CISCO数据设置参考
cisco设置

cisco设置连接1.用Cisco 2600路由器自带的一条串行电缆将路由器的Console口与1台运算机串口相连。
2.启动Windows 2000后,执行以下操作:“开始→程序→附件→通讯→超级终端”,在“连接描述”对话框的名称一栏中输入超级终端名,运行Hypertrm.exe,点击“确定”。
3.在“连接到”窗体中的“连接时使用”栏选择“COM1”,单击确定。
在弹出的“COM1属性”窗体中进行端口设置。
设置终止,打开路由器电源,就会显现路由器的启动信息。
这时就能够像在终端一样对路由器进行操作了。
配置路由器的配置操作都必须连接到路由器的终端上,在Cisco路由器操作系统IOS的提示符下进行操作。
常用配置方法如下:配置以太网络接口的IP地址Router> enable '进入特权模式Password:'特权用户口令Router# configure terminal '进入配置模式Enter configuration commands one per line. End with CNTL/Z.Routerconfig# interface Ethernet 0 '进入外部以太网口配置Routerconfig-if# ip address 192.168.0.11 255.255.255.0 '进入AUI0接口的IP地址配置为192.168.0.11,子网掩码为255.255.255.0。
配置静态路由表Router> enablePassword:Router# config terminalEnter configuration commands one per line. End with CNTL/Z.Routerconfig# ip route 192.168.2.0 255.255.255.0 192.168.0.1 '配置进入AUI0接口的IP地址。
cisco设备详细配置(全)

cisco设备详细配置(全)实验一口令和主机名设置1. 口令和设备名设置添加一个交换机或一个路由器,先对交换机进行操作,双击SwitchAswitch>enpassword: ;第一次密码为空,直接回车switch#conf t ;进入全局配置模式switch(config)#hostname swa ;设置交换机名swa(config)#enable secret aaa ;设置特权加密口令为aaaswa(config)#enable password aax ;设置特权非密口令为aax swa(config)#line console 0 ;进入控制台口(Rs232)状态swa(config-line)#login ;允许登录swa(config-line)#password aa ;设置登录口令aaswa(config-line)#line vty 0 4 ;进入虚拟终端virtual ttyswa(config-line)#login ;允许登录swa(config-line)#password a ;设置登录口令aswa(config-line)#exit ;返回上一层swa(config)#exit ;返回上一层swa#sh run ;看配置信息swa#exit ;返回命令swa>enpassword: ;哪一个口令可以通过双击ROA对路由器进行与交换机类似的设置。
2. 清除口令清除交换机口令,实际中是在开机时按住交换机上的mode钮,本模拟机按Ctrl+Break。
口令请除,可以重新配置口令了。
清除路由器口令,实际中是在开机时上电时,按Ctrl+Break,本模拟机按Ctrl+Break。
参考操作如下:双击RouterA 。
先配置路由的特权口令:router>enpassword: ;第一次密码为空,直接回车router#conf t ;进入全局配置模式router(config)#enable secret aaa ;设置特权加密口令为aaa router(config)#exit ;返回router#exitrouter>enpassword:aaarouter#清除路由器的口令是在假设口令丢失情况下使用的方法,具体的操作是开机进入rommon状态,打开寄存器配置开关:router#reload ;重新启动,按Ctrl+Break rommon>rommon>confreg 0x2142 ;跳过配置,26xx 36xx 45xxrommon>reset;重新引导,等效于重开机router>enpassword:router#conf trouter(config)#enable secret bbb ;设置特权加密口令为aaa router(config)#config-register 0x2102 ;正常使用配置文件router(config)#exitrouter#exitrouter>enpassword:bbbrouter#在实际工作中一般要备份路由器的配置文件,当系统有问题时将配置文件复原。
思科 sx20 快速设置 数据表说明书

Data SheetCisco SX20 Quick SetProduct overviewThe Cisco SX20 Quick Set (SX20 Quick Set) can transform any flat panel display into a sleek and powerful video conferencing system. The SX20 Quick Set is designed to deliver high definition video and multiparty conferencing with the flexibility to accommodate various room size and configurations - all at a value price. The SX20 Quick Set supports optional embedded multipoint support with Cisco ® MultiSite technology, enabling users to add three additional participants to a video call.SX20 Quick Set combines a powerful codec, premium resolution of 1080p, two camera choices, and a dual-display feature in an easy-to-deploy and easy-to-use solution. Whether you're a small business just getting started with telepresence or a large enterprise looking to expand your existing deployment, the SX20 Quick Set delivers the performance you would expect from more expensive systems - in a compact, feature-rich and affordable package. Now, the SX20 Quick Set supports cloud registration to Cisco Webex for even faster and more cost effective deployment 1. Cisco SX20 Quick Set is designed to truly extend the power of in-person to everyone, everywhere.Figure 1.Cisco SX20 quick set in a small meeting room environmentFeatures and benefitsTable 1 summarizes the primary features for the Cisco SX20 Quick Set.Table 1.Cisco SX20 Quick Set feature summary1Requires Collaboration Endpoint Software Version 8.2 or later (CE8)Figure 2. Cisco SX20 Quick Set on optional wall mount2 Requires Collaboration Endpoint Software Version 8.0 or later (CE8)3 Requires Collaboration Endpoint Software Version 8.1 or later (CE8)Product specificationsTable 2 lists the product capability specifications for the Cisco SX20 Quick Set. Table 2. Product specificationsVideo Outputs (Two Outputs) Two HDMI Outputs Supported Formats:●1920 x 1080@60 fps (1080p60)●1920 x 1080@50 fps (1080p50)●1280 x 720@60 fps (720p60)●1280 x 720@50 fps (720p50)●1366 x 768@60 fps (WXGA)4●1360 x 768@60 fps(WXGA)4●1280 x 768@60 fps (WXGA)4●1280 x 1024@60 fps4●1024 x 768@60 fps4VESA Monitor Power Management (DPM)CEC Power Management supported on HDMI output EDIDLive Video Resolutions (Encode and Decode):●176 x 144@30, 60 fps (QCIF) (Decode only)●352 x 288@30, 60 fps (CIF)●512 x 288@30, 60 fps (w288p)●576 x 448@30, 60 fps (448p)●768 x 448@30, 60 fps (w448p)●704 x 576@30, 60 fps (4CIF)●1024 x 576@30, 60 fps (w576p)●640 x 480@30, 60 fps (VGA)●800 x 600@30, 60 fps (SVGA)●1024 x 768@30, 60 fps (XGA)●1280 x 768@30, 60 fps (WXGA)●1280 x 720@30, 60 fps (HD720p)●1920 x 1080@30, 60 fps (HD1080p)Audio Standards ●G.711, G.722, G.722.1, G.728, G.729, AAC-LD and OPUS Audio Features ●High quality 20 KHz stereo●Two acoustic echo cancellers●Automatic Gain Control (AGC)●Integration with third-party audio systems●Automatic noise reduction●Active lip synchronizationAudio Inputs (Four Inputs) ●Two microphones, 4-pin minijack ●One minijack for line-in (stereo) ●One audio in from camera (HDMI)Audio Outputs (Two Outputs) ●One minijack for line out (stereo) ●One HDMI, (digital main audio)Dual Stream ●H.239 (H.323) dual stream●BFCP (SIP) dual stream●Support resolutions up to 1080p) at 30 frames per secondMultipoint Support ●Four-way embedded SIP/H.323 conferencing capability with MultiSite option●Ad-hoc conferencing supported through:◦Unified Communications Manager Media Resource Group (requires a Cisco TelePresence MCU)◦Cisco TelePresence Multiway [requires Cisco TelePresence Video Communication Server (Cisco VCS)and a Cisco TelePresence MCU]4●Ability to natively join multipoint conferences hosted on Cisco Telepresence Multipoint Switch (CTMS)3●Switched conferencing (SVC)24 Requires TC Software Version TC5.1 or later. Not supported in CE8MultiSite Features (Embedded Multipoint) (Optional upgrade) ●Adaptive SIP/H.323 MultiSite; resolution up to 720p30◦3-way resolution up to 720p30◦4-way resolution up to 576p30●Full individual audio and video transcoding●Individual layouts in MultiSite continuous presence●H.323/SIP/VoIP in the same conference●Support for Presentation (H.239/BFCP) from any participant at resolutions up to 1080p15 ●Best Impression (automatic continuous presence layouts)●H.264, encryption and dual stream from any site●IP downspeeding●Participants can be added by dialing in or host can dial out●Conference rates up to 6 MbpsProtocols ●H.323●SIP●ISDN (requires Cisco ISDN Link)Embedded Encryption ●H.323 and SIP point-to-point●Standards-based: H.235 v3 and Advanced Encryption Standard (AES)●Automatic key generation and exchange●Supported in dual streamIP Network Features ●DNS lookup for service configuration●Differentiated services (quality of service [QoS])●IP-adaptive bandwidth management (including flow control)●Automatic gatekeeper discovery●Dynamic playout and lip-sync buffering●H.245 Dual Tone Multi-frequency (DTMF) tones in H.323●RFC 4733 DTMF tones in SIP●Date and time support using Network Time Protocol (NTP)●Packet loss-based down speeding●Uniform Resource Identifier (URI) dialing●TCP/IP●DHCP●802.1x network authentication●802.1Q Virtual LAN●802.1p (QoS and class of service [QoS])●ClearPathCisco Unified Communications Manager (requires Cisco Unified Communications Manager Version 8.6 or later) ●Native registration with Cisco Unified Communications Manager●Basic Cisco Unified Communications Manager provisioning●Software upgrade from Cisco Unified Communications Manager●Cisco Discovery Protocol and DHCP option 150 support●Basic telephony features such as hold/resume/transfer and Corporate Directory lookupCisco Video CommunicationServer●Recommend latest softwareIPv6 Network Support ●Single call stack support for both H323 and SIP●Dual-stack IPv4 and IPv6 for DHCP, SSH, HTTP, HTTPS, DNS, DiffServ●Support for both Static and Automatic IP configuration (stateless address auto configuration)Security Features ●Management using HTTPS and SSH●IP administration password●Menu administration password●Disable IP services●Network settings protectionCertificate management ●Certificate Authority Proxy Function (CAPF) support for additional security●Manufacturer-Installed Certificates (MIC)●Locally Significant Certificates (LSC)●X.509 Digital Certificates (DER encoded binary); both DER and Base-64 formats are acceptable for theclient and server certificates; certificates with a key size of 1024, 2048, and 4096 are supportedPrecision 40 Camera PrecisionHD 12x Camera 8x zoom (4x optical plus digital)Motorized +15°/-25°tilt, +/- 90°panRegulatory compliance●Directive 2006/95/EC (Low-Voltage Directive) - Standard IEC/EN 60950-1●Directive 2004/108/EC (EMC Directive) - Standard EN 55022, Class A - Standard EN 55024 - Standard EN61000-3-2/-3-3●Approved according to UL 60950-1 and CAN/CSA-C22.2 No. 60950-1-07●Complies with FCC CFR 47 Part 15 Class AOrdering informationTo place an order, please contact your local Cisco representative and refer to Table 3.Table 3. Ordering informationCisco service and supportCisco and our partners provide a broad portfolio of smart, personalized services and support that can help you realize the full business value of your Cisco video collaboration investment by increasing business agility and network availability. This portfolio of services accelerates business innovation by harnessing the network as a powerful business platform. For more information about these services, please visit:https:///go/telepresenceservices.Cisco CapitalFlexible payment solutions to help you achieve your objectivesCisco Capital makes it easier to get the right technology to achieve your objectives, enable business transformationand help you stay competitive. We can help you reduce the total cost of ownership, conserve capital, andaccelerate growth. In more than 100 countries, our flexible payment solutions can help you acquire hardware,software, services and complementary third-party equipment in easy, predictable payments. Learn more.For more informationVisit the Cisco SX Series web page or contact your local account representative for more information.Printed in USA C78-688342-24 09/18。
Cisco基本网络配置

