Comments on “Transparent User-Level Process Checkpoint and Restore for Migration ” by Boz
有关网络暴力的三段式英语作文120词

有关网络暴力的三段式英语作文120词全文共6篇示例,供读者参考篇1Title: Say No to Online Bullying!Hey guys! Today I want to talk to you about something super important - online bullying. Did you know that online bullying can hurt people's feelings and make them feel really sad? It's not cool at all! So let's learn more about it and see what we can do to stop it.First of all, what is online bullying? Online bullying is when someone says mean or hurtful things to someone else on the internet. It can happen on social media, in text messages, or even in online games. Cyberbullies might call people names, spread rumors about them, or even threaten them. It's really not nice and it can make people feel terrible.So, what can we do to help stop online bullying? The most important thing is to always be kind and respectful to others online. If you see someone being bullied, don't join in - stand up for them and tell an adult. You can also block the bully or reportthem to the website or app they're using. And remember, if you wouldn't say it to someone's face, don't say it online!In conclusion, online bullying is a serious problem that can have a big impact on people's lives. We all have the power to make the internet a safer and happier place by being kind to others and standing up against bullies. So let's work together to say no to online bullying and spread kindness instead! Let's make the internet a place where everyone feels safe and respected. Thanks for listening, guys! Let's all be cyber superstars and make a positive difference online!篇2Title: Don't Bully Online!Paragraph 1:Hey everyone! Today I want to talk to you about something super important - online bullying. It's when someone says mean things to you or makes you feel bad on the internet. It can happen on social media, through text messages, or even in online games. It's not cool and it's not okay. People should always be kind to each other, even when they're online. If someone is being mean to you online, you can always talk to agrown-up or someone you trust. Remember, you're awesome just the way you are!Paragraph 2:Online bullying can make you feel sad, scared, or even angry. It's not nice to have someone say mean things to you whenyou're just trying to have fun on the internet. But you know what? You don't have to listen to them. You can block them, report them, or just ignore them. You are in control of how you feel and no one has the power to make you feel bad about yourself. Remember, you are strong, you are smart, and you are loved. Don't let anyone tell you otherwise.Paragraph 3:Let's all work together to make the internet a kinder and safer place. If you see someone being bullied online, don't be a bystander. Stand up for them and let them know that they're not alone. Be a good friend and spread kindness wherever you go. Treat others the way you want to be treated, both online and in real life. Together, we can make a difference and stop online bullying for good. Remember, we're all in this together!So, let's all make a promise today to be kind, spread love, and stand up against online bullying. We can make the internet a better place for everyone. Don't bully online!篇3Title: Say No to CyberbullyingHey guys! Today I want to talk to you about something super important - cyberbullying. It's like when people say mean things or spread rumors about someone online. It's not cool and it can really hurt people's feelings.First of all, we should always remember to be kind to each other online. Just because we're not talking face to face doesn't mean we can say whatever we want. Words can still hurt, even when they're typed on a screen. So let's use our online powers for good and spread positivity instead of negativity.Secondly, if you see someone being cyberbullied, don't just stand by and watch. Speak up and tell a teacher or a parent. We need to look out for each other and make sure everyone feels safe and supported, both online and offline. And remember, it's never okay to join in on cyberbullying or make fun of someone on the internet.Lastly, let's all work together to create a kinder online community. We can start by thinking before we type and treating others with respect. We all deserve to feel happy and loved, so let's make sure our online world is a place where everyone feels safe and included. Together, we can say no to cyberbullying and spread kindness instead.So let's all make a promise today to use our words to lift each other up, not tear each other down. Let's stand together against cyberbullying and make the internet a better place for everyone. Thanks for listening, guys!篇4Yo! Today, let's talk about something super important: cyberbullying. It's like when people are mean and rude to each other online. And guess what? It's not cool at all!First of all, cyberbullying is just not nice, dude. Imagine if someone said mean things about you on the internet. How would you feel? Probably not too good, right? It can make you sad, angry, or even scared. No one deserves to be treated like that, online or offline.Secondly, cyberbullying can really hurt someone's feelings. The things people say online can stick with them for a long time.It can make them doubt themselves and feel like they're not good enough. That's so not fair! We should all try to lift each other up and be kind, instead of tearing each other down.Lastly, we need to stand up against cyberbullying. If you see someone being bullied online, don't just ignore it. Speak up and say something! Let the bully know that their behavior is not okay. And if you're the one being bullied, don't be afraid to reach out for help. Talk to a teacher, parent, or trusted adult. Remember, you're not alone.So let's all work together to make the internet a safer and kinder place. Let's spread love and positivity instead of hate and negativity. Together, we can put an end to cyberbullying for good!篇5Title: Stop Cyberbullying!Hey guys, have you ever heard of something called cyberbullying? It's when mean people use the internet to say hurtful things to others. It's like when someone calls you names or spreads rumors about you online. It's not cool at all!First of all, cyberbullying can make people feel really sad and hurt. Imagine if someone said mean things about you on social media where all your friends can see. That would be embarrassing and it could make you feel like nobody likes you. It's not fun to be on the receiving end of cyberbullying, so we need to make sure we're always kind and respectful online.Secondly, cyberbullying can also be really dangerous. People might start to believe the lies that are being spread about you, and it could affect your reputation. Some kids even feel so upset by cyberbullying that they don't want to go to school anymore. That's not fair at all! We should all stand up against cyberbullying and make sure everyone feels safe and happy online.Lastly, we need to remember that our words have power, even when they're typed on a screen. Before you send a message or post a comment, think about how it might make the other person feel. If it's not something nice, then maybe it's better not to say it at all. Let's spread kindness and positivity instead of hate and negativity online.So let's all work together to stop cyberbullying and make the internet a better place for everyone. Remember, be kind, be respectful, and always think before you type. Let's make sure thatcyberbullying has no place in our online world. Let's stand up against cyberbullying!Stay safe and be kind, everyone!篇6Title: Say No to CyberbullyingHey, guys! Today, I want to talk to you about something really important – cyberbullying. Have you ever heard of it? Cyberbullying is when people are mean to each other online, like sending nasty messages or spreading rumors on social media. It's not cool at all!First of all, cyberbullying is never okay. It can hurt people's feelings and make them feel really sad. Just because you're behind a screen, doesn't mean you can say whatever you want. Remember, there's a real person on the other side who has feelings too. So, always think before you type and be kind to others online.Secondly, if you see someone being cyberbullied, don't just stand by and watch. Speak up and report it to a trusted adult or teacher. You can also support the person being bullied bysending them a kind message or offering to help. Together, we can make the internet a safer place for everyone.In conclusion, let's all work together to stop cyberbullying. Treat others the way you want to be treated and spread kindness online. Remember, words can hurt, so let's use ours to uplift and encourage each other. Say no to cyberbullying and yes to kindness!。
NQA – 1 QUALITY ASSURANCE REQUIREMENTS FOR NUCLEAR FACILITY APPLICATIONS

TYPICAL USERS
Utilities / Power Generators ASME Section III Users Department of Energy National Laboratories, Repositories and Fuel Fabrication facilities Trans Alaska Pipeline Offshore Nuclear Power Projects LES Enrichment Project
N46.2 QA Program Requirements for Post Nuclear Fuel Cycle Facilities
N45.2.6-Qualification of Inspection, Examination and Testing Personnel for Nuclear Power Plants N45.2.9-Requirements for Collection, Storage and Maintenance of Quality Assurance Records N45.2.10-Quality Assurance Terms and Definitions N45.2.11-Quality Assurance Requirements for the Designof Nuclear Power Plants N45.2.12-Requirements for Auditing of Quality assurance Programs for Nuclear Power Plants N45.2.13-Quality Assurance Requirements for Control of Procurement of Items and Services for Nuclear Power Plants N45.2.23-Qualification of Quality Assurance Program Audit Personnel for Nuclear Power Plants
译林版高中英语必修第三册UNIT 2 Natural disasters UNIT 2单元综合巩固练

Ⅳ.阅读理解 A
Apps to Help in a Disaster Disasters almost always arrive unexpectedly.But there are computer apps to help people prepare for disasters.Some apps warn users when a disaster has taken place.
ⅠⅡⅢⅣⅤ
Life360 The Life360 app provides a service to keep the loved ones ers can set up a network of people to share their location,chat and get informed when they are near someone in their network.People in the same network can use the app on iPhone and Android devices. The app helps users communicate when they are in danger.The location sharing function can be suspended(暂停) when desired. The Life360 app is free,with some services available for a fee.
ⅠⅡⅢⅣⅤ
1.Which is not the feature of the Siren GPS Mobile app? B A.It connects users to emergency services. B.It is useless if your cellphone network is down. C.Rescuers can get your health information through it. D.Rescue workers can know where the injured person is. 解析 细节理解题。根据Siren GPS Mobile部分第二段中“But it also works on Wi-Fi if cellphone networks are down after an emergency.”可知,B项“如果 你的手机网络坏了,它就没用了。”不是Siren GPS Mobile应用程序的特点。
Practice CS 安装指南说明书

