An Efficient Distributed Group Mutual Exclusion Algorithm for Non-Uniform Group Access
深度合作展宏图的英语作文

In todays rapidly evolving world,the concept of deep cooperation has become increasingly significant.It is a strategic approach that enables entities to leverage each others strengths,share resources,and achieve common goals more effectively.This essay will explore the importance of deep cooperation,its benefits,and how it can be applied in various sectors to create a more prosperous future.The Essence of Deep CooperationDeep cooperation is not merely a partnership it is a profound alliance where parties work closely to understand each others needs,capabilities,and aspirations.It involves a high level of trust,transparency,and mutual respect.This form of collaboration goes beyond surfacelevel agreements and dives into a realm where shared values and longterm visions are the driving forces.Benefits of Deep Cooperation1.Resource Optimization:By cooperating deeply,organizations can pool resources, leading to more efficient use and reduced costs.This is particularly beneficial in research and development,where the costs can be prohibitive for a single entity.2.Innovation Acceleration:When different entities with diverse expertise come together, they can accelerate the innovation process.The exchange of ideas and knowledge can lead to breakthroughs that might not have been possible in isolation.3.Risk Mitigation:Sharing risks is a key advantage of deep cooperation.When responsibilities and potential losses are distributed among partners,the overall risk for each party is reduced.4.Market Expansion:Cooperation allows for easier access to new markets.Partners can leverage each others networks and customer bases,expanding their reach and influence.5.Enhanced Competitiveness:By combining strengths,cooperative entities can offer more competitive products or services,thus gaining an edge over competitors who operate independently.Application in Various Sectors1.Business:Corporations often engage in strategic alliances to enter new markets or develop new products.For instance,tech companies may collaborate on research to create cuttingedge devices.cation:Educational institutions can partner with industry leaders for internships and research opportunities,providing students with realworld experience and institutions with access to industry insights.ernment and Public Policy:Governments can work with NGOs and private sectors to address social issues more effectively.Such cooperation can lead to wellrounded policies that consider various perspectives.4.Environmental Conservation:Deep cooperation among nations is crucial in combating global environmental challenges like climate change.Sharing technology and best practices can lead to more effective conservation efforts.5.Healthcare:During a pandemic,for example,deep cooperation among countries, healthcare providers,and pharmaceutical companies is vital for vaccine development and distribution.ConclusionDeep cooperation is a powerful tool for driving progress and achieving ambitious goals. It requires commitment,open communication,and a willingness to work towards a shared vision.By embracing deep cooperation,we can tackle the complex challenges of our time and create a more interconnected and prosperous world.The future belongs to those who can collaborate effectively,and deep cooperation is the key to unlocking our collective potential.。
英语作文介绍侗族

英语作文介绍侗族The Dong people, also known as the Kam people, are an ethnic minority group in China. They are mainly distributed in the southwestern provinces of Guizhou, Hunan, and Guangxi, with a population of over 3 million. The Dong people have a rich and unique culture, with their own language, customs, and traditions.The Dong people are known for their exquisite architecture, especially their iconic drum towers and wind and rain bridges. These structures are not only functional but also serve as important cultural symbols for the Dong people. The drum towers are used for public gatherings, performances, and important ceremonies, while the wind and rain bridges are not only used for transportation but also as meeting places for the community.In addition to their architectural achievements, the Dong people are also known for their rich musical traditions. They have a long history of creating andperforming beautiful folk songs, which are often accompanied by unique instruments such as the lusheng, a reed-pipe wind instrument. The Dong people's music reflects their close connection to nature and their deepappreciation for the natural world.The Dong people also have a strong tradition of embroidery and textile arts. Dong embroidery is known forits intricate designs and vibrant colors, and it is often used to decorate traditional clothing and household items. The Dong people take great pride in their embroidery skills, and it is an important part of their cultural heritage.One of the most important aspects of Dong culture is their traditional festivals and rituals. The Dong people celebrate a number of festivals throughout the year, each with its own unique customs and traditions. These festivals often involve music, dance, and elaborate ceremonies, and they are an important way for the Dong people to connectwith their cultural roots and pass down their traditions to future generations.The Dong people have a strong sense of community and place a high value on hospitality and mutual support. They have a unique system of mutual aid called "huanji," which is a form of community cooperation and assistance. This system helps to strengthen social bonds within the Dong community and ensures that everyone has the support they need in times of need.In recent years, the Dong people have faced challenges in preserving their cultural heritage and traditions. Modernization and urbanization have brought new influences and changes to Dong communities, and there is a growing concern about the loss of traditional knowledge and practices. However, efforts are being made to preserve and promote Dong culture, including the establishment of cultural centers, museums, and educational programs.Overall, the Dong people have a rich and vibrant culture that is deeply rooted in their history and traditions. Their unique architecture, music, festivals, and strong sense of community make them a truly remarkable ethnic group in China. It is important to recognize andcelebrate the cultural diversity of the Dong people and to support their efforts to preserve their heritage for future generations.。
【英文原版】操作系统_精髓与设计原理_第6版 - Chapter18-new

Load Sharing
• Move processes from heavily loaded to lightly load systems
– Significant improvements are possible – Must be careful that the communications overhead does not exceed the performance gained.
• Checkpoint/restart capability is useful.
Precopy
• Process continues to execute on the source node while the address space is copied
– Pages modified on the source during precopy operation have to be copied a second time – Reduces the time that a process is frozen and cannot execute during migration
– Who initiates the migration? – What is involved in a Migration? – What portion of the process is migrated? – What happens to outstanding messages and signals?
Motivation
• Process migration is desirable in distributed computing for several reasons including:
人简 历 吴维刚 - z 个人信息
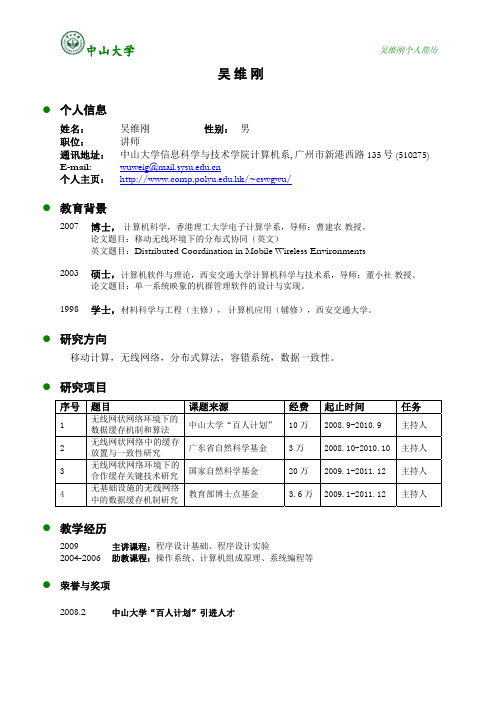
吴维刚z个人信息姓名:吴维刚性别:男职位:讲师通讯地址:中山大学信息科学与技术学院计算机系, 广州市新港西路135号 (510275) E-mail: wuweig@个人主页:.hk/~cswgwu/z教育背景2007 博士,计算机科学,香港理工大学电子计算学系,导师:曹建农教授。
论文题目:移动无线环境下的分布式协同(英文)英文题目:Distributed Coordination in Mobile Wireless Environments2003 硕士,计算机软件与理论,西安交通大学计算机科学与技术系,导师:董小社教授。
论文题目:单一系统映象的机群管理软件的设计与实现。
1998 学士,材料科学与工程(主修),计算机应用(辅修),西安交通大学。
z研究方向移动计算,无线网络,分布式算法,容错系统,数据一致性。
z研究项目序号题目课题来源经费起止时间任务1 无线网状网络环境下的数据缓存机制和算法中山大学“百人计划” 10万 2008.9-2010.9 主持人2 无线网状网络中的缓存放置与一致性研究广东省自然科学基金 3万 2008.10-2010.10 主持人3 无线网状网络环境下的合作缓存关键技术研究国家自然科学基金 20万 2009.1-2011.12 主持人4 无基础设施的无线网络中的数据缓存机制研究教育部博士点基金 3.6万2009.1-2011.12 主持人z教学经历2009主讲课程:程序设计基础、程序设计实验2004-2006 助教课程:操作系统、计算机组成原理、系统编程等z荣誉与奖项2008.2 中山大学“百人计划”引进人才z学术活动国际会议TPCEUC’09, EUC’08, ICCCN’08, NIMC’08, CODS’07, MSN’07论文评审期刊IEEE TC, IEEE TMC, JPDC, PMC会议ICDCS’08, MDM’08, ICPP’08, ICC’08DSN’07, PerCom’07, ICC’07, CCGrid07, AINA’07;ICDCS’06, PerCom’06, IPDPS’06;DSN’05, SRDS’05, ICCCN’05, Globecom’05.会议组织2005The 6th Int’l Workshop on Advanced Parallel Processing Technologies (APPT'05)2004The 2nd Int’l Symposium on Parallel and Distributed Processing and Applications (ISPA'04)z学术论文期刊论文:1.Weigang Wu, Jiannong Cao, Michel Raynal, Eventual Clusterer: a Modular Approach to DesigningHierarchical Consensus Protocols in MANETs, IEEE Transactions on Parallel and DistributedSystems (TPDS), 20(6), pp. 753-765, June 20092.Jin Yang, Jiannong Cao, Weigang Wu, Chengzhong Xu, Efficient Algorithms for Fault TolerantMobile Agent Execution, International Journal of High Performance Computing andNetworking(IJHPCN), 6(2), pp. 106-118, 20093.Weigang Wu, Jiannong Cao, Jin Yang, Michel Raynal, Using Asynchrony and Zero Degradation toSpeed up Indulgent Consensus Protocols, Journal of Parallel and Distributed Computing (JPDC),Elsevier, 68(7), Jul. 2008, pp. 984-996.4.Jin Yang, Jiannong Cao, Weigang Wu, Efficient Global Checkpointing Algorithms for MobileAgents, Concurrency and Computation: Practice and Experience, John Wiley & Sons, 20(7), May.2008, pp. 825-838.5.Weigang Wu, Jiannong Cao, Jin Yang, A Fault Tolerant Mutual Exclusion Algorithm for Mobile AdHoc Networks, Pervasive and Mobile Computing (PMC), Elsevier, 4(1), February 2008, pp. 139-160.6.Weigang Wu, Jiannong Cao, Jin Yang, Michel Raynal, Design and Performance Evaluation ofEfficient Consensus Protocols for Mobile Ad Hoc Networks, IEEE Transactions on Computers (TC),56(8), Aug. 2007, pp. 1055-1070.会议论文:1.Xiaopeng Fan, Jiannong Cao, Weigang Wu, Contention-Aware Data Caching in Wireless Multi-hopAd Hoc Networks, 6th IEEE International Conference on Mobile Ad-hoc and SensorSystems(MASS’09), October 12 - 15, 2009, Macau2.Weigang Wu, Jiannon Cao, Xiaopeng Fan, Overhearing-aided Data Caching in Wireless Ad HocNetworks, 6th IEEE ICDCS International Workshop on Wireless Ad hoc and SensorNetworks (WWASN’09). June 22-26, 2009 Montreal, Canada3.Jiannong Cao, Kun Xie, Weigang Wu, Chuda Liu, et al., HAWK: Real-world Implementation ofHigh-performance Heterogeneous Wireless Network for Internet Access, 1st ICDCS International Workshop on Next Generation Network Architectures (NGNA’09), June 22-26, 2009Montreal, Canada.4.Ye Yan, Jiannong Cao, Chuda Liu, SeongWoo Kim, Weigang Wu, A Dual Re-authenticationScheme for Fast Handoff in IEEE 802.11 Wireless Mesh Networks, IEEE Wireless Communications and Networking Conference (WCNC’09), April 4 – 8, 2009. Budapest, Hungary.5.Xiaopeng Fan, Jiannong Cao, Weigang Wu, Hui Cheng, Modeling Hierarchical Gossiping inReliable Multicast Protocols, Proc. The 2nd International Conference on Future Generation Communication and Networking(FGCN’08), December 2008, Sanya, Hainan Island, China.6.Xiaopeng Fan, Jiannong Cao, Weigang Wu, Michel Raynal, On Modeling Fault Tolerance ofGossip-Based Reliable Multicast Protocols, Proc. of the 37th International Conference on Parallel Processing (ICPP’08), Portland, USA, Sep. 8 – 12 2008.7.Vaskar Raychoudhury, Jiannong Cao, Weigang Wu, Top K-leader Election in Wireless Ad HocNetworks, Proc. of the 17th International Conference on Computer Communication Networks (ICCCN'08), St. Thomas, US Virgin Islands, August 4-7, 2008.8.Jiannong Cao, Corentin Travers, Michel Raynal, Weigang Wu, The Eventual Leadership inDynamic Mobile Networking Environments, Proc. of the 13th IEEE Pacific Rim International Symposium on Dependable Computing (PRDC'07), Melbourne, Australia, December 17-19, 2007. 9.Weigang Wu, Jiannong Cao, Michel Raynal, A Dual-Token-based Fault Tolerant Mutual ExclusionAlgorithm for MANETs, Proc. of the 3rd International Conference on Mobile Ad-hoc and Sensor Networks (MSN’07), Beijing, China,12-14 December 2007.10.Weigang Wu, Jiannong Cao, Michel Raynal, The Eventual Clusterer Oracle and Its Application toConsensus in MANETs, Proc. of the 26th IEEE International Symposium on Reliable Distributed Systems (SRDS’07), Beijing China, Oct. 10-12, 2007.11.Jiannong Cao, Miaomiao Wang, Weigang Wu, Xianbing Wang, Stephen C.F. Chan, A GenericDistributed Monitor Construct for Programming Process Synchronization in Distributed Systems, Proc. of the5th International Symposium on Parallel and Distributed Processing and Applications (ISPA’07), Niagara Falls, Canada, Aug. 29-31, 200712.Jin Yang, Jiannong Cao, Weigang Wu, An Integrated Approach to Checkpointing in Mobile AgentSystems, Proc. of the 2nd International Conference on Semantics, Knowledge and Grid (SKG’06), Guilin, China, Nov. 1-3, 200613.Jin Yang, Jiannong Cao, Weigang Wu, Checkpoint Placement Algorithms for Mobile Agent System,Proc. of the5th International Conference on Grid and Cooperative Computing (GCC’06), Changsha, China, Oct. 21-23, 2006.14.Jiannong Cao, Michel Raynal, Xianbing Wang, Weigang Wu,The Power and Limit of AddingSynchronization Messages for Synchronous Agreement, Proc. of the 35th International Conference on Parallel Processing (ICPP’06), Columbus, USA, Aug. 14-18, 2006.15.Jin Yang, Jiannong Cao, Weigang Wu, Corentin Travers The Notification based Approach forImplementation Failure Detector, Proc. of the1st International Conference on Scalable Information System (InfoScale’06) , Hong Kong, May 29-Jun. 1, 2006.16.Weigang Wu, Jiannong Cao, Jin Yang, Michel Raynal, A Hierarchical Consensus Protocol forMobile Ad Hoc Networks, Proc. of the14th Euromicro Conference on Parallel, Distributed and Network based Processing (PDP’06), Montbéliard, France, Feb. 15~17, 2006.17.Jin Yang, Jiannong Cao, Weigang Wu, Chengzhong Xu, A Framework for Transactional MobileAgent Execution, Proc. of the4th International Conference on Grid and Cooperative Computing (GCC’05), Beijing, China, Nov. 30-Dec. 3, 2005.18.Jiannong Cao, Jin Yang, Weigang Wu, Chengzhong Xu, Exception Handling in DistributedWorkflow Systems Using Mobile Agents, Proc. of the IEEE International Conference on E-Business Engineering (ICEBE’05), Beijing, China, Oct. 18-20, 2005.19.Weigang Wu, Jiannong Cao, Jin Yang, A Scalable Mutual Exclusion Algorithm for Mobile Ad HocNetworks, Proc. of the14th International Conference on Computer Communications and Networks (ICCCN’05), San Diego, USA, Oct. 17-19, 2005.20.Jin Yang, Jiannong Cao, Weigang Wu, Chengzhong Xu, Parallel Algorithms for Fault-TolerantMobile Agent Execution, Proc. of the6th International Conference on Algorithms and Architectures(ICA3PP’05), Melbourne, Australia, Oct. 2-5, 2005.。
基于混合整数二阶锥规划的主动配电网有功无功协调多时段优化运行

