Cooperative Interoperability of Debugger and Editor in Distributed Tools Environment
合作博弈代码

合作博弈代码合作博弈(Cooperative game)是博弈论中的一个重要分支,研究的是参与者通过合作来实现组织目标的博弈模型。
在合作博弈中,参与者之间通过协商、合作来达成最优解,共同分享收益或承担风险。
为了解决这类问题,人们开发了各种合作博弈模型和相应的求解方法。
本文将介绍一种常见的合作博弈代码实现方法。
合作博弈模型可以用一个特征函数(characteristic function)来表示。
特征函数描述了博弈参与者之间的合作关系以及相应的收益分配方式。
以合作博弈中的N人问题为例,特征函数可以表示为:v(S):对于任意的联盟S,v(S)表示这个联盟合作所能获得的总收益。
基于这个特征函数,我们可以使用Shapley值(Shapley value)来确定参与者的个人收益。
Shapley值是一个有理分配方式,可以确保参与者之间的收益是公平和合理的。
为了实现合作博弈的代码,我们可以按照以下步骤进行:第一步:定义特征函数根据实际情况,我们可以首先定义特征函数v(S)。
这个函数可以是一个字典或一个矩阵,用来表示各个联盟合作所能获得的总收益。
第二步:计算Shapley值根据定义的特征函数,我们可以使用迭代的方法计算每个参与者的Shapley值。
Shapley值的计算方式如下所示:1. 初始化参与者的Shapley值为0;2. 对于每个参与者i,依次计算他参与所有可能的联盟所能获得的平均边际值;3. 将每个参与者的平均边际值累加到其对应的Shapley值上。
具体而言,我们可以使用以下伪代码来实现Shapley值的计算:```pythondef shapley_value(v):n = len(v) # 参与者的个数shapley = [0] * n # 初始化Shapley值为0for i in range(n):for j in range(2 ** n):if (j >> i) % 2 == 1:coalition = [k for k in range(n) if (j >> k) % 2 == 1]m = len(coalition)marginal_value = (v[coalition + [i]] - v[coalition]) / b(n - 1, m)shapley[i] += marginal_valuereturn shapley```第三步:应用代码在得到了Shapley值之后,我们可以根据实际需要进行进一步的分析和应用。
Abstract Interpretation of Programs for Model-Based Debugging
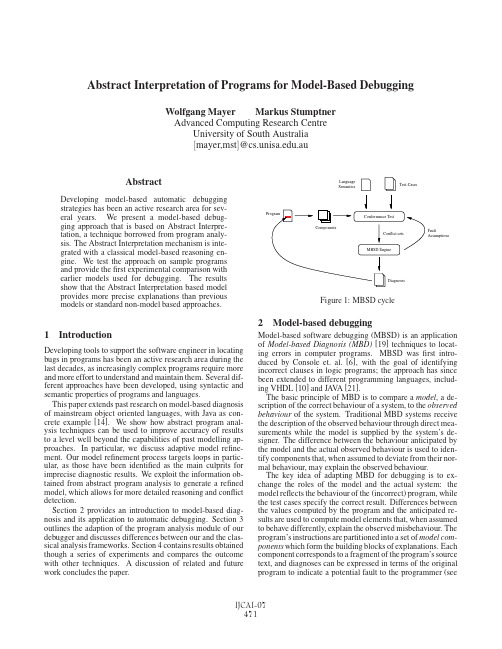
Abstract Interpretation of Programs for Model-Based Debugging Wolfgang Mayer Markus StumptnerAdvanced Computing Research CentreUniversity of South Australia[mayer,mst]@.auAbstractDeveloping model-based automatic debuggingstrategies has been an active research area for sev-eral years.We present a model-based debug-ging approach that is based on Abstract Interpre-tation,a technique borrowed from program analy-sis.The Abstract Interpretation mechanism is inte-grated with a classical model-based reasoning en-gine.We test the approach on sample programsand provide thefirst experimental comparison withearlier models used for debugging.The resultsshow that the Abstract Interpretation based modelprovides more precise explanations than previousmodels or standard non-model based approaches.1IntroductionDeveloping tools to support the software engineer in locating bugs in programs has been an active research area during the last decades,as increasingly complex programs require more and more effort to understand and maintain them.Several dif-ferent approaches have been developed,using syntactic and semantic properties of programs and languages.This paper extends past research on model-based diagnosis of mainstream object oriented languages,with Java as con-crete example[14].We show how abstract program anal-ysis techniques can be used to improve accuracy of results to a level well beyond the capabilities of past modelling ap-proaches.In particular,we discuss adaptive model refine-ment.Our model refinement process targets loops in partic-ular,as those have been identified as the main culprits for imprecise diagnostic results.We exploit the information ob-tained from abstract program analysis to generate a refined model,which allows for more detailed reasoning and conflict detection.Section2provides an introduction to model-based diag-nosis and its application to automatic debugging.Section3 outlines the adaption of the program analysis module of our debugger and discusses differences between our and the clas-sical analysis frameworks.Section4contains results obtained though a series of experiments and compares the outcome with other techniques.A discussion of related and future work concludes the paper.LanguageSemantics Test-CasesFaultAssumptionsFigure1:MBSD cycle2Model-based debuggingModel-based software debugging(MBSD)is an application of Model-based Diagnosis(MBD)[19]techniques to locat-ing errors in computer programs.MBSD wasfirst intro-duced by Console et.al.[6],with the goal of identifying incorrect clauses in logic programs;the approach has since been extended to different programming languages,includ-ing VHDL[10]and JA V A[21].The basic principle of MBD is to compare a model,a de-scription of the correct behaviour of a system,to the observed behaviour of the system.Traditional MBD systems receive the description of the observed behaviour through direct mea-surements while the model is supplied by the system’s de-signer.The difference between the behaviour anticipated by the model and the actual observed behaviour is used to iden-tify components that,when assumed to deviate from their nor-mal behaviour,may explain the observed behaviour.The key idea of adapting MBD for debugging is to ex-change the roles of the model and the actual system:the model reflects the behaviour of the(incorrect)program,while the test cases specify the correct result.Differences between the values computed by the program and the anticipated re-sults are used to compute model elements that,when assumed to behave differently,explain the observed misbehaviour.The program’s instructions are partitioned into a set of model com-ponents which form the building blocks of explanations.Each component corresponds to a fragment of the program’s source text,and diagnoses can be expressed in terms of the original program to indicate a potential fault to the programmer(seeFigure1).Each component can operate in normal mode,denoted ¬AB(·),where the component functions as specified in the program,or in one or more abnormal modes,denoted AB(·), with different behaviour.Intuitively,each component mode corresponds to a particular modification of the program. Example1The program in Figure2can be partitioned intofive components,C1,...,C5,each representing a sin-gle statement.For components representing assignments,a possible AB mode is to leave the variable’s value undeter-mined.Another possibility is to expand the assignment to a set of variables,rendering their values undetermined.For loops,the number of iterations could be altered.The model components,a formal description of the seman-tics of the programming language and a set of test cases are submitted to the conformance testing module to determine if the program reflecting the fault assumptions is consistent with the test cases.A program is found consistent with a test case specification if the program possibly satisfies behaviour specified by the test case.In case the program does not compute the anticipated re-sult,the MBSD engine computes possible explanations in terms of mode assignments to components and invokes the conformance testing module to determine if an explanation is indeed valid.This process iterates until one(or all)possible explanations have been found.Formally,our MBSD framework is based on Reiter’s the-ory of diagnosis[19],extended to handle multiple fault modes for a component.MBSD relies on test case specifications to determine if a set of fault represents is a valid explanation, where each test case describes the anticipated result for an execution using specific input values.Definition1(Debugging Problem)A Debugging Problem is a triple P,T,C where P is the source text of the pro-gram under consideration,T is a set of test cases,and C denotes the set of components derived from P.The set C is a partition of all statements in P and contains the building blocks for explanations returned by the debugger. For simplicity of presentation,it is assumed that there is a separate component for each program statement.A set of fault assumptionsΔˆ= {AB(C1),...,AB(C k)}is a valid explanation if the model modified such that components C i may exhibit deviating behaviour,while the remaining components exhibit normal behaviour,no longer implies incorrect behaviour. Definition2(Explanation)A fault assumptionΔis a con-sistent explanation for a Debugging Problem P,T,C iff for all test cases T∈T,it cannot be derived that all executions of P(altered to reflectΔ)violate T:∀Tˆ= I,O ∈T[[P⊕Δ⊕O]](I)=⊥.I and O represent the input values and assertions describing the correct output values specified in a test specification,re-spectively.[[·]]denotes the semantic function of the program-ming language and the fault assumptions.⊕denotes the ap-plication of the fault assumptions inΔand test assertions O to P.⊥denotes an infeasible program state.I:n→41int i=12int x=13while(i≤n){4x=x+i“correct is x=x∗i”5i=i+16}O:assert(x==24)Figure2:Example program and test specificationExample2Assume component C1representing line1of the program in Figure2is abnormal.In this case,there is no ex-ecution that terminates in a state satisfying x==24.There-fore,a fault in line1cannot explain the program’s misbe-haviour.In contrast,if the value of x is left undetermined after line2,an execution exists where the program satisfies the assertion.Therefore,C2is a potential explanation. While the definition of an explanation is intuitive,the pre-cise test is undecidable and must be approximated.Differ-ent abstractions have been proposed in the literature,ranging from purely dependency-based representations[10]to Pred-icate Abstraction[13].The following section introduces an approximation based on Abstract Interpretation[8],a tech-nique borrowed from program analysis.3Model constructionModels developed for VHDL and early models for Java were based on static analysis and represented the program as a fixed model representing the program’s structure.As test cases were not taken into account,it was necessary to repre-sent all possible executions and fault assumptions.While this approach has been used successfully to debug VHDL pro-grams,the dynamic method lookup and exception handling lead to large models for Java programs.Mayer and Stumptner[15]propose an approach where the model is constructed dynamically,taking into account only executions that are feasible given a test case.The ap-proach is based on Abstract Interpretation[8]of programs, generalised to take fault assumptions and test case informa-tion into account.In the following,the basic principles are introduced.More detailed presentations are given in[15; 16].3.1Abstract interpretationThe model is derived from a graph representing the effects of individual statements of the program.Definition3(Program Graph)A program graph for a pro-gram P is a tuple V,S ,Sω,E where V is afinite set of vertices,E⊆V×V a set of directed edges,and S ∈V and Sω∈V denote distinct entry and exit vertices.The vertices of the program graph represent sets of program states;the edges represent the effects of program instructions, transforming sets of program states into new sets of states. The initial vertex is associated with the initial program state I described by the test specification.An execution of a pro-gram starts in the initial state in S and proceeds following theC 5:[[i =i +1]]→4C 2:[[x =1]]C 4:[[x =x +i ]]C 1:[[i =1]]6n ]]ˆS=ˆI ˆS 1= [[i =1]](ˆS )ˆS 2= [[x =1]](ˆS3) ˆS 5ˆS 3=∇( [[i ≤n ]](ˆS 2),ˆS 3)ˆS 4= [[x =x +i ]](ˆS 3)ˆS 5= [[i =i +1]](ˆS4)ˆS6= [[i >n ]](ˆS 2)ˆSω= [[x ==24]](ˆS 6)Figure 3:Program graph and abstract equation system edges until the final vertex ωhas been reached.The program states in S ωrepresent the result computed by the program.Example 3Figure 3depicts the program graph derived from the program in Figure 2(where Δ=∅).Each program state-ment is represented as an edge,connecting the program state before the statement is executed to the successor state.The loop statement in line 3induces two possible successors:one transition representing the case where the loop is entered,and one transition representing loop termination.Starting in the initial state where n →4,the flow graph induces a trace that traverses the loop four times and the stops in S ωwith x →12.In case the initial state is not fully specified or parts of an intermediate state become undetermined due to fault assump-tions,a potentially infinite number of paths must be followed to determine the states in S ω.To ensure every analysis of the graph is finite,the concrete program states and the concrete semantics of the program are replaced with abstract versions.Formally,the Abstract Interpretation framework [8]uses complete lattices to repre-sent concrete (S )and abstract states (ˆS)such that ˆS ,⊥, , , , is a safe abstraction of P (S ),∅,S ,⊆,∪,∩ .⊥de-notes infeasibility and represents all possible states. rep-resents the abstract state ordering,and and denote the least upper bound and greatest lower bound operator,respec-tively.The key component in this framework is a pair of functions α,γ (“Galois connection”),where αmaps sets of concrete program states to their abstract representation and γimple-ments the reverse mapping.The semantic functions operatingon the abstract domain can then be defined as [[·]]ˆ=α◦[[·]]◦γ.An approximation of the program execution can be obtained by translating the program graph into a set of equations and computing the fixpoint solution.In case the abstract lattice is of infinite height and the program graph is cyclic,widening operators (∇)must be applied to ensure termination.Widen-ing operators selectively discard information from the ab-stract states to guarantee that the computation of mutually dependent equations eventually converges.Similar equations systems and fixpoint solutions can be de-rived for backward analyses,where for any given ˆSωan ap-proximation of S is computed such that the program is guar-anteed to terminate in a state in γ(ˆSω).In our work we apply a variant of Bourdoncle’s bidirectional method [2]where for-ward and backward analyses are applied repeatedly to refine approximations.Example 4Using backward analysis it can be derived that if the program in Figure 2should terminate in S ωwith i →24,then n ≤4must hold in S (assuming that n has been left undetermined in I ).3.2Dynamic model creationTo utilise Abstract Interpretation for debugging,Definition 2must be lifted to the abstract domain,replacing [[·]]and Iwith their abstract counterparts [[·]]and ˆI,respectively.For O translation is not necessary,as it is assumed that O is rep-resented as assertions in the programming language and canbe evaluated using [[·]].In our framework,we apply the well-known non-relational interval abstraction [8]to approximate concrete program states.Further,we use the simple abstraction described in [7]to ensure dynamically allocated data structures are repre-sented finitely.In contrast to purely static program analysis,we do not assume a fixed program graph modelling all possible execu-tions.Instead,the graph is constructed dynamically,using in-puts I and assertions O from the test case specifications.Only the paths that may be executed when starting in a state I are created.Paths that contain ⊥are ignored.Once a program state is reached where multiple paths could be followed,we apply the conventional equation-based analysis to the remain-ing execution.Our framework can thus be placed in the mid-dle grounds between purely static analysis [8]and dynamic analysis [9].The algorithm for determining consistency for a program P with fault assumptions Δand test case T is outlined as follows:1.Add the assertions in T to P and apply Δto P .2.Construct the initial program graph using the forwardabstract semantics [[·]]and initial state ˆI.3.Apply backward analysis to approximate the initial pro-gram states not implying assertion violations later in the execution.4.Analyse program graph in forward direction using the new initial program states to eliminate values that cannot be realised.5.Repeat from step 3until a fixpoint is reached.6.In case the initial program state is is ⊥,no execution satisfying all test case specifications can be found and Δis not a valid explanation.Otherwise,Δis consistent and another test case is considered.The benefits of the dynamic approach are as follows:(i)The equation system is concise.This is a significant advantage when dealing with paths representing excep-tions,as in Java runtime exceptions may be thrown by a large number of statements.However,typically only a few of these paths are actually followed in an execution.(ii)Ambiguity in controlflow is reduced compared to the purely static approach.This is an important advan-tage for the precision of the abstraction of dynamic data structures,which deteriorates dramatically in the pres-ence of loops in the program graph.