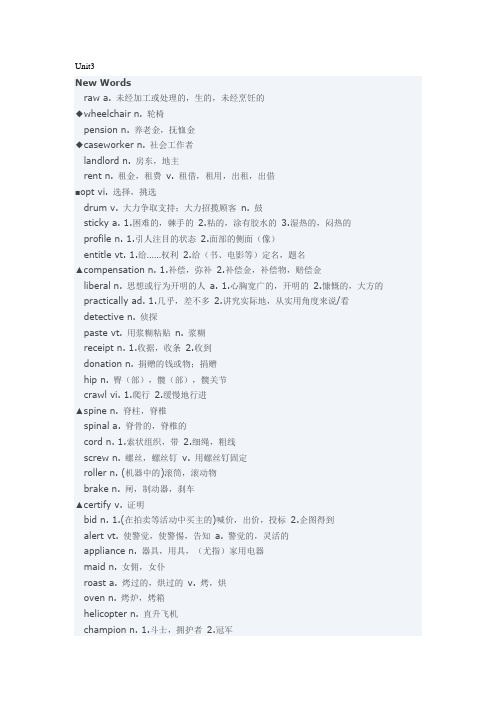
Unit3New Wordsraw a. 未经加工或处理的,生的,未经烹饪的◆wheelchair n. 轮椅pension n. 养老金,抚恤金◆caseworker n. 社会工作者landlord n. 房东,地主rent n. 租金,租费v. 租借,租用,出租,出借■opt vi. 选择,挑选drum v. 大力争取支持;大力招揽顾客n. 鼓sticky a. 1.困难的,棘手的2.粘的,涂有胶水的3.湿热的,闷热的profile n. 1.引人注目的状态2.面部的侧面(像)entitle vt. 1.给……权利 2.给(书、电影等)定名,题名▲compensation n. 1.补偿,弥补2.补偿金,补偿物,赔偿金liberal n. 思想或行为开明的人a. 1.心胸宽广的,开明的2.慷慨的,大方的practically ad. 1.几乎,差不多2.讲究实际地,从实用角度来说/看detective n. 侦探paste vt. 用浆糊粘贴n. 浆糊receipt n. 1.收据,收条2.收到donation n. 捐赠的钱或物;捐赠hip n. 臀(部),髋(部),髋关节crawl vi. 1.爬行 2.缓慢地行进▲spine n. 脊柱,脊椎spinal a. 脊骨的,脊椎的cord n. 1.索状组织,带 2.细绳,粗线screw n. 螺丝,螺丝钉v. 用螺丝钉固定roller n. (机器中的)滚筒,滚动物brake n. 闸,制动器,刹车▲certify v. 证明bid n. 1.(在拍卖等活动中买主的)喊价,出价,投标2.企图得到alert vt. 使警觉,使警惕,告知a. 警觉的,灵活的appliance n. 器具,用具,(尤指)家用电器maid n. 女佣,女仆roast a. 烤过的,烘过的v. 烤,烘oven n. 烤炉,烤箱helicopter n. 直升飞机champion n. 1.斗士,拥护者2.冠军chemist n. 1.药剂师,药商2.化学家,化学师leak v. 1.漏,泄漏2.(液体、气体等)漏,渗3.泄漏(秘密)n. 漏洞,漏隙senator n. 参议员governor n. 州长,总督,统治者thrive v. 兴旺发达,茁壮成长convict vt. (经审讯)证明 ... ... 有罪,宣判 ... ... 有罪Phrases and Expressionsface with 面对drum up 大力争取,大力招揽(顾客)under the table 背地里,私下get / be involved in 卷入,介入,参与deep down 在内心深处,在心底make a fool of sb. 愚弄某人talk back 顶嘴break down 发生故障,坏掉get around 四处走动look into 调查,仔细检查fill out 填写account for 解释,说明(原因等)build up 逐步建立,逐步建设go through 经历,遭受,蒙受lend oneself/sth. to 适宜于(某事),有助于(某事),会造成(某结果)convict …of 判决……有罪,使深感有罪,使服罪Proper NamesJohn Callahan 约翰·卡拉汉(人名)Suzanne 苏珊娜(人名)New Wordsstack n. 1.整齐的一堆,一叠2.藏书书架v. 把……叠成堆dense a. 1.密集的,稠密的2.厚的,浓密的charter v. 1.租,包(车、船、飞机)2.特许成立,发放执照n. 宪章,章程van n. 中型运货篷车,客货两用车angle n. 1.角,角度 2.角度,方面,观点jaw n. 颌,下颌,下巴mist n. 1.雾气2.薄雾v. (使)蒙上薄雾,(使)模糊steer v. 1.引导,带领2.驾驶stoop n. 弓背v. 俯身,弓腰,弓背liter(英litre) n. 升(体积单位)grape n. 葡萄soda n. 1.汽水 2.苏打水rug n. (铺在地上或作为装饰的)小地毯dye v. 染n. 染料lad n. 男孩,小伙子,年轻人violin n. 小提琴bow n. 1.弦乐器的弓,琴弓2.弓,弓形物gallery n. 1.收集,聚集2.画廊,美术馆lower v. 1.降低,调低2.放下,降下a. 下部的,底层的intensity n. 强烈,强度violet n. 紫罗兰花a.&n. 紫罗兰色(的),紫色(的)crown n. 1.王冠,皇冠 2.冠军称号v. 加顶于,覆盖……的顶部centimeter(英centimetre) n. 厘米highlight v. 引起注意,强调n. 最精彩的部分dessert n. (正餐之后的)甜食,甜点brass n. 黄铜(铜锌合金)overhead a.&ad. 在头顶上的(地),架空的(地)curve v. 弯曲;转弯n. 曲线,转弯lump n. 糊,团,块状物cab n. 出租车,计程车inn n. 小旅馆,客栈pat v. 轻拍,轻打n. 轻拍,拍打skim v. 1.掠过,擦过2.浏览,初步考虑3.(从液体面上)撇去浮物▲veil n. 1.面纱,面罩2.遮盖物,掩饰物v. 遮盖,掩盖realm n. 领域,范围,范畴magic n. 1.魔法,巫术2.魔术,戏法3.魅力,魔力Phrases and Expressionsbear witness to 对……做出证明,表明catch up 赶上load with 满载着switch on 开(电灯、收音机等);接通(电流)out of tune 走调hold up 举起,抬起skim the surface 触及表面Proper NamesBangkok 曼谷(泰国首都)Thailand 泰国(东南亚国家)Belgian 比利时人,比利时的Scandinavian 斯堪的纳维亚的,斯堪的纳维亚人Unit4New Words▲telecommunications n. 电信,远距离通信dumb a. 哑的,不会说话的utility n. 1.公用事业,公用事业设施2.功用,效用,利用optical a. 1.光学的,光的2.视力的,视觉的,眼睛的diameter n. 直径millimeter n. 毫米cable n. 缆索,电缆copper n. 紫铜,紫铜色 a. 铜的,铜色的parade n. 1.一连串,一批2.(庆祝)游行,检阅spider n. 蜘蛛▲web n. (蜘蛛等的)网condense v. 1.缩短,压缩2.(使)冷凝intensive a. 密集的,集中的,加强的desperate a. 1.极度需要的,非常想要的2.拼死的,铤而走险的,绝望的rust v. 生锈n. 铁锈antique n. 古董lick vt. 1.击败,克服2.舔strategic a. 战略的recession n. 经济衰退scratch vt. 抓,搔,划province n. 1.省2.(学术)领域,活动范围provincial a. 1.省的,地方的2.眼界狭窄的■infrastructure n. 基础设施log v. 1.记载2.砍伐n. 1.原木,木料2.航海(或飞行)日志peak n. 1.高峰,最高点 2.山顶,山峰invest v. 投(资),投入investor n. 投资者stake n. 1.股份,利益关系2.桩,标桩lease v. 租借,出租n. 租约ridge n. 脊状突起部分,(尤指)山脊reliable a. 可靠的,可依赖的,值得信赖的tag n. 标签,标牌usage n. 1.使用,对待方式2.用法width n. 宽度,阔度,广度nowhere ad. 任何地方都不disposal n. 1.支配权,处置权2.处理,消除revenue n. (政府的)岁入,税收,(公司的)收入fax n.&v. 传真;发传真electron n. 电子persist v. 坚持不懈,执意Phrases and Expressions(be) stuck with 无法摆脱,解脱不了a matter of sth. / doing sth. 需要……的问题,需要……的事情choose between 在两者中作出选择date from 始于be stuck in 陷入scratch the surface 触及表面log on to 进入(计算机)系统,登录at one's disposal 供某人使用,由某人支配make use of 使用,利用keep pace with 与……齐步前进lag behind 落后,落在……后面Proper NamesLatin America 拉丁美洲Eastern Europe 东欧Budapest 布达佩斯(匈牙利首都)Vietnam 越南(东南亚国家)Russia 俄罗斯Tibet 西藏Manhattan 曼哈顿区(美国纽约市政区名)Hungary 匈牙利(欧洲中部国家)Dutch 荷兰的,荷兰人的,(the ~)荷兰人BellSouth Corporation 南方贝尔电话公司Western European 西欧的,西欧人(的)New Wordsbeast n. 1.野兽2.粗鲁或残忍的人guitar n. 吉他jazz n. 爵士乐cassette n. 盒式录音带,盒式录像带reading n. 1.阅读,读2.读数 3.读物edition n. 版本tutor n. 家庭教师,私人教师,辅导教师,导师v. 教授,指导feedback n. 反映,反馈信息semiconductor n. 半导体transmit v. 传播,传送carrier n. 1.运送工具,运载工具2.搬运东西的人laser n. 激光; 激光器hence ad. 因此,所以format n. (安排或表现的)样式,方式,计划audio a. 与音响有关的,播音的,音频的dose n. (药的一次)用量,剂量blade n. 1.刀片 2.草叶robot n. 机器人,自动控制装置keyboard n. (电脑、打字机或乐器的)键盘correspondent n. 记者,通讯员vacuum n. 1.真空般的状态,空白2.真空v. 用真空吸尘器清扫synthetic a. 1.人造的,合成的2.虚假的universe n. 1.世界,领域,范围2.宇宙,天地万象crucial a. 至关重要的,关键的postman n. 邮递员correspondence n. 1.信件,函件2.通信,通信联系diagram n. 图解,示意图spokesman n. 发言人portion n. 一部分,一份insure v. 1.保证,担保2.给……保险,投保terminal n. 1.计算机终端2.候机楼,码头,出入口typewriter n. 打字机librarian n. 图书管理员Phrases and Expressionssign up (经报名或签约)获得,从事broadly speaking 一般说来refer to 指的是,涉及be compared to 比作come up with 1.拿出,提供2.提出,想出in the hands of 在……手上,在……掌握之中have access to 享有接近(或进入)……的机会,享有使用……的权利rely on 依靠fall behind 落后,落在……后面devote to 把……专用(于)Proper Names◆Beauty and the Beast 《美女与野兽》(电影名)Al Gore 阿尔·戈尔(美国前副总统)Clinton 克林顿(美国前总统)Jeffrey Chester 杰弗里·切斯特the Center for Media Education 大众媒介教育中心Washington, D.C 华盛顿(市)(美国首都)Berkeley 伯克利(美国加利福尼亚州西部城市)California 加利福尼亚州Community Memory Project 社区存储器项目Santa Monica 圣莫尼卡(美国加利福尼亚州西南部城市)Unit6New Words▲bribe n. 贿赂(尤指钱) vt. 向……行贿,买通bribery n. 行贿, 受贿◆ethics n. 道德准则,伦理标准Phrases and Expressionson the increase 在增长中a way of life 生活方式pay up 付款,还钱stand by 遵守,履行in practice 实际上,事实上,在实践中accuse of 指控,指责in private 私下地,秘密地a fact of life 现实,残酷的事实consist of 由……组成in support of 支持,拥护under investigation 正在调查中throw out 抛弃,扔掉,驱除close a deal 完成交易,生意成交speed up (使……)加快速度hit upon /on 碰巧想出,忽然想出distinguish between 区分,辨别,分清amount to 实际上,意味着behave oneself 检点(自己的)行为,(使自己)循规蹈矩be caught in 陷入,遭到on the take 受贿square …with 符合,相符Proper NamesSwitzerland 瑞士(欧洲中部国家)Chrysler Corporation 克莱斯勒汽车公司U.S. Securities and Exchange Commission 美国证券交易委员会Chile 智利(南美洲西南部国家)Iran 伊朗(西南亚国家)Caribbean 加勒比海(诸岛)的,加勒比人(的)International Chamber of Commerce 国际商会New Words◆lethal a. 致命的,致死的▲disable vt. 使丧失能力,使伤残Phrases and Expressionscrop up (问题等)突然发生,突然出现act out 表演nothing more (…) than 只不过,仅仅是up to scratch 达到标准,合格,处于良好状态be on the wrong end of 承担(……)的不利后果law and order 法律和秩序throw up 产生,使……突出,匆匆建造on duty 值班,当班on sick leave 休病假in favor 赞同,支持derive from 来自,源于,从……中得到wash away 冲掉,冲走lose count of 数不清,不清楚……的确切数目come up to 走近,靠近carry out 开展,执行take up 占据(时间、空间等)Proper NamesNorthumbria 诺森布里亚郡(地名, 位于英格兰的东北部)John Stevens 约翰·史蒂文斯(人名)Unit9New Words▲contend v. 1.声称2.争夺,竞争; 斗争▲attendance n. 出席人数, 到场人数▲legend n. 传说,传奇故事▲contemplate v. 思量,对……周密考虑Phrases and Expressionsshave off 剃(胡须、毛发等)take sb. to court 对某人提出起诉put before 认为……比……更重要for all 尽管come into 开始进入(某种活动或状态)so far 到目前为止,迄今为止in response to 作为对……的答复,作为对……的反应focus on 把(注意力等)集中在in a flash 转眼间,一眨眼Proper NamesEuro Disneyland 欧洲迪斯尼乐园Mickey Mouse 米老鼠(Walt Disney创造的儿童性格的雄性老鼠动画形象)TGV abbr. (法)高速电气铁路Sleeping Beauty 睡美人(法国童话中因着魔而昏睡100年的公主)Snow White 白雪公主Peter Pan 彼得·潘(苏格兰剧作家James Barrie所著剧本名及其中的主角,一个不肯长大的小孩)Pinocchio 匹诺曹(同名故事和电影中的主角,一个木偶男孩,说谎时,他的鼻子就变长)Walt Disney World 沃尔特·迪斯尼世界Jules Verne 儒勒·凡尔纳(1820-1905,法国小说家,现代科学幻想小说的奠基人)the Louvre 罗浮宫(法国国立美术博物馆,位于巴黎)Minnie Mouse 米尼老鼠(Walt Disney 创造的儿童性格的雌性老鼠动画形象)Mona Lisa 《蒙娜·丽莎》(欧洲文艺复兴时期意大利画家达·芬奇所作的一幅著名肖像画)New Words◆franc n. 法郎■analyst n. 分析家Phrases and Expressionsgear up (使)准备好,作好安排warn against 告诫,提醒(某人)以防备(……的危险等)react to (对……)作出反应be superior to 优于on a /an… basis 以……方式in the long term 从长远来说,长期来说hang over (威胁、危险等)临头,笼罩,迫近account for (指数量等)占解释,说明(原因等)in line with 与……一致,符合,按照Proper NamesJohn Forsgren 约翰·佛斯格伦(人名)Paribas Capital Markets Group 帕里巴斯资本市场集团Unit10New Words◆EQ n. 情商◆IQ n. 智商▲incorporate vt. 把……合并,使并入◆maturity n. 成熟情况; 成熟时期▲trigger vt. 触发,引起Phrases and Expressionsmake a contribution to 对……作出贡献sort through 整理,捡出aim at 旨在,追求on purpose 故意,特意in the act of doing (sth.) 正在做某事时take note of 注意,注意到set aside 拨出,留下以备将来使用reflect on/upon 思考,考虑,沉思pull away from 使脱身,使脱离keep at 继续做,坚持干Proper NamesDaniel Goleman 丹尼尔·戈尔曼(人名)Emotional Intelligence 《情感智能》Time 《时代周刊》Karen Boylston 凯伦·波尔斯顿(人名)New Words◆upbeat a. 乐观的; 快乐的,愉快的Phrases and Expressionsturn out 结果是,证明为interact with 互相交流,互相影响hold out 坚持,支持,维持shy away from (由于厌恶、害怕、缺乏信心等)躲开,回避,退缩show up 出现,露面end up 结束,告终on sight/at sight 一见到就in(the) face of 尽管,不顾在……面前be about to do sth. 刚要做某事,行将做某事,打定主意要…… thanks to 幸亏,由于at first glance 乍一看,乍看上去have authority over 对……有控制能力,对……有管辖权substitute for 替代,用……来代替break out 发生,爆发,突然开始be blessed with 有幸得到,具有count for 值,计Proper NamesJerome Kagan 杰罗姆·凯根(人名)。
Official Journal of the European Communities

COMMISSION DECISIONof27June2002amending Annex II of Directive2000/53/EC of the European Parliament and of the Council onend-of-life vehicles(notified under document number C(2002)2238)Text withEEA relevance)(2002/525/EC)THE COMMISSION OF THE EUROPEAN COMMUNITIES,Having regard to the Treaty establishing the European Commu-nity,Having regard to Directive2000/53/EC of the European Parlia-ment and of the Council of18September2000on end-of-life vehicles(1),and in particular Article4(2)(b)thereof,Whereas:(1)Under Directive2000/53/EC the Commission is requiredto evaluate certain hazardous substances prohibited pur-suant to Article4(2)(a)of that Directive.(2)Having carried out the requisite technical and scientificassessments the Commission has reached a number ofconclusions.(3)Certain materials and components containing lead,mer-cury,cadmium or hexavalent chromium should be ex-empt or continue to be exempt from the prohibition,since the use of these hazardous substances in those spe-cific materials and components is still unavoidable.(4)Some exemptions from the prohibition for certain speci-fic materials or components should be limited in theirscope and temporal validity,in order to achieve a gra-dual phase-out of hazardous substances in vehicles,giventhat the use of those substances in such applications willbecome avoidable.(5)Cadmium in batteries for electrical vehicles should be ex-empt until31December2005since,in view of presentscientific and technical evidence and the overall environ-mental assessment undertaken,by that date,substituteswill be available and the availability of electrical vehicleswill be ensured.The progressive replacement of cad-mium should,however,continue to be analysed,takinginto account the availability of electrical vehicles.TheCommission will publishits findings and,if proven justi-fied by the results of the analysis,may propose an exten-sion of the expiry date for cadmium in batteries for elec-trical vehicles.(6)The exemption from the prohibition relating to lead forcoating inside petrol tanks should be deleted,since theuse of lead in these specific components is already avoid-able.(7)Since it is evident that a total avoidance of heavy metalsis in some instances impossible to achieve,certain con-centration values of lead,mercury,cadmium or hexava-lent chromium in specific materials and componentsshould be tolerated,provided that these hazardous sub-stances are not intentionally introduced.(8)Directive2000/53/EC should therefore be amended ac-cordingly.(9)The measures provided for in this Decision are in accor-dance with the opinion of the Committee established byArticle18of Council Directive75/442/EEC of15July1975on waste(2),as last amended by Commission Deci-sion96/350/EC(3),HAS ADOPTED THIS DECISION:Article1Annex II to Directive2000/53/EC is replaced by the text set out in the Annex to this Decision.Article2Member States shall ensure that cadmium in batteries for elec-trical vehicles is not put on the market after31December 2005.In the framework of the overall environmental assessment al-ready undertaken,the Commission shall continue to analyse the progressive substitution of cadmium,taking into account the need to maintain the availability of electrical vehicles.The Commission shall finalise and make public its findings by31 December2004at the latest and may make,if proven justified by the results of the analysis,a proposal to extend the deadline in accordance withArticle42)b)of Directive2000/53/EC.(1)OJ L269,21.10.2000,p.34.2p.39.(3)OJ L135,6.6.1996,p.32.Article3This Decision shall apply from1January2003.Article4This Decision is addressed to the Member States.Done at Brussels,27June2002.For the CommissionMargot WALLSTRÖMMember of the CommissionMaterials and componentsScope and expiry dateof the exemptionTo be labelled or made identifiablein accordance withArticle42)b)iv) ANNEX‘ANNEX IIMaterials and components exempt from Article4(2)(a)Lead as an alloying element1.Steel for machining purposes and galvanisedsteel containing up to0,35%lead by weight2.a)Aluminium for machining purposes with alead content up to2%by weight1July2005(1)b)Aluminium for machining purposes with alead content up to1%by weight1July2008(2)3.Copper alloy containing up to4%lead byweight4.Lead-bronze bearing shells and bushesLead and lead compounds in components5.Batteries X6.Vibration dampers X7.Wheel balance weights Vehicles type-approved before1July2003and wheelbalance weights intended forservicing of these vehicles:1July2005(3)X8.Vulcanising agents and stabilisers for elastomersin fluid handling and powertrain applications1July2005(4)9.Stabiliser in protective paints1July200510.Carbon brushes for electric motors Vehicles type-approved before1July2003and carbonbrushes for electric motorsintended for servicing of thesevehicles:1January200511.Solder in electronic circuit boards and otherelectric applicationsX(5)12.Copper in brake linings containing more than0,5%lead by weight Vehicles type-approved before1July2003and servicing onthese vehicles:1July2004X13.Valve seats Engine types developed before1July2003:1July2006Materials and components Scope and expiry dateof the exemptionTo be labelled or made identifiablein accordance withArticle42)b)iv)14.Electrical components which contain lead in aglass or ceramic matrix compound except glass in bulbs and glaze of spark plugs X(6)(for components other than piezo in engines)15.Glass in bulbs and glaze of spark plugs1January200516.Pyrotechnic initiators1July2007Hexavalent chromium17.Corrosion preventive coatings1July200718.Absorption refrigerators in motorcaravans XMercury19.Discharge lamps and instrument panel displays XCadmium20.Thick film pastes1July200621.Batteries for electrical vehicles After31December2005,theplacing on the market ofNiCd batteries shall only beallowed as replacement partsfor vehicles put on the marketbefore this date.X(1)By1January2005the Commission shall assess whether the phase-out time scheduled for this entry has to be reviewed in relation to theavailability of substitutes for lead,taking into account the objectives of Article4(2)(a).(2)See footnote1.(3)By1January2005,the Commission shall assess this exemption in relation to road safety aspects.(4)See footnote1.(5)Dismantling if,in correlation with entry14,an average threshold of60grams per vehicle is exceeded.For the application of this clause,electronic devices not installed by the manufacturer on the production line shall not be taken into account.(6)Dismantling if,in correlation with entry11,an average threshold of60grams per vehicle is exceeded.For the application of this clause,electronic devices not installed by the manufacturer on the production line shall not be taken into account.Notes:—a maximum concentration value up to0,1%by weight and per homogeneous material,for lead,hexavalent chromium and mercury and up to0,01%by weight per homogeneous material for cadmium shall be tolerated, provided these substances are not intentionally introduced(1),—a maximum concentration value up to0,4%by weight of lead in aluminium shall also be tolerated provided it is not intentionally introduced(2),—a maximum concentration value up to0,4%by weight of lead in copper intended for friction materials in brake linings shall be tolerated until1July2007provided it is not intentionally introduced(3),—the reuse of parts of vehicles which were already on the market at the date of expiry of an exemption is allowed without limitation since it is not covered by Article4(2)(a),—until1July2007,new replacement parts intended for repair(4)of parts of vehicles exempted from the provisions of Article4(2)(a)shall also benefit from the same exemptions.’(1)“Intentionally introduced”shall mean“deliberately utilised in the formulation of a material or component where its continuedpresence is desired in the final product to provide a specific characteristic,appearance or quality”.The use of recycled materials as feedstock for the manufacture of new products,where some portion of the recycled materials may contain amounts of regulated metals,is not to be considered as intentionally introduced.(2)See footnote1.(3)See footnote1.(4)This clause applies to replacement parts and not to components intended for normal servicing of vehicles.It does not apply towheel balance weights,carbon brushes for electric motors and brake linings as these components are covered in specific entries.。
European Union

European Ombudsman (deals with citizens' complaints about maladministration by any EU institution or body);
40% of population work in industry
37% of population work in service
By 2001, 15 members
4% of population relied on farming for job.
29% of population work in industry
Chronology of EU.
1967 The Merger Treaty enters into force on July 1
1973 1979
1981 1985
The United Kingdom, Ireland, and Denmark join the European Community (EC).
2
Chronology of EU.
1952 1958 1965
3
Six countries - Belgium, France, the Federal Republic of Germany, Italy, Luxembourg and the Netherlands - create the European Coal and Steel Community (ECSC) by pooling their coal and steel resources in a common market controlled by an independent supranational authority.
European Union语法填空

European Union语法填空(后附答案解析)【语法填空】The European UnionThe European Union is an 1 (organise) of European countries. The countries are independent and 2 (govern) in different ways. But each of them 3 (send) representatives to the European Parliament, 4 has some control over what happens in each of the member countries.The idea of the European Union 5 (begin) in the 1950s. The first members were France, Germany, Belgium, Luxembourg, the Netherlands and Italy. Little by little, the number increased during the second half of the twentieth century. By the year 2000, there 6 (be) 15 member countries.In 2004, the European Union increased 7 25 members.The 8 (expand) European Union has 9 population of more than half a billion people, 10 (two) as big as the population of the United States.【答案】1. organization2. are governed3. sends4. which5. began6. were7. to8. expanded9. a10. twice【解析】anisation考查名词。
the European Communities

