人文社科软件用户手册_userguide2016
zenoss中文管理手册05.用户管理
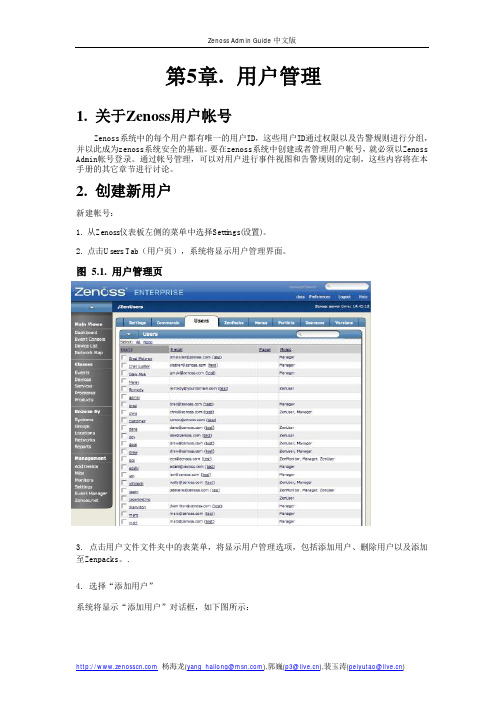
第5章.用户管理1. 关于Zenoss用户帐号Zenoss系统中的每个用户都有唯一的用户ID,这些用户ID通过权限以及告警规则进行分组,并以此成为zenoss系统安全的基础。
要在zenoss系统中创建或者管理用户帐号,就必须以Zenoss Admin帐号登录。
通过帐号管理,可以对用户进行事件视图和告警规则的定制,这些内容将在本手册的其它章节进行讨论。
2. 创建新用户新建帐号:1. 从Zenoss仪表板左侧的菜单中选择Settings(设置)。
2. 点击Users Tab(用户页),系统将显示用户管理界面。
图 5.1. 用户管理页3. 点击用户文件文件夹中的表菜单,将显示用户管理选项,包括添加用户、删除用户以及添加至Zenpacks。
.4. 选择“添加用户”系统将显示“添加用户”对话框,如下图所示:图 5.2. 添加用户对话框5. 输入用户名.6. 输入该用户帐号的一个电子邮件地址。
该电子邮件帐号将是未来接收系统告警的邮件帐号。
7. 点击OK按钮,新建的用户帐号将出现在用户列表中。
至此,一个新的用户帐号创建完毕。
管理员还可以继续编辑用户帐号以设置用户帐号口令以及其它更详细的信息,具体操作详见本用户手册的编辑用户帐号部分。
3. 编辑用户帐户1. 从Zenoss仪表板左侧的菜单中选择Settings(设置)。
2. 点击Users Tab(用户页),系统将显示用户管理界面。
3.点击需要编辑的帐号的用户名,系统将显示单一用户管理界面,如下图所示。
图 5.3. 单一用户管理页面4. 修改用户详细信息,点击Save(保存)按钮后保存退出。
.3.1. 设定用户密码从单一用户管理界面中,可以为用户指定口令。
在第一个文本框中输入用户口令,在第二个文本框中再次输入口令进行确认。
3.2. 编辑用户联系信息在单一用户管理界面中,管理员可以重新输入或者编辑用户的电子邮件地址或者寻呼机号码。
3.3. 向用户分派角色和权限在单一用户管理界面中,管理员可以为用户指定具体的角色。
ThinkServer TS140 用户手册 V1.2

IT用户帐号管理系统指导手册(中英文版)

IT用户帐号管理系统指导手册(中英文版)Ref: 3.1.DIT System GuidelineIT用户邮管理系统指导手册(IT User Account Management System Guideline) Rev Revision Details Author Effective Date 1.0 Initial release Ada Wong Dec 8, 2010 1.1 Updated Ada Wong Feb 16, 2011Main Contents1. 建立用户帐号(Create User Account)2. 编辑用户帐号信息(Modify User Account Information3. 删除用户帐号(Delete User Account)4. 邮件组(Email Grouping)5. 其它邮件授权(Other Email Authority)IT System GuidelineContents1. 建立用户帐号(Create UserAccount) (1)1.1 邮件(Email)................................................................. (1)1.1.1 邮件地址本显示名规则(Email Address Book Display Name Convention) .. 11.1.2 职员信息(StaffInformation) ........................................................... .. (2)1.1.3 邮件组(EmailGrouping) .............................................................. .. (2)1.1.4 Out of OfficeCalendar .................................................. 错误~未定义书签。
社科项目管理系统使用手册

社科项目管理系统使用手册(普通用户版)2020年3月目录一、用户登录 (3)1、用户登录 (3)2、用户注册 (4)二、普通用户操作说明 (7)1、首页 (7)2、项目申报 (7)(1)发起申报 (7)(2)选择申报项目类型 (9)(3)填写申报表 (9)(4)提交申报表 (11)(5)查看已申报项目状态 (12)3、待办任务 (14)(1)进度汇报 (15)(2)中期评估申请 (16)(3)结题申请 (16)(4)提交课题成果 (17)4、已办任务 (18)一、用户登录1、用户登录注意:(1)如果已经在社科联门户网站、“社科学术数据服务平台”的社科评奖系统、创新团队管理系统、社科项目管理系统、社科组织管理系统等系统注册过账号,使用已注册账号、密码登录即可;(2)如果没有注册过,需要先进行注册,具体操作参见“用户注册”章节。
社科项目管理系统的入口,在云南省社科联门户网站首页的“社科学术数据服务平台”中,点击“社科项目管理系统”:出现登录页面后,输入正确的账号、密码,点击登录即可:2、用户注册注意:以下情况不需要再进行注册:如果已经在社科联门户网站、“社科学术数据服务平台”的社科评奖系统、创新团队管理系统、社科项目管理系统、社科组织管理系统等系统注册过账号,使用已注册账号、密码登录即可。
如果之前没有注册过账号,需要先进行注册。
点击云南省社科联门户网站首页右上角的“用户登录”:出现如下登录界面:如果没有注册过,点击“申请注册”,在下面的界面中填写信息:填写说明:姓名、手机、身份证号、Email请务必填写正确。
填写完所有信息后,请点击“获取验证码”,获取到手机短信验证码,并填写在“验证码:”之后,再点击“注册”。
二、普通用户操作说明1、首页普通用户登录成功后,进入普通用户首页,可以进行信息查看,包括待办任务、通知公告、申报指南:对于已经申报的项目,如果有需要您处理的任务(如进度汇报、提交课题成果等),会出现在待办任务中,您可以点击待办任务中的项目名称进行处理。
Veritas 用户手册说明书
Veritas User Guide Quick Reference GuideTHANK YOU FOR VOTING TEXECOM THANK YOU FOR VOTING TEXECOMUSER GUIDESecurity Control PanelsIssue 21 INS167Overview Premier Series User Guide 2 INS221 IntroductionUsers of the alarm system will be assigned a unique 4, 5 or 6 digit User code. User codes are used to arm and disarm the system. Some User codes can also access additional options such as, system tests and omitting zones.Keypads will be installed throughout the premises, usually one at each entry/exit door. The keypads are used to perform all of the system operations i.e. Arming, Disarming etc. Most User codes can be used at any keypad on the system. However, Local Users will only be able to use certain keypads on the system.The Emergency KeysIn case of emergency, the alarm system can provide three immediate emergency alarms by pressing and holding two specific keys for two seconds. !"The emergency keys can be enabled/disabled for each keypad on the system.The Panic alarm can be programmed for either audible or silent operation.The Panic alarm can be programmed for either instant or delayed operation. Emergency AlarmPress KeysPanic Alarm (PA)! & " Fire# & $ Medical% & &The Quick Arm Keys The ‘Quick Arm’ keys allow the system to be armed without having to enter a User code first. !"The ‘Quick Arm’ keys will only work if the keypad has been programmed to allowarming in this way.To FULL arm the system, press '.To PART arm the system, press !, ( or " followed by ).Keypad LockThe keys on the keypad can be locked to prevent unwanted access to the system. !"The Emergency keys will NOT operate with the keys locked.To Lock the keys, press * and + together.To Unlock the keys, press * and + together again.Premier Serie s User Guide Overview INS221 3LED IndicatorsFive LED indicators have been provided to indicate the status of the system. LEDStatus Meaning PowerOn AC mains is present on the control panelFlashing AC Mains is not present, the control panel is running on the standby battery ServiceOn The system requires attention, contact your installerOff The system does NOT require attention ReadyOn All zones are secure and the system is ready to be armedOff One or more zones are activeFlashing The system has zones (with the ‘Force Omit’ attribute) that are active Info.On The system is armed (can also be programmed for other indications)Off The system is unarmed (can also be programmed for other indications) OmitOn One or more zones are omitted Off No zones are omittedZone Faults During ArmingBefore attempting to arm the system, ensure that the premises are secure (all doors and windows closed etc.) and the Ready light is on.If an attempt is made to arm the system with any zones active (e.g. door ajar, open window, etc.) the internal sounders will bleep repeatedly (fault tone) and the display will show the zones that are active.The fault tone will stop and the exit tone will resume when all zones are secure. If it is necessary to leave a zone open then it must be omitted (see page 8 for details). !"If an active zone cannot be secured then it may be ‘in fault’, in this case contact the alarm company immediately. Arm Fail - Failing to Arm If the exit procedure is started and zones are still ‘Active’ at the end of the exit procedure, an Internal alarm will occur (internal sounders only) and the strobe light on the external sounder will flash. !"If this occurs the arm fail must be cleared and the zone in fault identified before the system can be armed (see page 6 for details on clearing an Arm Fail). The Ready LED To help prevent faults during arming a Ready light has been provided, see table above for details on how the Ready LED operates.Operating the Alarm System Premier Series User Guide 4 INS221 To FULL Arm the SystemThe system is FULL Armed when ALL zones are ON (not omitted). !"Your Installer may have programmed the system so that it can be set by just pressing', if this is the case then there is no need to enter the User code below.1. Ensure that the premises are secure (all doors and windows closed etc.) and the Ready light is on2. Enter a valid User code ,,,,3. Press * to armThe exit tone will sound4. Leave the premisesWhen the system has armed the exit tone will stopTo PART Arm the SystemThe system is PART Armed , when ONE OR MORE zones have been left OFF (omitted) i.e. the landing or a bedroom. !"The system is only Part Armed when zones are omitted using the ‘Part Arm’ procedure(omitting zones manually (see page 8 for details) is not classed as Part Arming).The bottom line of the display is programmable for each Part Arm.Your Installer may have programmed the system so that it can be Part Armed by just pressing !, ( or " followed by ), if this is the case then there is no need to enter the User code below.1. Ensure that the premises are secure (all windows and doors not being omitted are closed) and the Ready light is on2. Enter a valid User code ,,,,3. Press )4. Use keys ! - " to select the required Part Arm5. Press * to arm normally or press - to arm silentlyThe exit tone will sound (if silent arm has not been selected)6. Leave the protected areaWhen the system has armed, the exit tone (if sounding) will stopPremier Serie s User Guide Operating the Alarm System INS221 5 To ARM Individual AreasIf the system has been split up into separate areas of protection i.e. Area 1 = House, Area 2 = Garage, Area 3 = Shed etc. These areas can be individually selected for FULL or PART arming as required. !"Areas are selected by using keys ! - . (the / key can also be used toselect an area followed by ' or +).Only areas that exist on the system can be selected. (A ‘Star’ means the area can be selected and a ‘Dot’ means the area cannot be selected).Pressing 0 will select/deselect all areas, pressing ' will toggle between the first 8 areas and the second 8 areas (where applicable).1. Ensure that the premises are secure (all windows and doors not being omitted are closed) and the Ready light is on2. Enter a valid User code ,,,,3. Press '4. Use keys ! - . to select the required areas5. Press * or - to FULL arm the areasOr5. Press )!, ( or " followed by * or - to PART arm the areas The exit tone will sound (if silent arm has not been selected)6. Leave the premisesWhen the system has armed, the exit tone (if sounding) will stop To DISARM the SystemThe entry time is divided into two sections, the Entry time and the 2nd Entry time. If the Entry time expires, an Internal alarm will occur and the 2nd Entry time will start. If the 2nd Entry time expires, an Intruder alarm will occur (all internal and external sounders). !"It is perfectly normal for the 2nd Entry time to be programmed as zero, in whichcase, an Intruder alarm will occur as soon as the Entry time expires.1. Enter the premises via the designated entry pointThe entry tone will start2. Enter a valid User code ,,,,The entry tone will stopOperating the Alarm System Premier Series User Guide 6 INS221 To DISARM the System When Not in Entry1. Enter a valid User code ,,,,2. Press * To CANCEL the Exit ModeOnce the exit mode has been started you should leave the premises immediately, however, if for some reason you decide not to leave, the exit mode must be cancelled.1. Enter a valid User code ,,,,2. Press *The exit tone will stop. To CLEAR an Arm FailWhen the system tries to arm with zones active (open), the internal sounders will sound and the external strobe will be flashing to indicate a problem. For details on preventing an Arm Fail condition, please refer to page 3. !"If you were not present when the Arm Fail occurred or you do not clear the ArmFail, the internal sounders will continue to sound and the external strobe will continue to flash.1. Enter a valid User code ,,,,The internal and external sounders will stop, the external strobe will continue to flash and the number of the zone that caused the Arm Fail will be displayed.2. Enter a valid User code ,,,, and press 12 To SILENCE an AlarmWhen an alarm occurs on the system, the internal and external sounders will normally sound for a pre-programmed time (normally 15 minutes). !"If you were not present when the alarm activated, the internal and externalsounders may have already stopped but the external strobe will still be flashing. When alarm information is being displayed, pressing the SCROLL key will slow down the display and also allow manual scrolling through the events.1. Enter a valid User code ,,,,The internal and external sounders will stop and the number of the zone that caused the alarm will be displayed.The alarm now needs to be reset.Premier Serie s User Guide Operating the Alarm System INS221 7 To RESET After an AlarmUSER ResetOnce the alarm has been silenced (see page 6 for details), the system will need to be reset. !"If the system has been programmed, to be reset by an Engineer, pressing 1 willnot return the display to normal, if this is the case see ENGINEER Reset for details. The system may have been programmed to be reset by Anti-code, if this is the case, see ANTI-CODE Reset for details.1. Enter a valid User code ,,,,2. Press 1The external strobe will stop, the system will chime and the display will return to normal. ENGINEER ResetIf the system has been programmed to be reset by an Engineer following an alarm activation, you will still be able to silence the alarm by entering a valid User code (see page 6 for details). !"The system cannot be armed again until the alarm has been reset.1. Contact the telephone number on the display (if programmed) or the telephone number on the last page of this User GuideANTI-CODE ResetIf the system has been programmed to be reset using an Anti-Code following an alarm activation, you will still be able to silence the alarm by entering a valid User code (see page 6 for details).!"The system cannot be armed again until the alarm has been reset.1. Enter a valid User code ,,,,2. Press 1The display will show a random code number i.e. 4281.3. Contact the telephone number on the display (if programmed) or the telephone number on the last page of this User Guide and quote the random code number You will be given a 4-digit Anti-Code i.e. 5624.4. Enter the Anti-code that has been given to you ,,,,5. Press *If the Anti-code is correct, the keypad will bleep to indicate that the system has been reset and the display will return to normal.Operating the Alarm System Premier Series User Guide 8 INS221 To OMIT ZonesIt is possible to exclude (omit) individual zones when arming i.e. if a zone is ‘in fault’. Users with access to this function can only omit zones that have been programmed as ‘Omittable’. !"If the zone can be omitted, there will be a ‘Star’ to the right of the zone number.Only zones that have the ‘Omit’ attribute assigned to them can be omitted.A ‘Star’ will appear to the left of the zone number to indicate that the zone has been selected for omitting.All omitted zones will be automatically reinstated the next time the system is disarmed, unless programmed otherwise.To re-instate zones manually, simply follow the instructions again. However, when the 3 key is pressed on this occasion, the zones will be re-instated.1. Enter a valid User code ,,,, and press 32. Enter the zone number ,,,3. Press 3 to omit the selected zoneRepeat for other zones if required.4. Press 4 when finishedContinue to arm the system as normal. The Turn CHIME On and OffThe system can be set up so that activating (opening) certain zones will cause the internal sounders to chime. This would normally be used on a front door, exit button etc. !"Zones will only cause the internal sounders to chime if they are selected for chime (see page Master User Guide for details on selecting which zones chime). Once a zone has been selected for chime, the Chime facility can be manually turned on and off as required.!"The system can also be programmed to automatically turn chime on and off under certain conditions i.e. certain times of the day, door left open etc.If no zones have been programmed for Chime, then turning Chime on and off will have no effect.To turn CHIME OnTo turn CHIME Off 1. Press -1. Press - The Chime tone will sound.The Error tone will sound.Premier Serie s User Guide Operating the Alarm System INS221 9 To CHANGE Your User CodeUsers with access to this option can change their own User codes. User codes are unique to each user and can be 4, 5 or 6 digits long.!"Only the User code that is entered to access the change code menu will be changed. Before changing your code, it is vital that you memorise or write down the new code you are about to program. Failure to remember your code will require an engineer visit to re-program a new code for you. This may incur a call-out charge.1. Enter the User code that requires changing ,,,,2. Press 43. Press *4. Press (5. Press *6. Enter a new 4, 5 or 6-digit User code ,,,,7. Press * to accept the new code8. Press 1 to exit the menuThe display will return to normal.Quick Reference Guide Premier Series User Guide10 INS221 OperationDescription Action To Full Arm the SystemEnter a valid User code ,,,, Press Yes (or press Chime to arm silently) * or - To Part Arm the System Enter a valid User code ,,,, Press Part ) Select Required Part Arm !, ( or " Press Yes (or press Chime to arm silently) * or - To Arm Individual Areas Enter a valid User code ,,,, Press Area ' Select Required Area using keys 1 - 8 ! - . Press Yes (or press Chime to arm silently) * or - To Disarm the System Enter a valid User code ,,,, Press Yes (if the entry mode was not started) *To Cancel the Exit Mode Enter a valid User code ,,,, Press Yes * To Clear an Arm Fail Enter a valid User code ,,,, Press Reset 1 To Silence an Alarm Enter a valid User code ,,,, To Reset After an Alarm Enter a valid User code ,,,, Press Reset 1 To Engineer Reset Contact Your Installation Company_____________ To Anti-code Reset Enter a valid User code ,,,, Press Reset 1 Contact Your Alarm Receiving Centre_____________ Quote 4-digit code shown on display !"#$%&'((((' Enter 4-digit code given by Receiving Centre ,,,, Press Yes *To Omit Zones Enter a valid User code ,,,, Press Omit 3 Enter Zone Number(s) ,,,… Press Menu when finished 3 Press Yes to Arm * Turn Chime On/Off Press Chime Once to Turn ON - Press Chime Again to Turn OFF - To Change User Code Enter a valid User code ,,,, Press Menu followed by Yes 4* Press 2 followed by Yes (* Enter a new 4, 5 or 6 digit User code ,,,, Press Yes to accept * Press Reset to return to the normal display 1Premier Series User Guide Installation DetailsINS221 11AreasNo. DescriptionExit TimeEntry Time 1Entry Time 2Bell DelayBell DurationAbort TimeSec. Sec. Sec. Min. Min. Sec. Sec. Sec. Sec. Min. Min. Sec. Sec. Sec. Sec. Min. Min. Sec.Sec.Sec.Sec.Min.Min.Sec.KeypadsEmergency Keys No. LocationArea Quick Arm PA Fire MedUser CodesUser Name Type Default New Code Area Time Lock 01 Master 5678N/AN/AN/AN/AN/AZonesPart ArmsNo. DescriptionType Area Omit 12 3Installation Company DetailsInstallation Engineer:Installation Company:Address:Telephone Number:Installation Date:Service RecordDate Serviced Comments EngineerEmergency Telephone NumbersFor 24 Hour Call Out For Anti-Code ResetControl PanelDetailsModel Premier 24 ❏Premier 48 ❏Premier 88 ❏Premier 168 ❏ Premier 640 ❏Location© TEXECOM LTD. 2000 - 2005INS221-2。
软件使用手册范文(3篇)