19
防火墙asa基本设置
asa特点: • (1)从高安全级别接口到低安全级别接口的流量叫outside 流量,这 种流量默认是允许的 • (2)从低安全级别接口到高安全级别接口的流量叫inbound流量,这 种流量默认是不允许的,但我们可以使用ACL来放行inbound流量 • (3)相同安全级别的接口之间的流量默认是不允许的,但是可以用 命令打开 • (4) 安全级别的范围为0-100 • (5)默认inside安全级别为100,其余接口默认为0
进入vlan 1 设置IP地址 设置默认网关
6、交换机如何划分vlan switch#vlan database switch(vlan)#vlan 2 switch(vlan)#no vlan 2 或者 switch(config)#interface vlanX
进入VLAN设置 新建VLAN 2 删除VLAN 2 X表示vlan数
一、cisco的三种设备类型
• 1、cisco 路由器 • 2、cisco switch (思科交换机) • 3、cisco asa5510(思科防火墙)
1
1、路由器设备型号
• • • • • •
871 1800 2600 2800 3600 7200
2
2、交换机设备型号
• • • • • • • • 2950 2960 2970 3550 3560 4506 4510 6050
13
Cisco 基本网络设置
17、cisco路由器查看命令 Who 查看telnet 登陆用户 Show running-configure 查看配置信息 Show running-configure interface fx/x 查看接口详细配置 Show ip route 查看路由表 Show interface fastethernet x/x 查看快速以太网接口 Show ip interface brief 查看接口链路层状态 Show arp 查看ARP地址表 Show version 查看路由器版本信息 Show user 查看登陆用户 Show processes cpu 查看cpu使用进程 Show log 查看日志
cisco双线双路网络路由器怎么设置

cisco双线双路网络路由器怎么设置思科cisco是全球领先且顶尖的通讯厂商,出产的路由器功能也是很出色的,那么你知道cisco双线双路网络路由器怎么设置吗?下面是店铺整理的一些关于cisco双线双路网络路由器怎么设置的相关资料,供你参考。
cisco双线双路网络路由器设置一,路由策略的优势:经常关注我们IT168网络频道的读者都知道之前我们介绍过如何从本地计算机的路由信息入手解决这种双线双路的实际网络问题,然而该方法只限于在单台计算机上操作,如果企业的员工计算机非常多,一台一台机器的设置肯定不太现实,这时我们就可以通过路由策略实现对企业网络路由器设置出口的统筹管理,将出口网络路由器设置合理的路由策略,从而让网络数据包可以根据不同需求转发到不同的线路。
总体说来路由策略各个命令只需要我们在企业连接网络外部出口的网络路由器设置即可,该路由器实际连接的是双线双路,即一个接口连接通往中国网通的网络,一个接口连接抵达中国电信的网络。
cisco双线双路网络路由器设置二,路由策略命令简单讲解:路由策略的意义在于他可以让路由器根据一定的规则选择下一跳路由信息,这样就可以自动的根据接收来的网络数据包的基本信息,判断其应该按照哪个路由表中的信息进行转发了。
通过路由策略我们可以为一台路由器指定多个下一跳转发路由地址。
下面我们来看一段路由策略指令,然后根据其后面的指示信息来了解他的意义。
(1)路由策略基本信息的设置:route-map src80 permit 10//建立一个策略路由,名字为src80,序号为10,规则为容许。
match ip address 151//设置match满足条件,意思是只有满足ip address符合访问控制列表151中规定的才进行后面的set操作,否则直接跳过。
set ip next-hop 10.91.31.254//满足上面条件的话就将这些数据的下一跳路由信息修改为10.91.31.254。
cisco路由器完整版配置大全

CISCO路由器设置完全手册文章主要分析了路由器设置方面的一些技巧,同时讲解了在使用BT/PPLive一些注意的要点,很多人都喜欢看网络电视,但是也会出现很多问题。
如何正确的进行路由器设置,是用户最为关心的问题,可能好多人还不了解如何在家庭使用中将路由器设置到最佳,没有关系,看完本文你肯定有不少收获,希望本文能教会你更多东西。
使用路由器设置共享上网后,在进行BT下载,收看PPLive视频时很多网友反应通过路由器设置无法进行BT下载,或者下载速度与PC直接连接网络时的下载相比甚慢,PPLive 也出现了同样的问题。
下文我们将以网件WGR614v7无线路由为例对二者剖析释疑,并给予解决之法或有效建议。
BT下载速度的快慢主要取决于BT的监听端口是否映射成功,该参数是可以在BT工具中自定义的。
监听端口若映射不成功将严重影响下载速率,种子数量极少的文件则可能完全无法下载,种子数量多的下载速率亦不会很快。
但经测试,BitComet的UPnP与WGR614v7(固件:V1.0.14/V1.3.16)的UPnP存在兼容性问题,最近出的最新版0.84亦不例外,而BitSpirit最新版3.2.2.215则能与路由器设置很好地协同工作,强烈推荐WGR614v7的用户使用。
以下行2M上行512K的ADSL为例,对应的最大下载上传速率分别为256KB/S和64KB/S,若BT的传输数据占用了所有带宽,那么不仅会使得其他应用无法正常使用,BT下载亦会受到影响,那是由于除传输数据以外,BT还有控制信息亦同时在传送,以此保证该应用的正常进行。
ADSL亦有通讯信息不断发送,保证宽带的正常连接。
因此强烈建议ADSL用户设置下载和上传的上限。
若内网有不止一个用户使用BT工具,那么需要注意BT的监听端口不要相同,且最好都设置下载上传上限,合理的带宽分配使各人的下载都得到保证。
即使无其他特别应用,所有PC的总的下载上传上限值亦尽量不要超过宽带最大带宽的80%。
cisco思科路由器设置

cisco思科路由器设置思科cisco是全球领先且顶尖的通讯厂商,出产的路由器功能也是很出色的,那么你知道cisco路由器详细知识吗?下面是小编收集整理的cisco思科路由器设置范文,欢迎借鉴参考。
cisco思科路由器设置(一)1. Cisco交换机支持的命令:交换机基本状态:switch: ;ROM状态,路由器是rommon>hostname> ;用户模式hostname# ;特权模式hostname(config)# ;全局配置模式hostname(config-if)# ;接口状态交换机口令设置:switch>enable ;进入特权模式switch#config terminal ;进入全局配置模式switch(config)#hostname ;设置交换机的主机名switch(config)#enable secret xxx ;设置特权加密口令switch(config)#enable password xxa ;设置特权非密口令switch(config)#line console 0 ;进入控制台口switch(config-line)#line vty 0 4 ;进入虚拟终端switch(config-line)#login ;允许登录switch(config-line)#password xx ;设置登录口令xxswitch#exit ;返回命令交换机VLAN设置:switch#vlan database ;进入VLAN设置switch(vlan)#vlan 2 ;建VLAN 2switch(vlan)#no vlan 2 ;删vlan 2switch(config)#int f0/1 ;进入端口1switch(config-if)#switchport access vlan 2 ;当前端口加入vlan2switch(config-if)#switchport mode trunk ;设置为干线switch(config-if)#switchport trunk allowed vlan 1,2 ;设置允许的vlanswitch(config-if)#switchport trunk encap dot1q ;设置vlan 中继switch(config)#vtp domain ;设置发vtp域名switch(config)#vtp password ;设置发vtp密码switch(config)#vtp mode server ;设置发vtp模式switch(config)#vtp mode client ;设置发vtp模式交换机设置IP地址:switch(config)#interface vlan 1 ;进入vlan 1switch(config-if)#ip address ;设置IP地址switch(config)#ip default-gateway ;设置默认网关switch#dir flash: ;查看闪存交换机显示命令:switch#write ;保存配置信息switch#show vtp ;查看vtp配置信息switch#show run ;查看当前配置信息switch#show vlan ;查看vlan配置信息switch#show interface ;查看端口信息switch#show int f0/0 ;查看指定端口信息2. 路由器支持的命令:路由器显示命令:router#show run ;显示配置信息router#show interface ;显示接口信息router#show ip route ;显示路由信息router#show cdp nei ;显示邻居信息router#reload ;重新起动路由器口令设置:router>enable ;进入特权模式router#config terminal ;进入全局配置模式router(config)#hostname ;设置交换机的主机名router(config)#enable secret xxx ;设置特权加密口令router(config)#enable password xxb ;设置特权非密口令router(config)#line console 0 ;进入控制台口router(config-line)#line vty 0 4 ;进入虚拟终端router(config-line)#login ;要求口令验证router(config-line)#password xx ;设置登录口令xxrouter(config)#(Ctrl+z) ;返回特权模式router#exit ;返回命令路由器配置:router(config)#int s0/0 ;进入Serail接口router(config-if)#no shutdown ;激活当前接口router(config-if)#clock rate 64000 ;设置同步时钟router(config-if)#ip address ;设置IP地址router(config-if)#ip address second ;设置第二个IProuter(config-if)#int f0/0.1 ;进入子接口router(config-subif.1)#ip address ;设置子接口IProuter(config-subif.1)#encapsulation dot1q ;绑定vlan中继协议router(config)#config-register 0x2142 ;跳过配置文件router(config)#config-register 0x2102 ;正常使用配置文件router#reload ;重新引导路由器文件操作:router#copy running-config startup-config ;保存配置router#copy running-config tftp ;保存配置到tftprouter#copy startup-config tftp ;开机配置存到tftprouter#copy tftp flash: ;下传文件到flashrouter#copy tftp startup-config;下载配置文件ROM状态:Ctrl+Break ;进入ROM监控状态rommon>confreg 0x2142 ;跳过配置文件rommon>confreg 0x2102 ;恢复配置文件rommon>reset ;重新引导rommon>copy xmodem: flash: ;从console传输文件rommon>IP_ADDRESS=10.65.1.2 ;设置路由器IP rommon>IP_SUBNET_MASK=255.255.0.0 ;设置路由器掩码rommon>TFTP_SERVER=10.65.1.1 ;指定TFTP服务器IP rommon>TFTP_FILE=c2600.bin ;指定下载的文件rommon>tftpdnld ;从tftp下载rommon>dir flash: ;查看闪存内容rommon>boot ;引导IOS静态路由:ip route ;命令格式router(config)#ip route 2.0.0.0 255.0.0.0 1.1.1.2 ;静态路由举例router(config)#ip route 0.0.0.0 0.0.0.0 1.1.1.2 ;默认路由举例动态路由:router(config)#ip routing ;启动路由转发router(config)#router rip ;启动RIP路由协议。
CISCO路由器的一般配置与调试