WonderWeb Deliverable D16Reusing semi-structured terminologies for ontology building: A realistic case study in fishery information systemsAldo Gangemi ISTC-CNR email: a.gangemi@r.itIdentifier Class Version Date Status Distribution Lead PartnerD16 Deliverable 1.0 7-05-2004 public ISTC-CNR1IST Project 2001-33052 WonderWeb: Ontology Infrastructure for the Semantic WebiiIST Project 2001-33052 WonderWeb: Ontology Infrastructure for the Semantic WebWonderWeb ProjectThis document forms part of a research project funded by the IST Programme of the Commission of the European Communities as project number IST-2001-33052. For further information about WonderWeb, please contact the project co-ordinator:Ian Horrocks The Victoria University of Manchester Department of Computer Science Kilburn Building Oxford Road Manchester M13 9PL Tel: +44 161 275 6154 Fax: +44 161 275 6236 Email: wonderweb-info@iiiIST Project 2001-33052 WonderWeb: Ontology Infrastructure for the Semantic WebRevision InformationRevision Version date 5-05-2004 V1.0 ChangesivIST Project 2001-33052 WonderWeb: Ontology Infrastructure for the Semantic WebTable of Contents11.1 1.2INTRODUCTION................................................................... 6Bootstrapping dedicated semantic webs. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6 A bit of history. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 722.1 2.2 2.3THE FISHERY CASE STUDY: RESOURCES, ISSUES, AND METHODS ........................................................................... 8Resources . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8 Some issues . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9 Some methods. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1 133.1 3.2 3.3 3.4KOS REENGINEERING LIFECYCLE .....................................12Formatting and lifting. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1 2 Formalization, and Core ontology building . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1 4 Modularization, and alignment. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1 7 Annotation, refinement, merging. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2 044.1 4.2 4.3POST-PROCESSING LIFECYCLE ........................................24Services for information retrieval. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2 5 Services for distributed database querying . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2 6 Tools .................................................................................... 2 75 6FURTHER DISCUSSION ON THE CASE STUDY AND ITS RELEVANCE TO THE SEMANTIC WEB ................................29 REFERENCES ....................................................................31vIST Project 2001-33052 WonderWeb: Ontology Infrastructure for the Semantic Web1 Introduction1.1 Bootstrapping dedicated semantic websA main issue in the deployment of the Semantic Web (SW) is currently its population: very few ontologies and tagged documents exist in comparison to the huge amount of domains and documents that exist on the Web. Several strategies are being exploited to bootstrap the SW: machine learning [1,2,3], NLP techniques [4,5], semantic services [6], lifting existing metadata [7,8,9,10,11,12], etc. These strategies have different advantages according to the type of documents or domains: while machine learning and NLP techniques try to extract useful recurrent patterns out of existing (mostly free text or semi-structured) documents, and semantic services try to generate semantically indexed, structured documents e.g. out of transactions, existing metadata can be considered proto-ontologies that can be "lifted" from legacy indexing tools and indexed documents. In other words, metadata lifting ultimately tries to reengineer existing document management systems into dedicated semantic webs.1 Legacy information systems often use metadata contained in Knowledge Organization Systems (KOSes), such as vocabularies, taxonomies and directories, in order to manage and organize information. KOSes support document tagging (thesaurus-based indexing) and information retrieval (thesaurus-based search), but their semantic informality and heterogeneity usually prevent a satisfactory integration of the supported documentary repositories and databases. As a matter of fact, traditional techniques mainly consist of time-consuming, manual mappings that are made – each time a new source or a modification enter the lifecycle – by experts with idiosyncratic procedures. Informality and heterogeneity make them particularly hostile with reference to the SW. This document describes the methodology used for the creation, integration and utilization of ontologies for information integration and semantic interoperability, with respect to a case study: fishery information systems. Such a case study, which is definitely not a toy example, has been the target of an institutional project carried out by CNR and UN-FAO, which exploited the DOLCE ontology and the methods developed within the WonderWeb project, as well as previous methodologies developed in the past by ITBM-CNR2 We describe various methods to reengineer, align, and merge KOSes in order to build a large fishery ontology library. Some examples of semantic services based on it, either for a simple one-access portal or a sophisticated web application are also sketched, which envisage a fishery semantic web. With respect to the main threads of WonderWeb (languages, tools, foundational ontologies, versioning, and modularity), we concentrate this section on a demonstration of KOS reengineering issues from the viewpoint of formal ontology, therefore the main threads will appear in the context of the case study description rather than as explicitly addressed topics. We assume a basic knowledge of the deliverable D18 for full comprehension of this section.1Notice that the different strategies are not mutually exclusive, but can be combined. In the FOS project, we have also used techniques from NLP and semantic services. 2 The former ontology group of ITBM-CNR has now joined ISTC-CNR6IST Project 2001-33052 WonderWeb: Ontology Infrastructure for the Semantic WebWe thank the UN-FAO WAICENT-GILW department for allowing us to reuse in this deliverable some of the FOS project documentation.1.2 A bit of historyIn the beginning of 2002 the Food and Agriculture Organization of the United Nations (FAO, in the following)1 , based in Rome, took action in order to enhance the quality of its information and knowledge services related to fishery. The following internal agencies were asked to participate into a task-force by providing manpower and/or data, information or knowledge repositories: FAO Fishery Department2 provided the reference tables of its Internet portal, the Fishery Global Information System (FIGIS). ASFA secretariat3 , the managing body of the Aquatic Sciences and Fisheries contributed its online thesaurus for fishery. SIFAR, the Support unit for International Fisheries and Aquatic Research4 , contributed the contents and the structure of the oneFish community directory. FAO WAICENT, the World Agricultural Information Centre5 , provided access, through its office for General Information Systems and Digital Libraries (GILW), to the fishery part of the AGROVOC Thesaurus. FOS naturally fitted the wider AOS (Agriculture Ontology Service) long-term programme6 , started by FAO at the end of 2001, of which FOS constitutes one major case study (together with the Food Safety project [12], and others). The scientific coordination and supervision of the FOS project was assigned to the Laboratory for Applied Ontology of the Institute of Cognitive Sciences and Technology of the Italian National Research Council (LOA, in the following)7 . The outline of the project and the preliminary methods have already been presented in [13]. Here we describe some salient aspects of the FOS project after the completion of the first phase (2002-2003), which show the principles (and their applicability) that can be adopted when reengineering semi-structured KOSes into formal ontologies, in formats and with the tools envisaged by the WonderWeb project. Section 2 describes the sources that were subject to reengineering, integration, alignment, and merging, and the general issues and principles. Section 3 presents the methodology with more detail, an outline of the global results, and provides some examples of the interoperability between the sources, which was achieved. Finally, section 4 draws some conclusions.1 2 /figis/servlet/FiRefServlet?ds=staticXML&xml=webapps/figis/wwwroot/fi/figis/index.x ml&xsl=webapps/figis/staticXML/format/webpage.xsl 3 /fi/asfa/asfa.asp 4 /global/about.htm 5 /WAICENT/ 6 /agris/aos 7 http://www.loa-cnr.it7IST Project 2001-33052 WonderWeb: Ontology Infrastructure for the Semantic Web2 The fishery case study: resources, issues, and meth ods2.1 ResourcesThe following resources have been singled out from the fishery information systems considered: OneFish topic trees OneFish [14] is a portal for fishery activities and a participatory resource gateway for the fisheries and aquatic research and development sector. It contains heterogeneous data, organized through hierarchical topic trees (more than 1,800 topics, increasing regularly), made up of hierarchical topics with brief summaries, identity codes and attached knowledge objects (documents, web sites, various metadata). The hierarchy (average depth: 3) is ordered by (at least) two different relations: subtopic, and intersection between topics, the last being notated with @ , similarly to relations found in known subject directories like DMOZ. There is one 'backbone' tree consisting of five disjoint categories, called worldviews (subjects, ecosystem, geography, species, administration) and one worldview (stakeholder), maintained by the users of the community, containing own topics and topics that are also contained in the first four other categories (Figure 5). Alternative trees contain new 'conjunct' topics deriving from the intersection of topics belonging to different categories. AGROVOC thesaurus AGROVOC [15] has been developed by FAO and the Commission of the European Communities in the early 1980s and is used for document indexing and retrieval. It is a multilingual structured and controlled vocabulary designed to cover the terminology of all subject fields of agriculture, forestry, fisheries, food and related domains (e.g. environment) in order to describe the documents in a controlled language system. Different hierarchical and associative relations (broader/narrower terms, related terms, equivalent terms, used for) are established between the terms. AGROVOC contains approximately 2,000 fishery related descriptors out of about 16,000 descriptors. ASFA thesaurus ASFA [16] is an abstracting and indexing service covering the world's literature on the science, technology, management, and conservation of marine, brackishwater, and freshwater resources and environments, including their socio-economic and legal aspects. The thesaurus is an online service, which provides terminological definitions in terms of various relations, e.g. narrower term, related term, used for. It consists of more than 6,000 descriptors. FIGIS reference tables FIGIS [17] is a global network of integrated fisheries information. Presently its thematic sections are four: aquatic species (i.e. biological information); geographic objects (water and continental areas, political geographic entities); marine resources (information on the state of world resources, data on regional fish stocks, major issues affecting stocks); marine fisheries (data and maps on the exploitation of the major species, management-related information) fishing technologies (information on high seas vessels identification, on the selection of technologies and on training and on international legal issues). The FIGIS reference tables comprise all the contents of this huge database. The reference tables consists of approximately 200 top-level concepts, with a max depth of 4, 30,000 'objects'8IST Project 2001-33052 WonderWeb: Ontology Infrastructure for the Semantic Web(mixed concepts and individuals), relations (specialized for each top category, but scarcely instantiated) and multilingual support. FIGIS DTDs Some XML Document Types Definitions (now moving to RDFS) are also maintained by FIGIS to organize their databases. The original set included 823 elements with a rich attribute structure. Those related to fishery ontologies have been taken into account.2.2 Some issuesAs mentioned in the introduction the sources to be integrated were rather variate under many perspectives(semantic, lexical and structural).9IST Project 2001-33052 WonderWeb: Ontology Infrastructure for the Semantic WebAQUACULTURE (AGROVOC) NT1 fish culture NT2 fish feeding NT1 frog culture … rt agripisciculture rt aquaculture equipment … Fr aquaculture Es acuicultura AQUACULTURE (ASFA) NT Brackishwater aquaculture NT Freshwater aquaculture NT Marine aquaculture rt Aquaculture development rt Aquaculture economics rt Aquaculture engineering rt Aquaculture facilitiesBiological entity (FIGIS) Taxonomic entity Major group Order Family Genus Species Capture species (filter) Aquaculture species (filter) Production species (filter) Tuna atlas spec SUBJECT (OneFish) Aquaculture Aquaculture development Aquaculture economics @ Aquaculture planningTable 1. Sample aquaculture descriptors in the four resources. NT means narrower than; rt means related term, Fr and Es are the corresponding French and Spanish terms)An example of how formal ontologies can be relevant for fishery information services is shown by the information that someone could get if interested in aquaculture (Tab. 1). In fact, beyond simple keyword-based searching, searches based on tagged content or sophisticated natural-language techniques require some conceptual structuring of the linguistic content of texts. The four systems concerned by this case study provide this structure in very different ways and with different conceptual “textures”. For example (Tab. 1), the AGROVOC and ASFA thesauri put aquaculture in the context of different thesaurus hierarchies. The AGROVOC thesaurus seems to conceptualize aquaculture types from the viewpoint of techniques and species. ASFA aquaculture hierarchy is substantially different, since the hierarchy seems to stress the environment and disciplines related to aquaculture. A different resource is constituted by the so-called reference tables in FIGIS system; the only reference table mentioning aquaculture puts it into another context (taxonomical species). The last resource examined is oneFish directory, which returns a context related to economics and planning. With such different interpretations of aquaculture, we can reasonably expect different search and indexing results. Nevertheless, our approach to information integration and ontology building is not that of creating a homogeneous system in the sense of a reduced freedom of interpretation, but in the sense of navigating alternative interpretations, querying alternative systems, and conceiving alternative contexts of use. Once made clear that different fishery information systems provide different views on the domain, we directly enter the paradigm of ontology integration, namely the integration of schemas that are arbitrary logical theories, and hence can have multiple models (as opposed to database schemas that have only one model) [19]. As a matter of fact, thesauri, topic trees and reference tables used in the systems to be integrated could be considered as informal schemata conceived in order to query semistructured or informal databases such as texts, forms and tagged documents. In order to benefit from the ontology integration framework, we must transform informal schemata into formal ones. In other words, thesauri and other terminology management resources must be transformed into formal ontologies. In order to do this, we require a comprehensive set of ontologies that are designed in a way that admits the existence of many possible pathways among concepts under a common conceptual framework. In our opinion, the framework should: — reuse domain-independent ontologies shared by the resources, in order to make the different components interoperate 10—be flexible enough, so that different views have a common context—be focused on the core reasoning schemata for the fishery domain, otherwise the common conceptual framework would be too abstract.Domain-independent, foundational ontologies [18] characterise the general notions needed to talk about economics, biological species, fish production techniques; for example: parts, agents, attribute, aggregates, activities, plans, devices, species, regions of space or time, etc.Furthermore, so-called core ontologies [18] characterise the main conceptual schemata that the members of the fishery community use to reason, e.g. that certain plans govern certain procedures involving certain devices applied to activities like capturing fish of a certain species in certain areas of water regions, etc.Foundational and core ontologies provide the framework to integrate in a meaningful and intersubjective way different views on the same domain, such as those represented by the queries that can be done to a set of distributed information systems containing (un)structured data.2.3 Some methodsIn order to perform this reengineering task, we have applied the techniques of three methodologies: ap-plication of DOLCE foundational principles introduced in WonderWeb D18 [18], ONIONS [20], and OnTopic [21].WonderWeb D18 contains principles for building and using foundational ontologies for core and domain ontology analysis, revision, and development. DOLCE is an axiomatic, domain-independent theory based on formal principles.ONIONS is a set of methods for reengineering (in)formal domain metadata, such as glossaries, terminologies, data models, conceptual schemata, business models, etc. to the status of formal ontology data types, for integrating them in a common formal structure, for aligning them to a foundational ontology, and for merging them. Some methods are aimed at reusing the structure of hierarchies (e.g., BT/NT relations, subtopic relation, etc.), the additional relations that can be found (e.g., RT relations), and at analysing the compositional structure of terms in order to capture new relations and definitional elements. Other methods concern the management of semantic mismatches between alternative or overlapping ontologies, and the exploitation of systematic polysemy t o discover relevant domain conceptual structures.OnTopic is about creating dependencies between topic hierarchies and ontologies. It contains methods for deriving the elements of an ontology that describe a given topic, and methods to build “active” topics that are defined according to the dependencies of any individual, concept, or relation in an ontology. OnTopic has only suggested design decisions in the case study.In section 3, we describe these methods as used in the KOS reengineering lifecycle, the types of data extracted from the fishery resources, with examples of their porting, translation, transformation, and refinement.In section 4 we finally give a resume of the tools tested and/or endorsed in the case study.3 KOS REENGINEERING LIFECYCLEIn Fig.s 1,3,6,8,9, a UML "activity diagram" is shown that summarizes the main steps of the methods we have followed to create the Fishery Ontology Library (FishOL). For the sake of readability, we have split the activity diagram into five pieces as follows:1)Terminological database (TDB) formatting and schema lifting2)TDB porting, formalization, and Core ontology building3)Modularization, ontology library building, and alignment to reference ontologies4)Annotation, refinement, and merging of the library5)Measures for finalisation, maintenance, and exploitation3.1Formatting and liftingIn the first phase of the lifecycle (Fig. 1), the original terminological databases are im-ported into a common database format. The conceptual schemata of the databases are lifted (either manually, or by using automatic reverse engineering components [11]). At the same time, a common Ontology Data Model (ODM) should be chosen. This can be partly derived from the semantics of ontology representation languages (e.g. the OWL ODM [22]), enhanced with criteria for distinguishing the different data types at the onto-logical level (e.g. individual, class, meta-property, relation, property name, lexicon, etc.). Ontologically explicit ODMs are described in [23,24].With the help of the ODM, lifted schemata can be translated and then integrated (the integration methodology assumed is [19]).In FOS, the original TDBs resulted to be syntactically heterogeneous, specially FIGIS with respect to ASFA and AGROVOC. In fact, the first is controlled through a set of XML DTDs (currently moving to RDFS), while the seconds are implemented in relational databases with one basic relational table.Semantically, TDB schemata are even more heterogeneous (see Table 1 for examples). ASFA is a typical thesaurus, made up of descriptors (equivalence classes of terms with the same assumed meaning), equivalent terms, and relations among descriptors (BT, NT, RT, UF) that create a forest structure (an indirect acyclic graph, [25]). Descriptors are encoded via a "preferred" term. AGROVOC is also a thesaurus, but contains multilingual equivalent terms, and descriptors are encoded via alphanumeric codes. FIGIS is not a thesaurus, but a collection of TDBs organised into modules containing different domain terminologies, e.g. vessels, organisms, techniques, institutions, etc. Equivalence classes of multilingual terms are defined (similar to thesaurus descriptors). Each equivalence class has an identification code. Each module has a peculiar schema including local relations defined on (classes of) classes of terminological equivalence classes. E.g., a relation between institutions and countries, a relation between vessels and techniques, between organism species and genera, etc.Figure 1. A UML activity diagram for formatting and lifting activities.These relations are more informative than generic RT thesaurus relations (see phase 2 about additional transforms to TDB).FIGIS DTDs encode heterogeneous metada for the management of the FIGIS database. These XML elements can refer to domain-specific information (e.g. "Location"), datatypes (e.g. "Date"), data about data (e.g. "Available"), foreign keys (e.g. "AqSpecies_Text").AdministrationSubjects EcosystemStakeholdersGeography SpeciesFig. 2. Topic spaces ("worldviews") in oneFish.Finally, OneFish is a tree structure of subjects (keywords used to classify documents), with multihierarchical links, similar to Web directories like DMOZ [26]. The top subjects in OneFish are depicted in Fig. 2.The integrated schema results to include all the data types from the TDBs. On the other hand, we needed to interpret the original data types into an (onto)logically valid integrated schema. Therefore, we have created a mapping from each (domain-related) legacy data type to an ODM data type, e.g. owl:Class, to which "descriptor" and "FIGIS equivalence class" have been mapped, owl:ObjectProperty, to which "RT" and most FIGIS relations have been mapped (as instances), topic, to which OneFish "subject" has been mapped, etc.As explained below, some adjustments are needed to the original TDBs in order to preserve a correct semantics when translating some elements to the integrated schema.3.2Formalization, and Core ontology buildingAfter a common format and an integrated ontology data model have been obtained, the second phase (Fig. 3) starts by choosing an Ontology Representation Language (ORL).E.g., in FOS some tests have been performed at the beginning of the project, and we have decided to take a layered approach, maintaining the TDBs into different ontology re-positories represented into languages of increasing expressivity. RDF(S) [27] has been chosen for the basic layer, DAML+OIL [28] (currently OWL-DL [22]) for the middle layer, and KIF [29] for the expressive layer.The reason for such layering resides in a) the necessity of carrying out certain ontology learning procedures (see phase 4) with the expressive version, b) the necessity of using the standard Semantic Web ontology languages to carry out inferences with the middle layer, and c) the necessity of maintaining a lightweight ontology with the basic layer. RDF(S) can also be used to import the original TDBs without using the ODM. In fact, a preliminary decision was required when deciding how the ontologies that were obtained from the TDBs should get used.1The first choice has been to preserve the TDB elements into the original data models. In this case, no mapping has been performed from original data models to the ODM, and only an integrated (non-refined) data model has been used. The advantage of this choice is that no interpretation is performed on the legacy TDBs, but there are two disadvantages: translated TDBs are not (proto-)ontologies, but RDF models, hence no ontology inferencing can be made using them; imported TDBs cannot be aligned or merged, but only integrated.The second choice has been to translate the TDBs according to the ODM, then interpreting and mapping the original data models, and making needed refinements in order to preserve the semantics of ODM. This solution overcomes the disadvantages of the first choice at the cost of making interpretations. E.g. in FOS the maintainers of the legacy TDBs are members of the task-force, then we can expect that interpretations are not harmful. In other contexts – specially if experts are not collaborating –interpretations may be more problematic.Figure 3. The activity diagram for metadata formalization and Core ontology building.In the case study, the first choice has been easily produced through a rather economic procedure. Most efforts have then been put into translating and sometimes transforming the TDBs into proto- and then full-fledged ontologies. In particular, a translation t o1 A similar problem is discussed in the W3C SW Best Practices and Deployment Working Group wrt to wordnets and thesauri [30].ODM data types has been performed.For certain terminological data types, a refinement is performed at this stage and after alignment (see phase 3).For example, AGROVOC makes no difference between descriptors denoting owl:classes (e.g. agrovoc:River), and descriptors denoting owl:individuals (e.g. agrovoc:Amazon). Most individuals have been found in subdomains like geography and institutions. Another example concerns thesauri relations: while RT (Related Term) needs no refinement wrt ODM: it is imported as a subproperty of owl:ObjectProperty holding between individuals (and defined on classes), and UF is an owl:DatatypeProperty holding between lexical items (strings), on the contrary BT (Broader Term) is usually the rdfs:subClassOf property, but sometimes it is used as a "part of" owl:ObjectProperty. Translation and refinement have been complemented by transforming the applications of RT and of owl:ObjectProperties from FIGIS into formal owl:Restrictions.The working hypotheses in making these transformations are that:—the resulting owl:Restrictions are inheritable to all the subclasses of the rdfs:class to which the restriction pertain, and—the quantification applicable to restrictions is owl:someValuesFromBoth hypotheses result confirmed in most FOS cases, e.g. in AGROVOC, from the original record:<Fishing vessel> <RT> <Fishing gear>it is semantically correct to derive the following transform (we use OWL abstract syntax [31] for most examples in this section of the deliverable):Class(agrovoc:Fishing_vessel partial(restriction(agrovoc:RT someValuesFrom(agrovoc:Fishing_gear))))Figure 4. The DOLCE+ top level.In phase 4 we explain that RT restrictions can be refined in order to make their intended meaning more precise.A concurrent task has been performed during the translation and tranformation phase, which provides the means to fulfil the tasks in phase 3. Such task is about the construction of a Core Ontology, in this case study a Core Ontology of Fishery (COF). For the many theoretical underpinnings in core ontology construction that come from modularization and reuse wrt foundational ontologies, we refer to [18]. As an example, we only provide here a basic description of COF and of the reusable reference ontologies that have been employed.COF has been designed by specializing the DOLCE-Lite-Plus ("DOLCE+" in the following, Fig. 4 shows the most general classes) ontology[18], developed within。
COMMISSION OF THE EUROPEAN COMMUNITIES DIRECTORATE-GENERAL INFORMATION SOCIETY

