Agent Solutions for Navy Shipboard Power Systems
卡巴斯基安全中心事件追踪器集成指南说明书

Integrate Kaspersky Security Center EventTracker v9.0 and aboveAbstractThis guide will facilitate a Kaspersky Security Center user to send logs to EventTracker.ScopeThe configurations detailed in this guide are consistent with EventTracker 9.x or later and Kaspersky Security Center 10.AudienceAdministrators who want to monitor the Kaspersky Security Center using EventTracker.The information contained in this document represents the current view of Netsurion on theissues discussed as of the date of publication. Because Netsurion must respond to changingmarket conditions, it should not be interpreted to be a commitment on the part of Netsurion, andNetsurion cannot guarantee the accuracy of any information presented after the date ofpublication.This document is for informational purposes only. Netsurion MAKES NO WARRANTIES, EXPRESSOR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT.Complying with all applicable copyright laws is the responsibility of the user. Without limiting therights under copyright, this paper may be freely distributed without permission from Netsurion, ifits content is unaltered, nothing is added to the content and credit to Netsurion is provided.Netsurion may have patents, patent applications, trademarks, copyrights, or other intellectualproperty rights covering subject matter in this document. Except as expressly provided in anywritten license agreement from Netsurion, the furnishing of this document does not give you anylicense to these patents, trademarks, copyrights, or other intellectual property.The example companies, organizations, products, people and events depicted herein are fictitious.No association with any real company, organization, product, person or event is intended orshould be inferred.© 2019 Netsurion. All rights reserved. The names of actual companies and products mentionedherein may be the trademarks of their respective owners.Table of Contents1.Introduction (3)1.1.Pre-requisites (3)1.2.Enabling Kaspersky Event Logs and Sending logs to EventTracker (3)2.EventTracker Knowledge Pack (6)2.1.Categories (6)2.2.Alerts (7)2.3.Report (7)3.Importing Kaspersky Security Center knowledge pack into EventTracker (9)3.1.Category (9)3.2.Alerts (10)3.3.Flex Reports (11)3.4.Token Templates (12)4.Verifying Kaspersky Security Center knowledge pack in EventTracker (15)4.1.Categories (15)4.2.Alerts (15)4.3.Reports (16)4.4.Token Template (17)5.Sample Dashboards (18)1.I ntroductionKaspersky Lab offers consumer security products, such as anti-virus, anti-malware and firewall applications, in addition to security systems designed for small businesses, corporations and large enterprises. Corporate solutions include protection for workstations, file servers, mail servers, payment gateways, banking servers, mobile devices, and internet gateways managed through a centralized administration kit. These applications are also available in bundled security suites scaled to fit the requirements of organizations of varying sizes. 1.1.Pre-requisites•EventTracker 9.x or later should be installed.•EventTracker Agent to be installed on Kaspersky Security Center administrative server.•Advance licensed Kaspersky is required to forward the syslog.1.2.Enabling Kaspersky Event Logs and Sending logs to EventTracker1.Open Kaspersky Security Center 10 and go to Administration Server.Figure 12.In Admin Administration Server, select Events in the right frame.3.Click on Configure notifications and event export.Figure 24.Select Configure export to the SIEM system.Figure 35.Select the check box Automatically export events to the SIEM system database.Figure 46.Choose the SIEM system. Specify the EventTracker Manager address.7.Click OK.Figure 52.E ventTracker Knowledge PackOnce Kaspersky Security Center events are enabled and Kaspersky Security Center events are received in EventTracker, Alerts, and Reports can be configured in EventTracker.The following Knowledge Packs are available in EventTracker to support the Kaspersky Security Center monitoring.2.1.Categories•Kaspersky Security Center: Report management: This category provides information related to report management when a report is added, deleted or modified on Kaspersky Security Center.•Kaspersky Security Center: Task management: This category provides information related to task management when a task is added, deleted or modified on Kaspersky Security Center.•Kaspersky Security Center: Policy management: This category provides information related to policy management when a policy is added, deleted or modified on Kaspersky Security Center.•Kaspersky Security Center: Group task management: This category provides information related to group task management when a group task is added, deleted or modified on Kaspersky Security Center.•Kaspersky Security Center: Administrative group management: This category provides information related to administrative group management when an administrative group is added, deleted or modified on Kaspersky Security Center.•Kaspersky Security Center: Malicious object scan status: This category provides information related to the malicious object which has been detected and untreated on Kaspersky Security Center.•Kaspersky Security Center: Application privilege management: This category provides information related to applications that have been added to the trusted group on Kaspersky Security Center.•Kaspersky Security Center: Application settings change: This category provides information related to applications where their settings are changed on Kaspersky Security Center.•Kaspersky Security Center: Blocked files: This category provides information related to files which are being blocked by Kaspersky Security Center.•Kaspersky Security Center: Device Control:This category provides information related to devices which have been blocked when inserted into the Kaspersky Security Center system.•Kaspersky Security Center: Malware detected:This category provides information related to malwares which have been detected in the system of Kaspersky Security Center.•Kaspersky Security Center: Object quarantine:This category provides information related to malware objects which are added into the quarantine list in Kaspersky Security Center.•Kaspersky Security Center: Task management:This category provides information related to task management of Kaspersky Security Center.•Kaspersky Security Center: Vulnerability detected: This category provides information related to a vulnerability which has been detected in Kaspersky Security Center.2.2.Alerts•Kaspersky Security Center: Attack Detected: This alert is generated when an Alert is detected in the Kaspersky Security Center.•Kaspersky Security Center: Suspicious Object Found: This alert is generated when a malicious/Suspicious object is detected in Kaspersky Security Center.•Kaspersky Security Center: Virus Found: This Alert is generated when one of the files or web Viruses is detected in the Kaspersky Security Center.2.3.Report•Kaspersky Security Center- Suspicious Object Found: This report provides information related to malware detected in the web for which the user tries to access an unidentified object.Logs consideredJan 14 05:04:28 ccc-app9CEF:0|KasperskyLab|SecurityCenter|10.3.407|GNRL_EV_SUSPICIOUS_OBJECT_FOUND|Probably infected object detected|4|msg=Result: Detected: not-a-virus:WebToolbar.Win32.Asparnet.gen\r\nUser:CCCNTR\\CCC5055$ (Initiator)\r\nObject: C:\\Program Files(x86)\\askpartnernetwork\\toolbar\\updater\\tbnotifier.exe\r\n rt=1547463838 dhost=CCC5055dst=192.168.6.242 cs2=KES cs2Label=ProductName cs3=10.2.4.0 cs3Label=ProductVersionfilePath=C:\Program Files (x86)\AskPartnerNetwork\Toolbar\Updater\TBNotifier.exe cs1=not-a-virus:WebToolbar.Win32.Asparnet.gen cs1Label=VirusName duser=CCCNTR\CCC5055$Sample Report•Kaspersky Security Center-Task Status Updated: This report provides information related to task management where the task is started or stopped.Logs consideredJan 14 05:07:58 ccc-app9CEF:0|KasperskyLab|SecurityCenter|10.3.407|KLPRCI_TaskState|Completed|1|rt=1547464052 dhost=CCC-RD-HOST11 dst=192.168.0.101 cs2=WSEE cs2Label=ProductName cs3=10.0.0.0 cs3Label=ProductVersioncs5=Server Database Update cs5Label=TaskName cs4=204 cs4Label=TaskId cn2=4 cn2Label=TaskNewState cn1=1 cn1Label=TaskOldStateSample Report3.I mporting Kaspersky Security Center knowledge pack into EventTrackerunch the EventTracker Control Panel.2.Double click Export Import Utility, and then click the Import tab.Import Token Templates/Category/Alert/Tokens/ Flex Reports as given below.Note: Importing should be in the same order as mentioned above.Figure 63.1.Category1.Click the Category option, and then click the browse button.Figure 72.Locate All Kaspersky Security Center group of Categories.iscat file, and then click the Open button.3.To import categories, click the Import button.EventTracker displays a success message.Figure 84.Click OK, and then click the Close button.3.2.Alerts1.Click Alerts option, and then click the browse button.Figure 92.Locate All Kaspersky Security Center group of Alerts.isalt file, and then click the Open button.3.To import alerts, click the Import button.EventTracker displays a success message.Figure 104.Click OK, and then click the Close button.3.3.Flex Reports1.Click the Report option, and then click the browse button.Figure 112.Locate All Kaspersky Security Center group of Flex Report.issch file, and then click the Open button.3.To import reports, click the Import button.EventTracker displays a success message.Figure 124.Click OK, and then click the Close button.3.4.Token Templates1.Click the Admin menu, and then click Parsing rule.2.Select the Template tab, and then click on ‘Import’ option.Figure 133.Click on the Browse button.Figure 144.Locate All Kaspersky Security Center group of template.ettd file, and then click the Open button.Figure 155.Now select the check box and then click on ‘Import’ option.EventTracker displays a success message.Figure 166.Click on the OK button.4.V erifying Kaspersky Security Center knowledge pack in EventTracker4.1.Categories1.Logon to EventTracker.2.Click the Admin menu, and then click Categories.3.In Category Tree to view imported categories, scroll down and expand the Kaspersky Security Centergroup folder to view the imported categories.Figure 174.2.Alerts1.Logon to EventTracker.2.Click the Admin menu, and then click Alerts.3.In the Search field, type ‘Kaspersky Security Center', and then click the Go button.Alert Management page will display all the imported Kaspersky Security Center alerts.Figure 184.To activate the imported alerts, select the respective checkbox in the Active column.EventTracker displays a message box.Figure 195.Click OK, and then click the Activate Now button.NOTE:You can select alert notification such as Email, and Message, etc. For this, select the respective checkbox in the Alert management page, and then click the Activate Now button.4.3.Reports1.Logon to EventTracker.2.Click the Reports menu, and then select Configuration.3.In Reports Configuration pane, select the Defined option.EventTracker displays the Defined page.4.In search box enter ‘Kaspersky Security Center’, and then click the Search button.EventTracker displays Flex reports of Kaspersky Security Center.Figure 204.4.Token Template1.Logon to EventTracker.2.Click the Admin menu, and then click Parsing Rules.Figure 215.S ample Dashboards•Kaspersky Security Center- Suspicious object Found by HostFigure 22 •Kaspersky Security Center- Suspicious object Found on IP AddressFigure 23•Kaspersky Security Center- Suspicious object Found by ThreatFigure 24 •Kaspersky Security Center- Suspicious object Found by userFigure 25•Kaspersky Security Center- Suspicious object Found by Task StatusFigure 26 •Kaspersky Security Center- Suspicious object Found by SystemFigure 2720。
美海军新信息技术战略计划致力于加强网络防御

美海军新信息技术战略计划致力于加强网络防御信息系统技术员Athena Stovall,隶属于美国第3舰队指挥官,位于圣地亚哥,在她的计算机上扫描网络,搜寻入侵情况,这是在航天和海上作战系统中心进行的一次网络作战演习。
这一过程是用来提高军事人员在真实的网络战争环境中,通过扫描系统保卫网络,和对类似于病毒和探测的入侵做出反应的能力。
Jason Simmons上校和Clinton Tips上士在路易斯安那州的巴克斯代尔空军基地的空军单位升级反病毒软件,以支持新的网络、全球打击和网络作战司令部,该司令部是依照海军网络作战司令部的模式建立的。
保卫海军的网络中心信息基础设施免受攻击是重中之重。
海军新的网络防御作战司令部在全世界的海军及海军陆战队网络上进行着“每周7天每天24小时的监控”。
网络作战司令部称,这些网络每小时要受到90000次具有潜在危害的探测,自2001年以来已经受到60000多次软件计算机蠕虫和病毒的影响。
该司令部受益于与计算机一起成长的一代年轻人。
计算机辅助信息高速公路或者说网络,已经成为军事上越来越重要的工具,无论行政管理还是作战指挥,都离不开它。
海军也是一样,它的许多海外设施和分布于世界各地的舰队行动,都非常依赖“力量网络”的网络中心(环境)-这是一个致力于将战斗者、传感器、网络、指挥控制、平台和武器整合成一个分布式可升级的战斗部队的作战结构。
但是由于互联网和其它数字网络容易进入,它们面对攻击时显得脆弱,这使得这些有价值的工具转变为危险的负担。
海军部长Donald C. Winter于2007年10月发布了一个新的信息技术战略计划,要求建立一个全球性的网络中心信息基础设施,并把防止它受到攻击作为第一要务。
Winter说:“对我们来说,挑战是如何确保我们在信息技术上的投入在战场上能形成优势。
”为应对这些威胁,海军已经在网络作战司令部内建立了一个比较小的机构来监视可能的针对全球信息系统破坏性行为,并做出反应。
vSphere Management Assistant(vMA)安装Agent软件指南说明书

