WinPcap所涉及的Windows驱动基础知识(三)
WinPcap开发-零基础知识入门基础

WinPcap开发(一):零基础入门*原创作者:追影人0×00 前言网络编程在网络安全方面具有举足轻重的作用,如何快捷高效的监听、分析、构造网络流量,成为很多安全从业者需要解决的重点问题。
而winpcap这一免费开源项目恰好可以为win32应用程序提供访问网络底层的能力,所以其成为了相关网络编程的首选开发工具。
0×01 winpcap是什么?winpcap(windows packet capture)是windows平台下一个免费的网络访问系统,可用于windows系统下的网络编程。
著名的wireshark便是基于winpcap开发的,大家在安装wireshark中可以看到winpcap驱动程序的安装过程。
有关winpcap的介绍网络上很多,百科里面介绍的也很详细,我就不再copy了。
需要注意的一点是,winpcap并不是一个简单的library,而是一个针对Win32平台上的抓包和网络分析的一个架构,它包括一个核心态的包过滤器,一个底层的动态链接库(packet.dll)和一个高层的不依赖于系统的库(wpcap.dll)。
所以它只能“嗅探”到物理线路上的数据包,而不具备拦截的能力,因此不适用于个人防火墙等项目。
0×02 你需要准备些什么?本系列文章主要带大家认识和了解如何利用winpcap网络编程技术进行网络的协议分析、流量统计及网络探测扫描等,这里我们并不会去深硬的解读相关源代码,而是以轻松的方式结合实验来对相关原理进行深入理解。
在本系列文章中,笔者从简到难,简明介绍winpcap架构原理、相关环境搭建及快速编写核心代码。
但是在开始前,读者需要有一些相关基础:了解网络协议相关基础知识,掌握一门winpc ap开发库支持的编程语言,自己能动手实践编写一些例子。
Winpcap提供的开发接口原生是c语言的,不过热心肠的程序猿们已经为其他语言的使用提供了封装,比如java、.net、python,好像连易语言都有。
WinPcap编程
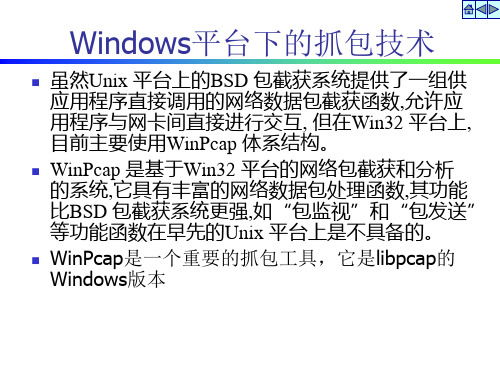
Packet.dll应用步骤
2) 打开指定的网卡 lpAdapter = PacketOpenAdapter(AdapterList [0 ]) ; if ( ! lpAdapter | | (lpAdapter - > hFile = = INVALID_HANDLE_VALUE) ) { dwErrorCode = GetLastError() ; sprintf ( szErr ,″Unable to open the adapter ,error code : %lx″, dwErrorCode) ; AfxMessageBox(szErr) ; return FALSE; }
1> LPPACKET PacketAllocatePacket(void) 如果运行成功,返回一个_PACKET结构的指针, 否则返回NULL。成功返回的结果将会传送到 PacketReceivePacket()函数,接收来自驱动的网络 数据报。 2> VOID PacketFreePacket(LPPACKET lpPacket) 释放参数提供的_PACKET结构。 3> VOID PacketCloseAdapter(LPADAPTER lpAdapter) 关闭参数中提供的网络适配器,释放相关的 ADAPTER结构。
WinPcap
WinPcap包括三个部分 第一个模块:内核级的包过滤驱动程序
NPF(Netgroup Packet Filter),是一个虚拟设备驱动程序文件, 是架构的核心(在Win95/98 中是一个VXD文件,在NT/2000 中是 一个SYS 文件) ,它的主要功能是过滤数据包,在包上附加时间戳、 数据包长度等信息。
第二个模块:低级动态链接库packet.dll,在Win32 平台 上提供了与NPF 的一个通用接口。 packet.dll数据包驱 动程序库是与libpcap 相兼容的一组用户级的函数库。 第三个模块:用户级的Wpcap.dll。通过调用packet.dll 提供的函数生成,它包括了过滤器生成等一系列可以被 用户级调用的高级函数,另外还有诸如数据包统计及发 送功能。
WinPcap 教程
WinPcap 教程: 循序渐进教您使用WinPcap本节将向您展示如何使用WinPcap API的一些特性。
这部分教程细化成若干节课,以循序渐进的方式介绍给读者,让读者从最基本的部分(获得设备列表)到最复杂的部分(控制发送队列并收集和统计网络流量)来了解如何使用WinPcap进行程序开发。
有时,我们会给出一些简单使用的代码片断,但同时,我们提供完整程序的链接:所有的源代码包含一些指向手册其他地方的链接,这可以让您很方便地通过点击鼠标来跳转到您想查看的函数和数据结构的内容中去。
范例程序都是用纯C语言编写, 所以,掌握基本的C语言编程知识是必须的,而且,这是一部关于处理原始网络数据包的教程,因为,我们希望读者拥有良好的网络及网络协议的知识。
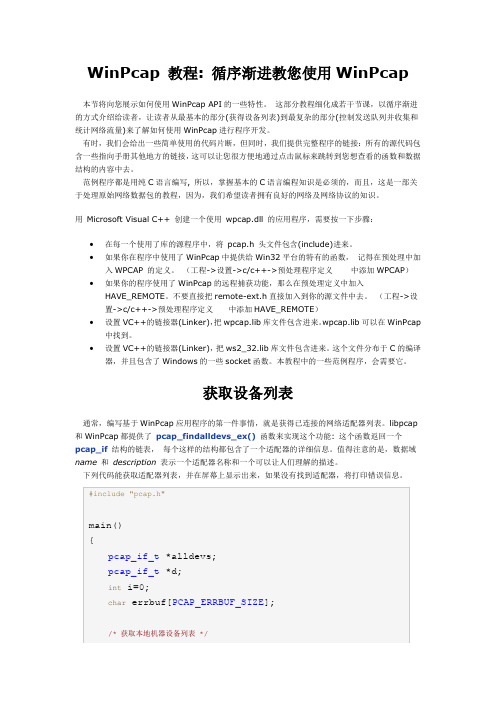
用Microsoft Visual C++ 创建一个使用wpcap.dll 的应用程序,需要按一下步骤:∙在每一个使用了库的源程序中,将pcap.h 头文件包含(include)进来。
∙如果你在程序中使用了WinPcap中提供给Win32平台的特有的函数,记得在预处理中加入WPCAP 的定义。
(工程->设置->c/c++->预处理程序定义中添加WPCAP)∙如果你的程序使用了WinPcap的远程捕获功能,那么在预处理定义中加入HAVE_REMOTE。
不要直接把remote-ext.h直接加入到你的源文件中去。
(工程->设置->c/c++->预处理程序定义中添加HAVE_REMOTE)∙设置VC++的链接器(Linker),把wpcap.lib库文件包含进来。
wpcap.lib可以在WinPcap 中找到。
∙设置VC++的链接器(Linker),把ws2_32.lib库文件包含进来。
这个文件分布于C的编译器,并且包含了Windows的一些socket函数。
本教程中的一些范例程序,会需要它。
获取设备列表通常,编写基于WinPcap应用程序的第一件事情,就是获得已连接的网络适配器列表。
winpcap网络开发库入门

while( ( retValue = pcap_next_ex( adapterHandle, &packetHeader, &packetData ) ) >= 0 ) { // timeout elapsed if we reach this point if( retValue == 0 ) continue; //打印捕获数据包的信息 printf( "length of packet: %d\n", packetHeader->len ); } // if we get here, there was an error reading the packets if( retValue == -1 ) { printf( "Error reading the packets: %s\n", pcap_geterr( adapt erHandle ) ); return -1; } system( "PAUSE" ); return 0; } 示例程序 3 发送数据封包 #include <pcap.h> int _tmain(int argc, _TCHAR* argv[]) { pcap_if_t * allAdapters;//适配器列表 pcap_if_t * adapter; pcap_t u_char * adapterHandle;//适配器句柄 packet[ 20 ]; //待发送的数据封包
ext) {//遍历输入适配器信息(名称和描述信息) printf( "\n%d.%s ", ++crtAdapter, adapter->name ); printf( "-- %s\n", adapter->description ); } printf( "\n" ); //选择适配器 int adapterNumber; printf( "Enter the adapter number between 1 and %d:", crtAdapte r ); scanf_s( "%d", &adapterNumber ); if( adapterNumber < 1 || adapterNumber > crtAdapter ) { printf( "\nAdapter number out of range.\n" ); // 释放适配器列表 pcap_freealldevs( allAdapters ); return -1; } adapter = allAdapters; for( crtAdapter = 0; crtAdapter < adapterNumber - 1; crtAdapter+ + ) adapter = adapter->next; // 打开指定适配器 adapterHandle = pcap_open( adapter->name, // name of the adapter 65536, t to capture // 65536 guarantees tha t the whole // packet will be captured PCAP_OPENFLAG_PROMISCUOUS, // promiscu ous mode 1000, t - 1 millisecond NULL, e remote machine errorBuffer ); if( adapterHandle == NULL ) {//指定适配器打开失败 fprintf( stderr, "\nUnable to open the adapter\n", adapter->n ame ); // 释放适配器列表 pcap_freealldevs( allAdapters ); return -1; // error buffer // authentication on th // read timeou // portion of the packe
winpcap编程_适合当讲授课件

要向VC++6.0中添加一个新的包含文件所在的路径,你必 须打开Tool菜单,选择Options,然后选择Directories选项卡, 在Show directories下拉框中选择Include files,并且将新的 路径添加到Directories中去 。
二、获得设备列表
通常,编写基于WinPcap应用程序的第一件事情,就是获得已 连接的网络适配器列表。WinPcap提供了 pcap_findalldevs_ex( ) 函数来实现这个功能:
由 pcap_findalldevs_ex()返回的每一个 pcap_if 结构体, 都包含一个 pcap_addr 结构体,这个结构体由如下元素组成:
通过返回的结构,我们可以得到探测到的网卡设备的更 详尽信息。
例子:
二、打开适配器开始捕获数据包
现在,我们已经知道如何获取适配器的信息了,那我们就开始 一项更具意义的工作,打开适配器并捕获数据包。本节中,我们会 编写一个程序,将每一个通过适配器的数据包打印出来。
Sniffer,中文可以翻译为嗅探器,是一种基于被动侦听原理的网络 分析方式。使用这种技术方式,可以监视网络的状态、数据流动情况 以及网络上传输的信息。当信息以明文的形式在网络上传输时,便可 以使用网络监听的方式来进行攻击。将网络接口设置在监听模式,便 可以将网上传输的源源不断的信息截获。 wireshark(2006年之前称为Ethereal)一是全球相当行流行的开放 源代码的网络协议分析软件,功能强大而且支持平台最多,它可以实 时检测网络通讯数据,也可以检测其抓取的网络通讯数据快照文件;可 以通过图形界面浏览这些数据,可以查看网络通讯数据包中每一层的 详细内容;Wireshark还拥有许多强大的特性:包含有强显示过滤器语 言和查看TCP会话重构流的能力。它可以支持七百多种协议的解析和 多种媒体类型。
winpcap驱动

winpcap驱动WinPcap驱动是一种用于Windows操作系统的网络数据包捕获和分析的工具。
它提供了一种简单和有效的方式,使用户能够捕获和分析计算机与网络之间传输的数据包。
不管是网络管理员、安全专家还是网络开发人员,WinPcap驱动都是一个强大而有用的工具。
WinPcap驱动是一个开源项目,由意大利中科院主导开发,最初是为Unix-like系统设计的。
随着Windows操作系统的普及和用户的需求,WinPcap驱动很快被移植到了Windows平台上。
它可以兼容Windows 2000和后续版本的操作系统。
WinPcap驱动的主要功能是对计算机和网络之间的数据流进行捕获和分析。
通过捕获数据包,用户可以了解网络流量的实时情况、分析网络协议、排查网络问题以及进行网络安全监控等工作。
此外,WinPcap驱动还可以用于网络流量生成、网络性能测试和网络协议栈的开发调试等工作。
WinPcap驱动的使用非常灵活和简单。
用户只需要安装驱动程序,并在自己的应用程序中调用相关的库函数,即可实现数据包的捕获和分析。
WinPcap驱动提供了一组API,这些API可以通过编程语言(如C、C++、Python等)调用,从而方便用户编写自己的网络数据包分析和工具。
另外,WinPcap驱动还支持远程数据包捕获。
用户可以通过在远程计算机上安装WinPcap驱动,并通过网络连接进行远程数据包捕获。
这个功能对于网络管理员或者安全专家来说非常有用,可以在分布式环境中实时监控多个计算机的网络流量。
虽然WinPcap驱动提供了强大的功能和方便的接口,但是用户在使用时也需要注意一些安全和隐私问题。
首先,WinPcap驱动具有高权限的操作系统级别的访问权限,因此需要用户具备足够的权限来安装和使用。
其次,在进行网络流量分析时,用户应当严格遵守相关法律法规,并保护用户隐私和网络安全。
总的来说,WinPcap驱动是一个强大而实用的工具,可以帮助用户更好地理解和分析网络数据包。
实验3:WinPcap技术的使用

实验3:WinPcap技术的使用1实验目的和要求学习使用WinPcap开发包实现网络数据包的捕获、过滤和分析的功能,具体要求如下:1)WinPcap开发包的下载和安装;2)使用WinPcap获取与网络适配器绑定的设备列表;3)使用WinPcap获取网络适配器的高级属性信息;4)使用WinPcap打开网络适配器并实现抓包功能5)使用WinPcap过滤数据包、分析数据包。
2实验设备及材料1)Windows主机2)Visual Studio 2005或Visual Studio 20083实验内容本实验学习WinPcap开发包的使用,利用WinPcap实现网络数据包捕获、过滤和分析的功能,实验内容如下。
3.1 WinPcap开发包的下载和安装下载并安装WinPcap开发包,下载地址:/archive/。
1)4.1.1-WinPcap.exe的安装;2)4.1.1-WpdPack.zip的下载和使用。
3.2获取与网络适配器绑定的设备列表信息pcap_findalldevs_ex()函数的使用。
调用pcap_findalldevs_ex()函数,获取的网络设备信息将存储在结构体pcap_if_t中,然后打印网卡设备列表信息,包括网络适配器名称和描述。
3.3获取网络适配器的高级属性信息在3.2的基础上,除打印本地主机所有网络适配器的名称、描述外,还打印是否回环地址、协议簇类型、协议簇名称、IP地址、子网掩码、广播地址和目标地址等信息。
3.4打开网络适配器并通过事件处理器来捕获数据包pcap_open()函数和pcap_loop()函数的使用。
程序的运行过程如下:1)调用pcap_findalldevs_ex()函数获取并打印本机的网络设备列表。
2)要求用户选择用于捕获数据包的网络设备。
3)使用for语句跳转到选中的网络设备,以便在后面的程序中打开该设备,并在该设备上捕获数据。
4)调用pcap_open()函数打开选择的网络设备。
WinPcap基础

SUP-5.1.3