COMMISSION OF THE EUROPEAN COMMUNITIESDIRECTORATE-GENERAL INFORMATION SOCIETYThe IST ProgrammeCost reimbursement contract for research and technological development projectsFuture and Emerging TechnologiesAction Line: IST-2001-6.2.2PEPITOPeer-To-Peer-Implementation-and-TheOryContract Number IST-2001-33234CONTRACT No IST-2001-33234The European Community ("the Community"), represented by the Commission of the European Communities ("the Commission"), itself represented in view of the signature of this contract by Mr Robert Verrue, Director-General for Information Society or his duly authorised representative,of the one partand-SICS, SWEDISH INSTITUTE OF COMPUTER SCIENCE AB (SICS) ("the coordinator"), established in SWEDEN - ISAFJORDSGATAN 22, 164 29 KISTA, represented by its legal/statutory representative[s], DR. GUNNAR BJUREL, MANAGING DIRECTOR and/or MR JANUSZ LAUNBERG, BUSINESS MANAGER or his/her/their authorized representative[s],-ECOLE POLYTECHNIQUE FEDERALE DE LAUSANNE (EPFL), established in SWITZERLAND - ECUBLENS, 1015 LAUSANNE, represented by its legal/statutory representative[s], PROFESSOR MARTIN ODERSKY, DIRECTOR and/or ASSISTANT PROFESSOR RACHID GUERRAOUI, DIRECTOR or his/her/their authorized representative[s],-INSTITUT NATIONAL DE RECHERCHE EN INFORMATIQUE ET EN AUTOMATIQUE (INRIA), established in FRANCE - DOMAINE DE VOLUCEAU, ROCQUENCOURT, 78153 LE CHESNAY, represented by its legal/statutory representative[s], PROFESSOR JEAN-PIERRE BANATRE, DIRECTOR or his/her/their authorized representative[s],-KUNGLIGA TEKNISKA HOGSKOLAN (KTH), established in SWEDEN -VALHALLAVAEGEN 79, 100 44 STOCKHOLM, represented by its legal/statutory representative[s], PROFESSOR ANDERS FLODSTRÖM, PRESIDENT or his/her/their authorized representative[s],-THE CHANCELLOR, MASTERS AND SCHOLARS OF THE UNIVERSITY OF CAMBRIDGE (UCAM), established in UNITED KINGDOM - THE OLD SCHOOLS, TRINITY LANE, CAMBRIDGE CB2 1TS, represented by its legal/statutory representative[s], MS KATHLEEN GRAY, CONTRACTS AND APPLICATIONS MANAGER and/or MS JENNY WALSHAM, CONTRACTS AND APPLICATIONS MANAGER or his/her/their authorized representative[s],-UNIVERSITE CATHOLIQUE DE LOUVAIN (UCL), established in BELGIUM - 1 PLACE DE L'UNIVERSITE, 1348 LOUVAIN-LA-NEUVE, represented by its legal/statutory representative[s], PROF. MARCEL CROCHET, RECTOR and/or PROF.MICHEL MOLITOR, VICE-RECTOR or his/her/their authorized representative[s],(collectively "the principal contractors"),of the other part,(collectively ″the contracting parties″)HAVE AGREED to a project called "Peer-To-Peer-Implementation-and-TheOry" to be carried out in the framework of the specific programme for research, technological development and demonstration on a user-friendly information society (1998-2002), (the “IST Programme”) (the “specific programme”) according to the following provisions.Article 1 - ScopeThe contractors1 shall carry out the work set out in Annex I to this contract up to the milestones specified in Annex I("the project") in accordance with the conditions set out in this contract.Subject to cases of force majeure, the principal contractors shall use reasonable endeavours to achieve the results aimed at by the project and shall carry it out jointly and severally vis-à-vis the Community. The assistant contractors shall use reasonable endeavours to carry out the part of the project specifically assigned to them.Article 2 - Duration1.The duration of the project shall be 36 months from 1 January 2002.2.This contract shall enter into force following its signature by all the contracting parties.This contract shall be completed on the date of the final payment of the Community’s financial contribution. However,-Articles 5, 6 and 8 of this contract,-Article 2(1), first subparagraph, points (a), (d), (e) and (f), Article 2(2) (c), (d), (h) and (j), Article 3(4) and (5), Article 4(5), Article 6, Articles 9 to 21 and Articles 25, 26 and 28 of Annex II to this contractshall continue to apply after that date to the extent of any limitations specified in those Articles.Article 3 - Estimated costs and maximum financial contribution of the Community1.The total estimated eligible costs of the project are EUR 2,777,458 (TWO MILLIONSEVEN HUNDRED SEVENTY-SEVEN THOUSAND FOUR HUNDRED FIFTY-EIGHT euro).1The terms in italics are used in accordance with the definition given in Article 1 of Annex II to this contract.2.The Community shall fund the eligible costs of the project in accordance with the table of theindicative breakdown of the estimated eligible costs which follows the signatures to this contract up to a maximum of EUR 1,771,000 (ONE MILLION SEVEN HUNDRED SEVENTY-ONE THOUSAND euro).3.The Community's financial contribution to the project shall be paid as specified in Article 3 ofAnnex II to this contract to the coordinator's following bank account:Beneficiary name :SWEDISH INSTITUTE OF COMPUTER SCIENCE CICS Bank :SVENSKA HANDELSBANKENAddress :11, BLASIEHOLMSTORGSTOCKHOLMSWEDENAccount Number : 692138171848Payment Reference…………….IST-2001-33234The initial advance for the project is fixed at EUR 708,400 (SEVEN HUNDRED EIGHT THOUSAND FOUR HUNDRED euro). It is distributed among the contractors in accordance with the indications laid down in the table of the indicative breakdown of the estimated eligible costs.The total amount of the initial advance and the periodic payments shall not exceed the maximum amount of the Community's financial contribution referred to in paragraph 2 of this Article, lessa guarantee retention. The guarantee retention shall be 15% of the maximum amount of thatcontribution.Article 4 – Project deliverables and summary statements of amounts transferred by the coordinator to be submitted to the Commission1. 3 copies of the reports and of the cost statements required under this contract shall besubmitted by the coordinator in accordance with Article 4 of Annex II to this contract. The reports shall be in English.Annex I to this contract shall determine the number of copies and the language of drafting of the other project deliverables.2.The periodic and final reports, the corresponding cost statements, including each integrated coststatement, as well as each summary statement of amounts transferred to the contractors by the coordinator shall cover successive periods of 12 months from the project commencement date.Where the work is completed before the end of the duration of the project, the final report(s) and the corresponding cost statements, including the integrated cost statement, as well as the summary statement of amounts transferred to the contractors by the coordinator shall cover the period ending on such date.However, and without prejudice to the first or second subparagraph of this paragraph, the last cost statement of the coordinator and integrated cost statement shall also cover the periodnecessary for the drafting of the final report(s) within the maximum time limit of two months as of the end of the duration of the project.The other project deliverables, except the technological implementation plan, shall cover the periods set out in Annex I to this contract.The technological implementation plan shall cover the results of work performed within the duration of the project or until the work is completed if such completion occurs at an earlier date.Article 5 - Applicable law and jurisdiction1.The law of BELGIUM shall govern this contract.2.The Court of First Instance of the European Communities and, in the case of an appeal, theCourt of Justice of the European Communities shall have sole jurisdiction to hear any disputes between the Community, on the one hand, and the contractors, on the other hand, as regards the validity, the application or any interpretation of this contract.Article 6 - Special conditionsIn addition to the special conditions set out in Annex III, the following special conditions shall apply to this contract:6.1On the date of signature of this contract, "A ssociated States" means Bulgaria, the CzechRepublic, the Republic of Cyprus, Estonia, Hungary, Iceland, Israel, Latvia, Liechtenstein, Lithuania, Norway, Poland, Romania, Slovakia and Slovenia.Subject to its final conclusion, the Association Agreement signed with the Swiss Confederation is expected to enter into force on 1 January 2001.6.2Insert at the end of Article 3(2) of this contract: "Where the eligible costs of the project arelower than the total estimated eligible costs of the project, the financial contribution from the Community shall be limited to the sum calculated by application of the rates of financial participation set in the table of indicative breakdown of the estimated eligible costs which follows the signatures to this contract."6.3The second sentence of the second subparagraph of Article 3(1) point (b) of Annex II to thiscontract shall be replaced by the following: "When each periodic payment is made, an amount equivalent to the percentage of the total Community contribution paid as the initial advance shall be retained."6.4Notwithstanding the second sentence of the first subparagraph of Article 5(1) of Annex II tothis contract, no coordination tasks may be subcontracted under this contract.6.5The following is added to Article 6 of Annex II to this contract: "The contractors shall bearsole responsibility for assessing that the use of acronyms within the framework of this contract, including but not limited to the acronyms of the project, does not infringe existing trademarks, registered patents and other similar rights."6.6Where a contractor having successfully fulfilled its obligations withdraws from the projectbefore the termination date of the contract, in accordance with either the provision of Annex I or with Article 7(2) point (b) of Annex II to this contract, the final payment to this contractor shall include the guarantee retention as specified under Article 3 (3) of this contract.6.7The access rights granted under Articles 13 and 14 of Annex II to this contract in respect ofknowledge in the form of software shall include the right for the beneficiary to grant the sublicenses required due to amalgamation and incorporation of the software with the beneficiary's own knowledge for its products or processes.6.8Insert at the end of Article 23(7) of Annex II to this contract: "The costs of protection of theknowledge and of measures to demonstrate the potential for exploitation of the knowledge shall also exclude the costs of creating and marketing a product and process and the costs of creating and providing a service."6.9The following is added to Article 4 of Annex II to the contract :"The first periodic cost statement shall be accompanied by an audit certificate in all cases where the eligible costs declared by the contractor exceed EUR 250,000 in the case of a cost statement covering a first period of 12 months, or EUR 125,000 in the case of a cost statement covering a first period of 6 months.The cost statement for the final period shall be accompanied by an audit certificate covering all the periodic cost statements and the cost statement for the final period, in all cases where the total eligible costs declared by the contractor exceed EUR 250,000.These audit certificates must be issued and certified by independent and qualified auditors approved by the competent authorities of the country of legal residence of the contractor to carry out statutory financial audits in accordance with the relevant national legislation and, where applicable, in compliance with the Eighth Council Directive 84/253/EEC of 10 April 1984.In case a contractor is not in a position to provide an audit certificate by such an independent and qualified auditor as a result of restrictions in its statutes or under national legislation, no audit certificate will be required.Where the audit certificate covering the first periodic cost statement is qualified, the Commission reserves the right to withhold part, or exceptionally, all of the payment of the Community's financial contribution until the period covered by the next cost statement in case of failure of the contractor to submit, within the time limits laid down in paragraph 3 of this Article, an unqualified audit certificate or an audit certificate incorporating qualifications acceptable to the Commission.Where the audit certificate covering all periodic cost statements and the cost statement for the final period is qualified, the Commission may decide not to make the payment corresponding to the costs incurred during the final period or may require reimbursement of part, or exceptionally, all of the Community's financial contribution in case of failure of the contractor to submit, within the time limits laid down in paragraph 3 of this Article, an unqualified audit certificate or an audit certificate incorporating qualifications acceptable to the Commission,subject to two month's written notice of non-receipt of that document.These audit certificates shall be drawn up in accordance with the provisions laid down in Annex IV - "Special conditions for audit certificates" to this contract."6.10The first subparagraph of Article 3(4) of Annex II to the contract shall be replaced by thefollowing:"Where the total financial contribution due from the Community, taking into account any adjustments, including as a result of a financial audit as referred to in Article 26 of this Annex or as a result of the absence of an audit certificate or as a result of an audit certificate incorporating qualifications non acceptable to the Commission as referred to in Articles 4 and22 of this Annex, is less than the total amount of the payments referred to in paragraph 1, firstsubparagraph, of this Article, the contractors concerned shall reimburse the difference, in euro, within the time limit set by the Commission in its request sent by registered letter with acknowledgement of receipt."6.11The following is added to Article 22 of Annex II to the contract :"In all cases where a certification in an audit certificate is required under Article 4 of this Annex, costs for which there is no such certification shall not be considered as eligible costs."6.12The following text is added to the end of the second sentence of the first subparagraph ofArticle 23(8) of Annex II to the contract : "......., or in providing the audit certificates required under the provisions of Article 4 of this Annex. The Community's financial contribution in respect of the costs incurred for the audit certificate shall not exceed EUR 4,000 per audit certificate."6.13The final sentence of the third subparagraph of Article 3(3) of this contract shall be replacedby the following : "The guarantee retention shall be 20% of the maximum amount of that contribution."6.14The following is added to the first paragraph of Article 8 of the contract :"Annex IV - Special conditions for audit certificates"6.15The third paragraph of Article 8 of the contract shall be replaced by the following:"The special conditions set out in Article 6 of and Annex III - "Special conditions for the IST Programme" and Annex IV - "Special conditions for audit certificates" to this contract shall take precedence over any other provisions."6.16For the purposes of this contract, KTH and SICS, acting in close cooperation, shall ensurescientific coordination of the project and administrative and financial coordination of the project respectively.The scientific coordinator shall perform the following obligations:- scientific monitoring of the project;- drafting of reports (including the summary of the technological implementation plan) and verification of the data submitted for this purpose by the contractors and of the corresponding cost statements;- formalities prior to termination of participation of a contractor.The administrative and financial coordinator shall perform all the other obligations incumbent upon the coordinator, especially those set out in Article 2(1) of Annex II to this contract.All documents sent by the Commission in connection with the project shall be addressed to the administrative and financial coordinator.Article 4(2) subparagraph 3 of this contract and Article 2(1) subparagraph 2 and the third sentence of Article 23(1) point (a) of Annex II to the contract shall apply to the scientific coordinator and to the administrative and financial coordinator.Only the administrative and financial coordinator may charge to the contract the administrative and financial coordination costs set out in Article 23(9) of Annex II to this contract.Article 7 - AmendmentsThis contract, including the Annexes thereto, may be modified only in writing, by way of an amendment between the authorised representatives of the contracting parties. No verbal agreement may be binding on the contracting parties for this purpose.Any request for amendment must be received by the Commission at least two months before the expiry of the duration of the project.Article 8 - Final provisions1.The following annexes are an integral part of this contract:Annex I - Description of workAnnex II - General conditionsAnnex III - Special conditions for the IST ProgrammeAnnex IV – Special conditions for audit certificates2.In the event of any conflict between Annex I and any other provision of this contract, the lattershall take precedence.3.The special conditions set out in Article 6 of and Annex III to this contract shall takeprecedence over any other provisions.Article 9 - Signature and language of the contractTwo copies of the contract in English shall be signed by the contracting parties and only that language version shall be authentic.Done at Brussels,On behalf of:SICS, SWEDISH INSTITUTE OF COMPUTER SCIENCE AB (SICS) Name:DR. GUNNAR BJURELTitle:MANAGING DIRECTORSignature:Name:MR JANUSZ LAUNBERGTitle:BUSINESS MANAGERSignature:(stamp of the organisation)On behalf of the Commission:Name: (written out in full)Title:Signature:Date:On behalf of:ECOLE POLYTECHNIQUE FEDERALE DE LAUSANNE (EPFL) Name:PROFESSOR MARTIN ODERSKYTitle:DIRECTORSignature:Name:ASSISTANT PROFESSOR RACHID GUERRAOUITitle:DIRECTORSignature:(stamp of the organisation)On behalf of the Commission:Name: (written out in full)Title:Signature:Date:On behalf of:INSTITUT NATIONAL DE RECHERCHE EN INFORMATIQUE ET EN AUTOMATIQUE (INRIA)Name:PROFESSOR JEAN-PIERRE BANATRETitle:DIRECTORSignature:(stamp of the organisation)On behalf of the Commission:Name: (written out in full)Title:Signature:Date:On behalf of:KUNGLIGA TEKNISKA HOGSKOLAN (KTH) Name:PROFESSOR ANDERS FLODSTRÖMTitle:PRESIDENTSignature:(stamp of the organisation) On behalf of the Commission:Name: (written out in full)Title:Signature:Date:On behalf of:THE CHANCELLOR, MASTERS AND SCHOLARS OF THE UNIVERSITY OF CAMBRIDGE (UCAM)Name:MS KATHLEEN GRAYTitle:CONTRACTS AND APPLICATIONS MANAGER Signature:Name:MS JENNY WALSHAMTitle:CONTRACTS AND APPLICATIONS MANAGER Signature:(stamp of the organisation)On behalf of the Commission:Name: (written out in full)Title:Signature:Date:On behalf of:UNIVERSITE CATHOLIQUE DE LOUVAIN (UCL) Name:PROF. MARCEL CROCHETTitle:RECTORSignature:Name:PROF. MICHEL MOLITORTitle:VICE-RECTORSignature:(stamp of the organisation) On behalf of the Commission:Name: (written out in full)Title:Signature:Date:1[CETO 2.0.15][Doc1.1] 06/11/01 12:03P a r t i c i p a n t R o l e s (1)P a r t i c i p a n t N oA s s i s t a n t t o P a r t i c i p a n t N oP a r t i c i p a n t S h o r t N a m e (2)P e r s o n n e lT r a v e l a n d s u b s i s t e n c eD u r a b l e e q u i p m e n tO t h e r s p e c i f i c c o s t sO v e r h e a d sS u b c o n t r a c t i n gC o m p u t i n gS u b t o t a l p a r t 1CO 1SICS343.52729.000 6.0008.000353.37200739.899Coordination70.7997.80008.00058.7160145.315Total Coordinator costs 414.32636.800 6.00016.000412.08800885.214CR 2EPFL 281.33929.0000018.62100328.960CR 3INRIA 156.37629.00008.000276.17600469.552CR 4KTH 298.21929.000 6.000 4.00067.44400404.663CR 5UCAM 211.86529.000 6.000 4.00050.17300301.038CR 6UCL274.16929.000 6.000 4.00064.63405.000382.803Total1.636.294181.80024.00036.000889.1365.0002.772.2301. Participant Role Codes3. All amounts are in euroCO = CoordinatorCR = Principal Contractor 4. Financial Participation Codes :AC = Assistant ContractorCS = Scientific CoordinatorFC = Full Cost - actual overheads FF = Full Costs - flat-rate overheads AC = Additional Costs2. Coordination = Administrative and financial coordination costs only2[CETO 2.0.15][Doc1.1] 06/11/01 12:03P a r t i c i p a n t R o l e s (1)P a r t i c i p a n t N oA s s i s t a n t t o P a r t i c i p a n t N oP a r t i c i p a n t S h o r t N a m e (2)S u b t o t a l o f p a r t 1C o n s u m a b l e sP r o t e c t i o n o f k n o w l e d g eT o t a l o f E s t i m a t e d E l i g i b l e C o s t s (3)T y p e o f F i n a n c i a l P a r t i c i p a t i o n (4)M a x i m u m C o m m u n i t y C o n t r i b u t i o nA d v a n c e p a y m e n tR a t e o f F i n a n c i a l P a r t i c i p a t i o nCO 1SICS739.89900739.899FC369.94950,00%Coordination145.3152280145.54372.77150,00%Total Coordinator costs 885.2142280885.442442.720177.08950,00%CR 2EPFL 328.96000328.960AC 00CR 3INRIA 469.55200469.552FC 234.77693.91050,00%CR 4KTH 404.66300404.663AC 404.663161.865100,00%CR 5UCAM 301.03800301.038AC 301.038120.415100,00%CR 6UCL382.803 5.0000387.803AC387.803155.121100,00%Total2.772.230 5.2282.777.4581.771.000708.40063,76%1. Participant Role Codes3. All amounts are in euroCO = CoordinatorCR = Principal Contractor 4. Financial Participation Codes :AC = Assistant ContractorCS = Scientific CoordinatorFC = Full Cost - actual overheads FF = Full Costs - flat-rate overheads AC = Additional Costs2. Coordination = Administrative and financial coordination costs only。
Cultural Corner用

How did it start?
The idea of the European Union began in the 1950s.
How many countries belong to it now?
In 2004 the European Union increased to 25 countries. The expanded European Union has a population of more than half a billion people.
• Ⅱ.选词填空 • range range;on the other hand;in terms of;ever since;little by little In terms of • 1.________________________the size and population,how big is the European Union compared with China? • 2.The prices of the shirts ________ range from $50 to $100.
• ①It is a small country both in terms of size and population. • 就面积和人口而言,它是一个小国。 • ②He thought of everything in terms of money. • 他每件事都从钱的角度考虑。 • ③In terms of money we’re quite rich, but not in terms of happiness. • 从钱的角度说,我们相当富有,但就幸 福而言则不然。
• 3.Because of his illness,he got little by little thin______________________. • 4.He moved to New York five years ago and has lived there________________. ever since • 5.I’d like to pay a second visit to the on the other hand beautiful West Lake,but ______________ I can’t afford enough time.
The_European_Political_Community

The European Political Community: Establishment, Motivation and ProspectCui HongweiT he European Political Com-munity (EPC) is a forum-likeinstitution established by the European countries out of their geo-political needs and to overcome the dilemma of EU enlargement after the outbreak of Ukraine crisis. It has held three summit meetings so far in Prague on 6 October 2022, Burboac on 1 June 2023 and Granada on 5 October 2023 respectively. A s defined by the European Council, it is a coor-dination platform of great symbolic importance that shall not replace any existing organization, structure or process, nor intends to create new ones at this stage. It aims to make up for the lack of appropriate institu-tional framework for political coordi-nation in Europe under the Ukraine crisis. At the same time, it shuns away from the rigid institutional approach to deal with security challenges, and offers a new way to take EU out of its enlargement dilemma. Based on effectiveness and sustainability, it cannot avoid the key issues of power resources and leadership during its development, and more importantly, it will forge close relations with the future European security architecture in order to meet the common security challenges of Europe.ESTABLISHMENTAfter the outbreak of the Ukraine crisis on 24 February 2022, the EU ac-celerated its pace of enlargement, not only restarting the accession negotia-tions of the Western Balkan countries,but also granting Ukraine, Moldovaand Georgia the status of candidatecountries for accession. In view ofthe security challenges posed by theUkraine crisis, most member statesagree on the need for EU enlarge-ment, yet there is wide disagreementon the timetable for enlargement asit involves important fiscal transfersand institutional reforms of the EU.In his address to the closing cer-emony of the Conference on theFuture of Europe on 9 May 2022, Ma-cron pointed out that the EU couldnot in the short term be the only wayto structure the European continent,proposed to establish a “new politicalcommunity” that would allow coun-tries that subscribe to the “core val-ues” to find “a new space for politicalcooperation” within its framework,so as to maintain the stability of thecontinent. Macron’s proposal receivedstrong support from European Coun-cil President Charles Michel. On 22June 2022, the proposal for EPC wasdiscussed during the EU Summit.The European Council stated that, theEPC was to be established to provide aplatform for across continent politicalcoordination, and to foster politicaldialogue and cooperation in order toaddress issues of common interestand promote the security, stabilityand prosperity of the European conti-nent.In October 2022, the first summitwas held in Prague, bringing togetherheads of state from 44 countries in-cluding the EU and its 27 memberstates, the UK, Iceland, Norway, Swit-zerland, Liechtenstein from the Eu-ropean Free Trade A rea, the WesternBalkans of Serbia, Bosnia and Herze-govina, North Macedonia, Montene-gro, Albania and Kosovo, and EasternPartnership countries of Ukraine,Georgia, Moldova, Azerbaijan, A rme-nia and Türkiye. Leaders agreed tohold summit meetings twice a year,with the host rotating between EUand non-EU member states. At theMoldova Summit in June 2023, Mo-naco, San Marino and Andorra wereadded to its membership.The EPC sets up an attractivemode for equal cooperation betweensovereign states as it adopts flexibleand informal intergovernmentalexchanges, coordination and coopera-tion by holding round tables, bilateraland small multilateral meetings,without setting up corresponding per-manent institutions and funds. TheUkraine crisis and energy crisis are atthe heart of the leaders’ discussions,with other areas covered includingdigital facility (networks, underseacables, data centers), infrastructure,gas pipelines, defense, migration, andregional disputes.France is a staunch supporter ofthe EPC. In France’s view, the Com-munity could become an integralpart of the European political archi-tecture, not only as a useful forum for36September/October 2023 CONTEMPORARY WORLDdialogue, but also as a source of coop-eration projects among its members. Close to the French position, Italy is keen to exploit the potential of the Community to promote concrete co-operation projects. Germany, Poland and the European Commission have expressed measured support for co-operation projects. Most EU member states do not want EU institutions to spend too much EU fund due to their participation in the Community, and EU candidate countries fear that the Community could become an alter-native to EU enlargement.Non-EU countries of Moldova, Türkiye and the UK have taken a pos-itive stance towards the EPC. Moldova offered to host the second summit. Türkiye is looking to the Community as a new way to develop relations with European countries while bypassing EU institutions. For the UK, as the Eu-ro-Atlantic region remains a priority in its international strategy and prac-tical cooperation with the EU stays high on its foreign policy agenda, it will host the fourth Summit in the first half of 2024.While still in its infancy, the EPC member states have already reached some bilateral and small multilateral agreements through the platform. To name a few, the UK and the NorthSeas Energy Cooperation whoseorganization membership includeseight EU member states and Norwayhave signed a MOU to deal with en-ergy supply issues. The French andBritish leaders pledged to boost bilat-eral cooperation in energy, illegal im-migration and defense. In the area ofmediating regional disputes, Michel,Macron and Scholz met with the lead-ers of Azerbaijan and A rmenia in aneffort to forge consensus on Nagorno-Karabakh peace agreement. Theleaders of Türkiye and A rmenia heldmeetings to normalize bilateral rela-tions. The issue of Kosovo was alsohigh on its agenda.MOTIVATIONSFirst, the EPC offers a new ap-proach to solve the tough issues of EUenlargement under the new situation.In the context of the Ukraine crisis,the EU has accelerated its enlarge-ment process, not only restarting theaccession negotiations of the WesternBalkan countries, but also grantingcandidate status to Ukraine, Moldovaand Georgia, aiming to promote“geostrategic investment in a stable,strong and united Europe”. Enlarge-ment not only involves budget, struc-tural funds, common agriculturalpolicy and other issues of interest,but also affects decision-making ef-ficiency, making it a new impetus forthe reform of EU institutions.Second, it aims to fill the EU’sgeopolitical and geostrategic voidand wipe off the continent’s securitygray zone, which refers to the EU andRussia’s common neighborhood ofEastern Europe, the Western Balkans,the South Caucasus, the Black Seaand Eastern Mediterranean regions.A s Russia sees these areas as geostra-tegic buffer zones and border zonesof the “EU empire”, the EU needs astrategy to strengthen its influencein these areas, which explains whythe EPC was materialized in a shortperiod of time. In Macron’s view, Brit-ain must become a member of theCommunity. As the second largesteconomy in Europe and a powerfulcountry in military strength, UK’sBrexit has dealt a serious blow to theEU’s geopolitical influence. Türkiye isof strategic importance to Europeansecurity in the Middle East, EasternMediterranean and Black Sea regions.A s the EU is decoupled from its larg-est energy supplier of Russia, it facesa huge challenge of energy supplysubstitution. Countriessuch as Norway, Azerbaijanand Georgia are importantsources of oil and gas forthe EU, and Türkiye playsan important role in termsof infrastructure such as oiland gas corridors and gasterminals.Last but not least, Eu-rope is in urgent pursuitof strategic autonomy inthe face of its increasingdependence on Americandecisions and capabilitieswhen dealing with its ownaffairs. The Ukraine crisishas dealt a heavy blow to(Photo/IC Photo)37the goal of strategic independence of Europe, and Europe strategically re-lies more on the US. Macron warned that “Europe should not be a vassal of the United States”. The European stra-tegic community generally believes that only by offering solutions to end conflicts in its neighborhood, and by making effective strategic responses to the challenges in its neighborhood can the EU have global weight and credibility. The EU’s lack of strategic autonomy is highlighted by its lack of defense autonomy. From the per-spective of A Strategic Compass for Security and Defense released by the EU in 2022, its strategic autonomy is obviously diluted, and most of the increased military expenditure of Eu-ropean countries may still flow to the US rather than to their own military industry.Although the Ukraine crisis is far from over and the US has increased its military presence in eastern Europe, Europe has a relatively di-minished role in US global strategy. America itself is divided over the Ukraine crisis, the role of its Euro-pean allies, climate, energy and other issues. Fearful of increased burden of European security guarantees, theUS expects Europe to increase its ownmilitary and security commitment toUkraine.PROSPECTWill the EPC serve only as an ex-pedient solution to the Ukraine crisis?Or, will it develop into a useful po-litical and security organization thatunite European countries? It dependslargely on the political will of theEuropean leaders. So far, its structure,function, orientation and relationswith the future European security ar-chitecture are yet to be clear and needto be further observed.First, the structure and leadershipcapability. In view of the different pri-orities and expectations of memberstates, the EPC maintains a vaguestrategic direction and runs as an in-formal body in order to guarantee itspracticality. But the informal and non-centralized model makes it hard tobe effective. Leadership is a questionmust be answered for the organiza-tion with 47 member states to providesolutions to problems. In this regard,the European academic communityhas two basic ideas: one is to form astructure with France, Germany, theEU and the UK as the core, whichis the only way to formulate a clearlist of strategies and in line withthe resource capacities of Europeancountries. Another is to establish astructure dominated by the Weimartriangle of France, Germany andPoland, the consideration of which isbased on its institutional maturity, aswell as the need to bridge the rift be-tween East and West Europe over theUkraine and migration crises.Second, its relations with the fu-ture European security architecture.The Ukraine crisis has paralyzed theOSCE. The NATO cannot cover thewhole of Europe in short term. Eu-rope needs a new security frameworkto meet common challenges. It is inconformity with the birth of the EPC.It is not clear, however, whether it willform the foundation of a new securityarchitecture for the continent. A Ger-man foreign policy think tank hasproposed to set up Joint European De-fense Initiative as the new Europeanpillar of NATO. According to theinitiative, NATO’s major European al-lies such as Britain, France, GermanyEuropean Commission President von der Leyen (L), European Council President Charles Michel (C) and Albanian Prime Minister Edi Rama (R) attend a press conference to reiterate their commitment to the accession of the Western Balkan countries to the EU, in the Albanian capital Tirana on December 6, 2022.(Photo/Xinhua)38September/October 2023 CONTEMPORARY WORLDand Poland will use their advantage to protect Ukraine and Eastern Euro-pean countries, and take more respon-sibility for future European security.Whether it is the EPC or the above Initiative that will become the future European security architecture, the core is the EU-Russia relations. Yet, France and Germany are at odds with each other on this issue. At the Mu-nich Security Conference in February 2023, Macron said that “to crush Rus-sia has never been France’s position and it will never be”. For Germany, it agreed with France that Russia was an essential player in the future Europe-an security order before the Ukraine crisis, but it changed its position dras-tically after the crisis broke out. On 14 June 2023, the German government issued National Security Strategy stating that Russia is the most grave threat to peace and security in the Euro-Atlantic region in the foresee-able future and German foreign and security policy will adjust to the threat accordingly.Third, the France-Germany rela-tions within the EPC. The relations between France and Germany willbe the key to the EPC no matterwhat shape its future structure takes.France is the largest military coun-try in the EU, with a complete andadvanced system and productioncapacity of military industry, as wellas the ability to manufacture nuclear-powered aircraft carriers, but France’seconomic strength is not enough tosupport European security needs, andits ambitions must be supported byGermany. In the new security environ-ment, France-Germany competitionfor European leadership is on the rise.Germany is likely to break through itshurdles as a “reluctant great power”and define itself as a stronger geo-political and security actor, playing aleading role in EU’s future policy onRussia and Eastern Europe. As a re-sult, France’s status as a political andsecurity power in the EU is bound tobe challenged by Germany’s pursuitof the role of a geopolitical leader.CONCLUSIONThe EPC provides a platform fordialogue and coordination betweenEU member states and non-EUneighbors. Its future developmentfaces two interrelated questions: First,whether Europe’s pursuit of its geo-political role will change the criteriafor EU enlargement. Second, whetherEurope’s new security environmenthas changed the way Europeans thinkabout and pursuit of peace. MarkLeonard, Director of the EuropeanCouncil on Foreign Relations, ar-gues that over the past half century,European countries have developeda concept of freedom based on uni-versalism, rejection of military force,economic interdependence, sharedsovereignty, and the establishment ofEurope as a single entity based on aset of common institutions. And theEU’s response to the Ukraine crisiscould turn the project of peacefulEuropean integration into a securityproject.——————————————Cui Hongwei is Researcher at theInstitute of International Studies,Shanghai Academy of Social SciencesPeople take partin an anti-NATOand anti-Aurora 23military exerciseprotest on April 22,2023 in Stockholm,Sweden.(Photo/Xinhua)39。
英语国家社会与文化入门 课后题答案之欧阳德创编