第1篇第一章:概述1.1 软件简介XX办公自动化系统是一款集成了文档管理、邮件处理、日程安排、会议管理、项目管理等功能于一体的综合性办公软件。
它旨在提高工作效率,简化办公流程,为用户提供便捷、高效的办公体验。
1.2 系统功能1. 文档管理:支持文档的上传、下载、编辑、分享等功能。
2. 邮件处理:提供邮件收发、邮件分类、邮件搜索等功能。
3. 日程安排:支持日程的添加、修改、删除、提醒等功能。
4. 会议管理:支持会议的创建、修改、删除、参会人员管理等功能。
5. 项目管理:支持项目的创建、分配、进度跟踪、任务管理等功能。
1.3 系统环境1. 操作系统:Windows 7/8/10、Mac OS X 10.10及以上版本2. 处理器:Intel Core i3及以上3. 内存:4GB及以上4. 硬盘:100GB及以上5. 网络环境:宽带网络第二章:安装与启动2.1 安装步骤1. 下载软件安装包:请访问官方网站或授权渠道下载最新版本的XX办公自动化系统安装包。
2. 双击安装包,进入安装向导。
3. 阅读许可协议,勾选“我同意”后点击“下一步”。
4. 选择安装路径,点击“下一步”。
5. 等待安装完成,点击“完成”。
2.2 启动软件1. 在桌面找到XX办公自动化系统的快捷方式,双击打开。
2. 输入用户名和密码,点击“登录”。
第三章:功能模块使用指南3.1 文档管理1. 上传文档:点击“文档”菜单,选择“上传文档”,选择需要上传的文件,点击“上传”。
2. 下载文档:点击文档列表中的文件名,点击“下载”。
3. 编辑文档:双击文档列表中的文件名,打开文档进行编辑。
4. 分享文档:选中文档,点击“分享”,输入分享对象和权限,点击“分享”。
3.2 邮件处理1. 收发邮件:点击“邮件”菜单,进入邮件收发界面。
2. 邮件分类:点击“邮件”菜单,选择“邮件分类”,创建或编辑分类。
3. 邮件搜索:在邮件收发界面,输入搜索关键词,点击“搜索”。
CSSCNeoShineOffice3.0UserGuide-Chinese

3.3 文件操作及格式 ......................................................................................................... 38 3.3.1 新建文件..................................................................................................................... 38 3.3.2 打开文件..................................................................................................................... 40 3.3.3 保存文件..................................................................................................................... 42 3.3.4 发送文件..................................................................................................................... 45 3.3.5 关闭文件..................................................................................................................... 46 3.3.6 查看文件的属性 ......................................................................................................... 46 3.3.7 文件兼容性 ................................................................................................................. 47
软件用户操作手册编写模板

软件用户操作手册1.引言1.1编写目的【阐明编写手册的目的,指明读者对象。
】1.2项目背景【说明项目来源、委托单位、开发单位及主管部门。
】1.3定义【列出手册中使用的专门术语的定义和缩写词的原意。
】1.4参考资料【列出有关资料的作者、标题、编号、发表日期、出版单位或资料来源,可包括:a.项目的计划任务书、合同或批文.b.项目开发计划.c.需求规格说明书;d.概要设计说明书;e.详细设计说明书;f.测试计划;g.手册中引用的其他资料、采用的软件工程标准或软件工程规范。
】2.软件概述2.1目标2.2功能2.3性能a.数据精确度【包括输入、输出及处理数据的精度。
】b.时间特性【如响应时间、处理时间、数据传输时间等。
】c.灵活性【在操作方式、运行环境需做某些变更时软件的适应能力。
】3.运行环境3.1硬件【列出软件系统运行时所需的硬件最小配置,如a.计算机型号、主存容量.b.外存储器、媒体、记录格式、设备型号及数量.c.输入、输出设备;d.数据传输设备及数据转换设备的型号及数量。
】3.2支持软件【如:a.操作系统名称及版本号.b.语言编译系统或汇编系统的名称及版本号;c.数据库管理系统的名称及版本号;d.其他必要的支持软件。
】4.使用说明4.1安装和初始化【给出程序的存储形式、操作命令、反馈信息及其含意、表明安装完成的测试实例以及安装所需的软件工具等。
】4.2输入【给出输入数据或参数的要求。
】4.2.1数据背景【说明数据来源、存储媒体、出现频度、限制和质量管理等。
】4.2.2数据格式【如.a.长度.b.格式基准;c.标号;d.顺序;e.分隔符;f.词汇表;g.省略和重复;h.控制。
】4.2.3输入举例4.3输出【给出每项输出数据的说明。
】4.3.1数据背景【说明输出数据的去向、使用频度、存放媒体及质量管理等。
】4.3.2数据格式【详细阐明每一输出数据的格式,如:首部、主体和尾部的具体形式。
】4.3.3举例4.4出错和恢复【给出:a.出错信息及其含意.b.用户应采取的措施,如修改、恢复、再启动。
用户手册(英文)模板 (user manual template)

