大学计算机组织与结构习题
计算机组织与结构智慧树知到答案章节测试2023年河北师范大学

第一章测试1.运算器的主要功能是执行()。
A:算术运算B:加减乘除运算C:逻辑运算D:算术运算和逻辑运算答案:D2.冯·诺依曼结构计算机中数据采用二进制编码表示,其主要原因是()。
A:便于用逻辑门电路实现算术运算B:制造两个稳态的物理器件较容易C:二进制的运算规则简单答案:ABC3.下列软件中,不属于系统软件的是()。
A:编译软件B:操作系统C:C语言源程序D:数据库管理系统答案:C4.MIPS描述()。
A:计算机的可靠性B:计算机的可扩充性C:计算机的整数运算速度D:计算机的可运行性答案:C5.下列选项中,能缩短程序执行时间的是()。
Ⅰ提高CPU的时钟频率Ⅱ优化数据通路结构Ⅲ对程序进行编译优化A:仅Ⅱ和ⅢB:Ⅰ、Ⅱ和ⅢC:仅Ⅰ和ⅡⅢD:仅Ⅰ和Ⅲ答案:B第二章测试1.88H可表示成多种形式,以下选项中错误的表示是()。
A:压缩型BCD码数88B:无符号十进制数136C:带符号十进制数-120D:8位二进制数-8的补码答案:D2.某计算机以两个字节存储短整数,若某短整数在内存中的机器码为FFFFH,则此短整数的真值不可能是()。
A:-1B:1C:0D:-7FFFH答案:B3.十进制-61的8位二进制原码是()。
A:00101111B:10101111C:10111101D:00111101答案:C4.当运算结果的最高位为1时,标志位()。
A:OF=1B:SF=1C:ZF=1D:CF=1答案:B5.若x=103, y=-25,则下列表达式采用8位定点补码运算实现时,会发生溢出的是()。
A:-x+yB:x+yC:-x-yD:x-y答案:D6.整数x的机器数为1101 1000,分别对x进行逻辑右移1位和算术右移1位操作,得到的机器数分别为()。
A:1110 1100、1110 1100B:1110 1100、0110 1100C:0110 1100、0110 1100D:0110 1100、1110 1100答案:D7.下列有关浮点数加减运算的叙述中,正确的是()。
2022年东北师范大学计算机科学与技术专业《计算机系统结构》科目期末试卷A(有答案)

2022年东北师范大学计算机科学与技术专业《计算机系统结构》科目期末试卷A(有答案)一、选择题1、下列关于虚拟存贮器的说法,比较正确的应当是( )A.访主存命中率随页面大小增大而提高B.访主存命中率随主存容量增加而提高C.更换替换算法能提高命中率D.在主存命中率低时,改用堆栈型替换算法,并增大主存容量,可提高命中率2、浮点数尾数基值rm=8,尾数数值部分长6位,可表示的规格化最小正尾数为( )A.0.5B.0.25C.0.125D.1/643、"一次重叠"中消除"指令相关"最好的方法是( )。
A.不准修改指令B.设相关专用通路C.推后分析下条指令D.推后执行下条指令4、“启动I/O”指令是主要的输入输出指令,是属于()。
A.目态指令B.管态指令C.目态、管态都能用的指令D.编译程序只能用的指令5、对机器语言程序员透明的是()A.中断字B.主存地址寄存器C.通用寄存器D.条件码6、除了分布处理、MPP和机群系统外,并行处理计算机按其基本结构特征可分为流水线计算机,阵列处理机,多处理机和()四种不同的结构。
A.计算机网络B.控制流计算机C.机群系统D.数据流计算机7、计算机系统结构不包括( )。
A.主存速度B.机器工作状态C.信息保护D.数据8、在多用户机器上,应用程序员不能使用的指令是()A.“执行”指令B.“访管”指令C.“启动IO”指令D“测试与置定”指令9、Cache存贮器常用的地址映象方式是( )。
A.全相联映象B.页表法映象C.组相联映象D.段页表映象10、从计算机系统结构上讲,机器语言程序员所看到的机器属性是()A.计算机软件所要完成的功能B.计算机硬件的全部组成C.编程要用到的硬件组织D.计算机各部件的硬件实现。
11、传统机器语言机器级,是用()来()机器指令。
A.硬件,翻译B.编译程序,翻译C.微指令程序,解释D.微指令程序,翻译12、IBM360/91对指令中断的处理方法是()A.不精确断点法B.精确断点法C.指令复执法D.对流水线重新调度13、输入输出系统硬件的功能对()是透明的。
计算机组成原理(微课版) 谭志虎习题答案

计算机组成原理(微课版)谭志虎习题答案1. 介绍计算机组成原理作为一门计算机科学与技术专业的必修课程,对于理解计算机硬件结构和原理起着重要的作用。
谭志虎编写的计算机组成原理习题集是一本很好的参考书籍,可以帮助学生巩固和应用课堂上学到的知识。
本文档为谭志虎习题集的答案,以Markdown文本格式输出。
2. 第一章题目2.1 问题一题目:计算机的五大基本组成部分是什么?简要描述每个部分的功能和作用。
答案:计算机的五大基本组成部分包括输入设备、输出设备、存储设备、控制单元和运算单元。
具体描述如下:•输入设备:用于将外部数据转换为计算机可以识别的内部数据格式,并将其传输给计算机的存储器或处理器。
常见的输入设备有键盘、鼠标、扫描仪等。
•输出设备:用于将计算机结果的数据转换为人类可以识别的形式,并输出给用户或其他外部设备。
常见的输出设备有显示器、打印机、音频设备等。
•存储设备:用于存储和访问计算机程序和数据。
存储设备可以分为主存储器和辅助存储器两种类型。
主存储器用于临时存储计算机当前正在处理的数据和程序,辅助存储器用于长期存储和备份数据和程序,例如硬盘、固态硬盘等。
•控制单元:用于控制和协调计算机的各个部件,指挥计算机的操作和工作流程。
控制单元负责解析和执行存储在存储器中的指令,控制数据传输和执行各种逻辑操作。
•运算单元:用于执行计算机的算术和逻辑运算。
运算单元包括算术逻辑单元(ALU)和寄存器,用于执行加法、减法、乘法、除法等算术运算,以及逻辑运算和位操作。
2.2 问题二题目:什么是存储器的存取周期?如何计算存储器的存取时间?答案:存储器的存取周期是指从发出存取请求到获得存储单元数据的时间。
存储器的存取时间由存储器的寻址方式和存储器的延迟时间决定。
计算存储器的存取时间的公式如下:存取时间 = 寻址时间 + 延迟时间其中,“寻址时间”指执行寻址操作所需的时间,包括指令地址的读取和指令地址的解码时间。
它取决于存储器的寻址方式和地址总线的宽度。
计算机组织与结构实验讲义(2014版)

计算机组织与结构实验讲义(2014版)任国林编写东南大学计算机科学与工程学院计算机组织与结构课程实验是为巩固教学效果而设置的,学生可以通过这些实验掌握计算机部件的逻辑组成及其工作原理,熟悉数字电路芯片的使用方法,提高逻辑设计能力,为设计计算机模型机打下基础。