基于混合整数二阶锥规划的主动配电网有功无功协调多时段优化运行一、本文概述Overview of this article随着可再生能源的大规模接入和电力电子设备的广泛应用,主动配电网(Active Distribution Network, ADN)的运行和管理面临着前所未有的挑战。
有功功率和无功功率的协调优化是保障ADN安全、经济、高效运行的关键。
本文提出了一种基于混合整数二阶锥规划(Mixed-Integer Second-Order Cone Programming, MISOCP)的主动配电网有功无功协调多时段优化运行方法。
该方法旨在通过综合考虑ADN中的多种约束条件和运行目标,实现有功和无功功率的协同优化,提高配电网的运行效率和稳定性。
With the large-scale integration of renewable energy and the widespread application of power electronic devices, the operation and management of Active Distribution Network (ADN) are facing unprecedented challenges. The coordinated optimization of active and reactive power is the key to ensuring the safe, economical, and efficient operation of ADN. Thisarticle proposes a multi period optimization operation method for active and reactive power coordination in active distribution networks based on Mixed Integer Second Order Cone Programming (MISOCP). This method aims to achieve collaborative optimization of active and reactive power by comprehensively considering various constraints and operational objectives in ADN, and improve the operational efficiency and stability of the distribution network.本文首先介绍了ADN的特点和面临的挑战,然后详细阐述了有功无功协调优化的重要性。
关于团队合作的英语作文

Teamwork is a vital component in various aspects of life,from the workplace to sports and even in academic settings.It is the collaborative effort of a group to achieve a common goal or to complete a task in the most effective and efficient way.Here are some key points to consider when discussing the importance of teamwork in an English essay:1.Definition of Teamwork:Begin by defining what teamwork means.It is the process where interdependent individuals work together towards a common goal,sharing responsibilities,and making collective decisions.2.Importance in the Workplace:Discuss how teamwork is crucial in a professional environment.It fosters innovation,as diverse ideas and perspectives can be shared and built upon.It also improves productivity,as tasks can be divided among team members according to their strengths.munication Skills:Highlight the role of effective communication in teamwork. Clear and open communication helps in understanding each others roles,resolving conflicts,and ensuring everyone is on the same page.4.Diversity and Inclusion:Emphasize the value of diversity in a team.Different backgrounds,experiences,and skills can enrich the teams problemsolving capabilities and creativity.5.Leadership and Delegation:Talk about the importance of strong leadership in guidinga team.A good leader delegates tasks effectively,ensuring that each team members talents are utilized to their fullest potential.6.Trust and Respect:Trust is fundamental in a team.Members must trust each other to fulfill their responsibilities and respect each others contributions.This fosters a positive and supportive environment.7.ProblemSolving:Teamwork enhances problemsolving by allowing for the collective analysis of issues.Multiple perspectives can lead to more innovative and effective solutions.8.Adaptability and Flexibility:Teams that work well together are often more adaptable to change.They can adjust strategies and roles as needed to meet new challenges.9.Success Stories:Provide examples of successful teams from various fields,such as sports teams winning championships,scientific teams making breakthrough discoveries, or business teams launching successful products.10.Challenges and Solutions:Acknowledge the challenges that can arise in teamwork, such as conflicts,lack of motivation,or poor communication.Discuss strategies for overcoming these issues,such as teambuilding exercises,regular meetings,and clear goal setting.11.Personal Development:Explain how participating in a team can contribute to personal growth.Team members can learn new skills,improve their ability to work with others,and gain confidence in their abilities.12.Conclusion:Conclude by summarizing the key points and reiterating the significance of teamwork in achieving success in various fields.Encourage readers to value and practice teamwork in their own lives.Remember to use clear and concise language,provide specific examples,and maintain a logical flow throughout your essay to effectively convey the message about the importance of teamwork.。
An Overview of Recent Progress in the Study of Distributed Multi-agent Coordination