(iii)Simple non-relational abstractions are sufficient to ob-tain good results if values for most related variables are known.Expressions can be partially evaluated,leading to tighter bounds for the remaining variables.(iv)In case all values potentially accessed by a called method are known in a program state and the method does not include AB components,thefixpoint compu-tation can be replaced with native execution.Thefixpoint analysis is limited to the regions of the execu-tion where the values of abstract states critical to the region’s execution are undetermined.As many fault assumptions af-fect only a minor part of a program state,execution can pro-ceed normally in unaffected regions.Consequently,many al-ternative branches that must be considered by purely static Abstract Interpretation can be eliminated.Example5Assume that the MBSD examinesΔ= {AB(C4)}for our running example.In this case,execu-tion proceeds normally until line4is reached.The execution of AB(C4)leads to a state where i→1and x is unde-termined.As i is known,the execution of statement5can proceed normally and no ambiguity in the controlflow arises at line3.In fact,the entire trace reduces to a linear chain. Backward analysis derives that the value of x must hold af-ter statement4was last executed.The remaining occurrences of x have undetermined values.Since the initial state in the graph is not⊥,Δis consistent and is considered a valid ex-planation.3.3Iterative refinementThe partially determined abstract states facilitate further iter-ative model refinement.Abstraction of the effects of loops and recursive method calls can be improved if the known states before and after a loop or method call contain conflict-ing values.In this case,the execution is either inconsistent, or the loop(or method)must be expanded further.In case the loop(call)has been shown to terminate(for example, through syntax-based methods presented in[16])or a limit on the number of iterations(recursive calls)has been set by the user,the loop(call)can be expanded.As a result,values lost through widening and heap abstraction may be regained, potentially leading to a contradiction elsewhere.Similar im-provements can be achieved through informed restructuring of the model based on automatically derived or user-specified properties of program regions.For space reasons we illus-trate the refinement approach in the context of our running example and rely on[16]for more detailed discussion. Example6Assume the MBSD engine examines the candi-date explanationΔ={AB(C3)}.As the loop condition is assumed incorrect,the loop condition cannot be evaluated uniquely.This implies that the number of loop iterations is not known and the program state S6after the loop is approx-imated using intervals:S6:x→[1..∞),i→[1..∞).The upper bound of the intervals is due to the widening opera-tor.The assertion x==24may be satisfied in S6,leading to Sω:x→24,i→[1..∞).Backward analysis reveals that x→24must also hold after the loop.This state con-flicts with the program state before the loop,which contains x→1.Subsequently,the loop is expanded in an attempt to prove thatΔdoes not represent the true fault.The pro-cess repeats and stops after six expansions,leading to a state S6:i→[8..∞],x→[29..∞].At this point,it can be proved that the assertion is violated and Sω:⊥.A subsequent back-ward pass derives S :⊥and eliminatesΔfrom the set of potential explanations.3.4Fault assumptions/structuralflawsSimilar to model-based hardware diagnosis[1],previous MBSD approaches have great difficulty with faults that mani-fest as structural differences in the model.The dynamic mod-elling approach described here is moreflexible in that fault assumptions modifying variables that were originally not af-fected by a component’s behaviour can now be addressed appropriately.The modelling of dynamically allocated data structures benefits in particular,as the scope of fault assump-tions can now be determined more precisely compared to the crude modelling in previous MBSD approaches,which led to a large fraction of undesirable explanations.Together with more expressive specifications of the correct behaviour[17], we believe that extended fault modes can deal effectively with complex faults.4EvaluationThis section presents experimental results obtained from the model described in the previous sections and compares the results with other MBSD approaches,as well as results ob-tained by Slicing[20].Readers interested in a theoretical comparison of the different models are referred to[18].4.1SlicingThe classic principle of Program Slicing[20]is to eliminate all statements from a program that cannot influence the value of a distinguished variable at a given location in the program. The pair V ariable,Location denotes the slicing criterion. The working hypothesis is that typically,only a small fraction of a program contributes to a variable’s value;the rest can be pruned away to reduce debugging effort.Static backward slicing starts at the variable and location mentioned in the slicing criterion and recursively collects all statements that may influence the variable’s value in any pro-gram execution.Further,all statements that may cause the location to be skipped are also included.This process repeats until afixpoint is reached.While static slices can be com-puted quickly even for large programs,the remaining pro-gram often remains large.Dynamic slicing aims at reducing the number of statements by considering only dependencies that arise between state-ments executed for a particular test case execution.Similar to static slicing,dependencies for a variable are followed and all statements contributing to the variable’s value are collected. While dynamic slices are typically much smaller than their static counterparts,for programs with many control depen-dencies or long data-flow chains,results remain similar. Example7The static slice of the program in Figure2w.r.t. the slicing criterion i,6 includes statements1,3and5.Theremaining statements are ignored as they are not relevant for the computation of i.For this test case dynamic slicing com-putes the same result.The difference between the two ap-proaches can be seen in case the loop is executed only once: The static slice for x,6 contains all statements,while the dynamic slice does not include statement5.4.2Dependency-based MBSDA number of dependency-based MBSD approaches have been introduced in[21].Wotawa[22]has shown that these ap-proaches provide results equivalent to static or dynamic slic-ing in case only a single abnormal variable is observed.In the following,we limit our attention to results obtained through slicing without explicitly stating that the same results hold for dependency-based MBSD.4.3Value-based MBSDValue-based Models(VBM)[14]extend beyond simple de-pendency tracking and model the effects of program state-ments explicitly.In contrast to the Abstract Interpretation-based approach discussed here,the VBM does not abstract from the concrete semantics and relies on statically con-structed models.While the model is effective for programs where dependency-based representations do not provide ac-curate results,the poor abstraction causes the model to col-lapse when loop iterations or recursive method calls cannot be determined precisely.4.4Experimental resultsA set of test programs have been used to evaluate the perfor-mance of different debugging approaches.Some programs were taken from the Siemens Test Suite1(transcribed to Java), a debugging test bench commonly used in the debugging community;others have been retained from earlier tests of the VBM and dependency-based models.A summary of he results obtained is given in Figure4. LoC denotes the number of non-comment lines in the pro-gram’s source code,Comp represents the number of diagno-sis components used to construct explanations,SSlice,DSlice and Exec denote the number of statements in the static slice, dynamic slice and the number of executed statements,respec-tively.VBM and AIM denote the number of statements re-turned as potential explanations for the VBM and the model described in this paper,and Time is the average diagnosis time in seconds(wall-clock time)required for the AIM.The results of the AIM and the VBM are limited to single fault explana-tions.Due to limitations of the implementation of the VBM, some diagnoses listed for the AIM may not be included in the VBM’s results.Initial experiments with multiple faults indi-cated that the number of explanations does not differ signifi-cantly from static slicing and does not warrant the additional overhead necessary for the AIM and VBM.For each program,n variants with different faults were cre-ated and tested with up to eight test cases per variant.The test results reported are the averages for each program over all variants and test cases.Slight improvements could be ob-served when using two rather than a single test case;no sig-1/aristotle/ Tools/subjects/nificant differences could be detected in any of the test pro-grams(with the exception of Adder)when using more than two test cases.This can be attributed to the structure of the selected programs,where a large fraction of statements and test cases are executed for all test cases.It can be seen that static slicing and dynamic slicing in many cases cannot improve much compared to the entire pro-gram and the statements executed in test cases.Similarly,dy-namic slices often improve little compared to the executed statements,as all statements contribute to thefinal result. Comparing VBM and AIM,it can be seen that the AIM im-proves over the VBM in most cases.In fact,the case where the VBM provides fewer explanations is due to explanations missed by the paring AIM and slicing:the AIM provides significantly fewer explanations,but is computation-ally more demanding.(Slicing approaches typically compute solutions in a few milliseconds).Note that VBM and AIM are not currently optimised for speed and rely on a Java inter-preter written in VisualWorks Smalltalk.5Related WorkDelta Debugging[5]aims at isolating a root cause of a pro-gram failure by minimising differences between a run that exhibits a fault and a similar one that does not.Differences between program states at the same point in both executions are systematically explored and minimised,resulting in a sin-gle“root cause”explaining why the program fails.Model checking has recently been applied to locate faults[11;3]by comparing abstract execution traces leading to correct and erroneous program states.Likely causes for a misbehaviour can be identified by focussing on traces that deviate only slightly from passing and failing test cases. Error traces have also been applied to synthesise poten-tial corrections of faulty programs,given a specification of the program’s correct behaviour[12].Symbolic evaluation is used to compare symbolic representations of program states as computed by the program versus states necessary to satisfy the post condition of the program.Differences in the pred-icates allow to heuristically synthesise replacement expres-sions correcting single faults in the program.The approach is able to provide corrections automatically only if a formal specification is given,which is not required for MBSD.6ConclusionWe introduced the basic principle of model-based software debugging and illustrated a model centred around abstract simulation of programs.Differences to previous approaches were outlined and results obtained using different debugging strategies were compared.Notable improvements over other approaches have been achieved,in particular for“difficult”programs where traditional debugging techniques do not per-form well.The Abstract Interpretation based model has been shown to achieve considerable improvement compared to slicing and previous model-based debugging approaches,with a reduc-tion of the average number of explanations from81%for static slicing to roughly26%.Conversely,the model is com-putationally more demanding and will require optimisation to be applicable to mid-sized or large programs in an interactive setting.Name n LoC Comp SSlice DSlice Exec VBM AIM Time(s) Adder5493124.32229.29.87.610.9 BinSearch62924.924.920.520.56 3.612.2 Binomial7804532.427.432(9)9.872.6 BubbleSort52911111010648 Hamming648383830.930.911 5.2218.3 Permutation554252524.424.410.3879 Polynom910366.939.82837.51412584.4 SumPowers7271614.811.412.3107.4 3.8 TCAS87842423535.5n/a2034.5 Total 6.455.533.727.522.725.89.58.9115.5 %81.667.476.628.226.4Figure4:Debugging resultsCurrent ongoing and future work includes(i)broadening fault modes to deal with a wider range of complex faults,such as assignments to incorrect variables,missing or swapped statements,etc.,and(ii)providing simple user interaction for incremental specification of complex program behaviour.Re-cent advances in automatic abstraction and program verifica-tion[4]could lead the way to an MBSD engine with a fast but powerful adaptive abstract conformance checker.References[1]Claudia B¨o ttcher.No faults in structure?How to diag-nose hidden interaction.In Proc.IJCAI,1995.[2]Franc¸ois Bourdoncle.Abstract debugging of higher-order imperative languages.In Proc.SIGPLAN Conf.PLDI,pages46–55,1993.[3]Sagar Chaki,Alex Groce,and Ofer Strichman.Explain-ing abstract counterexamples.In Richard N.Taylor and Matthew B.Dwyer,editors,SIGSOFT FSE,pages73–82.ACM,2004.[4]Edmund Clarke,Daniel Kroening,Natasha Sharygina,and Karen Yorav.Predicate abstraction of ANSI-C pro-grams using SAT.Formal Methods in System Design, 25(2-3):105–127,2004.[5]Holger Cleve and Andreas Zeller.Locating causes ofprogram failures.In Gruia-Catalin Roman,William G.Griswold,and Bashar Nuseibeh,editors,ICSE,pages 342–351.ACM,2005.[6]Luca Console,Gerhard Friedrich,and Daniele Thesei-der Dupr´e.Model-based diagnosis meets error diagno-sis in logic programs.In Proc.13th IJCAI,pages1494–1499,1993.[7]James Corbett,Matthew Dwyer,John Hatcliff,Co-rina Pasareanu,Robby,Shawn Laubach,and Hongjun Zheng.Bandera:Extractingfinite-state models from Java source code.In Proc.ICSE-00,2000.[8]Patrick Cousot and Radhia Cousot.Abstract interpreta-tion:A unified lattice model for static analysis of pro-grams by construction of approximation offixpoints.In POPL’77,pages238–252,1977.[9]Michael D.Ernst,Adam Czeisler,William G.Griswold,and David Notkin.Quickly detecting relevant program invariants.In Proc.ICSE-00,pages449–458,2000.[10]Gerhard Friedrich,Markus Stumptner,and FranzWotawa.Model-based diagnosis of hardware designs.In Wolfgang Wahlster,editor,ECAI,pages491–495.John Wiley and Sons,Chichester,1996.[11]Alex Groce and Willem Visser.What went wrong:Explaining counterexamples.In Thomas Ball and Sriram K.Rajamani,editors,SPIN,volume2648of Lecture Notes in Computer Science,pages121–135.Springer-Verlag,2003.[12]Haifeng He and Neelam Gupta.Automated debuggingusing path-based weakest preconditions.In Michel Wer-melinger and Tiziana Margaria,editors,FASE,volume 2984of Lecture Notes in Computer Science,pages267–280.Springer-Verlag,2004.[13]Daniel K¨o b,Rong Chen,and Franz Wotawa.Abstractmodel refinement for model-based program debugging.In Proc.DX’05,pages7–12,2005.[14]Cristinel Mateis,Markus Stumptner,and Franz Wotawa.A Value-Based Diagnosis Model for Java Programs.InProc.DX’00Workshop,2000.[15]Wolfgang Mayer and Markus Stumptner.Model-baseddebugging using multiple abstract models.In Proc.AADEBUG’03Workshop,pages55–70,2003. [16]Wolfgang Mayer and Markus Stumptner.Debuggingprogram loops using approximate modeling.In Proc.ECAI,2004.[17]Wolfgang Mayer and Markus Stumptner.High level ob-servations in java debugging.In Proc.ECAI,2004. [18]Wolfgang Mayer and Markus Stumptner.Model-baseddebugging–state of the art and future challenges.In Workshop on Verification and Debugging,2006. [19]Raymond Reiter.A theory of diagnosis fromfirst prin-ciples.Artificial Intelligence,32(1):57–95,1987. [20]Frank Tip.A Survey of Program Slicing Techniques.Journal of Programming Languages,3(3):121–189, 1995.[21]Dominik Wieland.Model-Based Debugging of JavaPrograms Using Dependencies.PhD thesis,Technische Universit¨a t Wien,2001.[22]Franz Wotawa.On the Relationship between Model-Based Debugging and Program Slicing.Artificial Intel-ligence,135(1–2):124–143,2002.。
核间通信机制 英语

