Windows Phone 7 Security Model_FINAL_122010
微软公司产品指南说明书
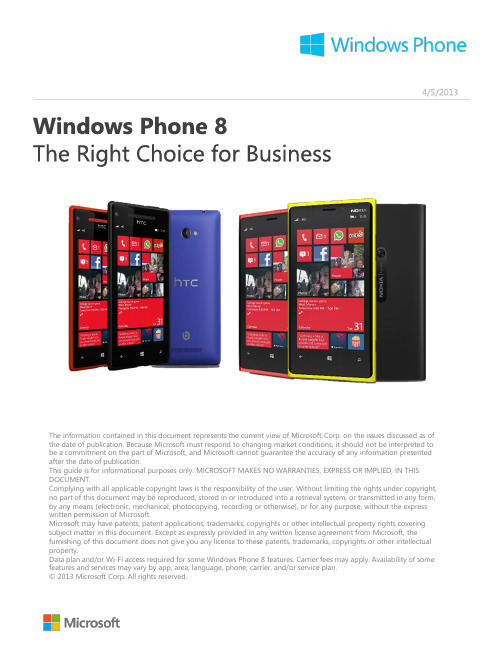
The information contained in this document represents the current view of Microsoft Corp. on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication.This guide is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS DOCUMENT.Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form, by any means (electronic, mechanical, photocopying, recording or otherwise), or for any purpose, without the express written permission of Microsoft.Microsoft may have patents, patent applications, trademarks, copyrights or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights or other intellectual property.Data plan and/or Wi-Fi access required for some Windows Phone 8 features. Carrier fees may apply. Availability of some features and services may vary by app, area, language, phone, carrier, and/or service plan.© 2013 Microsoft Corp. All rights reserved.With BYOD (Bring Your Own Device) becoming the industry norm, it is important for IT departments to choose a smartphone platform that appeals to consumers and will delight their end users. Windows Phone is rapidly winning the hearts of consumers and gathering industry accolades.Consumers love Windows PhoneBoth Windows Phone 8 and Windows Phone 8 devices are receiving high praise from consumers. Windows Phone 8 was rated the #1 OS by all readers of PC magazine and the Nokia Lumia 920 was rated the #1 phone by AT&T readers of PC Magazine.PC Magazine 2013Reader’s Choice AwardWindows Phone Accolades and Awards• 4 of the top 9smartphones across all carriers on are Windows Phone 8 devices •The Nokia Lumia 920 won the 2012 Engadget Readers Choice Award•The Windows Phone 8X by HTC won the Red Dot Design Award for 2013Your favorite apps, and over 130,000 moreWindows Phone has the apps and games youwant from brands you love. The WindowsPhone store has 130,000+ apps and 48 of thetop 50 apps on competing platforms. Get appsfor personal use such as Flixster, Cut theRope®, and Pandora. Or get apps for worksuch as, Evernote, Box, and LinkedIn. OnlyWindows Phone has Live Apps that bring youthe info you want, right on your start screen.With Windows Phone 8 we made certain that IT professionals could have peace of mind and effortlessly integrate with their Exchange, SharePoint, Lync and Office 365 infrastructure to lower their TCO. We ensured end users had the best possible Office, Outlook and Lync experience on their Windows Phone 8 devices. And we ensured that developers could use the Visual Studio and .NET tools they are already familiar with to develop code that would run on PCs, tablets and smartphones.Windows Phone Gaining Momentum Among CIOs•In a recent poll by Aberdeen Group, CIOs revealed that they plan to deploy mobile apps forWindows Phone and Windows tablets more than any other platform over the next 12 months. •Windows Phone has also seen significant growth over the past year, at the expense of BlackBerry.• A report by Strategy Analytics indicates that Windows Phone surpassed BlackBerry in Q4 2012 to become the #3 smartphone platform in the US.13432191012 118765The 13 Layers of Security on Windows Phone 8Below is an explanation of the security provided by the 13 numbered boxes in the security architecture diagram above:1.All Windows Phone 8 devices have to meet specific hardware requirements. This not onlyguarantees a base-level user experience, it limits the hardware-related security attack vectors.2.Windows Phone 8 is the only smartphone platform that has a Trusted Platform Module (TPM) 2.0chip embedded on every device. The TPM chip is a huge boost to security –it protects encryptionkeys, contains a crypto processing engine, and is a foundational element of a secure boot chain.3.Windows Phone 8 uses the Unified Extensible Firmware Interface (UEFI) Secure Boot industrystandard. UEFI is the new BIOS. In a UEFI Secure Boot process the firmware, the bootloader, thekernel and kernel extensions, are all cryptographically signed. This makes it easy to detect when any of these layers has been tampered with. If any layer in this boot process has been maliciouslyaltered, the device won’t boot.4.The crypto signing goes beyond the kernel –the entire OS and every single app on the system iscode-signed to guarantee a chain of trust from the hardware all the way up. This is not necessarilythe case for competing platforms. There is no real concept of a trusted boot chain on Android . And it is well known that the trusted boot chain on iPhone is not entirely trustworthy because everysingle version of iOS has been jailbroken within days of release .5.Windows Phone 8 uses the same NT Kernel as Windows 8 and Windows Server 2012. But it alsoshares the same driver model, developer platform, security, and networking stack and graphics and media platform. All of these have been tried and tested on more than a billion client and servermachines, many running mission-critical workloads.6.All updates to Windows Phone 8 now come directly from, and only from, Microsoft. This ensures theintegrity of the OS. Also all security fixes follow the same rigorous standards set by the Microsoft Security Response Center or MSRC for our client and server products.7.Windows Phone 8 supports alpha-numeric and complex passwords for device-locking.8.The internal storage on a device can now be fully encrypted using the same BitLocker technology thatships with Windows. The BitLocker encryption key is protected by the TPM 2.0 chip and will only be released if i) the device successfully passes the UEFI Secure Boot process to boot up a trusted OS, and ii) if the encrypted disk is physically located in the original device. This protects data at rest and guards against offline attacks. So it is not possible to take the encrypted storage out and get access to the data by booting from another OS, and it is also not possible to place the encrypted storage in another Windows Phone 8 device to access the data. This protects data at rest and guards against offlineattacks. With both device-lock and BitLocker enabled it is extremely difficult to gain unauthorized access to data on the internal storage.9.Every app runs in its own isolated chamber. Even the OS services run in their own isolated chamber.Each app receives only the capabilities it needs to perform all its use cases. It cannot elevate itsprivileges at run time, it cannot communicate with other apps on the phone other than through the cloud, and it cannot access memory, data or the keyboard cache used by another app.10.Even the browser runs in its own sandbox. Windows Phone 8 ships with a locked down version ofInternet Explorer 10 that does not support plug-ins, and comes with anti-phishing filters built-in.11.To further protect the data in each app, Windows Phone 8 provides another layer of encryption via theData Protection API. This is smart technology that uses entropy information already available on the device to automatically generate new encryption keys. This way apps do not have to worry about generating, storing and managing new keys. Each app also automatically receives its own decryption key when it first runs.12.However, no amount of encryption will prevent an authenticated user on a trusted device from sharingdata with unintended parties, willingly or unwillingly. This makes Information Rights Management (IRM) critical and Windows Phone is the only smartphone platform that has IRM built-in to prevent data leakage.13.Finally, data synchronization with most cloud services like Office 365 and on-premise servers likeExchange and SharePoint is done via the latest SSL 3.0 technology with AES 128 or 256 encryption.This protects data in transit.Note on TPM and UEFI Secure Boot standardsMicrosoft is a strong believer in open standards for security, like UEFI Secure Boot and TPM. Standards have numerous advantages over proprietary methods used by other smartphone platforms. Standards go through a transparent development process, survive rigorous open review from the best security minds across multiple organizations, and help ensure broad support across companies. The list of 100+ companies that define the TPM specifications can be found here and the firms behind the UEFI specifications can be found here.Maximize Value from Existing Microsoft InvestmentsThe built-in IRM client on Windows Phone helps you maximizevalue from your existing investments because it uses the ActiveDirectory Rights Management Service already available with yourWindows Servers. Exchange ActiveSync is also built-in andsupported and this is how Microsoft IT manages more than70,000 BYOD Windows Phone devices. Additionally, a built-inmanagement client is available so you can use your existingMobile Device Management software such as MobileIron,AirWatch, Citrix XenMobile, Symantec or Windows InTune andSystem Center 2012 SP1. Finally, to further lower your TCO,Windows Phone 8 comes with full-fidelity mobile versions ofOffice so you can make the most of your existing investments inExchange, SharePoint, Lync and Office 365.Windows Phone 8 integrates with your existing Microsoft infrastructure. Right out of the box, Windows Phone seamlessly works with Microsoft products you know and already own, such as Exchange, Office, SharePoint, Lync and Office 365 –no need to purchase additional third-party software.BES server software and admin costThird-party software for OfficeThird-party software for SharePointTypical incremental software & administration cost required to leverageSharePoint, Office and Exchange functionality on1,000 smartphonesWindows Phone 8 gives you the best Outlook and Exchange experience, the best mobile versions of Office, and the best communication and collaboration experiences with Lync and SharePoint.WP 8iOS 6Android4.0BB 10Setup,Lock screen, and Start screen Fast Office 365setup with simple input of ID and passwordResizable live tiles to access more information Notifications on lock screenOutlook e-mail, calendar, and contacts Pin frequently accessed e-mail folders to the Start screenSame integrated mail and calendar as Outlook on PC Access and search for e-mails on the Exchange Server Read protected e-mail (IRM)Office documents View, edit, and comment on Word, Excel, and PowerPoint documents“Places” panel for easy access to docs opened via email, or stored on SharePoint, SkyDrive or the phone Read protected IRM documents“Thumbnail” view to easily navigate long ppt decksLync communication Make VoIP and HD video Lync calls, and receive Lync calls like standard voice callsMultitask during Lync call -read email, view/edit/save docs, access SharePoint sites, use other apps etc. Attend Lync meetings with audio, video, and web conferencing with one click from OutlookSharePoint sites Sync documents across devices. Edit on one device andcontinue working right where you left offDownload documents for offline access and editing;upload changes when you are back onlineSearch for content on SharePoint team sites, lists ordocument librariesWrite and edit documents with colleagues at thesame timePin SharePoint sites to the Start screen for easy access485936Feature available Feature not available Feature available with conditions11.Not open to third party developers2.Requires setup through widgets3.Requires BlackBerry Enterprise Server (BES)4.View only5.Supported only by a few devices6.Documents To Go included7.No Lync app for BB 108.Access and view only, no editing9.Supported only by a few devices21777Common Development Foundation for Client and Mobile ComputingHistorically, apps for client computing devices like PCs, laptops and desktops have been developed separately from apps for mobile computing devices like smartphones and tablets. But as more client computing devices get touch screens and mobile broadband radios, and more mobile computing devices take on client computing workloads, it is going to be critical for you to be able to share code between the mobile and client computing worlds.From an app development perspective there is deep commonality between Windows Phone 8, Windows 8 and Windows RT.In fact, Windows Phone 8, Windows 8 and Windows RT share several components in a common development foundation that makes it easy to port apps across different form factors on the Windows platform.First, Windows Phone 8, Windows 8 and Windows RT share a common development environment and tools with Visual Studio and .NET. Second, they also share the same driver model, security model, web browser and managed code Common Language Runtime (CLR). Finally, Windows Phone 8, Windows 8 and Windows RT all support native code and have the exact same API set for Networking, File System, Input, Sensors, Graphics and Media, Audio, and Commerce.Flexibility with 3 Development ModelsApp developers also have flexibility in how they develop apps and can choose from 3 development models. They can write an app that uses whatever combination they desire between managed code, native code and HTML/JavaScript code. And they can run a lot of that code across Windows Phone 8, Windows 8 and Windows RT because of the common foundation. So porting apps and business functionality across your mobile and client computing worlds becomes a lot faster. This will be a critical capability needed by businesses as the worlds of mobile and client computing converge.There are a number of programs available to help you transition your organization to Windows Phone. Your Microsoft account team can provide more information and help you get started.Frequently Asked QuestionsWhat support options are available for businesses?The “Get technical support” section on /gp/windows-phone-8lists a variety of Windows Phone 8 technical support options available to businesses.Where can I learn more about Microsoft’s Support Lifecycle policy?The most common questions on this topic have been answered on/gp/lifepolicyWill Windows Phone 8 devices be upgradeable to the next version of the Windows Phone OS? Yes, Windows Phone 8 devices will be able to upgrade to the next version of Windows Phone OS when it is launched.Where can I get an in-depth overview of Windows Phone 8 for businesses?The Windows Phone 8 Reviewers Guide goes into considerable depth for all the areas covered by this document.。
微软办公室移动版在Windows Phone 7上的产品指南说明书

目錄Microsoft Office Mobile:概觀 (1)Office Mobile:概觀 (2)Office Mobile:深入探討 (3)檢視及更新 Office 文件 (3)Office 整合中心 - 新功能! (3)使用者介面 - 改良功能! (5)註解 - 新功能! (6)檔案格式支援 - 改良功能! (7)產品相關要點 (8)Word Mobile (8)Excel Mobile (9)PowerPoint Mobile (10)更有效率地導覽文件 (11)大綱窗格 - 新功能! (11)導覽式目錄 - 新功能! (12)改良的尋找功能! (12)手勢支援 - 改良功能! (13)保持收件匣井然有序 (14)電子郵件帳戶設定 - 改良功能! (14)收件匣檢視 - 新功能! (16)電子郵件選擇模式 - 新功能! (16)全盤掌握行程 (17)行事曆檢視 - 全新及改良的功能! (17)「遲到」電子郵件 - 新功能! (19)排程工具 - 改良功能! (19)行駛路線 - 新功能! (20)隨時隨地記錄筆記並與他人共用 (22)筆記記錄工具 - 改良功能! (22)電子郵寄筆記 - 新功能! (23)OneNote 電子郵件附件 - 改良功能! (24)隨時皆可使用筆記及保持筆記的一致性 (24)與 Windows Live或 SharePoint 進行同步 - 新功能! (25)筆記方塊 - 新功能! (27)搜尋筆記 - 新功能! (27)筆記結構 - 改良功能! (28)從遠端參加 PowerPoint 簡報廣播 (29)檢視 PowerPoint 簡報廣播 - 改良功能! (29)電子郵寄 Office 文件 (30)存取及更新儲存在 SharePoint 中的資訊 (31)更新 Office 文件與筆記 - 改良功能! (31)管理 SharePoint 檔案 - 改良功能! (32)從「我的網站」匯入最愛的連結 - 新功能! (33)伺服器轉譯的文件 - 新功能! (33)Office Mobile:常見問題集 (35)功能的可用性/公開揭示 (36)Microsoft Office Mobile:概觀最近您可能都是仰賴行動裝置隨時獲取工作、親朋好友與外界的最新消息。
零信任网络中基于区块链的访问风险评估模型构建