Installing the Agent Software on vSphere Management Assistant NodesTable of Contents Introduction (2)Prerequisites (3)Setting up vMA (3)Enabling the communication across firewalls (3)Enabling the root login (3)Installing the agent software on vMA nodes (5)To install the HP Operations agent (5)To install the HP Performance Agent (5)IntroductionYou can install the agent software (HP Operations agent or HP Performance Agent) using the installation scripts provided with the products (opc_inst for the HP Operations agent;ovpa.install for the HP Performance Agent). The agent installation mechanism uses the 'root' user on a UNIX/Linux node to install the agent. On a vSphere Management Assistant (vMA) system, the root login is disabled by default. If you try to install the agent on the vMA node with the 'vi-admin' user, the installation fails.You can continue to install the agent using one of the following options:•Enable the root login, log on to the node using the root login, and then install the product.•Use the vi-admin user to log on to the node, and then use the sudo bash command before installing the product.This document provides you with the information to install the agent software manually on a vMA node using different command-line options.PrerequisitesSetting up vMATo set up and configure a vMA system, follow the instructions in the vSphere Management Assistant Guide provided by VMware.Enabling the communication across firewallsThe agent uses the port 383 to facilitate the communication with other systems across firewalls. You must configure the vMA node to accept communication traffic on the port 383. To achieve this, follow these steps:1.On the vMA node, run the following command:sudo iptables -I RH-Firewall-1-INPUT 3 -p tcp -m tcp --dport 383 --tcp-flags SYN,RST,ACK SYN -j ACCEPTThe vMA system is configured to accept communication traffic on the port 383.2.Run the following command:sudo service iptables saveThe command saves the configuration set in step 1.3.To verify the configuration settings, follow these steps:a.Run the following command:sudo vi /etc/sysconfig/iptablesThe vi editor opens the iptables file from the /etc/sysconfig directory.b.In the iptables file, verify that the following line is present:-A RH-Firewall-1-INPUT -p tcp -m tcp --dport 383 --tcp-flagsSYN,RST,ACK SYN -j ACCEPTEnabling the root loginOptional. Use this procedure only when you want to log on to the vMA node with the root login. To enable the root login on vMA, follow these steps:4.Log on to the vMA system with the vi-admin login.5.Change the password of the root user with the following command:sudo passwd root6.Run the following command:vi /etc/passwdThe vi editor opens the passwd file from the /etc directory.7.Locate the line beginning with root.8.Make sure the shell for the root user is set to /bin/bash.TipThe passwd file lists the properties of every user in the following format:user:x:user ID:group ID:user description:shellMake sure that the shell of the root user is set to /bin/bash (and not to/sbin/nologin).Alternatively, you can enable the SSH root login on vMA. To enable the SSH root login, follow these steps:1.Log on to the vMA system with the vi-admin login.2.Run the following command:sudo vi /etc/ssh/sshd_configThe vi editor opens the sshd_config file from the /etc directory.3.In the sshd_config file, uncomment the statement PermitRootLogin yes.4.Save the sshd_config file.Installing the agent software on vMA nodesTo install the HP Operations agent1.Make sure the prerequisites are met (Prerequisites).2.Transfer the HP Operations agent package from the following location of the management serverto a temporary location on the vMA node:a.On HPOM for Windows:%ovdatadir%\shared\Packages\HTTPS\linux\linux\2.6\x86\Operations-agent\<version>\32 64b.On HPOM for UNIX:/var/opt/OV/share/databases/OpC/mgd_node/vendor/linux/x86/linux26/<HPOM_version>/RPC_BBC/3.If you want to use the root user to install the agent, follow these steps:a.Make sure the root user is enabled on the vMA node (Enable the root login).b.Install the HP Operations agent on the vMA node by following the instructions in theManually install a default HTTPS agent section in HPOM for Windows online help orthe Install an Agent Manually from Package Files section in the HTTPS AgentConcepts and Configuration Guide.4.If you do not want to enable the root user and want to install the product with the vi-admin user,follow these steps:a.Log on to the vMA node as the vi-admin user.b.Type the following command:sudo bashThe command line prompts you for the password of the root user.c.Specify the password of the root user.d.Install the HP Operations agent on the vMA node by following the instructions in theManually install a default HTTPS agent section in HPOM for Windows online help orthe Install an Agent Manually from Package Files section in the HTTPS AgentConcepts and Configuration Guide.To install the HP Performance Agent1.Make sure the prerequisites are met (Prerequisites).2.If you want to use the root user to install the HP Performance Agent, follow these steps:a.Make sure the root user is enabled on the vMA node (Enable the root login).b.Install the HP Performance Agent on the vMA node by following the instructions in theInstalling Performance Agent section in the HP Performance Agent (Linux) Installationand Configuration Guide.3.If you do not want to enable the root user and want to install the product with the vi-admin user,follow these steps:a.Log on to the vMA node as the vi-admin user.b.Type the following command:sudo bashThe command line prompts you for the password of the root user.c.Specify the password of the root user.d.Install the HP Performance Agent on the vMA node by following the instructions in theInstalling Performance Agent section in the HP Performance Agent (Linux) Installationand Configuration Guide.© 2009 Hewlett-Packard Development Company, L.P. The information contained herein is subject to change without notice. The only warranties for HP products and services are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. HP shall not be liable for technical or editorial errors or omissions contained herein.。
Agent Vi Vi-Search产品介绍说明书

Comprehensive Video Analytics SolutionsVi-SearchThe Complete Video Search and Analysis ToolVi-Search is an innovative video search software that enables rapid and effective retrieval and presentation of specific video segments, events and data from vast amounts of recorded video. While video recording is a basic component of most surveillance networks, the recorded video is rarely utilized due to the lack of an automated and time-efficient solution that enables search and analysis of such stored video. In response, V i-Search automates the search and analysis process and allows for true leveraging of the stored video.The software analyzes the video stream, generates metadata describing the scene content, and allows for later retrieval and analysis of the video through an automatic search within the stored metadata.Based on Agent Vi’s open architecture, pure software approach, Vi-Search seamlessly integrates with a wide range of edge devices and video management systems, in both new and existing surveillance networks.Vi-Search HighlightsAutomatic and Time-Efficient• Scans days of stored video in seconds to display precise results• Eliminates the need for time-consuming manual search and review of stored videoSearch Flexibility• Enables search by event or search by target parameters, including type, size and color• Scene metadata is continuously collected and logged, with no need to pre-define search parametersHighly Scalable• Can be easily applied and expanded to surveillance networks of any size• Enables simultaneous search on multiple cameras Open Architecture• Integrated with a wide range of edge devices and video management systems• Search can be conducted through Vi-Search’s GUI or an integrated third party video management system Hardware-Efficient• Single server can generate detailed and accurate scene metadata for hundreds of cameras simultaneously User-Friendly• No complicated set-up or training required• Operated by simple search queries• Enables easy export of specific video segments and reports as stand-alone filesApplicationsVi-Search enables utilization of stored video for a wide variety of security, safety, law enforcement and business intelligence applications:Business Intelligence and Operational Efficiency applications can benefit from statistical analysis of human or vehicle traffic in specific areas and in distinct time frames. Retail chains and other businesses or organizations can better understand and predict traffic patterns to efficiently allocate resources, provide better customer care, and improve operational procedures.Forensic Analysis often requires search through vast amounts of stored video to pinpoint certain events, or to trace events back to their origin. Through its wide range of search parameters and capabilities, Vi-Search enables users to locate an event in the stored video with high precision in a matter of seconds. A stand-alone file containing the relevant video segment can be easily extracted and saved as evidence.Time-Critical Security and Law Enforcement Opera-tions require quick and effective responses to events as they occur. Once there is knowledge of a criminal or ter-rorist activity, events can be traced back for immediate investigation, providing law enforcement agencies with a full picture of the event including origin and evolution. In this way, deployment and tactical responses are better informed, improving crisis management.V i-Search allows you to reap the true benefits of your surveillance network by enabling automatic and effortless retrieval and analysis of valuable information contained in your stored video.Search and Analysis Functionality Vi-Search provides the following main search and analysis functionalities:Forensic SearchEnables search for particular events or objects in a speci-fied group of cameras and within a distinct time frameStatistical AnalysisConducts people or vehicle counting and generates statistical reports, for a specified group of cameras and within a distinct time frameMotion Path AnalysisProduces graphical presentation of all motion paths in a scene, with immediate access to the video segment relating to each pathVideo SummaryAllows debriefing of multiple search results through one condensed clipSearch Parameters and CapabilitiesVi-Search offers an extensive set of intuitive search parameters and capabilities, including: • Target Type – People, Vehicles, Objects• Event Type – Moving, Stationary, Crossing a line, Occupancy, Crowding • Search by Color and/or Size • Search within defined time frames• Search on selected cameras or group of cameras • Search for Similar Targets – Once a target is observed, a simple search can be conducted to locate additional appearances of the same or similar target in the recorded videoVi-Search is a complete video search and analysis solution. Its open architecture, hardware-efficient approach makes Vi-Search a feasible and effective solution for all markets and industries.Software & Hardware RequirementsVi-Search Server(for 100 cameras)•CPU - Core2Duo 2.66 GH (or similar), RAM - 2 GB• Hard drive - 200 GB per month of storage• OS - Windows XP Professional, Windows Server 2003, Windows Server 2008Vi-Search Client• CPU - Core2Duo 2.4G Hz (or similar), RAM - 1 GB• Hard drive - 50 GB• OS - Windows XP Professional, Windows VistaServer Scalability Analytics servers can be easily added to support more camerasStronger processors can support more cameras on one serverSystem PerformanceQuery Time Average of 15 seconds per camera per 24 hours of recorded metadataRequired Metadata Storage Average of 50 MB per camera per dayIntegration PartnersSupported Edge Devices Axis, COE, IQInVision, MangoDSP, Sony, Verint, VivotekFor additional devices and specific models contact ****************Supported VideoManagement SystemsMilestone, OnSSI, ViconFor a list of vendors and supported versions contact****************Agent Video Intelligence (Agent Vi) is a leading provider of open architecture, video analytics software deployed in a variety of security, safety and business intelligence applications worldwide. The comprehensive video analytics solutions offered by Agent Vi extend from real-time video analysis and alerts to forensic search and post-event analysis, and are fully integrated with a range of third party edge devices and video management systems. Integrating Agent Vi’s advanced video analytics capabilities into existing or new surveillance networks enables users to benefit from the true potential of their surveillance networks, transforming them into intelligent tools that respond to the practical challenges of the 21st century.Agent Video Intelligence Ltd. USA: +1 303 534 5106 EMEA & APAC: +972 72 220 1500For more information, visit: or email: *****************。
Fortinet FortiNAC产品概述说明书

FORTINAC AND THE FORTINET SECURITY FABRIC EXECUTIVE SUMMARYOutdated endpoint access security solutions leave mobile and Internet of Things (IoT) devices vulnerable to targeted attacks that can put the entire network at risk.To protect valuable data, organizations need next-generation network access control (NAC). As part of the Fortinet Security Fabric, FortiNAC provides comprehensive device visibility, enforces dynamic controls, and orchestrates automated threat responses that reduce containment time from days to seconds. It enables policy-based network segmentation for controlling access to sensitive information.THE NEED FOR THIRD-GENERA TION NACEnterprise networks are undergoing dramatic change through the widespread adoptionof bring-your-own-device (BYOD) policies, loT, and multi-cloud technologies. When thisis coupled with a highly mobile workforce and geographically dispersed data centers,the security challenges multiply. With endpoint devices remaining a top attack target, organizations must address the outdated access controls that leave their networks exposed to undue risk.The first generation of NAC solutions authenticated and authorized endpoints (primarily managed PCs) using simple scan-and-block technologies. Second-generation NAC products solved the emerging demand for guest network access—visitors, contractors, and partners.But securing dynamic and distributed environments now requires security and networking that share intelligence and collaborate to detect and respond to threats. As part of the Fortinet Security Fabric architecture, FortiNAC offers a third-generation NAC solutionthat leverages the built-in commands of network switches, routers, and access points to establish a live inventory of network connections and enforce control over network access. FortiNAC identifies, validates, and controls every connection before granting access. COMPREHENSIVE DEVICE AND USER VISIBILITYAs a result of BYOD and IoT proliferation, security teams must now protect countless devices that aren’t owned, managed, or updated by corporate IT. FortiNAC addresses this challenge in a couple of different ways. First, it enables detailed profiling of even headless devices using multiple information and behavior sources to accurately identify everythingon the network. Comprehensive agentless scanning automatically discovers endpoints, classifies them by type, and determines if the device is corporate-issued or employee-owned. Second, the user is also identified in order to apply additional role-based policies. HIGHLIGHTSnn Comprehensive network visibilitynn Profiles and classifies all devices and usersnn Provides policy-based access controlsnn Extends dynamic segmentationto third-party devicesnn Orchestrates automated threat responsesnn Contains potential threats in seconds nn Simplifies guest access and onboardingnn Low TCO—maximizes existing security investmentsSOLUTION BRIEF: FORTINAC AND THE FORTINET SECURITY FABRICMacintosh HD:Users:bhoulihan:Documents:_Projects:Solution Brief:Solution Brief - FortiNAC:sb-fortiNAC:sb-fortiNACCopyright © 2018 Fortinet, Inc. All rights reserved. Fortinet , FortiGate , FortiCare and FortiGuard , and certain other marks are registered trademarks of Fortinet, Inc., and other Fortinet names herein may also be registered and/or common law trademarks of Fortinet. All other product or company names may be trademarks of their respective owners. Performance and other metrics contained herein were attained in internal lab tests under ideal conditions, and actual performance and other results may vary. Network variables, different network environments and other conditions may affect performance results. Nothing herein represents any binding commitment by Fortinet, and Fortinet disclaims all warranties, whether express or implied, except to the extent Fortinet enters a binding written contract, signed by Fortinet’s General Counsel, with a purchaser that expressly warrants that the identified product will perform according to certain expressly-identified performance metrics and, in such event, only the specific performance metrics expressly identified in such binding written contract shall be binding on Fortinet. For absolute clarity, any such warranty will be limited to performance in the same ideal conditions as in Fortinet’s internal lab tests. Fortinet disclaims in full any covenants, representations, and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise revise this publication without notice, and the most current version of the publication shall be applicable. Fortinet disclaims in full any covenants, representations, and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise revise this publication without notice, and the most current version of the publication shall be applicable.GLOBAL HEADQUARTERS Fortinet Inc.899 Kifer RoadSunnyvale, CA 94086United StatesTel: +/salesEMEA SALES OFFICE 905 rue Albert Einstein 06560 Valbonne FranceTel: +33.4.8987.0500APAC SALES OFFICE8 Temasek Boulevard #12-01Suntec Tower Three Singapore 038988Tel: +65-6395-7899Fax: +65-6295-0015LATIN AMERICA HEADQUARTERS Sawgrass Lakes Center13450 W. Sunrise Blvd., Suite 430Sunrise, FL 33323Tel: +1.954.368.9990August 31, 2018 12:32 PMDYNAMIC NETWORK CONTROLOnce devices and users are identified, FortiNAC assigns the appropriate level of access while restricting use of non-relatedcontent. This dynamic, role-based system logically creates detailed network segments by grouping applications and like data together to limit access to specific groups of users. In this manner, if a device is compromised, its ability to travel in the network and attack other assets will be limited. Security Fabric integration allows FortiNAC to implement segmentation policies and change configurations on switches and wireless products, including solutions from more than 70 different vendors.FortiNAC also streamlines the secure registration process of guest users while keeping them safely away from any parts of the network containing sensitive data. When appropriate, users can self-register their own devices (laptops, tablets, or smartphones), shifting the workload away from IT staff.AUTOMA TED RESPONSIVENESSAutomation is the “holy grail” of an integrated security architecture. Policy-based automated security actions help Security Fabric solutions share real-time intelligence to contain potential threats before they can spread. FortiNAC offers a broad and customizable set of automation policies that can instantly trigger containment settings in other Security Fabric elements such as FortiGate, FortiSwitch, or FortiAP when a targeted behavior is observed. This extends to all Fabric-integrated products, including third-party solutions.Potential threats are contained by isolating suspect users and vulnerable devices, or by enforcing a range of responsive actions. This in turn reduces containment times from days to seconds—while helping to maintain compliance with increasingly strict standards, regulations, and privacy laws.HOW IT WORKSAs an integrated Security Fabric solution, FortiNAC helps to provide additional layers of protection against device-borne threats. For example, if a customer is using FortiSIEM, FortiNAC providescomplete visibility and policy-based control for network, mobile, and IoT devices, while FortiSIEM provides the security intelligence. FortiNAC offers complete visibility into all of these devices, gathers the alerts, and provides the contextual information—the who, what, where, and when for the events. This increases the fidelity of the alerts and enables accurate triage.FortiNAC sends the event to FortiSIEM to ingest the alert, then FortiSIEM directs FortiNAC to restrict or quarantine the device if necessary. FortiSIEM and FortiNAC communicate back and forth to compile all relevant information and deliver it to a security analyst.。
dnv-os-e201_2013-04