核间通信机制英语Inter-core communication is a crucial aspect of modern computing, enabling processors to efficiently share data and coordinate tasks. When you think about it, it's like having a team of experts working in the same office but specialized in different areas. They need to communicate quickly and effectively to achieve their common goals.In the digital world, these "experts" are the cores of a processor, and the office is the motherboard. Each core has its own responsibilities, but they all need to be on the same page to get the job done. So, how do they communicate? Well, there are various methods, ranging from shared memory to message passing protocols.Think of shared memory as a whiteboard in the office. Everyone can see it and write on it. In the processor, cores can access the same memory locations, making data sharing a breeze. However, this also requires careful synchronization to avoid conflicts and ensure dataintegrity.On the other hand, message passing protocols are more like sending notes or emails. Cores send messages to each other containing the necessary information. This approachis more decoupled, allowing for more flexibility and scalability. But it also adds some overhead, as messages need to be packaged, sent, and received.The choice of communication mechanism depends on the specific application and requirements. For example, inhigh-performance computing, shared memory may be preferred for its speed and low latency. While in distributed systems, message passing may be more suitable due to its scalability and fault.。
BPMN 2.0 跨平台互操作性标记:使交流数据中的互操作性问题显现说明书

Interoperability Markers for BPMN 2.0Making Interoperability Issues ExplicitXabier Heguy1, Gregory Zacharewicz2,*, Yves Ducq3 and Said Tazi41University of Bordeaux, IMS, UMR 5218 CNRS, Talence – France and ONETIK, D252, 64240 Macaye – France 2,3University of Bordeaux, IMS, UMR 5218 CNRS, Talence – France4University of Pau, Pau, – France*Corresponding authorAbstract—Business Process Model and Notation (BPMN) is being becoming the most used standard for business process modelling. One of the important upgrades of BPMN 2.0 with respect to BPMN 1.2 is the fact that Data Objects are now handling semantic elements. Nevertheless, BPMN doesn't enable the representation of interoperability problems in the exchanged data object, which remains a limitation when using BPMN to express interoperability issues in enterprise processes. We propose to extend the Meta-Object Facility meta-model and the XML Schema Definition of BPMN as well as the notation in order to fill this gap. The extension, named Data Interoperability, is defined using the BPMN Extension Mechanism. This new elements will allow to represent existing interoperability problems as well as interoperability concerns which have been solved. We illustrate the Data Interoperability capabilities with an example from a real industrial case.Keywords-interoperability; BPMN; modelling; CBPI.I NTRODUCTIONThe global economic context requires enterprises to acquire and maintain an efficient information system. An adapted and well-defined ERP is today a sine qua non condition for the success of a company. In addition, exchanges of information between various information systems are increasingly necessary: In particular, information exchanges is growing with customers, suppliers, subcontractors or when the enterprise is bought out and integrated in another company, but also within an internal department. Also, assuming one ERP covering all sectors of the company is not always possible, which entails grafting many heterogeneous ERP or at least modules. The crucial problem of interoperability then arises.Cross-organizational Business Process (CBP) modeling aims to describe the interactions between different organizations [1] but also between different systems within a single organization. Process modeling at the highest level should enable the various partners to understand the articulation of the different processes in a simple and intuitive way. However, defining user needs is not necessarily collaborative. Users rarely understand the differences between inter-organization processes and internal processes.BPMN 2.0 [2] is a de facto standard in the modeling of business processes. BPMN is currently the most used language among process modelers (64% of industry penetration according to P. Harmon's study) [3]. It provides a meta-model and notation for defining and visualizing them. BPMN 2.0 allows the modeling of CBP by clearly identifying independent resources pools and collaborative swim lanes within the same resource group. However, the representation of data in BPMN 2.0 does not reflect the concept of interoperability. Whether data is exchanged within the same information system or between two entities, the representation of the data remains the same. This is a weakness because this model hides the challenge and the difficulty of solving interoperability problems, in particular in the eyes of decision-makers. This lack of visibility can lead to incomprehension between IT technicians and managers and may lead them to underestimate both the impact of the lack of interoperability in the representation of the existing system and to make difficult the evaluation of costs and delays to produce the system to set up.The technical structuring of BPMN is based on the concept of extensible layers around a core set of basic elements. This extensibility makes it possible to define an overlay of elements in order to better represent concepts inherent in the targeted sector of activity. Each new layer is constructed in extension of a lower layer. BPMN extensions are most often used to represent the specific needs of an industry [4]. But they can also be used to fill a general gap. This is the proposition of this paper: Prolonging the BPMN model specification by adding an extension representing the data concerned by interoperability.II.P ROBLEM S TATEMENT AND B ACKGROUNDA.Problem StatementThe problem tackled in this paper is a lack of modeling data in a context of interoperability in BPMN. We propose to fill this gap defining a BPMN 2.0 metamodel extension to represent data interchanges with an interoperability problem. It will allow defining barriers and solved problems.B.CBPs Modeling RequirementsWhether they are interchanges between customers, suppliers or providers, or between different information systems within a company, data interchanges are more and more necessary. In order to ensure a decent implementation of these interchanges, a preliminary model is an essential stage.The goal of CBP modelling is to describe the interactions between different systems [1]. The processes modelling at the higher level must allow to the various partners to understand2nd International Conference on Electrical, Automation and Mechanical Engineering (EAME 2017)the articulation of the processes in a simple and intuitive way. The model has to be easily understandable by all parts, be they managers, processes owners or IT technicians who will have to implement the system. But user-driven requirements are not necessarily collaboration-oriented. Hence, users hardly understand the differences between internal business processes and cross-organizational processes, and thus the difficulties that these last ones represent.For a successful CBP modelling, interoperability points have to be necessarily shown. The managers and the users of the different organizations must be able to represent interaction from a high level business point of view in order to visualize data interchanges with interoperability problem. Thus, they will be able to grasp them. Hence, resolving interoperability problems involves an enhancement of the work.C.BPMN Shortcomings.One of the important upgrades of BPMN 2.0 with respect to BPMN 1.2 is the fact that Data Objects are now semantic elements defined as additional Data Categories aside form swim-lanes, flow objects, connecting objects and artifacts (whereas in the precedent version, they were considered as simple artifacts, simple annotation without any semantic).However, BPMN 2.0 does not distinguish between data with an interoperability issue. In order to represent the exchange of data between different systems, the corridors (swim lanes) [1] are used. However, the notion of interoperability is absent from this representation, because if we distinguish between different systems, there is no indication that the data exchanged can be integrated as such in the target system or that Must undergo pre-treatment. A modeling of CBP carried out using BPMN 2.0 therefore does not allow the different actors to understand the problem of interoperability in the exchange of data.We propose to enrich the BPMN meta-model with the addition of a Data Interoperability object which will mean that a data exchange must take into account interoperability.D.InteroperabilityThe most common definition of interoperability tells us that it is: "the ability of two (or more) systems or components to exchange information and use it" [5]. The InterOp NoE Network of Interoperability (Interoperability) defined interoperability as "the ability of a system to work with another system without effort on the part of the user" [6]. To complement these definitions we can say that interoperability is “the ability of systems, natively independent, to interact in order to build harmonious and intentional collaborative behaviors without deeply modifying their individual structure or behavior” [7]. These definitions demonstrate that interoperability is rapidly becoming complex and that its success depends on the resolution of a number of barriers [8]. rmational Perspective of BPMN 2.0We present here an overview of BPMN's informational perspective. In BPMN, the construct that allows modeling any type of information entity, regardless of its nature (electronic document, paper, etc.) is the Data Object [2]. In BPMN 2.0, Data Objects become first-class elements at the same level as tasks or activities [9]. They are visually represented in the process diagrams. Data can be referenced by DataObjectReference that specifies different states of the same object. The structure of the Data Objects is not visible in the diagrams, but can be defined by the itemDefinition element associated with it by specifying it in an XML schema. The data are represented graphically by the Data Objects as (Figure I).FIGURE I.BPMN DATA OBJECTF.BPMN Extension Mechanism.BPMN has been designed to be extensible. The technical structuring of BPMN is based on the concept of extensible layers around a core of simple elements. Extensibility is used to define an overlay of elements to better represent concepts inherent in the targeted industry. Each new layer is constructedin extension of a lower layer. BPMN provides generic extension elements in the meta-model.The BPMN extension mechanism consists of a set of extension elements that allow the addition of additional elements and attributes for standard and existing BPMN elements. These extension elements are: ExtensionDefinition, ExtensionAttributeDefinition, ExtensionAttributeValue and Extension. The Extension element is used to connect to the BPMN model an extension whose structure is defined using the ExtensionDefinition element. This adds additional attributes used to extend the BPMN model by attaching them to any BPMN element. The definition of each attribute includes the name and type of the attribute; given by the corresponding ExtensionAttributeValue element. In a BPMN extended element, ExtensionAttributeValue is used to assign a value to a extension attribute that was defined in the ExtensionDefinition by using ExtensionAttributeDefinition element.III.R ELATED W ORKSSeveral works treats of the problems of interoperability in data interchange between different Information Systems. Wexin Mu [11] focuses on automatically generate the cartography of collaborative processes. His method consists first in gathering knowledge of partners’ data, then building a repository of partners’ services and finally deducing a collaborative process model that can run and a workflow engine that enables to run it. Among the different modelling languages he uses, we can find BPMN. But he does not represent the problems of interoperability in his models.The approach of Jankovic et. al. [9] relates to ours since they propose an extension of BPMN 2.0 meta-model to represent information requirements in BPMN 2.0. They state that information requirements should be specified in terms of a common, reference ontology. Their methodology is based on the use of reference ontology as an unambiguous and formal representation of a set of business concepts and their relationships for a particular CBP environment. Thus, they exclude technological and organizational barriers. Furthermore,this BPMN extension is directed only to IT technicians and not to managers and processes owners.All mentioned works cover the problems of interoperability in data interchange between different Information Systems. But the goal of these works is to help the job of IT technicians. This is surely useful, but it doesn’t offer a possibility to make these problems visible for all the collaborating business partners (and not only IT technicians). With the extension we define in our work, we offer the possibility of that shared understanding, which is one of the main goals of BPMN.IV.E XTENSIONSPurpose: Our aim is to create a sustainable (conservative) extension of BPMN, which allows representing interoperabilityin data exchanges in the framework of process diagrams. This new extension can be used in very different business contexts, whether in inter-company data exchanges, in web applications, etc. It will make possible to represent explicitly and intuitivelythe exchanges of data presenting an interoperability problem.Framework: In order to explicit interoperability problemsin BPMN data exchanges, we introduce two extensions: dataInteroperabilityBarrier and dataInteroperabilitySolute.The first (dataInteroperabilityBarrier) represents a data exchange with an unresolved interoperability problem. It allows representing this drawback so that all the participants ofthe project (managers, IT technicians, owners of the process, etc.) can realize that there is a problem to solve. Its aim is notto enter into technical considerations. Ideally, it should be used only in existing modeling (AsIs), since the realization of the project should include resolution of the difficulty. But it can be assumed that in some cases, for various reasons (lack of funding or time for example) no solution will be put in place. This extension can thus also be part of the modeling of the future system (ToBe).The second extension (dataInteroperabilitySolute) will be used to represent an overcoming interoperability issue. As such,it should have its place only in the modeling of the project of the future system (ToBe).A.StructureWe used the extension mechanism of BPMN 2.0 to define the extension of the BPMN meta-model. It allows the inclusionof the definition of the interoperability document template. The structure of the proposed element is defined by the ExtensionDefinition and ExtensionAttributeDefinition elements. The structure of BPMN is described using two representations: a Meta-Object Facility (MOF) meta-model that describes the concepts and an XML Schema Definition (XSD) that establishes the format of exchanges [10]. The MOF class diagram of the BPMN meta-model is visible in the specification manual. It is divided into different sections. We will only represent here that which concerns the data objects. The classes corresponding to the extensions we propose are represented in gray in Figure II.This illustration shows that dataInteroperabilityBarrier and dataInteroperabilitySolute extend dataObject. These two classes therefore inherit its attributes and models of association.FIGURE II.BPMN CLASS EXTENSION.No additional attributes are defined. It would have beeninteresting to associate an association constraint with these two extensions: that they can only be linked to tasks belonging to different corridors. Indeed, a problem of interoperability can only exist between different systems, represented by distinct corridors. But in the basic structuring of BPMN, any source task can be linked to any target task. We have respected this flexibility. It is therefore up to the modelers to take account of this flexibility and not to use these extensions properly, that is to say between two tasks belonging to different corridors.V.G RAPHICAL R EPRESENTATIONWe propose to provide the following graphical representations for the interoperability extensions in figure III.(a)(b)FIGURE III. DATAINTEROPERABILITYBARRIER ANDDATAINTEROPERABILITYSOLUTEWe have extended the graphical representation of the Data Object to which we have added two inverse arrows, representing interoperability. The barred means that interoperability is not assured, as presented in Figure III left (a): dataInteroperabilityBarrier, is placed in the BPMN model with the same rules and constraints as the Data Object. In case of dataInteroperabilitySolute extension, Figure III right (b), the representation is similar, except the arrows are not barred, indicating that interoperability is assured.VI.U SE C ASETo illustrate the interest of dataInteroperabilityBarrier and dataInteroperabilitySolute extensions, we will study the case of Onetik SME. This company of the Basque Country manufactures and markets cheeses. It uses the Nodhos ERP. The shipment management module of this ERP does not give it complete satisfaction, and its use is source of errors and therefore, among other things, disputes with customers that are costly for the company. The replacement of the ERP is not envisaged in the short term mainly for financial reasons. The management of Onetik has then decided to graft the shipment management module of another ERP (Integraal Agro).In the framework of this project, two models were carried out using BPMN: one is corresponding to the existing system (AS IS) and the other to the desired system (TO BE). Each model consisted of several models of the various processes. We will represent the (simplified) process of order preparation.This AS IS model (Figure IV) is representing real case proposed by the current organization of the information system in the enterprise. This is to be developed by describing the problem faced by the enterprise and the problem that isengendered by this situation.FIGURE IV.DATAINTEROPERABILITYBARRIER On the TO BE model (Figure V), it can be seen that the BP document must be transmitted from the Nodhos ERP to the Integraal Agro module. The transmitted data is represented by the dataInteroperabilitySolute icon to specify that an interoperability problem among the two tasks has to be solved.FIGURE V.DATAINTEROPERABILITYSOLUTE Similarly, once the package has been weighed, the BP, together with the weight of the package and the batch number of the cheeses used, is transmitted in the opposite direction (from Integraal Agro to Nodhos).VII.P ERSPECTIVES AND I MPLEMENTATION These works are still under development. The next phase will consist in implementing the proposition within a software solution. The SLMToolBox [11] has been selected for its capacity to integrate a Model Driven approach, BPMN 2.0 models and simulation aspects. This extension will be validated and then will be the baseline for representing performance aspects on the BPMN model. We are working now on extending on performance aspects in the process modeling. We will refer to reference works in this domain such as the works of [13] and [14].VIII.C ONCLUSIONThis paper is proposing an extension to BPMN 2.0 in the context of interoperability identification and solving. This extension makes explicit the modeling of interoperability barriers and problem solved thanks to two graphical icons added to the original data item of BPMN. The interest of this approach has been illustrated on a use case from industry. These new features of BPMN allow bringing to light to all participants of a CBP project (managers, IT technicians, processes owners, etc.) the presence of an interoperability barrier and its solution.REFERENCES[1]ATHENA, D.A2.1: Cross-Organisational Business Process requirementsand the State of the Art in Research, Technology and Standards Version2. ATHENA Project No. (507849), 2005[2]OMG, OMG: MDA Guide Version 1.0.1, /mda/ 2003[3]Harmon, The State of Business Process Management 2016. BusinessProcess Trends, 2016[4]Braun R., W. Esswein, Classification of domain-specific bpmnextensions, in: The Practice of Enterprise Modeling, Springer, 2014 [5] A. Geraci, Katki F., McMonegal L., Meyer B., Lane J., Wilson, P.,Radatz J., Yee M., Porteous H., and Springsteel F., IEEE standard computer dictionary: Compilation of IEEE std computer glossaries, 1991 [6] D. Konstantas., Bourrières J. P., Léonard M., and Boudjlida N.,Interoperability of enterprise software and applications, 2005[7]S. Truptil, F. Bénaben, H. Pingaud. A Mediation Information System toHelp to Coordinate the Response to a Crisis. Luis M. Camarinha-Matos;Xavier Boucher; Hamideh Afsarmanesh. Collaborative Networks for a Sustainable World, 336, Springer, pp.173-180, 2010, IFIP Advances in Information and Communication Technology, 978-3-642-15960-2.[8] D. Chen, N. Daclin, Framework for Enterprise Interoperability, In book:Interoperability for Enterprise Software and Applications: Proceedings of the Second IFAC/IFIP I-ESA International Conference: EI2N, WSI, IS-TSPQ 2006, pp.77 - 88 2006[9]M. Jankovic, M. Ljubicic, N. Anicic, and Z. Marjanovic, EnhancingBPMN 2.0 Informational Perspective to Support Interoperability for Cross-Organizational Business Processes, 2015[10]M. Cortes-Cornax, S. Dupuy-Chessa, D. Rieu and M. Dumas,Evaluating Choreographies in BPMN 2.0 Using an Extended Quality Framework, 2014[11]H. Bazoun, Y. Bouanan, G. Zacharewicz, Y. Ducq, Hadrien Boye:Business process simulation: transformation of BPMN 2.0 to DEVS models (WIP). SpringSim (TMS-DEVS) 2014: 20[12]W. Mu, Caractérisation et logique d'une situation collaborative, 2012[13] C.J. Pavlovski, J., Zou, (2008). Non-functional requirements in businessprocess modeling. In proceedings of the fifth Asia-Pacific conference on Conceptual Modelling, Vol. 79, pp. 103-112, Australian Comp. Soc., Inc.[14]K. Saeedi, L., Zhao, P., Sampaio, (2010). Extending BPMN forsupporting customer- facing service quality requirements. In Web Services (ICWS’10), pp. 616–623.。
基于议价博弈论的无线协作中继网络性能改进算法

3 Sa e aoa r o ol eor s n a ii , uhu2 10 , h a .teK yLb r o f a R s c dSf M n g X zo 20 8 C i ) t ty C u e a e n n
Abt c:o m ly — d—owr( F addcd —ad —o ad D ) rt o i sls opr i e. s atFr p f—a —f ad A 、 n eoe— —f r( F po cln e hc ea v nt r a i n r n w r法
刘 鹏 徐 秀2 , 思 园 , , ,巩 一 丁恩杰
(. 1中国矿业大学 感 知矿山物联 网研究 中心 , 江苏 徐州 2 10 ; . 2 08 2 中国矿业大学 计算机科 学与技术 学院 , 江苏 徐州 2 11 ;. 2 16 3 中国矿业 大学 煤炭 资源 与安全开采 国家重点实验室 , 江苏 徐州 2 10 ) 20 8
Pe f r a c m p o e e tAl o ih s Ba e n Ba g i i r o m n e I r v m n g rt m s d o r a n ng
Ga e The r o ie e s Co p r tv l y Ne wo k m o y f r W r l s o e a i e Re a t r s
雷德朋体系设计原则

雷德朋体系设计原则雷德朋体系设计原则是一种用于软件系统架构设计的方法论,旨在提高系统的可靠性、可维护性和可扩展性。
本文将介绍雷德朋体系设计原则的四个基本原则,分别是单一职责原则、开放封闭原则、里氏替换原则和依赖倒置原则。
一、单一职责原则单一职责原则(SRP)要求一个类或模块只负责完成一个职责或功能。
这意味着一个类应该只有一个引起它变化的原因。
通过将一个类的职责进行细分,可以提高代码的可读性、可维护性和重用性。
如果一个类承担了过多的职责,那么当其中一个职责发生变化时,可能会影响到其他职责的实现,导致系统的不稳定。
二、开放封闭原则开放封闭原则(OCP)要求软件实体(类、模块、函数等)应该对扩展开放,对修改封闭。
这意味着在系统需要进行变化时,应该通过扩展现有的实体来实现,而不是去修改已有的实体。
通过遵循开放封闭原则,可以有效地降低系统的维护成本,提高系统的可维护性和扩展性。
三、里氏替换原则里氏替换原则(LSP)是指在一个软件系统中,子类应该能够替换掉父类并且不会产生任何错误或异常。
也就是说,子类的行为应该符合父类的行为规范。
通过遵循里氏替换原则,可以提高代码的可复用性,降低系统的耦合度,提高系统的稳定性。
四、依赖倒置原则依赖倒置原则(DIP)是指高层模块不应该依赖于低层模块,两者都应该依赖于抽象。
抽象不应该依赖于具体实现细节,具体实现细节应该依赖于抽象。
通过遵循依赖倒置原则,可以降低模块间的耦合度,提高系统的灵活性和可维护性。
雷德朋体系设计原则是一组用于软件系统架构设计的基本原则,包括单一职责原则、开放封闭原则、里氏替换原则和依赖倒置原则。
遵循这些原则可以提高系统的可靠性、可维护性和可扩展性。
同时,设计人员应该根据具体的业务需求和系统特点,结合实际情况进行合理的设计和实践,以达到最佳的设计效果。
白领常说的英文单词

