BHDTP Hi_Tee_George_1.8.03
Allen_et_al-2011-New_Directions_for_Teaching_and_Learning

N EW D IRECTIONS FOR T EACHING AND L EARNING , no. 128, Winter 2011 © Wiley Periodicals, Inc.Published online in Wiley Online Library (wileyonlinelibrary .com) • DOI: 10.1002/tl.4653Problem-Based LearningDeborah E. Allen, Richard S. Donham, Stephen A. BernhardtProblem-based learning (PBL) has wide currency on many college and uni-versity campuses, including our own, the University of Delaware. Although we would like to be able to claim clear evidence for PBL in terms of student learning outcomes, based on our review of the literature, we cannot state that research strongly favors a PBL approach, at least not if the primary evidence is subject matter learning.There is some evidence of PBL effectiveness in medical school settings where it began, and there are numerous accounts of PBL implementation in various undergraduate contexts, replete with persuasively positive data from course evaluations (Duch, Groh, and Allen, 2001). However, evidence for learning outcomes is still needed. In this chapter, we review the origins of PBL, outline its characteristic methods, and suggest why we believe PBL has a persistent and growing infl uence among educators.Origins of PBL in Medical SchoolsPBL was formalized by medical educators in the 1950s and 1960s to address the exponential expansion of medical knowledge while better aligning traditional classroom problem-solving approaches with those used in clinical practice (Barrows and Tamblyn, 1980; Boud, 1985). Traditional approaches were based on the bucket theory (Wood, 1994): If medical stu-dents were fi lled with the requisite foundational knowledge, they would be able to strategically retrieve and direct just the right subsets of it toward problems of clinical practice. PBL was designed to address the underlying fl aws of the bucket theory , especially leaky , overfl owing, or inappropriately 21In problem-based learning, students working in collaborative groupslearn by resolving complex, realistic problems under the guidance of faculty. In this chapter , we examine the evidence for effectiveness ofthe method to achieve its goals of fostering deep understandingsof content and discuss the potential for developing process skills:research, negotiation and teamwork, writing, and verbalcommunication.22E VIDENCE-B ASED T EACHINGfi lled buckets. By presenting complex case histories typical of real patients as the pretext for learning, PBL demanded that students call on an inte-grated, multidisciplinary knowledge base (Wood, 1994).In the idealized learning cycle of medical school PBL (Engle, 1999), students working in teams learn by solving real or realistic problems. Stu-dents grapple with a multistage, complex medical case history, which offers an engaging and memorable context for learning. As they defi ne the prob-lem’s scope and boundaries, student teams identify and organize relevant ideas and prior knowledge. The teams form questions based on self- identifi ed gaps in their knowledge, and they use these questions to guide subsequent independent research outside the classroom, with research tasks parceled out among team members. When the students reconvene, they present and discuss their fi ndings, integrating their new knowledge and skills into the problem context. As they move through the stages of a complex problem, they continue to defi ne new areas of needed learning in pursuit of a solution. In the case of this original PBL model, a solution is an accurate diagnosis and recommendation of successful treatment of the patient.PBL continues to be a favored method in many medical schools. What became evident in effectiveness studies was that there was no simple answer to the question “Is PBL better than traditional methods?” Several meta-analyses of the data suggested that PBL has modest or no benefi cial effect on student learning of content (from the United States Medical Licensing Examination [USMLE] Step 1—basic science understanding; Albanese and Mitchell, 1993; Nandi and others, 2000; Vernon and Blake, 1993). In fact, it appears that students in a traditional medical program sometimes, but not consistently, slightly outperform their PBL counterparts.However, disaggregation of the data suggests an underlying richness that is not captured simply by looking at student achievement on content recall exams. If, for example, scores on the USMLE Step 2 (knowledge of clinical practice) or ability to apply knowledge in the clinic after graduation are considered, medical school students with PBL experience frequently outperform their traditional counterparts (Albanese and Mitchell, 1993; Dochy, Segers, Van den Bossche, and Gijbels, 2003; Koh, Khoo, Wong, and Koh, 2008; Vernon and Blake, 1993). Recent meta-analyses have begun to tease apart some of the relative merits of PBL and suggest that the most positive effects are seen with student understanding of the organizing prin-ciples that link concepts in the knowledge domain being studied (Gijbels, Dochy, Van den Bossche, and Segers, 2005). Dochy and others (2003) reported a robust positive effect from PBL on the skills of students, noting that, intriguingly, students in PBL remember more acquired knowledge compared with their traditional counterparts. The early meta-analyses of PBL outcomes in the medical school setting (Albanese and Mitchell, 1993; V ernon and Blake, 1993) also document positive student attitudes about N EW D IRECTIONS FOR T EACHING AND L EARNING • DOI: 10.1002/tlP ROBLEM-B ASED L EARNING 23 learning, with students frequently viewing PBL as both a challenging and a motivating approach.Strategies for PBL ImplementationBecause PBL explicitly addresses some of the shortcomings of science edu-cation, it migrated into undergraduate science and engineering classrooms (Woods, 1985). It then expanded into basic as well as applied fi elds as well as into the humanities and social sciences (Duch and others, 2001). With the introduction of PBL to undergraduate courses, teachers modifi ed the method to accommodate larger class sizes, greater student diversity, timing and scheduling issues, multiple classroom groups, and lack of suitable classroom space (Allen, Duch, and Groh, 1996).PBL requires a shift in the educational paradigm for faculty. In PBL, the role of the instructor shifts from presenter of information to facilitator of a problem-solving process. Although the PBL process calls on students to become self-directed learners, faculty facilitators guide them by monitoring discussion and intervening when appropriate, asking questions that probe accuracy, relevance, and depth of information and analyses; raising new (or neglected) issues for consideration; and fostering full and even participa-tion (Mayo, Donnelly, and Schwartz, 1995).Instead of lecturing, PBL instructors must fi nd or create good prob-lems based on clear learning goals. Through these problems, instructors lead students to learn key concepts, facts, and processes related to core course content. PBL problems must be carefully constructed—not only to present students with issues and dilemmas that matter to them but also to foster their development of conceptual frameworks (Hung, Jonassen, and Liu, 2007). PBL problems may intentionally pose cognitive challenges by not providing all the information needed, thereby motivating a self-directed search for explanations. Instructors often allow students considerable lati-tude to make false starts and wrong turns. Well-developed, peer-reviewed problems can be found at the PBL Clearinghouse (University of Delaware, 2010).Successful implementation of PBL is critically dependent on the instructor’s scaffolding of students’ active learning and knowledge con-struction (Amador, Miles, and Peters, 2006; Duch and others, 2001). For example, PBL instructors can plan for intervals of class discussion or mini-lectures to help students navigate conceptual impasses, to dig more deeply into certain topics, or to fi nd useful resources. Instructors can enter team discussions to listen and pose questions (Hmelo-Silver, Duncan, and Chinn, 2007). They can also use student facilitators to extend their instruc-tional reach.Importantly, PBL can support the development of a range of “soft” skills: research skills, negotiation and teamwork, reading, writing, and oral communication. Cooperative learning strategies that foster effectiveN EW D IRECTIONS FOR T EACHING AND L EARNING • DOI: 10.1002/tl24 E VIDENCE -B ASED T EACHINGN EW D IRECTIONS FOR T EACHING AND L EARNING • DOI: 10.1002/tlteamwork become critical, as does the need for everyone to work to keep team members engaged and on track (Johnson, Johnson, and Smith, 1998). PBL classrooms are particularly well suited to the development of writing abilities. PBL instructors tend to rely on authentic assessment, with most problems leading up to a demonstration or presentation of learning, often taking the form of a written product: a solution, a recommendation, a sum-mary of what was learned, or some other form of group or individual reporting. To encourage development of writing skills, thinking skills, and learning in general, instructors can call for students to produce specifi c genres of writing: progress reports, schedules, task lists, meeting minutes, abstracts, literature reviews, proofs, lab reports, data analyses, and technical briefi ngs (Klein, 1999). Alaimo, Bean, Langenhan, and Nichols (2009) showed how to integrate writing as a core activity in an inquiry-based chemistry course, demonstrating strong learning outcomes in the process.Instructors must also encourage good team communication strategies. Teams must avoid reaching premature closure or succumbing to group-think—where a group seizes on a path because a team member is forceful or persuasive. The teams that perform best are those that generate and sus-tain consideration of multiple alternatives, engaging in and sustaining “substantive confl ict” (Burnett, 1991).Effectiveness of PBL on Content Learning in Undergraduate SettingsConfusion and lack of specifi cation about what PBL is as it is actually prac-ticed in the classroom hampers analysis of the effect of PBL on the acquisi-tion of content learning. In particular, PBL adopters in undergraduate settings, grappling with the diffi culties of monitoring multiple classroom groups, hybridize the method in various ways to incorporate aspects of discussion and case study method teaching (Silverman and Welty , 1990). Instructors tend to insert highly choreographed segments of instructor-centered, whole-class discussions into the PBL cycle and to interpose PBL problems intermittently throughout the course schedule, blended with more traditional instruction (Duch and others, 2001). As Newman (2003) noted, this hybridization of PBL makes it “diffi cult to distinguish between different types of PBL and even to distinguish between PBL and other edu-cational interventions” (p. 7).Nevertheless, there are scattered reports of positive outcomes. In a study of over 6,500 students, Hake (1998) found that interactive engage-ment methods (broadly defined as heads-on, hands-on activities with immediate feedback) were strongly superior to lecture-centered instruction in improving performance on valid and reliable mechanics tests used to assess students’ understanding of physics. Williams (2001) reported gains in the Force Concept Inventory for students in a PBL course that are con-sistent with the averages in other introductory physics courses that useP ROBLEM-B ASED L EARNING 25 interactive engagement methods. Palaez (2002) observed that students in a PBL biology course with an intensive writing component outperformed students in a course using traditional lecture-based instruction on exams that assessed conceptual understandings.Although there is less research on undergraduate learning than in medical education, the data support the broad conclusion that PBL may show only modest benefi ts on recalled content knowledge, but it positively infl uences integration of new knowledge with existing knowledge. How-ever, faculty members frequently adopt PBL to help students develop life-long learning skills. These skills are exercised routinely in the natural course of the PBL learning cycle. Given these additional but divergent stu-dent learning goals, many faculty members are satisfi ed with student con-tent learning that is similar or not signifi cantly decreased when using PBL. At the very least, these fi ndings assuage any residual concerns they or oth-ers may have that spending time on these ambitious process objectives undermines the learning of essential course content.Effectiveness of PBL on Process SkillsBecause PBL engages students in a range of soft skills, perhaps other posi-tive learning outcomes can be claimed for the method. A case in point is the benefi t of using cooperative learning groups on such general aspects of academic success as retention as well as on fostering positive student atti-tudes about learning (Springer, Stanne, and Donovan, 1999). Another is the use of writing-to-learn strategies in PBL. Incorporation of short, in-class writing assignments improves student performance on traditional concept and content-based exams (Butler, Phillmann, and Smart, 2001; Davidson and Pearce, 1990; Drabick, Weisberg, Paul, and Bubier, 2007; Stewart, Myers, and Culley, 2010).There is some evidence that systemic and sustained use of PBL in the classroom fosters cognitive growth. Downing and others (2009) followed two parallel cohorts of students in degree programs, one taught with PBL, the other by traditional methods, and found greater gains in metacognitive skills in the PBL group. Tiwari, Lai, So, and Yurn (2006) similarly reported signifi cant differences in the development of undergraduate nursing stu-dents’ critical thinking dispositions in a PBL versus a lecture-based course, as determined by comparisons of pre- and posttest scores on the California Critical Thinking Disposition Inventory.Effectiveness of PBL on Student EngagementWidespread agreement is emerging that at the core of effective teaching are activities that engage students by challenging them academically and involving them intensely, within supportive environments that provide multiple opportunities for interactions with faculty, peers, and members ofN EW D IRECTIONS FOR T EACHING AND L EARNING • DOI: 10.1002/tl26E VIDENCE-B ASED T EACHINGthe surrounding community (Smith, Sheppard, Johnson, and Johnson, 2005). Because PBL uses an assortment of methods associated with student engagement—active, collaborative, student-centered, and self-directed learning focused on realistic problems and authentic assessments—we might expect that it would lead to increased student engagement. By requiring students to talk to each other and collaborate on projects impor-tant to their academic success, PBL addresses student alienation and failure to form social networks, major reasons for students dropping out of college (Tinto, 1994). Two systematic analyses of students’ perceptions of the immediate and longer-term value and transferability of the reasoning and processing skills they developed during PBL courses (using the National Study of Student Engagement survey [NSSE] or a similarly designed instru-ment) in fact provide support for characterization of PBL as a pedagogy of engagement (Ahlfeldt, Mehta, and Sellnow, 2005; Murray and Summerlee, 2007).An important aspect of engagement is students’ ability to practice self-regulated or lifelong learning behaviors (Smith et al., 2005): the ability to defi ne what to learn and to effectively use the time and resource manage-ment needed to learn it. Blumberg’s (2000) review of the literature described numerous instances of documented gains in these areas that can be attributed to students’ PBL experiences.Incorporating writing tasks into PBL problems also shows promise for enhancing student engagement. Butler and others (2001) found that short, in-class microthemes increased positive motivation to attend class and increased student engagement. Additionally, Light (2001) found that writ-ing increases the time students spend on a course, increases the extent to which they are intellectually challenged, and increases their level of inter-est. Confi rming Light’s fi ndings are the very compelling data emerging from the NSSE (Gonyea, Anderson, Anson, and Paine, 2010). NSSE personnel worked with writing faculty to develop a special set of add-on questions concerning writing to the spring 2009 administration of NSSE. The data strongly supported writing as the single most important determinant of engaged, deep learning. When the independent variable is assigning mean-ing-constructing writing tasks, the NSSE data show moderate to strong effects on increased higher-order thinking, integrative learning, and refl ec-tive learning.ConclusionsThere is broad support for the conclusion that PBL methods enhance the affective domain of student learning, improve student performance on complex tasks, and foster better retention of knowledge. We would argue that more research is needed, research that is sensitive to the range of out-comes that we have discussed. For example, we would like to see addi-tional research into the effects of PBL on student performance on state N EW D IRECTIONS FOR T EACHING AND L EARNING • DOI: 10.1002/tlP ROBLEM-B ASED L EARNING 27N EW D IRECTIONS FOR T EACHING AND L EARNING • DOI: 10.1002/tlboard examinations and on students’ gains in problem-solving, critical thinking, motivation, and self-regulated learning. Another important area of future research would identify the particular PBL implementation meth-ods that lead to improved outcomes.PBL continues to enjoy popularity among a wide range of instructors across numerous disciplines at many institutions. Because PBL changes the nature of teaching and learning, many instructors embrace the method without clear, confi rming evidence of its effectiveness. In essence, they like being freed to work within a different classroom model, one where students are active and in control of learning. They like their role as consultant or facilitator better than their previous role of lecturer. The PBL classroom is, after all, a place that is lively with controversy , debate, and peer-to-peer communication—providing both faculty and students with immediate and unmistakable evidence of their competencies and understandings of and about what matters.ReferencesAhlfeldt, S., Mehta, S., and Sellnow, T. “Measurement and Analysis of Student Engagement in University Classes where Varying Levels of PBL Methods of Instruction Are in Use.” Higher Education Research and Development, 2005, 24, 5–20.Alaimo, P . J., Bean, J. C., Langenhan, J. M., and Nichols, L. “Eliminating Lab Reports: A Rhetorical Approach for Teaching the Scientific Paper in Sophomore Organic Chemistry .” WAC Journal, 2009, 20, 17–32.Albanese, M. S., and Mitchell, S. “Problem-Based Learning: A Review of Literature on Its Outcomes and Implementation Issues.” Academic Medicine, 1993, 68, 52–81.Allen, D. E., Duch, B. J., and Groh, S. E. “The Power of Problem-Based Learning in T eaching Introductory Science Courses.” In L. Wilkerson and W . H. Gijselaers (eds.), Bringing Problem-Based Learning to Higher Education: Theory and Practice . New Directions for T eaching and Learning Series, no. 68. San Francisco: Jossey-Bass, 1996.Amador, J. A., Miles, L., and Peters, C. B. The Practice of Problem-Based Learning: A Guide to Implementing PBL in the College Classroom. Bolton, Mass.: Anker, 2006.Barrows, H., and Tamblyn, R. Problem-based Learning: An Approach to Medical Education. New York: Springer, 1980. Blumberg, P . “Evaluating the Evidence that Problem-Based Learners Are Self-Directed Learners: Review of the Literature.” In D. H. Evensen and C. E. Hmelo (eds.), Problem-Based Learning: A Research Perspective on Learning Interactions (pp. 199–222). Mahwah, N.J.: Lawrence Erlbaum, 2000.Boud, D. J. “Problem-Based Learning in Perspective. In D. Boud (ed.), Problem-Based Learning in Education for the Professions (pp. 13–18). Sydney , Australia: HERDSA, 1985.Burnett, R. E. “Substantive Confl ict in a Cooperative Context: A Way to Improve the Collaborative Planning of Workplace Documents.” Technical Communication, 1991, 38, 532–539.Butler, A., Phillmann, K.-B., and Smart, L. “Active Learning within a Lecture: Assessing the Impact of Short, In-Class Writing Exercises.” Teaching of Psychology, 2001, 28, 57–59.Davidson, D., and Pearce, D. “Perspectives on Writing Activities in the Mathematics Classroom.” Mathematics Education Research Journal, 1990, 2, 15–22.28 E VIDENCE -B ASED T EACHINGN EW D IRECTIONS FOR T EACHING AND L EARNING • DOI: 10.1002/tlDochy , F ., Segers, M., Van den Bossche, P ., and Gijbels, D. “Effects of Problem-Based Learning: A Meta-Analysis.” Learning and Instruction, 2003, 13, 533–568.Downing, K., and others. “Problem-Based Learning and the Development of Metacognition.” Higher Education, 2009, 57, 609–621,Drabick, D.A.G., Weisberg, R., Paul, L., and Bubier, J. L. “Keeping It Short and Sweet: Brief, Ungraded Writing Assignments Facilitate Learning.” Teaching of Psychology, 2007, 34, 172–176. Duch, B., Groh, S. E., and Allen, D. E. (eds.). The Power of Problem-Based Learning: A Practical “How-to” for T eaching Undergraduate Courses in Any Discipline. Sterling, Va.: Stylus, 2001.Engle, C. E. “Not Just a Method but a Way of Learning.” In D. Boud and G. Feletti (eds.), The Challenge of Problem-Based Learning (pp. 17–27). London: Kogan Page, 1999.Gijbels, D., Dochy , F ., Van den Bossche, P ., and Segers, M. “Effects of Problem-Based Learning: A Meta-Analysis from the Angle of Assessment.” Review of Educational Research, 2005, 75, 27–61.Gonyea, R., Anderson, P ., Anson, C., and Paine, C. “Powering Up Your WAC Program: Practical, Productive Ways to Use Assessment Data from NSSE’s Consortium for the Study of Writing in College.” Paper presented at the 10th International Writing across the Curriculum Conference, Bloomington, Indiana, May 2010.Hake, R. “Interactive Engagement versus Traditional Methods: A Six Thousand-Student Survey of Mechanics Test Data for Introductory Physics Courses.” American Journal of Physics, 1998, 66, 64–74.Hmelo-Silver, C. E., Duncan, R. G., and Chinn, C. A. “Scaffolding and Achievement in Problem-based and Inquiry Learning: A Response to Kirschner, Sweller, and Clark (2006).” Educational Psychologist, 2007, 42, 99–107.Hung, W ., Jonassen, D. H., and Liu, R. “Problem-based Learning.” In J. M. Spector, J. van Merrienboer, M. D. Merrill, and M. P . Driscoll (eds.), Handbook of Research for Educational Communications and T echnology (pp. 485–505). Mahwah, N.J.: Lawrence Erlbaum, 2007.Johnson, D. W ., Johnson, R. T., and Smith, K. A. “Cooperative Learning Returns to College: What Evidence Is There that It Works?” Change , July-Aug. 1998, 27–35.Klein, P . D. “Reopening Inquiry into Cognitive Processes in Writing-to-Learn.” Educational Psychology Review , 1999, 11, 203–270.Koh, G.C.-H., Khoo, H. E., Wong, M. L., and Koh, D. “The Effects of Problem-Based Learning During Medical School on Physician Competency: A Systematic Review.” Canadian Medical Association Journal, 2008, 178, 34–41.Light, R. J. Making the Most of College . Cambridge, Mass.: Harvard University Press, 2001. Mayo, W . P ., Donnelly , M. B., and Schwartz, R. W . “Characteristics of the Ideal Problem-Based Learning T utor in Clinical Medicine.” Evaluation and the Health Professions, 1995, 18, 124–136.Murray, J., and Summerlee, A. “The Impact of Problem-based Learning in an Interdisciplinary First-Year Program on Student Learning Behaviour.” Canadian Journal of Higher Education, 2007, 37, 87–107.Nandi, P . L., and others. “Undergraduate Medical Education: Comparison of Problem-Based Learning and Conventional Teaching.” Hong Kong Medical Journal, 2000, 6, 301–306.Newman, M. “A Pilot Systematic Review and Meta-Analysis on the Effectiveness of Problem Based Learning.” On Behalf of Campbell Collaboration Systemic Review Group on the Effectiveness of Problem-based Learning. Newcastle upon T yne, U.K.: University of Newcastle upon Tyne, 2003. /static/uploads/resources /pbl_report.pdfP ROBLEM-B ASED L EARNING 29N EW D IRECTIONS FOR T EACHING AND L EARNING • DOI: 10.1002/tl Pelaez, N. J. “Problem-Based Writing with Peer Review Improves Academic Performance in Physiology .” Advances in Physiology Education, 2002, 26(3), 174–184.Silverman, R., and Welty , W . H. “Teaching with Cases.” Journal on Excellence in College T eaching, 1990, 1, 88–97.Smith, K. A., Sheppard, S. D., Johnson, D. W ., and Johnson, R. T. “Pedagogies of Engagement: Classroom-Based Practices.” Journal of Engineering Education, 2005, 94, 1–15.Springer, L., Stanne, M. E., and Donovan, S. S. “Measuring the Success of Small-Group Learning on Undergraduates in Science, Mathematics, Engineering and Technology: A Meta-Analysis.” Review of Educational Research, 1999, 69, 21–51.Stewart, T. L., Myers, A. C., and Culley , M. R. “Enhanced Learning and Retention Through ‘Writing to Learn’ in the Psychology Classroom.” Teaching of Psychology, 2010, 37, 46–49.Tinto, V . Leaving College: Rethinking the Causes and Cures of Student Attrition (2nd ed.). Chicago: University of Chicago Press, 1994.Tiwari, A., Lai, P ., So, M., and Yurn, K. “A Comparison of the Effects of Problem-based Learning and Lecturing on the Development of Students’ Critical Thinking.” Medical Education, 2006, 40, 547–554.University of Delaware. PBL Clearinghouse, 2010. https:///Pbl/Vernon, D.T.A., and Blake, R. L. “Does Problem-Based Learning Work? A Meta-Analysis of Evaluative Research.” Academic Medicine, 1993, 68, 550–563.Williams, B. A. “Introductory Physics: A Problem-Based Model.” In B. J. Duch, S. E. Groh, and D. E. Allen (eds.), The Power of Problem-Based Learning (pp. 251–269). Sterling, Va.: Stylus, 2001.Wood, E. J. “The Problems of Problem-Based Learning.” Biochemical Education, 1994, 22, 78–82.Woods, D. “Problem-Based Learning and Problem-Solving. In D. Boud (ed.), Problem-Based Learning for the Professions (pp. 19–42). Sydney , Australia: Higher Education Research and and Development Society of Australasia, 1985.D EBORAH E. A LLEN is an associate professor of biological sciences at the University of Delaware.R ICHARD S. D ONHAM is senior science education associate at the Mathematics and Science Education Resource Center at the University of Delaware.S TEPHEN A. B ERNHARDT is the Andrew B. Kirkpatrick Jr . chair in writing and professor of English at the University of Delaware.。
byd battery-box 2.0 系统集成商手册说明书
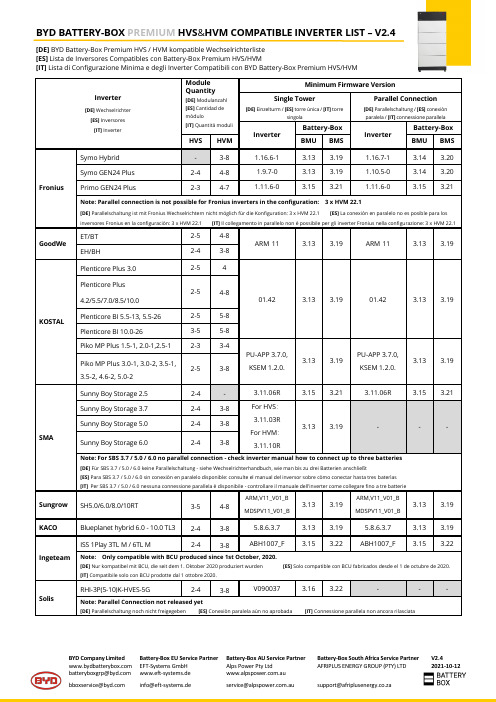
BYD Company Limited Battery-Box EU Service Partner Battery-Box AU Service Partner Battery-Box South Africa Service Partner EFT-Systems GmbH Alps Power Pty Ltd AFRIPLUS ENERGY GROUP (PTY) LTD www.eft-systems.de .au V2.4 2021-10-12Inverter [DE] Wechselrichter [ES] Inversores[IT] Inverter ModuleQuantity[DE] Modulanzahl[ES] Cantidad demódulo[IT] Quantità moduliMinimum Firmware VersionSingle Tower[DE] Einzelturm / [ES] torre única / [IT] torresingolaParallel Connection[DE] Parallelschaltung / [ES] conexiónparalela / [IT] connessione parallelaInverterBattery-BoxInverterBattery-Box HVS HVM BMU BMS BMU BMSFronius Symo Hybrid - 3-8 1.16.6-1 3.13 3.19 1.16.7-1 3.14 3.20 Symo GEN24 Plus 2-4 4-8 1.9.7-0 3.13 3.19 1.10.5-0 3.14 3.20 Primo GEN24 Plus 2-3 4-7 1.11.6-0 3.15 3.21 1.11.6-0 3.15 3.21 Note: Parallel connection is not possible for Fronius inverters in the configuration: 3 x HVM 22.1[DE] Parallelschaltung ist mit Fronius Wechselrichtern nicht möglich für die Konfiguration: 3 x HVM 22.1 [ES] La conexión en paralelo no es posible para los inversores Fronius en la configuración: 3 x HVM 22.1 [IT] Il collegamento in parallelo non è possibile per gli inverter Fronius nella configurazione: 3 x HVM 22.1GoodWe ET/BT 2-5 4-8ARM 11 3.13 3.19 ARM 11 3.13 3.19 EH/BH 2-4 3-8KOSTAL Plenticore Plus 3.0 2-5 401.42 3.13 3.19 01.42 3.13 3.19 Plenticore Plus4.2/5.5/7.0/8.5/10.02-5 4-8Plenticore BI 5.5-13, 5.5-26 2-5 5-8Plenticore BI 10.0-26 3-5 5-8Piko MP Plus 1.5-1, 2.0-1,2.5-1 2-3 3-4PU-APP 3.7.0,KSEM 1.2.0.3.13 3.19PU-APP 3.7.0,KSEM 1.2.0.3.13 3.19 Piko MP Plus 3.0-1, 3.0-2, 3.5-1,3.5-2,4.6-2,5.0-22-5 3-8SMA Sunny Boy Storage 2.5 2-4 - 3.11.06R 3.15 3.21 3.11.06R 3.15 3.21Sunny Boy Storage 3.7 2-4 3-8 For HVS:3.11.03RFor HVM:3.11.10R3.13 3.19 - - - Sunny Boy Storage 5.0 2-4 3-8Sunny Boy Storage 6.0 2-4 3-8Note: For SBS 3.7 / 5.0 / 6.0 no parallel connection - check inverter manual how to connect up to three batteries[DE] Für SBS 3.7 / 5.0 / 6.0 keine Parallelschaltung - siehe Wechselrichterhandbuch, wie man bis zu drei Batterien anschließt[ES] Para SBS 3.7 / 5.0 / 6.0 sin conexión en paralelo disponible: consulte el manual del inversor sobre cómo conectar hasta tres baterías[IT]Per SBS 3.7 / 5.0 / 6.0 nessuna connessione parallela è disponibile - controllare il manuale dell'inverter come collegare fino a tre batterieSungrow SH5.0/6.0/8.0/10RT 3-5 4-8 ARM,V11_V01_BMDSPV11_V01_B3.13 3.19ARM,V11_V01_BMDSPV11_V01_B3.13 3.19KACO Blueplanet hybrid 6.0 - 10.0 TL3 2-4 3-8 5.8.6.3.7 3.13 3.19 5.8.6.3.7 3.13 3.19Ingeteam ISS 1Play 3TL M / 6TL M 2-4 3-8 ABH1007_F 3.15 3.22 ABH1007_F 3.15 3.22 Note: Only compatible with BCU produced since 1st October, 2020.[DE] Nur kompatibel mit BCU, die seit dem 1. Oktober 2020 produziert wurden [ES] Solo compatible con BCU fabricados desde el 1 de octubre de 2020. [IT] Compatibile solo con BCU prodotte dal 1 ottobre 2020.Solis RHI-3P(5-10)K-HVES-5G 2-4 3-8 V090037 3.16 3.22 - - - Note: Parallel Connection not released yet[DE] Parallelschaltung noch nicht freigegeben [ES] Conexión paralela aún no aprobada [IT] Connessione parallela non ancora rilasciataBYD BATTERY-BOX PREMIUM HVS&HVM COMPATIBLE INVERTER LIST – V2.4 [DE] BYD Battery-Box Premium HVS / HVM kompatible Wechselrichterliste[ES] Lista de Inversores Compatibles con Battery-Box Premium HVS/HVM[IT] Lista di Configurazione Minima e degli Inverter Compatibili con BYD Battery-Box Premium HVS/HVMBYD Company Limited Battery-Box EU Service Partner Battery-Box AU Service Partner Battery-Box South Africa Service Partner EFT-Systems GmbH Alps Power Pty Ltd AFRIPLUS ENERGY GROUP (PTY) LTD*********************www.eft-systems.de .au*******************V2.4 2021-10-12Note:∙Always install the latest firmware on the Battery-Box!∙Requirements for Parallel Connection: Maximum three battery systems could be connected in parallel; HVS system CANNOT be connected in parallel with HVM system; Every tower connected in parallel requires the same module quantity;[DE] Bemerkung:∙Installieren Sie immer die neueste Firmware auf der Battery-Box!∙Anforderungen an Parallelschaltung: Es dürfen maximal drei Batteriesysteme parallel geschaltet werden; Ein HVS-System kann NICHT mit einem HVM-System kombiniert werden; Jeder parallel geschaltete Turm benötigt die gleiche Modulanzahl[ES] Nota:•¡Instale siempre el firmware más reciente en la Battery-Box!•Requisitos para la conexión en paralelo: se pueden conectar en paralelo un máximo de tres sistemas de baterías; El sistema HVS NO PUEDE conectarse en paralelo con el sistema HVM; Cada torre conectada en paralelo requiere la misma cantidad de módulos por torre;[IT] Nota:•Installare sempre l'ultimo firmware sul Battery-Box!•Requisiti per il collegamento in parallelo: è possibile collegare in parallelo un massimo di tre sistemi di batterie; Il sistema HVS NON può essere collegato in parallelo al sistema HVM; Ogni torre collegata in parallelo richiede la stessa quantità di moduli per torri; The Information in this document is subject to change without notice. Please take the latest version of this document at our websites into account.[DE] Die Informationen in diesem Dokument können ohne vorherige Ankündigung geändert werden. Bitte berücksichtigen Sie die neueste Version dieses Dokuments auf unseren Websites.[ES] La información de este documento está sujeta a cambios sin previo aviso. Tenga en cuenta la última versión de este documento en nuestros sitios web.[IT]Le informazioni contenute in questo documento sono soggette a modifiche senza preavviso. Si prega di prendere in considerazione l'ultima versione di questo documento sui nostri siti web.。
优质课件 牛津译林版选择性必修二Unit 2 复习