CISCO路由器的一般配置与调试一.配置---- 1 .配置以太网(Enthernet)端口# conf t从终端配置路由器。
# int e0指定E0口。
# ip addr ABCD XXXXABCD为以太网地址,XXXX为子网掩码。
# ip addr ABCD XXXX secondaryE0口同时支持两个地址类型。
如果第一个为A类地址,则第二个为B或C类地址。
# no shutdown激活E0口。
# exit2.X.25的配置# conf t# int S0指定S0口.# ip addr ABCD XXXXABCD为以太网S0的IP地址,XXXX为子网掩码.。
# encap X25-ABC封装X.25协议。
ABC指定X.25为DTC或DCE操作,缺省为DTE。
# x25 addr ABCDABCD为S0的X.25端口地址,由邮电局提供。
# x25 map ip ABCD XXXX br映射的X.25地址.ABCD为对方路由器(如:S0)的IP地址,XXXX为对方路由器(如:S0)的X.25端口地址。
# x25 htc X配置最高双向通道数.X的取值范围1-4095,要根据邮电局实际提供的数字配置。
# x25 nvc X配置虚电路数。
X不可超过据邮电局实际提供的数,否则,将影响数据的正常传输。
# exit---- 3 .专线的配置# conf t# int S2指定S2口。
# ip addr ABCD XXXXABCD为S2的IP地址,XXXX为子网掩码。
# exit4.帧中继的配置# conf t# int s0# ip addr ABCD XXXXABCD为S0的IP地址,XXXX为子网掩码。
# encap frante_relay封装frante_relay协议。
# no nrzi_encodingNRZI=NO# frame_relay lmi_type q933aLMI使用Q933A标准.LMI(Local managementInterface)有3种:ANSI:T1.617;CCITTY:Q933A和CISCO特有的标准。
Cisco路由器的调试和配置

Cisco路由器的调试和配置Cisco路由器是一种非常常用和重要的网络设备,用于实现网络的连接、安全性和数据传输。
路由器的调试和配置是保证网络正常运行和安全性的重要环节。
本文将介绍Cisco路由器的调试和配置的基本知识和步骤。
一、Cisco路由器的调试1. 确定问题:在进行路由器调试之前,首先要确定问题所在。
可以通过网络的错误报告、用户的反馈以及某些网络测试工具等来分析问题,并在调试过程中持续监测和排查。
2. 登录路由器:通过终端或远程连接方式登录到路由器的命令行界面。
输入正确的用户名和密码,并进入特权模式。
3. 开启调试模式:输入命令“debug”来开启调试模式。
可以使用“debug all”命令来开启所有的调试功能,也可以使用具体的调试功能命令来针对性地进行调试。
4. 监测和分析:在调试模式下,可以通过显示和分析路由器的调试输出信息来排查问题。
可以使用命令“show”来查看和比较不同的网络状态和配置信息。
5. 停止调试:当问题排查完毕后,应使用“undebug all”命令来关闭所有的调试功能,以避免对路由器的正常工作造成影响。
二、Cisco路由器的配置1. 登录路由器:同样,通过终端或远程连接方式登录到路由器的命令行界面。
输入正确的用户名和密码,并进入特权模式。
2. 进入全局配置模式:在命令行界面中输入“configure terminal”命令,进入全局配置模式。
在全局配置模式下,可以对路由器的各项配置进行修改和优化。
3. 配置主机名:通过命令“hostname”来配置路由器的主机名。
主机名应具有辨识度,并符合命名规范。
4. 配置接口:使用命令“interface”来配置路由器的各个接口。
通过这些接口,路由器可以与其他网络设备进行通信。
可以设置接口的IP地址、子网掩码、MTU(最大传输单元)等。
5. 配置路由协议:使用命令“router”来配置路由器的路由协议。
不同的路由协议有不同的特点和适用范围,可以根据实际需求来选择并配置适当的路由协议。
CISCO 网络设备使用及配置文档

CISCO 网络设备使用及配置文档一、网络结构:光纤传输-------光猫----------路由器2800的F0/1(外网地址:58.221.220.166)-------路由器的F0/0口(内网网关IP:192.168.1.1)-----------防火墙ASA5510的0(透明模式为外接口)-------防火墙的1(透明模式为内接口)-------------核心交换3560G的(G1 和G2 都可以上接)------核心交换机的其它接口分别对应各层接入交换机。
二、设备配置说明:路由器:F0/1 IP 是58.221.220.166 掩码:255.255.255.252 网关:58.221.220.165 F0/0 IP是192.168.1.1 掩码:255.255.255.0远程TELNET 的用户名:admin 密码:admin@123 特权密码:cisco防火墙:F0/0 是外部接口F0/1是内部接口系统管理IP 192.168.1.2 网关192.168.1.1 掩码:255.255.255.0 远程TELNET 密码:cisco特权密码:cisco核心交换:G1-G2 VLAN 1 IP 地址:192.168.1.3 掩码:255.255.255.0G3-G4 VLAN10 IP 地址:192.168.10.254 掩码:255.255.255.0G5-G6 VLAN20 IP 地址:192.168.20.254 掩码:255.255.255.0G7-G8 VLAN30 IP地址:192.168.30.254 掩码:255.255.255.0G9-G10 VLAN40 IP地址:192.168.40.254 掩码:255.255.255.0G11-G12 VLAN50 IP地址:192.168.50.254 掩码:255.255.255.0G13-G14 VLAN60 IP地址:192.168.60.254 掩码:255.255.255.0G21-G22 VLAN70 IP地址:192.168.70.254 掩码:255.255.255.0G23-G24 VLAN80 IP地址:192.168.80.254 掩码:255.255.255.0DHCP:各个VLAN 分发IP地址及其它信息。
cisco设置方法步骤

cisco设置方法步骤思科(Cisco)路由器是一个集成多业务路由器,福利综合服务网络路由器,以及获得回报的网络路由器。
cisco路由器怎么设置??有网友提到自己不会设置思科的设备,该怎么办?店铺在网上找了一些教程及命令,需要的朋友可以参考下。
以下是cisco路由器设置具体命令一、 host到router1、实验网络拓扑:pc( client 4.01)---switch---router1720 ( access server)pc配置:ip:10.130.23.242/28gw:10.130.23.2461720接口ip:f0:10.130.23.246/28lo0:172.16.1.1/241720的ios为c1700-k93sy7-mz.122-8.T5.bin2、步骤:1、配置isakmp policy:crypto isakmp policy 1encr 3desauthen pre-sharegroup 22、配置 client地址池cry isa client conf address-pool local pool192ip local pool pool192 192.168.1.1 192.168.1.2543、配置 client有关参数cry isa client conf group vclient-group####vclient-group就是在client的连接配置中需要输入的group authentication name。
key vclient-key####vclient-key就是在client的连接配置中需要输入的group authentication password。
pool pool192 ####client的ip地址从这里选取####以上两个参数必须配置,其他参数还包括domain、dns、wins等,根据情况进行配置。
4、配置ipsec transform-setcry ipsec trans vclient-tfs esp-3des esp-sha-hmac5、配置map模板cry dynamic-map template-map 1set transform-set vclient-tfs ####和第四步对应6、配置mapcry map map 1 ipsec-isakmp dynamic template-map#### 使用第?*脚渲玫?map 模板cry map map isakmp author list vclient-group ####使用第三步配置的参数authorizationcry map map client conf address respond ####响应client分配地址的请求7、配置静态路由ip route 192.168.1.0 255.255.255.0 fastethernet03、说明几点:(1)因为1720只有一个fastethernet口,所以用router1720上的lo0地址来模拟router内部网络。
CISCO官方配置手册ACL