PRACTICE CS INSTALLATION INSTRUCTIONSInstalling Practice CS (1)Downloading and installing the license (2)Obtaining and installing licenses via CS Connect (2)Installing licenses received via email (2)Running desktop setup (for network installations only) (3)Use this document to do the following:▪install Practice CS®▪download and install the license and application updates, and▪run desktop setup (for network installations only)Installing Practice CSYou can install Practice CS to a network or to a standalone computer.Notes▪The installation process may require you to restart the computer. If you are installing the application on a network, be sure that all other users have logged off the network.▪Installation must be performed at the computer that you want to designate as the Database Server.▪The computer where the shared files are installed must be turned on in order for the application files to be available to users (workstations).1. If you haven’t done so already, download the application installation file from our website. (See thePractice CS download page for instructions.)2. From the computer on which the database will reside, verify that you are logged in to your computeror server as an administrator.3. Close all open applications, including background virus protection applications.4. Navigate to the EXE file that you downloaded from the website. If you saved the file to the browser’sdefault location, the EXE will be in your DOWLNLOADS folder.5. Double-click the EXE to extract the files to the default folder (C:\Practice CS\ <version> Download) orto another folder of your choosing. If the installation wizard doesn’t start automatically, navigate to the folder to which you extracted the files and double-click Setup.exe.6. When Practice CS Setup starts, click the Install Practice CS link. The wizard will guide you throughthe rest of the installation.7. Practice CS uses Microsoft® SQL Server® (including 2008 Express Edition and later) for storing data.The computer on which the data is located (the SQL server) must be turned on in order for others to access the data. In addition, you must create an exception within the firewall for the instance of SQL Server you are using (recommended) or disable the firewall (not recommended) to run Practice CS. Ifyou need assistance in creating an exception for the instance of SQL Server you are using, please refer to your firewall’s documentation.Downloading and installing the licenseAfter you install the application files, use CS Connect™ to download and install the license. In rare cases, you may receive a license file via email. If you received a license file via email, please skip the following procedure and proceed to “Installing licenses received via email” on page 2. Otherwise, complete the following procedure to install the licenses for your Practice CS application.Obtaining and installing licenses via CS ConnectComplete the following procedure to open Practice CS and use CS Connect to obtain and install the licenses electronically.1. Verify that you are logged in to your computer or server as an administrator.2. Start Practice CS.3. Click Cancel to close the login dialog.4. To open CS Connect, choose Help > About Practice CS, and click the Download Licenses button.5. Enter your firm ID (listed on your CS web account and on your mailing label) and your firm mailingaddress ZIP code, or PIN, and click Next.Note: If the Connect – Communications Setup dialog opens, verify or select the applicablecommunications settings, and then click OK to close the dialog.6. In the CS Connect dialog, click OK. CS Connect logs in to our secure data centers and downloadsyour licenses.7. Follow the remaining prompts to install the licenses.Installing licenses received via email1. If you received a Practice CS license file via email, please follow the instructions in that emailmessage and then follow the steps below.2. The installation wizard prompts you to choose the destination location for Practice CS. You need tochoose the folder where the shared files are installed. (The final destination for the application should be a folder called \WINCSI. For example, you may have installed your shared files inF:\APPS\WINCSI.)3. After you have verified the destination path, click Next to continue with the installation.Important! Even if you received your original license files via email, all updates to your Practice CS license information are available only via CS Connect. If you require an updated license in the future (for example, if you purchase a license for an optional add-on module later), you will need to download and install the updated license via CS Connect, as described in “Obtaining and installing licenses via CS Connect” on page 2.Running desktop setup (for network installations only) Important! If you installed the shared files on a network, you must also run the desktop setup program on each workstation.The desktop setup program ensures that each workstation meets the minimum operating system requirements and confirms that all required components are installed. When you run the desktop setup program, a shortcut to the single network installation of Practice CS (on your firm’s server) is added to each desktop. This keeps all firm-wide files and data in a single location on the server. We recommend that network users do not install the full application on their local computers.1. Verify that you are logged in to your computer as an administrator.2. Close all open applications.3. Click Start on the Windows taskbar and choose Run.Note: In Windows 8, enter Run in the search box.4. In the Run dialog, enter Z:\path\Practice CS\Desktop\Setup.exe (where Z represents the mappeddrive letter for the network path to the server on which you installed the shared files, and path is the path to your Practice CS folder). For example, if you installed the shared files inF:\WINAPPS\WINCSI, you would need to enter F:\WINAPPS\WINCSI\Practice CS\Desktop\Setup.exe in the Run dialog or \\<name of server>\WINAPPS\WINCSI\Practice CS\Desktop\Setup.exe.Note: If you need to uninstall the Practice CS desktop setup from a workstation, choose Start > Control Panel > Programs and Features, select Practice CS, and then click the Uninstall button.In Windows 8, enter Control Panel in the search box and choose Programs & Features.5. Click OK and follow the prompts.6. Remote Entry requires a local installation of Microsoft SQL Server, version 2008 or later. If you choseto enable Remote Entry, you will be prompted to select an existing instance of SQL Server, or to install a new instance. Select an existing instance of SQL Server to use for Remote Entry, or click the option to install a new instance. Then click Next.7. When prompted that the Practice CS setup has been successfully completed, click Finish.。
(完整版)仁爱英语九年级上册知识点归纳

Unit 1 Topic 1I.重点词组1.take photos 照相2.learn…from…向……学习3.in detail 详细地4.in order to为了5.give support to…为……提供帮助6.se.sth.onesel.亲眼所见某物7.keep in touch with 与……保持联系8.sorts of各种各样的9.make progress 取得进步10.draw up 起草,拟定11.thanks to 由于II.重点句型1.I.on.plac..sa.childre.workin.fo..crue.boss.在一处我看到了孩子们为残忍的老板干活。
2..fel.sorr.fo.them.我对他们深表同情。
3.Wher.hav.yo.been.Jane.你去过哪里, 简?4.Sh.ha.gon.t.Cub.t.b..volunteer.她去古巴当志愿者了。
5.Ther.goe.th.bell.铃响了。
6.Thoug..ha.n.tim.t.travel..stil.fel.ver.happy.虽然我没有时间去旅行,但是我仍然感到很开心。
7.No.ou.countr.ha.develope.rapidly.现在我们国家发展迅速。
III.语法1.现在完成时态的构成: 助动词have/has+动词的过去分词.bac.fro.you.hometown.2.现在完成时态的句式:e.g.(1..hav.bee.t.Moun.Huan.wit.m.parents.(2) I haven’t seen him for a long time.(3) Where have you been?(4.——Hav.yo.eve.cleane..room?.——Yes..have..No..haven’t.3.have.ha.been.have/ha.gon.的区别have/has been to sp.表示曾经到过某地—— have/has gone to sp.表示已经去了某地e.g.(1..hav.bee.t.Moun.Huan.wit.m.parents. .(2.Sh.ha.gon.t.Cub.t.b..vo lunteer.Unit 1 Topic 2I.重点词组1. get lost 迷路2. each other 彼此3.at least 至少4take place发生5because of 因为6.b.stric.wit.sb.对某人严格要求.7.carry out 实行8.be short of 缺乏9.take measures to do sth.采取措施做某事10.be known as…作为……而著名11.work well in doing…在……方面起作用12.a couple of 一些13keep up with赶上,跟上II.重点句型1.Hav.yo.foun.hi.yet.你已经找到他了吗?2.——.reall.hat.t.g.shopping.我的确讨厌购物。
Linksys智能WiFi无线路由器说明书
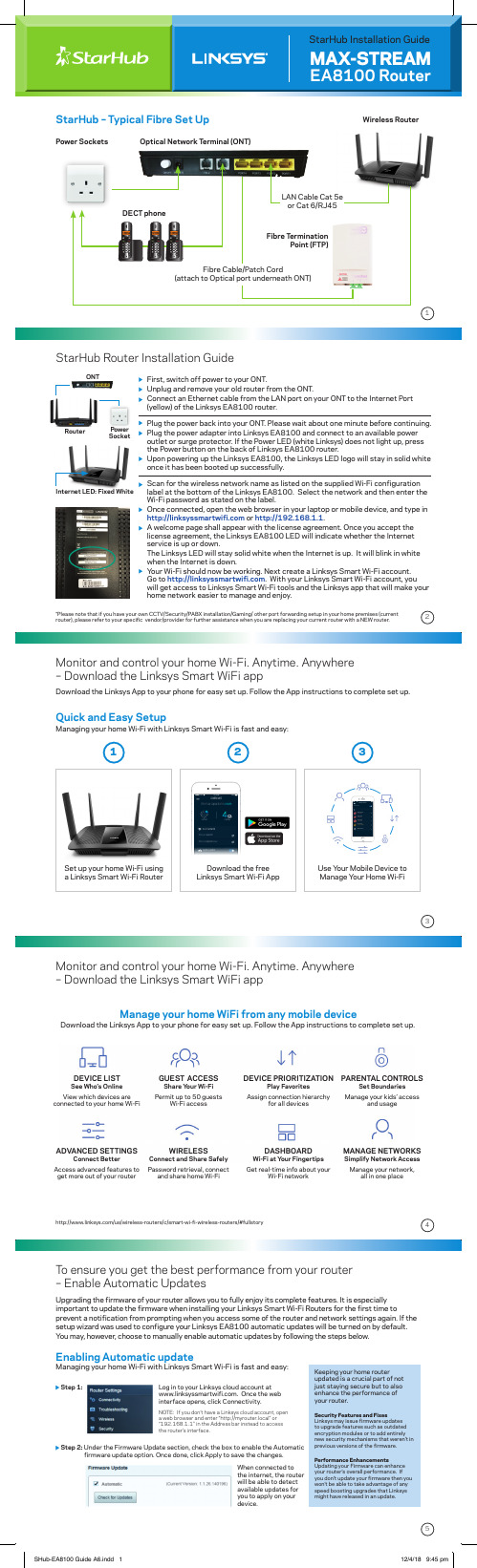
/us/wireless-routers/c/smart-wi-fi-wireless-routers/#fullstoryMonitor and control your home Wi-Fi. Anytime. Anywhere – Download the Linksys Smart WiFi appDownload the Linksys App to your phone for easy set up. Follow the App instructions to complete set up.Manage your home WiFi from any mobile deviceDEVICE LIST See Who’s Online View which devices are connected to your home Wi-FiGUEST ACCESSShare Y our Wi-Fi Permit up to 50 guestsWi-Fi accessDEVICE PRIORITIZATIONPlay FavoritesAssign connection hierarchyfor all devicesPARENTAL CONTROLSSet Boundaries Manage your kids’ accessand usageADVANCED SETTINGSConnect BetterAccess advanced features to get more out of your routerWIRELESSConnect and Share Safely Password retrieval, connectand share home Wi-FiDASHBOARD Wi-Fi at Y our Fingertips Get real-time info about yourWi-Fi networkMANAGE NETWORKSSimplify Network Access Manage your network,all in one placeStarHub – Typical Fibre Set UpFibre T erminationPoint (FTP)Wireless RouterPower Sockets Optical Network T erminal (ONT)LAN Cable Cat 5eor Cat 6/RJ45StarHub Installation GuideEA8100 RouterMAX-STREAMDECT phone*Please note that if you have your own CCTV/Security/PABX installation/Gaming/ other port forwarding setup in your home premises (current router), please refer to your specific vendor/provider for further assistance when you are replacing your current router with a NEW router.Internet LED: Fixed WhiteONTPower SocketRouterMonitor and control your home Wi-Fi. Anytime. Anywhere – Download the Linksys Smart WiFi appDownload the Linksys App to your phone for easy set up. Follow the App instructions to complete set up.Quick and Easy SetupSet up your home Wi-Fi using a Linksys Smart Wi-Fi Router Download the free our Mobile Device to Manage Y our Home Wi-FiManaging your home Wi-Fi with Linksys Smart Wi-Fi is fast and easy:11: When connected tothe internet, the router will be able to detect available updates for you to apply on your device.Under the Firmware Update section, check the box to enable the Automatic firmware update option. Once done, click Apply to save the changes.In order to optimize your antennas’ maximum signal, the following positions are recommended:For multi-storey environments:• two (2) of the antennas should be pointing straight up and the other two (any two) should be adjusteddepending where you need the coverage and where you want the signal to radiate.For Additional information and how to videos visit the links below./fi/support-article?articleNum=142491https:///watch?v=tXlS9eObXuATroubleshooting1. How can I reset the Linksys EA8100 to factory defaults?ways to reset the Linksys EA8100 to factory defaults:Press and hold the Reset button on the back panel of the Linksys EA8100 for about – Log in to your Linksys Smart Wi-Fi Account. Under Router Settings, click Troubleshooting > Diagnostics . Click 2. I have reset the Linksys EA8100 and now I can’t launch the setup page. What should I do?Y ou need more help?Alternatively, you may call Linksys at:6701-69718820-02607 Rev.A00ou can try the following troubleshooting suggestions:Access your Linksys Smart Wi-Fi account locally by opening your web browser and typing in . Input the admin password which is ‘admin’If your computer has a static IP Address, make sure it has valid DNS numbers. If not, set the computer Remote Assistance –Should you need more helpIMPORTANT NOTICE: In activating Agent Assist, the Linksys Support Agent (“Agent”) will have access to Customer’s Smart Wi-Fi account settings but not to computer settings or any information stored on the computer, and the Customer’s Wi-Fi network name and password will be visible to the Agent. We therefore strongly encourage Customer to change his/her Wi-Fi password immediately after the Agent Assist session.。
google浏览器网页第一次加载时不能播放声音问题Uncaught(inpromise)D。。。