6. Why does the woman want to buy a computer?
A. To help her with her lessons.
B. To help her to write a book.
C. To look up information from the Internet.
W:I’m sorry, but I’m not going to office today. You might ask Linda. She’s leaving
aro1u.nWdhhaatlfdopeassttheeigwhto.man mean? W:hloe’oskalvreeraydytirveisdit. ed the museum. MW::YHBe.asTv.hIeesnt’maytaenydocuuopufilvndeipsrhyroelbadateibt?llyasgtonwigithht,Lrinewdar.iting my paper. M:NC.oLtinydeat. wI dillotna’kethkinmotwo wthheeonf.fice. Mflig:I2Ath..toWHsn.ehlyaisttaqckuaeintseytocwouonlefhiadoreunnrats.btoougteBtth. HetoemNiasenvw?erYyosrlko,wb.ut you’ll have a Cs.ixH-heoisurraltahyeorvteirrebde.tween W:O3.hH,tohwatm’asngyohoodu.rIsdwoinll’thtemwionmd ahnavbiengintNhewtimYoerkin? New York. I still have a few things to
ARIES ARIES-P -Ver.04- 8 0 2 7 9 0 8 1 1 3 7 4 0 产

ISTRUZIONI D'USO E DI INSTALLAZIONE INSTALLATION AND USER'S MANUALINSTRUCTIONS D'UTILISATION ET D'INSTALLATION INSTALLATIONS-UND GEBRAUCHSANLEITUNG INSTRUCCIONES DE USO Y DE INSTALACION INSTRUÇÕES DE USO E DE INSTALAÇÃOCENTRALINA DI COMANDO D811184A ver. 04 08-02-02I CONTROL UNIT GB UNITÉ DE COMMANDE F STEUERZENTRALE D CENTRAL DE MANDO E CENTRAL DO MANDOP ARIES - ARIES P8027908113740a“WARNINGS” leaflet and an “INSTRUCTION MANUAL”.These should both be read carefully as they provide important information about safety, installation, operation and maintenance. This product complies with the recognised technical standards and safety regulations. We declare that this product is in conformity with the following European Directives: 89/336/EEC and 73/23/EEC (and subsequent amendments).1) GENERAL OUTLINEThe ARIES control unit has been designed for swing gates. It can be used for one or two gate controllers.The control unit mod. ARIES P can also be used to perform opening of a single actuator while keeping the other one closed (pedestrian access).2) FUNCTIONSSTOP: In all cases: it stops the gate until a new start command is given.PHOT:Functions can be set with Dip-Switch.Activated during closing.Activated during opening and closing.Rapid closingON: When the position of the gate photocells is exceeded, during both opening and closing, the gate automatically starts to close even if TCA is activated. We recommend setting DIP3 to ON (photocells only activated during closing).Blocks impulsesON: During opening, START commands are not accepted.OFF: During opening, START commands are accepted.PhotocellsON: Photocells only activated during closing.OFF: Photocells activated during opening and closing.Automatic closing time (TCA)ON: Automatic closing activated (can be adjusted from 0 to 90s)Preallarm (mod. ARIES P only)ON: The flashing light turns on abt 3 seconds before the motors start.FOR THE INSTALLER: check the boxes you are interested in.START:four-step logic Gate closedGate openDuring openingDuring closingAfter stop START: two-step logic SCA: Gate open indicating lightit opens it opensit stops and activates TCAit closesit stops and does not activate TCAit starts opening it stops and activats TCA (if activated)it closesit opensit opensoffononflashingATTENTION:Dip non used in mod. ARIES (always in OFF set).3) MAINTENANCE AND DEMOLITIONThe maintenance of the system should only be carried out by qualified personnel regularly. The materials making up the set and its packing must be disposed of according to the regulations in force.Batteries must be properly disposed of.WARNINGSCorrect controller operation is only ensured when the data contained in the present manual are observed. The company is not to be held responsible for any damage resulting from failure to observe the installation standards and the instructions contained in the present manual.The descriptions and illustrations contained in the present manual are not binding. The Company reserves the right to make any alterations deemed appropriate for the technical, manufacturing and commercial improvement of the product, while leaving the essential product features unchanged, at any time and without undertaking to update the present publication.D 811184A _04Thank you for buying this product, our company is sure that you will be more than satisfied with the product ’s performance. The product is supplied with a “WARNINGS ” leaflet and an “INSTRUCTION MANUAL ”.These should both be read carefully as they provide important information about safety, installation, operation and maintenance.This product complies with the recognised technical standards and safety regulations. We declare that this product is in conformity with the following European Directives: 89/336/EEC and 73/23/EEC (and subsequent amendments).1) GENERAL OUTLINEThe ARIES control unit has been designed for swing gates. It can be used for one or two gate controllers.The control unit mod. ARIES P can also be used to perform opening of a single actuator while keeping the other one closed (pedestrian access).2) GENERAL SAFETYWARNING! An incorrect installation or improper use of the product can cause damage to persons, animals or things.•The “Warnings ” leaflet and “Instruction booklet ” supplied with this product should be read carefully as they provide important information about safety, installation, use and maintenance.•Scrap packing materials (plastic, cardboard, polystyrene etc) according to the provisions set out by current standards. Keep nylon or polystyrene bags out of children ’s reach.•Keep the instructions together with the technical brochure for future reference.•This product was exclusively designed and manufactured for the use specified in the present documentation. Any other use not specified in this documentation could damage the product and be dangerous.•The Company declines all responsibility for any consequences resulting from improper use of the product, or use which is different from that expected and specified in the present documentation.•Do not install the product in explosive atmosphere.•The Company declines all responsibility for any consequences resulting from failure to observe Good Technical Practice when constructing closing structures (door, gates etc.), as well as from any deformation which might occur during use.•The installation must comply with the provisions set out by the following European Directives: 89/336/EEC, 73/23/EEC, 98/37/ECC and subsequent amendments.•Disconnect the electrical power supply before carrying out any work on the installation. Also disconnect any buffer batteries, if fitted.•Fit an omnipolar or magnetothermal switch on the mains power supply,having a contact opening distance equal to or greater than 3mm.•Check that a differential switch with a 0.03A threshold is fitted just before the power supply mains.•Check that earthing is carried out correctly: connect all metal parts for closure (doors, gates etc.) and all system components provided with an earth terminal.•The Company declines all responsibility with respect to the automation safety and correct operation when other manufacturers ’ components are used.•Only use original parts for any maintenance or repair operation.•Do not modify the automation components, unless explicitly authorised by the company.•Instruct the product user about the control systems provided and the manual opening operation in case of emergency.•Do not allow persons or children to remain in the automation operation area.•Keep radio control or other control devices out of children ’s reach, in order to avoid unintentional automation activation.•The user must avoid any attempt to carry out work or repair on the automation system, and always request the assistance of qualified personnel.•Anything which is not expressly provided for in the present instructions,is not allowed.3) TECHNICAL SPECIFICATIONSPower supply:...............................................................230V ±10% 50Hz Absorption on empty:.................................................................0.5A max Output power for accessories:..........................................24V~ 6VA max Max relay current:................................................................................8A Max power of motors:...............................................................300 W x 2Torque limiter:.................................................Self-transformer with 4 pos Limit switch:................................................................Adjustable run timePanel dimensions:.........................................................................See fig.1Cabinet protection:............................................................................IP55Working temperature:...............................................................-20 +55°C 4) TERMINAL BOARD CONNECTIONS(Fig.2)CAUTION: Keep the low voltage connections completely separated from the power supply connections.Fig.3 shows the fixing and connection method of the drive condensers whenever they are not fitted to the motor.JP51-2 Single-phase power supply 230V ±10%, 50 Hz (1=L/2=N).For connection to the mains use a multiple-pole cable with a minimum cross section of 3x1.5mm 2 of the type indicated in the above-mentioned standard (by way of example, if the cable is not shielded it must be at least equivalent to H07 RN-F while, if shielded, it must be at least equivalent to H05 VV-F with a cross section of 3x1.5mm 2).JP33-4 (mod.ARIES-P) 230V 40W max. blinker connection.5-6 (mod.ARIES) 230V 40W max. blinker connection.7-8-9 Motor M1 connection - 8 common, 7-9 start.10-11-12 Motor M2(r) connection - 11 common, 10-12 start.JP413-14 Open-close button and key switch (N.O.).13-15 Stop button (N.C.). If unused, leave bridged.13-16 Photocell or pneumatic edge input (N.C.). If unused, leave bridged.17-18 24V 3W max. gate open warning light.18-19 24V~ 0.25A max. (6VA) output (for supplying photocell or other device).20-21 Antenna input for radio-receiver board (20 signal - 21 braid).22 Common terminal (equivalent to terminal 13).23 Terminal for pedestrian control. It moves the leaf of motor M2 connected to terminal 10-11-12. This terminal is available only in ARIES-P control unit.JP225-26 2nd radio channel output of the double-channel receiver board (terminals not fitted on ARIES but fitted on ARIES-P) contact N.O.JP1 Radio-receiver board connector 1-2 channels.5) FUNCTIONSDL1:Power-on LedIt is switched on when the board is electrically powered.START: four-step logic: (DIP5 OFF)gate closed:..................................................................................it opens during opening:............................................... it stops and activates TCA gate open:................................................................................... it closes during closing:.................................... it stops and does not activate TCA after stop:.........................................................................it starts opening START: two-step logic: (DIP5 ON)gate closed:..................................................................................it opens during opening:................................it stops and activats TCA (if activated)gate open:....................................................................................it closes during closing:..............................................................................it opens after stop:.....................................................................................it opens STOP: In all cases: it stops the gate until a new start command is given.PHOT:Functions can be set with DIP-SWITCH.Activated during closing if DIP3-ON.Activated during opening and closing if DIP3-OFF.SCA: Gate open indicating light.with gate closed:...................................................................................off when gate is opening:...........................................................................on with gate open:.......................................................................................on when gate is closing:.....................................................................flashing 6) DIP-SWITCH SELECTION DIP1 Rapid closingON: When the position of the gate photocells is exceeded, during both opening and closing, the gate automatically starts to close even if TCA is activated. We recommend setting DIP3 to ON (photocells only activated during closing).OFF: Function not activated.DIP2 Blocks impulsesON: During opening, START commands are not accepted.OFF: During opening, START commands are accepted.DIP3 PhotocellsON: Photocells only activated during closing.OFF: Photocells activated during opening and closing.D 811184A _04DIP4 Automatic closing time (TCA)ON: Automatic closing activated (can be adjusted from 0 to 90s).OFF: Automatic closing not activated.DIP5 Control logicON: 2-step logic is activated (see start paragraph).OFF: 4-step logic is activated (see start paragraph).DIP6: Preallarm (mod.ARIES P only)ON: The flashing light turns on abt 3 seconds before the motors start.OFF The flashing light turns on simultaneously with the start of the motors.ATTENTION:Dip non used in mod. ARIES (always in OFF set).7) TRIMMER ADJUSTMENTTCA This adjusts the automatic closing time, after which time the gate automatically closes (can be adjusted from 0 to 90s).TW This adjusts the motor working time, after which time the motor stops (can be adjusted from 0 to 40s).TDELAY This adjusts the closing delay time of the second motor (M2).8) MOTOR TORQUE ADJUSTMENTThe ARIES control unit has electric torque adjustment which allows the motor force to be adjusted.The adjustment should be set for the minimum force required to carry out the opening and closing strokes completely.Adjustment is carried out by moving the connection 55 (fig.3) on the tran-sformer sockets as described below:Pos.T1 1st TORQUE (MINIMUM TORQUE)Pos.T2 2nd TORQUE Pos.T3 3rd TORQUEPos.T4 4th TORQUE (MAXIMUM TORQUE)4 motor torque values can be obtained.To gain access to the torque adjustment sockets, disconnect the mains supply and remove the protective case “P ” of the transfomer.CAUTION: Excessive torque adjustment may jeopardise the anti-squash safety function. On the other hand insufficient torque adjustment may not guarantee correct opening or closing strokes.9) MAINTENANCE AND DEMOLITIONThe maintenance of the system should only be carried out by qualified personnel regularly. The materials making up the set and its packing must be disposed of according to the regulations in force.Batteries must be properly disposed of.WARNINGSCorrect controller operation is only ensured when the data contained in the present manual are observed. The company is not to be held responsible for any damage resulting from failure to observe the installation standards and the instructions contained in the present manual.The descriptions and illustrations contained in the present manual are not binding. The Company reserves the right to make any alterations deemed appropriate for the technical, manufacturing and commercial improvement of the product, while leaving the essential product features unchanged, at any time and without undertaking to update the present publication.D811184A_04ARIES/ARIES-P - Ver. 04 -23。
Atmel MEGA-1284P Xplained 评估板启动指南说明书
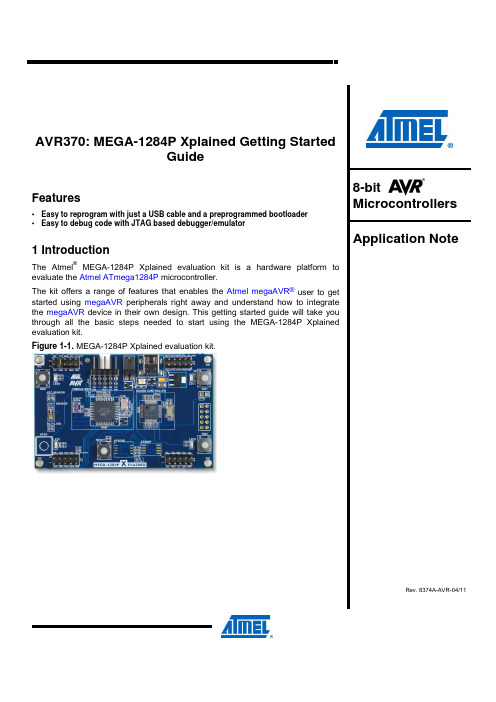
AVR370: MEGA-1284P Xplained Getting StartedGuideFeatures• Easy to reprogram with just a USB cable and a preprogrammed bootloader• Easy to debug code with JTAG based debugger/emulator 1 IntroductionThe Atmel ® MEGA-1284P Xplained evaluation kit is a hardware platform toevaluate the Atmel ATmega1284P microcontroller.The kit offers a range of features that enables the Atmel megaAVR ® user to getstarted using megaAVR peripherals right away and understand how to integratethe megaAVR device in their own design. This getting started guide will take youthrough all the basic steps needed to start using the MEGA-1284P Xplainedevaluation kit.Figure 1-1. MEGA-1284P Xplained evaluation kit.8-bit Microcontrollers Application NoteRev. 8374A-AVR-04/112 AVR3708374A-AVR-04/11 2 What is needed to get started To be able to run the preprogrammed code, you need the Atmel MEGA-1284P Xplained evaluation kit and a USB cable (standard A to mini-B or mini AB) to connect the board to a PC.To modify the example code or write new code and compile it, you need a toolchain for the Atmel AVR ® microcontrollers and an IDE to edit and debug code. Atmel provides both the AVR Studio ® 4 and the AVR GNU toolchain. Other IDEs and toolchains are also available like the IAR Embedded Workbench ®.If you, in addition, want to debug the code at runtime, you’ll need a debugger like the Atmel AVR JTAGICE mkII or the Atmel AVR ONE! More information on these tools is available at the Atmel webpage. See the reference section later in this document for more details.2.1 Documentation for MEGA-1284P XplainedThe “AVR364 MEGA-1284P Xplained Hardware User’s Guide” package includes all in-depth information about the kit like schematics, BOM, assembly drawings, 3D plots and more. The package is available from the Atmel web-site. /xplained2.2 AVR Studio 4The AVR Studio 4 is a free IDE for the Atmel 8-bit AVR microcontrollers. It can be used to write code, program, and debug a microcontroller.AVR Studio 4 /avrstudio2.3 Bootloader programming tools2.3.1 AVR open source programmer (AVROSP)The AVR Open Source Programmer (AVROSP) is an AVR programmer application that offers the possibility to program the Atmel megaAVR devices via a bootloader. It is a command-line tool, using the same syntax as the Atmel STK ®500 and the Atmel AVR JTAGICE command-line tools in the Atmel AVR Studio .AVR911: AVR Open Source Programmer /dyn/resources/prod_documents/doc2568.pdf /dyn/resources/prod_documents/AVR911.zipOn the MEGA-1284P Xplained board the Atmel ATmega1284P microcontroller is preprogrammed with a bootloader firmware that is compatible to the AVROSP.2.3.2 FLIP (BatchISP)BatchISP is a command line tool for programming the flash and the EEPROM memories of the board controller, and is part of the FLIP installation. It can be used to communicate with the preprogrammed DFU bootloader on the board controller.FLIP (FLexible In-system Programmer) for programming /dyn/products/tools_card.asp?tool_id=3886AVR37038374A-AVR-04/11 2.4 Toolchain In order to build an application from the source code a toolchain is needed, which includes the required tools like assembler, compiler, and linker. The code for this kit is compatible with the AVR GNU and IAR™ AVR toolchains.2.4.1 AVR GNU toolchainThe AVR GNU toolchain is a free toolchain that can be downloaded from the Atmel webpage. It includes all necessary tools like a C/C++ compiler, assembler and linker, which are necessary for the AVR application development. The toolchain integrates with the Atmel AVR Studio 4 through the AVR GCC plug-in.AVR GNU toolchain (free C/C++ compiler for 8-bit and 32-bit AVRs) /dyn/products/tools_card.asp?tool_id=41182.4.2 IAR AVR toolchainThe IAR AVR toolchain is a commercial toolchain which includes all necessary tools like C/C++ compiler, assembler and linker which are needed for the AVR application development. There is a 30 day evaluation version as well as a 4k (code size limited) kick-start version available from their website.IAR Embedded Workbench for the Atmel AVR /website1/1.0.1.0/107/1/2.5 Programmers and debuggersProgrammers and debuggers are needed when either the application should be programmed without using the bootloader, or when debugging support is needed. Several different tools are available that can be used directly with the Xplained kit; the most common of these are described in the next chapters.2.5.1 Atmel AVR DragonThe AVR Dragon™ is a low-cost debug/programming tool that can be used for code development with the Atmel MEGA-1284P Xplained kit.Atmel AVR Dragon (on-chip programming and debugging tool) /dyn/products/tools_card.asp?tool_id=38912.5.2 Atmel AVR JTAGICE mkIIThe AVR JTAGICE mkII is a mid-range debug/programming tool that can be used for code development with the MEGA-1284P Xplained kit.Atmel AVR JTAGICE mkII (on-chip programming and debugging tool) /dyn/products/tools_card.asp?tool_id=33532.5.3 Atmel AVR ONE!The AVR ONE! is a high-end debug/programming tool that can be used for code development with the MEGA-1284P Xplained kit.Atmel AVR ONE! (on-chip programming and debugging tool) /dyn/products/tools_card.asp?tool_id=42794 AVR3708374A-AVR-04/11 3 Board overviewFigure 3-1 shows most of the available features on the board. For more detailed information on the Atmel MEGA-1284P Xplained hardware, take a look at the Atmel application note “AVR364: MEGA-1284P Xplained Hardware User’s Guide”. Figure 3-1. Overview of the MEGA-1284P Xplained kit.Header J4JTAG HeaderPower measurement USB Connector QTouch Button (QTB0)Mechanical Button (SW0)Power & Status LED NTC Sensor LIGHT Sensor RC Filter Button (SW1)Mechanical Button (SW2)ATmega1284PAVR37058374A-AVR-04/11 4 Connecting the board Connect a USB cable between the board and a PC or a USB power supply to power it up. This is all that is needed. When power is applied the power/status LED will light up in green.WARNING Do not power the board without having the jumper next to the USBconnector or an ammeter mounted. Otherwise, the device may bedamaged.When connecting the Atmel MEGA-1284P Xplained to a PC, the operating system will request a driver file for installing the serial communication driver. This driver file is available in the zip-file associated with this document. The driver file supports both 32-bit and 64-bit versions of Windows ® XP and Windows 7. Driver installs are not necessary on Linux ® operating systems.4.1 Connecting the Atmel AVR DragonIn order to connect the AVR Dragon to the MEGA-1284P Xplained, a 10-pin header cable is needed. Connect the cable between the JTAG connector on the AVR Dragon kit and the MEGA-1284P Xplained JTAG connector. Take a look at Figure 4-1 how the connection should be done.Figure 4-1. Connecting AVR Dragon to an Xplained board.6 AVR3708374A-AVR-04/11 4.2 Connecting the Atmel AVR JTAGICE mkII The grey connector on the AVR JTAGICE mkII probe has to be used when connecting to the Atmel MEGA-1284P Xplained. See Figure 4-2 for reference of how to make the connection.Figure 4-2. Connecting AVR JTAGICE mkII to an Xplained board.4.3 Connecting of the Atmel AVR ONE!The AVR ONE! JTAG connector can be connected to the MEGA-1284P Xplained kit with a standoff adapter as shown in Figure 4-3.Figure 4-3. Connecting AVR ONE! to a Xplained board.AVR37078374A-AVR-04/11 5 Programming the kit5.1 Programming via the bootloader The preprogrammed bootloader on the Atmel ATmega1284P offers the possibility toprogram the device via the UART interface. Since the default firmware of the boardcontroller acts as UART to USB bridge the ATmega1284P can be programmed fromthe PC via the USB connection to the kit.The bootloader on the ATmega1284P is evoked by pushing the mechanical switch (SW0) during reset. Programming can be performed by using the command line tool from the AVROSP package. More information about AVROSP can be found in the application note that is available for this package. The executable file avrosp.exe is the only file required to use AVROSP. It is contained in the avr911.zip file that comes with this application note. The zip-file also contains the complete source code and a copy of the part description files from an Atmel AVR Studio 4 installation.5.1.1 Step-by-step guideTo program the device, follow these steps:1.Connect the USB cable from the PC to the kit 2.Press the reset button and the SW0 button 3.Release the reset button while still pressing the SW0 button 4.Release the SW0 button 5. Open the device manager and locate the COM port used by the kit, it should belisted as “XPLAINED Virtual Com Port” as shown in Figure 5-1Figure 5-1. Xplained kit COM port.6. The communication port settings (baud rate, parity control etc.) must be setmanually before using AVROSP. The needed settings are 57600bps, no paritycontrol and eight data bits. Therefore the following command must be executedon the DOS command interpreter assuming the kit is listed under COM6, asshown in Figure 5-1: mode com6 baud=57600 parity=n data=88 AVR3708374A-AVR-04/11 7. Now the AVROSP application can be started to program the kit with theapplication. Following command can be used assuming that the kit uses COM6:avrosp –dATmega128 –cCOM6 –pf –vf -ifmega_1284p_xplained_example.hex –e8. Your firmware should now be runningNOTE AVROSP only supports comports COM1 through COM8. Connecting to a highercomport than this will not work.5.2 Restoring the bootloaderWhen the bootloader has been erased it can be restored with any of the previously mentioned programming tools.The hex file for the bootloader is a part of the application note zip (in the folder named hex) file and is called mega_1284p_xplained_bootloader_and_example.hexAVR37098374A-AVR-04/11 6 Example applications6.1 Preprogrammed firmware The preprogrammed firmware in the Atmel ATmega1284P is set up with an example code that demonstrates some of the basic features of the MEGA-1284P Xplained kit. This includes sleep modes, reading the light sensor and the ntc sensor. The example application has two main modes, demo mode or terminal mode. For more information please refer to the doxygen documentation (readme.html) found in the zip file associated with this application note. It also includes a bootloader (AVROSP) which allows the user to re-program the ATmega1284P without using an external programmer.The Atmel AT32UC3B1256 board controller is also pre-programmed with a bootloader and an USART-to-USB gateway application which can be used to communicate with the target controller ATmega1284P .10 AVR3708374A-AVR-04/11 7 How to compile example projects7.1 Atmel AVR Studio 4 Open the AVR Studio 4 project and compile the project. The compiler will generate an Intel hex file and an ELF file. The Intel hex file can be downloaded to the Atmel ATmega1284P via the AVROSP program.7.2 IAR Embedded WorkbenchOpen the IAR Embedded Workbench project and compile the code. After compilation an Intel hex and a debug file will be available. The Intel hex file can be downloaded to the ATmega1284P via the AVROSP program.AVR370118374A-AVR-04/118 EVALUATION BOARD/KIT IMPORTANT NOTICEThis evaluation board/kit is intended for use for FURTHER ENGINEERING, DEVELOPMENT, DEMONSTRATION, OR EVALUATION PURPOSES ONLY. It is not a finished product and may not (yet) comply with some or any technical or legal requirements that are applicable to finished products, including, without limitation, directives regarding electromagnetic compatibility, recycling (WEEE), FCC, CE or UL (except as may be otherwise noted on the board/kit). Atmel supplied this board/kit “AS IS,” without any warranties, with all faults, at the buyer’s and further users’ sole risk. The user assumes all responsibility and liability for proper and safe handling of the goods. Further, the user indemnifies Atmel from all claims arising from the handling or use of the goods. Due to the open construction of the product, it is the user’s responsibility to take any and all appropriate precautions with regard to electrostatic discharge and any other technical or legal concerns.EXCEPT TO THE EXTENT OF THE INDEMNITY SET FORTH ABOVE, NEITHER USER NOR ATMEL SHALL BE LIABLE TO EACH OTHER FOR ANY INDIRECT, SPECIAL, INCIDENTAL, OR CONSEQUENTIAL DAMAGES.No license is granted under any patent right or other intellectual property right of Atmel covering or relating to any machine, process, or combination in which such Atmel products or services might be or are used.Mailing Address: Atmel Corporation, 2325 Orchard Parkway, San Jose, CA 95131 Copyright © 2011, Atmel Corporation12AVR3708374A-AVR-04/119 Table of contentsFeatures ............................................................................................... 1 1 Introduction ...................................................................................... 1 2 What is needed to get started ......................................................... 2 2.1 Documentation for MEGA-1284P Xplained ......................................................... 2 2.2 AVR Studio 4 ....................................................................................................... 2 2.3 Bootloader programming tools ............................................................................ 2 2.3.1 AVR open source programmer (AVROSP) ................................................................ 2 2.3.2 FLIP (BatchISP) ........................................................................................................ 2 2.4 Toolchain ............................................................................................................. 3 2.4.1 AVR GNU toolchain ................................................................................................... 3 2.4.2 IAR AVR toolchain ..................................................................................................... 3 2.5 Programmers and debuggers .............................................................................. 3 2.5.1 Atmel AVR Dragon .................................................................................................... 3 2.5.2 Atmel AVR JTAGICE mkII ......................................................................................... 3 2.5.3 Atmel AVR ONE! ....................................................................................................... 3 3 Board overview ................................................................................ 4 4 Connecting the board ...................................................................... 5 4.1 Connecting the Atmel AVR Dragon ..................................................................... 5 4.2 Connecting the Atmel AVR JTAGICE mkII ......................................................... 6 4.3 Connecting of the Atmel AVR ONE! .................................................................... 6 5 Programming the kit ........................................................................ 7 5.1 Programming via the bootloader ......................................................................... 7 5.1.1 Step-by-step guide .................................................................................................... 7 5.2 Restoring the bootloader ..................................................................................... 8 6 Example applications ...................................................................... 9 6.1 Preprogrammed firmware .................................................................................... 9 7 How to compile example projects ................................................ 10 7.1 Atmel AVR Studio 4 ........................................................................................... 10 7.2 IAR Embedded Workbench ............................................................................... 10 8 EVALUATION BOARD/KIT IMPORTANT NOTICE ........................ 11 9 Table of contents (12)8374A-AVR-04/11。
同杆线路纵联零序保护误动分析及措施