Cisco − Access Control Lists and IP FragmentsTable of ContentsAccess Control Lists and IP Fragments (1)Document ID: 8014 (1)Introduction (1)Types of ACL Entries (2)ACL Rules Flowchart (3)How Packets Can Match an ACL (4)Example 1 (4)Example 2 (4)fragments Keyword Scenarios (5)Scenario 1 (5)Scenario 2 (6)Related Information (9)Access Control Lists and IP FragmentsDocument ID: 8014IntroductionTypes of ACL EntriesACL Rules FlowchartHow Packets Can Match an ACLExample 1Example 2fragments Keyword ScenariosScenario 1Scenario 2Related InformationIntroductionThis White Paper explains the different kinds of Access Control List (ACL) entries and what happens when different kinds of packets encounter these various entries. ACLs are used to block IP packets from being forwarded by a router.RFC 1858 covers security considerations for IP fragment filtering and highlights two attacks on hosts that involve IP fragments of TCP packets, the Tiny Fragment Attack and the Overlapping Fragment Attack. Blocking these attacks is desirable because they can compromise a host, or tie up all of its internal resources.RFC 1858 also describes two methods of defending against these attacks, the direct and the indirect. In the direct method, initial fragments that are smaller than a minimum length are discarded. The indirect method involves discarding the second fragment of a fragment set, if it starts 8 bytes into the original IP datagram. Please see RFC 1858 for more details.Traditionally, packet filters like ACLs are applied to the non−fragments and the initial fragment of an IP packet because they contain both Layer 3 and 4 information that the ACLs can match against for a permit or deny decision. Non−initial fragments are traditionally allowed through the ACL because they can be blocked based on Layer 3 information in the packets; however, because these packets do not contain Layer 4 information, they do not match the Layer 4 information in the ACL entry, if it exists. Allowing the non−initial fragments of an IP datagram through is acceptable because the host receiving the fragments is not able to reassemble the original IP datagram without the initial fragment.Firewalls can also be used to block packets by maintaining a table of packet fragments indexed by source and destination IP address, protocol, and IP ID. Both the Cisco PIX Firewall and the Cisco IOS® Firewall can filter all the fragments of a particular flow by maintaining this table of information, but it is too expensive to do this on a router for basic ACL functionality. A firewall's primary job is to block packets, and its secondary role is to route packets; a router's primary job is to route packets, and its secondary role is to block them. Two changes were made in Cisco IOS Software Releases 12.1(2) and 12.0(11) to address some security issues surrounding TCP fragments. The indirect method, as described in RFC 1858 , was implemented as part of the standard TCP/IP input packet sanity checking. Changes were also made to ACL functionality with respect to non−initial fragments.Types of ACL EntriesThere are six different types of ACL lines, and each has a consequence if a packet does or does not match. In the following list, FO = 0 indicates a non−fragment or an initial fragment in a TCP flow, FO > 0 indicates that the packet is a non−initial fragment, L3 means Layer 3, and L4 means Layer 4.Note: When there is both Layer 3 and Layer 4 information in the ACL line and the fragments keyword is present, the ACL action is conservative for both permit and deny actions. The actions are conservative because you do not want to accidentally deny a fragmented portion of a flow because the fragments do not contain sufficient information to match all of the filter attributes. In the deny case, instead of denying anon−initial fragment, the next ACL entry is processed. In the permit case, it is assumed that the Layer 4 information in the packet, if available, matches the Layer 4 information in the ACL line.Permit ACL line with L3 information onlyIf a packet's L3 information matches the L3 information in the ACL line, it is permitted.1.2.If a packet's L3 information does not match the L3 information in the ACL line, the next ACL entry is processed.Deny ACL line with L3 information onlyIf a packet's L3 information matches the L3 information in the ACL line, it is denied.1.2.If a packet's L3 information does not match the L3 information in the ACL line, the next ACL entry is processed.Permit ACL line with L3 information only, and the fragments keyword is presentIf a packet's L3 information matches the L3 information in the ACL line, the packet's fragment offset is checked.a.If a packet's FO > 0, the packet is permitted.b.If a packet's FO = 0 , the next ACL entry is processed.Deny ACL line with L3 information only, and the fragments keyword is presentIf a packet's L3 information does match the L3 information in the ACL line, the packet's fragment offset is checked.If a packet's FO > 0, the packet is denied.a.b.If a packet's FO = 0, the next ACL line is processed.Permit ACL line with L3 and L4 information1.If a packet's L3 and L4 information matches the ACL line and FO = 0, the packet is permitted.2.If a packet's L3 information matches the ACL line and FO > 0, the packet is permitted.Deny ACL line with L3 and L4 information1.If a packet's L3 and L4 information matches the ACL entry and FO = 0, the packet is denied.2.If a packet's L3 information matches the ACL line and FO > 0, the next ACL entry is processed.ACL Rules FlowchartThe following flowchart illustrates the ACL rules when non−fragments, initial fragments, and non−initial fragments are checked against the ACL.Note: The non−initial fragments themselves contain only Layer 3, never Layer 4 information, although the ACL may contain both Layer 3 and Layer 4 information.How Packets Can Match an ACLExample 1The following five possible scenarios involve different types of packets encountering ACL 100. Please refer to the table and flow chart as you follow what happens in each situation. The IP address of the web server is 171.16.23.1.access−list 100 permit tcp any host 171.16.23.1 eq 80access−list 100 deny ip any anyThe packet is an initial fragment or a non−fragment destined for the server on port 80:The first line of the ACL contains both Layer 3 and Layer 4 information, which matches the Layer 3 and Layer 4 information in the packet, so the packet is permitted.The packet is an initial fragment or a non−fragment destined for the server on port 21:1.The first line of the ACL contains both Layer 3 and Layer 4 information, but the Layer 4 information in the ACL does not match the packet, so the next ACL line is processed.2.The second line of the ACL denies all packets, so the packet is denied.The packet is a non−initial fragment to the server in a port 80 flow:The first line of the ACL contains Layer 3 and Layer 4 information, the Layer 3 information in the ACL matches the packet, and the ACL action is to permit, so the packet is permitted.The packet is a non−initial fragment to the server in a port 21 flow:The first line of the ACL contains both Layer 3 and Layer 4 information. The Layer 3 information in the ACL matches the packet, there is no Layer 4 information in the packet, and the ACL action is to permit, so the packet is permitted.The packet is an initial fragment, non−fragment or non−initial fragment to another host on the server subnet:1.The first line of the ACL contains Layer 3 information that does not match the Layer 3 information in the packet (the destination address), so the next ACL line is processed.2.The second line of the ACL denies all packets, so the packet is denied.Example 2The following same five possible scenarios involve different types of packets encountering ACL 101. Again, please refer to the table and flow chart as you follow what happens in each situation. The IP address of the web server is 171.16.23.1.access−list 101 deny ip any host 171.16.23.1 fragmentsaccess−list 101 permit tcp any host 171.16.23.1 eq 80access−list 101 deny ip any anyThe packet is an initial fragment or non−fragment destined for the server on port 80:The first line of the ACL contains Layer 3 information which matches the Layer 3 information in the1.packet. The ACL action is to deny, but because the fragments keyword is present, the next ACLentry is processed.2.The second line of the ACL contains Layer 3 and Layer 4 information, which matches the packet, so the packet is permitted.The packet is an initial fragment or non−fragment destined for the server on port 21:1.The first line of the ACL contains Layer 3 information, which matches the packet, but the ACL entry also has the fragments keyword, which doesn't match the packet because FO = 0, so the next ACLentry is processed.The second line of the ACL contains Layer 3 and Layer 4 information. In this case, the Layer 42.information does not match, so the next ACL entry is processed.3.The third line of the ACL denies all packets, so the packet is deniedThe packet is a non−initial fragment to the server in a port 80 flow:The first line of the ACL contains Layer 3 information which matches the Layer 3 information in the packet. Remember that even though this is part of a port 80 flow, there is no Layer 4 information in the non−initial fragment. The packet is denied because the Layer 3 information matches.The packet is a non−initial fragment to the server in a port 21 flow:The first line of the ACL contains Layer 3 information only, and it matches the packet, so the packet is denied.The packet is an initial fragment, non−fragment or non−initial fragment to another host on the server subnet:1.The first line of the ACL contains Layer 3 information only, and it does not match the packet, so the next ACL line is processed.2.The second line of the ACL contains Layer 3 and Layer 4 information. The Layer 4 information in the packet does not match that of the ACL, so the next ACL line is processed.3.The third line of the ACL denies this packetfragments Keyword ScenariosScenario 1Router B connects to a web server, and the network administrator does not want to allow any fragments to reach the server. This scenario shows what happens if the network administrator implements ACL 100 versus ACL 101. The ACL is applied inbound on the routers Serial0 (s0) interface and should allow onlynon−fragmented packets to reach the web server. See the ACL Rules Flowchart and the How Packets Can Match an ACL sections as you follow the scenario.Consequences of Using the fragments KeywordThe following is ACL 100:access−list 100 permit tcp any host 171.16.23.1 eq 80access−list 100 deny ip any anyThe first line of the ACL 100 allows only HTTP to the server, but it also permits non−initial fragments to any TCP port on the server. It permits these packets because non−initial fragments do not contain Layer 4 information, and the ACL logic assumes that if the Layer 3 information matches, then the Layer 4 information would also match, if it was available. The second line is implicit and denies all other traffic.It is important to note that, as of Cisco IOS Software Releases 12.1(2) and 12.0(11), the new ACL code drops fragments that do not match any other line in the ACL. Earlier releases allow non−initial fragments through if they do not match any other line of the ACL.The following is ACL 101:access−list 101 deny ip any host 171.16.23.1 fragmentsaccess−list 101 permit tcp any host 171.16.23.1 eq 80access−list 101 deny ip any anyACL 101 does not allow non−initial fragments through to the server because of the first line. A non−initial fragment to the server is denied when it encounters the first ACL line because the Layer 3 information in the packet matches the Layer 3 information in the ACL line.Initial or non−fragments to port 80 on the server also match the first line of the ACL for Layer 3 information, but because the fragments keyword is present, the next ACL entry (the second line) is processed. The second line of the ACL permits the initial or non−fragments because they match the ACL line for Layer 3 and Layer 4 information.Non−initial fragments destined to the TCP ports of other hosts on the 171.16.23.0 network are blocked by this ACL. The Layer 3 information in these packets does not match the Layer 3 information in the first ACL line, so the next ACL line is processed. The Layer 3 information in these packets does not match the Layer 3 information in the second ACL line either, so the third ACL line is processed. The third line is implicit and denies all traffic.The network administrator in this scenario decides to implement ACL 101 because it permits onlynon−fragmented HTTP flows to the server.Scenario 2A customer has Internet connectivity at two different sites, and there is also a backdoor connection between the two sites. The network administrator's policy is to allow Group A in Site 1 to access the HTTP server atSite 2. The routers at both sites are using private addresses (RFC 1918 ) and Network Address Translation (NAT) to translate packets that are routed through the Internet.The network administrator at Site 1 is policy−routing the private addresses assigned to Group A, so that they use the backdoor through Router A's Serial0 (s0) when accessing the HTTP server at Site 2. The router at Site 2 has a static route to 172.16.10.0, so that return traffic to Group A is also routed through the backdoor. All other traffic is processed by NAT and routed through the Internet. The network administrator in this scenario has to decide which application or flow is going to work if the packets are fragmented. It is not possible to make both the HTTP and File Transfer Protocol (FTP) flows work at the same time because one or the other breaks.See the ACL Rules Flowchart and the How Packets Can Match an ACL sections as you follow the scenario. Explanation of the Network Administrator's OptionsIn the following example, the route map called FOO on Router A sends packets that match ACL 100 across to Router B through s0. All packets that do not match are processed by NAT and take the default route through the Internet.Note: If a packet falls off the bottom of the ACL, or is denied by it, then it is not policy−routed.The following is a partial configuration of Router A, showing that a policy route−map called FOO is applied to interface e0, where the traffic from Group A enters the router:hostname Router_Aint e0ip policy route−map FOOroute−map FOO permit 10match ip address 100set ip next−hop 10.1.1.2access−list 100 permit tcp 172.16.10.0 0.0.0.255 host 192.168.10.1 eq 80access−list 100 deny ip any anyACL 100 allows policy routing on both initial, non−fragments and non−initial fragments of HTTP flows to the server. Initial and non−fragments of HTTP flows to the server are permitted by the ACL and policy routed because they match the Layer 3 and Layer 4 information in the first ACL line. Non−initial fragments are permitted by the ACL and policy routed because the Layer 3 information in the packet also matches the firstACL line; the ACL logic assumes that the Layer 4 information in the packet would also match if it was available.Note: ACL 100 breaks other types of fragmented TCP flows between Group A and the server because the initial and non−initial fragments get to the server through different paths; the initial fragments are processed by NAT and routed through the Internet, but the non−initial fragments of the same flow are policy routed.A fragmented FTP flow helps illustrate the problem in this scenario. The initial fragments of an FTP flow match the Layer 3 information, but not the Layer 4 information, of the first ACL line, and they are subsequently denied by the second line. These packets are processed by NAT and routed through the Internet. The non−initial fragments of an FTP flow match the Layer 3 information in the first ACL line, and the ACL logic assumes a positive match on Layer 4 information. These packets are policy routed, and the host reassembling these packets does not recognize the initial fragments as part of the same flow as thepolicy−routed non−initial fragments because NAT has changed the source address of the initial fragments. ACL 100 in the configuration below fixes the FTP problem. The first line of ACL 100 denies both initial and non−initial FTP fragments from Group A to the server.hostname Router_Aint e0ip policy route−map FOOroute−map FOO permit 10match ip address 100set ip next−hop 10.1.1.2access−list 100 deny tcp 172.16.10.0 0.0.0.255 host 192.168.10.1 fragmentsaccess−list 100 permit tcp 172.16.10.0 0.0.0.255 host 192.168.10.1 eq 80access−list 100 deny ip any anyInitial fragments match on the Layer 3 information in the first ACL line, but the presence of the fragments keyword causes the next ACL line to be processed. The initial fragment does not match the second ACL line for Layer 4 information, and so the next implicit line of the ACL is processed, which denies the packet.Non−initial fragments match the Layer 3 information in the first line of the ACL, so they are denied. Both initial and non−initial fragments are processed by NAT and routed through the Internet, so the server has no problem with reassembly.Fixing FTP flows breaks fragmented HTTP flows because the initial HTTP fragments are now policy routed, but the non−initial fragments are processed by NAT and routed through the Internet.When an initial fragment of an HTTP flow from Group A to the server encounters the first line of the ACL, it matches on the Layer 3 information in the ACL, but because of the fragments keyword, the next line of the ACL is processed. The second line of the ACL permits and policy routes the packet to the server.When non−initial HTTP fragments destined from Group A to the server encounters the first line of the ACL, the Layer 3 information in the packet matches the ACL line and the packet is denied. These packets are processed by NAT and traverse the Internet to get to the server.The first ACL in this scenario allows fragmented HTTP flows and breaks fragmented FTP flows. The second ACL allows fragmented FTP flows and breaks fragmented HTTP flows. The TCP flows break in each case because the initial and non−initial fragments take different paths to the server. Reassembly is not possible because NAT has changed the source address of the non−initial fragments.It is not possible to construct an ACL that allows both kinds of fragmented flows to the server, so the network administrator has to choose which flow he wants to work.Related InformationConfiguring Access Control Lists••IP Routing Support PageTechnical Support − Cisco Systems•All contents are Copyright © 1992−2005 Cisco Systems, Inc. All rights reserved. Important Notices and Privacy Statement. Updated: Aug 02, 2005Document ID: 8014。
思科基本配置命令详解