零信任网络中基于区块链的访问风险评估模型构建作者:***来源:《无线互联科技》2023年第16期摘要:区块链技术为零信任网络访问风险控制提供了新的思路,凭借区块链技术的去中心化、防篡改和可溯源特征,可为零信任网络提供更加可靠的安全保障。
文章介绍了区块链技术,结合零信任网络访问要求,基于区块链技术构建了贝叶斯优化LightGBM模型。
该模型解决了传统模型固有的单点故障问题,通过访问特征定义与数据预处理,极大地提升了用户访问的安全性,为用户身份管理提供了有效方式。
模型经过验证,最终得分为5.22,训练速度为30 s,结果表明该模型具有较好的拟合度、精准性和训练速度,能够满足零信任网络的访问控制需求。
关键词:零信任网络;区块链;访问控制;用户访问中图分类号:TP311 文献标志码:A0 引言考虑到传统访问控制策略的局限性,且在当前数据共享环境下面临着信息安全问题,目前基于区块链技术进行访问控制已经成为热点研究方向[1]。
区块链技术具有去中心化、不可篡改等优势,可以通过构建智能合约,实现访问控制与身份管理的结合,有效避免传统访问控制策略中的单点故障问题[2]。
然而,这种访问控制策略同样面临着单次验证信任问题,因此仍然无法完全适用零信任网络[3]。
考虑到零信任网络的特性,部分学者提出需要在分布式属性访问控制的基础上,进一步对访问行为的风险等级进行评估与划分,从而进一步优化访问控制的灵活性,提高基于区块链技术的访问控制手段在零信任网络中的应用可行性[4]。
鉴于此,本研究着重探讨了零信任网络中基于区块链的访问风险评估模型,以准确评估访问控制风险,从而有效提高访问行为的安全性。
1 基于区块链的访问风险评估模型构建1.1 访问风险特征定义零信任网络的特征为对每个环节的访问控制均需要验证,通过该用户的历史访问行为准确评估此次访问风险,从而完全杜绝恶意用户的非法访问行为。
根据这一特征,可考虑构建的访问风险特征体系为“主体特征+资源特征+环境特征”,并对上述大类别进行详细分类,最终确定8个访问风险特征,分别为用户账号信息(account)、用户所属组(group)、请求资源地址(url)、请求终端ip(ip)、请求终端端口号(port)、请求终端所在虚拟网域编号(vlan)、请求终端连接交换机ip(ip_s)、访问时间(time)[5-6]。
湖北省重点高中协作体2025届高考英语二模试卷含解析

湖北省重点高中协作体2025届高考英语二模试卷注意事项:1.答题前,考生先将自己的姓名、准考证号码填写清楚,将条形码准确粘贴在条形码区域内。
2.答题时请按要求用笔。
3.请按照题号顺序在答题卡各题目的答题区域内作答,超出答题区域书写的答案无效;在草稿纸、试卷上答题无效。
4.作图可先使用铅笔画出,确定后必须用黑色字迹的签字笔描黑。
5.保持卡面清洁,不要折暴、不要弄破、弄皱,不准使用涂改液、修正带、刮纸刀。
第一部分(共20小题,每小题1.5分,满分30分)1.________about the man wearing sunglasses during night that he was determined to follow him.A.So curious the detective wasB.So curious was the detectiveC.How curious was the detectiveD.How curious the detective was2.Reporters asked him to ______ his position on welfare reform.A.clarify B.divide C.instruct3.Jane’s grandmother had wanted to write children’s book for many years, but one thing or anotheralways got in way.A.a;不填B.the;theC.不填;the D.a;the4.Comparison may make something appear more beautiful than it is when _____ alone.A.seen B.seeing C.see D.to see5.The only problem was ______ we kept getting lost! But people in Tianjin are very friendly and helpful.A.why B.whetherC.that D.how6.Some drunken drivers think that they may be lucky to________a fine, which may cost their own lives.A.get through B.get along withC.get down to D.get away with7.According to the school rule, no child be allowed out of the school, unless accompanied by his or her own parents.A.should B.mustC.shall D.can8.—Congratulations!I hear you’ve won the first prize in the singing competition.—You _____ be mistaken.I’m in the dance class.A.must B.may C.should D.could9.There are also people who object to fairy stories on the grounds ______ they are not objectively true, and that giants,witches, two-headed dragons etc do not exist.A.that B.what C.which D.when10.________enough money, the young man was unable to buy his girlfriend expensive jewelry.A.Not to save B.Not savingC.Not having saved D.Not saved11.Nicholas was very kind, merciful and generous. This is ________ Father Christmas is based on.A.where B.how C.what D.why12.---- Which of these digital cameras do you like best?---- ______. They are both expensive and of little use.A.None B.Neither C.Nothing D.No one13.The press should expand its influence in international public opinion to make China’s voice better ______ in the world.A.hearing B.to be heardC.hear D.heard14.— I wonder what chance there is of me passing by the old places without thinking of you.— ______. Time cures all wounds.A.My pleasure B.Don’t mention it C.I can’t agree more D.Never mind15.Why do you turn to me for help ______ you can easily work out the problem independently?A.until B.whenC.after D.unless16.As is known, it was Hu Jintao, _______ president of our nation, who gave ________ lecture at the ceremony of National DayA.the; a B.the ; / C.a; the D./; a17.We have decided to fulfill the task in time, difficulties we may meet with.A.no matter how B.however C.whatever D.whichever18.---Sorry to have broken your glass.---_____________. You didn’t mean to, did you?A.No problem B.Forget itC.All right D.Don’t say so19.---Nowadays, buyers accustomed to prices moving upward just adopt a wait-and-see attitude.---If they continue to _____, then our company is closing down.A.fish in the air B.sit on the fenceC.fly off the handle D.beat around the bush20.Word came that 30 firefighters gave their lives to our country _______ national property security.A.in exchange for B.in response toC.in terms of D.in contrast with第二部分阅读理解(满分40分)阅读下列短文,从每题所给的A、B、C、D四个选项中,选出最佳选项。
WP7芒果解锁支持Mango图文教程

ChevronWP7是一款解锁软件,在早期的Windows Phone 7系统越狱当中立下了悍马功劳,此前微软一直都以破坏安全性能为由将其拒之门外。
不过为了让开发者可以更快更方便的开发程序,近日微软官方已经允许ChevromWP7解锁程序面向开发者,每次的解锁费用为9美元。
/file/dneobt4q#ChevronLabs.Unlock32-bit.rar/file/dneobkgb#ChevronLabs.Unlock64-bit.rar教程:/news/wanjijiaocheng/wp_177.html請詳細閱讀下面的訊息这软件版本支持5款设备:*HTC Mozart (莫扎特,HD3,T8697,T8698,T8699) *HTC Mondrian (蒙德里安,Surround,T8788)*HTC Spark (斯帕克,Trophy,T8686)*HTC GOLD(Htc 7 Pro,T7575,T7576)*HTC Schubert (舒伯特,HD7,T9292,T9295,T9296)这些设备大多有几个ModelID(ModelID例如“PC921000”)。
当前版本只支持数量有限的一些MID的。
这是旨在最大限度地减少可能对用户的设备造成危害。
支持的MIDS清单:Gold: “PC92****”, “PC921000”Mozart: “MOZA1000”, “PD67****”, “PD671000”, “PD671200”Mondrian: “PD26****”, “PD261000”, “PD261100”Spark: “PC401000”Schubert: “PD29****”, “PD291000”, “PD291100”如果有未知的MID,请停止使用此程序。
如果你的有未知的MID,请在此主题跟帖说明:你的MID,设备名称,ROM版本。
如果你能提供此版本的ROM下载连接,将是更有用的。
技术开发合同英文 示范文本

技术开发合同英文示范文本TECHNOLOGY DEVELOPMENT CONTRACT.I. Parties to the Contract.Party A (the Entrusting Party):Full name: [Party A's full name]Address: [Party A's address]Contact person: [Contact person's name]Contact number: [Phone number]Email: [Email address]Party B (the Developer):Full name: [Party B's full name]Address: [Party B's address]Contact person: [Contact person's name]Contact number: [Phone number]Email: [Email address]II. Background and Purpose of the Contract.Party A has certain technological needs and hopes to rely on Party B's professional technology development capabilities to achieve specific technological development goals. Party B is willing to use its owntechnical strength to undertake this technology development project for Party A.III. Subject Matter of the Technology Development.1. Project Name: [The specific name of the technology development project]2. Project Description:Party B will develop [describe the general function or product to be developed]. This will involve [mention key aspects such as algorithms, software features, or hardware design if applicable].The developed technology should meet the following requirements:[List specific requirements, e.g., performance standards, compatibility with certain systems, etc.][If there are any regulatory or industry specific compliance requirements, mention them here]IV. Development Plan and Schedule.1. Milestones and Deadlines.Milestone 1: Concept Design.Party B will complete the concept design of the technology within [number of days/weeks] from the effective date of this contract. This will include [describe what the concept design should cover, e.g., basic functionality layout, initial technology framework].Party A will review and provide feedback on the concept design within [number of days] after receiving it from Party B.Milestone 2: Prototype Development.Based on Party A's feedback, Party B will start the prototype development. The prototype should be completed within [number ofdays/weeks]. The prototype will be a basic working model that demonstrates the key functions of the final technology.Party A will test the prototype and provide test results and further improvement suggestions within [number of days] after receiving the prototype.Milestone 3: Final Development and Testing.Party B will use Party A's feedback to complete the final developmentof the technology within [number of days/weeks]. This includes optimizing the performance, fixing any bugs, and ensuring all requirements are met.Party B will conduct comprehensive testing, including [mention types of testing such as functionality testing, security testing, etc.]. The test report will be provided to Party A within [number of days] after the completion of testing.Milestone 4: Delivery.If the technology passes all tests and meets Party A's requirements, Party B will deliver the final technology to Party A within [number of days] after the test report is approved by Party A.2. Delays and Penalties.If Party B fails to meet any of the above mentioned milestones without justifiable reasons, Party B shall pay a penalty to Party A. The penalty amount for each day of delay is [specify the amount].However, if the delay is caused by Party A's failure to provide necessary information or feedback in a timely manner, the corresponding milestone deadline will be extended accordingly, and Party B will not be liable for the delay.V. Intellectual Property Rights.1. Ownership of Intellectual Property.The intellectual property rights of the technology developed under this contract, including but not limited to patents, copyrights, and trade secrets, shall belong to Party A.Party B shall transfer all relevant intellectual property rights to Party A upon the completion of the project and delivery of the technology.2. Use of Intellectual Property by Party B.Party B may use the technology developed under this contract only for the purpose of this project during the development process. After the completion of the project, Party B shall not use the technology without Party A's written permission.VI. Confidentiality.1. Confidential Information.Both parties shall keep confidential all information related to this technology development project, including but not limited to technical details, business plans, and customer information.2. Duration of Confidentiality.The confidentiality obligation shall start from the effective date of this contract and last for [number of years] after the completion of the project.3. Exceptions.The confidentiality obligation does not apply to information that is already publicly known at the time of disclosure, or becomes publicly known through no fault of the receiving party, or is required to be disclosed by law.VII. Consideration and Payment.1. Total Contract Price: The total price for this technology development project is [amount in currency].2. Payment Schedule.Initial Payment: Party A will pay an initial payment of [percentage of the total price] of the total contract price, which is [amount in currency], within [number of days] after the effective date of this contract. This payment is to cover Party B's initial costs such as research and design work.Milestone Payments:Upon the successful completion of Milestone 1 (Concept Design), Party A will pay [percentage of the total price] of the total contract price, which is [amount in currency].Upon the successful completion of Milestone 2 (Prototype Development), Party A will pay [percentage of the total price] of the total contract price, which is [amount in currency].Upon the successful completion of Milestone 3 (Final Development and Testing), Party A will pay [percentage of the total price] of the total contract price, which is [amount in currency].Final Payment: After Party B has delivered the final technology and Party A has accepted it, Party A will pay the remaining [percentage of the total price] of the total contract price, which is [amount in currency].3. Taxes.Each party shall be responsible for paying its own taxes in accordance with the applicable laws.VIII. Warranties and Representations.1. Party A's Warranties.Party A warrants that it has the legal right to enter into this contract and to request the development of the technology.Party A will provide Party B with all necessary information and assistance in a timely manner to ensure the smooth progress of the project.2. Party B's Warranties.Party B warrants that it has the necessary technical capabilities and resources to complete the technology development project.Party B will use its best efforts to develop the technology in accordance with the requirements and schedule specified in this contract.Party B warrants that the technology developed will not infringe on any third party intellectual property rights.IX. Termination of the Contract.1. By Mutual Agreement.The two parties may terminate this contract by mutual written agreement at any time.2. For Cause.If either party materially breaches this contract, the non breaching party may terminate the contract by giving written notice to the breaching party. In case of termination due to Party B's breach, Party B shall refund any payments already received from Party A and be liable for any losses caused to Party A. In case of termination due to Party A's breach, Party A shall pay Party B for the work completed up to the date of termination according to the proportion of the work completed.3. Consequences of Termination.Upon termination of the contract, both parties shall return or destroy any confidential information obtained from the other party in accordance with the confidentiality provisions of this contract.X. Dispute Resolution.1. Negotiation.In case of any disputes arising from this contract, the two parties shall first try to resolve the disputes through friendly negotiation.2. Arbitration or Litigation.If the negotiation fails, the parties may choose either arbitration or litigation. If they choose arbitration, the arbitration shall be conducted in accordance with the rules of [specify the arbitration institution]. Ifthey choose litigation, the lawsuit shall be filed in the court with jurisdiction over [specify the location].XI. Miscellaneous.1. Amendments and Supplements.Any amendments or supplements to this contract shall be made in writing and signed by both parties.2. Entire Agreement.This contract constitutes the entire agreement between the two parties regarding the technology development project and supersedes all prior agreements and understandings related to the same subject matter.3. Severability.If any provision of this contract is found to be invalid or unenforceable, the validity and enforceability of the other provisionsshall not in any way be affected.This contract is made in duplicate, with each party holding one copy. The contract shall come into effect on the date of signing by both parties.Party A (Signature and Seal): [Signature and company seal]Date: [Date]Party B (Signature and Seal): [Signature and company seal]Date: [Date]。
2025届南通启秀中学英语九年级第一学期期末经典试题含解析