An Overview of Recent Progress in the Study of Distributed Multi-agent CoordinationYongcan Cao,Member,IEEE,Wenwu Yu,Member,IEEE,Wei Ren,Member,IEEE,and Guanrong Chen,Fellow,IEEEAbstract—This article reviews some main results and progress in distributed multi-agent coordination,focusing on papers pub-lished in major control systems and robotics journals since 2006.Distributed coordination of multiple vehicles,including unmanned aerial vehicles,unmanned ground vehicles and un-manned underwater vehicles,has been a very active research subject studied extensively by the systems and control community. The recent results in this area are categorized into several directions,such as consensus,formation control,optimization, and estimation.After the review,a short discussion section is included to summarize the existing research and to propose several promising research directions along with some open problems that are deemed important for further investigations.Index Terms—Distributed coordination,formation control,sen-sor networks,multi-agent systemI.I NTRODUCTIONC ONTROL theory and practice may date back to thebeginning of the last century when Wright Brothers attempted theirfirst testflight in1903.Since then,control theory has gradually gained popularity,receiving more and wider attention especially during the World War II when it was developed and applied tofire-control systems,missile nav-igation and guidance,as well as various electronic automation devices.In the past several decades,modern control theory was further advanced due to the booming of aerospace technology based on large-scale engineering systems.During the rapid and sustained development of the modern control theory,technology for controlling a single vehicle, albeit higher-dimensional and complex,has become relatively mature and has produced many effective tools such as PID control,adaptive control,nonlinear control,intelligent control, This work was supported by the National Science Foundation under CAREER Award ECCS-1213291,the National Natural Science Foundation of China under Grant No.61104145and61120106010,the Natural Science Foundation of Jiangsu Province of China under Grant No.BK2011581,the Research Fund for the Doctoral Program of Higher Education of China under Grant No.20110092120024,the Fundamental Research Funds for the Central Universities of China,and the Hong Kong RGC under GRF Grant CityU1114/11E.The work of Yongcan Cao was supported by a National Research Council Research Associateship Award at AFRL.Y.Cao is with the Control Science Center of Excellence,Air Force Research Laboratory,Wright-Patterson AFB,OH45433,USA.W.Yu is with the Department of Mathematics,Southeast University,Nanjing210096,China and also with the School of Electrical and Computer Engineering,RMIT University,Melbourne VIC3001,Australia.W.Ren is with the Department of Electrical Engineering,University of California,Riverside,CA92521,USA.G.Chen is with the Department of Electronic Engineering,City University of Hong Kong,Hong Kong SAR,China.Copyright(c)2009IEEE.Personal use of this material is permitted. However,permission to use this material for any other purposes must be obtained from the IEEE by sending a request to pubs-permissions@.and robust control methodologies.In the past two decades in particular,control of multiple vehicles has received increas-ing demands spurred by the fact that many benefits can be obtained when a single complicated vehicle is equivalently replaced by multiple yet simpler vehicles.In this endeavor, two approaches are commonly adopted for controlling multiple vehicles:a centralized approach and a distributed approach. The centralized approach is based on the assumption that a central station is available and powerful enough to control a whole group of vehicles.Essentially,the centralized ap-proach is a direct extension of the traditional single-vehicle-based control philosophy and strategy.On the contrary,the distributed approach does not require a central station for control,at the cost of becoming far more complex in structure and organization.Although both approaches are considered practical depending on the situations and conditions of the real applications,the distributed approach is believed more promising due to many inevitable physical constraints such as limited resources and energy,short wireless communication ranges,narrow bandwidths,and large sizes of vehicles to manage and control.Therefore,the focus of this overview is placed on the distributed approach.In distributed control of a group of autonomous vehicles,the main objective typically is to have the whole group of vehicles working in a cooperative fashion throughout a distributed pro-tocol.Here,cooperative refers to a close relationship among all vehicles in the group where information sharing plays a central role.The distributed approach has many advantages in achieving cooperative group performances,especially with low operational costs,less system requirements,high robustness, strong adaptivity,andflexible scalability,therefore has been widely recognized and appreciated.The study of distributed control of multiple vehicles was perhapsfirst motivated by the work in distributed comput-ing[1],management science[2],and statistical physics[3]. In the control systems society,some pioneering works are generally referred to[4],[5],where an asynchronous agree-ment problem was studied for distributed decision-making problems.Thereafter,some consensus algorithms were studied under various information-flow constraints[6]–[10].There are several journal special issues on the related topics published af-ter2006,including the IEEE Transactions on Control Systems Technology(vol.15,no.4,2007),Proceedings of the IEEE (vol.94,no.4,2007),ASME Journal of Dynamic Systems, Measurement,and Control(vol.129,no.5,2007),SIAM Journal of Control and Optimization(vol.48,no.1,2009),and International Journal of Robust and Nonlinear Control(vol.21,no.12,2011).In addition,there are some recent reviewsand progress reports given in the surveys[11]–[15]and thebooks[16]–[23],among others.This article reviews some main results and recent progressin distributed multi-agent coordination,published in majorcontrol systems and robotics journals since2006.Due to space limitations,we refer the readers to[24]for a more completeversion of the same overview.For results before2006,thereaders are referred to[11]–[14].Specifically,this article reviews the recent research resultsin the following directions,which are not independent but actually may have overlapping to some extent:1.Consensus and the like(synchronization,rendezvous).Consensus refers to the group behavior that all theagents asymptotically reach a certain common agreementthrough a local distributed protocol,with or without predefined common speed and orientation.2.Distributed formation and the like(flocking).Distributedformation refers to the group behavior that all the agents form a pre-designed geometrical configuration throughlocal interactions with or without a common reference.3.Distributed optimization.This refers to algorithmic devel-opments for the analysis and optimization of large-scaledistributed systems.4.Distributed estimation and control.This refers to dis-tributed control design based on local estimation aboutthe needed global information.The rest of this article is organized as follows.In Section II,basic notations of graph theory and stochastic matrices are introduced.Sections III,IV,V,and VI describe the recentresearch results and progress in consensus,formation control, optimization,and estimation.Finally,the article is concludedby a short section of discussions with future perspectives.II.P RELIMINARIESA.Graph TheoryFor a system of n connected agents,its network topology can be modeled as a directed graph denoted by G=(V,W),where V={v1,v2,···,v n}and W⊆V×V are,respectively, the set of agents and the set of edges which directionallyconnect the agents together.Specifically,the directed edgedenoted by an ordered pair(v i,v j)means that agent j can access the state information of agent i.Accordingly,agent i is a neighbor of agent j.A directed path is a sequence of directed edges in the form of(v1,v2),(v2,v3),···,with all v i∈V.A directed graph has a directed spanning tree if there exists at least one agent that has a directed path to every other agent.The union of a set of directed graphs with the same setof agents,{G i1,···,G im},is a directed graph with the sameset of agents and its set of edges is given by the union of the edge sets of all the directed graphs G ij,j=1,···,m.A complete directed graph is a directed graph in which each pair of distinct agents is bidirectionally connected by an edge,thus there is a directed path from any agent to any other agent in the network.Two matrices are used to represent the network topology: the adjacency matrix A=[a ij]∈R n×n with a ij>0if (v j,v i)∈W and a ij=0otherwise,and the Laplacian matrix L=[ℓij]∈R n×n withℓii= n j=1a ij andℓij=−a ij,i=j, which is generally asymmetric for directed graphs.B.Stochastic MatricesA nonnegative square matrix is called(row)stochastic matrix if its every row is summed up to one.The product of two stochastic matrices is still a stochastic matrix.A row stochastic matrix P∈R n×n is called indecomposable and aperiodic if lim k→∞P k=1y T for some y∈R n[25],where 1is a vector with all elements being1.III.C ONSENSUSConsider a group of n agents,each with single-integrator kinematics described by˙x i(t)=u i(t),i=1,···,n,(1) where x i(t)and u i(t)are,respectively,the state and the control input of the i th agent.A typical consensus control algorithm is designed asu i(t)=nj=1a ij(t)[x j(t)−x i(t)],(2)where a ij(t)is the(i,j)th entry of the corresponding ad-jacency matrix at time t.The main idea behind(2)is that each agent moves towards the weighted average of the states of its neighbors.Given the switching network pattern due to the continuous motions of the dynamic agents,coupling coefficients a ij(t)in(2),hence the graph topologies,are generally time-varying.It is shown in[9],[10]that consensus is achieved if the underlying directed graph has a directed spanning tree in some jointly fashion in terms of a union of its time-varying graph topologies.The idea behind consensus serves as a fundamental principle for the design of distributed multi-agent coordination algo-rithms.Therefore,investigating consensus has been a main research direction in the study of distributed multi-agent co-ordination.To bridge the gap between the study of consensus algorithms and many physical properties inherited in practical systems,it is necessary and meaningful to study consensus by considering many practical factors,such as actuation,control, communication,computation,and vehicle dynamics,which characterize some important features of practical systems.This is the main motivation to study consensus.In the following part of the section,an overview of the research progress in the study of consensus is given,regarding stochastic network topologies and dynamics,complex dynamical systems,delay effects,and quantization,mainly after2006.Several milestone results prior to2006can be found in[2],[4]–[6],[8]–[10], [26].A.Stochastic Network Topologies and DynamicsIn multi-agent systems,the network topology among all vehicles plays a crucial role in determining consensus.The objective here is to explicitly identify necessary and/or suffi-cient conditions on the network topology such that consensus can be achieved under properly designed algorithms.It is often reasonable to consider the case when the network topology is deterministic under ideal communication chan-nels.Accordingly,main research on the consensus problem was conducted under a deterministicfixed/switching network topology.That is,the adjacency matrix A(t)is deterministic. Some other times,when considering random communication failures,random packet drops,and communication channel instabilities inherited in physical communication channels,it is necessary and important to study consensus problem in the stochastic setting where a network topology evolves according to some random distributions.That is,the adjacency matrix A(t)is stochastically evolving.In the deterministic setting,consensus is said to be achieved if all agents eventually reach agreement on a common state. In the stochastic setting,consensus is said to be achieved almost surely(respectively,in mean-square or in probability)if all agents reach agreement on a common state almost surely (respectively,in mean-square or with probability one).Note that the problem studied in the stochastic setting is slightly different from that studied in the deterministic setting due to the different assumptions in terms of the network topology. Consensus over a stochastic network topology was perhaps first studied in[27],where some sufficient conditions on the network topology were given to guarantee consensus with probability one for systems with single-integrator kinemat-ics(1),where the rate of convergence was also studied.Further results for consensus under a stochastic network topology were reported in[28]–[30],where research effort was conducted for systems with single-integrator kinematics[28],[29]or double-integrator dynamics[30].Consensus for single-integrator kine-matics under stochastic network topology has been exten-sively studied in particular,where some general conditions for almost-surely consensus was derived[29].Loosely speaking, almost-surely consensus for single-integrator kinematics can be achieved,i.e.,x i(t)−x j(t)→0almost surely,if and only if the expectation of the network topology,namely,the network topology associated with expectation E[A(t)],has a directed spanning tree.It is worth noting that the conditions are analogous to that in[9],[10],but in the stochastic setting. In view of the special structure of the closed-loop systems concerning consensus for single-integrator kinematics,basic properties of the stochastic matrices play a crucial role in the convergence analysis of the associated control algorithms. Consensus for double-integrator dynamics was studied in[30], where the switching network topology is assumed to be driven by a Bernoulli process,and it was shown that consensus can be achieved if the union of all the graphs has a directed spanning tree.Apparently,the requirement on the network topology for double-integrator dynamics is a special case of that for single-integrator kinematics due to the difference nature of thefinal states(constantfinal states for single-integrator kinematics and possible dynamicfinal states for double-integrator dynamics) caused by the substantial dynamical difference.It is still an open question as if some general conditions(corresponding to some specific algorithms)can be found for consensus with double-integrator dynamics.In addition to analyzing the conditions on the network topology such that consensus can be achieved,a special type of consensus algorithm,the so-called gossip algorithm[31],[32], has been used to achieve consensus in the stochastic setting. The gossip algorithm can always guarantee consensus almost surely if the available pairwise communication channels satisfy certain conditions(such as a connected graph).The way of network topology switching does not play any role in the consideration of consensus.The current study on consensus over stochastic network topologies has shown some interesting results regarding:(1) consensus algorithm design for various multi-agent systems,(2)conditions of the network topologies on consensus,and(3)effects of the stochastic network topologies on the con-vergence rate.Future research on this topic includes,but not limited to,the following two directions:(1)when the network topology itself is stochastic,how to determine the probability of reaching consensus almost surely?(2)compared with the deterministic network topology,what are the advantages and disadvantages of the stochastic network topology,regarding such as robustness and convergence rate?As is well known,disturbances and uncertainties often exist in networked systems,for example,channel noise,commu-nication noise,uncertainties in network parameters,etc.In addition to the stochastic network topologies discussed above, the effect of stochastic disturbances[33],[34]and uncertain-ties[35]on the consensus problem also needs investigation. Study has been mainly devoted to analyzing the performance of consensus algorithms subject to disturbances and to present-ing conditions on the uncertainties such that consensus can be achieved.In addition,another interesting direction in dealing with disturbances and uncertainties is to design distributed localfiltering algorithms so as to save energy and improve computational efficiency.Distributed localfiltering algorithms play an important role and are more effective than traditional centralizedfiltering algorithms for multi-agent systems.For example,in[36]–[38]some distributed Kalmanfilters are designed to implement data fusion.In[39],by analyzing consensus and pinning control in synchronization of complex networks,distributed consensusfiltering in sensor networks is addressed.Recently,Kalmanfiltering over a packet-dropping network is designed through a probabilistic approach[40]. Today,it remains a challenging problem to incorporate both dynamics of consensus and probabilistic(Kalman)filtering into a unified framework.plex Dynamical SystemsSince consensus is concerned with the behavior of a group of vehicles,it is natural to consider the system dynamics for practical vehicles in the study of the consensus problem. Although the study of consensus under various system dynam-ics is due to the existence of complex dynamics in practical systems,it is also interesting to observe that system dynamics play an important role in determining thefinal consensus state.For instance,the well-studied consensus of multi-agent systems with single-integrator kinematics often converges to a constantfinal value instead.However,consensus for double-integrator dynamics might admit a dynamicfinal value(i.e.,a time function).These important issues motivate the study of consensus under various system dynamics.As a direct extension of the study of the consensus prob-lem for systems with simple dynamics,for example,with single-integrator kinematics or double-integrator dynamics, consensus with general linear dynamics was also studied recently[41]–[43],where research is mainly devoted tofinding feedback control laws such that consensus(in terms of the output states)can be achieved for general linear systems˙x i=Ax i+Bu i,y i=Cx i,(3) where A,B,and C are constant matrices with compatible sizes.Apparently,the well-studied single-integrator kinematics and double-integrator dynamics are special cases of(3)for properly choosing A,B,and C.As a further extension,consensus for complex systems has also been extensively studied.Here,the term consensus for complex systems is used for the study of consensus problem when the system dynamics are nonlinear[44]–[48]or with nonlinear consensus algorithms[49],[50].Examples of the nonlinear system dynamics include:•Nonlinear oscillators[45].The dynamics are often as-sumed to be governed by the Kuramoto equation˙θi=ωi+Kstability.A well-studied consensus algorithm for(1)is given in(2),where it is now assumed that time delay exists.Two types of time delays,communication delay and input delay, have been considered in the munication delay accounts for the time for transmitting information from origin to destination.More precisely,if it takes time T ij for agent i to receive information from agent j,the closed-loop system of(1)using(2)under afixed network topology becomes˙x i(t)=nj=1a ij(t)[x j(t−T ij)−x i(t)].(7)An interpretation of(7)is that at time t,agent i receives information from agent j and uses data x j(t−T ij)instead of x j(t)due to the time delay.Note that agent i can get its own information instantly,therefore,input delay can be considered as the summation of computation time and execution time. More precisely,if the input delay for agent i is given by T p i, then the closed-loop system of(1)using(2)becomes˙x i(t)=nj=1a ij(t)[x j(t−T p i)−x i(t−T p i)].(8)Clearly,(7)refers to the case when only communication delay is considered while(8)refers to the case when only input delay is considered.It should be emphasized that both communication delay and input delay might be time-varying and they might co-exist at the same time.In addition to time delay,it is also important to consider packet drops in exchanging state information.Fortunately, consensus with packet drops can be considered as a special case of consensus with time delay,because re-sending packets after they were dropped can be easily done but just having time delay in the data transmission channels.Thus,the main problem involved in consensus with time delay is to study the effects of time delay on the convergence and performance of consensus,referred to as consensusabil-ity[52].Because time delay might affect the system stability,it is important to study under what conditions consensus can still be guaranteed even if time delay exists.In other words,can onefind conditions on the time delay such that consensus can be achieved?For this purpose,the effect of time delay on the consensusability of(1)using(2)was investigated.When there exists only(constant)input delay,a sufficient condition on the time delay to guarantee consensus under afixed undirected interaction graph is presented in[8].Specifically,an upper bound for the time delay is derived under which consensus can be achieved.This is a well-expected result because time delay normally degrades the system performance gradually but will not destroy the system stability unless the time delay is above a certain threshold.Further studies can be found in, e.g.,[53],[54],which demonstrate that for(1)using(2),the communication delay does not affect the consensusability but the input delay does.In a similar manner,consensus with time delay was studied for systems with different dynamics, where the dynamics(1)are replaced by other more complex ones,such as double-integrator dynamics[55],[56],complex networks[57],[58],rigid bodies[59],[60],and general nonlinear dynamics[61].In summary,the existing study of consensus with time delay mainly focuses on analyzing the stability of consensus algo-rithms with time delay for various types of system dynamics, including linear and nonlinear dynamics.Generally speaking, consensus with time delay for systems with nonlinear dynam-ics is more challenging.For most consensus algorithms with time delays,the main research question is to determine an upper bound of the time delay under which time delay does not affect the consensusability.For communication delay,it is possible to achieve consensus under a relatively large time delay threshold.A notable phenomenon in this case is that thefinal consensus state is constant.Considering both linear and nonlinear system dynamics in consensus,the main tools for stability analysis of the closed-loop systems include matrix theory[53],Lyapunov functions[57],frequency-domain ap-proach[54],passivity[58],and the contraction principle[62]. Although consensus with time delay has been studied extensively,it is often assumed that time delay is either constant or random.However,time delay itself might obey its own dynamics,which possibly depend on the communication distance,total computation load and computation capability, etc.Therefore,it is more suitable to represent the time delay as another system variable to be considered in the study of the consensus problem.In addition,it is also important to consider time delay and other physical constraints simultaneously in the study of the consensus problem.D.QuantizationQuantized consensus has been studied recently with motiva-tion from digital signal processing.Here,quantized consensus refers to consensus when the measurements are digital rather than analog therefore the information received by each agent is not continuous and might have been truncated due to digital finite precision constraints.Roughly speaking,for an analog signal s,a typical quantizer with an accuracy parameterδ, also referred to as quantization step size,is described by Q(s)=q(s,δ),where Q(s)is the quantized signal and q(·,·) is the associated quantization function.For instance[63],a quantizer rounding a signal s to its nearest integer can be expressed as Q(s)=n,if s∈[(n−1/2)δ,(n+1/2)δ],n∈Z, where Z denotes the integer set.Note that the types of quantizers might be different for different systems,hence Q(s) may differ for different systems.Due to the truncation of the signals received,consensus is now considered achieved if the maximal state difference is not larger than the accuracy level associated with the whole system.A notable feature for consensus with quantization is that the time to reach consensus is usuallyfinite.That is,it often takes afinite period of time for all agents’states to converge to an accuracy interval.Accordingly,the main research is to investigate the convergence time associated with the proposed consensus algorithm.Quantized consensus was probablyfirst studied in[63], where a quantized gossip algorithm was proposed and its convergence was analyzed.In particular,the bound of theconvergence time for a complete graph was shown to be poly-nomial in the network size.In[64],coding/decoding strate-gies were introduced to the quantized consensus algorithms, where it was shown that the convergence rate depends on the accuracy of the quantization but not the coding/decoding schemes.In[65],quantized consensus was studied via the gossip algorithm,with both lower and upper bounds of the expected convergence time in the worst case derived in terms of the principle submatrices of the Laplacian matrix.Further results regarding quantized consensus were reported in[66]–[68],where the main research was also on the convergence time for various proposed quantized consensus algorithms as well as the quantization effects on the convergence time.It is intuitively reasonable that the convergence time depends on both the quantization level and the network topology.It is then natural to ask if and how the quantization methods affect the convergence time.This is an important measure of the robustness of a quantized consensus algorithm(with respect to the quantization method).Note that it is interesting but also more challenging to study consensus for general linear/nonlinear systems with quantiza-tion.Because the difference between the truncated signal and the original signal is bounded,consensus with quantization can be considered as a special case of one without quantization when there exist bounded disturbances.Therefore,if consensus can be achieved for a group of vehicles in the absence of quantization,it might be intuitively correct to say that the differences among the states of all vehicles will be bounded if the quantization precision is small enough.However,it is still an open question to rigorously describe the quantization effects on consensus with general linear/nonlinear systems.E.RemarksIn summary,the existing research on the consensus problem has covered a number of physical properties for practical systems and control performance analysis.However,the study of the consensus problem covering multiple physical properties and/or control performance analysis has been largely ignored. In other words,two or more problems discussed in the above subsections might need to be taken into consideration simul-taneously when studying the consensus problem.In addition, consensus algorithms normally guarantee the agreement of a team of agents on some common states without taking group formation into consideration.To reflect many practical applications where a group of agents are normally required to form some preferred geometric structure,it is desirable to consider a task-oriented formation control problem for a group of mobile agents,which motivates the study of formation control presented in the next section.IV.F ORMATION C ONTROLCompared with the consensus problem where thefinal states of all agents typically reach a singleton,thefinal states of all agents can be more diversified under the formation control scenario.Indeed,formation control is more desirable in many practical applications such as formationflying,co-operative transportation,sensor networks,as well as combat intelligence,surveillance,and reconnaissance.In addition,theperformance of a team of agents working cooperatively oftenexceeds the simple integration of the performances of all individual agents.For its broad applications and advantages,formation control has been a very active research subject inthe control systems community,where a certain geometric pattern is aimed to form with or without a group reference.More precisely,the main objective of formation control is to coordinate a group of agents such that they can achievesome desired formation so that some tasks can befinished bythe collaboration of the agents.Generally speaking,formation control can be categorized according to the group reference.Formation control without a group reference,called formationproducing,refers to the algorithm design for a group of agents to reach some pre-desired geometric pattern in the absenceof a group reference,which can also be considered as the control objective.Formation control with a group reference,called formation tracking,refers to the same task but followingthe predesignated group reference.Due to the existence of the group reference,formation tracking is usually much morechallenging than formation producing and control algorithmsfor the latter might not be useful for the former.As of today, there are still many open questions in solving the formationtracking problem.The following part of the section reviews and discussesrecent research results and progress in formation control, including formation producing and formation tracking,mainlyaccomplished after2006.Several milestone results prior to 2006can be found in[69]–[71].A.Formation ProducingThe existing work in formation control aims at analyzingthe formation behavior under certain control laws,along with stability analysis.1)Matrix Theory Approach:Due to the nature of multi-agent systems,matrix theory has been frequently used in thestability analysis of their distributed coordination.Note that consensus input to each agent(see e.g.,(2))isessentially a weighted average of the differences between the states of the agent’s neighbors and its own.As an extensionof the consensus algorithms,some coupling matrices wereintroduced here to offset the corresponding control inputs by some angles[72],[73].For example,given(1),the controlinput(2)is revised as u i(t)= n j=1a ij(t)C[x j(t)−x i(t)], where C is a coupling matrix with compatible size.If x i∈R3, then C can be viewed as the3-D rotational matrix.The mainidea behind the revised algorithm is that the original controlinput for reaching consensus is now rotated by some angles. The closed-loop system can be expressed in a vector form, whose stability can be determined by studying the distribution of the eigenvalues of a certain transfer matrix.Main research work was conducted in[72],[73]to analyze the collective motions for systems with single-integrator kinematics and double-integrator dynamics,where the network topology,the damping gain,and C were shown to affect the collective motions.Analogously,the collective motions for a team of nonlinear self-propelling agents were shown to be affected by。
尊重共担当的英语作文