OFFSHORE STANDARDDNV-OS-E201Oil and Gas Processing SystemsAPRIL 2013The electronic pdf version of this document found through is the officially binding version© Det Norske Veritas AS April 2013Any comments may be sent by e-mail to rules@FOREWORDDNV is a global provider of knowledge for managing risk. Today, safe and responsible business conduct is both a license to operate and a competitive advantage. Our core competence is to identify, assess, and advise on risk management. From our leading position in certification, classification, verification, and training, we develop and apply standards and best practices. This helps our customers safely and responsibly improve their business performance. DNV is an independent organisation with dedicated risk professionals in more than 100 countries, with the purpose of safeguarding life, property and the environment.DNV service documents consist of among others the following types of documents:—Service Specifications. Procedural requirements.—Standards. Technical requirements.—Recommended Practices. Guidance.The Standards and Recommended Practices are offered within the following areas:A)Qualification, Quality and Safety Methodology B)Materials Technology C)Structures D)SystemsE)Special Facilities F)Pipelines and Risers G)Asset Operation H)Marine Operations J)Cleaner Energy O)Subsea SystemsU)Unconventional Oil & GasCHANGESGeneralThis document supersedes DNV-OS-E201, December 2012.Text affected by the main changes in this edition is highlighted in red colour. However, if the changes involve a whole chapter, section or sub-section, normally only the title will be in red colour.Main changes•General—Revised references w.r.t. number and/or title.—In addition to the below stated changes, a number of corrections and clarifications have been made in the existing text.•Ch.1 Introduction—Sec.1 [2]: References w.r.t. number and/or title have been revised. New definition of safety system has been added.•Ch.2 Technical Provisions—Sec.2 [6.1.1]: Requirement for shutdown valves at injection point to well for all injection systems has been harmonised.—Sec.1 & Sec.2: Requirements to block valve near PSV's have been revised.—Sec.4: [1]: Requirement for re-ignition of pilot flame in flare system has been added.—Sec.4: [4]: Requirements for emergency disconnect for DP positioned vessels and reference to Sec.12 for offloading systems have been added.—Sec.5: Definitions in accordance with same in DNV-OS-A101 have been deleted and adjusted. A general statement on automation/control system as well as for process shutdown system have been added.•Ch.3 Certification and Classification—Sec.3: [2]: Tables w.r.t. certification requirements have been corrected.Editorial CorrectionsIn addition to the above stated main changes, editorial corrections may have been made.CONTENTSCH. 1INTRODUCTION (8)SEC. 1INTRODUCTION (9)1General (9)1.1Introduction (9)1.2Objectives (9)1.3Organisation of this standard (9)1.4Scope and application (9)1.5Assumptions (10)2Normative References (10)2.1General (10)2.2DNV Offshore Standards, etc (10)2.3Other references (11)3Definitions (13)3.1Verbal forms (13)3.2Definitions (13)3.3Abbreviations (16)4Documentation (17)4.1General (17)CH. 2TECHNICAL PROVISIONS (18)SEC. 1DESIGN PRINCIPLES (19)1General (19)1.1Overall safety principles (19)2Design Loads (19)2.1General principles (19)2.2Environmental conditions (19)2.3Design pressure and temperature (20)3Plant Arrangement and Control (20)3.1Operational considerations (20)3.2Monitoring, control and shutdown (21)3.3Shutdown devices and failure modes (22)3.4General requirements for valves (22)3.5Wellhead control system (23)3.6Subsea control system (23)SEC. 2PRODUCTION AND UTILITY SYSTEMS (24)1General (24)1.1General requirements (24)1.2Interconnection between hazardous and non-hazardous systems (24)2Wellhead and Separation System (25)2.1General (25)2.2Separator System (25)3Gas Treatment and Compression System (25)3.1General (25)4Water Injection, Gas Injection and Gas Lift System (25)4.1General (25)5Heating and Cooling Systems (26)5.1General (26)6Chemical Injection Systems (26)6.1General (26)7Drainage Systems (26)7.1Open drainage system (26)7.2Additional requirements for closed drainage systems (27)SEC. 3RELIEF AND DEPRESSURISING SYSTEMS (28)1General (28)1.1General requirements (28)3Depressurising System (29)3.1General (29)4Disposal System (30)4.1General (30)SEC. 4HYDROCARBON IMPORT/ EXPORT (32)1General (32)1.1General (32)1.2Recognised codes (32)1.3Riser disconnection systems (for floating installations) (32)1.4Monitoring and control (32)2Pig Launchers and Receivers (33)2.1General (33)3Crude Export Pump Systems (33)3.1General (33)4Offloading System (33)4.1General (33)SEC. 5ELECTRICAL, AUTOMATION AND SAFETY SYSTEMS (34)1Electrical Systems (34)1.1Application (34)2Automation and Safety Systems (34)2.1Application (34)2.2Scope (34)3System Requirements (34)3.1Clarification and amendments to system requirements in DNV-OS-D202 (34)SEC. 6PIPING (35)1General (35)1.1Application (35)1.2Recognised codes and standards (35)2Design Requirements (35)2.1General (35)2.2Wall thickness (36)2.3Expansion joints and flexible hoses (36)2.4Valves and special items (36)2.5Piping connections (36)2.6Supporting elements (37)SEC. 7EQUIPMENT (38)1General (38)1.1Application (38)2Recognised Codes and Standards (38)2.1Unfired pressure vessels (38)2.2Boilers (38)2.3Atmospheric vessels (39)2.4Pumps (39)2.5Compressors (39)2.6Combustion engines (39)2.7Gas turbines (40)2.8Shafting (40)2.9Gears (40)2.10Couplings (40)2.11Lubrication and sealing (40)2.12Wellhead equipment (41)2.13Lifting appliances (41)2.14Swivels and swivel stacks (41)2.15Risers (41)SEC. 8STRUCTURES (42)1General (42)1.1Application (42)1.2Recognised codes and standards (42)3Manufacture and Testing (42)3.1General (42)SEC. 9MATERIALS AND CORROSION PROTECTION (43)1General (43)1.1Objective (43)2Principles (43)2.1General (43)3Specific Requirements (43)3.1Materials for load-carrying parts (43)3.2Bolts and nuts (43)4Specific Requirements for Pressure Retaining Equipment (44)4.1Materials for pressure vessels, piping and equipment - General requirements (44)4.2Rolled steel, welded and seamless pipes (44)4.3Steel forgings (44)4.4Steel castings (44)4.5Aluminium, copper and other non-ferrous alloys (44)4.6Requirements to duplex stainless steel (45)4.7Bolts and nuts (45)4.8Sealing materials and polymers (45)5Material Certificates (45)5.1General (45)5.2Type of document (45)6Corrosion Protection (46)6.1General (46)7Erosion (47)7.1General (47)SEC. 10MANUFACTURE, WORKMANSHIP AND TESTING (48)1General (48)1.1Application (48)1.2Quality assurance and quality control (48)1.3Marking (48)2Manufacture (48)2.1Welder's qualification (48)2.2Welding (48)2.3Heat treatment (48)2.4Pipe bending (49)3Non-destructive Testing (NDT) (49)3.1General (49)3.2Structures (49)4Testing (49)4.1Testing of weld samples (49)4.2Pressure testing and cleaning (49)4.3Functional testing (50)SEC. 11SUPPLEMENTARY PROVISIONS FOR LNG IMPORT AND EXPORT TERMINALS (AND LNG PRODUCTION UNITS) (51)1General (51)1.1General (51)2Scope and Application (51)2.1Scope (51)2.2Codes and standards (51)3Technical Provisions (52)3.1General (52)3.2Initial gas treatment (52)3.3Liquefaction plant (52)3.4Regasification plant (52)3.5LNG transfer (53)SEC. 12CRUDE OFFLOADING SYSTEM (FOR FLOATING INSTALLATIONS) (55)1General (55)1.1General (55)CH. 3CERTIFICATION AND CLASSIFICATION (58)SEC. 1CERTIFICATION AND CLASSIFICATION (59)1General (59)1.1Introduction (59)1.2Class designation (59)1.3Assumptions (59)SEC. 2DESIGN REVIEW (60)1General (60)1.1Application (60)2Specific Requirements for Certification or Classification (60)2.1General (60)2.2Design principles (60)2.3Electrical, automation and safety systems (60)2.4Piping (60)2.5Materials and corrosion protection (61)2.6Manufacture, workmanship and testing (61)3Documentation Requirements (61)3.1General (61)SEC. 3CERTIFICATION OF EQUIPMENT (62)1General (62)1.1General (62)2Equipment Categorisation (63)2.1General (63)2.2Pressure containing equipment and storage vessels (63)2.3Miscellaneous items (66)SEC. 4SURVEY DURING CONSTRUCTION (67)1General (67)1.1General (67)2Quality Assurance or Quality Control (67)2.1General (67)3Module Fabrication (67)3.1General (67)4Module Installation (67)4.1General (67)5Specific Requirements in Relation to the Requirements of Ch.2 of this Standard (67)5.1Welder qualifications (67)5.2Welding (67)SEC. 5SURVEYS AT COMMISSIONING AND START-UP (69)1General (69)1.1General (69)2System and Equipment Checks (69)2.1General (69)3Functional Testing (69)3.1General (69)4Start-up (69)4.1General (69)OFFSHORE STANDARDDNV-OS-E201OIL AND GAS PROCESSING SYSTEMSCHAPTER 1INTRODUCTIONCONTENTS PAGE Sec.1Introduction (9)SECTION 1 INTRODUCTION1 General1.1 Introduction1.1.1 This offshore standard contains criteria, technical requirements and guidance on design, construction and commissioning of offshore hydrocarbon production plants and associated equipment.The standard also covers liquefaction of natural gas and regasification of liquefied natural gas and also associated gas processing.1.1.2 The standard is applicable to plants located on floating offshore units and on fixed offshore structures of various types.Offshore installations include fixed and floating terminals for export or import of LNG.1.1.3 The requirements of Ch.2 relate primarily to oil and gas production activities. Ch.2 Sec.11 provides additional requirements to LNG terminals and should be read as a supplement to the other sections in Ch.2.1.1.4 The standard has been written for general worldwide application. Governmental regulations may include requirements in excess of the provisions of this standard depending on the size, type, location and intended service of the offshore unit or installation.1.2 Objectives1.2.1 The objectives of this standard are to:—provide an internationally acceptable standard of safety for hydrocarbon production plants and LNG processing plant by defining minimum requirements for the design, materials, construction and commissioning of such plant—serve as contractual a reference document between suppliers and purchasers—serve as a guideline for designers, suppliers, purchasers and contractors—specify procedures and requirements for hydrocarbon production plants and LNG processing plant subject to DNV certification and classification.1.3 Organisation of this standard1.3.1 This standard is divided into three main chapters:Chapter 1: General information, scope, definitions and references.Chapter 2: Technical provisions for hydrocarbon production plants and LNG processing plant for general application.Chapter 3: Specific procedures and requirements applicable for certification and classification of plants in accordance with this standard.1.4 Scope and application1.4.1 The standard covers the following systems and arrangements, including relevant equipment and structures:—production and export riser systems—well control system—riser compensating and tensioning system—hydrocarbon processing system—relief and flare system—production plant safety systems—production plant utility systems—water injection system—gas injection system—storage system—crude offloading system—LNG liquefaction system—LNG regasification system—LNG transfer system.1.4.2 The following are considered as main boundaries of the production plant, as relevant:—including connection to production buoy—including shutdown valve at crude outlet from production plant to crude storage or loading buoy —including shutdown valve between liquefaction plant and LNG storage tanks (LNG FPSO)—including shutdown valve between LNG storage and regasification plant, and between regasification plant and export line (LNG FSRU).1.5 Assumptions1.5.1 The requirements apply to oil and gas processing plant as such, and presuppose that systems and arrangements as listed below are provided on the unit or installation:—safe escape—adequate separation between hydrocarbon processing plant, utility area, accommodation —fire and explosion safety —emergency shutdown —alarm and communication —utility systems.1.5.2 It is assumed that the subsea production system to which the unit or installation is connected, is equipped with sufficient safe closure barriers to avoid hazards in case of accidental drift-off of the unit or dropped objects from the unit or installation.2 Normative References2.1 General2.1.1 The following standards include provisions which, through references in the text are relevant for this offshore standard. The latest edition of the references shall be used unless otherwise agreed.2.1.2 Codes and standards other than those stated in this standard may be acceptable as alternative or supplementary requirements, provided that they can be demonstrated to achieve a comparable, or higher, safety level.2.1.3 Any deviations, exceptions and modifications to the design codes and standards shall be documented and agreed between the contractor, purchaser and verifier, as applicable.2.2 DNV Offshore Standards, etc.2.2.1 The standards listed in Table 1-1 apply.Guidance note:Table 1-1 DNV Offshore Standards and other DNV referencesCodeTitleDNV-OS-A101Safety Principles and Arrangement DNV-OS-B101Metallic MaterialsDNV-OS-C101Design of Offshore Steel Structures, General LRFD method DNV-OS-C401Fabrication and Testing of Offshore Structures DNV-OS-D101Marine and Machinery Systems and Equipment DNV-OS-D201Electrical InstallationsDNV-OS-D202Automation, Safety, and Telecommunication Systems DNV-OS-D301Fire ProtectionDNV-OS-F101Submarine Pipeline Systems DNV-OS-F201Dynamic RisersClassification Note 41.2Calculation of Gear Rating for Marine Transmission Rules for Certification of Flexible Risers and Pipes Rules for Classification of Ships DNV Standard for Certification No. 2.22Lifting Appliances2.3 Other references2.3.1 In Table 1-2 other references are listed.Table 1-2 Other referencesCode TitleAISC Manual of Steel ConstructionAISC Manual of Steel Construction: Load and Resistance Factor DesignANSI/AGMA 6032-A94Standard for Marine Gear Units: RatingANSI/ASME B31.3Process PipingAPI RP 2A-WSD Planning, Designing and Constructing Fixed Offshore Platforms - Working Stress Design API RP 14B Design, Installation, Repair and Operation of Subsurface Safety Valve SystemAPI RP 14C Analysis, Design, Installation, and Testing of Basic Surface Safety Systems for OffshoreProduction PlatformsAPI RP 14E Design and Installation of Offshore