计算机组织与结构课程实验共有4个,分别是运算器组成实验、存储器组成实验、寄存器组成实验、CPU数据通路实验。
所有实验均基于EDA工具Quartus II进行设计和功能仿真,条件允许时基于FPGA芯片进行功能验证。
实验一运算器组成实验一、实验目的(1)熟悉加/减法器的功能及使用方法。
(2)掌握算术逻辑部件(ALU)的功能及其逻辑组成。
(3)加深对运算器工作原理的理解。
二、实验内容(1)掌握Quartus II的使用方法,能够进行数字电路的设计及仿真。
(2)验证Quartus II所提供加/减法器的功能及使用方法。
(3)设计具有加法、减法、逻辑与、逻辑非4种功能的ALU,并进行功能仿真/验证。
三、实验原理及方案运算器是计算机硬件对数据进行加工的重要部件,算术逻辑部件ALU是其核心,还包括存放操作数和运算结果的寄存器/锁存器、存放运算结果状态的触发器等器件。
根据给定控制信号的不同,运算器可以实现不同的运算功能。
为便于运算器组成设计有效进行,先介绍一下Quartus II的使用方法。
1、基于Quartus II的电路设计及仿真方法基于Quartus II,电路设计的主要过程包括:建立工程文件、编辑原理图文件、编译原理图文件,电路仿真的主要过程包括:编辑仿真波形文件、生成功能仿真网表、验证仿真波形正确性。
以功能为Z=X·Y的电路为例,使用Quartus II、采用原理图方法进行电路设计的过程如下:1)建立工程文件:通过主菜单File→New Project Wizard可建立工程文件,包含5个页面的设置。
·第1页为设置工程文件信息,包括工程文件名、工作目录名·第2页为在工程中加入文件,可将已有的GDF文件添加到工程文件中,本例中无·第3页为选择FPGA器件型号,本例中采用Cyclone系列的EP1C6Q240C8芯片·第4页为添加准备使用的EDA工具,通常直接选择Next·第5页为查看、确认工程文件信息,无误时选择Finish即可。
数据结构复习题(计算机大专)

数据结构复习题1一、选择题1. 以下四类基本的逻辑结构反映了四类基本的数据组织形式,解释错误的是 ( ) A 、集合中任何两个结点之间都有逻辑关系但组织形式松散 B 、线性结构中结点按逻辑关系依次排列形成一条"锁链"C 、树形结构具有分支、层次特性,其形态有点像自然界中的树D 、图状结构中的各个结点按逻辑关系互相缠绕,任何两个结点都可以邻接2. 若结点的存储地址与其关键字之间存在某种映射关系,则称这种存储结构为( ) A 、顺序存储结构 B 、链式存储结构 C 、索引存储结构 D 、散列存储结构3. 在长度为n 的顺序表的第i (1≤i ≤n+1)个位置上插入一个元素,元素的移动次数为( ) A 、n-i+1 B 、n-i C 、i D 、i-14. 对于只在表的首、尾两端进行插入操作的线性表,宜采用的存储结构为( )A 、顺序表B 、用头指针表示的单循环链表C 、用尾指针表示的单循环链表D 、单链表5. 一个栈的入栈序列是a,b,c,d,e ,则栈的不可能的输出序列是( )A 、e d c b aB 、d e c b aC 、d c e a bD 、a b c d e6. 已知图1如右所示,若从顶点A 出发按深度优先搜索进行遍历,则可能得到的顶点序列为( ) A 、 A ,B ,E ,C ,D ,F B 、 A ,C ,F ,E ,B ,DC 、 A ,E ,B ,C ,F ,DD 、 A ,E ,D ,F ,C ,B7. n 个顶点的有向图中含有向边的数目最多为 ( )A 、n-1B 、nC 、n(n-1)/2D 、n(n-1) 8. 若一个栈的输入顺序是1,2,…,n ,输出序列的第一个元素是n ,则第i (1≤i ≤n )个输出元素是( )A 、n-iB 、n-i-1C 、i+1D 、n -i+1 9. 已给图2,( )是该图的正确的拓扑排序序列A 、1,2,3,4,5B 、1,3,2,4,5C 、1,2,4,3,5D 、1,2,3,5,4 10. 为查找某一特定单词在文本中出现的位置,可应用的串运算是( )A 、插入B 、删除C 、串联接D 、子串定位二、填空题A BC D E F 图1 1 2 34 5 图21.存储结构是逻辑结构的__________实现。
计算机存储和组织数据方式之《数据结构》关于“树”的习题(PPT内含答案)

• 12.已知二叉树的先序遍历和后序遍历不能唯一确定这棵 二叉树,这是因为不知道根结点是哪一个。
•
(T )
• 7.树结构中的每个结点最多只有一个直接前驱。 (T )
• 8.完全二叉树一定是满二叉树。 (F)
• 9.由树转换成二叉树,其根结点的右子树一定为空。 (T )
• 10.在先序遍历二叉树的序列中,任何结点的子树的所有 结点都是直接跟在该结点之后。( F )
• 11.一棵二叉树中序遍历序列的最后一个结点,发家是该 二叉树先序遍历的最后一个结点。 ( T )
B.CBDGFEA D.CBEGFDA
• 8.某二又树的后序遍历序列为DABEC,中序遍历序列为
DEBAC,则先序遍历序列为( D )。
• A.ACBED C.DEABC
B.DECAB D.CEDBA
• 9.在完全二叉树中,如果一个结点是叶子结点,则它没 有( C )。
• A.左孩子结点
B.右孩子结点
• 5.对于二叉树来说,第i层上最多有___2i-1______个结点。 • 6.由三个结点构成的二叉树,共有____5_____种不同的
结构。
• 7.由一棵二叉树的先序序列和___中序____序列可唯一 确定这棵二叉树。
习题6
• 9.先序序列和中序序列相同的二叉树为单右枝二叉树或 孤立结点。
• 10.设一棵二叉树共有50个叶子结点(终端结点),则有 ______49______度为2的结点。
• A. 5
B. 6
• C. 7
D. 8
• 6.二叉树的先序遍历序列为ABC的不同二叉树有( C ) 种形态。
• A. 3
B. 4
• C. 5
D.6
习题6
计算机组织与系统结构第四章习题答案
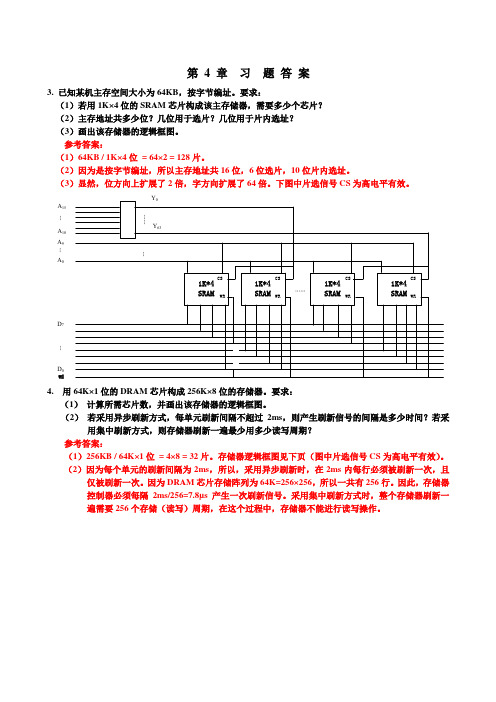
第 4 章 习 题 答 案3. 已知某机主存空间大小为64KB ,按字节编址。
要求: (1)若用1K×4位的SRAM 芯片构成该主存储器,需要多少个芯片? (2)主存地址共多少位?几位用于选片?几位用于片内选址? (3)画出该存储器的逻辑框图。
参考答案: (1)64KB / 1K×4位 = 64×2 = 128片。
(2)因为是按字节编址,所以主存地址共16位,6位选片,10位片内选址。
(3)显然,位方向上扩展了2倍,字方向扩展了64倍。