google浏览器⽹页第⼀次加载时不能播放声⾳问题Uncaught(inpromise)D。
Google states: Autoplay with sound is allowed if:User has interacted with the domain (click, tap, etc.).On desktop, the user's Media Engagement Index threshold has been crossed, meaning the user has previously play video with sound.On mobile, the user has added the site to his or her home screen.意思是必须⽤户有点击浏览的页⾯后才能播放声⾳,下⾯是正确的做法DOMException: The play() request was interruptedDid you just stumble upon this unexpected media error in the Chrome DevTools JavaScript Console?Uncaught (in promise) DOMException: The play() request was interrupted by a call to pause().orUncaught (in promise) DOMException: The play() request was interrupted by a new load request.You're in the right place then. Have no fear. I'll explain and .What is causing thisHere's some JavaScript code below that reproduces the "Uncaught (in promise)" error you're seeing:DON'T<video id="video" preload="none" src="https:///file.mp4"></video><script>video.play(); // <-- This is asynchronous!video.pause();</script>The code above results in this error message in Chrome DevTools:Uncaught (in promise) DOMException: The play() request was interrupted by a call to pause().As the video is not loaded due to preload="none", video playback doesn't necessarily start immediately after video.play() is executed.Moreover since , a play() call on an a <video> or <audio> element returns a , a function that returns a single result asynchronously. If playback succeeds, the Promise is fulfilled and the playing event is fired at the same time. If playback fails, the Promise is rejected along with an error message explaining the failure.Now here's what happening:1. video.play() starts loading video content asynchronously.2. video.pause() interrupts video loading because it is not ready yet.3. video.play() rejects asynchronously loudly.Since we're not handling the video play Promise in our code, an error message appears in Chrome DevTools.Note: Calling video.pause() isn't the only way to interrupt a video. You can entirely reset the video playback state, including the buffer,with video.load() and video.src = ''.How to fix itNow that we understand the root cause, let's see what we can do to fix this.First, don't ever assume a media element (video or audio) will play. Look at the Promise returned by the play function to see if it was rejected. It is worth noting that the Promise won't fulfill until playback has actually started, meaning the code inside the then() will not execute until the media is playing.Example: Autoplay<video id="video" preload="none" src="https:///file.mp4"></video><script>// Show loading animation.var playPromise = video.play();if (playPromise !== undefined) {playPromise.then(_ => {// Automatic playback started!// Show playing UI.}).catch(error => {// Auto-play was prevented// Show paused UI.});}</script>Example: Play & Pause<video id="video" preload="none" src="https:///file.mp4"></video><script>// Show loading animation.var playPromise = video.play();if (playPromise !== undefined) {playPromise.then(_ => {// Automatic playback started!// Show playing UI.// We can now safely pause video...video.pause();}).catch(error => {// Auto-play was prevented// Show paused UI.});}</script>That's great for this simple example but what if you use video.play() to be able to play a video later?I'll tell you a secret. You don't have to use video.play(), you can use video.load() and here's how:Example: Fetch & Play<video id="video"></video><button id="button"></button><script>button.addEventListener('click', onButtonClick);function onButtonClick() {// This will allow us to play video later...video.load();fetchVideoAndPlay();}function fetchVideoAndPlay() {fetch('https:///file.mp4').then(response => response.blob()).then(blob => {video.srcObject = blob;return video.play();}).then(_ => {// Video playback started ;)}).catch(e => {// Video playback failed ;(})}</script>Warning: Don't make your onButtonClick function asynchronous with the async keyword. You'll lose the "user gesture token" required to allow your video to play later.Play promise supportAt the time of writing, HTMLMediaElement.play() returns a promise in , Firefox, Opera, and . is still working on it.Danger zone<source> within <video> makes play() promise never rejectsFor <video src="not-existing-video.mp4"\>, the play() promise rejects as expected as the video doesn't exist. For <video><source src="not-existing-video.mp4" type='video/mp4'></video>, the play() promise never rejects. It only happens if there are no valid sources.。
Clearswift SECURE Email Gateway说明书

With email still being the primary business collaboration tool, organizations need to ensure that the content and information they send and receive is both appropriate and permitted to enter or leave the organization. The Clearswift SECURE Email Gateway (SEG) helps to secure against critical information data loss; protecting the intellectual property and brand reputation of your organization and ensuring compliance with current regulations and standards.Clearswift’s award-winning deep-content inspection capabilities facilitate the competitive advantages inherent in open and safe communications; transforming email from a high-risk communication channel to one tailored exactly to your organization’s needs.The Gateway scans emails for sensitive content, and based on a granular organizational policy it provides the necessary flexibility to permit multiple behaviours, depending on the senders and recipients of the message. The Clearswift Adaptive Redactionfunctionality allows for content to be dynamically modified to make the content safe rather than having to stop and block and forcea remediation.Inbound threat protectionFeaturing integrated, cloud-assisted Kaspersky and / or Sophos anti-virus, with automatic updates every fifteen minutes toprovide the latest protection. These technologies are supplemented with zero-hour anti-malware and active code detection to ensure that no malware comes in, or goes out, via email. Targeted ransomware and spyware attacks typically use email with commonly used Office and PDF files as a means to deliver a payload. If these exploits manage to reach the desktop they will be run with the user privileges of the recipient, which could provide access to sensitive data. So as an addition to standardanti-malware features the Structural Sanitization feature permits macro’s, scripts and Active/X to be removed from messages, PDF and Office file formats significantly reducing the risk of targeted ransomware and spyware attacks being successful.Message Sanitization is able to remove URLs, attachments and HTML from messages to ensure there is no potential riskfrom that message.Best-of-Breed spam detectionThe new Clearswift SECURE Email Gateway comes with a completely redesigned anti-spam engine incorporating thebest-of-breed Mailshell component. This reduces the amount of spam reaching the end-user and the number of false positives.DMARC, SPF and DKIM support enables yet further spam reduction and with an Outlook Spam Reporter included, spam can be monitored, registered and eliminated. Featuring a new multi-layer spam defence mechanism using IP reputations, greylisting, signatures, SPF, RBL, recipient authentication and machine learning (Bayesian) engines to provide > than 99.9% detection rates, the SEG is able to drastically reduce the amount of time users spend managing their inboxes and significantly reduces theeffect of malware contained in spam.Context-aware content inspection policiesFlexible policies and context-aware content inspection mean you no longer have to choose between free-flowing communications and unacceptable risk. Flexible policy is the key to any real-world deployment. If the policy is too restrictive then people either cannot work effectively, or they find ways to get around their security policy.Adaptive RedactionClearswift’s unique Adaptive Redaction features permit the content of messages and attachments to be modified dynamically based on policy. The Data Redaction feature allows information to flow when before it would have been blocked. Customers can create policies to change specific words and phrases in messages and documents with “*” characters to make the content safe.This can apply to Credit Card numbers, Social Security details, Project codes, individual names or any custom value.Figure 1. Clearswift Adaptive Redaction: Data RedactionThe Document Sanitization feature can remove outstanding revision changes, clearing history and fast-save data that can also hold embarrassing critical information being accidentally disclosed. Document properties, such as “Author”, “Organization” and “Status” can be completely removed or bespoke properties can be preserved.DATA REDACTIONAdaptive RedactionOriginal Email with attachmentsEmail after Adaptive RedactionAdaptive Data Loss PreventionData loss is one of today’s biggest organizational concerns. Be it the latest designs, customer details or private employee information, the loss of intellectual property can ruin a company, both from a financial and reputational perspective.To reduce the chances of accidental data loss, the SECURE Email Gateway is able to control messages based on their content and their context. Context is provided through integration with Active Directory or LDAP, so policy can be applied to a specific individual or group (or the whole organization). The content of the message is checked through looking for text in the message body, subject line and also attachments, against 180 predefined policies.Policies consist of standard words, phrases or regular expressions, which can be used to look for complex alphanumeric patterns. These patterns could be used to identify an organization’s assets, such as credit cards, IBAN numbers, social security numbers, and many more.These phrases can be combined using Boolean and positional operators to create examples such as: • Credit .FOLLOWEDBY=1. Card• Confidential .AND. (Project .OR. Material)• C hecking for policy violations can also take place within image content such as screen shots, attachments and embedded content in documents.ComplianceStaying within the bounds of a regulatory framework is very important. To help you maintain compliance, the SECURE Email Gateway includes standard templates and dictionaries for common terms that may indicate a data breach.The Gateways are supplied with customisable dictionaries for GLBA, HIPAA, SEC and SOX to save deployment time. Organizations that must adhere to PCI and PII regulations can use a custom dictionary and the special ‘credit card’ and ‘social security’ tokens. Customers can augment the standard dictionaries with ones that may be more applicable.Organizations that must adhere to PCI and PII regulations, such as the EU GDPR, can use a custom dictionary and any of the more than 200+ pre-configured PCI and PII tokens to simplify policy definition and enforcement. Customers can augment the standard dictionaries with ones that may be more applicable.Some information will always need to be shared and email encryption is another important capability of the Gateway, ensuring that regulations relating to sensitive data sent over the internet are protected using strong encryption. The HITECH Act in the US and the EU’s General Data Protection Regulation make it clear that sensitive data must be encrypted when sent via email; the SECURE Email Gateway supports a number of different encryption mechanisms to provide flexibility as required.Email encryptionWith TLS as standard, and cost options to provide either S/MIME, PGP and password protected files or Web portal-based encryption, the Email Gateway offers a variety of options to cater for customer requirements. Whichever you choose, the Gateway allows sensitive data to be delivered securely, in seconds, using the optimal format for the recipient.Management and reportingThe user interface of the Gateway is powerful, yet simple to use. With roles based administration, automation and policy re-use, it’s quick and easy to build policy, manage violations, track messages and report on trends and behaviour. In this way, valuable insight is provided without consuming valuable admin resource.Deep content inspectionTrue file-type detection that recognizes files by signature and not by extension allows the Clearswift SECURE Email Gateway to understand files accurately. Compressed file archives are opened and the contents examined in real-time; embedded documents are discovered, and content is scanned in depth, to ensure data leakage is kept at bay.Flexible deployment optionsYou decide how you want to buy and deploy the Clearswift SECURE Email Gateway, either as a pre-installed hardware appliance, as a software image that can be loaded on a choice of hardware platforms, or alternatively virtualized in a VMware / Hyper-V environment. The Clearswift SECURE Email Gateway is also available as a Cloud solution using providers such as AWS and Azure or from Clearswift (regional offerings) as hosted virtual servers where you maintain control of the platform, but with the convenience and benefits of a Cloud delivery model.About ClearswiftClearswift is trusted by organizationsglobally to protect their criticalinformation, giving them the freedomto securely collaborate and drivebusiness growth. Our uniquetechnology supports a straightforwardand ‘adaptive’ data loss preventionsolution, avoiding the risk of businessinterruption and enabling organizationsto have 100% visibility of their criticalinformation 100% of the time.Clearswift operates world-wide, havingregional headquarters in Europe, AsiaPacific and the United States. Clearswifthas a partner network of more than 900resellers across the globe.More information is available atUK - International HQClearswift Ltd1310 WatersideArlington Business ParkTheale, Reading, BerkshireRG7 4SATel : +44 (0) 118 903 8903Fax : +44 (0) 118 903 9000Sales: +44 (0) 118 903 8700Technical Support: +44 (0) 118 903 8200Email:*******************AustraliaClearswift (Asia/Pacific) Pty LtdLevel 17 RegusCoca Cola Place40 Mount StreetNorth Sydney NSW 2060AustraliaTel: +61 2 9424 1200Technical Support: +61 2 9424 1210Email:*******************.auGermanyClearswift GmbHIm Mediapark 8D-50670 CologneGermanyTel: +49 (0)221 828 29 888Technical Support: +49 (0)800 1800556Email:******************JapanClearswift K.KShinjuku Park Tower N30th Floor3-7-1 Nishi-ShinjukuTokyo 163-1030JapanTel: +81 (3)5326 3470TechnicalSupport************Email:**********************United StatesClearswift Corporation309 Fellowship Road, Suite 200Mount Laurel, NJ 08054United StatesTel: +1 856-359-2360Technical Support: +1 856 359 2170Email:******************.comIntuitive web-based interface Ease of use and no requirement to learn complex syntax or Linuxcommands.Multi-gateway consolidated reporting Consolidated reporting view of user’s activities for easier analysis andsharing of management data.Multi-gateway message tracking Enables a view of where messages came from, how they wereprocessed and where they went across multi-gateways, complete withmanual or scheduled export capability.Centralized SYSLOG, SCOM, SNMP, SMTP Alerting Consolidate to a central SIEM, or use SCOM, SNMP or SMTP management alerts for a ‘lights out’ data centre deployment.* Cost Option。
NOTIFIRE WEB SERVER NWS-3 说明书