网络组包过滤(NPF)模块
1.数据包的捕获和过滤 捕获数据库是WinPcap的核心技术。在捕 获时,驱动器使用网络接口嗅探数据包 ,并把它们完整地传送到用户层应用程 序。 可以看到,捕获数据包时使用了两个组 件,即过滤器和核心缓冲区。
2.监测和统计
NPF中包含一个可编程的监测模块,它可以对网络流量 进行简单的统计和计算。不需要把数据包复制到用户 层应用程序,只要简单地接收和显示从监测引擎获得 的结果即可收集到统计信息。不需要捕获数据包,也 就避免了捕获过程中可能耗费的CPU和内存资源。 监测引擎由一个带有计数器的分类器构成。NPF中的一 个过滤引擎对数据包进行分类,没有被过滤掉的数据 会进入计数器。计数器拥有一些变量,用于保存接收 到的数据和过滤器接收的字节数。每当有新的数据包 进入时,这些变量的值都会被更新。监测引擎会定期 将这些变量的值传递给用户层应用程序,传递的时间 可以由用户自行配置。
以简洁方式来描述WinPcap体系结构
SUP-5.1.2
NIC驱动器和NDIS
网络接口卡和NIC驱动器 中间层驱动器 传输驱动器或者协议驱动器
1.网络接口卡和NIC驱动器
NIC驱动器可以直接管理网络接口卡。它的下端接口与硬 件关联,而其上端接口允许高层向网络中发送数据包、处 理中断、重置网络适配器、中止网络适配器以及查询和设 置驱动器的操作属性。NIC驱动器可以是微端口,也可以 是传统的完全NIC驱动器。 微端口仅实现硬件指定的、用于管理网络适配器的必 要操作,包括在网络适配器上发送和接收数据。大多 数最低层NIC驱动器的操作(例如同步操作)都是由 NDIS操作的。微端口不会直接调用操作系统例程, NDIS是微端口访问操作系统的接口。微端口将数据包 传送到NDIS,而NDIS确保这些数据包会传送给正确的 网络协议。 完全NIC驱动器用于执行硬件指定的操作以及所有由 NDIS完成的同步和队列操作。
winpcap分析

4.3.2 4.3.3 4.4 4.4.1 4.4.2
结构图............................................................................................................... 25 源码分析............................................................................................................29 系统特色............................................................................................................46 分布式网络监听 .................................................................................................46 简单网络管理.................................................................................................... 46
第 5 章 系统测试与使用说明书 ......................................................................................47 5.1 5.1.1 5.1.2 5.1.2 5.1.3 5.2 5.3 结论 致谢: 系统测试............................................................................................................47 监听功能............................................................................................................47 显示功能............................................................................................................48 管理功能............................................................................................................51 连接功能............................................................................................................52 工具软件的配置 .................................................................................................54 监听工具的使用 .................................................................................................55 .....................................................................................................................56 .....................................................................................................................61
WinPcap 原理技术

WinPcap 原理技术winpcap是windows平台下一个免费,公共的网络访问系统。
开发winpcap这个项目的目的在于为win32应用程序提供访问网络底层的能力。
1、网络及协议分析2、网络监控3、通信日志记录4、traffic generators5、用户级别的桥路和路由6、网络入侵检测系统(NIDS)7、网络扫描8、安全工具WinPcap导入WinPcap是一个开源的专业网络数据捕获开发包,其实,WinPcap的强大功能并不仅限于数据包的获取,主要功能:捕获原始数据包,包括在共享网络上各主机发送/接收的以及相互之间交换的数据包;在数据包发往应用程序之前,按照自定义的规则将某些特殊的数据包过滤掉;在网络上发送原始的数据包;收集网络通信过程中的统计信息。
Sniffer 嗅探原理Winpcap是针对Win32平台上的抓包和网络分析的一个架构。
它包括一个核心态的包过滤器,一个底层的动态链接库(packet.dll)和一个高层的不依赖于系统的库(wpcap.dll)Packet.dll提供更方便更易用的编程接口,wpcap.dll中的接口函数Sniffer嗅探器,是一种基于被动侦听原理的网络分析方式。
使用这种技术方式,可以监视网络的状态、数据流动情况以及网络上传输的信息。
当信息以明文的形式在网络上传输时,便可以使用网络监听的方式来进行攻击。
将网络接口设置在监听模式,便可以将网上传输的源源不断的信息截获。
Sniffer技术常常用于网络故障诊断、协议分析、应用性能分析和网络安全保障等各个领域。
实现Sniffer 功能函数序列第一步:获取网络设备指针pcap_findalldevs_ex()第二步:打开网卡pcap_open()第三步:检查链路层pcap_datalink()第四步:编译BPF过滤规则pcap_compile第五步:设置过滤规则pcap_setfilter第六步:注册回调函数,循环捕获数据包pcap_loop()第七步:释放网络设备列表pcap_freealldevs()第八步:关闭WinPcap会话句柄pcap_close()获取网络设备指针(查找机器的所有网络设备接口,并使用链表结构返回)打开网络设备(打开一个用来捕获或发送流量的通用源(网卡))检查链路3层类型(检查链路层类型)编译BFP过滤规则(编译数据包过滤器,将程序中高级的过滤表达式(即过滤规则字符串)转换为能被内核级的过滤引擎所处理的内容)执行过滤规则(把一个过滤器绑定到WinPcap会话句柄)注册回调函数,循环捕获数据包(循环捕获数据包并分析)释放网络设备列表(释放链表空间)关闭WinPcap会话句柄(关闭一个和p关联的文件,并释放资源)数据包分析1.数据包的分析内容数据包(Packet)是TCP/IP协议通信传输中的数据单位,TCP/IP协议是工作在OSI模型第三层(网络层)、第四层(传输层)上的,而帧是工作在第二层(数据链路层)。
WinPcap基础知识(第一课:获得设备列表)

WinPcap基础知识(第一课:获得设备列表)一个基本的WinPcap应用程序所需的第一件事情是获得合适的网络适配器。
Libpcap/ Winpcap提供pcap_findalldevs() 函数完成这个功能:这个函数返回一个相连的pcap_if结构的列表。
列表的每一项包含关于适配器的复杂的信息。
特别的,name和description域数据包含设备的名称和可读的描述。
如下的代码提取设备列表,然后打印到屏幕上。
如果没有发现适配器,则显示一个错误。
view plaincopy to clipboardprint?#include <pcap.h>void main(){pcap_if_t *alldevs;pcap_if_t *d;int i=0;char errbuf[PCAP_ERRBUF_SIZE];/* 取得本机的网络设备列表 */if (pcap_findalldevs_ex(PCAP_SRC_IF_STRING, NULL /* 这个参数在这里不需要 */, &alldevs, errbuf) == -1){fprintf(stderr,"Error in pcap_findalldevs_ex: %s\n", errbuf);exit(1);}/* 显示列表 */for(d= alldevs; d != NULL; d= d->next){printf("%d. %s", ++i, d->name);if (d->description)printf(" (%s)\n", d->description);elseprintf(" (No description available)\n");}if (i == 0){printf("\nNo interfaces found! Make sure WinPcap is installed.\n");return;}/* We don't need any more the device list. Free it */pcap_freealldevs(alldevs);}#include <pcap.h>void main(){pcap_if_t *alldevs;pcap_if_t *d;int i=0;char errbuf[PCAP_ERRBUF_SIZE];/* 取得本机的网络设备列表 */if (pcap_findalldevs_ex(PCAP_SRC_IF_STRING, NULL /* 这个参数在这里不需要 */, &alldevs, errbuf) == -1){fprintf(stderr,"Error in pcap_findalldevs_ex: %s\n", errbuf);exit(1);}/* 显示列表 */for(d= alldevs; d != NULL; d= d->next){printf("%d. %s", ++i, d->name);if (d->description)printf(" (%s)\n", d->description);elseprintf(" (No description available)\n");}if (i == 0){printf("\nNo interfaces found! Make sure WinPcap is installed.\n");return;}/* We don't need any more the device list. Free it */pcap_freealldevs(alldevs);}在第一行#include <pcap.h>的前面加上#define HAVE_REMOTE,或者你在项目属性里面添加“C语言预处理程序定义”一栏里面加上HAVE_REMOTE(注意用‘,’隔开)。
Winpcap学习笔记

说明:本系列文章是我阅读winpcap手册后整理的一个学习笔记。
文章中出现的所有代码是我根据winpcap手册中的示例代码进行了学习,并调试通过,其中对部分代码作了修改,关于代码的版权我尊重winpcap手册中的版权说明,如果你使用了本系列文章中的代码而引起任何的版权或造成安全威胁等问题,我将不负任何责任。
下载好了WpdPack_3_2_alpha1.zip(下载地址:/install/bin/WpdPack_3_2_alpha1.zip),解压后除了有文档,例子外还有Include和lib,于是想用TC2来做开发环境,但是编译的时候老是出问题,于是放弃。
后来阅读了Winpcap手册后才知道因为是在windows上开发,所以它推荐用VC++6.0,于是改用VC。
第一个试验是:#include#includeint main() {pcap_if_t *alldevs;pcap_if_t *d;int i = 0;char errbuf[PCAP_ERRBUF_SIZE];/* Retrieve the device list from the local machine*/if (pcap_findalldevs_ex(PCAP_SRC_IF_STRING, NULL /* auth is not needed */, &alldevs, errbuf) == -1){printf("Error in pcap_findalldevs_ex: %s\n", errbuf);exit(1);}/* Print the list */for (d = alldevs; d != NULL; d = d->next){/* Print the device’s name */printf("%d. %s", ++ i, d->name);/* Print the device’s dscription */if (d->description){printf("(%s)\n", d->description);}else{printf("(No description available)\n");}}if (i == 0){printf("\nNo interfaces found! Make sure WinPcap is installed.\n");return 0;}/* We don’t need any more the device list. Free it */pcap_freealldevs(alldevs);return 1;}编译的时候又遇到问题——“无法打开pcap.h”。
WinPcap:网络监控的基石

WinPcap:⽹络监控的基⽯稳定版本:WinPcap 4.0.2最近版本:WinPcap 4.1 beta5WinPcap是Windows环境访问链路层的⼯业标准级别的⼯具。
允许应⽤程序绕过协议栈抓取和传输⽹络包,且有以下有⽤特性,包括内核级包过滤,⽹络统计引擎并⽀持远程抓包。
WinPcap包括⼀个继承操作系统以提供底层⽹络访问的驱动,和⼀个⽤来轻松访问底层⽹络的库。
该库也包含Unix下的API libpcap。
由于众多特性,WinPcap成为许多开源或商业⽹络⼯具的抓包和过滤引擎,包括协议分析,⽹络监控,⽹络⼊侵检测系统,嗅探器,流量⽣成器和⽹络测试器。
其中⼀些⼯具,像Wireshar,Nmap,Snort,ntop在⽹络社区被⼴泛使⽤。
