Overview of VPE a visual environment for message-passing parallel programming
science of the total environment模板 -回复

science of the total environment模板-回复Subject: Understanding the Importance of Science of the Total EnvironmentIntroduction (150 words)The scientific study of the environment is crucial for understanding the complex interactions between natural systems and human activities. The journal "Science of the Total Environment" provides a platform for researchers to explore a wide range of topics related to environmental science, including pollution, climate change, biodiversity, and sustainable development. In this article, we will delve into the significance of the journal and discuss how it contributes to our understanding of the environment.1. Overview of Science of the Total Environment (200 words)1.1 Historical BackgroundScience of the Total Environment, established in 1972, has evolved as a leading interdisciplinary journal in environmental studies. It covers research from various fields, including environmental chemistry, ecology, geosciences, and atmospheric sciences.1.2 Aim and ScopeThe primary objective of the journal is to publish high-quality research that aids in the comprehensive understanding of environmental processes. It promotes the integration of scientific knowledge across disciplines to address the complex environmental challenges we face today.2. Contributions to Environmental Science (400 words)2.1 Pollution ResearchScience of the Total Environment plays a crucial role in advancing pollution research. It covers a broad spectrum of pollutants, including air, water, soil, and noise pollution. By providing a platform for publishing groundbreaking studies, the journal helps in developing strategies to mitigate pollution and protect human health and ecosystems.2.2 Climate Change StudiesAs climate change continues to pose significant threats to our planet, the journal is instrumental in disseminating research related to this issue. It supports studies on climate modeling, impact assessment, mitigation, and adaptation strategies. These publications contribute to a better understanding of the global climate system and enable informed decision-making.2.3 Biodiversity and Ecosystem ScienceScience of the Total Environment features research articles on biodiversity conservation and ecosystem dynamics. It sheds light on the impacts of human activities on biodiversity loss and habitat degradation. This knowledge is essential for effective conservation initiatives and sustainable ecosystem management.2.4 Sustainable DevelopmentThe journal plays a vital role in promoting sustainable development by publishing research on environmental indicators, assessment tools, and policy evaluation. It encourages the inclusion of environmental, economic, and social perspectives indecision-making processes, ensuring the long-term well-being of both current and future generations.3. Research Methodologies and Techniques (300 words)3.1 Integrative ApproachesScience of the Total Environment encourages interdisciplinary research that integrates various scientific disciplines. This approach enhances our understanding of complex environmental issues, as it considers multiple factors and their interactions.3.2 Advanced Analytical TechniquesThe journal highlights studies that utilize advanced analytical techniques to measure pollutants, evaluate environmental changes, and assess ecosystem health. These techniques include remote sensing, geospatial analysis, mass spectrometry, and molecular biology approaches. Such methodologies provide accurate and comprehensive data required for addressing environmental challenges.4. Dissemination of Research Findings (200 words)4.1 Global RelevanceScience of the Total Environment serves as a global platform, attracting contributions from scientists worldwide. This diversity ensures a broad understanding of environmental issues and fosters collaboration among researchers from different countries and cultural backgrounds.4.2 AccessibilityThe journal publishes peer-reviewed articles that are freely accessible, fostering the dissemination of knowledge to a wide audience. Open access improves the visibility and impact ofresearch findings, ultimately leading to more informed environmental policies and practices.Conclusion (150 words)The "Science of the Total Environment" journal is of significant importance in unraveling the complexities of our environment. By covering a wide range of environmental topics and fostering interdisciplinary research, it contributes to our understanding of pollution, climate change, biodiversity, and sustainable development. Through the utilization of advanced research techniques and the dissemination of findings to a global audience, this journal plays a crucial role in addressing pressing environmental challenges. Understanding the science of our total environment is vital for promoting responsible stewardship of our planet and ensuring a sustainable future.。
TTI ISO 14001环境管理指南说明书

TTI ISO 14001 Environmental Programs Overview There is a growing awareness about the condition of our world and the fact that it really isn’t the self-cleaning planet we humans hoped it would be. Now major initiatives are required by everyone to limit our footprint on ecosystems that we are increasingly discovering to be much more fragile than was once thought. The electronics industry is at the forefront of this effort and TTI is doing our part to lessen the impact our operations have on the environment. A major component of our initiative is certification under ISO 14001 – an international standard for processes and procedures that guide various aspects of the TTI environmental program. This standard covers TTI headquarters and warehouse operations and serves as guidance for our locations and sales offices around the world.ISO 14001 Array In 2014, TTI met the registration requirements of ISO 14001 as apart of our corporate commitment to ongoing management andimprovement of our environmental programs and processes.This included a top-to-bottom review of how we do businessand the manner in which we use resources, the byproductswe create, and how we dispose of waste. This review, which iscontinually ongoing as part of our environmental policy, allowsTTI to identify the major areas where we target emphasis for themost effective return on our efforts.Current information is available on our website – or by contacting the TTI quality department at 1.800.CALL.TTI.Focused on ResultsAs TTI is a distributor and not a manufacturer, we have a limitedwaste stream. In fact, it’s primarily cardboard used for thepacking and shipping of our products. That became our first pri-ority, as we sought out the areas where, as an entity with peopleworking around the globe we could do the most good. T o do thatwe’ve identified more efficiently consuming power, and reducingour water usage as areas with the most opportunity to help theenvironment.TTI, Inc. – A Berkshire Hathaway Company | 1.800.CALL.TTI • RecyclingTTI recycles all waste paper material including routine office paper waste as well as the tons of cardboard shipping materials processed through our shipping and receiving areas. Through these processes, we prevent tons of cardboard from going into landfills every year.Electricity ReductionOne of TTI’s largest areas targeted for reduction is electricalusage. With hundreds of employees and hundreds of thousandsof square feet of warehouse space to light, heat and cool, it’s achallenging balance between a comfortable working environment,productivity and environmental impact. We’ve installed high-efficiency lighting fixtures and motion sensors to trigger them onlywhen necessary. T o improve the efficiency of heating and cooling,new high-efficiency chillers and air handlers replaced old unitsand air curtains were installed at warehouse dock doors to reduceexterior air infiltration.Saving WaterWater conservation is a part of life at TTI – low-flow toilets andfixtures, and motion-operated automatic shut-off facets are nowinstalled in all TTI restrooms. Outside, our landscaping is irrigatedvia a drip system, which has replaced the traditional stylesprinkler system.Environmental Policy (per CP 48)TTI is committed to environmental stewardship pursuing program and initiatives designed to protect and improve our environment. We believe that this stewardship as a responsible corporate citizen contributes to the achievement of our mission to provide a home for hard working, dedicated, knowledgeable, ethical people who believe completely in this company and this philosophy.Our guiding principles:• Reduce and minimize energy and water consumption and prevention of pollution through continualimprovement of our environmental management system using recycled materials and earth-friendlysubstances whenever practical. Lessen our impact through reuse, recycling and reduction.• Determine the significant environmental aspects over which the organization has control. Set and review applicable environmental objectives and targets through periodic meetings.• Comply with relevant environmental legislation and regulations and with other requirements to which the organization subscribes including ISO 14001.7/225 0。
保护森林类vi手册

保护森林类vi手册Forests are vital ecosystems that provide a wide range of environmental, social, and economic benefits. 森林是至关重要的生态系统,提供广泛的环境、社会和经济利益。
They are home to countless species of plants and animals, serving as a crucial habitat for biodiversity. 它们是无数植物和动物的家园,对生物多样性起着至关重要的作用。
Additionally, forests play a crucial role in carbon sequestration, helping to mitigate the effects of climate change. 此外,森林在碳封存中发挥着至关重要的作用,有助于减轻气候变化的影响。
In recent years, forests around the world have been facing increasing threats from deforestation, illegal logging, and wildfires. 近年来,全球各地的森林面临着日益严重的砍伐、非法采伐和森林大火的威胁。
These activities not only result in the loss of valuable habitat for wildlife but also contribute to the release of carbon dioxide into the atmosphere, exacerbating climate change. 这些活动不仅导致珍贵的野生动物栖息地丧失,还导致二氧化碳释放到大气中,加剧了气候变化。
HPE OneView和Synergy学习路径说明书
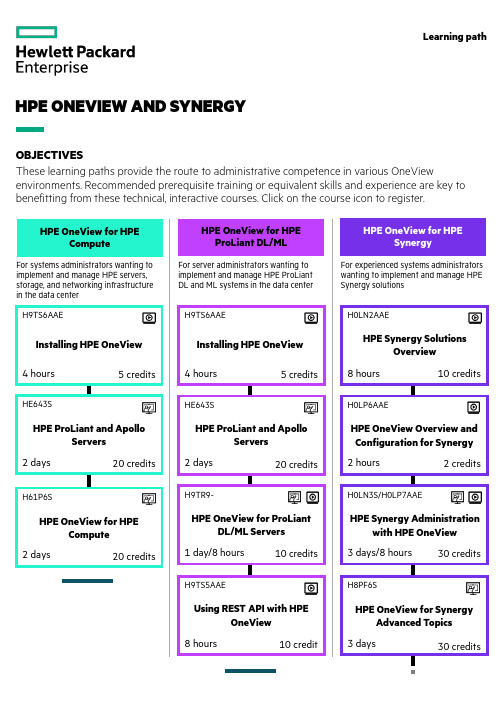
HPE ONEVIEW AND SYNERGYOBJECTIVESThese learning paths provide the route to administrative competence in various OneViewenvironments. Recommended prerequisite training or equivalent skills and experience are key to benefitting from these technical, interactive courses. Click on the course icon to register.Learning pathHPE OneView for HPEComputeHPE OneView for HPE ProLiant DL/MLHPE OneView for HPESynergyFor systems administrators wanting to implement and manage HPE servers, storage, and networking infrastructurein the data center For server administrators wanting to implement and manage HPE ProLiant DL and ML systems in the data center For experienced systems administrators wanting to implement and manage HPESynergy solutions HPE ProLiant and ApolloServers HE643S2days20 credits Installing HPE OneView H9TS6AAE4hours5 credits Installing HPE OneView H9TS6AAE4 hours5 credits HPE ProLiant and ApolloServers HE643S2days20 credits HPE OneView for ProLiantDL/ML Servers H9TR9-1 day/8 hours10 credits Using REST API with HPEOneView H9TS5AAE8 hours10 creditHPE Synergy SolutionsOverview H0LN2AAE8 hours10 creditsHPE OneView Overview and Configuration for Synergy H0LP6AAE2hours2 creditsHPE Synergy Administrationwith HPE OneView H0LN3S/H0LP7AAE3 days/8 hours30 creditsHPE OneView for SynergyAdvanced Topics H8PF6S3days30 creditsHPE OneView for HPECompute H61P6S2days20 creditsLearning pathSelf-Study Labs -HPESynergy Firmware H61P4AAE2 days10 credits© Copyright 2023 Hewlett Packard Enterprise Development LP. The information contained herein is subject to change without notice. The only warranties for Hewlett Packard Enterprise products and services are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. Hewlett Packard Enterprise shall not be liable for technical or editorial errors or omissions contained herein.All third-party marks are property of their respective owners.July 2023eLearningVirtual instructor-led training (VILT)Required courseOptional course KEYLEARN MORE AT/ww/learnconvergedsystemsIntroduction to Managing HPE Synergy with OneView H8PF2S1day10 creditsOne-day workshop focusing on HPE Synergy solutions for those considering a composable infrastructure project HPE Synergy WorkshopImplementing Advanced VMware Technologies on HPE Synergy and Primera H9TS9S2days 20 credits。
environmental engineering 书

environmental engineering 书
1. 《环境工程学导论》(Introduction to Environmental Engineering):作者是Mackenzie L Davis和David A. Cornwell,这本书是环境工程领域的入门教材,涵盖了水质、水污染控制、废水处理、大气污染控制等内容。
2. 《环境工程学基础》(Fundamentals of Environmental Engineering):作者是James R. Mihelcic和Julie B. Zimmerman,这本书介绍了环境工程学的基本概念、原则和方法,包括水、废水、固体废弃物和大气污染控制等内容。
3. 《环境工程实践》(Environmental Engineering Practice):作者是N. K. Nema,这本书侧重于环境工程在实际项目中的应用,包括环境影响评价、环境管理系统、环境监测与调查等方面。
4. 《环境化学与环境工程》(Environmental Chemistry and Environmental Engineering):作者是James G. Speight,这本书结合环境化学和环境工程,介绍了环境污染的化学特性以及相应的治理技术。
Envision
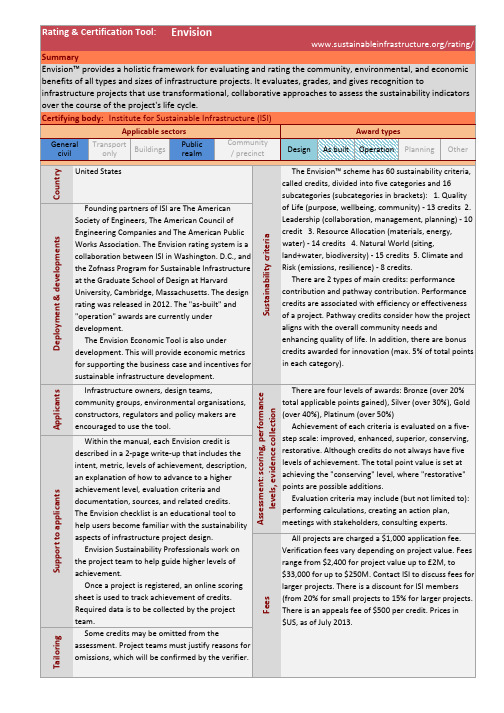
Award types
General civil
Transport only
Buildings
Public realm
Community / precinct
Design Aቤተ መጻሕፍቲ ባይዱ built Operation Planning Other
Country
Deployment & developments
over the course of the project's life cycle.
Certifying body: Institute for Sustainable Infrastructure (ISI)
Applicable sectors
benefits of all types and sizes of infrastructure projects. It evaluates, grades, and gives recognition to
infrastructure projects that use transformational, collaborative approaches to assess the sustainability indicators
There are four levels of awards: Bronze (over 20% total applicable points gained), Silver (over 30%), Gold (over 40%), Platinum (over 50%) Achievement of each criteria is evaluated on a five-‐ step scale: improved, enhanced, superior, conserving, restorative. Although credits do not always have five levels of achievement. The total point value is set at achieving the "conserving" level, where "restorative" points are possible additions. Evaluation criteria may include (but not limited to): performing calculations, creating an action plan, meetings with stakeholders, consulting experts.
visual question answering综述 -回复