NWS-3NOTI•FIRE•NET™Web ServerDN-6928:C • A0-810GeneralThe NOTI•FIRE•NET™ Web Server(NWS-3) is a web-baseddevice that acts as an HTML server, allowing remote access tothe NOTI•FIRE•NET™ network via the Internet or an intranet.With the NWS-3 interface, users can view fire alarm controlpanel (FACP) event history, event status, device properties andother information based on access permissions defined by thesystem administrator. All data available on the NWS-3 is a“snapshot” of the data on the NOTI•FIRE•NET™ network atthe time the browser requested the information.The NWS-3 interfaces to the Internet/intranet using an IP-basedwire Ethernet connection.FeaturesFOR THE NOTI•FIRE•NET™ WEB SER ER ANDBROWSER CONFIGURATION TOOL•Access NOTI•FIRE•NET™ device statuses and properties remotely via the Internet or an intranet.•Automatically send up to 50 emails or text messages in response to any system event.•Compatible with standard and high speed NOTI•FIRE•NET™.•Unacknowledged Beep feature, if enabled, causes the com-puter browsing the NWS-3 to beep at three-second intervals if there are unacknowledged events in the Multiple Event List.•Compatible with NOTI•FIRE•NET™ version 5.0 and higher.•One NWS-3 supports multiple users.•Standard Ethernet over IP connection.•Y our system remains secure by installing the NWS-3 behind your network firewall.•Supports up to 64 operator and 64 administrator accounts.•Built-in password security and user-access record.•Multiple users can access the web server at the same time.•Supports standard Microsoft® Internet Explorer 8.0 or higher.•Intuitive Explorer-style user interface.•Ability to use V eriFire® Tools (version 3.0 or higher) for remote programming/configuration of the NWS-3 and ONYX® Series products.NOTE: No fire alarm control functions are permitted. The NWS-3 is an ancillary device and not intended for primary reporting.CompatibilityThe NWS-3 is compatible with NOTI•FIRE•NET™ version 5.0 and higher for the following panels and devices:•ONYX® Series.•AM2020/AFP1010 (version 5.0 SIB).•AFP-200 (events only).•AFP-300/AFP-400.•BACnet Gateway (events only).•NCS Network Control Station (events only).•NCA(-2) Network Control Annunciator (events only).•Compatible with high speed network HS-NCM version 1.0 and higher.NOTE: The NWS-3 is NOT intended as a primary annunciator and is ancillary in nature.System Requirements•NOTI•FIRE•NET™ Web Server (NWS-3).•NCM card.•Browser: Microsoft Internet Explorer, version 8.0 or higher.•JAVA version 6 or later.Agency Listings and ApprovalsThese listings and approvals apply to the NOTI•FIRE•NET™Web Server. In some cases, certain modules or applications may not be listed by certain approval agencies, or listing may be in process. Consult factory for latest listing status.•UL/ULC Listed: S635.•CSFM: 7165-0028:0247.•FDNY: COA#6045.NFN-GW-EM-3.JPGDN-6928:C • 08/15/2012 — Page 1 of 2Page 2 of 2 — DN-6928:C • 08/15/2012ONYX ®, NOTIFIER ®, and VeriFire ® are registered trademarks, and NOTI•FIRE•NET ™ and ONYXWorks ™ are trademarks of Honeywell International Inc. Microsoft ® and Windows ® are registered trademarks of Microsoft Corporation.©2012 by Honeywell International Inc. All rights reserved. Unauthorized use of this document is strictly prohibited.This document is not intended to be used for installation purposes. We try to keep our product information up-to-date and accurate. We cannot cover all specific applications or anticipate all requirements.All specifications are subject to change without notice.For more information, contact Notifier. Phone: (203) 484-7161, FAX: (203) 484-7118.System Architecture•Connect to the NOTI•FIRE•NET™ network. The NWS-3can be connected to the NOTI•FIRE•NET™ network via the Network Control Module (NCM) network interface card (see diagram).•The NWS-3 can be directly connected to ONYX® series pan-els for stand-alone panel applications.•The NWS-3 can also be connected to high speed networks using HS-NCM network interface.System Architecture DiagramNWS -3 HS-NCM OR NCM ARCHITECTURECAB-4 Cabinet with NWS-3 Assembly and HS-NCM W/SF/MF or NCM W/F BoardNFN NetworkInternet/IntranetSupported FACP Supported FACPPC Browser InterfaceHS-NCM-W/SF/MFor NCM-W/FHS-NCM-W/SF/MF or NCM-W/FNWS-3 DIRECT PANEL ARCHITECTUREInternet/IntranetPC Browser InterfaceSupported ONYX Series FACPwith Web Server Assembly。
《Concentrator连接手册》说明书

Step Four: Set the node numbersEach concentrator must have a unique node number so the adapter can recognize it in the chain. In general, you should set the node number of a concentrator according to its relative position in the chain. For example, the concentrator closest to the adapter would be node 1, the second would be node 2, and so on. To set the node number, do the following:1.Wait until you see P1 displayed on the front panel of the unit (about30 seconds after you power on the unit). This indicates that thePower-on Self Test has successfully completed.2.Press the right arrow button once to display the current node number.(1n is the default.)3.Press the left arrow button to increment the node number. Node num-bers go up to 8n and then return to 1n.4.To save the node number currently displayed on the front panel, pressthe right arrow button once. If the number was successfully saved to EEPROM, the display will read Pn.Step Five: Install peripheral cablingYou can connect printers, terminals, modems (or any other standard EIA-232 device to be controlled by applications on the computer) to the EPC/CON-16 concentrator using a cable between the peripheral and the concentrator.On the peripheral end of the cable, the cable connector depends on the requirements of the peripheral. The EPC/CON-16 (or PORTS/Xem mod-ule) end of the cable must fit either an RJ-45 or DB-25 connector, depending on the model you have.The pin assignments for each type of EPC/CON-16 (or PORTS/Xem module) connector are shown on the back.Refer to the CD-ROM for more detailed cabling information.What Next?At this point the hardware installation for your EPC/X system is com-plete. However, since the EPC/X host adapter and the EPC/CON-16 con-centrators must have software downloaded to their internal RAM beforethey become functional, you must next install the software drivers foryour operating system.•Read the instruction booklet for the CD-ROM that came with yourEPC/X system for instructions on installing software.•View the on-line documentation on the CD-ROM for more informa-tion about your EPC/X system.The Digi logo and AccelePort are registered trademarks of Digi International. EPC/X,EPC/CON-16, PORTS/8em, PORTS/16em, Modem/4em, and Modem/8em are trademarksof Digi International. All other brand and product names are trademarks of their respectiveholders.© Digi International Inc., 1998; All Rights Reserved; Information in this document is subject to change without notice and does not represent acommitment on the part of Digi International.Digi provides this document “as is”, without warranty of any kind, either expressed orimplied, including, but not limited to, the implied warranties of fitness or merchantabilityfor a particular purpose. Digi may make improvements and/or changes in this manual or inthe product(s) and/or the program(s) described in this manual at any time.This product could include technical inaccuracies or typographical errors. Changes are peri-odically made to the information herein; these changes may be incorporated in new editionsof the publication.AccelePort EPC/X SystemEPC/X ISA Host AdapterEPC/CON-16 ConcentratorHardwareInstallation GuideIntroductionAn AccelePort® EPC/X™ system consists of an EPC/X host adapter cou-pled with EPC/CON-16™ concentrators from which EIA-232 peripheraldevices such as printers, terminals or modems can be cabled and con-trolled. The adapter has two lines that can each support one or more con-centrators. Multiple concentrators can be linked in a chain, and DigiPORTS/8em™, PORTS/16em™, Modem/4em™, and/or Modem/8em™modules can be added to a concentrator to expand the number of portsavailable.Figure 41. Example EPC/CON-16 setupThis installation guide describes how to plan your setup and install theEPC/X host adapter and concentrator hardware.DB-25 Pin assignments RJ-45 Pin AssignmentSignalDescription Pin Signal Description PinGND Chassis Ground1*RI Ring Indicator1TxD T ransmitted Data2DSR Data Set Ready2†RxD Received Data3RTS Request T o Send3RTS Request T o Send4GND Chassis Ground4CTS Clear T o Send5TxD T ransmitted Data5DSR Data Set Ready6RxD Received Data6SG Signal Ground7SG Signal Ground7DCD Data CarrierDetect8CTS Clear T o Send8DTR Data T erminalReady20DTRData T erminalReady9RI Ring Indicator22DCD Data CarrierDetect10* Chassis Ground is also availableon the connector shell† Pin 2 can be configured for DCD(through Digi software) if you wantto connect using an 8 pinconnector91000748 AStep One: Plan your setupAn EPC/X system can be set up in a variety of ways. Before you start your installation, be sure of the following:Number of components. You can connect up to fourteen concentrators and Xem modules onto one EPC/X host adapter (using both lines). It is a good idea to balance the number of connections on each line.Having 12 concentrators and modules on one line, and 2 on the other, for example, may not make the best use of line resource.Location of components. Using the cables that come with the product, concentrators can be located up to ten feet apart. (The daisy-chain cable that comes with each Xem module allows it to be stacked on top of the concentrator to which it is attached via the EBI connector.)If your installation calls for greater distances between concentrators, you can use twisted pair cabling in a maximum cumulative length of up to 2000 feet (600 meters) from the host adapter.Note:The length of twisted pair cabling affects the maximum data transfer rate that can be expected over the cable. Thelonger the length, the lower the rate. To maintain a baudrate of 10 Mbaud, the maximum cumulative twisted paircable length cannot exceed 30 feet (9 meters).You can also use fiber optic cable (a special fiber optic conversion option is available from Digi) that will allow a distance of up to 1.2 miles (2000 meters) from the adapter.For even greater distances, you can attach a synchronous modemdirectly to the adapter, and remotely locate concentrators and Xem modules attached to a second synchronous modem.Cabling. Before beginning the installation, be sure that you have the cables that you will need for the distances between concentrators, as well as cables for the peripherals that you will be attaching to the con-centrators and Xem modules. EPC/CON-16 concentrators andPORTS/Xem modules are available with RJ-45 or DB-25 connectors for peripheral cabling. You will need to be sure that you have cables of the correct length and with the right connectors to properly attach the devices you want to use with each concentrator or Xem module. Power Requirements. Each EPC/CON-16 concentrator (and Modem/Xem module) requires its own power supply. Before pro-ceeding with installation, you should verify that adequate line power is available where each concentrator (and Modem/Xem) will beinstalled. Note that PORTS/Xem modules do not require power sup-plies when attached to an EPC/CON-16 concentrator.Additional information about the options available with the EPC/X sys-tem, such as specifications and cabling details, is provided on the CD-ROM that is packaged with the host adapter.Step Two: Install the EPC/X ISA host adapterBefore installing the EPC/X host adapter, you should do the following:•Check system resources for a free I/O port address. The EPC/Xadapter uses four bytes of address space on the I/O bus of the com-puter into which you are installing it.•Wear an ESD wrist strap to ground yourself while handling theadapter. If one is not available, discharge static electricity from yourbody by touching an unpainted metal surface, such as the computer’schassis, prior to handling the adapter.•Record the adapter serial number, which will enable Digi to provideyou with better service, should the need arise. The serial number labelhas this general format: S/N: (S) XXX XXXXX•Unplug power from the PC.Figure 42. EPC/X ISA host adapter1.Set the I/O port address of the adapter to one of the followingaddresses using the DIP switch at the location indicated in Figure 1:2.Remove the computer’s cover.3.Locate an available ISA slot in your computer and remove the slotplate.4.Insert the adapter into the slot and screw the endplate to the computerchassis. The endplate must be screwed into the computer chassis toremain in compliance with Part 15 of FCC rules.5.Replace the computer’s cover.6.Attach an EIA-422 cable to the connector of each line you will use onthe adapter.Step Three: Install concentrators and add-ons1.Position concentrators and Xem modules (if any) at the location youhave prepared according to the plan you developed in Step One.2.Attach the cable from line l on the adapter to the connector labelledHOST ADAPTER on the first concentrator of the chain that is to beconnected to Line 1.Figure 43. Side Panel of EPC/CON-16 concentratorIf you are cabling multiple concentrators together, attach anothercable to the REMOTE connector of the first concentrator. Connect thiscable to the HOST ADAPTER connector of the second concentrator.Continue cabling until all concentrators in the chain are connected.3.Install a terminator plug in the REMOTE connector of the last concen-trator in the chain.4.Repeat steps 2 and 3 for Line 2 on the adapter (if you are using it).5.To cable PORTS/Xem or Modem/Xem modules to the EBI bus of aconcentrator, attach one end of an EBI cable to the EBI OUT connec-tor on a concentrator and the other end to the EBI IN connector on theXem module. Continue similarly using the EBI IN and EBI OUT con-nectors on the Xem modules until all the modules for a concentratorare cabled together.6.Attach power supplies to the concentrators (and Modem/Xem mod-ules).7.Turn on power to the unit(s).I/Oaddress1234108-10Bh up up down down118-11Bh up down up down128-12Bh up down down down208-20Bh down up up down228-22Bh down up down down308-30Bh down down up down328-32Bh down down downdown。
ELM-07S IEC 62056-21 to Modbus converter Instructi