Book1 Unit 1时间:2021.03.07 创作:欧阳德1.What was the British Empire? What do you know about it? In what way is the “Empire” still felt in Britain and in the international field?The British Empire comprised the dominions, colonies, protectorates, mandates, and other territories ruled or administered by the United Kingdom, that had originated with the overseas colonies and trading posts established by England in the late 16th and early 17th centuries. In the international field, Britain has great voice in politics, economy and culture and so on.2.Why impossible to sum up British people with a few simple phrases: The UK is made up of different elements. It includes 4 parts within the one nation-state. It is now a multiracial society with different religion believes. It is dividedeconomically and it is a society with a class-structure. And within each of the four countries there are different regions. Since this country was so complicated both in history or humanity, it is impossible to sum up their people. 3.A history of invasions: (1) Before the 1st century AD Britain was made up of tribal kindoms of Celtic people. They brought the central Europen culture to Britain. Then in 43AD, Roman Empire invaded Britain and controlled it for slave society but also disseminated their Catholicism.(2)However, in the 5th century, the Roman Empire rapidly waned in power and Britain was conquered by the Angles and the Saxons. In order to defend the Saxons, a great leader—King Arthur appeared. He created the "round table" to satisfy all the knights' requirement of having equal precedence. Thus it gradually formed the monarchy in Britain as a more democratic system. Whether Arthur's a real person in thehistory or not, Anglo-Saxons did succeed in invading Britain and they were the forefathers of the English. (3)In the 8th century, the Vikings from Denmark controlled the nothern and eastern England. A Anglo-Saxon herio, king Alfred the Great fought against the vikings with the truly English. And that's why there's a certain cultural difference between northerners and southerners in England (4)Later, the Nomans from northern France, under the leading of William of Normandy, killed the king and William became the Frist of England. They imported a rulling class that French-speaking Norman aristocracy rulled Saxon and English-speaking population. In this condition, there weren't a lot of rebellions among the English people. That directly formed an English unique character: a richly unconventional interior life hidden by an external conformity. Even today, we can still find this personality from the British people through their lifestyles.How did they influence culture:[接着上边一起看](2) a lot of stories of King Arthur, which brought a lot of singers, poets, novelists and filmmakers. Places associated with his legend. Round table was ween as an indicator of the way in which the English have wished to see their monarch as something other than a remote dictator.(3)anglo-saxon invaders were the forefathers of the English. By Vikings' settlements the Enlish heroes were truly English. There remains to this day a certain cultural divide between northerners and southerners in england.(4)Norman aristocracy ruling a largely Saxon and English-speaking population. the legend of Robin Hood.4.General characteristic of Scotland: Scotland is the second largest of the four nations, both in population and in geographical area. It is also the most confident of its own identity because alone amongst the non-English components of the UK it has previously spent a substantial periodof history as a unified state independent of the UK. (1) rugged. (2) not conquered by the Romans (3) maintain its separate political identity for more than a hundred years.(4) eager for independence.How Scotland became part of the union of Great Britain: in 1707 by agreement of the English and Scottish parliaments, Scotland joined the Union. In 1745 there was a brutal military response from the British army. The rebel army was destroyed at the battle of Culloden in northern Scotland.5.Describe Wales and the unification with Britain: (1) wales was an important element in Britain's industrial revolution, as it had rich coal deposits. It is successful in attracting investment from abroad. Wales has been dominated by England for longer than the other nations of the union. Despite this nearness and long-standing political integration Wales retains a powerful sense of its difference from England. (2)Wales has beendominated by England for longer than the other nations of the union. Despite this nearness and long-standing political integration Wales retains a powerful sense of its difference from England. In 1536, wales was brought legally, administratively, and politically into the UK by an act of the British parliament. This close long-standing relationship means that modern wales lacks some of the outward signs of difference which Scotland possesses --- its legal system and its education system are exactly the same as in England.6.Differences between England, Scotland and Wales in terms of cultural tradition: [书上说的比较散,建议参考festival那章的答案,这里只有一些零散的不系统的比较] (1) English character: a richly unconventional interior life hidden by an external conformity. But young people are not all stereotypes. But it is certainly true that the lifeless fronts of many english houses conceal beautiful back gardens. (2)The dream of an independentScotland has not vanished. They are always eager for freedom. Scotland has a great tradition of innovation in the arts, philosophy and science. "Superficially fully integrated into the UK, but concealed beneath this is a still-strong Scottish identity." Some people speak Gaelic.(3)Wales is different, and one of the key markers of that diffenece is the Welsh language -- the old British Celtic tongue which is still in daily use. Modern wales lacks some of the outward signs of difference which Scotland possesses. (its legal system and education system are exactly the same as in England)Unit 21.Why is Northern Ireland so significant in the UK: Though Northern Ireland is small it is significant because of the political troubles there.Its political problem: The problem is in Northern Ireland in 1921 in southern Ireland independence from Britain, Ireland North and South following theseparation of issues left over by history, mixed it with historical, political, ethnic and religious conflicts, extremely complex. Ireland’s independence, to remain under British rule within the framework of the 6 in the northern island of Ireland residents of the pro-British Protestant majority (about 51%), the Catholic nationalist minority (about 38%), as a result of the two major forces in Northern Ireland On the contrary position of ownership and lead to confrontation, conflict. [因为发现实在太难sum up了,所以就搜了一下,以下是wikipedia版本]Northern Ireland was for many years the site of a violent and bitter ethno-political conflict —the Troubles —which was caused by divisions between nationalists, who are predominantly Roman Catholic, and unionists, who are predominantly Protestant. Unionists want Northern Ireland to remain as a part of the United Kingdom,[6] while nationalists wish for it to be politically reunited with the rest of Ireland, independent of British rule. [网络其它版本]Until 1921 the full name of the UK was "The United Kingdom of Great Britain and Ireland", not only "Northern Ireland", because the whole island of Ireland was politically integrated with Great Britain, and had been since 1801, while Britain's domination of the Irish dated back centuries even before that date. But Irish desires for an independent Irish state were never lost, and one of the key issues in late nineteenth century British politics was a campaign in parliament for what was called "home-rule"—Irish political control of Irish affairs. The Home Rule Bill was finally passed in 1914, but the process was overtaken by the First World War and was suspended for the duration of the war.2.Factors in Irish and English history that affect the situation in Northern Ireland today: Along with the political campaign for home-rule there were groups who followed a more direct method of pursuing Irish independence, engaging in guerillaor terrorist activities against British institutions and the British military forces. During the First World War and immediately after, this activity increased, sometimes brutally suppressed by British forces.3.Sum up solutions to NI's political problems of different parties and groups in the UK: Margaret Thatcher's government did not give in to this demand for political status and 11 prisoners starved to death. This event revitalised the political campaign of Sinn Fein, the legal political party which supports the IRA's right to fight. Its leaders spoke of a twin campaign for union with Ireland, both political and military, which they called the policy of "The Bullet and the Ballot Box".4.What do you think should be the right solution to the political problem in Northern Ireland: I think they can ask the UN for help. / Keep the presentstatus. Turn to other countries for help. [自由发挥啦]Unit 31.Characteristics of the British constitutional monarchy: The monarch of the country has limited rights because of Bill of Right. For example, while the official head of state is the queen, her powers are largely traditional and symbolic. The government at national and local levels is elected by the people and governs according to British constitutional principles.How the English monarchy evolved to present constitutional monarchy: Originally the power of the monarch was largely derived from the ancient doctrine of the "divine right of kings". For a thousand years Britain has had a hereditary king or queen as the head of the state. While the King in theory had God on his side, in practice even in medieval times it was thought that he should not exercise absolute power. King Johnwas unwilling to receive advice from prominent men, which led battles between the king and other powerful groups. Finally the king granted them a charter, named Magna Carta, of liverty and political rights. The civil war2.The civil war was rooted in a dispute over the power of the king vis-a-vis Parliament. James I and his successor Charles I both insisted on their divine right as kings. They felt Parliament had no real political right to exist, but only existed because the king allowed it to do so. It was the effort to reassert the rights of parliament that led to the civil war.English Revolution: "English Revolution" has been used to describe two different events in English history. The first was the Glorious Revolution of 1688, whereby James II was replaced by William III and Mary II as monarch and a constitutional monarchy established, was described by Whig historians as the English Revolution.[1]In the twentieth-century, however, Marxist historians used the term "English Revolution" to describe the period of the English Civil Wars and Commonwealth period (1640-1660), in which Parliament challenged King Charles I's authority, engaged in civil conflict against his forces, and executed him in 1649. This was followed by a ten-year period of bourgeoisrepublican government, the "Commonwealth", before monarchy was restored in the shape of Charles' son, Charles II, in 1660.3.History of English parliament: Traditionally, when medieval kings wanted to raise money he would try to persuade the Great Council, a gathering of leading, wealthy barons which the kings summoned several times a year. Later kings found this group was so small that they could not make ends meet. So they widened the Great Council to include representatives of counties, cities and towns and get them to contribute. Itwas in this way that the Great Council came to include the House of Lords(who were summoned) and the House of Commons(representatives of communities).What role did the parliament play in the Civil War: Since James I and Charles I both thought that Parliament didn't need to exist, the Parliament was enraged. Leading politicians and church authorities asked William of Orange to replace them two. In 1689 Parliament passed the bill of Rights which ensured that the King would never be able to ignore Parliament.4.Characteristics of British constitution: Unlike many nations, Britain has no core constitutional documents.Contents: Statute laws(laws passed by Parliament); the common laws(laws which have been established through common practice in the courts); and conventions(rules and practices which do not exist legally but are neverthelessregarded as vital to the workings of government). 5.Why parliament is supreme: because it alone has the power to change the terms of the Constitution. There are no legal restraints upon Parliament.Parliament's function: First, it passes laws. Second, it provides the means of carrying on the work of government by voting for taxation. Third, it scrutinises government policy, administration and expenditure. Fourth, it debates the major issues of the day.Queen/King's role: To symbolise the tradition and unity of the British state. To represent Britain at home and broad. To set standards of good citizenship and family life. She is legally head of the executive, an integral part of the legislature, head of the judiciary, commander in chief of the armed forces and "supreme governor" of the Church of England.PM's role: The Prime Minister is the leader of thepolitical party which wins the most seats in a general election. He/She chose usually around 20 MPs to become government ministers in the Cabinet. Together they carry our the functions of policy-making, the coordination of government departments and the supreme control of government.6.The House of Lords: It was below the Queen, consisting of the Lords Spiritual(who are the Archbishops and most prominent bishops of the Church of England) and the Lords Temporal(which refers to those lords who either have inherited the seat from their forefathers of they have been appointed). The lords mainly represent themselves instead of the interests of the public. It is the upper house of the Parliament of the United Kingdom, the United Kingdom's national legislature. It remains the relationship with government, debates legislation and has some power to amend or reject bills (has somelegislative functions).Unit 41.Anyone who is eligible to vote can stand as an MP. It is necessary only to make a deposit of 500 pounds.Why small parties and independent candidates powerless: Voters will see it as a wasted vote because even if they were to win the seat they would be powerless in parliament against the big parties' representatives. Voting them will prevent the voters from contributing to the competition between the big parties as to which of them will form a government.2.Three big parties in the UK: the Labour party, the Conservative party, the Liberal Democrats. Similarities: Since Conservative began to have a "fartherly" sense of obligation to the less fortunate in society, they didn't dismantle principles the Labour set up. That indicates that thus thedifference between the Labour and Conservative is one of degree, not an absolute. Dissimilarities: (1) Labour is a socialist party. They believe a society should be relatively equal in economic terms and that part of the role of government is to act as a "redistributive" agent. They think government should provide a range of public services, therefore high taxes. (2) Conservative is the party that spent most time in power. They are seen as the party of the individual, protecting individual's right to acquire wealth and to spend it how they choose, therefore low taxes. (3) Liberal Democrats is a party of the "middle", occupying the ideological ground between the two main parties. They are comparatively flexible and pragmatic in their balance of the individual and the social.3.Recent political trends [注意下一小问]: (1) Conservatives won the election under their leader Margaret Thatcher in the 1970s. Duringthat time the economy did badly, with high inflation and low growth. (2) she dismissed being "fartherly", encourages entrepreneurship. One of the major policies was the privatisazion of nationalised industry. (3)part of the mechanism of change was a less redistributive taxation system. Tax rate were cut to allow people to keep more of what they earned.Author's opinion: The 1980s have seen British politics move to the "right", away from the "pulic" and toward the "private"; away from the "social", and toward the "individual", and all parties have had to adjust to those changes.4.How people are divided into different classes: (1) employment: manual(or blue-collar) workers usually call themselves working-class, and office(or white-collar) workers would usually call themselves middle-class. (2) cultural differences: like what newspaper they read. Working-class often read THE SUN, a newspaper with little hardnews and more about soap operas, royal family and sports. Middle-class often read THE GUARDIAN, a larger newspaper with longer stories, covering national and international events. (3) education: private school or public school. (4) the UK has also retained a hereditary aristocracy. (5) the way they speak.Compare with the US and China: not similar at all. The UK has also retained a hereditary aristocracy. Among the students at the private schools attended by the upper-middle-class above would be a thin scattering of aristocratic children, who will inherit titles like baronets. This is due to Britain's different history and convention.Unit 51.Absolute decline means recession, developing in a minus speed.Relative decline means that although the UK improved, other countries developed more rapidly than the UK, which made it slid from beingthe second largest economy to being the sixth. Reasons: (1) The UK had gone into debt after WWII. (2) Britain spent a higher proportion of its national wealth on the military than most of its competitors. (Joining NATO and UN Security Council) (3)The era of empire was over. Former colonial countries announced independence, leaving Britain as a medium-size Euporean country. (4)Britain's industry survived comparatively unaffected, but its competitors did not. So the competitors invested in modern equipment and new products while British industry still continue with older ones. (5) Low rates of investment. The UK lacks a close relationship between industry and banks due to its history. A low rate of domestic industrial investment coupled with a very high rate of overseas investment.2.What did the conservative party under Mrs. Thatcher promise to do to the UK nationaleconomy in 1979: A radical programme of reform.What was her radical reform programme: Bureaucracy was reduced, (foreign exchange controls were lifted, rules governing banks loosened, for example). Throughout the 1980s an extensive programme of privatisation was carried out.Was is successful: It seemed in some ways to be successful in that inflation came under control, and business made profits. The negative aspect was a rapid increase in unemployment. The national economy as a whole continued to grow at lower rates than its competitors.3.Main areas in national economies: Primary industries such as agriculture, fishing and mining; secondary industries which manufacture complex goods from those primary products; tertiary/service industries such as banking, insurance, tourism and the retailing.Development of each: (1) agricultural sector is small but efficient. Energy production is an important part of the UK economy. (2)in the secondary sector, manufacturing industry remains important, producing 22% of national wealth. (3)tertiary or service industries produce 65% of national wealth.4.Why relatively shrinking of the important secondary industry and a spectacular growth in tertiary or service industries: A lot of the tertiary or service industries is domestic activity, accounting for about 10% of the world's exports of such services. 70% of the UK's workforce are employed in the service sector.Compare tertiary industries in China in the past 20 years or so: Chinese tertiary industries didn't grow as fast as the UK, though the portion was increasing.How is this growth related to the reform and opening up to the outside world: China wasfamous for the name of "world factory", which means Chinese workforces can produce products at low paid. China is a developing country, experiencing the transfer of manufacturing is reasonable. However, as China is developing, wages of workforces are also increasing. Comparing to India, we may lose our "advantage" gradually.Unit 61.Why Geoffrey Chaucer's work written in Middle English can still read and studied today: It is notable for its diversity, both in the range of social types amongst the 31pilgrims, and the range in style of the stories they tell.2.Do you think Elizabethan Drama occupies a significant position in British literature: Yes. Elizabethan drama, and Shakespeare in particular, is considered to be among the earliest work to display a "modern" perception of theworld: full of moral doubts and political insecurities, where the right of those who wield power to do so is put in question.The most important figure in Elizabethan Drama: William ShakespeareSome of his well-known plays: (tragedies)Romeo and Juliet, Hamlet, Othello, King Lear, Macbeth; (comedies)The Taming of the Shrew, A Midsummer Night's Dream, Twelfth Night, the Tempest; (history plays)Richard III, Richard II, Henry IV, Henry V jJulius Caesar, Antony and Cleopatra.3.Some of the features of Romantic Literature: writers of romantic literature are more concerned with imagination and feeling than with the power of reason.4.Modernism: it refers to a form of literature mainly written before WWII. It is characterized by a high degree of experimentation. It can be seen as areaction against the 19th century forms of Realism. Modernist writers express the difficulty they see in understanding and communicating how the world works. Often they seem disorganized, hard to understand. It often portrays the action from the viewpoint of a single confused individual, rather than from the viewpoint of an all-knowing impersonal narrator outside the action.Postmodernism: After WWII. Postmodernist can be thought of as abandoning the search of buried meaning below confusing surfaces.Examples to illustrate: (modernist) Virginia Woolf "Mrs.Dalloway""to the Lighthouse""Orlando";wrence "Sons and Lovers" andE.M.Forster"a Passage to India"; (postmodernist)George Orwell "1984", John Fowles "the French Lieutenant's woman"Book I Unit 7, British Education System1.What are the purposes of the British educationsystem? Please comment on these purposes.What are the main purposes of the Chinese education system? Are there any differences or similarities in the education of the two nations?Schools in Britain do not just teach the students 3 Rs, (reading, writing and arithmetic), but to provide children with literacy and the other basic skills they will need to become active members of society.2.How does the British education system reflectsocial class?Firstly, in Britain, the school you attend can refer to your social status.And the school tie is a clear market of social class,3.What are the major changes that have takenplace since World War II? Is British education moving towards more progress or more equality?Pick up some examples from the text to illustrate your points.1)The old education system has disrupted due tothe war. So with the help of the church andnewly powerful trade unions began to reconstruct a new education system.2)The new system emphasizes equality. 1944education act made entry to secondary schools and universities meritocratic. Children would be able admitted to schools not because they were of a certain social class or because their parents possessed a certain amount of money, but because of the abilities they displayed. All children were given right to a free secondary education and the main concern was to make sure more children had access to a good education.3)1989, a national curriculum was introduced bythe government.4.Why does the author say that universities in Britainhave rather elitist?Most students in British universities are from the middle classes, attend good schools, perform well in their A-levels and receive a fully-funded place in a university. And when they graduate,they can become very influential in banking, the media, the arts, education or even the government.5.What is the Open University in Britain? What doyou think of this system?The opening university offers a non-traditional route for people to take university level courses and receive a university degree. People can register without having any formal educational qualifications. They follow university courses through textbooks, TV and radio broadcasts, correspondence, videos, residential schools anda network of study centre.I think the system has been quite successful.Thanks to the system, tens of thousands of Britons, from various statuses attend the Open University each year. And this has improve the equality in Britain’s high education.Unit 8 British Foreign Relations1.What and how did the British Empire end? Howdid the Britain react to this reality? How did theend of British imperialism influence the psychology of the British and the making of Britain’s foreign policy?1)After the World War II the British could no longerafford to maintain its empire; while Britain had won the war, it had paid a terrible price in terms of lives and in terms of economic destruction.And the British realized that countries should be granted the independence and left to run their own affairs. People and territory should not just be treated as a source of economic resources for the ruling centers of commerce in Europe.2)Many people are still alive who can rememberwhen Britain was one of the most powerful and rich nations on earth. It is sometimes hard to think about Britain as it really is today.3)Because Britain lost its empire so recently, britishpolicy makers frequently forget that Britain is not as influential as it used to be in world affairs.Historians argue that the British foreign policy makers retain very conservative and traditionalviews of Britain’s role as a world power and point to many major foreign policy decisions as examples.2.What are the foundations of Britain’s foreignpolicy?It is greatly influenced by its imperial history and also by its geopolitical traits.Britain’s imperial history m ade the policy maker very conservative and traditional.And its geopolitical traits created a sense of psychological isolation in its inhabitants. And as Britain is an island state, it naturally developed asa nation of seafarers who roamed the globelooking for territory and economic opportunities.3.How is Britain’s foreign policy made? Does thegovernment’s foreign policy represent the desires of British citizen?1)The prime minister and cabinet decide on thegeneral direction of Britain’s foreign policy. Th e main government department involved is of course the foreign and commonwealth office。
英语国家概况课后习题答案完整版