Production Platform Piping SystemsAPI RP 14H Installation, Maintenance and Repair of Surface Safety Valves and Underwater Safety Valves OffshoreAPI RP 16Q Design, Selection, Operation and Maintenance of Marine Drilling Riser SystemsAPI RP 17A Design and Operation of Subsea Production SystemsAPI RP 17B Flexible PipeAPI RP 500Recommended Practice for Classification of Locations for Electrical Installations onPetroleum Facilities Classed as Class I, Division 1 and Division 2API RP 505Recommended Practice for Classification of Locations for Electrical Installations at Petroleum Facilities Classified as Class I, Zone 0, and Zone 2API RP 520Sizing, Selection and Installation of Pressure Relieving Devices in RefineriesAPI RP 521Guide for Pressure Relieving and Depressurising SystemsAPI Spec 2C Offshore CranesAPI Spec 12D Field Welded Tanks for Storage of Production LiquidsAPI Spec 12F Shop Welded Tanks for Storage of Production LiquidsAPI Spec 12J Oil and Gas SeparatorsAPI Spec 16R Marine Drilling Riser CouplingsAPI Spec 6A Wellhead and Christmas Tree EquipmentAPI Spec 6FA Fire Test for ValvesAPI Spec 6FC Fire Test for Valve With Automatic BackseatsAPI Spec 6FD Fire Test for Check ValvesAPI Std 530Calculation of Heater Tube Thickness in Petroleum RefineriesAPI Std 610Centrifugal Pumps for Petroleum, Heavy Duty Chemical and Gas Industry ServicesAPI Std 611General Purpose Steam Turbines for Petroleum, Chemical and Gas Industry ServicesAPI Std 612Special Purpose Steam Turbines for Petroleum, Chemical and Gas Industry ServicesAPI Std 613Special Purpose Gear Units for Petroleum, Chemical and Gas Industry ServicesAPI Std 614Lubrication, Shaft-Sealing, and Control-Oil Systems and Auxiliaries for Petroleum, Chemical and Gas Industry ServicesAPI Std 616Gas Turbines for the Petroleum, Chemical and Gas Industry ServicesAPI Std 617Centrifugal Compressors for Petroleum, Chemical and Gas Industry ServicesAPI Std 618Reciprocating Compressors for Petroleum, Chemical and Gas Industry ServicesAPI Std 619Rotary-Type Positive Displacement Compressors for Petroleum, Chemical and Gas Industry ServicesAPI Std 620Design and Construction of Large, Welded Low-Pressure Storage TanksAPI Std 650Welded Steel Tanks for Oil StorageAPI Std 660Shell-and-Tube Heat ExchangersAPI Std 661Air-Cooled Heat Exchangers for General Refinery ServiceAPI Std 671Special Purpose Couplings for Petroleum, Chemical and Gas Industry ServicesAPI Std 672Packaged, Integrally Geared Centrifugal Air Compressors for Petroleum, Chemical and Gas Industry ServicesAPI Std 674Positive Displacement Pumps - ReciprocatingAPI Std 675Positive Displacement Pumps - Controlled VolumeAPI Std 676Positive Displacement Pumps - RotaryAPI Std 2000Venting Atmospheric and Low-Pressure Storage Tanks: Non-refrigerated and RefrigeratedASME BPVC Boiler and Pressure Vessel Code, Section I, Rules for Construction of Power Boilers ASME BPVC Boiler and Pressure Vessel Code, Section IV, Rules for Construction of Heating Boilers ASME BPVC Boiler and Pressure Vessel Code, Section VIII, Rules for Construction of Pressure Vessels ASME PTC 22Performance Test Code on Gas Turbines (Performance Test Codes)ASME B73.1Specification for Horizontal End Suction Centrifugal Pumps for Chemical Process ASME B73.2Specification for Vertical In-line Centrifugal Pumps for Chemical ProcessASTM A923Standard Test Methods for Detecting Detrimental Intermetallic Phase in Wrought Duplex Austenitic/Ferritic Stainless SteelsBS 1113Specification for design and manufacture ofwater-tube steam generating plantEN 1834, Part 1-3Reciprocating internal combustion engines - Safety requirements for design and constructionof engines for use in potentially explosive atmospheresEN 14015Specification for the design and manufacture of site built, vertical, cylindrical, flat-bottomed,above ground, welded, steel tanks for the storage of liquids at ambient temperature and aboveBSI PD 5500Specification for unfired fusion welded pressure vessels EN 1993, several parts Eurocode 3: Design of steel structures EN 14015Specification for the design and manufacture of site built, vertical, cylindrical, flat-bottomed,above ground, welded, steel tanks for the storage of liquids at ambient temperature and aboveEN 14620, several parts Design and manufacture of site built, vertical, cylindrical, flat-bottomed steel tanks for thestorage of refrigerated, liquefied gases with operating temperatures between 0°C and -165°CDNV-RP-A201Plan Approval Documentation Types - Definitions DNV-RP-D101Structural analysis of Piping systems DNV-RP-O501Erosive Wear in Piping Systems EN 13480Metallic Industrial Piping EN 1473Installation and equipment for liquefied natural gas: Design of onshore installations EN 1474Installation and equipment for liquefied natural gas: Design and testing of loading/unloadingarmsEN 12952Water-tube boilers and auxiliary installations EN 12953Shell Boilers EN 13445Unfired pressure vessels ICS/OCIMF Ship to Ship Transfer Guide (Petroleum)IEC 60079-2Explosive atmospheres, Part 2 Equipment protection by pressurized enclosures IGC Code The International Code for the Construction and Equipment of Ships carrying Liquefied Gasesin BulkISO 898Mechanical properties of fasteners made of carbon steel and alloy steel ISO 2314Gas turbine - Acceptance tests ISO 3046-1Reciprocating internal combustion engines Performance - Part 1: Declarations of power, fueland lubricating oil consumptions, and test methods - Additional requirements for engines for general useISO 6336 Pt. 1-5Calculation of load capacity of spur and helical gears ISO 10418Petroleum and natural gas industries - Offshore production platforms - Analysis, design,installation and testing of basic surface safety systemsISO 10474Steel and steel products - Inspection documents ISO 13631Petroleum and Natural Gas Industries - Packaged reciprocating gas compressors ISO 15156Petroleum and Natural Gas Industries - Materials for Use in H2S-containing Environments inOil and Gas ProductionNACE SP0176Corrosion Control of Steel Fixed Offshore Platforms Associated with Petroleum Production NFPA 37Standard for the Installation and Use of Stationary Combustion Engines and Gas Turbines NFPA 59A Standard for the Production, Storage, and Handling of Liquefied Natural Gas EN 1999 part 1-1 to 1-4Eurocode 9: Design of aluminium structures OCIMF Guide to purchasing, manufacturing and testing of loading and discharge hoses for offshoremooringTEMA Standards for Heat exchangers Table 1-2 Other references (Continued)CodeTitle3 Definitions3.1 Verbal forms3.1.1 Shall: Indicates requirements strictly to be followed in order to conform to this standard and from which no deviation is permitted.3.1.2 Should: Indicates that among several possibilities one is recommended as particularly suitable, without mentioning or excluding others, or that a certain course of action is preferred but not necessarily required. Other possibilities may be applied subject to agreement.3.1.3 May: Verbal form used to indicate a course of action permissible within the limits of the standard.3.1.4 Agreement or by agreement: Unless otherwise indicated, agreed in writing between manufacturer or contractor and purchaser.3.2 Definitions3.2.1 Abnormal conditions: A condition that occurs in a process system when an operating variable goes outside its normal operating limits.3.2.2 Alarm: A combined visual and audible signal for warning of an abnormal condition, where the audible part calls the attention of personnel, and the visual part serves to identify the abnormal condition.3.2.3 Blow-by: A process upset resulting in gas flowing through a control valve designed to regulate flow of liquid.3.2.4 Bulkhead: An upright partition wall.3.2.5 Choke valve: Control valve designed to regulate or reduce pressure.3.2.6 Christmas tree: Combination of valves and connectors designed to stop the flow of well fluids, i.e. act as a barrier to the hydrocarbon reservoir.3.2.7 Client: May be either the yard, the owner, or, with regard to components, the manufacturer.3.2.8 Closed drains:Drains for pressure rated process components, piping or other sources which could exceed atmospheric pressure, such as liquid outlets from pressure vessels and liquid relief valves, where such discharges are hard piped without an atmospheric break to a drain tank.3.2.9 Cold venting: Discharge of vapour to the atmosphere without combustion.3.2.10 Completed wells: Wells fitted with Christmas trees attached to the wellhead, such that the flow of fluids into and out of the reservoir may be controlled for production purposes.3.2.11 Contractor:A party contractually appointed by the purchaser to fulfil all or any of, the activities associated with design, construction and operation.3.2.12 Control room: Continuously manned room for control of the installation. The room offers operator interface to the process control and safety systems.3.2.13 Control station or Control room: General term for any location space where essential control functions are performed during transit, normal operations or emergency conditions. Typical examples are central control room, radio room, process control room, bridge, emergency response room, etc. For the purpose of compliance with the SOLAS Convention and the MODU Code, the emergency generator room, UPS rooms and fire pump rooms are defined as control stations.3.2.14 Control system: Is a system that receives inputs from operators and process sensors and maintains a system within given operational parameters. It may also register important parameters and communicate status to the operator.3.2.15 Design pressure: The maximum allowable working or operating pressure of a system used for design. The set point of PSVs can not exceed this pressure. (Identical to MAWP).3.2.16 Disposal system: A system to collect from relief, vent and depressurising systems. Consists typically of collection headers, knock-out drum and vent discharge piping or flare system.3.2.17 Double block and bleed: Two isolation valves in series with a vent valve between them.3.2.18 Emergency shutdown, (ESD): An action or system designed to isolate production plant and ignition sources when serious undesirable events have been detected. It relates to the complete installation. See also safety system below.3.2.19 Escape route: A designated path to allow personnel egress to a safe area in the most direct way possible.3.2.20 Explosive mixture: A vapour-air or gas-air mixture that is capable of being ignited by an ignition source that is at or above the ignition temperature of the vapour-air or gas-air mixture.3.2.21 Fail safe: Implies that a component or system goes to or remains in the mode that is deemed to be safest on failures in the system.3.2.22 Failure: An event causing one or both of the following effects:—loss of component or system function—deterioration of functionality to such an extent that safety is affected.3.2.23 Flammable liquid: A liquid having a flash point below 37.8 ºC (100 ºF) and having a vapour pressure not exceeding 2.8 kg/cm2 (40 psi absolute) at 37.8 ºC (100 ºF).3.2.24 Flare system: A system which ensure safe disposal of vapour by combustion.3.2.25 Flash point: The minimum temperature at which a combustible liquid gives off vapour in sufficient concentration to form an ignitable mixture with air near the surface of the liquid.3.2.26 Hazardous area: Space in which a flammable atmosphere may be expected at such frequency that special precautions are required. See DNV-OS-A101 for a complete definition including zones etc.3.2.27 High Integrity Pressure Protection System (HIPPS): A highly reliable, self contained, instrumented safety system to protect against overpressure.3.2.28 Ignition temperature: The minimum temperature required at normal atmospheric pressure to initiate the combustion of an explosive mixture.3.2.29 Independent systems: Implies that there are no functional relationships between the systems, and they can not be subject to common mode failures.3.2.30 Inert gas: A gas of insufficient oxygen content to support combustion when mixed with flammable vapours or gases.3.2.31 Installation: An offshore platform which may be either bottom-founded (permanently affixed to the sea-floor) or floating.3.2.32 Interim class certificate: A temporary confirmation of classification issued by the surveyor attending commissioning of the plant upon successful completion.3.2.33 Interlock system:A set of devices or keys that ensure that operations (e.g. opening and closing of valves) are carried out in the right sequence.3.2.34 L.E.L. (lower explosive limit): The lowest concentration of combustible vapours or gases by volume in mixture with air that can be ignited at ambient conditions.3.2.35 Master valve: A fail safe remotely operated shutdown valve installed in the main body of the Christmas tree, acting as a well barrier.3.2.36 Maximum allowable working pressure, (MAWP): The maximum operating pressure of a system used for design. The set point of PSVs can not exceed this pressure. (Identical to design pressure).3.2.37 Maximum shut in wellhead pressure: The maximum reservoir pressure that could be present at the wellhead.3.2.38 Minimum design temperature, MDT: Minimum design operating or ambient start-up temperature. The lowest predictable metal temperature occurring during normal operations including start-up and shutdown situations is to be used. (If no thermal insulation is fitted, then ambient temperature is to be used if this is lower than the temperature of the content.)3.2.39 Open drains: Gravity drains from sources, which are at or near atmospheric pressure, such as open deck drains, drip pan drains and rain gutters.3.2.40 Pressure safety valve, (PSV): A re-closing valve designed to open and relieve pressure at a defined pressure and rate.3.2.41 Process shutdown, (PSD): Isolation of one or more process segments by closing designated shutdown valves and tripping equipment. The shutdown is initiated through the process shutdown system that is a safety system designated to monitor the production plant.3.2.42 Processing plant: Systems and components necessary for safe production of hydrocarbon oil and gas.3.2.43 Production system: The system necessary for safe delivery of hydrocarbon oil and gas. The production system may include separation process, compression, storage and export facilities, hydrocarbon disposal, produced water treatment, etc.。
VIAVI NITRO Mobile 产品简介说明书