WinPcap同时也是WinDump诞⽣之地,WinPcap是windows版本的流⾏tcpdump,能被⽤来按照各种各样复杂的规则监视,分析⽹络流量并存盘。
看看基于WinPcap开发出的众多知名产品:Ethereal,Windump等等,当然还包括国内有名(⾮常有⽤但被⼈滥⽤⼜⼗分讨厌)的⽹络剪⼑⼿,P2P终结者,⽹络执法官等等.还包括基于它开发的不同语⾔的库,如JPcap(⽤于Java),pypcap(⽤于Python),sharpcap(.NET)0x4553-IntercepterThis program offers the following features: - Sniffing passwords\hashes of the types:ICQ\IRC\AIM\FTP\IMAP\POP3\SMTP\LDAP\BNC\SOCKS\HTTP\WWW\NNTP\CVS\TELNET\MRA\DC++\VNC\MYSQL\ORACLE -Sniffing chat messages of ICQ\AIM\JABBER\YAHOO\MSN\GADU-GADU\IRC\MRA - Changing MAC address of LAN adapters - Raw mode (with filtering rules) - Capturing packets and post-capture (offline) analyzing - Remote traffic capturing via RPCAP daemon -Reconstruction of SMTP\POP3 messagesAerosolWardriving utility for Windows.AirSnareAirSnare is an intrusion detection system to help you monitor your wireless network.AnalyzerAnalyzer is a fully configurable Network Analyzer for Win32. It includes several functionalities that are needed by network management operator. Analyzer is based on WinPcap and it is able to capture packets on most Win32 platforms (and link-layer technologies). Analyzer 3.0 comes out with some event logging, LAN monitoring and traffic monitoring capabilities. However,Analyzer 3.0 most valuable point is the ability to parse network packets according to the protocol description contained into some external files, which can be modified at run-time by the user.AnetTestAnetTest is a integrated packet generator and sniffer for Ethernet, but also works with blocks of data over TCP connection.Enables you to use scripts for automated testing, monitoring, imitating of various network objects, creating custom network tools.ArchaeopteryxArchaeopteryx is a Passive mode OS Identification Tool. It is based off Siphon v.666 by SubTerrain. It has a GUI and a highly configurable OS signature file.ARP0cARP0c is an ARP redirector and bridging engine. ARP requests from various sources in a switched environment get false ARP response which point to the host running ARP0c. Packets from these hosts are bridged to the realdestination address to allow normal network operation and keep TCP connections alive.Asn1BrowserThe Asn1Browser analyzer decodes ASN1 binary data and provides an advanced display for the user.assnifferassniffer can monitor a network, and for every HTTP transfer it sees, save a copy of the transferred data.AutoScan-Network AutoScan-Network is a network discovering and managing application.BillSniffBillSniff is a free (freeware) sniffer under MS Windows.CAS BACnet ExplorerAutomatically discover all the BACnet® IP, BACnet® Ethernet and BACnet® MSTP devices, objects, and their properties on your network. The objects and devices are arranged in an easy to use tree format with braches for each network, object, and device.Bit-TwistBit-Twist is a simple yet powerful WinPcap-based Ethernet packet generator. It is designed to compliment WinDump, which by itself has done a great job in capturing network traffic. With Bit-Twist, you can now regenerate the captured traffic onto a live network! Packets are generated from windump trace file (.pcap file). Bit-Twist also comes with a comprehensive trace file editor to allow you to change the contents of a trace file.BochsBochs is a highly portable open source IA-32 (x86) PC emulator written in C++, that runs on most popular platforms.It includes emulation of the Intel x86 CPU, common I/O devices, and a custom BIOS.Busted!Busted! records AOL instant message conversations, web sites visited, applications used, keystrokes and takes periodic screen shots.CableMonCable traffic monitoring tool.Cain & AbelCain & Abel is a password recovery tool for Microsoft Operating Systems. It allows easy recovery of various kind of passwords by sniffing the network, cracking encrypted passwords using Dictionary, Brute-Force and Cryptanalysis attacks, recording VoIP conversations, decoding scrambled passwords, revealing password boxes, uncovering cached passwords and analyzing routing protocols. The program does not exploit any software vulnerabilities or bugs that could not be fixed with little effort.CarnivorePECarnivore is a surveillance tool for data networks. At the heart of the project is CarnivorePE, a software application that listens to all Internet traffic (email, web surfing, etc.) on a specific local network. Next, CarnivorePE serves this data stream tointerfaces called "clients." These clients are designed to animate, diagnose, or interpret the network traffic in various ways.cdpr - Cisco Discovery Protocol Reportercdpr is used to decode a Cisco Disovery Protocol (CDP) packet, by default it will report the device ID, the IP Address (of the device), and the port number that the machine is connected to. Optionally it will decode the entire CDP packet.choozmailparental control software.CHScannerCHScanner allows you to scan in "style" from Windows XP SP2 and higher OS. It is IPv4 and IPv6 enabled, it has a skinnable interface and it has the ability to mimic various operating systems. Last but not least, it has many scanning methods.coLinuxCooperative Linux is the first working free and open source method for optimally running Linux on Microsoft Windowsnatively. More generally, Cooperative Linux (short-named coLinux) is a port of the Linux kernel that allows it to run cooperatively alongside another operating system on a single machine. For instance, it allows one to freely run Linux on Windows 2000/XP, without using a commercial PC virtualization software such as VMware, in a way which is much more optimal than using any generalpurpose PC virtualization software.CORE IMPACTAutomated, comprehensive penetration testing product for assessing specific information security threats to an organization.dasniffdaSniff is an open source customizable sniffer for win32 systems. It helps you to log your LAN traffic by specifyingpacket rules as filters.Deep Network Analyzer (DNA)DNA is an open, flexible and extensible deep network analyzer (software server) and architecture for gathering and analyzing network packets, network sessions and applications protocols, passively off enterprise class networks. DNA is designed to be used for Internet Security, Intrusion detection, Network Management, Protocol and Network Analysis, Information Gathering, Network Monitoring applications.dsniffdsniff is a collection of utilities to aid in sniffing network data.E.L.AE.L.A. identifies and counts the network traffic by any application. In addition the traffic is separated between local network(s) and Internet (external networks).EffeTech HTTP SnifferEffeTech HTTP Sniffer is a HTTP protocol network sniffer, packet analyzer and file rebuilder based on Windows platform. Unlike most other sniffers, it is dedicated to capture IP packets containing HTTP protocol and to rebuild the HTTP communications and files sent through HTTP protocol.Engage Packet BuilderScriptable libnet-based packet builder for Windows platform.EthergrouikEthergrouik