Respecting and sharing responsibilities are fundamental values that underpin a harmonious society.In our daily lives,we encounter various situations where these principles come into play,shaping our interactions with others and contributing to a collective sense of wellbeing.First and foremost,respecting others is about acknowledging their rights,opinions,and feelings.It involves listening actively,being empathetic,and treating everyone with dignity.When we respect others,we create an environment where people feel valued and heard,which is essential for building trust and fostering positive relationships.Sharing responsibilities,on the other hand,is about recognizing that we all have a part to play in maintaining the social fabric.This can be seen in the way we contribute to our families,communities,and workplaces.By taking ownership of our actions and their consequences,we demonstrate a sense of accountability that encourages others to do the same.In a family setting,respect and shared responsibility are crucial for maintaining a healthy and supportive atmosphere.Parents who respect their childrens individuality and listen to their opinions create a nurturing environment where children feel safe to express themselves.Similarly,when family members share chores and responsibilities,it teaches the importance of teamwork and cooperation.In the workplace,respecting colleagues and sharing workloads can lead to a more efficient and collaborative environment.When employees feel respected,they are more likely to be engaged and motivated,contributing to the overall success of the organization. Sharing responsibilities also ensures that tasks are distributed fairly,preventing burnout and promoting a sense of fairness.In the broader community,respect and shared responsibility are vital for social cohesion. Citizens who respect the rights and opinions of others,regardless of their background, help to create an inclusive society.Sharing responsibilities,such as participating in community projects or volunteering,strengthens social bonds and contributes to the common good.Moreover,respecting and sharing responsibilities on a global scale is essential for addressing pressing issues like climate change,poverty,and inequality.International cooperation and mutual respect among nations can lead to more effective solutions and a more sustainable future for all.In conclusion,respecting others and sharing responsibilities are not just personal virtuesbut also societal needs.They are the building blocks of a harmonious and just world, where everyone has a role to play and a stake in the outcome.By embracing these values, we can create a society that is more understanding,supportive,and resilient.。
team work英语作文

Teamwork, an integral part of any successful endeavor, holds the key to achieving high-quality outcomes. It involves a group of individuals working together towards a common goal, leveraging their diverse skills and perspectives to create a cohesive and efficient team. In today's world, where complex problems require multifaceted solutions, the importance of teamwork cannot be overstated.One of the fundamental aspects of teamwork is the sharing of ideas and perspectives. When individuals from different backgrounds and experiences come together, they bring a unique set of insights and perspectives to the table. This diversity of thought leads to a richer and more comprehensive understanding of the problem at hand. It allows the team to identify potential blind spots and consider a wider range of solutions.Moreover, teamwork fosters a sense of collective responsibility and accountability. Each member of the team feels a sense of ownership over the project and is committed to its success. This shared responsibility ensures that everyone is pulling their weight and contributing to the best of their abilities. It also creates a sense of mutual support and encouragement, where team members are more likely to offer help and feedback when needed.The ability to communicate effectively is crucial in teamwork. Clear and concise communication ensures that everyone is on the same page and understands their roles and responsibilities. It also helps to resolve conflicts and misunderstandings quickly, preventing them from escalating into bigger issues. Effective communication also enhances the flow of information within the team, allowing ideas and feedback to be shared freely and openly.Another key aspect of teamwork is the ability to delegate tasks and manage resources effectively. A skilled team leader will identify the strengths and weaknesses of each team member and assign tasks accordingly. This ensures that the workload is distributed evenly and that each member is able to contribute to their full potential. Effective resource management also ensures that the team has the necessary tools and support to complete the project efficiently.Moreover, teamwork fosters a culture of learning and continuous improvement.As team members work together, they have the opportunity to learn from each other's successes and failures. This shared learning experience not only enhances individual skills but also strengthens the team's overall performance. It allows the team to adapt to changing circumstances and improve its processes over time.In addition to these benefits, teamwork also enhances creativity and innovation. When individuals work together, they are able to generate new ideas and solutions that might not have occurred to them individually. The collective brainpower of the team can lead to breakthrough ideas and innovative approaches that can significantly improve the quality of the outcomes.However, it is important to note that teamwork is not always easy. Conflicts and differences of opinion can arise, and it takes effort and commitment to overcome these challenges. Successful teams are those that are able to navigate through these difficulties and find common ground, focusing on the bigger picture and the shared goal.In conclusion, teamwork is a powerful tool that can lead to high-quality outcomes. It leverages the diverse skills and perspectives of individuals, fosters a sense of collective responsibility, enhances communication, and fosters a culture of learning and improvement. While it may present challenges, the benefits of teamwork far outweigh the difficulties. By working together towards a common goal, teams can achieve remarkable success and create lasting impact.。
teamwork英语作文

teamwork英语作文In today's fast-paced world, the ability to work effectively as part of a team is more important than ever. Teamwork is the secret ingredient that can turn a group of individuals into a cohesive and successful unit. It is the glue that binds people together, allowing them to achieve goals that would be impossible on their own.Understanding the Concept of TeamworkTeamwork is defined as the collaborative effort of a group to achieve a common goal or complete a task in the mosteffective and efficient way. It involves clear communication, mutual respect, and the understanding that each member of the team has a vital role to play.Benefits of Teamwork1. Enhanced Problem Solving: When diverse perspectives come together, they can generate more innovative solutions to problems.2. Increased Motivation: Team members often feel more motivated knowing they are part of a collective effort.3. Shared Workload: Tasks can be distributed among team members, reducing the burden on any single individual.4. Learning from Each Other: Teamwork provides an opportunity for individuals to learn from the skills and experiences of others.Challenges in TeamworkDespite its benefits, teamwork can also present challenges:1. Conflict Resolution: Disagreements can arise, and it's crucial to address them constructively.2. Coordination: Ensuring that all team members are working towards the same goal can be difficult.3. Dependency: Over-reliance on certain team members can lead to inefficiencies if those individuals are unavailable.Tips for Successful Teamwork1. Establish Clear Roles: Each team member should understand their responsibilities.2. Communicate Openly: Regular and open communication is key to a successful team dynamic.3. Trust and Respect: Trust your teammates and show them respect; this fosters a positive environment.4. Be Flexible: Be willing to adapt to changes and take on different roles as needed.ConclusionTeamwork is an essential skill in both professional and personal settings. It requires patience, cooperation, and a willingness to compromise. When done right, it can lead to remarkable achievements and a sense of camaraderie that is hard to find in individual endeavors. Embracing teamwork canunlock a group's full potential and lead to success beyond what each member could accomplish alone.。
集体的重要性和意义英语作文

The Vital Importance and Significance ofCollectivismIn the tapestry of human society, the thread of collectivism stands out as a vital and indispensable element. Its importance and significance are manifest in various aspects of our lives, from the smallest communities to the largest nations. The essence of collectivism lies in the belief that the welfare and interests of the group are paramount, surpassing the interests of the individual. This belief finds expression in various forms, such as cooperation, solidarity, and the sharing of resources and responsibilities.Firstly, collectivism fosters a sense of belonging and unity among members of a group. When individuals feel that their actions and efforts are part of a larger, shared objective, they are more likely to identify with the group and contribute their best. This sense of belonging not only enhances the cohesion and stability of the group but also acts as a powerful motivator, driving individuals to excel and achieve beyond their individual capabilities.Secondly, collectivism promotes cooperation and collaboration, which are essential for the achievement of complex tasks and goals. In a collectivist culture, individuals are encouraged to work together, pooling their resources, talents, and knowledge to achieve common objectives. This approach not only enhances efficiency and productivity but also fosters a spirit of mutual respectand understanding among group members.Moreover, collectivism plays a pivotal role in the distribution of resources and responsibilities within a group. By emphasizing the collective welfare, collectivism ensures that resources are allocated fairly and efficiently, meeting the needs of all members. Similarly,responsibilities are shared equitably, ensuring that the burden is not borne by a few but distributed across the entire group. This approach not only ensures the smooth functioning of the group but also cultivates a sense of responsibility and accountability among its members.Collectivism also plays a crucial role in the socialization process, shaping the values, attitudes, and behaviors of individuals. In a collectivist society,children are taught from a young age to value cooperation, solidarity, and the welfare of the group above all else. This socialization process not only prepares them to become responsible and contributing members of society but also helps them develop a sense of empathy and compassion for others.In conclusion, the importance and significance of collectivism cannot be overstated. It is a fundamentalsocial principle that underpins the stability, cohesion,and progress of any group or society. By fostering a senseof belonging, promoting cooperation and collaboration, ensuring fair distribution of resources andresponsibilities, and shaping the values and attitudes of individuals, collectivism acts as a powerful force for unity, harmony, and development.**集体的重要性和意义**在人类社会的织锦画卷中,集体主义这一线条显得格外重要且不可或缺。
团体工作英语作文

团体工作英语作文In today's fast-paced and competitive world, the ability to work effectively in a group is not just a soft skill; it is a necessity. Teamwork is the secret sauce that can transform a group of individuals into a cohesive unit capable of achieving remarkable feats. This essay will explore the importance of teamwork, its benefits, and how it can be harnessed to achieve success.Understanding TeamworkTeamwork is the collaborative effort of a group to achieve a common goal or to complete a task in the most efficient way. It involves clear communication, mutual respect, and the sharing of responsibilities and rewards. Each member of the team plays a unique role, and their combined skills and efforts contribute to the overall success of the project.Benefits of Teamwork1. Diverse Perspectives: A team with members from different backgrounds brings a range of perspectives, which can lead to more innovative and effective solutions.2. Shared Workload: Tasks can be distributed among team members, reducing the pressure on any single individual and allowing for larger projects to be tackled.3. Increased Motivation: Working in a team can boost motivation as members encourage and support each other, fostering a positive work environment.4. Learning Opportunities: Team members can learn from each other's experiences and expertise, leading to personal and professional growth.5. Better Decision Making: Group discussions can lead to more thorough analysis and better decision-making, as different viewpoints are considered.Challenges in TeamworkDespite its benefits, teamwork can also present challenges:1. Conflicts: Disagreements can arise due to differences in opinion or working styles.2. Coordination: Ensuring that all team members are on the same page and working towards the same goal can be difficult.3. Responsibility: There can be a tendency for some members to rely on others, leading to an uneven distribution of work.Strategies for Effective Teamwork1. Clear Goals: Establishing clear objectives and roles for each team member is crucial.2. Communication: Open and honest communication is key toresolving conflicts and ensuring everyone is informed.3. Trust and Respect: Building trust among team members and showing respect for each other's contributions can create a strong team dynamic.4. Leadership: Effective leadership can guide the team, motivate members, and help to keep the team focused on its goals.5. Evaluation: Regularly reviewing the team's progress and providing constructive feedback can help to improve performance.ConclusionTeamwork is an essential component of success in both professional and personal spheres. It allows for the pooling of resources, skills, and ideas, leading to more robust and creative outcomes. By understanding the principles of effective teamwork and implementing strategies to overcomeits challenges, any group can become a high-performing team capable of achieving its goals. The power of teamwork lies not in the strength of each individual but in the combined strength of all its members working together towards a common vision.。
有关众人拾柴火焰高的英语相关范文

