SECURE DIRECT COMMUNICATION USING QUANTUM CALDERBANK-SHOR-STEANE CODES
导入设备介绍 导入保护REG615标准配置A说明书

—G U I DEFO R M S PECI FI C ATI ONInterconnection Protection REG615std configuration ANumerical interconnection protectionin medium-voltage networksThe relay is intended for protection, control, measurement and supervision of interconnection points of distributed generation units in utility and industrial power distribution systems.Mechanical and construction details• The relay shall have compact dimensions not exceeding 4U in height. The depth of the relay shall, without any additional raising frame, not exceed 160 mm when flush mounted so as not to foul with other equipment mounted inside the cabinet.• The weight of the relay must not exceed 5 kgs to permit use of optimized sheet metal thickness in construction of panels.• The relay shall support flush, semi-flush, rack and wall mounting options.• As flush mounted, the relay shall meet the IP54 ingress protect ion requirements on the front side and IP20 on the rear side and connection terminals.• To facilitate quick unit replacement, the relay design shall be of draw-out type with secure current transformer (CT) shorting . It shall be possible to quickly replace a faulty unit with a less than 30 minutes.• To prevent unauthorized detachment of the relay plug-in unit, the relay shall be provided with an integrated seal.• The relay shall have a graphical display with at least 7 rows of characters and up to 20 characters per row.Protection functionsDistributed Power Generation Units (DPGU):• In distributed power generation applications where the power generation units (PGU) are connected to the grid, the PGUs are required to comply with grid connection requirements (grid codes) including system stability, reactive power support, transient recovery and voltage-frequency regulations. The grid codes require the distributed PGUs to remain connected even during network disturbances to ensure grid stability and reliability and thus avoiding a grid collapse. To enable the connection of distributed power generation units to the grid the relay shall include the following protection functions:-To determine whether and when to disconnect a distributed generation unit from the grid during network disturbances, the relay shall have three-stage low-voltage ride-through protection 27RT) with a user-definable Low-Voltage Ride-Through (LVRT) curve, to comply with local or national grid cod e requirements.-To ensure power system stability, the relay shall have directional reactive power and undervoltage protection (32Q,27) and monitor the reactive power flow to prevent a power system voltage collapse in the event of a network fault.-To detect islanding or loss-of-mains conditions of distributed generation units, the relay shall have vector shift protection (78V). The function shall continuously measure the voltage cycle shift in terms of the phase angle, which shall be settable between 2 and 30 degrees with 1 degree resolution.-The relay shall support the combined and parallel use of multiple protection functions to detect loss-of-mains conditions. The relay shall to minimize the non-detectable zone , support the combination of vector shift protection (78V) and frequency rate-of-change protection (81R), or other user-definable combinations of passive detecting techniques such as overvoltage, undervoltage, overfrequency, underfrequency, rate-of-change of frequency and voltage unbalance.-The relay must have three-stage frequency protection, including at least overfrequency (81O), underfrequency (81U) and frequency rate-of-change (81R) protection with rate-of-rise or rate-of-fall freely selectable for each stage.2 Other protection functions:• The relay shall have non-directional overcurrent(50) and earth -fault (50N) protection.• The relay shall have three-stage directionalovercurrent and earth-fault protection (67/67N)with voltage memory and positive and negative-sequence voltage polarization. I0 and Ushall bederived either from the phase voltages and currents or from the measured neutral current and residual voltage.• In compensated, unearthed and high-resistance earthed networks, the relay shall be able to detect transient, intermittent and continuous earth faults.• The relay shall have two-stage negative-sequence overcurrent protection (46) settable between 0.01and 5 times In , definite time (DT) and inversedefinite minimum time (IDMT) characteristics, supporting both IEC and ANSI/IEEE operating curves.• The relay shall have comprehensive voltage protection functionality, including at least overvoltage (59), undervoltage (27), positive-sequence undervoltage (47U+), negative-sequence overvoltage(47O-) and residual overvoltage (59G) protection with multiple stages.• The relay shall have three-phase thermal overload protection (49F).• The relay shall have a three-phase inrush detector (68) to avoid tripping during magnetizing inrush conditions. It shall be possible to selectively block the overcurrent and earth-fault protection stages when the ratio of the 2nd harmonic component to the fundamental component exceeds the set value.• To protect the generator and turbine from the harmful effect of excessive power/motoring, the relay shall have two stage reverse power/ directional overpower protection (32R/32O). It shall be possible to use positive-sequence components for calculating power, which makes the determination of power insensitive to the possible asymmetry in currents or voltages and corresponds to the real load of the generator’s prime mover . The protection function shall have a settable power angle between -90 to +90 degrees and an adjustable power setting range of 1 % to 200 %.• The relay shall have circuit breaker failure protection (51BF/5 1NBF) including independent timers for repeated tripping of the same breaker and backup tripping of the upstream breaker. The function shall allow higher selectivity by avoiding tripping of the upstream breaker if the repeated tripping of the breaker closest to the fault is successful.• The relay shall have arc protection based on simultaneous detection of current and light. During maintenance work at the substation, it shall be possible to change the operation criteria to light only via a binary input.Inputs and outputs• The relay shall have 12 binary inputs and 9 binary outputs and all of them freely configurable. Optionally, it must be possible to add 4 more binary inputs and 1 more binary output.• To enable direct tripping of the circuit breaker, the relay must have 2 double-pole power output relays with integrated trip-circuit supervision (TCS). The two power output relays shall be rated to make and carry 30 A for 0.5 s with a breaking capacity of ≥1 A (L/R<40 ms).• To enable fast direct tripping of the circuit breaker, the relay must have 3 optional high-speed binary outputs with an operate time of ≤ 1 ms. The binary output contacts shall be rated to make and carry 30 A for 0.5 s with a breaking capacity of ≥1 A(L/R<40 ms).• The threshold voltage of the relay’s binary inputs shall be set table to 16...176 V DC.• The relay shall be equipped with inputs for detecting temperature using resistance temperature detector (RTD) sensors. At least 2 inputs shall be required. It shall be possible to include the ambient temperature measured from an external temperature sensor in thermal modeling of the three-phase thermal protection for feeders.• The relay shall support the commonly used sensor types Pt100, Pt250 ,Ni100, Ni120, Ni250 and Cu10 with 2-wire or 3-wire connection with common ground.• The phase current inputs and the residual current input of the relay shall be rated 1/5 A. The selection of 1 A or 5 A shall be software based.• For applications requiring sensitive earth fault protection the relay shall offer an optional 0.2/1 A residual current input. The selection of 0.2 A or 1 A shall be software based.3Measurements, alarms and reporting• The relay shall have three-phase current and voltage measurement (fundamental or RMS-based as selectable options) with an accuracy of ±0.5% and zero, negative and positive-sequence current and voltage measurement functionality with an accuracy of ±1% within the range of ±2Hz of the nominal frequency.• To collect sequence-of-events (SoE) information, the relay must include a non-volatile memory with a capacity of storing at least 1024 event codes with associated time stamps.• The relay must support the storage of at least 128 fault records in the relay’s non-volatile memory.• The fault record values must at least include phase currents, phase voltages, zero, negative and positive-sequence currents and voltages, and the active setting group.• The relay shall have a disturbance recorder supporting a sampling frequency of 32 samples per cycle and featuring up to 12 analog and 64 binary signal channels.• The relay’s disturbance recorder shall support not less than 6 three-second recordings at 32 samples per cycle for 12 analog channels and 64 binary channels.• The relay shall support up to 100 disturbance recordings.• The relay must have a load profile recorder for phase currents and voltages supporting up to 12 selectable load quantities and more than 1 year of recording length. The load profile recorder output shall be in COMTRADE format.• The relay shall include a motor runtime counter for calculating and presenting the accumulated operation time of a machine. The function shall alert the operator via a warning and an alarm when the accumulated operation time exceeds the set munication• The relay must support IEC 61850 Edition 1 and Edition 2.• The relay must support, besides IEC 61850, simultaneous communication using one of the following communication protocols: Modbus® (RTU-ASCII/TCP), IEC 60870-5-103 orDNP3 (serial/TCP).• The relay must have an Ethernet port (RJ45) on the front for local parametrization and data retrieval.• The relay shall support up to five IEC 61850 (MMS) clients simultaneously.• The relay must have two fiber-optic Ethernet ports with HSR and PRP-1.• The relay shall have a third Ethernet port for providing connectivity of any other Ethernet device to an IEC 61850 station bus inside a switchgear bay.• The relay must support IEC 61850 GOOSE messaging and meet the performance requirements for tripping applications (<10 ms) as defined by the IEC 61850 standard.• The relay shall have support for sharing analog values like temperature, resistance, tap positions using IEC 61850 GOOSE messaging.• The relay must support IEEE 1588 v2 for high-accuracy time synchronization (< 4 μs) in Ethernet-based applications. The relay shall also support the SNTP (Simple Network Time Protocol ) and IRIG-B (Inter-Range Instrumentation Group - Time Code Format B) time synchronization methods.• The relay must support IEC 61850-9-2LE with IEEE 1588 v2 for accurate time synchronization.Engineering and configurability• The relay must have 6 independent settings groups for the relevant protection settings (start value, operate time). It must be possible to change protection setting values from one setting group to another in less than 20 ms from the binary input activation.• The relay must have a web browser-based human-machine interface (WHMI) with secured communication (TLS) and shall provide the following functions:-Programmable LEDs and event lists-System supervision-Parameter settings-Measurement display-Disturbance records-Phasor diagram-Single-line diagram (SLD)-Importing and exporting of parameters• When a protection function is disabled or removed from the configuration, neither the relay nor the programming tool shall show the function-related settings.• The relay HMI and engineering tool shall have multilingual support.• The relay HMI and engineering tool shall support IEC and ANSI protection function codes.• The relay shall have at least 11 freely configurable and programmable two-color LEDs.• The relay must have at least 10 user-configurable local HMI views including measurements and SLDs.• The relay shall have a graphical configuration tool for the complete relay application including multi-level logic programming support, timers and flip-flops.• The relay configuration tool must include online visualization of the relay application state.• It must be possible to keep the relay configuration tool up-to- date using an online update functionality.• The relay configuration tool shall support viewing of relay events, fault records and visualization of disturbance recordings.• The relay configuration tool must include the complete relay documentation including operation and technical details.• The relay configuration tool must include functionality for comparing the archived configuration to the configuration in the relay.• The relay configuration tool must allow configuration of IEC 61850 vertical and horizontal communication including GOOSE and sampled values.• The relay configuration tool must supportimporting and exporting of valid IEC 61850 files (ICD, CID, SCD, IID).• The relay configuration tool must be compatiblewith earlier relay versions.Type tests and other compliance requirements• The relay shall have an operational temperaturerange of -25 … +55°C and transport/storage temperature range of -40...+85°C.• The relay must fulfill the mechanical test requirements according to IEC 60255-21-1, -2 and-3, Class 2 for vibration, shock, bump and seismic compliance.• The relay’s maximum DC auxiliary power consumption shall be less than 20 W (all inputs activated and over the full supply range).• The relay must have an IEC 61850 Edition 2certificate from an accredited Level A testing laboratory.• The relay must fulfill the electromagnetic compatibility (EMC) test requirements accordingto IEC 60255-26.• The relay must be tested according to the requirements of the IEC or an equivalent standard. Additional informationFor more information, please contact your local ABB representative or visit our website at:/substationautomation/mediumvoltage1MRS758551B©Copyright218ABB.Allrightsreserved.—The information in this document is subject to change without notice and should not be construed as a commitment by ABB. ABB assumes no responsibility for any errors that may appear in this document. ABB is a registered trademark of the ABB Group. All other brand or product names mentioned in this document may be trademarks or registered trademarks of their respective holders.—/mediumvoltage。
成人高考真题试卷英语