visual question answering综述-回复Visual Question Answering (VQA) is a growing field in computer vision and natural language processing that aims to develop algorithms capable of answering questions about visual content. In this article, we will provide an overview of VQA, discussing its applications, challenges, and recent advances.1. Introduction to Visual Question Answering:Visual Question Answering is a task that requires the understanding of both visual and textual information. It aims to bridge the gap between images and natural language by equipping machines with the ability to comprehend and respond to questions about visual content. VQA algorithms typically take an image and a corresponding question as input and generate a textual answer as output.2. Applications of Visual Question Answering:VQA has numerous applications across various domains. Some of the key application areas include:- Assistive Technology: VQA can be used to develop tools that assist visually impaired individuals by providing them with relevant information about their surroundings.- E-commerce: VQA can enhance the online shopping experience by allowing users to ask questions about products and receive immediate answers.- Virtual Assistants: VQA can empower virtual assistants like Amazon Alexa or Google Assistant to answer questions about images shown on user devices.- Autonomous Vehicles: VQA can be utilized in autonomous vehicles to understand and respond to visual queries about the environment.3. Challenges in Visual Question Answering:VQA poses several challenges due to the complexity of understanding visual content and interpreting questions. Some of the key challenges include:- Visual Understanding: Images can contain intricate details, and algorithms need to accurately interpret and comprehend them.- Linguistic Understanding: Understanding the semantics, syntax, and context of questions is crucial for generating accurate answers. - Scalability: VQA models need to handle a large number of images and questions efficiently to be practical for real-time applications. - Bias: VQA models can inherit biases from training data, leading to biased or unfair answers.4. Approaches in Visual Question Answering:There are two primary approaches in VQA: classical and deep learning-based methods.- Classical Approaches: These methods use handcrafted features extracted from images and questions, combined with techniques like support vector machines or decision trees to answer questions. These approaches often rely on engineered features and linguistic priors.- Deep Learning Approaches: Deep learning-based methods have gained popularity in VQA due to their ability to learn features directly from data. Convolutional Neural Networks (CNNs) are used to encode visual information, while Recurrent Neural Networks (RNNs) or Transformers encode textual information. These models are trained end-to-end to answer questions.5. Recent Advances in Visual Question Answering:Recent advancements in VQA have focused on tackling challenges related to bias, interpretability, and robustness. Some notable approaches include:- Attention Mechanisms: Attention mechanisms help models focus on relevant parts of the image or question, improving performance.- Adversarial Training: Adversarial training techniques mitigate bias in VQA models by explicitly addressing dataset imbalances or biased annotations.- Explainable VQA: Researchers are developing novel approaches to provide explanations or reasoning steps for VQA model predictions, enhancing interpretability.- Multimodal Fusion: Advanced fusion techniques combine visual and textual information more effectively, resulting in improved answer generation.In conclusion, Visual Question Answering is an exciting and rapidly evolving field that aims to bridge the gap between visual content and natural language understanding. It has various applications and poses significant challenges. The integration of deep learning techniques and recent advancements has shown promising results, making VQA an active area of research with immense potential for practical applications.。
environmental science英文缩写

environmental science英文缩写Environmental science, often abbreviated as "ES", is an interdisciplinary academic field that integrates various scientific disciplines to study the environment and solve environmental issues. It combines knowledge from biology, chemistry, physics, geology, ecology, and other disciplines to understand the Earth's natural systems and the impact of human activities on the environment.One of the primary goals of environmental science is to identify and address environmental problems, such as pollution, deforestation, climate change, and loss of biodiversity. By studying the interactions between humans and the environment, environmental scientists can develop solutions to protect natural resources, reduce pollution, and promote sustainable development.Environmental science encompasses a wide range of topics, including environmental chemistry, environmental biology, environmental geology, environmental policy, and environmental management. Researchers in this field study the Earth's ecosystems, natural resources, and the impact of human activities on the environment.Environmental science is also closely related to environmental engineering, which focuses on developing technologies to mitigate environmental problems and improve environmental quality. Together, environmental scientists and engineers work to develop innovative solutions to protect the environment and promote sustainable development.In recent years, environmental science has become increasingly important as the world faces growing environmental challenges, such as climate change, pollution, and habitat destruction. Governments, businesses, and individuals are turning to environmental science to understand these issues and develop strategies to address them.Overall, environmental science plays a critical role in promoting environmental sustainability and protecting the Earth's natural resources for future generations. By studying the environment and developing innovative solutions, environmental scientists are working towards a more sustainable and healthy planet.。
2024年教师资格考试高级中学学科知识与教学能力英语模拟试卷与参考答案