下图中片选信号CS 为高电平有效。
A 15A 10A 9A 0D 0D 7……WE…4. 用64K×1位的DRAM 芯片构成256K×8位的存储器。
要求:(1) 计算所需芯片数,并画出该存储器的逻辑框图。
(2) 若采用异步刷新方式,每单元刷新间隔不超过2ms ,则产生刷新信号的间隔是多少时间?若采用集中刷新方式,则存储器刷新一遍最少用多少读写周期? 参考答案:(1)256KB / 64K×1位 = 4×8 = 32片。
存储器逻辑框图见下页(图中片选信号CS 为高电平有效)。
(2)因为每个单元的刷新间隔为2ms ,所以,采用异步刷新时,在2ms 内每行必须被刷新一次,且仅被刷新一次。
因为DRAM 芯片存储阵列为64K=256×256,所以一共有256行。
因此,存储器控制器必须每隔2ms/256=7.8µs 产生一次刷新信号。
采用集中刷新方式时,整个存储器刷新一遍需要256个存储(读写)周期,在这个过程中,存储器不能进行读写操作。
A 17A 16A 15A 0D 0D 7………5. 用8K×8位的EPROM 芯片组成32K×16位的只读存储器,试问:(1)数据寄存器最少应有多少位? (2) 地址寄存器最少应有多少位? (3) 共需多少个EPROM 芯片? (4) 画出该只读存储器的逻辑框图。
计算机结构面试题目及答案

计算机结构面试题目及答案面试题一:什么是计算机结构?计算机结构是指计算机硬件系统的组成和工作原理,它包括计算机的内部组织结构、各部件之间的联系以及数据在计算机内部的传输和处理方式。
面试题二:请列举计算机结构的各个层次。
计算机结构包括以下几个重要层次:1. 逻辑门电路层:由多个逻辑门组成,实现基本的逻辑运算。
2. 组合逻辑层:由多个逻辑门构成组合逻辑电路,实现复杂的逻辑运算。
3. 时序逻辑层:在组合逻辑电路的基础上添加时钟信号,实现同步电路功能。
4. 微程序层:通过微指令控制计算机的操作,使计算机具备执行指令集的能力。
5. 控制器层:控制计算机的运行流程和各部件的工作状态,实现指令的解析和执行。
6. 运算器层:执行算术和逻辑操作,实现数据的处理和运算。
7. 存储器层:用于存储指令和数据,包括主存和辅存。
8. 输入输出设备层:将信息输入到计算机中或将计算机处理结果输出到外部设备。
面试题三:请解释冯·诺依曼结构。
冯·诺依曼结构是由冯·诺依曼于1945年提出的一种计算机结构,它是现代计算机设计的基础。
冯·诺依曼结构包括五个重要组成部分:输入设备、输出设备、存储器、运算器和控制器。
其中,存储器用于存储指令和数据,运算器用于执行算术和逻辑操作,控制器用于控制计算机的运行流程和各部件的工作状态,输入设备用于将信息输入到计算机中,输出设备用于将计算机处理结果输出到外部设备。
面试题四:请解释指令周期和时钟周期。
指令周期是指一个完整的指令执行所需要的时间,它包括取指令、指令解析、操作数取得、执行指令等各个阶段。
时钟周期是指计算机系统中的基本时钟信号的周期,它决定了计算机的工作速度。
一个指令周期通常由多个时钟周期组成。
面试题五:请解释数据通路和控制信号。
数据通路是指计算机中用于传输和处理数据的部件以及它们之间的连接方式。
数据通路包括运算器、寄存器、ALU(算术逻辑单元)等。
控制信号是指用于控制数据通路工作的信号,它通常由指令中的操作码产生,用于指示各个部件执行相应的操作。
系统结构习题

选择题第一章对计算机系统结构,下列()是透明的阵列运算部件计算机使用的语言是()。
分属于计算机系统各个层次实现汇编语言源程序变换成机器语言目标程序是由()。
汇编程序翻译系列机软件必须保证()。
向后兼容,力争向上兼容输入输出系统硬件的功能对( )是透明的。
应用程序员并行处理发展通过资源共享途径形成了( )。
分布式处理系统利用时间重叠实现并行处理的是( )。
流水处理机就使用语言的角度而言,可将计算机系统看成是按功能划分的()组成的层次结构多个机器级利用资源重复实现并行处理的是()。
阵列处理机计算机系统结构也称计算机体系结构,指的是( )。
传统机器级计算机的结构与组成不包括()。
操作系统字串位并是指同时对一个字的所有位进行处理,其并行等级( )。
已经开始出现的并行性计算机系列化的优点不包括( ) 同一系列内的软件一定是向下兼容的开发并行性的途径有时间重叠、资源重复和()。
资源共享对计算机系统结构,下列()是透明的阵列运算部件系列机软件必须保证向后兼容,一般应该做到()。
向上兼容用微程序直接解释另一种机器指令系统的方法称为仿真,用机器语言解释实现软件移植的方法称为()。
模拟高级语言是由()翻译成汇编语言程序编译程序就使用语言的角度而言,可将计算机系统看成是按功能划分的()组成的层次结构多个机器级VonNenmann型计算机不具有的特点是()。
以数据流驱动位片处理是指计算机采用()方式对数据进行处理。
字并位串除了分布处理、MPP和机群系统外,并行处理计算机按其基本结构特征可分为流水线计算机,阵列处理机,多处理机和()四种不同的结构。
数据流计算机费林按指令流和数据流的多倍性把计算机系统分类,这里的多倍性指()。
系统瓶颈部件上处于同一执行阶段的指令或数据的最大可能个数系列机在软件兼容上应该做到()。
向后兼容,并力争向上兼容计算机系统的层次结构按照由高到低的顺序分别为()。
高级语言机器级,汇编语言机器级,传统机器语言机器级,微程序机器级1TFLOPS计算机能力,1TBYTE/S的I/O带宽和()称为计算机系统的3T性能目标。
计算机组织与系统结构第七章习题答案

习题1.给出以下概念的解释说明。
指令流水线(Instruction pipelining)流水线深度(Pipeline Depth)指令吞吐量(Instruction throughput)流水线冒险(Hazard)结构冒险(Structural hazard)控制冒险(Control hazard)数据冒险(Data hazard)流水线阻塞(Pipeline stall)气泡(Bubble)空操作(nop)分支条件满足(Branch taken)分支预测(Branch predict)静态分支预测(Static predict)动态分支预测(Dynamic predict)延迟分支(Delayed branch)分支延迟槽(Delayed branch slot)转发(Forwarding)旁路(Bypassing)流水段寄存器(Pipeline register)IPC(Instructions Per Cycle)静态多发射(Static multiple issue)动态多发射(Dynamic multiple issue)超流水线(Superpipelining)超长指令字VLIW超标量流水线(Superscalar)动态流水线(Dynamic pipelining)指令预取(Instruction prefetch)指令分发(Instruction dispatch)按序发射(in-order issue)无序发射(out-of-order issue)存储站(Reservation station)重排序缓冲(Reorder buffer)指令提交单元(Instruction commit unit)乱序执行(out-of-order execution)按序完成(in-order completion)无序完成(out-of-order completion)2. 简单回答下列问题。