Part I Listening Comprehension (25 points)Section A (5 points)In this section, you will hear 5 short conversations. At the end of each conversation, a question will be asked about what was said. Both the conversation and the question will be spoken only once. After each question there will be a pause. During the pause, you must read the four choices marked A), B), C) and D), and decide which is the best answer. Then mark the corresponding letter on Answer Sheet 1 with a single line through the centre.1. A) He doesn't want to join the sports club.B) He doesn't like the sports club.C) He wants to join the sports club.D) He is not sure about joining the sports club.2. A) She is a teacher.B) She is a student.C) She is a doctor.D) She is a nurse.3. A) They will go to the beach.B) They will go to the mountain.C) They will go to the park.D) They will go to the cinema.4. A) The man is a teacher.B) The man is a student.C) The man is a doctor.D) The man is a doctor.5. A) The woman will help the man.B) The man will help the woman.C) The woman will not help the man.D) The man will not help the woman.Section B (10 points)In this section, you will hear 5 short passages. At the end of each passage, you will hear some questions. Both the passage and the questions will be spoken only once. After you hear a question, you must choose the best answer from the four choices marked A), B), C) and D). Then mark the corresponding letter on Answer Sheet 1 with a single line through the centre.Passage 1Questions 6 to 8 are based on the passage you have just heard.6. A) He is a student.B) He is a teacher.C) He is a doctor.D) He is a lawyer.7. A) He likes to read books.B) He likes to watch movies.C) He likes to travel.D) He likes to play sports.8. A) He wants to become a writer.B) He wants to become a teacher.C) He wants to become a doctor.D) He wants to become a lawyer.Passage 2Questions 9 to 11 are based on the passage you have just heard.9. A) They are friends.B) They are colleagues.C) They are relatives.D) They are classmates.10. A) He is a doctor.B) He is a teacher.C) He is a lawyer.D) He is a student.11. A) He will go to the hospital.B) He will go to the library.C) He will go to the gym.D) He will go to the park.Passage 3Questions 12 to 14 are based on the passage you have just heard.12. A) She is a student.B) She is a teacher.C) She is a doctor.D) She is a nurse.13. A) She likes to read books.B) She likes to watch movies.C) She likes to travel.D) She likes to play sports.14. A) She will go to the library.B) She will go to the hospital.C) She will go to the gym.D) She will go to the park.Passage 4Questions 15 to 17 are based on the passage you have just heard.15. A) They are friends.B) They are colleagues.C) They are relatives.D) They are classmates.16. A) He is a doctor.B) He is a teacher.C) He is a lawyer.D) He is a student.17. A) He will go to the hospital.B) He will go to the library.C) He will go to the gym.D) He will go to the park.Passage 5Questions 18 to 20 are based on the passage you have just heard.18. A) She is a student.B) She is a teacher.C) She is a doctor.D) She is a nurse.19. A) She likes to read books.B) She likes to watch movies.C) She likes to travel.D) She likes to play sports.20. A) She will go to the library.B) She will go to the hospital.C) She will go to the gym.D) She will go to the park.Part II Structure and Vocabulary (30 points)Section A (15 points)In this section, there are 15 incomplete sentences. For each sentence there are four choices marked A), B), C) and D). Choose the one that best completes the sentence. Then mark the corresponding letter on Answer Sheet 1 with a single line through the centre.21. A) Because he was late for the meeting.B) Because he was tired of the meeting.C) Because he was hungry for the meeting.D) Because he was excited for the meeting.22. A) They are playing football.B) They are watching football.C) They are playing basketball.D) They are watching basketball.23. A) She is a teacher.B) She is a doctor.C) She is a nurse.D) She is a student.24. A) He is a doctor.B) He is a teacher.C) He is a lawyer.D) He is a student.25. A) She is a student.B) She is a teacher.C) She is a doctor.D) She is a nurse.26. A) He is a doctor.B) He is a teacher.C) He is a lawyer.D) He is a student.27. A) She is a student.B) She is a teacher.C) She is a doctor.D) She is a nurse.28. A) He is a doctor.B) He is a teacher.C) He is a lawyer.29. A) She is a student.B) She is a teacher.C) She is a doctor.D) She is a nurse.30. A) He is a doctor.B) He is a teacher.C) He is a lawyer.D) He is a student.31. A) She is a student.B) She is a teacher.C) She is a doctor.D) She is a nurse.32. A) He is a doctor.B) He is a teacher.C) He is a lawyer.D) He is a student.33. A) She is a student.B) She is a teacher.C) She is a doctor.D) She is a nurse.34. A) He is a doctor.B) He is a teacher.D) He is a student.35. A) She is a student.B) She is a teacher.C) She is a doctor.D) She is a nurse.Section B (15 points)In this section, there are 15 incomplete sentences. For each sentence there are four choices marked A), B), C) and D). Choose the one that best completes the sentence. Then mark the corresponding letter on Answer Sheet 1 with a single line through the centre.36. I'm sorry, but I can't come to the party tonight. I have to work late.A) because B) so that C) although D) in order that37. The teacher asked us to read the book before the class.A) in order to B) so that C) because D) in case38. I'm not sure if he will come to the meeting.A) unless B) whether C) because D) although39. He is too tired to go to the party.A) so that B) in order to C) because D) in case40. The weather is too hot to go out.A) so that B) in order to C) because D) in case41. She was happy to see her friend after a long time.A) so that B) in order to C) because D) in case42. The teacher was angry because the students were late.A) so that B) in order to C) because D) in case43. He was late for the meeting because he didn't have a car.A) so that B) in order to C) because D) in case44. She was worried about her exam because she didn't study hard.A) so that B) in order to C) because D) in case45. The doctor advised him to take medicine because he was sick.A) so that B) in order to C) because D) in case46. The teacher asked us to write a composition because we didn't have a topic.A) so that B) in order to C) because D) in case47. She was late for the train because she didn't leave on time.A) so that B) in order to C) because D) in case48. He was tired of the job because it was too difficult.A) so that B) in order to C) because D) in case49. The teacher was pleased with the students' performance because they worked hard.A) so that B) in order to C) because D) in case50. She was excited about the party because she had been looking forward to it for a long time.A) so that B) in order to C) because D) in casePart III Reading Comprehension (40 points)Section A (20 points)In this section, there are 4 passages, each with 5 questions. For each question there are four choices marked A), B), C) and D). You shoulddecide on the best answer to each question and mark the corresponding letter on Answer Sheet 1 with a single line through the centre.Passage 1Questions 51 to 55 are based on the following passage.The internet has changed our lives in many ways. It has made communication easier, provided access to a vast amount of information, and allowed us to connect with people from all over the world. However, it has also brought about some negative effects, such as information overload, privacy concerns, and cyberbullying.One of the most significant impacts of the internet is the way it has transformed communication. We can now send emails, chat with friends on social media platforms, and even make video calls. This has made it possible to stay in touch with people who are far away, regardless of time or distance. However, this constant connectivity can also lead to information overload, where we are bombarded with too much information, making it difficult to focus and process.Another negative effect of the internet is privacy concerns. With the rise of social media and online shopping, our personal information is more vulnerable than ever. Companies can track our browsing habits, and hackers can steal our passwords and other sensitive information. This has led to increased concerns about online privacy and the need for better security measures.Cyberbullying is another issue that has emerged with the rise of the internet. It involves using digital communication to harass, threaten, or intimidate someone. This can have serious consequences for the victims, including depression, anxiety, and even suicide. It isessential for parents, educators, and policymakers to address this issue and take steps to prevent cyberbullying.51. What is the main topic of the passage?A) The positive effects of the internet.B) The negative effects of the internet.C) The impact of the internet on communication.D) The challenges of online privacy.52. Which of the following is NOT mentioned as a negative effect of the internet?A) Information overload.B) Privacy concerns.C) Cyberbullying.D) Increased job opportunities.53. According to the passage, what is one of the ways the internet has changed communication?A) It has made communication slower.B) It has made communication more difficult.C) It has made communication easier.D) It has made communication more expensive.54. What is the author's opinion about the rise of social media?A) It has improved our privacy.B) It has increased our privacy concerns.C) It has decreased our privacy concerns.D) It has had no effect on our privacy.55. What is the author's suggestion to address the issue of cyberbullying?A) To increase the use of social media.B) To limit the use of the internet.C) To educate people about online safety.D) To ban all forms of digital communication.Passage 2Questions 56 to 60 are based on the following passage.The importance of exercise cannot be overstated. Regular physical activity has numerous benefits for both our physical and mental health. It can help us maintain a healthy weight, reduce the risk of chronic diseases, improve our mood, and increase our energy levels.One of the primary benefits of exercise is weight management. Regular physical activity helps burn calories and build muscle, which can help us maintain a healthy weight. Additionally, it can increase our metabolism, making it easier to maintain weight loss over time.Exercise also has a significant impact on our mental health. Physical activity can release endorphins, which are chemicals in the brain that make us feel good. This can help reduce symptoms of depression and anxiety, improve our mood, and increase our overall sense of well-being.Furthermore, exercise can reduce the risk of chronic diseases such as heart disease, diabetes, and certain types of cancer. Regular physical activity can help control blood pressure, improve cholesterol levels, and reduce inflammation in the body.In addition to the physical benefits, exercise can also improve our cognitive function. Studies have shown that regular physical activity can improve memory, attention, and problem-solving skills. This is especially important for older adults, who may experience a decline in cognitive function as they age.56. What is the main topic of the passage?A) The benefits of exercise for physical health.B) The benefits of exercise for mental health.C) The benefits of exercise for cognitive function.D)。
量子安全直接通信方案的研究

量子安全直接通信方案的研究王争艳; 李晖【期刊名称】《《微处理机》》【年(卷),期】2019(040)005【总页数】5页(P29-33)【关键词】量子通信; 单光子; Bell态; 量子安全直接通信【作者】王争艳; 李晖【作者单位】沈阳工业大学信息科学与工程学院沈阳110870【正文语种】中文【中图分类】TN9181 引言量子通信,作为运用量子力学基本原理及量子特性进行信息传输的一种通信方式,因其具有无条件安全、传输效率高、可利用量子物理纠缠资源等特点,受到人们的重视。
量子通信主要包括基于量子密钥分发的量子保密通信[1]、以量子隐形传态为主的量子间接通信[2]和量子安全直接通信[3]等模式。
诸多模式当中,量子安全直接通信是一种直接在量子信道中传输秘密消息的技术[4],它不需要事先传输秘钥,因此简化了通信过程。
2002年,Kim Bostrom 和Timo Felbinger 提出基于EPR 纠缠粒子的量子安全直接通信方案,即Ping-Pong 方案[5],该方案分为两个消息和控制模式,但它仅仅为一个准安全的方案。
2003年,邓富国等运用量子密集编码和块传输的思想,提出了基于纠缠对的Two-Step QSDC 方案[6],采用块传输思想保证通信的安全性。
根据加载信息载体的不同,量子安全直接通信的方案可大致分为两类:(1)基于单光子的量子安全直接通信;(2)基于纠缠的量子安全直接通信[7]。
其中,由于纠缠态具有独特的性质,基于纠缠的量子安全直接通信方案占大部分。
为提高传输效率,翁鹏飞等人提出W 态的量子直接通信方案[8],该方案利用密集编码对消息序列进行编码,利用W 态粒子的纠缠特性进行信道检测,保证信道的安全性。
2015年,Siddharth Patwardhan等人提出高效的受控量子安全直接通信[9],该方案的特点是仅在控制者允许的情况下方可传输信息。
2016年,曹正文等人提出基于Bell 态粒子和单光子混合的量子安全直接通信方案[10],该方案直接对量子态编码进行消息传送。
杨幼凤开题报告

对各章节进行撰写
完成论文初稿
2014.3-2014.4
论文修改并定稿
完成论文
6.主要参考文献
[1]BENNETT C H, BRASSARD G. Quantum cryptography: public key and coin tossing [J]. International conference on computers, Syatem & Signal Processing Bangalore,1984:175-179.
在1984年,Bennett和Brassard提出了第一个量子密钥分发协议,也就是有名的BB84协议[1]。在这个协议中,相距很远的通信双方,Alice和Bob共享一个密钥。Shimizu和Imoto于1999年第一个提出了量子安全直接通信(QSDC)[2],该协议中无需产生量子密钥,发送者可以直接传输经典秘密信息给接收者,提高通信效率。但是最早提出的量子安全直接通信方案只能实现通信双方单向秘密信息的传输,人么就考虑能否实现秘密信息的双向传输。在2004年,Nguyen[14]提出了第一个量子对话方案,实现了通信双方同时交换他们的秘密信息。自此,量子对话协议研究在学术界成为一个热点。2006年,Xia、Fu和Zhang等提出了一种基于GHZ态的量子对话方案;2007年,杨宇光和温巧燕提出了一种准安全量子对话协议[15];同年,Xia和Song[16]等提出了一个用纯纠缠GHZ态实现的受控安全量子对话协议;2008年,Ji等提出了一个用单光子实现的量子对话方案[17];2009年,Shi和Xi等提出了一个改进的利用EPR对实现的量子对话协议[18];同年,Li,Xiu和Gao等提出了一个基于一类三光子W态的量子对话协议[19];2008年,高等[20]指出了一些量子对话协议[14]中存在信息泄露问题,于是量子通信的安全开始受到人们的关注。提出的量子对话协议安全性是首当其冲要解决的问题。2010年,Shi和Xi等]提出了一种用单光子实现量子安全对话协议[20];Gao Gan也同时利用Bell态纠缠交换提出了两种可以克服信息泄露的量子对话方案[21];2013年,邹等[22]提出了一个受控的安全量子对话方案。还有一些量子对话协议理论[23-25]没有详细的列出。
电子专业学术语英文缩写简称对照表
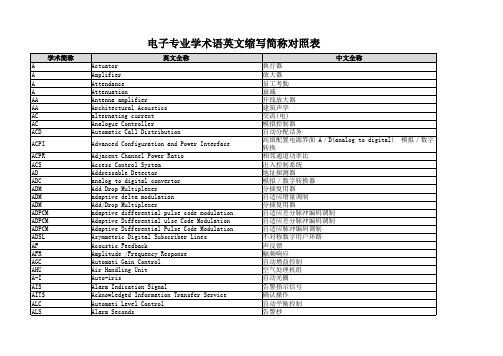
CC CCD CCD CCD CCF CCFL CCFL(CCFT) CCTV CCTV CD CD CDCA CDDI CDES CDMA CDMA CDMA CDR CDVCC CF CFM CIF CIS CISPR CLNP CLP CM CM CM CMI CMISE CMOS CMRS CMTS COB
算术逻辑单元 模拟用户线单元 调幅 管理模块 隔位标志翻转 接入网 美国国家标准学会 美国国家标准协会 全光网络指信号仅在进出网络时才进行电/光和光/电的变 All Optical Network 换,而在网络中传输和交换的过程中始终以光的形式存在。 Automatic Protection Switching 自动保护倒换 Access and Remote Control 接入和遥控 Automati Slope Control 自动斜率控制 American standard code for information interchange 美国信息交换标准码 Application-Specific Integrated Circuits 专用集成电路 Advanced Technology Attachment 高级技术附加装置 pulse code 脉冲码 Analogue Trunk Unit 模拟中继单元 Asynchronous Transfer Mode 异步传输模式 异步转移模式。将话音、图像、数据、视频等多种业务数字 Asynchronous Transfer Mode 化后转换成长度相同的分组(信元),包括信息域和元头, 根据元头的信息进行传送。 Asynchrous Transfer Mode 异步传送方式 Administration Unit 管理单元 AU Pointer Positive Justification 管理单元正指针调整 Administrative Unit Alarm Indication SignalAU 告警指示信号 Administration Unit Group 管理单元组 Loss of Administrative Unit Pointer AU指针丢失 AU Pointer Negative Justification 管理单元负指针调整 Administration Unit Pointer 管理单元指针 audio visual 声视,视听 Auchio &Video Control Device 音像控制装置 American Wire Gauge 美国线缆规格 Bridge Amplifier 桥接放大器 Building Automation & Control net 建筑物自动化和控制网络
如何在网上保证购物安全英语作文