5,T0r6o*7u,b'8l7e9s*h6:o9o*/t)i'#n,g49
;'#0/<=2,4>//9*)?
Assurance and Optimization
Application Aware HetNet/C-RAN/vRAN
IoT Device, Location, UP/CP Analytics Real Time, Low Latency Services
Site Planning Small Cells Optimization
Performance Security CEM
VIP Assurance
Location Insights
Handsets
Monetization
Events
Smart Cities
HetNets IoT
Video
3rd Party Applications
Assurance & Optimization
VIAVI Integrated Data Feeds
Real-time Correlation & Mediation Layer
RAN Data Collection
Core Data Collection
All subscribers, all sessions / events, 24 x 7
By increasing the automation of context-driven workflows, NITRO Mobile helps you manage your mobile network with less manual intervention. Through feeding real-time data from instruments and software virtual agents into a single presentation layer, NITRO Mobile, together with the scalability of the virtualized platform, helps reduce complexity and increase the automation necessary to confidently manage the evolution to 5G.
Sophos UTM 产品说明说明书

Sophos UTM Feature ListGeneral ManagementÌCustomizable dashboardÌRole-based administration: Auditor, read-only and manager for all functionsÌNo-charge, centralized management of multipleUTMs via Sophos UTM Manager (SUM)ÌConfigurable update serviceÌReusable system object definitions for networks, services, hosts, time periods, users and groups, clients and servers ÌPoint & Click IPS rule managementÌSelf-service user portal for one-click VPN setupÌConfiguration change trackingÌManual or fully automated backup and restore optionsÌEmail or SNMP trap notification optionsÌSNMP supportÌOne-time password (OTP) / Two-factor authentication(2FA) supports OATH protocol for WebAdmin, User Portal, SSL VPN, IPSec VPN, HTML5 Portal and SSH Login*ÌOne-click secure access for Sophos customer support** Network Routing and ServicesÌRouting: static, multicast (PIM-SM)and dynamic (BGP, OSPF)ÌNAT static, masquerade (dynamic)ÌP rotocol independent multicast routing with IGMP snooping ÌBridging with STP support and ARP broadcast forwarding ÌW AN link balancing: 32 Internet connections, auto-link health check, automatic failover, automatic andweighted balancing and granular multipath rulesÌZ ero-config active/passive high- availabilityÌA ctive/active clustering for up to 10 appliancesÌ802.3ad interface link aggregationÌQoS with full control over bandwidth pools anddownload throttling using Stochastic Fairness Queuingand Random Early Detection on inbound trafficÌF ull configuration of DNS, DHCP and NTPÌS erver load balancingÌI Pv6 supportÌR ED supportÌVLAN DHCP support and tagging**ÌMultiple bridge support**Network ProtectionÌStateful deep packet inspection firewallÌIntrusion protection: Deep packet inspectionengine, 18,000+ patternsÌSelective IPS patterns for maximumperformance and protectionÌIPS pattern aging algorithm for optimal performance*ÌFlood protection: DoS, DDoS and portscan blockingÌCountry blocking by region or individual country(over 360 countries) with separate inbound/outbound settings and exceptionsÌSite-to-site VPN: SSL, IPSec, 256- bit AES/3DES,PFS, RSA, X.509 certificates, pre-shared keyÌRemote access: SSL, IPsec, iPhone/iPad/Cisco VPN client supportÌVoIP handling for SIP and H.323 connectionsÌConnection tracking helpers: FTP, IRC, PPTP, TFTPÌIdentity-based rules and configuration withAuthentication Agent for usersAdvanced Threat Protection*ÌDetect and block network traffic attempting tocontact command and control servers usingDNS, AFC, HTTP Proxy and firewallÌIdentify infected hosts on the network Sandstorm Protection***ÌCloud-based sandbox to detect, block and gain visibility into evasive zero-day targeted attacks in active content such as executables, PDFs, Office Documents, and more ÌPreviously unseen suspicious files aredetonated in the cloud-sandbox and monitoredbefore being released to the end-userÌComplete reporting on all suspicious file activityincluding detailed sandbox analysis results AuthenticationÌTransparent, proxy authentication (NTLM/Kerberos) or client authenticationÌAuthentication via: Active Directory, eDirectory,RADIUS, LDAP and TACACS+ÌSingle sign-on: Active directory, eDirectoryÌSophos Transparent Authentication Suite (STAS)provides AD agent for transparent reliable SSOauthentication with Microsoft Active Directory***ÌSSL supportÌTools: server settings check, username/passwordtesting and authentication cache flushÌGraphical browser for users and groupsÌAutomatic user creationÌScheduled backend synchronization prefetchÌComplex password enforcementWeb ProtectionÌURL Filter database with 35 million+ sitesin 96 categories and 65+ languagesÌApplication Control: Accurate signatures andLayer 7 patterns for thousands of applicationsÌDynamic application control based onproductivity or risk thresholdÌView traffic in real-time, choose to block or shapeÌMalware scanning: HTTP/S, FTP and web-based email via dual independent antivirus engines (Sophos & Avira) block all forms of viruses, web malware, trojans and spywareÌFully transparent HTTPS filtering of URLs*ÌOption for selective HTTPS Scanning of untrusted sites**ÌAdvanced web malware protectionwith JavaScript emulation*ÌLive Protection real-time in-the-cloud lookupsfor the latest threat intelligenceÌPotentially unwanted application (PUA) download blocking*ÌMalicious URL reputation filtering backed by SophosLabs ÌReputation threshold: set the reputation threshold awebsite requires to be accessible from internal networkÌActive content filter: File extension, MIME type,JavaScript, ActiveX, Java and FlashÌTrue-File-Type detection/scan within archive files**ÌYouTube for Schools enforcementÌSafeSearch enforcementÌGoogle Apps enforcement*Web PolicyÌAuthentication: Active Directory, eDirectory,LDAP, RADIUS, TACACS+ and local databaseÌSingle sign-on: Active Directory,eDirectory, Apple Open DirectoryÌProxy Modes: Standard, (Fully) Transparent, Authenticated, Single sign-on and Transparent with AD SSO*ÌTransparent captive portal with authenticationÌSupport for separate filtering proxies in different modesÌTime, user and group-based access policiesÌBrowsing quota time policies and quota reset option**ÌAllow temporary URL filter overrides with authentication ÌClient Authentication Agent for dedicated per-user tracking ÌCloning of security profilesÌCustomizable user-messages for events in local languages ÌCustom HTTPS verification CA supportÌSetup wizard and context sensitive online helpÌCustomizable block pagesÌCustom categorization to override categoriesor create custom categories*ÌSite tagging for creating custom site categories**ÌAuthentication and filtering options by device typefor iOS, Android, Mac, Windows and others*ÌPolicy testing tool for URLs, times,users and other parameters*Email ProtectionÌReputation service with spam outbreak monitoring based on patented Recurrent-Pattern-Detection technologyÌAdvanced spam detection techniques: RBL, heuristics,SPF checking, BATV, URL scanning, grey listing, RDNS/HELO checks, expression filter and recipient verification ÌBlock spam and malware during the SMTP transaction ÌDetects phishing URLs within e-mailsÌGlobal & per-user domain and address black/white lists ÌRecipient Verification against Active Directory accountÌE-mail scanning with SMTP and POP3 supportÌDual antivirus engines (Sophos & Avira)ÌTrue-File-Type detection/scan within archive files**ÌScan embedded mail formats: Block maliciousand unwanted files with MIME type checkingÌQuarantine unscannable or over-sized messagesÌFilter mail for unlimited domains and mailboxesÌAutomatic signature and pattern updatesÌSophos Live Anti-Virus real-time cloud lookups** Email Encryption and DLPÌPatent-pending SPX encryption for one-way message encryption*ÌRecipient self-registration SPX password management**ÌAdd attachments to SPX secure replies**ÌTransparent en-/decryption and digitalsigning for SMTP e-mailsÌCompletely transparent, no additionalsoftware or client requiredÌSupports S/MIME, OpenPGP, and TLS standardsÌPGP key server supportÌAllows content/virus scanning even for encrypted e-mails ÌCentral management of all keys and certificates- no key or certificate distribution requiredÌDLP engine with automatic scanning of emailsand attachments for sensitive data*ÌPre-packaged sensitive data type contentcontrol lists (CCLs) for PII, PCI, HIPAA, andmore, maintained by SophosLabs*Email ManagementÌUser-quarantine reports mailed outdaily at customizable timesÌLog Management service supportÌCustomizable User Portal for end-usermail management, in 15 languagesÌAnonymization of reporting data to enforce privacy policy ÌOver 50 Integrated reportsÌPDF and CSV exporting of reportsÌCustomizable email footers and disclaimersÌSetup wizard and context sensitive online helpÌEmail header manipulation support**End-User PortalÌSMTP quarantine: view and releasemessages held in quarantineÌSender blacklist/whitelistÌHotspot access informationÌDownload the Sophos Authentication Agent (SAA)ÌDownload remote access clientsoftware and configuration filesÌHTML5 VPN portal for opening clientless VPN connections to predefined hosts using predefined servicesÌDownload HTTPS Proxy CA certificatesVPNÌPPTP, L2TP, SSL, IPsec, HTML5-based and Ciscoclient-based remote user VPNs, as well as IPsec, SSL,Amazon VPC-based site-to-site tunnels and SophosRemote Ethernet Device (RED) plug-and-play VPNÌIPv6 SSL VPN support***VPN IPsec ClientÌAuthentication: Pre-Shared Key (PSK), PKI(X.509), Smartcards, Token and XAUTHÌEncryption: AES (128/192/256), DES, 3DES(112/168), Blowfish, RSA (up to 2048 Bit), DHgroups 1/2/5/14, MD5 and SHA-256/384/512ÌIntelligent split-tunneling for optimum traffic routingÌNAT-traversal supportÌClient-monitor for graphical overview of connection status ÌMultilingual: German, English and FrenchÌIPsec Tunnel BindingVPN SSL ClientÌProven SSL-(TLS)-based securityÌMinimal system requirementsÌProfile support for varying levels of accessÌSupports MD5, SHA, DES, 3DES and AESÌWorks through all firewalls, regardless of proxies and NAT ÌSupport for iOS and AndroidClientless VPNÌTrue clientless HTML5 VPN portal for accessingapplications securely from a browser on any device VPN One-ClickÌEasy setup and installations of every client within minutes ÌDownload of client-software, individual configurationfiles, keys and certificates one click away fromthe Security Gateway end-user portalÌAutomatic installation and configuration of the clientÌNo configuration required by end userVPN REDÌCentral Management of all REDappliances from Sophos UTMÌNo configuration: Automatically connectsthrough a cloud-based provisioning serviceÌSecure encrypted tunnel using digital X.509certificates and AES256- encryptionÌRED sites are fully protected by the Network, Weband Mail security subscriptions of the Central UTM.ÌVirtual Ethernet for reliable transfer ofall traffic between locationsÌIP address management with centrally definedDHCP and DNS Server configurationÌRemotely de-authorize RED devicesafter a select period of inactivityÌCompression of tunnel traffic* (RED50, RED 10 revision 2, 3)ÌVLAN port configuration options* (RED 50)ÌSupport for RED 15w with integrated 802.11n WiFi AP*** Secure Wi-FiÌSimple plug-and-play deployment,automatically appearing in the UTMÌCentral monitor and manage all access points (APs) and wireless clients through the built-in wireless controller ÌIntegrated security: All Wi-Fi traffic isautomatically routed through the UTMÌWireless 802.11 b/g/n at 2.4 GHz and 5GHz (AP 50)ÌPower-over-Ethernet 802.3af (AP 30/50)ÌMultiple SSID support: Up to 8ÌStrong encryption supports state-of-the-artwireless authentication including WPA2-Enterpriseand IEEE 802.1X (RADIUS authentication)ÌWireless guest Internet access with customizablesplash pages on your captive portalÌVoucher-based guest access for daily or weekly access ÌTime-based wireless network accessÌWireless repeating and bridging meshednetwork mode with AP 50ÌHotspot backend authentication support*(RADIUS, TACACS, LDAP, AD)ÌAutomatic channel selection background optimization**ÌMulti-tenant hotspot administration**ÌSupport for HTTPS login support**Web Application Firewall ProtectionÌReverse proxyÌURL hardening engineÌForm hardening engineÌDeep-linking controlÌDirectory traversal preventionÌSQL injection protectionÌCross-site scripting protectionÌDual-antivirus engines (Sophos & Avira)ÌHTTPS (SSL) encryption offloadingÌCookie signing with digital signaturesÌPath-based routingÌOutlook anywhere protocol supportÌReverse authentication (offloading) for form-basedand basic authentication for server access*ÌPersistent session cookie support***Web Application Firewall ManagementÌAuto server discovery scans attachednetworks and identifies web serversÌIntegrated load balancer spreadsvisitors across multiple serversÌPredefined firewall profiles for MicrosoftOutlook Web Access (OWA)ÌQuick server switch allows easy maintenanceÌSkip individual checks in a granular fashion as required ÌMatch requests from source networksor specified target URLsÌSupport for logical and/or operatorsÌAssists compatibility with various configurationsand non-standard deploymentsÌOptions to change WAF performance parameters**ÌUpload custom WAF rules**ÌScan size limit option**ÌAllow/Block IP ranges**ÌWildcard support for server paths**ÌAutomatically append a prefix/suffix for authentication** UTM Endpoint ProtectionÌWindows endpoint protection with SophosAntivirus and device controlÌOn-access, on-demand or scheduled scanningfor malware, viruses, spyware and TrojansÌPUA scanningÌLive Protection Antivirus provides real-time, in-the-cloud lookups for the latest threat intelligenceÌHIPS with suspicious behavior detectionÌWeb protection with malicious site protectionÌDownload scanningÌDevice control including removable storage, optical media, modems, Bluetooth, wireless, infrared and more * New in UTM Accelerated (9.2)** New in UTM Advantage (9.3)*** New in UTM Elevated (9.4)ÌWeb in Endpoint enforcement of web policy and webmalware scanning on the endpoint with full policyand reporting synchronization with the UTMUTM Endpoint ManagementÌFully managed within the UTMÌEasy deployment from the UTM using using our installer ÌMonitor connected endpoints, threat statusand device utilization with full log accessÌAlerts for infected endpoints*SEC Endpoint Integration*ÌI ntegration with Sophos Enterprise ConsoleEndpoint Management provides UTM webpolicy and reporting for Web in EndpointLogging and ReportingÌLogging: Remote syslog, nightly rotation, email/ftp/SMB/SSH archiving and log management serviceÌOn-box reporting: Packet filter, intrusion protection,bandwidth and day/week/month/year scalesÌIdentity-based reportingÌPDF or CSV report exportingÌE xecutive report scheduling and archivingÌR eactive reporting engine crafts reports as you click on data ÌS ave, instantly email or subscribe recipients to any reports ÌP DF and CSV exporting of reportsÌN ightly compression and rotation of logsÌL og file archiving: On-box, FTP, SMB, SSH, Email and Syslog ÌH undreds of on-box reportsÌD aily activity reportingÌU RL filter override reportÌP er-user tracking and auditingÌA nonymization of reporting data to enforce privacy policy ÌF ull transaction log of all activity in human-readable formatUnited Kingdom and Worldwide Sales Tel: +44 (0)8447 671131Email:****************North American SalesToll Free: 1-866-866-2802Email:******************Australia and New Zealand SalesTel: +61 2 9409 9100Email:****************.auAsia SalesTel: +65 62244168Email:********************Oxford, UK | Boston, USA© Copyright 2016. Sophos Ltd. All rights reserved.Registered in England and Wales No. 2096520, The Pentagon, Abingdon Science Park, Abingdon, OX14 3YP, UK Sophos is the registered trademark of Sophos Ltd. All other product and company names mentioned are trademarks or registered trademarks of their respective owners.1129-02.13DD.dsna.simple。
KasperskyEP10新产品及服务介绍

系统管理
Mail & web
Agenda
1.Kaspersky Endpoint Security for Business介绍 2.报价和授权 3.IRIS 和APS服务
Kaspersky Security for Business
Bundles and product functionality
Workstations, laptops + Smartphones + File servers + Mail servers, Mail gateways + Internet gateway + Anti-spam + Collaboration servers
1 activation code + 4 key files : 1 key file for the protection of mail systems + 1 key file for the protection of Internet gateways + 1 key for anti-spam protection + 1 key file for collaboration protection
Cloud Enabled via the Kaspersky Security Network (KSN)
Core
Select
Advanced
Total
Mobile Endpoint Security
Data Protection (Encryption)
Endpoint
Management
Kaspersky EP10新产品及服务介绍
TASCAM DV-RA1000HD高分辨率音频 DSD主机录音机说明书