2024年教师资格考试高级中学英语学科知识与教学能力模拟试卷与参考答案一、单项选择题(本大题有30小题,每小题2分,共60分)1、题干:The teacher’s ability to foster critical thinking in students is particularly important in the discipline of ________.A. MathematicsB. HistoryC. EnglishD. Science答案:C解析:The correct answer is C. English. The question emphasizes the importance of fostering critical thinking, which is a key aspect of language arts education. English as a discipline often emphasizes critical thinking skills, such as analyzing texts and interpreting literature, which makes it the most relevant option among the choices provided.2、题干:Which of the following is NOT a common instructional strategy used to promote student engagement in an English class?A. Group discussionsB. Project-based learningC. Teacher-centered lecturesD. Socratic seminars答案:C解析:The correct answer is C. Teacher-centered lectures. The question asks for the instructional strategy that is NOT common for promoting student engagement. Group discussions (A), project-based learning (B), and Socratic seminars (D) are all known to increase student participation and engagement.Teacher-centered lectures (C), on the other hand, are more traditional and may not encourage active student involvement as much as the other strategies.3、The se ntence “She has a bright smile” can be paraphrased as:A. She has a cheerful expression.B. She has a dim smile.C. She has a bright thought.D. She has a dark smile.Answer: AExplanation: The phrase “a bright smile” implies a pleasant and friendly expres sion, which can be accurately paraphrased as “a cheerful expression.” The other options either change the meaning or are not close synonyms of the original phrase.4、Which of the following sentences is an example of a declarative sentence?A. “Where is my pen?”B. “I will be there tomorrow.”C. “Don’t you think she’s talented?”D. “Can you help me with this?”Answer: BExplanation: A declarative sentence makes a statement or declares a fact. “I will be there tomorrow” is a clear statement of future intentio n, making it a declarative sentence. The other options are questions (A and D) or a tag question (C), which are not declarative sentences.5、The teacher’s role in the classroom is crucial for student learning. Which of the following statements best describes the role of a teacher in fostering student engagement?A)The teacher should act as a passive facilitator, allowing students to guide their ownlearning.B)The teacher should dominate the class, ensuring that all students follow the samecurriculum.C)The teacher should create a supportive and interactive environment that encouragesstudent participation.D)The teacher should primarily focus on correcting student mistakes to improve theirperformance.Answer: C) The teacher should create a supportive and interactive environment that encourages student participation.Explanation: A supportive and interactive classroom environment is essential for student engagement. This approach allows students to actively participate in their learning, which can lead to better understanding and retention of the material.6、When designing a lesson plan for a unit on environmental conservation, which of the following teaching strategies would be most effective in promoting critical thinking and understanding among students?A)Presenting a lecture and providing a list of facts about different environmental issues.B)Using multimedia presentations to showcase images and videos related toenvironmental conservation.C)Facilitating a debate or discussion on the causes and solutions to environmentalproblems.D)Assigning a research project where students investigate a specific environmentalissue.Answer: C) Facilitating a debate or discussion on the causes and solutions to environmental problems.Explanation: A debate or discussion encourages students to think critically about the topic, analyze different perspectives, and develop arguments. This interactive approach can enhance their understanding and appreciation of the complexities involved in environmental conservation.7、The following sentence is a fragment. Which of the following words can be added to make it a complete sentence?A. The students enjoyed the movie, but they _______.B. The students were enjoying the movie _______.C. The students enjoyed the movie _______.D. The students were enjoying the movie, and they _______.Answer: BExplanation: The sentence “The students were enjoying the movie” is a complete sentence on its own. The word “but” can be added to show contrast with the following clause, making it a compound sentence. The other options do not make the sentence grammatically correct or complete.8、Which of the following sentence structures is most appropriate for describing a sequence of events?A. It is important that we should do this, because it will help us learn.B. The first step is to collect the necessary information, the second step is to analyze it, and the final step is to make a decision.C. Although we tried, we were unable to reach the destination on time.D. If we do not act now, the situation will become worse.Answer: BExplanation: The structure “The first step is to collect the necessary information, the second step is to analyze it, and the final step is to make a decision” effectively describes a sequence of events, with each step clearly identified. The other options do not present a clear sequence of events.9、The sentence “The students were all engaged in their activities when the bell rang.” is an example of which tense structure?A. Simple PresentB. Simple PastC. Present ContinuousD. Past ContinuousAnswer: C. Present ContinuousExplanation: The sentence describes an action that was ongoing at the moment the bell rang. The present continuous tense is used to talk about actions happening at the moment of speaking, which fits the context of the sentence.10、In the following sentence, “She has finished her homework and is now preparing for the exam,” which part of speech is underlined?A. has finishedB. herC. nowD. preparingAnswer: D. preparingExplanation: The underlined word “preparing” is a gerund, which is a verb form that functions as a noun. Gerunds are often used as subjects, objects, or complements in sentences. In this case, “preparing” is the gerund that functions as the subject of the second clause.11.The teacher, who has been teaching for five years, is highly respected by his students for his_______teaching style.A. creativeB. strictC. humorousD. traditionalAnswer: AExplanation: The question is asking about the teacher’s teaching style that is highly respected by his students. “Creative” is the most appropriate choice to describe a style that is likely to be respected, as it implies innovation and engagement in the teaching process.12.In order to enhance the students’ reading comprehension, the teacher uses a variety of_______techniques in her English class.A. readingB. questioningC. listeningD. writingAnswer: BExplanation: The question is inquiring about the techniques used to improve reading comprehension in an English class. “Questioning” techniques, such as Socratic questioning or guided inquiry, are specifically designed to enhance comprehension and critical thinking skills, making it the most suitable answer among the options provided.13、What is the most appropriate tense to use when describing a routine activity that occurs on a daily basis?A. Present simpleB. Present perfectC. Past simpleD. Future simpleAnswer: A. Present simpleExplanation: The present simple tense is used to describe habits, regular routines, and general truths. It is the correct tense to use when referring to daily activities that are habits or routines.14、Which of the following sentences uses the correct form of the passive voice?A. The students are given by the teacher.B. The teacher gives the students.C. The students are given to by the teacher.D. The students are given from the teacher.Answer: C. The students are given to by the teacher.Explanation: The passive voice is formed by using the past participle of the verb after “be” followed by the subject. In this case, “given” is the past participle of “give.” The correct construction uses “given to by” to indicate that the students are the recipients of the action.15.The teacher is discussing the importance of reading aloud with the students. Which of the following statements is the most appropriate to use in this context?A)“Reading silently is better because it helps you concentrate better.”B)“Reading aloud is unnecessary; it only slows down the reading process.”C)“Reading aloud is beneficial because it enhances comprehension and pronunciation.”D)“We should only read aloud in class when we have time.”Answer: CExplanation: The correct answer is C because it highlights the positive aspects of reading aloud, such as improving comprehension and pronunciation. The other options either dismiss the importance of reading aloud or suggest it is unnecessary, which are not appropriate responses in the context of discussing its benefits.16.In a lesson on Shakespeare’s “Romeo and Juliet,” the teacher wants to engage students in a debate about the theme of fate versus free will. Which activity would best facilitate this discussion?A)Assigning students to write a short essay on the theme.B)Organizing a group discussion with prepared questions.C)Playing a scene from the movie adaptation of the play.D)Giving students a multiple-choice quiz about the characters.Answer: BExplanation: The correct answer is B because it encourages active participation and discussion among the students, which is ideal for exploring complex themes like fate versus free will. The other options either focus on individual writing or passive consumption, which may not foster the kind of interactive and critical thinking required for this type of discussion.17.The sentence “She is as tall as her father” is an example of which sentence structure?A. ComparisonB. ConditionalC. FutureD. PastAnswer: AExplanation: The sentence “She is as tall as her father” is using the comparison structure to show that two things (her height and her father’s height) are equal.18.Which of the following sentence is correct in terms of verb tense and subject-verb agreement?A. The dog run in the park every morning.B. The dogs are runs in the park every morning.C. The dog runs in the park every morning.D. The dogs is runs in the park every morning.Answer: CExplanation: The correct sentence is “The dog runs in the park every morning.” It uses the present simple tense correctly with the subject “dog,” which is singular, and agrees with the singular verb “runs.” The other options have incorrect verb tenses or subject-verb agreement errors.19.The teacher is using a teaching strategy to encourage student participation. Which of the following is the most appropriate strategy for discussing a complex historical event?A)Presenting a detailed timeline of the event.B)Asking students to write a brief summary of the event.C)Pairing students to debate the causes and effects of the event.D)Showing a documentary about the event.Answer: C) Pairing students to debate the causes and effects of the event.Explanation: Pairing students to debate a complex historical event encourages critical thinking and collaborative learning. It allows students to engage with the material from different perspectives, fostering a deeper understanding of the event.20.In the context of English language teaching, which of the following activities is most effective for improving students’ listening skills?A)Reading aloud a passage of text and asking students to retell it.B)Listening to a short story and then summarizing the main points.C)Watching a video clip and discussing the characters’ motivations.D)Listening to a dialogue and then analyzing the pronunciation of the speakers.Answer: B) Listening to a short story and then summarizing the main points.Explanation: Listening to a short story and summarizing the main points helps students practice active listening skills, identify key information, and improve their ability to process and recall spoken language. It also encourages them to engage with the content on a deeper level.21.The sentence “He has lived here for ten years, but he doesn’t feel at home yet.” demonstrates which of the following sentence structures?A)SimpleB)ComplexC)CompoundD)Complex-complexAnswer: B) ComplexExplanation: This sentence is a complex sentence because it has one mainclause (“He doesn’t feel at home yet”) and one or more dependent clauses that provide additional information. The dependent clause “He has lived here for ten years” adds extra informa tion about the main clause.22.Which of the following phrases is an example of a gerund phrase?A)To eating ice creamB)Eating ice creamC)Eat ice creamD)Eating ice-creamAnswer: B) Eating ice creamExplanation: A gerund phrase is a phrase that functions as a noun and consists of a gerund (a verb form that ends in -ing and functions as a noun). In this case, “Eating ice cream” is a gerund phrase that can act as a subject, object, or complement in a sentence. The other options do not fit the definition of a gerund phrase.23.What is the main purpose of using cooperative learning in the English classroom?A)To ensure that all students have the same level of English proficiency.B)To encourage students to work independently and develop their own learningstrategies.C)To promote interaction and collaboration among students.D)To test students’ ability to work under time pressure.Answer: CExplanation: The main purpose of using cooperative learning in the English classroom is topromote interaction and collaboration among students. This approach helps students develop their communication skills, critical thinking, and teamwork abilities.24.Which of the following activities is most suitable for assessing students’ understanding of a literary text in an English class?A) A written test that covers all the details of the text.B) A group discussion where students present their own interpretations of the text.C)An individual project that requires students to create a visual representation of thetext.D) A multiple-choice quiz that tests students’ recall of the main events.Answer: BExplanation: A group discussion where students present their own interpretations of the textis the most suitable activity for assessing students’ understanding of a literary text. This method encourages critical thinking, creativity, and the ability to articulate thoughts and ideas. It also promotes peer learning and collaboration.25.The following sentence is a direct quote. Which one of the following punctuation marks is correctly used at the end of the quote?A)Period (.)B)Question mark (?)C)Exclamation mark (!)D)Semicolon (;)Answer: A) Period (.)Explanation: When a direct quote is used within a sentence, it is always followed by a period. The period signifies the end of the quote.26.In the following sentence, “They had been working on the project for months, and it was finally completed,” the comma after “months” is used to:A)Separate a list of itemsB)Introduce a non-restrictive relative clauseC)Indicate a pause in the sentenceD)Separate independent clausesAnswer: B) Introduce a non-restrictive relative clause.Explanation: The comma after “months” i s used to introduce anon-restrictive relative clause, which provides additional information about the subject but is not essential to the main idea of the sentence. The clause “and it was finally completed” adds detail to the time frame of the project.27.The following sentence contains an error in verb tense usage. Which one is it?A. The students will be working on their projects until the end of the month.B. The students worked on their projects last week.C. The students are working on their projects at the moment.D. The students will have worked on their projects by the end of the month.Answer: BExplanation: The sentence that contains an error in verb tense usage is B. The correct tense should be present continuous for the ongoing action, but “worked” is in the past simple tense, which does not fit with the present continuous tense of “are working” in the other parts of the sentence.28.Choose the word that best fits the blank in the following sentence:The teacher_______to the students that the exam would be postponed due to bad weather.A. mentionedB. suggestedC. notifiedD. impliedAnswer: CExplanation: The correct word to fill in the blank is “notified.” The teacher is informing the students of an important change, which is best described by “notified,” meaning to inform formally. “Mentioned” could also be correct, but “notified” is more formal and appropriate for official announcements. “Suggested” and “implied” do not fit the context of formally informing students of a change.29、Which of the following is NOT a component of communicative language teaching (CLT)?A) Focus on accuracyB) Emphasis on using the language for real communicationC) Grammar translation as the main activityD) Task-based learning activitiesAnswer: C) Grammar translation as the main activityExplanation: Communicative Language Teaching (CLT) emphasizes the use of language for real communication and often incorporates task-based learningactivities. While focus on accuracy is also important, CLT moves away from the traditional grammar-translation method, which focuses more on the analysis and translation of written texts rather than the ability to communicate effectively in the target language.30、In the context of second language acquisition, what does the term “comprehensible input” refer to?A) Input that is slightly above the learner’s current level of competenceB) Input that is slightly below the learner’s current level of competenceC) Input that matches exactly the learner’s current level of competenceD) Any form of input regardless of the learner’s level of competenceAnswer: A) Input that is slightly above the learner’s current level of competenceExplanation: The concept of “comprehensible input,” developed by Stephen Krashen, suggests that learners acquire language best when they receive input that is just beyond their current linguistic capabilities, known as i+1, where “i” represents the learner’s current language level and “+1” is the next level of language complexity. This type of input challenges learners without overwhelming them, facilitating language acquisition effectively.二、简答题(20分)Question:In your opinion, what are the key factors that contribute to successful language learning inhigh school students? Explain how you would incorporate these factors into your teaching practice.Answer:The key factors that contribute to successful language learning in high school students include:1.Motivation: Motivation plays a crucial role in language learning. High school students need to be intrinsically motivated to learn the language, as well as extrinsically motivated by the goals and expectations set by their teachers and parents. As a teacher, I would create a positive learning environment by using engaging materials, encouraging students to set personal goals, and recognizing their achievements.2.Interaction: Interaction among students and with the teacher is essential for language learning. By incorporating activities such as group discussions, role-playing, and pair work, I would encourage students to communicate in English and practice their speaking and listening skills.3.Authentic materials: Using authentic materials such as newspapers, films, and songs can help students connect the language they learn in the classroom to real-life situations. I would integrate these materials into my lessons to provide students with practical language use.4.Effective assessment: Regular and varied assessment methods can help students monitor their progress and identify areas for improvement. As a teacher, I would use formative and summative assessments to track student performance and adapt my teaching strategies accordingly.5.Collaborative learning: Encouraging students to collaborate and worktogether can enhance their language skills and foster a sense of community in the classroom. I would incorporate group projects, peer tutoring, and cooperative learning activities to promote collaboration among students.6.Individual differences: Recognizing and addressing individual differences among students is crucial for successful language learning. I would differentiate my instruction by using varied teaching methods, providing additional support for struggling students, and challenging advanced learners.Incorporating these factors into my teaching practice would involve: •Creating a motivating and supportive learning environment•Incorporating interactive and collaborative activities•Utilizing authentic materials•Employing various assessment methods•Differentiating instruction to meet individual student needs•Continuously reflecting on and improving my teaching strategiesBy focusing on these key factors, I believe that high school students can achieve successful language learning and develop their English language skills.三、教学情境分析题(30分)III.Teaching Situation Analysis (30 points)Question 1:You are a high school English teacher preparing to teach a unit on American literature. Your students come from diverse backgrounds and have varying levelsof English proficiency. You notice that some students are particularly interested in contemporary issues, while others prefer classic literature. Considering these factors, design a lesson plan for a 45-minute class session that incorporates both traditional and modern elements of American literature. The lesson should aim to engage all students and foster critical thinking about the relevance of literature today. Include:•Objectives•Materials needed•Activities and procedures•Assessment methodsAnswer:Lesson Plan: Bridging Past and Present Through American LiteratureObjectives:1.Students will explore themes common to both classical and contemporary American literature.2.Students will analyze how different literary works reflect societal changes over time.3.Students will engage in a group discussion to compare and contrast two texts: one classical and one contemporary.Materials Needed:1.Excerpts from “The Great Gatsby” by F. Scott Fitzgerald (classical text).2.A short story or poem from a contemporary author such as “Interpreter of Maladies” by Jhumpa Lahiri.3.Handouts with guiding questions for each text.4.Access to online resources for additional research if available.Activities and Procedures:1.Introduction (5 minutes): Briefly introduce the authors and provide historical context for their works.2.Reading and Individual Analysis (20 minutes): Distribute the excerpts and handouts. Instruct students to read the texts silently and answer the guiding questions individually.3.Group Discussion (15 minutes): Organize students into small groups to share their insights and discuss the similarities and differences between the texts. Encourage them to consider how each work reflects its respective era.4.Whole-Class Sharing (5 minutes): Invite each group to present key points from their discussion to the class.Assessment Methods:1.Participation in group discussions will be observed and noted.2.Students’ written response s to the guiding questions will be collected and evaluated for comprehension and critical analysis.3.Group presentations will be assessed based on clarity, engagement, and depth of analysis.Analysis:This lesson plan addresses the diverse interests and English proficiency levels of the students by combining classical and contemporary literature. It allows for differentiated instruction, as students can choose which text theyfeel more comfortable with initially, yet still exposes them to both. The guiding questions facilitate deeper understanding and encourage students to make connections between the texts and the world around them, thereby enhancing their critical thinking skills. The combination of individual work, group discussion, and whole-class sharing ensures multiple opportunities for engagement and learning, catering to different learning styles and preferences within the classroom.四、教学设计题(40分)Question:Design a 45-minute lesson plan for an Advanced High School English class on the topic of “Global Warming and Its Impact on the Environment”. The lesson should include activities that encourage critical thinking, group discussion, and a creative project. Students are expected to be able to identify the causes of global warming, discuss its effects, and propose potential solutions.Answer:Lesson Title: “The Perils of Climate Change: Causes, Effects, and Solutions”Objective:By the end of this lesson, students will be able to:1.Identify the main causes of global warming.2.Discuss the effects of global warming on the environment.3.Propose potential solutions to mitigate the impact of global warming.Materials:1.Projector and screen2.Handouts with facts about global warming3.Whiteboard and markers4.Chart paper5.Pencils and colored markersLesson Outline:I. Introduction (10 minutes)1.Begin with a short video clip on global warming to spark students’ interest.2.Ask students to write down three things they learned from the video.3.Facilitate a class discussion on what global warming is and its importance.II.Group Work - Causes of Global Warming (15 minutes)1.Divide the class into small groups of four.2.Distribute handouts with facts about the causes of global warming.3.Instruct each group to identify at least three causes and explain their impact.4.Each group will create a poster highlighting their findings.5.Allow groups to present their posters to the class.III.Class Discussion - Effects of Global Warming (15 minutes)1.Discuss the effects of global warming on the environment, such as rising sea levels, extreme weather events, and loss of biodiversity.2.Facilitate a class discussion, encouraging students to share their opinions and experiences.3.Summarize the key points on the whiteboard.IV.Creative Project - Potential Solutions (5 minutes)1.Instruct students to work in pairs to brainstorm potential solutions to mitigate the impact of global warming.2.Give each pair 5 minutes to present their ideas to the class.V. Conclusion (5 minutes)1.Summarize the main points discussed in the lesson.2.Encourage students to continue exploring the topic outside the classroom.Explanation:The lesson plan is designed to engage students in an interactive and thought-provoking way. By using a combination of videos, group work, and class discussions, students will be able to gain a deeper understanding of the causes, effects, and potential solutions to global warming. The creative project allows students to apply their knowledge and come up with innovative ideas to tackle this pressing issue.。
pe monitor英语作文

pe monitor英语作文英文回答:Physical education is an essential component of a well-rounded education, providing numerous benefits forstudents' physical, cognitive, and social development. Incorporating physical activity into the school day notonly enhances students' overall health and well-being but also contributes to improved academic performance, behavior, and social skills.Cognitive Benefits:Regular physical activity has been shown to improve cognitive function, including memory, attention, andproblem-solving skills. Exercise increases blood flow tothe brain, which provides oxygen and nutrients essentialfor optimal brain function. Studies have demonstrated that students who engage in physical activity before or during school perform better on standardized tests and haveimproved academic achievement.Physical Benefits:Physical education classes provide a structured environment for students to engage in physical activities that promote cardiovascular health, muscle strength, flexibility, and coordination. Exercise helps reduce therisk of chronic diseases such as heart disease, stroke, obesity, and type 2 diabetes. It also improves bone density, posture, and balance, contributing to overall physical fitness.Social Benefits:Physical education fosters teamwork, cooperation, and communication skills. Team sports encourage students towork together towards a common goal, while individual activities promote self-confidence and self-discipline. Through physical activity, students learn to interact with peers from diverse backgrounds, build friendships, and develop a sense of belonging.Behavioral Benefits:Physical activity has been linked to improved behavior in children and adolescents. Exercise releases endorphins, which have mood-boosting effects. It also helps reduce stress, improve sleep quality, and enhance self-esteem. Studies have shown that students who participate in regular physical activity have fewer behavioral problems, better classroom attendance, and improved focus and concentration.Recommendations:To maximize the benefits of physical education, schools should incorporate at least 150 minutes of moderate-intensity physical activity per week into the curriculumfor all students. This can be achieved through physical education classes, recess, intramural sports, and after-school programs. Schools should also provide adequate facilities and equipment to support physical activity, such as gymnasiums, playgrounds, and walking trails.中文回答:体育教育是全方位教育的重要组成部分,对学生的生理、认知和社交发展都有着诸多好处。
《环境保护英语》课件