U SER’SM ANUALProject or System NameU.S. Department of Housing and Urban Development Month, YearRevision Sheet Revision SheetI have carefully assessed the User’s Manual for the (System Name). This document has been completed in accordance with the requirements of the HUD System Development Methodology. MANAGEMENT CERTIFICATION - Please check the appropriate statement.______ The document is accepted.______ The document is accepted pending the changes noted.______ The document is not accepted.We fully accept the changes as needed improvements and authorize initiation of work to proceed. Based on our authority and judgment, the continued operation of this system is authorized._______________________________ _____________________ NAME DATEProject Leader_______________________________ _____________________ NAME DATEOperations Division Director_______________________________ _____________________ NAME DATEProgram Area/Sponsor Representative_______________________________ _____________________ NAME DATEProgram Area/Sponsor DirectorUSER'S MANUALTABLE OF CONTENTSPage #1.0 GENERAL INFORMATION .......................................................................................................... 1-11.1 System Overview ................................................................................................................... 1-11.2 Project References .................................................................................................................. 1-21.3 Authorized Use Permission .................................................................................................... 1-21.4 Points of Contact .................................................................................................................... 1-21.4.1 Information .............................................................................................................................1-21.4.2 Coordination ...........................................................................................................................1-21.4.3 Help Desk ...............................................................................................................................1-21.5 Organization of the Manual ................................................................................................... 1-21.6 Acronyms and Abbreviations ................................................................................................. 1-22.0 SYSTEM SUMMARY .................................................................................................................... 2-12.1 System Configuration ............................................................................................................. 2-12.2 Data Flows.............................................................................................................................. 2-12.3 User Access Levels ................................................................................................................ 2-12.4 Contingencies and Alternate Modes of Operation ................................................................. 2-13.0 GETTING STARTED ..................................................................................................................... 3-13.1 Logging On ............................................................................................................................. 3-13.2 System Menu .......................................................................................................................... 3-13.2.x [System Function Name] .........................................................................................................3-13.3 Changing User ID and Password ............................................................................................ 3-13.4 Exit System ............................................................................................................................ 3-14.0 USING THE SYSTEM (ONLINE) .................................................................................................. 4-14.x [System Function Name] ........................................................................................................ 4-14.x.y [System Sub-Function Name] .................................................................................................4-14.2 Special Instructions for Error Correction ............................................................................... 4-14.3 Caveats and Exceptions .......................................................................................................... 4-15.0 USING THE SYSTEM (BATCH) ................................................................................................... 5-15.x [System Function Name] ........................................................................................................ 5-15.x.y [System Sub-Function Name] .................................................................................................5-15.2 Special Instructions for Error Correction ............................................................................... 5-15.3 Caveats and Exceptions .......................................................................................................... 5-15.4 Input Procedures and Expected Output .................................................................................. 5-16.0 QUERYING ..................................................................................................................................... 6-16.1 Query Capabilities .................................................................................................................. 6-16.2 Query Procedures ................................................................................................................... 6-17.0 REPORTING ................................................................................................................................... 7-17.1 Report Capabilities ................................................................................................................. 7-17.2 Report Procedures .................................................................................................................. 7-11.0 GENERAL INFORMATIONNOTE TO AUTHOR:highlighted, italicized text throughout this template is provided solely as background information to assist you in creating this document. Please delete all such text, as well as the instructions in each section, prior to submitting this document. ONLY YOUR PROJECT-SPECIFIC INFORMATION SHOULD APPEAR IN THE FINAL VERSION OF THIS DOCUMENT.The User’s Manual provides the information necessary for the user to effectively use the automated information system.1.0 GENERAL INFORMATION1.1 System OverviewExplain in general terms the system and the purpose for which it is intended. The description shall include:•Major functions performed by the system•Describe the architecture of the system in non-technical terms, (e.g., client/server, Web-based, etc.)•User access mode, (e.g., graphical user interface)•Responsible organization•System name or title•System code•System category:-Major application:performs clearly defined functions for which there is a readily identifiable security consideration and need-General support system:provides general ADP or network support for a variety of users and applications•Operational status:-Operational-Under development-Undergoing a major modification•General description•System environment or special conditions1.2 Project ReferencesProvide a list of the references that were used in preparation of this document in order of importance to the end user.1.3 Authorized Use PermissionProvide a warning regarding unauthorized usage of the system and making unauthorized copies of data, software, reports, and documents, if applicable. If waiver use or copy permissions need to be obtained, describe the process.1.4 Points of Contact1.4.1 InformationProvide a list of the points of organizational contact (POCs) that may be needed by the document user for informational and troubleshooting purposes. Include type of contact, contact name, department, telephone number, and e-mail address (if applicable). Points of contact may include, but are not limited to, help desk POC, development/maintenance POC, and operations POC.1.4.2 CoordinationProvide a list of organizations that require coordination between the project and its specific support function (e.g., installation coordination, security, etc.). Include a schedule for coordination activities. 1.4.3 Help DeskProvide help desk information including responsible personnel phone numbers for emergency assistance.1.5 Organization of the ManualProvide a list of the major sections of the User’s Manual (1.0, 2.0, 3.0, etc.) and a brief description of what is contained in each section.1.6 Acronyms and AbbreviationsProvide a list of the acronyms and abbreviations used in this document and the meaning of each.2.0 SYSTEM SUMMARY2.0 SYSTEM SUMMARYThis section provides a general overview of the system written in non-technical terminology. The summary should outline the uses of the system in supporting the activities of the user and staff.2.1 System ConfigurationBriefly describe and depict graphically the equipment, communications, and networks used by the system. Include the type of computer input and output devices.2.2 Data FlowsBriefly describe or depict graphically, the overall flow of data in the system. Include a user-oriented description of the method used to store and maintain data.2.3 User Access LevelsDescribe the different users and/or user groups and the restrictions placed on system accessibility or use for each.2.4 Contingencies and Alternate Modes of OperationOn a high level, explain the continuity of operations in the event of emergency, disaster, or accident. Explain what the effect of degraded performance will have on the user.3.0 GETTING STARTED3.0 GETTING STARTEDThis section provides a general walkthrough of the system from initiation through exit. The logical arrangement of the information shall enable the functional personnel to understand the sequence and flow of the system. Use screen prints to depict examples of text under each heading.3.1 Logging OnDescribe the procedures necessary to access the system, including how to get a user ID and log on. If applicable, identify job request forms or control statements and the input, frequency, reason, origin, and medium for each type of output.3.2 System MenuThis section describes in general terms the system menu first encountered by the user, as well as the navigation paths to functions noted on the screen. Each system function should be under a separate section header, 3.2.1 - 3.2.x.3.2.x [System Function Name]Provide a system function name and identifier here for reference in the remainder of the subsection. Describe the function and pathway of the menu item. Provide an average response time to use the function.3.3 Changing User ID and PasswordDescribe how the user changes a user ID. Describe the actions a user must take to change a password.3.4 Exit SystemDescribe the actions necessary to properly exit the system.4.0 USING THE SYSTEM (ONLINE)This section provides a detailed description of the online system from initiation through exit, explaining in detail the characteristics of the required input and system-produced output. THIS SECTION IS ONLY TO BE USED FOR ONLINE SYSTEMS. IF YOU ARE DEVELOPING A BATCH SYSTEM, USE SECTION 5.0 AND OMIT THIS SECTION ENTIRELY.4.0 USING THE SYSTEM (ONLINE)This section provides a detailed description of system functions. Each function should be under a separate section header, 4.1 - 4.x, and should correspond sequentially to the system functions (menu items) listed in subsections 3.2.1 - 3.2.x.4.x [System Function Name]Provide a system function name and identifier here for reference in the remainder of the subsection. Describe the function in detail and depict graphically. Include screen captures and descriptive narrative.4.x.y [System Sub-Function Name]This subsection provides a detailed description of system sub-functions. Each sub-function should be under a separate section header, 4.1.1. - 4.x.y . Where applicable, for each sub-function referenced within a section in 4.x, describe in detail and depict graphically the sub-function name(s) referenced. Include screen captures and descriptive narrative.The numbering of the following two sections will depend on how many system functions there are from 4.1 through 4.x. They are numbered here as 4.2 and 4.3 only for the sake of convenience. For example, if system functions run from sections 4.1 through 4.17, then the following two sections would be numbered 4.18 and 4.19.4.2 Special Instructions for Error CorrectionDescribe all recovery and error correction procedures, including error conditions that may be generated and corrective actions that may need to be taken.4.3 Caveats and ExceptionsIf there are special actions the user must take to insure that data is properly saved or that some other function executes properly, describe those actions here. Include screen captures and descriptive narratives, if applicable.5.0 USING THE SYSTEM (BATCH)This section provides a detailed description of the batch system from initiation through exit, explaining in detail the characteristics of the required input and system-produced output. THIS SECTION IS ONLY TO BE USED FOR BATCH SYSTEMS. IF YOU ARE DEVELOPING AN ONLINE SYSTEM, USE SECTION 4.0 AND OMIT THIS SECTION ENTIRELY.5.0 USING THE SYSTEM (BATCH)This section provides a detailed description of system functions. Each function should be under a separate section header, 5.1 - 5.x, and should correspond sequentially to the system functions (menu items) listed in subsections 3.2.1 - 3.2.x.5.x [System Function Name]Provide a system function name and identifier here for reference in the remainder of the subsection. Describe the function in detail and depict graphically. Include screen captures and descriptive narrative.5.x.y [System Sub-Function Name]This subsection provides a detailed description of system sub-functions. Each sub-function should be under a separate section header, 5.1.1 - 5.x.y. Where applicable, for each sub-function referenced within a section in 5.x, describe in detail and depict graphically the sub-function name(s) referenced. Include screen captures and descriptive narrative.The numbering of the following three sections will depend on how many system functions there are from 5.1 through 5.x. They are numbered here as 5.2, 5.3, and 5.4 only for the sake of convenience. For example, if system functions run from sections 5.1 through 5.17, then the following three sections would be numbered 5.18, 5.19 and 5.20.5.2 Special Instructions for Error CorrectionDescribe all recovery and error correction procedures, including error conditions that may be generated and corrective actions that may need to be taken.5.3 Caveats and ExceptionsIf there are special actions the user must take to insure that data is properly saved or that some other function executes properly, describe those actions here. Include screen captures and descriptive narratives, if applicable.5.4 Input Procedures and Expected OutputPrepare a detailed series of instructions (in non technical terms) describing the procedures the user will need to follow to use the system. The following information should be included in these instructions: •Detailed procedures to initiate system operation, including identification of job request forms or control statements and the input’s frequency, reason, origin, and medium for each type of output•Illustrations of input formats•Descriptions of input preparation rules•Descriptions of output procedures identifying output formats and specifying the output’s purpose, frequency, options, media, and location•Identification of all codes and abbreviations used in the system’s output6.0 QUERYING6.0 QUERYINGThis section describes the query and retrieval capabilities of the system. The instructions necessary for recognition, preparation, and processing of a query applicable to a database shall be explained in detail. Use screen prints to depict examples of text under each heading.6.1 Query CapabilitiesDescribe or illustrate the pre-programmed and ad hoc query capabilities provided by the system. Include query name or code the user would invoke to execute the query. Include query parameters if applicable.6.2 Query ProceduresDevelop detailed descriptions of the procedures necessary for file query including the parameters of the query and the sequenced control instructions to extract query requests from the database.7.0 REPORTING7.0 Reporting 7.0 REPORTINGThis section describes and depicts all standard reports that can be generated by the system or internal to the user. Use screen prints as needed to depict examples of text under each heading.7.1 Report CapabilitiesDescribe all reports available to the end user. Include report format and the meaning of each field shown on the report. If user is creating ad hoc reports with special formats, please describe here. A separate subsection may be used for each report.7.2 Report ProceduresProvide instructions for executing and printing the different reports available. Include descriptions of output procedures identifying output formats and specifying the output’s purpose, frequency, options, media, and location.User’s Manual Page 7-1。
H3C WX5510E无线控制器 安装指导-AW100-整本手册