is a Windows open source project (C + GTK) whose main goal is to represent graphically connections by protocols on your network.EtherSnoopEtherSnoop is a basic network sniffer, that can capture all packets going through the network. It lists the captured data in real-time, using an easy-to-understand interface with a hex and text display of the packet content. EtherSnoop also offers basic filtering by protocol type and a tree-style packet explorer. The output can be saved to file and reloaded later if needed. ettercapEttercap is a multipurpose sniffer/interceptor/logger for switched LAN. It supports active and passive dissection of many protocols (even ciphered ones) and includes many feature for network and host analysis.FAP GuardFAP Guard allows DirecPC and DirecWay users to monitor their Fair Access Policy ( FAP ) download level, thus preventing them from getting throttled or disconnected. You might also find this application useful if you are paying for download, or have a download limit imposed by your ISP. It provides some interesting network traffic statistics as well.FanfareSVTThe Fanfare Group delivers one-click test automation™ for communication equipment manufacturers who need to reduce their time to market and improve product quality.FramePadFramePad is a Windows based packet sniffer and protocol analyzer, designed from the ground up with ease and functionality in mind. It allows you to examine data from a live network or from a capture file on disk.FTPXeroxFTPXerox grabs files that are transferred across the network using the FTP protocol. It implements a full end-to-end TCP re-assembly engine that watches for FTP transfers.Gamer's IPX Tunnel (GIT)GIT is a freeware utility to link LANs together over the internet for IPX-based network gameplay. It can also be used to bridge many configurations of IPX packets and frames from once point to another.GIPS IP Network SimulatorThe GIPS IP Network Simulator is a software tool that allows the user to emulate network behavior by delaying and/or dropping packets in an IP-network. Installed in a laptop it can be placed between two LAN’s, two gateways, or any two IP devices and simulate the network conditions experienced by the two end-points.Hammer Call AnalyzerThe Hammer Call Analyzer enables users to visualize signaling and voice quality problems in VoIP networks. For example, the unique call list and multistage call flow display features walk engineers through the legs of a particular call. In addition, the Hammer Call Analyzer displays waveforms and the Stream Quality Signature for any call. HiDownloadHiDownload is a multi-threaded download manager that allows you to download individual files (or lists of files) from web and FTP.HoneydHoneyd is a small daemon that creates virtual hosts on a network that enhances network security by providing "honeypot" decoys that enable network security officers to detect, monitor, and contain unauthorized network activities without the intruder knowing they are being tracked.hpinghping is a command-line oriented TCP/IP packet assembler/analyzer. The interface is inspired to the ping(8) unix command, but hping isn't only able to send ICMP echo requests. It supports TCP, UDP, ICMP and RAW-IP protocols, has a traceroute mode, the ability to send files between a covered channel, and many other features.HTTP snoop A simple but functional HTTP sniffer application. It will display a few basic information about every "HTTP packet" that it sees on the NIC and decode all basics authentication header entries it finds (both for proxies and for web sites). It will also write everything in the HTTP request that is both in the same packet and before the firs null char.HttpTracerView web traffic between browser and any Internet server. HttpTracer is a windows program that runs as a proxy server on your desktop, catching and displaying all textual commands and data sent and recieved by a web browser. jNetPCAPjNetPCAP is a java library that is a wrapper around WinPcap. What makes this library unique is that it is a comprehensive and accurate wrapper around the libpcap library.JPcapA Java wrapper for WinPcap. It allows Java code to access to the WinPcap (and libpcap on UNIX) calls.IM SnifferIntercepts and decodes all instant message traffic received by the computer. A high performance engine delivers real time message decryption. Conversations can be viewed immediately or saved for later analysis. Freeware. iNetWatcheriNetWatcher© is based on Winpcap, may fully monitor the Internet activity of staff or students, record the E-mail transmitting through the Internet and Web Page; monitor the various real-time chatting messages and IM files sent; monitor the register table, hard disk, system information of the employee's computer; monitor FTP; monitor net flow of all staff. ipInterceptorTrace TCP/UDP Packets on your workstation. View packets in a logical sequence, with requests and responses grouped into conversations (showing the resulting response times). Set filters for tracing. View headers and data in text or HEX format. IpMaster/IpMasterProInternet/Network Ip address & data packet monitor.IP SnifferWindows 2000/XP packet sniffer with replay function. Monitor is a bandwidth analysis utility. Besides giving a graphical illustration of the bandwidth usage on your computer or the network it resides, you get a list of all incoming and outgoing connections. KolSnifferKolsniffer contains a component to write very small self-contained WinPcap applications with Delphi and the Key Object Library framework. The source code is a translation of the Tsniffer class that Umar Sears wrote earlier. The source code is freeware, with the permission of the original author. It was written by . The zip filecontains a demo with sources, that illustrates how to use the component. The Key Object Library framework itself is available fromLaBrea@HomeLaBrea@Home is a version of the original network administrator's tool "LaBrea" for home use. LaBrea is a way to combat both port scanners and worms such as Code Red and Nimda. The original network administrator's "LaBrea" creates phantom machines which hold scanners and worms in a sort of "tarpit", luring them in, and holding onto their communications with what they think are real machines.LeetGeek ICMP TunnelerAn ICMP tunneling program.LibnetLibnet is a high-level API (toolkit) allowing the application programmer to construct and inject network packets. It provides a portable and simplified interface for low-level network packet shaping, handling and injection.LibnidsLibnids is an implementation of an E-component of Network Intrusion Detection System. It emulates the IP stack of Linux 2.0.x. Libnids offers IP defragmentation, TCP stream assembly and TCP port scan detection.LineAge UtilsLineAge Utils is tool that allows editing of colored chat, and NPC/mob description in Lineage 2 game. It also has integrated sniffer which allows user