Environmental Protection is crucial for safeguarding the health of ecosystems, maintaining biodiversity, and ensuring sustainable development It also plays a vital role in addressing the impact of human activities on the environment and mitigating the negative sequences of climate change
Strengthening noise management, optimizing urban planning, promoting low-noise equipment, etc. are effective measures to control noise pollution.
Ecological protection and sustainable development
PPT courseware for Environmental Protection Englis
2023-2026
ONE
KEEP VIEW
REPORTING
目录
CATALOGUE
Overview of Environmental ProtectionEnvironmental pollution and controlEcological protection and sustainable developmentEnvironmental laws, regulations, and policiesPublic participation and environmental education
tpo54三篇阅读原文译文题目答案译文背景知识

托福阅读tpo54全套解析阅读-1 (2)原文 (2)译文 (4)题目 (5)答案 (9)背景知识 (10)阅读-2 (10)原文 (10)译文 (12)题目 (13)答案 (18)背景知识 (20)阅读-3 (25)原文 (26)译文 (27)题目 (28)答案 (33)背景知识 (35)阅读-1原文The Commercialization of Lumber①In nineteenth-century America, practically everything that was built involved wood.Pine was especially attractive for building purposes.It is durable and strong, yet soft enough to be easily worked with even the simplest of hand tools.It also floats nicely on water, which allowed it to be transported to distant markets across the nation.The central and northern reaches of the Great Lakes states—Michigan, Wisconsin, and Minnesota—all contained extensive pine forests as well as many large rivers for floating logs into the Great Lakes, from where they were transported nationwide.②By 1860, the settlement of the American West along with timber shortages in the East converged with ever-widening impact on the pine forests of the Great Lakes states. Over the next 30 years, lumbering became a full-fledged enterprise in Michigan, Wisconsin, and Minnesota. Newly formed lumbering corporations bought up huge tracts of pineland and set about systematically cutting the trees. Both the colonists and the later industrialists saw timber as a commodity, but the latter group adopted a far more thorough and calculating approach to removing trees. In this sense, what happened between 1860 and 1890 represented a significant break with the past. No longer were farmers in search of extra income the main source for shingles, firewood, and other wood products. By the 1870s, farmers and city dwellers alike purchased forest products from large manufacturingcompanies located in the Great Lakes states rather than chopping wood themselves or buying it locally.③The commercialization of lumbering was in part the product of technological change. The early, thick saw blades tended to waste a large quantity of wood, with perhaps as much as a third of the log left behind on the floor as sawdust or scrap. In the 1870s, however, the British-invented band saw, with its thinner blade, became standard issue in the Great Lakes states' lumber factories.Meanwhile, the rise of steam-powered mills streamlined production by allowing for the more efficient, centralized, and continuous cutting of lumber. Steam helped to automate a variety of tasks, from cutting to the carrying away of waste. Mills also employed steam to heat log ponds, preventing them from freezing and making possible year-round lumber production.④For industrial lumbering to succeed, a way had to be found to neutralize the effects of the seasons on production. Traditionally, cutting took place in the winter, when snow and ice made it easier to drag logs on sleds or sleighs to the banks of streams. Once the streams and lakes thawed, workers rafted the logs to mills, where they were cut into lumber in the summer. If nature did not cooperate—if the winter proved dry and warm, if the spring thaw was delayed—production would suffer. To counter the effects of climate on lumber production, loggers experimented with a variety of techniques for transporting trees out of the woods. In the 1870s, loggers in the Great Lakes states began sprinkling water on sleigh roads, giving them an artificial ice coating to facilitate travel. The ice reduced the friction and allowed workers to move larger and heavier loads.⑤But all the sprinkling in the world would not save a logger from the threat of a warm winter. Without snow the sleigh roads turned to mud. In the 1870s, a set of snowless winters left lumber companies to ponder ways of liberating themselves from the seasons. Railroads were one possibility.At first, the remoteness of the pine forests discouraged common carriers from laying track.But increasing lumber prices in the late 1870s combined with periodic warm, dry winters compelled loggers to turn to iron rails. By 1887, 89 logging railroads crisscrossed Michigan, transforming logging from a winter activity into a year-round one.⑥Once the logs arrived at a river, the trip downstream to a mill could be a long and tortuous one.Logjams (buildups of logs that prevent logs from moving downstream) were common—at times stretching for 10 miles—and became even more frequent as pressure on the northern Midwest pinelands increased in the 1860s. To help keep the logs moving efficiently, barriers called booms (essentially a chain of floating logs) were constructed to control the direction of the timber. By the 1870s, lumber companies existed in all the major logging areas of the northern Midwest.译文木材的商业化①在19世纪的美国,几乎所有建筑材料都含有木材。
九年级英语上册(外研版)教学课件-M8U

Teaching Courseware for Grade 9 English
Volume 1 (Foreign
目录
• introduction • Vocabulary learning • Grammar knowledge • Listening training • Oral expression • reading comprehension • Writing improvement
Reading comprehension
Students will use their vocabulary knowledge to improve their reading comprehension, understanding the meaning of texts more deeply.
Common modal verbs
can, could, may, might, must, shall, should, will, would.
Uses
to express different degrees of certainty or possibility about something; to make requests, offers, or suggestions; to express obligation or necessity.
Sophos for Virtual Environments配置指南说明书

ContentsAbout this guide (1)Configure policies (2)Create or edit a policy (2)Policy settings (2)Check that guest VMs are protected (5)Check the protection settings (5)Test real-time scanning (5)Troubleshoot real-time scanning (6)View guest VMs (7)View connected guest VMs (7)View protected guest VMs (7)Scan guest VMs (8)What happens when a threat is detected (9)Clean up a threat (10)Uninstall the Security VM (11)Uninstall the Guest VM Agent (12)Appendix: Add Security VMs for guest VM migration (13)Appendix: Add CPUs to the Security VM (14)Support (15)Legal notices (16)Sophos for Virtual Environments1 About this guideThis guide tells you how to configure Sophos for Virtual Environments.The guide assumes that you use Sophos Central to manage your security software.If you use Sophos Enterprise Console, see the configuration guide for Sophos Enterprise Console users.Sophos for Virtual Environments2 Configure policiesYou configure Sophos for Virtual Environments by using Sophos Central policies.You can only use the Threat Protection policy type, but you can create multiple policies if you want to.By default, Sophos Central applies a base Threat Protection policy to all your Security VMs. The settings in the policy are then used for the guest VMs.These settings offer:•Detection of known malware.•In-the-cloud checks to enable detection of the latest malware known to Sophos.•Proactive detection of malware that has not been seen before.•Automatic cleanup of malware.Related tasksCreate or edit a policy (page 2)You configure Sophos for Virtual Environments by using Sophos Central policies.Related referencePolicy settings (page 2)The options that you can use for Security VMs2.1 Create or edit a policyYou configure Sophos for Virtual Environments by using Sophos Central policies.You can only use the Threat Protection policy type, but you can create multiple policies if you want to.To create or edit a Threat Protection policy:1.Open Sophos Central and go to Server Protection > Policies.2.Click on a Threat Protection policy or click Add Policy to create a new one.3.On the Servers tab, select the Security VMs you want to apply the policy to.4.On the Settings tab, enter the settings you want.2.2 Policy settingsThe options that you can use for Security VMsLive ProtectionLive Protection checks suspicious files against the latest malware information in the SophosLabs database.Sophos for Virtual EnvironmentsSophos for Virtual EnvironmentsSophos for Virtual Environments3 Check that guest VMs are protectedThis section tells you how to check that your guest VMs are protected. You can:•Check the protection settings on a guest VM.•Test real-time scanning on a guest VM.•Troubleshoot real-time scanning.3.1 Check the protection settingsYou can check that Windows client guest VMs are protected. This does not apply to Windows Server guest VMs.1.Go to the guest VM and search for Security and Maintenance from the start menu. If this option isnot found search for Action Center.AttentionIf neither of these options are found then the guest VM doesn't provide Windows SecurityCenter. You must check whether the guest VM is protected using the steps described in Testreal-time scanning (page 5).2.Click the drop-down arrow beside Security. You should see that Sophos for Virtual Environmentsis on.NoteIf it is not on, see Troubleshoot real-time scanning (page 6).3.2 Test real-time scanningCheck that real-time scanning works on a Security VM.Real-time scanning is your main method of protection against threats. When you open, write, move,or rename a file the Security VM scans the file and grants access to it only if it does not pose a threat. When you run a program the Security VM scans the executable file and any other files it loads.ImportantEnsure that Sophos Endpoint for Windows is not installed on any guest VMs that are protectedwith a Security VM.To check that a Security VM is scanning files on access:1.Go to /86-0-Intended-use.html and use the test EICAR file.2.Copy the EICAR test string to a new file. Give the file a name with a .com extension and save it toone of the guest VMs.3.Try to access the file from the guest VM.Sophos for Virtual Environments4.Sign in to Sophos Central.•If you have automatic cleanup on, go to the Servers page and click the Security VM to open its details page. On its Events tab, you should see that EICAR has been detected and cleaned up.•If you don't have automatic cleanup on, look at the Alerts page. You should see an alert on the Security VM. EICAR has been detected but not cleaned up.If EICAR has not been detected, see Troubleshoot real-time scanning (page 6). If EICAR is notcleaned up, simply delete it.3.3 Troubleshoot real-time scanningIf real-time scanning is not working:1.Ensure that real-time scanning is enabled in the server policy applied to the Security VM:a)In Sophos Central, go the Servers page, find the Security VM and click on it to display itsdetails.b)In the Summary tab, under Summary, you can see the Threat Protection Policy applied to theserver. Click the policy name.c)In the policy, find the Real-time scanning section. Ensure that Scan is enabled.d)Check that the Security VM is compliant with the policy.2.Ensure that the guest VM is protected. Go to the Security VM host and look in the log file. Fordetails, see View protected guest VMs (page 7).3.Ensure that Windows Security Center shows the guest VM as protected by Sophos for VirtualEnvironments.4.Check that there are no pending restarts requested by Microsoft updates. These can preventinstallation of the Sophos Guest VM Agent from being completed.5.Check that aren't any other anti-virus products installed. On server platforms where the securitycenter is not present check that Windows Defender isn't active. Remember that you cannot useSophos for Virtual Environments to protect guest VMs that run other anti-virus products.6.If on-access scanning is still not working, contact Sophos Technical Support.Sophos for Virtual Environments4 View guest VMsYou can view details of all the guest VMs as follows:•View connected guest VMs (page 7). You can do this in Sophos Central.•View protected guest VMs (page 7)."Connected" guest VMs have the Sophos agent installed and can connect to the Security VM. Usually, a connected guest VM is also protected. However, if the agent is newly installed, or there isa problem, scanning for threats may not have started yet.4.1 View connected guest VMsYou can view all the guest VMs that are connected to a Security VM as follows.1.Sign in to Sophos Central.2.Go to Server Protection > Servers.3.Find the Security VM in the list and click on it to view its details.4.On the Summary tab, under Virtual Environments Status, find Connected Guest VMs. Click onthe number shown.NoteIf no guest VMs are powered on, or if you’re still installing agents on them, you may see zeroguest VMs.5.You see a list of VM names and IP addresses.You can search the list for a particular guest VM, or use the filter to display desktop or serverguest VMs.4.2 View protected guest VMsYou can view all guest VMs that are protected by a Security VM.1.Browse to the Security VM. You must use Windows Explorer and you must use the IP address.2.Double-click the Logs share.3.When prompted, enter your credentials.•Username is "sophos".•Password is the access password you set when you installed the Security VM.4.Open ProtectedGVMs.log to view the protected guest VMs.NoteThe ProtectedGVMs.log file only appears when the Security VM starts protecting guestVMs.Sophos for Virtual Environments5 Scan guest VMsThe Security VM always scans files on access, that is, when they are opened and closed.The Security VM can also perform a full scan of all guest VMs. You can either run a scanimmediately or at set times.The full system scan detects but doesn't clean up threats.NoteThe Security VM staggers scans so that the host is not placed under a high load. By default, twoguest VMs are scanned at a time. Therefore, it may take longer for the scanning of all guest VMs managed by the Security VM to complete.•To run a full scan of all the guest VMs immediately:a)Sign in to Sophos Central.b)Go to the Servers page.c)Find the Sophos Security VM and click on it to open its details page.d)In the left pane, click Scan Now.•To run a full scan of all the guest VMs at set times:a)Sign in to Sophos Central.b)Go to the Servers page.c)Find the Sophos Security VM and click on it to view its details page.d)On the Summary tab, look under Summary for the Threat Protection policy that applies. Clickon it to edit it.e)In the policy, go to the Scheduled scanning section. Enable scanning and specify the timeswhen the scan will be run.6 What happens when a threat is detected If the Security VM detects a threat on one of the guest VMs, it does as follows:•Blocks the threat.•Attempts to clean up the threat automatically.•Sends an alert to Sophos Central if you need to take any action.NoteThe Security VM does not automatically clean up threats detected during a full scan of all guest VMs.What you see in Sophos CentralSophos Central:•Shows that the threat has been blocked. See the Events tab of the details page for the Security VM.•Displays an alert in the Alerts page. This shows what the threat is, which VM it is on, and whether it is cleanable.•Removes the alert if automatic cleanup is successful.If automatic cleanup is not available or is not successful, an alert in the Alerts page prompts you to clean up manually.For more information on cleanup, see Clean up a threat (page 10).What the user sees on the guest VMIf the Security VM detects a threat when a user tries to access a file, it blocks access to that file from the Guest VM. If the application used to access the file can do so, it notifies the user that the file isno longer accessible.7 Clean up a threatThis section describes both automatic and manual cleanup of threats.For information about a threat and advice on cleanup, log in to Sophos Central, go to the Alerts page, look for the threat alert, and click on the threat name.Automatic cleanupThe Security VM automatically cleans up threats it detects.NoteAutomatic cleanup is not available on CDs, read-only file systems and media or on remote file systems.Manual cleanupYou can clean up a guest VM manually.To clean up manually, you restore the guest VM. Note that you may lose data (see details below). Use one of these methods:•Delete the guest VM and reclone it from the template image. You will lose your data.•Revert the guest VM to the previous known clean snapshot. You will lose data added since the taking the snapshot.Whichever method you use, run a full scan of the guest VM afterwards to ensure that it is clean.8 Uninstall the Security VMBefore you start, ensure that guest VMs will continue to be protected. Go to the Security VM and View protected guest VMs (page 7). Then move guest VMs to another Security VM with similar policy settings.To uninstall a Security VM, you delete it.To move your guest VMs:1.Uninstall the Guest VM Agent, see Uninstall the Guest VM Agent.2.Reinstall the Guest VM Agent with the new Security VM IP address.Once you have moved your guest VMs you can delete the Security VM. To do this:3.Go to your hypervisor.4.Power down the Security VM.5.Delete the VM.9 Uninstall the Guest VM Agent You can uninstall the Guest VM Agent from Control Panel.1.On the guest VM, open Control Panel.2.Click Programs and Features.3.Select these features and click Uninstall:•Sophos for Virtual Environments•Sophos Guest VM Scanning Service•Sophos Virus Removal Tool.10 Appendix: Add Security VMs for guest VM migrationAt any time you can add more Security VMs that will be available to protect migrating guest VMs.If you are planning to create more Sophos Security VMs in the future you should reserve IP addresses for the Sophos Security VMs you are likely to add. To do this create a prepopulatedmaster version of this file. This file should contain all the IP addresses of Sophos Security VMs you have, and will have in the future. You can then copy this file to each Sophos Security VM as it is created.ImportantYou need to perform these steps on the Security VM that you want to add and on the existing Security VMs.1.Open a console to the Security VM.2.Log on:Username is "sophos".Password is the access password you set when you installed the Security VM.3.Open the additional_svms.txt configuration file for editing, by running the following command: sudovi /opt/sophos-svms/etc/additional_svms.txt4.Edit the file to add or remove IP addresses of Security VMs that are available to protect migratingguest VMs, with one IP address per line and no additional separating characters.a)Press i to open edit mode in vi.b)Put one IP address per line with no additional separating characters. For example:1.2.3.45.6.7.8c)You don't need to include the IP address for the Security VM you're currently logged in to.d)Press Esc to get out of edit mode in vi.e)Save and close the file by entering :wq.5.Check the SVM log (/var/log/ssvm.log) to see if there were any errors in processing theadditional Security VMs list.If there are no errors, the updated list is sent to all connected guest VMs so that they can get protection from the new Security VMs.11 Appendix: Add CPUs to the Security VMIf you have many guest VMs on a host, you should ensure that the Security VM has enough processing power to scan the files they use when they all start up.To do this, add more CPUs for the Security VM. You can do this any time.Depending on the type of load, adding CPUs can also improve overall system performance. Add CPUs in VMware ESXiAdd CPUs as follows:1.Power off the Security VM.2.In vSphere Client, select the Security VM.3.Select Edit Settings > Hardware > CPUs. Then specify the number of CPUs.Add CPUs in Microsoft Hyper-VAdd CPUs as follows:1.Click Start, select Administrative Tools, and then click Hyper-V Manager.2.In the results pane, under Virtual Machines, select the Security VM.3.In the Action pane, under the VM name, click Settings.4.Click Processor and specify the number of processors.12 SupportYou can find technical support for Sophos products in any of these ways:•Visit the Sophos Community at / and search for other users who are experiencing the same problem.•Visit the Sophos support knowledge base at /en-us/support.aspx.•Download the product documentation at /en-us/support/documentation.aspx.•Open a ticket with our support team at https:///support/contact-support/ support-query.aspx.13 Legal noticesCopyright © 2020 Sophos Limited. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording or otherwise unless you are either a valid licensee where the documentation can be reproduced in accordance with the license terms or you otherwise have the prior permission in writing of the copyright owner.Sophos, Sophos Anti-Virus and SafeGuard are registered trademarks of Sophos Limited, Sophos Group and Utimaco Safeware AG, as applicable. All other product and company names mentioned are trademarks or registered trademarks of their respective owners.Third-party licensesFor third-party licenses that apply to your use of this product, please refer to the following folder on the Sophos Security VM: /usr/share/doc.Some software programs are licensed (or sublicensed) to the user under the GNU General Public License (GPL) or similar Free Software licenses which, among other rights, permit the user to copy, modify, and redistribute certain programs, or portions thereof, and have access to the source code. The GPL requires for any software licensed under the GPL, which is distributed to a user in an executable binary format, that the source code also be made available to those users. For anysuch software which is distributed along with this Sophos product, the source code is available by following the instructions in knowledge base article 124427.。
高级英语第一册lessen9ppt课件