白领常说的英文单词共100个1. Initiative -主动性2. Productivity -生产力3. Efficiency -效率4. Collaboration -协作5. Deadline -截止日期6. Innovation -创新7. Networking -网络拓展8. Flexibility -灵活性9. Prioritize -优先考虑10. Multitasking -多任务处理11. Proactive -积极主动12. Feedback -反馈13. Strategic -战略性的14. Benchmark -基准15. Synergy -协同效应16. Stakeholder -利益相关者17. Accountability -责任心18. Resilience -韧性19. Empowerment -授权20. KPI (Key Performance Indicator) -关键绩效指标21. Core Competency -核心竞争力22. ROI (Return on Investment) -投资回报率23. Onboarding -入职培训24. Work-life Balance -工作与生活的平衡25. Mentorship -导师制度26. Cross-functional -跨职能的27. Disruption -颠覆性变革28. Paradigm Shift -范式转变29. Synergize -协同合作30. SWOT Analysis - SWOT分析(优势、劣势、机会、威胁)31. Benchmarking -基准比较32. Milestone -里程碑33. Outsource -外包34. Thought Leadership -思想领导力35. Holistic -全面的36. Paradigm -范式37. Incentivize -提供激励38. 360-degree Feedback -全方位反馈39. Tangible -有形的40. ROI (Return on Investment) -投资回报率41. Agile -敏捷的42. Leverage -利用43. Paradigm Shift -范式转变44. Brainstorm -集思广益45. Gamification -游戏化46. Inclusive -包容性的47. Disruptive Innovation -颠覆性创新48. Visionary -有远见的49. Optimize -优化50. Sustainability -可持续性51. Client-Centric -客户至上的52. Value Proposition -价值主张53. Iterative -迭代的54. Cross-platform -跨平台55. Intrapreneurship -企业内部创业56. Tangible Results -明显的成果57. Breakthrough -突破58. Scalability -可扩展性59. Streamline -精简60. Seamless -无缝的61. Best Practice -最佳实践62. Empathy -共情63. Benchmark -基准64. Paradigm Shift -范式转变65. Compliance -合规性66. Meritocracy -精英管理制度67. Customer-centric -客户中心68. Holistic Approach -全面的方法69. Optimal -最佳的70. Agile Methodology -敏捷方法论71. Best-in-class -最佳的72. ROI (Return on Investment) -投资回报率73. Key Player -关键人物74. Win-win -双赢75. On the Same Page -理念一致76. Out of the Box -创新的77. Cutting-edge -尖端的78. Go the Extra Mile -额外努力79. Seamless Integration -无缝集成80. Pivot -转变方向81. Value-added -增值的82. Core Values -核心价值观83. In the Loop -了解最新情况84. Take the Lead -领先85. Mission Critical -使命关键86. Customer Retention -客户保留87. Disruptor -颠覆者88. Break Even -收支平衡89. Paradigm Shift -范式转变90. Milestone -里程碑91. Game Plan -行动计划92. Vision Statement -愿景陈述93. ROI (Return on Investment) -投资回报率94. Big Picture -大局95. On the Horizon -在望96. Roadmap -路线图97. Blue Sky Thinking -充满创意的思考98. Key Performance Indicator (KPI) -关键绩效指标99. Customer Engagement -客户参与100. Forward-thinking -有远见的。
ZG离线TTP公平非否认协议的一种新改进

体, 增加 了协议的复杂性 。本文 提出一种新 的方案 , 在增加少
O 引言
由于电子商务的不 断推广和 应用 , 买卖 双方通 过 Itrc ne t a
为三种 :) a 逐步交换 协议 , 这种方 式不要 求 r P参 与 , 通信 r r 但 双方需具有相同的计 算能力 ; ) b 在线 , P 即 r P在整个协议 r , r r r
: A设定 的消息的对称加密密钥 ;
C: 代表用密钥 K加 密 m 以后的密文 , C= K( ; 即 e m) E 0: 收方 用 来 建 立 消息 来 源 证 据 , 中 E O C和 O 接 其 O —
Ne i r v me to G f-i e T a ra d n n—e u ito r t c l w mp o e n fZ o l TP f i n o r p d a i n p o o o n
YA NG h n y a S a .u n 一,Z HU Ja . n in mig
第 2 第 1 期 7卷 2
21 0 0年 l 2月
计 算 机 应 用 研 究
Ap l ai n Re e r h o o u e s p i t s a c fC mp tr c o
Vo 7 No 1 L2 . 2
De .2 1 c O0
Z 离 线 T P公 平 非 否 认 协 议 的 一 种 新 改 进 G T
完成交易 , 非否认协议变得越来 越重要 , 不可否认 服务的 目的
协同设计过程中互操作性的研究

第37卷 第2期2003年2月 西 安 交 通 大 学 学 报JOURNAL OF XI′AN J IAO TON G UN IV ERSIT YVol.37 №2Feb.2003协同设计过程中互操作性的研究田 锋,李人厚,顾新华,秦 明(西安交通大学电子与信息工程学院,710049,西安)摘要:针对多代理系统中知识的使用,特别是知识的互操作以及知识管理等问题,并结合工作流、人工智能和XML技术,提出一种解决协同设计过程中的互操作的方法和分布式知识的逻辑管理.其中利用扩展置标语言(XML)表达本体来解决协作知识集成和分布式知识互操作;用工作流技术描述协作过程来解决协作过程互操作;最终提供了基于XML的各协同工作过程的互操作原语,并用一个原型系统进行验证.该方法使协同工作能够在因特网环境下得到最大的效能.关键词:计算机支持下的协作设计;互操作性;协作设计过程;扩展置标语言本体中图分类号:TP274 文献标识码:A 文章编号:0253ν987X(2003)02ν0179ν05R esearch on Interoperability in Cooperative Design ProcessesTian Feng,L i Renhou,Gu Xinhua,Qin Ming(School of Electronics and Information Engineering,Xi′an Jiaotong University,Xi′an710049,China)Abstract:Aiming at problems in multi2agent systems,such as knowledge use,especially the knowledge interoperability or knowledge management etc.,a method using techniques of workflow,artificial intelligence and XML to solve the interoperability of processes of collaborative design and the logical management of distributed knowledge are proposed.The ontology is represented by XML to solve the integration of collaborative knowledge and interoperability of distributed knowledge,and the collaborative process based on work2 flow technology.The method is verified by a prototype system and shows the maximum efficiency of collaborative works under Inter2 net.K eyw ords:CS CD;interoperability;collaborative design processes;XML ontology 协同设计是网络环境下协同工作的具体应用.协同系统的重要挑战之一是协作过程的互操作.由于存在着协作过程动态特性、协作人员的动态特性、协作设计业务流程的动态特性以及软件的动态特性等问题,使得协同设计系统对互操作性的要求更为突出.特别是在业务流程存在多学科的交叉协作时,如何综合分析不同的业务流程,并把它们集成到统一的协作过程中就将成为当前协同系统互操作性的重要内容.国内外的许多学者对互操作问题都进行了研究,并提出了各自的解决方案.例如,马先林等人认为KQML语言是解决计算机支持下的协同工作(CSCW)系统互操作性的一个重要解决方案[1];陈涵生分析并解释了信息系统的互操作,讲述了当时的研究现状[2];苏森等人采用CORBA技术建立了互操作中间件(OSEwan),从技术角度解决分布式处理问题[3];李强、吴泉源等人利用代理(Agent)的语言解决互操作性,以KQML为基础定义了ACOL 语言来解决特定领域的问题[4];丁俊华、董桓等人综述软件互操作的研究和进展,列举了基于接口标准化的互操作方法、基于接口桥接的互操作方法、面向Internet的方法(基于Agent、基于Java)以及面向应用框架的方法[5],等等.在当前的协作系统中对知识管理的要求也日益增加.不同的业务需要对相关领域知识进行管理.特别是在多业务环境下的协同工作中,设计单位使用各自专业领域的知识和管理方法,即使是同一专业也会因为不同的领域分支所处理的具体问题不同,导致所使用和管理的知识不同,这就要求从系统工程的角度对整个协作设计使用知识进行管理,而人工智能所提出的本体(Ontology)的概念正好符合了这种需求.在Internet环境下,多Agent技术是解决协同设计系统不同标准、不同结果输出、不同业务流程等收稿日期:2002ν05ν20. 作者简介:田 锋(1972~),男,博士生;李人厚(联系人),男,教授,博士生导师. 基金项目:国家自然科学基金资助项目(69773004);教育部“教育振兴行动计划”资助项目.问题的重要技术之一,而建立统一的协作过程互操作接口标准化语言是解决上述问题的一种主要手段.我们提议:将协同系统中业务流程之间的互操作接口用一种符合Internet标准的、满足业务知识需求的语言XML来描述,引入Ontology概念进行协同系统中知识逻辑管理.1 协同设计管理系统协同设计管理系统实际上是一种CSCW技术,是结合具体业务活动的网络化设计管理系统.按照工作流的观点,它可以分为以下几个阶段.(1)协同设计过程建模阶段.它实际是对协作的流程进行定义,系统设计过程会因为不同的业务领域而不同.因此,在协同过程建模中,必须对所面向的业务过程进行标定,进而定义互操作过程的对象,为协同设计过程执行期间的互操作打下基础.(2)协同设计执行阶段.它按照建模定义的过程,执行并完成协同设计活动实例.它的互操作性体现在各个流程之间的接口、对服务的请求调用等需求上.这些也是协同设计管理的一个重要内容.(3)协作结果的管理阶段.它实际上是系统对协作结果的归档整理以备后用的后期处理.这一阶段越来越受到重视,因为知识的再挖掘、重用等均是从对协作过程、结果的学习和再利用得来的.互操作过程是协作的体现,所以它被存储和处理,然后作为系统学习的依据,为更好的协作提供指导.2 基于Ontology的知识库的集成管理2.1 集成管理需求分析当前一个大的协同设计项目涉及到很多种知识,这些知识的资源要么组织逻辑紧密,要么组织逻辑松散,如果要很好地利用它们,则需对系统中各种知识进行集成管理.如果为每一种业务领域建立各自的知识库,这会导致知识库的种类繁多、各自为政,同时知识库也得不到很好的利用;这些知识库也可能是异构的,致使知识的利用变得很复杂.如果建立集中式的知识库,很容易造成知识库臃肿,一旦被访问人数超过限制,查询效率就会降低,甚至系统出现崩溃.这样,分布式知识库就成为可行的方案之一,但是它的维护比较复杂,根据已往的经验,只要建立统一的标准化互操作语言,这种知识库还是能够得到很好的维护的.由于知识库的元信息异质性,所以利用元信息建立知识的逻辑管理会引起管理复杂和繁重.Ontology具有描述物质存在性的特点,利用它对立统一的特性及其关系逻辑,在业务知识和知识元信息之间建立桥梁关系,可为应用提供主动服务、知识管理及互操作.2.2 知识集成管理策略根据以上分析,我们将系统中的知识资源进行了集成,对协同设计中所面向的业务领域以及相关的资源进行知识信息集成,并建立以下逻辑.(1)保证系统中应用知识逻辑的一致性.这是一个概念模型,主要是保证现实中具体业务领域的知识和元信息的正确使用.(2)知识资源的管理.需要对协作设计中的知识资源进行管理,包括对协作结果、协作规则知识的管理.(3)保证系统中Ontology本身逻辑的一致性.使用Ontology的系统,需要对自身的逻辑层次进行维护,这样才能正确调用相关的知识逻辑和业务知识.依据以上3种维护逻辑对知识层次、知识结构等知识逻辑进行表述,将使Agent系统的互操作一致性得以实现.2.3 分布式知识管理互操作模块根据分布式知识的特性建立了一个分布式知识管理互操作模块,该模块由互操作系统进行维护和执行,其结构如图1所示.其中,Ontology到知识的映射完成了分布式知识库的定义、位置连接和解释,这些知识库包括资源知识库、成员个性化知识库、业务知识库和协作过程管理知识库,它们都是分布式存储的.Ontology逻辑完成了分布式知识库中的,以Ontology为主分类的知识库结构层次、元信息以及相关逻辑的定义,它主要是结合基于XML互操作原语中的Ontology,使操作原语能够针对目标知图1 基于Ontology的知识逻辑081西 安 交 通 大 学 学 报 第37卷 识库实现正确的操作.Ontology解释器利用Ontolo2 gy到知识的映射和Ontology逻辑模块,实现互操作原语对知识的使用和管理(检索、定义、建模、维护等操作).3 基于XML语言的互操作接口语义化互操作语言首推Agent互操作语言(KQML),但它存有缺陷[4].当前Internet下协同设计的互操作还对知识管理提出了要求,包括知识表示、知识挖掘、知识获取和知识提炼等.Agent通信语言(例如KQML)只能表示语义、知识信息及操作,不能共享知识管理.只有充分共享知识及其管理,系统才能获得更大的知识利用率和协作效率.基于Ontology的知识逻辑管理思路,我们建立了一套基于XML的互操作原语,定义如下.定义1 结合工作流互操作接口定义[6]和KQML 的结构,定义一个基于XML的互操作原语,按照XML的D TD文件格式,一个消息的原语结构为〈!EL EM EN T COOPProcessMessage(COOPMessageHeader, COOPMessageBody)〉〈!EL EM EN T COOPMessageHeader(Message Type,Sender,Reply2to, Reply2with,Receiver,Language, Ontology,Business,TaskStyle)〉其中:消息类型(Message Type)分为请求(request)和回应(response)两种.Ontology决定使用哪个知识库,它由分布式知识库管理模块的Ontology解释器来处理.消息体(COOPMessageBody)的定义分为以下几个部分.定义2 消息体消息类型(COOPMessage Type)按照类型可分为知识管理(查询、修改、添加和删除)、业务操作两种,其原语结构为〈!EN TIT Y%KnowledgeMng(Query| Modify|Add|Delete)〉〈!EN TIT Y%BusinessOpereation(CreateProcessInstance|G etC oop InstanceData| ChangeCoop InstanceState| Coop InstanceState)〉〈!EN TIT Y%COOPMessage Type (KnowledgeMng|BusinessOperation)〉定义3 过程上下文数据和结果数据主要是为了传送上述操作的具体数据,其原语结构为〈!EL EM EN T content AN Y〉〈!EL EM EN T data AN Y〉其中:content和data的数据类型表示可以是结构化的,也可以是单个元素,但一般是结构化的.定义4 协作设计过程状态主要描述建模、准备、运行、结束、终止、挂起、继续、异常终止、异常放弃和异常完成,其原语结构为〈!EL EM EN T COOPStatus〉〈!A TL IST COOPStatus(modeling|prepare|running|completed|terminated|suspend|resume|exception|abortcomplete|terminatedcomplete)〉定义5 错误处理是对协同设计过程中出现操作异常进行处理的描述,包括异常Ontology、异常隶属业务、异常隶属类型ID、异常子码和异常描述,其原语结构为〈!EL EM EN T Exception(Ontology,business, ExceptionID,SubExceptionCode)〉4 具体实例依据协同设计的特性建立了协作过程建模工具,该工具可以利用图形化、可视化的工具将协同设计过程定义转换为基于XML语言的过程定义,其设计界面如图2所示.图2 协作过程建模工具图形界面该工具依据Ontology对业务知识进行分类并定义其关联,按照Ontology的层次化模型将虚拟设计中的活动分为元操作类型和高级操作类型(见图2中左面图库),用户可以利用这些操作实现快速协作设计过程建模.该建模工具还结合工作流技术完成了协同设计过程建模所需的各种功能,例如汇合181 第2期 田 锋,等:协同设计过程中互操作性的研究节点、分支节点等高级过程建模所应具备的特性.该界面中的实例是一个网上虚拟机械产品(螺纹套件)设计过程的定义.在协作设计中,用建立的多Agent分布式平台来进行基于XML的互操作消息传送.该平台能够完成同步消息和异步消息(包括电子邮件)的传送.在协同设计系统中向协作管理消息服务器发送消息,下面给出了一个发起螺纹机械部件组装的虚拟设计活动的具体操作语句.〈?xml version=”110”encoding=”gb2312”standalone=”no”?〉〈!DOCT YPE COOPProcessMessaage SYSTEM”ftp://COOPMessage.dtd”!〉〈COOPProcessMessage〉〈COOPProcessMessageHeader〉〈Message Type〉Request〈/Message Type〉〈Sender〉TianFeng〈/Sender〉〈Reply2to〉NULL〈/Reply2to〉〈Reply2with〉NULL〈/Reply2with〉〈Receiver〉Facilitator〈/Receiver〉〈Language〉COOPMANA GE〈/Language〉〈Ontology〉COOPOntology〈/Ontology〉〈Business〉Mechanic〈/Business〉〈TaskStyle〉AccesssoryDesign〈/TaskStyple〉〈/COOPProcessMessageHeader〉〈COOPProcessMessageBody〉〈COOPMessage Type〉 BusinessOperation.CreateCoop Instanc eData〈/COOPMessage Type〉〈COOPStatus〉prepare〈/COOPStatus〉〈content〉〈TaskName ID=”4”〉ThreadAccessoryAssembling1〈/TaskName〉〈MeetingName〉ThreadAccessoryAssembling1〈/MeetingName〉〈COOPTOOL〉Solidworks2000〈/COOP2 TOOL〉〈Date〉2002.4.12〈/Date〉〈/content〉〈data〉 〈Input〉 〈Participate〉 〈member〉田锋〈/member〉 〈Organizational2Role〉组长 〈/Organizational2Role〉 〈Professional2Role〉Designer 〈/Professional2Role〉 〈/Participate〉 … 〈Participate〉 〈member〉顾新华〈/member〉 〈Organizational2Role〉成员 〈/Organizational2Role〉 〈Professional2Role〉Designer 〈/Professional2Role〉〈/Participate〉 〈File〉 〈FileStyle〉prt〈FileStyle〉 〈FileName〉bolt1.prt〈FileName〉 〈Location〉ftp://202.117.14.69 〈/Location〉 〈/File〉 〈File〉 〈FileStyle〉prt〈/FileStyle〉 〈FileName〉nut2.prt〈/FileName〉 〈Location〉ftp://202.117.14.69 〈/Location〉 〈/File〉 〈File〉 〈FileStyle〉prt〈/FileStyle〉 〈FileName〉gasket3.prt〈/FileName〉 〈Location〉ftp://202.117.14.69 〈/Location〉 〈/File〉 〈/Input〉 〈Output〉 〈File〉 〈FileStyle〉asm〈/FileStyle〉 〈FileName〉ThreadAccessoryl.asm 〈/FileName〉 〈Location〉ftp://202.117.14.69 〈/Location〉 〈/File〉 〈/Output〉〈/data〉〈/COOPProcessMessageBody〉协作过程的实例以及协作任务过程中的异步消281西 安 交 通 大 学 学 报 第37卷 息可以进行Internet 上的发送、访问和查询浏览.针对一个具体实例(螺纹协作设计)的内容查询结果界面见图3.该工具主要为协作成员或者客户提供异步协作消息的查询功能.图3 一个协作信息查询界面5 结 论本文提出了一种基于XML 和Ontology 的互操作性接口语言,该语言解决了Internet 环境下协同设计过程中的互操作性问题,同时实现了对协同设计知识库逻辑进行管理.强调了业务知识的融合能力和描述能力等,以便系统能够真正达到服务共享和互操作.参考文献:[1] 马先林,林宗楷,郭玉钗.CSCW 中的通讯语言[J ].计算机工程与应用,1996(6):28~30.[2] 陈涵生.信息系统互操作[J ].计算机工程,1998,24(10):2~4.[3] 苏 森,唐雪飞.开放系统的互操作性[J ].计算机应用,1997,17(6):4~8.[4] 李 强,吴泉源,王怀民.一种Agent 互操作语言的设计[J ].计算机学报,1998,21(增刊):213~217.[5] 丁俊华,董 桓,吴定豪,等.软件互操作研究与进展[J ].计算机研究与发展,1998,35(7):577~583.[6] TC002100321995,Workflowmanagementcoalitionworkflow reference model [S].(编辑 苗 凌)(上接第162页)参考文献:[1] Shigeta T ,Saegusa N ,Honda H ,et al.Im provement ofmoving 2video image quality on PDPs by reducing the dy 2namic false contour [A ].SID ′98International Sympo 2sium[C].Anaheim ,California ,USA :S ociety for Informa 2tion Display ,1998.287~290.[2] K anazawa Y ,Ueda T ,Kuroki S ,et al.High 2resolution in 2terlaced addressing for plasma displays [A ],SID ′99In 2ternational Symposium [C ].San Jose ,California ,USA :S ociety for Information Dis play ,1999.154~157.[3] Tekalp A M.Digital video processing[M ].北京:清华大学出版社,1998.312.[4] Park S H ,Choi Y S ,K im C W.Optimum selection of sub 2field patterns for plasma displays based on genetic algo 2rithm [A ].International Dis play Workshops IDW ′99[C ].Sendai ,Japan :S ociety for Information Dis play ,1999.715~718.[5] Shinoda T ,Wakitani M ,Nanto T ,et al.Develo pment ofpanel structure for a high 2resolution 212in 2diagonal full 2color surface 2discharge plasma display panel [J ].IEEE Transactions on Electron Devices ,2000,47(1):77~81.(编辑 刘 杨)381 第2期 田 锋,等:协同设计过程中互操作性的研究。
网络英语 带音标