2025届南通启秀中学英语九年级第一学期期末经典试题注意事项:1.答题前,考生先将自己的姓名、准考证号码填写清楚,将条形码准确粘贴在条形码区域内。
2.答题时请按要求用笔。
3.请按照题号顺序在答题卡各题目的答题区域内作答,超出答题区域书写的答案无效;在草稿纸、试卷上答题无效。
4.作图可先使用铅笔画出,确定后必须用黑色字迹的签字笔描黑。
5.保持卡面清洁,不要折暴、不要弄破、弄皱,不准使用涂改液、修正带、刮纸刀。
Ⅰ. 单项选择1、Don't throw away the clothes that you ____________. Y ou can give them to children in the poor villages.A.wear B.don't wear C.are wearing D.won't wear2、Ann always goes over her exercises to ________ there are no mistakes.A.set up B.make sure C.find out D.talk about3、---How is your close friend Katie?---Oh, she’s moved to another city, so I’ve ever seen her since then.A.completely B.hardly C.simply4、--- I don’t know ______. --- She is a doctor.A.how is your sister B.how your sister isC.what is your sister D.what your sister is5、What are the people in the US ____ to do when they meet ____?A.supposed; at the first time B.supposed; for the first timeC.expected; in the first time D.be supposed; for the first time6、—Jane,is this your bag?—No. bag is pink.A.I B.My C.Me D.Mine7、To protect the environment, supermarkets don’t ________ free plastic bags to shoppers.A.take B.show C.provide D.carry8、It _____ an hour to like someone, and a day to love someone, but it needs a lifetime to forget someone. Be kind to others. They will bring happiness to you.A.costs B.takes C.spends9、--Excuse me, I wonder _____ I can pay for the new shoes?--You can pay by using wechat or Alipay(支付宝).A.whether B.when C.how D.why10、—I don’t know how to reduce stress from my studi es.—I think you can _____ a hobby. It will make you relaxed.A.take off B.take up C.take inⅡ. 完形填空11、A Faithful FatherMy husband kissed the baby’s cheek, and hugged me goodbye, then rushed out of the door, into his busy day.I stayed seated, thinking, with the baby in my arms. The 1 ran into memories of the mornings with my husband rushing out of the door to meet the responsibility of life. It was only a small jump to thoughts of my own 2 .My father brought me up alone. As I looked 3 I could see how much of a family man my dad was. He went to work every morning and returned home every evening. He provided food, clothing, warmth, and protection. He was a faithful father.Setting the baby down, I telephoned my father. I had just 4 the importance of the daily life going on around us, and that it needed to be recognized.“Hi, Dad.”I said, 5 back tears.“Hey, Bud. How are you?” worry was in his voice.“Fine, I’m just calling to say … thank you.” I got it out before I cried.“What for?”“For getting up and going to work every morning of my life. Now that I have my own childand I see my husband doing the same, I just wanted to thank you for being faithful.”There was 6 for a moment, and with a small tremble(颤抖) in his voice he sa id, “You’re welcome, Bud.”I don’t remember much of the call, but the tremble in my father’s voice, I will never 7 . There are those who are known for their heroic achievements, but the common everyday fathers are the true heroes. I’m8 that my father was one of them.1.A.thoughts B.ideas C.imaginations D.opinions2.A.mother B.father C.husband D.son3.A.ahead B.around C.forward D.back4.A.wondered B.understood C.realized D.known5.A.taking B.holding C.putting D.pushing6.A.music B.noise C.sound D.silence7.A.miss B.mention C.forget D.expect8.A.thankful B.surprised C.doubtful D.satisfiedⅢ. 语法填空12、根据短文内容及所给提示,补全文中单词或用所给单词的正确形式填空。
听力中经常出现的12组场景词归纳总结

听力中经常出现的12组场景词归纳总结1 学校(1)Lecture 可能表示讲座或者研讨会的意思,相对应的讲座-----speaker / lecturer;研讨会-----seminar(研究会, 讨论发表会)在lecture中topic对应的形容词为interesting . Content对应的形容词为difficult(2) 家庭作业work assignment作业形式group discussion ; presentation(演示) ; paper(美)/essay(英) 学期中的小论文; dissertation(美)/thesis(英) /project(工科) 毕业论文。
时间问题on time 准时; deadline最终期限; due预期的(be due on)定律无论A怎么样抱怨作业的种种情况( too much ; too difficult ; stay up 通宵;polish 润色). 最后的结果始终是作业会按时交上的!(3) 考试种类exam ; test; quiz; contest.分数mark(英) ; grade (美) ; score等级男的pass 或者fail;女的merit(良好) 或者distinction(优秀,卓越)大小考Mid-term exam 期中考;final exam 期末考;oral test 口语考试;m ake up for …..(某学科) course 补考考试临近draw on / draw nearly/ in sight of;考试推迟delay / defer/ postpone / put off/ hold up(推迟,拖延,hold up另有抢劫的意思);考试取消cancel / be off常见考试名称TOEFL (托福)/ GRE / IELTS (雅思) / GMAT / LSAT学位名称BS (Bachelor Science) 理学学士学位;BA( Bachelor Arts) 文学学士学位;BBA (Bachelor Business administration) 工商管理学士学位;MS(Master Science) 理学硕士学位;MA(Master Arts) 文学硕士学位;MBA (Master Business administration) 工商管理硕士学位老师的称呼DR.(在听力中泛指医生或者老师.) professor年级学生大一freshman 大二sophomore 大三junior 大四senior上课上课attend a class 旷课miss a class 逃课skip/cut a class.学期term(英) ; semester(美)两学期制; trimester (美)三学期制.助教TA: Teaching Assistant助研RA: Researching Assistant2 旅游基本词汇travel agency旅行社/ agent 代理人/ arrange a trip (安排一次旅行) / accommodation住所/ tour guide 导游/ destination目的地旅游景点(1) sightseeing 观光scenic resort风景名胜/ place of interests(名胜古迹)/ historic relics(历史遗迹);(2) amusement park 游乐场;(3) theme park 主题公园住处Hotel旅馆/Motel汽车旅馆/ Inn客栈/ Hostel 青年旅社.3 房子买卖对话A中含有动词call/ring 或者询问inquire/enquire ; X-bedroom house ; advertised 做广告的.那么多半可以确认此次对话是关于买卖房屋的。
Win7旗舰版Windows安全中心打不开的解决方法

Win7旗舰版Windows安全中心打不开的解决方法电脑系统的安全中心是很重要的,就像一个公司的保安系统,如果出现问题就会危及整个系统的安全,而且不及时处理可能还会造成重大损失或麻烦。
那么有win7系统的用户就遇到了这样的情况,安全中心出现了故障。
那么该如何修复解决这个问题呢?现在就让来告诉大家具体的解决方法步骤吧!第一步、先打开电脑系统的运行窗口,并在窗口地址栏中键入services.msc,然后单击回车确认,从而打开电脑服务窗口。
第二步、在打开的服务窗口中,找到右侧窗口中一大排列表的“Security Center”选项,然后双击打开其属性窗口。
第三步、打开属性窗口后,就把“启动类型”设置成自动,并在服务状态中选择为“启动”,最后点击保存即可。
这就是win7系统安全中心出现故障的处理了,如果有用户的安全中心也出现问题了就用这个设置方法来解决吧!Win7旗舰版打不开IE浏览器Inter选项的解决方法:U大侠时间:xx-01-13众所周知,Win7系统内置IE浏览器,可以完美的兼容各种插件,深受广大用户的小。
虽然微软停止了对IE8/IE9/IE10的技术支持,但是用户还是可以升级到IE11的。
升级IE11浏览器后难免会遇到一些小问题,部分win7旗舰版用户在打开Inter选项对IE进行设置的时候出现了点小故障,Inter选项打不开了,怎么回事呢?下面,U大侠就给大家介绍Win7旗舰版打不开IE浏览器Inter选项的解决方法。
解决方法:1、在键盘上按“WIN+R”快捷键,打开运行界面,输入“gpedit.msc”指令,按“回车键”既能打开“本地组策略器”。
2、在“本地组策略器”界面中,依次展开“用户配置”——“管理模块”——“windows组件”——“Inter explorer”——“浏览器菜单”。
点击“浏览器菜单”,在右侧找到并打开“工具菜单:禁用Inter选项”。
Win7系统3、在“工具菜单:禁用Inter选项”界面中,点击“已禁用”选项,按“确定”。
Windows Phone开发入门教程_wdxtub_CodePlane

CodePlane
- 27 - 29 - 29 - 29 - 30 -
WINDOWS PHONE 7 高级主题
传感器 加速计 Compass Gyroscope Vibration 计划任务 不支持的 API 需要注意的 API 限制 后台代理 闹铃与提醒 后台传输与后台音乐 本地数据库 开发流程 Database Schema Upgrades 性能和最佳实践
注册成为学生开发者
为什么需要注册成为学生开发者呢,因为只有注册成功了,才能在市场上发 布应用。针对学生微软提供了一些优惠,例如不用交每年 99 美元的注册费用, 虽然我们不能发布收费的应用,但是有一个市场,让用户去检验我们的应用, 也 很不错了。具体的注册和发布教程可以查看下面这两个网页: /zh-cn/hh678673 /zh-cn/hh678674 都注册好之后,我们就准备开始真正进入 Windows Phone 7 的大门吧!
CodePlane & MAD -4SYSU
Windows Phone 7 开发入门教程
CodePlane
面,并且基于 silverlight 的机制,我们获得了类似 ios 的沙盒的机制,一个应用 程序只能访问自己的东西,相当于每个应用都有自己独立的文件系统。 好了,如果遇到不明白的缩写,上网搜搜吧,相信大家很快就能明白了。
Silverlight 介绍
可能大家对于 silverlight 不甚了解,不过真正做开发的时候,似乎我们也并 不需要特别去在意这个问题, 但是因为我们是在这个上面进行开发,最好还是要 了解一点相关的东西。 Silverlight 是 WPF 的一个子集, 准确的来说, 是一个更加适应 Web 的 WPF 子集。问题又来了,WPF 是什么?能吃么? 不能吃,WPF 的全称是 Windows Presentation Foundation,是微软推出 的基于 Windows Vista 的用户界面框架。这话太空了,总而言之,言而总之, 就是换了一个绘图引擎的图形界面,从原来的底层 API 换成了现在的 DirectX, 并且可以比较容易的实现界面和代码的分离。 好,这才是重点,重点就是界面和代码的分离。无论是 android 的 xml 还 是 ios 的 xib,都是为了解决同一个问题,就是实现 MVC 的模型,MVC 在我看 来的精髓就是各个组件的独立, 可以分别进行开发,而不是像一锅粥一样牵一发 而动全身,现在可以做到后台代码不改变但是界面部分天翻地覆,这就是关键所 在。 言归外传,Silverlight 在 Windows Phone 7 上又是一个比较特别的集合, 大部分是原本 silverlight 的子集,而又根据手机平台的特殊性,加入了一些原 来本不属于 silverlight 的东西,所以对于 silverlight,我们真正用到的并不是其 本身,而是 silverlight for windows phone。再具体一点,我们用这个来做界
owners_说明书