to import game character inventory and warehouse into material calculator, which is also part of LineAge Utils.lwIPlwIP is a small independent implementation of the TCP/IP protocol suite. The focus of the lwIP TCP/IP implementation is to reduce the RAM usage while still having a full scale TCP.MSN Protocol AnalyzerMSNProtocol Analyzer(MSNPAnalyzer) is a network utility that can monitor (or capture, monitor) the sessions of MSN Protocol. If you use this program in conbination with SwitchSniffer program, you can capture and see all the MSNP sessions including conversations and MSN commandsMSN Webcam RecorderMSN Webcam Recorder is a tool that allows you to record video streamed to and from your computer by MSN Messenger's Webcam Feature.myNetMonmyNetMon is windows based network monitor and packet analyzing (sniffer).NemesisNemesis is a command-line network packet injection utility for UNIX-like and Windows systems. You might think of it as an EZ-bake packet oven or a manually controlled IP stack. With Nemesis, it is possible to generate and transmit packets from the command line or from within a shell script.Net::Pcap for Win32A Perl interface to the libpcap library. Net::PcapUtils is available on the same site.NETI@homeNETI@home is an open-source software package that collects network performance statistics from end-systems. It has been written for and tested on the Windows, Linux, and Solaris operating systems, with testing for other operating systems to be completed soon. NETI@home is designed to run on end-user machines and will collect various statistics about Internet performance. These statistics will then be sent to a server at the Georgia Institute of Technology (Georgia Tech), where they will be collected and made publicly available.NetCalibratorNetCalibrator offers statistical analysis of captured data in support of performance analysis. The approach being used provides ability to quantify performance issues for small as well as large (>500,000) number of packets. NetPredictorNetPredictor offers monitoring and prediction of application performance. It enables you to build, or to interactively discover, the path between an application user and the server.netwib, netwox and netwagNetwib provides sniff, spoof, client, server and most functions needed by network programs. Toolbox netwox helps to find and solve networks' problems. Netwag is a graphical network toolbox. Netwox and netwag contain over 150 tools.NetWitnessNetWitness gives an organization the ability to quickly understand and respond to network activity of interest, regardless of the device provisioning the data or the application producing the packets.NetworkMinerA passive network monitoring tool for Windows with an easy-to-use graphical interface. NetworkMiner can detect operating systems, sessions, hostnames, open ports etc. without putting any traffic on the network. NetworkMiner can also parse PCAP files for off line analysis. The source code is available as open source.Network packet generatorNetwork Packet Generator (npg) is a free GNU GPL Windows packet injector (generator) that utilizes WinPcap to send specific packets out a single or multiple network interfaces. These packets and other extended options can be defined on the command line, in a packet file, or combination of the two.NeVODetermine vulnerabilities on your network through passive monitoring much like a sniffer. NeVO dynamically learns about your servers, services and vulnerabilities by performing signature and protocol analysis of the observed network sessions.NeWTEasy-to-use windows vulnerability scanner based on Nessus technology. NeWT installs on any Windows 2000 or Windows XP computer and can quickly scan several thousand hosts for vulnerabilities and produce detailed vulnerability reports. ngrepNgrep strives to provide most of GNU grep's common features, applying them to the network layerNmapNTNmap is a utility for network exploration or security auditing. It supports ping scanning (determine which hosts are up), many port scanning techniques (determine what services the hosts are offering), and TCP/IP fingerprinting (remote host operating system identification). Nmap also offers flexible target and port specification, decoy scanning, determination of TCP sequence predictability characteristics, sunRPC scanning, reverse-identd scanning, and more.ntopntop is a tool that shows the network usage, similar to what the popular top Unix command does.Nuzzler IDSThe Securepoint Intrusion Detection System (Nuzzler) allows to analyse the network for intrusion detection. Nuzzler can detect possible attacks, viruses, trojans and other bad traffic.Oidview MIB BrowserMIB browser and snmp toolset for network fault management. Free download for network professionals.P2P WatchDogP2P WatchDog is a network sniffer which can monitor and block several Peer-to-Peer file transfer protocols, including FastTrack, Gnutella, DirectConnect, EarthStation5, eDonken, Filetopia, BitTorrent, MP2P, and Overnet.PacanalPacket capture and analyzer program. The source contains a C# reimplementation of the packet.dll WinPcap library. Packet ExcaliburA multi-platform graphical and scriptable network packet engine with extensible text based protocol descriptions.PacketVBIts an ActiveX for use with Visual Basic that wraps the function exported by the WinPcap API (packet.dll). PacketXPacketX is set of ActiveX classes that integrate winpcap packet capture functionality with Visual Basic or anyother programming environment supporting Microsoft ActiveX technology.PacketyzerPacketyzer is a Windows user interface for the Ethereal packet capture and dissection library.PcapyPcapy is a Python extension module that interfaces with WinPcap/libpcap. Pcapy enables python scripts to capture packets on the network. is a .net wrapper for WinPcap written in C++/CLI and C#. It Features almost all WinPcap features and includes a packet interpretation framework. It has different advantages over previously existing WinPcap wrappers and is still in development for new features and bug fixes and is written with pretty high standards of coding.PerformaSureSitraka PerformaSure allows J2EE development teams to identify sources of performance problems within an assembled application. PerformaSure coordinates the collection of performance metrics for any given transaction, following the path of execution from the initial HTTP request through load balancers, application servers, to the database and back again.PI IT MonitorPI IT Monitor collects real-time information regarding the performance of various elements that compose an IT infrastructure. But in addition to collecting real-time values, PI IT Monitor archives such data and makes them available for use in reporting, analysis, troubleshooting, and decision making.PingPlotterPingPlotter is a network troubleshooting and diagnostic tool. It uses a combination of traceroute, ping, and whois to collect data quickly, and