IEC 62056-21 to Modbus converter ELM-07S Converter SeriesInstruction ManualELM-07S is microcontroller-based RS-485 IEC62056-21 (former IEC61107) to Modbus RS-485 RTU/TCP converter. ELM-07S is used as a gateway/bridge in building and industrial networks where it is needed to read IEC62056-21 (mainly electricity meters) in Modbus RS-485 RTU based SCADA systems. ELM-07S can connect up to 32 IEC62056-21 devices in its network. It is mounted on standard M36 DIN rail and comes with both Modbus RTU and TCP.1. General technical data- max. number of IEC62056-21 devices – 32 - max. number of decoded IEC62056 registers per device – 64 - power supply voltage – 165-235 VAC (210-270 VDC) - max. power consumption < 5 W - ambient temperature, operating - -20÷+50 °C - ambient temperature, storage - -50÷+90 °C - air humidity - 40÷90 % - dimensions (H/W/D) – 105/107/74 mm - IP protection class – IP20 - IEC62056 interface – 300, 1.2k, 2.4k, 4.8k, 9.6k , 19.2k, 38.4k, 57.6k, 115.2k bps, 7 bit even - RS-485 RTU Modbus interface baud rate – 300, 1.2k, 2.4k, 4.8k, 9.6k, 19.2k , 38.4k, 57.6k, 115.2k bps, 8 bit even - Modbus TCP interface – TCP/IP 10/100 Mbit, port 502, DHCP-capable - display - 3 LEDs (on, comm IEC, comm Modbus) - weight – 475 g2. ELM-07S operationELM-07S begins operation immediately after power-up. The sequence is the following:Initialization mode (0.2-0.3 s)– In the first 0.2-0.3s the device initializes its internal data structures. LED “on” is lit. – After 10s ELM-07 starts reading the network of IEC62056-21 devices. All devices to be readshould have their addresses preprogrammed in ELM-07S memory. This process is repeated after predefined time.Normal operationIn normal mode ELM-07 waits predefined period of time and then reads all pre-programmedIEC62056-21 devices. For each device (32 max) there are 128 Modbus registers (4096 registers total). These registers are updated on each device readout. The value of each IEC62056-21 register is split in two Modbus registers. Before reading the IEC62056-21 devices it is needed their ID-addresses and the registers for readout to be programmed in the ELM-07 internal memory. IEC62056-21 devices can be added, deleted, their registers changed any time when device is operational.The Modbus registers can be accessed any time either on Modbus RTU or TCP, as well assimultaneously via both RTU and TCP.3. Mounting and electrical connectionsELM-7S should be mounted on standard M36 din-rail. All connections should be made with isolated multi-wire cables with cross section 0.5mm 2÷2.5mm 2. Mounting should be done in industrial enclosurewith high IP class. All the connections are shown in the figure and the tables below:С1 ‘Power’ – 3P terminal blockNo Description 1, 3 Power input L , N 2 Power Grounding inputPEС2 ‘IEC62056-21' – 5P terminal blockNo Description 1 GND 2,4 RS-458 “+” (B) 3,5 RS-458 “-” (A)C3 ‘Modbus RTU' – 5P terminal block No Description 1 GND 2,4 RS-458 “+” (B) 3,5 RS-458 “-” (A)С4 ‘Modbus TCP' – RJ-45 No Description - RJ-45/TCP Ethernet4. WarrantyThe warranty of the device is limited to 3 years from the date of sale. If the device shows any defect or malfunctions during that period, the manufacturer is obligated to repair the device in its own service for manufacturer’s expense, or, if the repair is impossible, to replace the device with new one. The transportation costs to the manufacturer’s service are due to the client. The warranty voids if this manual’ instructions are not met, warranty seals are removed or the device was opened by unauthorized by the manufacturer personnel.Serial number:.................... Date of sale:.............................Signature:................................5. The package containsELM-7S - 1 pcs.Instruction manual - 1 pcs.6. Manufacturer1528 Sofia, Bulgaria7 Iskarsko shausse blvd, Trade center “Europe”, building 7B, floor 3 phone/fax: +359 2 975 81 05 , e-mail:******************。
关于停止网络暴力的英语作文120词

关于停止网络暴力的英语作文120词In today's digital era, online violence has become a pervasive issue, threatening the safety and well-being of individuals worldwide. From cyberbullying to hate speech, this form of violence leaves victims feeling helpless and alone. It is crucial to recognize that words can hurt as much as physical blows, and the anonymity of the internet often emboldens perpetrators to act with impunity.To combat online violence, it is essential to educate individuals about its harmful effects. Social media platforms must take responsibility and implement strict policies to combat hate speech and cyberbullying. Moreover, users must be encouraged to report instances of online violence, ensuring that perpetrators are held accountable for their actions.Additionally, we must promote a culture of kindness and respect online. By speaking out against online violence and amplifying voices of compassion and understanding, we can create a safer and more inclusive digital space for everyone. Only by working together can we stop onlineviolence and ensure that everyone is treated with dignity and respect.**停止网络暴力——行动的呼唤**在当今数字化时代,网络暴力已成为一个普遍存在的问题,威胁着世界各地个人的安全和福祉。
关于解决网络欺凌的英语作文

关于解决网络欺凌的英语作文英文回答:Cyberbullying is a serious issue that affects many people, especially young people, in today's digital age. It can take many forms, such as spreading rumors, sharing embarrassing photos, or sending threatening messages online. As someone who has experienced cyberbullying firsthand, I understand the emotional toll it can take on a person.One way to combat cyberbullying is to educate people about the impact of their words and actions online. Many times, people may not realize the harm they are causing when they engage in cyberbullying. By raising awareness and promoting empathy, we can help prevent cyberbullying from happening in the first place.Another important step in addressing cyberbullying isto create a safe and supportive online community. This means standing up to bullies and supporting those who arebeing targeted. It's important for people to feel like they have a support system in place when they are facing cyberbullying.In my own experience, I was able to overcome cyberbullying by reaching out to friends and family for support. They helped me see that the hurtful words of bullies did not define me and that I was not alone in facing this issue. By surrounding myself with positive influences, I was able to build my confidence and stand up to the bullies.Overall, addressing cyberbullying requires a collective effort from everyone in the online community. By promoting kindness, empathy, and support, we can create a safer and more positive online environment for all.中文回答:网络欺凌是一个严重的问题,尤其是在当今数字化时代影响许多人,特别是年轻人。
如何应对网络欺凌英语作文120字