u Fully integrated intrusion, fire, and access control allows users to interface with one system instead of threeu Conettix IP‑based communication option provides high‑speed, secure alarm transport and controlu Eight programmable areas with perimeter and interior partitioningu246 points with flexible configuration options to meet multiple installation requirementsu Your choice of vacuum fluorescent or ATM style user interface keypadsThe D9412GV2 Control Panel provides an integrated solution for intrusion, access control, and fire alarm system applications. The control panel includes a communicator that sends events to selected public switched telephone network (PSTN) or IP network destinations through four programmable route groups. The control panel provides up to 246 individually identified points. Each point:•Accommodates normally‑open (NO) andnormally‑closed (NC) devices with end‑of‑line (EOL)resistor supervision•Is programmable for fire, fire supervisory, or intrusion applications.With the D9412GV2 you can:•Monitor alarm points for intruder or fire alarms while operating user keypads and other outputs •Program all system functions on‑site through a D5200 Programmer or remotely through RemoteProgramming Software (RPS).•Add up to eight doors of access control using theoptional D9210BLC Access Control Interface Module. FunctionsProgrammable Outputs• 2 A alarm power at 12 VDC• 1.4 A auxiliary power at 12 VDC•Four alarm‑output patterns•Programmable bell test•Programmable bell shut‑off timerSystem Response•31 custom point indexes, including fire supervisory •Selectable point response time•Cross point capability•Fire alarm verification•Fire inspector’s local test•Watch mode•Scheduled events (skeds) arm, disarm, bypass andunbypass points, control relays, control authoritylevels, and control door accessUser Interface•Supervision of up to eight keypads (up to 32unsupervised keypads can be used)•Custom keypad text•Full function command menu including customfunctions•Authority by area and 16‑character name for eachuser•14 custom authority levels control user’s authority to change, add, or delete passcodes or access controlcredentials; to disarm or bypass points; and to start system testsNoticeUse at least one keypad in each system.Area ConfigurationsArea programming offers a wide selection of different system configurations. Each area is assigned an account number to define annunciation, control, and reporting functions. Multiple areas can be linked to a shared area which is automatically controlled (hallway or lobby). Area arming can be conditional on other areas (master or associate).Two Man RuleTwo Man Rule provides added security by requiring:•Two people present at opening•Two unique passcodes on the same keypad to disarm an areaWithout the second passcode, the system denies entry.Early AmbushEarly Ambush requires two passcode entries on the same keypad. Enter the same passcode twice or have two unique passcodes, depending on the configuration. The first entry disarms the area and the second entry stops a timer programmed to send a duress event. If the second entry does not occur within the programmed time, the system generates a duress event. Early Ambush allows users to inspect the premises and use the system to confirm that the area is safe to enter, providing added security.Easy Exit ControlThe D9412GV2 Control Panel changes from one armed state to another armed state without disarming. For example, if you change the state from Master Arm to Perimeter Arm, the control panel complies and reports the change. Easy Exit Control reduces the number of keystrokes, simplifying system operation. Programmable Passcode‑controlled Menu ListThe system prompts users to enter a passcode prior to viewing the keypad menu. The keypad display shows the user the menu options allowed according to the user’s authority level. Passcode-controlled menus provide users only with the options and information pertinent to them, simplifying system operation. Passcode Follows ScopeUse Passcode Follows Scope to restrict passcode arming and disarming to the keypad's immediate local area, even if the keypad can report events from other areas. Passcode Follows Scope simplifies the arming and disarming procedure without limiting any other keypad capabilities.Invisible Walk TestA menu item allows the user to test invisible 24‑hour points within the scope of the keypad without sending a report to the central station.Door‑Activated Custom FunctionA custom function activates when user credentials are presented to a D9210B door controller's reader. The custom function behaves as though the user performed a function at the keypad associated with the door controller.PasscodesUser passcodes contain three to six digits. Assign each user one of 14 customized authority levels in each area. Restrict passcodes to operate only during certain times.The Two Man Rule and Early Ambush options require two passcodes, providing additional security in financial establishments such as banks. CommunicationsThe D9412GV2 Control Panel prioritizes and sends reports in BFSK or Modem IIIa2 communications formats to four route groups. Each group has a programmable primary and backup destination.The D9412GV2 works with the Conettix D6600 Communications Receiver/Gateway using a Conettix DX4020 Network Interface Module. When using aDX4020, the D9412GV2 has programmable anti-replay anti-substitution features.The Modem IIIa2 Communications Format, available with Bosch receivers, adds central station reporting capabilities such as:•Individual point numbers and text•Opening or closing reports by area number •Remote programming attempts•Diagnostic reports•User name reportsSecurity and Fire DetectionThe D9412GV2 Control Panel provides eight on‑board points, and up to 238 additional off‑board points (depending on model and expansion interfaces). You can program individual points to monitor all types of burglar alarms, fire alarms, and supervision devices. Event LogThe event log stores up to 1,000 local and transmitted events. The event log includes time, date, event, area, point, and user number. View the event log from a keypad or use RPS to remotely retrieve event information. RPS operators can retrieve events periodically using one phone call, rather than receiving several calls each day. When the event log reaches a programmed threshold of stored events, it can send an optional report to a receiver.Access ControlThe D9412GV2 provides custom door strike, point shunt and auto disarming response by area. There are 14 panel‑wide access levels with both manual and scheduled control.Store, view, or print access events such as:•Access granted•No entry•Request-to-enter•Request-to-exitScheduled Events (Skeds)The internal clock and calendar start individually scheduled events (skeds). Skeds perform functions such as arm or disarm, relay control, or point bypassing. The D9412GV2 Control Panel offers:•40 scheduled events with up to 25 different functions •Eight opening windows and eight closing windows •Eight user windows•Day-of-week, date-of-month, or holiday only schedules •Four holiday schedules of 366 days each (leap year) Fire TestWhen a user activates Fire Test Mode, the control panel suppresses all reports to the central station. The keypad and annunciator show all testing data. An automatic sensor reset feature saves time; you do not need to reset the sensors manually. At the end of test, the keypad shows the number of untested points. Programming, Diagnostics and ControlsUsers can program on-site with a D5200 Programmer, or program remotely through RPS. A programmable system passcode prevents unauthorized remote programming.D9412GV2 Control Panels accommodate up to four separate telephone numbers for primary, alternate, and backup receivers for automatic test reports. When resetting alarms or arming or disarming a system, the user is identified by name and number.Installation/configuration notesCompatible ProductsKeypads D1260 Series Keypads(D1260, D1260W, D1260R, D1260BLK,D1260B)D720 Series Keypads(D720, D720W, D720R, D720B)D1255 Series Keypads(D1255, D1255W, D1255R, D1255B,D1255RB)D1256 and D1256RB Fire KeypadsD1257 and D1257RB Remote Fire AlarmAnnunciatorsD279A Independent Zone ControlDetectors D278S Four‑wire Addressable Detector Base,12 VDCD285/TH Photoelectric Smoke Detector HeadsD298S Addressable Detector Base, 24 VDCD7050 Series Addressable PhotoelectricSmoke and Smoke Heat Detector HeadsF220‑B6PM/S Addressable Detector Baseswith POPITsMX250 Series Smoke DetectorsMX775i Addressable PIR DetectorMX794i Long Range Multiplex PIR DetectorMX934i Addressable PIR DetectorMX938i Addressable PIR DetectorZX776Z PIR DetectorZX794Z Long Range PIR DetectorZX835 TriTech Microwave/PIR DetectorZX935Z PIR DetectorZX938Z PIR DetectorZX970 PIR/Microwave DetectorBosch conventional detectors, including BlueLine, seismic, PIR, TriTech PIR Microwave,photoelectric, heat, and smoke. Enclosures D8103 Universal EnclosureD8108A Attack‑resistant EnclosureD8109 Fire EnclosureD9101 Fire Enclosure (large)Magnetic Contacts Bosch magnetic contacts include recessed,terminal connection, miniature, overheaddoor,and surface mount.Modules C900V2 Dialer Capture ModuleD113 Battery Lead Supervision ModuleD125B Dual Class B Initiating ModuleD127 Reversing Relay ModuleD129 Class A Initiating ModuleD130 Auxiliary Relay ModuleD185 Reverse Polarity Signaling ModuleD192C Notification Appliance Circuit ModuleD192G Notification Appliance Circuit ModuleD928 Phone Line SwitcherD5060 MUX ProgrammerD8125 POPEX Point ExpanderD8128D OctoPOPIT Eight‑point ExpanderD8125MUX Point ExpanderD8125INV Wireless Interface ModuleD8129 Octo‑relay ModuleD8130 Door Release ModuleD9127 Series POPIT ModulesD9131A Parallel Printer Interface ModuleD9210BLC Access Control Interface ModuleDS7432 Eight‑input Remote ModuleDS7457i Series Single‑zone Multiplex InputModulesDS7460i Two‑input ModuleDS7461i Single‑input Multiplex ModuleDS7465i Input and Output ModuleDX4010i RS‑232 Serial Interface ModuleConettix DX4020 Network Interface ModuleICP-SDI-9114 SDI SplitterPeripheral Hardware rvm4c Remote Video Module Programming D5200 Series ProgrammersRPS or RPS‑LITE Remote ProgrammingSoftwareReaders ARD‑R10 iCLASS Mullion ReaderARD‑R40 iCLASS Switchplate ReaderARD‑RK40‑09 iCLASS PIN ReaderARD‑VSMART iCLASS ReaderD8201/W Series Low‑profile ReadersD8203/W Series Mullion Proximity ReadersD8223 Prox Pro ReaderD8224 Mullion ReaderD8224‑SP Switch Plate ReaderD8225 Mini Mullion ReaderD8227 Insert Card ReaderD8301/W Series Low‑profile ProximityReadersD8302 Vandal‑resistant ReaderD8303/W Series Mullion Proximity ReadersD8304/W Series Extended Range ProximityReadersWP644 Series Waterproof Pass‑throughReadersSAFECOM Radio SC2104 Series Slave Communicators Communicators SC3100 Series Data Transfer RadioCommunicatorsSC4000 Series Full Data Transfer RadioCommunicatorCommercialWirelessISW‑D8125CW Commercial Wireless Interface Products ISW‑EN7280 Serial ReceiverISW‑EN4200 Serial ReceiverISW‑EN4204R LED ReceiverISW‑EN4216R LCD ReceiverISW‑EN4016SK Survey ReceiverISW‑EN5040‑T High‑power RepeaterISW‑EN1210 Universal Transmitter(Single‑input)ISW‑EN1210EOL Universal Transmitter withEOL ResistorISW‑EN1210SK Survey TransmitterISW‑EN1210W Door‑Window Transmitter withReed SwitchISW‑EN1215EOL Universal Transmitter withWall Tamper and EOL ResistorISW‑EN1215WEOL Door‑Window Transmitterwith Wall Tamper, Reed Switch, and EOLResistorISW‑EN1223D Water‑resistant PendantTransmitter (Double‑button)ISW‑EN1223S Water‑resistant PendantTransmitter (Single‑button)ISW‑EN1223SK Survey Pendant TransmitterISW‑EN1233D Necklace Pendant Transmitter (Double‑button)ISW‑EN1233S Necklace Pendant Transmitter (Single‑button)ISW‑EN1235D Beltclip Pendant Transmitter (Double‑button)ISW‑EN1235S Beltclip Pendant Transmitter (Single‑button)ISW‑EN1235DF Fixed‑location Transmitter (Double‑button)ISW‑EN1235SF Fixed‑location Transmitter (Double‑button)ISW‑EN1242 Smoke Detector‑Transmitter ISW‑EN1247 Glass‑break Sensor Transmitter ISW‑EN1249 Billtrap TransmitterISW‑EN1260 PIR Motion Sensor Transmitter (Commercial and High‑end Domestic Applications)ISW‑EN1261HT PIR Motion Sensor Transmitter (High‑traffic Areas)ISW‑EN1262 PIR Motion Sensor Transmitter (Residential and Low‑traffic Commercial Applications)ISW‑EN1265 PIR Motion Sensor Transmitter (Ceiling‑mount Applications)Technical specifications CommunicationsEnvironmental ConsiderationsNumber of…Power RequirementsOrdering informationD9412GV2 Fire and Burglar KitContains one PCB, one dual battery harness, two telephone cords, one telephone line switcher, one transformer, and one fire enclosure.Order number D9412GV2-BAccessoriesD110 Tamper SwitchScrew‑on tamper switch that fits all enclosures. Shipped in packages of two.Order number D110ICP‑EZTS Dual Tamper SwitchCombination tamper switch with a wire loop for additional tamper outputs.Order number ICP-EZTSD101 Lock and Key SetShort-body lock set with one key supplied. Uses the D102 (#1358) replacement key.Order number D101D122 Dual Battery HarnessHarness with circuit breaker. Connects two batteries to a compatible control panel.Order number D122D122L Dual Battery Harness with Long LeadsColor-coded harness with circuit breaker and leads measuring 89 cm (35 in.). Connects 12 V batteries to compatible control panels.Order number D122LD137 Mounting BracketUsed to mount accessory modules in D8103, D8108A, and D8109 enclosures.Order number D137D138 Mounting Bracket, Right AngleUsed to mount accessory modules in D8103, D8108A, and D8109 enclosures.Order number D138D928 Dual Phone Line SwitcherAllows the control panel to operate over and supervise two separate phone lines. Only one D162 phone cord is supplied. Two additional D161 or D162 phone cords are required.Order number D928D126 Standby Battery (12 V, 7 Ah)A rechargeable sealed lead‑acid power supply used as a secondary power supply or in auxiliary or ancillary functions.Order number D126D1218 Battery (12 V, 18 Ah)A 12 V sealed lead‑acid battery for standby and auxiliary power with two bolt‑fastened terminals. Includes hardware for attaching battery leads or spade connectorsOrder number D1218D1224 Battery (12 V, 26‑28 Ah)A 12 V sealed lead‑acid battery for standby and auxiliary power with two bolt‑fastened terminals. Includes hardware for attaching battery leads or spade connectors.Order number D1224D1238 Battery (12 V, 38 Ah)A 12 V sealed lead-acid battery for standby and auxiliary power with two bolt‑fastened terminals. Includes hardware for attaching battery leads or spade connectors.Order number D1238D1640 TransformerSystem transformer rated at 16.5 VAC, 40 VA.Order number D1640D1640-CA TransformerFor use in Canada. System transformer rated at16.5 VAC, 40 VA.Order number D1640-CAD8103 EnclosureGrey steel enclosure measuring 41 cm x 41 cm x 9 cm(16 in. x 16 in. x 3.5 in.).Order number D8103D8108A Attack Resistant EnclosureGrey steel enclosure measuring 41 cm x 41 cm x 9 cm(16 in. x 16 in. x 3.5 in.). UL Listed. Includes lock andkey set. Requires the D2402 Mounting Plate.Order number D8108AD8109 Fire EnclosureRed steel enclosure measuring 40.6 cm x 40.6 cm x 8.9cm (16 in. x 16 in. x 3.5 in). UL Listed. Includes a lockand key set.Order number D8109D9101 Fire EnclosureLarge red enclosure for fire applications. It isconstructed of 16 gauge (1.5 mm) cold rolled steeland measures (H x W x D) 37.4 in x 23.5 in. x 2.4 in.(94.8 cm x 59.6 cm x 10.5 cm).Order number D9101D9002‑5 Mounting SkirtMounts inside D8103, D8108A, and D8109 enclosures.Can accept up to six standard 7.62 cm x 12.7 cm (3 in.x 5 in.) cards.Order number D9002-5Software OptionsRPS Kit (LPT)Account management and control panel-programmingsoftware with LPT connection.Order number D5500C-LPTRPS Kit (USB)Account management and control panel programmingsoftware with USB security key (dongle).Order number D5500C-USBRepresented by:Americas:Europe, Middle East, Africa:Asia-Pacific:China:America Latina:Bosch Security Systems, Inc. 130 Perinton Parkway Fairport, New York, 14450, USA Phone: +1 800 289 0096 Fax: +1 585 223 9180***********************.com Bosch Security Systems B.V.P.O. Box 800025617 BA Eindhoven, The NetherlandsPhone: + 31 40 2577 284Fax: +31 40 2577 330******************************Robert Bosch (SEA) Pte Ltd, SecuritySystems11 Bishan Street 21Singapore 573943Phone: +65 6571 2808Fax: +65 6571 2699*****************************Bosch (Shanghai) Security Systems Ltd.201 Building, No. 333 Fuquan RoadNorth IBPChangning District, Shanghai200335 ChinaPhone +86 21 22181111Fax: +86 21 22182398Robert Bosch Ltda Security Systems DivisionVia Anhanguera, Km 98CEP 13065-900Campinas, Sao Paulo, BrazilPhone: +55 19 2103 2860Fax: +55 19 2103 2862*****************************© Bosch Security Systems 2013 | Data subject to change without notice 2492389899 | en, V1, 01. Oct 2013。
23年十二月四级试卷