239PRICEVOCOP RO CDR1000-P RO CD-R/RW RECORDER A standalone CD burnerdesigned for quick burning of music and vocals on the road or on stage without acomputer. It has the ability to burn music to CD-R, CD-RW live in real-time, erasedata from CD-RW discs and create separate tracks while recording live. It featuresa digital coaxial audio input (compatible with 44.1 kHz), RCA and balanced XLR audioline in/out connections, headphone jack, and recording level control. It is 1RU andcomes rackmount ready.ITEM DE S CRIPTION PRICE CDR1000-PRO ...........CD-R/RW recorder, 1RU ...............................................................399.00 UBLISHING EZ Dupe’s Publishing Plant is a full-on produc-tion facility for all of your DVD or CD media needs. The Publishing Plant is only 23 inches wide and 21 inches deep. Its engineering design segues into an Epson Artisan 50 printer, creating a fully automatic system. It writes DVDs at 20x speed, and CDs at 48x. It features a 100 disc capacity, and is compatible with most DVD and CD formats. Includes an LICATION All models come standard with a 160GB HDD and USB2.0 interconnect. Stand-alone tower models only. Professional duplication with up to 20x speed for DVD+/-R, 8x for DVD+/-RW, 8x for DVD+/-DL, 52x for CD-R, and up to 32x for CD-RW. Available in 2- to 11-target configurations. Models shown below are most popular configurations, call for others. PRICEEPSON PP-100 DISCPRODUCER SERIESDISC PRINTERS Offering the lowest cost per print,and Epson’s renowned print quality, Discproducer has amaximum output of 100 disc per session, with an hourlyrate of 30 CDs or 15 DVDs. In print-only mode, thePP-100 can print up to 45 discs per hour. The networkedversion can receive up to five jobs at the same time andhas been optimized for working in groups. The security version is designed for applica-tions requiring top-level security and archived data protection. The Autoprinter can printonto 100 CDs and/or DVDs in one session, with an hourly rate of 95 discs. All modelsfeature bi-directional printing and print at resolutions of up to 1440x1440 dpi.ITEM DE S CRIPTION PRICEPP-100......................Epson Discproducer ...................................................................2695.00PP-100N worked version of PP-100 ..........................................................CALLPP-100NS worked version of PP-100 w/security .........................................CALLPP-100AP .................Epson Autoprinter ......................................................................1950.00AccessoriesPJIC-SET ...................Set of 6 ink cartridges, 1 in each color .......................................230.00PJIC1-C .....................Cyan ink cartridge .........................................................................40.00PJIC2-LC ...................Light cyan ink cartridge ................................................................40.00PJIC3-LM ...................Light magenta ink cartridge .........................................................40.00PJIC4-M ....................Magenta ink cartridge ...................................................................40.00PJIC5-Y .....................Yellow ink cartridge .......................................................................40.00PJIC6-K .....................Black ink cartridge ........................................................................40.00C13S020476 .............N E W !240EZ DU E MEDIA MIRROR MULTI-FORMAT DUPLICATOR The Media/Mirror backs up audio andvideo DVDs and CDs, many types of media cards (CFI/II, SD, MS-Pro Duo are most common types), andUSB media devices. Features multi-session technology,which permits several memory cards or USB devices tobe placed on a single DVD or CD. It will also place mediafrom media cards larger than CD or DVD capacity ontomultiple discs. Professional duplication with up to 20x for DVD±R, 8x for DL DVD±R, DVD+RW, 6x for DVD-RW, 56x for CD-R, and 32x for CD-RW. All units carry a 3-year manufacturer’s warranty.ITEM DE S CRIPTION PRICE MM01PIB ..................Single-target multi-format duplicator .........................................389.00MM02PIB ..................Dual-target multi-format duplicator ...........................................459.00MM03PIB ..................Triple-target multi-format duplicator ..........................................529.00EZ DUPE MEDIA MAVEN SERIES DVD /CD /MEDIACARD DUPLICATION SYSTEM This series of profes-sional duplicators is lightning fast in reproducing mirror-image copies of virtually every type of media card with theoptional media expander. It features a SATA drives for themost accurate transfer of data. Create DVD & CD cop-ies from USB directly to disc with the touch of a button.Professional duplication with up to 8x speed for DVD, 52xon CD. Optional media expander writes to Micro SD, MS/MS Duo, Mini SD, SD/SDHC and MMC cards.ITEM DE S CRIPTION PRICE MMM30 .....................1 source, 3 target DVD/CD duplicator .........................................479.00MMM50 .....................1 source, 5 target DVD/CD duplicator .........................................629.00MMM70 .....................1 source, 7 target DVD/CD duplicator .........................................769.00MMM90 ..................... 1 source, 9 target DVD/CD duplicator .......................................1019.00MMMEX .....................11 target media expander for multi-media maven .......................22.95MICROBOARDS COPYWRITER® ive bring digital-quality audio to your church, school, studio, or boardroom. Record from practically any audio source, including live feed from a microphone, a cassette deck, a mixer, and many MICROBOARDS COPY WRITER & COPY WRITER PRO CD/These towers feature industrial Optiarc recorders that copy both DVD and CD formats. In addition these support bit to bit data verification, ensuring a perfect burn every time. These support nearly every format like DVD Video, DVD ROM, DVD+R/-R, DVD-RW, DVD+RW, and dual layer DVD. Supported CD formats are CD-DA (Red Book), CD-ROM modes 1&2, XA forms 1&2, ISO 9660, Photo CD, CD-Extra, HFS, and Hybrid. The Pro versions feature onboard 320GB hard disc drives. EZ DUP E P ORTABLE USBDUPLICATORS These por-table, stand-alone USB dupli-cation systems feature userfriendly 4-key control with L CD, 2GB per minute USB duplication andbit-by-bit Compare function to confirm successful copies. No warm-up or cool-down is required. Other features include test and check functions for USB drives, real-time display of detailed information, and ergonomic, portable design.ITEM DE S CRIPTION PRICE 2CUSB .......................2 target, portable USB duplicator/tester .....................................149.956CUSB .......................6 target, portable USB duplicator/tester .....................................989.002CUSB 6CUSB MICROBOARDS G3 SERIES DISC PUBLISHERS The G3P-1000 DVD/CD disc publisher has a single recorder, with 50 disc input capacity. It burns 24x for DVDs, and 48x for CDs. Utilizes HP inkjet technology to produce images at up to 4800dpi via a single tri-color cartridge (GX-300HC). The G3PBD-1000 shares the same features but adds 8x Blu-Ray disc publish-ing capability. The G3A-1000 is an autoprinter version only. Compatible with Pentium 4 3.0GHz or greater machines running: Windows and Intel-based Macs OSX 10.5+ compatible. Comes MICROBOARDS CX-1 DVD/CD/BLU-RAY low cost-per-unit. Comes with PRINTWRITE-2 disc EZ DUPE STUDIO STANDARD RACKMOUNT SERIESDurable, stylish, and rugged designs with heavy-duty housing which are ideal for an industrial environment. These commonly feature a 250W, 350W, and 400W industrial power supply with safety approved selectable voltage, 8cm ball bearing fan to maxi-mize ventilation, and 80GB hard drive standard. Professional duplication with up to 20x speed for DVD+/-R, 8x for DVD+/-RW, 10x for DVD+/-DL, 40x for CD-R, and up to 32x for CD-RW. Units carry a 4-year manufacturer’s warranty.ITEM DE S CRIPTION PRICE RK3TDVDSOB ..3-target CD/DVD rackmt duplicator, Sony, 80 GB HDD, black ................589.00RK5TDVDSOB ..5-target CD/DVD rackmt duplicator, Sony, 80 GB HDD, black ................759.00RK7TDVDSOB ..7-target CD/DVD rackmt duplicator, Sony, 80 GB HDD, black ................899.00RK9TDVDSOB ..9-target CD/DVD rackmt duplicator, Sony, 80 GB HDD, black ..............1099.00Shop anytime. Buy online. Honesty and Valuesince 1971242MICROBOARDS QD/QDH SERIES DVD/CD DUP LICATORSAffordable duplication solutions for copying audio, video,or data. They feature small desktop footprints, anduse an easy-to-use 4 button touch panel interface.Supported formats include DVD-R, DVD+R, DVDVideo, DVD-ROM, DVD-DL, All CD formatsincluding CD+G. Also features copyverification & track extractionfeatures, USB 2.0 intercon-nect, and Zulu2 disc masteringsoftware. 1 year manufacturer’sRECORDEX RX-100 SERIES CD DUP LICATORSThese small, high-capacitysional gravity disc feeding system (as opposed to roboticpicking arms) that can load and unload a disc in just 3seconds. You can leave it unattended for hours with the100-disc input and output bin. Duplicators feature singletiple simultaneous operations. Enclosed design systemkeeps the unit dust-free and nearly silent. The RX-100PCincludes a premium software suite that allows it to ripCDs to MP3s, back up data, create and restore ISO files,erase RW discs, duplicate data discs, and burn copies ofaudio files. In addition to MP3, the unit supports WMA, WAV, and OGG formats. The RO™ COMMERCIAL RINTERS These are auto printers that create photo-quality results in under a minute. They have a smart dual cartridge system which prints true black while saving the color cartridge specifically for color applications tridges. Compatible with most major brands of optical media. Both printers use standard off-the-shelf HP ink cartridges (HP56 black, HP57 color). Minimum system requirements – Pentium Designed for industrial environments, the MX-1 and MX-2 come with 1 or 2 high-speed DVD/CD recorders, and a low cost-per-disc inkjet printer (4800dpi) for a complete publishing solution. The PF-Pro (PFP-1000) is a printer only, with no recorders. All units feature 100-disc input/output and enhanced automation for reliable loading & unloading of discs. Ships with software for Mac/PC and connects via USB2.0. Please call to verify sions are also available. Comes with PRINTWRITE-2 disc publishing software.This small autoloader has 3 recording drives, a 250GB hard drive and can make 60 discs a run. Records at speedsup to 24x for DVD±Rs & DVD±RWs, and 48x for CD-R &CD-RWs. Writes at speeds up to 40x for CD-Rs, 24x forCD-RWs, DVD-Rs, and DVD+Rs, 8x for DVD+RWs, and 6x forN E W !Tenemos ventas y servicio en Español.Expertos que hablan Español disponibles en x1178 y x1164.Honesty and Valuesince 1971。
FortiManager 自动化驱动中心化管理系统说明书