The lesson also includes additional resources such as audio scripts and vocabulary lists to further support learners' listening development.
Requirements
Students are required to actively participate in class discussions, complete assigned readings and written assignments, and demonstrate their understanding of the lesson material through oral presentations or written exams.
01
Course Introduction and Background
Purpose of Advanced English Course
To improve students' proficiency in English language skills, including listening, speaking, reading, and writing.
Grammatical accuracy
The author demonstrates a high level of grammatical accuracy, with correct use of tenses, voice, mood, and punctuation.
Cohesive devices
2014年英语6级作文

2014年英语6级作文2014年英语六级作文题目,The Importance ofEnvironmental Protection。
参考范文:The Importance of Environmental Protection。
In recent years, the issue of environmental protection has become a hot topic in society. It is widely acknowledged that the environment is deteriorating at an alarming rate due to human activities. Therefore, it is crucial for us to take immediate action to protect our environment.First and foremost, environmental protection isessential for the survival of all living creatures on Earth. The air we breathe, the water we drink, and the food we eat all come from the environment. If the environment is polluted, it will have a negative impact on our health andwell-being. In addition, environmental protection is important for the preservation of biodiversity. Many species of plants and animals are facing extinction due to habitat destruction and pollution. If we do not take action to protect the environment, many species will disappear forever.Furthermore, environmental protection is crucial for the sustainability of our planet. The Earth has a limited amount of natural resources, such as water, forests, and minerals. If we continue to exploit these resources at the current rate, they will eventually run out. Therefore, itis important for us to use these resources wisely and to find alternative sources of energy and materials. In addition, environmental protection is important for the prevention of natural disasters. Deforestation and the emission of greenhouse gases are contributing to climate change, which is causing more frequent and severe natural disasters, such as hurricanes, floods, and droughts.In conclusion, environmental protection is of great importance for the survival of all living creatures onEarth, the preservation of biodiversity, the sustainability of our planet, and the prevention of natural disasters. Therefore, it is crucial for us to take immediate action to protect our environment. We can start by reducing our carbon footprint, conserving water and energy, recycling and reusing materials, and supporting environmentally friendly policies and practices. If we all work together, we can make a positive impact on the environment and ensure a sustainable future for generations to come.。
supervisor environment写法

supervisor environment写法Supervisor EnvironmentIn the position of a supervisor, creating a conducive and supportive environment is crucial for the smooth functioning of a team. A supervisor is responsible for setting the tone and atmosphere of the workplace, which directly influences the motivation, productivity, and satisfaction of the team members. Therefore, it is essential to pay attention to the supervisor environment and employ effective strategies to foster a positive and productive work atmosphere.One of the key aspects of a supervisor environment is effective communication. Maintaining open lines of communication between the supervisor and the team members allows for clear expectations, feedback, and guidance. Regular team meetings, one-on-one discussions, and providing opportunities for team members to express their opinions and concerns can contribute to a healthy and collaborative supervisor environment.Another important element is trust. To foster trust, a supervisor should be transparent, fair, and consistent in their actions and decisions. This involves acknowledging and valuing the contributions of each team member, treating them with respect, and being accountable for their own actions. Trust can enhance teamwork, promote autonomy, and create a positive supervisor environment where team members feel safe and valued.A supervisor environment should also encourage professional growth and development. Providing opportunities for training, mentoring, and continuous learning can help team membersenhance their skills and knowledge. A supervisor should recognize and support individual career aspirations, offer constructive feedback, and promote a supportive environment that fosters creativity, innovation, and growth.Furthermore, a supervisor environment should prioritize work-life balance. Supporting flexible work arrangements, encouraging breaks, and promoting a healthy work-life integration can help prevent burnout and improve overall well-being. A supervisor should be empathetic and understanding towards personal commitments and challenges faced by team members, promoting a compassionate and caring work environment.Lastly, a supervisor environment should be inclusive and diverse. Acknowledging and respecting individual differences, promoting equality, and fostering a sense of belonging can create a positive and enriched workplace. A supervisor should actively listen to diverse perspectives, address any incidents of discrimination or bias, and ensure an inclusive atmosphere for all team members. Overall, creating an effective supervisor environment requires a combination of communication, trust, professional growth, work-life balance, and inclusiveness. By prioritizing these aspects, a supervisor can support their team members in reaching their full potential, fostering a productive and harmonious work environment.。
Environmental Science

Environmental Science is a multidisciplinary field that focuses on understanding the interactions between the environment and human activities. It encompasses various disciplines such as biology, chemistry, physics, geology, and sociology to study the complex systems that make up our planet.One of the key areas of Environmental Science is studying the impact of human activities on the environment. Human activities, such as industrialization and urbanization, have resulted in various environmental issues. For example, the burning of fossil fuels for energy generation has led to air pollution and climate change. The excessive use of natural resources has caused deforestation and loss of biodiversity. These issues have far-reaching consequences for the health and well-being of both humans and the planet. Another important aspect of Environmental Science is the study of ecosystems and their functioning. Ecosystems are dynamic systems that consist of living organisms and their physical environment. Understanding how ecosystems work and how they are influenced by human activities is crucial for their conservation and sustainable use. Ecosystem services, such as clean air and water, nutrient cycling, and climate regulation, are vital for human survival and well-being. By studying ecosystems, scientists can develop strategies to preserve and restore them.Environmental Science also plays a crucial role in addressing environmental challenges and developing sustainable solutions. Scientists and researchers work together to develop innovative technologies and practices that minimize the negative impact on the environment. For instance, renewable energy sources like solar and wind power are being extensively studied and implemented to reduce reliance on fossil fuels. Waste management techniques, such as recycling and composting, are being promoted to reduce the amount of waste sent to landfills.Furthermore, Environmental Science involves studying the social and economic aspects of environmental issues. It recognizes that environmental problems are not just scientific or technical in nature but also have social and economic dimensions. Environmental justice, for example, focuses on the fair distribution of environmental benefits and burdens among different social groups. Sustainable development seeks to balance economic growth with environmental protection and social well-being.In conclusion, Environmental Science is a multidisciplinary field that encompasses various scientific disciplines to study the interactions between the environment and human activities. It addresses environmental issues, studies ecosystems, develops sustainable solutions, and considers social and economic aspects. By understanding the complexities of the environment, we can work towards a more sustainable future where humans and nature can coexist harmoniously.。
Cognitive Agents for Virtual Environments说明书