一、选择题(答案在下面)I. Choose the one that best completes each of the following statements.1.The two main islands of the British Isles are .A. Great Britain and IrelandB. Great Britain and ScotlandC. Great Britain and WalesD. Great Britain and England2.is the capital city of Scotland.A. BelfastB. EdinburghC. AberdeenD. Cardiff3.According to a 2005 estimate, Britain now has a population of over million.A. 160B. 600C. 60D. 164.Among the four parts of the United Kingdom, is the smallest.A. EnglandB. ScotlandC. WalesD. Northern Ireland5.Almost a quarter of the British population lives in England.A. northeasternB. southeasternC. northwesternD. southwestern6.English belongs to the group of Indo-European family of languages.A. CelticB. Indo-IranianC. GermanicD. Roman7.The introduction of Christianity to Britain added the first element of words to English.A. Danish and FinnishB. Dutch and GermanC. French and ItalianD. Latin and Greek8.The evolution of Middle English was reinforced by the influence.A. NormanB. DutchC. GermanD. Danish9.Samuel Johnson’s dictionary was influential in establishing a standard form of .A. grammarB. handwritingC. spellingD. pronunciation10.At present, nearly of the world’s population communicate in English.A. halfB. a quarterC. one thirdD. one fifth11.The attack on Rome ended the Roman occupation in Britain in 410.A. NormanB. DanishC. CelticD. Germanic12.By the late 7th century, became the dominant religion in England.A. Celtic ChristianityB. Anglo-Saxon ChristianityC. Germanic ChristianityD. Roman Christianity13.Westminster Abbey was built at the time of .A. St. AugustineB. Edward the ConfessorC. William the ConquerorD. Alfred the Great14.The marked the establishment of feudalism in England.A. Viking invasionB. signing of the Magna CartaC. Norman ConquestD. Adoption of common law15.The end of the Wars of the Roses led to the rule of .A. the House of ValoisB. the House of YorkC. the House of TudorD. the House of Lancaster16.The direct cause for the Religious Reformation was King Henry VIII’s effort to .A. divorce his wifeB. break with RomeC. support the ProtestantsD. declare his supreme power over the church17.The English Civil War broke out in 1642 between .A. Protestants and PuritansB. Royalists and ParliamentariansC. nobles and peasantsD. aristocrats and Christians18.was passed after the Glorious Revolution.A. Bill of RightsB. Act of SupremacyC. Provisions of OxfordD. Magna Carta19.The Industrial Revolution was accomplished in Britain by the middle of the century.A. 17thB. 18thC. 19thD. 20th20.Britain faced strong challenges in its global imperial dominance by the beginning of the century.A. 17thB. 18thC. 19thD. 20th21.The British government is characterized by a division of powers between three of the following brancheswith the exception of the .A. judiciaryB. legislatureC. monarchyD. executive22.The importance of the British monarchy can be seen in its effect on .A. passing the billsB. advising the governmentC. political partiesD. public attitude23.As a revising chamber, the House of Lords is expected to the House of Commons.A. rivalB. complementC. criticizeD. inspect24.British Cabinet works on the principle of .A. collective responsibilityB. individual responsibilityC. defending the collectivismD. defending the individuals25.The main duty of the British Privy Council is to .A. make decisionsB. give adviceC. pass billsD. supervise the Cabinet26.In Britain, the parliamentary general election is held every years.A. threeB. fourC. fiveD. six27.has a distinct legal system based on Roman law.A. WalesB. EnglandC. ScotlandD. Northern Ireland28.Generally speaking, the British Parliament operates on a system.A. single-partyB. two-partyC. three-partyD. multi-party29.The policies of the Conservative Party are characterized by pragmatism and .A. government interventionB. nationalization of enterprisesC. social reformD. a belief in individualism30.The Labor Party affected the British society greatly in that it .A. set up the National Health ServiceB. improved public transportationC. abolished the old tax systemD. enhanced the economic development31.The British economy achieved global dominance by the .A. 1860sB. 1870sC. 1880sD.1890s32.In , the British Parliament passed two important acts to establish a welfare state.A. 1945B. 1946C. 1947D. 194833.The in the early 1970s worsened an already stagnant economy in Britain.A. oil crisisB. high inflation ratesC. large importsD. unemployment problem34.Of the following practices, does not belong to Thatcher’s social welfare reform.A. reducing child benefitsB. shortening the unemployment benefits periodC. reducing the unemploymentD. lowering old age pensions35.The Blair government has been successful in all the following aspects except .A. limiting government spendingB. keeping inflation under controlC. reducing unemploymentD. reducing inequality36.Britain has devoted of its land area to agriculture.A. 54%B. 64%C. 74%D.84%37.Britain’s important fishing areas include all the following except .A. the North SeaB. the English ChannelC. The sea area around IrelandD. The sea area between Britain and Ireland38.Coal mining industry in Britain provides of the energy consumed in the country.A. 1/3B. 1/4C. 1/5D. 2/339.The car industry in Britain in mostly .A. foreign-ownedB. state-ownedC. joint-ventureD. privately-owned40.Of the following sectors in Britain, has experienced spectacular growth since the end of WordWar II.A. agricultureB. energy industryC. service industryD. manufacturing industry41.In Britain, the division between grammar schools and vocational schools were ended by the introductionof comprehensive schools in the .A. 1930sB. 1940sC. 1950sD. 1960s42.About of British children receive primary and secondary education through the independentsystem.A. 5%B. 6%C. 7%D. 8%43.Partially funded by central government grants, the British universities receive their remaining funds fromall the following sources except .A. tuition feesB. loansC. donationsD. corporate contributions44.Of the following, is NOT a basis of admission to Britain’s universities.A. result in national entrance testB. A-level resultC. an interviewD. school references45.To be admitted to the Open University, one need .A. some educational qualificationsB. no educational qualificationsC. General Certificate of Education-AdvancedD. General National Vocational Qualifications46.Among Britain’s quality press, the following newspapers are regarded as the “Big Three” with theexception of .A. The TimesB. The GuardianC. The ObserverD. The Daily Telegraph47.Life on Earth is a kind of program produced by the BBC and is popular among 500 millionviewers worldwide.A. featureB. dramaC. documentaryD. soap opera48.is Britain’s top pay television provider.A. BSBB. SkyTVC. BBCD. BSkyB49.Of the following, is NOT a common feature of all the British holidays.A. families getting togetherB. friends exchanging good wishesC. friends enjoying each other’s companyD. families traveling overseas50.The following Christmas traditions are particularly British except .A. Trooping the ColorB. Queen’s Christmas messageC. Boxing DayD. Christmas pantomime51.The most significant achievement of the English Renaissance is .A. poetryB. dramaC. novelD. pamphlet52.is viewed as Romantic poetry’s “Declaration of Independence.”A. “I Wondered Lonely as a Cloud”B. Don JuanC.“Preface to Lyrical Ballads”D. Prometheus Unbound53.Of Dickens’ novels, is considered autobiographical.A. A Tale of Two CitiesB. David CopperfieldC. Oliver TwistD. Great Expectations54.is a representative of English Critical Realism at the turn of the 19th century.A. Robert Louis StevensonB. John MiltonC. Joseph ConradD. Thomas Hardy55.Of the following statements, is NOT correct in terms of Neo-Romanticism.A. It prevailed at the end of the 19th century.B. The writers were dissatisfied with the social reality.C. The writers believed in “Art for Art’s Sake”.D. Treasure Island was a representative work.56.is NOT included in the modernist group.A. Oscar WildB. Virginia WoolfC. William Butler YeatsD. T. S. Eliot57.Of the following books, was NOT written by Thomas Hardy.A. Jude the ObscureB. Tess of the D’UrbervillesC. Adam BedeD. The Return of the Native58.Of the following statements, is NOT correct about Virginia Woolf.A. She was a central figure of the “Bloomsbury Group”.B. She experimented with stream of consciousness.C. She was an influential feminist.D. Her masterpiece was The Rainbow.59.Of the following writers, is NOT a Nobel Prize winner.A. Samuel BeckettB. James JoyceC. William GoldingD. V. S. Naipaul60.Waiting for Godot is written by .A. Samuel BeckettB. George OrwellC. William GoldingD. D. H. Lawrence61.The United States has states on the continent.A. 50B. 49C. 48D. 3562.The state of is the largest in area of all the states.A. AlaskaB. HawaiiC. TexasD. Florida63.The U. S. lies in North America, with Canada to the north, Mexico to the south, the Atlantic toits and the Pacific to its .A. northern, east, westB. central, east, westC. southern, west, eastD. western, east, west64.The largest river in the U. S. is .A. the Missouri RiverB. the Mississippi RiverC. the Ohio RiverD. the Colorado River65.Some of the world famous universities like Harvard, Yale and MIT are located .A. in the SouthB. along the Pacific CoastC. in New EnglandD. in the Midwest66.is located on the U. S. –Canadian border between Lake Erie and Lake Ontario.A. Yellowstone National ParkB. The Grand CanyonC. Niagara FallsD. The Great Salt Lake67.The native Alaskan population includes the following except the .A. IndiansB. EskimosC. AleutsD. Blacks68.The largest minority in the United States is the .A. Pacific IslandersB. BlacksC. Native AmericansD. Asians69.The Immigrants Act of 1924 restricted the further immigration into the United States, particularlyfrom .A. EuropeB. AsiaC. AfricaD. South America70.The characteristic of dominant American culture is .A. English-speaking, northern European, Roman Catholic and middle-classB. English-speaking, western European, Roman Catholic and upper-classC. English-speaking, northern European, Protestant and upper-classD. English-speaking, western European, Protestant and middle-class71.The first successful English colony in North America was founded at in .A. Jamestown, LouisianaB. Boston, MassachusettsC. Jamestown, VirginiaD. Plymouth, Georgia72.Pilgrim Fathers are a group of who came to America to avoid persecution in England.A. ProtestantsB. PuritansC. CatholicsD. Christians73.The Seven Years’ War occurred between the .A. French and American IndiansB. French and SpaniardsC. French and BritishD. British and American Indians74.“No taxation without representation” was the rallying slogan of .A. the settlers of VirginiaB. the people of PennsylvaniaC. the colonists in New EnglandD. the people of the 13 colonies75.The first shots of the American War of Independence were fired in .A. ConcordB. LexingtonC. PhiladelphiaD. Boston76.In May 1775, was held in Philadelphia and began to assume the functions of a nationalgovernment.A. the First Continental CongressB. the Second Continental CongressC. the Boston Tea PartyD. the Congress of Confederation77.Abraham Lincoln issued to grant freedom to all slaves.A. Declaration of IndependenceB. ConstitutionC. Emancipation ProclamationD. Bill of Rights78.The policy of the United States was at the beginning of the two world wars.A. neutralityB. full involvementC. partial involvementD. appeasement79.President applied New Deal to deal with the problems of the Great Depression.A. WilsonB. TrumanC. RooseveltD. Kennedy80.The Vietnam War was a long-time suffering for Americans, and it continued throughout the terms ofPresidents .A. Johnson, Nixon and FordB. Truman, Eisenhower and KennedyC. Kennedy, Johnson and NixonD. Eisenhower, Kennedy and Johnson81.The U. S. Constitution came into effect in .A. 1787B. 1789C. 1791D. 179382.The Constitution of the United States .A. gives the most power to CongressB. gives the most power to the PresidentC. tries to give each branch enough power to balance the othersD. gives the most power to the Supreme Court83.The Bill of Rights .A. defines the rights of Congress and the rights of the PresidentB. guarantees citizens of the United States specific individual rights and freedomsC. is part of the Declaration of IndependenceD. has no relationship with the Constitution84.The following except are guaranteed in the Bill of Rights.A. freedom of religionB. the right to get into people’s house by policeC. freedom of speech and of pressD. the right to own one’s weapon if one wishes85.All the following except cannot make legislative proposal.A. the SenatorB. the RepresentativeC. the Secretary of StateD. the President86.The following except are all powers of the President.A. vetoing any bills passed by CongressB. appointing federal judges when vacancies occurC. making lawsD. issuing executive orders87.According to the Constitution, a candidate for President must be .A. at least 35 years oldB. at least a 14 years’ resident of the United StatesC. born in AmericaD. all of the above88.The terms for a Senator and Representative are and years respectively.A. two, fourB. two, threeC. two, sixD. six, two89.The Supreme Court is composed of justices.A. sixB. sevenC. eightD. nine90.The President is directly voted into office by .A. all citizens of AmericaB. the citizens over 18 years oldC. electors elected by the votersD. the senators and representatives91.America produces a major portion of the world’s products in the following fields except .A. machineryB. automobilesC. oreD. chemicals92.The modern American economy progressed from to , and eventually, to .A. colonial economy, handcraft economy, industrial economyB. farming economy, handcraft economy, industrial economyC. colonial economy, farming economy, industrial economyD. handcraft economy, farming economy, industrial economy93.Chartered companies were NOT granted the by the British King or Queen.A. political authorityB. economic rightsC. judicial authorityD. diplomatic authority94.The first National Bank of the United States was established with the urge of .A. George WashingtonB. Thomas JeffersonC. Andrew JacksonD. Alexander Hamilton95.The following inventions took place during the “second industrial revolution” except .A. typewriterB. telephoneC. electric lightD. refrigerator96.President Johnson tried to build a “Great Society” by introducing various programs like the followingexcept .A. MedicareB. Food StampsC. Education InitiativesD. Unemployment Pension97.About of American crops are for export.A. halfB. one thirdC. one fourthD. one fifth98.The following statements are all true except .A. Agribusinesses reflect the big, corporate nature of many farm enterprises.B. Agribusinesses maintain a balanced trade pattern between agricultural imports and exports.C. Agribusinesses range from one-family corporations to multinational firms.D. Agribusinesses include a variety of farm businesses and structures.99.is not one of the three giants in American automobile industry.A. FordB. General MotorsC. ChryslerD. American Motors100.At present, U. S. exports account for of the world’s total.A. 10%B. 15%C. 20%D. 25%101.Formal education in the United States consists of , secondary and higher education.A. kindergartenB. publicC. elementaryD. private102.Of the following subjects, are NOT offered to elementary school students.A. mathematics and languagesB. politics and business educationC. science and social studiesD. music and physical education103.Higher education in the United States began with the founding of .A. Yale UniversityB. Harvard UniversityC. Princeton UniversityD. New York University104.Of the following, are NOT among the categories of American higher education.A. universities and collegesB. research institutionsC. technical institutionsD. community colleges105.Of the following, is NOT the responsibility of the board of trustees in U. S. institutions.A. choosing the presidentB. establishing policies for administrators and facultyC. approving budget and other financial projectD. decide which student to enroll106.To get a bachelor’s degree, all undergraduate students are required to do the following except .A. attending lectures and completing assignmentsB. passing examinationsC. working for communitiesD. earning a certain number of credits107.Of the following universities, has NOT cultivated any American President yet.A. Harvard UniversityB. Massachusetts Institute of TechnologyC. Princeton UniversityD. Yale University108.is sold especially to the upper or upper-middle class and it has a reputation for its serious attitude and great bulk.A. The Washington PostB. The New York TimesC. Los Angeles TimesD. New York Daily News109.Of the following, is NOT among the three major radio and TV networks in America.A. the National Broadcasting System (NBS)B. the Public Broadcasting Service (PBS)C. the Columbia Broadcasting System (CBS)D. the American Broadcasting System (ABS)110.The National Day of the United States falls on .A. June 4thB. July 4thC. June 14thD. July 14th111.Of the following writers, are from the Colonial and Revolutionary Periods.A. Benjamin Franklin & Edgar Ellen PoeB. Edgar Ellen Poe & Jonathan EdwardsC. Benjamin Franklin & Jonathan EdwardsD. Edgar Ellen Poe & Washington Irving112.is regarded as “the father of American literature”.A. James Fennimore CooperB. Ralph Waldo EmersonC. Thomas JeffersonD. Washington Irving113.Of the following, is NOT Nathaniel Hawthorne’s work.A. The Scarlet LetterB. The House of the Seven GablesC. The Marble FaunD. Nature114.Of the following, is considered Herman Melville’s masterpiece.A. The Last of the MohicansB. The Legend of Sleepy HollowC. Moby DickD. Daisy Miller115.Of the following, is NOT characteristic of Mark Twain’s works.A. colloquial speechB. a sense of humorC. a realistic viewD. an idealistic view116.Of the following writers, is NOT included in the group of naturalists.A. Stephen CraneB. Frank NorrisC. Theodore DreiserD. Herman Melville117.F. Scott Fitzgerald’s finest novel is , and its theme is about .A. The Great Gatsby, the American DreamB. Tender is the Night, loveC. Tales of the Jazz Age, the loss of oneselfD. The Beautiful and the Damned, the evil of human nature118.Of the following books, is NOT written by Ernest Hemingway.A. The Sun Also RisesB. The Sound and the FuryC. A Farewell to ArmsD. For Whom the Bell Tolls119.Of the following writers, is Not a Nobel Prize winner.A. Alice WalkerB. Ernest HemingwayC. William FaulknerD. Eugene O’Neil120.is the first African-American winner of the Nobel Prize for Literature.A.Ralph EllisonB. Tony MorrisonC. Richard WrightD. James Baldwin选择题参考答案:第一章 A B C D B C D A C B第二章 D D B C C A B A C D三 C D B A B C C B D A四 C B A C D C D B A C五 D B B A B C C D D A六 B C B D C A C D B A八 C A B B C C D B A D九 C B C D B B C A C D十 B C B B C C D D D C十一 C C D D D D B B D A十二 C B B B D C B B B B十三 C D D C D D A B A B二、判断题及答案Chapter 11.The island of Great Britain is geographically divided into three parts: England, Scotland and Wales. (T)2.People in different parts of Britain like to use the name England to refer to their country.(F)3.Today more than half of the people in Wales still speak the ancient Welsh language.(F)4.In terms of population and area,Northern Ireland is the second largest part of the United Kingdom.(F)5.The longest river of Britain originates in Wales.(T)6.Because of political troubles,Northern Ireland has been quite significant among the four constituent parts of the United Kingdom.(T)7.Though the climate in Britain is generally mild,the temperature in northern Scotland often falls below --10C in January.(F)8.The majority of the people in Britain are descendants of the Anglo--Saxons.(T)9.The Celtic people are the earliest known inhabitants of Britain.(T)10.English changed into what is described as Modern English from the late 16th century.(F)Chapter 21.The British history before 55BC is basically undocumented.(T)2.The Celts became the dominant group in Britain between the 8th and 5th centuries BC.(T)3.The name of Britain came from a Celtic tribe--- the Britons.(T)4.The Anglo--Saxons came to Britain in the mid--5th century.(T)5.The chief or king of the Anglo--Saxon tribes exercised power at their own will.(F)6.The Vikings began to attack the English coast in the 8th century.(T)7.Henry II built up a large empire which included England and most of France.(T)8.The Magna Carta was designed to protect the rights of both the privileged class and the townspeople.(F)9.The Hundred Years' War was a series of wars fought between England and Normans foe trade and territory.(F)10.In an effort to make a compromise between different religious factions,Queen Elizabeth I actually defended the fruit of the Religious Reformation.(T)Chapter 31.Conventions are regarded less important than common law in the working of the British government.(F)2.The British monarchy has never been interrupted throughout the history.(F)3.In reality,the British King or Queen is the source of all government powers.(F)4.British Parliament is the law--making body of the Commonwealth of Nations.(F)5.Lords Spiritual and Lords Temporal are all members in the British Upper House.(T)6.The members in the House of Commons are appointed rather than elected.(F)7.The British Prime Minister is the leader of the majority party in Parliament.(T)8.Cabinet members are chosen by the Prime Minister from various political parties in Parliament.(F)9.British law consists of two parts,the civil law and the criminal law.(T)10.The legal systems in England, Wales, Scotland and Northern Ireland are much similar in terms of law, organization and practice.(F)Chapter 41.Britain was the first industrialized nation in the world.(T)2.The British economy experienced a relative decline during the postwar period.(T)3.Limited resources and high unemployment rate were persistent problems that prevented rapid economic development in Britain.(F)4.Thatcher's revolution turned out to be a great success in dealing with all the British econimic and social problems.(F)5.The economic approach adopted by Tony Blair is different from that of the Labor party and the Conservative Party.(T)6.Blair made the Bank of England independent in order to separate politics and economic policy.(T)7.Britain is the world's leading exporter of poultry and dairy products.(F)8.The fishing industry provides more than 50%of Britain's demand for fish.(T)9.Britain is an important oil exporter since its oil industry has a long history.(F)10.Nuclear power is one of the major energy sources in Britain.(T)Chapter 51.The British government has been responsible for education since the early 1800s.(F)cation in Britain is compulsory for all children between the ages of 6 and 15.(F)3.The National Curriculum is compulsory in both the state system and the independent system.(F)4.When children finish their schooling at 16, they are required to take a national GCSE examination.(T)5.Graduates from state schools in Britain have a less favorable chance to enter famous universities than those from independent schools.(T)6.In the 1960s, a large number of new universities were founded in Britain.(T)7.Most British people begin their day with reading the morning newspaper and end it watching television in the evening.(T)8.The Times is the world's oldest national newspaper(F)9.The BBC World Service broadcasts only in English throughout the world.(F)10.Some British holidays are celebrated to mark the important events of the Christian calendar, and others are related to local customs and traditions.(T)Chapter 61.The Canterbury Tales is a representative work of the Old English Period.(F)2.Renaissance is characterized by admiration of the Greek and Latin classics.(T)3.Hamlet depicts the hero's struggle with two opposing forces: moral integrity and the need to avenge his father's murder.(T)4.Alexander Pope was a great English poet who also translated Homer's Iliad.(T)5.Jonathan Swift is probably the foremost prose satirist in the English language, and Robinson Crusoe is his masterpiece.(F)6.William Wordsworth and Samuel Taylor Coleridge brought the Romantic Movement to its height.(F)7.Lord Byron distinguished himself by the musical quality of his short poems, such as "Ode to the West Wind".(F)8.Jane Austen was a well--known novelist of the stream of consciousness school.(F)9.Joseph Conrad is classified as a forerunner of Modernism, which prevailed before World War II.(T)10.detailed in his works the dual problems of the Third World: the oppression of colonialism and the chaos of postcolonialism.(T)Chapter 71.The Republic of Ireland occupies the entire area of the island of Ireland.(F)2.The earliest inhabitants in Ireland were Celtic tribes from Europe.(F)3.In the 1800s, Ireland gained in prosperity because it became a part of Britain.(F)4.In the 1930s, Ireland was not indeed a republic,but belonged to the Commonwealth of Nations.(T)5.To support the government's neutrality in World War II, there was no Irishman participating in the war.(F)6.With the help of Britain, Ireland entered the EEC in 1973 without difficulties.(F)7.In 1949, Britain recognized the independence of the Irish Republic and returned the six northern countries.(F)8.In Ireland, both the House of Representatives and the Senate have the power of making laws.(F)9.English is the only official language in Ireland, because the majority of people speak it as their tongue.(F)10.Catholicism in Ireland is more than a mere matter of private faith.(T)Chapter 8。
EN Official Journal of the European Communities732002 L