思科交换机基本配置实例讲解目录1、基本概念介绍 (1)2、密码、登陆等基本配置 (1)3、CISCO设备端口配置详解 (7)4、VLAN的规划及配置 (12)4.1核心交换机的相关配置 (12)4.2接入交换机的相关配置 (24)5、配置交换机的路由功能 (29)6、配置交换机的DHCP功能 (30)7、常用排错命令 (31)1、基本概念介绍IOS: 互联网操作系统,也就是交换机和路由器中用的操作系统VLAN: 虚拟lanVTP: VLAN TRUNK PROTOCOLDHCP: 动态主机配置协议ACL:访问控制列表三层交换机:具有三层路由转发能力的交换机本教程中“#”后的蓝色文字为注释内容。
2、密码、登陆等基本配置本节介绍的内容为cisco路由器或者交换机的基本配置,在目前版本的cisco交换机或路由器上的这些命令是通用的。
本教程用的是cisco的模拟器做的介绍,一些具体的端口显示或许与你们实际的设备不符,但这并不影响基本配置命令的执行。
Cisco 3640 (R4700) processor (revision 0xFF) with 124928K/6144K bytes of memory. Processor board ID 00000000R4700 CPU at 100MHz, Implementation 33, Rev 1.22 Ethernet interfaces8 Serial interfacesDRAM configuration is 64 bits wide with parity enabled.125K bytes of NVRAM.8192K bytes of processor board System flash (Read/Write)--- System Configuration Dialog ---Would you like to enter the initial configuration dialog? [yes/no]: n# 此处我们选择no,不进入他的初始化配置向导Press RETURN to get started!# 选择no以后,提示你按回车键开始,此处我们需要按回车键*Mar 1 00:43:56.591: %IP-5-WEBINST_KILL: Terminating DNS process*Mar 1 00:43:58.379: %SYS-5-RESTART: System restarted --Cisco IOS Software, 3600 Software (C3640-JK9O3S-M), Version 12.3(14)T7, RELEASE SOFTWARE (fc2)Technical Support: /techsupportCopyright (c) 1986-2006 by Cisco Systems, Inc.Compiled Wed 22-Mar-06 21:46 by pwade*Mar 1 00:43:58.411: %SNMP-5-COLDSTART: SNMP agent on host Router is undergoing a cold startRouter># 等显示稳定后,出现最初的提示符,注意提示符是“>”,目前所处的状态称为用户模式。
Cisco 300 系列交换机数据手册说明书

Cisco 300 Series SwitchesCisco Small BusinessEasy-to-Use Managed Switches that Provide the Ideal Combination of Features and AffordabilityTo stay ahead in a competitive marketplace, small businesses need to make every dollar count. That means getting the most value from your technology investments, but it also means making sure that employees have fast, reliable access to the business tools and information they need. Every minute an employee waits for an unresponsive application – and every minute your network is down – has an impact on your bottom line. The importance of maintaining a strong and dependable business network only grows as your business adds more employees, applications, and network complexity.When your business needs advanced security and features but value is still a top consideration, you’re ready for the new generation of Cisco® Small Business managed switches: the Cisco 300 Series.Cisco 300 Series SwitchesThe Cisco 300 Series, part of the Cisco Small Business line of network solutions, is a portfolio of affordable managed switches that provides a reliable foundation for your business network. These switches deliver the features you need to improve the availability of your critical business applications, protect your sensitive information, and optimize your network bandwidth to deliver information and applications more effectively. Easy to set up and use, the Cisco 300 Series provides the ideal combination of affordability and capabilities for small businesses, and helps you create a more efficient, better-connected workforce.The Cisco 300 Series is broad portfolio of fixed-configuration managed Ethernet switches. Models are available with 8 to 48 ports of Fast Ethernet and 10 to 52 ports of Gigabit Ethernet connectivity, providing optimal flexibility to create exactly the right network foundation for your business. However, unlike other small business switching solutions that provide managed network capabilities only in the costliest models, all Cisco 300 Series Switches support the advanced security management capabilities and network features you need to support business-class data, voice, security, and wireless technologies. At the same time, these switches are simple to deploy and configure, allowing you to take advantage of the managed network services your business needs.Business ApplicationsWhether you need a basic high-performance network to connect employee computers or a solution to deliver data, voice, and video services, the Cisco 300 Series offers a solution to meet your needs. Possible deployment scenarios include:●Secure desktop connectivity: Cisco 300 Series Switches can simply and securely connectemployees working in small offices with each other and with all of the servers, printers, and other devices they use. High performance and reliable connectivity helps speed file transfers and data processing, improves network uptime, and keeps your employees connected and productive.●Secure Wireless connectivity: With its advanced Security features, Power over Ethernet, AutoSmartports, QoS, VLAN and Access Control features, the Cisco 300 Series Switches are the perfect foundation to add Business Grade wireless to an SMB network.●Unified communications: As a managed network solution, the Cisco 300 Series provides theperformance and advanced traffic-handling intelligence you need to deliver all communications and data over a single network. Cisco offers a complete portfolio of IP telephony and other unifiedcommunications products designed for small businesses. Cisco 300 Series Switches have been rigorously tested to help ensure easy integration and full compatibility with these and other products, providing a complete small business solution.●Highly secure guest connectivity. Cisco 300 Series Switches let you extend highly secure networkconnectivity to guests in a variety of settings, such as a hotel, an office waiting room, or any other area open to nonemployee users. Using powerful but easy-to-configure security and traffic segmentation capabilities, you can isolate your vital business traffic from guest services and keep guests’ network sessions private from each other.Features and BenefitsCisco 300 Series Switches provide security, performance, traffic management, and other capabilities –optimized and customized, and at the right price for small businesses. The Cisco 300 Series provides:●High performance and reliability: Cisco 300 Series Switches have been rigorously tested to deliverthe high availability and performance you expect from a Cisco switch. The solutions speed up file transfer times and improve slow, sluggish networks, while keeping your vital business applications available and preventing costly downtime. As a managed switching solution, the Cisco 300 Series also gives you the flexibility to manage and prioritize high-bandwidth traffic such as voice. That means you can empower your employees with state-of-the-art communication and productivity solutions, without draining the performance of your other business applications.●Fast, easy setup and configuration: Cisco 300 Series Switches are designed to be easy to use andmanage by small businesses and the partners who serve them. The included device manager software provides an intuitive, web-based interface to simplify setup, security, and quality of service (QoS) traffic prioritization, allowing even users without IT expertise to configure the switch in minutes. Cisco also provides a Cisco FindIT Network Discovery Utility. This utility that works through a simple toolbar on the user’s web browser to discover Cisco devices in the network and display basic information, such as serial numbers and IP addresses, to aid in the configuration and deployment of Cisco Small Business products. For more information, and to download the utility, please visit /go/findit.These switches use Cisco Discovery Protocol as well as Link Layer Discovery Protocol (LLDP-MED) to automatically detect all the devices connected to your network, and then automatically configure themselves for the appropriate connectivity and instructs the devices to use appropriate voice VLAN orQoS parameters. For more advanced capabilities and hands-on control, the switches supportSmartport roles which configure the ports with specific levels of Security, QoS, and availabilityaccording to the type of connected device, based on Cisco best practices and pretested configurations.The Auto Smartports feature applies the intelligence delivered through the Smartport roles and applies it automatically to the port based on the devices discovered over CDP or LLDP-MED. This facilitates zero touch deployments. Although the Cisco 300 Series is designed to be deployed without using a command-line interface (CLI), Cisco Textview is available for those who prefer to use text-based configuration. Together, these features reduce the time your staff must devote to network deployment, management, and troubleshooting.●Strong security: The Cisco 300 Series Switches provide a high level of security and give you fine-grained control to safeguard your network from unauthorized users. Advanced security featuresinclude:◦Embedded security to protect management data traveling to and from the switch and encrypt network communications.◦Extensive access control lists (ACLs) to restrict sensitive portions of the network from unauthorized users and guard against network attacks.◦Guest virtual LANs (VLANs) to let you provide Internet connectivity to nonemployee users while isolating critical business services from guest traffic.◦Support for advanced network security applications such as IEEE 802.1X port security to tightly limit access to specific segments of your network. Web based authentication provides a consistentinterface to authenticate all types of host devices and operating systems, without the complexity of deploying IEEE 802.1X clients on each endpoint.◦Time based ACLs and Port Operation restrict access to the network during predesignated times, such as business hours.◦Security mechanisms such as, Bridge Protocol Data Unit (BPDU) Guard andbroadcast/multicast/unknown unicast storm control, protect the network from invalid configurations or malicious intent.◦Secure Core Technology (SCT) helps ensure that the switch will receive and process management and protocol traffic no matter how much traffic is received.◦Advanced defense mechanisms, including Dynamic ARP Inspection (DAI), IP Source Guard, and Dynamic Host Configuration Protocol (DHCP) snooping, detect and block deliberate network attacks.Combinations of these protocols are also referred to as IPMB (IP-MAC-port binding).◦IPv6 First Hop Security extends the advanced threat protection to IPv6. This comprehensive security suite includes ND inspection, RA guard, DHCPv6 guard and neighbor binding integrity check,providing unparalleled protection against a vast range of address spoofing and man in the middle attack on IPv6 networks.◦DOS (denial-of-service) attack prevention maximizes network uptime in the presence of an attack. ◦Protection of management sessions using Radius, TACACS+ and local database authentication as well as secure management sessions over SSL, SSH, and SNMPv3.●Power over Ethernet: Cisco 300 Series Switches are available with up to 48 PoE ports of FastEthernet or Gigabit Ethernet connectivity. This capability simplifies advanced technology deployments such as IP telephony, wireless, and IP surveillance by allowing you to connect and power network endpoints over a single Ethernet cable. With no need to install separate power supplies for IP phones or wireless access points, you can take advantage of advanced communications technologies more quickly, and at a lower cost. Some models support both IEEE 802.3af PoE and IEEE 802.3at PoE+ while others support IEEE 802.3af PoE only.●IP telephony support: Cisco 300 Series Switches include embedded QoS intelligence to prioritizedelay-sensitive services such as voice and video, simplify unified communications deployments, and help ensure consistent network performance for all services. For example, automated voice VLAN capabilities let you plug any IP phone (including third-party phones) into your IP telephony network and receive an immediate dial tone. The switch automatically configures the device with the right VLAN and QoS parameters to prioritize voice traffic.●Networkwide Automatic Voice Deployment: Using a combination of CDP, LLDP-MED, AutoSmartports, and VSDP (Voice Services Discovery Protocol – a unique patent-pending Cisco protocol), customers can deploy an end-to-end voice network dynamically. The switches in the networkautomatically converge around a single voice VLAN and QoS parameters and then propagate them out to the phones on the ports where they are discovered. For example, automated voice VLAN capabilities let you plug any IP phone (including third-party phones) into your IP telephony network and receive an immediate dial tone. The switch automatically configures the device with the right VLAN and QoS parameters to prioritize voice traffic.●Advanced network management capabilities: As managed switches, the Cisco 300 Series lets youuse a variety of advanced features to control traffic over your network. Features include:◦Static routing/Layer 3 switching between VLANs: This capability allows you to segment your network into separate workgroups and communicate across VLANs without degrading applicationperformance. As a result, you can manage internal routing with your switches and dedicate your router to external traffic and security, helping your network run more efficiently.◦IPv6 support: As the IP network addressing scheme evolves to accommodate more devices, you can make sure that your network is ready. The Cisco 300 Series provides native support for IPv6, the newest version of the Internet Protocol, as well as the previous IPv4 standard. As a result, you will be able to move up to the next generation of networking applications and operating systems without an extensive equipment upgrade.◦Dual image support: With the ability to maintain dual images of your switches, you can perform software upgrades without having to take the network offline and without worrying about an outage during an upgrade.◦Dual Configuration files support: Allows configuring the device, validating that it is configured correctly and then saving this configuration to become effective after reboot. Additionally, a mirror configuration file, providing automatic back-up of the latest stable configuration file maximizesnetwork uptime.◦Remote management: Using Simple Network Management Protocol (SNMP), you can set up and manage all switches and other Cisco devices in your network remotely, instead of having to directly connect to them.◦Additional management options: The switches can be fully managed using the Web GUI or using a full command-line interface (CLI).●Optimal energy efficiency: Cisco 300 Series Switches are designed with a variety of power-savingfeatures across all models, providing the industry’s broadest portfolio of “green” s witches. These switches optimize power use to protect the environment and reduce energy costs, withoutcompromising performance. Power-saving features include:◦The latest application-specific integrated circuits (ASICs), using low-power 65-nanometer technology (these chipsets allow for lower power consumption and thinner, more efficient designs).◦Support for the Energy Efficient Ethernet (IEEE 802.3az) standard, which reduces energy consumption by monitoring the amount of traffic on an active link and putting the link into a sleep state during quiet periods.◦Automatic power shutoff on ports when a link is down.◦Embedded intelligence to adjust signal strength based on cable length.◦Fanless design in most models, which reduces power consumption, increases reliability, and provides quieter operation.◦LEDs can be turned off to conserve power.●Expansion ports: The Cisco 300 Series provides more ports per Gigabit Ethernet switch thantraditional switch models, giving you more flexibility to connect and empower your business. Gigabit Ethernet models feature 28- and 52-port switches, versus traditional devices that offer 20 or 44 ports with four shared ports giving you more value. The Cisco 300 Series also offers mini gigabit interface converter (mini-GBIC) expansion slots that give you the option to add fiber-optic or Gigabit Ethernet uplink connectivity to the switch. With the ability to increase the connectivity range of the switches, you have more flexibility to design your network around your unique business environment, and to easily connect switches on different floors or across the business.●Multiple languages: The Cisco 300 Series is available in seven languages: English, French, German,Italian, Spanish, Japanese, and simplified Chinese. All product user interfaces and documentation are translated, giving you the ability to select your preferred language.●Peace of mind and investment protection: Cisco 300 Series Switches offer the reliable performance,investment protection, and peace of mind you expect from a Cisco switch. When you invest in the Cisco 300 Series, you gain the benefit of:◦Cisco limited lifetime warranty with next business day advance replacement (where available).◦Rigorous testing to help ensure easy integration and compatibility with other Cisco networking and communications products, including the complete Cisco Small Business portfolio.●Service and Support: Cisco 300 Series Switches are backed by the Cisco Small Business SupportService, which provides affordable peace-of-mind coverage. This subscription-based service helps you protect your investment and derive maximum value from Cisco Small Business products. Delivered by Cisco and backed by your trusted partner, this comprehensive service includes software updates, access to the Cisco Small Business Support Center, and extends technical service to three years.Cisco Small Business products are supported by professionals in Cisco Small Business Support Center locations worldwide who are specifically trained to understand your needs. The Cisco Small Business Support Community, an online forum, enables you to collaborate with your peers and reach Cisco technical experts for support information.●Cisco Limited Lifetime Hardware Warranty: Cisco 300 Series Switches offer a limited lifetimehardware warranty with next business day advance replacement (where available, otherwise same day ship) and a limited lifetime warranty for fans and power supplies. In addition, Cisco offers software application updates for bug fixes for the warranty term, and telephone technical support at no charge for the first 12 months following the date of purchase. To download software updates, go to:/cisco/web/download/index.html.Product warranty terms and other information applicable to Cisco products are available at/go/warranty.Product SpecificationsTable 1 gives the product specifications for the Cisco 300 Series Switches.Table 1. Product SpecificationsStandard MIBs (continued) SNMPv2-MIBSNMPv2-SMISNMPv2-TMRMON-MIB.mydcb-raj-DCBX-MIB-1108-MIBrfc1724-MIBRFC-1212.my_for_MG-Softrfc1213-MIBrfc1757-MIBRFC-1215.mySNMPv2-CONF.mySNMPv2-TC.myrfc2674-MIBrfc2575-MIBrfc2573-MIBrfc2233-MIBrfc2013-MIB rfc1907-MIB rfc2571-MIB rfc2572-MIB rfc2574-MIB rfc2576-MIB rfc2613-MIB rfc2665-MIB rfc2668-MIB rfc2737-MIB rfc2925-MIB rfc3621-MIB rfc4668-MIB rfc4670-MIB trunk-MIB tunnel-MIB udp-MIBPrivate MIBs CISCOSB-lldp-MIBCISCOSB-brgmulticast-MIBCISCOSB-bridgemibobjects-MIBCISCOSB-bonjour-MIBCISCOSB-dhcpcl-MIBCISCOSB-MIBCISCOSB-wrandomtaildrop-MIBCISCOSB-traceroute-MIBCISCOSB-telnet-MIBCISCOSB-stormctrl-MIBCISCOSB-ssh-MIBCISCOSB-socket-MIBCISCOSB-sntp-MIBCISCOSB-smon-MIBCISCOSB-phy-MIBCISCOSB-multisessionterminal-MIBCISCOSB-mri-MIBCISCOSB-jumboframes-MIBCISCOSB-gvrp-MIBCISCOSB-endofmib-MIBCISCOSB-dot1x-MIBCISCOSB-deviceparams-MIBCISCOSB-cli-MIBCISCOSB-cdb-MIBCISCOSB-brgmacswitch-MIBCISCOSB-3sw2swtables-MIBCISCOSB-smartPorts-MIBCISCOSB-tbi-MIBCISCOSB-macbaseprio-MIBCISCOSB-policy-MIBCISCOSB-env_mibCISCOSB-sensor-MIBCISCOSB-aaa-MIBCISCOSB-application-MIBCISCOSB-bridgesecurity-MIBCISCOSB-copy-MIBCISCOSB-CpuCounters-MIBCISCOSB-Custom1BonjourService-MIB CISCOSB-ip-MIBCISCOSB-iprouter-MIB CISCOSB-ipv6-MIBCISCOSB-mnginf-MIB CISCOSB-lcli-MIBCISCOSB-localization-MIB CISCOSB-mcmngr-MIB CISCOSB-mng-MIBCISCOSB-physdescription-MIB CISCOSB-Poe-MIBCISCOSB-protectedport-MIB CISCOSB-rmon-MIBCISCOSB-rs232-MIBCISCOSB-SecuritySuite-MIB CISCOSB-snmp-MIBCISCOSB-specialbpdu-MIB CISCOSB-banner-MIB CISCOSB-syslog-MIB CISCOSB-TcpSession-MIB CISCOSB-traps-MIBCISCOSB-trunk-MIBCISCOSB-tuning-MIB CISCOSB-tunnel-MIB CISCOSB-udp-MIBCISCOSB-vlan-MIBCISCOSB-ipstdacl-MIBCISCO-SMI-MIBCISCOSB-DebugCapabilities-MIB CISCOSB-CDP-MIBCISCOSB-vlanVoice-MIB CISCOSB-EVENTS-MIB CISCOSB-sysmng-MIB CISCOSB-sct-MIBCISCO-TC-MIBCISCO-VTP-MIBCISCO-CDP-MIBCISCOSB-eee-MIBCISCOSB-ssl-MIBOrdering InformationTable 2 provides ordering information for the Cisco 300 Series Switches. Table 2. Cisco 300 Series Switches Ordering InformationEach combo mini-GBIC port has one 10/100/1000 Ethernet port and one mini-GBIC/SFP Gigabit Ethernet slot, with one port active at a time.Table 3. MFE and MGE Transceiver Ordering InformationA Powerful, Affordable Foundation for Your Small Business NetworkAs you strive to make your employees as productive and effective as possible, your business applications and information – and the network that delivers them – become an ever more vital part of your business. You need a technology foundati on that can meet your business’s needs today and in the future, and that delivers the right feature set at the right price. The Cisco 300 Series portfolio of managed switches provides the reliability, performance, security, and capabilities you need to power your business.For More InformationTo find out more about the Cisco 300 Series, visit /go/300switches.。
思科路由器设置方法和常见配置命令