C !! G. 78 @ P[ _ L % x D Zl ’ & 2" OP % I 3 7 5 &!!a & 9 *1 & G & 4 : &’ * 5 8 3 & 13 8> ( + + & 9 & 4 8 W B & * & 9 3 8 ( 4 1 8 3 8 & 1% 9 ( H 3 5 1 ( > &’ 3 5 G & 1 M B M
ab ’ ( * + Zd{Z4C ! 3# & $R LD! 2 % r %# 3 2R LD! 2 % r &# 3 &R LD! 2 % r 0# $ ’R LD% r Zd{dTC $ &# 2 ’R LD! 2 % r !# 3 !R LD! 2 % r 3 3# !R LD! 2 % r ! %# " ’R LD! 2 % r
!! 78
P . $ # ’( LO 8 : v "F B _ op Ko , N PQ’( ) " # Y ,-1 8{ ’ h tr L = 8{ J
. ! / " & s > v I y {|N y O # l v fg@ F {|Q . $ / 3 # g w $ # ’( N Bj:KgK ? f 4L L Y M
pw _ 3 ) a b# j"MTaZd{6C$# 1w s 1 2 . * K 1 | . * M a B j N v @ # Y < !@ + 1;N O I } # Z 4 } o q _ y T " Y F < {R + N O Z { # T0vZ4#OI}oN12 .*# w Vy T{| 8 s 1w ’ 1 ! N ab & , n J TL }~ O Z { G F _ @ y / ! G H ] { | I ^" # .OOZ{S ! % %R =# 1 %R =# " %R = [ 3 ) a b# % % S! M # 1 ; %# $ # 1 ; %# $$ R =’ 0$ R =# 4# , n \ z5 R $’ R3@+& : R $’ R3iT# HO Z { { | G F & / X v J# Z d { # 8 O {12 . * & / y M # H {| G F Wj" Zd{ Z 4 C # d T C $ # 1 w I %R = J# G}# RJ# 12.*b_I]$#1!N#XQ !# Z4C$#1w*EgN1s$#1!0 % rv _m80 Z4C$ . [ u " _ i G# P.$#’ # % r ( 1q , T ? &
Glider Flying Handbook说明书

Glider Flying Handbook2013U.S. Department of TransportationFEDERAL AVIATION ADMINISTRATIONFlight Standards Servicei iPrefaceThe Glider Flying Handbook is designed as a technical manual for applicants who are preparing for glider category rating and for currently certificated glider pilots who wish to improve their knowledge. Certificated flight instructors will find this handbook a valuable training aid, since detailed coverage of aeronautical decision-making, components and systems, aerodynamics, flight instruments, performance limitations, ground operations, flight maneuvers, traffic patterns, emergencies, soaring weather, soaring techniques, and cross-country flight is included. Topics such as radio navigation and communication, use of flight information publications, and regulations are available in other Federal Aviation Administration (FAA) publications.The discussion and explanations reflect the most commonly used practices and principles. Occasionally, the word “must” or similar language is used where the desired action is deemed critical. The use of such language is not intended to add to, interpret, or relieve a duty imposed by Title 14 of the Code of Federal Regulations (14 CFR). Persons working towards a glider rating are advised to review the references from the applicable practical test standards (FAA-G-8082-4, Sport Pilot and Flight Instructor with a Sport Pilot Rating Knowledge Test Guide, FAA-G-8082-5, Commercial Pilot Knowledge Test Guide, and FAA-G-8082-17, Recreational Pilot and Private Pilot Knowledge Test Guide). Resources for study include FAA-H-8083-25, Pilot’s Handbook of Aeronautical Knowledge, FAA-H-8083-2, Risk Management Handbook, and Advisory Circular (AC) 00-6, Aviation Weather For Pilots and Flight Operations Personnel, AC 00-45, Aviation Weather Services, as these documents contain basic material not duplicated herein. All beginning applicants should refer to FAA-H-8083-25, Pilot’s Handbook of Aeronautical Knowledge, for study and basic library reference.It is essential for persons using this handbook to become familiar with and apply the pertinent parts of 14 CFR and the Aeronautical Information Manual (AIM). The AIM is available online at . The current Flight Standards Service airman training and testing material and learning statements for all airman certificates and ratings can be obtained from .This handbook supersedes FAA-H-8083-13, Glider Flying Handbook, dated 2003. Always select the latest edition of any publication and check the website for errata pages and listing of changes to FAA educational publications developed by the FAA’s Airman Testing Standards Branch, AFS-630.This handbook is available for download, in PDF format, from .This handbook is published by the United States Department of Transportation, Federal Aviation Administration, Airman Testing Standards Branch, AFS-630, P.O. Box 25082, Oklahoma City, OK 73125.Comments regarding this publication should be sent, in email form, to the following address:********************************************John M. AllenDirector, Flight Standards Serviceiiii vAcknowledgmentsThe Glider Flying Handbook was produced by the Federal Aviation Administration (FAA) with the assistance of Safety Research Corporation of America (SRCA). The FAA wishes to acknowledge the following contributors: Sue Telford of Telford Fishing & Hunting Services for images used in Chapter 1JerryZieba () for images used in Chapter 2Tim Mara () for images used in Chapters 2 and 12Uli Kremer of Alexander Schleicher GmbH & Co for images used in Chapter 2Richard Lancaster () for images and content used in Chapter 3Dave Nadler of Nadler & Associates for images used in Chapter 6Dave McConeghey for images used in Chapter 6John Brandon (www.raa.asn.au) for images and content used in Chapter 7Patrick Panzera () for images used in Chapter 8Jeff Haby (www.theweatherprediction) for images used in Chapter 8National Soaring Museum () for content used in Chapter 9Bill Elliot () for images used in Chapter 12.Tiffany Fidler for images used in Chapter 12.Additional appreciation is extended to the Soaring Society of America, Inc. (), the Soaring Safety Foundation, and Mr. Brad Temeyer and Mr. Bill Martin from the National Oceanic and Atmospheric Administration (NOAA) for their technical support and input.vv iPreface (iii)Acknowledgments (v)Table of Contents (vii)Chapter 1Gliders and Sailplanes ........................................1-1 Introduction....................................................................1-1 Gliders—The Early Years ..............................................1-2 Glider or Sailplane? .......................................................1-3 Glider Pilot Schools ......................................................1-4 14 CFR Part 141 Pilot Schools ...................................1-5 14 CFR Part 61 Instruction ........................................1-5 Glider Certificate Eligibility Requirements ...................1-5 Common Glider Concepts ..............................................1-6 Terminology...............................................................1-6 Converting Metric Distance to Feet ...........................1-6 Chapter 2Components and Systems .................................2-1 Introduction....................................................................2-1 Glider Design .................................................................2-2 The Fuselage ..................................................................2-4 Wings and Components .............................................2-4 Lift/Drag Devices ...........................................................2-5 Empennage .....................................................................2-6 Towhook Devices .......................................................2-7 Powerplant .....................................................................2-7 Self-Launching Gliders .............................................2-7 Sustainer Engines .......................................................2-8 Landing Gear .................................................................2-8 Wheel Brakes .............................................................2-8 Chapter 3Aerodynamics of Flight .......................................3-1 Introduction....................................................................3-1 Forces of Flight..............................................................3-2 Newton’s Third Law of Motion .................................3-2 Lift ..............................................................................3-2The Effects of Drag on a Glider .....................................3-3 Parasite Drag ..............................................................3-3 Form Drag ...............................................................3-3 Skin Friction Drag ..................................................3-3 Interference Drag ....................................................3-5 Total Drag...................................................................3-6 Wing Planform ...........................................................3-6 Elliptical Wing ........................................................3-6 Rectangular Wing ...................................................3-7 Tapered Wing .........................................................3-7 Swept-Forward Wing ..............................................3-7 Washout ..................................................................3-7 Glide Ratio .................................................................3-8 Aspect Ratio ............................................................3-9 Weight ........................................................................3-9 Thrust .........................................................................3-9 Three Axes of Rotation ..................................................3-9 Stability ........................................................................3-10 Flutter .......................................................................3-11 Lateral Stability ........................................................3-12 Turning Flight ..............................................................3-13 Load Factors .................................................................3-13 Radius of Turn ..........................................................3-14 Turn Coordination ....................................................3-15 Slips ..........................................................................3-15 Forward Slip .........................................................3-16 Sideslip .................................................................3-17 Spins .........................................................................3-17 Ground Effect ...............................................................3-19 Chapter 4Flight Instruments ...............................................4-1 Introduction....................................................................4-1 Pitot-Static Instruments ..................................................4-2 Impact and Static Pressure Lines................................4-2 Airspeed Indicator ......................................................4-2 The Effects of Altitude on the AirspeedIndicator..................................................................4-3 Types of Airspeed ...................................................4-3Table of ContentsviiAirspeed Indicator Markings ......................................4-5 Other Airspeed Limitations ........................................4-6 Altimeter .....................................................................4-6 Principles of Operation ...........................................4-6 Effect of Nonstandard Pressure andTemperature............................................................4-7 Setting the Altimeter (Kollsman Window) .............4-9 Types of Altitude ......................................................4-10 Variometer................................................................4-11 Total Energy System .............................................4-14 Netto .....................................................................4-14 Electronic Flight Computers ....................................4-15 Magnetic Compass .......................................................4-16 Yaw String ................................................................4-16 Inclinometer..............................................................4-16 Gyroscopic Instruments ...............................................4-17 G-Meter ........................................................................4-17 FLARM Collision Avoidance System .........................4-18 Chapter 5Glider Performance .............................................5-1 Introduction....................................................................5-1 Factors Affecting Performance ......................................5-2 High and Low Density Altitude Conditions ...........5-2 Atmospheric Pressure .............................................5-2 Altitude ...................................................................5-3 Temperature............................................................5-3 Wind ...........................................................................5-3 Weight ........................................................................5-5 Rate of Climb .................................................................5-7 Flight Manuals and Placards ..........................................5-8 Placards ......................................................................5-8 Performance Information ...........................................5-8 Glider Polars ...............................................................5-8 Weight and Balance Information .............................5-10 Limitations ...............................................................5-10 Weight and Balance .....................................................5-12 Center of Gravity ......................................................5-12 Problems Associated With CG Forward ofForward Limit .......................................................5-12 Problems Associated With CG Aft of Aft Limit ..5-13 Sample Weight and Balance Problems ....................5-13 Ballast ..........................................................................5-14 Chapter 6Preflight and Ground Operations .......................6-1 Introduction....................................................................6-1 Assembly and Storage Techniques ................................6-2 Trailering....................................................................6-3 Tiedown and Securing ................................................6-4Water Ballast ..............................................................6-4 Ground Handling........................................................6-4 Launch Equipment Inspection ....................................6-5 Glider Preflight Inspection .........................................6-6 Prelaunch Checklist ....................................................6-7 Glider Care .....................................................................6-7 Preventive Maintenance .............................................6-8 Chapter 7Launch and Recovery Procedures and Flight Maneuvers ............................................................7-1 Introduction....................................................................7-1 Aerotow Takeoff Procedures .........................................7-2 Signals ........................................................................7-2 Prelaunch Signals ....................................................7-2 Inflight Signals ........................................................7-3 Takeoff Procedures and Techniques ..........................7-3 Normal Assisted Takeoff............................................7-4 Unassisted Takeoff.....................................................7-5 Crosswind Takeoff .....................................................7-5 Assisted ...................................................................7-5 Unassisted...............................................................7-6 Aerotow Climb-Out ....................................................7-6 Aerotow Release.........................................................7-8 Slack Line ...................................................................7-9 Boxing the Wake ......................................................7-10 Ground Launch Takeoff Procedures ............................7-11 CG Hooks .................................................................7-11 Signals ......................................................................7-11 Prelaunch Signals (Winch/Automobile) ...............7-11 Inflight Signals ......................................................7-12 Tow Speeds ..............................................................7-12 Automobile Launch ..................................................7-14 Crosswind Takeoff and Climb .................................7-14 Normal Into-the-Wind Launch .................................7-15 Climb-Out and Release Procedures ..........................7-16 Self-Launch Takeoff Procedures ..............................7-17 Preparation and Engine Start ....................................7-17 Taxiing .....................................................................7-18 Pretakeoff Check ......................................................7-18 Normal Takeoff ........................................................7-19 Crosswind Takeoff ...................................................7-19 Climb-Out and Shutdown Procedures ......................7-19 Landing .....................................................................7-21 Gliderport/Airport Traffic Patterns and Operations .....7-22 Normal Approach and Landing ................................7-22 Crosswind Landing ..................................................7-25 Slips ..........................................................................7-25 Downwind Landing ..................................................7-27 After Landing and Securing .....................................7-27viiiPerformance Maneuvers ..............................................7-27 Straight Glides ..........................................................7-27 Turns.........................................................................7-28 Roll-In ...................................................................7-29 Roll-Out ................................................................7-30 Steep Turns ...........................................................7-31 Maneuvering at Minimum Controllable Airspeed ...7-31 Stall Recognition and Recovery ...............................7-32 Secondary Stalls ....................................................7-34 Accelerated Stalls .................................................7-34 Crossed-Control Stalls ..........................................7-35 Operating Airspeeds .....................................................7-36 Minimum Sink Airspeed ..........................................7-36 Best Glide Airspeed..................................................7-37 Speed to Fly ..............................................................7-37 Chapter 8Abnormal and Emergency Procedures .............8-1 Introduction....................................................................8-1 Porpoising ......................................................................8-2 Pilot-Induced Oscillations (PIOs) ..............................8-2 PIOs During Launch ...................................................8-2 Factors Influencing PIOs ........................................8-2 Improper Elevator Trim Setting ..............................8-3 Improper Wing Flaps Setting ..................................8-3 Pilot-Induced Roll Oscillations During Launch .........8-3 Pilot-Induced Yaw Oscillations During Launch ........8-4 Gust-Induced Oscillations ..............................................8-5 Vertical Gusts During High-Speed Cruise .................8-5 Pilot-Induced Pitch Oscillations During Landing ......8-6 Glider-Induced Oscillations ...........................................8-6 Pitch Influence of the Glider Towhook Position ........8-6 Self-Launching Glider Oscillations During Powered Flight ...........................................................8-7 Nosewheel Glider Oscillations During Launchesand Landings ..............................................................8-7 Tailwheel/Tailskid Equipped Glider Oscillations During Launches and Landings ..................................8-8 Aerotow Abnormal and Emergency Procedures ............8-8 Abnormal Procedures .................................................8-8 Towing Failures........................................................8-10 Tow Failure With Runway To Land and Stop ......8-11 Tow Failure Without Runway To Land BelowReturning Altitude ................................................8-11 Tow Failure Above Return to Runway Altitude ...8-11 Tow Failure Above 800' AGL ..............................8-12 Tow Failure Above Traffic Pattern Altitude .........8-13 Slack Line .................................................................8-13 Ground Launch Abnormal and Emergency Procedures ....................................................................8-14 Abnormal Procedures ...............................................8-14 Emergency Procedures .............................................8-14 Self-Launch Takeoff Emergency Procedures ..............8-15 Emergency Procedures .............................................8-15 Spiral Dives ..................................................................8-15 Spins .............................................................................8-15 Entry Phase ...............................................................8-17 Incipient Phase .........................................................8-17 Developed Phase ......................................................8-17 Recovery Phase ........................................................8-17 Off-Field Landing Procedures .....................................8-18 Afterlanding Off Field .............................................8-20 Off-Field Landing Without Injury ........................8-20 Off-Field Landing With Injury .............................8-20 System and Equipment Malfunctions ..........................8-20 Flight Instrument Malfunctions ................................8-20 Airspeed Indicator Malfunctions ..........................8-21 Altimeter Malfunctions .........................................8-21 Variometer Malfunctions ......................................8-21 Compass Malfunctions .........................................8-21 Glider Canopy Malfunctions ....................................8-21 Broken Glider Canopy ..........................................8-22 Frosted Glider Canopy ..........................................8-22 Water Ballast Malfunctions ......................................8-22 Retractable Landing Gear Malfunctions ..................8-22 Primary Flight Control Systems ...............................8-22 Elevator Malfunctions ..........................................8-22 Aileron Malfunctions ............................................8-23 Rudder Malfunctions ............................................8-24 Secondary Flight Controls Systems .........................8-24 Elevator Trim Malfunctions .................................8-24 Spoiler/Dive Brake Malfunctions .........................8-24 Miscellaneous Flight System Malfunctions .................8-25 Towhook Malfunctions ............................................8-25 Oxygen System Malfunctions ..................................8-25 Drogue Chute Malfunctions .....................................8-25 Self-Launching Gliders ................................................8-26 Self-Launching/Sustainer Glider Engine Failure During Takeoff or Climb ..........................................8-26 Inability to Restart a Self-Launching/SustainerGlider Engine While Airborne .................................8-27 Self-Launching Glider Propeller Malfunctions ........8-27 Self-Launching Glider Electrical System Malfunctions .............................................................8-27 In-flight Fire .............................................................8-28 Emergency Equipment and Survival Gear ...................8-28 Survival Gear Checklists ..........................................8-28 Food and Water ........................................................8-28ixClothing ....................................................................8-28 Communication ........................................................8-29 Navigation Equipment ..............................................8-29 Medical Equipment ..................................................8-29 Stowage ....................................................................8-30 Parachute ..................................................................8-30 Oxygen System Malfunctions ..................................8-30 Accident Prevention .....................................................8-30 Chapter 9Soaring Weather ..................................................9-1 Introduction....................................................................9-1 The Atmosphere .............................................................9-2 Composition ...............................................................9-2 Properties ....................................................................9-2 Temperature............................................................9-2 Density ....................................................................9-2 Pressure ...................................................................9-2 Standard Atmosphere .................................................9-3 Layers of the Atmosphere ..........................................9-4 Scale of Weather Events ................................................9-4 Thermal Soaring Weather ..............................................9-6 Thermal Shape and Structure .....................................9-6 Atmospheric Stability .................................................9-7 Air Masses Conducive to Thermal Soaring ...................9-9 Cloud Streets ..............................................................9-9 Thermal Waves...........................................................9-9 Thunderstorms..........................................................9-10 Lifted Index ..........................................................9-12 K-Index .................................................................9-12 Weather for Slope Soaring .......................................9-14 Mechanism for Wave Formation ..............................9-16 Lift Due to Convergence ..........................................9-19 Obtaining Weather Information ...................................9-21 Preflight Weather Briefing........................................9-21 Weather-ReIated Information ..................................9-21 Interpreting Weather Charts, Reports, andForecasts ......................................................................9-23 Graphic Weather Charts ...........................................9-23 Winds and Temperatures Aloft Forecast ..............9-23 Composite Moisture Stability Chart .....................9-24 Chapter 10Soaring Techniques ..........................................10-1 Introduction..................................................................10-1 Thermal Soaring ...........................................................10-2 Locating Thermals ....................................................10-2 Cumulus Clouds ...................................................10-2 Other Indicators of Thermals ................................10-3 Wind .....................................................................10-4 The Big Picture .....................................................10-5Entering a Thermal ..............................................10-5 Inside a Thermal.......................................................10-6 Bank Angle ...........................................................10-6 Speed .....................................................................10-6 Centering ...............................................................10-7 Collision Avoidance ................................................10-9 Exiting a Thermal .....................................................10-9 Atypical Thermals ..................................................10-10 Ridge/Slope Soaring ..................................................10-10 Traps ......................................................................10-10 Procedures for Safe Flying .....................................10-12 Bowls and Spurs .....................................................10-13 Slope Lift ................................................................10-13 Obstructions ...........................................................10-14 Tips and Techniques ...............................................10-15 Wave Soaring .............................................................10-16 Preflight Preparation ...............................................10-17 Getting Into the Wave ............................................10-18 Flying in the Wave .................................................10-20 Soaring Convergence Zones ...................................10-23 Combined Sources of Updrafts ..............................10-24 Chapter 11Cross-Country Soaring .....................................11-1 Introduction..................................................................11-1 Flight Preparation and Planning ...................................11-2 Personal and Special Equipment ..................................11-3 Navigation ....................................................................11-5 Using the Plotter .......................................................11-5 A Sample Cross-Country Flight ...............................11-5 Navigation Using GPS .............................................11-8 Cross-Country Techniques ...........................................11-9 Soaring Faster and Farther .........................................11-11 Height Bands ..........................................................11-11 Tips and Techniques ...............................................11-12 Special Situations .......................................................11-14 Course Deviations ..................................................11-14 Lost Procedures ......................................................11-14 Cross-Country Flight in a Self-Launching Glider .....11-15 High-Performance Glider Operations and Considerations ............................................................11-16 Glider Complexity ..................................................11-16 Water Ballast ..........................................................11-17 Cross-Country Flight Using Other Lift Sources ........11-17 Chapter 12Towing ................................................................12-1 Introduction..................................................................12-1 Equipment Inspections and Operational Checks .........12-2 Tow Hook ................................................................12-2 Schweizer Tow Hook ...........................................12-2x。
RedGiant红巨星系列插件(包括Trapcode系列MagicBullet系列等)注册码

Red Gi ant 红巨星系列插件(包括T rapco de系列,Magic Bulle t系列等)注册码Tra pcode系列插件 32位/64位 AE7.0 c s3 cs4 cs5已测试注册成功Trap code3dstr oke v2.6.08504-8786-2500-7973-4045Tr apcod e Ech o Spa ce v1.1.01806-9363-1382-3577-4294Trap codeform v1.1.08963-8983-1000-6183-3028T rapco de ho rizon v1.1.08407-9462-1000-8739-6032Trapc ode L ux v1.1.09351-9185-1115-4017-51058813-9153-1391-3563-82938901-9141-1535-5036-4525Trap codeparti cular v2.1.08476 8810 2111 5743 91408291 8812 2111 9741 5955T rapco de sh ine v1.6.0 (注意:先装演示版再在A ECS5中注册)9018-8522-1500-3971-1535Trapc ode S oundkeysv1.2.01406-9268-1890-7019-3890Tr apcod e Sta rglow v1.6.09122-8674-1500-6827-0151=========================================RedGiant Magi c Bul let 系列插件 32bi t 64b it 注册码Ma gic B ullet Mojov1.1/v1.28450 1630 1000 4153 01398357-1608-1000-4258-9046Magic Bull et Lo oks v1.4.1/v1.4.38335 2967 1000 7517 96809443-2929-1498-8572-38362226-2975-1561-7392-91258946-2914-1090-9732-7381Magic Bull et Co loris ta Ⅱ调色师1759 1720 1942 8719 98951520-1761-1281-4491-29951623-1704-1894-4141-77111669-1738-1942-6448-38052077-1774-1115-5675-2386M agicBulle t Ins tantH D v1.1/v1.2 视频转换8680-8082-1000-3600-21378374-8050-1000-7790-58318651-8096-1000-8165-81088341-8036-1000-6446-8798======================================== RedGiant红巨星其它插件 32b it 64bit 注册码R ed Gi ant K ey Co rrect v1.1/v1.2抠像校正8884 7072 1000 6861 92218831-7014-1000-7750-71688524-7000-1000-5504-98618932-7028-1000-7300-8269Red G iantKnoll Ligh t Fac tory2.7 灯光工厂9248-3000-2939-3565-1044Red Gian t Pla neSpa ce v1.4 3D助手2272-5113-1995-5538-18691785-5150-1912-5669-62991555-5174-1711-8253-68681728-5161-1306-8162-8636R ed Gi ant I mageLoung e v1.4 烟雾水火9601-7161-1124-7096-5124Red Gian t Psu namiv1.3.1/v1.4 天空海洋8918-5306-1340-8021-98918755-5319-1340-9790-27288695-5367-1340-8236-86688539-5315-1340-9036-6512R ed Gi ant W arp v1.1 三维变形反射投影2264-0345-1839-7036-81291530-0325-1394-5601-09502072-0325-1600-5426-96981732-0305-1823-5049-0581RedGiant Text Anar chy v2.4 极品文字特效8418-5446-2340-7452-29038630-5454-2340-8133-7115Re d Gia nt Ho lomat rix v1.2 屏幕视觉效果1772-6157-1942-4827-54361841-6194-1153-6422-8716R ed Gi ant P rimat te Ke yer v4.1 极品抠像8528-4002-4000-9517-05058783-4068-4000-6068-87609150-4038-4000-9260-21278704-4062-4000-7287-2681Re d Gia nt To onItv2.1卡通、水墨、油画2224-5529-2995-5538-18691737-5574-2912-5669-62991456-5541-2035-8665-5141R ed Gi ant C ompos ite W izard 1.4.5 1558-7224-1340-6093-82528338-7202-1384-7715-20839116-7278-1571-5973-40481377-7270-1729-7167-94601695-7274-1450-8641-5499******************************************************* 附:旧版 Red Gian t红巨星系列插件注册码R ed Gi ant C ompos ite W izard v1.4seri al: 1558-7224-1340-6093-8252After Effe cts 6.0-8.0 Sup portRed Gian t Ima ge Lo ungev1.4seria l: 9601-7161-1124-7096-5124A fterEffec ts 6.0-8.0 Supp ort RedGiant Knol l Lig ht Fa ctory Prov2.5.2ser ial:9248-3000-2939-3565-10448405-3024-2555-8703-3817Af ter E ffect s, Pr emier e Pro,Fina l Cut Pro,Motio n, Av idRed.G iant.Prima tte.K eyer.Pro.v4.0.f or.AE.and.AVXs erial: 9473-4044-4228-6877-3228Af ter E ffect s, Av id,Fi nal C ut Pr o, an d Mot ionRed G iantRadiu m Glo w v1.0ser ial:1374-0436-1563-3568-3475FCP6.x下使用有退出状况,建议使用前保存FC P工程文件。
Image Registration fot remote sensing