23年十二月四级试卷一、写作(15%)题目:The Importance of Lifelong Learning。
要求:1. 阐述终身学习的重要性;2. 给出一些实现终身学习的途径;3. 字数不少于120字,不多于180字。
二、听力理解(35%)Section A.Directions: In this section, you will hear three news reports. At the end of each news report, you will hear two or three questions. Both the news report and the questions will be spoken only once. After you hear a question, you must choose the best answer from the four choices marked A), B), C) and D).News Report 1.1. A) A new species of plant was discovered in the Amazon rainforest.B) A scientific research project in the Amazon rainforest was completed.C) A large - scale deforestation in the Amazon rainforest was halted.D) A new conservation area was established in the Amazon rainforest.Question 1: What is the main news about the Amazon rainforest?Question 2: What is the significance of this event according to the report?News Report 2.2. A) The number of international students in a certain country has increased significantly.B) A new policy to attract international students was introduced in a country.C) Some international students faced difficulties in adapting to a new educational system.D) A university in a country offered special courses for international students.Question 1: What is the news mainly about?Question 2: What is the possible impact of this situation?News Report 3.3. A) A new technology for reducing air pollution was developed.B) A city launched a campaign to improve air quality.C) The air quality in a certain city reached a new low.D) A research showed the main sources of air pollution in a city.Question 1: What is the news about?Question 2: What measures might be taken according to the report?Section B.Directions: In this section, you will hear two long conversations. At the end of each conversation, you will hear four questions. Both the conversation and the questions will be spoken only once. After you hear a question, you must choose the best answer from the four choices marked A), B), C) and D).Conversation 1.1. A) They are discussing a travel plan.B) They are talking about a new movie.C) They are choosing a restaurant for dinner.D) They are planning a party.Question 1: What are the two speakers mainly doing?Question 2: What is the man's preference?Question 3: What does the woman worry about?Question 4: How will they make the final decision?Conversation 2.2. A) She is applying for a job.B) She is preparing for an exam.C) She is doing a research project.D) She is having a meeting with her supervisor.Question 1: What is the woman doing?Question 2: What difficulties does she encounter?Question 3: How does the man offer to help?Question 4: What is the woman's attitude towards the man's help?Section C.Directions: In this section, you will hear three passages. At the endof each passage, you will hear three questions. Both the passage and the questions will be spoken only once. After you hear a question, you must choose the best answer from the four choices marked A), B), C) and D).Passage 1.1. A) The history of a famous university.B) The development of modern education.C) The characteristics of a good teacher.D) The importance of educational reform.Question 1: What is the passage mainly about?Question 2: What qualities should a good teacher have according to the passage?Question 3: How can a teacher keep up with the development of education?Passage 2.2. A) A new trend in fashion.B) The influence of social media on fashion.C) The history of a particular fashion style.D) How to choose the right clothes for different occasions.Question 1: What is the passage mainly about?Question 2: How does social media affect fashion according to the passage?Question 3: What advice does the passage give to fashion lovers?Passage 3.3. A) The benefits of reading books.B) The popularity of e - books.C) Different reading habits among people.D) How to improve reading speed.Question 1: What is the passage mainly about?Question 2: What are the benefits of reading books mentioned in the passage?Question 3: How can people develop good reading habits?三、阅读理解(35%)Section A.Directions: In this section, there is a passage with ten blanks. You are required to select one word for each blank from a list of choices given in a word bank following the passage. Read the passage through carefully before making your choices. Each choice in the word bank is identified by a letter. Please mark the corresponding letter for each item on Answer Sheet 2. You may not use any of the words in the word bank more than once.The Internet and Our Lives.The Internet has become an indispensable part of our lives. It has_(1)_ changed the way we communicate, learn, and work. For communication, we can now easily connect with people all over the world through various_(2)_ such as email, instant messaging, and social media platforms. In terms of learning, there are countless online courses available, allowing people to study _(3)_ at their own pace. When it comes to work, many companies are now _(4)_ remote work options, which are made possible by the Internet.However, the Internet also brings some problems. For example, the _(5)_ of false information can mislead people. Also, some people may become addicted to the Internet, which can _(6)_ their real - life relationships. Moreover, there are concerns about online _(7)_ such as hacking andidentity theft.Despite these problems, the Internet continues to develop and evolve. New technologies are being developed to address these issues, such as more advanced _(8)_ systems to filter out false information. And people are also becoming more aware of the importance of using the Internet _(9)_. In conclusion, the Internet has a profound _(10)_ on our lives, and we need to make the best use of it while minimizing its negative impacts.Word Bank:A) significantly.B) means.C) independently.D) offering.E) spread.F) affect.G) security.H) verification.I) impact.J) responsible.Section B.Directions: In this section, you will read several passages. Each passage is followed by some questions or unfinished statements. For each of them there are four choices marked A), B), C) and D). You should decide on the best choice and mark the corresponding letter on Answer Sheet 2.Passage 1.The concept of "green building" has been around for some time, but itis becoming increasingly important in today's world. Green buildings are designed to be environmentally friendly in every aspect, from the materials used in construction to the energy sources that power them.One of the key features of green buildings is their use of sustainable materials. For example, instead of using traditional concrete, which has a high carbon footprint, green buildings may use recycled materials or materials that are sourced locally. This not only reduces the environmental impact of the building but also supports local economies.Another important aspect of green buildings is energy efficiency. They are designed to use as little energy as possible, through features such as efficient insulation, energy - saving lighting, and smart thermostats. Somegreen buildings even generate their own energy through renewable sources such as solar panels or wind turbines.1. What is the main idea of this passage?A) The history of green building.B) The importance of green building.C) The features of green building.D) The future of green building.2. According to the passage, what is an advantage of using sustainable materials in green buildings?A) It is cheaper.B) It is more beautiful.C) It reduces environmental impact and supports local economies.D) It is easier to construct.3. Which of the following is NOT an energy - saving feature of green buildings?A) Efficient insulation.B) Traditional lighting.C) Smart thermostats.D) Solar panels.Passage 2.The sharing economy has emerged as a new economic model in recent years. It is based on the idea of sharing resources, such as cars, homes, and tools, among individuals. Platforms like Airbnb and Uber are well - known examples of the sharing economy.The sharing economy has several benefits. For consumers, it offers more choices and often lower prices. For example, instead of staying in a hotel, a traveler can choose to stay in a private home through Airbnb, which maybe more affordable and offer a more unique experience. For providers, it allows them to earn extra income by sharing their under - utilized resources.However, the sharing economy also faces some challenges. One of themain challenges is regulation. Since the sharing economy operates in a different way from traditional industries, existing regulations may not be applicable. This can lead to issues such as safety concerns and unfair competition.1. What is the sharing economy based on?A) Buying new resources.B) Sharing resources among individuals.C) Producing more resources.D) Selling unused resources.2. What are the benefits of the sharing economy for consumers?A) Only lower prices.B) More choices and often lower prices.C) Only more choices.D) Higher quality services.3. What is one of the main challenges faced by the sharing economy?A) Lack of users.B) High cost.C) Regulation.D) Technical problems.Passage 3.Artificial intelligence (AI) has made remarkable progress in recent years. It has been applied in various fields, such as healthcare, finance, and transportation.In healthcare, AI can be used to assist in diagnosis. For example, it can analyze medical images, such as X - rays and MRIs, to detect diseasesat an early stage. In finance, AI can be used for fraud detection. It can analyze large amounts of financial data to identify suspicious transactions. In transportation, AI is being used in self - driving cars. These cars can sense their surroundings and make decisions to drive safely.However, the development of AI also raises some concerns. One concernis the potential loss of jobs. As AI can perform many tasks that were previously done by humans, there is a fear that many jobs will be replaced. Another concern is ethics. For example, how should AI be programmed to make ethical decisions?1. In which fields has AI been applied?A) Only healthcare.B) Healthcare, finance, and transportation.C) Only finance.D) Only transportation.2. What can AI do in healthcare?A) Only treat diseases.B) Assist in diagnosis by analyzing medical images.C) Replace doctors.D) Manage hospitals.3. What are the concerns about the development of AI?A) Only the potential loss of jobs.B) Only ethics.C) The potential loss of jobs and ethics.D) None of the above.Section C.Directions: There are 2 passages in this section. Each passage is followed by some questions or unfinished statements. For each of them there are four choices marked A), B), C) and D). You should decide on the best choice and mark the corresponding letter on Answer Sheet 2.Passage 1.A new study has found that reading books can have a positive impact on our mental health. The study surveyed a large number of people and foundthat those who read books regularly were less likely to suffer from depression and anxiety.The researchers believe that reading books can help us to escape from our daily stressors. When we read a book, we enter into a different world, and this can give our minds a break from the problems in our real lives. Additionally, reading can also improve our cognitive abilities, such as our memory and concentration.However, the type of book we read may also matter. For example, reading self - help books may be more directly beneficial for those who are struggling with mental health issues, while reading fiction can alsoprovide an emotional outlet and help us to understand different perspectives.1. What did the new study find?A) Reading books has no impact on mental health.B) Reading books can have a positive impact on mental health.C) Reading books can cause mental health problems.D) Only reading self - help books is good for mental health.2. Why do researchers believe reading books can help with mental health?A) Because it can make us more intelligent.B) Because it can make us forget our real - life problems.C) Because it can help us to face our problems directly.D) Because it can give us more stress.3. What does the passage say about the type of book we read?A) It doesn't matter what type of book we read.B) Only self - help books are beneficial.C) Different types of books may have different benefits.D) Fiction books are not good for mental health.Passage 2.The popularity of e - sports has been on the rise in recent years. E - sports are competitive video games that are played at a professional level.One of the reasons for the growth of e - sports is the increasing availability of high - speed Internet. This allows players to compete against each other in real - time, no matter where they are located. Another reason is the development of more sophisticated video games that require a high level of skill and strategy.E - sports events are now attracting large audiences, both in person and online. These events are often sponsored by major companies, which see the potential for marketing to the young and tech - savvy demographic.1. What are e - sports?A) Traditional sports played with electronics.B) Competitive video games played at a professional level.C) Video games played for entertainment only.D) Sports that use electronic equipment.2. What are the reasons for the growth of e - sports?A) Only the increasing availability of high - speed Internet.B) Only the development of more sophisticated video games.C) The increasing availability of high - speed Internet and the development of more sophisticated video games.D) None of the above.3. Why are e - sports events attracting major sponsors?A) Because they are cheap to organize.B) Because they can reach a young and tech - savvy demographic.C) Because they are not very popular.D) Because they are easy to manage.四、翻译(15%)题目:中国的城市化(urbanization)将会充分释放潜在内需(domestic demand)。
专题06网络安全 -备战2022年中考英语阅读理解热点话题模拟练