DATA SHEETFortiManagerAutomation-Driven Centralized Management Manage all your Fortinet devices in a single-console central management system. FortiManager provides full visibility of your network, offering streamlined provisioning and innovative automation tools.Integrated with Fortinet’s Security Fabric , the security architecture and FortiManager’s Automation Driven Network Operations capabilities provide a foundation to secure and optimize network security , such as provisioning and monitoring SD-WANs.Orchestrate security devices and systems on-premise or in the cloud to streamline network provisioning, security policy updates & change management.Automate your time-intensive processes and accelerate workflows to offload NOC-SOC, reduce administrative tasks and address talent shortages.Optimize Visibility to the entire digital attack surface and awareness of increasing cyber threats from one centralized location, through accurate detection, automated correlation and rapid response features.§ § § § § § §DATA SHEET | FortiManager2HighlightsSingle Pane Automation and OrchestrationFortinet Security Fabric delivers sophisticated security management for unified, end-to-end protection. Deploying Fortinet-based security infrastructure to battle advanced threats, and adding FortiManager to provide single-pane-of-glass management across your entire extended enterprise provides insight into network-wide traffic and threats.FortiManager offers enterprise-class features to contain advanced threats. FortiManager also delivers the industry’s best scalability to manage up to 100,000 Fortinet devices. FortiManager, coupled with the FortiAnalyzer family of centralized logging and reporting appliances,provides a comprehensive and powerful centralized management solution for your organization.Centralized SD-WAN Deployment & MonitoringPowerful SD-WAN management capabilities by using templates. Enhanced SD-WAN monitoring for each SD-WAN link member with visibility of link status, application performance, bandwidth utilization. The SLA targets are included in performance monitoring graphs for each WAN provider.Configuration and Settings ManagementCollectively configure the device settings - using the provisioning templates and advance CLI templates improves management of a large number of devices. Automatic device configuration backup with revision control and change audit make it easier for daily administrative tasks.Central Management of Network InfrastructureCentrally manage FortiGate , FortiSwitch, FortiExtender, FortiAP . The VPN manager simplifies the deployment and allows centrally-provisioned VPN community and monitoring of VPN connections on Google Map. FortiAP Manager allows configuring, deploying and monitoring FortiAPs from a single console with Google Map view. The FortiClient Manager allows centralized configuration, deployment and monitoring of FortiClients.Multi-Tenancy & Role Based AdministrationFortiManager equips admins with granular device and role based administration for deploying multi-tenancy architecture to large enterprises, with a hierarchical objects database to facilitate re-use of common configurations and serve multiple customers. The graphical interface makes it easy to view, create, clone and manage ADOMs. You can use ADOMs to manage independent security environments, each ADOM with its own security policies and configuration database. FortiManager enables you to group devices logically or geographically for flexible management, and the zero-touch deployment uses templates to provision devices for quick mass deployment and supports firmware version enforcement. Define global objects such as Firewall Objects, Policies and Security Profiles to share across multiple ADOMs. Granular permissions allow assigning ADOMs, devices and policies to users based on role and duties.API for Automation and OrchestrationRESTful API allows MSSPs/large enterprises to create customized, branded web portals for policy and object administration. Automate common tasks such as provisioning new FortiGates and configuring existing devices. Join Fortinet Developer Network (FNDN) to access exclusive articles, how-to content for automation and customization, community-built tools, scripts and sample code.Security Policy ManagementA set of commonly used security policies can be now grouped in a Policy Block and inserted as needed in different Policy Packages.Global policy feature that allows companies such as: Telecom, MSSP , SAAS providers applies a header and/or footer policy at the ADOM level to all the policy packages or to a selection of packages, as needed.DATA SHEET | FortiManagerHighlightsFortiManager VMFortinet offers the FortiManager VM in a stackable license model. This model allows you to expand your VM solution as your environment expands. Utilizing virtualization technology, FortiManager-VM is a software-based version of the FortiManager hardware appliance and is designed to run on many virtualization platforms. It offers all the features of the FortiManager hardware appliance.The FortiManager virtual appliance family minimizes the effort required to monitor and maintain acceptable use policies, as well as identify attack patterns that can be used to fine tune the security policy, thwarting future attackers.SpecificationsFMG-VM-10-UG FMG-VM-100-UG FMG-VM-1000-UG FMG-VM-5000-UG10 +100 +1,000 +5,000 +200 GB 1 TB 4 TB8 TB251025VMware ESX/ESXi 5.0/5.1/5.5/6.0/6.5/6.7, Microsoft Hyper-V 2008 R2/2012/2012 R2/2016, Citrix XenServer 6.0+ and Open SourceXen 4.1+, KVM on Redhat 6.5+ and Ubuntu 17.04, Nutanix AHV (AOS 5.10.5), Amazon Web Services (AWS), Microsoft Azure, GoogleCloud (GCP), Oracle Cloud Infrastructure (OCI), Alibaba Cloud (AliCloud)vCPU Support (Minimum / Maximum) 2 / UnlimitedNetwork Interface Support (Min / Max) 1 / 4Integration & Security FabricIntegration with ITSM to mitigate security events and applyconfiguration changes and policy updates. Seamless integrationwith FortiAnalyzer appliances provides in-depth discovery, analysis,prioritization and reporting of network security events. Create fabricconnectors to facilitate connections with third-party vendors viapxGrid , OCI, ESXi and others, to share and exchange data.FortiManager’s workflow for audit and compliance enables youto review, approve and audit policy changes from a central place,including automated processes to facilitate policy compliance,policy lifecycle management, and enforced workflow to reduce riskfor policy changes.Monitor and Report for Deep VisibilityAccess vital security and network statistics, as well as real-timemonitoring and integrated reporting provides visibility into networkand user activity. For more powerful analytics, combine with aFortiAnalyzer appliance for additional data mining and graphicalreporting capabilities.Network & Security Operations VisibilityAutomated data exchanges between security (SOC) workflows andoperational (NOC) workflows, creating a single, complete workflowthat not only saves time, but also provides the capacity to completeadditional incident response activities. FortiManager’s NOC-SOCdelivers advanced data visualization to help Analysts quicklyconnect dots and identify threats, simplifying how organizationsdeliver security and remediate breaches, data exfiltration, andcompromised hosts.DATA SHEET | FortiManager4Safety CertificationscUL, CB CE, BSMI, KC, UL/cUL, CB, GOST FCC Part 15 Class A, C-Tick, VCCI, CE, UL/cUL, CBSpecifications1 Each Virtual Domain (VDOM) operating on a physical or virtual device counts as one (1) licensed network device. Global Policies and high availability support available on all models* Optional redundant AC power supply, not includedDATA SHEET | FortiManager5FMG-2000EFMG-3000FSafety CertificationscUL, CBCE, BSMI, KC, UL/cUL, CB, GOSTcUL, CB, GOSTSpecifications1 Each Virtual Domain (VDOM) operating on a physical or virtual device counts as one (1) licensed network device Global Policies and high availability support available on all models. 4 + Indicates Device Add-On License availableDATA SHEET | FortiManagerOrder InformationProduct SKU DescriptionFortiManager FMG-200F Centralized management, log and analysis appliance — 2xRJ45 GE, 2xSFP, 8 TB storage, up to 30x Fortinet devices/virtual domains.FMG-300F Centralized management, log and analysis appliance — 4x GE RJ45, 2xSFP, 16 TB storage, up to 100x Fortinet devices/virtual domains.FMG-1000F Centralized management, log and analysis appliance — 2x RJ45 10G, 2x SFP+ slots, 32 TB storage, up to 1000x Fortinet devices/virtual domains.FMG-2000E Centralized management, log and analysis appliance — 4x GE RJ45, 2x 10 GE SFP+ slots, 36 TB storage, dual power supplies, manages up to 1,200Fortinet devices/virtual domains.FMG-3000F Centralized management, log and analysis appliance — 4x GE RJ45, 2x 10 GE SFP+ slots, 48 TB storage, dual power supplies, manages up to 4,000Fortinet devices/virtual domains.FMG-3700F Centralized management, log and analysis appliance — 2x10GbE SFP+, 2x1GbE RJ-45 slots, 240 TB storage, dual power supplies, manages up to 10,000Fortinet devices/virtual domains.FortiManager Device Upgrade FMG-DEV-100-UG FortiManager device upgrade license for adding 100 Fortinet devices/VDOMs (3000 series and above - hardware only)FortiManager VM Built-in Evaluation Built-in 15-day EVAL license, no activation required.Full Evaluation (60-days)EVAL license. License and activation required.FMG-VM-Base Base license for stackable FortiManager-VM. Manages up to 10 Fortinet devices/Virtual Domains, 1 GB/Day of Logs and 100 GB storage capacity. Designedfor all supported platforms.FMG-VM-10-UG Upgrade license for adding 10 Fortinet devices/Virtual Domains; allows for total of 2 GB/Day of Logs and 200 GB storage capacity.FMG-VM-100-UG Upgrade license for adding 100 Fortinet devices/Virtual Domains; allows for total of 5 GB/Day of Logs and 1 TB storage capacity.FMG-VM-1000-UG Upgrade license for adding 1,000 Fortinet devices/Virtual Domains; allows for total of 10 GB/Day of Logs and 4 TB storage capacity.FMG-VM-5000-UG Upgrade license for adding 5,000 Fortinet devices/Virtual Domains; allows for total of 25 GB/Day of Logs and 8 TB storage capacity.Additional FortiManager Items FC-10-FDN1-139-02-12 1 Year Subscription Renewal for 1 User to Fortinet Developer NetworkFC-10-FDN2-139-02-12 1 Year Subscription for Unlimited Users to Fortinet Developer NetworkFMG-SDNS License to operate FortiManager as a dedicated Secure DNS server appliance (3000 series and above – hardware only) Copyright © 2019 Fortinet, Inc. All rights reserved. Fortinet®, FortiGate®, FortiCare® and FortiGuard®, and certain other marks are registered trademarks of Fortinet, Inc., and other Fortinet names herein may also be registered and/or common law trademarks of Fortinet. All other product or company names may be trademarks of their respective owners. Performance and other metrics contained herein were attained in internal lab tests under ideal conditions, and actual performance and other results may vary. Network variables, different network environments and other conditions may affect performance results. Nothing herein represents any binding commitment by Fortinet, and Fortinet disclaims all warranties, whether express or implied, except to the extent Fortinet enters a binding written contract, signed by Fortinet’s General Counsel, with a purchaser that expressly warrants that the identified product will perform according to certain expressly-identified performance metrics and, in such event, only the specific performance metrics expressly identified in such binding written contract shall be binding on Fortinet. For absolute clarity, any such warranty will be limited to performance in the same ideal conditions as in Fortinet’s internal lab tests. Fortinet disclaims in full any covenants, representations, and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise revise this publication without notice, and the most current version of the publication shall be applicable. Fortinet disclaims in full any covenants, representations, and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise revise this publication without notice, and the most current version of the publication shall be applicable.FST-PROD-DS-FMG FMG-DAT-R47-201908。
国外部分著名数据挖掘软件评价,作者不详
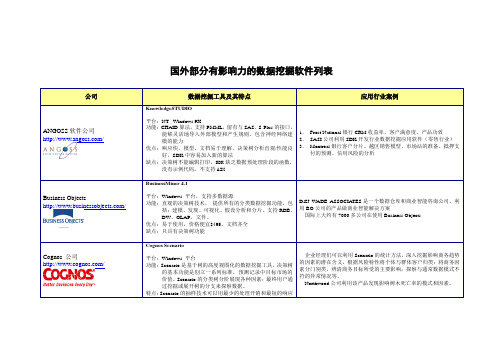
大化客户的生命周期价值,从而作出一对一的市场。学生分析人口统 计数据、POS 交易数据、商品目录和经常购买的数据。利用 MODEL1 做客户分片,分析过去推销的商品的有效性,定位将来的市场,增加 交叉销售,标记最有价值的客户。 Fort Worth Star-Telegram 是新闻单位, 利用 MODEL1 进行数据库营 销 DRG 集团是出版公司,利用 MODEL1 进行 MAIL 战略
Sears, Roebuck and Co.公司是大的服饰、家庭和汽车零售商,利用 该产品分析其忠诚卡交易的欺诈行为
IBM /data/
Decision Edge for Finance——专门为金融行业设计的综合解决方 案。Decision Edge for Finance 不仅仅是简单的报告工具,它提供了行 销经理所需的全部技术,以制定战略业务决策并开展行销活动。 Decision Edge for Insurance——端到端的解决方案,包括硬件、软 件、顾问和服务,其设计目的是帮助保险业行销经理制定战略业务决 策并开展行销活动。
IBM Discovery Series for Banking——为满足“客户至上”的银行业 需求而设计的应用程序套件。 IBM Discovery for telecommunications——为电信行业提供完美的 客户服务的应用程序套件。 Business Analysis Suite for SAP——适用于下列公司: 已经安装 SAP 事务处理系统,并需要建立数据仓库,以充分利用日常运作中收集的 所有事务数据。 Surf-Aid——数据采集应用程序,用于分析 Web 站点利用率。 Info Print Business Intelligence Solution——允许企业将自定义消息、 姓名及地址同图形和条形码相结合,向客户提供有独特个性的行销资 料。 Global Services BI Offering——包含不同角度(行业、业务功能、技 术)的战略和规划功能,以及帮助客户理解和解决业务困难、管理数 据仓库项目、开发和实现先进分析功能的方法。 Insurance Underwriting Profitability Analysis-将数据仓库和数据采 集技术相结合,帮助保险业执行人员处理保险业过程。
Sarad Radon Vision 操作手册说明书

Setting the clock (initial operation or after battery removal for longer periods)Download the software Radon Vision and the USB driver from our website (www.sarad.de) and install both on your computer.the manual of Radon Vision on our website.Sampling Turn on the display by button (B) and set the slide switch (D) to the right. The first measured results will be presented after four hours (Avg = Average of the whole measurement, 24h = average of the last 24 hours). The display will alternate between temperature/humidity and Radon automatically. The unit records the readings every four-hours. When operated from battery, the display turns off after 30 seconds. Use button (B) to turn it on again. Another keystroke turns on the backlight. If Radon 3concentration exceeds 300Bq/m , the red LED (A) starts blinking (four consecutive flashes each four seconds). To cancel a measurement, shift the slide switch (D) into the left position.Hints for battery and mains power operationThe Radon Scout Home can be operated several months by battery. Here are some tips for a long-lasting battery operation: Use batteries of best quality brand that are especially optimized for long term use and low power consumption.Reduce usage of display and backlight.In case of low battery the red indicator (A) starts blinking, one single flash each four seconds. The measurement continues for a few days but it is impossible to start a new measurement. Remove discharged batteries immediately. Do not dispose batteries in domestic waste. You are legally obliged to return them to the appropriate waste collection centres. The internal clock will be sustained for a couple of minutes during battery replacing. For mains power operation, use always a wall adapter with USB connector. Do not use the USB port of a computer for power supply.Selection of the right place of measurementDo not expose the instrument to permanent shocks or vibrations. Place the unit stationary in that room where you will stay most frequently. Avoid heat sources or radiofrequency emitting devices (e.g. mobile phones, microwave stoves, DECT phones or base stations) in the immediate surrounding of the instrument. The distance from the wall should be more than 25cm (10inches) because the wall itself could be the reason for an increased Radon concentration.Further processing of measured resultsMeasured values of the previous eight years are stored in the instrument (circular memory structure). The measured data can be read through the USB port (C) and shown, exported or printed by Radon Vision. Refer software manual (SARAD website) to findout the complete functionality of Radon Vision. Manual Radon Scout HomeThank you for the purchase of a Radon Scout Home. The instrument hasbeen designed for long-term indoor measurements of the Radonconcentration. The manufacturer cannot guarantee for damages that willresult from use other than intended. Please read the manual carefullybefore operating the unit.Set the slide switch (D) into theleft position (sampling stopped)Unscrew both screws (E) at the rear of the instrument Remove rear panel by slightly tilting on theupper rounding Insert/replace the batteries (AAA/LR6) on the left and right (bottom first – check polarity)03/2020 - SARAD GmbH www.sarad.de 1E D C A BEN。
思科 Stealthwatch 6.8(第 1.1 版) 猎捕邪恶!演示指南说明书

Cisco dCloudStealthwatch 6.8(第 1.1 版)—猎捕邪恶!最后更新日期:2017 年 2 月 13 日关于此演示“Stealthwatch 6.8(第 1.1 版)猎捕邪恶!”演示指南包括以下内容:要求拓扑入门指南帐户和密码场景 1:WebUI场景 2:Swing 客户端场景 3:检查主机组设置场景 4:执行流量查询场景 5:使用文档场景 6:确认规则/策略参数场景 7:调查警告场景 8:版权侵犯事件场景 9:检验思科 TrustSec 实施情况场景 10:恶意软件调查场景 11:调查代理连接场景 12:内部威胁检测场景 13:构建审计追踪附录 A:额外资源Cisco dCloud关于此解决方案思科 StealthWatch 通过收集并分析网络数据,为您的网络提供全面的可视性和保护,即使是规模最大、变动最频繁的网络,也尽在其掌握之中。
Stealthwatch 分析来自思科和其他供应商的路由器、交换机、防火墙和其他网络设备的行业标准 NetFlow 数据,以检测高级长期安全威胁,如内部传播的恶意软件、数据泄露、僵尸网络命令和控制流量和网络侦察。
作为对抗隐秘、复杂网络攻击的关键组成部分,Stealthwatch 通过分析网络内部(局域网和边界)的流量模式提供行为见解。
思科身份服务引擎 (ISE) 解决方案使用情景信息(如用户身份、用户权限级别、设备类型和状态)补充 Stealthwatch 基于 NetFlow 的威胁行为检测数据。
同时,StealthWatch 和思科 ISE 可为网络安全分析师提供一个集成用户、设备信息和网络流量数据的建议,使安全分析师能够以及时、高效且具成本效益的方式检测和辩明潜在威胁的严重程度。
此演示旨在让您熟悉思科 Stealthwatch 解决方案的用法。
您将在模拟的企业环境中与先前配置和部署的解决方案进行交互。
Stealthwatch 包括若干核心和可选组成部分。
Kaspersky Vulnerability and Patch Management说明书