大学计算机第四章 练习题答案

第四章练习题答案(1) 下面叙述正确的是______ 。
(C)A)算法的执行效率与数据的存储结构无关B)算法的空间复杂度是指算法程序中指令(或语句)的条数C)算法的有穷性是指算法必须能在执行有限个步骤之后终止D)以上三种描述都不对(2) 算法的时间复杂度是指 ______ 。
(C)A. 执行算法程序所需要的时间B. 算法程序的长度C. 算法执行过程中所需要的基本运算次数D. 算法程序中的指令条数(3) 算法的空间复杂度是指 ______ 。
(D)A. 算法程序的长度B. 算法程序中的指令条数C. 算法程序所占的存储空间D. 算法执行过程中所需要的存储空间(4) 下列叙述中正确的是______ 。
(B)A) 算法的效率只与问题的规模有关,而与数据的存储结构无关B) 算法的时间复杂度是指执行算法所需要的计算工作量C) 数据的逻辑结构与存储结构是一一对应的D) 算法的时间复杂度与空间复杂度一定相关(5)算法的有穷性是指 ______ 。
( A )A)算法程序的运行时间是有限的B)算法程序所处理的数据量是有限的C)算法程序的长度是有限的D)算法只能被有限的用户使用(6) 数据的存储结构是指______ 。
( B )A. 数据所占的存储空间量B. 数据的逻辑结构在计算机中的表示C. 数据在计算机中的顺序存储方式D. 存储在外存中的数据(7) 下面描述线性表的链式存储结构错误的是 ______ 。
(A)A)线性表顺序存储B)线性表随机存储C)线性表的链式存储结构也称为线性链表D)线性表的链式存储结构只能顺序存取(8)数据的存储结构是指 ______ 。
( B)A.数据所占的存储空间量B.数据的逻辑结构在计算机中的表示C.数据在计算机中的顺序存储方式D.存储在外存中的数据(9) 下列叙述中正确的是______ 。
(D )A)一个逻辑数据结构只能有一种存储结构B)数据的逻辑结构属于线性结构,存储结构属于非线性结构C)一个逻辑数据结构可以有多种存储结构,且各种存储结构不影响数据处理的效率D)一个逻辑数据结构可以有多种存储结构,且各种存储结构影响数据处理的效率(10)下列叙述中正确的是 ______ 。
东南大学计算机组织结构2016试卷

东南大学考试卷( A 卷) 学号姓名密 封 线自觉遵守考场纪律如考试作弊此答卷无效学号 姓名4.(3points) One technique for implementing a control unit is referred to as hardwiredimplementation, in which the control unit is a combinatorial circuit. Its input logic signals, governed by the current machine instruction, are transferred into a set of output control signals.二、Fill blanks (Total 10points, 2 points/blank)1. A computer has a cache of 8k Bytes and a main memory of 16M Bytes dressed on Bytes.The address format is 13, 8, and 3 bits for Tag, Set, and Word respectively. It is needed to compare tags to search a word in the cache. For one word access, the times of tag comparison is ( ) at most.puter memory is organized into a hierarchy. At the highest level (closest to theprocessor) are the processor ( ).3.In ( ) addressing, the operand value is present in the instruction.4.In register windows the ( ) at one level are physically the sameas the parameter registers at the next lower level.5.Some dependencies, such as the write-write dependency of a symbol, can be solved by( ).三、Select A, B, C, or D corresponding to the best answer from the given items (Total 10 points, 2 points/blank)1.When a processor accesses a cache, the reference address is ( )A.Register addressB.Cache addressC.Main memory addressD.Disk address2.By using the ( ), a word is retrieved based on a portion of its contents ratherthan its address.A.direct accessB.random accessC.sequential accessD.associative access3.If most memory references are relatively near to the instruction being