I(Acts whose publication is obligatory)REGULATION(EC)No417/2002OF THE EUROPEAN PARLIAMENT AND OF THE COUNCILof18February2002on the accelerated phasing-in of double hull or equivalent design requirements for single hull oil tankers and repealing Council Regulation(EC)No2978/94THE EUROPEAN PARLIAMENT AND THE COUNCIL OF THE EUROPEAN UNION,Having regard to the Treaty establishing the European Community,and in particular Article80(2)thereof,Having regard to the proposal from the Commission(1),Having regard to the opinion of the Economic and Social Committee(2),Having regard to the opinion of the Committee of the Regions(3),Acting in accordance with the procedure laid down in Article 251of the Treaty(4),Whereas:(1)Within the framework of the common transport policy,further measures must be taken to enhance safety andprevent pollution in maritime transport.(2)The Community is seriously concerned by the shippingaccidents involving oil tankers and the associated pollu-tion of its coast-lines and harm to its fauna and floraand other marine resources.(3)In its communication‘a common policy on safe seas’,the Commission underlined the request of the extraor-dinary Council on Environment and Transport of25January1993to support the action in the InternationalMaritime Organisation(IMO)on the reduction of thesafety gap between new and existing ships by upgradingand/or phasing out existing ships.(4)In its Resolution on a common policy on safe seas(5),the European Parliament welcomed the Commissioncommunication and called in particular for action to betaken to improve tanker safety standards.(5)By its Resolution of8June1993on a common policyon safe seas(6),the Council fully supported the objec-tives of the Commission communication.(6)In its Resolution on the oil slick off the French coastadopted on20January2000,the European Parliamentwelcomed any efforts by the Commission to bringforward the date by which oil tankers will be obliged tohave a double-hull construction.(7)The International Maritime Organisation(IMO)hasestablished,in the International Convention for thePrevention of Pollution from Ships,1973and theProtocol of1978related thereto(MARPOL73/78),internationally agreed pollution prevention rulesaffecting the design and operation of oil tankers.Member States are Parties to MARPOL73/78.(8)According to Article3.3of MARPOL73/78,thatConvention does not apply to warships,naval auxiliaryor other ships owned or operated by a State and usedonly for government non-commercial services.(9)Comparison of tanker age and accident statistics showsincreasing accident rates for older ships.It has beeninternationally agreed that the adoption of the1992amendments to MARPOL73/78requiring the applica-tion of the double hull or equivalent design standards toexisting single hull oil tankers when they reach a certainage will provide those tankers with a higher degree ofprotection against accidental oil pollution in the event ofcollision or stranding.(10)It is in the Community's interest to adopt measures toensure that oil tankers entering into ports and offshoreterminals under the jurisdiction of Member States andthat oil tankers flying the flags of Member States complywith Regulation13G of Annex I of MARPOL73/78asrevised in2001by Resolution MEPC95(46)in order toreduce the risk of accidental oil pollution in Europeanwaters.(1)OJ C212E,25.7.2000,p.121andOJ C154E,29.5.2001,p.41.(2)OJ C14,16.1.2001,p.22.(3)OJ C22,24.1.2001,p.19.(4)Opinion of the European Parliament of30November2000(OJ C228,13.8.2001,p.140),Council Common Position of7August2001(OJ C307,31.10.2001,p.41)and Decision of the EuropeanParliament of13December2001.(5)OJ C91,28.3.1994,p.301.(6)OJ C271,7.10.1993,p.1.(11)Amendments to the MARPOL73/78Conventionadopted by the IMO on6March1992entered intoforce on6July1993.These measures impose doublehull or equivalent design requirements for oil tankersdelivered on or after6July1996aimed at preventing oilpollution in the event of collision or stranding.Withinthese amendments,a phasing-out scheme for single hulloil tankers delivered before that date took effect from6July1995requiring tankers delivered before1June1982to comply with the double hull or equivalentdesign standards not later than25years and,in somecases,30years after the date of their delivery.Suchexisting single hull oil tankers would not be allowed tooperate beyond2007and,in some cases,2012unlessthey comply with the double hull or equivalent designrequirements of Regulation13F of Annex I of MARPOL73/78.For existing single hull oil tankers delivered after1June1982or those delivered before1June1982andwhich are converted,complying with the requirementsof MARPOL73/78on segregated ballast tanks and theirprotective location,this deadline will be reached at thelatest in2026.(12)New important amendments to Regulation13G ofAnnex I of MARPOL73/78were adopted on27April2001by the46th session of the IMO Marine Environ-ment Protection Committee(MEPC-46)by ResolutionMEPC95(46),entering into force on1September2002,in which a new accelerated phasing-out scheme forsingle hull oil tankers was introduced.The respectivefinal dates by which tankers must comply with Regula-tion13F of Annex I of MARPOL73/78depend on thesize and age of the ship.Oil tankers are therefore in thatscheme divided into three categories according to theirtonnage,construction and age.All these categories,including the lowest one(3),are important for intra-Community trade.(13)The final date by which a single hull oil tanker is to bephased out is the anniversary of the date of delivery ofthe ship,according to a schedule starting in2003until2007for Category(1)oil tankers,and until2015forCategory(2)and(3)oil tankers.(14)The revised Regulation13G of Annex I of MARPOL73/78maintains the requirements for Category(1)tankers,after25years,to have wingtanks or doublebottoms in protective locations not used for the carriageof cargo or to operate only with hydrostatically balancedloading.(15)That same Regulation introduces a requirement thatCategory(1)and(2)oil tankers may only continue tooperate after the anniversary of the date of their deliveryin2005and2010respectively subject to compliancewith a Condition Assessment Scheme(CAS),adopted on27April2001by IMO in Resolution MEPC94(46).TheCAS imposes an obligation that the flag State adminis-tration issues a Statement of Compliance and is involvedin the CAS survey procedures.(16)Paragraph5of the said Regulation allows for an excep-tion for Category(2)and(3)oil tankers to operate,under certain circumstances,beyond the time-limit oftheir phasing-out.Paragraph8b of the same Regulationgives the right for Parties to the MARPOL73/78Convention to deny entry into the ports or offshoreterminals under their jurisdiction of oil tankers allowedto operate under this exception.Member States havedeclared their intention to use the right.Decision tohave recourse to this right has to be communicated tothe IMO.(17)It is important to ensure that the provisions in thisRegulation do not endanger the safety of crew or oiltankers in search of a safe haven or a place of refuge.(18)In order to allow shipyards in Member States to repairsingle hull oil tankers,Member States may make excep-tions to allow entry into their ports of such vessels,provided they are not carrying any cargo.(19)It should be possible to amend certain provisions of thisRegulation so as to bring them into line with inter-national instruments adopted,amended or entering intoforce after the entry into force of this Regulationwithout broadening its scope.Such amendments shouldbe adopted in accordance with Council Decision1999/468/EC of28June1999laying down the procedures forthe exercise of implementing powers conferred on theCommission(1).(20)In view of the approaching deadline for single hull oiltankers which do not comply with the requirements ofMARPOL73/78on segregated ballast tanks and theirprotective location,and given that this is most relevantfor Category(1)tankers,there are no reasons to main-tain the differential charging system for which Regula-tion(EC)No2978/94(2)provides between such oiltankers and oil tankers that comply with the saidrequirements beyond2007,and therefore Regulation(EC)No2978/94should be repealed,HAVE ADOPTED THIS REGULATION:Article1PurposeThe purpose of this Regulation is to establish an accelerated phasing-in scheme for the application of the double hull or equivalent design requirements of the MARPOL73/78Conven-tion to single hull oil tankers.(1)OJ L184,17.7.1999,p.23.(2)Council Regulation(EC)No2978/94of21November1994on the implementation of IMO Resolution A.747(18)on the application of tonnage measurement of ballast spaces in segregated ballast oil tankers(OJ L319,12.12.1994,p.1).Article2Scope1.This Regulation shall apply to oil tankers of5000tons deadweight and above:—entering into a port or offshore terminal under the jurisdic-tion of a Member State,irrespective of their flag,or —flying the flag of a Member State.2.This Regulation shall not apply to any warship,naval auxiliary or other ship,owned or operated by a State and used, for the time being,only on government non-commercial service.Member States shall,so far as is reasonable and practic-able,endeavour to respect this Regulation for the ships referred to in this paragraph.Article3DefinitionsFor the purpose of this Regulation,the following definitions shall apply:1.‘MARPOL73/78’shall mean the International Conventionfor the Prevention of Pollution from Ships,1973,as modi-fied by the Protocol of1978relating thereto together with the amendments thereto,in force on18February2002;2.‘revised Regulation13G of Annex I of MARPOL73/78’shall mean the amendments to Regulation13G of Annex I to MARPOL73/78and to the Supplement to the IOPP Certificate,as adopted by Resolution MEPC94(46)of27 April2001which enters into force on1September2002;3.‘oil tanker’shall mean an oil tanker as defined in Regula-tion1(4)of Annex I of MARPOL73/78;4.‘deadweight’shall mean deadweight as defined in Regula-tion1(22)of Annex I of MARPOL73/78;5.‘new oil tanker’shall mean a new oil tanker as defined inRegulation1(26)of Annex I of MARPOL73/78;6.‘category(1)oil tanker’shall mean an oil tanker of20000tons deadweight and above carrying crude oil,fuel oil, heavy diesel oil or lubricating oil as cargo,and of30000 tons deadweight and above carrying oil other than the above,which does not comply with the requirements for new oil tankers as defined in Regulation1(26)of Annex I of MARPOL73/78;7.‘category(2)oil tanker’shall mean an oil tanker of20000tons deadweight and above carrying crude oil,fuel oil, heavy diesel oil or lubricating oil as cargo,and of30000 tons deadweight and above carrying oil other than the above,which complies with the requirements for new oil tankers as defined in Regulation1(26)of Annex I of MARPOL73/78;8.‘category(3)oil tanker’shall mean an oil tanker of5000tons deadweight and above but less than that specified in definitions6and7;9.‘single hull oil tanker’shall mean an oil tanker not meetingthe double hull or equivalent design requirements of Regu-lation13F of Annex I of MARPOL73/78;10.‘double hull oil tanker’shall mean an oil tanker meetingthe double hull or equivalent design requirements of Regu-lation13F of Annex I of MARPOL73/78;11.‘age’shall mean the age of the ship,expressed in numberof years after the date of its delivery;12.‘heavy diesel oil’shall mean diesel oil as defined in revisedRegulation13G of Annex I of MARPOL73/78;13.‘fuel oil’shall mean heavy distillates or residues from crudeoil or blends of such materials as defined in revised Regu-lation13G of Annex I of MARPOL73/78.Article4Compliance with the double hull or equivalent design requirements by single hull oil tankers1.No oil tanker shall be allowed to operate under the flag of a Member State,nor shall any oil tanker,irrespective of its flag,be allowed to enter into ports or offshore terminals under the jurisdiction of a Member State after the anniversary of the date of delivery of the ship in the year specified hereafter, unless such tanker is a double hull oil tanker:(a)for category(1)oil tankers:—2003for ships delivered in1973or earlier,—2004for ships delivered in1974and1975,—2005for ships delivered in1976and1977,—2006for ships delivered in1978,1979and1980,—2007for ships delivered in1981or later; (b)for category(2)oil tankers:—2003for ships delivered in1973or earlier,—2004for ships delivered in1974and1975,—2005for ships delivered in1976and1977,—2006for ships delivered in1978and1979,—2007for ships delivered in1980and1981,—2008for ships delivered in1982,—2009for ships delivered in1983,—2010for ships delivered in1984,—2011for ships delivered in1985,—2012for ships delivered in1986,—2013for ships delivered in1987,—2014for ships delivered in1988,—2015for ships delivered in1989or later;(c)for category(3)oil tankers:—2003for ships delivered in1973or earlier,—2004for ships delivered in1974and1975,—2005for ships delivered in1976and1977,—2006for ships delivered in1978and1979,—2007for ships delivered in1980and1981,—2008for ships delivered in1982,—2009for ships delivered in1983,—2010for ships delivered in1984,—2011for ships delivered in1985,—2012for ships delivered in1986,—2013for ships delivered in1987,—2014for ships delivered in1988,—2015for ships delivered in1989or later.2.A Category(1)oil tanker of25years and over after the date of its delivery shall comply with either of the following provisions:(a)it shall have wing tanks or double bottom spaces,not used for the carriage of oil and meeting the width and height requirements of Regulation13E(4)of Annex I of MARPOL 73/78,cover at least30%of L t,for the full depth of the ship on each side or at least30%or the projected bottom shell area within L t where L t is as defined in Regulation 13E(2)of Annex I of MARPOL73/78,or(b)it shall operate with hydrostatically balanced loading, taking into account the guidelines developed by the IMO Resolution MEPC64(36).Article5Compliance with the Condition Assessment Scheme for Category(1)and Category(2)ships1.An oil tanker shall not be allowed to enter into ports or offshore terminals under the jurisdiction of a Member State beyond the anniversary of the date of delivery of the ship,in 2005for Category(1)ships,and in2010for Category(2) ships,unless it complies with the Condition Assessment Scheme referred to in Article6.2.The competent authorities of a Member State may allow an oil tanker flying the flag of that Member State to continue operation beyond the anniversary of the date of delivery of the ship in2005for Category(1)ships and in2010for Category (2)ships,but only when subject to compliance with the Condi-tion Assessment Scheme referred to in Article6.Article6Condition Assessment SchemeFor the purposes of Article5,the Condition Assessment Scheme adopted by MEPC Resolution94(46)of27April2001 shall apply.Article7Final dateAfter the anniversary of the date of delivery of the ship in 2015:—the continued operation,in accordance with paragraph5of revised Regulation13G of Annex I to MARPOL73/78,of Category(2)and Category(3)oil tankers under the flag of a Member State,and—the entry into the ports or offshore terminals under the jurisdiction of a Member State of other Category(2)and Category(3)oil tankers,irrespective of the fact that they continue to operate under the flag of a third State in accordance with paragraph5of revised Regulation13G of Annex I to MARPOL73/78,shall no longer be allowed.Article8Exemptions for ships in difficulty or for ships to berepaired1.By way of derogation from Articles4,5and7,the competent authority of a Member State may,subject to national provisions,allow,under exceptional circumstances,an individual ship to enter the ports or offshore terminals under the jurisdiction of that Member State,when:—an oil tanker is in difficulty and in search of a place of refuge,—an unloaded oil tanker is proceeding to a port of repair.2.Member States shall,in due time,but before1September 2002,communicate to the Commission the provisions of national law which they will apply in the circumstances referred to in paragraph1.The Commission shall inform the other Member States thereof.Article9Notification to the IMO1.The Presidency of the Council,acting on behalf of the Member States,and the Commission shall jointly inform the IMO of the adoption of this Regulation,whereby reference shall be made to Article211,paragraph3of the United Nations Convention on the Law of the Sea.2.Each Member State shall inform the IMO of its decision to deny entry of oil tankers,pursuant to Article7of this Regulation,operating in accordance with the provisions of paragraph5of revised Regulation13G of Annex I of MARPOL 73/78into the ports or offshore terminals under its jurisdic-tion,on the basis of paragraph8(b)of revised Regulation13G of Annex I of MARPOL73/78.3.Each Member State shall notify the IMO if it allows, suspends,withdraws or declines the operation of a Category(1) or a Category(2)oil tanker entitled to fly its flag,in accordance with Article5,on the basis of paragraph8(a)of revised Regula-tion13G of Annex I of MARPOL73/78.Article10Committee procedure1.The Commission shall be assisted by the committee set up pursuant to Article12(1)of Council Directive93/ 75/EEC(1),hereinafter referred to as‘the Committee’.2.Where reference is made to this paragraph,Articles5and 7of Decision1999/468/EC shall apply,having regard to the provisions of Article8thereof.The period laid down in Article5(6)of Decision1999/468/EC shall be set at three months.3.The Committee shall adopt its rules of procedure.Article11Amendment procedureThe references in the Articles of this Regulation to the regula-tions of Annex I of MARPOL73/78and to Resolutions MEPC 94(46)and95(46)shall,if appropriate,be amended in accord-ance with the procedure referred to in Article10(2),in order to bring the references into line with amendments to these regula-tions and resolutions adopted by the IMO,in so far as such amendments do not broaden the scope of this Regulation.Article12RepealCouncil Regulation(EC)No2978/94is hereby repealed as from31December2007.Article13Entry into forceThis Regulation shall enter into force on the twentieth day following its publication in the Official Journal of the European Communities.It shall apply from1September2002.This Regulation shall be binding in its entirety and directly applicable in all Member States. Done at Brussels,18February2002.For the European ParliamentThe PresidentP.COXFor the Council The President J.PIQUÉI CAMPS(1)Council Directive93/75/EEC of13September1993concerning minimum requirements for vessels bound for or leaving Community ports and carrying dangerous or polluting goods(OJ L247, 5.10.1993,p.19).Directive as last amended by Commission Direc-tive98/74/EC(OJ L276,13.10.1998,p.7).。
Languages

According to a survey published by theEuropean Commission, the British are officially theworst language learners in Europe — 62 percentof them can’t speak any other language apart fromtheir own! While 38 percent of Britons speak at leastone foreign language, only 18 percent speak two.The European Union average showed that 56percent speak at least one foreign language and 28percent speak at least two. Moreover, 51 percent ofEU citizens can have a conversation in English.Learning a foreign language is not a popular option at school in Britain. Children start studying a foreign language at the age of 11 and many give up completely at 14. So why don’t young people continue with languages at school? Research suggests that students think that it is more difficult to get good grades in languages than in other subjects such as science or history.The government is now looking for different ways to improve language learning. One idea is to start much earlier and introduce foreign languages from the age of 5. Another plan is to give school children more choice and expand the range of languages taught to include Arabic, Mandarin and Urdu.Mandarin Chinese is predicted to become the second most popular foreign language learned in UK schools. Gareth from Wales says, “I am learning Chinese, and find it fun.” Another student, Thomas from London, says, “Just ◎英国大使馆文化教育处/学习魔盒Learning Box 64Crazy English Copyright ©博看网. All Rights Reserved.saying that I learn Mandarin impresses people. Even having a very basic level gives you an advantage.”It may be an ambitious task to change the Brits’ attitude to learning languages, but the government is determined to try!Activity 1 Match the words from the text to their definitions.1. give up2. grade3. impress4. research5. survey6. task a. an investigation using questions to find out what people think or dob. stop doing somethingc. systematic study of a subjectd. a mark to show someone’s level of achievemente. create a favourable effect in someone else’smindf. a specific job or duty(初中天地)65 Copyright©博看网. All Rights Reserved.。
欧洲中心主义英语作文高中

欧洲中心主义英语作文高中Title: Eurocentrism in English Education。
Eurocentrism, the tendency to view the world from a European perspective, has significantly influenced English education in high schools. This phenomenon has both positive and negative implications, which I aim to explore in this essay.To begin with, Eurocentrism in English education often leads to the prioritization of European literature and history in the curriculum. Classic works by Shakespeare, Dickens, and Austen are commonly emphasized, while the contributions of non-European authors may be marginalized or overlooked entirely. This focus on European literary tradition can provide students with a rich cultural background and linguistic proficiency. However, it also perpetuates a narrow worldview that fails to acknowledge the diversity and richness of global literature.Moreover, Eurocentrism extends beyond the literary realm to influence the study of history. European historyis frequently taught as the standard, with other regions being treated as peripheral or subordinate. This approach reinforces the notion of European superiority and downplays the achievements and perspectives of non-European civilizations. As a result, students may graduate with a skewed understanding of world history and a limited appreciation for the contributions of diverse cultures.Furthermore, Eurocentrism can manifest in the English language itself. Standard British English is often privileged over other varieties, such as American English, Indian English, or African English. This linguistic bias can perpetuate cultural hegemony and marginalize speakers of non-standard varieties. It also reinforces the idea that European norms and standards are inherently superior, undermining linguistic diversity and inclusivity.However, it is essential to recognize that efforts are being made to address Eurocentrism in English education. Many educators are advocating for a more inclusivecurriculum that incorporates a broader range of voices and perspectives. This may involve integrating literature and history from diverse cultures, promoting multilingualism, and challenging linguistic biases. By embracing a more global outlook, educators can foster critical thinking skills and empathy in students, preparing them to thrive in an increasingly interconnected world.In conclusion, Eurocentrism has profoundly influenced English education in high schools, shaping curriculum content, linguistic norms, and historical narratives. While this influence can enrich students' understanding of European culture and language, it also perpetuates a narrow worldview and marginalizes non-European perspectives. Efforts to combat Eurocentrism by promoting inclusivity and diversity are essential for creating a more equitable and globally aware educational system. By embracing a broader range of voices and perspectives, educators can empower students to become informed, empathetic, and culturally competent global citizens.。
欧盟的形成与发展讲义

1951
Founding Members
Belgium France Germany
Italy Luxembourg Netherlands
budgets. • Approves EU Commissioners.
European Court of Justice • Highest EU judicial authority. • Ensures all EU laws are interpreted and applied
correctly and uniformly. • Can act as an independent policy maker but unlike
The European Union
United in Diversity - The €uro
The European Union
The €uro
€ In 1999, the euro area was established as a currency in eleven of the then fifteen EU Member States.
Turkey
Potential Candidate Countries
Albania Bosnia & Herzegovina
Montenegro Serbia including Kosovo
under UN Security Council Resolution 1244
The European Union
EUROPEAN COMMUNITY