如何应对网络欺凌英语作文120字全文共6篇示例,供读者参考篇1How to Deal with CyberbullyingHi there! My name is Sam, and I'm a 4th grader at Oakwood Elementary School. Today, I want to talk to you about a really important topic – cyberbullying. You might be wondering, "What is cyberbullying?" Well, it's when someone is being mean, rude, or hurtful to another person online. It can happen on social media, in online games, through text messages, or even in emails. Cyberbullying is a big problem, and it can make people feel really sad, angry, or scared.I know how it feels because last year, some kids in my class started making fun of me on a group chat. They called me names and said mean things about how I looked or how I dressed. At first, I didn't know what to do. I felt really upset and didn't want to go to school anymore. But then, I talked to my parents and my teacher, and they helped me figure out how to deal with the bullies.Here are some tips that I learned, and that I want to share with you:Don't respond to the bullies. I know it's really tempting to fight back or say something mean to them, but that's exactly what they want. If you respond, it just gives them more attention and makes them think they can keep bullying you.Block the bullies. Most social media sites and apps have a way for you to block people who are being mean to you. That way, you won't see their messages or posts anymore. Ask your parents or a trusted adult to help you if you're not sure how to do it.Save the evidence. Take screenshots or save any messages, posts, or emails from the bullies. That way, you have proof of what they're doing, and you can show it to your parents, teachers, or even the police if the bullying gets really bad.Tell someone you trust. This is super important! Don't try to deal with cyberbullying all by yourself. Talk to your parents, teachers, or another trusted adult about what's happening. They can help you figure out what to do next and make sure you're safe.Be kind online. This might seem like a weird tip, but it's actually really important. When you're kind and respectful to others online, it sets a good example and makes it harder for bullies to target you.Don't forget to take care of yourself. Cyberbullying can be really stressful and upsetting. Make sure you take breaks from your devices and do things that make you happy, like playing outside, reading a book, or spending time with friends and family who care about you.Remember, you didn't do anything wrong – the bullies are the ones who are being mean and hurtful. You have the right to feel safe and happy, both online and in real life.If you're being cyberbullied, don't be afraid to ask for help. There are lots of people and organizations out there that want to support you and make sure you're okay. Together, we can stop cyberbullying and make the internet a kinder, safer place for everyone.So there you have it, my friends! Those are my tips for dealing with cyberbullying. I hope they help you feel more confident and prepared if you ever have to deal with mean people online. Remember, you're not alone, and there's nothingwrong with asking for help. Stay strong, stay kind, and keep being the awesome person you are!篇2How to Handle CyberbullyingHi there! My name is Alex, and I'm ten years old. Today I want to talk to you about something really important - cyberbullying. It's when people are mean to you online, like sending you nasty messages or posting embarrassing pictures of you without your permission. It can really hurt, but don't worry, there are ways to deal with it!First of all, if someone is cyberbullying you, don't respond or retaliate. That's exactly what they want - to get a reaction out of you. Instead, save all the evidence like screenshots of the messages or posts. You'll need that proof to show adults what's going on.Next, block the bullies from contacting you online. Remove them from your friends lists, block their accounts and phone numbers, everything. You don't need that negativity in your life! If the bullying is happening on a game, website or app, report them to the moderators too.The most important step is to tell a trusted adult - like your parents, teacher, school counselor or principal. They can help stop the bullying and make sure you stay safe, both online and in the real world. Don't keep it a secret, because that lets the bullies win.While the adults are handling it, try your best to ignore the bullies and stay positive. Spend time with your real friends who care about you. Do activities you enjoy to take your mind off the situation. Remember, the bullying is NOT your fault and you didn't do anything to deserve it.Cyberbullying is just plain wrong, but sadly it happens a lot these days. Bullies get their power by making others feel scared, alone and ashamed. Don't let them! By blocking them, reporting them, and getting help from adults, you can take that power away.I know how awful cyberbullying feels, but I promise it does get better. Stay strong, stay brave, and don't let the bullies dim your light. You've got this! Thanks for listening, and spread the word to stop cyberbullying!篇3How to Deal with CyberbullyingCyberbullying is when people are mean to you online or through texting and apps. It can really hurt your feelings and make you not want to go on your phone or computer. I know because it happened to me when I was in 4th grade.There was this kid in my class named Jake who started saying awful things about me on this group chat we were all in. He called me names like "loser" and "dweeb" and made fun of my haircut. A bunch of other kids started joining in and laughing at his mean comments. It made me feel so embarrassed and sad, especially when I saw that some of my closest friends didn't stick up for me.At first I didn't tell anyone because I was scared Jake and his friends would make it even worse for "snitching." But eventually I couldn't take it anymore and I broke down crying in front of my mom. That's when she realized what was going on and we were able to get the bullying to stop. Looking back, here are some tips I wish I had known about dealing with cyberbullies:Don't respond or retaliate. As tempting as it is to send a mean message back, that will only make the bullies keep going after you. The best thing is to not react at all.Block the bullies. Most apps and games let you block people so you don't have to see their mean messages or comments. Blocking them takes away their power.Save the evidence. Take screenshots or download any bullying messages or posts. Having proof makes it easier to report them and get the bullying stopped.Report the behavior. Don't keep cyberbullying a secret. Tell parents, teachers, coaches, or other trusted adults about what's happening so they can step in.Be kind online yourself. Set a good example for how to treat others online with respect. Don't say anything you wouldn't say in person.Protect your privacy. Don't share personal information or passwords that could let bullies get into your accounts. Use privacy settings.Take breaks from technology. If the bullying gets really bad, log off for a while to take care of your mental health.Don't pass it on. When you see someone else being bullied, don't like or share the mean posts. Stick up for the person getting bullied instead.Build confidence offline. Spend time doing activities you're good at and being around positive people. That way bullies' harsh words won't affect your self-esteem as much.Get help if you're struggling. Experiencing bullying can lead to depression, anxiety, and other hard feelings. Talk to a counselor or therapist for support.After telling my mom, she contacted Jake's parents and our teacher to put a stop to the bullying group chat. I also worked on building my confidence through sports and scouts. Now I'm older and that experience made me realize how crucial it is to treat people with kindness online and off.While cyberbullying is never the victim's fault, following tips like these can help protect you and push back against the bullies' harmful behavior. Don't let them make you afraid to participate online or feel bad about yourself. With defenses in place and strong self-confidence, cyberbullies' insults will have a hard time bringing you down.篇4How to Deal with CyberbullyingCyberbullying is when someone is mean to you online or on their phone or tablet. It can happen on social media, in games, through texts or emails, or anywhere else on the internet. Cyberbullying can make you feel really sad, scared, embarrassed or angry. But there are ways to stop it and get help.First, it's important to know that cyberbullying is never your fault. You didn't do anything to deserve being bullied online. The bully is the one doing something wrong, not you. Don't blame yourself or feel ashamed.If someone sends you a mean message or post online, don't respond to it. Bullies want to get a reaction out of you and make you upset. If you don't react, they might get bored and stop. Just ignore them.You should also block or unfriend the bully so they can't contact you anymore. On most apps and games there is a way to block someone so you don't see their messages or posts. Ask an adult if you need help figuring out how to do this.The next thing to do is tell a trusted adult about what's happening. This could be a parent, teacher, school counselor or principal. Show them the messages or posts from the bully. Adults can help stop the bullying and make sure you stay safe online.It's also a good idea to keep all the evidence of the bullying by taking screenshots or recording it somehow. That way you have proof of what happened in case you need to show it to someone.You don't have to deal with cyberbullying alone. There are organizations that can help, like and . They have advice for kids as well as adults on what to do about online bullies.If the bullying is really serious and won't stop, or if you ever feel unsafe, report it to the police or other authorities right away. Threatening violence, stalking or relentless harassment online is illegal.Try your best not to let the bullies get you down. Remind yourself that it's not your fault and you did nothing wrong. The bully is the one with the problem, not you. Stay positive and keep doing the things you love online, like playing games with friends or watching videos.Remember that you're not alone and there are people who can help if you're being cyberbullied. Don't be afraid to speak up and get an adult involved. With the right support, the bullying can stop and you can feel safe online again.It's awful to be bullied, whether it's online or in person. But you have the power to stop it by blocking bullies, reporting them, and getting help from adults you trust. Don't let the cyberbullies win - stand up for yourself and stay positive. You've got this!篇5Here's an essay on "How to Deal with Cyberbullying," written in English from a primary school student's perspective, with a length of approximately 2,000 words.Title: Dealing with the Cyberbullies: A Guide for KidsHi there, friends! It's me, your pal Emily. Today, I want to talk about something really important – cyberbullying. You know, that mean and hurtful behavior that happens online, like when someone sends you nasty messages or spreads rumors about you on social media.Now, I know what you might be thinking – "But Emily, I'm just a kid! Why would anyone want to bully me?" Well, let me tell you, bullies can be pretty mean and they don't always need a good reason to be mean. Sometimes, they're just feeling bad about themselves and they take it out on others.But you know what? We don't have to take their bullying lying down! We can fight back in a really cool and smart way. And that's what I'm going to teach you today.First things first, if someone is being a big meanie to you online, don't respond! I know it's tempting to tell them off or say something really clever to put them in their place, but that's just going to make things worse. Instead, take a deep breath and walk away from your computer or phone for a little bit.Once you've calmed down, it's time to gather some evidence. Screenshot or save any nasty messages or posts they've made about you. This will come in handy later.Now, it's time to tell a grown-up you trust, like your parents, a teacher, or a school counselor. Show them the evidence you've collected and let them know what's been going on. They can help you figure out the next steps to take, whether it's reporting the bully to the social media platform or even going to the authorities if things get really serious.But what if the bullying doesn't stop, even after you've told an adult? That's when it's time to get a little creative! Here are some fun and smart ways to deal with cyberbullies:Kill 'em with kindness! Sometimes, the best way to shut down a bully is to be super nice to them. Compliment them or say something positive about them. It might just throw them off their game and make them realize how mean they're being.Make a joke out of it! Bullies hate it when you don't take them seriously. So, if they're saying something mean about you, make a joke out of it or respond with a funny meme or GIF. It'll show them that their words don't have any power over you.Block and report! Most social media platforms have tools that allow you to block and report bullies. Use them! That way, you won't have to see their nasty messages or posts anymore, and the platform can take action against them.Start a kindness campaign! Spread some positivity and kindness online by starting a campaign or challenge that encourages people to say nice things to each other. It might just inspire the bullies to be nicer too!Take a break from social media! Sometimes, the best thing you can do is take a break from the online world for a little while. Unplug, go outside, and hang out with your friends in the real world. It'll remind you that there's so much more to life than what happens online.Remember, my friends, cyberbullying is never okay, and you don't have to put up with it. By following these tips and staying strong, you can show those bullies that they can't bring you down!And if you ever need someone to talk to or just want to share a funny meme or joke, you know where to find me. I'll always have your back, because that's what friends are for!Alright, that's all for now. Stay awesome, stay kind, and don't let the cyberbullies get you down!Your pal,Emily篇6How to Deal with CyberbullyingCyberbullying is when people are mean to you online. It can happen on social media, gaming sites, texts or emails. Cyberbullies might call you names, spread rumors about you, or share embarrassing pictures or videos without your permission. It can make you feel really sad, scared or angry.If you're being cyberbullied, the most important thing is to not respond or retaliate. That's exactly what the bullies want - toget a reaction out of you. Instead, save the evidence by taking screenshots or printing out the messages or posts. This proof can help if you need to report them later.Next, block the bullies so they can't contact you anymore. On most apps and websites, you can block certain users so you don't see their mean comments or messages. Your parents or teacher can help you figure out how to do this on different platforms.Tell a trusted adult like your parents or a teacher about what's happening. Bullying should never be kept a secret. The adults can work with the school or website to try to stop the bullying behavior. They can also give you advice and emotional support during this difficult time.Sometimes it helps to take a break from the app, game or website where the bullying is happening until things calm down. Spend time doing activities you enjoy with family and friends who care about you. Their love and support can help you feel better.If the bullying persists or escalates, there are organizations that can help like . Your parents may want to report serious cases to the police or lawyers if threats or harassment are involved.Most importantly, remember that being bullied is never your fault. Bullies pick on people for no good reason, and it says much more about their own unhappiness than it does about you. Don't let their cruel words damage your self-esteem. You have value, and you deserve to feel safe both online and offline.Stay strong, surround yourself with positive people, and don't be afraid to keep speaking up about bullying until it stops. With patience and support, you can overcome this challenge. Things will get better!。
网络霸凌的解决办法英语作文

网络霸凌的解决办法英语作文Cyberbullying is a serious issue that affects many individuals, especially teenagers, in today's society. 网络霸凌是一个严重的问题,尤其是影响到当今社会许多人,尤其是青少年。
It involves the use of electronic communication to bully, harass, or threaten others, often through social media platforms. 它涉及使用电子通讯来欺凌、骚扰或威胁他人,通常是通过社交媒体平台进行。
Cyberbullying can have detrimental effects on the mental health and well-being of the victims, leading to anxiety, depression, and even suicidal thoughts. 网络霸凌可能对受害者的心理健康和幸福产生不良影响,导致焦虑、抑郁,甚至自杀念头。
One way to address the issue of cyberbullying is by promoting digital literacy and online safety education. 一种解决网络霸凌问题的方法是通过推广数字素养和网络安全教育。
Educating individuals, especially young people, on how to navigate the digital world safely and responsibly can help prevent them from becoming both perpetrators and victims of cyberbullying. 教育个人,特别是年轻人,如何安全、负责任地使用数字世界,可以帮助他们避免成为网络霸凌的施害者和受害者。
关于治理网络暴力的英语作文