Lecture Notes in Artificial Intelligence7764 Subseries of Lecture Notes in Computer ScienceLNAI Series EditorsRandy GoebelUniversity of Alberta,Edmonton,CanadaYuzuru TanakaHokkaido University,Sapporo,JapanWolfgang WahlsterDFKI and Saarland University,Saarbrücken,GermanyLNAI Founding Series EditorJoerg SiekmannDFKI and Saarland University,Saarbrücken,GermanyFrank Dignum Cyril Brom Koen Hindriks Martin Beer Deborah Richards(Eds.) Cognitive Agentsfor Virtual EnvironmentsFirst International Workshop,CA VE2012 Held at AAMAS2012Valencia,Spain,June4,2012Revised Selected Papers13Series EditorsRandy Goebel,University of Alberta,Edmonton,CanadaJörg Siekmann,University of Saarland,Saarbrücken,GermanyWolfgang Wahlster,DFKI and University of Saarland,Saarbrücken,GermanyV olume EditorsFrank DignumUtrecht University,The NetherlandsE-mail:******************Cyril BromCharles University,Prague,Czech RepublicE-mail:*************.cuni.czKoen HindriksDelft University of Technology,The NetherlandsE-mail:***********************Martin BeerSheffield Hallam University,UKE-mail:*************.ukDeborah RichardsMacquarie University,Sydney,AustraliaE-mail:***********************.auISSN0302-9743e-ISSN1611-3349ISBN978-3-642-36443-3e-ISBN978-3-642-36444-0DOI10.1007/978-3-642-36444-0Springer Heidelberg Dordrecht London New YorkLibrary of Congress Control Number:2013930424CR Subject Classification(1998):I.2.11,K.8.0,K.3.1,I.2.0-1LNCS Sublibrary:SL7–Artificial Intelligence©Springer-Verlag Berlin Heidelberg2013This work is subject to copyright.All rights are reserved,whether the whole or part of the material is concerned,specifically the rights of translation,reprinting,re-use of illustrations,recitation,broadcasting, reproduction on microfilms or in any other way,and storage in data banks.Duplication of this publication or parts thereof is permitted only under the provisions of the German Copyright Law of September9,1965, in ist current version,and permission for use must always be obtained from Springer.Violations are liable to prosecution under the German Copyright Law.The use of general descriptive names,registered names,trademarks,etc.in this publication does not imply, even in the absence of a specific statement,that such names are exempt from the relevant protective laws and regulations and therefore free for general use.Typesetting:Camera-ready by author,data conversion by Scientific Publishing Services,Chennai,India Printed on acid-free paperSpringer is part of Springer Science+Business Media()PrefaceThere is a wide range of activity within the agent community considering various aspects of multi-agent systems,both theoretical as well as practical.This includes communication,team work,coordination,and cooperation of agents.In the First International Workshop on Cognitive Agents for Virtual Environments (CAVE-2012)we explored how these results might be used in the context of games and other virtual applications that require interaction with real users and perhaps identify any additional requirements that should be imposed for these contexts.We also explored similarities between solutions developed within the agent community with those used by people studying cognitive architectures.The workshop brought individuals working on virtual characters together with those working on agent platforms and languages and cognitive architectures. All three communities have important parts of solutions for creating agents for games and similar applications,but very little is currently being done to combine these solutions.Thus the workshop hoped to connect the different communities and show the benefits from this combination.Although some cross-fertilization took place there is still room for improvement.However,the proceedings give a good indication of the state of the art in this area.The workshop builds upon the AAMAS AGS2009/10,EduMAS2009,and AEGS2011workshops where the main issue has been to incorporate elements of agent technology in games and similar virtual environments such as3D training and educational applications to create moreflexible and realistic game play. Although some of the technical issues have been overcome and middleware(such as Pogamut,EIS,and CIGA)has been developed to connect agent platforms to games like Unreal Tournament,there are a number of fundamental challenges both on the technical as well as on the conceptual and design level.In these proceedings we include papers that address several of these chal-lenges and were presented at CAVE2012held on June4in Valencia,Spain, in colocation with AAMAS2012.We received14submissions of high quality covering many of the aspects mentioned above.Each submission was reviewed by at least three Program Committee members.We accepted10papers for pre-sentation,which can be found in this proceedings.Afterwards we invited several persons to submit additional contributions for this volume in order to make the overview complete.However,we only selected one high-quality contribution of these submissions(reflecting that quality is more important than completeness).We have grouped the papers into four sections.Thefirst section contains papers that are related to architectures combining agents and game engines.VI PrefaceThe paper of Tomas Plch,Tomas Jedlicka,and Cyril Brom discusses the use of HLA,a standard for coupling simulations,for coupling agents to game engines. HLA seems to provide a useful language to define(part of)such a coupling.The second paper by Jeehang Lee,Vincent Baines,and Julian Padget also looks at the more practical side of the coupling and discusses,for instance,performance issues related to tight and loose coupling.The last paper in this section from Joost van Oijen and Frank Dignum discusses the informationflow between agents and game engines that is necessary to generate realistic communication between virtual characters.In the second section we included papers that focus on using agents and virtual environments for training team work.It is an excellent area where the use of cognitive agents is imperative for good results,but also where many issues are still open.The paper of Martin Beer,Emma Norling,Peter Wallis and Lyuba Alboul discuss how agents and controllers can work together in order to get(unmanned)aircrafts to discover lost persons in mountainous areas as quickly and efficiently as possible.The second paper in this section is from Nader Hanna and Deborah Richards and looks at the very essential issue of two-way human–agent communication within the context of an educational game.One of the prime challenges is the combination of verbal and non-verbal communication in this context.The paper from Marie Manner and Maria Gini relates how agents can assist people to improve team performance.The third section contains papers that describe how cognitive agents can be used for simu-lation environments.Both visualization issues as well as issues of efficiency and scale play an important role in this area.The visualization issue is the focus of thefirst paper in this section,which is from Athanasia Louloudi and Franziska Kl¨u gl.The second paper,from Quentin Reynaud,Etienne de Sevin,Jean-Yves Donnart,and Vincent Corruble,breaches the topic of combining cognitive and reactive architectures for urban simulations.The last section groups some papers around performance issues of cognitive agents for virtual environments.The pa-per from Surangika Ranathunga and Stephen Cranefield discusses the problem of interpreting useful events from the low-level data that an agent receives from the game engine.Having an efficient translation of this low-level information is important for the cognitive agents being able to react to it on time.The second paper in this section is from Rudolf Kadlec,Michal Cermak,Zdenek Behan,and Cyril Brom and discusses issues in generating corpora of daily living memories for cognitive agents.These agents should have some history to be believable,but this history should of course also be manageable!The last paper in this section discusses the tools that should be used to define agents for games.This paper from Jakub Gemrot,Zdenek Hlavka,and Cyril Brom describes an experiment in which different agent behavior specification tools are compared and the authors check whether high-level specification of behavior leads to higher productivity. Read the paper to check the results!All in all we are very happy with the papers contained in this volume.We are sure they form a valuable overview of the current state of the art of cognitive,Preface VII intelligent characters in virtual environments.Finally,we would like to thank the Program Committee members and external reviewers without whom the reviewing would not have been possible and who gave valuable comments on all papers.December2012Frank DignumDeborah RichardsKoen HindriksMartin BeerCyril BromOrganizationProgram CommitteeRuth Aylett Heriot-Watt University,UKMartin Beer Sheffield Hallam University,UKCyril Brom Charles University,Czech RepublicAndr´e Campos UFRN,BrazilVincent Corruble LIP6,Universite Pierre et Marie Curie(Paris6),FranceYves Demazeau CNRS-Laboratoire LIG,UKFrank Dignum Utrecht University,The NetherlandsVirginia Dignum TU Delft,The NetherlandsHiromitsu Hattori Kyoto University,JapanKoen Hindriks Delft University of Technology,The Netherlands Stefan Kopp University of Bielefeld,GermanyMei Yii Lim Heriot-Watt University,UKSimon Lynch University of Teesside,UKHector Munoz-Avila Lehigh University,USAJeffOrkin MIT,USADavid Pynadath University of Southern California,USA Deborah Richards Macquarie University,AustraliaAvi Rosenfeld Jerusalem College of Technology(JCT),Israel Ilias Sakellariou University of Macedonia,GreeceDavid Sarne Bar-Ilan University,IsraelBarry Silverman University of Pennsylvania,USAPieter Spronck Tilburg University,The Netherlands Demosthenes Stamatis Alexander TEI of Thessaloniki,GreeceIoanna Stamatopoulou CITY College,International Faculty ofthe University of Sheffield,GreeceKatia Sycara Carnegie Mellon University,USADuane Szafron University of Alberta,USAJoost Van Oijen University of Utrecht,The NetherlandsAdditional ReviewersBuschmeier,HendrikShamoun,SimonVan Der Zwaan,JannekeTable of ContentsCoupling Agents and Game EnginesHLA Proxy:Towards Connecting Agents to Virtual Environments byMeans of High Level Architecture(HLA) (1)Tomas Plch,Tomas Jedliˇc ka,and Cyril BromDecoupling Cognitive Agents and Virtual Environments (17)Jeehang Lee,Vincent Baines,and Julian PadgetAgent Communication for Believable Human-Like Interactions betweenVirtual Characters (37)Joost van Oijen and Frank DignumUsing Games with Agents for EducationUsing Agents in Virtual Environments to Assist Controllers to Manage Multiple Assets (55)Martin D.Beer,Lyuba Alboul,Emma Norling,and Peter WallisA Collaborative Agent Architecture with Human-Agent Communication Model (70)Nader Hanna and Deborah RichardsImproving Agent Team Performance through Helper Agents (89)Marie D.Manner and Maria GiniVisualisation and SimulationVisualisation on Demand for Agent-Based Simulation (106)Athanasia Louloudi and Franziska Kl¨u glA Cognitive Module in a Decision-Making Architecture for Agents inUrban Simulations (120)Quentin Reynaud,Etienne de Sevin,Jean-Yves Donnart,andVincent CorrubleEvaluating Games with AgentsImproving Situation Awareness in Intelligent Virtual Agents (134)Surangika Ranathunga and Stephen CranefieldXII Table of ContentsGenerating Corpora of Activities of Daily Living and towardsMeasuring the Corpora’s Complexity (149)Rudolf Kadlec,MichalˇCerm´a k,Zdenˇe k Behan,and Cyril BromDoes High-Level Behavior Specification Tool Make Production ofVirtual Agent Behaviors Better? (167)Jakub Gemrot,Zdenˇe k Hl´a vka,and Cyril BromAuthor Index (185)。
阅读理解B篇 (解析+词汇+变式+技巧+模拟) -2024年浙江1月卷深度解析及变式训练 (原卷版)