全文分为作者个人简介和正文两个部分:作者个人简介:Hello everyone, I am an author dedicated to creating and sharing high-quality document templates. In this era of information overload, accurate and efficient communication has become especially important. I firmly believe that good communication can build bridges between people, playing an indispensable role in academia, career, and daily life. Therefore, I decided to invest my knowledge and skills into creating valuable documents to help people find inspiration and direction when needed.正文:如何在网上保证购物安全英语作文全文共3篇示例,供读者参考篇1How to Shop Online SafelyOnline shopping has become an integral part of our modern lives. With the convenience of being able to purchase anything from the comfort of our homes and having it delivered right toour doorsteps, it's no wonder that e-commerce has skyrocketed in popularity. However, as with any activity involving the internet and financial transactions, there are inherent risks that come with online shopping. As a student who frequently shops online for textbooks, clothes, and other essentials, I've learned the importance of taking precautions to ensure a safe and secure shopping experience.First and foremost, it's crucial to only shop on reputable and well-known websites. While there may be tempting deals on lesser-known sites, the risk of falling victim to fraudulent activities is much higher. Stick to established retailers with a proven track record of protecting their customers' personal and financial information. Additionally, look for websites that use secure socket layer (SSL) encryption, which is indicated by the "https://" prefix in the website's URL and a lock icon in the address bar.Before making a purchase, take the time to read reviews and research the seller or website thoroughly. Look for feedback from other customers, paying close attention to any complaints or issues related to security breaches, poor customer service, or product quality. It's also a good idea to check the website'sprivacy policy and terms of service to understand how they handle and protect your personal data.When it comes to payment methods, using a credit card is generally safer than a debit card or direct bank transfer. Credit cards offer additional fraud protection and the ability to dispute unauthorized charges more easily. If possible, consider using a virtual credit card or a service like PayPal, which adds an extra layer of security by keeping your actual credit card information hidden from the merchant.Strong and unique passwords are essential for online shopping. Avoid using easily guessable passwords or the same password across multiple accounts. Instead, opt for complex passwords that include a combination of uppercase and lowercase letters, numbers, and special characters. Consider using a password manager to generate and store unique passwords for each website you use.Be wary of suspicious emails, text messages, or pop-ups claiming to be from legitimate retailers. These could be phishing attempts aimed at tricking you into revealing sensitive information or downloading malware. Always verify the authenticity of such communications by contacting the retailerdirectly through their official website or customer service channels.When shopping on public Wi-Fi networks, such as those found in coffee shops or airports, it's best to avoid making any financial transactions or entering sensitive information. Public Wi-Fi networks are generally less secure and more susceptible to eavesdropping and man-in-the-middle attacks. If you must use public Wi-Fi, consider using a virtual private network (VPN) to encrypt your internet traffic and protect your online activities.After completing a purchase, keep a close eye on your bank or credit card statements for any unauthorized charges or suspicious activity. If you notice anything out of the ordinary, report it immediately to your financial institution and the retailer. Many banks and credit card companies have fraud protection policies that can help you recover any losses resulting from unauthorized transactions.Finally, be cautious when it comes to sharing personal information online. Avoid providing unnecessary details, such as your full name, address, or Social Security number, unless it's absolutely required for the transaction. Additionally, be wary of promotional offers or surveys that ask for excessive personalinformation, as these could be attempts to gather data for identity theft or other malicious purposes.By following these simple yet effective guidelines, you can significantly reduce the risks associated with online shopping and enjoy a safe and secure e-commerce experience. Remember, staying vigilant and taking proactive measures to protect your personal and financial information is key to navigating the digital marketplace with confidence.篇2How to Shop Safely OnlineAs students, we love the convenience of online shopping. With just a few clicks, we can order anything from new clothes and shoes to textbooks and school supplies. But online shopping also comes with risks like credit card fraud, identity theft, and getting ripped off with counterfeit goods. It's important to know how to protect yourself when shopping online.The first step is to only shop on secure, reputable websites that you can trust. Before entering any payment information, look for signs that the site is secure like a URL that starts with "https://" and a lock icon in the browser bar. Secure sites use encryption to protect your data as it gets transmitted. Majorretailers like Amazon, Walmart, Target etc. are generally very secure. But smaller retailers or unknown sites require more caution.Another red flag is if the website looks unprofessional with a lot of typos, blurry images, or strange product descriptions. Scammers often create fake online stores that exist just to steal credit card numbers. Do your research on the company and read reviews from other customers before placing an order. Stick to sites that you've heard of or that are recommended by friends.When entering payment information, be sure to use a credit card rather than a debit card if possible. Credit cards offer more protection against fraud and limit your liability if your card number gets stolen. Debit cards are linked directly to your bank account which scammers can drain if they get access.Never send cash, money orders, or wire transfers when buying online as these cannot be traced or reversed if you get scammed. Only use secure payment methods like credit cards or services like PayPal that allow you to dispute charges. Be very wary of sellers that request unusual payment methods.Another key tip is to never give out things like your Social Security number, birthdate, or mother's maiden name to online merchants as this information could be used for identity theft.Only provide the bare minimum information required to complete the purchase.When receiving shipments, check orders carefully as soon as they arrive to ensure you got the correct items as described. If anything is wrong or missing, contact the seller immediately. Keep good records like confirmation numbers and emails in case you need to follow up.For extra protection when shopping on a new site for the first time, use a virtual credit card number if your credit card company offers this feature. These are randomly generated numbers linked to your real card account but can easily be cancelled if compromised. Some browsers also offer options to use virtual card numbers when checking out online.Be very cautious of emails or calls claiming to be from a company about a shipping issue or problem with your order. These could be "phishing" attempts trying to get you to reveal personal or financial information. Only log into your account through the company's main website if you need to check an order status.Watch out for "too good to be true" deals like super low prices on luxury items or hot products. These are often counterfeit or stolen goods. Stick to prices that are reasonableand be skeptical of deeply discounted sales, especially on new release products.Another common scam to avoid is sellers asking you to go "off-site" and pay them directly versus using the secure online checkout. This is a big red flag. Only complete transactions using the official site's payment processing.While free public WiFi is convenient for mobile shopping, it also increases risks. Unsecured WiFi hotspots make it easier for hackers to intercept your data. It's best to avoid entering credit card numbers over public WiFi and instead wait until you're on a secure private connection.Finally, be very careful when clicking links in emails supposedly about shipping updates or promotions. Phishing emails often contain malicious links designed to steal your login credentials or download malware to your device. Always go directly to the retailer's main website rather than clicking links in emails.By following these precautions, we can shop online safely and avoid becoming victims of fraud or scams. It's all about shopping smart, using secure payment methods, watching for red flags, and knowing how to spot potential dangers. Withsome basic cybersecurity awareness, we can enjoy the convenience of online shopping worry-free!篇3How to Stay Safe While Shopping OnlineAs a student, online shopping has become a integral part of my life. With limited funds and a busy schedule, the convenience of being able to browse and purchase items from my dorm room is incredibly appealing. However, with the rise of cyber crimes and online scams, it's crucial to take precautions and ensure safe online shopping practices. In this essay, I'll share some valuable tips and strategies to help you navigate the world ofe-commerce securely.Stick to Reputable and Trusted WebsitesOne of the golden rules of online shopping is to stick to well-known and reputable websites. These established online retailers have invested heavily in security measures and have built a solid reputation for protecting customers' personal and financial information. Some examples of trusted websites include Amazon, eBay, Best Buy, and major retail chains with online stores.When shopping on unfamiliar websites, take the time to research the company's reputation. Look for customer reviews, check if they have a physical address and contact information listed, and see if they are accredited by organizations like the Better Business Bureau (BBB). A little due diligence can go a long way in avoiding potential scams and fraudulent websites.Secure Your Devices and Internet ConnectionBefore making any online purchases, ensure that your devices (laptops, smartphones, tablets) are protected withup-to-date antivirus software and firewalls. These security measures can help prevent malware and viruses from compromising your personal information.Additionally, it's essential to use a secure internet connection when shopping online. Public Wi-Fi networks, while convenient, are often unsecured and can leave you vulnerable to cyber attacks. Whenever possible, use a trusted private network or a virtual private network (VPN) to encrypt your internet traffic and protect your sensitive data.Use Strong and Unique PasswordsWeak or reused passwords are like leaving the front door of your digital life wide open for cyber criminals. To safeguard youraccounts and personal information, create strong, unique passwords for each website or online service you use. A strong password should be a combination of uppercase and lowercase letters, numbers, and special characters, and should be at least 12 characters long.Consider using a password manager to generate and store complex passwords securely. This way, you don't have to remember multiple complicated passwords, and your accounts remain protected.Embrace Two-Factor Authentication (2FA)Two-factor authentication (2FA) adds an extra layer of security to your online accounts by requiring a second form of verification beyond just a password. This could be a one-time code sent to your mobile device, a fingerprint or facial recognition, or a physical security key.Enabling 2FA on your shopping accounts and other sensitive online accounts significantly reduces the risk of unauthorized access, even if your password is compromised. Many online retailers now offer 2FA as an optional or mandatory security feature, so take advantage of it whenever possible.Be Cautious with Email Links and AttachmentsPhishing attempts, where cyber criminals try to trick you into revealing sensitive information or installing malware, often come in the form of emails with malicious links or attachments. Be extremely cautious when receiving unsolicited emails, especially those claiming to be from online retailers or financial institutions.Never click on links or open attachments from untrusted sources, as they may lead to fake websites designed to steal your login credentials or infect your device with malware. If an email seems suspicious, visit the official website directly by typing the URL into your browser or contacting the company through verified channels.Utilize Safe Payment MethodsWhen making online purchases, it's essential to use secure payment methods that offer buyer protection. Credit cards are generally the safest option, as they typically have fraud protection policies and allow you to dispute unauthorized charges more easily than debit cards or bank transfers.Additionally, consider using trusted online payment services like PayPal or Apple Pay, which add an extra layer of security by keeping your financial information separate from the merchant's website.Keep an Eye on Your StatementsRegularly monitoring your credit card and bank statements is crucial for detecting any unauthorized or suspicious activity. Many financial institutions now offer mobile apps and email alerts that can notify you of transactions in real-time, making it easier to spot potential fraud early on.If you notice any unfamiliar charges or discrepancies, report them immediately to your bank or credit card company. Acting quickly can help minimize potential losses and prevent further fraudulent activity.Be Cautious with Personal InformationOnline retailers often request personal information such as your name, address, and phone number during the checkout process. While this information is necessary for completing the transaction, be cautious about sharing any unnecessary personal details, especially sensitive information like your Social Security number or financial account numbers.Reputable online stores should have clear privacy policies that outline how they collect, use, and protect your personal information. Review these policies carefully and only share the minimum required information to complete your purchase.Stay Updated on Cyber Security TrendsCyber threats and online scams are constantly evolving, so it's essential to stay informed about the latest security risks and best practices. Follow trusted sources like government cybersecurity agencies, consumer protection organizations, and reputable technology publications for updates on emerging threats and recommended security measures.Additionally, many online retailers and financial institutions offer security awareness resources and tips for safe online shopping. Taking the time to educate yourself and stayup-to-date can help you stay one step ahead of cyber criminals.ConclusionOnline shopping has revolutionized the way we purchase goods and services, offering convenience and accessibility like never before. However, it's crucial to prioritize security and take proactive measures to protect yourself from cyber threats and online scams. By following the tips outlined in this essay, such as sticking to trusted websites, using strong passwords andtwo-factor authentication, being cautious with emails and personal information, and utilizing safe payment methods, you can enjoy the benefits of e-commerce while minimizing the risks.Remember, staying vigilant and informed about cyber security best practices is an ongoing process. As technology continues to evolve, so do the tactics of cyber criminals. By embracing a security-conscious mindset and staying up-to-date with the latest trends, you can navigate the online shopping world with confidence and peace of mind.。
MX行业领先云管理系统说明书