有关众人拾柴火焰高的英语相关范文The proverb "many hands make light work" is a well-known saying that emphasizes the power of collective effort and cooperation. This ancient wisdom speaks to the idea that when people work together towards a common goal, the task at hand becomes significantly easier and more manageable. This principle has profound implications for how we approach challenges both in our personal lives and in the broader social and professional realms.At its core, the proverb "many hands make light work" reflects a fundamental truth about human nature and the nature of work itself. As social creatures, we are innately wired to collaborate and support one another. When we pool our resources, skills, and efforts, we are able to accomplish far more than we ever could alone. This is because each individual brings a unique perspective, set of abilities, and energy to the table, and by combining these elements, the workload becomes exponentially lighter.In a practical sense, this proverb is applicable to a wide range of scenarios. Consider, for example, a large-scale construction project. Ifa single individual were tasked with erecting an entire building, the undertaking would be daunting, if not outright impossible. However, when a team of skilled workers, each with their own specialized roles, come together to tackle the project, the work becomes far more manageable. By dividing the labor and capitalizing on the strengths of each team member, the construction process becomes streamlined and efficient.The same principle holds true in our personal lives as well. Imagine a family tackling the chore of cleaning their home. If one person were solely responsible for scrubbing floors, dusting surfaces, doing laundry, and organizing closets, the task would quickly become overwhelming. But when each family member takes on a specific responsibility, the workload is distributed, and the job is completed in a fraction of the time.Moreover, the proverb "many hands make light work" extends beyond the realm of physical labor. It is equally applicable to intellectual and creative endeavors. When a group of people with diverse backgrounds and expertise collaborate on a project, the result is often more innovative, comprehensive, and effective than what a single individual could have produced. By drawing upon a collective pool of knowledge, ideas, and perspectives, complex problems can be solved more efficiently, and ambitious goals can be achieved more readily.In the realm of problem-solving, the power of collective effort is particularly evident. When faced with a daunting challenge, it is often tempting to try to tackle it alone, believing that we can find the solution through sheer force of will and individual ingenuity. However, this approach can be shortsighted and ultimately less effective. By enlisting the help of others, we can leverage a wider range of expertise, experiences, and creative thinking to arrive at more comprehensive and sustainable solutions.Furthermore, the proverb "many hands make light work" speaks to the importance of fostering a sense of community and shared responsibility. When individuals come together in a spirit of collaboration and mutual support, they not only accomplish more, but they also cultivate a deeper sense of belonging and purpose. This, in turn, can have far-reaching implications for individual and societal well-being, as people feel empowered, valued, and connected to a larger purpose.In conclusion, the proverb "many hands make light work" is a profound and timeless piece of wisdom that holds immense relevance in our modern world. By embracing the power of collective effort and cooperation, we can tackle even the most daunting challenges with greater ease and efficiency. Whether in our personal lives, our professional pursuits, or our broader social endeavors, theprinciple of "many hands make light work" serves as a guiding light, reminding us that by working together, we can achieve far more than we ever could alone.。
理解共发展的英语作文

Understanding mutual development is a concept that has gained significant importance in todays globalized world.It emphasizes the idea that progress and growth should not be limited to a single entity but should be shared among all stakeholders involved.This essay will explore the essence of mutual development,its benefits,and the challenges faced in achieving it.The Essence of Mutual DevelopmentMutual development is based on the principle that when different entities,whether they are individuals,organizations,or nations,work together towards a common goal,they can achieve more than they would independently.It is about creating a symbiotic relationship where each party contributes and benefits from the collective effort.Benefits of Mutual Development1.Enhanced Efficiency:By pooling resources and expertise,mutual development allows for more efficient use of available assets,leading to better outcomes.2.Innovation:Collaboration fosters an environment where new ideas can be exchanged, leading to innovation and the development of novel solutions to existing problems.3.Sustainability:Mutual development promotes sustainable growth by ensuring that the benefits of progress are distributed equitably,reducing the likelihood of resource depletion and environmental harm.4.Economic Growth:When multiple parties contribute to a project or initiative,the potential for economic growth is increased,as the combined efforts can lead to larger markets and more significant opportunities.5.Social Cohesion:Working together towards shared goals can strengthen social bonds and promote understanding among diverse groups,leading to a more cohesive society. Challenges in Achieving Mutual Development1.Divergent Interests:One of the primary challenges is aligning the interests of all parties involved.What benefits one may not necessarily benefit another,leading to potential conflicts.2.Resource Allocation:Deciding how to fairly distribute resources can be difficult, especially when there are limited resources and high demand.3.Cultural Differences:Mutual development requires understanding and respecting cultural differences,which can be challenging when working across different societies or regions.4.Power Imbalances:There may be power imbalances between parties,which can lead to one party dominating the decisionmaking process and potentially undermining the mutual aspect of development.ck of Trust:Building trust is crucial for mutual development,but it can be difficult to establish,especially in competitive environments.ConclusionMutual development is a complex yet rewarding approach to progress.It requires a commitment to collaboration,understanding,and respect for the contributions of all parties involved.While there are challenges to overcome,the potential benefits of enhanced efficiency,innovation,sustainability,economic growth,and social cohesion make it a worthwhile pursuit.As the world becomes increasingly interconnected,the importance of mutual development will only grow,making it a critical concept for the future.。
互助的蚂蚁蚂蚁英文作文

互助的蚂蚁蚂蚁英文作文回答例子1:Title: The Ants of Mutual Aid: An Essay on CooperationIn the intricate tapestry of nature, the tiny ant emerges as a paragon of cooperation and mutual aid. Despite their diminutive size, ants exhibit remarkable social behavior that centers around the collective well-being of their colony. From foraging for food to defending their nest, ants exemplify the power of collaboration and solidarity. In this essay, we delve into the fascinating world of ants, exploring how their mutual aid strategies can inspire and inform human societies.Ant societies are structured around a division of labor that maximizes efficiency and ensures survival. Within a colony, individuals are assigned specific roles based on their capabilities and the needs of the group. For instance, worker ants diligently gather food, nurse the young, and maintain the nest, while soldier ants defend against threats and intruders. This division of labor not only optimizes productivity but also fosters interdependence among colony members.Central to the success of ant colonies is the principle of mutual aid, where individuals cooperate for the greater good of the community. Unlike some species where competition reigns supreme, ants prioritize collective well-being over individual gain. When a worker ant discovers a source of food, it communicates its findings to others through intricate chemical trails, allowing fellow workers to join in the harvest. This collaborative foraging behavior ensures that resources are efficiently utilized and distributed among the colony.Moreover, ants display remarkable altruism towards their fellow colony members, often sacrificing their own well-being for the common good. In times of scarcity or danger, ants exhibit solidarity by sharing food resources and defending the nest as a unified front. This selfless behavior reflects adeep-seated sense of community and cooperation ingrained within ant societies.The concept of mutual aid extends beyond immediate survival tasks to encompass collective problem-solving and innovation. Ants employ sophisticated strategies to overcomechallenges such as navigating complex terrain, building intricate nests, and combating predators. Through communication and collaboration, ants are able to adapt and thrive in diverse environments, showcasing the power of collective intelligence.Furthermore, ant colonies demonstrate resilience in the face of adversity through their ability to recover and rebuild after disturbances. Whether facing natural disasters or human disturbances, ants exhibit remarkable adaptability and resilience, driven by their innate sense of solidarity and mutual support. This resilience stems from the interconnectedness and cohesion of the colony, where individuals work together towards common goals.The lessons gleaned from the world of ants hold profound implications for human societies striving to address pressing challenges such as climate change, resource scarcity, and social inequality. By embracing the principles of mutual aid and cooperation, humans can build more resilient and sustainable communities that prioritize collective well-being over individual interests. Just as ants thrive throughcollaboration and solidarity, so too can humanity forge a brighter future by working together towards common goals.In conclusion, the ants' paradigm of mutual aid serves as a powerful reminder of the transformative potential of cooperation and solidarity. From their division of labor to their altruistic behavior, ants exemplify the virtues of collective action in the face of adversity. As we navigate the complexities of the modern world, let us draw inspiration from the humble ant and strive to build societies founded on mutual aid, empathy, and collaboration. In doing so, we can create a more harmonious and resilient world for generations to come.回答例子2:Title: The Ants of Cooperation: An Essay on Mutual AidIn the vast world of nature, amidst the bustling activities and intricate ecosystems, lies a tiny yet remarkable creature - the ant. Despite its diminutive size, the ant embodies the essence of cooperation and mutual aid, serving as a profound example of unity and collective effort. In this essay, we delve into the world of ants to explore the dynamics of their social structure, the mechanisms of their cooperation, and thelessons they impart to humanity.Ant colonies are marvels of organization, comprising thousands, even millions, of individuals working tirelessly towards a common goal. Each member of the colony plays a specific role, whether it be foraging for food, tending to the young, defending the nest, or constructing elaborate tunnels and chambers. Through division of labor and coordination, ants achieve feats that seem inconceivable for creatures of their size.Central to the success of ant colonies is the principle of mutual aid. Ants understand the importance of collaboration and selflessness, recognizing that by helping one another, they ensure the survival and prosperity of the entire colony. This spirit of cooperation is evident in various aspects of ant behavior, from cooperative hunting and food sharing to collective defense against predators and rival colonies.One remarkable example of mutual aid among ants is seen in their sophisticated communication systems. Through the use of pheromones, vibrations, and even sound signals, antsare able to convey vital information to their fellow colony members, alerting them to food sources, danger, and opportunities for expansion. This seamless exchange of information facilitates efficient decision-making and enhances the collective intelligence of the colony.Moreover, ants display remarkable adaptability and resilience in the face of adversity. When confronted with challenges such as food scarcity, environmental changes, or threats from predators, ants demonstrate remarkable problem-solving abilities and a willingness to collaborate for the greater good. Through collective effort and ingenuity, they are able to overcome obstacles and thrive in even the most challenging conditions.The lessons of mutual aid and cooperation imparted by ants are not confined to the realm of nature; they hold profound relevance for human society as well. In an increasingly interconnected and interdependent world, the importance of collaboration and solidarity cannot be overstated. Just as ants rely on each other for survival and prosperity, so too must humanity recognize the value ofmutual aid in addressing the complex challenges we face, from climate change and global poverty to political unrest and pandemics.In conclusion, the ants exemplify the power of cooperation and mutual aid in achieving common goals and overcoming adversity. By studying the social structure, behaviors, and strategies of ants, we gain valuable insights into the dynamics of cooperation and the importance of collective action. As we navigate the complexities of the modern world, let us heed the lessons of the ants and strive to build a society founded on principles of solidarity, compassion, and mutual support.。
关于经济贸易的英语

关于经济贸易的英语In the intricate web of global affairs, economic trade stands as a pivotal strand, connecting nations andfostering mutual growth. It is a multifaceted phenomenon, encompassing diverse activities, ranging from the exchange of goods and services to the intricate negotiations of trade agreements and policies. The significance of economic trade lies not only in its contribution to economic growth but also in its ability to foster cultural exchange and political stability.The contemporary landscape of economic trade is marked by a series of interlocking trends and forces. Technological advancements, particularly in the fields of transportation and communication, have revolutionized the way trade is conducted, making it faster, more efficient, and more inclusive. The emergence of digital trade platforms has enabled small and medium-sized enterprises (SMEs) to participate in global trade, broadening the scope and impact of trade activities.Moreover, the globalization of production has led to the emergence of complex supply chains, with variouscomponents and stages of production being distributed across multiple countries. This trend has not only increased the efficiency of production but also made countries more dependent on each other for their economic well-being. The interconnectedness of global economies has also given rise to new challenges, such as the management of trade imbalances and the mitigation of the negative effects of economic shocks.The role of trade agreements and policies in shaping the landscape of economic trade cannot be overstated. Trade agreements, such as the World Trade Organization (WTO) and regional trade blocs like the European Union (EU), have established a framework for the conduct of trade, promoting fairness and transparency. However, the negotiation and implementation of these agreements are often fraught with political and economic considerations, reflecting the complex interplay of national interests and global objectives.In addition, the rise of protectionist policies in some countries has posed a challenge to the open and inclusive nature of global trade. While these policies may bemotivated by domestic political and economic considerations, they often have negative spillover effects on other countries, disrupting supply chains and undermining the benefits of trade.Amidst these challenges, the future of economic trade remains uncertain yet promising. The ongoing digital revolution, coupled with advancements in artificial intelligence and blockchain technology, is likely tofurther transform the way trade is conducted. These technologies have the potential to streamline trade processes, enhance transparency, and reduce costs, thus making trade more accessible and inclusive.Moreover, the increasing awareness of the environmental impact of trade activities is likely to lead to theadoption of more sustainable trade practices. This shift towards green trade will not only mitigate the negative environmental effects of trade but also create new economic opportunities in the fields of renewable energy and environmental technologies.In conclusion, economic trade remains a critical component of global affairs, shaping the economic, cultural,and political landscapes of nations. While it faces numerous challenges, the potential for growth and innovation remains vast. As we navigate the complexities and dynamism of economic trade, it is imperative that we strive for a balance between national interests and global objectives, fostering a trade environment that is fair, inclusive, and sustainable.**经济贸易的复杂性与动态性**在全球事务的纷繁复杂中,经济贸易作为关键的一环,连接着各国,促进着相互间的增长。
战胜疫情的英语作文80词

战胜疫情的英语作文80词篇1During the pandemic, it was truly a challenging time for all of us. I remember those days clearly. I was stuck at home, but my determination to learn never wavered. Despite the difficulties, I kept studying every day. There were times when I felt frustrated because the online classes weren't as smooth as I hoped. But I told myself, "How can I give up? I must keep going!"I also witnessed the selfless dedication of the volunteers around me. They worked tirelessly, delivering daily necessities to every household. Their efforts were like a beam of light in the darkness. How could we not be moved? How could we not be inspired?I firmly believe that as long as we all stay united and determined, we will surely overcome this pandemic! We can do it!篇2During the pandemic, our community showed an extraordinary spirit of unity and mutual assistance. It was a time filled with challenges and uncertainties, but we stood together. We distributed essential supplies to each other. Neighbors who were previously just familiar faces now became close friends, sharing food and protective items. We encouraged one another constantly. "Don't worry! We will get through this together!" wasthe common refrain. The community also organized online activities to enrich our lives. We had virtual fitness classes, art competitions, and story-telling sessions. How wonderful it was! Everyone participated actively. Wasn't this the power of unity? Could anything stop us when we were united like this? We firmly believed that we would overcome the pandemic and return to our normal lives. Yes, we did it! With love and support, we triumphed over the difficulties.篇3During these challenging times of the epidemic, the dedication and bravery of our medical workers have been nothing short of extraordinary! How can we forget that doctor who worked tirelessly for hours on end, disregarding his own exhaustion? He was there, day and night, fighting against the unseen enemy to save lives. And what about the teams of medical experts who were constantly working to develop a vaccine? Their efforts were like a beacon of hope in the darkness.The spirit of these heroes is truly inspiring! They faced the unknown with courage and determination. They put others' lives before their own, without a moment's hesitation. Isn't this the true essence of humanity?With such selfless warriors on the front line, how can we not have faith in defeating this epidemic? We must believe that together, we will overcome this difficult period and emerge stronger than ever before. Let us all show our gratitude and support to these amazing heroes!篇4During the pandemic, our lives underwent tremendous changes. My family's lifestyle shifted dramatically. We used to have frequent outings and gatherings, but now we stayed at home most of the time. However, we didn't give up! We learned new skills and spent quality time together. We adapted to online shopping for daily necessities. It was not easy, but we persisted!In the business world, many enterprises transformed their production lines to manufacture epidemic prevention materials. They faced numerous challenges and difficulties. How could they succeed? Through unity and perseverance! They worked day and night, constantly adjusting and improving. Wasn't it amazing?This pandemic taught us that when we unite and insist, no obstacle is insurmountable! Let's always remember this and move forward bravely in the face of any hardship. Isn't that the spirit we should carry with us?篇5During the pandemic, life was turned upside down. I witnessed fear, uncertainty, and loss. But it also made me rethink the meaning of life. I realized how precious life is and how we often take simple things for granted.The mundane activities like going to the park, meeting friends, orhaving a meal together became a luxury. Now, as we come out of it, I cherish every moment of normalcy. I vow to make the most of each day, to love more deeply, and to laugh louder.I ask myself, how can I contribute to making the world a better place? Maybe it's by helping those in need, or by spreading kindness and positivity. The pandemic has taught me that we are all in this together, and our actions matter.I believe that the future holds hope and countless possibilities. Let's move forward with courage and determination, creating a brighter world for ourselves and others. Isn't that what we all deserve?。
商务英语综合教程答案