网络英语Alphamosic Graphics['ɡræfiks]字母镶嵌图形Anonymous [ə'nɔniməs] FTP 匿名文件传输Access Control 访问控制Average seek time 平均寻道时间Aliasing ['eiliəsiŋ]混淆Aactive matrix ['meitriks]动态矩阵Active Network 动态网络Authentication [ɔ:,θenti'keiʃən] and Authorization [,ɔ:θərai'zeiʃən]鉴别与授权Auditing ['ɔ:ditiŋ]审计,计审BIS商务信息系统Bundled ['bʌndl] Software捆绑软件Bookmark ['bukmɑ:k]书签BASIC 编程语言B2B 商务对商务BBS 电子布告栏系统Beta 测试第二版Bug 程序缺陷、臭虫Byte-Oriented ['ɔ:rientid] Protocol 面向字节规程Bus Topology [təu'pɔlədʒi]总线拓扑Bursts [bə:st] 突发传送Burst Mode NetWare NetWare的突发方式Bulletin ['bulitin] Board System 公告牌系统Broadcast Storm 广播风暴Broadcast 广播Broadband Services 宽带(通信)服务Broadband ISDN 宽带综合业务数字网Breakout ['breikaut] BoX 中断盒BNC Connector [kə'nektə] BNC连接器Block Suballocation [sʌb,ælə'keiʃən] 磁盘块再分配Bit-Oriented ['ɔ:rientid]Protocol 面向位协议Bindery ['baindəri]装订Binary Synchronous ['siŋkrənəs] Communications 二进制同步通信(规程)Distance-Vector['vektə] Routing Algorithm['siŋkrənəs]距离向量Cable 电缆Cable Modem 电缆调制解调器Cache 高速缓冲存储器Cookie ['kuki]网络小甜饼Cryptography [krip'tɔɡrəfi]密码术;密码学Corporation [,kɔ:pə'reiʃən] for Open Systems 开放系统公司Copper ['kɔpə] Distributed [di'stribjutid] Data Interface 铜质分布式数据接口Cooperative [kəu'ɔpərətiv] Accessing 协同处理Controlled Access Unit 受控访问单元Contention [kən'tenʃən]争用Container [kən'teinə] Objects 所有者对象Connection-Oriented ['ɔ:rientid] and Connectionless Protocols 面向连接和无连接协议Connectionless and Connection-Oriented Transactions 无连接和面向连接事务Configuration Management 配置管理Conditioning [kən'diʃəniŋ]调节Concentrator ['kɔnsəntreitə] Devices 集中器设备Compression Techniques 压缩技术Compound ['kɔmpaund] Documents 复合文档Complex ['kɔmpleks] Instruction [in'strʌkʃən] Set Computer 复杂指令系统计算机Common ['kɔmən] Programming Interface for Communication IBM IBM的通信公用编程接口Common Open Software Environment 公用开放软件环境Common Object Request Broker Architecture ['ɑ:kitektʃə]公用对象请求代管者体系结构Common Object Model 公用对象模型Digital camera 数码相机Dynamic [dai'næmik] Routing 动态路由选择Dynamic Data Exchange 动态数据交换Duplex ['dju:pleks] Transmission [trænz'miʃən]双工传输Duplexed Systems 双工系统Downsizing 向下规模化,下移Document Management 文档管理Document Interchange Standard ['stændəd]文档交换标准Distributed [di'stribjutid] System Object Model 分布式系统对象模型Distributed Relational Database Architecture 分布式关系数据库体系结构Distributed Queue [kju:] Dual ['dju:əl]Bus 分布式队列双总线Distributed Processing 分布式处理Distributed Objects EveryWhere(DOE),SunSoft SunSoft的全分布式对象Distributed Object Management Systems 分布式对象管理系统Distributed Object Management Facility(DOMF),Hewlett-Packard HP的分布式对象管理设施Distributed Name Service,DEC DEC的分布式命名服务Distributed Management Environment 分布式管理环境Distributed Management 分布式管理Distributed File Systems 分布式文件系统Distributed File System,OSF DCE OSF DCE的分布式文件系统Distributed Database 分布式数据库Distributed Computing Environment(DCE),OSF 开放软件基金会(OSF)的分布式计算环境Edge Device 边界设备Email Filter [filtə]电子邮件过滤器EPP 增强型并行端口Extended [ik'stendid] Industry ['indəstri] Standard Architecture Bus 扩展工业标准体系结构(EISA)总线Ethernet100VG-AnyLAN(V oice Grade)100VG-AnyLAN(语音级)以太网Ethernet 100Base-X 100Base-X以太网Ethernet 10BaSe-T(Twisted-pair)10Base-T(双绞线)以太网Ethernet 10Base-5(Thicknet)10Base-5(粗电缆)以太网Ethernet 10Base-2(Thinnet)10Base-2(细电缆)以太网Error Detection [di'tekʃən]and Correction [kə'rekʃən] 检错和纠错Elevator ['eliveitə]Seeking 电梯式查找[寻道]算法Electronic [,ilek'trɔnik]Software Distribution(ESD)and Licensing 电子软件分发(ESD)和特许(ESL)Electronic Mail Broadcasts to a Roaming Computer 对漫游计算机的电子函件广播Electronic Mail 电子函件Electronic Industries Association 电子工业协会Electronic Data Interchange 电子数据交换Electromagnetic [i,lektrəumæɡ'netik] Interference [,intə'fiərəns] 电磁干扰FCC & BCC转发与密送Failback 自动恢复Full-Duplex Transmissions 全双工传输Front-End System 前端(台)系统Front-End Processor ['prəusesə]前端(台)处理机Frequency ['frikwənsi]Division [di'viʒən]Multiplexing 频分多路复用Frames in Communication 通信帧Frame Relay 帧中继Forwarding['fɔ:wədiŋ] 转发Flow Control Methods 流控方法File Transfer Access and Management 文件传输访问和管理File Systems in the Network Environment [in'vaiərənmənt]网络环境中的文件系统File Systems Distributed 分布式文件系统Fiber Channel 光纤通道Fiber-Optic Cable 光缆Fiber Distributed Data Interface 光纤分布式数据接口Federated ['fedəreitid] Database 联合数据库Federal ['fedərəl]Information Processing Standards 联邦信息处理标准GPRS通用分组无线业务Grounding ['ɡraundiŋ] Problem s 接地问题Government OSI Profile ['prəufail]政府OSI框架文件Glue [ɡlu:]Oracle Oracle的Glue解决方法Global ['ɡləubəl] Naming Services 全局命名服务Gateway-to-Gateway Protocol 网关对网关协议HDF 层次型数据格式Horizontal ['hɔri'zɔntəl] Wiring ['waiəriŋ] System 水平布线系统Homogeneous [,hɔmə'dʒi:niəs] Network Environments 同构网络环境Home Directory 私人目录High-Speed Serial ['siəriəl]Interface 高速串行接口High-Speed Networking 高速联网高速网包括传输速度高于在1990年前占主导地位的传统传输速度的LAN 和W ANHigh Performance [pə'fɔ:məns] Routing(HPR),IBM IBM 的高性能路由选择High Performance Parallel ['pærəlel] Interface 高性能并行接口High Performance File System 高性能文件系统High-Level Data Link Control 高级数据链路控制(规程)High Capacity [kə'pæsəti] Storage['stɔridʒ] System(HCSS),Novell NetWare Novell NetWare的大容量存储系统High-bit-rate Digital Subscriber [səb'skraibə] Line 高位速率数字用户专用线Heterogeneous [,hetərəu'dʒi:njəs] Network Environments 异构网络环境Hermes ['hə:mi:z],Microsoft Microsoft的企业网管理系统Handshaking 握手,联络,信号交换Half-Duplex Transmission 半双工传输Insert Mode插入模式iPAQ Pocket ['pɔkit] PC 智能手机的一种IrDA 红外线传输装置Instructions Cache 指令缓存Internet backbone Internet骨干网Internal [in'tə:nəl]Bus 内部总线IDE 集成驱动电子设备IS-IS Interdomain Routing Protocol IS-IS域间路由选择协议Interoperability ['intər,ɔpərə'biləti]互操作性,互用性Internetwork Routing 网间路由选择Internetwork Packet Exchange 网间分组交换Internetworking 网络互联Internet Engineering Task [tɑ:sk]Force 互联网工程任务组JPEG 联合图像专家组规范Jukebox ['dʒu:kbɔks] Optical Storage Device 自动换盘光盘存储设备Jabber ['dʒæbə] 超时传输Key recovry 密钥恢复Knowbots ['nəubɔt]智能程序Key Encryption [in'kripʃən] Technology 密钥加密技术Kerberos Authentication Kerberos鉴别Light Cabel 光缆Leased [li:st] line 专线LPT 打印终端接口、打印终端Login Scripts 登录原语Logical ['lɔdʒikəl] Units 逻辑单元Logical Links 逻辑链路Local Procedure [prə'si:dʒə] Calls 本地过程调用Local Loops 局部环路Local Exchange Carrier ['kæriə]本地交换电信局Local Area Transport 局域传输协议Local Area NetWorks 局域网Local Access and Transport Area 本地访问和传输区域Load-Balancing['bælənsiŋ] Bridges 负载平衡桥接器,负载平衡网桥Link State Routing 链路状态路由选择Link Services Protocol,NetWare NetWare的链路服务协议Link Access Procedure 链路访问规程Line Conditioning [kən'diʃəniŋ]线路调节Legacy ['leɡəsi] Systems 保留系统Leased [li:st]Line 租用线路Learning Bridges 自学习桥接器Leaf Objects 叶对象Layered Architecture 分层体系结构Large Internetwork Packet Exchange 大型网间分组交换LAN Troubleshooting 局域网故障诊断LAN Requester 局域网请求解释器MO 磁性光盘MAN 城域网Memory Stick 存储棒Multistation Access Unit 多站访问部件Multipurpose [,mʌlti'pə:pəs] Internet Mail Extension Internet多功能邮件传递扩展标准Multiprotocol Transport Network(MPTN),IBM IBM的多协议传输网络Multiprotocol Router 多协议路由器Multiprotocol Networks 多协议网络Multiprocessor Systems 多处理器系统Multiprocessing 多处理器处理Multiplexing 多路复用技术Multimedia 多媒体Multidrop(Multipoint)Connection 多点连接MOTIS(Message Oriented Text Interchange System)MOTIS(面向消息的文本交换系统)Motif Motif 工具Mobile Computing 移动计算Middleware 中间件Microwave Communication 微波通信Micro-to-Mainframe Connectivity 微型计算机到大型计算机的互联性Microsoft At Work Architecture Microsoft At Work体系结构Microsegmentation 微分段Microkernel 微内核Microcom Networking Protocol(MNP)Microcom的联网协议MicroChannel Architecture(MCA)Bus 微通道体系结构(MCA)总线Metropolitan Area Networks 城域网Messaging Application Programming Interface 消息应用程序编程接口Messaging API,Inter-Application 应用程序间的消息传递API Messaging API,E-mail E-mail的消息传递APIMessage Transfer Agent 消息传送代理Message Queuing Interface(MAI),IBM IBM的消息排队接口NOC网络操作中心Network Architecture 网络体系结构NSR 渲染引擎NFS 网络文件系统NWLink IPX/SPX协议微软执行部分NetBIOS 网络基本输入/输出系统NTFS(New Technology File System)NTFS(新技术文件系统)Novell Novell公司Node 节点,结点,网点Network Troubleshooting 网络故障诊断与维修NetWork Management 网络管理Network Layer,OSI Model OSI模型的网络层Networking Blueprint 联网方案Network File System 网络文件系统Network Dynamic Data Exchange 网络动态数据交换Network Driver Standards 网络驱动程序标准Network Driver Interface Specification [,spesifi'keiʃən]网络驱动程序接口规范NetWork Control Program 网络控制程序Network Architecture 网络体系结构NetWare V olumes NetWare的(文件)卷宗NetWare Shell NetWare工作站外壳程序NetWare SFT Level ⅢNetWare的三级系统容错NetWare Products NetWare软件产品NetWare Loadable Module NetWare的可装入模块NetWare Link Service Protocol NetWare的链路服务协议NetWare Electronic Software Distribution NetWare的电子软件分发NetWare Disks,Partitions,and V olumes NetWare的磁盘、分区和卷宗NetWare Core Protocol NetWare的核心协议NetView,IBM IBM的NetView网络管理系统NetLS(Network License Server)NetLS(网络许可权服务器)OEM原装备生产厂商OSD 屏幕视控系统OAW 光学辅助温式技术Open Source [sɔ:s]开放源代码Organization Containers 机构包容器对象Optical Libraries 光盘库,光盘存储库Optical Fiber 光纤Open View Management System,Hewlett-Packard HP的Open VieW管理系统Open Systems Interconnection(OSI)Model 开放式系统互联(OSI)模型Open Systems 开放式系统Open Software Foundation(OSF)开放软件基金会(OSF)Open Network Computing [kəm'pju:tiŋ](ONC),SunSoft SunSoft的开放式网络计算环境Open Messaging Interface(OMI)开放消息传递接口Open Document Architecture ['ɑ:kitektʃə]开放文档体系结构OpenDoc Alliance,Apple Apple的OpenDoc联盟OpenData-link Interface 开放数据链路接口Open Database Connectivity(ODBC),Microsoft Microsoft的开放式数据库互联性Open Collaborative Environment(OCE),Apple Apple的开放协作环境On-line Transaction Processing 联机(在线)事务处理Objects,NetWare Directory Services NetWare目录服务中的对象Objects 对象,目标,实体Object Request Broker 对象请求代管者Object-Oriented ['ɔ:rientid]technology[tek'nɔlədʒi] 面向对象技术Object-Oriented Interfaces and Operating Systems 面向对象接口和操作系统Object-Oriented Database 面向对象数据库Object Management Group 对象管理组织Object Management Architecture 对象管理体系结构Object Linkingand Embedding [im'bediŋ]对象链接与嵌入Packetsniffer包嗅探器Push Technology[tek'nɔlədʒi]推技术PVM并行虚拟机Path 路径、通路PKI 公开密钥基础设施PAP 密码验证协议PDS 个人数字系统Plasma ['plæzmə] Display 等离子显示器Punchdown [pʌntʃ] Block 穿孔板,分线盒Pulse [pʌls]-Code Modulation [,mɔdju'leiʃən]脉码调制,脉冲代码调制Public Switched Data NetWork 公共交换数据网Public Key Cryptographic [,kriptə'ɡræfik] Systems 公开密钥加密系统Public Data NetWorks(PDNs)公用数据网(PDN)Protocol Stack 协议栈Protocol Data Unit 协议数据单元Protocol Converters 协议转换器Protocol Analyzers ['ænə,laizə] 协议分析器(程序)Protected of Data 数据的保护Protected Mode (受)保护模式Properties of Objects 对象的性质,对象的特性Propagation [,prɔpə'ɡeiʃən] Delay 传播延迟Project DOE(Distributed Objects Everywhere)企业(工程)DOE(全分布式对象)Private ['praivit] Network 私用网,专用网Privacy['praivəsi]Enhanced[in'hɑ:nst] Mail 增强安全的私人函件Print Server 打印服务器Premises ['premisiz] Distribution System 规整化布线系统Preemptive [pri'emptiv]Multitasking 抢先多任务处理Quadrature ['kwɔdrətʃə] Amplitude ['æmplitju:d] Modulation [,mɔdju'leiʃən]正交振幅调制,正交调幅RAID 冗余独立磁盘阵列RSA Data Security RSA数据安全性RSA数据安全性Routing Protocols 路由选择协议Routing Information Protocol 路由选择信息协议Ring Network Topology [təu'pɔlədʒi]环网拓扑结构环网拓扑结构Rights(Permissions)in Windows NT Windows NT权限(准许权限)Rights in Windows for Workgroups Windows for Workgroups中的权限Rights in Novell NetWare Novell NetWare中的权限RG-62 Coaxial ['kəu'æksəl] Cable RG-62同轴电缆Remote [ri'məut] Procedure [prə'si:dʒə] Call 远程过程调用Remote Access Software 远程访问软件Regional Bell Operating Companies(RBOC)地方贝尔运营公司Redundant [ri'dʌndənt] Arrays [ə'rei] of Inexpensive Disks(RAID)廉价磁盘冗余阵列Reduced Instruction [in'strʌkʃən] Set Computer 精简指令系统(集)计算机Redirector 重定向器(程序)RAM Mobile Data RAM 移动数据公司Radio Networks 无线电网络SAA系统应用架构SMP 对称多处理结构SET 安全电子商务协议SCSI 小型计算机系统接口SystemView,IBM IBM的SystemView网络管理系统Systems Network Architecture(SNA),IBM IBM 系统网络体系结构Systems Application Architecture 系统应用体系结构System Object Model(SOM),IBM IBM的系统对象模型(SOM)System Fault Tolerance ['tɔlərəns]系统容错Synchronous ['siŋkrənəs] Optical Network 同步光纤网Synchronous Data Link Control 同步数据链路控制(规程)Synchronous Communication 同步通信Symmetrical [si'metrikəl] Multiprocessing 对称多处理Switching Hubs 交换式集线器Switched Virtual ['və:tʃuəl] Circuit ['sə:kit]交换式虚电路Switched Services 交换式服务Switched Multimegabit Data Service 交换式多兆位数据服务Switched-56 Services Switched-56服务,交换式56服务Surge [sə:dʒ] Suppressors [sə'presə]浪涌电压抑制器,电涌抑制器Supervisor 超级用户,监管员SunOS,SunSoft SunSoft的SunOS操作系统SunNet Manager,Sun Microsystems,Inc.Sun公司的SunNet ManagerSun Microsystems,Inc.Sun 微系统公司TFT 有源矩阵彩色显示器Twisted-Pair ['twistid]Cable 双绞线,双绞线电缆Tunneling ['tʌnəliŋ]管道传送,隧道,管道传输Trustees [,trʌs'ti:s] 受托者Troubleshooting 故障诊断与维修,排错Transmission [trænz'miʃən]Media,Methods,and Equipment 传输介质、方法和设备Transmission Control Protocol/Internet Protocol 传输控制协议/Internet协议Transfer Rates 传输率Transceiver[træns'si:və]Ethernet 以太网收发器,以太网的接收发送器Transaction [træn'zækʃən]Processing 事务处理Topology [təu'pɔlədʒi拓扑结构Token ['təukən] Ring NetWork 令牌环网Token Bus NetWork 令牌总线网Token and Token Passing Access Methods 令牌和令牌传递访问方式Time Synchronization[,siŋkrənai'zeiʃən] Services 时间同步服务Time Domain Reflectometer [,ri:flek'tɔmitə]时域反射计(仪,器)Throughput ['θru:put]吞吐率,处理能力Threads[θred] 线程Testing Equipment and Techniques[tek'ni:k] 测试设备和技术Technical ['teknikəl]Office Protocol 技术办公系统协议UDA统一数据读取UML 统一建模语言Ultra ['ʌltrə]DMA 33 同步DMA协定User Datagram Protocol 用户数据报协议Unshielded[,un'ʃi:ldid] Twisted ['twistid] Pair 非屏蔽双绞线Video Compression [kəm'preʃən]视频压缩Virtual['və:tʃuəl] reality[ri'æləti 虚拟现实VOD 视频传播系统VESA 视频电子标准协会VRML 虚拟现实建模语言VESA 视频电子标准Virtual Telecommunication Access Method 虚拟远程通信访问方法Virtually Integrated['intiɡreitid] Technical Architecture Lifecycle 虚拟集成技术体系结构生命周期Virtual ['və:tʃuəl] Circuit 虚电路Video conferencing ['kɔnfərənsiŋ] and Desktop Video 电视会议和台式(桌面)视频系统Very Small Aperture ['æpə,tjuə] Terminals(VSATs)卫星小站电路设备Vertical ['və:tikəl]Wiring ['waiəriŋ]垂直布线系统Value-Added['vælju:] Carrier ['kæriə]增值网WINS IP解析WEB VOD WEB视频点播Wavetable 波表合成Workplace OS Workplace操作系统Workflow Software 工作流软件Wireless ['waiəlis] Mobile Communication 无线移动通信Wireless LAN Communication 无线局域网通信Windows Telephony Application Interface Windows 电话应用程序接口Windows Sockets API Windows套节字(嵌套字)APIWindows Open System Architecture(WOSA)Windows开放式系统体系结构(WOSA)Wide Area Networks 广域网XUL扩展用户接口语言XON/XOFF异步通信协议X2/DSL调制解调器XML 扩展标签语言X.500 Directory Services X.500目录服务X.400 Message Handling System X.400消息处理系统Zone Multicast ['mʌltikɑ:st]Address,AppleTalk AppleTalk的区广播地址Zone Information Table(ZIT),AppleTalk AppleTalk 的区信息表Zone Information Protocol(ZIP),AppleTalk AppleTalk的区信息协议Zone,AppleTalk AppleTalk 的区,AppleTalk的域ZMODEM Protocol ZMODEM 协议Distributed [di'stribjutid] file system 分布式文件系统External [ik'stə:nəl] security [si'kjuəriti]外部安全性T0,DS0 56或者64kbpsT1,DS1 24路PCM数字话,总速率为1.544MbpsT3,DS3 28个T1信道,速率为44.736Mbpsrouted daemon['di:mən]利用RIP的UNIX寻径服务impersonation [im,pə:sə'neiʃən] attack 伪装攻击directory replication [,repli'keiʃən]目录复制classless [/'klɑ:sl is/] addressing 无类地址分配GDI(graphical ['ɡræfikəl] device interface) 图形设备界面archive ['ɑ:kaiv] file attribute [ə'tribju:t]归档文件属性CPU(Center Processor['prəusesə] Unit)中央处理单元RAM(random ['rændəm] access memory)随机存储器(内存)UPS(Uninterruptable Power Supply)不间断电源BIOS(Basic-input-Output System)基本输入输出系统high jacking 劫持终端,攻击者捕获另一个用户会话的控制adaptive [ə'dæptiv] speed leveling 自适应速率等级调整java script [skript] 基于Java语言的一种脚本语言TCPDUMP 是UNIX中捕获数据包的实用工具logic bomb(逻辑炸弹)一种可导致系统加锁或者故障的程序或代码。
写一篇互信开放是团队合作的关键的英语作文