环境保护
本产品符合关于环境保护方面的设计要求,产品的存放、使用和弃置应遵照相关国家法律、法规要 求进行。
前言
H3C WX5510E 无线控制器安装指导介绍了 WX5510E 安装前的准备、安装、初次上电启动、故障 处理、接口模块选配参考和软件维护等内容。 前言部分包含如下内容: • 读者对象 • 本书约定 • 资料获取方式 • 技术支持 • 资料意见反馈
• 在断开光纤连接器之前,在命令行接口视图下使用 shutdown 命令以确保关闭光源。 • 断开光纤后使用光纤帽保护光纤连接器,避免因灰尘过多而产生静电,导致激光器损坏或影响
其性能指标。
1.2 安装场所要求
设备必须在室内使用,为保证设备正常工作并延长使用寿命,安装场所应该满足下列要求。
1.2.1 温度/湿度要求
称,由各自权利人拥有。
由于产品版本升级或其他原因,本手册内容有可能变更。H3C 保留在没有任何通知或者提示的情况 下对本手册的内容进行修改的权利。本手册仅作为使用指导,H3C 尽全力在本手册中提供准确的信 息,但是 H3C 并不确保手册内容完全没有错误,本手册中的所有陈述、信息和建议也不构成任何
明示或暗示的担保。
H3C WX5510E 无线控制器 安装指导
杭州华三通信技术有限公司 资料版本:AW100-20140102
Copyright © 2014 杭州华三通信技术有限公司及其许可者 版权所有,保留一切权利。 未经本公司书面许可,任何单位和个人不得擅自摘抄、复制本书内容的部分或全部,并不得以任何 形式传播。
表1-2 粒/m3
单位
含量 ≤3×104(3天内桌面无可见灰尘)
注:灰尘粒子直径≥5μm
1-2
除灰尘外,设备机房对空气中所含的盐、酸、硫化物也有严格的要求。这些有害气体会加速金属的 腐蚀和某些部件的老化过程。机房内应防止有害气体如 SO2、H2S、NH3、Cl2 等的侵入,其具体限 制值参见下表。
软件使用手册模板

软件使用手册模板一、前言。
本手册旨在为用户提供关于软件的详细使用说明,帮助用户快速上手并熟练使用软件。
在阅读本手册之前,请确保您已经安装了最新版本的软件,并且已经准备好开始使用。
二、软件概述。
软件是一款功能强大的工具,它能够帮助用户实现各种操作,包括但不限于数据管理、图形处理、文档编辑等。
通过本手册,您将了解到软件的各项功能和操作方法,从而更好地利用软件进行工作和学习。
三、安装与启动。
1. 安装软件。
在安装软件之前,请确保您的设备符合最低系统要求,并且已经下载了软件的安装包。
双击安装包,按照提示完成安装步骤,即可成功安装软件。
2. 启动软件。
安装完成后,双击软件图标即可启动软件。
在首次启动时,您可能需要进行一些初始化设置,根据提示完成设置即可进入软件主界面。
四、界面介绍。
软件的主界面由若干功能区域组成,包括菜单栏、工具栏、状态栏等。
在软件的主界面上,您可以快速找到各项功能按钮和操作区域,方便您进行各种操作。
五、功能操作。
1. 数据管理。
软件提供了数据管理功能,您可以通过该功能进行数据的导入、导出、整理和分析。
在数据管理界面,您可以进行数据的查看、编辑和删除操作。
2. 图形处理。
软件支持各种图形处理功能,包括但不限于图片编辑、绘图、图表制作等。
您可以通过图形处理功能,实现对图形的各种操作和处理。
3. 文档编辑。
软件提供了文档编辑功能,您可以通过该功能进行文档的创建、编辑、格式设置等操作。
在文档编辑界面,您可以使用各种工具和功能,编辑出符合您需求的文档。
六、常见问题解答。
1. 如何导入数据?在数据管理界面,点击“导入数据”按钮,选择需要导入的数据文件,按照提示完成导入操作即可。
2. 如何进行图片编辑?在图形处理界面,选择需要编辑的图片,点击“编辑”按钮,即可进入图片编辑界面进行编辑操作。
3. 如何创建新文档?在文档编辑界面,点击“新建文档”按钮,选择文档类型和格式,即可创建新文档并进行编辑。
七、结束语。
用户操作手册说明书

目 录使用说明User Guide简 介 15开始步骤电池的安装 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -17按键功能------------------------------------------------------------18基本菜单操作 --------------------------------------------------------18开机与关机 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -20第一次开机 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -20基本录音与回放基本录音------------------------------------------------------------22停止录音------------------------------------------------------------23录音回放------------------------------------------------------------24使用“录音场景”录音场景的选择 ------------------------------------------------------25内置和外置麦克风内置麦克风 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -26专用外置麦克风 ------------------------------------------------------26第三方麦克风 --------------------------------------------------------27麦克风线缆的固定-----------------------------------------------------27麦克风供电 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -28麦克风毛衣的使用-----------------------------------------------------28耳机的连接和监听耳机的连接 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -29耳机线的固定 --------------------------------------------------------30耳机音量的调整 ------------------------------------------------------30使用耳机进行录音监听 -------------------------------------------------31录音详解录音界面元素介绍-----------------------------------------------------32录音中可进行的操作 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -40录音设置菜单 --------------------------------------------------------43播放详解播放界面------------------------------------------------------------52播放中可进行的操作 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -59文件管理进入和退出 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -62操作方法------------------------------------------------------------63对文件夹的操作 ------------------------------------------------------64对文件的操作 --------------------------------------------------------64播放列表------------------------------------------------------------65对播放列表的操作-----------------------------------------------------66对播放列表文件的操作 -------------------------------------------------66电池与外置供电电池的安装 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -67电池电量指示 --------------------------------------------------------68干电池与充电电池-----------------------------------------------------68电池的其他注意事项 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -69外置供电------------------------------------------------------------69系统设置录音提示灯 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -71播放提示灯 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -71 Peak提示灯 ---------------------------------------------------------71屏幕休眠------------------------------------------------------------72扬声器 -------------------------------------------------------------72自动关机------------------------------------------------------------72电池类型------------------------------------------------------------73语言 ---------------------------------------------------------------73 Fn键自定义 ---------------------------------------------------------73时间设置------------------------------------------------------------74储存信息------------------------------------------------------------75格式化 -------------------------------------------------------------75系统信息------------------------------------------------------------75恢复出厂设置 --------------------------------------------------------76更新数据库 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -76 APP解绑 -----------------------------------------------------------76 USB扩展USB-DAC -----------------------------------------------------------79 USB声卡 -----------------------------------------------------------79手机APP的使用APP的下载与安装 ----------------------------------------------------81与PAW-1进行绑定----------------------------------------------------81系统升级升级流程------------------------------------------------------------84PAW-1标准包装内包括如下部件:购买产品时请认真核实。
P V Tool Pro 用户手册说明书

P/V Tool® ProUser GuideAssessing lung recruitability and performing recruitment maneuvers in adult patientsThis User Guide describes how to assess recruitability and perform recruitment maneuvers in adult patients.While the information contained herein is believed to be accurate, it does not represent an official recommen-dation from Hamilton Medical, nor may it substitute an opinion, assessment, or instructions provided by a trained healthcare professional.This User Guide does not replace the clinical judgment of a physician, nor the content of the ventilator Operator’s Manual, which should always be available when using the ventilator.P/V Tool Pro is available as an option on the HAMILTON-C3/C6/G5 ventilators; it is a standard feature on the HAMILTON-S1 ventilator.References are provided at the back of this guide, on page 23.P/V Tool Pro2021-12-07Table of contents1. Overview (4)2. Conditions for use (6)3. Recruitment protocols: BASIC and ADVANCED (9)4. Step 1. Assess lung recruitability (10)5. Step 2a. Performing a recruitment maneuver (13)6. Step 2b. Performing a second recruitment maneuver (17)7. Performing decremental PEEP titration (20)8. Performing a third recruitment maneuver (21)9. Esophageal pressure measurement (22)10. Reference (23)1.1 Recruitment strategy and P/V Tool ProIn ARDS patients, a recruitment strategy combines recruitment maneuvers and positive end-expiratory pressure (PEEP) to prevent atelectrauma. Recruitment maneuver stands for a process of intentional transient increase of transpulmonary pressure (Ptranspulm) above values used during regular mechanical ventilation, where the main objective is to open unstable distal airways and/or airless alveoli. The maneu-ver is also often called an alveolar recruitment maneuver, as the opening of collapsed alveolar units is believed to represent the major effect of a recruitment maneuver.¹ PEEP may decrease ventilator-induced lung injury by keeping those lung regions open that may otherwise collapse.2The percentage of potentially recruitable lung varies widely among ARDS patients. Zones of collapsed and consolidated alveoli in the most dependent lung frequently require airway-opening pressures of more than 35 – 40 cmH2O to recruit.2Knowledge of the percentage of potentially recruitable lung is important for establishing the therapeutic efficacy of PEEP. Setting PEEP levels too low may reduce the possible benefits of PEEP, while use of high PEEP levels in patients with a low percentage of potentially recruitable lung provides little benefit and may actually be harmful.3P/V Tool ProP/V Tool Pro provides a bedside method for assessing lung recruitability and carrying out recruitment maneuvers.4, 5, 6Flow of less than or equal to 10 l/min has beenshown to be quick, safe, and reliable for determiningthe lung mechanics by means of a pressure-volume(P/V) loop at the bedside.7We suggest using the minimum ramp speed of2 cmH2O/s to eliminate the pressure change fromresistive elements of the respiratory system.To access this graph in P/V Tool ProX Touch the P/V Tool graphics panel and select the Paw/Flow option. 1.2 Quasi-static low-flow pressure/volume curvePaw cmH2O Flow l/min2.1 Important notes about recruitment and P/V Tool Pro• Most patients require deep sedation, with some patients requiring an additional neuromuscular blockade to prevent spontaneous breathing efforts.• Monitoring the patient‘s hemodynamics during maneuvers (diagnostic and recruitment) is crucial.In the event of any hemodynamic impairment, STOP the maneuver immediately.• Ensure the ETT cuff is inflated to a pressure higher than the maximum pressure specified in the P/V Tool settings.*• The patient must receive at least five (5) breaths between P/V Tool recruitment maneuvers.• Before use, carefully review the indications and contraindications for performing a recruitment maneuver, described next on pages 7 and 8.• P/V Tool Pro is disabled in several ventilation modes. Refer to your ventilator Operator’s Manual for details.* If using IntelliCuff, cuff pressure is monitored and maintained automatically.2.2 Indications for performing a recruitment maneuverIndications for use• Early in the management of moderate to severe ARDS.• As part of an open-lung approach.• In the case of impairment with oxygenation after an intervention such as surgery, resuscitation, or similar.Conditions for use• The patient is intubated and passive, that is, not breathing spontaneously.• The breathing circuit is gas tight. There must be no gas leak throughout the entire system of the ventilator, the breathing circuit, or at the ventilated patient.• Nebulization is deactivated. P/V Tool Pro is disabled during nebulization and for five (5) breaths following nebulization.• The flow sensor must perform optimally. The accuracy of the information provided depends on the quality of the flow sensor connection. P/V Tool Pro is disabled when the Flow sensor calibration needed alarm is active.2.3 Contraindications for performing a recruitment maneuverUse of the P/V Tool is contraindicated if any of the following conditions apply:• Air leaks• Pregnancy• Lung emphysema• Hemodynamic instability• Confirmed or suspected intracranial hypertension• Patients who cannot tolerate high intrapulmonary pressure (for example, right heart failure)3. Recruitment protocols: BASIC and ADVANCED The BASIC protocol comprises two steps that must be performed in the order shown.Do not skip a step!Step 1.Assess lung recruitabilityStep 2a.First lung recruitment maneuverIn the event that the BASIC protocol does not result in effective recruitment, proceed to the ADVANCED protocol.Step 2b.Second lung recruitment maneuverB A S IC P R O T O C O 4.2 Assess potential for recruitmentTo assess the patient‘s potential for lung recruitment, calculate the normalized maximum distance (NMD) using the low-flow P/V waveform (see page 10, example on page 12).8High potential for recruitmentNMD% ≥ 41%Low potential for recruitmentNMD% < 41%Consider:• Keeping PEEP < 10 cmH2O • Prone positioning• Persistent hypoxemia Consider ECMOSee page 12 for examples.Paw cmH2OV mlMax. vol. = 1500Max. dV = 330Max. dV / Max. volume = 600/1350NMD% = 44%V mlMax. vol. = 1350Max. dV = 600Paw cmH2O dV mldV ml5. Step 2a. Performing a recruitment maneuver5.1 Before you start• Before performing a recruitment maneuver, consider decreasing the Oxygen setting to reach an SpO2 value of 92%.16When the SpO2 saturation is above 92%, it can be difficult to evaluate the improvement inoxygenation after the recruitment maneuver.• If NMD%≥ 41% (pages 11 and 12), a recruitment maneuver is warranted.8Effective recruitmentWhen both of the following criteria are met, recruitment was effective:• Volume increase at Ptop was greater than 2.0 ml/kg IBW 6 (page 16)• SpO2 was above 97% within 5 minutes 17Ineffective recruitmentIf either of the above criteria was not met, proceed to the advanced protocol (page 17).NOTE. Effective recruitment increases respiratory system compliance, and results in eitheran increase in tidal volume or a reduction in driving pressure.5.3 Assess the effectiveness of the maneuverThe following criteria help you assess whether the recruitment maneuver was effective.* To view the volume difference, touch the P/V Tool graphics panel and select the Paw cmH2OV mldV mlA D V A N C E D P R O T O C O LONLY use the ADVANCED protocol if the first recruitment maneuver (using the BASIC protocol) was well tolerated hemodynamically.• Try to limit the patient‘s respiratory system driving pressure * to a maximum of 15 cmH2O after the recruitment maneuver.• If the patient shows indications of increased chest wall elastance, for example, morbid obesity or intra-abdominal hypertension, consider esophageal pressure measurement to guide your recruit-ment strategy (page 22).• Before performing the recruitment maneuver, consider decreasing the Oxygen setting to reach an SpO2 value of 92%.16When the SpO2 saturation is above 92%, it can be difficult to evaluate the improvement in oxy-genation after the recruitment maneuver.6. Step 2b. Performing a second recruitment maneuver6.1Before you start* Driving Pressure = Pplat – PEEPtotal6.3 Assess the effectiveness of the maneuverThe following criteria help you assess whether the recruitment maneuver was effective.Effective recruitmentWhen both of the following criteria are met, recruitment was effective.• Volume increase at Ptop was greater than 2.0 ml/kg IBW 6 (page 16)• SpO2 was above 97% within 5 minutes 17If the second recruitment maneuver was effective, perform decremental PEEP titration(page 20) to determine optimal PEEP for use in a third and final recruitment maneuver(page 21).Ineffective recruitmentIf either of the above criteria was not met, the recruitment maneuver was not effective.Consider using esophageal manometry in your recruitment strategy (page 22).21Hamilton Medical | P/V Tool Pro User Guide A D V A N C E D P R O T O C8. Performing a third recruitment maneuver8.1 Specify settings for a recruitment maneuverPstart: Optimal PEEPPtop: 50 cmH2OEnd PEEP: Optimal PEEP Ramp speed: 5 cmH2O/sTpause:10 s 13To start the maneuverX Touch Start/Stop maneuver .In the P/V Tool Settings window, specify the following settings to perform a third recruitmentmaneuver:10. Reference1 Oxford Textbook of Critical Care2 Borges, João, et al. Am J Respir Crit Care Med 174.3 (2006):268-278.3 Gattinoni, Luciano, et al. New England Journal of Medicine 354.17(2006): 1775-1786.4 Maggiore, Salvatore, et al. Am J Respir Crit Care Med 164.5(2001): 795-801. Web.5 Grasso, Salvatore, et al. Am J Respir Crit Care Med 171.9(2005): 1002-1008.6 Demory, Didier, et al. Intensive Care Med 34.11 (2008):2019-2025.7 Daniela Pasero M.D., Giorgio A. Iotti M.D., and Mirko Belliato M.D. White Paper: Respiratory system pressure-volume curve: Validation of a new, automatic, pressure ramp method of acquirement; 2004.8 Chiumello, D., et al. Critical Care Medicine, 48(10) (2020): 1494–1502.9 Borges, Joao B., et al. American journal of respiratory and critical care medicine 174.3 (2006): 268-278.10 Gattinoni, L. Current opinion in critical care 21.1 (2015): 50-57.11 Kacmarek, R., et al. Critical care medicine 44.1 (2016): 32-42.12 Kacmarek, Robert M., et al. Critical care medicine 44.1 (2016): 32-42.13 Arnal, Jean-Michel, et al. Intensive care medicine 37.10 (2011): 1588.14 Chiumello, D., et al., Intensive care medicine 39.8 (2013): 1377-1385.15 Kassis, E., Intensive care medicine 43.8 (2017): 1162-1163.16 Jones J. G., Jones S. E. J Clin Monit Comput 2000; 16:337–50.17 Tusman, G., et al (2014). Analgesia, 118(1), 137–144.23 Hamilton Medical | P/V Tool Pro User GuideManufacturer:Hamilton Medical AGVia Crusch 8, 7402 Bonaduz, Switzerland+41 (0)58 610 10 20*************************Specifications are subject to change without notice. Some features are options. Not all features are available in allmarkets. For all proprietary trademarks and third-party trademarks used by Hamilton Medical AG, see /trademarks. © 2021 Hamilton Medical AG. All rights reserved.10067117/01。
prti1516_users_guide用户手册