Appendix IKey to the ExercisesUnit 1I.Oral Practice.Example:My way to practise spoken English: Talk freely with my best friend in my spare time, for example, we usually talk in English when we climb the mountain and go to dinning hall.A: Marry, you have been learning English so well and your spoken English is almost like a native American. How are you becoming so excellent?B: Practice all the time with best way, I think.A: Sounds interesting, could you introduce your method of practising spoken English?B: Well. I have kept at least 5 years to practise speaking English everyday. My mother is an English teacher. I talk with her in English at home for years. And I speak English with my classmates at least 1 hour a day now.A: So great. Sometimes I want to keep on speaking, but always give it up after some days.B: That’s the problem. Interest is the best teacher. Y ou should enjoy speaking in English.A: How wonderful if I can speak with you from now. Could you help me?B: Surely. It’s my pleasure and it will improve my English level too. Let’s practice from now. A: Y ou are so kind. I will be surely improve my spoken English after some time.B: I think so. It can improve our friendship too.II.1. BCDEF AGIJK LMNOP QHI2. interest, satisfaction, simple, interpreters, essential, notes, summarization, review, record,deepen, burden, impressiveIII. 1. B 2.A 3.B 4.B 5.D 6.B 7.B 8.B 9.A 10.CIV.1. Introduced by our branch in New Y ork,2. you are one of the leading exporters of furniture.3. we shall appreciate it if you send us your price-list.4. you are interested in Electric Fans.5. To give you a general idea of the various Arts & Crafts we handle,6. your early reply.V.1.我们发邮件给您是要跟您在食品领域建立业务关系。
高铁作文素材英语

高铁作文素材英语High-speed Rail。
With the rapid development of technology and transportation, high-speed rail has become an increasingly popular mode of transportation in many countries. It offers a fast, efficient, and comfortable way to travel, and has greatly improved the accessibility and connectivity of different regions. In this essay, we will explore the benefits of high-speed rail and its impact on society.First and foremost, high-speed rail has significantly reduced travel time between cities and regions. For example, a journey that used to take several hours by car or conventional train can now be completed in just a fractionof the time with high-speed rail. This has not only made travel more convenient, but has also promoted economic development and tourism in various areas. Additionally,high-speed rail has helped to alleviate traffic congestion and reduce carbon emissions, as more people opt for thisefficient and environmentally friendly mode of transportation.Furthermore, high-speed rail has had a positive impact on the economy. The construction and operation of high-speed rail systems have created numerous job opportunities and stimulated investment in infrastructure and related industries. Moreover, the improved connectivity between cities has facilitated the flow of goods, services, and human capital, contributing to regional integration and economic growth. As a result, high-speed rail has become an important driver of economic development and urbanization.In addition to its economic benefits, high-speed rail has also brought about social and cultural changes. It has made it easier for people to travel for work, education, and leisure, and has encouraged greater interaction and exchange between different regions. This has not only enriched people's lives and broadened their horizons, but has also fostered a sense of unity and mutual understanding among diverse communities. Furthermore, high-speed rail has contributed to the development of new urban centers and therevitalization of rural areas, promoting balanced regional development and improving the quality of life for residents.However, it is important to acknowledge that the development of high-speed rail also presents challenges and considerations. For instance, the high cost of construction and operation, as well as the need for extensive land acquisition and environmental impact assessments, haveraised concerns about the financial and environmental sustainability of high-speed rail projects. Additionally,the potential social and cultural impacts of high-speedrail, such as changes in local communities and traditional ways of life, require careful planning and management to ensure that the benefits are equitably distributed and that the interests of all stakeholders are taken into account.In conclusion, high-speed rail has brought about significant changes in transportation, economy, and society. It has improved connectivity, reduced travel time, and promoted economic development, while also fostering social and cultural exchange. However, it is important tocarefully consider the challenges and implications of high-speed rail development in order to ensure its long-term sustainability and positive impact on society. With proper planning and management, high-speed rail can continue to play a vital role in shaping the future of transportation and urban development.。
VB外文翻译经典