executed, then theuse of ( ) addressing saves address bits in the instruction.A.directB.indirectC.registerD.relative4.To perform a sequence of 16 instructions using pipeline, each instruction is divided into4 stages FI, DI, EI and WO, where each of the stages require 1 cycle, 1 cycle, 2 cyclesand 1 cycle respectively. No branch is in the sequence. The speed up factor of the pipeline is ( )A.5B.16/7C.4D.64/195.The degree of instruction-level parallelism is determined by the frequency of ( )and procedure dependency in the code.A.Read-Write dependencyB.Write-Write dependencyC.Write-Read dependencyD.Resource conflict四、Answer according to given contents ( Total 10 points,2 points/blank)Based on the current microinstruction, condition flags, and the contents of the instruction register, a control memory address must be generated for the next microinstruction. A wide variety of techniques have been used. We can group them into three general categories. These categories are based on the format of the address information in the microinstruction: two address fields, single address field, and variable format.The simples approach is to provide two address fields in each microinstruction. A multiplexer is provided that serves as a destination for both address fields plus the instruction register. Based on an address-selection input, the multiplexer transmits either the opcode or one of the two addresses to the control address register (CAR). The CAR is subsequently decoded to produce the next microinstruction address. The address-selection signals are provided by a branch logic module whose input consists of control unit flags plus bits from the control portion of the microinstruction.Although the two-address approach is simple, it requires more bits in the microinstruction than other approaches. With some addition logic, saving can be achieved. A common approach is to have a single field. With this approach, the options for next address are address field, instruction register code, and next sequential address.The address-selection signals determine which option is selected. This approach reduces the number of address fields to one. Note, however, that the address field often will not be used. Thus, there is some inefficiency in the microinstruction coding scheme.Another approach is to provide for two entirely different microinstruction formats. One bit designates which format is being used. In one format, the remaining bits are used to activate control signals. In the other format, some bits drive the branch logic module, and the remaining bits provide the address. With the first format. The next address is either the next sequential address or an address derived from the instruction register. With the second format, either a conditional or unconditional branch is being specified. One disadvantage of this approach is that one entire cycle is consumed with each branch microinstruction. With the other approaches. Address generation occurs as part of the same cycle as control signal generation, minimizing control memory accesses.The approaches just described are general. Specific implementations will often involve a variation or combination of these techniques.