思科路由器设置方法和常见配置命令思科路由器设置方法和常见配置命令思科路由器怎么设置,是我们经常遇到的问题,下面店铺准备了关于思科路由器设置方法和常见配置命令,欢迎大家参考学习!一、基本设置方式一般来说,可以用5种方式来设置Cisco思科路由器:1.Console口接终端或运行终端仿真软件的微机;2.AUX口接MODEM,通过电话线与远方的终端或运行终端仿真软件的微机相连;3.通过Ethernet上的TFTP服务器;4.通过Ethernet上的TELNET程序;5.通过Ethernet上的SNMP网管工作站。
但Cisco思科路由器的第一次设置必须通过第一种方式进行,一般用超级终端通过com口进行控制。
此时终端的硬件设置如下: 波特率:9600数据位:8停止位:1奇偶校验: 无二、命令操作Cisco思科路由器所用的操作系统是IOS.共有以下几种状态:1、router>在router>提示符下,Cisco思科路由器处于用户命令状态,这时用户可以看Cisco思科路由器的连接状态,访问其它网络和主机,但不能看到和更改Cisco思科路由器的设置内容。
此时输入?并回车,可以查看到在此状态下可以用的命令。
(IOS允许你在任何时候用这种方式查看在某种状态下可以用的命令)。
在敲入enable并回车后,按照系统提示输入密码,(在新的Cisco思科路由器第一次进行调试的时候不需要输入密码,直接回车即可)进入#提示符,就可以对Cisco思科路由器进行各种操作了。
2、router#Cisco思科路由器进入特权命令状态router#后,不但可以执行所有的用户命令,还可以看到和更改Cisco思科路由器的设置内容。
此时就可以对Cisco思科路由器的名字、密码等进行设置。
3、router(config)#在router#提示符下键入configure terminal,出现提示符router(config)#,此时Cisco思科路由器处于全局设置状态,这时可以设置Cisco思科路由器的全局参数。
Cisco路由器配置命令大全

Cisco路由器配置命令大全本文档旨在提供一份最新最全的Cisco路由器配置命令范本,旨在帮助用户快速配置和管理Cisco路由器。
以下是具体的章节内容:⒈设置基本参数⑴主机名设置命令⑵控制台设置命令⑶用户密码设置命令⑷物理接口配置命令⒉配置IP网络⑴设置IP地质和子网掩码⑵配置静态路由⑶配置动态路由协议(如OSPF或EIGRP)⑷ ICMP设置命令⒊网络管理和监控⑴远程管理设置命令⑵ SNMP配置命令⑶日志记录命令⑷监控和排错命令⒋安全配置⑴访问控制列表(ACL)配置命令⑵ VPN配置命令⑶防火墙配置命令⑷加密和身份验证命令⒌功能扩展⑴ NAT配置命令⑵ QoS配置命令⑶ VLAN配置命令⑷ DHCP配置命令附件:本文档涉及附件,请参阅附件文件以获取更详细的配置示例和说明。
注释:⒈Cisco路由器:Cisco公司生产的用于网络互联的路由器设备。
⒉配置命令:指通过命令行界面输入的一系列指令,用于配置和管理Cisco路由器。
⒊IP地质:Internet协议地质,用于在网络中标识设备的唯一地质。
⒋子网掩码:用于确定IP地质中网络地质和主机地质的部分。
⒌静态路由:通过手动配置的路由信息,用于指定数据包的下一跳路径。
⒍动态路由协议:通过协议自动交换路由信息,动态更新路由表。
⒎OSPF:开放最短路径优先(Open Shortest Path First)协议,用于计算路径的最佳选择。
⒏EIGRP:增强型内部网关路由协议(Enhanced Interior Gateway Routing Protocol),Cisco公司开发的路由协议。
⒐ICMP:Internet控制报文协议,用于在IP网络中发送错误和控制消息。
⒑SNMP:简单网络管理协议,用于管理和监控网络设备。
1⒈ACL:访问控制列表,用于控制流经路由器的数据包的访问权限。
1⒉VPN:虚拟专用网络,通过加密和认证技术实现安全的远程连接。
1⒊防火墙:用于保护网络免受未经授权的访问和攻击的安全设备。
CISCO交换机配置操作学习教程(2024)