Spatial and Spectral Characteristics of Some Operational Sensors (Ch. 14-22
What is Image Registration …
• Definition
“Exact pixel-to-pixel matching of two different images or matching of one image to a map”
Misregistration
• (Towsnhend et al, 1992) and (Dai & Khorram, 1998): small error in registration may have a large impact on global change measurements accuracy • e.g., 1 pixel misregistration error => 50% error in Vegetation Index (NDVI) computation (using 250m MODIS data)
Experiments … Datasets (1) • Synthetic Data Experiments
Experiments (1) … Analysis Samples • Various Features; Convergence as a function of noise and radiometric variations
Image Registration for Remote Sensing
Jacqueline Le Moigne Nathan S. Netanyahu Roger D. Eastman
An Introduction to LDPC Codes

?W?|hL_ U| L?|L w# L_it` ** @4, +)@?#iT@h|4i?|Lu,*iU|h U@*@?_ L4T |ih,?} ?iih ?}A i N? iht |)Lu h 3L?@L 2 f feA UtL?c ~HD.2} t| bc2ffW?|hL_ U| L?wL _i?t |)T@h |) U iU!Ew# UL_it@hi@U*@tt Lu* ?i@h M*LU!UL_it U ThL _i?i@h U@T@U |)TihuLh4@?Ui L?@*@h}i UL**iU| L?Lu_@|@|h@?t4 tt L?@?_t|Lh@}i U @??i*t *i t 4 *|@?iL t*)@_4 || ?} 4T*i4i?|@M*i_iUL_iht w# UL_it ihi ht|ThLTLti_M)B@**@}ih ? t bSf_LU|Lh@*_ ttih|@| L?d o@?_ @t tU@hUi*)UL?t _ihi_ ?| i D)i@ht| @|uL**L i_ ?i?L|@M*i i UiT| L? t| i 4TLh|@?| Lh!Lu A@??ih ? bH d2o ? U A@??ih}i?ih@* 3i_ w# UL_it@?_ ?|hL_ Ui_@}h@T U@*hiThiti?|@| L?Lu w# UL_itc?L U@**i_A@??ih }h@T t A i t| _)Lu w# UL_it @t hit hhiU|i_ ?| i4 _ bbf<t | | i Lh!Lu @Uk@)c w M)c@?_L| iht d oc deoc dDo L?L| Ui_c@TT@hi?|*) ?_iTi?_i?|*)Lu| i Lh!Lu B@**@}ihc| i @_ @?|@}it Lu* ?i@h M*LU!UL_it U TLttitt tT@hti E*L _i?t |) T@h |) U iU!4@|h UitA t| |Lh @*U @T|ih ThL _it| i uL ?_@| L?t uLh| i t| _)@?_Th@U| Ui Lu w# UL_it `i **t|@h| | | i u ?_@4i?|@*hiThiti?|@| L?t Lu w# UL_it @T@h |) U iU!4@|h Uit @?_A@??ih}h@T t *@tt U@| L?Lu w# i?ti4M*it @A@??ih}h@T _i}hii_ t|h M | L?t **Mi ?|hL_ Ui_c M | i **L?*)t Tih U @**)UL ih| i_it }?Lu w# UL_it | LT| 4@* _i}hii_ t|h M | L?t @UL?t|h@ ?i_Tti _L h@?_L44@|h UL?t|h U| L? `i **@*tL hi i tL4i Lu| i L| ih w# UL_i UL?t|h U| L?|iU ? ^ it U @ i@TTi@hi_ ?| i* |ih@| hi A i i?UL_ ?}ThLM*i4uLh t U w# UL_it **Mi Thiti?|i_@?_Uih|@ ?tTiU @*U*@ttit Lu w# UL_it U hitL* i| i i?UL_ ?}ThLM*i4 **Mi ?|hL_ Ui_ 6 ?@**)c| i |ih@| i 4itt@}i T@tt ?}_iUL_ ?}@*}Lh | 4E@?_Uih|@ ?t 4T* U@| L?t U ThL _it?i@h LT| 4@* TihuLh4@?Ui **Mi Thiti?|i_ÆWklv zrun zdv ixqghg e|QVI judqwv FFU0<;477:5dqg FFU0<<:<643/QDVD judqw QDJ8043976/dqg d jliw iurp wkh LQVLF HKGU surjudp12 +iThiti?|@| L?t Lu w # L_it2 @|h +iThiti?|@| L?*| L } w# UL_it U@?Mi}i?ih@* 3i_|L?L? M ?@h)@*T @Mi|tc i t @**UL?t _ih L?*)M ?@h) w# UL_it uLh| i t@!i Lu t 4T U |) iU@ ti w# UL_it uLh4@U*@tt Lu* ?i@h M*LU!UL_itc | i)4@)Mi_itUh Mi_@t@Uih|@ ?& _ 4i?t L?@*t MtT@Ui F Lu| i iU|Lh tT@Ui I c2Lu M ?@h) ? | T*it L ih| i M ?@h) i*_I2 B i?| tc i4@) ?_@M@t t 'i}f c} c c}8Q j U tT@?t F tL| @|i@U U5F4@)Mi h ||i?@t U' f}f n } n n 8Q }8Q uLh tL4i i j( 4Lhi UL4T@U|*)c U' C ihi 'd f 8Q o@?_C t| i tL U@**i_& ?}i?ih@|Lh4@|h Lti hL t@hi| i iU|Lht i} j E@t t UL? i?| L?@* ?UL_ ?}c@** iU|Lht@hi hL iU|Lht A i E? & _ 4i?t L?@*? **tT@Ui F z Lu C UL4Th tit@** iU|Lht5I c2uLh U C e'f@?_ t tT@??i_M)| i M@t t z'i f c c c c Q8Q j A tc uLh i@U U5F c U e 'f uLh@** Lhc4Lhi UL4T@U|*)c U M e'f ihi M t| i tL U@**i_E? & ?T@h |) U iU!4@|h Lti hL t@hi | i iU|Lht i j c@?_ t| i}i?ih@|Lh4@|h uLh| i? **tT@Ui F z A i T@h |) U iU!4@|h M t tL?@4i_MiU@ ti |TihuLh4t6'? &tiT@h@|i T@h |)U iU!t L?@hiUi i_ Lh_ *L _i?t |)T@h |) U iU!UL_i t@* ?i@h M*LU!UL_i uLh U | i T@h |) U iU!4@|h M @t@*L _i?t |)Lu <t hi} *@h w# UL_i t@* ?i@h M*LU!UL_i Lti T@h |) U iU!4@|h M UL?|@ ?t i @U|*) <t ?i@U UL* 4?@?_i @U|*) o' E?*6 <t ?i@U hL c ihi 6Ei^ @*i?|*)c 6 A i UL_i h@|i-'&*? t hi*@|i_|L| iti T@h@4i|iht @ -' * o E| t@tt 4it M t u **h@?! Wu M t*L _i?t |)c M || i? 4Mih Lu <t ?i@U UL* 4?Lh hL t?L|UL?t|@?|c| i?| i UL_i t@? hhi} *@h w# UL_i W| t i@t it||L tii| i ti?ti ? U @?w# UL_i t hi} *@h Lh hhi} *@h| hL } |t}h@T U@*hiThiti?|@| L?2 2 Bh@T U@*+iThiti?|@| L?A@??ih UL?t _ihi_w# UL_it E@?_@}i?ih@* 3@| L? @?_t L i_ L | i)4@)Mi hiThiti?|i_ igiU| i*)M)@tL U@**i_M T@h| |i}h@T c?L U@**@A@??ih}h@T d2o A i A@??ih}h@T Lu@? w# UL_i t@?@*L}L t|L| i|hi** t Lu@UL? L* | L?@*UL_i ?| @| |ThL _it@UL4T*i|i hiThiti?|@| L?Lu| i UL_i@?_ |@ _t ?| i_itUh T| L?Lu| i_iUL_ ?}@*}Lh | 4 M T@h| |i }h@T t@}h@T E?L_it UL??iU|i_M)i_}it Lti?L_it4@)Mi tiT@h@|i_ ?|L| L|)Titc @?_i_}it4@)L?*)UL??iU|| L?L_it Lu_ gihi?||)Tit A i| L|)Tit Lu?L_it ?@A@??ih }h@T @hi| i @h @M*i?L_it@?_| i U iU!?L_it E U i t @**U@** ?L_it@?_U ?L_itc hitTiU| i*) A i A@??ih}h@T Lu@UL_i t_h@ ?@UULh_ ?}|L| i uL**L ?}h *iG U iU!?L_i t UL??iU|i_|L @h @M*i?L_i i?i ih i*i4i?| & ?M t@ ?i4@)_i_ Ui uhL4| t | @|| ihi@hi6'? &U iU!?L_itc L?i uLh i@U U iU!i^ @| L?c@?_? @h @M*i?L_itc L?i uLh i@U UL_i M |S 6 h| ihc| i6hL t Lu M tTiU u)| i6U ?L_i UL??iU| L?tc@?_| i? UL* 4?t Lu M tTiU u)| i? ?L_i UL??iU| L?t, @4T*i L?t _ih@E fc D * ?i@h M*LU!UL_i | '2@?_ o' E?*6 'e | | iWkh qrphqfodwxuh ydulhv lq wkh olwhudwxuh=yduldeoh qrghv duh dovr fdoohg elw ru v|pero qrghv dqg fkhfn qrghv duh dovr fdoohg ixqfwlrq qrghv1uL**L ?}M4@|h GM'59999997f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f6::::::8A i A@??ih}h@T ULhhitTL?_ ?}|L M t_iT U|i_ ?6 } Mtih i| @| ?L_it S f c S c S2c @?_S @hi UL??iU|i_|L U ?L_i s f ?@UULh_@?Ui | | i u@U|| @|c ?| i3ihL| hL Lu M c ff' f ' f2' f ' E@**L| iht@hi3ihL Mtih i| @|@?@*L}L t t | @| L?t L*_t uLh U ?L_it s c s2c s c@?_s e U ULhhitTL?_t|L hL t c2c c@?_e Lu Mc hitTiU| i*) L|ic@t uL**L t uhL4| i u@U|| @|U M e'f c| i M | @* it UL??iU|i_|L| i t@4i U iU!?L_i4 t|t 4 |L3ihL `i4@)@*tL ThLUii_@*L?}UL* 4?t|L UL?t|h U|| i A@??ih}h@T 6Lh i @4T*ic?L|i | @| ?L_i S f t UL??iU|i_|L U ?L_it s f@?_s ?@UULh_@?Ui | | i u@U|| @|c ?| i3ihL| UL* 4?Lu M c ff' f'L|i| @|| i A@??ih}h@T ?| t i @4T*i t hi} *@hG i@U ?L_i @t| L i_}i UL??iU| L?t @?_i@U U ?L_i @t uL h i_}i UL??iU| L?t E| @| tc| i_i}hii Lu i@U ?L_i t2@?_| i_i}hii Lu i@U U ?L_i t e A t t ?@UULh_@?Ui | | i u@U|| @| '2@?_ o'e Wt t@*tL U*i@h uhL4| t i @4T*i| @|6 o'?6Lh hhi} *@h w# UL_itc| i T@h@4i|iht @?_ o@hi u ?U| L?t Lu| i UL* 4?@?_hL ? 4Miht@?_tL t U ?L|@| L? t?L|}i?ih@**)@_LT|i_ ?| t U@ti W?t|i@_c | t t @* ? | i* |ih@| hi EuL**L ?}d.o |L tTiU u)| i ?L_i@?_U ?L_i_i}hii_ t|h M | L?TL*)?L4 @*t c _i?L|i_M)b E% @?_4E% c hitTiU| i*) W?| i TL*)?L4 @*b E% '['b % Q cb _i?L|it| i uh@U| L?Lu@**i_}it UL??iU|i_|L_i}hii _ ?L_it@?__ _i?L|it| i4@ 4 4 ?L_i_i}hii 5 4 *@h*)c ?| i TL*)?L4 @*4E% 'S['4 % Q c4 _i?L|it| i uh@U| L?Lu@**i_}it UL??iU|i_|L_i}hii _U ?L_it@?__ _i?L|it| i4@ 4 4 U ?L_i_i}hii L|i uLh| i hi} *@h UL_i@ML ic uLh U '_ '2@?_ o'_ 'ec i @ i b E% '%@?_4E% '%variable nodes2c 301c 465879f 0f 1f 2f 3f 4check nodes6 } A@??ih }h@T uLh i @4T*i UL_iU)U*i ELh *LLT Lu *i?}| D ?@A@??ih }h@T t @T@| UL4Th t ?}D i_}it U U*Ltit M@U!L? |ti*u A i A@??ih }h@T ?| i @ML i i @4T*i TLttittit @*i?}| S U)U*i @t i i4T* i_M)| i t ML*_i_}it ?| i } hi A i } h| Lu @A@??ih }h@T t | i 4 ? 4 4U)U*i *i?}| Lu | i }h@T A i t Lh|it|TLtt M*i U)U*i ?@M T@h| |i }h@T t U*i@h*)@*i?}| e U)U*ic @?_t U U)U*it 4@? uit|| i4ti* it ?| i M 4@|h @t uL h <t | @|* i L?| i ULh?iht Lu @t M4@|h Lu M `i @hi ?|ihit|i_ ?U)U*itc T@h| U *@h*)t Lh|U)U*itc MiU@ ti | i)_i}h@_i | i TihuLh4@?Ui Lu | i |ih@| i _iUL_ ?}@*}Lh | 4 ti_uLh w# UL_it A t u@U| **Mi 4@_i i _i?| ?| i _ tU tt L?Lu | i |ih@| i _iUL_ ?}@*}Lh | 4w# L_i #it }? TThL@U it*i@h*)c | i 4Lt|LM L t T@| |L | i UL?t|h U| L?Lu @?w# UL_i t @| i UL?t|h U| L?Lu @*L _i?t |)T@h |) U iU!4@|h | ThitUh Mi_ThLTih| it *@h}i ? 4Mih Lu _it }?|iU ? ^ it i t| ?| i * |ih@| hic @?_ i ?|hL_ Ui tL4i Lu | i 4Lhi ThL4 ?i?|L?it ?| t tiU| L?c @*Mi |@|@t Tih U @**i i* A i _it }?@TThL@U it |@h}i|_ gihi?|_it }?Uh |ih @c ?U* _ ?}i U i?|i?UL_ ?}@?__iUL_ ?}c ?i@h U@T@U |)TihuLh4@?Uic Lh *L ihhLh h@|i LLht Ew !i | hML UL_itc w # UL_it Lu|i?t gih uhL4*L ihhLh h@|i LLhtc L ?}ML| |L TLLh _ t|@?Ui tTiU|h@@?_ i@!?ittit ?| i |ih@| i _iUL_ ?}@*}Lh | 4 B@**@}ih L_itA i Lh } ?@*w# UL_it _ i |L B@**@}ih d o @hi hi} *@h w# UL_it | @?M 4@|h Lu | i uLh4M '599997M M 2 M %S6::::8ihi | i t M4@|h Uit M @ i | i uL**L ?}t|h U| hi 6Lh @?) ?|i}iht >@?_ o | @?}hi@|ih| @? c i@U t M4@|h M t > > o | hL i } | o @?_UL* 4? i } | A i t M4@|hM @t| i uL**L ?}tTiU U uLh4G uLh ' c2c c>c| i | hL UL?|@ ?t@**Lu |t o <t ? UL* 4?t E o n |L o A i L| ih t M4@|h Uit@hi t 4T*)UL* 4?Tih4 |@| L?t Lu M W| t i _i?|| @|M t hi} *@hc @t_ 4i?t L?> > o c@?_ @t hL @?_UL* 4? i } |t o@?_ c hitTiU| i*) A i@Mti?Ui Lu*i?}| e U)U*it ?M t?L|} @h@?|ii_c M || i)U@?Mi@ L _i_ @ UL4T |ih_it }?Lu M B@**@}ih t L i_| @|| i i?ti4M*i Lu t U UL_it @t i Ui**i?|_ t|@?Ui ThLTih| it ThL _i_ @?_ o: 6 h| ihc t U UL_it @ i*L UL4T*i |)i?UL_iht t ?Ui T@h |)M |t U@?Mi tL* i_uLh@t@u ?U| L?Lu| i tih M |t @| i T@h |) U iU!4@|h d o B@**@}ih UL_it ihi}i?ih@* 3i_M)A@??ih ? bH d2o@?_ ihi t| _ i_uLh@TT* U@| L?|L UL_i _ t L?4 *| T*i @UUitt UL44 ? U@| L?U @??i* ?dbo B@**@}ih UL_it ihi i |i?_i_M) @Uk@)@?_L| iht d oc deo2 @Uk@) L_it@Uk@) @_ ?_iTi?_i?|*)_ tUL ihi_| i Mi?i |t Lu_it }? ?}M ?@h)UL_it | tT@hti M 4@|h Uit@?_ @t| i ht||L t L | i@M * |)Lu| iti UL_it|L TihuLh4?i@h U@T@U |)* 4 |t d oc deo @Uk@) @t@hU i_L?@ iM T@}i d fo@*@h}i? 4Mih Lu w # UL_it i @t_it }?i_ uLh@TT* U@| L?|L_@|@UL44 ? U@| L?@?_t|Lh@}ic4Lt|Lu U @hi hi} *@h Oi ThL _i_ ? deo@*}Lh | 4t|L ti4 h@?_L4*)}i?ih@|i tT@hti M4@|h Uit ui Lu| iti@hi* t|i_Mi*L ? Lh_ih Lu ?Uhi@t ?}@*}Lh | 4UL4T*i |)EM |?L|?iUitt@h *) 4ThL i_TihuLh4@?UiM t Uhi@|i_M)h@?_L4*)}i?ih@| ?} i } | UL* 4?t@?_E@t?i@h@t TLtt M*i ? uLh4 hL i } |2 M t Uhi@|i_M)h@?_L4*)}i?ih@| ?} i } | UL* 4?tc *i i?t h ?} i } | o hL tc@?_?L| L UL* 4?t @ ?}L ih*@T}hi@|ih| @?L?iM t}i?ih@|i_@t ?2c T* t t Lh|U)U*it@hi@ L _i_e M t}i?ih@|i_@t ? c T* t M'd M M2o t UL?t|h@ ?i_tL| @|M2 t ? ih| M*i ELh@|*i@t|M t u **h@?!?i_h@ M@U!Lu @Uk@)UL_it t| @|| i)*@U!t U i?|t|h U| hi|L i?@M*i*L UL4T*i |) i?UL_ ?} ,?UL_ ?} t TihuLh4i_M)T || ?}M ?| i uLh4d e U o @B@ tt aLh_@?i* 4 ?@| L?c uhL4 U | i}i?ih@|Lh4@|h U@?Mi T | ?| i t)t|i4@| U uLh4C'd U o A i ThLM*i4 | i?UL_ ?} @C t| @|| i t M4@|h t}i?ih@**)?L|tT@hti tL| @|c uLh UL_it Lu*i?}| ?' fff Lh4Lhic i?UL_ ?}UL4T*i |) t } ?i U i?|i?UL_ ?}|iU ? ^ i i4T*L) ?}L?*) | i M4@|h @t ThLTLti_ ?dSoWhhi} *@h w# L_it+ U @h_tL?i|@* d.o@?_w M)i|@* dHo_i ?i_i?ti4M*it Lu hhi} *@h w# UL_it T@h@4i |ih 3i_M)| i_i}hii_ t|h M | L?TL*)?L4 @*t b E% @?_4E% @?_t L i_ L |L LT| 4 3i| iti TL*)?L4 @*t uLh@ @h i|)Lu U @??i*t T| 4@* |) t ?| i ti?ti| @|c@tt 4 ?}4itt@}i T@tt ?} _iUL_ ?}E_itUh Mi_Mi*L c@|)T U@*UL_i ?| i i?ti4M*i @t U@T@M*i Lu hi* @M*i UL44 ? U@ | L? ? Lhti U @??i*UL?_ | L?t| @?UL_it L |t _i| i i?ti4M*i@hi A i Lht| U@ti U @??i* UL?_ | L? t U@**i_| i_iUL_ ?}| hit L*_@?_| i LT| 4 3@| L?Lu b E% @?_4E% t uL ?_M)@ UL4M ?@| L?Lu@tL U@**i__i?t |)i L* | L?@*}Lh | 4@?_@?LT| 4 3@| L?@*}Lh | 4 #i?t |)i L* | L?hiuiht|L| i i L* | L?Lu| i ThLM@M * |)_i?t |)u ?U| L?t ET_u<t Lu| i @h L t^ @? | | it T@tti_@hL ?_| i_iUL_ih<t A@??ih}h@T A i_iUL_ ?}| hit L*_uLh@} i?b E% 4E% T@ h t_i|ih4 ?i_M)i @* @| L?| i T_u<t Lu UL4T |i_*L} * !i* LL_h@| Lt Etii| i?i |tiU| L? Lu| i UL_i M |t A i tiT@h@|i LT| 4 3@| L?@*}Lh | 4LT| 4 3it L ih| i b E% 4E% T@ ht Nt ?}| t@TThL@U @? hhi} *@h w# UL_i @t Mii?_it }?i_ Lti t 4 *@|i_TihuLh4@?Ui @t | ?f feD_ Lu| i U@T@U |)* 4 |uLh@M ?@h) ?T | `B U @??i*d o A t UL_i @_*i?}| ?' f.@?_h@|i-' *2 W| t}i?ih@**)|h i| @|_it }?t @_i?t |)i L* | L?@hi Mit|@TT* i_|L UL_it Lti h@|i t?L||LL } E- *e @?_ Lti*i?}| t?L||LL t Lh| E?z Dfff A i hi@tL? t| @|| i_i?t |)i L* | L?_it }?@*}Lh | 4@tt 4it?$4E i?Uic 6$4 c@?_tL b E% 4E% T@ ht U @hi LT| 4@*uLh ih)*L?}UL_itc **?L|Mi LT| 4@* uLh4i_ 4 *i?}| @?_t Lh|UL_it t_ tU tti_ ?d 2oc d oc d eoc d Doc t U b E% 4E% T@ ht @TT* i_|L4i_ 4 *i?}| @?_t Lh|UL_it} it h ti|L@ } ihhLh h@|i LLh6 ?@**)c i hi4@h!| @|c@t uLh| i @Uk@)UL_itc| iti hhi} *@h UL_it_L?L| ?|h ?t U@**) *i?_| i4ti* it|L i U i?|i?UL_ ?} OL i ihc@t4i?| L?i_@ML ic+ U @h_tL?@?_NhM@?!i dSo @ i ThLTLti_@*}Lh | 4t uLh@U i ?}* ?i@h | 4i i?UL_ ?}uLh| iti UL_ite 6 ? |i BiL4i|h) L_itW?d Soc d .oc hi} *@h w# UL_it@hi_it }?i_ t ?}L*_ u@t L?i_|i |MLL!d Ho|iU ? ^ it M@ti_ L? ? |i}iL4i|h it A i hit *| ?}w# UL_it u@** ?|L| i U)U* U@?_^ @t U)U* U U*@ttit Lu M*LU!UL_it@?_*i?_| i4ti* it|L t 4T*i i?UL_ih 4T*i4i?|@| L? @t u| hi} t|ih U hU |t A i U)U* U ? |i}iL4i|h)UL_it|i?_|L @ i hi*@| i*)*@h}i4 ? 4 4_ t|@?Uitc M || i^ @t U)U* U UL_it|i?_|L @ i tL4i @|t4@**4 ? 4 4_ t|@?Uit *tLc t Lh|w# UL_it E?L? | i Lh_ih Lu2ff M |t _it }?i_ t ?}| iti|iU ? ^ it@hi}i?ih@**)Mi||ih| @?t Lh|w# UL_it_it }?i_ t ?}Tti _L h@?_L4M4@|h UitA i U)U* U ? |i}iL4i|h)UL_it @ i| i_h@ M@U!| @|| i T@h |) U iU!4@|h ti_ ? _iUL_ ?} t? ? ?t|i@_Lu E? & ? EW| t TLtt M*i|L U LLti@?E? & ?t M4@|h Lu | i? ?4@|h |L_iUL_ic M || i*Ltt ?TihuLh4@?Ui t}i?ih@**)?L? ?i}* } M*i A i? ? 4@|h t U hU *@?|c | |t ht|hL i^ @*|L@Uih|@ ? ?U _i?Ui iU|L h d So ?L| ih_h@ M@U! t| @|| i @* it Lu o@?_ @hi hi*@| i*)*@h}i U t ?_it h@M*i t ?Ui| i UL4T*i |) Lu| i |ih@| i4itt@}i T@tt ?}_iUL_ih t ThLTLh| L?@*|L| iti @* it ?i ?@*_h@ M@U! t | @|| ihi t?L|@ i M * |) ?| i U L Ui Lu*i?}| @?_h@|ic@*| L } | t tt i U@?Mi_i@*| | M)UL_i t Lh|i? ?}@?_T ?U| h ?}D + c W+ c@?_iW+ L_it|)Ti Lu UL_ic U@**i_@hiTi@| @UU 4 *@|i E+ UL_ic U @t| i U @h@U|ih t| Ut Lu ML| tih @*| hML UL_it@?_w# UL_itc @t ThLTLti_ ?d2fo A i i?UL_ih uLh@?+ UL_i t t L ? ?6 } 2 ihi | t tii?| @| tih M |t@hi hiTi@|i_E2Lh | 4it t|)T U@* c Tih4 |i_c@?_ | i?ti?|| hL } @?@UU 4 *@|Lh E_ gihi?| @*i?UL_ih A iti UL_it @ i Mii?t L ?|L Mi U@T@M*i Lu LTih@| L??i@h U@T@U |)* 4 |tc M || i) @ i| i_h@ M@U!| @|| i)@hi?@| h@**) *L h@|i Eh@|i %2Lh*L ihA i+ UL_it ihi}i?ih@* 3i_ ?t U @ @)| @|tL4i M |t ihi hiTi@|i_4Lhi| @?L| iht ) i*_ ?} hhi} *@h hiTi@| @UU 4 *@|i EW+ UL_it d2 o t t L ? ?6 } 2c| i W+ i?UL_ih UL4Th tit@*L _i?t |)}i?ih@|Lh4@|h c@Tih4 |ihc@?_@?@UU 4 *@|Lh 5 U UL_it@hiU@T@M*i Lu LTih@| L?i i?U*Ltih |L | iLhi| U@** 4 |t | @?+ UL_itc @?_| i)Tih4 | } ih UL_i h@|it _h@ M@U!|L W+ UL_it t | @|| i)@hi ?L4 ?@**)?L? t)t|i4@| U UL_itc @*| L } | i)Mi T | ?@t)t|i4@| U uLh4c M | | t @|| i i Ti?ti Lu }hi@|*)*L ih ?}| i h@|i @t _iT U|i_ ?6 } 2v@?}@?_+)@?d oc d eoc d Do @ i ThLTLti_@U*@tt Lu i U i?|*)i?UL_@M*i hhi} *@h w# UL_it U 4 } |Mi U@**i_i |i?_i_W+ EiW+ UL_it EA iti UL_it ihi ?_iTi?_i?|*)ThLTLti_ ?d22o A i iW+ i?UL_ih t t L ? ?6 } 2 L|i | @|| i iW+ i?UL_ih t t)t|i4@| U @?_Tih4 |t ML| *L @?_ } h@|it 6 h| ihc i?UL_ ?}U@?Mi i U i?|*)TihuLh4i__ hiU|*)uhL4| i M 4@|h U TLttittit @?6 6t M4@|h U u@U * |@|it UL4T |@| L?Lu | i T@h |)M |t uhL4| i tih M |t d22oc d DoIRAeIRARA6 } 2 ,?UL_iht uLh | i hiTi@| @UUU 4 *@|i E+ c | i hhi} *@h + EW+ UL_ic @?_| ii |i?_i_W+ UL_i EiW+ S hh@) L_it6@? @t t L ?| @|@Uih|@ ?U*@tt Lu UL_it U@**i_@hh@)UL_it U@?Mi i i_@t w# UL_it @?_| t U@?Mi _iUL_i_ | @4itt@}i T@tt ?}@*}Lh | 4d2 oc d2eo 5 Mti^ i?||L 6@?<t Lh!c,*iu| ih L @?_ *U ih d2Do ThLTLti_@4L_ i_@hh@)UL_i i4T*L) ?}| i uL**L ?}M 4@|h uLh4@|M '599999997U U U U UUf U k k &Q 2k &Q k 8Q 2f f U k 2E &Q k 2E &Q 2k 2E 8Qf f f U k &Qk E &Q E 8Q &6:::::::8Eihi &@?_ @hi | L ?|i}iht t U | @|&c R ihi R _i?L|it @Th 4i ? 4Mih U t | i R R _i?| |)4@|h c | i R R ? **4@|h c @?_k @R R Tih4 |@| L?4@|h hiThiti?| ?}@t ?}*i*iu| Lh h } | U)U* U t u| A i TTih|h @?} *@h?@| hi Lu M} @h@?|iit i?UL_ ?}* ?i@h ?| i UL_i Lh_*i?}| Ei?UL_ ?} t itti?| @**)| i t@4i@t uLh iW+ UL_itA iti4L_ i_@hh@)UL_it @ i ih)*L ihhLh h@|i LLhtc@?_ML| *L @?_ } h@|i UL_it4@)Mi_it }?i_ OL i ihc@t t U*i@h uhL4| i_itUh T| L?Lu M@ML ic L?*)ti*iU|i_UL_i *i?}| t@?_h@|it@hi@ @ *@M*i. L4M ?@|Lh @*w# L_itW? i Lu| i u@U|| @|w# UL_it4@)Mi_it }?M)UL?t|h@ ?i_h@?_L4UL?t|h U| L?Lu M 4@|h Uitc | t?L|_ U *||L 4@} ?i| @|}LL_w# UL_it4@)Mi_it }?i_ @| i@TT* U@| L? Lu UL4M ?@|Lh @*4@| i4@| Ut A @| tc_it }?UL?t|h@ ?|t Et U @t?L U)U*it Lu*i?}| uL h @TT* i_|L@?M4@|h Lu t 3i E? & ?4@)Mi U@t|@t@ThLM*i4 ?UL4M ?@|Lh Ut 5i ih@* hiti@hU iht @ i t UUittu **)@TThL@U i_| t ThLM*i4 @t U UL4M ?@|Lh @*LM iU|t@t5|i ?ih t)t|i4tc k h!4@?t)t|i4tc@?_M@*@?Ui_ ?UL4T*i|i M*LU!_it }?t d2Soc d2.oc d2Hoc d2boc d Soe W|ih@| i#iUL_ ?} *}Lh | 4te ih iW?@__ | L?|L ?|hL_ U ?}w# UL_it ? t ti4 ?@* Lh! ? bSf d oc B@**@}ih@*tL ThL _i_ @_iUL_ ?}@*}Lh | 4| @| t|)T U@**)?i@h LT| 4@* 5 ?Ui| @|| 4ic L| ih hiti@hU iht @ i ?_iTi?_i?|*)_ tUL ihi_| @|@*}Lh | 4@?_hi*@|i_@*}Lh | 4tc@*Mi |tL4i| 4it uLh_ gih i?|@TT* U@| L?t deoc d fo A i@*}Lh | 4 |ih@| i*)UL4T |it| i_ t|h M | L?t Lu @h @M*it ? }h@T M@ti_4L_i*t@?_UL4it ?_ih_ gihi?|?@4itc_iTi?_ ?}L?| i UL?|i | A iti?@4it ?U* _iG| i t 4 ThL_ U|@*}Lh | 4E5 c| i Mi* iu ThLT@}@| L?@*}Lh | 4E c@?_| i 4itt@}i T@tt ?}@*}Lh | 4E A i|ih4R4itt@}i T@tt ?} t @**)hiuiht|L@**t U |ih@ | i@*}Lh | 4tc ?U* _ ?}| i5 E @?_ |t@TThL 4@| L?tU * !i LT| 4@*E4@ 4 4@TLt|ih Lh c t)4ML* M) t)4ML*_iUL_ ?}Lu|hi** t UL_itc i@hi ?|ihit|i_ ?UL4T | ?}| i@TLt|ih Lh ThLM@M * |)E | @|@} i?M | ?| i |h@?t4 ||i_UL_i Lh_U'd S f S S c Q o i^ @*t c} i?| i hiUi i_ Lh_)'d+f+ +c Q o ` | L |*Ltt Lu}i?ih@* |)c*i| t uLU t L?| i_iUL_ ?}Lu M |S tL| @| i@hi ?|ihit|i_ ? UL4T | ?}| ihE S ' m)Lh| i h@| L E@*tL U@**i_| i* !i* LL_h@| Lc w+,E S ] hE S 'f m) hE S ' m)w@|ih i **i |i?_| t|L| i4Lhi? 4ih U@**)t|@M*i UL4T |@| L?Lu| i*L} h@| Lc@*tL U@**i_| i*L} * !i* LL_h@| L Eww+ Gu E S ]*L}#hE S 'f m)$ihi ihi@?_ ?| i ti^ i*| i?@| h@**L}@h | 4 t@tt 4i_A i uLh| i UL4T |@| L?Lu hE S ' m) c,E S c Lh u E S t@? |ih@| i@*}Lh | 4 U t M@ti_L?| i UL_i<t A@??ih}h@T 5TiU U@**)c i 4@} ?i| @|| i ?L_it hiThiti?| ThLUittLht Lu L?i|)Tic U ?L_it hiThiti?|ThLUittLht Lu@?L| ih|)Tic@?_| i i_}it hiThiti?| 4itt@}i T@| t W?L?i @*u |ih@| L?c i@U ?L_i ThLUittit |t ?T |4itt@}it@?_T@ttit |t hit *| ?}L |T |4itt@}it T|L?i } MLh ?}U ?L_it E| L?L_it@hi t@ _|L Mi?i } MLht u| i) @hi UL??iU|i_M)@?i_}i A t t_iT U|i_ ?6 } uLh| i4itt@}i6Ãf2uhL4 ?L_i S f|L U ?L_i s2E| i t MtUh T|i_@hhL ?_ U@|it| i_ hiU| L?Lu| i4itt@}ic!iiT ?} ?4 ?_| @| L h A@??ih}h@T UL? i?| L?T*@Uit U ?L_it@ML i ?L_it A i ?uLh4@| L?T@tti_UL?Uih?t hE S f'K m ?T |4itt@}it c K5i f c j c| i h@| L Lu t U ThLM@M * | itc Lh| i*L}@h | 4Lu| i h@| L Lu t U ThLM@M * | it L|i ?| i } hi| @|| i ?uLh4@| L?T@tti_|L U ?L_i s2 t@**| i ?uLh4@| L?@ @ *@M*i|L ?L_i S f uhL4| i U @??i*@?_| hL } |t?i } MLhtc i U* _ ?}U ?L_i s2(| @| tc L?*)i |h ?t U ?uLh4@| L? t T@tti_ 5 U i |h ?t U ?uLh4@| L?6Ã & t UL4T |i_ uLh i@U UL??iU|i_ ?L_i%U ?L_i T@ h S *s&@|i@U @*u |ih@| L?f f f26 } 5 M}h@T Lu@A@??ih}h@T ULhhitTL?_ ?}|L@?M4@|h Lti3ihL| UL* 4? td f f foe A i@hhL t ?_ U@|i4itt@}i T@tt ?}uhL4?L_i S f|L?L_i s2W?| i L| ih @*u |ih@| L?c i@U U ?L_i ThLUittit |t ?T |4itt@}it@?_T@ttit |t hit *| ?} L |T |4itt@}it_L ?|L |t?i } MLh ?} ?L_it A t t_iT U|i_ ?6 } e uLh| i4itt@}i 6 fe uhL4U ?L_i s f_L ?|L ?L_i S e A i ?uLh4@| L?T@tti_UL?Uih?t hEU iU!i^ @| L?s f t t@| t i_m ?T |4itt@}it c K5i f c j c| i h@| L Lu t U ThLM@M * | itc Lh| i*L}@h | 4Lu| i h@| L Lu t U ThLM@M * | it L|ic@t uLh| i Thi L t U@tic L?*)i |h ?t U ?uLh4@| L? t T@tti_|L ?L_i S e 5 U i |h ?t U ?uLh4@| L?6 & t UL4T |i_uLh i@U UL??iU|i_U ?L_i% ?L_i T@ h @|i@U @*u |ih@| L?s&*Sf0 Array01246 } e 5 M}h@T Lu@A@??ih}h@T ULhhitTL?_ ?}|L@?M4@|h Lti3ihL| hL td f f f foe A i@hhL t ?_ U@|i4itt@}i T@tt ?}uhL4?L_i s f|L?L_i S eu|ih@ThitUh Mi_4@ 4 4? 4Mih Lu |ih@| L?t Lh@u|ih tL4i t|LTT ?}Uh |ih L? @t Mii? 4i|c| i_iUL_ih UL4T |it| i c| i w+c Lh| i ww+uhL4 U _iU t L?t L?| i M |t S @hi4@_i ?i i @4T*i t|LTT ?}Uh |ih L? t|L t|LT |ih@| ?} i? U O e'f c ihi U t@ |i?|@| i*)_iUL_i_UL_i Lh_A i @tt 4it| @|| i4itt@}it T@tti_@hi t|@| t| U@**) ?_iTi?_i?|| hL } L || i _iUL_ ?}ThLUitt ` i?| i+ @hi ?_iTi?_i?|c| t ?_iTi?_i?Ui@tt 4T| L? L *_ L*_|h i u| i A@??ih}h@T TLttitti_?L U)U*it 6 h| ihc| i L *_) i*_i @U| t ELh w+t Lh ww+tc_iTi?_ ?}L?| i iht L?Lu| i@*}Lh | 4 ?| t U@ti d fo OL i ihc uLh@}h@T Lu} h| c| i ?_iTi?_i?Ui@tt 4T| L? t L?*)|h i T|L| i *2 | |ih@| L?c@u|ih U 4itt@}it t|@h||L*LLT M@U!L?| i4ti* it ?| i}h@T <t @h L t U)U*it 5| **c t 4 *@| L?t @ i t L ? | @|| i4itt@}i T@tt ?}@*}Lh | 4 t}i?ih@**) ih)igiU| i ThL _i_*i?}| uL h U)U*it@hi @ L _i_ w ?i|@* d bo t L i_| @|tL4i UL? } h@| L?t Lu*i?}| uL h U)U*it@hi?L| @h4u * W| @t t L ? ?d o L | i4itt@}i T@tt ?}tU i_ *i_itUh Mi_@ML i@?_Mi*L E| i tL U@**i_ LL_ ?}tU i_ *i 4@)Mi4L_ i_|L4 | }@|i| i?i}@| i igiU|t Lu t Lh|U)U*it W?| i hi4@ ?_ih Lu| t tiU| L? i Thiti?|| i RThLM@M * |)_L4@ ? iht L?Lu| i5 E U UL4T |it t @?_ |t*L} _L4@ ? iht L?c| i*L} 5 E U UL4T |it ww+t c@t i**@t Uih|@ ?@TThL 4@| L?t h|hi@|4i?|UL?t _iht| i tTiU @*U@tit Lu| i M ?@h)ih@t hi U @??i*E , c| i M ?@h)t)44i|h U U @??i*E 5 c@?_| i M ?@h) ?T | `B U @??i* E W `Be 2 hLM@M * |) #L4@ ?5 #iUL_ih`i t|@h|M) ?|hL_ U ?}| i uL**L ?}?L|@| L?GT&'i ?L_it UL??iU|i_|L U ?L_i s&jT&q 'i ?L_it UL??iU|i_|L U ?L_i s&jqi ?L_i S j'i U ?L_it UL??iU|i_|L ?L_i S jq 'i U ?L_it UL??iU|i_|L ?L_i S jqi U ?L_i s&jE 'i4itt@}it uhL4@** ?L_it i UiT|?L_i S jE 'i4itt@}it uhL4@**U ?L_it i UiT|?L_i s&j' h E S ' m+7 'i i?|| @|| i U iU!i^ @| L?t ? L* ?}S @hi t@| t i_^ &E K ' h E S 'K m7 c+ c E c ihi K5i f c j 6Lh| i @*}Lh | 4Thiti?|*) ?_ih UL?t _ih@| L?c6Ã &'^ &E K (uLh| i w+@*}Lh | 4c6Ã &'^ &Ef *^ &E (@?_uLh| i ww+@*}Lh | 4c6Ã &'*L}d^ &Ef *^ &E oo& E K ' h EU iU!i^ @| L?s& t t@| t i_m S 'Kc E c ihi K5i f c j 6Lh| i @*}Lh | 4Thiti?|*) ?_ih UL?t _ih@| L?c6 & 'o& E K (uLh| i w+@*}Lh | 4c6 & ' o& Ef *o& E (@?_uLh| i ww+@*}Lh | 4c6 & '*L}d o& Ef *o& E oL|i | @|| i 4itt@}it ^ &E K c *i ?|ihThi|i_@t ThLM@M * | it ihic @hi h@?_L4 @h @M*it Eh <t @t | i)@hi u ?U| L?t Lu | i h <t + @?_L| ih 4itt@}it U @hi | i4ti* it h <t 5 4 *@h*)c M) h| i Lu | i 4itt@}i T@tt ?}@*}Lh | 4c | i 4itt@}it o & E K @hi h <tL?t _ih ?L | i uLh4Lu ^ &Ef U c } i?L h ?i ?L|@| L?@?_| i ?_iTi?_i?Ui @t t 4T| L?c i 4@)i Thitt @t Etii 6 } D^ &Ef ' h E S 'f m + c 7 c E'E h E 7 m S 'f c + c E * h E 7'g &E \& w ( F &o & EfEeihi i ti_ @)it<h *i | Ui |L LM|@ ?| i tiUL?_* ?i @?_| i ?_iTi?_i?Ui @tt 4T| L?|LLM|@ ?| i | h_* ?i 5 4 *@h*)c^ &E 'g &\& w ( F &o & E Ee 2A i UL?t|@?|t g &@hi U Lti?|L i?t hi | @|^ &Ef n ^ &E 'y if j6 } D W** t|h@| L?Lu 4itt@}i T@tt ?} @*u |ih@| L?uLh | i UL4T |@| L?Lu ^ &E K AL _i i*LT @?i Thitt L?uLh | i o & E K c i ?ii_| i uL**L ?}hit *|+it *| EB@**@}ih d o L?t _ih @ti^ i?Ui Lu ?_iTi?_i?|M ?@h)_ } |t @ uLh U h E @ ' 'R A i?| i ThLM@M * |)| @|i @ j ' UL?|@ ?t @?i i?? 4Mih Lu <t tn\D 'E 2R EehLLu G W?_ U| L?L?W? i Lu | t hit *|c |L}i| ih | | i ULhhitTL?_i?Ui R '^ &E c i @ i Etii 6 } So & Ef 'n\w FE 2^ &E Ee et ?Uic i?S 'f c | i M |t i S G 05T &q j 4 t|UL?|@ ?@?i i?? 4Mih Lu <t ?Lh_ih uLh U iU!i^ @| L?s &|L Mi t@| t i_ *i@h*)co & E ' o & EfEe Df jq ij6 } S W** t|h@| L?Lu4itt@}i T@tt ?} @*u |ih@| L?uLh| i UL4T |@| L?Lu o& E KA i uLh| i UL4T |@| L?Lu| i <t t ? | @* 3i_M)ti|| ?}^ &E K ' h E S 'K m+ uLh@** c uLh U &' E| @| tc^ &E ' @?_^ &Ef ' Oihic+ hiThiti?|t U @??i* t)4ML*| @| @t@U| @**)hiUi i_E i c | t@?L| @h @M*i ihi `i UL?t _ih| i uL**L ?} tTiU @*U@tit, W?| t U@tic+ 5i f c c.j ihi. t| i ih@t hi t)4ML*c@?_ i_i ?i B' hE+ ' .m S 'K |L Mi| i ih@t hi ThLM@M * |) A i? | t i@t)|L tii| @|h E S 'K m+ ';A?A=i?+ 'Kf i?+ 'K *2 i?+ '.ihi K hiThiti?|t| i UL4T*i4i?|Lu K5 W?| t U@tic+ 5i f c j@?_ i_i ?i0' hE+ 'K m S 'K |L Mi| i ihhLh ThLM@M * |) A i? | t LM L t| @|h E S 'K m+ '+0 i?+ 'K0 i?+ 'KW `B `i ht|*i|% ' 2S Mi| i | |h@?t4 ||i_M ?@h) @* i(?L|i% 'n E i?S 'fE `i t @** ti% @?_S ?|ihU @?}i@M*) ihi@u|ih A i?| i | hiUi i_t@4T*i t+ '% n? ihi| i? @hi ?_iTi?_i?|@?_?Lh4@**)_ t|h M |i_@t#Ef c j2 A i? | ti@t)|L t L | @|h E% '%m+ 'kn i T2+%*j2l Qihi%5i j5 44@h)Lu| i hLM@M * |) #L4@ ?5 #iUL_ih6Lh 'f c c c? c ti| ' h E S ' m+ ihi+ t| i | hiUi i_U @??i*t)4ML*A i?ti|^ &Ef ' @?_^ &E ' uLh@** c uLh U &'2 NT_@|i i o& E K j t ?}i^ @| L?t Ee e @?_Ee DNT_@|i i^& E K j t ?}i^ @| L?t Ee @?_Ee 2 5L* i uLh| i UL?t|@?|t g &e 6Lh 'f c c c? c UL4T |i' Ef 'g E\&w(o& Ef Ee S@?_' E 'g\&w(o& E Ee . ihi| i UL?t|@?|t g @hi U Lti?|L i?t hi| @|' Ef n' E 'D 6Lh 'f c c c? c ti|S '+u' E :' Ef f i*tiWu U O e'f Lh| i? 4Mih Lu |ih@| L?t i^ @*t| i4@ 4 4* 4 |c t|LT(i*tic}L|L5|iT 2+i4@h!t A t@*}Lh | 4 @t Mii?Thiti?|i_uLh Ti_@}L} U@*U*@h |)c M |4@)Mi@_ t|i_ |L LT| 4 3i| i? 4Mih Lu UL4T |@| L?t 6Lh i @4T*ic5|iT e4@)Mi UL4T |i_MiuLhi5|iT @?_5|iT 4@)Mi hiT*@Ui_ | | i t 4T*i_ t L?^ &E K 'g &' E K *o& E K `i?L|i@*tL | @|c uLh}LL_UL_itc| t@*}Lh | 4 t@M*i|L_i|iU|@? ?ULhhiU|i_UL_i Lh_ | ?i@h ? |) ThLM@M * |)E5|iT D c ?* !i| hML UL_it deoe wL} #L4@ ?5 #iUL_iht | | i ThLM@M * |) _L4@ ?V |ihM @?_ a+@*}Lh | 4tc| i ThLM@M * |) _L4@ ?5 t giht MiU@ ti4 *| T* U@| L?t@hi ? L* i_E@__ | L?t@hi*itt ULt|*)|L 4T*i4i?| @?_4@?)4 *| T* U@| L?t Lu ThLM@M * | it@hi ? L* i_ U UL *_MiUL4i? 4ih U@**) ?t|@M*i A tc@t | | i V |ihM @?_ a+@*}Lh | 4tc@*L} _L4@ ? iht L?Lu| i5 t|L Mi Thiuihhi_ AL _L tLc i ht|_i ?i| i uL**L ?}ww+tGu E S '*L}#h E S 'f m+ h E S ' m+$u E o& '*L}#o& Ef o& E$u E^ & '*L}#^ &Ef ^ &E$u E' '*L}#' Ef$A i ? | @* 3@| L?t|iTt uLh| i| hii U @??i*t ?_ih UL?t _ih@| L?| t MiUL4iGu E^ & 'u E S ';A?A=n4c+ 'f4c+ 'f c+ '.E , Ee Hu E^ & 'u E S 'E C *L} 0E 5u E^ & 'u E S '2+ *j2E W `B6Lh5|iT c i ht|hiT*@Ui o& Ef | o& E ?Ee D @?_hi@hh@?}i ||L LM|@ ?2o& E '\w FE 2^ &EL t ?}| i u@U|| @||@? k2*L}E R f*Rl'R f R ' 2R c i4@)hi h |i| i i^ @| L?@ML i@t|@?2u E o&'\w F|@?2u E^ &Ee bA i ThLM*i4 | | iti i Thitt L?t t| @| i@hi t| ***iu| | @ThL_ U|@?_| i UL4T*i |@? u ?U| L? `i U@?hi4i_)| t@t uL**L t d o 6 ht|c u@U|Lh u E^ & ?|L |t t }?@?_4@}? | _iGu E^ & 'k &q &k &'r }?d u E^ & oq &'m u E^ & mtL| @|Ee b 4@)Mi hi h ||i?@t|@?2u E o&'\w Fk &\w F|@?2q &`i| i? @ iu E o& '\k & 2|@? Q#\|@?q &$'\k & 2|@? Q *L}Q *L}#\|@?2q &$'\k & 2|@? Q *L}Q[*L}|@?2q &'\w F k &3C[w FE q &4D Ee fihi i @ i_i ?i_E% ' *L}d|@? E%*2 o'*L} e7n e7@?_ ti_| i u@U|| @| Q E% ' E% i?%:f A i u ?U| L? t u@ h*) i**Mi @ i_c@t t L ? ?6 } .c@?_tL4@)Mi 4T*i4i?|i_M)@*LL! T|@M*i6Lh5|iT2c i t 4T*)_ _i i^ @| L?Ee M)Ee 2 @?_|@!i| i*L}@h | 4Lu ML| t _it|L LM|@ ?u E^ & 'u E S n[& w( F&u E o& Ee 5|iT t t 4 *@h*)4L_ i_tL| @|u E' 'u E S n[&w(u E o& Ee 25 44@h)Lu| i wL} #L4@ ?5 #iUL_ih6Lh 'f c c c? c ? | @* 3i u E^ & @UULh_ ?}|L Ee H uLh@** c uLh U &'2 NT_@|i i u E o& j t ?}i^ @| L?Ee fNT_@|i i u E^ & j t ?}i^ @| L?Eee NT_@|i i u E' j t ?}i^ @| L?Ee 2D 6Lh 'f c c c? c ti|S '+u u E' f f i*tiWu U O e'f Lh| i? 4Mih Lu |ih@| L?t i^ @*t| i4@ 4 4* 4 |c t|LT(i*tic}L|L5|iT 2+i4@h! A t@*}Lh | 4U@?Mi t 4T* i_u h| ih uLh| i , @?_ 5 U @??i*t t ?Ui| i ? | @*ww+t Etii Ee H @hi|ih?@h) ?| i ht|U@ti@?_M ?@h) ?| i tiUL?_U@ti 5ii| i _ tU tt L?Lu| i4 ? t 4_iUL_ih Mi*L。
diffmatchpatch包的说明说明书