06 网络安全As we know, the time of 5G technology(技术)is coming. Recently, there's a lot of information about 5G. But what is this technology and how might it bring to our lives?What is 5G?5G means the fifth generation(第五代)mobile networks(网络), a better technology than 4G. And we know, 4G comes after 3G and makes the network run faster than 3G.When will 5G come to our life?Before we can all use 5G, there must be a new system(系统)for 5G to work. In the USA, some cities will first use 5G this year. Experts say it will take a few more years or even longer to reach every place. In China, a few cities are using 5G now. And more and more cities will join this group: Next year, 5G will become national, even in the countryside.What can 5G do?Experts say 5G will help to build future "smart cities" with the help of sensor networks(传感器网络). Such networks will be able to help the police with the traffic. They can help us know what’s happening in our homes when we are at work. They can even help to made it possible for doctors to perform an operation(手术)far away.________In the future, more information and more kinds of information will be travelling across 5G networks. Much of the information could be about persons, businesses or government organization(政府组织). So we can see the wider (更广泛地)use of a 5G network means any mistake of the system would cause serious results. Then they may bring problems of public security(安全)and world economic(经济)activity.1.According to the passage, 5G is ________.A.a kind of phone B.a kind of computer C.a kind of network D.a kind of website(网站)2.The underlined word “They” refers to ________.A.Experts B.The police C.Doctors D.The networks3.Which of the following is NOT mentioned about “smart cities” in this passage?A.House building. B.Traffic. C.Home security. D.Operations.4.The underlined word “national” in the passage means “________” in Chinese.A.民族的B.国立的C.全国性的D.普通的5.Which sentence is the best for the place ________A.Who will use 5G? B.Why will 5G be popular?C.How will people use 5G? D.What are the security problems?Passage2The night of Nov.3 was very special to Australian tennisplayer Ashleigh Barty,23. She won her first single title(单打冠军)at the 2019 Women's Tennis Association (WTA) Finalsin Shenzhen. Barty took home a record $4.42 million (31million yuan) prize for the title, the biggest prize in tennis.She has held the WTA World No.1 title for 15 weeks.becoming the first Australian woman to do so.China has built the world's largest high-speed rail network,which is still expanding(扩张).Last year, the total length ofthe network reached 29,000 kilometers. The trains haveattracted millions of travelers and greatly reduced travelingtime around the country. For example, travel time fromBeijing to Shanghai has been reduced from ten hours to fivehours. China is also sharing this technology with many othercountries.Over the past decades, many people have made greatcontribution(贡献) to China’s development, helping itgrow through their hard work. On Sept. 29, ahead ofNational Day, Chinese President Xi Jinping presentednational medals and honorary titles(荣誉称号) to some ofthese contributors,, including thirty-six Chinese citizens andsix foreigners. President Xi helped them put on the medalsand shook hands with them.Sept 16 to 22 is China's sixth annual Cyber Security Week(网络安全周). An opening ceremony and major activitieswere held Tianjin. First held in 2014, the event aims toremind people of the importance of fighting online threats(威胁)and cyber attacks. The theme of this year's event is"cyber security for the people and by the people". One of thegoals of this year’s event is to teach people how to protecttheir personal data(数据).6.About Ashleigh Barty, which of the following is TRUE?A.She won a single title at WIA Finals in Shenzhen, China last year.B.She got a prize of 3,100,000 yuan for her first single title at WTA.C.She has held the WTA World No.1 title for more than one year.D.She was the first Austrian woman to win the single title at WIA.7.From the above reading, we learn that _________.A.the total length of the network reached 29,000 meters last year.B.China has got the largest high-speed rail network in the world.C.it only took 5 hours from Shanghai to Shenzhen by high-speed train.D.China shares the high-speed rail technology with few other countries.8.According to the passage, how many people were awarded national metals and honorary titles? A.38 B.36 C.6 D.42 9.According to the passage.the purpose of Cyber Secuity Week is to _________.A.hold a wonderful opening ceremony and different kinds of activities.B.help people know that it is important to fight online threats and cyber attacks.C.help people know what is cyber secuity and how to protect themselves.D.teach people how to protect their personal data.Since May 12, a computer virus named WannaCry has infected (感染) more than 300,000computers in over 150 countries, according to Reuters.Wannacry is spread by using a weakness in Microsoft's Windows operating system. Once the virus gets into the computer, it locks all the papers and asks the user for money to unlock them. At first, it asks for $300, but if the user doesn't send the money in 72 hours, the price doubled. Papers are locked forever if the user doesn't pay in seven days.The virus has brought bad results. For example, in the UK, the virus left the country’sNational Health Service in a mess. Some hospitals had to cancel patient appointments(预约), reported The Telegraph. In China, the virus has hit thousands of computers, according to Qihoo360. One of the most hard-hit groups in China were university users. Many students' graduation papers were locked. They felt nervous and frightened. Also many gas stations were seriously hit, and the payment syst em didn’t work.WanaCry is the latest example of the cyber security(网络安全) problem. Matthew Hickey, who set up the security company Hacker House, said, "The attack is not surprising. It shows that many organizations do not use updates(更新) fast enough. Accor ding to a survey, nearly half of the people said, “We are not satisfied with the way software updates work.”As China Daily wrote, “We can’t completely protect our computers against these kinds of viruses, as this cat and mouse game will continue forever. The best choice for most users is to take care online and always install(安装)software updates.”10.What is WannaCry?A.A video game. B.A computer software. C.A computer virus. D.A TV programme.11.If your papers are locked by Wannacry, how much do you need to pay if you don’t send the money in 72 hours? A.$150. B.$300. C.$600. D.$900.12.According to the passage, the writer shows the bad results by ________.A.giving reasons B.giving examples C.comparing computers D.comparing numbers 13.From the last two paragraphs, we can know that________.A.Matthew Hickey thinks the attack on computers is very surprisingB.all the people are pleased with the way software updates workC.the computers can be completely protected against these virusesD.we should take care online and update software fast enoughPassage4Slowly but surely, we’re moving closer and closer to 5G world. From smart-home security to self-driving cars, all the internet-connected devices(装置)in your life will be able to talk to each other at lightning-fast speeds. Objectively speaking, the fastest 4G download speeds in the U.S. top out at an average of 19.42 Mbps. But by comparison 5G promises gigabit(千兆)speeds.“5G is one of those signs, along with artificial intelligence(人工智能), of this coming data age.” said Steve Koenig, senior director of market research for the Consumer Technology Association. The self-driving vehicle is a great emblem of this data age,and that is to say, it is a sign of time, because with one single task, driving, you have large amounts of data coming from the vehicle itself, and a variety of sensors(传感器)are collecting a lot of information to model its environment as it moves. It’s pulling in data from other vehicles about road conditions. It could be weather information, but also connected infrastructure construction(基础设施建设). There’s lots of data behind that task, which is why we need high speed.Augmented reality glasses(实境眼镜)and virtual headset haven’t yet broken the mainstream(主流), but tech companies are joyfully betting that these devices will finally take the place of our smartphones. With 5G, that could actually happen. This is notable because companies such as Apple are reportedly developing AR glasses to give help-or perhaps even replace-smartphones.Ericsson stated at Febr uary’s Mobile World Congress how smart glasses could become faster and lighter with a 5G connection,because instead of being weighed down with components, the glasses could depend on hardware for processing power.But don’t get too excited. There’s still a lot of work to be done, including various ways to make sure the radios play nicely with hardware and infrastructure construction so 5G isn’t used only in big cities.14.What does the author want to stress in Paragraph 1?A.The lighting-fast speed of 5G.B.The expectation of SG world.C.The difference between 4G and 5G.D.The internet-connected devices in our life.15.What does the underlined word "emblem"in Paragraph 2 mean________?A.Show. B.Success. C.Symbol D.Explanation16.We can infer from the text that ________A.5G world won’t come without AR glassesB.5G helps to create the artificial intelligence vehicleC.Apple company is developing AR glasses worldwideD.Tech companies will face the fact that smartphones may be replaced17.What will the author probably tell us next?A.How to make 5G cover more areas..B.Smart glasses will become faster and lighter.C.Why 5G Isn’t used in big cities.D.The importance of infrastructure construction.A few young students are talking about something on WeChat.Hi everyone! I like sports very much and play basketball almost every day. I also like to eat fast food, but my parents ask me to eat it only once a month.——Bill Sorry to hear that, Bill. However, maybe your parents are right. Fast food isn’t go od for you. I seldom eat it. On weekends, I often do some housework to make my parents relax ( 放松). And I use the Internet only once a week. I have a lot of homework to do every day.——Kate Yes, we students are always busy with our studies. But on Friday evening, I usually go shopping with my mother. It’s really fun. I enjoy watching TV, too. And I do it almost every day. So my parents are kind of unhappy sometimes.——Tony All parents like that. My parents never let me watch TV or play computer games! On weekends, they always want me to study almost every minute. But luckily, I can go to movies with them every Saturday. And on Sunday they let me go out with my friends when I finish my homework. Sometimes they are really good!——Lisa 18.Kate often ________ at the weekend.A.plays basketball B.helps with houseworkC.goes to the movies D.uses the Internet19.Who usually buys things on Friday evening?A.Bill. B.Kate. C.Tony. D.Lisa.20.Lisa can go to the movies ________.A.everyday B.once a week C.twice a week D.on weekdays21.From the passage, we can know that ________.A.Bill often eats fast foodB.Kate never uses the InternetC.Tony often watches TVD.Lisa can go out with her friends at any time22.What are these young students mainly (主要地) talking about?A.Their parents and their life. B.Their eating habits (习惯).C.Their free time. D.Their studying habits.Whether from news, reports or social media articles, you may know that 5G is coming.5G is the 5th generation network. It is a new network after 1G, 2G, 3G and 4G and it can connect everyone and everything together. 5G means super-fast data (数据) speed. One can download a two-hour movie in fewer than 10 seconds, and it is making our lives more and more convenient.5G will make self-driving cars possible. For safety, self-driving cars need super-fast data transmission (传输) to communicate with their nearby environment. 5G is just what makes self-driving cars achieve this. Even airplanes will become “smart” in the near future.5G will be a big help for students who take online classes. Students all over the world will be able to see places like the Great Wall without leaving their rooms.It will be also easier for doctors to treat patients remotely by 5G. It means caring for patients from far away.The facts listed above are only part of what 5G will make possible and popular. Just as in the early days of the Internet in the 1990s, few could see how it could change the world. The same will surely be true of 5G. With 5G,many things do not seem like dre ams to anyone. Now let’s get ready to say goodbye to 4G and welcome the coming of 5G.23.How long may it take to download a two-hour movie with 5G?A.15 seconds. B.8 seconds. C.10 minutes. D.2 hours.24.From the last paragraph, we can know that ________.A.4G is no more used in our daily life now B.the writer is worried about the coming of 5GC.with 5G, some of our dreams will come true for sure one day D.in the 1990s, all the people believed that the Internet would change our life25.5G will make the following things more and more popular EXCEPT ________.A.self-driving cars B.“smart” airplanes C.online classes D.hospitals with doctorsRecently a university in Nanjing, Jiangsu Province has set up facial recognition systems(人脸识别系统)in the classrooms to watch students’ behavior. As a result, it has caused a big discussion on the Internet.China Pharmaceutical University put the systems in two test classrooms as well as school gates, dormitory entrances(宿舍入口), the library and laboratory buildings.Acc ording to Xu Jianzhen, director of the university’s library and information center, the systems will help teachers check if students are in class and watch what they are doing during the lectures.“In the past, some students were absent from class after t eachers took attendance(考勤)or asked other students to answer “Present!” for them. So it was difficult to take control of them. Now with facial recognition, that would no longer be a problem,” he said.“As soon as you enter the classroom, the camera will wa tch you all the way through and record how long you put down your head, whether you’re playing with a smartphone, you’re sleeping or you’re reading other books,” he added.The news has raised wide discussion online. Many people are questioning if the cameras will infringe on students’ privacy(隐私). However, this is not the first university to use facial recognition technology in school. Many universities across the country have put cameras at the school gates to make sure of safety.26.Where can facial recognition systems be seen in China Pharmaceutical University?A.In all the classrooms.B.In the dining hall.C.In all the university buildings.D.In the places where students appear often.27.Why is the university using facial recognition systems?A.To help their students stay safer.B.To manage their students better.C.To help their students get better grades.D.To find out why the students don’t like attending classes.28.What can we infer from the passage?A.Almost everyone thinks the university should use facial recognition systems.B.No students will be absent from class in China Pharmaceutical University.C.Facial recognition technology is widely used in Chinese schools.D.Technology can change our life and make our life better.29.What’s the main idea o f the passage?A.Facial recognition systems have many advantages and universities should use them.B.College students are hard to deal with and universities are finding ways to solve the problem.C.China Pharmaceutical University started using facial recognition technology and people have different opinions on it.D.Facial recognition technology is important in helping students stay safe in school.Many children use the Internet to get useful knowledge (知识) and information, and to relax in their free time. But some of them are not using it in a good way. Here are some rules to make sure you are safe and have fun on the Internet.Make rules for Internet use with your parents. For example, when you can go online, for how long and what activities you can go online.Don’t give your password (密码) to anyone else, and never leak out the following information—your real name, home address, age, school, phone number or other personal information.Check with your parent before giving out a credit card (信用卡) number.Never send a photo yourself to someone in e-mail unless your parents say it’s OK.Check with your parents before going into a chat room. Different chat rooms have different rules and attractdifferent kinds of people. You and your parents must make sure it's a right place for you.Never agree to meet someone you met on the Internet without your parent’s permission (允许). Never meet anyone you met online alone.Always remember people online may not be who they say they are. Treat everyone online as strangers.If something you see or read online makes you uncomfortable, leave it at once. Tell it your parents or your teachers right away.Treat (对待) other people as you like to be treated. Never use bad language.Remember—not everything you read on the Internet is true.30.If you want a true friend on the Internet, you can ________.A.tell the people what your name is B.meet the people online aloneC.write an e-mail about yourself D.get your parent’s permission31.The underline phrase “leak out” in the third paragraph may mean ________.A.捐款B.离开C.泄露D.放好32.This passage is mainly about ________.A.how to use computers B.surfing on the InternetC.information on the internet D.internet safety rules33.If your parents don’t agree, never ________.A.read anything on the InternetB.relax in your free timeC.have a face-to-face meeting with anyone you met onlineD.treat other people as you would like to be treated【答案】1.C2.D3.A4.C5.C【分析】本文主要讲了什么是5G网络,5G网络能做什么以及未来怎样运用5G网络。
WindowsPhone操作系统 WP7、WP8系统手机必读手册
如何使用WP Windows Live ID与MetroWindowsPhone的许多服务和功能都是基于微软WindowsLive服务的,WindowsLiveID 可以说是连接微软这些服务的线索和脉络,例如,在商城(Marketplace)中购买安装游戏、使用Messenger即时通讯、SkyDrive云存储等服务时都需要通过个人WindowsLiveID来实现,如果缺少这个帐号,WindowsPhone的很多服务就无法正常使用。
这种对于个人网络帐号的依赖性要比iOS和安卓多,但也更容易让用户从根本上融入到WindowsPhone的实际体验之中。
对于使用个人电脑作为WindowsPhone管理器的标准用户而言,安装Zune软件可以减少很多麻烦,尤其表现在管理应用及个人多元信息方面。
当然如果已经有了WindowsLiveID,依靠网页版和手机版的商城,也可以直接上手WindowsPhone,从而减少了对Zune的依赖。
打开Zune即可在右上角的入口注册WindowsLiveID。
由于WindowsPhone商城目前尚未在中国内地市场上市,因而注册账号的地区建议填写美国或香港(更推荐注册香港地区账号,香港地区市场语言为中文),邮政编码则可以随意搜索对应地区城市的邮编,然后按照要求填写注册信息即可轻松注册WindowsLiveID。
注册好WindowsLiveID之后,我们还要将桌面电脑的区域位置修改为与WindowsLiveID 一致的地区,以便顺利访问Zune桌面端。
依次在桌面Windows的“控制面板”中的【区域与语言】里,把电脑位置设置成对应地区即可对应好区域之后,当用户连接WindowsPhone手机至桌面电脑,操作系统即自动调出Zune软件,用户即可发现顶部的导航条多了一个“商城”页签,点击该页签即可进入商城选择应用和游戏。
现在可以将注册的WindowsLiveID添加到WindowsPhone手机中了,需要注意的是每一部WindowsPhone手机只能绑定一个WindowsLiveID,如果需要更换账号就必须重置手机。
西仪通信设备:克雷电通联网关(模型:327W)说明书