INDUSTRY-LEADING CLOUD MANAGEMENT• Unified firewall, switching, wireless LAN, and mobile device man-agement through an intuitive web-based dashboard• Template based settings scale easily from small deployments to tens of thousands of devices• Role-based administration, configurable email alerts for a variety of BRANCH GATEWAY SERVICES• Built-in DHCP, NAT, QoS, and VLAN management services • Web caching: accelerates frequently accessed content• Load balancing: combines multiple WAN links into a single high-speed interface, with policies for QoS, traffic shaping, and failover FEATURE-RICH UNIFIED THREAT MANAGEMENT (UTM) CAPABILITIES• Application-aware traffic control: bandwidth policies for Layer 7 application types (e.g., block Y ouTube, prioritize Skype, throttle BitTorrent)• Content filtering: CIPA-compliant content filter, safe-seach enforcement (Google/Bing), and Y ouTube for Schools• Intrusion prevention: PCI-compliant IPS sensor using industry-leading SNORT® signature database from Cisco• Advanced Malware Protection: file reputation-based protection engine powered by Cisco AMP• Identity-based security policies and application managementINTELLIGENT SITE-TO-SITE VPN WITH MERAKI SD-WAN• Auto VPN: automatic VPN route generation using IKE/IPsec setup. Runs on physical MX appliances and as a virtual instance within the Amazon AWS or Microsoft Azure cloud services• SD-WAN with active / active VPN, policy-based-routing, dynamic VPN path selection and support for application-layer performance profiles to ensure prioritization of the applications types that matter • Interoperates with all IPsec VPN devices and services• Automated MPLS to VPN failover within seconds of a connection failure• Client VPN: L2TP IPsec support for native Windows, Mac OS X, iPad and Android clients with no per-user licensing feesOverviewCisco Meraki MX Security & SD-WAN Appliances are ideal for organizations considering a Unified Threat Managment (UTM) solution fordistributed sites, campuses or datacenter VPN concentration. Since the MX is 100% cloud managed, installation and remote management are simple. The MX has a comprehensive suite of network services, eliminating the need for multiple appliances. These services includeSD-WAN capabilities, application-based firewalling, content filtering, web search filtering, SNORT® based intrusion detection and prevention, Cisco Advanced Malware Protection (AMP), web caching, 4G cellular failover and more. Auto VPN and SD-WAN features are available on our hardware and virtual appliances, configurable in Amazon Web Services or Microsoft Azure.Meraki MXCLOUD MANAGED SECURITY & SD-WANRedundant PowerReliable, energy efficient design with field replaceable power suppliesWeb Caching 128G SSD diskDual 10G WAN Interfaces Load balancing and SD-WAN3G/4G Modem Support Automatic cellular failover1G/10G Ethernet/SFP+ Interfaces 10G SFP+ interfaces for high-speed LAN connectivityEnhanced CPU Layer 3-7 firewall and traffic shapingAdditional MemoryFor high-performance content filteringINSIDE THE CISCO MERAKI MXMX450 shown, features vary by modelModular FansHigh-performance front-to-back cooling with field replaceable fansManagement Interface Local device accessMulticolor Status LED Monitor device statusFRONT OF THE CISCO MERAKI MXMX450 shown, features vary by modelCryptographic AccelerationReduced load with hardware crypto assistCisco Threat Grid Cloud for Malicious File SandboxingIdentity Based Policy ManagementIronclad SecurityThe MX platform has an extensive suite of security features including IDS/IPS, content filtering, web search filtering, anti-malware, geo-IP based firewalling, IPsec VPN connectivity and Cisco Advanced Malware Protection, while providing the performance required for modern, bandwidth-intensive yer 7 fingerprinting technology lets administrators identifyunwanted content and applications and prevent recreational apps like BitT orrent from wasting precious bandwidth.The integrated Cisco SNORT® engine delivers superior intrusion prevention coverage, a key requirement for PCI 3.2 compliance. The MX also uses the Webroot BrightCloud® URL categorization database for CIPA / IWF compliant content-filtering, Cisco Advanced Malware Protection (AMP) engine for anti-malware, AMP Threat Grid Cloud, and MaxMind for geo-IP based security rules.Best of all, these industry-leading Layer 7 security engines and signatures are always kept up-to-date via the cloud, simplifying network security management and providing peace of mind to IT administrators.Organization Level Threat Assessment with Meraki Security CenterSD-WAN Made SimpleTransport independenceApply bandwidth, routing, and security policies across a vari-ety of mediums (MPLS, Internet, or 3G/4G LTE) with a single consistent, intuitive workflowSoftware-defined WAN is a new approach to network connectivity that lowers operational costs and improves resource us-age for multisite deployments to use bandwidth more efficiently. This allows service providers to offer their customers the highest possible level of performance for critical applications without sacrificing security or data privacy.Application optimizationLayer 7 traffic shaping and appli-cation prioritization optimize the traffic for mission-critical applica-tions and user experienceIntelligent path controlDynamic policy and perfor-mance based path selection with automatic load balancing for maximum network reliability and performanceSecure connectivityIntegrated Cisco Security threat defense technologies for direct Internet access combined with IPsec VPN to ensure secure communication with cloud applications, remote offices, or datacentersCloud Managed ArchitectureBuilt on Cisco Meraki’s award-winning cloud architecture, the MX is the industry’s only 100% cloud-managed solution for Unified Threat Management (UTM) and SD-WAN in a single appliance. MX appliances self-provision, automatically pulling policies and configuration settings from the cloud. Powerful remote management tools provide network-wide visibility and control, and enable administration without the need for on-site networking expertise.Cloud services deliver seamless firmware and security signature updates, automatically establish site-to-site VPN tunnels, and provide 24x7 network monitoring. Moreover, the MX’s intuitive browser-based management interface removes the need for expensive and time-consuming training.For customers moving IT services to a public cloud service, Meraki offers a virtual MX for use in Amazon Web Services and Microsoft Azure, enabling Auto VPN peering and SD-WAN for dynamic path selection.The MX67W, MX68W, and MX68CW integrate Cisco Meraki’s award-winning wireless technology with the powerful MX network security features in a compact form factor ideal for branch offices or small enterprises.• Dual-band 802.11n/ac Wave 2, 2x2 MU-MIMO with 2 spatial streams • Unified management of network security and wireless • Integrated enterprise security and guest accessIntegrated 802.11ac Wave 2 WirelessPower over EthernetThe MX65, MX65W, MX68, MX68W, and MX68CW include two ports with 802.3at (PoE+). This built-in power capability removes the need for additional hardware to power critical branch devices.• 2 x 802.3at (PoE+) ports capable of providing a total of 60W • APs, phones, cameras, and other PoE enabled devices can be powered without the need for AC adapters, PoE converters, or unmanaged PoE switches.MX68 Port ConfigurationVirtual MX is a virtual instance of a Meraki security appliance, dedicated specifically to providing the simple configuration benefits of site-to-site Auto VPN for customers running or migrating IT services to the public cloud. A virtual MX is added via the Amazon Web Services or Azure marketplace and then configured in the Meraki dashboard, just like any other MX. It functions like a VPN concentrator, and features SD-WAN functionality like other MX devices.• An Auto VPN to a virtual MX is like having a direct Ethernetconnection to a private datacenter. The virtual MX can support up to 500 Mbps of VPN throughput, providing ample bandwidth for mission critical IT services hosted in the public cloud, like Active Directory, logging, or file and print services.• Support for Amazon Web Services (AWS) and AzureMeraki vMX100MX68CW Security ApplianceLTE AdvancedWhile all MX models feature a USB port for 3G/4G failover, the MX67C and MX68CW include a SIM slot and internal LTE modem. This integrated functionality removes the need for external hardware and allows for cellular visibility and configuration within the Meraki dashboard.• 1 x CAT 6, 300 Mbps LTE modem • 1 x Nano SIM slot (4ff form factor)• Global coverage with individual orderable SKUs for North America and WorldwideMX67C SIM slotSmall branch Small branch Small branch Small branch50250 Mbps250 Mbps250 Mbps200 Mbps1Requires separate cellular modemMX67MX67C MX68MX68CW 1Requires separate cellular modemMedium branch Large branch Campus orVPN concentrator Campus orVPN concentratorRack Mount Models 1Requires separate cellular modemVirtual AppliancesExtend Auto-VPN and SD-WAN to public cloud servicesAmazon Web Services (AWS) and Microsoft Azure1 + VirtualIncluded in the BoxPackage Contents Platform(s)Mounting kit AllCat 5 Ethernet cable (2)AllAC Power Adapter MX64, MX64W, MX65, MX65W, MX67, MX67W, MX67C, MX68, MX68W, MX68CWWireless external omni antenna (2)MX64W, MX65W, MX67W, MX68W250W Power Supply (2)MX250, MX450System Fan (2)MX250, MX450SIM card ejector tool MX67C, MX68CWFixed external wireless and LTE paddle antennas MX68CWRemovable external LTE paddle antennas MX67CLifetime Warranty with Next-day Advanced ReplacementCisco Meraki MX appliances include a limited lifetime hardware warranty that provides next-day advance hardware replacement. Cisco Meraki’s simplified software and support licensing model also combines all software upgrades, centralized systems management, and phone support under a single, easy-to-understand model. For complete details, please visit /support.ACCESSORIES / SFP TRANSCEIVERSSupported Cisco Meraki accessory modulesNote: Please refer to for additional single-mode and multi-mode fiber transceiver modulesPOWER CABLES1x power cable required for each MX, 2x power cables required for MX250 and MX450. For US customers, all required power cables will beautomatically included. Customers outside the US are required to order power cords separately.SKUMA-PWR-CORD-AUThe Cisco Meraki MX84, MX100, MX250, MX450 models support pluggable optics for high-speed backbone connections between wir-ing closets or to aggregation switches. Cisco Meraki offers several standards-based Gigabit and 10 Gigabit pluggable modules. Each appliance has also been tested for compatibility with several third-party modules.Pluggable (SFP) Optics for MX84, MX100, MX250, MX450AccessoriesManagementManaged via the web using the Cisco Meraki dashboardSingle pane-of-glass into managing wired and wireless networksZero-touch remote deployment (no staging needed)Automatic firmware upgrades and security patchesTemplates based multi-network managementOrg-level two-factor authentication and single sign-onRole based administration with change logging and alertsMonitoring and ReportingThroughput, connectivity monitoring and email alertsDetailed historical per-port and per-client usage statisticsApplication usage statisticsOrg-level change logs for compliance and change managementVPN tunnel and latency monitoringNetwork asset discovery and user identificationPeriodic emails with key utilization metricsDevice performance and utilization reportingNetflow supportSyslog integrationRemote DiagnosticsLive remote packet captureReal-time diagnostic and troubleshooting toolsAggregated event logs with instant searchNetwork and Firewall ServicesStateful firewall, 1:1 NAT, DMZIdentity-based policiesAuto VPN: Automated site-to-site (IPsec) VPN, for hub-and-spoke or mesh topologies Client (IPsec L2TP) VPNMultiple WAN IP, PPPoE, NATVLAN support and DHCP servicesStatic routingUser and device quarantineWAN Performance ManagementWeb caching (available on the MX84, MX100, MX250, MX450)WAN link aggregationAutomatic Layer 3 failover (including VPN connections)3G / 4G USB modem failover or single-uplinkApplication level (Layer 7) traffic analysis and shapingAbility to choose WAN uplink based on traffic typeSD-WAN: Dual active VPN with policy based routing and dynamic path selection CAT 6 LTE modem for failover or single-uplink1MX67C and MX68CW only Advanced Security Services1Content filtering (Webroot BrightCloud CIPA compliant URL database)Web search filtering (including Google / Bing SafeSearch)Y ouTube for SchoolsIntrusion-prevention sensor (Cisco SNORT® based)Advanced Malware Protection (AMP)AMP Threat Grid2Geography based firewall rules (MaxMind Geo-IP database)1 Advanced security services require Advanced Security license2 Threat Grid services require additional sample pack licensingIntegrated Wireless (MX64W, MX65W, MX67W, MX68W, MX68CW)1 x 802.11a/n/ac (5 GHz) radio1 x 802.11b/g/n (2.4 GHz) radioMax data rate 1.2 Gbps aggregate (MX64W, MX65W), 1.3Gbps aggregate (MX67W,MX68W, MX68CW)2 x 2 MU-MIMO with two spatial streams (MX67W, MX68W, MX68CW)2 external dual-band dipole antennas (connector type: RP-SMA)Antennagain:*************,3.5dBi@5GHzWEP, WPA, WPA2-PSK, WPA2-Enterprise with 802.1X authenticationFCC (US): 2.412-2.462 GHz, 5.150-5.250 GHz (UNII-1), 5.250-5.350 GHZ (UNII-2), 5.470-5.725 GHz (UNII-2e), 5.725 -5.825 GHz (UNII-3)CE (Europe): 2.412-2.484 GHz, 5.150-5.250 GHz (UNII-1), 5.250-5.350 GHZ (UNII-2)5.470-5.600 GHz, 5.660-5.725 GHz (UNII-2e)Additional regulatory information: IC (Canada), C-Tick (Australia/New Zealand), RoHSIntegrated Cellular (MX67C and MX68CW only)LTE bands: 2, 4, 5, 12, 13, 17, and 19 (North America). 1, 3, 5, 7, 8, 20, 26, 28A, 28B, 34, 38, 39, 40, and 41 (Worldwide)300 Mbps CAT 6 LTEAdditional regulatory information: PTCRB (North America), RCM (ANZ, APAC), GCF (EU)Power over Ethernet (MX65, MX65W, MX68, MX68W, MX68CW)2 x PoE+ (802.3at) LAN ports30W maximum per portRegulatoryFCC (US)CB (IEC)CISPR (Australia/New Zealand)PTCRB (North America)RCM (Australia/New Zealand, Asia Pacific)GCF (EU)WarrantyFull lifetime hardware warranty with next-day advanced replacement included.Specificationsand support). For example, to order an MX64 with 3 years of Advanced Security license, order an MX64-HW with LIC-MX64-SEC-3YR. Lifetime warranty with advanced replacement is included on all hardware at no additional cost.*Note: For each MX product, additional 7 or 10 year Enterprise or Advanced Security licensing options are also available (ex: LIC-MX100-SEC-7YR).and support). For example, to order an MX64 with 3 years of Advanced Security license, order an MX64-HW with LIC-MX64-SEC-3YR. Lifetime warranty with advanced replacement is included on all hardware at no additional cost.*Note: For each MX product, additional 7 or 10 year Enterprise or Advanced Security licensing options are also available (ex: LIC-MX100-SEC-7YR).and support). For example, to order an MX64 with 3 years of Advanced Security license, order an MX64-HW with LIC-MX64-SEC-3YR. Lifetime warranty with advanced replacement is included on all hardware at no additional cost.*Note: For each MX product, additional 7 or 10 year Enterprise or Advanced Security licensing options are also available (ex: LIC-MX100-SEC-7YR).。
通信保密技术的革命——量子保密通信技术综述