写一篇互信开放是团队合作的关键的英语作文全文共10篇示例,供读者参考篇1In order for our team to work smoothly and effectively, trust and openness are super duper important! When we trust each other, we can work together like a well-oiled machine. And when we're open with each other, we can share our ideas and solve problems together. So, trust and openness are like the secret sauce that makes our team awesome!First of all, trust is like the glue that holds our team together. When we trust each other, we can rely on our team members to do their part and do it well. We believe in each other and know that we'll always have each other's backs. Trust helps us to build strong relationships and work together towards our common goals.And then there's openness, which is like the key that unlocks our team's full potential. When we're open with each other, we can communicate freely and share our thoughts and ideas. This helps us to come up with creative solutions to problems andmake decisions together. Openness also allows us to learn from each other and grow as a team.So, in conclusion, trust and openness are super important for our team to succeed. Let's keep on trusting each other and being open with our thoughts and ideas. Together, there's nothing we can't achieve!篇2Teamwork is super important, guys! And you know what? Trust and openness are the keys to making teamwork really work! When we trust each other, we believe in our teammates and know they will do their best. And when we are open with each other, we share our ideas and thoughts freely, making the team stronger.Trust is like when you know your best friend will always have your back. You can count on them to support you when you need it most. In a team, trust means that we can rely on each other to do our parts and work together towards our goal. Without trust, it's hard to work as a team because we are always worrying if someone will let us down.Being open means being honest and sharing our thoughts and ideas. It's like when you tell your friend about a cool idea youhave for a project, and they add their own thoughts to make it even better! In a team, being open helps us come up with new and creative solutions to problems. When we all share our thoughts, we can brainstorm together and find the best way forward.So, let's remember that trust and openness are super important for teamwork. Let's trust each other to do our best and be open to sharing our ideas. When we work together with trust and openness, we can achieve great things as a team! Let's go, team!篇3Mutual trust and openness are key factors in team cooperation. If everyone in the team believes in each other and is willing to share their thoughts and ideas openly, then the team can work together more effectively.Trust is like the glue that holds a team together. When team members trust each other, they are more willing to listen to each other's opinions, rely on each other to get things done, and support each other through challenges. Without trust, there can be misunderstandings and conflicts that can hinder the team's progress.Openness is also important in team cooperation. When team members are open about their thoughts and ideas, it creates a positive and collaborative atmosphere where everyone feels comfortable expressing themselves. This leads to better communication, more creative solutions, and a stronger sense of unity within the team.In a team where there is mutual trust and openness, everyone feels valued and respected. Team members are more likely to work together towards a common goal, share responsibilities, and celebrate achievements together. This sense of unity and camaraderie is what makes team cooperation successful.So, let's remember that mutual trust and openness are the keys to effective teamwork. Let's trust each other, communicate openly, and work together towards our goals. With these values in place, we can achieve great things as a team!篇4"Trust and openness are super duper important for teamwork!" Have you ever heard that before? Well, it's true! When we work together in a team, we need to trust each otherand be open with our ideas and feelings. That way, we can do our best work and have fun too!First of all, trust is like the glue that holds a team together. We need to trust that our teammates will do their part and help us out when we need it. If we don't trust each other, the team won't work well and we'll have a hard time getting things done. Trust is built by being honest, reliable, and supportive. So let's make sure we always trust our teammates and show them that we're trustworthy too!Next, openness is all about sharing our thoughts and feelings with each other. When we're open with each other, we can come up with better ideas and solve problems together. We should never be afraid to speak up or ask for help. It's okay to make mistakes or not know everything – that's why we're a team! By being open and communicating with each other, we can learn from each other and grow together.In conclusion, trust and openness are the keys to successful teamwork. Let's make sure we always trust each other and communicate openly. That way, we can work together like a well-oiled machine and achieve awesome results. Go team!篇5Title: Trust and Openness are the Keys to TeamworkHey guys! Today I want to talk about why trust and openness are super important for teamwork. You know, when we work together as a team, it’s kind of like being on a sports team or doing a group project at school. We all have to trust each other and be open with our ideas in order to succeed.First of all, trust is a big deal in teamwork. Imagine if you didn’t trust your teammates. You might be worried that they won’t do their part or that they’ll let you down. That would make it really hard to work together! So, it’s super important to trust each other and believe that everyone is doing their best.Next, being open with each other is key. If we keep our ideas to ourselves and don’t share them with the team, we might miss out on some great solutions or ways to improve. When we’re open with our i deas, we can all work together to come up with the best plan and make things happen.When we trust each other and are open with our ideas, it makes teamwork so much better! We can communicate easily, solve problems together, and achieve our goals. So, let’s remember to trust each other, be open with our ideas, and work as a team to make amazing things happen! Go team!篇6Mutual trust and openness are the key to teamwork! When we work together as a team, it's super important to trust each other and be open with one another. Trust means believing in each other and knowing that we all have each other's backs. Openness means being honest and sharing our thoughts and feelings.When we trust each other, we can rely on our team members to do their part and help us when we need it. We can count on each other to work hard and do our best. Trust helps us feel safe and supported, which makes us more likely to take risks and try new things. When we're open with each other, we can communicate better and solve problems faster. We can share our ideas and opinions without worrying about being judged. Openness helps us understand each other and work together more effectively.When our team has mutual trust and openness, we can achieve amazing things! We can brainstorm creative solutions, collaborate on projects, and support each other through challenges. We can celebrate our successes together and learn from our mistakes. Trust and openness are like the glue thatholds our team together. They help us build strong relationships and achieve our goals.So remember, when we trust each other and are open with one another, we can accomplish anything as a team. Let's work together, communicate openly, and support each other every step of the way. Together, we can make a difference and achieve great things!篇7Hey guys! Today, I want to talk to you about something really important for teamwork – trust and openness. Trust and openness are like the secret ingredients to a successful team. Without them, things can get really messy!First of all, trust is super important in a team. If we don’t trust each other, how can we work together? Trust means that we believe in each other and know that we can rely on each other. When we trust our team members, we can communicate better, share ideas freely, and support each other when things get tough. Trust is like the glue that holds a team together.Openness is also key to teamwork. Being open means being honest, listening to others, and being willing to share ourthoughts and feelings. When we are open with each other, we can solve problems faster, avoid misunderstandings, and learn from each other’s strengths and weaknesses. Openness is like a window – it lets in fresh ideas and keeps things clear and bright.So, how can we build trust and openness in our team? Well, we can start by being honest and reliable. If we say we will do something, we should do it. We can also listen to each other and show respect for everyone’s opinions. And remember, it’s okay to make mistakes – we should learn from them and move forward together.In the end, trust and openness are the keys to a happy and successful team. So let’s work together, support each other, and always communicate openly and honestly. With trust and openness, there’s nothing we can’t achieve!That’s all for now. Thanks for listening! Let’s go and be the best team ever!篇8Title: Trust and Openness are the Keys to TeamworkHey guys, today I want to talk about teamwork. Do you know what makes a team successful? It's all about trust and openness!When we can trust each other and be open with our ideas and feelings, we can work together really well.First of all, let's talk about trust. Trust means believing in each other and knowing that we can rely on our teammates. When we trust each other, we feel safe to share our thoughts and opinions. We know that our team will support us and help us when we need it. Trust is like the glue that holds the team together.Openness is also super important in teamwork. Being open means sharing our ideas and feelings honestly. When we are open with each other, we can communicate better and understand each other's perspectives. We can work together to come up with creative solutions and make good decisions. Openness creates a positive and supportive team environment.When we have trust and openness in our team, amazing things can happen! We can achieve our goals and overcome challenges together. We can celebrate our successes and learn from our mistakes. Trust and openness are the keys to building a strong and united team.So, let's remember to trust each other and be open with our thoughts and feelings. Let's work together as a team and makegreat things happen! Trust and openness are the keys to our success. Let's be a team that shines bright together!That's all for today. Thanks for listening!篇9Title: Mutual Trust and Openness are the Keys to TeamworkHey guys! Today, I want to talk to you about something super important when it comes to working together as a team. And that is mutual trust and openness. These two things are like peanut butter and jelly, they just go together perfectly!First things first, let's talk about mutual trust. Trust is like a super glue that holds a team together. When we trust each other, we feel safe to share our ideas and thoughts. We know that our team members have our back and will support us no matter what. Trust is built over time through honesty, reliability, and consistency. So let's make sure we always keep our promises and be there for each other when we need help.Next up is openness. Being open means being able to communicate freely and honestly with your team members. It's okay to share your ideas, thoughts, and feelings. It's important to listen to others and consider different perspectives. When we areopen with each other, we can solve problems together and come up with creative solutions. So let's make sure we always keep the lines of communication open and be willing to listen to each other.In conclusion, mutual trust and openness are the keys to successful teamwork. When we trust each other and communicate openly, we can achieve great things together. So let's always remember to trust, be open, and work together as a team. Let's go out there and rock it!篇10Hi guys,Today I want to talk about why trust and openness are important for teamwork. Trust means believing in each other and knowing that we can rely on each other. Openness means being honest and sharing our thoughts and feelings with each other.When we trust and are open with each other, we can work together better as a team. We can talk about our ideas and opinions without being afraid of judgment. We can ask for help when we need it and offer help when others need it. Trust and openness help us build strong relationships with our teammates.Without trust and openness, teamwork can be hard. We might not feel comfortable sharing our ideas or working together. We might not be able to communicate well with each other. This can lead to misunderstandings and conflicts within the team.So, let's remember to trust each other and be open with our thoughts and feelings. Let's support each other and work together as a team. Trust and openness are the keys to successful teamwork.Thanks for listening! Let's continue to build trust and openness in our team!Bye-bye!。
团队配合的体现英文