《2024年浙江1月卷深度解析及变式训练》专题03 阅读理解B 篇 (解析+词汇+变式+技巧+模拟) 原卷版养成良好的答题习惯,是决定高考英语成败的决定性因素之一。
做题前,要认真阅读题目要求、题干和选项,并对答案内容作出合理预测;答题时,切忌跟着感觉走,最好按照题目序号来做,不会的或存在疑问的,要做好标记,要善于发现,找到题目的题眼所在,规范答题,书写工整;答题完毕时,要认真检查,查漏补缺,纠正错误。
When was the last time you used a telephone box? I mean to make an actual phone call —not to shelter from the rain. Ages ago, right? The last time I used a phone box for its intended purpose was ... 2006. I was conducting auditions (试演) for my play in my tiny old shared house in London. Hoping to impress some talented actors to come and work for me for nothing, I spread some throws over the sofas and lit candles to make it seem a bit more “young professional”.As I rushed outdoors to empty the wastepaper baskets, the door swung shut behind me. Suddenly I was locked outside. My mobile phone was inside, but luckily there was a telephone box across the street. So I called Directory Assistance, got put through to our landlady’s managing agent, and had a spare key sent to me with just enough time to get bad in before the actors arrived.As it has been many years since I last used one, I should hardly be surprised that there are no longer any public telephones near my house. The last one standing has just been turned into a “mini community library”: any passer-by can “borrow” a book from its shelves, and return it later, or replace it with another title from their own collection.For a few months after the “library” opened, I didn’t bother taking a look, as I had assumed that it would be stuffed full of cheesy love stories. Then I noticed folk conducting spring cleans dropping boxes of voluminous books on various subjects there. And these books were free. This unbeatable price-point encouraged me to experiment with dozens of titles that I would never normally consider buying. And I’ve discovered some great books!If I ever get trapped outside my house again, my local telephone box will, sadly, no longer be able to connect me with my keys. But it can certainly keep me entertained while I wait for my wife to rescue me.24. What does the word “it” underlined in the first paragraph refer to?A. The play.B. The shared house.C. The sofa.D. The telephone box.25. Why did the author use the telephone box in 2006?A. To place an urgent call.B. To put up a notice.C. To shelter from the rain.D. To hold an audition.26. What do we know about the “mini community library”?A. It provides phone service for free.B. Anyone can contribute to its collection.C. It is popular among young readers.D. Books must be returned within a month.27. Why did the author start to use the “library”?A. He wanted to borrow some love stories.B. He was encouraged by a close neighbour.C. He found there were excellent free books.D. He thought it was an ideal place for reading.1. actual a.2. shelter vt.3. conduct vt4. talented a.5. sofa n.6. candle n.7.light(lit, lit) vt8. professional a.9. swing(swung, swung) v.10. directory n.11. assistance n.12. agent n.13. spare a.14. passer-by n.15. collection n.16. title n.17. assume vt.18. stuff vt.19. cheesy a. 20. voluminous a.21. unbeatable a.22. price-point n.23. entertained a.24. urgent a.25. ideal a.26. the last time…27. make a phone call28. light candles29. replace A with B 用B)30. don’t bother doing31. experiment with32. dozens of33. wait for sb to do34. refer to35. put up a notice36. contribute to37. be popular among38. for free1. The last time I used a phone box for its ____________(intend) purpose was ... 2006.2. ____________(hope) to impress some ____________(talent) actors to come and work for me for nothing, I spread some throws over the sofas and ____________(light) candles…3. As I rushed outdoors____________(empty) the wastepaper baskets, the door ____________ (swing) shut behind me.4. My mobile phone was inside, but ____________(lucky) there was a telephone box across the street.5. So I called Directory Assistance, ____________(get) put through to our landlady’s managing agent, and had a spare key ____________(send) sent to me.6. As it has been many years ____________ I last used one, I should hardly ____________(surprise) that there are no longer any public telephones near my house.7. For a few months after the “library” opened, I didn’t bother taking a look, as I ____________ (assume) that it would be stuffed full of cheesy love stories.8. Then I noticed folk ____________(conduct) spring cleans dropping boxes of voluminous books on various ____________(subject) there.9. This price-point encouraged me ____________(experiment) with dozens of titles ___________I would never normally consider ____________(buy).10. If I ever get ____________(trap) outside my house again, my local telephone box will, sadly, no longer be able to connect me with my keys.11. But it can certainly keep me ____________(entertain) while I wait for my wife ____________ (rescue) me.Live with roommates? Have friends and family around you? Chances are that if you’re looking to live a more sustainable lifestyle, not everyone around you will be ready to jump on that bandwagon.I experienced this when I started switching to a zero waste lifestyle five years ago, as I was living with my parents, and I continue to experience this with my husband, as he is not completely zero waste like me. I’ve learned a few things along the way though, which I hope you’ll find encouraging if you’re doing your best to figure out how you can make the change in a not-always-supportive household.Zero waste was a radical lifestyle movement a few years back. I remember showing my parents a video of Bea Johnson, sharing how cool I thought it would be to buy groceries with jars, and have so little trash! A few days later, I came back with my first jars of zero waste groceries, and my dad commented on how silly it was for me to carry jars everywhere. It came off as a bitdiscouraging.Yet as the months of reducing waste continued, I did what I could that was within my own reach. I had my own bedroom, so I worked on removing things I didn’t need. Since I had my own toiletries (洗漱用品), I was able to start personalising my routine to be more sustainable. I also offered to cook every so often, so I portioned out a bit of the cupboard for my own zero waste groceries. Perhaps your household won’t entirely make the switch, but you may have some control over your own personal spaces to make the changes you desire.As you make your lifestyle changes, you may find yourself wanting to speak up for yourself if others comment on what you’re doing, which can turn itself into a who le household debate. If you have individuals who are not on board, your words probably won’t do much and can often leave you feeling more discouraged.So here is my advice: Lead by action.24. What do the underlined words “jump on that bandwagon” mean in the first paragraph?A. Share an apartment with you.B. Join you in what you’re doing.C. Transform your way of living.D. Help you to make the decision.25. What was the attitude of the author’s father toward buying groceries with jars?A. He disapproved of it.B. He was favorable to it.C. He was tolerant of it.D. He didn’t care about it.26. What can we infer about the author?A. She is quite good at cooking.B. She respects others’ privacy.C. She enjoys being a housewife.D. She is a determined person.27. What is the text mainly about?A. How to get on well with other family members.B. How to have one’s own personal space at home.C. How to live a zero waste lifestyle in a household.D. How to control the budget when buying groceries.阅读理解记叙文解题指导一、“人物传记”类记叙文解题策略人物传记是高中记叙文考试中常遇到的体裁形式。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
6.0 Building and Running ProgramsVPE programs can be built and run directly from the VPE environment. When the user picks one of the build options from the Build menu, VPE will generate C (or Fortran and C) code to implement the visually specified program. It will then begin a parallel and distributed compile of all files produced that will ensure that all modules are built for all necessary machines. Once the compiles terminate successfully, the user can begin a program execution from the VPE environment.7.0 AnimationVPE will have the ability to animate the execution of a VPE program. This animation will be per-formed directly on the users VPE programs. It will include highlighting arcs when messages are sent on them. In PVM environments, XPVM [Gei94] will be able to show other animated displays.8.0 References[Beg91] A. Beguelin, J. Dongarra, G. A. Geist, R. Manchek, and V. S. Sunderam, “Graphical development tools for network-based concurrent supercomputing,” Proceedings of Super-computing 91, pages 435--444, Albuquerque, 1991.[Beg93] A. Beguelin, J. Dongarra, G. A. Geist, and V. S. Sunderam, “Visualization and Debugging in a Heterogeneous Environment,” IEEE Computer, v. 26, no. 6, June, 1993.[Gei94] A. Geist, A. Beguelin, J. Dongarra, W. Jiang, R. Manchek, V. Sunderam,PVM: Parallel Virtual Machine: A User’s Guide and Tutorial for Networked Parallel Computing, MIT [MPI94]Message Passing Interface Forum, “MPI: A Message-Passing Interface Standard”, Journal of Supercomputing Applications, V ol. 8, No. 3/4, 1994.[New92]P. Newton and J.C. Browne,“The CODE 2.0 Graphical Parallel Programming Language,”Proc. ACM Int. Conf. on Supercomputing, July, 1992.[New93]P. Newton, “A Graphical Retargetable Parallel Programming Environment and Its Effi-cient Implementation”, Technical Report TR93-28, Dept. of Computer Sciences, Univ. ofTexas at Austin, 1993.[Ous94]J. Ousterhaut,Tcl and the Tk Toolkit, Addison-Wesley, Reading, MA,1994.In the former case, of course, one wonders why the programmer bothered to bind M to N in C1 since it has no effect, but the program is legal as written.5.0 Message-Passing PrimitivesThis section describes the communications primitives that can be called from within VPE computa-tions. Collective operations apply to all replications of a single node instance. Additonal routines may be added to VPE as needed.Buffer Management Routinesvpe_initsend(encoding);Clear send buffer.vpe_pkTYPE(address, NumItems, Stride);Pack values into message buffer.vpe_upkTYPE(adress, NumItems, Stride);Unpack values from buffer.Communication Routinesvpe_send(PORT_NAME, index, ...);Send current buffer.vpe_psend(PORT_NAME, index, ..., data, length, type);Pack and send data.vpe_recv(PORT_NAME, index, ...);Receive buffer.vpe_nrecv(PORT_NAME, index, ...);Non-blocking receive.vpe_probe(PORT_NAME, index, ...);Test for message arrival.vpe_precv(PORT_NAME, index, ..., buffer, buflen, type, actual_len);Receive and unpack data.vpe_mcast(PORT_NAME, index_range, ...);Send current buffer to multiple node instances.Collective Routinesvpe_scatter(data, sendcount, recvcount, type, root);Root node instance divides data among all instances.vpe_gather(data, sendcount, recvcount, type, root);Each node instance (including root) sends data to the root.ated, but they may assume that all parameters will given values from initialization computations before they can be used by a comp node, even in a replication expression.4.2 Call ExampleThis section presents a very simple example of one graph (main) calling another (addN) in which both interface nodes and parameters are bound. Both graphs are shown in Figure 9. Graph addN’s purpose is to receive a stream of messages from its input interface node X. Each message contains an integer. It then adds the value of its parameter N to the integer and sends it back to main via its output interface node Z.Figure 9. Simple Graph Call Example.Graph addN’s parameter N is bound to main’s parameter M. Thus, as long as addN’s initialization computation does not change the value of N, it will have the value given to M in main’s initialization computation.On the other hand, it is legal for the programmer to choose to alter N in addN’s initialization compu-tation. It could completely override the value of M viaN = 10; /* Give N a fixed value, regardless on M */or it could change N in a way that still makes use of M’s value.N = N + 1; /* N ends up with value M+1 */4.0 Graph CallingVPE supports hierarchical program development and the creation of libraries of graphs. One VPE graph can call another by means of a call node, but neither direct nor indirect recursion is allowed. Calls have “inlining” semantics-- programmers can think of call nodes as being replaced by the graph they call. It is possible for the same graph to be called from two or more different call nodes, but a separate instance of the graph will be called from each.4.1 Graph InterfacesThere are two aspects to a graph’s interface, interface nodes (input and output), and parameters. They serve very different purposes.Interface nodes are points through which messages enter and leave graphs. There will be a port on a call node that calls a given graph for every interface node in the graph. There is a one-to-one corre-spondence between ports on call nodes and interface nodes in the graphs they call. When a message enters (or leaves) a port on a call to goes to (or comes from) the corresponding interface node. Natu-rally, input interface nodes pair with input ports and output interface nodes pair with output ports.All interface nodes must be named by a legal VPE identifier and no two input interface nodes in the same graph may have the same name. Similarly, no two output interface nodes in the same graph may have the same name. VPE also requires that all ports have an arc incident upon them. This implies that all interface nodes in a graph will have an actual parameter bound to them by means of an arc incident upon the corresponding port in a call node.Notice that ports and interface nodes are not typed. This is because the messages that flow through them are not typed, and may indeed have values of several types packed within them. Thus, type errors are manifested within computations where the programmer might unpack the wrong type from a message.Graph parameters are variables that are set in graph initialization computations and can then be read anywhere in the graph, but they also play a role in graph calling. Programmers can optionally bind a parameter in a calling graph to a parameter in the graph it calls. This binding is an attribute of a call node. Figure 9 shows graph main’s parameter M bound to graph addN’s parameter N by means of the expression “M:N” in call node C1. When parameters are bound, types must match exactly (array sizes must match).Bound parameters work in the following way. Let graph G1 have a parameter x and let G1 call graph G2 by means of a call node in G1. Furthermore, let G2 have parameters p and q. Assume that G1’s call node binds x to p by means of “x:p” but binds nothing to q.Execution will begin with G1’s initialization computation running to completion. It is expected to give a value to x. Then, G2’s initialization computation can begin, but in it p is given the value of x initially because of the binding. G2’s initialization computation is then free to optionally modify p but is expected to give a value to q since it not bound to a parameter in G1. When G’s initialization com-putation is complete, all comp nodes can be instantiated. Programmers, however, should not assume that all initialization computations are complete before any comp nodes in the program are instanti-sages to be received from the N dprod instances in any order. If, instead, vpe_recv(Y,i) were called then ReadPrint would receive messages in order first from dprod[0], then dprod[1], and so on.Comp Node dprodFigure 1 shows that the dprod is replicated N times with index variable i taking on values from 0 to N-1. Inside dprod’s computation,i will hold the index of the node instance. Furthermore, dprod has been configured so that all instances will run on available machines of type RS6K (IBM RS/6000 worksta-tions). Node dprod’s computation follows.double *SV1 = MkVect(VSize/N+1), *SV2 = MkVect(VSize/N+1),PartialSum = 0.0;int j, Len = VSize/N+1;if (i >= VSize % N) Len -= 1; /* Get the size right */vpe_recv(A); /* Receive and unpack subvectors */ vpe_unpkdouble(SV1, Len, 1); /* from ReadPrint. */ vpe_unpkdouble(SV2, Len, 1);for (j = 0; j < Len; j++) /* Form the partial sum. */ PartialSum += SV1[j] * SV2[j];vpe_initsend(VpeDataDefault); /* Send partial sum out on port */ vpe_pkdouble(&PartialSum, 1, 1); /* B, which is connected to port Y */ vpe_send(B); /* on ReadPrint. */ The dprod instances first receive a message containing subvectors of V1 and V2 by means of the call vpe_recv(A). There are no node indices since ReadPrint is not replicated. It then computes the dot product of the subvectors and sends it back to ReadPrint via vpe_send(B). Again, there are no node indices because ReadPrint is not replicated.3.3 Summary: Steps in Creating the Dot Product ProgramThis section summarizes the steps that a programmer must perform in order to create the dot product program. They do not necessarily have to be done in this order.1.Draw all nodes, ports, replication boxes, and arcs in the graph. Name the ports.2.Declare the parameters N and VSize.3.Enter the graph’s initialization computation. It must give values to the parameters. the comp nodes (optional).5.Choose the machine or machine type the comp nodes will run on. (Details vary according to thetarget machine. The default is to permit the node instances to run on any available processor).6.Enter dprod’s replication expression.7.Enter the computations for ReadPrint and dprod.At this point, the program is complete. It can be compiled, and executed.Parameters play a vital role in replicating comp nodes. They are the only variables other than the index variables themselves that may appear in replication expressions. Thus, in VPE one must decide at the beginning of a computation how many node instances will be created since parameter values used in replication expressions must be set in graph initialization computations. This is not a serious limitation for many algorithms since the number of instances to create is often dictated by the number of processors in the parallel machine on which the program will run.Section4.0 will describe how a call node can initialize parameters in the graph it calls using values of parameters in the graph containing the call node. A graph’s parameters together with its interface nodes completely define its interface.3.2 Comp Node SpecificationsComp Node ReadPrintFigure 1 shows that ReadPrint has been configured to run on a particular machine named “comet.cs”that is on a network of machines being used as a virtual parallel computer. It has an output port X and an input port Y. ReadPrint’s complete computation follows. Pay particular attention to the calls to vpe_send and vpe_recv. The other “vpe_” calls manage message buffers.double *V1 = MkVect(VSize), *V2 = MkVect(VSize), Sum = 0.0, PartSum;int i, Start = 0, Len = VSize/N+1, Extras = VSize % N;ReadVect(V1, VSize);/* Read vectors from somewhere.