Final Reporton the work carried out forContract Code GI-POLICY 10338:Study on Policy Issues Relating to Geographic Information in Europe within the framework ofthe IMPACT program of theEUROPEAN COMMUNITYHarald MeixnerAndrew U. FrankJune 1997Final Reporton the work carried out forContract Code GI-POLICY 10338:Study on Policy Issues Relating to Geographic Information in Europe within the framework ofthe IMPACT program of theEUROPEAN COMMUNITYDipl.-Ing. Dr. Harald Meixner, ContractorIngenieurkonsulent für VermessungswesenLinke Wienzeile 4A-1060 Viennameixner@agis.co.atUniv. Prof. Dr. Andrew U. Frank, Project LeaderDept. of GeoinformationTechnical University ViennaGusshausstr. 27-29A-1040 Viennafrank@geoinfo.tuwien.ac.atContract Code GI-POLICY 10338 Table of ContentsStudy on Policy Issues Relating to Geographic Information in EuropeFinal Report - February 1997Executive Summary11. Introduction12. Performance of the Study13. Recommendations3Introduction51. Objectives of the Study52. Contents and Structure of the Final Report53. Research Method53.1 Identify Issues53.2 Status of the Issues53.3 Interviews with Key Decision-Makers54. Background to Study65. Definition of ‘Geographic Information’ used here66. Geographic Information in the Information Age67. Need for Policy6What is Special about Geographic Information?91. Semantic Differences92. Technical Characteristics103. Operational Characteristics of Spatial Data114. Institutional and Legal Characteristics11Identifying The Issues131. Method to Identify other Issues132. The Major Users and Their Uses of Geographic Information132.1 Private142.2 Business142.3 The Public (res publica)142.4 The Administration152.5 Defence153. The Major Producers Within the Geographic Information Business153.1 Public and Private Geographic Information Agencies153.2 Data Collection by Administration and Business Enterprises not Primarily in theGeographic Information Business164. The Interests to Defend164.1 Privacy vs. Need to Know164.2 Copyright and Other Protection of the Data Collections174.3 Consumer vs. Provider of Geographic Information: Liability for Errors174.4 Public at Large174.5 National Security175. Active Groups17Assessment of Current Situation191. Method192. Importance of Digital GI193. Collection of GI193.1 National Mapping Agencies203.2 Topographic mapping203.3 Cadastre204. Conclusions for Europe205. Compare with US Situation20IVStudy on Policy Issues Relating to Geographic Information in EuropePolicy Issues231. Privacy232. Copyright and Protection of Databases233. Data Quality244. Liability245. Security of Data246. Data Access Policy256.1 Potential Misuse of Monopoly Power by NMA256.2 Pricing of Geographic Information, Cost Recovery257. Minimum EU-Wide Geographic Information Base Data268. Public Domain Data269. The Use of Geographic Information by the Public2610. Standardisation and Reference Systems2710.1 Co-ordinate Reference Frame2710.2 Non-Coordinate Reference Frame2711. Promotion for Use of Geographic Information2712. Interactions between the Issues2812.1 Copyright Law and Cost Recovery for NMA2812.2 Cost Recovery and Large Scale Data2812.3 Access to Data, Cost Recovery and Organisation of NMA2812.4 Data Quality, Certification, Liability and Product Differentiation2812.5 Privacy vs. Wider Access28Ranking of the Issues291. Method of Ranking291.1 Topics Discussed291.2 Organisations Interviewed292. Overall Ranking of the GI Policy Issues303. Copyright and IPR314. Data Quality325. Data Access Policies326. Privacy337. Liability338. Security of Data Bases339. Public Domain Data3310. Provision of Minimum EU-wide Geographic Data Base3411. Other Key Issues3412. National/Regional Issues3413. Changes in 5-10 Years3514. Barriers to the Development of the GI markets35Recommendations371. European-Wide Issues and Role of the Commission371.1 Developing a European Access Policy for GI371.2 Developing a European Base Reference Framework for GI Including Base Topographic andSocio-Economic Data371.3 Developing Metadata Standards and Services382. Recommendations to Create and Enhance Awareness of Issues383. Recommendations to Resolve Specific Issues383.1 Copyright393.2 Data Access Policy393.3 Minimum EU-Wide Geographic Information Base Data403.4 Metadata403.5 Issues of Minor Importance41Annex A:Report of Interviews with Key Decision-Makers in Europe on Geographic Information Policy Issues 431. Introduction to the Study451.1 Introduction45Table of Contents V1.2 Objectives and Scope451.3 Background to Study451.4 Structure of the Report462. Overview462.1 Methodology462.2 Topics Discussed472.3 Organisations Interviewed482.4 Overall Findings483. Analysis of the Key Issues513.1 Copyright and IPR513.2 Data Quality533.3 Data Access Policies533.4 Privacy543.5 Liability553.6 Security of Data Bases563.7 Public Domain Data563.8 Provision of Minimum EU-wide Geographic Data Base573.9 Other key Issues573.10 Expected Changes over the next 5-10 years583.11 National/Regional Issues583.12 Priority Issues for the European Commission583.13 Barriers to the Development of the European GI Market604. Conclusions: Priorities for the European Commission61Annex B:Performance Report and List of Contacts67Performance Report69List of contacts721 E XECUTIVE S UMMARYIntroductionThis study identifies and clarifies “issues relating to data policy which are specific to geographicinformation” and gives recommendations to increase awareness and for the resolution of some of theissues. It is mostly based and reports on a large number of contacts with knowledgeable individualsinfluencing the development of the GI market and on structured interviews with a number of keydecision-makers.Geographic information is information, which “can be related to a location (defined in terms ofpoint, area or volume) on the Earth, particularly information on natural phenomena, cultural and human resources“ [GIS Dictionary 1991]. The commission has identified the following list of issues to bestudied for a general European information policy:• Privacy,• Copyright and Protection of Databases,• Data Quality,• Liability,• Security of Data,• Data Access Policy,• Minimum EU-wide Geographic Information Base Data,• Public Domain Data.Performance of the StudyThe study reviewed systematically the issues in a broad context using desk research. It then gathered information to get an appraisal of the situation in Europe with respect to GI. The issues for a GI policywere systematically identified. In a series of interviews with key decision-makers their assessment of theissues was explored in open ended discussions. They were specifically asked to rank the issues. Theseopinion leaders were also asked to identify major barriers to the GI business and to assess some proposedfields of policy action.The team is led by Andrew U. Frank and advised by a steering committee consisting of PeterBurrough, Massimo Craglia, Ian Masser and David Rhind. The contract is administrated by Dr. Harald Meixner.Major FindingsCopyright and Protection of DatabasesThe protection for geographic data by the copyright rules in most European countries is limited, due tolack of originality. The new EU directive on legal protection of databases is assumed to apply forgeographic information. Its translation into national laws and its application by the courts will show ifthis protection is appropriate and sufficient.Data QualityStandardised methods to describe and measure data quality are crucial to develop a market in geographic information. Buyers of data must assess the fitness of datasets offered for their application.Data quality is one of the primary methods for data providers to differentiate the products theydeduce from their data and justify higher prices for higher quality data.Data Access PolicyAvailability of data is one of the most important limitations in the EU geographic information market(and the major difference to the situation in the USA). Data are collected, but access to the data isdifficult:Lack of mandate: Many of the data collectors, in particular the local authorities, have no mandateto make the data available to others (independent of pricing). Public accounting rules are often adisincentive to efforts to sell data. Only the NMA of UK, Netherlands and France have a mandate for2Study on Policy Issues Relating to Geographic Information in Europe‘cost recovery’. There is no organisation with a mandate to collect geographic data at the Europeanlevel.Bureaucratic procedures in different countries vary and it is often difficult to gain information ofwhat is available. The exact details of licences for use of geographic information vary and make itdifficult to assemble and sell pan-European datasets (also due to differences in national copyright rules). Emerging issuesThe other issues are considered less important today, probably due to the current immaturity of the GImarket, but it is pointed out that they will increase in importance for the GI business over the next years. Specific for geographic data are:PrivacyOne of the particular issues of the GIS technology is that it enables data integration to an extentpreviously not possible, which opens up new business opportunities but also dangers, such as invasion of privacy. Postal addresses provide a widely used key to data about individuals. Spatial processing of thesedata may circumvent privacy protection rules. Methods to protect privacy better and hinder analyticaluse of the data less, should be developed. Certain information about the location of some features, e.g.bird breeding places, should be kept secret, even if they are not associated with persons.Minimum EU-Wide Geographic Information Base DataThe respondents were divided on the question if a business case for a minimum EU-wide geographic information base can be made. Several key decision-makers pointed out that the EU is the major user ofpan-European data and harmonised approach by the EU could advance the GI market greatly. Standardisation, in Particular Spatial Reference SystemsThere is a European need for easy-to-follow procedures to integrate national data into an European framework. This applies not only to the co-ordinate based geodetic reference systems (exists in form ofthe little known EUREF datum), but also to non-coordinate based systems (e.g., postcode, statistical enumeration areas, political subdivisions).Barriers to the Development of the GI marketsThe key decision-makers considered the lack of awareness clearly as the most important major barrier tothe development of the GI markets. The lack of awareness is mostly among the politicians and keydecision-makers at the European, national, regional and local level.Two observations are noteworthy:• Technical issues are not considered as major obstacle, and• The Southern European leaders point to the lack of a critical mass of geographic data and users. Ranking of Priorities for the CommissionThe assessment of three potentially important issues for action by the commission resulted in broadvariation in the answers from the key decision-makers. Developing a European Access Policy for GI wasranked highest, but was considered very difficult, due to the many cultural, legal, social and economic barriers. The development of a European-wide Reference Framework ranked second. The lack ofinternal co-ordination within the EU, as the major consumer of pan-European geographic informationwas criticised by the key decision-makers. They assume the market could be developed to satisfy theneeds of the commission, if co-ordinated. The issue of Metadata standards and services was perceived asof lesser importance, partly because many already work on this front.SummaryIn general the situation regarding geographic data in Europe varies enormously. The differencesbetween the countries, within countries and among application areas are very large. There is a noticeable difference between Northern and Central/Southern European countries.The list of topics assembled by DG XIII covers the issues well. As a general observation, mostof the rules for information policy in general apply also to geographic information. Additionally,access and use of GI by the public, standardisation and reference systems and promotion for GI must be considered.Executive Summary3 The key decision-makers ranked Copyright, Data Quality and Access to Geographic Data highest. Leaders from Northern Europe stressed copyright more, whereas the respondents from Southern and Central Europe ranked Data Access Policy highest.Recommendations• The most important efforts must increase awareness for GI among politicians and administrative leaders at the EU-, national, regional and local level. Convincing benefits and concrete solutions of the perceived problems must be found and widely publicised. Focused GI awareness days at the national levels and preferably carried out in the national languages should concentrate on thelegal, administrative and economic aspects; technical problems seem not to be an impediment.• The development of an Access Policy is one of the most important tasks that the EC should undertake, as only the Commission has the opportunity to stimulate and coordinate nationalpolicies. Given the significant variations that exist at present, there is a need for the EC tostimulate the debate at the national levels and develop comparative profiles of the existingconditions in the 15 EU member countries similar to the EUROGI study on copyright.Further, efforts to publicise and promote ‘best business practice’ to demonstrate how theadministrative and legal impediments for a GI market can be overcome would contribute to amore immediate improvement of data access.• The co-ordination of the EU internal use of geographic data is urgently needed and will likely advance the GI market.• The differences in the national copyright and IPR regimes were studied by EUROGI and policies must be developed to promote an uniform implementation of the Database Directive into thenational legislation. The process under way with the Green Paper on Copyright should becontinued and it must be verified that the particular features of GI are covered.• Support the development of the GI market in the poorer regions through support for data sharing arrangements, improvement of data quality and modernising public administration to build acritical mass of geographic data and GI users.• In the existing efforts to address the needs of a general European Information Policy, especially the issues of copyright and Intellectual Property Rights, the special requirements of Geographic Information should be considered.5 I NTRODUCTIONObjectives of the StudyThe object of the ‘Study on Policy issues relating to Geographic Information in Europe’ is to “identifyand clarify issues relating to data policy which are specific to geographic information. The studyexamines data policy to determine the special elements that specifically relate to geographic information.For each issue, a statement will be developed summarising the current situation in regard to geographic information” [Request for Proposal on GI Policy Study]. The study had also to collect and analyse theopinions of key decision-makers in the field.Contents and Structure of the Final ReportThe final report consists of• an executive summary,• a list of issues and• their current status in the EU,• a ranking of the issues, and• detailed recommendations for improving awareness in general and• how to resolve particular issues at the EU level.The report starts in this section with the Terms of Reference and the method and background to the study. Section 3 discusses what is special about spatial information. Section 4 identifies the issues andsection 5 assesses briefly the current situation in Europe and compares it with the USA. Section 6describes the policy issues in detail. The following section ranks the issues based on interviews with key decision-makers and what these see as the major barriers to the GI business. The last section gives the proposed recommendations.The separate Report of Interviews with Key Decision-Makers in Europe, detailing the findingsfrom the interviews is Annex A. A report on the performance of the study, with a list of the contactsmade is found in Annex B.Research MethodThe study applied methods of desk research, questionnaires and interviews in its different phases.Interviews with key decision makers to elicit their views became the major part of the study. The resultsof the study are an interpretation of the opinions collected from key persons in this field. The issues encountered and the opinions found are here represented, but do not necessarily coincide with theopinion of any of the members of the steering committee or the team.Identify IssuesIn the initial phase of analysing the issues, academic style desk research was conducted. It appearednecessary to identity the special character of GI to allow the concentration on points where GI policymust differ from information policy in general. It should review the issues initially identified by the Commission to check if other important issues had to be added. A systematic, analytical review of GIuses and users and producers considered their interests and possible conflicts as source of issues whichcould require policy actions.Status of the IssuesDesk research and a questionnaire were used to make an assessment of the current situation. Informationwas collected from knowledgeable sources in most EU countries.Interviews with Key Decision-MakersThe study called for a collection of the opinions of the key decision-makers. A representative group of individuals were established by the steering committee. It was attempted to achieve regional balancewithin the EU, but also to collect the opinions of the different types of organisations implied in the GIfield. Besides some representatives of NMAs from different parts of the EU, EU-wide organisationsrelated to GI and active within the EU were contacted to get an assessment of their position, national6Study on Policy Issues Relating to Geographic Information in Europeorganisations responsible for co-ordinating GI matters, and companies active in the national orEuropean GI market. It was not intended to create a statistically valid sample - other studies by DG XIIIwere tasked do such - but to gain a valid overview of the current thinking of the key individuals whoinfluence the field, which is possible only by a careful selection of the individuals contacted. Care wastaken to achieve an equitable balance between EU countries, producers and consumers, public andprivate sector etc.In December 1996, 20 interviews with senior representatives of key organisations responsible forthe collection, supply or use of geographic information were conducted by Peter Burrough, MassimoCraglia, Ian Masser and David Rhind. An additional 5 decision-makers were interviewed by AndrewFrank. These interviews followed a structured set of open ended questions. Interviewees were sent the questionnaires a couple of weeks before the interviews so that they had a proper time to reflect on theissues being explored.The detailed results of these interviews are reported in Annex A. This report draws heavily on this material, especially for the ranking and the recommendations.Background to StudyIn August 1995, the European Commission’s DGXIII invited tenders for three studies within theframework of its GI2000 initiative: GI-BASE, GI-META, and GI-POLICY.• GI-BASE is concerned with an assessment of the current market for geographic information in Europe, and has to survey existing data sources and services.• GI-META is concerned with the feasibility of providing European geographic information metadata services by reviewing existing local, national and international metadata services.• The aim of the GI-POLICY study is to examine issues relating to data policies to determine if there are special elements which relate to geographic information.Definition of ‘Geographic Information’ used hereGeographic information is information, which “can be related to a location (defined in terms of point,area or volume) on the Earth, particularly information on natural phenomena, cultural and human resources. The position data can be a specific set of spatial co-ordinates, or it can cover less preciselocations or areas, such as addresses, postal codes or administrative boundaries, regions or even whole countries” [GI2000 1995].Geographic information provides an answer to a human question. It is as various as there are waysto understand the world and the things in it. Geographic information can describe the objects of thephysical reality, it can describe man-made objects, administrative and legal units, aspects of humanculture, economics etc. It describes relevant aspects of these objects in space, their position, their formand attributes describing the objects. Most geographic information also includes a time dimension. Geographic Information in the Information Age“Information is becoming a major world commodity in its own right. It is a major contribution toincrease competitiveness, make economies grow, create new jobs and improve the quality of life”[Request for Proposal on GIPolicy Study]. The transition from the industrial to the information age,which became possible with the development of technical means to process data separated from thephysical support used to represent the information, has profound effects on our social situation.Geographic information is just one kind of information, describing spatial situations in the world:where is what ? Geographic information has been distributed mostly in the form of descriptive texts and beautiful hand drawn maps. Today it has become possible to collect geographic informationsystematically, to manage and process it rapidly and to show results in varying form to suit a wide rangeof user needs. Information technology, especially the Internet, creates business opportunities. There isactually an emerging, rapidly growing business in geographic information and the structures currently inplace to deal with geographic information appear insufficient, on the legal, economic and organisationallevel.Need for PolicyA need for a European geographic information-policy follows from the Treaty of Maastricht:Introduction7• in particular the mandate for a European integrated market: Market opportunities must be available to every entrepreneur on fair competitive terms [GI2000 1995].• the efforts to promote the political, economic, social development in European transborder regions, e.g. Pyrenean region.In general, specific policies may be needed for each goal, but some policies may advance several points.9W HAT IS S PECIAL ABOUT G EOGRAPHIC I NFORMATION?Many of the issues for a GI policy are the same as in other areas of information policy. This study has to concentrate on aspects which are specific to GI. It is therefore necessary to analyse first those propertiesthat make GI special [Barr 1996].Computerised spatial data/information have the same characteristics as many otherdata/information in electronic form. Thus:• unlike most goods, they do not wear out,• they can be copied at low or even near-zero cost,• ‘information theft’ is rendered easier by the ease of copying and the possibility for disguising the source of the data,• use by one person need not preclude use by another,• their value to one person is often much greater than to another,• the value of the data is much greater if collected consistently to high standards which are explicitly defined,• the availability of metadata (data about data) is essential to support a broader use of the data and to guarantee data quality, and• long term archiving in digital form remains a problem as compared to the storage of paper-based information.For Geographic Information in particular, we can differentiate semantic, technical, operational, institutional and legal characteristics,in which it differs from information in general.Semantic DifferencesHuman beings live in space, all human actions are performed in space. For nearly all human actions, geographic information is necessary in one form or another. There are a number of elementaryobservations about space and objects in space, which indicate that geographic information requires somespecial provisions:• There is only one spatial reality and all geographic information refers to the same physical reality. The integration of observation with relation to space is important because activities inspace influence each other. Space provides a concept of neighbourhood and of distance.• The same objects are defined differently for different applications, which leads to confusions.Different activities use space differently and observe different properties and observe themdifferently.• The physical reality can be observed (for most aspects) by anybody. Relatively objective measurements are often possible, but there is no final authoritative source (as there is in adatabase about law).• Geographic information can be observed and collected at different levels of resolution (commonly known as ‘map scales’) and with different focus on content theme. There is no ultimate, finestresolution (as it is in a financial database). Fuzziness with the data is intrinsic and cannot beavoided.• Much geographic information is readily available and needs only to be collected. But some geoscientific data (geological, etc.) are not visible at all and require very complicated and costlyactivities for collection.• The presentation of geographic information follows very strict conventions.• The world is constantly changing and to keep geographic data up-to-date is difficult and requires resources. The data required are describing – at least in principle – a single, universally existingreality and can be used for many applications.Spatial data or information related to geographic units (or ‘real world states’ or ‘objects’) e.g.houses, fields, administrative areas or some representation of a geographical variable such as a set ofcontours describing air temperature or altitude above sea level.• These units are often highly complex and usually are not fixed in size or other properties (e.g. not all communes are the same shape and size and may be disjoint e.g. France includes Corsica).10Study on Policy Issues Relating to Geographic Information in Europe• There is an infinite number of ways of dividing space into such units or ‘objects’ (e.g. in Britain, the land surface is divided up into parliamentary constituencies, local government areas, postalareas and many others by different organisations and none of these match).• Many analyses have to cope with very different types of objects, e.g. some spatial units are assumed to be homogeneous with abrupt changes at their periphery (e.g. soil areas) while othersare functional (e.g. ‘travel to work areas’ are focused on a node but their boundaries are astatistical abstraction).Technical CharacteristicsIrrespective of the type of applications, there are two kinds of spatial data - framework data (represented normally by topography or cadastral information) and related spatial data (of all kinds), which arepositioned in relation to the framework data. This descriptive data cannot be used spatially without the framework even though its involvement may be implicit, rather than explicit.Perhaps the main attribute of the spatial object - its position in space - requires at least 2dimensions (often 3, often additionally a reference to time) to describe it. Simple sorting on onedescription (c.f. on the funds available in bank accounts) will not give a reasonable representation of oraccess to a spatial data set. This has many implications both for the computer systems and for the way inwhich users understand the data/information.Integrating data may involve use of quite different geographical reference systems (e.g. GPS co-ordinates, co-ordinates on some nationally-based projection, relationally-based schemes (‘1.4 km downriver from the bridge’ or ‘1.2 m from the corner of this house’) or ‘nominal’ references such as streetnames and house numbers or postal/zip codes)Spatial data are inherently fuzzy. This occurs for three reasons:• as indicated above, there is no universal metric (e.g. monetary units) to which thedata/information may be related and from which it may be converted unambiguously into othermetrics. For example, conversion of altitudes measured by GPS are often difficult to relate tothose measured by more traditional means and relating postcoded information to informationbased on national co-ordinates systems is always an approximation process,• some of the spatial units or objects are themselves fuzzy (e.g. a mountain range, the Alps have no firmly defined boundaries),• it is possible to measure or record the data at many different levels of detail and even to generalise the data so as to caricature certain characteristics. A map compiled at, say, 1:1 millionscale depicts a different world from one at 1:10,000 scale in terms of the features shown, whereand how they are shown and the relationships between them; databases derived from differentsources retain the characteristics of the source materials.Maintenance of much spatial data is complex, involving up-dating and validation of the geometry, topology and attributes of the numerous objects/units. It is rarely automatable in its entirety andtherefore requires considerable staff skills.Some types of spatial error are insidious and difficult to detect, yet may be extremely serious for theend user. For example, a one millimetre gap between the end points of two roads as stored in a databasemay give rise to completely erroneous route instructions from a car guidance system.Because of the technical characteristics of spatial data, the relationships established betweendifferent data sets are dependent on various factors such as scale, resolution and the positioning and sizeof areas defined by humans (e.g. electoral areas). Thus definitions of, say, poverty, levels of commutingand other policy-related variables are very sensitive to the way in which the data have been assembledand processed and any incompatibilities across the domain of interest (e.g. between nations across the European Union)Spatial data are typically voluminous, especially when portrayed in multi-media form. Typically,many spatial queries involve searching - rather than simply playing back - these data, often for some combination of circumstances (e.g. ‘find me the location of soils of a particular quality and type onwhich crops of a certain type are being grown and where a particular kind of management is practised’).。
Backed by the European Commission, a consortium

Architecture and Design of aSecure Electronic Marketplace Matthias Schunter <schunter@> Michael Waidner <wmi@>AbstractBacked by the European Commission, a consor-tium of partners from European industry, financial institutions, and academia has embarked on a research project to develop the fundamentals of secure elec-tronic commerce. The goal of the ACTS Project SEMPER (Secure Electronic Marketplace for Europe) is to provide the first open and comprehen-sive solution for secure commerce over the Internet and other public information networks. SEMPER’s flexible open architecture is based on a model of elec-tronic commerce which comprehends a business sce-nario as a sequence of transfers and fair exchanges of “business items”, which are payments, data, or rights.This is reflected in the architecture: The exchange and transfer layer handles transfers and fair exchanges of items. The commerce layer provides methods for downloading certified commerce services and the nec-essary trust management. The commerce services implement the terms of business of a seller using the exchange and transfer layer services.A prototype of this architecture implemented in the Java programming language will be trialed for sales of multimedia courseware (EUROCOM, Ath-ens, GR), on-line consultancy and subscriptions (FOGRA, München, D) as well as mail-order retail-ing (Otto-Versand, Hamburg, D). It will integrate the payment systems SET (provided by IBM), Chipper (provided by KPN Research), and ecash™(provided by DigiCash)). The prototype uses a distinguished user-interface for trustworthy user in- and output which enables to use SEMPER on secure hardware.I. IntroductionA wide range of businesses are rapidly moving to explore the huge potential of networked information systems, especially with the Internet-based WWW (World-Wide Web). Although the Internet has its roots in academia and is still dominated by free-of-charge information, dramatic changes are expected in the near future.The goal of the 9-million ECU project, SEM-PER (Secure Electronic Marketplace for Europe) [1, 2], is to provide the first open and comprehensive solution for secure commerce over the Internet and other public information networks.The members of the SEMPER consortium are Cryptomathic (DK), DigiCash (NL), EUROCOM EXPERTISE (GR), Europay International (B),FOGRA Forschungsgesellschaft Druck (D), GMD –German National Research Center for Information Technology (D), IBM (CH, F), INTRACOM (GR), KPN Research (NL), Otto-Versand (D), r3 security engineering (CH), CNET (F), SINTEF (N), S S L (GB), Stichting Mathematisch Centrum / CWI (NL), Universities of Dortmund, Freiburg, and Saarbrücken (D). Banksys (B), Banque Générale du Luxembourg (L) and Telekurs (CH) are associated with SEMPER. IBM Zurich Research Laboratory provides the techni-cal leadership for the project.I.A. Roles and Services in the MarketplaceLike in a physical marketplace, the main purpose of an electronic marketplace is to bring potential sellers and buyers together:• Sellers offer their goods and buyers order these goods; together this is a two-party negotiation, sometimes ending with an agreement.• Both seller and buyer might need certain certifi-cates. For instance, a buyer might only want to buy from sellers that are accredited with a well-known payment system provider in order to usea certain payment instrument. A buyer may onlytrust a seller if a consumer organisation has de-clared them trustworthy. A seller might be al-lowed to deliver certain goods only to residents of the European Union.• Sellers deliver their goods and buyers make payments; together this is a two-party (fair) ex-change.• Buyers or sellers might be dissatisfied with what has happened so far, i.e., several exception han-dlers and dispute handlers which may involve an arbiter are necessary.• Many services require that buyer and seller have some relations already established, e.g., to banks or government agencies. This requires registra-tion, certification, and in most cases also direc-tory authorities.In all these actions, the parties have specific secu-rity requirements, namely integrity, confidentiality, and availability. Confidentiality includes anonymity, which is often a requirement for browsing catalogues or for low-value purchases. Examples of typical scenarios of electronic commerce are:• Mail-order Retailing: A retailer accepts electronic orders and payments, based on digital or conven-tional catalogues, and delivers physical goods.• On-line Purchase of Information and Subscrip-tions: Like mail-order retailing, but with digital,maybe copyright-protected goods that are deliv-ered on-line.• Electronic Mall : An organisation offers services for several service providers, ranging from direc-tory services (“index”) over content hosting to billing services.• Contract Signing : Two or more parties exchange signed copies of the same statement .Naturally, an open system for electronic com-merce cannot be restricted to these scenarios. It should be easily configurable and extensible to a broad range of different scenarios.I.B. What is New in SEMPER?SEMPER is the first project that aims at the complete picture of secure electronic commerce, not just on specific pieces (like electronic payments),specific scenarios (like electronic on-line purchases)or specific products and protocols (An overview can be found at </sirene/>).SEMPER provides an open architecture which enables the integration of any protocol and product providing the necessary services. Therefore, applica-tions are not restricted to specific proprietary tech-nology or specific protocols.Special attention is paid to customer anonymity and privacy. SEMPER develops an integrated ano-nymity management scheme extending the existing concepts for anonymous communication and creden-tials.II. Model for Electronic CommerceThe architecture described in this paper is based on a generic model for two-party electronic com-merce. This model describes the flow of control as well as actions, and decisions for any commerce serv-ice. The main idea of the model for electronic com-merce is describing business scenarios in terms of sequences of transfers and exchanges of data with decisions based on the success of these actions (see Figure 1). This model is similar to the dialogues of interactive EDI.II.A. Atomic Actions: ExchangesThe interactive actions between two players are transfers and exchanges . In a transfer , one party sends a package of business items to one or more other parties. The sending party can define certain security requirements, such as confidentiality, anonymity, or non-repudiation of origin.A fair exchange is a simultaneous exchange of packages of business items among two parties. The parties have the assurance that their packages are sent if and only if the peer entity send their package as expected. Either both packages are exchanged or none. If no fairness guarantee is required, we can model such an exchange by two transfers.Business items which can be exchanged include • credentials , such as access rights,• statements , such as signed documents, certifi-cates, or program and video data, and• money, such as credit-card, cash, or bank transfer payments.Figure 2 gives an overview of the possible ex-changes of these primitive types. Transfers are in-cluded as exchanges of “something” for “nothing.”Buyer:Seller:satisfied?satisfied?satisfied?satisfied?satisfied?satisfied?satisfied?satisfied?satisfied?satisfied?Figure 1Electronic Commerce is a Sequence of Transfers and Exchanges.Note that the protocol might enable other sequences as well, e.g., after "Contract" "Payment with-out Receipt" might also be enabled.II.B. Electronic Commerce: Sequence ofExchangesThe transfers and exchanges are fixed in our model given the data types and security attributes.Any business scenario is modeled as a sequence of exchanges with user-interaction and local decisions between successive exchanges (see Figure 1).In the course of an ongoing business, after each transfer or exchange, the parties are either• satisfied, and thus willing to proceed with a cer-tain number of other transfers or exchanges, or • dissatisfied , in which case an exception or dispute is raised which might end up at a real court if all else fails,depending on the success of the previous ex-change, the items received, and possibly user-input.After each round, a decision as to whether and how to proceed is made.III. The SEMPER ArchitectureThe SEMPER architecture (Figure 4) is struc-tured in layers. The lowest layer deals with low-level security primitives and other supporting services ,whereas the highest layer deals with commerce issues only:• The supporting services are the usual crypto-graphic services, communication, archiving of data (keys, non-repudiation tokens, audit trail),Transfer /Exchange of →for↓Money Credential Information Nothing (i.e.,Transfer)PaymentCertificate transfer rmation transfer Money Fair money exchange Fair payment with receipt Fair purchase CredentialSame as …Fair contract signing Fair conditionalaccess Information… in upper …… right halfFair information exchangeFigure 2Transfers and exchanges of primitive types.S erv e rFigure 3Client- and Server-Side Integration of the SEMPER Electronic Commerce Library.setting preferences, and the trusted user interface.• The exchange layer supports fair exchange and transfer services.• The commerce layer offers high-level services for business scenarios like “mail-order retailing,”“on-line purchase of information,” or “registration with service provider.” It is config-urable by downloading new services or extending existing ones.III.A. Commerce ServicesThe commerce layer implements the flow of con-trol of our model using the transfer and exchange service for interactions with the peer, and the sup-porting services for user-interaction and persistent storage. It also performs the trust management and access control necessary for downloading certified commerce services.The Commerce Layer provides services that di-rectly implement protocols of business scenarios,e.g., how specific merchants or types of merchants handle customer registration and offering, ordering,payment, and delivery of goods. It implements the flow of control, i.e., the enabled sequences of ex-changes, of the electronic commerce model. A set of client and server commerce services is the electronic equivalent of the “terms of business” for the seller.The commerce layer does not only offer entire such protocols, but also building blocks that may be of more general use, in particular services to manage and fill out standardized order forms.Since one cannot fix the set of services in ad-vance, the commerce layer includes services for se-cure downloading of services. This allows customers to participate in business scenarios they never en-countered before. Since arbitrary terms of business may be implemented in a new commerce service, a downloaded service need not be secure at all. Security of the implemented services can only be ensured by a separate evaluation, e.g., by trusted consumer or-ganizations who issue certificates on fair commerce services. The secure downloading process together with trust management and access control then en-sure that• each merchant fixes the terms of business in ad-vance, in a non-reputable way,• that each merchant keeps to its own terms during the whole business, and• that services which have not been evaluated by a trusted authority cannot do any harm.III.B. Exchange ServicesThe Exchange and Transfer Layer provides serv-ices for handling and packaging business items aswell as transfer and fair exchange of packages. It im-plements the exchanges of the electronic commerce model. The basic items are electronic payments, cre-dentials, and general statements which includes digi-tal signatures and data. These items can be bundled in tree-like packages called containers . The security at-tributes stored in each internal node of this tree de-termine the level of security which is required for the transfer or exchange of the corresponding subtree.Each type of items is managed by a separate manager which provides unified services integrating existing implementations. The payment manager for example provides three generic services for handling account-based (which includes credit-card payments)and cash-like payments together with the negotiation of the means of payment. Several payment systems of each of these classes can be installed. During a payment, the payer and the payee’s payment manager then automatically negotiate which payment system shall be used based on the preferences of the users.III.C. Supporting ServicesThe Supporting Services provide user preferencemanagement, persistent object storage, communica-tion, crypto services, and other supporting services such as access control.Supporting Services LayerE xchange and Transfer LayerFigure 4Architecture of SEMPERIV.The SEMPER TrialsIV.A. BasisThe SEMPER trials are based on the World Wide Web. The architecture is implemented by a library, as depicted in Figure 4 and described in detail in Sec-tion III. Service providers using SEMPER only need to implement the actual business terms (enabled se-quences of transfers and exchanges) by configuring so-called commerce services (Figure 3). The integra-tion into the World-Wide Web is done by interfacing with standard browsers and servers.In order to support secure human-computer inter-action, the SEMPER client provides a trusted user interface for security critical user in- and output, such as acknowledging a payment.The first version of the SEMPER library sup-ports only secure transfer services (i.e., no fair ex-changes).IV.B. EUROCOM: Courseware EUROCOM is a consulting company offering mul-timedia courseware in the area of telecommunica-tions. The EUROCOM trial implements on-line purchases of multimedia courses.IV.C. FOGRA: Consultancy andSubscriptionsFOGRA is a research organisation of the German printing and publishing industry. They distribute information to their members on a subscription basis and sell consultancy to non-members. The FOGRA trial uses SEMPER for on-line purchase and process-ing of subscriptions as well as sales of consultancy.IV.D. Otto Versand: Mail OrderOtto Versand is one of the largest mail-order retailers world wide. Currently, over 6000 articles can be browsed and ordered on the World-Wide Web. The Otto trial starts with on-line ordering of goods and may be extended to on-line ordering and delivery of tickets and other credentials.V. AcknowledgementsThis work was supported by the ACTS Project AC026, SEMPER. However, it represents the view of the authors. SEMPER is part of the Advanced Communication Technologies and Services (ACTS) research program established by the European Com-mission, Directorate General XIII. This description is based on joint work of the SEMPER consortium. It is a pleasure to thank all of them for their coopera-tion and contributions. The SEMPER home page is at <>.VI. References[1] SEMPER Consortium: Basic Services:ArchitectureandDesign; SEMPER Deliverable D03; Århus, October 1996.Available at <>[2] SEMPER Consortium: Survey Findings, TrialRequirements, and Legal Franework -- Results from First Year of Project SEMPER; SEMPER Deliverable D05; Hamburg, December 1996.Available at <>.Author InformationMatthias Schunter has been a researcher in com-puter science at the Universities of Hildesheim and Dortmund since 1994. His research interests include formal modelling of privacy and the design of proto-cols providing multi-party security. He has partici-pated in the projects CAFE on off-line electronic payments, and in SEMPER aiming at an open inte-grated solution for global electronic commerce. Both projects were funded by the European Union. He received a diploma in computer science from the University of Hildesheim. He is a member of IEEE, ACM, and IACR.Michael Waidner is the manager of the Network Security research group at the IBM Zurich Research Laboratory, Switzerland and Technical Leader of SEMPER. He has been working for the IBM Re-search Division since 1994. His research interests include cryptography, security, and all aspects of dependability in distributed systems. He has co-authored numerous publications in these fields. He received his diploma and doctorate in Computer Sci-ence from the University of Karlsruhe, Germany. He is a member of ACM, GI, IACR and SIAM.。
欧盟英语作文