通过命令`interface <端口类型> <端口号 >`进入端口配置模式。
设置端口属性
可设置端口的速率、双工模式、流控等属性 。
2024/1/27
启用/禁用端口
通过命令`no shutdown`或`shutdown`启用 或禁用端口。
14
VLAN概念及划分方法
2024/1/27
01
20
04
路由配置与IP地址规划
2024/1/27
21
静态路由配置方法
配置静态路由基本命令
使用`ip route`命令配置静态路由 ,指定目标网络和下一跳地址或 出口接口。
静态路由的优缺点
优点是配置简单、占用资源少; 缺点是缺乏灵活性,当网络拓扑 发生变化时需要手动更新路由表 。
静态路由适用场景
适用于小型、稳定的网络环境, 或者作为动态路由协议的补充, 用于特定路由的精确控制。
02 进入全局配置模式
在特权EXEC模式下输入 `configure terminal`命令,进 入全局配置模式,此时可以对 交换机进行各种配置。
03
配置主机名
在全局配置模式下输入 `hostname <hostname>`命令 ,为交换机配置主机名,方便识 别和管理。
04
配置接口
在全局配置模式下输入 `interface <interface-type> <interface-number>`命令,进 入接口配置模式,然后可以对该 接口进行各种配置,如设置IP地 址、启用/禁用接口等。
防止DoS攻击
通过限制特定流量的速率或数量,防 止DoS攻击对交换机造成影响。
Cisco思科路由器配置手册
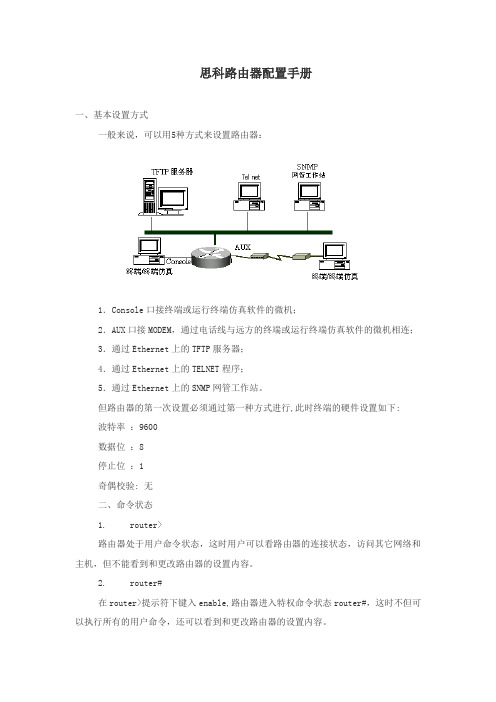
思科路由器配置手册一、基本设置方式一般来说,可以用5种方式来设置路由器:1.Console口接终端或运行终端仿真软件的微机;2.AUX口接MODEM,通过电话线与远方的终端或运行终端仿真软件的微机相连;3.通过Ethernet上的TFTP服务器;4.通过Ethernet上的TELNET程序;5.通过Ethernet上的SNMP网管工作站。
但路由器的第一次设置必须通过第一种方式进行,此时终端的硬件设置如下:波特率:9600数据位:8停止位:1奇偶校验: 无二、命令状态1. router>路由器处于用户命令状态,这时用户可以看路由器的连接状态,访问其它网络和主机,但不能看到和更改路由器的设置内容。
2. router#在router>提示符下键入enable,路由器进入特权命令状态router#,这时不但可以执行所有的用户命令,还可以看到和更改路由器的设置内容。
3. router(config)#在router#提示符下键入configure terminal,出现提示符router(config)#,此时路由器处于全局设置状态,这时可以设置路由器的全局参数。
4. router(config-if)#; router(config-line)#; router(config-router)#;…路由器处于局部设置状态,这时可以设置路由器某个局部的参数。
5. >路由器处于RXBOOT状态,在开机后60秒内按ctrl-break可进入此状态,这时路由器不能完成正常的功能,只能进行软件升级和手工引导。
6. 设置对话状态这是一台新路由器开机时自动进入的状态,在特权命令状态使用SETUP命令也可进入此状态,这时可通过对话方式对路由器进行设置。
三、设置对话过程显示提示信息全局参数的设置接口参数的设置显示结果利用设置对话过程可以避免手工输入命令的烦琐,但它还不能完全代替手工设置,一些特殊的设置还必须通过手工输入的方式完成。
思科数据中心网络管理器(DCNM)系统管理配置指南说明书

C H A P T E R S e n d d o c u m e n t c o m m e n t s t o n e x u s 7k -d o c f e e d b a ck @c i s c o.c o m 13-1Cisco DCNM System Management Configuration Guide, Release 5.xOL-23625-0113Working With Threshold RulesThis chapter describes how to configure threshold rules using Cisco Data Center Network Manager(DCNM).This chapter includes the following sections:•Information About Threshold Rules, page 13-1•Configuring Threshold Rules, page 13-4Information About Threshold RulesThis section includes the following topics:•Threshold Rules Overview, page 13-1•Threshold Rule Examples, page 13-2Threshold Rules OverviewCisco DCNM provides a feature that you use to specify rising or falling threshold rules for sample variablesin collected statistical data. Depending on the rule definition, a set of actions are performed by Cisco DCNM.You define the threshold rule on the Threshold Rules page, and you apply the threshold rule to the existingchart.This section includes the following topics:•Rising Threshold, page 13-1•Falling Threshold, page 13-2•Threshold Rule Properties, page 13-2•Threshold Rule Actions, page 13-2Rising ThresholdThe rising threshold is the upper threshold for a sample variable. When the current sampled variable isgreater than or equal to the specified threshold, a set of actions is performed.Chapter13 Working With Threshold Rules Information About Threshold RulesF I N A L D R A F TFalling ThresholdThe falling threshold is the lower threshold for a sample variable. When the current sampled variable islower than or equal to the specified threshold a set of actions is performed.Note You can specify only one rising threshold and one falling threshold for a single sampled variable.Threshold Rule PropertiesThreshold rule properties are as follows:•Name—Specifies the threshold rule name.•Frequency—Specifies the number of times the sampled variable must cross a threshold before triggering any actions.•Period—Specifies the interval of time the frequency is monitored.•Repeat—Prevents the timer from resetting after triggering an action within the period.•Trend—Specifies the rising or falling threshold.Threshold Rule ActionsThreshold rule actions are as follows:•Send an email or SMS to a mail server or mail to SMS gateway.•Run a script on the server.•Send an event to the current DCNM JMS channel.Threshold Rule ExamplesNote The granularity of a period is driven by the minimal interval of the collected data. Consequently, the period must be higher than that interval.This section includes the following topics:•Trigger an Action Each Time a Threshold is Crossed, page13-2•Trigger an Action Only Once in a Period When a Threshold is Crossed, page13-3•Trigger an Action Every Fourth Period When a Threshold is Crossed, page13-4Trigger an Action Each Time a Threshold is CrossedTo trigger an action each time a threshold is crossed, set properties as follows:•Frequency—1•Repeat—YesFigure13-1 shows the trigger action when you set rule properties to the preceding values.Cisco DCNM System Management Configuration Guide, Release 5.xOL-23625-01F I N A L D R A F T 13-3Cisco DCNM System Management Configuration Guide, Release 5.x OL-23625-01Chapter 13 Working With Threshold RulesInformation About Threshold RulesFigure 13-1T rigger an Action Each Time a Threshold is CrossedIf the sampled variable crosses the threshold, an action is taken the first time it crosses the threshold. As a result, an action is performed each time the threshold is crossed.Trigger an Action Only Once in a Period When a Threshold is CrossedTo trigger an action only once in a period when a threshold is crossed, set properties as follows:•Frequency—1•Period—300•Repeat—NoFigure 13-2 shows the trigger action when you set rule properties to the preceding values.Figure 13-2T rigger an Action Only Once When a Threshold is Crossed Within a PeriodIf the sampled variable crosses the threshold, an action is taken the first time it crosses the threshold. For the remaining 5 minutes, an action will not be taken. As a result, an action is performed only once during the specified period.F I N A L D R A F T Cisco DCNM System Management Configuration Guide, Release 5.x OL-23625-01Chapter 13 Working With Threshold RulesConfiguring Threshold Rules Trigger an Action Every Fourth Period When a Threshold is Crossed To trigger an action every fourth period when a threshold is crossed, set properties as follows:•Frequency—4•Period—300•Repeat—NoFigure 13-3 shows the trigger action when you set rule properties to the preceding values.Figure 13-3T rigger an Action Every Fourth Period When a Threshold is CrossedIf the sampled variable crosses the threshold, an action is taken the fourth time it crosses the threshold. For the remaining 5 minutes, an action is not taken. As a result, an action is performed only once during the specified period.Configuring Threshold RulesThis section includes the following topics:•Creating Threshold Rules, page 13-4•Deleting Threshold Rules, page 13-5•Editing Threshold Rules, page 13-6•Viewing Threshold Rules, page 13-6•Applying a Threshold Rule to a Chart, page 13-6Creating Threshold RulesYou can create threshold rules using Cisco DCNM.DETAILED STEPSStep 1From the Feature Selector pane, choose DCNM Server Administration > Threshold Rules .Chapter13 Working With Threshold RulesConfiguring Threshold RulesF I N A L D R A F TStep2From the toolbar, choose New, and then choose New Threshold Rule.The Details and Threshold Bindings tabs appear in the Details pane, with the Details tab open.Step3Create a threshold rule as follows:a.In the Name field, enter a name.b.In the Description field, enter a description of the threshold rule.After you have enter a description, the Rising Threshold check box is automatically checked and theThreshold field in the Settings area is outlined in red.Note A field outlined in red indicates that an entry is required. A field outlined in yellow indicatesthat the entry is satisfactory.c.In the Settings area, enter a value in the Threshold field.Once you have entered a value, the three options in the Action area are outlined in red.d.In the Action area, provide one of the following:–Enter email addresses (delimited with commas)–Select Sent Event to forward events to the DCNM Event Browser–Enter a script nameThe script receives all data regarding the crossed threshold. The script can be written in anyprogramming language and saved in one of the directories of the system PATH.Note Ensure that the Cisco DCNM server is configured for an SMTP server. For more informationabout configuring the Cisco DCNM server, see the Cisco DCNM Installation and LicensingGuide, Release 5.x.e.(Optional) In the corresponding Settings and Action areas, configure a Falling Threshold.f.(Optional) Click the Threshold Bindings tab to view bindings.g.Click Deploy.The rule is deployed.When you exit Cisco DCNM and Save Pending Changes is checked in the Warning dialog box, click Yesto save the rule.Deleting Threshold RulesYou can delete rules using Cisco DCNM.DETAILED STEPSStep1From the Feature Selector pane, choose DCNM Server Administration > Threshold Rules.The rules appear in the Summary pane.Step2From the Summary pane, right-click the appropriate rule.Cisco DCNM System Management Configuration Guide, Release 5.x OL-23625-01Chapter13 Working With Threshold Rules Configuring Threshold RulesF I N A L D R A F TStep3From the drop-down list, choose Delete Threshold Rule.A warning dialog box appears and displays “Are you sure you want to delete?”Step4Click Yes.The rule is deleted.Editing Threshold RulesYou can view threshold rules using Cisco DCNM.DETAILED STEPSStep1From the Feature Selector pane, choose DCNM Server Administration > Threshold Rules.The rules appear in the Summary pane.Step2Edit any appropriate areas.Note You cannot edit the Name field.Viewing Threshold RulesYou can view threshold rules using Cisco DCNM.DETAILED STEPSStep1From the Feature Selector pane, choose DCNM Server Administration > Threshold Rules.The rules appear in the Summary pane.Step2Click on a rule to view it.Applying a Threshold Rule to a ChartYou can apply threshold rules using Cisco DCNM.DETAILED STEPSStep1From the Feature Selector pane, choose the appropriate feature. For example, if you wanted to see statistics for an Ethernet port, choose Interfaces > Physical > Ethernet.The available devices appear in the Summary pane.Step2From the Summary pane, choose the appropriate device.Cisco DCNM System Management Configuration Guide, Release 5.xOL-23625-01Chapter13 Working With Threshold RulesConfiguring Threshold RulesF I N A L D R A F TStep3Click the Statistics tab.Step4In the toolbar, click New Chart and then from the drop-down list choose the chart that you want to view.For example, if you wanted to see statistics for traffic, choose Traffic Statistics Chart.Step5In the chart toolbar, click Launch Threshold Setting.Cisco DCNM System Management Configuration Guide, Release 5.xOL-23625-01Chapter13 Working With Threshold Rules Configuring Threshold RulesF I N A L D R A F TCisco DCNM System Management Configuration Guide, Release 5.xOL-23625-01。
CISCO数据设置参考