(1)Give a title for the above phases:(2)What are the “other approaches” underlined in the third phase?(3)What are the “these techniques” underlined in the last phase?(4)What are the “two entirely different microinstruction formats” underlined in the fifthphase?(5)Which of the mentioned address designate techniques has the highest bit efficiency onaverage? Why?五、Questions (Total 10 points)1.(4points) What is the relationship among direct mapping, associative mapping, and setassociative mapping in cache design?2.(3points) What are characteristics of RISC?3.(3points) What is the purpose of an instructionwindow?六、Problems (Total 48 points)1.(5 points) Suppose that a processor has access to two levels of memory. Level 1 contains1000 words and has an access time of 0.01 us; level 2 contains 100,000 words and has an access time of 0.1 us. Assume that if a word to be accessed is in level 1, then the processor accesses it directly. If it is in level 2, then the word is first transferred to level1 and then accessed by the processor. For simplicity, we ignore the time required for theprocessor to determine whether the word is in level 1 or level 2. Shows the average access time to the two-level memory as a function of the hit ratio H using a figure, where H is defined as the fraction of all memory accesses that are found in the faster memory.2.(5 points) An encoded microinstruction format is to be used. Show how an 8-bit micro-operation field can be divided into subfields to specify 38 different actions.3.(5 points) To compute Y=(A-B)÷(C+D ×E), we can use one-, two-, or three-address instructions, and we can also use zero addresses for some instructions. Zero-address instructions are applicable to a special memory organization, called a stack.a)Convert Y=(A-B)÷(C+D ×E) from infix to reverse Polish;b)List the instructions using a stack to compute Y=(A-B)÷(C+D ×E).4.(5 points) An instruction is 4 bytes long, and the start address in byte of the instruction is 360000 in decimal. PC-relative addressing mode is used in the instruction to access 0.010.1 0.111an operand and the displacement value in the address field is -30. Determine the address of the target operand.5.(10 points) A four-way set-associative cache has lines of 16 bytes and a total size of8kbytes.The main memory of 16-Mbyte is byte addressable.a)Show the format of main memory addresses;b)CPU is to read a data with address ABCDEF from the Cache-Memory structure.Describe the reading process step by step considering the cases of Hit and Miss;c)Draw a block diagram of this cache showing its organization and how the differentaddress fields are used to determine a cache hit/miss.6.