Pitch pRTI™User’s GuidepRTI™ 1516 USER’S GUIDEContents1INTRODUCTION 41.1ABOUT THIS DOCUMENT 4 1.2ABOUT PITCH TECHNOLOGIES 5 1.3ABOUT IEEE 1516 HLA 5 1.4ABOUT THE RUN TIME INFRASTRUCTURE 6 1.5ABOUT PRTI™ 1516 6 1.6PRODUCT LICENSING STRUCTURE 72PREPARING FOR PRTI™ 1516 82.1 A TOPOLOGY AND COMPONENTS EXAMPLE 8 2.2THE CENTRAL RTI COMPONENT (CRC) 9 2.3THE FEDERATES 9 2.4THE LOCAL RTI COMPONENT (LRC) 9 2.5THE FOM FILE 9 2.6THE COMPUTERS 10 2.7NETWORKING 103INSTALLING PRTI™ 1516 123.1WINDOWS INSTALLATION 12 3.2VERIFYING THE WINDOWS INSTALLATION 16 3.3LINUX INSTALLATION 18 3.4VERIFYING THE LINUX INSTALLATION 18 3.5INSTALLING ON SOLARIS 20 3.6VERIFYING THE SOLARIS INSTALLATION 20 3.7INSTALLING ON OTHER PLATFORMS 21 3.8INSTALLING PRTI™ 1516 FOR EXTREME PERFORMANCE 224UNINSTALLING PRTI™ 1516 234.1UNINSTALLING ON WINDOWS 23 4.2UNINSTALLING ON LINUX 23 4.3UNINSTALLING ON SOLARIS 23 4.4UNINSTALLING ON OTHER PLATFORMS 235RUNNING PRTI™ 1516 245.1USING THE GRAPHICAL USER INTERFACE 24 5.2USING THE COMMAND LINE INTERFACE 346RUNNING PRTI™ 1516 IN SERVICE-MODE 366.1INTRODUCTION 36 6.2LIMITATIONS 36 6.3INSTALLING THE SERVICE 36 6.4UNINSTALLING THE SERVICE 38 6.5SERVICE MANAGEMENT 387USING THE PRTI™ 1516 WEB GUI 417.1INTRODUCTION 41 7.2ACCESSING THE WEB GUI 42 7.3OPERATING THROUGH FIREWALLS 438DEVELOPING WITH PRTI™ 1516 448.1MICROSOFT VISUAL STUDIO 6.0 ON WINDOWS 44 8.2MICROSOFT VISUAL STUDIO .NET ON WINDOWS 48 8.3GCC ON LINUX 53 8.4JAVA 54 9WRITING A SIMPLE FEDERATE IN C++ 55 9.1THE FEDERATEAMBASSADOR AND THE RTIAMBASSADOR 559.2THE FEDERATION OBJECT MODEL 56 9.3PUBLISHING AND SUBSCRIBING TO INFORMATION 57 9.4SENDING INTERACTIONS 57 9.5RECEIVING INTERACTIONS 57 9.6CONCLUSIONS 5810WRITING A SIMPLE FEDERATE IN JAVA 5910.1THE FEDERATEAMBASSADOR AND THE RTIAMBASSADOR 59 10.2THE FEDERATION OBJECT MODEL 60 10.3PUBLISHING AND SUBSCRIBING TO INFORMATION 61 10.4SENDING INTERACTIONS 61 10.5RECEIVING INTERACTIONS 61 10.6CONCLUSIONS 6211TICK AND PROCESS MODELS 6311.1MULTIPLE TICK VERSIONS 63 11.2PRACTICAL GUIDELINES 63 11.3EXPLANATION OF PROCESS MODELS 6412DEBUGGING AND TRACING 6512.1OVERVIEW 65 12.2ENABLING THE TRACING 65 12.3FORMAT OF THE TRACE LOG 66 12.4 A SAMPLE TRACE LOG 6613NETWORKING 6813.1WHEN TO RECONFIGURE NETWORKING 68 13.2OVERVIEW OF PRTI™ 1516 COMMUNICATION 69 13.3USING MULTICAST 70 13.4OPERATING OVER FIREWALLS 70 13.5NETWORK SETTINGS 70 13.6PRTI™ 1516 AND PITCH BOOSTER™ 71 14ADVANCED PRTI™ NETWORK PERFORMANCE TUNING 74 14.1INTRODUCTION 74 14.2FEDERATE TUNING 74 14.3SETTING TUNING PARAMETERS 75 14.4PRTI™ 1516 TUNING ALGORITHMS 77 15CONFIGURATION REFERENCE 80 15.1SETTINGS FOR THE CENTRAL RTI COMPONENT 80 15.2SETTINGS FOR THE LOCAL RTI COMPONENT 81 15.3LRC SETTINGS FOR C++ FEDERATES 87 15.4TIME CLASS SETTINGS 87 16COMMON ERRORS 88 16.1COMPILING C++ FEDERATES 88 16.2COMPILING JAVA FEDERATES 89 16.3STARTING PRTI™ 1516 89 16.4RUNNING C++ FEDERATES 90 16.5FEDERATION STARTUP 91 16.6GET HANDLES AND REGISTER OBJECT INSTANCES 92 16.7UPDATES AND INTERACTIONS 93 16.8TIME MANAGEMENT 94 16.9MISCELLANEOUS 951Introduction1.1 About This DocumentpRTI™ and Visual OMT™ are registered trademarks belonging to PitchTechnologies AB. All rights reserved.This document provides information about how to install, run, troubleshoot andoptimize pRTI™ 1516, the leading commercial RTI for the HLA. The acronymRTI stands for Run-Time Infrastructure, pRTI™ stands for portable RTI and HLAstands for High Level Architecture, which is a standard for simulationinteroperability.These are the main audiences for this document:Developers of HLA compliant simulation system who wish to use pRTI™ 1516 in their development projects.IT Staff responsible for setting up and maintaining HLA based simulation applications in their IT environment. This group can concentrate on chapters2, 3 and 5.Technical specialist who wish to evaluate pRTI™ 1516 as aninteroperability infrastructure for their projects or products.The outline of the document is as follows:This introduction gives an initial overview of HLA and pRTI™ 1516.Preparing for pRTI™ 1516 describes the set-up you need to run anddevelop for pRTI™ 1516, such as networking, hardware, software andparticipating systems.Installing pRTI™ 1516 describes how to install pRTI™ 1516 on various platforms such as Windows, Linux etc.Running pRTI™ 1516 describes how to run and monitor your simulations using a graphical and command line interface.Running pRTI™ 1516 In Service-Mode describes how to install and setup pRTI™ 1516 to run as a service on Windows and Linux.Using the pRTI™ 1516 Web GUI describes how to access the pRTI™ 1516 web GUI.Developing with pRTI™ 1516 shows how to set up your developmentenvironment to be able to build federates.Writing a simple federate in C++ contains an example federate complete with C++ source code including instructions on how to compile and run thefederate.Writing a Simple Federate in Java contains an example federate complete with Java source code including instructions on how to compile and run thefederate.Tick and Process Model describes how the RTI and the federate share the CPU and how to achieve optimal performance and responsiveness.Debugging and Tracing describes the abilities of pRTI™ 1516 to aid you in debugging your federation.Networking describes networking functionality and tuning for pRTI™ 1516.Advanced pRTI™ Network Performance Tuning describes the advanced network tuning functionality available in pRTI™ 1516.Configuration Reference contains a summary of all the configuration switches that can be used with pRTI™ 1516.Common errors lists common errors and how to resolve them.1.2 About Pitch TechnologiesPitch Technologies is the world leading supplier of interoperability enablingproducts for simulation and training. Based on open international standards Pitchprovides COTS products for developing and deploying distributed simulationsaccording to the High Level Architecture (HLA). Our products pRTI™, 1516Adapter™, DIS Adapter™ and Visual OMT™ are used in a variety of both civilian and defense simulations world-wide to support training, acquisition and analysis.Furthermore, many of the simulation industry’s vendors use the Pitch products toHLA enable their solutions.1.3 About IEEE 1516 HLAThe HLA standard was initially defined in 1995 based on experiences from earlier simulation interoperability standards. The idea was to create a standard that couldembrace many domains and types of simulation. Although earlier standards existed they were limited to specific simulation domains or did not provide services formanaging time in simulations.The HLA standard has been developed in several steps from 1.0 up to the well-known HLA 1.3 standard. After this step it was decided to broaden the usageoutside the US defense, so the latest version of the standard is established as anopen and international IEEE standard: the IEEE 1516 HLA standard. The IEEE1516 HLA standard is the intended goal also for the US Department of Defensesimulations.IEEE accepted the standard in 2000. Since then the development of tools and RTI:s has started. The first complete RTI implementation, pRTI™ 1516, has beenavailable since December 2001. Other HLA 1516 tools available include objectmodel tools such as Visual OMT™ 1516. During 2003 more tools from severalvendors have been introduced.Starting with version 2.1, pRTI™ 1516 is based on the IEEE standards and theDMSO interpretations version 2.The IEEE 1516 standard is in active use in Europe, Asia and the US. Worth noting is the acceptance by the non-defense community. Commercial applications basedon the IEEE 1516 standard have already been completed and delivered to the enduser.HLA lets you interconnect simulations, devices and humans in a commonfederation. HLA builds on composability, letting you construct simulations frompre-built components.Each computer based simulation system is called a federate and the group ofinteroperating systems is called a federation.The HLA standard consists of three parts:The HLA rules that the entire federation and federates have to follow.The Object Model Template, which is used to describe object models for federates and federations. The leading graphical tool for working which suchobject models is Visual OMT™ 1516 from Pitch AB.The HLA Interface Specification, which describes the functionality that the RTI has to provide. The US Defense Modeling and Simulations Office(DMSO) verify RTI products to guarantee that they adhere to thisspecification. pRTI™ 1516 is certified by DMSO. The certification processwas completed in March 2003.To be able to successfully develop HLA compliant applications it is necessary togain a deeper understanding of HLA than this document provides. Recommendedsources are the DMSO web site (), HLA courses (availablefrom Pitch, see http://www.pitch.se for more information) and books. You may also want to study the FEDEP, which is the recommended process for developingfederations.The book Creating Computer Simulation Systems: An Introduction to the HighLevel Architecture by Dr. Frederick Kuhl, Dr. Richard Weatherley and Dr. JudithDahmann (ISBN 0-13-022511-8) contains an introduction and an in-depthwalkthrough of the old 1.3 version of the HLA standard.1.4 About the Run Time InfrastructureThe Run Time Infrastructure is responsible for the information exchange during the execution. It will let federates join and resign, declare their intent to publishinformation, send information about objects, attributes and interactions,synchronize time, etc. Note that the HLA is not the RTI but it specifies that theremust be an RTI with a standardized interface. The interface is specified in the HLA standard, but the implementation of the interface specification is left to the RTIdeveloper.1.5 About pRTI™ 1516The product pRTI™ 1516 is an implementation of the IEEE 1516 InterfaceSpecification. It lets you integrate simulations in an HLA compliant way. You can mix different operating systems and programming languages. The main advantages of pRTI™ 1516 are:It is complete, certified and HLA compliant. pRTI™ 1516 is a complete implementation of the HLA specification that has been certified by DMSO.This is a requirement for your federation to be HLA compliant.It offers excellent performance. pRTI™ 1516 features sender-side filtering for updates and interactions, which will substantially reduce network andCPU load in large federations. You may also reduce the workload of yourfederates using advisories which impose very little overhead. Still pRTI™1516 has very modest CPU and memory requirements.It provided advanced debugging capabilities. There is an extensive GUI that allows you to inspect the state of your federation during runtime as wellas a powerful set of debugging tools.It is easy to install and run. pRTI™ 1516 is extremely easy to install and configure. It is easy to mix various platforms and languages in the samefederation. The network setup is very simple and it works well over a WANsuch as the Internet.It is network-friendly. You can do optimizations and configurations for LAN, WAN and firewalls and inspect the status of the network graphically.It is commercially packaged and supported. It is possible to get an OEM license to include it with your products. You can get local support andconsulting in several countries (including the USA) from Pitch or one of ourdistributors. See http://www.pitch.se for details.It is superior for long-running federations. It handles unreliable federates gracefully including automatic resign, ownership and time managementrecovery and more.It gives you the ability to integrate your existing C/C++ simulators with platform-independent Java systems. pRTI™ 1516 provides API:s for bothC++ and Java, so you can use federates written in any of those languagestogether in the same federation.pRTI™ 1516 is developed by Pitch. Professional consulting services and training is also available.1.6 Product Licensing StructureThe product is structured in the following way:The pRTI™ 1516 base license enables you to run pRTI™ 1516 with the Java APIwith a certain number of federates. You may for example purchase a license for 10 federates. This will enable you to connect up to 10 federates (simulation systems)together. The federates may run on the same computer or several differentcomputers. The GUI for pRTI™ 1516 is included in the base license.In addition to this you can purchase add-ons such as:C++ interface for Windows.C++ interface for Linux.C++ interface for Solaris, etc.2 Preparing for pRTI™ 1516This chapter describes the computer hardware and software that is needed to run a simulation using pRTI™ 1516. It also describes various configurations that are possible.2.1 A Topology and Components ExampleAn example of a federation of computer-based simulations that interoperates using pRTI™ 1516 is described in the Figure 1Computer A Computer B Computer CFigure 1 – An example topology.The environment in Figure 1 consists of:1. The Central RTI Component that manages the federation.2. The federates participating in the federation.3.The Local RTI Component which each federate use to communicate in thefederation.4. The FOM file that describes the Federation Object Model.The federates and the Central RTI Component are running on separate computers. Note that this is not required. Any number of federates can run on the same computer, and any number of federates can run on the same computer as the Central RTI Component. Another possible topology that shown in Figure 2.Computer A Computer BFigure 2 - Another example topology.2.2 The Central RTI Component (CRC)The CRC is the central component of pRTI™ 1516, also known as the RTIexec. It provides a graphical and a command line interface that lets you monitor theexecution. It is responsible for coordinating the entire federation and distributes the work between the Local RTI Components.When a federate wants to join a federation execution, it connects to the CRC andreceives information about the federation execution such as which other federatesare currently joined to the federation and how to communicate with them.2.3 The FederatesThe federates may be implemented in several languages:C++Any computer language with an interface module written in C++JavaAny computer language, wrapped in JavaYou may mix different implementation languages in the same federation. Note that you need to purchase the C++ add-on (as mentioned in section 1.6) to be able tocall pRTI™ 1516 directly from a C++ application.2.4 The Local RTI Component (LRC)This is a local component that takes care of the local federate’s need to exchangeinformation with other federates. Every federate is compiled and linked with acomponent that contains the classes and methods that are used to connect to thefederation. This component is called the Local RTI Component.This makes pRTI™ 1516 a distributed application, consisting of both the CRC anda number of LRC:s (one for each federate). Figure 3 illustrates the relationshipbetween the CRC, the LRC and the federates.Figure 3 – The relationship between the CRC, the LRC and the federates.2.5 The FOM FileThis is a file that contains the Federation Object Model. The Federation ObjectModel describes the information exchange in the federation. This includes objects, interactions, attributes, parameters and data types for all the information that isexchanged between the federates. The data in the file is XML formatted.Federation object models can be edited using Visual OMT™ 1516. You can use itto create, edit and manage Federation Object Models. Figure 4 shows a screenshot of the tool.Figure 4 – Visual OMT™ 1516 object modeling tool.2.6 The ComputersThe computers that you use will have to provide appropriate networking according to the next section as well as meet the requirements of the local federates.Supported operating systems include:Windows NT/2000/XP on Intel x86.LinuxSolarisYou may mix different brands and operating system in the same federation.Additional platforms may be available and customer ports can be performed.Contact Pitch or your local dealer for more information.2.7 NetworkingThe protocol used for pRTI™ 1516 is the industry standard TCP/IP. The mostcommonly used network configurations for simulations are:An Ethernet-based LAN (Local Area Network). All computers are equipped with Ethernet cards and connected to a hub or switch with 10/100/1000 Base-T cables. Note that using a switch may significantly improve performance for federations exchanging large amounts of data.WLAN. All computers are equipped with a WLAN card and establishes wireless connections through a WLAN hub or switch.Dial-up connections to the network (or the Internet) using a modem.All federates run on a single computer, which is not connected to a network.In this case you will usually need a piece of software called a loop-backdevice. This device is usually installed by default in some operating systems (such as Linux), but may need to be added for others (such as Windows2000).In addition to this you will need to be able to specify the address of the RTI to which you are trying to connect using one of the following:If you have a DNS service it will provide the translation between names (such as myhost.pitch.se) and IP addresses (such as 192.168.1.1). In this case you will need to know the name of the computer running pRTI™ 1516. Note that the DNS server should also be able to resolve IP addresses to names, also known as reverse lookups.If you do not have a DNS service you can use the IP address directly.If you are using a loop-back device, the standard address is 127.0.0.1. Contact your network administrator for details about your organization’s network. The default pRTI™ 1516 settings are suitable for both local area networks and wide area networks. pRTI™ 1516 runs well over WAN:s with routers, for example over the Internet or big corporate networks. See chapter 13 for more information.3Installing pRTI™ 1516This chapter covers how to install and verify the Central RTI Component ofpRTI™ 1516 using the sample federates. It also covers the installation of the LocalRTI Components for the use by your own federates.3.1 Windows InstallationBefore you start, check that you have:The installation executable.You license number that you will use to activate the software. This is not required for the pRTI™ 1516 LE version.Perform the initial installation by double-clicking on the installer. A graphicalinstaller will now start. The first screen you will see contains an important note tousers upgrading from an older version of pRTI™ 1516. As of version 2.3 a newinternal licensing structure is used and old license keys will no longer be valid. Ifyou have received the new pRTI™ 1516 version as part of a maintenance contract,please contact your supplier to obtain a new license key.Figure 5 shows the introduction screen which gives you a general introduction tothe installation and informs you of the new licensing structure.Figure 5 – Installation introduction.Click Next to continue. The license agreement will then be presented to you asshown in Figure 6.Figure 6 – End user license agreement.Read the license agreement and make the appropriate selection. Then click Next. You can now select which type of installation you want. The default selection installs all components, including documentation and example federates. If you are installing on a computer that will run the actual RTI (the CRC) we recommend the Complete installation option. If you are installing on a computer where only federates will be running, we recommend the LRC Only option.Figure 7 – Install set selection.Make your selection and click Next.You will then be asked where to install pRTI™ 1516. You are recommended not to change the default directory.Figure 8 – Installation destination.Make your selection and click Next. You are then asked in which program group that you want the shortcuts.Figure 9 – Create icons in the start menu.Click Next after making your selection. Finally a summary will be presented to you before the installation starts as shown in Figure 9.Figure 10 – Installation summary.Press Install to finish the installation.Figure 11 – Installation progress.When the installation is complete you will see the screen shown in Figure 12.Figure 12 – Installation complete.Press Done to close the installer.3.2 Verifying the Windows InstallationIt is now time to verify your installation.Start pRTI™ 1516 using the start menu command:Start → Programs → pRTI 1516 → pRTI 1516This starts both a textual and a graphical user interface. If you are using the fullversion of pRTI™ 1516 (not LE) you will be required to enter the license number.You may find it more convenient to use cut-and-paste to do this.Figure 13 – Enter the license number.Important note: The license number is used to activate the Central RTIComponent. You are only allowed to use the license number on one computer. Youshould (and need) not enter the license number on computers that only run federates that use the Local RTI Component.Figure 14 – The pRTI™ 1516 GUI.Start a Java based federate using the start menu command:Start → Programs → pRTI 1516 → Samples → Chat Federate (Java)Start a C++ based federate using the start menu command:Start → Programs → pRTI 1516 → Samples → Chat Federate (Visual C++)You will be prompted to enter a name, as an example we will use Fred and Barney.Enter your name: FredAfter entering the names, type a message in one of the federate windows and press the Enter key.> Hello BarneyThe message will now appear in the other federate window (Barney’s) as: > Fred: Hello BarneyNow click in the other federate window (Barney’s) and type the following and finish by pressing the Enter key.> Hello FredThe message will now appear in the other federate window (Fred’s) as: > Barney: Hello FredNow type a period (.) in each federate window followed by the Enter key twice to shut down the chat federates.Switch to the pRTI™ 1516 textual interface and type QUIT followed by the Enter key or click Shut Down RTIexec in the graphical interface. Both these alternatives will shut down the CRC.If you want to run the chat sample over a network, edit the run.bat file in thesamples/chat subdirectory. Add a space followed by the IP address of the computer running the Central RTI Component last on the line that ends with Chat. Start that federate and watch it connect to the remote CRC of the pRTI™ 1516.3.3 Linux InstallationBefore you start, check that you haveThe installation executable.You license number that you will use to activate the software. This is not required for the pRTI™ 1516 LE version.Execute the file prti1516_vX.Y.Z.bin (where X.Y.Z is the pRTI™ 1516 version).Note that you may have to modify the file permissions using the chmod command before running the file:[root@Enorm root] # ./chmod u+x prti1516_v3.0.0.bin[root@Enorm root] # ./prti1516_v3.0.0.binA graphical installer will now start. The graphical installer is very similar to theWindows installer, so check the instructions in section 3.1 if anything is unclear.3.4 Verifying the Linux InstallationIn the bin directory, found in the installation directory, there are three shell scripts, prti1516.sh, java-chat.sh and cpp-chat.sh. These can be used to start pRTI™ 1516 and the two Chat federates that are supplied with the default installation. There isalso a fourth shell script, lrcGui1516.sh, that is used to modify the LRC settings.See section 15.2 for more information. To start pRTI™ 1516, run the fileprti1516.sh. This starts both a textual and a graphical user interface. If you areusing the full version of pRTI™ 1516 (not LE) you will be required to enter thelicense number as shown below. You may find it convenient to use cut-and-pastewhen doing this.[root@Enorm root]# cd /opt/prti1516/bin/[root@Enorm bin]# ./prti1516.shRTIexec for pRTI(tm) 1516 v3.0.0 Certified for IEEE 1516Copyright (c) 2000-2005 Pitch Technologies AB, http://www.pitch.seJava Home = /opt/prti1516/jreCLASSPATH = .Java Ext Dirs = /opt/prti1516/jre/lib/extpRTI Classes = file:/opt/prti1516/jre/lib/ext/prti1516.jar!User Name = rootUser Home = /rootSettings dir = /root/prti13License file: /root/prti1516/pRTI1516.licensePlease enter license number:>After entering your license number the CRC GUI will start as shown in Figure 15.Figure 15 – The pRTI™ 1516 GUI.Important note: The license number is used to activate the Central RTI Component. You are only allowed to use the license number on one computer. You should (and need) not enter the license number on computers that only run federates that use the Local RTI Component.To start the Java Chat federate, run the java-chat.sh file in a new command prompt window. Make sure that pRTI™ 1516 is running before you start the federate.[root@Enorm root]# cd /opt/prti1516/bin/[root@Enorm bin]$ ./java-chat.shEnter your name: FredType messages you want to send. To exit, type . <ENTER>>Now, to start the C++ Chat federate, open another command prompt window and run the cpp-chat.sh file.[root@Enorm root]# cd /opt/prti1516/bin/[root@Enorm bin]# ./cpp-chat.shEnter your name: BarneyType messages you want to send. To exit, type . <ENTER>>Enter a message in one of the federate windows (Barney’s):> Hello FredFinish by pressing the Return key. Watch the message appear in the window of the other federate:> Barney: Hello FredNow click in the other federate window (Fred’s) and type:> Hello BarneyFinish by pressing the Return key. Watch the message appear in the window of the other federate:> Fred: Hello BarneyNow type a period (.) in each federate window followed by the Return key twice.Switch to the pRTI™ 1516 textual interface and type QUIT followed by Return.3.5 Installing on SolarisBefore you start, check that you haveThe installation executable.You license number that you will use to activate the software. This is not required for the pRTI TM 1516 LE version.Execute the file prti1516_vX.Y.Z.bin (where X.Y.Z is the pRTI™ 1516 version).Note that you may have to modify the file permissions using the chmod commandbefore running the file:bash-2.05$ chmod u+x prti1516_ vX.Y.Z.binbash-2.05$ ./prti1516_ vX.Y.Z.binA graphical installer will now start. The graphical installer is very similar to theWindows installer, so check the instructions in section 3.1 if anything is unclear.After the graphical installer completes pRTI™ 1516 will be installed with the Java bindings only. If you also need the C++ bindings (and have the appropriate license) you will need to perform some additional steps.Depending on which C++ environment you use, you’ll need to install differentlibraries. In the pRTI™ 1516 installation directory you’ll find one or more fileswith the general name SunOs_<os version>_<compiler>_<compilerversion>.tar.zip, e.g. SunOS_5.9_CC_6.2.tar.zip. These files contain the C++binaries used by pRTI™ (including the sample Chat federate) for the environment specified by the file name. To install the appropriate C++ binding simply followthe procdure below:1.Open a console window and unzip the file. In this example we’re installingthe C++ bindings built on Solaris 9 using the Forte 6 Update 2 compiler.bash-2.05$ cd /opt/prti1516/bash-2.05$ unzip SunOS_5.9_CC_5.6.tar.zipArchive: SunOS_5.9_CC_5.6.tar.zipinflating: SunOS_5.9_CC_5.6.tar2.Unpack the resulting tar file.bash-2.05$ tar xvf SunOS_5.9_CC_5.6.tarx ./lib, 0 bytes, 0 tape blocksx ./lib/librti1516.so, 1189448 bytes, 2324 tape blocksx ./samples, 0 bytes, 0 tape blocksx ./samples/chatcc, 0 bytes, 0 tape blocksx ./samples/chatcc/ChatCC, 206884 bytes, 405 tape blocksbash-2.05$That’s it! Now just verify your installation as described below and you’ll be ready to start using pRTI™ 1516.3.6 Verifying the Solaris InstallationIn the bin directory, found in the installation directory, there are three shell scripts, prti1516.sh, java-chat.sh and cpp-chat.sh. These can be used to start pRTI TM 1516 and the two Chat federates that are supplied with the default installation. To startpRTI TM 1516, run the file prti1516.sh:bash-2.05$ cd /opt/prti1516/bin/bash-2.05$ ./prti1516.sh。
cmg用户指南英文手册