then allows you to continue to collect data over time to give you the information you really need to identify problems (both short-term and long-term trends).PromiScanSoftware for remotely monitoring computers on local networks to locate network interfaces operating in a promiscuous mode.PortScannerA TCP port scanner.PSentry Internet Policy Guard & SurveillancePSentry sniffs network traffic at gateway point, captures and records user activites like web surf, emails, web submissions, instant messager sessions (AOL aim, MSN, ICQ, Yahoo, QQ, googletalk). It can log or block ftp, p2p file transfers. PSentry deloys different Internet policies by IP/MAC address or by user, to controls which resource or servce is permited or blocked on a LAN.Pseud IP MasqueradePseud IP Masquerade is a Windows application and NT/2000 Serivce, that has some basic functions of "IP Masquerade".pypcapsimplified object-oriented Python extension module for libpcap - the current version, the legacy version shipping with some of the BSD operating systems, and the WinPcap port for Windows.QtNetworkMonitorThe project is a KISS network monitor that works under both Windows and Linux. It shows how much bandwidth you are taking on a daily basis.rawstuffrawstuff is a toolkit for totally raw (MAC level and with no TCP/IP installed) send and receive on Windows. SatoriSatori is a passive OS Fingerprinting tool for Windows. Unlike most other passive tools it parses and tries to use the following protocols for OS Identification: CDP, DHCP, EIGRP, HPSP , HSRP, ICMP, IGMP, HTTP, MDNS, OSPF, SAP, SCCP, SMB, SNMP, STP, TCP, and UPNP with new protocols being added from time to time.Show TrafficShow Traffic monitors network traffic on the chosen network interface and displays it continuously. It could be used for locating suspicious network traffic or to evaluate current utilization of the network interface.SIMHSIMH is a highly portable, multi-system simulator.SniphereSniphere is an another network wiretapping program for Windows using winpcap. Nevertheless, Sniphere is a pretty handy program with a lot of possibilities which most of free sniffers do not have.SmartSniffSmartSniff allows you to capture TCP/IP packets that pass through your network adapter, and view the captured data as sequence of conversations between clients and servers. You can view the TCP/IP conversations in Ascii mode (for text-based protocols, like HTTP, SMTP, POP3 and FTP.) or as hex dump.snoopSnoop is component library encapsulating WinPcap used in Delphi.SnoopAnalyzerSnoopAnalyzer Standard is a network protocol analyzer based on network data capturing technology under Microsoft Windows platforms(95/98/Me/2000/NT/XP).SnoopMSNBlockSnoopMSNBlock is a software to block MSN messenger service used in your company. SnoopNetCoopSnoopNetCop Standard is a program that can detect possible packet sniffing attack on your network. snortSnort is a lightweight network intrusion detection system, capable of performing real-time traffic analysis andpacket logging on IP networks.snotSnot is an arbitrary packet generator, that uses snort rules files as its source of packet information. It can be used asan IDS evasion tool, by using specific decoy hosts, or just something to keep your friendly IDS monitoring staff busy. SOAPscopeSOAPscope is a Web services diagnostic system that collects and analyzes information about SOAP and WSDL by monitoring communications among SOAP endpoints.ssldumpssldump is an SSLv3/TLS network protocol analyzer. It identifies TCP connections on the chosen network interface and attempts to interpret them as SSLv3/TLS traffic. When it identifies SSLv3/TLS traffic, it decodes the records and displays them in a textual form to stdout. If provided with the appropriate keying material, it will also decrypt the connections and display the application data traffic.STINGA NGN Monitor:Protocol analyser focusing on SS7oIP from Utel Systems. Protocols like ISUP (ITU, ANSI, UK), SCCP, TCAP, MAP, INAP, CAP/CAMEL, SMS, IS-41, Megaco/H.248, MGCP, SIP, SDP, RTP, SIP-T (ITU, ANSI, UK, DPNSS/DASS2), SCTP,M2PA, M2UA, M3UA, SUA, IAU, DUA, V5UA, TCP, UDP, IP and others are decoded in detaild by this product.STINGA SIP SimulatorProtocol simulator for SIP and SDP protocol testing.SuperAgentThis product from NetQoS analyzes application response times without the need to deploy client-side agents. TCPKillNTTCPKillNT is a TCP connection "Reset" utility for Microsoft Windows NT platforms. It has the ability to send RST packets to already established TCP connections. Quite deadly on a LAN. It is very useful for IDS kind of products which need to terminate a TCP session.tingting is an OSI layer 4 connectivity assurance tool. It supports UDP multicast, unicast and TCP/IP. It makes use of the packet capture library to perform passive multicast monitoring.TJesNetMonitorBorland C++ Builder wrapper for WinPcap. Comes with a sample application.TraceDetTraceDet is a Traceroute Detector for Windows NT. Basically, it detects and logs if somebody trace routes to your host. The idea is that when somebody traces to your host, you receive IP packets with TTL value equal to 1. So, TraceDet looks out for suchpackets.tracetcptracetcp is a command line traceroute utility for WIN32 that uses TCP SYN packets rather than ICMP/UDP packets that the usual implementations use, thus bypassing gateways that block traditional traceroute packets.TrafficStatisticMZL & Novatech TrafficStatistic shows the consumed traffic volume comfortably in system tray.TrafficWatcherA tool to measure network traffic by service (FTP, mail, news, web, UDP etc)TrafMeterTrafMeter is an utility for accounting and realtime monitoring of Internet traffic to and from a local network. It includes flexible filter engine, extensive logging facility and friendly user interface.uIPuIP is an implementation of the TCP/IP protocol stack intended for small 8-bit and 16-bit microcontrollers. It provides the necessary protocols for Internet communication, with a very small code footprint and RAM requirements - the uIP code size is on the order of a few kilobytes and RAM usage is on the order of a few hundred bytes.Unsniff Network AnalyzerUnsniff features brand new visualization of packet data, advanced reassembly capabilities, full stream monitoring and several other enhancements over the current crop of network analyzers. What really sets Unsniff apart is its Scripting capabilities. Unsniff allows you to write your own network analysis scripts using the Ruby scripting language.You can also write powerful protocol handlers and other types of plugins using XML and/or C++. Unsniff is even available in Japanese.Url SnooperUrl Snooper is a a program written to help users locate the urls of audio and video files so that they can be recorded. VB.PCAPVB.PCAP is an "Open Source and completely free" packet capture library for Visual Basic (tested on VB5 andVB6, not tested on ) based on Winpcap. The library