Package‘diffmatchpatch’October13,2022Type PackageTitle String Diff,Match,and Patch UtilitiesVersion0.1.0Date2021-04-10Copyright Google Inc.,Neil Fraser,Mike Slemmer,Sergey Nozhenko,Christian Leutloff,Colin RundelDescription A wrapper for Google's'diff-match-patch'library.It provides basic tools for computing diffs,finding fuzzy matches,and constructing/applying patches to strings. Encoding UTF-8Imports cli,RcppLinkingTo RcppRoxygenNote7.1.1License Apache License(>=2)URL https:///rundel/diffmatchpatchBugReports https:///rundel/diffmatchpatch/issues NeedsCompilation yesAuthor Colin Rundel[aut,cre],Google Inc.[cph](diff_match_patch.h),Neil Fraser[cph](diff_match_patch.h),Mike Slemmer[cph](diff_match_patch.h),Sergey Nozhenko[cph](diff_match_patch.h),Christian Leutloff[cph](diff_match_patch.h)Maintainer Colin Rundel<****************>Repository CRANDate/Publication2021-04-1607:00:05UTC1R topics documented:diff_make (2)dmp_options (4)match_find (5)patch_make (6)Index8 diff_make Compute diffs between text stringsDescriptionThe following functions are used to construct or work with diff(s)between text strings.Specifically, diff_make()computes the character level differences between the source string(x)and destination string(y).These diffs can be made more human friendly via a secondary cleaning process via the cleanup argument.Once computed,diffs are represented using diff_df data frames,which consist of just two columns: text and op.Basic convenience functions for pretty printing of these are provided by the package.The following helper functions are provided:•print()-prints a diff using ANSI colors if available.•as.character()-converts a diff(using ANSI colors if available)to a character vector.•diff_levenshtein()calculates the Levenshtein distance of a diff.•diff_to_delta()converts a diff to a delta string.•diff_from_delta()creates a diff from a source string(x)and a delta string.•diff_to_html()converts a diff to pretty HTML string.•diff_to_patch()converts a diff to a patch string.•diff_text_source()recovers the source string from a diff.•diff_text_dest()recovers the destination string from a diff.Usagediff_make(x,y,cleanup="semantic",checklines=TRUE)diff_levenshtein(diff)diff_to_delta(diff)diff_from_delta(x,delta)diff_to_html(diff)diff_to_patch(diff)diff_text_source(diff)diff_text_dest(diff)Argumentsx The source stringy The destination stringcleanup Determines the cleanup method applied to the diffs.Allowed values include: semantic,lossless,efficiency,merge and none.See Details for the behav-ior of these methods.checklines Performanceflag-if FALSE,then don’t run a line-level difffirst to identify the changed areas.If TRUE,run a faster slightly less optimal diff.Default:TRUE.diff A diff_df data frame.delta A delta string.DetailsCleanup methods:•semantic-Reduce the number of edits by eliminating semantically trivial equalities.•semantic lossless-Look for single edits surrounded on both sides by equalities which canbe shifted sideways to align the edit to a word boundary.e.g:The c at c ame.->The**cat**came.•efficiency-Reduce the number of edits by eliminating operationally trivial equalities.•merge-Reorder and merge like edit sections.Merge equalities.Any edit section can moveas long as it doesn’t cross an equality.•none-Do not apply any cleanup methods to the diffs.Value•diff_make()returns a diff_df data frame containing the diffs.•diff_make()returns the Levenshtein distance as an integer.•diff_to_delta()returns an character string.•diff_from_delta()returns a diff_df data frame.•diff_to_html()returns a character string.•diff_to_patch()returns a character string.•diff_text_source()returns a character string.•diff_text_dest()returns a character string.4dmp_optionsExamples(d=diff_make("abcdef","abchij"))diff_levenshtein(d)diff_to_html(d)diff_text_source(d)diff_text_dest(d)diff_to_patch(d)(delta=diff_to_delta(d))diff_from_delta("abcdef",delta)dmp_options diffmatchpatch settingsDescriptionAllows for examining or setting options that affect the behavior of the diff,match,and patch related functions in this package.Usagedmp_options(...)Arguments...No arguments returns all current options and their values.Character values re-trieve a subset of options and the current values.Options can be set,using name=value.However,only the options named below are used.Options can also bepassed by giving a single unnamed argument which is a named list.DetailsAvailable options:•diff_timeout(float)-Number of seconds to map a diff before giving up(0for infinity).•diff_edit_cost(int)-Cost of an empty edit operation in terms of edit characters.•match_threshold(float)-At what point is no match declared(0.0=perfection,1.0=veryloose).•match_distance(int)-How far to search for a match(0=exact location,1000+=broadmatch).A match this many characters away from the expected location will add1.0to thescore(0.0is a perfect match).match_find5•patch_delete_threshold(float)-When deleting a large block of text(over~64characters),how close does the contents have to match the expected contents.(0.0=perfection,1.0=very loose).Note that Match_Threshold controls how closely the end points of a delete needto match.•patch_margin(int)-Chunk size for context length.•match_max_bits(int)-The number of bits in an int.ValueWhen getting options returns a named list of options and their current values,when setting options returns a named list of the previous value(s).Examplesdmp_options()dmp_options("diff_timeout")prev=dmp_options(diff_timeout=5)prevmatch_find Fuzzy matching of a text stringDescriptionLocate the best instance of pattern in the text near loc using the Bitap algorithm.Returns-1if no match found.Assumes R’s typical1-based indexing for loc and the returned value.This algorithm makes use of the match_distance and match_threshold options to determine the match.If these values are not set explicitly via the threshold and distance arguments-their value will use the currently set global option value.Candidate matches are scored based on:a)the number of spelling differences between the pattern and the text and b)the distance between the candidate match and the expected location.The match_distance option determines the relative importance of these two metrics.Usagematch_find(text,pattern,loc=1L,threshold=NULL,distance=NULL) Argumentstext The text to search.pattern The pattern to search for.loc The expected location of the pattern.threshold Threshold for determining a match(0-perfect match,1-very loose).distance Distance from expected location scaling for score penalty.ValueIndex of best match or-1for no match.Examplesx="Lorem ipsum dolor sit amet,consectetur adipiscing elit,sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.Ut enim ad minim veniam,quis nostrudexercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.Excepteur sint occaecat cupidatat non proident,sunt in culpa qui officia deseruntmollit anim id est laborum."match_find(x,"Loren Ibsen")match_find(x,"Loren Ibsen",threshold=0.1)match_find(x,"minimum")match_find(x,"minimum",threshold=0.4)patch_make Create and apply patches to a text stringDescriptionPatches are constructed via patch_make()and applied using patch_apply().Usagepatch_make(x,y)patch_apply(x,patch)Argumentsx The source stringy The destination stringpatch A string representation of the patch(es).Valuepatch_make()returns a string representation of the patch(es).•patch_apply()returns the patched version of the string x,the matches attribute contains logical values indicating which patches were successfully applied.Examples(p=patch_make("abcdef","abchij"))patch_apply("abcdef",p)patch_apply("abc",p)patch_apply("def",p)patch_apply("hij",p)Indexdiff(diff_make),2diff_from_delta(diff_make),2diff_levenshtein(diff_make),2diff_make,2diff_text_dest(diff_make),2diff_text_source(diff_make),2diff_to_delta(diff_make),2diff_to_html(diff_make),2diff_to_patch(diff_make),2dmp_options,4match(match_find),5match_find,5patch(patch_make),6patch_apply(patch_make),6patch_make,68。
FullProf_详细使用教程