关于治理网络暴力的英语作文英文回答:Cyberbullying has become a pervasive issue in the digital age, posing significant threats to individuals and society as a whole. It is essential to address this problem through comprehensive governance strategies that encompass legal, technological, and educational measures.Legal Measures:Enacting and enforcing laws that criminalize cyberbullying and impose strict penalties on perpetrators.Establishing reporting mechanisms for victims and witnesses to facilitate prompt investigation and legal action.Expanding the scope of existing laws to cover online harassment, defamation, and other forms of cyberbullying.Technological Measures:Developing filtering and moderation tools to identify and remove harmful content from online platforms.Empowering users with control over their online experiences through privacy settings, reporting features, and blocking mechanisms.Collaborating with technology companies to implement machine learning and artificial intelligence algorithms for detecting and preventing cyberbullying.Educational Measures:Incorporating digital literacy and cyberbullying prevention programs into school curricula.Educating students, parents, and the general public about the harmful effects of cyberbullying and strategies for safe online behavior.Training educators, law enforcement, and mental health professionals to recognize and respond to cyberbullying incidents.Community-Based Initiatives:Encouraging open dialogue and fostering a culture of respect and empathy online.Establishing support groups and resources for victims of cyberbullying, providing emotional support and guidance.Collaborating with non-profit organizations and community leaders to raise awareness and promote responsible online behavior.International Cooperation:Recognizing the cross-border nature of cyberbullying, coordinating efforts among nations to develop and enforce international laws and guidelines.Establishing mechanisms for cross-border reporting and investigation of cyberbullying cases.Promoting collaboration and information sharing among law enforcement agencies and judicial authorities.By implementing these comprehensive governance strategies, we can create a safer and more inclusive online environment, where individuals can express themselvesfreely without fear of harassment or harm.中文回答:网络暴力的治理。
消除网络欺凌英语作文

消除网络欺凌英语作文Title: Combating Cyberbullying: A Call to Action。
Cyberbullying, a prevalent issue in today's digital age, poses serious threats to the well-being and mental healthof individuals, particularly adolescents and teenagers. As we navigate the intricate web of the internet, it is imperative to address this issue with urgency and vigilance. In this essay, we delve into the complexities of cyberbullying and explore effective strategies to combat it.First and foremost, it is crucial to understand what constitutes cyberbullying. Cyberbullying encompasses arange of behaviors, including harassment, intimidation, spreading rumors, and maliciously targeting individuals through various online platforms such as social media, messaging apps, and online forums. Unlike traditional bullying, cyberbullying has the potential to reach a vast audience within seconds, amplifying its impact and causing lasting harm to the victims.One of the most effective strategies in combating cyberbullying is raising awareness and promoting digital literacy among individuals, especially the youth. Education plays a pivotal role in empowering individuals to recognize the signs of cyberbullying, understand its consequences, and develop strategies to protect themselves and others. Schools, parents, and community organizations should collaborate to integrate comprehensive digital literacy programs into curricula and provide resources for students to navigate the online world safely.Furthermore, fostering a culture of empathy and respect is essential in preventing cyberbullying. By promoting kindness, tolerance, and inclusivity, we can create online environments where bullying behavior is not tolerated. Encouraging positive interactions and teaching individuals to stand up against cyberbullying can significantlymitigate its prevalence and impact.Moreover, effective enforcement of policies and regulations is paramount in combating cyberbullying. Socialmedia platforms and online communities must implementstrict guidelines to address cyberbullying promptly and decisively. This includes providing clear reporting mechanisms, conducting thorough investigations, and imposing appropriate sanctions on perpetrators. Additionally, law enforcement agencies should work closely with internet service providers to track and prosecute individuals engaged in severe cases of cyberbullying.Another crucial aspect of combating cyberbullying is providing support and resources for victims. Victims of cyberbullying often experience feelings of isolation, anxiety, and depression, and it is essential to offer them avenues for seeking help and assistance. Counseling services, helplines, and support groups can provide emotional support and guidance to victims as they navigate the aftermath of cyberbullying incidents.In conclusion, cyberbullying is a pervasive problemthat demands collective action and collaboration from all sectors of society. By raising awareness, promoting digital literacy, fostering empathy, enforcing regulations, andsupporting victims, we can create safer and more inclusive online spaces for everyone. Let us work together to eliminate cyberbullying and cultivate a culture of respect and kindness in the digital realm.。
关于解决网络欺凌的英语作文

关于解决网络欺凌的英语作文English:Cyberbullying has become a pressing issue in today's society, with individuals using the anonymity of the internet to spread hate and harm to others. In order to address this problem, it is crucial for schools, parents, and law enforcement to work together to educate young people about the impact of cyberbullying and the importance of treating others with respect online. Schools should implement comprehensive anti-bullying programs that specifically address cyberbullying, teaching students how to recognize and report online harassment. Parents also play a crucial role in preventing cyberbullying by monitoring their children's online activity and fostering open communication about their experiences. Additionally, law enforcement should take online harassment seriously and hold perpetrators accountable for their actions. By working together and taking proactive measures, we can create a safer online environment for everyone.Translated content:网络欺凌已成为当今社会的一个紧迫问题,个人利用互联网的匿名性向他人传播仇恨和伤害。
面对网络霸凌应该如何做英语作文

面对网络霸凌应该如何做英语作文全文共3篇示例,供读者参考篇1Facing Online Bullying: How to Deal with itIn today's digital age, the rise of social media and online communication platforms has brought people closer together, but it has also opened the door to a new form of bullying known as cyberbullying. Online bullying can take many forms, from hurtful comments on social media to spreading rumors and even threats of violence. The anonymity that the internet provides can make it easier for bullies to target their victims without fear of reprisal.So, how can we deal with online bullying in a way that protects our mental health and well-being?1. Recognize the SignsThe first step in dealing with online bullying is to recognize when it's happening to you. This can be difficult, especially if the bullying is subtle or disguised as a joke. Pay attention to how you feel after interacting with certain people online. If you feelanxious, depressed, or self-conscious, it may be a sign that you are being bullied.2. Don't EngageOne of the worst things you can do when faced with online bullying is to engage with the bully. Responding to their hurtful comments or threats only gives them the satisfaction of knowing that they have gotten to you. Instead, block or unfriend the bully, report their behavior to the platform, and focus on surrounding yourself with positive and supportive people.3. Reach Out for HelpDon't suffer in silence. If you are being bullied online, reach out to someone you trust for support. This could be a friend, family member, teacher, or counselor. Talking about your experience can help you to process your emotions and come up with a plan to deal with the bullying.4. Take Care of YourselfIt's important to prioritize self-care when dealing with online bullying. This might mean taking breaks from social media, practicing relaxation techniques like deep breathing or meditation, or engaging in activities that bring you joy andpeace. Remember that you are not alone, and there are people who care about you and want to help.5. Report the BullyingMost social media platforms have policies in place to deal with bullying behavior. If you are being bullied online, report the bully to the platform and provide evidence of the bullying, such as screenshots of hurtful messages or comments. The platform may take action against the bully, such as suspending their account or banning them from the platform.6. Educate Yourself and OthersFinally, one of the best ways to combat online bullying is to educate yourself and others about its harmful effects. Talk to your friends and family about the importance of being kind and respectful online, and stand up to bullying behavior when you see it happening. By spreading awareness and promoting a culture of positivity and inclusivity online, we can create a safer and more supportive environment for everyone.In conclusion, online bullying is a serious issue that can have devastating effects on our mental health and well-being. By recognizing the signs of bullying, not engaging with the bully, reaching out for help, taking care of ourselves, reporting thebullying, and educating ourselves and others, we can take steps to protect ourselves and create a more positive online community. Remember that you are not alone, and there are people who care about you and want to help. Stay strong, and don't be afraid to speak up against bullying behavior. Together, we can make a difference.篇2Facing Cyberbullying: How to RespondCyberbullying has become a prevalent issue in today's digital age, with the anonymity and accessibility of the internet making it easier for individuals to engage in harmful behavior towards others. From hurtful comments on social media to malicious rumors spread online, cyberbullying can have a lasting impact on its victims. Therefore, it is important for individuals to know how to respond effectively when faced with cyberbullying.First and foremost, it is crucial to not engage with the cyberbully. Responding with anger or retaliating only fuels the situation and gives the cyberbully the attention they seek. Instead, it is best to block or report the individual and remove yourself from the situation. By disengaging, you are taking awaythe power from the cyberbully and taking control of your own well-being.Next, it is important to reach out for support. Talk to a trusted friend, family member, or counselor about what you are experiencing. It can be comforting to have someone to confide in and offer guidance during difficult times. Additionally, many websites and hotlines offer support for those facing cyberbullying, providing resources and advice on how to cope with the situation.Furthermore, it is essential to practice self-care and prioritize your mental health. Engage in activities that bring you joy and relaxation, such as exercise, meditation, or hobbies. Taking care of yourself emotionally and physically can help you build resilience and navigate through the challenges of cyberbullying.In addition, consider documenting the cyberbullying incidents. Keep a record of the messages, posts, or comments that are being directed towards you. Having evidence of the cyberbullying can be helpful if you decide to take further action, such as reporting the behavior to social media platforms or authorities.Lastly, remember that you are not alone. Many individuals have experienced cyberbullying and have found ways toovercome it. Seek out support groups or online communities where you can connect with others who have gone through similar experiences. By sharing your story and hearing from others, you can gain strength and perspective on how to move forward.In conclusion, facing cyberbullying can be a daunting and distressing experience. However, by responding proactively and seeking support, you can overcome the challenges and emerge stronger from the ordeal. Remember to prioritize yourwell-being, reach out for help, and stay resilient in the face of adversity. Together, we can create a safer and kinder online environment for all.篇3Facing Cyberbullying: What You Should DoIn today's digital age, the prevalence of cyberbullying has become a serious issue that many individuals, especially teenagers, are facing. With the increasing use of social media and online platforms, it has become easier for people to hide behind the screen and engage in harmful behavior. Cyberbullying can have serious consequences on a person's mental health and overall well-being, which is why it is importantto know how to effectively deal with it. In this article, we will discuss some strategies on how to face cyberbullying and protect yourself from its harmful effects.The first step in facing cyberbullying is to recognize it for what it is. Cyberbullying can take many forms, such as sending threatening or harassing messages, spreading rumors or lies about someone online, or even creating fake accounts to impersonate and harm someone's reputation. It is important to understand that cyberbullying is not just harmless teasing or joking around – it is a deliberate and malicious act intended to harm or intimidate someone. By recognizing cyberbullying for what it is, you can take the necessary steps to address and stop it.The next step in facing cyberbullying is to seek help and support from trusted individuals. If you are being cyberbullied, it is important to reach out to someone you trust, such as a parent, teacher, or counselor. Talking to someone about what you are experiencing can help you feel less alone and provide you with the support and guidance you need to deal with the situation. Remember that you do not have to face cyberbullying alone –there are people who care about you and want to help you through this difficult time.In addition to seeking help from others, it is important to take action to protect yourself from cyberbullying. This may involve blocking the person who is cyberbullying you, reporting their behavior to the website or platform where it is occurring, or even contacting law enforcement if the cyberbullying is severe or involves threats of violence. Remember that you have the right to defend yourself and take action to stop the cyberbullying. Do not be afraid to stand up for yourself and protect yourwell-being.It is also important to take care of your mental health and well-being while facing cyberbullying. Dealing with cyberbullying can be emotionally draining and stressful, so it is important to practice self-care and prioritize your mental health. This may involve talking to a therapist or counselor, practicing relaxation techniques such as deep breathing or mindfulness, or engaging in activities that bring you joy and relaxation. Remember that your mental health is important and deserves attention, especially during difficult times like facing cyberbullying.In conclusion, facing cyberbullying can be a challenging and distressing experience, but it is important to know that you are not alone and that there are steps you can take to protect yourself and address the situation. By recognizing cyberbullyingfor what it is, seeking help and support from trusted individuals, taking action to protect yourself, and prioritizing your mental health and well-being, you can effectively face cyberbullying and overcome its harmful effects. Remember that you have the right to be treated with respect and dignity, both online and offline, and do not hesitate to take action to protect yourself from cyberbullying.。
op:权限插件指令