Get full visibilityFull network visibility from a single console eliminates administrator guesswork and provides complete awareness of every application and device, including guest devices, entering the network. This drives centralized control of user and device access to organizational data and applications, in line with IT policies and regulatory compliance requirements.Enhance securityIncrease the effectiveness of your IT security and reduce time-consuming routine tasks with timely, automated patching and updates. Kaspersky Vulnerability and Patch Management provides total visibility, so you know exactly what needs to be done to keep your business safe. Automating the entire cycle of vulnerability assessment and patch management, including vulnerability detection and prioritization, patch and update download, testing and distribution, result monitoring and reporting, supports greater efficiency and significantly reduces the burden on resources.Unpatched vulnerabilities in popular applications pose a significant threat to IT security. And it’s not just zero-day vulnerabilities that are a problem - growing IT complexity further complicates the task of plugging gaps in vulnerable software swiftly: if you don’t know exactly what you’ve got, how can you secure it?Reduce complexity and strengthen security with centralized IT management toolsStreamline IT tasksKaspersky Vulnerability and Patch Management includes a set of client management tools to automate a wide range of IT administrative functions. Automated provisioning of applications and audited, remote access and troubleshooting help to minimize the time and resources necessary to set up new workstations and roll out new applications.Manage centrallyKaspersky Vulnerability and Patch Management is a managed component of the Kaspersky Security Center. Each feature is accessed and managed through this central console, using consistent, intuitive commands and interfaces to automate routine IT tasks.Kaspersky Managing and administering software updates while constantly monitoring for potential vulnerabilities is one of the most important but tedious and time-consuming tasks faced by IT departments. By centralizing and automating essential security and configuration and management tasks, such as vulnerability assessment, patch and update distribution, inventory management and application rollouts, Kaspersky Vulnerability and Patch Management saves time and optimizes security.Vulnerability Assessment and Patch ManagementMonitor results and run reportsKaspersky Vulnerability and Patch Management notifies IT administrators about a patch installation status and enables them to run reports on scans, look for potential weak spots, track changes and gain extra insights into their organizational IT security – as well as on every device and system across the corporate network. Information about existing exploits and known threats as well as CVEs (common vulnerabilities and exposures) are also available.Detect and prioritize vulnerabilitiesAutomated vulnerability scanning enables rapid vulnerability detection, prioritization and remediation. Vulnerability scanning can be delivered automatically or be scheduled according to the administrator’s requirements. Flexible policy management facilitates the distribution of updated, compatible software as well as creating exceptions.Time-saving software distributionDeploy or update remotely, from a single console. Over 150 popular applications, identified via Kaspersky Security Network can be automatically installed, after working hours if desired. Save on traffic to remote offices with Multicast technology for local software distribution.Download, test and distribute patches and updatesUpdates and patches can be downloaded automatically through Kaspersky Lab’s servers. Before distribution, these can be tested to ensure they won’t impact on system performance and employee efficiency. The administrator can limit the list of applicable patches on endpoints to approved patches only. Patches and updates can be distributed immediately or postponed until a more suitable time.Client management toolsScan your network to create hardware and software inventoriesAutomated discovery and hardware and software tracking give administrators detailed insights into every asset on the corporate network. Automated software scanning enables rapid detection of outdated software that may pose a security risk if not updated.Increase efficiency with remote troubleshootingFor reduced response times, increased efficiency and streamlined support for remote sites, Kaspersky Security Center uses Remote Desktop Protocol (RDP) and Windows Desktop Sharing technology (used in Windows Remote Assistance). Remote connection to client computers through the Network Agent allows full administrator access to the data and applications installed on the client, even if the client TCP and UDP ports are closed.An authorization mechanism prevents unauthorized remote access. For traceability and auditing, all activities performed during a remote access session are logged.Convenient OS deploymentKaspersky Vulnerability and Patch Management automates and centralizes the creation, storage and cloning of secured system images, and supports operating system (OS) deployment to new machines (as well as re-installations). All images are held in a special inventory, ready to be accessed during deployment.Client workstation image deployment can be made with either PXE servers (Preboot eXecution Environment – also for new machines without OS) or using Kaspersky Vulnerability and Patch Management tasks (to deploy OS images to managed client machines). By sending Wake-on-LAN signals to computers, you can automatically distribute the images out of normaloffice hours. UEFI support is also included.How to buyKaspersky Vulnerability and Patch Management is available:• As part of Kaspersky Total Security for Business• As part of Kaspersky Endpoint Security for Business Advanced You can also buy it as an add-on for Kaspersky Endpoint Security for Business Select or as a standalone targeted solution Kaspersky Vulnerability and Patch ManagementKaspersky LabFind a partner near you: /buyoffline Kaspersky for Business: /businessTrue Cybersecurity: /true-cybersecurity IT Security News: #truecybersecurity #HuMachine© 2019 AO Kaspersky Lab. All rights reserved. Registered trademarks and service marks are the property of their respective owners.。
25000 DWT化学品船计算机电子辅助拉锚实验

第34卷第5期2017年10月江苏船舶JIANGSU SHIPVol . 34 No . 5Oct . 201725 000 DW T 化学品船计算机电子辅助拉锚实验赵学春\刘志强2,董帆1(1.中航鼎衡造船有限公司,江苏扬州225217;.江苏科技大学机械工程学院,江苏镇江212003)摘要:对25 000 DW T 双相不锈钢化学品船锚系运用计算机虚拟拉锚仿真实验系统实现了锚系三维模型的虚拟建模以及虚拟装配,并且对船舶锚系泊锚系统进行运动仿真分析,重点对锚唇与锚座进行优化设计分析,最终 确定船舶锚系的修改方案。
实践证明:这项虚拟模拟仿真比当下根据制作木模或者刚模确定方案的方法更加精 准快捷。
关键词:化学品船;三维模型;虚拟;拉锚;仿真实验;设计;装配 中图分类号:U 664.4文献标志码:A0引言船舶锚系的收放运动受众多因素影响,比如拉锚时的航速、海水的流速和海面上的风力等。
假如 船舶锚系各个组成部分(锚链舱、导链滚轮、锚唇 等)的设计与装配不当,那么很有可能在船舶锚系 泊锚系统工作过程中出现异常。
目前,大多数船厂采用传统的制作1:1钢模或 者木模拉锚实验,经过反复拉锚实验对锚系部件形 状和位置进行调整,直至达到理想的效果,其中最为 重要的就是锚唇与锚台的外形尺寸与相对位置关 系。
木模拉锚试验存在如下问题:(1)木模拉锚试验往往安排在详细的生产设计 后期,一旦木模拉锚出现问题,修改约束条件较大,影响其他专业设计。
(2) 由于木模表面木质摩擦系数与钢摩擦系数 存在差异并且密度存在差异,时常造成木模拉锚试 验没有问题,但在后期建造过程中发现各种问题。
随着计算机在造船行业的应用和发展,近年来 研制出不少优秀的电子拉锚系统以替代木模拉锚试 验的方法。
电子拉锚系统采用计算机虚拟样机技术 确定锚系设计,并建立虚拟三维模型、开展虚拟实 验,从而摆脱钢模或木模拉锚试验。
其优点如下:(1)三维设计模型比二维图纸更为直观,便于 确定其布置角度,找到贴合点和碰撞点。
PMS320

AIPS/GAITS Surface
Problem Cause Solution
-- Lack of integration across applications & data sources -- Lack of data for decision making -- Duplication of data, applications, & work -- Data sources were developed as stovepipes (proprietary data & interface standards) & by different natural process owner -- Integrate processes through a unified data environment -- Process Reengineering – better flow of information between processes tracked in Use Cases -- Less admin work & overhead (increased efficiency) -- Better program/acquisition management (efficient spending)
Integrated Suite of Applications
Enterprise Integration
Virtual SYSCOM processes are nonEnterprise to redundant, high Enterprise velocity, automated, & achieving internal seamless. Real time process integration and Integrated information visibility extending focus Enterprise outside of the reaching a high level enterprise of process & systems integration
NAVTEX系统的安装与操作

【知识链接】
• 3.辅助性播发手段 • 尽管根据SOLAS公约第IV章“无线电通信”的要求,当船舶航行在
没有NAVTEX播发台覆盖的海域时可以通过EGC系统的Safety NET(安全网)业务获得MSI,但是国际海事组织从保障海上人命和财 产安全的角度出发,积极鼓励沿岸国主管机关为船舶提供其他发送方 式的警告和常规预报,作为国际NAVTEX业务和安全网业务的有益补 充,主要包括以下内容。 • (1)无线电传真图:包括气象图,冰况图以及其他航海者感兴趣的资料。 • (2)无线电气象以及航行警告业务:有一些海岸电台通过甚高频、中频 和高频无线电话和电传向海上船舶播发无线电气象和航行警告信息。 • 4. MSI信息的播发频率 • 海上安全信息专用广播频率如表7一1所示。根据国际海事组织和电信 联盟的规定,这些频率主要用于国际业务,语言为英语。
• (2) EGC系统。该系统主要提供国际安全网业务。信息提供者把信息 转发到特定区域的地面站,地面站通过NCS经过卫星向自己负责的洋 区广播。因此,在海上航行的船舶,无论距离地面站和信息提供者多 远,都可以接收到海上安全信息。
• (3) HF NBDP。远程安全信息播发业务是利用高频(H F)窄带直接印 字电报(NBDP)技术对A3, A4海域进行播发。根据SOLAS公约1988 年修正案规定,如果配备了高频(HF)海上安全信息的接收设备,可以 免除对EGC设备配备的要求,但是根据设备配备的实际情况,几乎 所有的远洋船舶均配备INMARSAT一C移动站,因此协调国在播发区 域安全信息时,基本全用EGC的方式播发,高频安全信息播发系统 主要用于播发沿海安全信息,对国际NAVTEX系统进行补充。
上一页 下一页 返回
பைடு நூலகம்
谛听——工业网络空间安全态势感知系统-北京威努特技术有限公司

谛听——工业网络空间安全态势感知系统DITECTING THE INDUSTRY NETWORK SPACE SECURITY SITUATION AWARENESS SYSTEM为工业4.0保驾护航·助您赢在工控安全北京威努特技术有限公司电 话:4000-680-620 传 真:************邮 箱:*********************邮 编:100085微 博:/winicssec 微信公众号:威努特工控安全地 址:北京市海淀区上地三街9号嘉华大厦F 座907室辨工控网间之万物 探恶意漏洞以补天“谛听”(DITECTING)工业网络空间安全态势感知系统()是为顺应国家网络空间安全形势,由东北大学“谛听”网络安全团队基于自身传统安全研究的优势,与国内工控安全领军企业北京威努特技术有限公司联合开发,意在辨识暴露在工业网络空间里的工业控制系统联网设备,帮助安全厂家维护工控系统安全、循迹恶意企图人士。
谛听工业网络空间安全态势感知系统支持Siemens S7、Modbus、IEC 60870-5-104、DNP3等12种工控服务的指纹识别,可实现对全球工控设备信息和开放常规服务的隐匿探测和全局采集,同时准确定位工控设备。
该搜索引擎为用户提供了查看工控服务、厂商、设备的搜索入口,用户也可根据搜索语法自定义搜索,通过可视化统计报告直观展示全球工控设备的区域分布情况、十二种工控系统服务的使用和工控系统上常规服务开放情况,提供全球工业网络空间安全威胁态势感知,为工控安全发展提供真实的数据支持。
“谛听”系统定位于工业网络空间的搜索引擎,其搜索信息全面,信息丰富,范围广效率高,对于评估工业控制系统的安全性,推动国家关键基础设施的信息安全保障工作有极为重要的意义。
系统概述/Product Overview功能特性/Features工控设备全网在线探测·全球工控协议及设备的探测与定位·网络设备及物联网设备的探测与定位·常规服务的探测与定位工控系统漏洞态势感知·工控系统漏洞扫描,漏洞库覆盖CVE、CNNVD等国际和国家级漏洞库·工控系统漏洞、设备资产智能分析及安全评分全球威胁可视化·扫描全球网络的工控系统及常规服务·多维度展示扫描分析结果,并以地域图、柱状图、饼图、多层饼图等形式呈现系统优势/Product Advantages★ 广泛的工控协议支持支持Siemens S7、Modbus、IEC 60870-5-104、DNP3、EtherNet/IP、BACnet、Tridium Niagara Fox、OMRON FINS、PCWorx、ProConOs、MELSEC-Q、Crimson V3等多种工控服务协议指纹识别,能获取使用这些协议的工控设备的基本信息,同时也可识别常规服务。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
David A. Cartes
Li Liu
Abstract- It is envisioned that in the future a naval electric ship should be operated with minimum number of human operators, while having the intelligence to automatically reconfigure its power plant under various scenarios. This should be accomplished with less response time and adequate configurations when compared to the systems operated by humans. Multi agent systems have been shown as a promising technology to achieve this goal. In this paper, the authors present a study of various agent systems being developed for Navy shipboard power systems. A particular focus is given on agent based solutions for fault detection and reconfiguration of a shipboard power system. Test scenarios are presentedfor each agent based solution.
Agent Solutions for Navy Shipboard Power Systems
Kai Huang
Sanjeev K. Srivastava
ห้องสมุดไป่ตู้
Center for Advanced Power Systems Florida State University 2000 Levy Ave,Tallahassee, FL 32310
flexible and scalable solutions.
Shipboard power systems (SPS) are responsible for supplying power to the various system including propulsion system, weapon systems, communication systems, and other service systems. SPS consists of electric components such as generators, transformers, power conversion components, mission loads, etc. During the operation of a ship, the SPS changes its working mode in order to fulfill ship's current mission. For e.g., when the faults happen in the SPS, the system has to isolate the fault(s) from the rest of the system, and maintain the availability of the power to the vital loads to increase ship's survivability and reliability. The traditional SPS is mainly operated manually. In recent years, intelligent control methods are being applied to SPS. The goals of such applications are to increase the survivability and reliability, decrease human mistakes, and improve the efficiency of the SPS.
In recent years, agent technology has been increasingly applied to SPS. The agent is defined as "a computer system that is situated in some environment in order to meet its design objectives" [4]. Multiagent systems (MAS) are systems that are composed of agents. The agents in the M\AS can work autonomously and can make independent decision in order to achieve their objectives. The agents can also interact with one another. These interactions are not simply for exchanging data but also include the social activities such as cooperation, coordination, and negotiation. Although the M\AS technology is currently being applied to several terrestrial power system problems, these agent based solutions cannot be directly applied to an SPS. The reason is that various features of SPS are different from terrestrial power systems [5]. In an SPS, the electrical proximity of large numbers of electrical components and insufficient mechanical decoupling due to finite inertia makes an SPS tightly coupled. A drop in voltage due to a fault is seen by a large number of neighboring electrical components and loads. Further a large percentage of the loads in an SPS are time varying loads such as motors. There is no external generation support available to an SPS, whereas, a utility distribution system can get support from the neighboring feeder in case of an emergency. The generationto-load ratio is much smaller in an SPS as compared to a terrestrial power system. Some electrical components, which affect the reconfiguration process, are unique to SPS. Therefore methods that were developed for utility systems
In order to maintain efficient operation of an SPS, a number of control functionalities have to be implemented. These functionalities include reconfiguration, restoration, load shedding, fault detection and isolation, condition based maintenance, and power quality monitoring and improvement, An intelligent methodology for reconfiguration for SPSs was proposed in [1]. The reconfiguration method proposed in that paper uses an expert system to determine control operations
Keywords: Multi agent system, reconfiguration, shipboard power system. fault
detection,
1
Introduction
necessary to restore power supply to deenergized loads after battle damage or cascading faults. In [2], the authors put forward a methodology for load shedding. In that paper, an analytical hierarchy process based method was used for dynamic load shedding scheme. The authors of [3] present a power node control center to provide power distribution, switch control, and conditioning functions in order to enhance the power quality of an SPS. However, in [1-3], centralized controllers with global information are required. The centralized control system without redundancy may lead to single point failure, which needs to be avoided for an SPS. Even if the control system has a backup controller, there is still a strong possibility that during a battle damage part(s) of the system will lose connectivity to the controller, depending on the location of the controller and the system topology. Comparing with centralized control systems, distributed control systems are able to avoid the single point of failure. Furthermore, the distributed control systems can provide more