Rietveld refinement of complex inorganic materials using FullProf
(Extended version in tutorial form)
Juan Rodríguez-Carvajal Laboratoire Léon Brillouin (CEA-CNRS), CEA/Saclay FRANCE
Durban, August 24, 2003
ECM-21 Software Workshop
A program for analysis of diffraction patterns: FullProf
• A program for : Simulation of powder diffraction patterns Pattern decompositionÖ integrated intensities Structure refinement Powder and single crystal data Crystal and magnetic structures Multiple data sets: simultaneous treatment of several powder diffraction patterns (CW X-rays & neutrons, Energy dispersive X-rays, TOF neutron diffraction) Combined treatment of single crystal and powder data Crystal and magnetic Structure determination capabilities: simulated annealing on integrated intensity data
国外各行贸易商

Electronic Instruments Apparel,Health & Beauty,baby Chemical Equipment Sand
Personal Care
Perfumes, Skin Care, Snail Cream, Snail Gel, Snail Soap, Emu Oil, Nacre Shell Cream
公司名 SAEED AND SONS INTERNATIONAL
UP-FORMULA SDN BHD VASANT DIGNITY EXIM CORPORATION HABIB CARPETS (PVT) LTD BEAUTY OF LIFE LTD LEGEND INDIA'S IMPORT EXPORT LIMITED LTD
BMM TRADING
ASIASELLING PTE LTD
国籍 Indonesia Malaysia
Yemen Pakistan
China India
India India India Indonesia Jordanian
Vietnam Malaysia
USA MALAYSIA
INDIA
行业
主营产品
EFlsatvaoteu/rFalonodring
SNuaptuprlaielsE,sCsheenmtiaicl aOlilSso, uHrecrinbga,l ELoxgtriasctitcssA, LnadmNinaatuteral
FCroaagmraentciceand
Products, Cigerette Packaging Materials, Printing Inks,
Beauty/Personal Solid Timber Floor, Fuel Saver Additive, Bath Shower
hudi源码编译

hudi源码编译
编译Hudi源码是一个相对复杂的过程,需要一些基本的编程和系统知识。
下面是编译Hudi源码的一般步骤:
1. 首先,在你的开发环境中安装Java开发工具包 (JDK)。
确保你安装了正确的版本(例如,Java 8或Java 11),并且配置了JAVA_HOME环境变量。
2. 下载Hudi源码。
你可以从Hudi的官方GitHub仓库中获取源码。
请注意,GitHub仓库可能会根据发布的版本而有所不同。
选择相应的分支或标记下载源码。
3. 安装Maven。
Maven是一个用于构建Java项目的强大工具。
确保你安装了最新版本的Maven,并配置了MAVEN_HOME环境变量。
4. 进入Hudi源码的根目录,并使用终端或命令行窗口运行以下命令:
```shell
mvn clean install -DskipTests
```
这个命令会清理和构建整个项目,并跳过运行单元测试。
这个过程可能需要一些时间,因为它会下载所有必需的依赖项。
5. 如果编译成功,你将在输出的目录(通常是`/target`)中找到已编译的Hudi JAR文件。
这个JAR文件可以用于构建Hudi应用程序或在其他项目中使用Hudi。
请注意,编译Hudi源码需要一些系统和网络资源,并且可能因你的环境和网络状况而有所不同。
如果在编译过程中遇到问题,你可以查阅Hudi的官方文档或在开发社区寻求帮助。
Control of coleopteran insect pests through RNA interference
Control of coleopteran insect pests through RNA interferenceJames A Baum 1,Thierry Bogaert 2,William Clinton 1,Gregory R Heck 1,Pascale Feldmann 2,Oliver Ilagan 1,Scott Johnson 1,Geert Plaetinck 2,Tichafa Munyikwa 1,Michael Pleau 1,Ty Vaughn 1&James Roberts 1,3Commercial biotechnology solutions for controllinglepidopteran and coleopteran insect pests on crops depend on the expression of Bacillus thuringiensis insecticidalproteins 1,2,most of which permeabilize the membranes of gut epithelial cells of susceptible insects 3.However,insect control strategies involving a different mode of action would be valuable for managing the emergence of insect resistance.Toward this end,we demonstrate that ingestion of double-stranded (ds)RNAs supplied in an artificial diet triggers RNA interference in several coleopteran species,most notably the western corn rootworm (WCR)Diabrotica virgifera virgifera LeConte.This may result in larval stunting and mortality.Transgenic corn plants engineered to express WCR dsRNAs show a significant reduction in WCR feeding damage in a growth chamber assay,suggesting that the RNAi pathway can be exploited to control insect pests via in planta expression of a dsRNA.Eukaryotic organisms,including insects,possess a common machinery for sequence-specific gene silencing that is triggered by the presence ofdsRNA 4.This process is called RNA interference (RNAi)in animals 4and post-transcriptional gene silencing in plants 5.dsRNA-mediated silencing of essential genes in insects can induce cessation of feeding and ultimately morbidity,but requires efficient uptake of dsRNA either by feeding or by topical application.Ingestion of dsRNA can silence specific genes in the nematode Caenorhabditis elegans 6,7,planarian flatworms 8and ticks 9.Micro-injection of dsRNA into adults and late-instar larvae has been used to silence genes and study gene function in the coleopteran Tribolium castaneum 10,11.Similarly,dsRNA induced an RNAi response in the lepidopteran Spodoptera litura upon injection,but not after ingestion 12.In contrast,oral delivery of highly concentrated (4,000p.p.m.)dsRNA reduced target mRNA levels in the lepidopteran Epiphyas postvittana ,but did not cause mortality 13.T o assess coleopteran sensitivity to ingested dsRNAs,candidate target genes from several WCR cDNA libraries 14were selected (Sup-plementary Fig.1online)and dsRNAs prepared for testing in a WCR feeding assay.We reasoned that genes encoding proteins with essential functions would be the best RNAi targets for causing lethality.In theinitial bioassays,dsRNAs were applied to the surface of the WCR agar diet at concentrations from 520ng/cm 2to 780ng/cm 2.As we anticipated a slower response to dsRNAs than to B.thuringiensis insecticidal proteins,the WCR bioassay incubation period was extended from 5d to 12d.Indeed,7d after infestation,little if any effect was observed.However,numerous dsRNAs exhibited significant activity 12d after infestation,resulting in both larval stunting and mortality (Supplementary Table 1online).Subsequent feeding assays demonstrated that certain dsRNA sam-ples,including dsRNAs targeting putative genes encoding vacuolar ATPase (V-ATPase)subunit A,D and E,as well as a -tubulin,were active at applied concentrations well below 52ng/cm 2.We identified additional WCR genes that caused mortality when targeted for suppression using dsRNAs in the WCR feeding assay.A two-tiered screen was implemented in which dsRNAs targeting different genes were tested at 52and 5.2ng/cm 2.Of the 290dsRNAs tested,125showed significant (P o 0.05)larval mortality and/or stunting at 52ng/cm 2.Of these,67showed significant mortality and/or stunting at 5.2ng/cm 2.T o quantify this activity more precisely,we tested serial twofold dilutions of the most active dsRNAs in the WCR feeding assay to derive LC 50values,defined here as the concentration causing 50%mortality after 12d.Fourteen dsRNAs were identified that yielded LC 50values r 5.2ng/cm 2(Table 1),with the most active dsRNAs registering LC 50values near 0.52ng/cm 2.Concentration-response curves for several dsRNAs are shown in Supplementary Figure 2online.T o confirm that ingestion of dsRNA triggered a specific RNAi response in WCR larvae,we analyzed total RNA from dsRNA-fed and untreated larvae on northern blots to demonstrate downregulation of specific target genes.WCR larvae that ingested dsRNA directed against the V-ATPase A exhibited a dramatic suppression of the endogenous V-ATPase A mRNA within 24h of ingestion,with reduced mRNA levels apparent as early as 12h (Fig.1f ,0.5d).In contrast,levels of a -tubulin mRNA appeared unaltered in larvae that had ingested the V-ATPase A dsRNA (Fig.1e ).Likewise,WCR larvae that ingested the a -tubulin dsRNA exhibited a gradual suppression of the endogenous a -tubulin mRNA over 6d (Fig.1c ).The time course of V-ATPase A mRNA accumulation in these larvae resembled that of larvae fed a normal diet alone (Fig.1d ),indicating specific suppression of theReceived 15June;accepted 10October;published online 4November 2007;doi:10.1038/nbt13591MonsantoCompany,700Chesterfield Parkway West,Chesterfield,Missouri 63017-1732,USA.2Devgen N.V .,Technologiepark 30,B-9052Ghent–Zwijnaarde,Belgium.3Correspondenceshould be addressed to J.R.(james.k.roberts@).©2007 N a t u r e P u b l i s h i n g G r o u p h t t p ://w w w .n a t u r e .c o m /n a t u r e b i o t e c h n o l o g ya -tubulin mRNA.Northern blot analyses for other gene targets confirmed the specificity of suppression of the targeted mRNAs by dsRNAs,including targets that do not cause mortality when silenced (Supplementary Fig.3online).Although suppression of targeted mRNAs could be observed by northern blot analysis within 1d of exposure to dsRNAs included in an artificial diet,gross effects on larval growth and development were not immediately apparent.At applied concentrations of 52ng/cm 2,even the best WCR dsRNAs had little visible effect on rootworm larvae after 7d of exposure.Measurements of larval mass over time indicated significant mass reduction compared to the untreated control after only 3d of feeding (data not shown).The small amounts of dsRNArequired for gene silencing and larval mortality suggest an amplifica-tion pathway in which ingested dsRNAs are processed to siRNAs,presumably within insect gut epithelial cells,which may prime the synthesis of more abundant secondary siRNAs,as has been proposed for C.elegans 6.Northern blot analysis of total RNA from whole WCR larvae revealed almost complete suppression of targeted transcripts from several housekeeping genes (Fig.1),suggesting systemic spread of silencing beyond gut epithelial cells,the presumed initiation site of the RNAi response.The requirement for amplification and systemic spread could account in part for the time-lag between the gene silencing event and larval death.Although a search of the WCR-expressed sequence tag data set failed to identify an RNA-dependent RNA polymerase that would presumably be required for the amplification step as it is presently understood,this may be due to the incomplete nature of the data set.Orthologs of the C.elegans sid-1gene,responsible for systemic spread of dsRNAs in C.elegans 15,have been identified in insects such as T.castaneum ,Bombyx mori and Apis mellifera 16.A partial sid-1-like sequence was identified in the WCR data set but has not been demonstrated to function in RNAi.Three other coleopteran species were tested for their sensitivity to dsRNAs in diet.WCR dsRNAs targeting putative b -tubulin,V-ATPase A and V-ATPase E orthologs (Supplementary Table 1)were observed to cause significant (P o 0.05)larval mortality whentested in a bioassay with the southern corn rootworm,Diabrotica undecimpunctata howardii (Supplementary Fig.4online).Likewise,dsRNAs targeting the V-ATPase A and V-ATPase E orthologs each caused significant larval mortality in the Colorado potato beetle (CPB;Leptinotarsa decemlineata )bioassay (Supplementary Fig.5online).T o extend these observations,we cloned the orthologous V-ATPase A and V-ATPase E sequences of CPB and used them as templates for dsRNA synthesis.The V-ATPase A target sequences from CPB and WCR share 83%nucleotide-sequence identity (Supplementary Fig.6online)whereas the V-ATPase E target sequences from these organisms share 79%nucleotide-sequence identity (Supplementary Fig.7online).As expected,the CPB dsRNAs appeared more active than the orthologous WCR dsRNAs in the CPB assay (Supplementary Fig.5).More specifically,the CPB V-ATPase A dsRNA yielded an LC 50value of 5.2ng/cm 2in the CPB bioassay,whereas the orthologous WCR dsRNA yielded a LC 50value 452ng/cm 2a greater than tenfold difference in activity that can be attributed to divergence in target sequence.An appealing aspect of gene silencing for pest control is its potential for selectivity based entirely on nucleotide-sequence identity.However,other barriers to oral toxicity certainly exist.For instance,larvae of the cotton boll weevil,Anthonomus grandis boheman,showed no effects on mortality or mass upon ingestion of dsRNAs prepared using the orthologous boll weevil target gene sequences compared to control.This lack of response may result from the particular feeding physiology of the boll weevil,behavioral factors such as burrowing into the diet,or might indicate that some,but not all,coleopteran larvae are sensitive to orally delivered dsRNAs.dsRNAs were prepared from contiguous sections of the full-length 1,842base pair (bp)V-ATPase A coding region (Supplementary Fig.8online)and tested for differences in activity in the WCR bioassay.Six dsRNAs of B 300base pairs (bp)showed activity comparable to the full-length dsRNA,with no individual section yielding a superior target sequence.Additional sectioning experiments demonstrated that dsRNAs as small as 134bp retained activity in the feeding assay.T o test whether corn plants expressing a WCR-derived dsRNA were protected from rootworm feeding damage,we assembled a section of the putative V-ATPase A coding region from WCR into a corn transfor-mation expression cassette designed to express dsRNA targeting a small section (246bp)of the WCR gene (Supplementary Fig.9online).The expression cassette (Fig.2a )consisted of the CaMV e35S promoter 17,a maize heat shock protein (hsp)70intron 18,the region of the V-ATPase A gene designed to assemble into a dsRNA upon expression,and the wheat hsp173¢untranslated region 18.This expression cassette was combined with a plant selectable marker gene that confers tolerance to glyphosate and placed into an Agrobacterium tumefaciens plant transformation vector to give theTable 1LC 50values determined from the WCR feeding assayPlasmid Nearest ortholog a AnnotationLC 50b pMON101053F38E11_5Putative COPI coatomer,b ¢subunit c 0.57pMON102873CG6223Putative COPI coatomer,b subunit c 0.73pMON78428CG8055Putative ESCRT III_Snf7ortholog c1.20pMON78416CG11276Putative ribosomal protein S4ortholog c1.30pIC16005CG2934-PA Putative v-ATPase D subunit 1ortholog d 1.72pIC17504CG3762Putative v-ATPase A subunit 2ortholog d 1.82pMON78412CG3416Putative mov34ortholog (proteosome)c1.98pMON98445F37C12_9Putative ribosomal protein rps-14ortholog c2.60pMON101120M03F4.2Putative actin ortholog c2.86pMON96168CG2331Putative apple ATPase ortholog c4.16pMON102861CG12770Putative ESCRT I_Vps28ortholog c4.47pMON78424CG6141Putative ribosomal protein L9ortholog c5.20pMON78425CG2746Putative ribosomal protein L19ortholog c 5.20pIC17503CG1913-PA Putative alpha tubulin ortholog d 5.20pMON78440CG3180Putative RNA polymerase II ortholog c 7.80pMON102865CG14542Putative ESCRT III_vps2ortholog c11.96pMON30694CG9277Putative beta tubulin ortholog d51.98a CGorthologs are from D.melanogaster ,all others are from C.elegans.b LC 50values in ng dsRNA/cm 2.c Identified as part of the Monsanto Devgen collaborative research agreement.d Sequence identified and tested by Monsanto.0.5eProbe:Day:0.5121246a α-tubulinV-ATPase 46c fb d Figure 1Suppression of target mRNA in WCR.(a –f )Neonates were allowed to feed for 0.5–6d on an artificial diet (a ,b )or the same diet containing 52ng/cm 2dsRNA derived from a -tubulin (c ,d )or V-ATPase A (e ,f )sequences,respectively.mRNA abundance in larvae was determined by northern blot analysis using a -tubulin or V-ATPase A probes.©2007 N a t u r e P u b l i s h i n g G r o u p h t t p ://w w w .n a t u r e .c o m /n a t u r e b i o t e c h n o l o g yplasmid pMON94805.pMON94805maize transformants were trans-ferred to soil 19and backcrossed with an inbred line to generate F 1hybrid progeny.F 1hybrid plants from each cross containing one or two copies of the expression cassette,as checked by a quantitative PCR assay (data not shown),were evaluated using a growth chamber assay to assess rootworm feeding damage.Pots containing plants at the four-leaf stage were infested with B 1,000WCR eggs in the root zone.Emerging larvae were allowed to feed on the roots for 3weeks,after which the plants were removed from the soil and rated for larval feeding damage 20.Similar hybrid plants expressing the Cry3Bb protein of B.thuringiensis 2showed excellent root protection in the pot assay,providing a useful benchmark for efficacy.Progeny from several pMON94805F 1crosses showed obvious reductions in root damage when compared to the control hybrid line as evidenced by the low nodal injury scores (Fig.2b )and healthy root masses (Fig.2c ).Progeny from one of the eight F 1crosses scored at or lower than the accepted economic threshold nodal injury score of 0.25(ref.20).T o further characterize the different transgenic F 1hybrids used in this WCR feeding assay,we extracted RNA from individual plants for northern blot analysis.Transgenic events containing detectable RNA corresponding to the dsRNA construct expressed both the full-size transcript and small 21-bp siRNAs processed from the larger dsRNA (Fig.3a ,c ).RNA corresponding to the dsRNA construct was not detected in plants with the highest nodal injury scores (event numbers 1and 2).Similar results have been obtained with transgenic corn plants targeting other WCR genes,including feeding assays withisolated transgenic root tissue demonstrating severe larval stunting (Supplementary Fig.10online).The ability to trigger RNAi in coleopterans by oral delivery of dsRNAs has obvious commercial implications.RNAi provides a unique mode of action for the control of insect pests that could complement the current strategy of expressing B.thuringiensis (Bt )insecticidal proteins in crops such as corn,cotton and soybeans.As larvae of the WCR and related Diabrotica species are devastating pests of corn in the United States 21and are refractory toward most Bt insecticidal proteins,it is especially noteworthy that WCR is sensitive to an oral RNAi approach.Accordingly,RNAi has the potential to increase both the efficacy and durability of insect-protected crops designed to control this important coleopteran pest.METHODSDNA and RNA manipulations.WCR cDNA libraries were prepared from whole larvae harvested at either the 1st instar stadium or the 2nd –3rd instar stadium.RNA was extracted using TRIzol reagent (Invitrogen)and Poly A+RNA was isolated from the total RNA prep using Dynabeads Oligo dT (Dynal)following the manufacturers’instructions.A cDNA library was constructed from the Poly A+RNA using the SuperScript Plasmid System (Invitrogen).cDNA was size-fractionated using chromatography.The fourth and fifth fractions were collected and ligated into the pSPORT1vector (Life T echnolo-gies)between the Sal 1and Not 1restriction endonucleases recognition sites,and used to transform E.coli DH10B electro-competent cells by electroporation.Likewise,high molecular weight cDNA libraries from 1st instars and pooled 2nd -3rd instars were made from 20micrograms of Poly A+RNA using the SuperScript Plasmid System (Invitrogen).The cDNA was size fractionated on a 1%agarose gel in TAE,and cDNA between the range of 1Kb to 10Kb was collected and ligated into the pSPORT1vector in between the Sal 1and Not 1restriction sites and transformed into E.coli DH10B electro-competent cells by electroporation.Sequencing was performed using Applied Biosystems capillary sequencers.Insect gene sequences were amplified from either genomic DNA orV-ATPase ANon-transgenic corn Transgenic cornM e a n n o d a l i n j u r y s c o r eE ve n t 1E ve n t 2E ve nt 3E ve nt 4E ve n t5E ve n t 6E ve n t7E ve n t8Mo n 863Ne g . co n t r olabcFigure 2F1plants expressing a V-ATPase A dsRNA are protected from WCR feeding damage.(a )Map of the expression cassette.(b )Mean root damage ratings for eight F 1populations,the parental inbred line (negative control)and the corn rootworm–protected Cry3Bb event MON863;NIS,nodal injury score (Iowa State ranking system).(c )The plant on left is a non-transgenic control with average root damage,whereas the plant on the right shows the average root protection seen when the transgene is expressed.N e g a t i v e c o n t r o l E v e n t 1E v e n t 2E v e n t 3E v e n t 4E v e n t 5E v e n t 6E v e n t 7E v e n t 81.35 kb0.24 kb24 nt21 ntmiR159LMWEtBr stainedHMWabc dFigure 3Northern blot analysis of large and small RNAs produced by F 1plants expressing the V-ATPase A dsRNA transcript.(a –d )Individual plants from different transgenic events were infested with WCR and RNA was extracted from roots after scoring for damage.The full-length transcript from the WCR V-ATPase cassette accumulates in events 3–8(a ).Ethidium bromide–stained ribosomal RNA provided a loading control (b ).Those events where the full-size transcript is present also contained small RNAs ofabout 21base pairs (c ).The small RNA blot was stripped and reprobed for maize miR159to confirm equal loading (d ).There was no large or small RNA from the WCR V-ATPase cassette in events 1and 2,which had the most root damage.©2007 N a t u r e P u b l i s h i n g G r o u p h t t p ://w w w .n a t u r e .c o m /n a t u r e b i o t e c h n o l o g yfrom cDNA using Taq DNA polymerase and the amplicons cloned into pCR2.1-TOPO or pCR4-TOPO (Invitrogen)for sequence confirmation.Amplified DNA framents flanked by T7polymerase promoter sequences served as the template for dsRNA synthesis using the MEGAscript kit and recom-mended procedures (Ambion).Alternatively,dsRNAs were prepared using the T7RiboMAX Express RNAi system and protocols (Promega).Purified dsRNAs were quantified by spectroscopy and examined by agarose gel electrophoresis to ensure their integrity.Target gene sequences from CPB and the cotton boll weevil were amplified from larval cDNA using Taq polymerase and degenerate primers designed from the alignment of the WCR target sequences with putative orthologs from several insect species.The putative V-ATPase A subunit 2ortholog sequences were amplified using primers pr550(5¢-GGTGA CATGGCCACCATCCAGGT-3¢)and pr552(5¢-ACCCCAGAACACCTGYACR ATACC-3¢).The putative V-ATPase E ortholog sequences were amplified using primers pr591(5¢-ATCATGGART ACTAYGARAARAARGAG-3¢)and pr592(5¢-GTTGCGWCCGAASAGMGCVT TWCGGATCTSSGG-3¢).Amplified DNA fragments were cloned into pCR2.1-TOPO and confirmed by DNA sequencing.Primers pr568(5¢–TTAATACGACTCACTATAGGGAGACCAGT GTGCTGGAATTCGCC-3¢)and pr569(5¢-TTAATACGACTCACTATAGGGAG AGGATATCTGCAGAATTCGCC-3¢)were used as universal primers to amplify inserts cloned into pCR2.1,resulting in DNA templates containing flanking T7RNA polymerase promoters suitable for in vitro synthesis of dsRNAs.Insect bioassays.Varying doses of dsRNA were applied as an overlay to corn rootworm artificial diet according to the following procedure.Diabrotica virgifera virgifera (WCR)eggs were obtained from Crop Characteristics.The non-diapausing WCR eggs were incubated in soil for about 13d at 251C,60%relative humidity,in complete darkness.On day 13the soil containing WCR eggs was placed between no.30and no.60mesh sieves and the eggs were washed out of the soil using a high-pressure garden hose.The eggs were surface disinfested,rinsed and dispensed onto sterile coffee filters and hatched overnight at 251C,60%relative humidity,in complete darkness.Insect diet was prepared essentially according as described 22.Twenty microliter volumes of test samples containing either control reagents or dsRNA in varying quantities were over-layed onto the surface of the insect diet.One WCR neonate larva was deposited to each well with a fine paintbrush.Plates were then sealed with mylar and ventilated using an insect pin.Twelve to 72insect larvae were tested per dose,depending on the design of the assay.The bioassay plates were incubated at 271C,60%relative humidity in complete darkness for 12–14d.The number of surviving larvae per dose was recorded at the 12–14d time point.Data were analyzed using JMP4statistical software (SAS Institute,1995)and a full factorial ANOV A was conducted with a Dunnet’s test to look for treatment effects compared to the untreated control (P o 0.05).A Tukey-Kramer post hoc test was performed to compare all pairs of the treatments (P o 0.05).Bioassays with the southern corn rootworm (SCR),Diabrotica undecimpuc-tata howardii ,were conducted in a similar manner using insects purchased from Crop Characteristics.SCR eggs were incubated in soil for 6d at 251C,60%relative humidity,in complete darkness.On day 6,the soil containing SCR eggs was placed between no.30and no.60mesh sieves and the eggs were washed out of the soil using a high-pressure garden hose.The eggs were surface disinfested,rinsed and suspended in a 0.2%agar solution.SCR diet was prepared as previously desribed 23.Twenty (20)microliter volumes of test samples containing either control reagents or dsRNA in varying quantities was overlayed onto the surface of the insect diet.Plates were allowed to dry before adding insect eggs suspended in 0.2%agar as described above,and were again allowed to dry to remove the water from the 0.2%agar.Plates were then sealed with mylar and ventilated using an insect pin.Twelve to 72wells containing insects were tested per dose depending on the design of the assay.The bioassay plates were incubated at 271C,60%relative humidity in complete darkness for 12–14d.The number of surviving larvae per dose was recorded at the 12-to 14-d time point.Data were analyzed using JMP4statistical software and a full factorial ANOV A was conducted with a Dunnet’s test to look for treatment effects compared to the untreated control (P o 0.05).A Tukey-Kramer post hoc test was performed to compare all pairs of the treatments (P o 0.05).Bioassays with the CPB were conducted using an artificial diet consisting of 13.2g/l agar,140.3g/l Bio-Serve pre-mix,5ml/l KOH (18.3%wt/wt),and1.25ml/l formalin (37%).The diet was dispensed in 200-m l aliquots into 96-well plates and dried briefly before sample application.We applied 20m l of test sample per well,with sterile water serving as the untreated check.Plates were allowed to dry before adding insect larvae.CPB larvae were obtained from the New Jersey Department of Agriculture.One neonate CPB larva was added per well with a fine paintbrush.Plates were sealed with mylar and ventilated using an insect pin.Forty larvae were tested per treatment.The bioassay plates were incubated at 271C,60%relative humidity,in complete darkness for 10–12d.The plates were scored for larval stunting and mortality.Data were analyzed using JMP4statistical software.Plant cloning vectors and transformation.Transgenic corn plants were generated by Agrobacterium -mediated transformation of corn embryos as previously described 19.Initial transgenic (R0)plants were selected on medium containing glyphosate and were tested by PCR for the presence of the transgene.Plants containing a single copy of the transgene were selfed and pollen used to make hybrids (F 1)by crossing with a complementary genotype.The resulting hybrids were used in corn root feeding assays.Northern blot analysis.T otal RNA was extracted from rootworm larvae using the mir Vana miRNA isolation kit (Ambion)according to manufacturer’s instructions.T en micrograms of total RNA was loaded per lane,blotted and probed as described 24,except Dig Easy Hyb (Roche)was used as a hybridization buffer at 421C and final wash of 0.1ÂSS,0.1%SDS was performed at 651C.Probe (section 4,Supplementary Fig.2)for the detection of the V-ATPase A transcript was labeled with 32P-dCTP using the RadPrime DNA Labeling System (Invitrogen).The entire a -tubulin cDNA (PIC17503,Supplementary Fig.1)was used as probe after amplification with vector primers flanking the clone and labeling with 32P-dCTP .Hybridization signals were visualized with BioMax MR film (Kodak).RNA from corn plants was extracted with Trizol (Invitrogen)and 10m g of total RNA was loaded per lane.Small RNA gels were run as previously described 25and the maize miR159probe (CaGaGCTCCCTT CaaTCCaaa)was end-labeled 24with 32P ATP .Whole plant feeding assays.Transgenic corn plants (F 1)generated using pMON94805were planted into 10inch pots containing Metromix soil after reaching an appropriate size.When plants reached the V4growth stage,B 1,000WCR eggs were infested into the root zone.Non-transgenic corn of the same genotype was infested at a similar growth stage to serve as a negative control.Eggs were pre-incubated so hatch would occur within 24h of rvae were allowed to feed on the root systems for 3weeks.Plants were removed from the soil and washed so that the roots could be evaluated for larval feeding.Root damage was rated using the Iowa State nodal injury scale to score the level of damage where 0indicates no damage,1indicates that one node of roots was pruned to within 1.5inches,2indicates that two nodes were pruned,and 3indicates that three nodes were pruned 20.Corn root feeding assays.Transformed roots expressing a -tubulin dsRNA were fed to WCR larvae.Transgenic corn roots were maintained in Petri dishes with MSOD medium containing the antibiotics and glyphosate for in vitro selection.Two WCR larvae were infested per root in each dish with a fine tip paint brush.The dishes were sealed with Parafilm to prevent the larvae from escaping.The assays were placed in a 271C,60%relative humidity Percival incubator in complete darkness.Contamination and larval quality were monitored.After 6d of feeding on root tissue,the larvae were transferred to an artificial diet in a 96-well plate.The larvae were allowed to feed on the diet for an additional rval mass and survivorship were recorded for analysis.A one-way analysis was performed on the larval mass data and a Dunnett’s test for statistical significance compared to LH244,an untransformed negative control.Note:Supplementary information is available on the Nature Biotechnology website.ACKNOWLEDGMENTSWe are grateful to Tom Adams,Claire CaJacob and Steve Padgette for their support and helpful discussions;Wendy Maddelein and Steffy Denorme for molecular cloning support and dsRNA preparations;David Kovalic,Wei Wu,Marc Logghe and Irene Nooren for bioinformatics support;Robin Camp and©2007 N a t u r e P u b l i s h i n g G r o u p h t t p ://w w w .n a t u r e .c o m /n a t u r e b i o t e c h n o l o g yShubha Subbarao for assistance with plant feeding assays;Tim Coombe,Barbara Wiggins,Heidi Windler and Rich Yingling for corn transformation,propagation and analysis.COMPETING INTERESTS STATEMENTThe authors declare competing financial interests:details accompany the full-text HTML version of the paper at /naturebiotechnology/.Published online at /naturebiotechnology/Reprints and permissions information is available online at /reprintsandpermissions1.James,C.Global review of commercialized transgenic crops.Curr.Sci.84,303–309(2003).2.Vaughn,T.et al.A method of controlling corn rootworm feeding using aBacillus thuringiensis protein expressed in transgenic maize.Crop Sci.45,931–938(2005).3.Rajamohan,F .,Lee,M.K.&Dean,D.H.Bacillus thuringiensis insecticidal proteins:Molecular mode of action.in Progress in Nucleic Acid Research and Molecular Biology 60,1–27(1998).4.Hannon,G.J.RNA interference.Nature 418,244–251(2002).5.Baulcombe,D.RNA silencing in plants.Nature 431,356–363(2004).6.Fire,A.et al.Potent and specific genetic interference by double-stranded RNA inCaenorhabditis elegans .Nature 391,806–811(1998).7.Timmons,L.&Fire,A.Specific interference by ingested dsRNA.Nature 395,854(1998).8.Newmark,P .A.,Reddien,P .W.,Cebria,F .&Alvarado,A.S.Ingestion of bacteriallyexpressed double-stranded RNA inhibits gene expression in A 100,11861–11865(2003).9.Soares,C.A.G.et al.Capillary feeding of specific dsRNA induces silencing of the isacgene in nymphal Ixodes scapularis ticks.Insect Mol.Biol.14,443–452(2005).10.Bucher,G.,Scholten,J.&Klingler,M.Parental RNAi in Tribolium (Coleoptera).Curr.Biol.12,R85–R86(2002).11.Tomoyasu,Y.&Denell,rval RNAi in Tribolium (Coleoptera)for analyzing adultdevelopment.Dev.Genes Evol.214,575–578(2004).12.Rajagopal,R.,Sivakumar,S.,Agrawal,N.,Malhotra,P .&Bhatnagar,R.K.Silencing ofmidgut aminopeptidase N of Spodoptera litura by double-stranded RNA establishes its role as Bacillus thuringiensis toxin receptor.J.Biol.Chem.277,46849–46851(2002).13.Turner,C.T.et al.RNA interference in the light brown apple moth,Epiphyas postvittana(Walker)induced by double-stranded RNA feeding.Insect Mol.Biol.15,383–391(2006).14.Anderson,S.,Hicks,G.,Heussing,J.,Romano, C.P .&Vetch, C.Nucleic acidsequences from Diabrotica virgifera virgifera Le Conte and the uses patent application publication number 2007–0050860.15.Winston,W.M.,Molodowitch, C.&Hunter, C.P .Systemic RNAi in C-elegansrequires the putative transmembrane protein SID-1.Science 295,2456–2459(2002).16.Honeybee Genome Sequencing Consortium Insights into social insects from thegenome of the honeybee Apis mellifera .Nature 443,931–949(2006).17.Kay,R.,Chan,A.,Daly,M.&McPherson,J.Duplication of CaMV 35S promotersequences creates a strong enhancer for plant genes.Science 236,1299–1302(1987).18.McElwain,E.F .&Spiker,S.A wheat cDNA clone which is homologous to the 17kdheat-shock protein gene family of soybean.Nucleic Acids Res.17,1764(1989).19.Armstrong,C.&Rout,J.Agrobacterium-mediated plant transformation patent number 6,603,061(2003).20.Oleson,J.D.,Park,Y.L.,Nowatzki,T.M.&Tollefson,J.J.Node-Injury Scale to EvaluateRoot Injury by Corn Rootworms (Coleoptera:Chrysomelidae).J.Econ.Entomol.98,1–8(2005).21.Drees,B.M.,Levine,E.,Steward,J.W.,Sutter,G.R.&Tollefson,J.J.Corn rootworms.inHandbook of corn insects (eds.Steffey,K.et al.)61–68,(Entomological Society of America,Lanham,Maryland,1999).22.Pleau,M.J.,Huesing,J.E.,Head,G.P .&Feir,D.J.Development of an artificial diet forthe western corn rootworm.Entomol.Exp.Appl.105,1–11(2002).23.Marrone,P .,Ferri,F .D.,Mosley,R.T.&Meinke,L.J.Improvements in laboratory rearingof the southern corn rootworm,Diabrotica undecimpunctata howardi Barber (Coleop-tera:Chrysomelidae).J.Econ.Entomol.78,290–293(1985).24.Sambrook,J.&Russell,D.W..Molecular Cloning (Cold Spring Harbor Laboratory Press,Cold Spring Harbor,2001).25.Allen,E.et al.Evolution of microRNA genes by inverted duplication of target genesequences in Arabidopsis thaliana .Nat.Genet.36,1282–1290(2004).©2007 N a t u r e P u b l i s h i n g G r o u p h t t p ://w w w .n a t u r e .c o m /n a t u r e b i o t e c h n o l o g y。
THUGSTOOLS