exposes a set of APIs, that wrap aroud Winpcap using the _stdcall convention. The library is the foundstone for a network analyzer in VB.Viper ChatViperChat is a FREE LAN chat client compatible with Vypress Chat™ protocol version 1.93. It uses UDP communication over WinPcap.VLADescu VLADescu is a network content sniffer, it is currently able to recognize gif, jpeg and audio mpeg files. VLADescu listens to network traffic and picks out images and mp3s from sniffed TCP streams. It can be used on local LAN or on wireless network (if your driver supports promiscuous mode, or even better, monitor mode).WallCoolerWallCooler is a powerful and flexible VPN solution to access Home or Office computers & networks from anywhere. All Windows based applications are supported, no need to use special applications or synchronize files. Users can remote access organization's databases, e-mails, remote desktops, product catalogue... from anywhere. WallCooler sits on the local company network, uses an existing Internet connection and automatically manages incoming connections via relay servers.Warp PipeWarp Pipe is free software that runs on your PC or Mac and is available for Windows, Mac OSX, Linux, and BSD operating systems. While running on your PC or Mac, Warp Pipe allows you to play LAN-enabled Nintendo GameCube games over the Internet with other GameCube gamers.Watt-32Watt-32 is a library for making networked TCP/IP programs in the language of C and C++ under DOS and Windows-NT. WebSnurfWebsnurf is a small application that follows a user web-surfing; that is to say, as you run WebSnurf on your PC, you can pursue web-surfing movements made on another PC. Obviously, you have to be connected over the same LAN.Win32::NetPacketWin32::NetPacket is an Object-Oriented interface to the WinPcap packet.dll library.Windows ARP SpooferWindows ARP Spoofer (WinArpSpoof) is a program that can scan the computers including network devices and can spoof their ARP tables on local area network and can act as a router while pulling all packets on LAN.Windows ToolboxThe Windows Toolbox is a comprehensive collection of software and information for Windows - a toolbox of high quality applications and utilities for a wide array of functions, all freely re-distributable and under Free, Open Source, Freeware, Shareware or similar licences; documents on installing, configuring and maintaining Windows and various software applications, for stability, performance, usability and security.WindumpWinDump is the Windows version of the famous tcpdump Unix tool. It's developed and maintained by the WinPcap team. WinfingerprintWinfingerprint is a Win32 Host/Network Enumeration Scanner. Winfingerprint is capable of performing SMB, TCP, UDP, ICMP, RPC, and SNMP scans.WinPcapArpWinPcapArp is ARP client library that works on Windows OS(NT and 2000). The main purpose of this library is to get a MAC address of the target ethernet NIC with the IP address.WinPcapDhcpCDWinPcapDhcpCD is a DHCP client demon library that works on Windows OS (NT and 2000). The purpose of this library is to get more than one IP addresses in your application program.winpcapyPython port of Winpcap functions using ctypes. Work with Python 2.x and 3 under Linux / Windows. This is a low level implementation, no object or pythonic way, so you need ctypes knowledge to use it.WinSniffWinSniff is an application for capturing packets on the network. It displays all the packets that are transmitted on the local network and gives detailed information about each header in the packet.WinWhifWinWhif allows any PC running Windows (95, 98, NT or 2000) to record the DICOM traffic between two machines on the same network. It can be useful in diagnosing DICOM communications problems.Wireshark/EtherealWireshark (formerly known as Ethereal) is the world's most popular network analyzer. It allows you to examine data from a live network or from a capture file on disk. You can interactively browse the capture data, viewing summary and detail information for each packet. Wireshark has several powerful features, including a rich display filter language and the ability to view the reconstructed stream of a TCP session.wpa_supplicantwpa_supplicant is a WPA Supplicant for Linux, BSD and Windows with support for WPA and WPA2 (IEEE 802.11i / RSN). It implements key negotiation with a WPA Authenticator and it controls the roaming and IEEE 802.11authentication/association of the wlan driver.WIRE1xWIRE1x is an open source implementation of IEEE 802.1x client (supplicant). It supports various EAP authentication methods.YATTYATT is a project to replace the current proliferation of trace tools ( tcpTrace, proxyTrace, pcapTrace ), with a single extensible tracing tool. YATT features a new GUI built with WTL, complete with a Hex View mode, and currently ships with 2 Trace providers, one based on WinPCAP and one based on the W2K Raw sockets support.YorkYork logs ip/fqdn addresses if all traffic. It can save sniffed http and ftp files. Also you can sniff for HTTP, FTP, POP3, SMTP, SMB, VNC and AIM password/hash. Further you can see the web browsing from other users, so your browser will show the same pages as the selected user. A screensaver is included, it shows the pictures which are sniffed in a slide show manner.。
Winpcap使用介绍
Winpcap使用介绍1. Winpcap简介Winpcap(windows packet capture)是在Win32平台上的强大的、有较好扩展性的底层网络分析体系结构,是Unix下的lipbcap移植到windows下的产物,是Win32环境下数据包捕获的开放代码函数库。
Winpcap是第一个Win32开放式的捕获包的体系结构,能够支持大多数应用程序的需要。
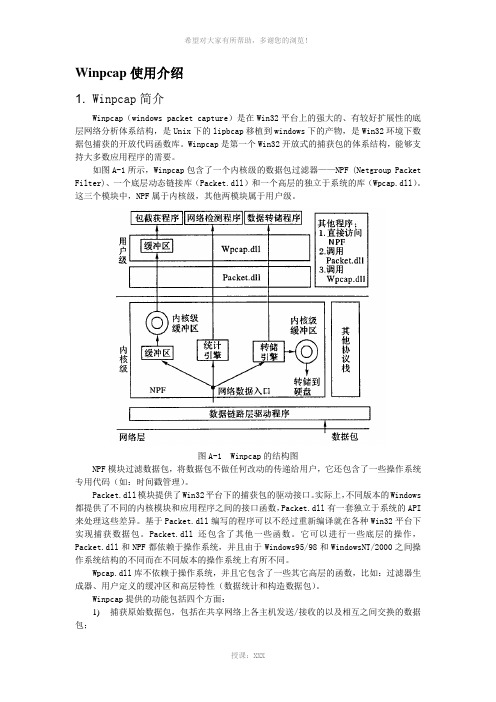
如图A-1所示,Winpcap包含了一个内核级的数据包过滤器——NPF (Netgroup Packet Filter)、一个底层动态链接库(Packet.dll)和一个高层的独立于系统的库(Wpcap.dll)。
这三个模块中,NPF属于内核级,其他两模块属于用户级。
图A-1 Winpcap的结构图NPF模块过滤数据包,将数据包不做任何改动的传递给用户,它还包含了一些操作系统专用代码(如:时间戳管理)。
Packet.dll模块提供了Win32平台下的捕获包的驱动接口。
实际上,不同版本的Windows 都提供了不同的内核模块和应用程序之间的接口函数,Packet.dll有一套独立于系统的API 来处理这些差异。
基于Packet.dll编写的程序可以不经过重新编译就在各种Win32平台下实现捕获数据包。
Packet.dll还包含了其他一些函数。
它可以进行一些底层的操作,Packet.dll和NPF都依赖于操作系统,并且由于Windows95/98和WindowsNT/2000之间操作系统结构的不同而在不同版本的操作系统上有所不同。
Wpcap.dll库不依赖于操作系统,并且它包含了一些其它高层的函数,比如:过滤器生成器、用户定义的缓冲区和高层特性(数据统计和构造数据包)。
Winpcap提供的功能包括四个方面:1)捕获原始数据包,包括在共享网络上各主机发送/接收的以及相互之间交换的数据包;2)在数据包发往应用程序之前,按照自定义的规则将某些特殊的数据包过滤掉;3)在网络上发送原始的数据包;4)收集网络通信过程中的流量信息。
WinpCap的详解(一)

WinpCap的详解(一)首先来百科一下Winpcap是一个什么东东。
Winpcap(windows packet capture)是windows平台下一个免费,公共的网络访问系统。
它有如下几个功能:1、捕获原始数据包,包括在共享网络上各主机发送/接收的以及相互之间交换的数据;2、在数据包发往应用程序之前,按照自定义的规则将某些特殊的数据包过滤掉;3、在网络上发送原始的数据包;4、收集网络通信过程中的统计信息。
从上面的功能来看,这个库文件提供了许多的API函数,可以让我们捕获网络上的数据包以及统计网络通信的信息。
为了更直观的反应这个库文件的作用,我们来看看利用这个库文件写出来的一个应用软件,wireshark。
界面如下图所示,这个界面只是捕获数据的一个小界面,里面有很多的设置,有兴趣可以下载一个试试。
他能统计在一个局域网的所有网络信息。
这里面重要一点,需要提醒的是:winpcap的主要功能在于独立于主机协议(如TCP-IP)而发送和接收原始数据包。
也就是说,winpcap不能阻塞,过滤或控制其他应用程序数据包的发收,它仅仅只是监听共享网络上传送的数据包。
也就是说,WinpCap主要功能不能截取网络中的数据,他只能监听里面的数据。
对于WinpCap的结构以及原理,我们自然可以不用理会啦,我们只需要知道他的用途就行啦!一、安装WinpCap1、首先我们来看看如何安装WinpCap这个库,首先是下载WinpCap安装文件,这里有许多的版本,可以在官网上下载,,这里重点提醒一下,特别需要注意一下版本,如果你的版本是4.02,那么你的安装包也必须下载对应的版本,这里特别注意下,你可以下载当前比较稳定的版本。