(10 points) The instruction “AND X, (Y)” includes the following stages:a.Instruction Fetchb.Load AC the Data with address Xc.Indirect Addressingd.AND executione.Store AC to memory with address XShow the micro-operations of these stages and the corresponding control signals gate inthe figure.7.(8 points) Consider the following programA compiler for a RISC machine can either insert NOOP instructions or use delayed branch todeal with data dependencies and procedure dependences among instructions in the operation of pipelines. Assume that each instruction is divided into three stages: Fetch, Execute, (with or without) Write,a.Show the compiled code using NOOP instruction.b.Show the compiled code using delayed branch method.c.Draw diagrams to show the timing of instruction pipelines for traditional pipeline, RISCpipeline with inserted NOOP, and RISC pipeline with delayed branch.。
计算机架构面试题库及答案

计算机架构面试题库及答案1. 什么是计算机架构?计算机架构是指计算机系统的组织结构和功能实现方式,包括计算机的硬件组成、指令系统、数据类型和编程模型等。
2. 为什么需要面试计算机架构?在计算机领域,计算机架构是一个重要的概念,对于软硬件开发者以及计算机系统设计师而言,了解和掌握计算机架构是必不可少的。
面试计算机架构相关问题可以考察面试者的计算机基础知识、分析和解决问题的能力,以及对计算机系统优化和性能改进的理解。
3. 3.1 按照MIPS架构回答以下问题:1) 什么是MIPS?MIPS(Microprocessor without Interlocked Pipelined Stages)是一种常见的RISC(Reduced Instruction Set Computer)架构。
2) MIPS架构的特点是什么?MIPS架构的特点包括精简的指令集、固定长度指令、五级流水线,以及强大的编译器支持等。
3) MIPS架构流水线的五个阶段是什么?MIPS架构的流水线包括取指(IF)、译码(ID)、执行(EX)、访存(MEM)和写回(WB)五个阶段。
3.2 按照x86架构回答以下问题:1) 什么是x86架构?x86是一种常见的CISC(Complex Instruction Set Computer)架构,被广泛应用于个人计算机。
2) x86架构的特点是什么?x86架构的特点包括复杂的指令集、可变长度指令、多级缓存以及向下兼容性等。
3) x86架构中的寄存器有哪些?x86架构中包括通用寄存器(EAX、EBX、ECX、EDX等)、段寄存器(CS、DS、SS等)、指令指针寄存器(EIP)等。
4) x86架构的主要寻址方式是什么?x86架构的主要寻址方式是基于变址寻址和间接寻址的形式。
3.3 按照ARM架构回答以下问题:1) 什么是ARM架构?ARM(Advanced RISC Machine)是一种常用的嵌入式处理器架构,广泛应用于智能手机和物联网设备等领域。
计算机组织与系统结构第五章习题答案

第 5 章习题答案3.假定某计算机中有一条转移指令,采用相对寻址方式,共占两个字节,第一字节是操作码,第二字节是相对位移量(用补码表示),CPU每次从内存只能取一个字节。
假设执行到某转移指令时PC的内容为200,执行该转移指令后要求转移到100开始的一段程序执行,则该转移指令第二字节的内容应该是多少?参考答案:因为执行到该转移指令时PC为200,所以说明该转移指令存放在200单元开始的两个字节中。
因为CPU每次从内存只能取一个字节,所以每次取一个字节后PC应该加1。
该转移指令的执行过程为:取200单元中的指令操作码并译码→PC+1→取201单元的相对位移量→PC+1→计算转移目标地址。
假设该转移指令第二字节为Offset,则100=200+2+Offset,即Offset = 100–202 = –102 = 10011010B(注:没有说定长指令字,所以不一定是每条指令占2个字节。
)4.假设地址为1200H的内存单元中的内容为12FCH,地址为12FCH的内存单元的内容为38B8H,而38B8H单元的内容为88F9H。
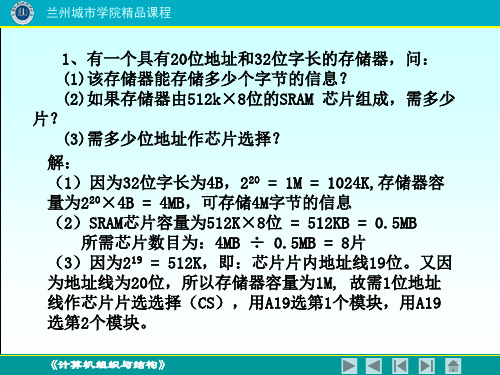
说明以下各情况下操作数的有效地址和操作数各是多少?(1)操作数采用变址寻址,变址寄存器的内容为12,指令中给出的形式地址为1200H。
(2)操作数采用一次间接寻址,指令中给出的地址码为1200H。
(3)操作数采用寄存器间接寻址,指令中给出的寄存器编号为8,8号寄存器的内容为1200H。
参考答案:(1)有效地址EA=000CH+1200H=120CH,操作数未知。
(2)有效地址EA=(1200H)=12FCH,操作数为38B8H。
(3)有效地址EA=1200H,操作数为12FCH。
5.通过查资料了解Intel 80x86微处理器和MIPS处理器中各自提供了哪些加法指令,说明每条加法指令的汇编形式、指令格式和功能,并比较加、减运算指令在这两种指令系统中不同的设计方式,包括不同的溢出处理方式。