Visual Basic language and arithmeticThe United States launched the Microsoft Visual Basic (may be referred to VB), is the latest version of the current VB 2008 Beta2 (VB9) Chinese version.Visual meaning the visual, visible, referring to the development of operating systems like windows graphical user interface (Graphic User Interface, GUI) method, it does not need to prepare a large number code to describe the appearance of the interface elements and location, as long as the pre - The establishment of good drag and drop objects on the screen corresponding to the location.Basic is actually an abbreviation of the phrase; this phrase is Beginners all-purpose symbolic instruction code, the Chinese meaning "to the initial directive GM symbol code language."Visual Basic learning, Professional Edition and Enterprise Edition versions to meet the different needs of the development. Study and apply to the ordinary version of the majority of learners and the use of Visual Basic development of the general staff of Windows applications, but; professional version for computer professional development of staff, including the study of functional version of the full content control and Internet development tools such as advanced features ,Enterprise contain not only all the professional version of the content, there are automated tools such as Component Manager, professional programmers to make the development of a powerful group essence of distributed applications.Visual BasicSection 1 the summary of Visual BasicMicrosoft Visual Basic,( abbreviate VB )as tool the most of application program one of under Windows operating platform. No matter beginner or professional developer, VB has all offered a whole set of tools to them, Development application program that it can be relaxed and convenient. So VB as most computer first-selected the ABC of programming language of beginner." Visual" mean method to adopt visual user of development figure interface (GUI), need and write a large number of code go and describe interface appearance and position of element seldom, Tow and show controlling part that need corresponding position to get screen can help figure design interface, user of figure,; " Basic" means BASIC language, because VB is developed on the basis of already existing BAISC language.VB is a kind of programming language in common use of Microsoft, It, including VBA of the numerous Windows application software use VB language in Microsoft Excel, Microsoft Accessed., For users to carry on the secondary development; Make web page use more VBScript script language sub collection of VB too at present.Utilize data of VB visit characteristic user can establish the data base to most data base forms including Microsoft SQL Server and other enterprises data base With the application program of front, and adjustable service end part. Utilize ActiveX(TM) technology, VB can use word processor, electronic data list he Windows function that application program offers extremely, Excel of Microsoft,, Word of Microsoft,, Even can use by VB specialty edition or enterprise application program and target that edition establish directly.The procedure that users established finally is a real .EXE file , can issue freely .VB offer study edition, the specialty edition and enterprise edition, use to satisfied with different development demands. Study edition make programming personnel develop Windows and Windows application program of NT very easily. The specialty edition has offered the developing instrument with complete function to programming personnel of the specialty, Include studying all functions of edition in the specialty edition. Enterprise edition allow the professional personnel to establish strong distributed application program in the form of group. It includes all characteristics of the specialty edition. So can choose different editions according to different needs.Section 2 integrated development environmentsIntegrated environment of VB call IDE, made up of a lot of parts , include title board, menu fence, tool fence, controlling part case, And window body window, engineering management device window, attribute window, code window and window body overall arrangement window body overall arrangement, etc. of designing etc.. Have covered all functions, such as design which develops the application program, editting, compiling and debugging, etc..In VB, the application program calls the project too. When start VB and open a new project for the first time, can see and pursue integrated development environment interface that show.Visual Basic Integrated development environmentVB come and organize development of application program through project, use project come and manage and form files of application program. One project uses the environment to make up by several window bodies, standard module generally. The system manages project through the project menu, for instance add the window body, quote . System allow turn on and manage a lot of projects besides.Section 3 Visual Basic language brief introductionsBasic use and do the elementary high-level language that used often most. Its full name is Beginner' s All-purpose Symbolic Instruction Code, abbreviate as BASIC. As its name suggests, Basic one specially for language that beginner design, because it easy to learn easy to know, So the body is popular. Early Basic language to belong to and solve translating type, so can carry outline by line , So it can see the result carried out at once , this is a very convenient design for beginner. But it have concept of structure either, one that is in procedure maintain and management have as much as other language problems. But back-end Basic correct shortcoming of the above (such as Quick Basic), make it may used for and develop the large-scaler procedure too.The language is the basic composition, which forms VB procedure. VB has stipulated the form of sentences and function.Grammar:The sentence defines incantations [Sentence body]Sentence define agree with and used in fixed function of sentence, sentence body appoint concrete content or want concrete operation that carry out of sentence. All set of sentence VB language, carry on with VB sentence organic association finish a certain specific function the procedure. Interface + procedure can solve a certain application problem.VB application program code window write in" code editing machine" generally. " editing machine of code" is like the word processing software of a piece of height specialization, there are many easies function of writing VB code, Pursue to show [Example Ex-Hello ]In" code editing machine" code that window written.“Editing machine of code” windowSection 4 develop the application program with Visual BasicUse VB programming, design appearance of application program first generally, write every target procedure code or other treatment procedure of incident respectively, Work of programming should be light more.The procedure of establishing the application program is as follows:Establish application program interfaceThe interface is the mutual bridge of user and procedure, Generally formed of window body and vision frame of the button, menu, text frameset. with standard WINDOWS interface of application program that VB establish. Require according to function of procedure and user and need of information interchange of procedure, Come to confirm that need those targets , plan the overall arrangement of the interface.2. Design by each attributes of target in interfaceDemand and set up each attribute of target such as appearance, name,, size of targeted. according to interface of planning.Most attribute person who fetch can set up through the attribute window when design already, Too can set up revising when operating in procedure through programming in procedure code.Have the targets respond programming by procedure code3. Respond procedure code of programming targetInterface determine appearance of procedure only, design window add codes through" code editing machine" soon after the interface, Realize some make the tasks, such as responding, information processing,etc. after accepting external message, Add code , realize some response, information processing that make after accepting external information task, As editor's window of code pursued shows add codes“code editing ma chine” window4. Keep projectOne VB procedure one project, at the time of designing a application program, system will set up one be expanded and called. Project file of vbp, project file include all relevant information of file that project set up this, Keep project keep associated documents of project this at the same time. For example the window body produced when design interfaces is kept and being expanded and being called. Frm sum. In the window body of foxfire. At the time of opening a project( file), this project relevant files load at the same time.5. Operate and debugged by procedureOperate the procedure thoroughpin operate" selecting in the menu, when the mistake appears, VB system can offer information prompt can looked for and get rid of the mistake thoroughpin debug" within operate" menus too.6. Can produce by executive programFor make procedure can break away from VB environment, order to become next life through" file"" producing project 1.exe" of menu but executive program (eyeful), Can carry out this file directly after this. In produce, + executive program, and then through install guide bale all associated documents, Can run independently after installation under the environment of windows 9 x/2000 as a software product.In computer system's any software, is by the every large or small each kind of software constituent constitution, defers to the specific algorithm to realize respectively, the algorithm quality direct decision realizes the software performance fit and unfit quality. Designs the algorithm with any method, what resources designs the algorithm to need, requires how many running time, how many storage space, how to determine an algorithm the quality, when realizes a software, is must give to solve. In computer system's operating system, the language compiling system, the database management system as well as in various computer application system's software, must use each one concrete algorithm to realize. Therefore, the algorithm design and the analysis are the computer science and a technical core question.The algorithm is the problem-solving step, we may define the algorithm Cheng Jie a determination class question the random one special method. In the computer science, the algorithm needs to use the computer algorithmic language to describe, the algorithm represents with the computer solves a kind of question precisely, the effective method. The algorithm construction of data = procedure, solves one to assign may calculate or the solvable question, the different person may compile the different procedure, solves the identical problem, here has two problems: First, with computational method close related algorithm question; Second, programming technical question. Between the algorithm and the procedure has the close relationship. The algorithm is a group has the poor rule, they had stipulated solves some specific type question a series of operations, is to the problem solving plan accurate and the complete description. Formulates an algorithm, generally must pass through stages and so on design, confirmation, analysis, code, test, debugging, time. To algorithm study including five aspect contents:①Design algorithm. The algorithm design work is impossible completely the automation, should study the understanding already by the practice to prove that was the useful some basic algorithm design method, these basic design method was not only suitable for the computer science, moreover was suitable for domains and so on electrical engineering, operations research;②Expresses the algorithm. The description algorithm's method has many kinds of forms, for example the natural language and the algorithmic language, have the suitable environment and the characteristic respectively;③Confirms the algorithm. The algorithm confirmed the goal is causes the people to believe firmly that this algorithm can work unmistakably correctly, namely this algorithm has the circularity. The correct algorithm describes with the computer algorithmic language, constitutes the computer program, the computer program moves on the computer, obtains the algorithm operation result;④Parsing algorithm. The algorithmic analysis is requires how many computing time and the storage space to an algorithm makes the quota the analysis. The parsing algorithm may forecast that what environment this algorithm does suit in moves effectively, to solves the identical question different algorithm validity to make the comparison;⑤Confirmation algorithm. With machine language description algorithm whether can calculate effectively, reasonable, must carry on the test to the procedure, the test order work and makes the space and time distribution map by the debugging to be composed.But the algorithm has certain characteristic, it includes:①Determinism. Algorithm each kind of operation must have the determination significance, this kind of operation should carry out what kind of movement should not to have the ambiguity, the goal is clear;②Effectiveness. Requests the operation which in the algorithm waits for realizing is basic, each kind of operation can at least completes in the principle by the human with the paper and the pen in the limited time;③Input. An algorithm has 0 or the many inputs, before the algorithm operation starts gives the algorithm to need the data the starting value, these inputs are from the specific object set;④Output. Does for the algorithm operation result, an algorithm has or many outputs, the output has some kind of specific relational quantity with the input;⑤Has poor. An algorithm always after carrying out had the poor step operation has terminated, namely this algorithm was may reach.Satisfies a first four characteristic group of rule not to be able to be called the algorithm, can only be called the computational process, the operating system is a computational process example, the operating system uses for to manage the computer resources, controls the manufacture industry movement, when has not made industry the movement, the computational process does not stop, but is at the waiting status.The algorithm complexity is the algorithm efficiency measure, when appraises the algorithm performance, the complexity is an important basis. The algorithm complex degree with moves computer resources how many which this algorithm needs related, needs the resources are more, indicated that this algorithm the complexity is higher; Needs the resources are less, indicated that this algorithm the complexity is lower.The spatial resources, which computer’s resources, operate most importantly, needs the time which and the stored routine and the data need, the algorithm complexity has division time complexity and the spatial complexity.The algorithm carries out the operation on the computer, needs the data which certain storage space depositing description algorithm the procedure and the algorithm need, the computer completes the operation task to require certain time. The procedure which writes according to the different algorithm places when on the computer operates, needs the time and the space are different, the algorithm complexity is needs the time and the spatial one kind of measure to the algorithm operation. The different computer its operating speed difference is very big, is weighing an algorithm the complexity to note this point.Regarding question, which assigns willfully, a profitable target which designs, the complex low algorithm is as far as possible when designs algorithm considered. Moreover, when the question, which assigns already when has many kinds of algorithms, an important criterion which choice complexity low, is when selects algorithm should follow. Therefore, the algorithm complex analysis or selects to the algorithm design has the important guiding sense and the use value.When discussion algorithm complexity, two questions need to clarify:(1) An algorithm's complexity expresses with what kind of quantity;(2) How to calculate one to assign the algorithm the complexity. After finding solves a question the algorithm, is this algorithm realization, as for whether could find the method whichrealized, was decided in the algorithm circularity and the computation complexity, whether this question did have the solution algorithm, whether to provide the time resources which and the spatial resources the algorithm needed.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
AN EFFICIENT DISTRIBUTED GROUP MUTUAL EXCLUSION ALGORITHM FOR NON-UNIFORM GROUP ACCESSNeeraj Mittal Department of Computer Science The University of Texas at Dallas Richardson,TX75083,USA email:neerajm@Prajwal K.Mohan∗Digital Home GroupIntel CorporationHillsboro,OR97124,USA email:prajwal.karur.mohan@ABSTRACTIn the group mutual exclusion problem,each critical sec-tion has a type or a group associated with it.Processes requesting critical sections of the same type may execute their critical sections concurrently.However,processes re-questing critical sections of different types must execute their critical sections in a mutually exclusive manner.Most algorithms for group mutual exclusion that have been proposed so far implicitly assume that all groups are equally likely to be requested.In this paper,we propose an efficient algorithm for solving the problem when a rel-atively small number of groups are requested more fre-quently than others.Our algorithm has a message com-plexity of2n−1per request for critical section,where n is the number of processes in the system.It has low syn-chronization delay of t and low waiting time of2t,where t denotes the maximum message delay.The maximum con-currency of our algorithm is n,which implies that if all processes have requested critical sections of the same type, then all of them may execute their critical sections con-currently.Finally,the amortized message overhead of our algorithm is O(1).Our experimental results indicate that our algorithm outperforms the existing algorithms by as much as50%in some cases.KEY WORDSmessage-passing system,resource management,group mu-tual exclusion,token-based algorithm,non-uniform group access1IntroductionResource management is one of the most important and fundamental problems in distributed systems.Typically, to maintain the integrity of a resource,at most one process should access the resource at any time.As a result,accesses to the same resource(that is,execution of critical sections) by different processes have to be serialized.This prob-lem is referred to as the mutual exclusion problem.Mutual exclusion has been studied extensively and a large num-ber of solutions have been developed(e.g.,[1,2,3,4,5]). Many different variants of mutual exclusion have also been ∗This work was done when the author was a student in the Department of Computer Science at the University of Texas at Dallas.defined.Some examples of variants include k-mutual ex-clusion problem[6],dining philosophers problem[7]and drinking philosophers problem[8].Recently,Joung proposed another variant of the mu-tual exclusion problem called the group mutual exclusion problem[9].In the group mutual exclusion(GME)prob-lem,every critical section is associated with a type or a group.Critical sections belonging to the same group can be executed concurrently.However critical sections be-longing to different groups must be executed in a mutu-ally exclusive manner.Intuitively,if two critical sections belong to the same group,then their requesting processes share some common property.The multiple-readers/single-writer(MRSW)problem is a special case of the group mu-tual exclusion problem.Let n denote the number of pro-cesses in the system.The multiple-readers/single-writer problem can be modeled using n+1groups.All read crit-ical sections belong to the same group.On the other hand, write critical sections requested by different processes be-long to different groups.(There is one group for each pro-cess.)As another application of the problem,assume that data is stored on CDs in a CD-jukebox and only one disk can be loaded for access at any time[9].Clearly,when a disk is loaded,users that need data on the currently loaded disk can access the disk concurrently.On the other hand, users that need access to a different disk have to wait until no one is using the currently loaded disk.Manabe and Park [10]proposed an extension of group mutual exclusion in which,at the time of request,a process is allowed to spec-ify more than one type;the request can be fulfilled as long as the process gets to execute a critical section of any one of those types.This corresponds to the case when the same data is replicated on multiple CDs and any of those CDs can be used to satisfy a request for that data.Most algorithms that have been developed for group mutual exclusion so far[9,11,12,13,14,15]implicitly assume that all groups are equally likely to be requested whenever a request for critical section is generated.In a real world,however,probability of requesting a group may be non-uniformly distributed.Specifically,a small fraction of the groups may be requested more frequently than the rest of the groups.For instance,in a CD jukebox,few CDs may contain data that are accessed more frequently than data on other CDs.As another example,in the MRSW problem,read requests may be more common than writerequests.In this paper,our objective is to develop an ef-ficient distributed algorithm for solving the group mutual exclusion problem that exploits the fact that group access requests may not be uniformly distributed.Related Work:In[16],Joung modified Ricart and Agrawala’s algorithm for traditional mutual exclusion[2] to derive two algorithms for group mutual exclusion(RA1 and RA2).The message-complexity of the two algorithms (RA1and RA2)is2(n−1)messages and3(n−1)mes-sages(amortized over all requests),respectively,where n is the number of processes in the system.Their synchroniza-tion delay,typically measured when the system is heavily loaded,is at most t,where t is the maximum message de-lay.And,their waiting time,typically measured when the system is lightly loaded,is at most2t.Moreover,both al-gorithms have maximum concurrency of n,which implies that if all processes have requested critical sections of the same type,then it is possible for all of them to execute their critical sections concurrently.However,RA1has low ex-pected concurrency of O(1)under heavy loads,whereas RA2has high message overhead of O(n).