团队配合的体现英文Team CooperationTeam cooperation is the collective action of a group of individuals working together to achieve a common goal. It is the process of working collaboratively with a group of people in order to achieve a goal. It involves actively listening to each other, exchanging ideas, and working together to solve problems and reach agreement.Team cooperation is essential for any organization to reach its goals. It is also necessary for a team to perform its tasks effectively, efficiently and efficiently. It involves understanding each other’s strengths and weaknesses, and working together to achieve the goals.Team cooperation is also important to build relationships, trust and respect among the team members. This can help build a strong team dynamic. The team members must learn to appreciate each other’s contributions and recognize the importance of each individual’s skills and knowledge.Team cooperation can also allow a team to learn from each other and build on one another’s strengths. Through collaboration, team members can gain new knowledge and become more productive and efficient.Finally, team cooperation can help a team to face challenges, make decisions, and to be successful. By working together, team members can come up with creative solutions to difficult problems. This can help to create a stronger team that is more unified and successful.。
协同作战材料作文

协同作战材料作文The concept of cooperative combat operations has become increasingly crucial in modern warfare. (协同作战的概念在现代战争中变得越来越重要。
) The ability for different military units and allies to work together seamlessly can greatly enhance the effectiveness of a mission and increase the likelihood of success. (不同军事单位和盟友能够无缝地协同作战,可以极大地提高任务的效果,并增加成功的可能性。
) Whether it is joint exercises, combined arms operations, or multinational efforts, the collaboration and coordination of resources and personnel play a critical role in the outcome of military operations. (无论是联合演习、复合兵种作战还是多国力量的合作,资源和人员的协同配合在军事行动的结果中起着至关重要的作用。
)From a tactical perspective, cooperative combat operations allow for a diverse array of assets to be utilized in a complementary manner. (从战术角度来看,协同作战可以使得各种不同的资产以一种互补的方式被利用。
) For example, ground forces may work in conjunction with air and naval forces to execute a multi-faceted attack, incorporating the strengths of each branch to achieve a more comprehensive and impactful result. (例如,地面部队可以与空军和海军部队协同作战,执行多方面的攻击,结合各个部队的优势,以取得更全面和更有影响力的结果。
协作机制 英语

协作机制英语In the increasingly interconnected global workplace,the importance of collaborative mechanisms cannot be overstated. These mechanisms facilitate effective communication and teamwork among individuals and organizations, regardless of their geographical, linguistic, or cultural backgrounds. English, as the lingua franca ofthe global business world, plays a pivotal role in bridging the language and cultural barriers that can hinder collaboration.Collaborative mechanisms are essential for buildingtrust and promoting a shared understanding among team members. They encourage open communication, allowing ideas and perspectives to flow freely, leading to more innovative and comprehensive solutions. In a multicultural setting, where team members may have different ways of thinking and approaching problems, collaborative mechanisms can help facilitate a more inclusive and respectful workspace.The use of English as a common language ininternational business settings is crucial for bridging the language barrier. English serves as a neutral ground wherepeople from different cultures can communicate effectively, without the need for translation or interpretation. It enables participants to convey their ideas and concerns clearly, ensuring that no one's voice is lost in translation.However, relying solely on English can sometimes be inadequate in bridging the cultural gap. Cultural differences can still affect communication style, decision-making processes, and team dynamics. It is therefore essential to complement English with cultural awareness and sensitivity. Understanding the nuances of differentcultures can help individuals and teams adapt their communication and collaboration styles to suit the specific context.To enhance collaboration in a multicultural workspace, organizations should provide training and resources that promote cultural awareness. This includes educating employees on the importance of respecting and embracing diversity, understanding different communication styles, and recognizing the value of diverse perspectives. By fostering a culture of inclusivity and respect,organizations can create a more conducive environment for collaboration and innovation.Moreover, collaborative mechanisms should be tailored to the specific needs and challenges of the team. Different projects and organizations require unique approaches to collaboration. It is crucial to identify the barriers to collaboration within the team and implement strategies that address these issues effectively. This may include the use of technology tools that facilitate remote communication, regular team-building activities that promote trust and team spirit, or the establishment of clear communication protocols that ensure everyone's voice is heard.In conclusion, collaborative mechanisms are vital for fostering effective teamwork and communication in the global workplace. English plays a fundamental role in bridging language barriers, but cultural awareness and sensitivity are equally important in ensuring successful collaboration. By combining the use of English withcultural understanding and tailored collaboration strategies, organizations can create a more inclusive,respectful, and innovative workspace where teams can achieve their full potential.**协作机制在全球职场:跨越语言和文化障碍**在全球职场中,协作机制的重要性不言而喻。
交通设备信息工程 英语

Transportation equipment information engineering (TEIE) is an interdisciplinary field that integrates advanced information technologies with transportation systems to enhance efficiency, safety, sustainability, and overall performance. This comprehensive analysis delves into the multifaceted aspects of TEIE, emphasizing the importance of maintaining high quality and standards throughout the design, implementation, and operation phases. It explores key components, technological advancements, challenges, and strategies for ensuring excellence in this rapidly evolving domain.I. Introduction to Transportation Equipment Information EngineeringTEIE encompasses a broad spectrum of activities, including the development of intelligent transportation systems (ITS), vehicle telematics, traffic management solutions, and communication networks for seamless data exchange. These systems rely on cutting-edge technologies such as artificial intelligence (AI), Internet of Things (IoT), big data analytics, and cloud computing to optimize the functionality and interconnectivity of transportation infrastructure, vehicles, and users.II. Key Components and Technological AdvancementsA. Intelligent Transportation Systems (ITS)ITS forms the backbone of TEIE, integrating various subsystems such as traffic monitoring, control, and information dissemination. Advanced sensors, cameras, and GPS devices collect real-time data on traffic flow, weather conditions, and road incidents, which is then processed and analyzed by AI algorithms to generate actionable insights for traffic managers and commuters. Examples include adaptive signal control systems, predictive maintenance tools, and dynamic routing applications that significantly improve traffic flow, reduce congestion, and enhance safety.B. Vehicle TelematicsTelematics combines telecommunications and informatics to monitor and manage vehicles remotely. In-vehicle sensors and wireless communication devices transmit data on vehicle location, speed, fuel consumption, and mechanical health to central servers. This information enables fleet operators to optimize routes, schedule maintenance, and enhance driver behavior, thereby reducing operational costs, improving fuel efficiency, and minimizing environmental impact.C. Communication NetworksEffective communication networks are crucial for seamless data exchange between various TEIE components. Dedicated Short Range Communications (DSRC), Cellular-V2X (C-V2X), and 5G networks facilitate real-time communication between vehicles (V2V), vehicles and infrastructure (V2I), and vehicles and pedestrians/cyclists (V2P). These technologies underpin critical safety applications like collision avoidance, emergency braking alerts, and cooperative adaptive cruise control.III. Challenges in Ensuring High Quality and StandardsA. Interoperability and StandardizationEnsuring seamless interoperability among diverse TEIE components and systems from different manufacturers is a significant challenge. The lack of unified standards and protocols can lead to data incompatibility, hindering effective communication and coordination. Organizations like the International Organization for Standardization (ISO) and the European Telecommunications Standards Institute (ETSI) play a vital role in developing and promoting global standards for ITS and related technologies.B. CybersecurityThe increasing reliance on digital technologies in TEIE exposes transportation systems to cyber threats. Malicious attacks could disrupt operations, compromise sensitive data, or even endanger public safety. Implementing robust cybersecurity measures, including encryption, access controls, intrusion detection systems, and regular security audits, is imperative to safeguard against these risks.C. Data PrivacyTEIE generates vast amounts of personal and vehicular data, raising concerns about privacy protection. Striking a balance between utilizing data for enhancing services and respecting individuals' privacy rights requires robust data governance frameworks, anonymization techniques, and transparent data usage policies.IV. Strategies for Ensuring High Quality and Standards in TEIEA. Collaborative Research and DevelopmentCollaboration among academia, industry, and government agencies is essential for fostering innovation, accelerating technology adoption, and establishing common standards. Public-private partnerships, research consortia, and international forums facilitate knowledge sharing, joint problem-solving, and the development of harmonized guidelines and best practices.B. Regulatory Frameworks and EnforcementStrong regulatory frameworks and enforcement mechanisms are necessary to ensure compliance with established quality and safety standards. Governments should regularly review and update legislation to keep pace with technological advancements, address emerging risks, and incentivize the deployment of secure, efficient, and environmentally friendly TEIE solutions.C. Continuous Monitoring, Evaluation, and ImprovementRegular monitoring, evaluation, and performance benchmarking are crucial for identifying system weaknesses, measuring effectiveness, and driving continuous improvement. Establishing Key Performance Indicators (KPIs) related to traffic flow, safety, emissions, and user satisfaction can help assess the impact of TEIE initiatives and inform evidence-based decision-making.V. ConclusionTransportation equipment information engineering holds immense potential to revolutionize the way we plan, manage, and use transportation systems. To fully harness this potential, it is imperative to maintain high quality and standards throughout the lifecycle of TEIE projects. This necessitates concertedefforts from all stakeholders, including policymakers, researchers, industry players, and the public, to address challenges, leverage technological advancements, and implement effective strategies that foster innovation, ensure safety and security, protect privacy, and promote sustainable mobility.While this analysis has touched upon several key aspects of TEIE, the topic's depth and breadth warrant further exploration and ongoing discourse in the face of rapid technological progress and evolving societal needs. As we continue to navigate the complex landscape of TEIE, the unwavering commitment to quality and standards will remain a cornerstone for realizing its transformative promise for smarter, safer, and more sustainable transportation systems.。
软件集成与协同开发考核试卷

A. RESTful API
B. RPC
C. JSON
D. XML
18.在软件集成过程中,以下哪种方式主要用于功能测试?()
A.单元测试
B.集成测试
C.系统测试
D.验收测试
19.以下哪个工具主要用于自动化测试?()
A. Selenium
B. Git
C. Eclipse
C.软件集成可以消除系统间的依赖关系
D.软件集成可以提高系统的稳定性
15.以下哪个工具主要用于自动化构建和部署?()
A. Jenkins
B. Git
C. Eclipse
D. MySQL
16.在软件协同开发中,以下哪个角色主要负责协调团队成员之间的工作?()
A.项目经理
B.架构师
C.开发者
D.测试工程师
C.系统间同步操作频繁
D.过度的性能测试
16.以下哪些技术可用于协同开发中的自动化构建?()
A. Jenkins
B. Travis CI
C. GitLab CI
D. Docker
17.在协同开发中,以下哪些做法有助于风险管理?()
A.定期进行风险评估
B.制定风险应对计划
C.依赖关键开发人员
D.忽视项目变更
4.持续集成
5.项目管理工具
6.逐步迁移
7.项目经理
8.系统接口
9. CI/CD工具
10.代码审查
四、判断题
1. √
2. ×
3. √
4. ×
5. ×
6. √
7. ×
8. √
9. √
10. √
五、主观题(参考)
通用依存关系

通用依存关系通用依存关系(Universal Dependencies,简称UD) 是一种用于句法分析的形式化语言。
它旨在将不同语言的句子转化为通用格式,使得可以使用相同的语法规则,使得机器翻译、文本分类、信息提取等多个领域的自然语言处理技术可以在多语言之间共享。
同时,UD也试图展现不同语言之间的共性和差异性,为语言学家研究语言之间的演化和变化提供了有价值的工具。
UD的基本认知是句子中的词汇(token)之间的关系,它可以通过多种不同的方式来表达词汇之间的关系,而这些方式的灵活性正是UD 的优势所在。
例如,“狗咬了人”这句话中,狗和人之间可以表示为主谓关系,也可以表示为宾语关系,更复杂一些,还可以表示为依托关系,表明狗的“咬”是依托于人的存在而完成的。
这些不同表示方式的存在,使得UD可以灵活地应用于不同语言之间的句子分析。
UD的使用不仅仅是对句子中的词语和关系的描述,还提供了标记和规范化的方法。
UD标准化不同语言之间的结构和关系,它要求词汇和依赖关系的形式在不同语言之间具有一定的可比性。
这种标准化使得跨语言分析和翻译可以变得更加自然和准确。
UD在中文、英文、西班牙语等多个语言之间取得了成功,在自然语言处理中应用广泛。
除了在自然语言处理中的应用外,UD在语言学研究中也具有很大的价值。
UD通过描述不同语言之间的相似点和差异点,为语言学家研究语言之间的演化提供了新的视角。
例如,瑞典语和西班牙语都是主谓宾结构语言,但在这两种语言中动词和宾语的位置是不同的,这一差异可能给语言学家提供了在不同语言之间进行比较的有效工具。
总之,UD是一种新兴的语言描述工具,它通过规范化不同语言之间的相似性和差异性,提供了跨语言分析和翻译的新视角。
UD可以应用于自然语言处理和语言学研究等多个领域。
随着UD标准的不断完善,它将会成为越来越多的语言学家和自然语言处理研究者的首选工具。
P24 TEXTB翻译