第5期2012年10月Journal of CAEITVol.7No.5Oct.2012檵檵檵檵檵檵檵檵檵檵檵檵檵檵檵檵檵檵檵檵檵檵檵檵檵檵檵檵檵檵殝殝殝殝“量子信息技术”收稿日期:2012-07-13修订日期:2012-10-11通信保密技术的革命———量子保密通信技术综述刘阳,缪蔚,殷浩(中国电子科学研究院,北京100041)摘要:量子保密通信技术由于其具有严格意义上的安全性,得到各国政府及相关研究机构的广泛关注,并在近年来取得突破性进展。
简述了量子力学基本原理、量子密钥分发的经典理论方案及具体实现技术;总结了国内外量子密钥分发技术发展的现状和水平;分析了量子保密通信存在的问题并展望了未来的发展趋势。
关键词:量子保密通信;量子密钥分发;量子纠缠中图分类号:TN918文献标识码:A 文章编号:1673-5692(2012)05-459-07A Revolution of Communication Security Technology—Summary of Quantum Security Communication TechnologyLIU Yang ,MIAO Wei ,YIN Hao(China Academy of Electronics and Information Technology ,Beijing 100041,China )Abstract :More governments or research institutions are paying attention to quantum security communica-tion technology because of its strict security and more breakthroughs.Sketching the basic principle of quantum mechanics ,classical theory of QKD and its realisation technique.Summarizing the current situ-ation of QKD home and abroad.Analyzing the problems and the trendency of quantum security communi-cation technology.Key words :quantum private communication ;quantum key distribution ;quantum entanglement引言经典保密通信主要采用两种体制。
量子通信技术发展现状及面临的问题研究_徐兵杰

摘 要: 量子通信具有更高的传输速率和更可靠的保密性,是世界各国正在研究和发展的通信技术 热点之一。首先介绍量子通信技术的基本概念、发展历程、系统架构、特点优势,然后重点阐述国内 外量子密钥分配、量子隐形传态、量子安全直接通信、量子机密共享等技术的研究进展情况,最后分 析量子通信技术研究和发展过程中面临的困难及局限。 关键词: 量子通信 密钥分配 隐形传态 机密共享 中图分类号: TN91 文献标志码: A 文章编号: 1002-0802( 2014) 05-0463-06
同时,随着点对点 QKD 技术的成熟,基于量子 密钥分发技术的中小型规模的量子保密通信网络在 美国、欧盟、日本、中国等得到的多次实验演示验证, QKD 技术已经逐步接近实用化。2004 年,美国雷神 公司组和波士顿大学在 DARPA 支持下建了世界上 第一个量子密码通信网络; 2008 年,欧盟“基于量子 密码的全球保密通信网络”( SECOQC) 研发项目组 建的 7 节点量子保密通信演示验证网络运行成功; 2009 年,由日本国家情报通信研究机构 ( NICT) 主 导,联合日本 NTT、NEC 和三菱电机,并邀请到东芝 欧洲有限公司、瑞士 ID Quantique 公司和奥地利 All Vienna 共同协作在东京建成了六节点城域量子通 信网络“Tokyo QKD Network”,集中展示了欧洲和日 本在量子通信技术上的最新技术; 2010 年起,美国 洛斯阿拉莫斯国家实验室秘密构建了城域量子通信 网络,直到 2013 年才公布; 中国先后建设了芜湖、合 肥、济南、北京等量子城域网,在 QKD 网络应用探索 方面走在世界前列。国庆 60 周年之际,中国在天安 门城楼、中南海、国庆阅兵指挥部等地点之间构建的 实时语音加密量子通信热线。总之,经过近 30 年的 发展,从技术指标上来讲,国际上 QKD 系统最远传
用三比特GHZ态实现量子稠密编码的方案

用三比特GHZ态实现量子稠密编码的方案麦麦提依明·吐孙;日比古·买买提明;阿力木·阿布都拉【摘要】This article introduced the scheme of Zhang San and Li Si has a pair of three bits largest entangled Greenberger - Horne - Zeilinger state ( GHZ state) to achieve a quantum dense coding, through this scheme will help realize quantum dense coding in multibody system. This article also introduces simple method of any three bits system’ s density matrix reduces to two bits density matrix.%文章介绍了考虑张三和李四拥有一对三比特最大纠缠态Greenberger–Horne–Zeilinger态(简称GHZ态)来实现量子稠密编码的一种方案,通过此方案有助于研究多体系统中实现量子稠密编码。
文章中还介绍从任意三比特系统的密度矩阵约化到两体系统密度矩阵的简单方法。
【期刊名称】《新疆师范大学学报(自然科学版)》【年(卷),期】2015(000)004【总页数】6页(P65-70)【关键词】纠缠态;稠密编码;幺正变换;约化密度矩阵【作者】麦麦提依明·吐孙;日比古·买买提明;阿力木·阿布都拉【作者单位】新疆师范大学物理与电子工程学院,新疆乌鲁木齐830054;新疆莎车县城南双语实验高中,新疆喀什844700;新疆师范大学物理与电子工程学院,新疆乌鲁木齐830054【正文语种】中文【中图分类】O431.2量子纠缠在量子信息处理过程中起着重要作用,而且量子纠缠的研究对量子信息论的发展有重大的意义[1-5],因为它在量子信息处理过程中的核心资源,如量子隐形传态[6],量子稠密编码[7],量子密钥分配[8]等等。
secure的近义词常用短语

secure的近义词常用短语secure有保护; (使)获得; 使安全等意思,那么你知道secure的近义词都有哪些呢?secure的常用短语都有哪些?下面店铺为大家带来secure的近义词辨析及常用短语,供大家参考学习!secure近义词:acquire, obtain, gain, get, win, earn, securesecure近义词辨析:这些动词均含"获得,取得,得到"之意acquire 强调通过不断的、持续的努力而获得某物,也指日积月累地渐渐地获得。
书面语用词。
obtain 较正式用词,着重通过巨大努力、要求而得到所需或盼望已久的东西。
gain 侧重指经过努力或有意识行动而取得某种成就或获得某种利益或好处。
get 普通用词,使用广泛,可指以任何方式得到某物,也不一定要经过努力。
win 主要指通过努力、斗争、比赛等而获得胜利。
earn 侧重指依靠自己的劳动或因付出代价与有功而获得。
secure 强调要通过努力或竞争,或需要付出代价才能获得所渴望的东西。
secure的常用短语:secure communication 保密通信;安全通信secure electronic transaction 安全电子交易secure sockets layer 安全套层;安全套接层secure operating system 安全操作系统secure的英语例句:1. The dug-outs were secure from everything but a direct hit.除非是直接被击中,否则这个地下掩体是非常安全的。
2. He was indefatigable in his efforts to secure funding fornew projects.他不知疲倦地努力为新项目寻求资金。
3. I couldn't remember ever having felt so safe and secure.我从未有过如此安全的感觉。
IPD SE

IPD SEIntroductionIPD SE stands for Inter-Process Communication Design in Software Engineering. It refers to the design principles and practices employed when designing communication channels between different processes in a software system. Effective IPD SE is essential for ensuring seamless communication, coordination, and integration among various system components.Goals of IPD SEThe main goals of IPD SE are as follows:1.Reliability: IPD SE aims to establish reliable andfault-tolerant communication channels between processes.It ensures that messages are delivered accurately andefficiently, even in the presence of errors or failures.2.Efficiency: IPD SE focuses on designing efficientcommunication mechanisms that minimize latency andoverhead. This includes choosing appropriatecommunication protocols, minimizing message size, andoptimizing data serialization.3.Scalability: IPD SE must be scalable toaccommodate increasing demands as the system grows. It ensures that the communication architecture can handle a higher number of processes and increased message traffic without impacting performance.4.Flexibility: IPD SE allows for flexibility in choosingcommunication mechanisms and protocols. It shouldaccommodate different types of processes, such as client-server, peer-to-peer, or publish-subscribe architectures,and support different communication patterns, such assynchronous or asynchronous messaging.IPD SE Design PrinciplesTo achieve the goals mentioned above, the following design principles are commonly applied in IPD SE:1. Loose CouplingIPD SE encourages loose coupling between processes to enhance flexibility and maintainability. Loose coupling means minimizing dependencies between processes and allowing them to evolve independently. This is achieved by abstracting communication interfaces and protocols, using standardized message formats, and providing well-defined communication APIs.2. Message-Oriented CommunicationIPD SE favors message-oriented communication rather than shared memory or direct function calls. Messages are the primary means of communication between processes, allowing them to exchange data and synchronize their actions. Message-oriented communication provides better encapsulation, decoupling, and fault tolerance.3. Clear Communication Semantics and ContractsIPD SE emphasizes the need for clear communication semantics and contracts. Processes should agree upon the format, structure, and content of messages exchanged. It includes defining the expected behavior of the sender and receiver, error handling mechanisms, and possible message decoders.4. Error Handling and Fault ToleranceIPD SE must handle errors and failures gracefully. It includes defining error codes, exception handling mechanisms, and recovery strategies in case of message loss or network failures. Error detection, reporting, and recovery mechanisms should be in place to ensure reliable communication.5. Security and AuthenticationIPD SE addresses security and authentication concerns by implementing secure communication protocols, encrypting messages, and verifying the authenticity of the sender and receiver. It prevents unauthorized access, tampering, and interception of sensitive data.6. Performance OptimizationIPD SE considers performance optimization by minimizing message size, reducing network overhead, and optimizing message serialization and deserialization. It also involves adopting efficient communication protocols, such as UDP or TCP/IP, based on the system requirements.ConclusionIPD SE plays a crucial role in designing effective communication channels between processes in a software system. By following the design principles discussed above, developers can achieve reliable, efficient, and scalable communication, enabling seamless coordination and integration among system components. Implementing IPD SE principles ensures that the system can handle increasing demands, adapt to changes, and provide a robust and flexible communication infrastructure.。
ubuntu 路由规则

ubuntu 路由规则英文回答:Routing is an important aspect of network management in Ubuntu. It allows us to control the flow of network traffic by directing it through specific paths. In Ubuntu, we can configure routing rules using the `ip` command or by modifying the network configuration files.To add a routing rule using the `ip` command, we can use the following syntax:sudo ip route add <destination_network> via <gateway>。
For example, let's say we want to add a routing rule to send all traffic destined for the 192.168.1.0/24 network through the gateway with the IP address 192.168.0.1. We can use the following command:sudo ip route add 192.168.1.0/24 via 192.168.0.1。
This will add a routing rule that directs all traffic for the 192.168.1.0/24 network to the specified gateway.We can also modify the network configuration files to add persistent routing rules. The main configuration file is located at `/etc/network/interfaces`. We can add the following lines to the file to define a routing rule:up route add -net <destination_network> gw <gateway>。
通信原理(英文版)课件