Westell®V ERSA L INK™ G ATEWAY (M ODEL327W)Quick Start Guide030-300391 Rev. A May 2004Congratulations!You are on your way to experiencing the Internet with DSL at speeds significantly faster than traditional modems. With your purchase of the Westell® VersaLink™ Gateway, you will also enjoy the following features:• Always-on connection• Multiple users can share the connection using Wireless IEEE 802.11b/g/g+ and Ethernet connections.Follow the steps in this Quick Start Guide and get online fast! Before you begin, check the package contents to ensure that all components are included.NOTE: Internet service provider subscriber software and connection requirements may vary. Consult your Internet service provider for installation instructions. Please wait until you have received notification from your service provider that your DSL line has been activated before installing the Westell® VersaLink™ Gateway and software.030-300391 Rev. A May 2004Before you begin:Make sure that your kit contains the following items.• Westell® Versa Link™ Gateway• Power Supply• RJ-45 Ethernet cable (straight-through) (yellow)• RJ-11 Phone cable• SMA Antenna• Westell CD-ROM containing User Guide in PDF format• Quick Start Guide030-300391 Rev. A May 2004Networking RequirementsConnectionTypeMinimum System RequirementsETHERNET • Pentium® or equivalent and above class machines, Macintosh • Microsoft® Windows® (95, 98, 2000, ME, NT 4.0, or XP), Macintosh® OS X, or Linux installed• Computer Operating System CD-ROM on hand• Internet Explorer 4.x or Netscape Navigator 4.x or higher • 64 MB RAM (128 MB recommended)• 10 MB of free hard drive space• TCP/IP Protocol stack installed• 10/100 Base-T Network Interface Card (NIC)WIRELESS IEEE 802.11g • Pentium® or equivalent and above class machines • Microsoft® Windows® (98, ME, 2000, or XP) or Macintosh® OS X installed• Computer Operating System CD-ROM on hand • Internet Explorer 4.x or Netscape Navigator 4.x or higher• 64 MB RAM (128 MB recommended)• 10 MB of free hard drive space• An available IEEE 802.11b/g/g+ PC adapter030-300391 Rev. A May 2004030-300391 Rev. A May 2004INSTALLING THE MICROFILTERS If your DSL service shares the same line as your fax machine ortelephone, you need to install a filter. Please follow the installationprocedure in this section, and be sure to install one filter on everyphone line that has a telephone, answering machine, or faxmachine.Connect a DSL filter to standardtelephone equipment:1. Plug the short cord that isattached to the DSL filter intothe phone jack on the wall plate.2. Plug the standard telephonecable from the telephone deviceinto the jack of the DSL filterwhere it is labeled “PHONE.”Note: Repeat these steps for each telephone. However, DO NOT place a microfilter onthe DSL cord that is used to connect the Router to the wall jack.030-300391 Rev. A May 2004Connect a microfilter to telephoneequipment and DSL equipmentthat share the same wall jack:1. Plug the short cord that isattached to the DSL filter intothe phone jack on the wall plate.2. Plug the standard telephonecable from the telephone deviceinto the jack of the DSL filterwhere it is labeled “PHONE.”3. Plug one end of the DSL phonecable (that you received in themicrofilter kit) into the DSLfilter where it is labeled “HPN.”4. Plug the other end of the DSLphone cable into the DSL Linejack located on the rear panel ofthe Router.INSTALLING VERSALINKThis section explains the procedures for installing VersaLink. Youmay choose to install VersaLink in one of three ways: Ethernet only,Wireless only, or both Ethernet and Wireless simultaneously. Toinstall VersaLink via 10/100 Base-T Ethernet only, refer to section2A. To install VersaLink via Wireless only, refer to section 2B. Ifyou want to install VersaLink via Ethernet and Wireless portssimultaneously, refer to section 2C.NOTE: If you are using VersaLink™ in conjunction with an Ethernet Hub or Switch, refer to the manufacturer’s instructions for proper installation and configuration. When using a Microfilter, be certain that the DSL phone cable is connected to the “DSL/HPN” non-filtered jack. Westell recommends the useof a surge suppressor to protect equipment attached to the AC power supply.When using the optional uplink port (E1), Ethernet LAN connection is limited to E2, E3, and E4. The UPLINK feature is optional, and if UPLINK is not enabled in the .ini file, the Router will use DSL and Wireless only.030-300391 Rev. A May 2004030-300391 Rev. A May 20042A. Installation via 10/100 Base-T/Ethernet ConnectionsNOTE: Before you connect via 10/100 Base-T, you must have an available Ethernet card installed in your computer. If your Ethernet card does not auto-negotiate, you must set it to half duplex. Refer to the Ethernet card manufacturer’s instructions for installing and configuring your Ethernet card.1. Connect the power supply cord to the power connector marked DC 9V onthe rear panel of VersaLink. Plug the other end of the power supply into a wall socket.2.Connect the DSL phone cable from the jack marked on the rear panel ofVersaLink to the DSL-equipped telephone line jack on the wall.IMPORTANT: Do not use a DSL filter on this connection. You must use the phone cord that was provided with the kit.3. Connect the yellow Ethernet cable from any one of the Ethernet jacksmarkedon the rear panel of VersaLink to the Ethernet port on your computer. Repeat this step to connect up to three additional PCs to VersaLink.NOTE: You may connect to any of the four Ethernet jacks on the rear panel of VersaLink as they serve as an Ethernet switch.4. Check to see if the DSL LED is solid green. If the DSL LED is solid green,VersaLink is functioning properly.5. Check to see if the Ethernet LED is solid green. Solid green indicates thatthe Ethernet connection is functioning properly.Congratulations! You have completed the Ethernet hardware installation. No software installation is required when using only an Ethernet connection. You must now proceed to section 3 for instructions on accessing VersaLink.030-300391 Rev. A May 2004030-300391 Rev. A May 2004Figure 1. Connection via 10/100 Base-T/Ethernet2B. Installation via WirelessIMPORTANT: If you are connecting to VersaLink via a wireless network adapter, the service set ID (SSID) must be the same for both VersaLink and your PC’s wireless network adapter. The default SSID for VersaLink is the serial number of the unit (located below the bar code on the bottom of the unit and also on the Westell shipping carton). Locate and run the utility software provided with your PC’s Wireless network adapter and enter the SSID value. The PC’s wireless network adapter must be configured with the SSID (in order to communicate with VersaLink) before you begin the account setup and configuration procedures. Later, for privacy you can change the SSID by following the procedures outlined in the Wireless Configuration section of the User Guide provided with your kit.NOTE: Client PCs can use any Wireless Fidelity (Wi-Fi) 802.11b/g/g+ certified card to communicate with VersaLink. The Wireless card and VersaLink must use the same Wired Equivalent Privacy (WEP) security code type. The factory default for WEP is DISABLED. If you enable WEP, you must ensure the network setting for your wireless adapter is set to “Must Use Shared Key for WEP” or “Open Wi-Fi.” You must ensure that your PC’s Wi-Fi adapter is configured properly for whichever network setting you use. You can access the settings in the advanced properties of the wireless network adapter.030-300391 Rev. A May 2004To network VersaLink to additional computers in your home or office using a wireless installation, you will need to confirm the following:1. Ensure that an 802.11b/g/g+ wireless network adapter has been installed ineach PC on your wireless network.2. Install the appropriate drivers for your Wireless IEEE802.11b orIEEE802.11g adapter.3. Make sure the SMA antenna connector is loose. Orient the antenna in theproper configuration. Then, tighten the antenna knob to lock it into place.4. Connect the power supply cord to the power connector marked DC 9V onthe rear panel of VersaLink. Plug the other end of the power supply into a wall socket.5.Connect the DSL phone cable from the connector marked on the rear panel of VersaLink to the DSL-equipped telephone line jack on the wall. IMPORTANT: Do not use a DSL filter on this connection. You must use the phone cord that was provided with the kit.6. Check to see if the DSL LED is solid green. If the DSL LED is solid green,VersaLink is functioning properly.7. Check to see if VersaLink’s Wireless LED is solid Green. This means thatthe Wireless interface is functioning properly.Congratulations! You have completed the Wireless installation VersaLink. You must now proceed to section 3 for instructions on accessing VersaLink.030-300391 Rev. A May 2004030-300391 Rev. A May 2004Figure 2. Connection via Wireless030-300391 Rev. A May 20042C. Ethernet, Wireless, Combination Hardware InstallationVersaLink™ supports simultaneous use of 10/100 Base-T Ethernet and Wireless IEEE 802.11b/g ports. The following instructions explain how to install VersaLink for simultaneous use of Ethernet and Wireless ports.NOTE: Refer to Figure 1 and Figure 2 for illustrations on hardware installation via Ethernet and Wireless connections, respectively.1. Ensure that an 802.11b/g/g+ wireless network adapter has been installed ineach PC on your wireless network2. Install the appropriate drivers for your Wireless IEEE802.11b or IEEE802.11g adapter.3. Make sure the SMA antenna connector is loose. Orient the antenna in theproper configuration. Then, tighten the antenna knob to lock it into place.4. The Connect the power supply cord to the power connector marked DC 9Von the rear panel of VersaLink. Plug the other end of the power supply into a wall socket.5.Connect the DSL phone cable from connector marked on the rear panelof VersaLink to the DSL-equipped telephone line jack on the wall.IMPORTANT: Do not use a DSL filter on this connection. You must use the phone cord that was provided with the kit.6. Connect the yellow Ethernet cable from any one of the Ethernet jacksmarkedon the rear panel of VersaLink to the Ethernet port on yourcomputer. Repeat this step to connect up to three additional PCs toVersaLink.NOTE: You may connect to any of the four Ethernet jacks on the rear panel of VersaLink as they serve as an Ethernet switch.7. Check to see if the DSL LED is solid green. If the DSL LED is solid green,VersaLink is functioning properly.8. Check to see if the Ethernet LED is solid green. Solid green indicates theEthernet connection is functioning properly.9. Check to see if VersaLink’s Wireless LED is solid Green. This means thatthe Wireless interface is functioning properly.Congratulations! You have completed the simultaneous hardware (Ethernet and Wireless) installation. You must now proceed to section 3 for instructions on accessing VersaLink.030-300391 Rev. A May 2004ACCESSING VERSALINKBefore you can browse the Internet using VersaLink, you mustperform the following steps.1. Access VersaLink by clicking on your web browser. Next, type eitherhttp://dslrouter or http://192.168.1.1 in the web browser’s addresswindow and press ‘Enter’ on your keyboard.2. Follow the instructions in the screens to set up your account profile.NOTE: If you need further instructions during your Account Setup, refer to section 7,‘Configuring VersaLink for Internet Connection’ of the User Guide, which is located on the Westell CD-ROM that you received with your kit.030-300391 Rev. A May 2004PUBLICATION INFORMATIONWestell® VersaLink™ Gateway (Model 327W)Quick Start Part No. 030-300391 Rev. A© 2004 Westell, Inc.All rights reserved.Westell, Inc.750 North Commons DriveAurora, Illinois 60504 USAAll trademarks and registered trademarks are the property of their respective owners.030-300391 Rev. A May 2004。
微Focus安全ArcSight连接器智能连接器Microsoft Windows事件日志-本机:O