CISCO路由器在ISDN与数据网间互连中的应用摘要:ISDN与数据网的互连是广州市商业通信网工程的一项重要工作,本文对路由器在两网互连中的桥梁作用做了一些介绍,重点在路由器参数配置和调试方面提出参考性意见。
关键词:ISDN 远程接入IP IOS随着Internet、Intranet、远程个人办公室的浪潮兴起,ISDN做为一种廉价、中高速的接入手段日益受到人们欢迎,各种含ISDN远程接入的网络产品纷纷涌现,针对市场的需求,国内一些电信部门推出了ISDN接入Internet、Intranet的业务。
目前,CISCO路由器在中国的数据网中扮演了重要的角色,本文将谈谈CISCO路由器在ISDN数据网间的互连中的应用。
一、CISCO路由器的ISDN功能及参数设置从网络结构看,可以划分为ISDN业务提供方和ISDN远程接入方,前者如电信部门、一些ISP等,后者多为用户。
图图1 ISDN业务提供方和ISDN远程接入方在业务提供者一侧,常用的带ISDN功能的CISCO路由器有7000系列、4500系列、3600系列;在远程接入方,常用的CISCO、ISDN路由器有2500系列中ISDN产品、1000系列中ISDN产品、760系列中ISDN产品,这几种产品均带有BRI端口,可提供2B+D共128K的接入速率,用户甚至可以采用CISCO200系列的PC内置ISDN适配卡,俞地犹如Modem一样拨号上网,只是传输网是基于ISDN而不传统的PSTN,本文将以4500、1000为例,介绍相应的参数配置,同时也对CISCO200系列作些介绍,至于760系列,虽然这是一种典型的远程ISDN接入设备,但不带CISCO的IOS软件,本文不作讨论。
1、按静态IP用户配置设想有如下一个网络,见图二。
图图二按静态IP用户配置的网络范例在这个例子中,用户申请到一个子网202.100.100.0/27,这是从C类网202.100.100.0/24划分出的一个子网,用户以CISCO1003路由器做为网关设备,经ISDN网与4500相连。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
CISCO路由器在ISDN与数据网间互连中的应用摘要:ISDN与数据网的互连是广州市商业通信网工程的一项重要工作,本文对路由器在两网互连中的桥梁作用做了一些介绍,重点在路由器参数配置和调试方面提出参考性意见。
关键词:ISDN 远程接入IP IOS随着Internet、Intranet、远程个人办公室的浪潮兴起,ISDN做为一种廉价、中高速的接入手段日益受到人们欢迎,各种含ISDN远程接入的网络产品纷纷涌现,针对市场的需求,国内一些电信部门推出了ISDN接入Internet、Intranet的业务。
目前,CISCO路由器在中国的数据网中扮演了重要的角色,本文将谈谈CISCO路由器在ISDN数据网间的互连中的应用。
一、CISCO路由器的ISDN功能及参数设置从网络结构看,可以划分为ISDN业务提供方和ISDN远程接入方,前者如电信部门、一些ISP等,后者多为用户。
图图1 ISDN业务提供方和ISDN远程接入方在业务提供者一侧,常用的带ISDN功能的CISCO路由器有7000系列、4500系列、3600系列;在远程接入方,常用的CISCO、ISDN路由器有2500系列中ISDN产品、1000系列中ISDN产品、760系列中ISDN产品,这几种产品均带有BRI端口,可提供2B+D共128K的接入速率,用户甚至可以采用CISCO200系列的PC内置ISDN适配卡,俞地犹如Modem一样拨号上网,只是传输网是基于ISDN而不传统的PSTN,本文将以4500、1000为例,介绍相应的参数配置,同时也对CISCO200系列作些介绍,至于760系列,虽然这是一种典型的远程ISDN接入设备,但不带CISCO的IOS软件,本文不作讨论。
1、按静态IP用户配置设想有如下一个网络,见图二。
图图二按静态IP用户配置的网络范例在这个例子中,用户申请到一个子网202.100.100.0/27,这是从C类网202.100.100.0/24划分出的一个子网,用户以CISCO1003路由器做为网关设备,经ISDN网与4500相连。
4500参考设置:……hostname center ;路由器名!username remote password 7 xxxxxx ;远程用户名及握手密码……ip subnet-zero ;允许使用第0子网isdn switch-type primary-net5 ;适应中国PRI标准!controller E1 0 ;对E1板进行时隙配置pri-group timeslots 1-31!……interface Serial0:15 ;对PRI端口进行配置ip address 202.100.100.32 ;RPI口的IP地址255.255.255.224……encapsulation ppp ;无数据流通时该端口的激活时间dialer idle-timeout 7200 ;规定远程用户dialer map ip 202.100.100.31 nameremotedialer-group 1 ;允许使用带宽聚合no fair-queue ;规定验证协议ppp multilinkppp authentication chap! ;静态路由……ip route 202.100.100.0255.255.255.224 202.100.100.61 ;权限限制……dialer-list 1 protocol ip permit……!end1003参考设置:……hostname remote ;远程用户名!username center password 7 xxxxxxxx ;中心路由器名及握手密码……ip subnet-zero ;允许使用第0子网isdn switch-type basic-net3 ;适应中国BRI标准!……interface Ethernet0 ;对以太端口设置ip address 202.100.100.1255.255.255.224! ;对BRI口设置interface BRIOip address 202.100.100.61255.255.255.224 ;指明B道速率encapsulation pppbandwidth 64……dialer idle-timeout 300 ;指明拨号号码dialer wait-for-carrier-time 60dialer map ip 202.100.100.62 namecenter broadcast……dialer load-threshold 1dialer-group 1no fair-queueppp multilinkppp authentication chap! ;静态路由……ip route 0.0.0.0 0.0.0.0202.100.100.62……dialer-list 1 protocol ip permit……!end2、按动态IP用户配置图图三按动态IP用户配置的网络范例这个例子与上例不同,用户是采用动态IP上网,更适合实际组网需要。
……hostname center!username remote password 7 xxxxxx……ip subent-zeroisdn switch-type primary net5!controller E1 0pri-group timeslots 1-31!……interface Serial0:15ip address 202.100.100.62255.255.255.224……encapsulation ppp ;规定用地址池分配IPpeer default ip address pool isdndialer idle-timeout 7200dialer-group 1no fair-queueppp multilinkppp authentication chap!……! ;设置地址池ip local pool isdn 202.100.100.33202.100.100.60……dialer-list 1 protocol ip permit……end200卡的驱动程序有基于DOS、windows3.1、windows95的版本,其中DOS与win31版本推荐使用Novel Netware ODI Client方式,默义采用ipx包,如果用户要用TCP/IP包,则需添加TCP/IP协议栈,win95自带TCP/IP栈,因此使用起来较方便,为了充分利用200卡所遵循的RFC171MultiLink PPP功能,最好安装微软公司提供的ISDN补丁软件MSISDN11.EXE。
3、混合IP用户配置例3说明了1003GN 200卡共存的例子。
图图三按混合IP用户配置的网络范例在这个例子中,4500的PRI口同时处理静态IP与动态IP用户。
hostname center!username remote password 7 xxxxxx……ip subnet-zeroisdn switch-type primary-net5!controller E1 0pri-group timeslots 1-31!……interface Serial0:15ip address 202.100.100.62 255.255.255.224……encapsulation ppppeer default ip address pool isdndialer idle-timeout 7200dialer map ip 202.100.100.61 name remotedialer-group 1no fair-queueppp multilinkppp authentication chap!……!ip local pool isdn 202.100.100.33 202.100.100.60……ip route 202.100.100.0 255.255.255.224 202.100.100.61 ……dialer-list 1 protocol ip permit……!end在上面的配置中,注意静态IP与地址池不要有冲突。
1003参考设置:……hostname remote!username center password 7 xxxxxxxx……ip subnet-zeroisdn switch-type basic-net3!……interface Ethernet0ip address 202.100.100.1 255.255.255.244!interface BRIOip address 202.100.100.61 255.255.255.244 encapsulation pppbandwidth 64……dialer idle-timeout 300dialer wait-for-carrier-time 60dialer map ip 202.100.100.62 name center broadcast……dialer load-threshold 1dialer-group 1no fair-queueppp multilinkppp authentication chap!……ip route 0.0.0.0 0.0.0.0 202.100.100.62……disler-list 1 protocol ip permit……!end以上提供了路由器上有关的ISDN参数设置,实际开放业务时,还需考虑系统和用户的安全问题,以及其它的一些附加功能,情况会更复杂,例如动态IP用户贴不应在本地路由器上开设,而应在专门的用户验证服务器上开设,从而引出路由器与验证服务器的信息交换问题,凡此种种,均超出本文讨论的范围,这里不作详细介绍。
二、利用CISCO路由器在ISDN与数据网互连工程中进行调试实际组网时,会出现各种各样的问题,利用是国内ISDN交换机应用还处于起步阶段,技术上仍有不成熟之处,工程人员缺乏经验,都为工程带来麻烦,虽然有各种ISDN专用测试仪,但价格昂贵,不易推广,而CISCO IOS丰富的调试命令可以对一般的故障进行跟踪分析,功能虽不强但很实用。
本文也做一些经验介绍。
以下是一些常用调试命令:1、show version:以1003为例:Cisco Internetwork Operating System SoftwareIOS(tm) 1000 Software (C1000-Y-M), Version 11.1(9),RELEASE SOFTWARE (fc1)Copyright (c) 1986-1997 by cisco Systems, Inc.Compiled Mon 27-Jan-97 12:48 by dschwartImage text-base:0x02004000,data-base:0x02233824ROM: System Bootstrap, Version 5.3.2(9) [vatran 9],RELEASE SOFTARE(fc1)ROM:1000 Bootstrap Software (C1000-RB00T-R), Version 10.3(9), RELEASE SOFTWARE(fc1)……System restarted by power-onSystem image file is …flash:cl001-y-mz.111-9‟,booted via flashcisco 1000(68360) processor (revision E)with 3584K/512K bytes of memory.Processor board ID 03921963Bridging software.Basic Rate ISDN software, Version 1.0.1 Ethernet/IEEE 802.3 interface.1 ISDN Basic Rate interface.Integrated NT1 for ISDN Basic Rate interface8K bytes of non-volatile configuration memory.4096K bytes of processor board PCMCIA flash(Read/Write).从上面可以获得软件版本信息,以了解对ISDN及其它网络功能的支持程度,还可知道flash文件,必要时用作TFTP传输用。