中国企业做决策
中国式的典型的(好)经理的做事方式是亲力亲为,对公司的各方面运作都很熟悉。
他或她相比起西方的经理来说授权给下级的任务要少很多,花在会议上的时间较少,花在咨询上的时间较少,但花更多时间在做决策和执行政策上。
一些最近的调查显示中国的经理认为出差旅游和开会是他们工作中最不重要的部分;他们宁愿花更多时间在办公桌旁边做事,评测和评价信息以及做决策。
有趣的是只有31%的受访者认为事先安排好的会议是重要的,仅仅4%的人认为未事先安排时间的会议是重要的。
做决策一事在中国企业中是偏向于独裁的。
决策通常是由个人来做,所有者/经理/主管私自做决策。
然后结果会公布,通常不附带解释。
假定了这决策已经通过足够的深思熟虑以及能够被那些因这决策而受到影响的人所理解。
然而,这决策也似乎事先做了大量的咨询。
好的中国经理会倾听和考虑工人们的意见,在某种程度上。
在侧面上也会有与内阁,当地官员以及关系网进行的讨论。
做决策的过程在中国可以非常快也可以非常慢。
快的那些就是根据经验来解决的。
不过,这些都不会有很多民主;领导做决策,然后雇员就得毫不动摇地执行它。
一旦决策已经做好了,要去挑战它,会被认为是一种非常严重的冒犯行为;那会让上级丢脸的。
在这阶段,工人们应该把自己的想法藏在自己心里。
俗语有云:“首先尊重等级,再来尊重你自己的真理。
”
一个后果是在等级中级别较低的人通常在承担责任方面表现很差。
在中国企业中有很多推卸责任和拖延办事的情况:比西方要多得多。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Cooperative Interoperability of Debugger and Editorin Distributed Tools EnvironmentWłodzimierz Funika1, Marcin Białek2, Piotr Pęgiel3,Institute of Computer Science AGH, Mickiewicza 30, 30-059 Kraków, Poland<funika@.pl, bialekmarcin@poczta.fm, barca@wp.pl>AbstractThe main focus of the paper is on the benefits and ways of cooperation betweentools supporting the development of applications in a distributed environmentthrough enabling a kind of interoperability based on the functionality of amonitoring system. This research is based on the capabilities of the JINEXTextension to the J-OCM monitoring system, which provides a suite ofinteroperability mechanisms. The J-OCM implements J-OMIS, standing for theJava-oriented On-line Monitoring Interface Specification. The idea of the toolscooperation using JINTEXT is fairly simple - it uses a mediator’s template thatallows the communication of individual tools to be controlled in an easy andflexible way. We used a very well known "gdb" environment as the debuggerand a source code editor. Obviously, "gdb" itself doesn't have any JINEXTcooperation functions implemented (undoubtedly most programs don't).Therefore the idea was to create a proxy that was translating the editor eventsand was able to raise own events dependent on the "gdb" state. In this way, aquite universal scheme was designed, that can be used when running other toolsnon aware of interoperability.1.IntroductionThe first question we’ll try to answer in this paper is – what interoperability is, and what it’s role is in modern computing? There can be several answers to this question, let us review them:•ability of two or more systems or components to exchange information and to use the information that has been exchanged. The above definition stresses the information exchange aspect. An example could be a situation when two people speaking completely different languages are trying to communicate. As a result they can exchange information but unless they find a way how to interpret the information it will be useless. A similar situation can be considered when talking about an interaction of monitoring tools. Different tools can use completely different data formats, can work using different logics. They can even be provided by different vendors.•ability of two or more applications to communicate with each other. Any application in a given toolset can communicate with any other application in a reliable way. Exchange of information is done on syntactical as well as on semantic level.•ability of two or more software components written in different programming languages (C++, Java, etc.) to interact and communicate with each other.Nowadays when distributed systems are commonly used, the meaning of interoperability is gaining on meaning. Later on we’ll try explain the need for interoperability and an effective way of obtaining it on a multi-user application toolset containing: Compiler, Editor and Debugger. The mentioned tools will be working in an interoperable way, with communication channel running through mediator.2.Situation before interoperabilityIn modern computer systems, software written by a single programmer is becoming rarity. Software projects are tending to become robust, and consume a large amount of resources. Therefore if there id no interoperability provided in software development support tools, one faces many difficult problems to solve:•Using systems which come from different vendors may cause a lot of problems due to different techniques of data acquisition, different formats of exchanged data produced when tools are functioning, and alsocompletely different operation logics. Using tools from different vendors may not help in the development process but even disturb it. Let us consider a situation when a tool, for example a debugger, modifies the code of an application, say by inserting a trap instruction in the middle of it. If there is another tool, e.g. a profiler operating on the same application and that tool is not informed about actions of the debugger;changes to the code may seriously affect the functioning of the second tool, even lead to its failure.•If there is more than one programmer working on an atomic piece of code (they will have to change the same piece of code), there will be problems with interpersonal communication. There will emerge probablya need to keep additional communication channels, project version control, a shared repository. Of course,each of this solution has been already proved and in theory works fine in large projects. But as always theory hasn’t much to do with practice in which programmers are lazy, usually work on stored sources on their computers, and don’t make updates frequently.One of the main requirements from monitoring tools is the ability not to disturb each other and, what is more desirable, to cooperate with each other. Another common requirement is to provide some additional functionality resulting from the awareness of the presence of other monitoring tools working on the same application. An example of this additional functionality is to stop measuring CPU load (in case of profiler) or drawing charts (incase of visualizes) whenever the monitored application is suspended by the debugger.There are very few coherent sets of monitoring tools (toolsets) which can be used to support the process of designing, implementing and maintenance software systems. Most of them are handy only if it comes to few requirements from the list.3.SolutionProviding the interoperability support for monitoring tools implies a need to solve a lot of various problems. Some of these problems stay at the low level of abstraction (structural conflicts) and some are connected with user-level (logical conflicts). In the former case, the problem of concurrently executed tools observing the same target system should be solved, to enable concurrent execution. In the latter case, two problems arise. The consistency conflicts require that the modifications introduced by one monitoring tool should be visible to other tools. The transparency conflicts require something opposite. The presence of modifications done by one monitoring tool should hidden from other tools. To cope with the problem, we have introduced a layered architecture as shown in Fig. 1.Fig 1. 4-tiered interoperability model1.Software layer: commonly known software tools, in our case an editor and debugger (functionalitydescribed later in Section 3). This layer is responsible for interaction with the end user.2.Tool layer: The tool layer together with the JINEXT mediator are representing a proxy pattern for softwaretools. This layer is responsible for interacting with JINEXT mediators – tools are oriented as well for activating events coming from the software layer like setting breakpoints in the editor and sending them to the mediator, as activating actions on behalf of the mediator like the information that editor wants to set some breakpoints in debugger, and handling them (sending to a lower level, or forcing action at the lower level software). This approach enables full cooperation within our software tools, but as we are explaining later, additional outputs and interfaces have been made to allow future development, and the integration of further tools.3.Mediator layer: The mediator model underlines the separation between a behavior and the tool whichimplements this behavior. The behavioral relationship term is used to describe relations between different tools. On the one hand, in the mediator model, there are behaviors provided by tools, on the other hand there are behavioral relations. A behavioral relation is a kind of connection between two behaviors of two different tools. An integrated behavior is represented as a set of independent behaviors integrated in a network of relationships. The behavioral structure and relation must be defined in a clear way. Then, an implementation of behaviors and relations comes. Each behavior in the model is implemented by an object that represents this behavior. Adding relationships to the behavioral model results in adding an object that is representing this relationship. The mediator solution characterizes a high level of dynamics. Behavioral relationship objects are called mediators in this model. At the mediator level we exploit JINTEXT,an extension to J-OMIS designed to support interoperability in Java that allows each cooperating application to retain transparency of its implementation. As a result the applications do not need to know anything about each other while still being capable to work together.JINTEXT provides:• A mechanism allowing for the observation of events occurrences in tools, to call actions in a tool and to define a relation between an individual event and an action. This is necessary to provide thesemantic level integration between tools.• A mechanism enabling tools to observe and modify the state of different objects in the system. The changes introduced by one tool should be announced to these tools which are also observing thesame object (consistency) or transparent for other tools so that an access to modified object doesnot result in a system's failure (transparency).•An option to enable cooperation between different monitoring tools. It means that these tools agree to cooperate and monitor the same objects. As a result, a new functionality (new actions) of eachtool is visible since this agreement. This cooperation means that tools know about each other.•Obtaining control over possible interactions between monitoring tools, direct communication between tools is forbidden. Different monitoring tools should not be aware of each other.•Monitoring tools are divided into different categories ('tool types'). Each category has its specification and interface. Any particular monitoring tool can be replaced by another one,provided that it implements the same interface (i.e. it provides the same actions and generates thesame events) as expected by other tools.•In order to provide extensibility and to support new monitoring tools, it is possible to define a new monitoring tool type and relations between the new type and the existing ones.•Each tool type provides a list of events which can be raised by this tool type and a list of actions which can be called by other tools. An event is a kind of notification about an important change inthe system etc. An action is a service which can be used by other monitoring tools and monitoringsystem.•In order to avoid large modifications to the monitoring tools' source code there are just a few services provided by JINEXT extension which can be used by monitoring tools. In order to provideevent support in monitoring tools, the standard omis_request(":request")call should bereplaced by the omis_request(":jintex_request(':request')") call. In order to provideactions, new parts have to be added to the monitoring tools' source code.Monitoring system layer: As the monitoring system for our project, we have chosen J-OCM. It is an implementation of the J-OMIS specification, consisting of a set of distributed components providing tools an interactive access to the Java application and runtime environment. J-OCM is designed in the following way: the Local Monitor (LM) is an independent monitor process, which provides an interface similar to NDU, but only processes requests to operate on local objects. The functionality of the LM was extended to support the monitoring ofJava applications. An additional monitoring code, linked to local monitors as a dynamic library is called JVMEXT. To execute the requests received from LM, an agent embedded into Virtual Machine is used. It is based on standard Java native interfaces such as JVMPI, JNI, and JVMDI, later on replaced by the JVMTI interface.OMIS (On-line Monitoring Interface Specification) was designed to create a standard for runtime tool development for parallel and distributed systems. The specification defines an interface of a programmable monitoring system which supports variety of tools. OMIS is intended to be extensible, as it is necessary in order to be able to support new tools and different programming environment. J-OMIS is a Java-oriented extension to OMIS.4.DesignActions.An action is a kind of service provided by a tool type. An action means that the tool implementing a given tool type has the ability to execute some service, e.g. to perform some calculations or to retrieve/change the state of some object. In case of a debugger, an example action can be suspend. This action can be used to suspend a process.A compiler tool may provide the compile action, which is used to compile the source code of a program. An action has a name and, optionally, parameters. The parameters may be used, e.g. to pass a name of a file with a program’s source code, or the id of a process that we want to suspend. In Fig. 2 a fragment of the XML file responsible for introducing new actions is presented. In the XML description there is a name of the action and a description provided to better understand what this action is used for. For each action, a list of parameters is introduced. Each parameter has its name, description and the type. The type of parameter is one of the standard OMIS types, like Token, Integer, String etc.<actions><action><name>change_process_priority</name> <!—name of action<description>Used to change the priority of given process.</description><mode>Cooperation</mode> <!—mode of cooperation<parameters> <!—list of action’s parameters<param><name>process_id</name> <!—name of parameter<description>The id of the process.</description><type>Token</type> <!—type of parameter</param><param><name>priority</name><description>The new priority of the process.</description><type>Integer</type></param></parameters><action><action>……</action></actions>Fig. 2Fragment of the XML file responsible for introducing new actionsEvents. An event is raised by the tool if something important happens in this tool. An event can be raised if the internal state of the tool changes, if the tool starts or finishes some process, etc. An event may be, e.g., raised if an editor finishes saving a modified source code of some program. Every event is identified by its name. An event can be raised with some parameters. In our example, a parameter can be used to provide the name of the file saved by the editor. In Fig. 3 a fragment of the XML file describing events which can be raised in the example Debugger tool type, is presented. Implementing the Debugger tool type by some tool means that this tool must raise an event called process_suspended whenever it suspends a process. The type of the parameter can be one of standard OMIS types, like Token, Binary, String etc.<events><event><name>process_suspended</name> <!-- name of event --><description> <!-- description of event -->Event generated if a debugger stopped a process.</description><mode>Always</mode> <!-- mode of event --><parameters> <!-- list of event's parameters --><param><name>process</name> <!-- name of parameter --><description> <!-- description of parameter -->Suspended process token.</description><type>Token<type> <!-- type of parameter --></param></parameters></event><event>......</event></events>Fig 3. Fragment of the XML file describing events for the Debugger tool typeMediators. In JINEXT, in addition to the actions and events generated by tools, there are structures called mediators.A mediator is a kind of connection between the event generated by a tool (implementing a given tool type) and the action which should be executed by another tool (implementing a different tool type) when the event occurs. The use of mediators has many advantages mentioned above. The most important one is the isolation between the events and actions of tools, i.e. their behavior and dependences between different tools. Tools do not have to care about synchronization with other tools, they do not have to know about other tools features and even about their presence.5.Project DescriptionAs mentioned above, our project, consists of three developed tool applications working together in an interoperable environment.Editor Tool. Normally, the editor tool provides:•loading the file into memory, starting editing it•changing the content of the file•saving a modified file on disk•closing the file, finishing editing it.First of all, the editor tool is integrated with the software layer editor. As we have not found any open source project that met our criteria, we’ve written an editor from the scratch. The editor had been completely written in C++ using the Qt library (mainly for making GUI), and allows all the functionality listed above.The tool provides:Actions:•Debugger error – displays onto the screen error sent by debugger.•Source changed– warns that some of the sources opened in the current session have been changed, and shows the place of change (this way the programmer is aware of changes made byothers).•List watches – Editor has a list of watches it’s currently watching, so when asked to perform this action it is parsing the message to find the needed data.•Events:•Step, continue, start debugging– actions for the debugger.•Source changed – propagating information about changes made to the source code•Set break points – setting debugger breakpoints.Fig. 4. Editor GUIDebugger Tool. Our debugger is a standard on-line (interactive) debugger, it allows the user to get a detailed view of the program execution and interaction with debugger during the runtime of the debugged program. It provides functions to suspend threads at given locations in the source code (breakpoints), to view and modify the program's data structures, to determine the source code position where threads are suspended and to execute threads in a controlled fashion.A typical scenario of on-line debugging is to start the program, suspend it at a given breakpoint. Once the program is suspended, its state can be examined and modified. Finally, the program is resumed until another breakpoint occurs or the end of the program is reached.The debugger tool is completely written in C, as a software layer the tool uses the open-source gdb distribution. To operate this application, our tool captures its input and output streams so that every gdb command can be performed, and execution results can be read.The debugger tool can raise the following events:•Stop line – the debugger is informing that he was suspended at specified line.•Debugger error – the debugger has encounter some problems which it cannot deal on its own, and it is reporting the mediator about this fact.•List watches – the debugger is sending the values of all variables (total screen dump)It provides the following actions:•Continue, step – running standard debugger actions.•Begin debug – start a debugger instance•Set breakpoints – sending a breakpoint list for the debugger useCompiler Tool. The typical actions of the compiler tool are:•compiling a given file;•compiling a given file and linking it;•changing the parameters and settings of the compilation;Like in the case of debugger, there was no need here to make life more complicated, so we have used open-source g++ project to fulfill our needs. The only action that is made by the compiler is to compile a file with specified options. And it is made each time the editor changes anything in source files.Interoperability existing within tools (scenario)The below scenario describes a cooperation and integration between three different tools: the editor, which is used tointroduce changes to an application source code, the compiler, which compiles and links the code of application, andthe debugger used to locate bugs in the code and to improve the application's performance. The sequence diagram in Fig. 4 illustrates a following scenario:1.the editor displays the source code of a Java class2.the debugger attaches the application3.the debugger starts the application4.the user modifies the source code of the class being edited5.the editor saves the modified source code onto disk6.the compiler automatically recompiles the source code7.the debugger is notified about the changed code of the application8.the debugger optionally restarts the application.Fig. 5. Interoperability scenario6.Further enhancements of interoperabilityAs the basic set of tools was already developed and defining new interfaces is quite easy depending on the actual application structure, we’re intending to add more functionality to our project, so the next steps will be adding: Performance Analyzer: For optimizing a program it is necessary to look at possibilities to eliminate the sources of performance losses. The performance analyzer is a tool used to search those places of the program execution which are the most time and CPU load consuming.The major focus of the performance analyzer is on observing the parameters and state of the monitored application. The main reasons for performance loss are unnecessary invocations, bad code localization (for example, some parts of code which are used inside a loop) and idle processor cycles. In case of parallel and grid applications, the idle processor state may result from the sequential part of algorithms. Of course, if the sequential nature of an algorithm is the only reason of performance loss there is nothing to do. But if idle states are caused by delays due to accessing remote data or by conflicts when doing it, higher performance can be achieved by means of different data access, communication schemes.Flow-visualizer: The flow-visualizer tool is another type of monitoring tools. Its functionality is to present the global state of a whole application. Its functionality can be compared with a debugger's functionality, but on a completely different level of granularity. In case of a debugger tool, a fine-grained level is considered. The debugger provides information about a thread's state, variables' values etc. But, especially, for fixing bugs related to communication and/or synchronization, the global state of the program is much more importan t. The global state of the application can be presented by global views. Such views may contain information about the tasks which are currently waiting for messages, tasks which are sending data to which groups, what is a content of messages queues. This kind of information provides a global, coarse-grained view of the application state.A typical functionality provided by the flow-visualizer is:•attaching to an existing application•attaching to a particular, single node the application is running on•gathering information about communication and synchronization between tasks, threads etc., information is collected in some iterations•storing the information for future use•displaying the data using some graph•changing the time point on time line to view historical/actual data.7.SummaryThis paper focused on a kind of interoperability directly related to the functionality of application development support tools and providing the capabilities of their cooperation, to strengthen their potential when used in the application development process. We believe that the rapid growth of parallel processing, which is more close to the situation we are in nowadays – when many people are working in parallel with each other – will necessitate shortening the time and resources needed for completing the project. In the above sections we showed that interoperability can become a very useful feature in developing advanced computer software in multi-developer environment. We have shown that cooperation between Debugger and Editor can speed-up the development process, and limit the number of errors and misunderstandings during the development process. We think that when the rest of the system is finished, tools can form a useful toolset for working in a large programming team, with the capability of easy adding of further tools provided by JINEXT (e.g. project management tools).Acknowledgements.This research is partly supported by the KBN grant 4T11C 032 23.Bibliography1.Arkadiusz Janik: Interoperability of tools for development of distributed Java applications. Master of ScienceThesis. AGH, Krakow, 20042.Roland Wismüller: Interoperable Laufzeit-Werkzeuge für parallele und verteilteSysteme, Habilitationsschrift,Universität Munchen, 20013.Marcin Smetek: OMIS-based Monitoring System for Distributed Java Applications. Master of Science Thesis.AGH, Krakow, 20034.Piotr Mietel, Rafal Ostrowski: Extensions to On-line Monitoring Interface Specification for Java Applications.Master of Science Thesis. AGH, Krakow, 20015.Trinitis, J., Sunderam, V., Ludwig, T., and Wismüller, R.: Interoperability Support in Distributed On-lineMonitoring Systems. In: M. Bubak, H. Afsarmanesh, R. Williams, and B. Hertzberger, editors, High Performance Computing and Networking, 8th International Conference, HPCN Europe 2000, volume 1823 of Lecture Notes in Computer Science, Amsterdam, The Netherlands, May 2000. Springer。