Micro Focus SecurityArcSight ConnectorsSmartConnector for Microsoft Windows Event Log–Native:Oracle AuditSupplemental Configuration GuideDocument Release Date:May17,2019Software Release Date:May17,2019Legal NoticesWarrantyThe only warranties for products and services of Micro Focus and its affiliates and licensors (“Micro Focus”)are set forth in the express warranty statements accompanying such products and services.Nothing herein should be construed asconstituting an additional warranty.Micro Focus shall not be liable for technical or editorial errors or omissions contained herein.The information contained herein is subject to change without notice.Restricted Rights LegendConfidential computer software.Except as specifically indicated otherwise,a valid license from Micro Focus is required for possession,use or copying.Consistent with FAR 12.211and 12.212,Commercial Computer Software,Computer Software Documentation,and Technical Data for Commercial Items are licensed to the ernment under vendor's standard commercial license.Copyright Notice©Copyright 2019 Micro Focus or one of its affiliates.TrademarkNoticesAdobe™is a trademark of Adobe Systems Incorporated.Microsoft®and Windows®are U.S.registered trademarks of Microsoft Corporation.UNIX®is a registered trademark of The Open Group.SupportPhoneA list of phone numbers is available on the Technical SupportPage: https:///support-contact-informationSupport Web Sitehttps:///ArcSight Product Documentationhttps:///t5/ArcSight-Product-Documentation/ct-p/productdocsContact InformationSupplemental Configuration GuideDocument Revision HistoryThe title page of this document contains the following identifying information:l Software Version number,which indicates the software version.l Document Release Date,which changes each time the document is updated.To check for recent updates or to verify that you are using the most recent edition of a document,go to the:ArcSight Product Documentation Community on Protect724.Document ChangesContentsle SmartConnector for Microsoft Windows EventLog–Native:Oracle Audit5 Product Overview5 Configuration5 Enable Auditing5Audit Administrative Users5 Connector Installation and Configuration6 Collect Events from the Event Log6 Device Event Mapping to ArcSight Fields7 Oracle Windows Event Log Mappings to ArcSight ESM Fields7 Event ID48Event ID58Event ID88Event ID128 Oracle Audit SYSDBA Event Mappings to ArcSight ESM Fields9 Event ID349 Oracle Audit Trail Event Mappings to ArcSight ESM Fields9 Event ID349 Oracle Unified Audit Trail Event Mappings to ArcSight ESM Fields11 Event ID3611 Send Documentation Feedback12le SmartConnector for Microsoft Windows Event Log–Native:Oracle AuditThis guide provides information about the SmartConnector for Microsoft Windows Event Log–Native: Oracle Audit and its event mappings to ArcSight data fields.Oracle database versions10g,11g,12c R1 and18c with Microsoft Windows Server2012are supported.The SmartConnector for Microsoft Windows Event Log–Native Windows Security Event Mappings document provides the main mappings for the Windows Event Log SmartConnectors;the field mappings listed in this document are specifically for the SmartConnector for Windows Event Log–Native:Oracle Audit.Product OverviewAuditing is a default feature of the Oracle server.The standard audit commands allow all system privileges to be audited along with access at the object level to any table or view on the database for select,delete,insert or update.Audit can be run for either successful or unsuccessful attempts or both. It can be for each individual user or for all users,and it can also be done at the session level or access level.At action level a single record is created per action and at session level one record is created for all audit actions per session.ConfigurationFor complete information about Oracle database auditing,see"Configuring Auditing"in the Oracle Database Security Guide for your database version.Enable AuditingDatabase auditing is enabled and disabled by the AUDIT_TRAIL initialization parameter in the database initialization parameter file,init.ora.Setting it to OS enables database auditing and directs all audit records to an operating system file:AUDIT_TRAIL=OSAudit Administrative UsersSessions for users who connect as SYS can be fully audited,including all users connecting as SYSDBA or e the AUDIT_SYS_OPERATIONS initialization parameter to specify whether such usersare to be audited.For example,the following setting specifies that SYS is to be audited:AUDIT_SYS_OPERATIONS=TRUEThe default value,FALSE,disables SYS auditing.Connector Installation and ConfigurationFollow the installation and configuration procedures in the SmartConnector Configuration Guide for Microsoft Windows Event Log–Native,selecting Microsoft Windows Event Log–Native as the connector to be configured.Collect Events from the Event LogTo set up the connector to collect application events:1.From$ARCSIGHT_HOME\current\bin,double-click runagentsetup.bat.2.Select Modify Connector on the window displayed and click Next.3.Select Modify connector parameters and click Next.4.Parameter modification windows are displayed based on your initial connector configuration.Toensure the table parameter modification window is displayed for you to add Oracle Audit logs, select Customlogs on the initial modify parameter window.Click Next to navigate to the Modify table parameters window.5.To collect events from an application log,modify the Application field by selecting true for eventcollection in the Application field and enter Oracle Audit in the CustomLog Names field.You can specify multiple CustomLog Names in a comma-separated format,for example:Oracle Audit,Exchange Auditing6.Click Next to view the Summary window.Click Next.7.Select Exit and click Next to exit the configuration wizard.8.Restart the connector for your changes to take effect.For more information about application event support,see the SmartConnector Configuration Guide for Microsoft Windows Event Log–Native.Device Event Mapping to ArcSight FieldsThe following section lists the mappings of ArcSight data fields to the device's specific event definitions. See ArcSight101for more information about the ArcSight data fields.Oracle Windows Event Log Mappings to ArcSight ESM FieldsEvent ID4Event ID5Event ID8Event ID12Oracle Audit SYSDBA Event Mappings to ArcSight ESM Fields Event ID34Oracle Audit Trail Event Mappings to ArcSight ESM Fields Event ID34Supplemental Configuration GuideOracle Unified Audit Trail Event Mappings to ArcSight ESM Fields Event ID36Send Documentation FeedbackIf you have comments about this document,you can contact the documentation team by email.If an email client is configured on this computer,click the link above and an email window opens with the following information in the subject line:Feedbackon Supplemental Configuration Guide(Connectors)Just add your feedback to the email and click send.If no email client is available,copy the information above to a new message in a web mail client,and send your feedback to***************************.We appreciate your feedback!。
2020高考英语全真模拟卷1

2020高考英语全真模拟卷1What We Look ForWe seek promising students who will contribute to the Harvard community during their college years, and to society throughout their lives.While academic accomplishment is the basic requirement, the Admission Committee considers many other factors—strong personal qualities, special talents or excellences of all kinds, perspectives formed by unusual personal circumstances, and the ability to take advantage of available resources and opportunities.We outline everything you need to apply to Harvard.Click https: //college. harvard. edu/admissions/apply to get detailed requirements.1. Where can you find step-by-step information of how to apply?A. Common Application.B. Coalition Application.C. Universal College Application.D. Application Tips.2. Which is the final day for Financial Aid Application?A. November 1.B. January 1.C. March 1.D. May 1.3. What is the basic requirement to apply for Harvard University?A. Academic accomplishment.B. Strong personal qualities.C. Special talents.D. Unique perspectives.BA dog spent the last four years of his life waiting a crossroad in the Thai city of Khon Kaen as if waiting for someone. People originally thought the dog had been abandoned, but then realized that he looked healthy, so people asked around about him. It turned out that the dog had indeed been spending most ofhis time around that crossroad, but a woman had been coming -.round regularly to bring him food and water.One day, while photographing the dog everyone called Leo, a reporter met the woman who had been taking care of him. She had come to drop off some food. After learning the story about the dog and the woman, the reporter decided to share the story on social media. The post soon went viral and the photos of Leo got shared hundreds of times. And the photos reached the eyes of Leo^ former old owner.Nang Noi Sittisarn, a 64-year-old woman from Thailand’s Roi Et Province, almost had a heart attack when her daughter showed her a photo of the beloved dog named BonBon she had lost during a car trip. When she learned that he had been waiting for her in the same spot for the last four years,her heart melted(融化).Auntie Noi told her daughter to drive her to where the dog was waiting. When she got there and called his name. BonBon,the poor dog started wiggling(扭动)his tail and came to her,but when she tried to take him home with her, he was unwilling to follow. She didn’ t want to force the dog to come with her so she agreed to leave him with his new master. However, she and her daughter will come to visit him regularly.4. Why did the dog look healthy after separation from his former owner?A. He walked around the crossroad constantly.B. He was kept at a woman?s home all the time.C. A local reporter brought him food and water.D. A woman looked after him on a regular basis.5. What does the underlined phrase “went viral” in paragraph 2 probably mean?A. Changed surprisingly.B. Spread quickly.C. Appeared gradually.D. Fell directly.6. How did Nang Noi Sittisam feel about the dog's waiting for her?A. Shocked.B. Regretful.C. Touched.D. Proud7. What can we mainly learn from the story about the dog?A. Unbelievable success is worth waiting for.B. We should adjust ourselves to environments.C. We need to learn to be faithful and thankful.D. No one knows the result until the last minuteCA team of engineers at Harvard University has been inspired by Nature to create the first robotic fly. The mechanical fly has become a platform for a series of new high-tech integrated systems. Designed to do what a fly does naturally, the tiny machine is the size of a fat housefly. Its mini wings allow it to stay in the air and perform controlled flight tasks.“It’s extremely important for us to think about this as a whole system and not just the sum of a bunch of indiv idual components,” said Robert Wood, the Harvard engineering professor who has been working on the robotic fly project for over a decade. A few years ago, his team got the go-ahead to start piecing together the components. “The added difficulty with a proj ect like this is that actually none of those components are off the shelf and so we have to develop them all on our own,” he said.They engineered a series of systems to start and drive the robotic fly. “The seemingly simple system which just moves the win gs has a number of interdependencies on the individual components, each of which individually has to perform well, but then has to be matched well to everything it’s connected to,” said Wood. The flight device was built into a set of power, computation, sensing and control systems. Wood says the success of the project proves that the flying robot with these tiny components can be built and manufactured.While this first robotic flyer is linked to a small, off-board power source, the goal is eventually to equip it with a built-in power source, so that it might someday perform data-gathering work at rescue sites, in farmers’ fields or on the battlefield. “Basically, it should be able to take off, land and fly around,” he said.Wood says the design offers a new way to study flight mechanics and control at insect-scale. Yet, the power, sensing and computation technologies on board could have much broader applications. “You can start thinking about using them to answer open scientific questions, you know, to study biology in ways that would be difficult with the animals, but using these robots instead,” he said. “So there are a lot of technologies and open interesting scientific questions that are really what drives us on a day to day basis.”8. Which of the following statements was the difficulty engineers met while making the robotic fly?A. They did not have sufficient fund.B. No ready-made components were available.C. There was no model in their mind.D. It was hard for them to assemble the components.9. What can be inferred from paragraphs 3 and 4?A. The robotic fly has been put into wide application.B. The robotic fly consists of a flight device and a control system.C. Information from many sources can be collected by the robotic fly.D. The robotic fly can just fly in limited areas at present.10. Which of the following can be learned from the passage?A. Wood’s design can replace animals in some experiments.B. Animals are not allowed in biological experiments.C. The robotic flyer is designed to learn about insects.D. There used to be few ways to study how insects fly.11. Which of the following might be the best title of the passage?A. The Development of Robotic FlyB. Robotic Fly Promotes Engineering ScienceC. Harvard’s Efforts in Making Robot ic FlyD. Robotic Fly Imitates Real Life InsectDThe idea that computers have some amount of “intelligence” is not new, says Ralph Haupter, the president of Microsoft Asia, pointing as far back as 1950 when computer pioneer Alan Turing asked whether machines can think.“So it has taken nearly 70 years f or the right combination of factors to come together to move AI from concept to reality,” says Haupter.It is predicted that the development of artificial intelligence will be the story of the coming generations, not just the coming year, but as 2019 gets underway, you’ll find AI will begin to touch your life in many ways according to some researchers.“Personal assistant AIs will keep getting smarter. As our personal assistants learn more about our daily routines, I can imagine the day I need not to worry about preparing dinner. My AI knows what I like to eat, which days of the week I like to cook at home, and makes sure that when I get back from work all my groceries are waiting at my doorstep, ready for me to prepare that delicious meal I had been longing for.” ---Alecjandro Troccoli, senior research scientist, NVIDIA.“Thanks to AI, the face will be the new credit card, the new driver’s license and the new barcode (条形码). Facial recognition is already completely transforming security with biometric capabilities being adopted, and seeing how technology and business are connected, like Amazon is with Whole Foods, I can see a near future where people will no longer need to stand in line at the store.” ---Georges Nahon, president, Orange Institute, a global research laboratory.“2019 will be the year AI becomes real for medicine. By the end of the year we’re seeing solutions for population health, hospital operations and a broad set of clinical specialties quickly follow behind.” ---Mark Michalski, executive director, Massachusetts General Hospital.12. What can we know about AI from the first two paragraphs?A. People didn't expect AI to develop so rapidly.B. The idea of AI just came up recently.C. The concept of AI was put forward by Ralph Haupter.D. It took more than 70 years to turn the concept into reality.13. Who sees the future of AI doing housework instead of human being?A. Alan Turing.B. Georges Nahon.C. Mark Michalski.D. Alejandro Troccoli.14. What is Georges Nahon’s job?A. Executive director of a hospital.B. President of a research laboratory.C. Chairman of an energy corporation.D. Chief operating officer of a newspaper.15. How is the passage developed?A. By explaining cause and effect.B. By presenting research results.C. By listing some predictions.D. By describing personal experiences.第二节(共5小题;每小题2分,满分10分)根据短文内容,从短文后的选项中选出能填入空白处的最佳选项。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Chambers
The Windows Phone OS 7.0 security model is built on the principles of isolation and least privilege, and introduces the “chamber” concept. Each chamber provides a security boundary and, through configuration, an isolation boundary within which a process can run. Each chamber is defined and implemented using a policy system. The security policy of a specific chamber defines what operating system (OS) capabilities the processes in that chamber can access. There are four chamber types. Three of the chamber types have fixed permission sets, and the fourth chamber type is capabilities-driven. Applications that are designated to run in the fourth chamber type have capability requirements that are honored at installation and at run-time. The four chamber types are as follows: The Trusted Computing Base (TCB) chamber has the greatest privileges. It allows processes to have unrestricted access to most of the Windows Phone 7 resources. The TCB chamber can modify policy and enforce the security model. The kernel and kernel-mode drivers run in the TCB chamber. Minimizing the amount of software that runs in the TCB is essential for minimizing the Windows Phone 7 attack surface.
Developers use the capability detection tool that is distributed with the Windows Phone Developer Tools to create the capability list for their application. The capability list is included in the application manifest in the application package (WMAppManifest.xml).
OEG331 12/2010
Windows® Phone 7 for IT professionals Rights Chamber (ERC) can access all resources except security policy. The ERC is intended for services and user-mode drivers that provide functionality intended for use by other phone applications. The ERC is less privileged than the TCB chamber. The Standard Rights Chamber (SRC) is the default chamber for pre-installed applications. All applications that do not provide device-wide services run in the SRC. Microsoft Outlook® Mobile 2010 is an example of an application that runs in the SRC. The Least Privileged Chamber (LPC) is the default chamber for all non-Microsoft applications that are available through the Marketplace Hub (also known as the Windows Phone Marketplace). LPCs are configured using capabilities as described in the following section.
Windows® Phone 7 for IT professionals
Windows® Phone 7 security model
This article is part of an ongoing series designed to help IT pros evaluate Windows® Phone 7 and understand how it can play a role in their organization. The articles in this series will focus on different topics of interest, such as digital certificates, using Windows Phone 7 devices with other applications such as Microsoft® SharePoint®, and the Windows Phone 7 architecture. This article discusses the security model for Windows Phone 7. It provides some details about how the model evolved, and how it achieves its design goals. This article discusses the following topics: The need for protection Chambers Capabilities Sandbox Application deployment
1
The need for protection
As demand for and usage of mobile devices has ballooned, so has the need for effective protection of confidential data and communications. Whether they engage in confidential personal or business discussions via voice, text, email, or through websites and web content, users and organizations must know that their data and their identities are safe. Windows Phone 7 was designed to address these security concerns through a security model that includes an innovative architecture, and rigorous data protection policies.
Sandbox
Every application on Windows Phone 7 runs in its own isolated chamber, and is defined by the declared capabilities that the application needs to function. A basic set of permissions are granted to all applications, including access to an isolated storage file. There are no communication channels between applications on the phone other than through the cloud. Applications are isolated from each other and cannot access memory used or data stored by other applications, including the keyboard cache. In addition, applications developed by other companies that are distributed via the Windows Phone Marketplace cannot remain active in the background. The moment a user switches to a different application on Windows Phone 7, the previously used application is gracefully shut down and the application state is preserved. This approach ensures that an application cannot use critical resources or communicate with Internet–based services while the user is not using the application.