欧盟英语作文The European Union (EU) is a political and economic union of 27 member states that are located primarily in Europe. Established in the aftermath of World War II, the EU was designed to foster economic cooperation, secure peace, and prevent future conflicts by creating a single market and a customs union. Over time, it has evolved into a significant global actor, with substantial influence on the world stage. This essay will explore the EU's structure, its impact on member states, and the challenges it faces in maintaining unity amidst diversity.Structure and InstitutionsAt the heart of the EU is a complex system of institutions that guide its policies and actions. The most prominent among these are the European Commission, the European Parliament, the Council of the European Union, and the European Council. The European Commission, often referred to as the EU's executive arm, is responsible for proposing legislation, implementing decisions, and upholding the EU treaties. The European Parliament, directly elected by EU voters, provides democratic representation and has supervisory and budgetary powers. The Council of the European Union, composed of national ministers, defines and coordinates the general political direction of the EU, while the European Council, made up of the heads of state or government, providespolitical direction and priorities.Impact on Member StatesMembership in the EU brings both benefits and obligations. Economically, the EU has facilitated the free movement of goods, services, capital, and people, creating one of the world's largest single markets. This has led to increased trade, economic growth, and job creation. Politically, the EU has provided a platform for member states to collaborate on foreign policy and security matters, enhancing their collective influence. Additionally, the EU has established a framework for protecting human rights, promoting social justice, and ensuring environmental protection.Challenges of Unity in DiversityDespite its successes, the EU faces significant challenges in maintaining unity among its diverse membership. One of the most pressing issues is the management of economicdisparities among member states, which has been exacerbated by events such as the Eurozone crisis. The EU must also navigate the complexities of cultural and linguistic differences, which can sometimes lead to nationalist sentiments and calls for greater autonomy or even secession.Another challenge is the rise of anti-EU sentiment, fueled by concerns over immigration, globalization, and the perceived loss of sovereignty. This has led to the rise of populist movements and political parties that question the EU's value and advocate for a return to national control over various policies.ConclusionThe European Union represents a remarkable experiment in supranational governance, aiming to balance the competing interests of its member states while promoting a sharedvision of peace, prosperity, and cooperation. As it continues to evolve, the EU must address the challenges of economic inequality, cultural diversity, and political fragmentation. By doing so, it can hope to maintain its relevance and effectiveness in an increasingly interconnected and complex world.In conclusion, the EU's journey is a testament to the possibilities of international collaboration. Its ability to adapt and overcome the challenges it faces will not only determine its own future but also have profound implications for the global community.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Sensoria016004Software Engineering for Service-OrientedOverlay Computers D2.1.a:Core calculi for Service Oriented Computing Lead contractor for deliverable:UNIBO,Universit`a di BolognaAuthor(s):G.L.Ferrari(PISA),nese(UNIBO),R.Lucchi(UNIBO),R.Pugliese(DSIUF),and G.Zavattaro(UNIBO)Due date of deliverable:August31,2006Actual submission date:October10,2006Revision:FinalDissemination level:PUContract start date:September1,2005Duration:48monthsProject coordinator:LMUPartners:LMU,UNITN,ULEICES,UWARSAW,DTU,PISA,DSIUF,UNIBO,ISTI,FFCUL,UEDIN,ATX,TILab,FAST,BUTE,S&N,LSS-Imperial,LSS-UCLIntegrated Project funded by theEuropean Community under the“Information Society Technologies”Programme(2002—2006)Executive SummaryThe objective of Work Package2is the development of a foundational methodology for describing service specifications and for developing a discipline for their composition.This document reports on the work conducted inside the SENSORIA project on the definition of foundational calculi that rely on services as the fundamental elements for modelling applications conforming to the Service-Oriented Computing(SOC)paradigm.Relevant SOC idioms that have been considered are:service description,service invocation,service composition and orchestration.The fundamental vehicle undertaken within the project work plan is provided by the theory of process calculi,intended as the collection of linguistic constructs,tools and models that have been developed for designing,analysing,and experimenting with open components interactions.Two intertwined approaches have been followed in the design of core calculi for SOC:bottom-up and top-down.The bottom-up approach consists of electing one specific service oriented technology as the starting point,and extract from it a corresponding core model.The opposite top-down approach consists of designing an abstract model of services that do not tight to a specific technology.The advantage of the latter is that the designed calculi are general enough to be applied to different global computers on which services run.The calculi developed according to the former approach,on the other hand,will be fundamental to crosscheck whether the proposed general calculi actually adhere to the specificities of the currently available service oriented technologies.Contents1Introduction4 2Overview on the Calculi5 3SCC:Service Centered Calculus93.1Motivation (9)3.2Calculus description (9)3.3Discussion and future work (11)4SOCK:Service Oriented Computing Kernel114.1Motivation (11)4.2Calculus description (12)4.3Discussion and future work (14)5C˘o WS:Calculus for Orchestration of Web Services155.1Motivation (15)5.2Calculus description (15)5.3Discussion and future work (18)6SC:Signals Calculus196.1Motivation (19)6.2Calculus description (19)6.3Discussion and future work (21)7Relevant SENSORIA Publications and Reports22 8Conclusion and further plans221IntroductionThe main aim of Work Package2is to seek for a small set of primitives that might serve as a basis forformalising and programming service oriented applications over global computers.As an outcome of this study we describe here four different process calculi:SCC[BBC+06]which isthe result of a joint effort of four different sites(UNIBO,DSIUF,FFCUL,and PISA),SOCK[BGG+06b], C˘o WS[LPT06],and SC[FGS06a]developed in local smaller groups(UNIBO,DSIUF,and PISA,re-spectively).The advantage of working in a larger group,including different project sites,is that differentexpertises,knowledges and experiences merge.This revealed the most appropriate approach for devel-oping a general purpose service oriented calculus able to capture the essence of SOC independently ofspecific technological aspects.On the other hand,the work in smaller local groups permitted to achievemore focused calculi inspired by specific service oriented computing technologies.The research activity devoted to the definition of the core calculi was done in strict collaboration withthe group of researchers responsible for the definition of the SENSORIA ontology.In particular,the corecalculi are mainly focused on View1:Service Description for Coordination and Composition describedin the Deliverable D1.1.a where concepts such as Service,Session,and Orchestration are informallydescribed.For some of these terms,the calculi reported in this Deliverable represent a formal definitionuseful to clarify their actual meaning within the project activities.The general purpose calculus that we developed is SCC(Service Centered Calculus).SCC en-riches the name passing communication mechanism of traditional process calculi,such as theπ-calculus[MPW92],with an explicitic notion of service intended as an entity that can be invoked and that returnsvalues as the result of a client-service bidirectional interaction that we call session.One may argue thatwe could,in our analysis of service oriented computing,exploit directly theπ-calculus instead of intro-ducing yet another process calculus.According to our experience,if we use directly a communicationbased calculus such asπ-calculus,all the information pertaining to sessioning and client-service proto-cols get mixed up(if not lost)with the other communication primitives,making it difficult to reason onthe resulting processes.The motivation behind the introduction of a new calculus is that a small set ofwell-disciplined primitives will favor and make more scalable the development of typing systems andproof techniques centered around the notions of service and session,for ensuring,e.g.,compatibility ofclient and service behaviour,or the absence of deadlock in service composition.The other calculi are directly inspired by some specific technology.SOCK(Service Oriented Computing Kernel)proposes a three layered calculus inspired by theWeb services protocol stack.The service description layer consists of a simple calculus for serviceinterface description which takes inspiration from WSDL[W3Cc]and the abstract fragment of WS-BPEL[BCG+05].At the service engine layer,additional information can be added that indicates how aservice is actually run;this layer is inspired by the full(executable)WS-BPEL language.Finally,at theservice network layer,the modeling of an overall network of interacting services is permitted;the source of inspiration at this level is given by the SOAP[BEK+]protocol for message exchange among Web services.C˘o WS(Calculus for Orchestration of Web Services)considers in a more detailed manner WS-BPEL, the most credited service orchestration language.In particular,more expressive linguistic constructs are considered such as those permitting to interrupt arbitrarily complex processes and activate the needed compensation activities.Finally,SC(Signals Calculus)considers publish/subscribe service interaction instead of messagebased client-service communication.Publish/subscribe is an important paradigm that recently attracteda lot of research effort in the context of peer-to-peer interaction in structured as well as in unstructuredmobile ad hoc networks.The motivation behind the introductin of this calculus is that we intend toinvestigate the impact of service oriented computing also in this class of unstructured network.The remainder of the document is organized as follows.Section2provides an overview of themain characteristics of each calculus,focusing on their basic liguistic constructs and their similari-ties/differences.In Sections3,4,5,6we present the four calculi in more detail.For each calculuswe discuss the motivation for its introduction,its basic linguistic primitives,and the expected future work and results.We have opted for an informal and more gentle presentation of the semantics by means of examples.The advantages of the examples is that they allow us to show the different styles of pro-gramming supported by the different calculi.The formal definition of the semantics can be found in the papers attached to the document.Finally,in Section7we report some conclusive remark and we discuss how we intend to assess our proposals in the second year of SENSORIA project.2Overview on the CalculiThe aim of this section is to introduce the reader to the basic characteristics of each calculus.This permits us to give a look to the differentflavours of the calculi without going into technical details,and to discuss their similarities,differences and mainly their complementarity.Indeed,service oriented computing is a vast area and,at least during thefirst year of SENSORIA,we have found inconvenient to focus our attention on only one calculus with the risk to lose some relevant aspects.Thefirst calculus is the Service Centered Calculus SCC.It is based on some of the basic concepts of the SENSORIA ontology:Functional Description,Session,and Conversation.In SCC services are described via their functional description.This description defines how the service reacts to invocations. As an example,let us consider the service double defined as follows:double⇒(x)x+xThis service receives the value x and computes its double x+x.In SCC services are invoked sending them an invocation value,that is thefirst value passed from the client to the service.For instance,a client that invokes the service double with invocation value5is denoted as follows:double⇐5Given the above definition of the service double,this client reduces to the value10.According to this simple example,services strongly recall the notion of objects in the context of object oriented computing:the client invokes the service/object passing the actual parameter5,and the service/object produces the result10that is passed back to the client.This is only the simplest pattern of interaction in the context of service oriented computing,the so-called request-response pattern.Differ-ently from object oriented computing,in service oriented computing clients and services can interact via more complex patterns activating sessions after thefirst invocation.Within a session several values can be exchanged from the service to the client and vice versa.Moreover,also other services can be involved giving rise to a multi-party conversation.SCC permits to describe sessions specifying the protocols that are performed by clients and services. For instance,a ticket service that sells either economy or business tickets can be specified as follows:1 ticket⇒(x)if(x==economy){100.(resp)if(resp==accept)confirmelse if(resp==reject)cancel}else if(x==business){200.(resp)if(resp==accept)confirmelse if(resp==reject)cancel}The ticket service receives an invocation value that could be either economy or business.After invocation,the service communicates the corresponding price(100for economy ticket,200for business). After,the client is expected to indicate whether it accepts or rejects the offer;if it sends to the service the value accept then the ticket is confirmed,if it sends reject the ticket is cancelled.1We use an if,else if construct to make the example more readable even if this operator is not part of SCC.The specification of a client that invokes the ticket service in order to buy an economy ticket only if it costs less than110is as follows:ticket{(x)(price)if(price≤110)accept else reject}⇐economyNotice that the actual invocation value economy is reported after the⇐operator.The protocol run by the client is reported inside curly brackets and it always starts with an abstraction(x)used to refer to the actual invocation value(this will be described in more details in Section3).The simpler version of invocation a⇐v without any protocol specified inside curly backets is a shorthand notation for an invocation that simply returns thefirst value issued by the service.As already anticipated above,another interesting aspect of SCC is that other services can be invoked during the execution of a session thus giving rise to a multi-party conversation.As an example,let us consider the following travelAgency:travelAgency⇒(x)if((airplane⇐x)==ok)and((hotel⇐x)==ok)confirmelse cancelThe aim of the travelAgency is to organize a travel to a location x indicated by the client.Upon invocation the airplane and the hotel services are invoked in order to reserve an airplane ticket to the location x and a room in some hotel in the location x,respectively.If both reservations succeed,the travel is confirmed otherwise it is cancelled.SCC comprises also other more specific operators that permits,for instance,to interrupt the execu-tion of one session or to cancel/update service definitions.The interested reader canfind in Section3a more detailed description of the calculus.The SCC calculus is an abstract model that can be used to reason about concepts such as services, sessions,coonversations,etc.independently of any specific service oriented technology.In order to avoid to lose the contact with current technologies,in particular Web services,we have developed also another calculus called Service Oriented Computing Kernel SOCK.The Web services technology adds on top of the traditional Internet protocol stack new XML-based protocols that support interoperability among heterogeneous components.In particular,SOAP[BEK+] is the protocol for message exchange among Web services and WSDL[W3Cc]is the standard language for the description of the service interfaces.The WSDL language essentially permits to describe the kinds of messages that a service can receive,but it is not expressive enough to describe patterns of interaction that are more complex than,for instance,the basic request-response pattern described above. One of the main challange in the Web services area is to enrich the interface description language with behavioural information that can be effectively used to check the compatibility of services,not only at the static signature level,but also from a dynamic perspective.For instance,it could be relevant to check whether the composition of services is deadlock–free or not.SCC is not adequate to be applied directly to investigate the problem of composition of services based on their interface.Indeed,it does not provide the notion of service interface as afirst-class citizen. On the contrary,the calculus SOCK directly inspired by the Web services technology,separates the behavioural interface of services from their actual execution.We describe this separation by means of an example of service described using SOCK.Consider a service BOOK SHOP that permits to buy books on the Web.To this aim it can accept buy requests that contains,besides the client identifier,the code of the book the client is interested in.After, the service replies to the client with either a cancel(if,for instance,the book is not available)or a confirm message.On confirmation,the client indicates the credit card number for the payment;the book shop subsequently sends thefinal confirmation.The interface of the BOOK SHOP service is specifiedin SOCK as follows:BOOK SHOP=buy( client,book code );cancel@client( client,book code )+(confirm@client( client,book code,cost );payment( client,book code,credit card number );book@client( client,book code ))The basic activities in SOCK are receive and invoke operations.For instance,in the example abovecancel@client( client,book code )is an invoke operation(the overline distinguishes invoke from re-ceive operations)composed of a port name(cancel),a localization of the port(client),and a tuple ofparameters.The parameters denote variables:they are used to compose the message to be sent in thecase of invoke operations,or to store the received values in the case of receive.In order to describe morecomplex operations,sequential(;)and choice(+)composition operators can be used.The above specification is intended to be non executable.This because further information mustbe added in order to indicate how the service interface is actually run by an actual service executor.The information that must be added specifies if different instances of the same service are run either inparallel or sequentially,and how the variables are managed(they can be either persistent,that is they arekept also after the execution of a service instance,or they are volatile).An actual executor of the BOOK SHOP service can be specified as followsE BOOK SHOP=!({client,quantity} BOOK SHOP×)where!(the equivalent of the bang operator of theπ-calculus)denotes that different service instancescan be run in parallel and the subscript×indicates that variables are not persistent.Another relevant information in the specification of the E BOOK SHOP is the correlation set,givenby{client,quantity}.Correlation sets are a fundamental information in case of parallel execution ofdifferent instances of the same service.In fact,when messages are received by the executor of theservice,they must be delivered to the corresponding instance.The correlation set indicates which part ofthe message is used to identify the correct instance.Summarizing,the SOCK calculus has been developed to focus on the problem of composition ofservices not only based on the abstract protocol description(as done in SCC)but on the service interfacedescription as it happens,for instance,in the context of Web services.A more detailed presentation ofSOCK can be found in Section4.The travelAgency service reported above is a typical orchestrator,that is,a process that exploitsother already available services in order to provide a new more complex service(see the glossary in theDeliverable D1.1.a for a more detailed description of the meaning of orchestrator).In the context of Webservices,new languages called orchestration languages have been developed to program orchestrators.The most prominent orchestration language is WS-BPEL[BCG+05].This language comprises linguisticconstructs that are not usually available in process calculi.In particular,mechanisms are provided thatpermit to group operations in a so-called scope.Operations in one scope can be interrupted in case anunexpected event occurs during the execution of the scope,or they can be compensated in case a failureoccurs after the completion of the scope.Due to the high relevance of orchestration in the context of service oriented computing,we haveincluded in the core calculi of SENSORIA also a Calculus for Orchestration of Web Services(called C˘o WS),which takes directly inspiration from these new linguistic constructs of WS-BPEL.C˘o WS shares some basic aspects with SOCK,such as the notion of correlations or the exploitation of receive andinvoke operations as the basic activities,but it also comprises new operators.The main novelties areoperators that permits to define scopes,to interrupt scopes,and to protect part of the operations includedin one scope that are not affected by interruptions.We describe these basic aspects of C˘o WS by means ofan example.Consider an orchestrator that,in order to buy an airplane ticket to lisbon,contacts three differentairplane companies in order to collect their offers.This can be simply achieved putting in parallel threerequests with the three corresponding receive operations:lufthansa·req! lisbon |british·req! lisbon |alitalia·req! lisbon |lufthansa·resp? l |british·resp? b |alitalia·resp? aNote that the invoke operations are denoted with!while the receive operations with?.The above orches-trator collects in the three variables l,b,and a the three offers of Lufthansa,British Airways and Alitalia, respectively.Due to possible communication failures this orchestrator is not completely satisfactory.Indeed,if one of the replies is lost(or delayed indefinitely)the overall orchestrator will not complete due to the fact that one of the receive operations blocks.In order to overcome this problem,in C˘o WS it is possible to include the orchestrator within a scope k and use the kill(k)action in order to interrupt all pending activities:[k](lufthansa·req! lisbon |british·req! lisbon |alitalia·req! lisbon | lufthansa·resp? l .kill(k)|british·resp? b .kill(k)|alitalia·resp? a .kill(k))This enhanced version of the orchestrator interrupts pending receive operations when at least one of the receive succeeds.As afinal version of orchestrator,we assume that among the three requests there exists one,for instance Lufthansa,which is more important than the other ones in the sense that it is mandatory to wait for its offer.This can be achieved in C˘o WS using the protection operator↑↑to indicate that the interactions with Lufthansa are not interruptable.The new version of the orchestrator is:[k](↑lufthansa·req! lisbon ↑|british·req! lisbon |alitalia·req! lisbon |↑lufthansa·resp? l .kill(k)↑|british·resp? b .kill(k)|alitalia·resp? a .kill(k)) Details about C˘o WS can be found in Section5.The last calculus reported in this document is the Signals Calculus SC.It has been developed in order to investigate service composition under a different paradigm of interaction.The calculi described so far consider end-to-end interactions:one process can interact with only one service at a time.This form of communication is typical of wide area networks such as the Internet.In different contexts such as wireless mobile ad hoc networks,the absence of structure implies that clients are usually unaware of the currently available services.This requires to adopt different interaction paradigms,such as publish-subscribe,according to which a process emits requests without knowing a priori who is going to capture and replies to the request.More precisely,in the publish-subscribe paradigm,messages are emitted with an associated topic,and they are delivered to all the reachable process that previously registered their interest in the topic.SC is a calculus whose aim is to investigate service oriented computing under this alternative communication paradigm.In order to appreciate the novelty of this calculus with respect to the previous ones,we revisit the above example of orchestrator that collects the requests coming from three different aiplane companies:orchestrator[ req,lisbon :airplaneComp]∗( resp,x :response→store(x))airplaneComp lufthansa,british,alitaliaNote that only one request operation is done by emitting the message req,lisbon .This message has airplaneComp as the associated topic.The services interested in this topic that will receive the mes-sage are indicated in subscript position and they are given by the three airplane companies lufthansa, british,and alitalia.On the contrary,the superscript specifies how client reacts to the received messages;namely,when it receives messages with structure resp,x and topic response,it reacts by storing the received answer x.22We do not fully specify how the answers are actually stored;we simply denote this operation with store(x).P,Q::=0Nil|a.P Concretion|(x)P Abstraction|return a.P Return Value|a⇒(x)P Service Definition|a{(x)P}⇐Q Service Invocation|r P Session|P|Q Parallel Composition|(νa)P New NameFigure1:SCC:syntax of processes.3SCC:Service Centered Calculus3.1MotivationSCC is a calculus developed around the notions of service definition,service invocation and bi-directional sessioning.SCC has been influenced by Cook and Misra’s Orc[MC06],a basic programming model for structured orchestration of services.In particular,Orc is appealing because of its simplicity and yet great generality:its three basic composition operators can be used to model the most common workflow patterns,identified by van der Aalst et al.in[vdAtKB03].SCC has novel features for programming and composing services,while taking into account their dynamic behaviour.In particular,SCC supports explicit modeling of sessions both on client-and on service-side,including protocols executed by each side during an interaction and mechanisms for session naming and scoping,the latter inspired by theπ-calculus[MPW92].Sessions allow us to describe and reason about interaction modalities more structured than the simple one-way and request-response modalities provided by Orc and typical of a producer/consumer pattern.Moreover,in SCC sessions can be closed thus providing a mechanism for process interruption and service cancellation and update which has no counterpart in most process calculi.Summarising,SCC combines the service orientedflavour of Orc with the name passing communi-cation mechanism of theπ-calculus.3.2Calculus descriptionWithin SCC,services are seen as sort of interacting functions(and even stream processing functions) that can be invoked by clients.The syntax of(the kill-free fragment of)SCC is reported in Figure1. The operational semantics is not reported for space constraints,it can be found in[BBC+06].Service definitions take the form a⇒(x)P,where a is the service name,x is a formal parameter,and P is the actual implementation of the service.For instance,succ⇒(x)x+1(here and in the following we omit trailing0)models a service that,received an integer returns its successor.Service invocations are written as a{(x)R}⇐Q:each new value v produced by the client Q will trigger a new invocation of service a;for each invocation,an instance of the process R,with x bound to the actual invocation value v,implements the client-side protocol for interacting with the new instance of a.As an example, a client for the simple service described above will be written in SCC as succ{(x)(y)return y}⇐5: after the invocation x is bound to the argument5,the client waits for a value from the server and the received value is substituted for y and hence returned as the result of the service invocation.A service invocation causes activation of a new session.A pair of dual fresh names,r and r,identifies the two sides of the session.Client and service protocols are instantiated each at the proper side of thesession.For instance,interaction of the client and of the service described above triggers the session(νr)(r 5+1|r (y)return y)(in this case,the client side makes no use of the formal parameter).The value6is computed on the service-side and then received at the client side,that reducesfirst to r return6and then to6|r 0 (where0denotes the nil process).More generally,within sessions communication is bi-directional,in the sense that the interacting protocols can exchange data in both directions.Values returned outside the session to the enclosing environment can be used to invoke other services.For instance,a client that invokes the service succ and then prints the obtained result follows:print{(z)0}⇐(succ{(x)(y)return y}⇐5).(in this case,the service print is invoked with vacuous protocol(z)0).Example1(Service orchestration)As a more significant example than those reported above,we present a simple orchestrator written in SCC whose aim is to invoke two services,collect the produced results, and then invoke a third service with those results.Assume that there are the following available services:service emailMe that expects a value and then sends it to your email address;services BBC and CNN that produce the latest news.Then the processemailMe{(−)0}⇐(BBC{(x)(y)return y}⇐•|CNN{(x)(y)return y}⇐•)will send you an email for each news item collected from either BBC or CNN.Note that we use the names•and−to denote an unused name and a binder for an unused name,respectively.The full SCC comprises also mechanisms for session interruption.The full syntax is not reported here for space constraints,but can be found in[BBC+06].Nevertheless we describe informally how the interruption mechanism can be used.A protocol,both on client-side and on service-side,can be interrupted(e.g.due to the occurrence of an unexpected event),and interruption can be notified to the environment.More generally,the keyword close can be used to terminate a protocol on one side and to notify the termination to a suitable handler at the partner site.For example,the above client is extended below for exploiting a suitable service fault that can handle printer failures:print{(z)0}⇐fault(succ{(x)(y)return y}⇐5)|fault⇒(code)ErrorHandling. where ErrorHandling is a protocol able to manage printer errors according to their identifier code.Suppose that P is the printer protocol and that the keyword close occurs in P.When invoked by the above client,a service-side session of the form r fault P[fault/close]is created,where fault is substituted for close.In case of printer failure the protocol P should invoke the service close(in-stantiated to fault),with an error code err as a parameter.As effect of this invocation,the whole service-side session r is destroyed.The invocation will instantiate an error recovery session that exe-cutes ErrorHandling[err/code].Example2(Service update)Session closing can be used also for service update.Consider,for in-stance,the servicesoccerWorldChampion⇒(−)brasilthat returns the name of the last winner of the soccer world championship.The service must be updated as soon as a new team becomes the new world champion.In the kill-free fragment of SCC reported in Figure1there is no way to cancel a definition and replace it with a new one.By contrast,in the full。