THUGSTOOLSTHUGSTOOLS - 暴徒武器PROFESSIONALTOOLS - 专业武器NUTTERTOOLS - ⾼级武器PRECIOUSPROTECTION - 防弹⾐全满ASPIRINE - ⽣命值全满YOUWONTTAKEMEALIVE - 被通缉级级别+2LEAVEMEALONE - 被通缉级级别为0CHASESTAT - 2颗星以上显⽰媒体级别APLEASANTDAY - 晴天ALOVELYDAY - 好天⽓ABITDRIEG - 阴天CATSANDDOGS - ⾬天CANTSEEATHING - 雾天LIFEISPASSINGMEBY - 加速时间流动BIGBANG - 附近的交通⼯具全爆炸STILLLIKEDRESSINGUP - 改变玩家⽪肤FIGHTFIGHTFIGHT - 路上的⼈开始打⽃NOBODYLIKESME - 没⼈喜欢你(和你打架) OURGODGIVENRIGHTTOBEARARMS - 每⼈都持武器ONSPEED - 游戏速度加快BOOOOOORING - 游戏速度减慢WHEELSAREALLINEED - 汽车只剩轮⼦COMEFLYWITHME - 汽车开到⼀定速度会飘起来SEAWAYS - 汽车可以在⽔上开(摩托除外)AIRSHIP - 快艇会飘起来GRIPISEVERYTHING - 车辆有喷汽弹射功能(shift)CHICKSWITHGUNS - ⼿下变拿M4的MM(前提得做⽼⼤)ICANTTAKEITANYMORE - ⾃杀GREENLIGHT - 所有红绿灯变绿MIAMITRAFFIC - 所有的车辆都不遵守交通AHAIRDRESSERSCAR - 路上的车全变成紫⾊IWANTITPAINTEDBLACK -路上的车全变成爆炸后的颜⾊LOADSOFLITTLETHINGS - 跑车车轮变⼤(仅INFERNUS CHEETAH) PANZER - 得到坦克THELASTRIDE - 得到 CASKET-CAR(棺材车)ROCKANDROLLCAR - 得到豪华轿车(love first) RUBBISHCAR - 得到垃圾车GETTHEREFAST - 得到 SABRE TURBO BETTERTHANWALKING - 得到 CADDY TRAVELINSTYLE - 得到 27号车GETTHEREQUICKLY - 得到 48号车GETTHEREVERYFASTINDEED - 得到 46号车GETTHEREAMAZINGLYFAST - 得到 14号车IDONTHAVETHEMONEYSONNY - MAFIOSI ⽪肤FOXYLITTLETHING - MAFIOSI ⼥⼉的⽪肤LOOKLIKELANCE - LANCE ⽪肤MYSONISALAWYER - LAWYER ⽪肤ILOOKLIKEHILARY - HILARY ⽪肤ROCKANDROLLMAN - 摇滚舞者⽪肤ONEARMEDBANDIT - 强盗⽪肤WELOVEOURDICK - 苏格兰⼈⽪肤CHEATSHAVEBEENCRACKED - BALDGUY ⽪肤HOPINGIRL - 附近的⼈上你的车FANNYMAGNET - 吸引⼥⼈CERTAINDEATH - 嘴上有雪茄DEEPFRIEDMARSBARS - 变胖在游戏进⾏时,直接输⼊下以字母>THUGSTOOLS - 棍⼦类武器>PROFESSIONALTOOLS - 枪类武器>NUTTERTOOLS - 变态武器>PRECIOUSPROTECTION - 加满防弹⾐>ASPIRINE - 加满⾎>YOUWONTTAKEMEALIVE - 加2个警察抓你的星星>LEA VEMEALONE - 警察星星变零>APLEASANTDAY - 好天⽓>ALOVELYDAY - 超好天⽓>ABITDRIEG - 云天>CATSANDDOGS - ⾬天>CANTSEEATHING - ⼩⾬天>PANZER - 给你个坦克>LIFEISPASSINGMEBY - 时间过得更快>BIGBANG - 附近所有车⼦爆炸>STILLLIKEDRESSINGUP - 换玩家的⼈物>FIGHTFIGHTFIGHT - 街上⼈打架>NOBODYLIKESME - 街上⼈被你装了会跌到>OURGODGIVENRIGHTTOBEARARMS - 街上所有⼈有武器>ONSPEED - ⾛的更快>BOOOOOORING - ⾛的更慢>WHEELSAREALLINEED - 车⼦不见..只有轮⼦>COMEFL YWITHME - 苍蝇飞来飞去>GRIPISEVERYTHING ->CHASESTAT ->CHICKSWITHGUNS ->ICANTTAKEITANYMORE - ⾃杀>GREENLIGHT - 所有红绿灯变绿>MIAMITRAFFIC - 路上车⼦开的很快>AHAIRDRESSERSCAR ->IWANTITPAINTEDBLACK ->TRA VELINSTYLE - 车⼦会飞>THELASTRIDE - 给你⼀辆葬礼车>ROCKANDROLLCAR - 给你⼀辆limo>RUBBISHCAR - 给你⼀辆垃圾车>GETTHEREFAST - 给你⼀辆SABRE TURBO>BETTERTHANW ALKING - 给你⼀辆caddy>LOOKLIKELANCE - LANCE SKIN>MYSONISALAWYER - LAWYER SKIN>ILOOKLIKEHILARY - HILARY SKIN>ROCKANDROLLMAN - ROCK AND ROLL MAN SKIN >ONEARMEDBANDIT - ONE ARMED BANDIT SKIN >IDONTHA VETHEMONEYSONNY - MAFIOSI SKIN>SEAW AYS ->LOADSOFLITTLETHINGS ->HOPINGIRL - 没⽤>AIRSHIP ->FOXYLITTLETHING - MAFIOSI DAUGHTER SKIN>WELOVEOURDICK - SCOTTISH SKIN>GETTHEREQUICKLY - 车⼦超快>GETTHEREVERYFASTINDEED - 车⼦超超快>GETTHEREAMAZINGL YFAST - 车⼦超超超快>FANNYMAGNET - ⼥⼈都会被你吸引>CHEATSHA VEBEENCRACKED - BALDGUY SKIN>CERTAINDEATH - 嘴⾥放跟烟>DEEPFRIEDMARSBARS - 没⽤>PROGRAMMER - 没⽤JYSDSOD = 强壮值全满下⽔秘籍:SEAWAYS = ⽔⾏(罪恶都市)飞车秘籍(车⼦可以飞):COMETOFLYWITHME = 汽车飞⾏(罪恶都市)RIPAZHA = 汽车会飞(圣地安列斯)飞机秘籍:QQ空间留⾔代码JUMPJET = 战⽃机Spawn Hydra (圣地安列斯)URKQSRK = 杂技飞机Spawn Stunt Plane (圣地安列斯)坦克秘籍:giveusatank = 获得坦克(罪恶都市)AMOMHRER = 坦克(圣地安列斯)侠盗4⾼级秘籍:《侠盗猎车⼿-罪恶都市》垃圾车变直升机在GTA-VC(侠盗猎车-罪恶都市)中,能够⽤秘籍调出来的汽车有很多,其中最不常⽤的⼤概就是TRASHMASTER(⽤秘籍RUBBISHCAR调出来的垃圾运输车)它⼜⼤,⼜笨,的确很“垃圾”摸索中发现改进⽅法,化腐朽为神奇,把垃圾车变成直⽣机~不敢独享,发出来⼤家⼀起体验体验⽅法如下:1、在游戏⽬录下打开data⽂件夹,把⾥⾯的default.ide⽂件设成⾮只读的2、⽤记事本打开default.ide3、找到“138, trash,trash,car, trash, TRASHM,null,big,10,7,0,255,1.06”这⼀⾏,把它⾥⾯“CAR”后⾯的那个“TRASH”改成“HUNTER”变成“138,trash,trash,car, HUNTER, TRASHM,null,big,10,7,0,255, 1.06”4、保存,退出好啦!这样就可以了!QQ空间现在你再进⼊游戏,⽤秘籍“RUBBISHCAR”调⼀辆垃圾车出来,驾驶⼀下看看吧!除了不能发射导弹,不能开枪,其余性能和游戏中的阿帕奇直升机完全⼀样侠盗飞车5秘籍圣地安列斯秘籍作弊码⼤全车辆操控类CPKTNWT = Blow Up All Cars 所有车辆爆炸WHEELSONLYPLEASE = Invisible car 隐⾏车辆STICKLIKEGLUE = Perfect Handling 完美操控ZEIIVG = All green lights 交通信号灯变绿YLTEICZ = Aggressive Drivers 司机有攻击性LLQPFBN = Pink traffic 所有车辆变粉⾊IOWDLAC = Black traffic 所有车辆变⿊⾊FLYINGFISH = Boats fly 船只可以飞⾏EVERYONEISPOOR = Traffic is Cheap Cars 交通⼯具慢速EVERYONEISRICH = Traffic is Fast Cars 交通⼯具快速RIPAZHA = Cars Fly 汽车飞⾏CJPHONEHOME = Huge Bunny Hop 超级兔⼦跳JCNRUAD = Smash n' Boom 汽车⼀击必炸SPEEDFREAK = All Cars Have Nitro 所有车辆得到⼀氧化⼆氮加速剂BUBBLECARS = Cars Float Away When Hit 车辆被撞击时会漂移GHOSTTOWN = Reduced Traffic 减少路上的车辆FVTMNBZ = Traffic is Country Vehicles 交通⼯具变为乡村车辆VKYPQCF = Taxis Have Nitrous, L3 Bunny Hop 出租车得到⼀氧化⼆氮加速剂,超级兔⼦跳NATURALTALENT = Max All Vehicle Skill Stats 驾驶技术全满⽓候类PLEASANTLYWARM = Sunny Weather 万⾥⽆云TOODAMNHOT = Very Sunny Weather 阳光明媚ALNSFMZO = Overcast Weather 阴云密布AUIFRVQS = Rainy Weather 阴⾬绵绵CFVFGMJ = Foggy Weather ⼤雾弥漫侠盗飞车SCOTTISHSUMMER = Thunderstorm 雷暴天⽓CWJXUOC = Sandstorm 沙尘暴天⽓OFVIAC = Orange Sky 21:00 永远是晚上9点时间类YSOHNUL = Faster Clock 时钟加快SPEEDITUP = Faster Gameplay 操控加快SLOWITDOWN = Slower Gameplay 操控减慢NIGHTPROWLER = Always Midnight 永远是午夜主⾓状态类AEDUWNV = Never Get Hungry 主⾓没有进⾷要求CVWKXAM = Infinite Oxygen ⽆限氧⽓ANOSEONGLASS = Adrenaline Mode 刺激模式KANGAROO = Mega Jump 超级跳跃IAVENJQ = Mega Punch 超级攻击BTCDBCB = Fat 主⾓变胖KVGYZQK = Skinny 主⾓变得⽪包⾻HELLOLADIES = Max Sex Appeal 最⼤性感度BUFFMEUP = Max Muscle 主⾓肌⾁值最⼤LXGIWYL = Weapon Set 1, Thug's Tools 暴徒武器PROFESSIONALSKIT = Weapon Set 2, Professional Tools 专业武器UZUMYMW = Weapon Set 3, Nutter Tools 疯狂武器BAGUVIX = Infinite Health ⽆限⽣命HESOYAM = Health, Armor, $250k ⽣命、护甲满,加25万美圆OUIQDMW = Full Weapon Aiming While Driving 驾驶时瞄准度全满PROFESSIONALKILLER = Hitman In All Weapon Stats 全部武器等级达到Hitman FULLCLIP = Infinite Ammo, No Reload ⽆限弹药,不⽤换弹夹AIYPWZQP = Have Parachute 得到降落伞ROCKETMAN = Have Jetpack 得到⽕箭助⾏器警察和⿊帮类TURNUPTHEHEAT = Increase Wanted Level Two Stars 增加两星通缉度TURNDOWNTHEHEAT = Clear Wanted Level 清除通缉程度BRINGITON = Six Star Wanted Level 六星通缉(最⾼等级)AEZAKMI = Never Wanted 永远不会被通缉WORSHIPME = Max Respect 威望值最⾼ONLYHOMIESALLOWED = Gang Members Everywhere 到处都是⿊帮BIFBUZZ = Gangs Control the Streets ⿊帮控制街道刷新车辆类AIWPRTON = Spawn Rhino 刷新⼀辆坦克CQZIJMB = Spawn Bloodring Banger 刷新⼀辆Bloodring BangerJQNTDMH = Spawn Rancher 刷新⼀辆RancherVROCKPOKEY = Spawn Racecar 刷新⼀辆RacecarVPJTQWV = Spawn Racecar 刷新⼀辆Racecar#2 WHERESTHEFUNERAL = Spawn Romero 刷新⼀辆Romero CELEBRITYSTATUS = Spawn Stretch 刷新⼀辆Stretch TRUEGRIME = Spawn Trashmaster 刷新⼀辆Trashmaster QQ空间代码RZHSUEW = Spawn Caddy 刷新⼀辆CaddyJUMPJET = Spawn Hydra 刷新⼀架HydraKGGGDKP = Spawn Vortex Hovercraft 刷新⼀辆Vortex Hovercraft OHDUDE = Spawn Hunter 刷新⼀架Hunter FOURWHEELFUN = Spawn Quad 刷新⼀辆QuadAMOMHRER = Spawn Tanker Truck 刷新⼀辆Tanker Truck ITSALLBULL = Spawn Dozer 刷新⼀辆Dozer FLYINGTOSTUNT = Spawn Stunt Plane 刷新⼀架Stunt Plane MONSTERMASH = Spawn Monster 刷新⼀辆Monster武器及⽇常类LXGIWYL = ⼀般武器KJKSZPJ = 暴⼒武器UZUMYMW = 超级武器HESOYAM = 恢复⽣命值, 防弹⾐, $250kOSRBLHH = 增加两颗警星ASNAEB = 清除警星(偷渡和闯如军事基地⽆效)AFZLLQLL = 好天⽓ICIKPYH = ⾮常好的天⽓ALNSFMZO = 变阴暗天⽓AUIFRVQS = 下⾬的天⽓CFVFGMJ = 雾深的天⽓YSOHNUL = 时间过的更快PPGWJHT = 快速游戏LIYOAAY = 慢速游戏AJLOJYQY = 暴动BAGOWPG = 未知FOOOXFT = ⾏⼈拥有武器AIWPRTON = 未知CQZIJMB = 未知JQNTDMH = 未知PDNEJOH = 未知 Spawn Racecar VPJTQWV = 未知 Spawn Racecar AQTBCODX = 未知 Spawn Romero KRIJEBR = 未知Spawn Stretch UBHYZHQ = 未知 Spawn Trashmaster RZHSUEW = 未知 Spawn Caddy CPKTNWT = Blow Up All Cars XICWMD = 看不见的汽车PGGOMOY = 完美的处理SZCMAWO = ⾃杀ZEIIVG = 所有的红绿灯变绿灯YLTEICZ = 攻击性的驾驶员LLQPFBN = 粉红的交通(所有车变粉红⾊)IOWDLAC = ⿊⾊的交通(所有车变⿊⾊)AFSNMSMW = 船可以飞BTCDBCB = 肥胖JYSDSOD = 强壮值全满KVGYZQK = 薄的ASBHGRB = Elvis 在各处BGLUAWML = Peds ⽤武器攻击你, ⽕箭发射者CIKGCGX = 海滩党MROEMZH = 各处⼀组成员BIFBUZZ = 团队控制街道AFPHULTL = 忍者主题BEKKNQV = 所有丑⼥被你吸引BGKGTJH = 交通是便宜的汽车GUSNHDE = 交通是快速的汽车RIPAZHA = 汽车会飞JHJOECW = 未知JUMPJET = 战⽃机Spawn HydraKGGGDKP = ⽔翼船Spawn Vortex HovercraftJCNRUAD = ⾮常的繁荣Smash n' BoomCOXEFGU = 所有的汽车有Nitro All Cars Have Nitro(氮⽓)BSXSGGC = 未知Cars Float Away When HitXJVSNAJ = 总是午夜的OFVIAC = 橘⾊天空 21:00MGHXYRM = 雷⾬CWJXUOC = 沙暴LFGMHAL = 百万跳跃,跳的更⾼BAGUVIX = ⽆限健康CVWKXAM = ⽆限氧⽓AIYPWZQP = 降落伞YECGAA = ⽕箭飞⾏器JetpackAEZAKMI = 从不想要LJSPQK = 警星全满IAVENJQ = 百万打洞器AEDUWNV = 不会饥饿IOJUFZN = 暴动模态PRIEBJ = 玩趣屋主题MUNASEF = 肾上腺素模态WANRLTW = ⽆限弹药, 没有再装填OUIQDMW = 当驾驶的时候可以在车内使⽤准星瞄准攻击THGLOJ = 减少了交通FVTMNBZ = 交通是国家车辆SJMAHPE = 恢复任何⼈Recruit Anyone (9mm)BMTPWHR = 国家车辆和 Peds,拿天⽣的 2个卡车⽤具Country Vehicles and Peds, Get Born 2 Truck OutfitZSOXFSQ = 恢复任何⼈ (⽕箭)Recruit Anyone (Rockets)OGXSDAG = 最⼤尊敬Max RespectEHIBXQS = 最⼤性感Max Sex AppealVKYPQCF = Taxis 车可以跳舞NCSGDAG = 武器熟练度全满VQIMAHA = 更好的驾驶技能OHDUDE = 猎⼈AKJJYGLC = 未知Spawn QuadAMOMHRER = 坦克EEGCYXT = 未知Spawn DozerURKQSRK = 杂技飞机Spawn Stunt Plane /doc/a20832d5c1c708a1284a4475.html LXGIWYL = ⼀般武器KJKSZPJ = 暴⼒武器UZUMYMW = 超级武器HESOYAM = 恢复⽣命值, 防弹⾐, $250kOSRBLHH = 增加两颗警星ASNAEB = 清除警星(偷渡和闯如军事基地⽆效) AFZLLQLL = 好天⽓ICIKPYH = ⾮常好的天⽓ALNSFMZO = 变阴暗天⽓AUIFRVQS = 下⾬的天⽓CFVFGMJ = 雾深的天⽓YSOHNUL = 时间过的更快PPGWJHT = 快速游戏LIYOAAY = 慢速游戏AJLOJYQY = 暴动BAGOWPG = 街上的⼈见了你都逃跑(胆⼤者会向你开枪) FOOOXFT = ⾏⼈拥有武器AIWPRTON = 坦克CQZIJMB = 破旧的车JQNTDMH = 农场⼯⼈的车PDNEJOH = 赛车1VPJTQWV = 赛车2AQTBCODX = 葬礼车KRIJEBR = 环座型贵宾车UBHYZHQ = 垃圾车RZHSUEW = ⾼尔夫车CPKTNWT = 附近所有车爆炸XICWMD = 看不见的汽车PGGOMOY = 完美的处理SZCMAWO = ⾃杀ZEIIVG = 所有的红绿灯变绿灯YLTEICZ = 攻击性的驾驶员LLQPFBN = 粉红的交通(所有车变粉红⾊)IOWDLAC = ⿊⾊的交通(所有车变⿊⾊)AFSNMSMW = 船可以飞BTCDBCB = 肥胖JYSDSOD = 强壮值全满KVGYZQK = 薄的ASBHGRB = Elvis 在各处BGLUAWML = Peds ⽤武器攻击你, ⽕箭发射者CIKGCGX = 海滩党MROEMZH = 各处⼀组成员BIFBUZZ = 团队控制街道AFPHULTL = 忍者主题BEKKNQV = 所有丑⼥被你吸引BGKGTJH = 交通是便宜的汽车GUSNHDE = 交通是快速的汽车RIPAZHA = 汽车会飞JHJOECW = 未知JUMPJET = 战⽃机Spawn HydraKGGGDKP = ⽔翼船Spawn Vortex Hovercraft JCNRUAD = ⾮常的繁荣COXEFGU = 所有的汽车有Nitro All Cars Have Nitro(氮⽓) BSXSGGC = 未知Cars Float Away When Hit XJVSNAJ = 总是午夜的OFVIAC = 橘⾊天空21:00MGHXYRM = 雷⾬CWJXUOC = 沙暴LFGMHAL = 跳的更⾼BAGUVIX = ⽆限健康CVWKXAM = ⽆限氧⽓AIYPWZQP = 降落伞YECGAA = ⽕箭飞⾏器JetpackAEZAKMI = 不被通缉LJSPQK = 警星全满IAVENJQ = 百万打洞器AEDUWNV = 不会饥饿IOJUFZN = 暴动模态PRIEBJ = 玩趣屋主题MUNASEF = 肾上腺素模态WANRLTW = ⽆限弹药, 没有再装填OUIQDMW = 当驾驶的时候可以在车内使⽤准星瞄准攻击THGLOJ = 交通畅通FVTMNBZ = 交通是国家车辆SJMAHPE = 补充每⼀个⼦弹BMTPWHR = 国家车辆和Peds,拿天⽣的2个卡车⽤具ZSOXFSQ = 补充每⼀个(⽕箭筒)OGXSDAG = 最⼤威望Max RespectEHIBXQS = 最⼤性感Max Sex AppealVKYPQCF = Taxis 车可以跳舞NCSGDAG = 武器熟练度全满VQIMAHA = 更好的驾驶技能OHDUDE = 猎⼈(Ah-64阿帕奇战⽃机)AKJJYGLC = 四轮摩托车AMOMHRER = 超长拖粪车EEGCYXT = 推⼟机URKQSRK = 杂技飞机Spawn Stunt PlaneAGBDLCID = 越野型⼤脚车参考资料:LXGIWYL = ⼀般武器侠盗车⼿5城市风云THUGSTOOLS - 得到杀⼿武器PROFESSIONALTOOLS - 得到专业武器thugstools NUTTERTOOLS - 得到神秘武器PRECIOUSPROTECTION - 装甲全满ASPIRINE - 体⼒全满YOUWONTTAKEMEALIVE - 通缉级别+2 LEAVEMEALONE - 通缉级别变为0APLEASANTDAY - 好天⽓ABITDRIEG - 阴天CATSANDDOGS - ⾬天CANTSEEATHING - 雾天PANZER - 得到⼀辆坦克LIFEISPASSINGMEBY - 时间流逝加速BIGBANG - 附近车辆爆炸STILLLIKEDRESSINGUP - 改变玩家外貌FIGHTFIGHTFIGHT - 街上的市民互相残杀NOBODYLIKESME - 攻击市民造成更⼤伤害OURGODGIVENRIGHTTOBEARARMS - 每个⼈都拥有武器ONSPEED - ⾏动速度加快BOOOOOORING - ⾏动速度减慢ICANTTAKEITANYMORE - ⾃杀GREENLIGHT - 全部交通信号变为绿灯MIAMITRAFFIC - ⾏⼈加速TRAVELINstyle - 飞车ROCKANDROLLCAR - 得到豪华轿车RUBBISHCAR - 得到垃圾车GETTHEREFAST - 得到⼤马⼒车MYSONISALAWYER - 变成律师ROCKANDROLLMAN - 变成摇滚歌⼿ONEARMEDBANDIT - 变成武装强盗IDONTHAVETHEMONEYSONNY - 变成⿊⼿党成员GETTHEREQUICKLY - 得到快车GETTHEREVERYFASTINDEED - 得到拉⼒赛车GETTHEREAMAZINGLYFAST - 得到最快的跑车FANNYMAGNET - 吸引⼥性CHEATSHAVEBEENCRACKED - 变成秃顶。
Hossfeld方法中文版:高效学习西班牙文中文字典与语法大全说明书