des cript ion:将<用户>加入到<组>. (如果不存在便创建文件)usage: /ma nuadd <用户> <组>| 可选[世界]p ermis sions: gro upman ager.manua ddmanud el: de scrip tion:移除<用户>的配置并移动到默认组. us age:/manu del <用户> pe rmiss ions: grou pmana ger.m anude lm anuad dsub:descr iptio n: 添加一个<组>到<用户>的分组列表. usag e: /m anuad dsub<用户><组> pe rmiss ions: grou pmana ger.m anuad dsubman udels ub: de scrip tion:删除一个<组>从<用户>的分组列表.u sage: /man udels ub <用户> <组> perm issio ns: g roupm anage r.man udels ubmanga dd: de scrip tion:创建一个<组>.u sage: /man gadd<组> pe rmiss ions: grou pmana ger.m angad dm angde l: des cript ion:移除一个<组> (所有成员移动到默认组)usage: /ma ngdel <组>p ermis sions: gro upman ager.mangd elmanua ddp:d escri ption: 增加<用户>的<权限>.u sage: /man uaddp <用户> <权限>permi ssion s: gr oupma nager.manu addpman udelp: desc ripti on: 移除<用户>的<权限>. usag e: /m anude lp <用户> <权限> per missi ons:group manag er.ma nudel pm anuli stp:d escri ption: 列出<用户>的全部权限.u sage: /man ulist p <用户> perm issio ns: g roupm anage r.man ulist pm anuch eckp:descr iptio n: 查询<用户>是否具有<权限>, 以及它的由来. usag e: /m anuch eckp<用户><权限>p ermis sions: gro upman ager.manuc heckpma ngadd p: des cript ion:增加<组>的<权限>. usag e: /m angad dp <组> <权限> perm issio ns: g roupm anage r.man gaddp des cript ion:移除<组>的<权限>. usag e: /m angde lp <组> <权限> perm issio ns: g roupm anage r.man gdelpma nglis tp: de scrip tion:列出<组>的全部权限. usa ge: /mangl istp<组> pe rmiss ions: grou pmana ger.m angli stp mang check p: des cript ion:查询<组>是否具有<权限>,以及它的由来. usa ge: /mangc heckp <组><权限>p ermis sions: gro upman ager.mangc heckpma ngadd i: des cript ion:将<组1>增加到<组2>的继承列表. us age:/mang addi<组1><组2>p ermis sions: gro upman ager.manga ddi mang deli:descr iptio n: 将<组1>移除出<组2>的继承列表. usag e: /m angde li <组1> <组2> per missi ons:group manag er.ma ngdel im anuad dv: de scrip tion:增加或者替换<用户>的一个<变量><值> (如前缀和后缀). usag e: /m anuad dv <用户> <变量> <值> perm issio ns: g roupm anage r.man uaddvma nudel v: des cript ion:移除<用户>的<变量>. usa ge: /manud elv <用户> <变量> pe rmiss ions: grou pmana ger.m anude lvmanul istv:descr iptio n: 列出<用户>的全部变量(如前缀和后缀).u sage: /man ulist v <用户> perm issio ns: g roupm anage r.man ulist vm anuch eckv:descr iptio n: 验证<用户>的<变量>值, 以及它的由来.u sage: /man uchec kv <用户> <变量> per missi ons:group manag er.ma nuche ckv mang addv:descr iptio n: 增加或者替换<组>的一个<变量><值> (如前缀和后缀). usa ge: /manga ddv <组> <变量> <值> perm issio ns: g roupm anage r.man gaddvma ngdel v: des cript ion:移除<组>的<变量>. usag e: /m angde lv <组> <变量> perm issio ns: g roupm anage r.man gdelv de scrip tion:列出<组>的全部变量 (如前缀和后缀). usag e: /m angli stv <组> per missi ons:group manag er.ma nglis tvmangc heckv: desc ripti on: 验证<组>的<变量>值, 以及它的由来.u sage: /man gchec kv <组> <变量> perm issio ns: g roupm anage r.man gckec kvmanwh ois:d escri ption: 查询<用户>所属组. usa ge: /manwh ois <用户> pe rmiss ions: grou pmana ger.m anwho istempa dd: de scrip tion:创建<用户>的临时权限拷贝.usage: /te mpadd <用户>permi ssion s: gr oupma nager.temp add temp del:d escri ption: 移除<用户>的临时权限拷贝. usag e: /t empde l <用户> perm issio ns: g roupm anage r.tem pdeltem plist: desc ripti on: 列出所有使用 /tem padd进入超载模式的用户.usage: /te mplis t perm issio ns: g roupm anage r.tem plistte mpdel all:d escri ption: 移出所有使用/tempa dd 进入超载模式的用户. us age:/temp delal l perm issio ns: g roupm anage r.tem pdela llmansa ve: de scrip tion:保存所有权限信息.usage: /ma nsavepermi ssion s: gr oupma nager.mans ave manl oad:d escri ption: 重新加载正确的[世界]和配置. usa ge: /manlo ad [世界] per missi ons:group manag er.ma nloadli stgro ups:d escri ption: 列出可用的组.u sage: /lis tgrou ps per missi ons:group manag er.li stgro ups manp romot e: des cript ion:保留<用户>当前权限并移动到更高一级的<组>. us age:/manp romot e <用户> <组>permi ssion s: gr oupma nager.manp romot ed escri ption: 保留<用户>当前权限并移动到更低一级的<组>.usage: /ma ndemo te <用户> <组> perm issio ns: g roupm anage r.man demot em antog gleva lidat e: des cript ion:当用户在线的时候打开/关闭验证. usag e: /m antog gleva lidat e perm issio ns: g roupm anage r.man toggl evali dateman toggl esave: desc ripti on: 打开/关闭自动保存.u sage: /man toggl esavepermi ssion s: gr oupma nager.mant oggle saveman world: desc ripti on: 查看可以选择的世界名u sage: /man worldpermi ssion s: gr oupma nager.manw orldman selec t: des cript ion:选择世界执行下一个命令. usa ge: /manse lect<世界>p ermis sions: gro upman ager.manse lectman clear: desc ripti on: 清除选择的世界, 下一个命令在当前世界执行. usag e: /m ancle ar per missi ons:group manag er.ma nclea rm anche ckw:d escri ption: 列出<世界>存储(用户/组)数据的每个文件路径. usag e: /m anche ckw <世界> pe rmiss ions: grou pmana ger.m anche ckw。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Comments on“Transparent User-Level Process Checkpoint and Restore for Migration”by Bozyigit and WasiqFelix Rauch,Thomas M.StrickerLaboratory for Computer SystemsETH-Swiss Institute of TechnologyCH-8092Z¨u rich,Switzerland{rauch,tomstr}@inf.ethz.chAbstractThe simple checkpointing and migration system forUNIX processes as described in the article of Bozyigitand Wasiq[1]can be improved in two ways:First by atechnique to checkpoint and migrate applications withoutthe need to recompile them and second by an alternativeapproach to precisely locate all the data segments of a pro-cess that need to be checkpointed.We fully acknowledgethe difficulty to do checkpointing or even portable check-pointing for the general case of processes and do not claimto solve the many remaining problems with the simplisticcheckpointing and migration approaches presented in theearlier article.Still we are aware of many systems andapplications where a simple solution is extremely helpfulonce it also works with binaries.1IntroductionRecent multi purpose and multi boot clusters are not nec-essarily built out of rack mounted machines,but consistalso of users or even students workstations[4].On suchworkstations,memory intensive and long running pro-cesses cause mainly two kinds of problems:(1)Usersmight want all the available resources of their worksta-tions and therefore get rid of the resource intensive back-ground jobs and(2)the machines might be rebooted tochange the operating system or to perform maintenancetasks.In both cases it is desired that the long running pro-cess’state is not lost and therefore the process is check-pointed.To proceed the process’work,its state is mi-grated to another available and probably idle machine inthe cluster and the process is continued.There are different approaches to apply checkpointingand migration to self written programs or open sourcesoftware as the structure of the available source codecan be changed to match the chosen checkpointing tech-nique1.For other programs there is no source codecesses by transforming and recompiling the source code of an appli-cation,such as described in[2].checkpointed.On some UNIX systems,the data segment does not consist of contiguous,accessible pages.Writable pages containing data segments might be alternated with read only pages of constant data.All these problems lead to a more advanced approach of checkpointing the data parts of a process.3Suggested ImprovementsTo overcome the need for recompilation of applications to enable checkpointing,we suggest to use dynamic link-ing.Dynamic linking techniques allow to track open files,duplicatedfile handles and other program state by redirecting system calls to special library routines.In-stead of redirecting system calls by introducing macros in the source code,we dynamically link the existing ex-ecutable to our checkpointing library by the use of the LDpreinit()in our library is called.This function then initializes the checkpointing library.With this ap-proach the checkpointing library can be initialized with-out changing the source code of the application. Another suggested improvement is a better method to find the data segments of the process to checkpoint.In-stead of trying to link special variables at the beginning and the end of the data area and then checkpointing the memory between the addresses of the two variables,we suggest to analyze the ELF binary of the process.The binary in ELF format contains informations about its dif-ferent segments.The segments are marked as read only data(like program text and probably constant data)or read/write data(like initialized but not constant data). Read only segments need not be checkpointed as they do not change during the process’lifetime and are au-tomatically loaded into memory when the applications is restarted after its migration.On the other hand the pro-cess may change all data in read/write segments,there-fore it is best to checkpoint all its read/write segments. This method assures that all non-constant data segments are checkpointed and that there will be no error after mi-gration due to erroneously restored read only segments in the data space of the process.4ConclusionsThe improvements presented in this paper allow to check-point and migrate applications without the need to change the source or even recompile them.This enhancement is especially important for programs for which there is no source code available and allows to use the checkpointing and migration mechanism even with some commercial ap-plications.In our own experience we found that it is difficult to implement a truly portable user-level checkpointing and migration mechanism.Such a mechanism relies ex-tensively on subtle differences of the various existing UNIX systems and their associated libraries.Remain-ing problems for user-level checkpointing consist of non-checkpointable state in network sockets and randomly ac-cessedfiles.Checkpointing and migration mechanisms help to bet-ter utilize the available resources on modern clusters con-sisting of rack mounted machines or even users work-stations.Equiping a cluster with user-level checkpoint-ing facilities is easy and allows owners of large jobs to keep their long running jobs on unused and otherwise idle workstations.Our improvements allow to integrate some commercial applications into the checkpointing and mi-gration facilities without the need to recompile them. References[1]M.Bozyigit and er-Level ProcessCheckpoint and Restore for Migration.Operating Systems Review,35(2):86–95,2001.[2]Balkrishna Ramkumar and V olker Strumpen.Portable Checkpointing for Heterogeneous Archi-tectures.In In27th International Symposium on Fault-Tolerant Computing—Digest of Papers,pages 58–67,April1997.[3]F.Rauch.Porting ckpt。