cmg用户指南英文手册In the world of constantly evolving technology, user guides play a crucial role in enhancing the user experience. The CMG User Guide, an English manual tailored for users of the CMG product line, serves as a comprehensive resourcefor understanding and mastering the features of the CMG devices. This guide aims to provide a detailed overview of the product's capabilities, functions, and operational procedures, enabling users to make the most of their CMG devices.The CMG User Guide begins with an introduction to the product line, providing a broad overview of the various devices and their respective applications. This section highlights the key features of each device, explaining how they can be used to enhance workflow efficiency and productivity. It also introduces the user to the interface and basic navigation of the CMG devices, ensuring a smooth transition from beginner to experienced user.Following the introduction, the guide delves into the detailed features and functions of each CMG device. This section covers everything from basic setup andconfiguration to advanced features and customizations. The guide provides step-by-step instructions for setting up the device, connecting to external devices or software, and configuring settings to optimize performance. It also includes detailed explanations of advanced features such as data analysis, custom programming, and integration withother systems.To ensure maximum user satisfaction, the CMG User Guide also includes troubleshooting and FAQ sections. These sections provide solutions to common issues and answer frequently asked questions, helping users resolve problems quickly and efficiently. Whether you're encountering a technical issue or simply need clarification on a certain feature, these sections provide the answers you need.The guide concludes with a section dedicated to product updates and upgrades. This section keeps users informed of the latest updates and enhancements to the CMG product line, ensuring they always have access to the latest features and improvements. It also provides instructions for upgrading devices and software, ensuring a smooth transition to new versions.The CMG User Guide is an essential tool for anyoneusing CMG devices. It provides a comprehensive overview of the product line, detailed instructions for using and configuring devices, and solutions to common issues. Whether you're a beginner or an experienced user, thisguide will help you maximize the potential of your CMG devices and achieve optimal performance.**CMG用户指南:全面手册以实现最佳利用**在科技不断发展的世界里,用户指南在提升用户体验方面发挥着至关重要的作用。
cmg用户指南英文手册