(Each message in RA2carries a vector timestamp of size n.)In[14],Joung proposed two quorum-based algo-rithms for group mutual exclusion(Maekawa M and Maekawa S),which are based on Maekawa’s quorum-based algorithm for traditional mutual exclusion.He also proposed a quorum system suitable for group mutual exclu-sion called the surficial quorum system.Hisfirst algorithm Maekawa M has high message complexity of O(n·m) messages per request for critical section in the worst-case, where m is the number of different groups,but preserves the synchronization delay of the original Maekawa’s al-gorithm.His second algorithm Maekawa S has message complexity of2q+1,where q is the maximum size of a quorum.However,its synchronization delay is(q+1)t, which is quite high.In[15],Atreya and Mittal proposed another quorum-based group mutual exclusion algorithm using the notion of surrogate quorums.Algorithms for group mutual exclusion problem have also been developed for ring networks(processes are ar-ranged in a ring)[12,11]and tree networks(processes are arranged in a tree)[13].However,all these solutions have high synchronization delay and high waiting time.Our Contribution:In this paper,we propose a highly concurrent token-based algorithm for group mutual exclu-sion,especially suited for applications in which a relatively small fraction of groups is requested much more frequently than the rest of the groups.Our algorithm is derived from Suzuki and Kasami’s token-based algorithm for traditional mutual exclusion[4].We achieve concurrency by using two kinds of tokens,namely primary and secondary.At any time,there is only one primary token but there may be multiple secondary tokens.Our algorithm has a message-complexity of2n−1messages per request for critical sec-tion.It has low synchronization delay of at most t and low waiting time of at most2t.The maximum concurrency of our algorithm is n.Further,our algorithm has high ex-pected concurrency under heavy loads(as in the case ofRA2)and low amortized message overhead of O(1)(as in the case of RA1).Our experimental results indicate that ouralgorithm significantly outperforms the existing group mu-tual exclusion algorithms with respect to all the three im-portant complexity measures,namely message-complexity,waiting time and system throughput,by as much as50%insome cases.Paper Organization:This paper is organized as follows.We present our system model and formally describe thegroup mutual exclusion problem in Section2.Our token-based algorithm for group mutual exclusion is discussed inSection3.We present our experimental results in Section4.Finally,we present our conclusions and outline future re-search directions in Section5.2Model and Problem Definition2.1System ModelWe assume an asynchronous message-passing distributedsystem comprising of a set of n processes P={p1,p2,...,p n},which communicate with each other by sending messages over a set of channels.We assume thatthere is a channel between every pair of processes.Thereis no global clock or shared memory.Processes are non-faulty and channels are reliable.Message delays arefinitebut may be unbounded.2.2The Group Mutual Exclusion ProblemThe problem of group mutual exclusion(GME)wasfirst proposed by Joung in[9]as an extension of the traditional mutual exclusion problem.In this problem,every request for a critical section is associated with a type or a group. Any algorithm for group mutual exclusion should satisfy the following properties:•group mutual exclusion(safety):at any time,no two processes,who have requested critical sections belonging to different groups,are in their critical sec-tions simultaneously.•starvation freedom(liveness):a process wishing to enter critical section will succeed eventually.Intuitively,if two critical sections belong to the same group,then their requesting processes share some com-mon property.The multiple-readers/single-writer problem is a special case of the group mutual exclusion problem. Clearly,any algorithm for solving the traditional mutual exclusion problem also solves the group mutual exclusion problem.However,such algorithms are sub-optimal be-cause they force all critical sections to be executed in a mu-tually exclusive manner and therefore do not permit any concurrency whatsoever.To avoid such degenerate so-lutions and unnecessary synchronization,Joung proposedthat an algorithm for achieving group mutual exclusion should satisfy the following desirable property:•concurrent entry(non-triviality):if all requests are for critical sections belonging to the same group,thena requesting process should not be required to wait forentering its critical section until some other process has left its critical section.We use m to denote the number of different groups. For the multiple-readers/single-write problem,m=n+1.For convenience,we use the term session to refer to a time-interval in which all critical sections executed are of the same type.A session commences with the start of the first critical section and terminates with the end of the last critical section.2.2.1Complexity MeasuresTo measure the performance of a group mutual exclusion algorithm,we use the following metrics:•message complexity:the number of messages ex-changed per request for critical section •synchronization delay:the time elapsed between when the current session terminates and when the next session(of some other type)can commence •waiting time:the time elapsed between when a pro-cess issues a request for critical section and when it actually enters the critical section •message overhead:the amount of data piggybacked on a message(in terms of number of integers)•concurrency:the number of processes that are in a session at the same timeThefirst four metrics are used to evaluate the perfor-mance of a traditional mutual exclusion algorithm as well. Thefifth metric is specific to a group mutual exclusion al-gorithm.Message-complexity and message-overhead de-termine the overhead imposed on the system by the group mutual exclusion algorithm at runtime.Synchronization delay is usually measured when the system is heavily loaded and there is a lot of contention among processes for access to the resource.Intuitively,synchronization delay and concurrency measure the system throughput that can be achieved when the system is heavily loaded.(The lower the synchronization delay and higher the concurrency,the greater is the system throughput.)One way to measure the concurrency of a group mutual exclusion is to deter-mine the maximum number of processes that can execute their critical sections concurrently.This is referred to as the maximum concurrency of a group mutual exclusion al-gorithm.Waiting time captures the amount of time an application process has to wait for its request to be ful-filled.Waiting time is typically measured when the system is lightly loaded and,therefore,there is no contention for the resource.To measure synchronization delay and wait-ing time,we assume that message delay is bounded by t.3A Token-Based Distributed Algorithm for Group Mutual ExclusionIn this section,we describe our token-based algorithm for group mutual exclusion.Our algorithm is an extension of the Suzuki and Kasami’s algorithm for traditional mu-tual exclusion[4].(Note that any algorithm that solves the group mutual exclusion problem also solves the mutual ex-clusion problem.Therefore,not surprisingly,almost all al-gorithms for group mutual exclusion have been obtained by modifying some mutual exclusion algorithm.)For the sake of completeness,we provide a brief description of the Suzuki and Kasami’s algorithm as well.We also prove the correctness of our algorithm and analyze its performance. Due to lack of space,a formal description of our algorithm and proofs of various lemmas and theorems are given else-where[17].3.1The Background:Suzuki and Kasami’sToken-Based AlgorithmSuzuki and Kasami’s algorithm[4]achieves mutual exclu-sion by maintaining a unique token in the system.A pro-cess can enter the critical section only if it holds the token. The token is said to be busy if its holder is currently in the critical section;otherwise it is idle.Every process main-tains a vector containing the sequence number of the lat-est request made by each process that it is aware of.The token contains afirst-in-first-out(FIFO)queue of process that have requests waiting to be fulfilled.Additionally,the token also contains a vector that maintains the number of requests that have been fulfilled for each process.A pro-cess,on generating a request for critical section,sends a REQUEST message to other processes if it does not have the token already.The process holding the token,on learn-ing about a pending request,sends the token to the request-ing process(via a TOKEN message)as soon as the to-ken becomes idle.The message-complexity of Suzuki and Kasami’s algorithm is n messages per request for critical section.Its synchronization delay is at most t and its wait-ing time is at most2t.The amortized message overhead is O(1)because,for each request for critical section,there are n−1REQUEST messages of size O(1)and one TOKEN message of size O(n).3.2Our AlgorithmTo enhance concurrency of Suzuki and Kasami’s basic al-gorithm,we use multiple tokens.There are two kinds of tokens:primary and secondary.At any time,there is ex-actly one primary token in the system.However,the num-ber of secondary tokens may vary from time-to-time.Ini-tially,process p1has the primary token,and the number of secondary tokens is zero.A token has a type associated with it and it can only be used to enter critical section of that type.Similar to Suzuki and Kasami’s algorithm,a process can enter a critical sec-tion of certain type only if it holds a token—primary orsecondary—of that type.The difference between a primary and a secondary token is the following:A process holding a primary token is allowed to issue secondary tokens to other processes.However,a process holding a secondary token is not allowed to issue a token to another process.A process,on requesting a critical section,checks whether it has a token of the same type as the critical sec-tion requested.If yes,it can simply enter the critical sec-tion.If not,it sends a REQUEST message to all processes.Every process p i maintains a vector request i;the j th entry of request i contains the sequence number of the lat-est request of process p j,along with its type,that process p i knows of.A token—primary as well as secondary—contains a vector ful filled;the j th entry of ful filled cap-tures the number of requests of process p j that have been fulfilled so far as per the token.If a process p i holds a token,then it can determine whether a process p j has a pending request by comparing the j th entries of request i and token i.ful filled:p j has a pending(or new)request if request i[j].number>token i.ful filled[j].The process holding the primary token,on receiving a“new”request for critical section of the same type as the type of the token, issues a secondary token to the requesting process.Addi-tionally,a primary token also contains a queue of pending requests.In case a request cannot be fulfilled immediately, which happens if its type conflicts with that of the token, the request is stored in the token queue.A process holding a token keeps the token until it be-comes aware of a conflicting pending request,that is,pend-ing request for critical section of type that is different from the type of the token.Specifically,a process holding a sec-ondary token,on learning about a conflicting pending re-quest,releases the token by sending a RELEASE message to all processes once it is no longer in the critical section (that is,the token is idle).On the other hand,the process holding the primary token,on learning about a conflict-ing pending request,passes the primary token to another process,which has a pending request in the token queue, once the token becomes idle.To select the next primary token holder,wefirst determine the type(or group)of the next session that should be initiated using a priority-based scheme discussed later in Section3.2.1.Once the type has been determined,one of the processes that has requested a critical section of the selected type is chosen to become the next primary token holder.All other processes with pending requests for the selected type are issued secondary tokens.A process p j on receiving a token from the previous primary token holder p i may not be able to use the token immediately.In other words,the token may not be safe for use.This is because a non-zero number of secondary tokens may have been issued in the previous session and some of these tokens may still be busy.Clearly,process p j should wait until these tokens have been released be-fore it can use its token to enter the critical section.To that end,we associate a sequence number with each token that represents the session to which the token belongs(given by variable session in the token).A process,on releas-ing a secondary token,piggybacks this sequence number on the RELEASE message it sends.Each process records the number of RELEASE messages it has received con-taining the most recent session sequence number(given by variables numRelease j and session j for process p j). Further,a token contains the number of secondary tokens that were issued for the previous session(given by variable oldNumT okens in the token).To determine if a token it has received is safe for use,process p j evaluates the fol-lowing condition:(token j.oldNumT okens=0)((session j=token j.session−1)∧(numRelease j=token j.oldNumT okens))(1)Clearly,if no secondary tokens were issued in the pre-vious session,then the token is safe for use.Otherwise, the token is safe for use if process p j has received release messages for all secondary tokens issued in the previous session.Additionally,the token is also safe for use if pro-cess p j has received a RELEASE message for the current session from some other process,say p k.This implies that process p k deemed it safe to enter the critical section.This could have happened only if process p k received all RE-LEASE messages for the previous session or was told by some other process(via a RELEASE message)that it was safe to use the token.Therefore we modify the condition for testing for the safety of a token as follows:(session j=token j.session)∨(1)(2) Note that,in our algorithm,the relationship between a primary token holder and a secondary token holder of the same session is different from that of a captain and its follower in RA2[16].Specifically,in our algorithm,it is possible for a secondary token holder to enter the critical section and perhaps even leave it before the primary token holder is able to enter the critical section.This may hap-pen,for example,when a process receives a secondary to-ken from the primary token holder of the previous session before the token arrives at the primary token holder of the current session.3.2.1Criterion for Selecting the Type of theNext SessionTo minimize the waiting time,it is preferable that the next session be of type for which the number of pending re-quests in the token queue is the maximum.However,this simple approach may lead to starvation of a request.To avoid starvation,every pending request in the token queue is associated with an attribute called age;it measures the number of sessions that have been initiated since the re-quest was added to the queue.Therefore,every time a new session is initiated,the age of all(pending)requests in the token queue increases by one.Now,to select the type for the next session,all re-quests in the queue are grouped based on their type.Each type is then assigned a priority,which consists of two parts. Thefirst part depends on the group size,which is given bythe number of requests in the group for that type.The sec-ond part depends on the group age,which is given by the sum of the ages of all the requests in the group for that type. The priority of a type is then computed by simply adding the two parts.The next session that is initiated is of type for which the priority value is the maximum.As explained earlier,one of the processes in the group is selected to be-come the next primary token holder and other processes in the group become secondary token holders.We show that this approach prevents starvation,that is,it ensures that every request for critical section is even-tually fulfilled.3.3Proof of CorrectnessThe following property about our algorithm can be easily verified:Proposition1There is exactly one primary token in the system at any time.Moreover,two tokens with the same session number are of the same type.The following lemma can be proved using induction on the session number:Lemma2A token belonging to session s with s>1is busy only if all tokens with session number s−1have been released.The safety property can now be proved using Propo-sition1and Lemma2:Theorem3(group mutual exclusion)If two processes are concurrently executing their critical sections,then both critical sections are of the same type.To establish starvation freedom,wefirst show the fol-lowing:Lemma4If there is a pending request of type that is dif-ferent from the type of the current session,then the current session eventually terminates.For convenience,we refer to the act of selecting type for a session,which is done using a priority-based scheme, as a step.Note that the priority assigned to a type by our scheme is non-zero if and only if there is at least one pend-ing request(for critical section)of that type.Further,if there are one or more pending requests for a type,the pri-ority of the type strictly increases with each step until the type is“selected”for a session.In case the priority of a type increases,let l and u with0<l≤u denote the lower and upper bounds,respectively,on the amount by which the priority can increase.For our scheme,l=1and u=n. Now,consider a type x whose current priority is greater than some value,say v.Observe that once y has been se-lected as a type for some session,at least v/(u−l)steps are required before the priority of y can“catch up”with that of x.Therefore,once the priority of x becomes at least m∗(u−l),within m steps,the priority of x attains the largest value.Therefore,we have,Theorem5(starvation freedom)Every request for criti-cal section is eventually fulfilled.Finally,it can be verified that:Theorem6(concurrent entry)Our algorithm satisfies the concurrent entry property.3.4Performance AnalysisOur algorithm exchanges three kinds of messages,namely REQUEST,RELEASE and TOKEN.Clearly,for each re-quest,there are at most n−1REQUEST messages,at most n−1RELEASE messages and at most1TOKEN message. Also,all messages except the TOKEN message are of size O(1);the TOKEN message is of size O(n).Therefore, Theorem7(message complexity and overhead)The worst-case message complexity of our algorithm is2n−1 and its amortized message overhead is O(1).Assume that the system is heavily loaded.Once the current session terminates,the next session starts as soon as the primary token holder of the next session has(1)re-ceived the token from the primary token holder of the cur-rent session,and(2)received RELEASE messages from all secondary token holders of the current session.Thus, Theorem8(synchronization delay)The synchronization delay of our algorithm is at most t.Now,assume that the system is lightly loaded.A pro-cess,on generating a request for critical section,can en-ter the critical section as soon as(1)its REQUEST mes-sage has been received by the current primary token holder (which in turn sends the token to it),and(2)it has received the token.Hence,Theorem9(waiting time)The waiting time of our algo-rithm is at most2t.Finally,it can be easily verified that:Theorem10(maximum concurrency)The maximum concurrency of our algorithm is n.4Experimental ResultsWe experimentally compare the performance of our token-based algorithm with RA2,whose asymptotic performance is comparable to that of our algorithm in all complexity measures.We simulate the two algorithms using an event-based simulator on a Dell machine equipped with Pentium 4processor operating at2.00GHz with a RAM of512MB. Our simulation has the following parameters.There are n processes and m groups.To model non-uniform group ac-cess,we assume thatα%of the groups are requestedβ% of the times.The inter-request delay at each node is ex-ponentially distributed with meanµidle.Once a process enters a forum,it departs after a delay that is uniformlyr a t i o -->inter-request delay -->Metric Ratios vs Inter-Request DelayFigure 1.Performance of our algorithm relative to RA2.distributed in the range [0,2∗µbusy ](with mean µbusy ).Message transmission delay is modeled to follow an expo-nential distribution with mean µlink .In our simulation,we use the following values for various parameters:n =25,m =50,µbusy =2time units,µlink =4time units and bandwidth =1000integers per unit time.To simulate non-uniform request distribution,we assume that α=20and β=80.Each process generates 500requests for critical section.All results are averaged over 10runs.We measure the performance of the two algorithms with respect to three metrics,namely message complexity,system throughput and waiting time.To make it easier to compare the two algorithms,we report the ratio (Our Al-gorithm/RA2)for the three metrics.Figure 1depicts the variation in the ratios for the three metrics as the mean inter-request delay increases.As shown in the figure,our algorithm has consistently better performance than RA2in all three metrics.Specifically,as the inter-request delay increases,message complexity decreases by as much as 40%,waiting time decreases by as much as 28%and sys-tem throughput increases by as much as 50%.5Conclusion and Future WorkIn this paper,we proposed an efficient token-based dis-tributed algorithm for solving the group mutual exclusion problem.Our algorithm is especially suited for applica-tions in which a relatively small number of groups are re-quested more often than other groups.Our preliminary experiments indicate that our algorithm has much better performance than existing algorithms when group access is non-uniform.Clearly,the scheme for selecting the type of the next session is crucial to the performance of our algorithm.As future work,we plan to investigate other type-selection schemes and measure their performance experimentally.References[1]mport.Time,Clocks,and the Ordering of Events in aDistributed munications of the ACM (CACM),21(7):558–565,July 1978.[2]G.Ricart and A.K.Agrawala.An Optimal Algorithm forMutual Exclusion in Computer munications of the ACM (CACM),24(1):9–17,January 1981.[3]M.Maekawa.A √N Algorithm for Mutual Exclusion inDecentralized Systems.ACM Transactions on Computer Systems ,3(2):145–159,May 1985.[4]I.Suzuki and T.Kasami.A Distributed Mutual Exclu-sion Algorithm.ACM Transactions on Computer Systems ,3(4):344–349,1985.[5]K.Raymond.A Tree based Algorithm for Distributed Mu-tual Exclusion.ACM Transactions on Computer Systems ,7(1):61–77,1989.[6]M.J.Fischer,N.A.Lynch,J.E.Burns,and A.Borodin.Re-source Allocation with Immunity to Limited Process Fail-ure (preliminary report).In Proceedings of the 20th Annual Symposium on Foundations of Computer Science (FOCS),pages 234–254,October 1979.[7] E.W.Dijkstra.Hierarchical Ordering of Sequential Pro-cesses.Acta Informatica ,1(2):115–138,October 1971.[8]K.M.Chandy and J.Misra.The Drinking PhilosophersProblem.ACM Transactions on Programming Languages and Systems (TOPLAS),6(4):632–646,1984.[9]Y .-J.Joung.Asynchronous Group Mutual Exclusion.Dis-tributed Computing (DC),13(4):189–206,2000.[10]Y .Manabe and J.Park.A Quorum-Based Extended GroupMutual Exclusion Algorithm without Unnecessary Block-ing.In Proceedings of the International Conference on Par-allel and Distributed Systems (ICPADS),pages 341–348,Newport Beach,California,USA,2004.[11]K.-P.Wu and Y .-J.Joung.Asynchronous Group Mutual Ex-clusion in Ring Networks.IEEE Proceedings—Computers and Digital Techniques ,147(1):1–8,2000.[12]S.Cantarell,A.K.Datta,F.Petit,and V .Villain.TokenBased Group Mutual Exclusion for Asynchronous Rings.In Proceedings of the IEEE International Conference on Distributed Computing Systems (ICDCS),pages 691–694,2001.[13]J.Beauquier,S.Cantarell,A.K.Datta,and F.Petit.GroupMutual Exclusion in Tree Networks.Journal of Information Science and Engineering ,19(3):415–432,May 2003.[14]Y .-J.Joung.Quorum-Based Algorithms for Group MutualExclusion.IEEE Transactions on Parallel and Distributed Systems (TPDS),14(5):463–475,May 2003.[15]R.Atreya and N.Mittal.A Dynamic Group Mutual Exclu-sion Algorithm using Surrogate-Quorums.In Proceedings of the IEEE International Conference on Distributed Com-puting Systems (ICDCS),pages 251–260,Columbus,Ohio,USA,June 2005.[16]Y .-J.Joung.The Congenial Talking Philosophers Problemin Computer Networks.Distributed Computing (DC),pages 155–175,2002.[17]P.K.Mohan.An Efficient Distributed Group Mutual Exclu-sion Algorithm for Non-Uniform Group Access.Master’s thesis,Department of Computer Science,The University of Texas at Dallas,Richardson,TX 75083,USA,August 2005.。