S E E C G I N L H-FR N H D I CT I ONA RY
FRENCH- ENGLISH D ICTIONARY T H E T wo DICT ION \ R I E S i n o n e vol ume
.
MANU AL OF FRENCH CONVERSATION
I OO PASSAG ES FO R T RANSLATION I NTO ENGLISH AND
F I S A D O B y P R
RJ
.
.
.
NR .
P R IC E ONE SH I L L I NG .
HI R SOHF E L D B R OS
B RE AMS
B U I LD I NG S,
F ETTE RLANΒιβλιοθήκη ,L,OND
ON ,
EC
.
.
H O S SF E L D’S
M N E W P R A C T I C A L
ITALIAN COMPOSITION AND IDIOMS
CONJU G AT I ON O F I TALI AN R E GIILA R A ND I R R EG U LA R
VERBS .
ENGLIS H ITALIAN
A ND
ITALIAN
ENGLIS H
D I CT I ONA RY,
ENGLISH-GERMAN D ICTIONARY
GERMAN-ENGLISH DICTIONARY T HE T wo DI CT I ONAR I ES i n one volume
SELECT GER MAN
S W E DI S H .
T-DNAPrimerDesign

T-DNAPrimerDesignT-DNA Primer Design( Powered by GEBD )Please use the backup page served by AtTA, if the tdnaexpress server is down.The new T-DNA Primer Design Tool is now powered by Genome Express Browser Server (GEBD). The new tool can return the primers faster, and also give the insertion location information, the estimated T-DNA confirmation product size, as well as primer3-like format output. (July 28, 2005)Important Change: Now the RP is always on the side of the flanking sequence, that is, RP is always on the 3' end of the insertion. Therefore, the PCR reaction should always be set up as LB+RP for HM and LP+RP for WT. (Feb. 04, 2005)1. Protocol for SALK T-DNA primer designNote:N - Difference of the actual insertion site and the flanking sequence position, usually 0 - 300 basesMaxN - Maximum difference of the actual insertion site and the sequence, default 300 bps pZone - Regions used to pick up primers, default 100 bpsExt5, Ext3 - Regions between the MaxN to pZone, reserved not for picking up primersLP, RP - Left, Right genomic primerBP - T-DNA border primer LB - the left T-DNA border primerBPos - The distance from BP to the insertion siteLB - Left border primer of the T-DNA insertion:>LBb1 of pBIN-pROK2 for SALK linesGCGTGGACCGCTTGCTGCAACT>LBb1.3(Newly used by Salk Genotyping Project and with better results)ATTTTGCCGATTTCGGAAC>LBa1 of pBIN-pROK2 for SALK lines TGGTTCACGTAGTGGGCCATCG>LB_6313R for SALK linesTCAAACAGGATTTTCGCCTGCT>LB1 for SAIL lines C/418-451 of pCSA110-pDAP101_T-DNAs GCCTTTTCAGAAATGGATAAATAGCCTTGCTTCC> >LB2 for SAIL lines C/390-423 of pCSA110-pDAP101_T-DNAs GCTTCCTATTATATCTTCCCAAATTACCAATACA>LB3 for SAIL lines C/350-383 of pCSA110-pDAP101_T-DNAs TAGCATCTGAATTTCATAACCAATCTCGATACACTo download SAIL pCSA110 & pDAP101 T-DNAs.By using the three primers (LBb1.3+LP+RP) for SALK lines, users for WT (Wild Type - no insertion) should get a product of about 900-1100 bps ( from LP to RP ), for HM (Homozygous lines - insertions in both chromosomes) will get a band of 410+N bps ( from RP to insertion site 300+N bases, plus 110 bases from LBb1.3 to the left border of the vector), and for HZ (Heterozygous lines - one of the pair chromosomes with insertion) will get both bands. The product size should be 200 base larger if using LBa1 instead of LBb1.3.However, the protocol requires the same or similiar TM values for all the LB, LP and RP primers.You can set up two paired reactions, LP+RP and LB+RP. You should get a product in the LP+RP reaction for WT or HZ lines or get blank for HM lines, while get a band in the LB+RP for HM or HZ lines.2. SALK T-DNA verification primer designThe program will pick up LP and RP for you. Its product size is around 900-1100 bps. If you want to confirm whether the design is right, simply cut and paste the LP and RP sequences together (you can cut/paste whole returned primer info line) to the blast textarea on the tdnaexpress page, hit "Return" if only one line of text and submit it.Note: If you could not get primers or high quality primers for a line, it is possible that 1. either your input is "NOT RIGHT". 2. or the genomic region is "NOT GOOD" for picking up primers. However, you can change your settings, especially MAX_N,Ext5, Ext3, and/or pZone to get a return. You could also use the iSect tool to get the genomic sequences around the line and then design primers by yourself or other tools.。
Point-in-Polyhedron Test (2D and 3D) R包说明说明书

Package‘ptinpoly’October14,2022Title Point-in-Polyhedron Test(2D and3D)Version2.8Date2020-05-31Author Jose M.Maisog,Yuan Wang,George Luta,Jianfei LiuMaintainer Jose M.Maisog<******************>Description Function pip3d()tests whether a point in3D space iswithin,exactly on,or outside an enclosed surface defined by a triangular mesh.Function pip2d()tests whether a point in2D space is within,exactly on,or outside a polygon.For a reference,see:Liu et al.,A new point containment test algorithm based on preprocessing and determining triangles,Computer-Aided Design42(12):1143-1150.License GPL-2LazyLoad yesDepends R(>=2.10),misc3dSuggests rgl,geometryURL Repository CRANRepository/R-Forge/Project ptinpolyRepository/R-Forge/Revision41Repository/R-Forge/DateTimeStamp2020-05-3112:01:50Date/Publication2020-06-0215:10:07UTCNeedsCompilation yesR topics documented:blocks2vf (2)comb (3)cube (4)fractal (5)pip2d (5)pip3d (7)spiral (9)vf2blocks (10)12blocks2vf Index12blocks2vf Convertor from3-Block Representation Representation to Vertices-FacesDescriptionConverts a polyhedron from the three-block representation to the vertices-faces representation. Usageblocks2vf(Block1,Block2,Block3)ArgumentsBlock1M by3matrix containing the XYZ coordinates of vertex1of the M faces of the polyhedronBlock2M by3matrix containing the XYZ coordinates of vertex2of the M faces of the polyhedronBlock3M by3matrix containing the XYZ coordinates of vertex3of the M faces of the polyhedronDetailsThe values in thefirst output matrix can befloating point integers,representing the XYZ coordinates of the vertices of the polyhedron.The values in the second output matrix will be integers with values running from1to N,where N is the number of vertices.A value of’1’in this matrix,for example,represents the1st vertex,i.e.,the vertex defined by thefirst row in the matrix Vertices.Each row in this matrix defines a triangular face in the polyhedron.This function is the inverse of the vf2blocks function.ValueReturns a list of two matrices.Thefirst is a N by3matrix containing the XYZ coordinates of the N vertices of the polyhedron.The second M by3matrix containing indices of the vertices defining the M faces.See the example below.NoteThis function requires the misc3d library.comb3Examples#Load example data.data(verts)data(faces)#Use vf2blocks to convert from vertices-faces representation to3-block representation.#Note double square brackets.blocks=vf2blocks(verts,faces)block1=blocks[[1]]block2=blocks[[2]]block3=blocks[[3]]#Now use blocks2vf to convert back to vertices-faces representation.# verts2 and faces2 should encode the same polyhedron as the#original verts and faces ,although perhaps in a different order.#Note double square brackets.vertsFaces=blocks2vf(block1,block2,block3)verts2=vertsFaces[[1]]faces2=vertsFaces[[2]]comb Sample Data:Comb PolygonDescriptionSample data defining an enclosed comb2D polygon.Usagedata(comb)Examples#Load polygon.data(comb)#Plot the polygon.plot(rbind(comb,comb[1,]),type="l")#Generate3333random test points.set.seed(1902)n<-3333x1<-rnorm(n);x2<-rnorm(n)X<-cbind(x1,x2)queries<-as.matrix(X)#Check whether test points are contained in the polygon.#Most of these points will lie outside the polygon.containment=pip2d(comb,queries);4cube cube Sample Data:Simple CubeDescriptionThis is sample data that defines a simple cube:eight vertices,and twelve triangles that make up the six faces.Also included is an example matrix queries offive test points.Thefirst test point is contained within the cube,the second through fourth test points lie exactly on the surface of the cube,and the fifth test point lies outside the cube.Usagedata(verts)data(faces)data(queries)Formatverts is an8by3matrix containing the XYZ coordinates of the vertices of a simple cube.faces is a12by3matrix containing the indices of the vertices defining the twelve triangular faces making up the surface of the cube.queries is a5by3matrix containing the XYZ coordinates offive test points to be tested for containment within the cube.Examples#Load sample data defining a simple cube.data(verts)data(faces)#Also load sample data for five test points.data(queries)#Test whether each point in queries is contained in#the simple cube defined by verts and faces .#This should return"1000-1".containment=pip3d(verts,faces,queries);fractal5 fractal Sample Data:Fractal PolygonDescriptionSample data defining an enclosed fractal2D polygon.Usagedata(fractal)Examples#Load polygon.data(fractal)#Plot the polygon.plot(rbind(fractal,fractal[1,]),type="l")#Generate3333random test points.set.seed(1902)n<-3333x1<-rnorm(n);x2<-rnorm(n)X<-cbind(x1,x2)queries<-as.matrix(X)#Check whether test points are contained in the polygon.#Most of these points will lie outside the polygon.containment=pip2d(fractal,queries);pip2d Test for Point Containment in2D PolygonDescriptionTests whether points are contained within a two-dimensional polygon.Usagepip2d(Vertices,Queries)ArgumentsVertices N by2matrix containing the XY coordinates of N vertices of the polygon Queries P by2matrix containing the XY coordinates of P points to be tested for con-tainment in the polygon defined by’Vertices’DetailsThe XY coordinates of the vertices are stored in order in the matrix Vertices.It is assumed that the last vertex listed in the matrix is connected to thefirst vertex,so that the polygon does not have a”hole”.ValueReturns a vector containing P values,one for each of the P points listed in the Queries matrix.’1’indicates that the point is contained in the polygon.’0’indicates that the point lies exactly on the surface of the polygon.’-1’indicates that the point lies outside the polygon.’-3’(error)indicates that the Vertices matrix didn’t have two columns’-6’(error)indicates that the Queries matrix didn’t have two columns’-8’(error)indicates computational error not otherwise specifiedNoteThe polygon defined by Vertices must be"non-leaky";i.e.,it must define an"inside"versus "outside"and must not contain any holes.ReferencesW.P.Horn and D.L.Taylor,A theorem to determine the spatial containment of a point in a planar polygon,Computer Vision,Graphics and Image Processing,vol.45,pp.106-116,1989.S.Nordbeck and B.Rysedt,Computer cartography point-in-polygon programs,BIT,vol.7,pp.39-64,1967.J.A.Baerentzen and H.Aanaes,Signed distance computation using the angle weighted pseudo-normal,IEEE Trans.Visualization and Computer Graphics,vol.11,no.3,pp.243-253,May/June 2005.J.Liu,Y.Q.Chen,J.M.Maisog,G.Luta,A new point containment test algorithm for polygon composed of huge number of triangles,Computer-Aided Design,V olume42,Issue12,December 2010,Pages1143-1150./Examples#-------------------------------------------#Load sample data defining a comb,spiral,and fractal.data(comb)data(spiral)data(fractal)#Plot the comb,spiral,and fractal.plot(rbind(comb,comb[1,]),type="l")plot(rbind(spiral,spiral[1,]),type="l")plot(rbind(fractal,fractal[1,]),type="l")#Generate3333random test points.set.seed(1902)n<-3333x1<-rnorm(n);x2<-rnorm(n)X<-cbind(x1,x2)queries<-as.matrix(X)#Check whether test points are contained in the comb,spiral,and factal.#Most of these points will lie outside the polygons.containment1<-pip2d(comb,queries);containment2<-pip2d(spiral,queries);containment3<-pip2d(fractal,queries);pip3d Test for Point Containment in3D PolyhedronDescriptionTests whether points are contained within a three-dimensional polyhedron.Usagepip3d(Vertices,Faces,Queries)ArgumentsVertices N by3matrix containing the XYZ coordinates of N vertices of the polyhedron Faces M by3matrix containing the indices of the three vertices defining the M trian-gular faces of the polyhedronQueries P by3matrix containing the XYZ coordinates of P points to be tested for con-tainment in the polyhedron defined by’Vertices’and’Faces’DetailsThe values in the Faces matrix must be integers with values running from1to N,where N is the number of vertices.A value of’1’in this matrix,for example,represents the1st vertex,i.e.,the vertex defined by thefirst row in the matrix Vertices.ValueReturns a vector containing P values,one for each of the P points listed in the Queries matrix.’1’indicates that the point is contained in the polyhedron.’0’indicates that the point lies exactly on the surface of the polyhedron.’-1’indicates that the point lies outside the polyhedron.’-2’(error)indicates that the polyhedron was topologically defective(e.g.,had a hole)’-3’(error)indicates that the Vertices matrix didn’t have three columns’-4’(error)indicates that the Faces matrix didn’t have three columns’-5’(error)indicates that the Faces matrix was0-rather than1-offset’-6’(error)indicates that the Queries matrix didn’t have three columns’-7’(error)indicates that two faces in the polyhedron were too close to one another’-8’(error)indicates computational error not otherwise specified.A possible cause is when two faces of the polygon are extremely close to one another(imagine bending a cylindrical balloon until the two ends meet).Adjusting the spatial smoothness of the data mayfix this problem.NoteThe polyhedron defined by Vertices and Faces must be"non-leaky";i.e.,it must define an"inside"versus"outside"and must not contain any holes.For an example of external software that could potentially be used tofix defective polyhedra,see,e.g.,PolyMender(/~taoju/code/polymender.htm).Previous versions of this function would hang when there were more than two vertices very close to one another;this problem was discovered with a polyhedron in which there were multip;le duplicate vertices and one triplicate vertex.The triplicate vertex fulfilled the case of"more than two vertices very close to one another",and caused the code to hang.The threshold for vertices that are very close to one another has been increased to three.It is advisable to make sure that a polyhedron does not have more than three vertices that are"very close to one another",and to make sure that there are no duplicate vertices.Similarly,it is advisable to make sure that a polyhedron does not have faces that that are extremely close to one another.ReferencesW.P.Horn and D.L.Taylor,A theorem to determine the spatial containment of a point in a planar polygon,Computer Vision,Graphics and Image Processing,vol.45,pp.106-116,1989.S.Nordbeck and B.Rysedt,Computer cartography point-in-polygon programs,BIT,vol.7,pp.39-64,1967.J.A.Baerentzen and H.Aanaes,Signed distance computation using the angle weighted pseudo-normal,IEEE Trans.Visualization and Computer Graphics,vol.11,no.3,pp.243-253,May/June 2005.J.Liu,Y.Q.Chen,J.M.Maisog,G.Luta,A new point containment test algorithm for polyhedron composed of huge number of triangles,Computer-Aided Design,V olume42,Issue12,December 2010,Pages1143-1150./Examples#-------------------------------------------#Simple Cube example.#Load sample data defining a simple cube.data(verts)data(faces)spiral9#Also load sample data for five test points.data(queries)#Test whether each point in queries is contained in#the simple cube defined by verts and faces .#This should return"1000-1".containment<-pip3d(verts,faces,queries);#-------------------------------------------#Torus example.#Make a donut-shaped polyhedron.torus<-parametric3d(fx=function(u,v)(1+0.25*cos(v))*cos(u),fy=function(u,v)(1+0.25*cos(v))*sin(u),fz=function(u,v)0.25*sin(v),u=seq(0,2*pi,length.out=10),v=seq(0,2*pi,length.out=10),engine="none",color="orange",alpha=0.25)#If desired,this torus can be rendered for visualization,e.g.:#library(geometry)#library(rgl)#drawScene.rgl(torus)#Convert the torus to vertices-faces representation.ve<-misc3d:::t2ve(torus)Vertices<-t(ve$vb)Faces<-t(ve$ib)#Generate3333random test points.set.seed(1902)n<-3333x1<-rnorm(n);x2<-rnorm(n);x3<-rnorm(n)X<-cbind(x1,x2,x3)Queries<-as.matrix(X)#Check whether test points are contained in the torus.#Most of these points will lie outside the torus.containment<-pip3d(Vertices,Faces,Queries);#-------------------------------------------#If you remove one of the faces of the cube,the resulting cube#becomes"leaky".Running pip3d on the resulting defective#polyhedron will return-2.#NOT RUN##badcube<-faces[1:11,]#containment<-pip3d(verts,badcube,queries);spiral Sample Data:Spiral Polygon10vf2blocksDescriptionSample data defining an enclosed spiral2D polygon.Usagedata(spiral)Examples#Load polygon.data(spiral)#Plot the polygon.plot(rbind(spiral,spiral[1,]),type="l")#Generate3333random test points.set.seed(1902)n<-3333x1<-rnorm(n);x2<-rnorm(n)X<-cbind(x1,x2)queries<-as.matrix(X)#Check whether test points are contained in the polygon.#Most of these points will lie outside the polygon.containment=pip2d(spiral,queries);vf2blocks Convertor from Vertices-Faces Representation to3-Block Representa-tionDescriptionConverts a polyhedron from the vertices-faces representation to the three-block representation. Usagevf2blocks(Vertices,Faces)ArgumentsVertices N by3matrix containing the XYZ coordinates of N verticesFaces M by3matrix containing indices of vertices defining M facesDetailsThe values in the Face matrix must be integers with values running from1to N,where N is the number of vertices.A value of’1’in this matrix,for example,represents the1st vertex,i.e.,the vertex defined by thefirst row in the matrix Vertices.This function is the inverse of the blocks2vf function.vf2blocks11ValueReturns a list of three matrices.Thefirst is an M by3matrix containing the XYZ coordinates of vertex1of the M faces of the polyhedron.The second and third are similarly M by3matrices,but contain the XYZ coordinates of vertices2and3of the faces.See the example below.Examples#Load example data.data(verts)data(faces)#Use vf2blocks to convert from vertices-faces representation to3-block representation.#Note double square brackets.blocks=vf2blocks(verts,faces)block1=blocks[[1]]block2=blocks[[2]]block3=blocks[[3]]Index∗datasetscomb,3cube,4fractal,5spiral,10∗methodsblocks2vf,2pip2d,5pip3d,7vf2blocks,10blocks2vf,2comb,3cube,4faces(cube),4fractal,5pip2d,5pip3d,7queries(cube),4spiral,9verts(cube),4vf2blocks,1012。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Chrysanthemum 2003-2007 P/L RMBProfit & Loss Statement 2003---200720032004200520062007BCT Market size *36703990436047905290* to be confirmedJV Market Share 1%5%10%12%12%JV Market Size 37200436575635CMT Market Size 617070908270973011520JV Market Share 1%5%10%12%12%JV Market Size 6235582711681382ADT Market Size 285356445557696JV Market Share05%20%33%33%01889184230Sales 20032004200520062007合计Total Qty2087021472204623676795.1807ODT sub-total 11013012012012045.3Val (wo Tax)1359453000No reduction, price already lowBJZ3420 25TonsQty 205060606058.12Val (wo Tax)1162.42818.823281.1063182.6733087.1933% reduction every year, price already 20% lower than local competitor BJZ3480 30TonsQty 101000070.94Val (wo Tax)709709000No reduction, price already lowBJZ3530 32TonsQty 205060606092.31Val (wo Tax)184644775211505549033% reduction every year, price already 30% lower than local competitor articulated truck 25TonsQty 01889184230119.6Val (wo Tax)02130.37510119.2819827.4723545.125% reduction every year, price is 50% of the import Bulk cement truck (28)AQty 3720043657563529.47Val (wo Tax)1081.5495879.26512848.9216939.3618707.56No reduction, price is comparable with competitors, but offerBulk cement truck (28)BQty 00000better technology, faster turnaround time47.01Val (wo Tax)00000concrete truck mixer (12)Qty 62355827116813827% reduction to capture higher markets 68.00Val (wo Tax)419622419486396386370319Current price is 20% lower than competitorwater tanker Qty 00000Val (wo Tax)00000J-truck Qty 00000Val (wo Tax)00000Spare parts 100011001210.01331.01464.1Total sales 114573925480099108868120562S$ million25.4592287.23106177.998241.9284267.9165Cost of salesA Production Material 每辆材料,运费陈本BJZ3364J 20 tons 29.29879293000BJZ3364Q 22 tons 35.251058353000BJZ3420 25 ton 37.9575918412142207820163% reduction every year BJZ3480 30 ton 55.7557557000BJZ3530 32 ton 64.8129631433658354834423% reduction every year Articulated Truck 25 Tons 85.1201516720214111167575% reduction every year BMT (28 m 3 )2488146921005012984140522% reduction every year BMT (28 m 3 ) - luxury 24.700000Con Mixer Truck (12 m 3)43.0942659148193353245923527403% reduction every yearSpare parts 600660726798.6878.46# Direct Labour14141381810641144(B) Sub-total direct wages 1223.529155637132518091945逐年递增5%CPF, Insurance, etc 39.50%62253526718772Training & unions Funds 3.50%422466368AWS /Bonus 多一个月1053110151162Assumption# Indirect labor 8383164213229Total Salary2000149208433591636逐年递增5%CPF, Insurance, etc 39.50%5983172234252Training&unions Funds 3.50%47152122AWS/ Bonus 多一个月917364953Rental162216311626641Heating18.082939576870Water electricity 6384121146149Tools & replacement 881621231k per workerTransport (material)1%43196400544603Component Import 3.300%88489110715151740Travel expenses 912121212Depreciation118170*********Safty Related Expenses 4481111500 per employee Disposable Material 4481111500 per employee Export related expenses Not considered Production equipment repair 881621231k per employee Office Expenses 4481111500 per employeeR&D200393801108912062nd year onwards 1% of salesIP Amortization160160160160160Tooling amortization allowance other10% of Value Added Tax 57.3204.7399.7513.8536.4增值税的10%Gross profitDepreciation 021********Water/electricity/telephone 07.510101010# Sales/marketing/servicec 2530405060Salary - Sales/Marketing 1685.71386181101121CPF & others 39.50%1124324048Training & Unions Funds 3.50%12344AWS/Bonus 多一个月257810Rental -sales office 4101520305万元一个办事处,每年递增Export - Transportation 0Trasportation 253040506010K per person per yearExport cleanance 0Advertisement 0.50%43196400544603Entertainment 0.50%43196400544603Travel expenses 20003672.096.0120.0144.02k per person per monthExhibition 0.50%43196400544603commision0.50%43196400544603Type Approval expenses 0.50%43196400544603legal consultant2K 2.4 2.4 2.4 2.4 2.4New products Conference20.020.020.020.020.0设计单位、政府、客户联谊建筑金额5%,2007年8%其中预计66%入制造费用铰接车和半挂混凝土车 按照原材料10%的33%Management Cost# Staff4145505560Salary6044223326363399435CPF, Insurance etc39.50%66129143158172Training/ Union Funds 3.50%611131415AWS/Bonus多一个月1427303336Telephone Expenses1824242424Depreciation62106106106106Office Expense1827303336500 per person per month Travel / Transportation31546066721k per person per monthJV Start up Expense Amort4040404040Insurance0.10%RepairEntertainment0.543196400544603Audit 0.11214161922US$ 15 k Increase 15% per year ISO 900020k1111110K rmb per yearLegal fees 5666665k per monthRental8411116032333034%入管理费用Heating18.081520293536Water/electcity162130363720%入管理费用Fire Exercise11111Tax31224333600000Prov. For bad Debt0.50%43196400544603Environment Protection Expense912121212guards/security152020202012 个人(翻三班)和5条警犬interest00000 other income000000000000000Cum Profit681.7966270.921179523229746515petitor petitor。