cmg用户指南英文手册Welcome to the CMG User Guide English Manual, your comprehensive resource for navigating the functionalities and features of the CMG platform. Whether you're a new user or seeking to enhance your proficiency, this guide is tailored to provide you with clear instructions and insights into maximizing your experience with CMG.Getting Started。
Upon accessing the CMG platform, you'll be greeted with a user-friendly interface designed for ease of navigation. The homepage serves as your central hub, offering quick access to various tools and resources. Here, you can explore a range of features, including:1. Dashboard: The dashboard provides an overview of your account activity, displaying important metrics and insights at a glance. Monitor your progress and performance effortlessly.2. Marketplace: Browse through a diverse selection of content available on the CMG marketplace. From articles and videos to interactive modules, discover valuable resources to support your learning journey.3. Courses: Enroll in courses tailored to your interests and objectives. Whether you're seeking to develop new skills or expand your knowledge base, our curated courses cover a wide range of topics to suit your needs.4. Community: Engage with fellow users and experts in the CMG community. Share insights, ask questions, and collaborate on projects to foster meaningful connections and learning opportunities.Exploring Features。
mezz0-user-guide-cn说明书
用户手册系列重要安全说明的基本规范。
请在使用设备前认真阅读“ Important Safeguards (重要保障措施)”。
阅读这些说明。
保留这些说明。
注意所有警告。
遵循所有说明。
无靠近水源使用本设备。
仅用干布擦拭设备。
切勿阻塞任何通风口。
按照制造商的说明进行安装。
本设备设计和生产充分考虑了个人的使用安全。
但是使用不当可能会造成触点或火灾。
请避免削弱极性或接地型插头的保护作用。
极性插头有两个叶片,一窄一宽。
接地插头具有两个叶片和第三接地叉。
宽叶片或第三叉用于保护您的安全。
如果所提供的插头不无法使用您的插座,请咨询电工更换过时的插座。
保护电源线避免踩踏,特别注意保护插头、插座和设备接线处。
只使用制造商指定的附件/配件。
只能与制造商指定的手推车、支架、三脚架或工作台一起使用或搭配销售。
在使用手推车时,请小心移动手推车/设备,避免翻车造成损伤。
雷暴天气或长时间不使用时,请拔下电源线。
交由合格的维修人员进行维修。
若设备出现任何形式的损坏请联系维修,如电源插头或电源线损坏、液体倾倒或物体落入设备内、设备暴露于雨水或湿气中、设备无法正常工作或意外跌落等。
该设备应连接具有保护接地连接的电源插座。
当使用电源插头或耦合器作为断开装置时,断开装置应随时可操作。
带闪电三角形标志用于提醒用户有触电危险。
带感叹号的三角形用于提醒用户注意操作或维修说明。
CE 标志表明产品符合所有适用的欧洲指令标准。
接地/接地符号。
表示设备仅供室内使用。
符合欧洲议会关于废弃电子电气设备(WEEE )2012/ 19/ EC 指令。
-10℃至 +45℃10%至 90%湿度(非冷凝)。
降额高于 35℃切勿在海拔超过 2000米的地方使用本设备。
请勿在热带环境下使用本设备。
警告:为降低触电风险,请勿尝试打开本设备任何部分。
内部没有可供用户使用的部件。
寻求合格的维修人员的维修帮助。
只有具备电工技术的人才能连接电源,要遵循本设备销售国家的国家规范连接电源。
ThinkServer RD640 远程管理用户手册 V1.1

ThinkServerManagement Module User Guide远程管理用户手册V1.1目录第一章简介 (4)1.1 术语 (4)1.2 安全信息 (4)第二章联想远程管理模块概述 (5)2.1联想远程管理模块特性 (5)第三章配置联想远程管理模块 (6)第四章联想远程管理模块操作快速入门 (7)4.1开始之前 (7)4.2登录 (7)4.3导航 (8)4.4注销 (9)第五章远程控制台(KVM)操作 (10)5.1启动重定向控制台 (10)5.2主窗口 (10)5.3远程控制台菜单栏 (10)5.3.1远程控制台视图菜单 (10)5.3.2远程控制台宏菜单 (10)5.3.3远程控制台工具菜单 (11)5.3.4远程控制台电源菜单 (11)第六章联想远程管理模块Web控制台选项 (12)6.1属性 (12)6.2配置 (12)6.2.1网络 (12)6.2.2网络安全 (12)6.2.3安全 (12)6.2.4用户 (13)6.2.5服务 (13)6.2.6 IPMI (13)6.3会话 (14)6.4 LDAP (14)6.5更新 (14)6.6实用程序 (14)6.7服务器信息 (14)6.7.1电源 (15)6.7.2热量 (15)6.8系统事件日志 (15)6.9事件管理 (15)6.9.1平台事件 (15)6.9.2陷阱设置 (16)6.9.3电子邮件设置 (16)6.10 LAN串行 (16)6.11远程控制 (16)6.11.1远程管理 (16)6.11.2配置 (17)第七章语言 (18)附录A-常见问题 (19)第一章简介感谢你购买并使用联想远程管理模块,以下简称远程管理模块。
本用户指南讲述了如何使用远程管理模块,并简要概述了模块特性以及如何设置和操作。
本用户指南专供那些负责安装、故障排除、升级以及维修远程管理模块的系统技术人员使用。
作为系统管理员,您在熟读本指南后即可利用远程管理模块从任意位置远程访问,以便对紧急的关键事件做出即时响应。
Er9x简体中文用户手册