Network Security
• Firewalls: Devices that filter incoming and outgoing traffic based on security policies to protect against unauthorized access or malicious attacks.
Modulation and Demodulation
Modulation
The process of varying a property of a carrier wave, such as its amplitude, frequency, or phase, in accordance with the information to be transmitted. This allows information to be carried over long distances through various media.
Channel Capacity and Data Rate
Channel Capacity
The maximum amount of information that can be transmitted over a communication channel without loss of data or degradation in signal quality. It is typically limited by the physical properties of the channel and the noise level present.
上海市2023-2024学年高二下学期期中考试 英语含答案

5.When weighing Thomas Jefferson’s legacy, one must consider, ______, his promotion of democratic principles, despite his ownership of slaves.
A.empathy-oriented; charitableB.empathy-oriented; established
C justice-oriented; demandingD.justice-oriented; needy
10.This moment is an opportunity to build a sharper UNESCO, a UNESCO with better delivery, ______ its ambitions and in line with the needs of the 21st century.
2.The basketball coach’s course is known for its ______ training, as he pushes his players to their limits to achieve maximum performance.
A.humbleB.intenseC.randomD.undying
A.once and for allB.in allC.after allD.above all
6.While these measures have been helpful in reducing the recent stress in financial markets, they ______ providing a lasting solution to the challenges.
rfc5245 中文翻译

rfc5245 中文翻译RFC5245是一种名为"中继和端到端点对点协议:基于用户数据报协议(UDP)的实时通信协议(RTP)扩展"的技术规范文档。
它描述了如何使用RTP和用户数据报协议(UDP)实现实时通信应用程序的传输和中继功能。
RF5245的用法非常广泛,特别适用于需要实时性和低延迟的应用场景,例如音频通信、视频通信和多媒体流传输等。
它提供了一系列功能和协议扩展,以改善传输的可靠性、效率和安全性。
以下是十个双语例句,展示了RFC5245的用法和场景:1. The application uses RFC5245 to establish a direct peer-to-peer connection for real-time audio communication.应用程序使用RFC5245来建立实时音频通信的直接点对点连接。
2. With the help of RFC5245, the video conferencing system achieves low-latency and high-quality video streaming.在RFC5245的帮助下,视频会议系统实现了低延迟和高质量的视频流传输。
3. The RFC5245 extension provides secure and encrypted transmission of multimedia data over the internet.RFC5245的扩展提供了在互联网上安全加密的多媒体数据传输。
4. Using RFC5245, the application can seamlessly switch between relayed and direct connections based on network conditions.利用RFC5245,应用程序可以根据网络条件无缝切换中继连接和直接连接。
Edexcel BTEC Level 2和3信息技术系统和原则通信技术单元指南说明书

Unit 29: Communication TechnologiesUnit code: F/601/7264QCF Level 3: BTEC SpecialistCredit value: 10Guided learning hours: 60Aim and purposeThe aim of this unit is to ensure learners understand the communication principles of computer networks, know the elements of data communications systems and develop the skills to implement network communications.Unit introductionNew and developing communication technologies are used within the business world to maximise productivity and access information, whether an employee is working an office or travelling the world.This unit focuses on communication technologies, examining their use within social and business communities. Learners will explore the devices and communication technologies they use on a daily basis and gain an understanding of systems, including mobile internet. Learners will look at network topologies and services, connection software and access methods amongst other areas. They will investigate the OSI and TCP/IP models. Communications technology includes a large range of devices, which are used in the business and social communities. Devices include many of the next generation wireless devices, games consoles and newer generations of mobile phones with voice and video streaming. This unit explores these devices along with their transmission methods and the underlying protocols that enable connectivity and transmission of data including signal theory and data elements. Learners will appreciate why particular transmission methods are chosen for particular situations and be able to compare the effectiveness of the different methods.Finally, learners will be able to use their knowledge and understanding to directly connect communication devices between users.This unit could be delivered as part of a system support and networking focus including other units with networking content. Although largely theoretical, the emphasis in this unit should be on practical activity to learners to understand how modern IT can be used to enhance the commercial and personal environment. This unit has links directly to other network units and the vendor units.Learning outcomes and assessment criteriaIn order to pass this unit, the evidence that the learner presents for assessment needs to demonstrate that they can meet all the learning outcomes for the unit. The assessment criteria determine the standard required to achieve the unit.On completion of this unit a learner should:Learning outcomes Assessment criteria1 Understand thecommunication principlesof computer networks 1.1 explain how networks communicate1.2 identify communication protocols and models2 Know the main elementsof data communicationssystems 2.1 identify different types of communication devices 2.2 describe what data elements are and why theyare important2.3 describe the principles of signal theory2.4 describe different transmission methods used3 Be able to implementdifferent forms of networkcommunications 3.1 create direct network communication betweentwo users3.2 set up interconnection devices for directcommunicationUnit content1 Understand the communication principles of computer networksComputer networks: types eg LAN, WAN, wireless; network topologies eg star; mesh;bus; tree (or hierarchical); ring; network services eg packet switched, ISDN,multiplexed, ATM, WAP, broadband; network software eg network operating system;network connection software; access methods eg CSMA/CD, CSMA/CA, token passing Network components: servers; workstation; network cards eg Ethernet, wireless, token ringInterconnection devices: eg switches, routers, bridges, wireless access points, mobile base stationsModels: eg open system interconnection (OSI) model, TCP/IP modelProtocols: eg Bluetooth®, Wifi, IrDa, cellular radio, GSM/UMTS, WAP, WML, 802.11 standards, TCP/IP, wireless security protocols2 Know the main elements of data communications systemsMain elements: communication devices; data elements; electronic communication methods; transmission media and methodsCommunication devices: wired devices eg data terminal equipment (DTE), data circuit terminating equipment (DCE); wireless devices eg 3G, GPRS, mobile phone, laptop, netbookSignal theory: digital signalling methods; representing data electronically (bits, bytes, packet structures); synchronous transmission; asynchronous transmission; error detection; error correction; bandwidth limitation; bandwidth noise; channel types eg telephone, high frequency (HF) radio, microwave, satellite; other issues egbandwidth, data compressionData elements: checksum eg cyclic redundancy check (CRC); encapsulation egframes, packets, datagrams; addresses; sequence numbersElectronic communication: methods eg simplex, duplex, half-duplex communication, parallel, universal serial bus, serial, infra red, Bluetooth, WiFi, 3GTransmission: methods eg coaxial, optical fibre, unshielded twisted pair (UTP),shielded twisted pair (STP), infrared, radio, microwave, satellite3 Be able to implement different forms of network communicationsInternet communication: terminology eg HTTP, HTTPS, FTP, SMTP; uniform resource locator; worldwide web; other eg blogs, wikis, video conferencing, vlogs, socialnetworkingSystem requirements: wired or mobile systems; communication services eg email, video, internet, software, configurationDirect communication: eg instant messaging, video communication, email, webphone, social networking, web conferencing, desktop sharingInterconnection devices: eg switches, routers, bridges, wireless access points, mobile base stationsEssential guidance for tutorsDeliveryThis unit could be delivered as part of a system support and networking focus which includes other units with networking content. The emphasis is on practical activity to enable learners the to understand how modern IT can be used to enhance the commercial and personal environment. This unit links directly to other network units and the practical element in 3.1 and 3.2 could link with the vendor units.Delivery of the theoretical aspects should focus on the most up-to-date technology available, including all the latest developments in mobile communications such as third generation technology.The practical aspects of the unit that are practical should be opportunities to use the main technologies listed in the unit content, such as 3G hardware and mobile computing technology, for example, a wireless PDA. Ideally, the tutor should try to secure as many of these technologies as is feasible. For those that the centre cannot provide, it is recommended that the tutor tries and sources outside examples of this form of technology to demonstrate to learners.As an addition to the practical element, it may be useful for learners to have some input from an IT communications technology specialist, who can give an insight into career progression within this sector, as well as providing up to the minute technical knowledge that learners can draw on.Outline learning planThe outline learning plan has been included in this unit as guidance and can be used in conjunction with the programme of suggested assignments. The outline learning plan demonstrates one way in planning the delivery and assessment of this unit.Topic and suggested assignments/activities and/assessmentIntroduction to the unitThe main elements of data communications systems:•whole-class exercise – tutor presentation on communication devices•directed research – using tutor-provided materials on signal theory•whole-class exercise – tutor presentation on data elements•whole-class exercise – tutor presentation on methods of electronic communication, followed by whole class•practical•whole-class exercise – tutor presentation on transmission media and methods, followed by whole class•practical.Communication principles of computer networks:•individual exercise – use tutor-provided materials to understand the features of networks•whole-class exercise – tutor demonstrates network components to class•whole-class exercise – tutor demonstrates interconnection devices to class. Assignment 1 – From End to EndTransmission protocols and models:•whole-class exercise – tutor presentation on the open system interconnection (OSI) model and the TCP/IP•model, followed by a practical•individual exercise – learn about different electronic communication protocols from tutor-provided materials.Assignment 2 – A Bespoke SolutionImplementing different forms of internet communications:•whole-class exercise – tutor presentation on internet communication terminology, followed by practical tasks•whole-class exercise – tutor presentation on system requirements, followed by practical tasks•whole-class exercise – tutor presentation on direct communication methods, followed by practical tasks.Assignment 3 – LAN ManagerAssessmentThis unit can be assessed using three assignments as outlined in the Programme of suggested assignment table. However, there are other valid ways of assessment and the programme of suggested assignment is only a suggestion.Suggested Assignment 1 – From End to EndEvidence for this assignment could be in the form of a series of leaflets, posters or web pages which are suitably illustrated and annotated.1.1 requires learners to explain how networks communicate. This can be evidenced diagrammatically with annotations and notes, or it could be part of a presentation.For 1.2, communication protocols and models should be described using graphics where appropriate.For 2.1, learners must identify different types of communication devices, addressing the prescriptive elements of the unit content.For 2.2, learners must describe what data elements are and why they are important. Learners need to describe the different elements, and their importance, in their own words.Suggested Assignment 2 – A Bespoke SolutionA presentation is the suggested evidence format for this assignment.2.3 requires learners to describe the principles of signal theory as outlined in the unit. 2.4 is about transmission methods.Suggested Assignment 3 – LAN Manager3.1 is practical, and each learner must create a direct communication link between two networked devices. This could be a short video, observation evidence, or a written summary.3.2 is also practical. In this case, learners must create interconnection devices for direct communication. As with 3.1, evidence could be a short video, observation evidence, or a written summary.Programme of suggested assignmentsThe table below shows a programme of suggested assignments that cover the assessment criteria in the assessment and grading grid. This is for guidance and it is recommended that centres either write their own assignments or adapt any Edexcel assignments to meet local needs and resources.Criteria covered Assignment title Scenario Assessment method1.1-2.2 From End toEnd An ISP hascommissioned you towrite publicity materialsexplaining some of thebasics of ITcommunication.Leaflets or poster.2.3, 2.4 A BespokeSolution A client wishes to knowmore abouttransmission signals.Produce a presentationto describe theprinciples and methodsused.Presentation.3.1, 3.2 LAN Manager The ISP has asked youto create a system thatwill enable two users tomake directcommunication. Observation records. Witness statement. Notes.Links to National Occupational Standards, other BTEC units, other BTEC qualifications and other relevant units and qualificationsThis unit forms part of the BTEC in IT sector suite. This unit has particular links with: Level 1 Level 2 Level 3Systems ArchitectureArchitectureSystemsSetting up an IT Network Networking PrinciplesNetworking Principles Computer NetworksAn Introduction toCommunicationTechnologiesThis unit maps to some of the underpinning knowledge from the following areas of competence in the Level 3 National Occupational Standards for IT (ProCom):4.7 Systems Design5.1 Systems Development5.3 IT/Technology Solution Testing.Essential resourcesLearners will need access to practical resources and suitable technology; they can also use simulators or multimedia tools to gain prior experience before handling live resources.Employer engagement and vocational contextsVisits to a local ISP or using the centre’s network would provide a suitable vocational context.Indicative reading for learnersTextbooksDodd AZ – The Essential Guide to Telecommunications, 4th edition (Prentice Hall, 2005) ISBN-10 0131487256, ISBN-13 978-0131487253Hallberg B – Networking: A Beginner’s Guide, 5th Edition (Osborne/McGraw-Hill US, 2009) ISBN-10 0071633553, ISBN-13 978-0071633550Lowe D – Networking All-in-One Desk Reference for Dummies, 3rd Edition (John Wiley & Sons, 2008) ISBN-10 0470179155, ISBN-13 978-0470179154Schiller J – Mobile communications, 2nd Edition (Addison Wesley, 2003) ISBN-10 0321123816, ISBN-13 978-0321123817WebsitesFunctional Skills — Level 2Skill When learners are …ICT – Using ICTcreating network communicationsSelect, interact with and use ICTsystems safely and securely fora complex task in non-routineand unfamiliar contextsICT – Developing, presenting andcommunicating informationsetting up communication devicesUse communications software tomeet requirements of a complextaskexplaining protocols and transmission methods. Combine and presentinformation in ways that are fitfor purpose and audience。
谈谈你对现代通讯工具的使用及看法作文英语