下载之后安装就ok啦!这里我用的是WinpCap4.02.2、下载WinpCap Develop's Packs,这里我也提供相同的版本WpdPack4.02.3、解压后会得一个目录WpdPack四个子目录:docsExamples-pcapExamples-remoteIncludeLib然后配置VC++tools --> options --> Projects and Solutions --> VC++ Directories :Include files :WpdPackPath\includeLibrary files:WpdPackPath\lib4、经过上面的步骤之后,你的WinpCap应该就安装成功啦,之后就是运行一下里面提供的例程啦,如果有什么问题,就对应的把问题在网上查一查,总体来说有以下几个问题:第一个就是需要在工程的链接库上添加wpcap.lib链接库;第二个就是你的SDK太老了,需要添加更新你的SDK,相应的到官方网站上下载适合你电脑的SDK。
Winpcap使用

Winpcap使⽤前⾔随着⽹络⼊侵的不断发展,⽹络安全变得越来越重要,于是⽹络⼊侵取证系统的研究也变得⽇益重要。
在⽹络⼊侵取证系统中,对⽹络上传送的数据包进⾏有效的监听即捕获包是⽬前取证的关键技术,只有进⾏⾼效的数据包捕获,⽹络管理员才能对所捕获的数据进⾏⼀系列的分析,从⽽进⾏可靠的⽹络安全管理。
1winpcap简介WinPcap是由伯克利分组捕获库派⽣⽽来的分组捕获库,它是在Windows操作平台上来实现对底层包的截取过滤。
WinPcap为⽤户级的数据包提供了Windows 下的⼀个平台。
WinPcap是BPF模型和Libpcap函数库在Windows平台下⽹络数据包捕获和⽹络状态分析的⼀种体系结构,这个体系结构是由⼀个核⼼的包过滤驱动程序,⼀个底层的动态连接库Packet.dll和⼀个⾼层的独⽴于系统的函数库Libpcap组成。
底层的包捕获驱动程序实际为⼀个协议⽹络驱动程序,通过对NDIS中函数的调⽤为Win95、Win98、WinNT、和Win2000提供⼀类似于UNIX系统下Berkeley Packet Filter的捕获和发送原始数据包的能⼒。
Packet.dll是对这个BPF驱动程序进⾏访问的API接⼝,同时它有⼀套符合Libpcap接⼝(UNIX下的捕获函数库的函数库。
WinPcap的结构图如图1。
WinPcap包括三个部分:第⼀个模块NPF(Netgroup Packet Filter,是⼀个虚拟设备驱动程序⽂件。
它的功能是过滤数据包,并把这些数据包原封不动地传给⽤户态模块,这个过程中包括了⼀些操作系统特有的代码。
第⼆个模块packet.dll为win32平台提供了⼀个公共的接⼝。
不同版本的Windows系统都有⾃⼰的内核模块和⽤户层模块。
Packet.dll⽤于解决这些不同。
调⽤Packet.dll的程序可以运⾏在不同版本的Windows平台上,⽽⽆需重新编译。
第三个模块Wpcap.dll是不依赖于操作系统的。
Winpcap学习笔记

说明:本系列文章是我阅读winpcap手册后整理的一个学习笔记。
文章中出现的所有代码是我根据winpcap手册中的示例代码进行了学习,并调试通过,其中对部分代码作了修改,关于代码的版权我尊重winpcap手册中的版权说明,如果你使用了本系列文章中的代码而引起任何的版权或造成安全威胁等问题,我将不负任何责任。
下载好了WpdPack_3_2_alpha1.zip(下载地址:/install/bin/WpdPack_3_2_alpha1.zip),解压后除了有文档,例子外还有Include和lib,于是想用TC2来做开发环境,但是编译的时候老是出问题,于是放弃。
后来阅读了Winpcap手册后才知道因为是在windows上开发,所以它推荐用VC++6.0,于是改用VC。
第一个试验是:#include#includeint main() {pcap_if_t *alldevs;pcap_if_t *d;int i = 0;char errbuf[PCAP_ERRBUF_SIZE];/* Retrieve the device list from the local machine*/if (pcap_findalldevs_ex(PCAP_SRC_IF_STRING, NULL /* auth is not needed */, &alldevs, errbuf) == -1){printf("Error in pcap_findalldevs_ex: %s\n", errbuf);exit(1);}/* Print the list */for (d = alldevs; d != NULL; d = d->next){/* Print the device’s name */printf("%d. %s", ++ i, d->name);/* Print the device’s dscription */if (d->description){printf("(%s)\n", d->description);}else{printf("(No description available)\n");}}if (i == 0){printf("\nNo interfaces found! Make sure WinPcap is installed.\n");return 0;}/* We don’t need any more the device list. Free it */pcap_freealldevs(alldevs);return 1;}编译的时候又遇到问题——“无法打开pcap.h”。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
深度剖析WinPcap之(三)——所涉及的Windows驱动基础知识1.1 Windows驱动的基础知识本节主要描述在WinPcap的NPF中经常使用一些编写Windows驱动程序所需掌握的部分基础知识,以便于后面的理解。
1.1.1 驱动对象(DRIVER_OBJECT)每个驱动程序都有唯一的驱动对象与之对应,该驱动对象在驱动程序被加载时由内核的对象管理程序所创建。
驱动对象用DRIVER_OBJECT数据结构表示,它作为驱动程序的一个实例被内核加载,对一个驱动程序内核I/O管理器只加载一个实例。
驱动对象数据结构在wdm.h文件中的定义如下。
typedef struct _DRIVER_OBJECT {CSHORT Type;CSHORT Size;/**DeviceObject为每个驱动程序所创建的一个或多个设备对象链表,*Flags提供一个扩展的标识定位驱动对象*/PDEVICE_OBJECT DeviceObject;ULONG Flags;/*下列各成员字段描述驱动程序从哪儿被加载*/PVOID DriverStart;ULONG DriverSize;PVOID DriverSection;PDRIVER_EXTENSION DriverExtension;/**DriverName成员被错误日志线程用来*确定一个I/O请求越界的驱动名称*/UNICODE_STRING DriverName;/*指向注册表中硬件信息的路径*/PUNICODE_STRING HardwareDatabase;/**如果驱动支持“fast I/O”,*就指向一个“fast I/O”的派遣函数数组*/PFAST_IO_DISPATCH FastIoDispatch;/**描述该特定驱动的入口点。
*主函数(major function)派遣函数表必须是对象最后的成员,*因此它仍然是可扩展的*/PDRIVER_INITIALIZE DriverInit;PDRIVER_STARTIO DriverStartIo;PDRIVER_UNLOAD DriverUnload;PDRIVER_DISPATCH MajorFunction[IRP_MJ_MAXIMUM_FUNCTION + 1];} DRIVER_OBJECT;typedef struct _DRIVER_OBJECT *PDRIVER_OBJECT;下面分别描述驱动对象中驱动程序可访问的成员。
PDEVICE_OBJECT DeviceObject每个驱动对象会有一个或多个设备对象。
每个设备对象都有一个指针(NextDevice)指向下一个驱动对象,最后一个设备对象指向空。
此处的DeviceObject指向驱动对象的第一个设备对象。
该成员在成功调用IoCreateDevice后自动更新。
一个驱动程序使用该程成员与设备对象(DEVICE_OBJECT)的NextDevice可遍历给驱动对象的所有设备对象。
在驱动被卸载的时候,需要遍历每个设备对象,并将其删除。
PUNICODE_STRING HardwareDatabase指向注册表中硬件配置信息的路径,用UNICODE字符串表示。
该字符串一般为\REGISTRY\MACHINE\HARDWARE\DESCRIPTION\SYSTEM。
PFAST_IO_DISPATCH FastIoDispatch指向一个定义驱动快速 I/O结构体的入口点,该成员只用于文件系统驱动与网络传输驱动。
PDRIVER_INITIALIZE DriverInit是DriverEntry例程的入口点,由I/O管理器设置。
PDRIVER_STARTIO DriverStartIo是Startl0例程的的入口点,如果需要,由DriverEntry例程设置,否则为NULL。
PDRIVER_UNLOAD DriverUnload指向驱动卸载时所用回调函数的入口点。
PDRIVER_DISPATCH MajorFunction[IRP_MJ_MAXIMUM_FUNCTION+1]一个函数指针数组,数组MajorFunction中的每个成员保存着一个指针,每一个指针指向一个处理对应IRP(IRP_MJ_XXX)的派遣函数(DispatchXxx)。
每个派遣函数(DispatchXxx)声明如下:NTSTATUS(*PDRIVER_DISPATCH) (IN PDEVICE_OBJECT DeviceObject,IN PIRP Irp);1.1.2 设备对象(DEVICE_OBJECT)设备对象保存设备特征和状态的信息。
一个设备对象表示一个逻辑的、虚拟的或物理的设备,由一个驱动对象操控设备对象的I/O请求。
每一个内核模式的驱动必须创建设备对象,通过调用IoCreateDevice一次或多次。
每个驱动程序会创建一个或多个设备对象,用DEVICE_OBJECT数据结构表示。
每个设备对象有一个指针(NextDevice)指向下一个设备对象,从而形成一个设备链表。
设备链表第一个设备是由驱动对象结构体中DeviceObject指明的。
设备对象数据结构在wdm.h文件中的定义如下。
typedef struct DECLSPEC_ALIGN(MEMORY_ALLOCATION_ALIGNMENT) _DEVICE_OBJECT{CSHORT Type;USHORT Size;LONG ReferenceCount;struct _DRIVER_OBJECT *DriverObject;struct _DEVICE_OBJECT *NextDevice;struct _DEVICE_OBJECT *AttachedDevice;struct _IRP *CurrentIrp;PIO_TIMER Timer;ULONG Flags;ULONG Characteristics;__volatile PVPB Vpb;PVOID DeviceExtension;DEVICE_TYPE DeviceType;CCHAR StackSize;union {LIST_ENTRY ListEntry;WAIT_CONTEXT_BLOCK Wcb;} Queue;ULONG AlignmentRequirement;KDEVICE_QUEUE DeviceQueue;KDPC Dpc;/**下列成员是为支持文件系统的互斥操作,*为了对文件系统处理线程使用设备的计数保持跟踪*/ULONG ActiveThreadCount;PSECURITY_DESCRIPTOR SecurityDescriptor;KEVENT DeviceLock;USHORT SectorSize;USHORT Spare1;struct _DEVOBJ_EXTENSION *DeviceObjectExtension;PVOID Reserved;} DEVICE_OBJECT;typedef struct _DEVICE_OBJECT *PDEVICE_OBJECT;下面分别描述设备对象中驱动程序可访问的成员。
PDRIVER_OBJECT DriverObject指向驱动程序中的驱动对象。
同属于一个驱动程序的驱动对象指向的是同一个驱动对象。
PDEVICE_OBJECT NextDevice指向下一个设备对象。
这里的下一个设备对象是同一个驱动程序创建的若干设备对象。
每个设备对象根据NextDevice域形成链表,从而可以遍历每个设备对象。
在每次成功调用IoCreateDevice 后I/O管理器更新该链表。
在驱动被卸载的时候,需要遍历该链表,删除每个设备对象。
PIRP CurrentIrp如果驱动使用Startl0例程时,此成员指向当前IRP结构。
否则为NULL。
ULONG Flags此成员是一个32位昀无符号整型,每个位有不同的含义。
通过位或操作为新创建的设备对象设置不同的特性。
ULONG Characteristics当驱动程序调用IoCreateDevice时,设置下列一个合适的值:FILE_REMOVABLE_MEDIAFILE_READ_ONLY_DEVICEFILE_FLOPPY_DISKETTEFILE_WRITE_ONCE_MEDIAFILE_DEVICE_SECURE_OPENPVOID DeviceExtension指向设备扩展对象。
设备扩展对象是由程序员在驱动中自行定义的结构体,结构体的大小在调用IoCreateDevice时设置。
每个设备都会指定一个设备扩展对象,设备扩展对象记录的是特别定义的结构体。
在驱动程序中应该尽量避免全局变量的使用,因为全局变量涉及不容易同步的问题,解决的办法可将全局变量存储在设备扩展中。
DEVICE_TYPE DeviceType指明设备的类型,由IoCreateDevice设置。
根据设备需要填写相应的设备类型。
.CCHAR StackSize在多层驱动的情况下,驱动与驱动之间形成类似堆栈的结构。
IRP会依次从最高层传递到最底层。
StackSize就是指定发送到该驱动的IRP在堆栈位置的最小层数。
IoCreateDevice 在一个新创建的设备对象中设置该成员。
ULONG AlignmentRequirement设备在大容量传输的时候,为了保证传输速度需要内存对齐。
每个设备对象在它新创建的设备对象中设置该成员。
1.1.3 设备扩展(_DEVICE_EXTENSION)设备对象记录设备的“通用”信息,而另外一些“特殊”信息记录在设备扩展中。
设备扩展由程序员自行定义,指定内容与大小,由I/O管理器创建,保存在非分页内存中。
在驱动程序中,尽量避免使用全局函数,因为全局函数往往导致函数的不可重入性。
一个解决办法就是将全局变量以设备扩展的形式存储,并加以适当的同步保护措施。
WinPcap中NPF的设备扩展结构体,主要用于存储每个被NPF绑定的适配器的一些信息,结构体定义如下:typedef struct _DEVICE_EXTENSION {//适配器名称NDIS_STRING AdapterName;//设备导出的名称,也就是通过WinPcap应用程序使用该名称来打开该适配器PWSTR ExportString;} DEVICE_EXTENSION, *PDEVICE_EXTENSION;1.1.4 IRP与派遣函数驱动程序的主要功能是负责处理l/O请求,大部分1/0请求是在派遣函数中处理的。
IRP 的处理机制类似Windows应用程序中的“消息处理”机制。
用户空间对驱动程序的所有1/0请求,全部由操作系统转化为一个IRP数据结构,不同的IRP数据会被“派遣”到不同的派遣函数中,在派遣函数中处理IRP。