*/ ReadVect(V2, VSize);for (i = 0; i < N; i++) {/* for each i from 0 to N - 1, pack*/ if (i == Extras) Len -= 1;/* and send subvectors on port X*/ vpe_initsend(VpeDataDefault);/* with node index i. Since X leads */ vpe_pkdouble(&V1[Start], Len, 1); /* to port A on dprod, dprod[i] will */ vpe_pkdouble(&V2[Start], Len, 1); /* receive the message.*/ vpe_send(X, i);Start += Len;}for (i = 0; i < N; i++) { /* Wait for a message with partial*/ vpe_recv(Y, VpeAny);/* sum to arrive from each of*/ vpe_unpkdouble(&PartSum, 1, 1); /* the N dprod nodes. Messages can*/ Sum += PartSum;/* be received in any order.*/ }/* Now Sum contains the dot product */The first loop sends subvectors of V1 and V2 to all dprod nodes. The code involving variable Len makes sure things work when N does not evenly divide VSize. The message containing the subvectors is sent to node dprod[i] by the vpe_send(X,i) call. Here, X refers to the output port the message will be sent on and i refers to the index of the receiving node. Since there is an arc from port X to port A, this message will be received on port A of dprod[i].The second loop receives a dot product of subvectors from each dprod instance. The key call is to vpe_recv(Y, VpeAny). The use of value VpeAny for the index of the sending node allows the mes-Call to G2Graph G2Figure 8. Call Node and Graph Called from It.It is also possible to bind parameters from the calling graph to parameters of the graph that is called. This will be described in Section4.0.3.0 Example programIn this section, we return to the dot product program shown in Figure 1 and explain it in full. The pro-gram works as follows.1.There is a single instance of comp node ReadPrint and there are N instances of comp node dprodwhich are distinguished by differing index values (dprod[0] ... dprod[N-1]). All comp nodes instances are processes that run concurrently.2.ReadPrint first reads values for two vectors and then sends subvectors from each vector to each ofthe dprod nodes.3.The dprod nodes wait to receive their subvectors from ReadPrint. When they receive them, theycompute the dot product of their subvectors, forming a part of the final dot product. Each dprod node sends this value back to ReadPrint.4.ReadPrint waits to receive messages from the dprod nodes with the dot products of the subvec-tors. A running sum is kept as each message arrives. When N messages have arrived, the dot product is complete.3.1 Parameters and Graph Initialization ComputationsAs mentioned above, graph parameters are variables that are assigned a value by a graph’s initializa-tion computation and can then subsequently be read from any node in the graph. The “Params:” line at the top of Figure 1 shows that the programmer has declared two integer parameters for the graph:N (the number of dprod instances to create) and VSize (the length of the input vectors to read). Both are initialized by the graph’s programmer-supplied initialization computation which runs before any of the comp nodes in the graph are instantiated. When the initialization computation is complete, comp nodes are instantiated, and they may then read the values of N and VSize. The name “parameter” is intended to suggest parameterization of a graph at the time it is created.It is legal for nodes to write to parameters but changes will not be propagated to other node instances. Parameters are, in fact, node-local variables that happen to be initialized by the graph’s initialization computation.may be constants or graph parameters-- variables that can be read from anywhere in the graph, but can be given values only at graph creation time. Parameters are discussed in detail in Section3.0 and Section4.0.Input and Output PortsMessage that arrive at a comp node enter via named input ports and messages that leave exit via named output ports. Ports are added to comp nodes using the two port tools. Each port must be given a name and no node may have two input ports with the same name or two output ports with the same name.Calls to message-passing routines inside node computations refer to port names. VPE’s message-passing routines will be listed in Section5.0, but Figure 7 shows a simple example in which a single value of type double is sent from one comp node to a second comp node. The nodes’ computations are in C and are shown below the nodes.Figure 7. Example Send.Node Sender first initializes a data send buffer and then packs a double into it. It then sends a message containing the buffer out on port X_Out. Port X_Out is connect by an arc to port Y of node Recvr. This node receives a message from its port Y and unpacks a double from it.Section3.0 will present an example in which the receiving node is replicated (with a single replica-tion expression). In that case, the sending node would executevpe_send(X_Out, i);where i contains the index of the receiving node. This type of send would usually be placed inside a loop in which i takes on a sequence of values.2.2.2 Call and Interface NodesCall nodes represent calls from one graph to another and are represented as variable sized boxes with double vertical lines on the left and right side. Figure 8 shows an example of a call node and the graph it calls (G2). G2’s interface nodes define its interface. There is an exact correspondence between the interface nodes in a graph and the ports on a call node that calls it. When a message is sent on an arc to the call node’s port A, that message “appears” on input interface node A and goes to port X1 due to the arc from A to X1. The other ports act similarly.Figure 6. Sample Graph Showing VPE Node Types.2.2.1 Compute NodesCompute (comp) nodes represent processes and are displayed as variable sized boxes with single ver-tical lines on the left and right side. Comp nodes contain several fields that represent attributes. They are listed here from top to bottom and are set by clicking the Open tool on them.1.The name of a comp node is a comment, but it is a good idea to give comp nodes meaningfulnames since error messages refer to them.2.The Comp button holds the C or Fortran text of the node’s computation.3.The Conf button holds various node configuration options including a list of C or Fortran files thatmust be compiled with the node since it calls routines in them.4.The Architecture field shows the name of the machine or machine type the node is to execute on.5.Replication expressions (optional).Comp Node ReplicationA comp nodes can be replicated by adding a replicator box to it by clicking near the node with the replicate tool. A replication will appear. Click on it with an open tool and enter one or more replica-tion expressions. For example, one could enteri = 1, N+1; j = 1, M;to create a two-dimensional array of nodes, all running in parallel. V ariables i and j are may be refer-enced in the node’s computation. They will contain the values of the node instance’s indices.N and MFigure 4. VPE Graph Edit Tools.Attribute windows are opened by clicking the Open tool on an object or special part of an object. For example, to enter the computation of a computation node, the user clicks the Open tool on the box labelled “comp” shown on all comp nodes. Figure 5 shows a typical attribute window. This paper will define the attributes of VPE objects, but will not focus on the details of attribute forms.Figure 5. A Typical VPE Attribute Window.2.2 The VPE LanguagePrograms in VPE consist of both textual annotations and visual constructs including arcs and various types of nodes. There are four types of nodes in VPE and Figure 6 shows them all.Menu picks from the project window permit graphs to be added to and removed from project, build an executable program from the project, run the project, etc. In addition, users can easily open graphs in the project in a graph edit window by selecting one or more graphs with the mouse and picking “Open Selected” from the Graph menu or pressing Control-L. VPE has such keyboard alternatives for all frequently selected menu items.2.1.2 Graph Edit WindowsGraphs are viewed and edited in graph edit windows such as the one shown in Figure 3. VPE users can open graphs even if they are not in the project since they may wish to view a graph in another project while working on the current one. Or, they may wish to cut and paste nodes between graphs from different programs.Figure 3. An Empty Graph Edit WindowThe VPE graph editor is designed to be familiar to users of popular personal computer based drawing programs. Users select tools with the mouse from the toolbar on the left and then use the tool in the white space drawing area on the right. For example, to draw a comp node, the user selects the Comp tool (second down) and then clicks on white space. The Select tool (top) is used to select objects to cut, copy, delete, move, resize, etc. It is possible to select multiple objects simultaneously. The Open tool is used to open attribute forms for an object. Figure 4 summarizes VPE’s graph edit tools.2.1.3 Attribute WindowsMany objects in VPE have attributes that the user must be able to view and edit. Other than required node names, attributes are edited in non-model attribute windows.Select tools to draw objects, etc.from the tool bar on the left.Draw graphs in this white space area.There are menu picks for operations like cut, paste,and filling out graph-level attributes.Get online help.VPE’s language is explicitly parallel. Programmers directly specify the parallel structure of their pro-grams and must choose appropriate parallel structures in order to achieve good performance. VPE’s visual representations assist in this task.The VPE environment itself runs on UNIX workstations under X windows, although the parallel pro-grams created within it may be executed on different types of machines. VPE programs consist of several elements each of which is stored in a separate file.1.There is one project file (ending in “.proj”) that lists all of the graphs in the program. There is thusone project file per program.2.There is a graph file (ending in “.gr”) for each graph in the project.It is possible for a single graph file to be included in multiple projects. Thus, graph files may be stored in libraries. It is also possible for a graph file to exist without being in any project file. Such a graph is simply not used in any program at the moment.2.1 The VPE Graphical User Interface (GUI).When VPE is run, one or more windows will appear on the workstation screen. The project window will always be open and will display the contents of the project file, and zero or more graph edit win-dows will display graphs. In addition, users can open attribute windows to view and change attribute values of nodes, etc. These windows are generally non-modal so that information from multiple sources can be simultaneously viewed or manipulated, and objects can be cut and pasted between graphs.VPE’s graphical user interface is implemented using the Tcl/Tk toolkit [Ous94] developed by John Ousterhout.2.1.1 The Project WindowAs stated above, the project window simply lists the names of the graphs that are a part of the current project. It is these graphs (not the set of graphs that are open in edit windows) that will be translated to form a complete parallel program. Figure 2 shows the VPE project window.Figure 2. A VPE Project Window Showing Two Graphs in the Project,The problem with the HeNCE/CODE approach is that it forces computations to be split into separate nodes when communications occur or when branching decisions control communications. This can result in complicated, awkward, and large graphs. Consider a simple imaginary computation in which F and G are sequential functions.array A, B, C; scalar x = 0, y, z;1: receive A from some process.2: B = F(A);3: Send parts of B to a set of processes, S;4: For each process in S, receive z; x = x + z;5: if (x < 0) receive y from one processes;6: else receive y from some other process;7: C = G(A, y, x);Since communications cannot be embedded within HeNCE and CODE node computations, this pro-gram must be split into multiple nodes. In HeNCE a new computation node is required for lines 1, 4, 5, and 6 and four additional control flow nodes are needed as well. Thus eight nodes must be drawn, and six require annotation. Since communications are explicit (however abstract) in HeNCE and CODE, the programmer must state all communications such as the fact that the node running line 7 needs data from the processes running nodes 1, 4, and 5 or 6. This is wordy. CODE suffers from sim-ilar complexities involving multiple nodes or as few as one node that fires multiple times and has very complicated explicit firing conditions which are supplied by the programmer.If F and G are truly large-grain routines that are logically decoupled, the HeNCE and CODE pro-grams may be reasonable, but if they are not VPE’s representation will be much simpler and more natural since all seven lines above may be regarded as pseudocode for a single VPE node computa-tion. Also, the computation G always follows F due to data dependences. The HeNCE and CODE implementations must perform analysis to determine that both should be run within a single processor to avoid the overhead of sending A. The VPE implementation will naturally do the right thing since VPE directly implements the process structure specified by the programmer.Finally, we should note that the VPE model is a superset of the HeNCE and CODE models in the sense that it is possible for the user to choose to create nodes that communicate only at the beginning and end of computations. VPE is less abstract that HeNCE and CODE but provides greater expressive range. Its communications are specified less abstractly, but are simpler than those provided by most message-passing libraries since VPE uses graphical specification for the sources and sinks of mes-sages. It is also closer to current programming practice. For better or worse, this suggests users will be comfortable with VPE since its learning curve is less steep.2.0 Overview of VPE Environment and LanguagePrograms in VPE consist of a set of graphs which can call one another, thus permitting hierarchical program development much as subroutines do in conventional languages. Each graph contains com-putation (comp) nodes that represent processes that are specified as C and Fortran computations which contain calls to VPE message-passing routines. Messages flow on arcs that interconnect named ports attached to nodes. Message-passing calls reference port names. Also, comp nodes can be repli-cated in which case instances are distinguished by integer-valued indices.5.Be capable of using common message-passing libraries such as MPI and PVM as its executiontarget.6.Support heterogeneous execution if the target message-passing library supports it.7.Automate program compiles even in heterogeneous environments.8.Automate program execution and relate runtime performance data and animation back to theuser’s original program representation.e a hierarchical name space to permit the creation of libraries (at the source) level in a simplemanner that eliminates the need for complex “context” specifications.10.Permit reuse of existing C and Fortran sequential subprograms.11.Add little runtime overhead to what is already inherent in the target message-passing library.1.2 Related Work: HeNCE and CODEA number of other visual programming languages and environments have been developed (see [New93] for a survey). In fact, the authors are associated with the development of two previous sys-tems, HeNCE [Beg91, Beg93] and CODE 2.0 [New92, New93]. VPE and HeNCE and CODE have similar general goals, but the systems differ substantially in detail, just as HeNCE and CODE differ. The CODE model is dataflow oriented while HeNCE programs are (necessarily) structured “parallel flowcharts” in which nodes must declaratively specify access to shared variables in a global name space.All three environments are based upon the idea that nodes represent computation, and arcs represent interactions (of some form) among nodes. HeNCE and CODE, however, are not based upon a tradi-tional message-passing model. The fundamental difference between them and VPE is that HeNCE and CODE nodes represent sequential computations in which communications with other nodes occur only at the beginning and ending of the computation. Furthermore, these communications are expressed at a higher level of abstraction than are communications in VPE. HeNCE and CODE pro-grammers make no explicit calls to message-passing library routines as VPE programmers must. The HeNCE and CODE approach has many desirable properties. Nodes are essentially calls to sequential subroutines expressed in standard languages. The calls are embedded in an abstract visual specification of parallel structure. Programmers benefit from a separation of concerns. They first specify a set of sequential computations and then, separately, specify how they are to be composed into a parallel program. Also, the debugging process can be partitioned into the tasks of debugging a set of sequential routines and debugging the parallel interactions of the routines (which are then viewed as being atomic).HeNCE and CODE arguably (it has not been demonstrated by implementation) enhance the portabil-ity of parallel programs in the sense of running well on multiple targets rather than the sense of run-ning at all. This is because their models lends themselves to automatic analysis by intelligent translators. The program’s sequential components are of known (or measurable) granularity and their interactions are specified at an abstract level that promotes analysis due to their direct and unambigu-ous representations. Such analysis is far more difficult for VPE programs since calls to communica-tion routines are embedded within arbitrary C or Fortran computations.。