谈谈你对现代通讯工具的使用及看法英语作文1Modern communication tools have undoubtedly revolutionized the way we live and interact. Smartphones, for instance, have become an indispensable part of our daily lives. They have made communication incredibly convenient, allowing us to stay in touch with friends and family at any time and from anywhere. With just a few taps on the screen, we can share our thoughts, photos, and videos instantly. Moreover, they provide us with easy access to a vast amount of information, enabling us to learn and stay updated on various topics.However, along with these conveniences come certain drawbacks. The addiction to smartphones is a growing concern. Many people, especially teenagers, spend excessive amounts of time on their phones, neglecting real-life interactions and outdoor activities. This not only affects their physical and mental health but also hinders their ability to focus and develop essential social skills.Another issue is the threat of privacy leakage. Our personal data is often collected and used by various apps and companies without our explicit consent, raising serious privacy concerns.Social media platforms, on the other hand, have brought people closer together. We can reconnect with old friends and make new ones across theglobe. But they have also given rise to the phenomenon of "false socializing," where people present an idealized version of themselves, creating a sense of comparison and anxiety among users. Additionally, the overwhelming amount of information on these platforms often leads to information overload, making it difficult for us to filter out the useful from the useless.In conclusion, while modern communication tools have brought numerous benefits, we need to use them wisely and consciously to avoid the negative impacts they may have on our lives.2In today's digital age, modern communication tools have become an integral part of our lives and work. They have brought about significant changes and influences that cannot be ignored.Take remote office software, for instance. During the pandemic, it played a crucial role, allowing people to work from anywhere, breaking the geographical limitations. This not only ensured the continuity of business operations but also provided flexibility and convenience for employees. However, it also posed challenges. Without the direct supervision of the workplace, it demanded higher self-discipline and time management skills from individuals.Another example is the online education platform. It has revolutionized the way we learn. Students can access educational resourcesanytime and anywhere, enabling personalized learning. But it also tests the self-control and independent learning ability of learners. Some may struggle to stay focused and motivated in the absence of face-to-face interaction and supervision.In my view, modern communication tools are double-edged swords. On the one hand, they offer unprecedented convenience and efficiency, expanding our horizons and possibilities. On the other hand, they bring new challenges that require us to adapt and develop corresponding skills and qualities. We should make full use of their advantages while consciously avoiding the negative impacts, so as to better integrate them into our lives and work and promote our development and progress.3Modern communication tools have undoubtedly revolutionized the way we interact with one another. Take video calls, for instance. They have made it possible for relatives living far apart to see each other whenever they want, strengthening the bonds of family affection. I remember the times when I could chat with my grandparents who are in another city, and their smiles and kind words through the screen always warmed my heart.However, there is a flip side to this. Some people have become overly dependent on online communication and have neglected the importance of real-life companionship. They spend hours chatting on social media but fail to have meaningful conversations with the people sitting right next to them.I have witnessed friends constantly looking at their phones during gatherings, missing out on the precious moments of shared laughter and connection.In conclusion, modern communication tools are a double-edged sword. While they bring us closer to those who are physically distant, we must be cautious not to let them distance us from the ones who are right in front of us. We should strive to strike a balance, using these tools to enhance our relationships rather than allowing them to detract from the authenticity and depth of human interaction.4Modern communication tools have undoubtedly brought about revolutionary changes to our society. Take the prevalence of mobile payment as an example. It has greatly facilitated our daily lives, allowing us to make purchases with just a few taps on our smartphones. We no longer need to carry bulky wallets or worry about having the exact change. However, this convenience also comes with security risks. Cyber criminals can potentially exploit vulnerabilities to steal our financial information and cause significant losses.Another aspect is the Internet of Things (IoT) technology. It has enhanced the quality of our lives by enabling smart home devices to be controlled remotely. We can adjust the temperature of our houses, turn on the lights, and monitor security cameras from anywhere. But at the sametime, it raises concerns about data security and our increasing reliance on the network. A disruption in the network could leave us in a state of chaos and helplessness.In conclusion, while modern communication tools have brought numerous benefits, we must remain vigilant about the potential challenges they pose. We should take necessary precautions to safeguard our privacy and security, and use these tools wisely to truly enjoy the advantages they offer without falling victim to their drawbacks. Only by doing so can we ensure that these technological advancements continue to serve us positively and contribute to the sustainable development of society.5Modern communication tools have undoubtedly revolutionized the way we interact and exchange information. Take the example of virtual reality technology in the field of communication. It offers an immersive experience, allowing people to feel as if they are physically present in the same space, regardless of the actual distance. However, this also raises ethical concerns. For instance, the blurring of boundaries between virtual and real could lead to issues of identity and authenticity.Another cutting-edge development is quantum communication technology. Its potential to revolutionize information transfer is immense. It promises ultra-secure and near-instantaneous communication, which has significant strategic implications in various fields such as national securityand finance. However, its implementation on a large scale faces challenges related to cost and infrastructure.While these advancements bring countless benefits, they also pose challenges. The over-reliance on modern communication tools may lead to a decline in face-to-face interaction skills and a loss of genuine human connection. We must strike a balance between leveraging the power of these tools and preserving the essence of true communication.In conclusion, modern communication tools are a double-edged sword. Their impact on the future of humanity depends on how we utilize and regulate them. We need to be vigilant and ensure that they serve to enhance our lives rather than detract from them.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
SECURE DIRECT COMMUNICATION USING QUANTUM CALDERBANK-SHOR-STEANE CODESXin L¨u,Zhi MaState Key Laboratory of Information Security, Graduate School of Chinese Academy of Sciences,Beijing,100039,Chinaemail:lx@Deng-Guo FengState Key Laboratory of Information Security, Software Institute of Chinese Academy of Sciences,Beijing,100080,ChinaABSTRACTThe notion of quantum secure direct communication (QSDC)has been introduced recently in quantum cryptog-raphy as a replacement for quantum key distribution,in which two communication entities exchange secure clas-sical messages without establishing any shared keys pre-viously.In this paper,a quantum secure direct commu-nication scheme using quantum Calderbank-Shor-Steane (CCS)error correction codes is proposed.In the scheme, a secure message isfirst transformed into a binary error vector and then encrypted(decrypted)via quantum cod-ing(decoding)procedures.An adversary Eve,who has con-trolled the communication channel,can’t recover the se-crete messages because she doesn’t know the deciphering keys.Security of this scheme is based on the assumption that decoding general linear codes is intractable even on quantum computers.KEY WORDSQuantum cryptography;Secure direct communication1IntroductionQuantum key distribution provides a novel way to ob-tain ultimate security based on quantum mechanics,which cares about agreeing classical keys between two commu-nication entities over quantum channel[1].Different from quantum key distribution,quantum secure direct commu-nication permits important messages to be communicated directly without establishing a random shared key to en-crypt them.QSDC can be used in some special environ-ments,with an example where it is difficult to establish a session key between two communication parties.As a se-cure QSDC scheme,it requires that the secure messages encoded in the quantum states should not leak to an eaves-dropper Eve even if she has controlled the communication channel.A“good”QSDC scheme also expects that no ad-ditional classical messages are needed to exchange between communication entities except the encoded quantum mes-sages.Several QSDC protocols have been addressed re-cently.In2002,Beige et al.proposed a QSDC scheme based on sigle-photon two qubit states[2].In their scheme, the secure message can be read only after a transmission of an additional classical message for each qubit.Bostr¨o m and Felbingeer addressed a Ping-Pang QSDC protocol[3] using Einstein-Podolsky-Rosen(EPR)pairs as quantum in-formation carriers,in which the secure messages can be de-coded during the transmission and nofinal transmission of additional information is needed.However,w¨o jcik proved that,in this scheme,Eve can get a part of the secure mes-sage with some probability,especially in a noisy quantum channel.Recently,Deng et al.[4]put forward a quantum one-time-pad based QSDC scheme,in which batches of single photons were used to serve as a one-time-pad to en-code the secret messages.However,all the existed QSDC schemes need to publicize some additional classical mes-sages to check out whether there exist eavesdroppers over the quantum communication channel.In this paper,we propose a QSDC scheme using quan-tum Calderbank-Shor-Steane codes,more usually known as CSS codes,after the initials of the inventors of this class of codes.In the proposed scheme,we suppose that the channel between communication entities is noiseless.In this scheme,the receiver Bob sends some quantum states encoded using quantum CSS codes.Alice transforms the secure messages into some error vectors and applies these errors on the qubits and sends them to Bob.Bob receives the messages and recovers the secure messages.Security of this scheme is based on the fact that decoding an arbi-trary linear code is NP-hard and Goppa cods have efficient decoding algorithm.The remainder of this paper are ar-ranged as follows:Section2introduces the preliminaries and definitions that we will use in this paper.Section3describes the pro-posed QSDC scheme.Security analysis is performed in section4.Conclusions are made in section5.2Preliminaries2.1Quantum CSS CodesThe constructions of quantum CSS codes rely heavily on the properties of classical error-correcting codes[6,7]. Here,wefirst review the basic definitions of binary classi-cal linear codes.Let’s consider vectors and codes over the field F2,including two elements,one and zero.The num-ber of one’s in a binary vector v∈F2is called Hammingweight,noted as w(v).Hamming distance d(v,u)between two binary vectors v and u is w(v+w),which denotes the number of bits differing from each other between v and u.A binary linear code C is an[n,k]linear code over thefi-nitefield F2,or an[n,k]code,for short.If C has minimum distance d,which denotes the minimum distance between two distinct codewords,then C is called an[n,k,d]linear code over F2.A linear code c is always specified by an n by k generator matrix G whose entries are all zeroes and ones.The generator matrix G maps k bits of information to a set of binary vectors of length n,called codewords. Binary linear codes can be alternatively(but equivalently) formulated by so called parity matrix,which is used to per-form error-correction.The parity matrix H of a linear code [n,k]is an(n−k)×n matrix such thatHx=0(1) for all those and only those vectors x in the code C.The rows of H are n−k linearly independent vectors,and the code space is the space of vectors that are orthogonal to all of these vectors.A quantum bit,or a qubit,is a two-level system which can be in state|ψ =a|0 +b|1 .(2) The numbersαandβare complex numbers,always noted asα,β∈C,such that(α,β)=(0,0)and|a|2+|b|2=1. The way a qubit differs from a classical bit is that a qubit can be the superposition stateα|0 +β|1 ,not definitely in basis state|0 or|1 .An n-qubit state is a non-zero vector in the tensor product space(C2)⊗n=C2n.We usually choose the following orthonormal basis of C2n:{|a0a1···a n−1 =|a0 ⊗|a1 ⊗···⊗|a n−1|(a0,···,a n−1)∈F n2}(3) Thus an n-qubit state can be expressed by|ψ =(a0,···,a n−1)∈F n2c a0,···,a n−1|a0,···,a n−1= a∈F n2c a|a (4)where c a∈C.A quantum error correcting code(QECC)Q:[[n,k, d]]is a2k-dimensional subspace of the Hilbert space C2n. It is a way of encoding k-qubit quantum states into n qubits(k<n)such that any error in≤[d−12]qubits can bemeasured and subsequently corrected without disturbing the encoded states.d is called the minimal distance of Q. Quantum CSS codes can be constructed by using classical linear codes:Theorem1[6]Suppose that there exist two classical bi-nary linear codes C1=[n,k1,d1],C2=[n,k2,d2], and C1⊥⊆C2(so that n≤k1+k2).Then there exists a QECC Q:[[n,k=k1+k2−n,min{d1,d2}]].A set of its basis states can be expressed as{|c w =121 v∈C1⊥|w+v |w∈C2/C⊥1}.