Er9x user guide (Er9x 利用手冊)原作:繁体翻译:简体改编:目录一、介绍(一)工作原理(二)命名标准(三)编辑键(四)阅读操作(五)编辑与贮存(六)快速选择模型(七)遥控器配置二、主屏幕(一)General View 一样画面(二)Statistics Screens 统计值屏幕三、系统设置(一)Radio Setup 系统设置(1/6)(二) PPM In PPM教练信号输入设置(2/6)(三)Version Info 版本信息(3/6)(四)Diagnostics 检测(4/6)(五)Analog Inputs and Battery Voltage Calibration 类比信号输入及电压校正(5/6)(六) Calibration 校正(6/6)四、模型设置(一)Model Select 模型选择(1/10)(二)Model Setup 模型设置(2/10)(三)Heli Setup 直升机设置(3/10)(四)Expo/Dr 行程与大小动(4/10)(五)Mixer 混控器(5/10)(六)Limits 限制器(6/10)(七)Curves 曲线(7/10)(八)Custom Switches 定制切换开关(8/10)(九)Safety Switches 平安切换(9/10)(十)Templates 样板(10/10)五、相关信息一、介紹IMAX/FLYSKY/TURNIGY/EURGLE 9x 是由中国生产的电脑化无线遥控器。
发射机上配置有128X64单色液晶显示屏,2组摇杆,3个旋钮,6个2段开关,1个3段开关和微调。
而那个遥控器的最大吸引力是价钱,同配置的类似遥控器价钱从180美元到1000美元以上。
可是那个遥控器只要60美元,您可能会问是什么吸引人,告知你:重点是软件程序,原版的程序不是专门好,有些小错误,奇怪的导航顺序,烦人的鸣叫声,实在不睬想。
但是,一些爱整的家伙想通了,那个遥控器只是是由摇杆、开关、微调和一个通用的主处置器组成。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
全国普通高等学校人文社会科学研究管理系统(校级网络版V2016版)简要操作说明所有:中国高校人文社会科学信息网2016年11月第一章系统简介1.系统概述全国普通高等学校人文社会科学研究管理信息系统(RPMS),采用先进的Java软件技术开发,以支持多用户协同工作的B/S(浏览器/服务器)架构运行。
功能上,面向教育部人文社会科学年度统计要求,可便捷、完整的录入相关基础数据,并严格按照统计规自动生成统计报表,从而保障人文社会科学统计工作的顺利进行。
同时系统还可以有效支持学校的日常科研管理工作,成为高校科研管理工作的辅助平台。
2.版本情况全国普通高等学校人文社会科学研究管理信息系统(RPMS)分为省级版与校级版两个版本。
其中校级版,供各高校用户使用,进行校级的数据录入,报表生成,以及数据上报;省级版,供各省、自治区、直辖市教育厅及教委用户使用,用于汇总各高校上报的数据文件,生成省级报表及省级上报文件。
省级版与校级版系统,每年年末均会根据当年的统计报表制度要求及功能改进设计,发布一个当年的新版本。
但每个新版系统,都会保证校级版数据的兼容与延续性,上一版本中的数据,一定可以完整的移植到新版系统中。
为此,各高校可随时进行基础数据的录入与调整工作,无须待到统计工作开始了,新版系统发布后,再进行突击性录入。
第二章 2016及2016SP1版新特点1.功能改进1.1网页样式将网页页面加宽,改为面向1024X768像素屏幕分辨率进行设计,并调整了色调。
1.2新增办学性质字段1.3调整了研究机构的机构类型与组成方式机构类型可多选,并支持自定义。
组成方式精简为:校独立设置、校跨部门设置与校外合办。
1.4经费部分●针对民办高校,在“非政府资金投入”之中也加入了“科研人员工资”一项;●去除了“当年结余经费”之中的“其他结余”●根据新颁发的《高等学校哲学社会科学繁荣计划专项资金管理办法》要求,增加了“间接费”一栏1.5 调整了工作量复制功能本着项目完成周期为3年的原则,立项时间超出3年的项目,工作量将不被复制,比如,复制某年度项目到2016年度时,2013年1月1日之前立项的在研项目的工作量将不被复制。
另外,研究生的工作量也不会被复制。
1.6 成果获奖调整了奖励等级,分别为:一等、二等、三等、成果普及奖和其他。
2.报表部分●所有报表打印调整为横向打印,相应报表打印格式调整。
●社科3表:在“非政府资金投入”增加指标“科技活动人员工资”;去掉“当年经费结余”下的“其他结余”指标;人均工资校验改为1-6万元。
●社科4表:机构类型显示改为机构类型名称,如果有多个同时显示。
●社科6表:增加“皮书/发展报告”和“科普读物”两类成果的统计数据。
●社科7表:同一成果多次获奖改为多次统计。
●社科8表:国学术交流下的“赴境外”人数不可修改。
第三章安装配置1.系统配置与使用要求电脑最低配置要求:双核处理器 1.5GHz以上,2Gb存,Windows XP及以上操作系统,32或64位的Windows7、8、10均可。
强烈建议使用Microsoft Internet Explorer 10.0以上的浏览器访问,特别是报表预览及打印部分的功能,只支持IE浏览器2.安装流程安装程序请从社科网“管理软件”栏目下载(网址:/guanli/glrj)。
如果是初次安装,请下载安装“完全升级版”;若系统以前安装过旧版本的系统,请先通过“系统维护子系统”进行数据备份,再下载安装“升级安装版”程序即可,万一系统数据意外受损,再进行数据恢复。
安装成功后,会在Windows所有程序菜单中看到名为“科研管理系统(校级网络版)”的程序组,如上图。
如因异常原因,未能新建出这些菜单项。
可手工在桌面上自行创建启动快捷方式。
操作方法:在Windows桌面空白处,单击鼠标右键,选新建->快捷方式,先新建“启动数据库”,将目标程序指向到“C:\rpms\mysql\bin\winmysqladmin.exe”,再新建“启动rpms服务器”快捷方式,将目标程序指向到“C:\rpms\tomcat\env.bat”。
最后新建“系统维护子系统”,将目标程序指向到“C:\rpms\mysql\bin\jet.exe”即可。
3.系统启动及数据初始化系统安装成功后,如果在当前计算机上属于初次安装,须先重启计算机。
之后,先启动数据库服务器,再启动RPMS服务器,次序不得有误。
具体情况如下:3.1启动数据库服务器数据库服务器启动后会在任务栏右下角显示一个交通红绿指示灯样的图标。
如果图标中绿灯亮,则说明mysql数据库启动正常(如图3.1)一次试用时需要启动数据库服务器,以后服务器重新启动时mysql数据库会自动启动。
注意:在系统使用过程中,不要将mysql数据库关闭。
图3.1如果数据库服务器启动后,红绿灯状态为红灯,说明mysql服务没有能够正常启动。
此时,可在红绿灯处单击鼠标右键,从弹出菜单中点击Win NT-> Start the Server Standalone,如图,之后绿灯应该就能亮起,MySQL数据库服务器即可正常启动。
3.2启动rpms服务器在“启动rpms服务器”后,Windows界面中会弹出一个标题为”Tomcat”的窗口,并且可以看到窗口中不断有调试信息显示出来。
经过大约10到30秒的时间,当窗口中不再有调试信息出来,且最后一行显示为“Apahce Tomcat/4.0.3”时,说明rpms服务器(Tomcat)已经正常启动。
系统运行过程中,不得关闭该窗口,也不得随意用鼠标点击该窗口中的容。
如图3.2图3.23.3登录系统当MySQL数据库和Tomcat服务器启动正常,就可以开始使用本系统了。
如果在本地运行,请打开因特网浏览器,如Windows系统自带的Microsoft Internet Explorer,访问localhost:8080/school。
因为本系统采用Browser/Server架构,只要将系统安装在一台计算机上(这台电脑就相当于是服务器了),其他可以通过网络访问到这台服务器的计算机就可以通过因特网浏览器访问并使用本系统。
前提是需要知道先搞清该服务器的网络IP地址,假如我们把系统安装在IP地址为192.168.1.103服务器上,那么从其他可以访问该服务器的计算机上访问地址就为:192.168.1.103:8080/school。
如何查看计算机的IP地址呢?最简便的方式是,我们可以按下Windows+R键盘组合,调出“运行”对话框,在“打开”中键入“cmd”后,按确定。
在命令行窗口中再键入>“ipconfig”,并按回车键。
其中IPv4地址一行后面示出的192.168……..,就是这台电脑的IP地址。
那么,如果我们想从网络中其他计算机访问这套系统,在浏览器地址栏中,就应该键入:192.168.8.10:8080/school。
3.4历史数据的恢复如果手里有往年的校级系统历史数据备份文件,有如下两种方式可以将其恢复到系统中,无论采用哪种恢复方式,数据恢复的效果是一样的。
需要注意的是,必须要在安装有校级系统的计算机上直接进行数据恢复操作,不能通过从客户端访问服务器的方式进行。
恢复方式一:使用系统自带的“系统维护子系统”程序恢复.rpms格式数据库备份文件在启动mysql数据库的情况下,从Windows->开始菜单中,找到并启动“系统维护子系统”程序,点击数据库恢复中的“文件选择”按钮,选中.rpms格式的数据库历史备份文件,再点“恢复”按钮,等待数分钟,见到“成功提示”后,这套备份数据就已数据覆盖的方式恢复到了系统中,即系统中的原有数据会被覆盖掉。
恢复方式二:使用“数据初始化”流程导入.zip格式数据上报包如果安装的是完全安装版的校级系统,且没有恢复过数据,第一次访问系统时,会自动进入“数据初始化”流程。
在使用过程中,也随时可以通过“系统维护->数据库初始化”,进入这一流程。
如图:图3.4.1数据初始化的第二步是设置管理员和密码,如图3.4.2,输入信息后进入第三步。
图3.4.2之后,将导入.zip格式的数据库上报文件,其实也属于数据库备份文件,如图3.4.3。
如果是之前没有使用过系统,没有zip格式数据库上报文件的新学校用户,跳过该步骤,凭刚刚自行设定的用户名及密码,登录系统,开始工作即可。
如果不是新学校用户,“是否合并数据”处选“否”,点击“浏览”,选定要导入的zip格式文件,进行数据导入。
导入结束后,会显示当前这套数据中系统管理员的用户名和密码,凭此即可登入系统,如图3.4.4。
注:在系统使用过程中,如不知道或忘记了系统管理员用户名和密码,可在已启动MySQL数据库的前提下,双击运行c:\rpms\tomcat\findpassword.bat 进行查看。
其中login_id一栏下的字符即为用户名,password一栏下的字符为密码。
3.5基础数据录入建议流程对于新的学校用户,在初次开始使用本系统进行学校科研信息录入时,建议按照先录入学校基本信息、机构信息、人员信息,再录入项目信息、成果信息、学术会议和交流论文库的顺序进行。
第四章学校管理学校管理包括学校基本信息、学校经费情况、特殊人才统计、学科建设统计、学术期刊统计和科研管理部门信息等,须逐一完整、如实的填报。
其中最重要,且每年都需根据当年情况进行更新的是学校经费情况信息,如图。
此表中须填报,在统计年份,政府与非政府、以非项目经费形式投入学校的R&D经费、及其支出与结余情况。
这份数据与项目经费情况合并,最终汇总为年报3表。
其中的“上年结转经费”一栏,取自上一年度学校经费情况中的“当年结余经费”。
为保证数据延续性,原则上不应修改上年结转一栏的数额。
第五章机构管理1.机构概述“院系所”指学校下属有正式人员编制的机构,包括:院、系、研究所、研究中心、重点研究基地等。
“研究机构”栏目专门用于实体和非实体研究机构的科研管理。
实体研究机构应该在“院系所”和“研究机构”中分别录入。
例如:中国人民大学清史研究所的部分老师编制在清史研究所,部分老师编制不在清史研究所,在数据录入时要在“院系所”和“研究机构”中分别增加清史研究所这条信息,操作如下:点击机构管理中的“院系所”二级目录,就可以进入院系所的列表页面,院系信息也包括下属教研室的信息。
点击“新增”按钮,进入新增页面。
输入院系信息,院系信息包括院系名称、学科门类、负责人等院系基本信息,为保证数据的完整性和有效性,方便查询和修改,建议尽量输入比较完整的信息,其中用*标识的为必须填写的数据项录入过程需特别注意的是,录入系统中所有的日期字段,比如机构中的“成立时间”与人员中的“出生日期”时,应点击日期按钮,并从日期选择框中去选择具体的日期,而不要到日期文本框中直接去敲。