(5)Let G i,H i be the generator matrix and parity checkmatrix of C i respectively,(i=1,2).Without loss of gen-erality,we may assume that G2= H1D by C1⊥⊆C2,here the rank of D is k=k1+k2−n.Then each k-qubitbasis state|m =|m1···m k (m∈F k2)can be encoded into a quantum codeword|c m =12n−k12 v∈C1⊥|v+m·D=12n−k12 v∈C1⊥v+m1D(1)+···+m k D(k) (6)where D(j)is the j′th row of D,1≤j≤k.Quantum errors will occur when quantum states aretransmitted over quantum channels.There are three basicerrors on a qubit:bit error,phase error and their composi-tion,which can be described by Pauli matrices respectively:σx= 0110 ,σz= 100−1 ,σy= 0−i i0 .(7)For any a∈{x,y,z},r=(r1,···,r n)∈F n2,letσ[r]a=σ[r1]a⊗···⊗σ[r n]a,whereσ[r i]a= I if r i=0σa if r i=1.Then every error on n qubits can be represented as e=σ[X]xσ[Z]z,here X=(x1,···,x n),Z=(z1,···,z n)∈F n2.For convenience,we also use binary vector e=(X|Z)to describe the errorσ[X]xσ[Z]z.Then the error e acts onan n-qubit basis state|V =|v1,···,v n (V∈F n2)asfollowse|V =(−1)Z·V|X+V=(−1)z1·v1+···+z n·v n|x1+v1,···,x n+v n(8)The number of error positions on the quantum state|V canbe expressed asw q( e)=♯{i|(X i,Z i)=(0,0),1≤i≤n}(9).2.2Goppa CodesGoppa codes are an important class of linear codes,someof which can meet the Gilbert-Varshamov bound.Goppacodes have been widely used to construct public-key en-cryption systems and message authentication codes sincethey have a fast decoding algorithm and a large numberof nonequivalent classes[8].here we only consider binaryGoppa Codes.Definition 1Suppose g (z )is a polynomial of degree t over finite fields F 2m .Let L ={γ0,γ1,···,γn −1}⊂F 2m such that |L |=n and g (γi )=0for 0≤i ≤n −1.Then the Goppa code Γ(L,g )with Goppa polynomial g (z )is defined to be the set of codewords{c =(c 0,c 1,···,c n −1)∈F n 2|n −1 i =0c iz −γi≡0(mod g )(z ).(10)From the above definitions,it’s easy to know that Goppa code Γ(L,g )is uniquely determined by g (z )and L and has parameters [n,k ≥n −mt,d ≥t +1].By some computing results over finite fields we know that Goppa codes have a large number of nonequivalent classes,which makes it possible to construct cryptosystems by us-ing Goppa codes.The specific description of Goppa codes can refer to Ref.[11].3The Proposed SchemeLet C i =Γ(L i ,g i (z ))=[n,k i ,d i ](i =1,2)be both bi-nary Goppa codes such that C ⊥1⊆C 2,d =min {d 1,d 2},the Hamming weight of the error vectors t = d −12 ,k =k 1+k 2−n .We assume that the quantum channel used in this scheme is noiseless channel.3.1EncodingBob randomly chooses a generator matrix G i and paritycheck matrix H i of C i (i =1,2)such that G 2=H 1D,here the rank of D is k =k 1+k 2−n .He then randomly prepares a basis state |m such that m ∈F k 2and encodes it into |c using quantum CSS codes Q according to equation(6).Bob acts some error e′=(X ′|Z ′)on |c as |ψ =e ′|c=12n −k 12v ∈C 1⊥(−1)(v +m ·D )·Z ′|v +m ·D +X ′ (11)such that w q ( e ′)≤[t ]and t =[min {d 1,d 2}−1],d 1and d 2are defined the same as in Theorem 1.Bob keeps the matrixG i ,C i ,D (i =1,2)and the bits string e′,m as his private keys and sends |ψ to Alice over a public quantum channel.3.2Encryption Suppose that Alice has a privacy message p in hand and wants to transmit it to Bob securely.She firstly applies an algorithm (algorithm 1)to transform p into a binary errorvector e ′′=(X ′′|Z ′′)such that t ′′=w q ( e ′′)≤[t 2].Alice receives Bob’s qubits |ψ and applies error e ′′on them as |ψ′ =e ′′|ψ=12n −k 12v ∈C 1⊥(−1)(v +m ·D )·Z ′·Z ′′|v +m ·D +X ′+X ′′ (12)Alice sends |ψ back to Bob.For quantum CCS codes,there are 3t ′′·Nt ′′er-ror vectors whose Hamming weight is t ′′.Borrowing the idea from the literature [15],we can construct one-to-one correspondence between this set of quantum error vectorse ′′=(X ′′|Z ′′)and integer p if they satisfy 0≤p <3t ′′ N t ′′.Then,an algorithm can be devised to transform any integer p described above into a quantum error vector e ′′using the order-preserving mapping induced by the lexico-graphic order of the vectors and the natural order of the integers.Algorithm 1s ←⌊p/3t ′′⌋;u ←t ′′;v ←p ;ω←v −3u ·⌊p/3u ⌋For i =1,2,···,t ′′{if ω≥2·3m −i then {b i =2;u i ←1;v i ←1}else if 3m −i ≤ω<2·3m −i =0then {b i =1;u i ←1;v i ←0}else b i =0;u i ←0;v i ←1;}i=1;For j =1,2,···,N {if s ≥ N −j t ′′then {x ′′j ←u i ;z ′′j ←v i ;i ←i +1;s ← s −N −jt ′′;t ′′←(t ′′−1);}else x ′′j ←0;z ′′j←0;}3.3DecodingLet H (i )1,H (j )2represent the i ’th row of H 1and the j ’throw of H 2respectively,1≤i ≤n −k 1,1≤j ≤n −k 2.Bob receives the quantum state C and measures the eigen-values ofσ[H (i )1]x and σ[H (j )2]z (say (−1)z (i )and (−1)x (j ),z (i ),x (j )∈F 2)respectively.After that,Bob obtains the syndromes Y 1and Y 2.i.e.σ[H (i )1]x |Ψ =(−1)z (i )|Ψ ,1≤i ≤n −k 1σ[H (j )2]z|Ψ =(−1)x (j )|Ψ ,1≤j ≤n −k 2Y 1=(z (1),···,z (n −k 1)),Y 2=(x (1),···,x (n −k 2)).Bob computes Z =(z 1,···,z n ),X=(x 1,···,x n )∈F n2such thatH 1·Z T =Y T 1,(13)H 2·X T =Y T 2.(14)Bob obtains the error vector e=(X|Z)and recovers |m′ by decoding the quantum codes|ψ′ .He measures |m′ using computationally basis{|0 ,|1 }and compares the measurement result m′with his original bits m.If m= m′,he believes that eavesdropping happens in the quantum channel.Otherwise,he computes e′′=(X′′|Z′′)e′′=e+e′(15) and performs algorithm2to recover Alice’s secrete bits p. Algorithm2u←t′′;i=0;For j=1,2,···,N{b i←0;if(x′′j=1)∨(z′′j=1)then{s← s+ N−j t′′ ;t′′←(t′′−1);if(x′′j=1)∧(z′′j=1)then{b i=2;}else if(x′′j=1)∧(z′′j=0)then{b i=1;}else b i=0;}i=i+1;}k= t′′i=0b i·3i;p=s·3u+k.4Analysis4.1CorrectnessTheorem2(Correctness)Supposing all the entities in-volved in the scheme follow the protocol,then Bob obtains Alice’s secret messages correctly.Proof.The correctness of this scheme can be easily seen by inspection.In the absence of intervention and noise over quantum channel,Bob and Alice add some errors e′and e′′on the encoded messages respectively in the encoding and encryption phases.Because the summation of the numbers of error positions of e′and e′′is not larger than t,which can be corrected without disturbing the quantum states.Bob can obtain Alice’s secret message p by computing e′′= e′+e and performing algorithm2in the end of the decoding phase.By comparing the decoded bits m′with m,Bob can detect the existence of eavesdropper in the communication channel.4.2Security against eavesdroppingIn this subsection,we consider an adversary Eve who has controlled the quantum channel linking Alice and Bob and tries to recover the plaintext p that Alice has sent to Bob. Supposing Eve knows the parity check matrix H1and H2, she can obtain the error vectors if she can compute X and Z from the equations(13)and(14).We know that re-solving equations(13)and(14)equals to the problem of decoding general linear codes,which is an NP-C problem [8].Though quantum algorithms are shown exponentially faster than classical ones when coping with some problems, such as integer factor and discrete logarithm problem,it is widely believed that NP-C problems are still intractable by quantum(probabilistic)polynomial-time Turing machines [10].We know that the Goppa codes used in the proposed scheme are uniquely decided by polynomials g(Z)and or-dered sets L.Therefore,if Eve wants to get the fast de-coding algorithm of Goppa codes C1,C2,she mustfind g(z)and L.But the computational complexity of quantum Grover search algorithm to obtain g(z)and L by the key G2,H1is O((2mt n!)12),it’s still infeasible to break this cryptosystem by quantum searching algorithm in polyno-mial time.In fact,Eve doesn’t know the matrix H1,H2and G2because the generation matrices G1,G2and the parity check matrices H1,H2are Bob’s private keys.Therefore, the difficulties of Eve’s recovering of the secret messages are at least as decoding general linear codes.The essential difference between this scheme with the EPR protocol[3],Ping-Pong protocol[5]and one-time-pad based[4]protocol is that it doesn’t need to establish a quan-tum entangled channel and doesn’t need to exchange(or broadcast)any additional classical messages to detect the existence of eavesdropper.In the proposed scheme,eaves-dropping can be detected just by comparing some recov-ered bits m′and Bob’s original bits m.4.3Man-in-the-middle attackJust like all the existed QSDC schemes and Quantum key distribution,the proposed scheme does not also support the authenticity of the transferred message itself and works well only on an authenticated quantum channel.Similar to Diffie-Hellman protocol[13],this scheme permits Alice to communicate securely with Bob over an authenticated quantum channel without knowing Bob’s secret keys.An active adversary in the middle of the communication be-tween Alice and Bob can recover the secure messages and deceive both sides.This type of attack is so called man-in-the-middle attack(see protocol1).Protocol1(man-in-the-middle attack)1.Bob encodes|m using quantum CSS codes Q andadds some error e′,and sends the states|ψ to Alice.2.Eve intercepts|ψ and chooses a vicious message p′and transforms it to error vector e a.She applies er-ror e a on|ψ and obtains|ψa ,and she impersonates Alice to send them back to Bob.At the same time,she prepares another quantum states|ψe using her own CSS codes Q′(Q=Q′)and impersonates Bob to send them to Alice.3.Alice performs algorithm1and transforms her secretemessages p to e′′.She appplies error e′′on her re-ceived quantum states|ψe and sends them back to Bob.4.Eve intercepts Alice’s encoded states and decodesthem as e′′.She can do this because she knows the fast decoding algorithm of Q′.Eve recovers p using algorithm2and obtains Alice’s secrete states.5.The states Bob received in the decoding phase are thestates that Eve has sent and the messages Bob recov-ers are Eve’s spurious messages p′.There are two possible methods to avoid this kind of attack.One is to establish an quantum authenticated chan-nel between the communication entities.Another way is that the communication entities Alice and Bob should pre-share some secret keys.Studies of quantum message au-thentication are beyond the scope of this paper and the reader can refer to the literature[16].Though the security of this scheme should be based on the existence of quantum authenticated channel,it can be used to securely transmit messages in some special cases in which the transmission time is urgent and it is difficult to establish session keys between two communication parties.5ConclusionsError correcting codes have been widely used to construct cryptosytems in modern cryptography,including private-key and public-key encryption schemes.In this paper,a QSDC scheme is proposed using quantum CSS codes.In the proposed scheme,Alice can securely transmit some classical messages to Bob over an authenticated quan-tum channel without establishing any pre-shared keys and transforming any additional classical information.In this scheme,Alicefirstly maps her secure messages to some er-ror vector and applies this error on the encoded states that Bob sent to her.Eve can’t recover the plaintext because she knows nothing about Bob’s secrete keys.The security of the proposed scheme is based on the fact that decoding general linear codes is NP-C problem and Goppa cods have efficient decoding algorithm.References[1]Bennett,C.H.,Brassard,G.:Quantum cryptography:public key distribution and coin tossing.In:Proceed-ings of IEEE International Conference on Comput-ers Systems and Signal Processing,Bangalore,India (1984)175–179.[2]Beige A.,Englert B.G.,Kurtsierfer C.et al.:Se-cure communication with a publicly known key,Acta Phys.Pol.A.101(2002)357–368.[3]Bostr¨o m K.,Felbinger T.:Deterministic Secure Di-rect Communication Using Entanglement,Physics Review Letter.89(2002)187902.[4]Deng F.G.,and Long G.L.:Secure direct communica-tion with a quantum one-time pad,Physical ReviewA.69(2004)052319.[5]W`o jcik. A.:Eavesdropping on the“Ping-Pong”Quantum Communication Protocol,Physics Review Letter.90(2003)157901.[6]Calderbank A.R.,Shor P.W.:Good quantum error-correcting codes exist,Physics Review A.54(1996) 1098-1105.[7]Steane A.M.:Multiple particle interference and quan-tum error correction,Proc.Roy.Soc.Lond.A.452 (1996)2551-2577.[8]McEliece R.J.:A public-key cryptosystem based onalgebraic coding theory,DSN Prog.Rep.,Jet Prop.Lab.,Caltech,Jan(1978)114-116.[9]Shor,P.:Polynomial-time algorithms for prime fac-torization and discrete logarithms on a quantum com-puter.SIAM Review.41(1999)303–332.[10]Okamoto.T.,Tanaka K.,Uchiyama S.:Quan-tum public-key cryptosystems,In:Advances of Cryptology-CRYPTO2000,Lecture Notes in Com-puter Science,V ol.1880,Springer-Verlag,Berlin Heidelberg New York(2000)147–165.[11]MacWilliams F.J.,Sloane N.J.A.:The theory oferror-correcting codes,North-Holland,Amsterdam, 1977.[12]Grover,L.K.:A fast quantum mechanical algorithmfor database search.In:Proceedings of28th STOC.(1996)212–219.[13]Diffie,W.,Hellman,M.E.:New directions in cryp-tography,IEEE .Theory,IT-22(6)(1976) 644–654.[14]Nielson,M,Chuang,I.:Quantum computation andquantum Information,Cambridge university press, 2000.[15]Park,puter Networks.44(2004)265–273.[16]Barnum,C.,Gottesman,D.,Smith,A.et al.:Authen-tication of Quantum Messages.In:Proceedings of 43rd Annual IEEE Symposium on the Foundations of Computer Science,Vancouver,Canada(2002)449–458.。