计算机组织与结构选择题自测

半导体产业发展的前景的看法
随着科技的不断进步和全球经济的发展,半导体产业正处于蓬勃发展的阶段。
半导体是现代电子技术的核心,广泛应用于电子通信、计算机、医疗器械等领域。
作为半导体产业的关注者,我们有理由相信半导体产业在未来会有更加光明的前景。
1. 技术创新和应用需求推动产业发展
随着人工智能、5G、物联网等新兴技术的快速发展,对半导体产品性能和功能
提出了更高的要求。
这不仅推动了半导体产业加大研发投入,加速技术创新,还拓展了半导体在各个领域的应用场景。
例如,5G技术的普及将带动对高性能、低功
耗芯片的需求增加,而人工智能芯片在智能手机、无人驾驶、智能家居等领域的应用也将促进半导体产业的发展。
2. 产业链优化提高整体效益
当前,全球半导体产业链已经形成完整,生产环节包括晶圆制造、封装测试、
设计等多个环节,每个环节的创新都可能为半导体产业带来巨大发展机遇。
未来,随着技术的进步,不断优化产业链,降低生产成本,提高生产效率,可以使整个半导体产业获得更好的回报,进一步推进产业升级。
3. 国际市场需求持续增长
随着全球经济的不断增长,各国对高性能、高可靠性半导体产品的需求将持续
增长。
特别是在新兴市场,如亚洲、非洲等地区,对半导体产品的需求正在迅速增长。
中国作为全球最大的电子产品消费市场,对半导体产品的需求持续增长,将为全球半导体产业的稳步发展提供市场动力。
综上所述,半导体产业具有广阔的发展前景。
技朧创新、产业链优化和国际市
场需求的持续增长为半导体产业的发展提供了有力保障。
我们可以乐观地展望未来,相信半导体产业在未来会迎来更加辉煌的发展局面。
cache命中率习题
1 H H n 1 H' 1 n n
《计算机组织与结构》
兰州城市学院精品课程
解:n=4×5=20,采用预取技术之后, 命中率提高到:
H n 1 0.8 20 1 H' 0.99 n 20
Cache的块大小为一个字时,H=0.8,访问 效率为: e1=1/(0.8+5(1-0.8))=0.55… Cache的块大小为4个字时,H=0.99,访问 效率为: e2=1/(0.99+5(1-0.99))=0.96
《计算机组织与结构》
兰州城市学院精品课程
2、存储器容量为64M,字长64位,模块 数m = 8,分别用顺序方式和交叉方式进 行组织。存储周期T = 100ns,数据总线 宽度为64位,总线周期τ = 10ns .问顺 序存储器和交叉存储器的带宽各是多少?
《计算机组织与结构》
兰州城市学院精品课程
解:信息总量: q = 64位 ×8 =512位 顺序存储器和交叉存储器读出8个字的时间分别是: t2 = 8×100ns=8×10-7 (s) t1 = 100ns+7×10ns= 1.7×10-7 (s) 顺序存储器带宽是: W2 =q/t2=512÷(8×10-7)=64 ×107(位/S) 交叉存储器带宽是: W1 =q/t1=512÷(1.7×10-7)=301×107(位/S)
《计算机组织与结构》
兰州城市学院精品课程
7、假设主存容量为512KB,Cache容量为4KB, 每个字块为16个字,每个字32位。 求:在直接映射方式下,主存地址字段的位 数分配。 解:主存容量512K,(2的19次方),主存地 址为19位。 每个字块为16个字,每个字32位,即每个 字块为26字节。因此块内寻址需6为位, Cache容量为212字节,可分为26块,块号地 址也是6位,所以地址分配为程
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
前二章作业1.计算机的四个基本功能(Functions)是什么?2.在计算机的top-level structure view中,四个structural components 是什么?3.谁提出了store-program concept ?你能用汉语简单地描述这个存储程序的概念吗?4.CPU的英文全称是什么?汉语意义是什么?5.ALU的英文全称是什么?汉语意义是什么?6.V on Neumann 的IAS机的五大部件都是什么?7.在第一章中我们认识到的四个结构性部件(第2题)与V on Neumann的IAS机(第6题)中部件有本质差别吗?8.Fundamental Computer Elements 有哪几个?它们与计算机的四个基本功能的关系是什么?9.Moore’s Law在中文翻译为什么?它描述了什么事物的一般规律?10.本书的次标题和第二章第二节标题均为“Designing forPerformance”,Performance 主要指什么?Performance Balance的(balance)平衡要平衡什么?11.本书作者将他要研究的范围局限在“desktop, workstation , server“中,它们的中文名称是什么?各自的工作范围是什么?Chapter 3Homework1.PC means _________.A. personal computerB. programming controllerC. program counterD. portable computer2. PC holds _______________ .A. address of next instructionB. next instructionC. address of operandD. operand3. At the end of fetch cycle, MAR holds _____.A. address of instructionB. instructionC. address of operandD. operand4. Interrupt process steps are __________.A. suspending , resuming , branching & processingB. branching , suspending , processing & resumingC. suspending , branching , processing & resumingD. processing , branching , resuming & suspending5. A unsigned binary number is n bits, so it is can represent a value in the range between _________ .A. 0 to n-1B. 1 to nC. 0 to 2n-1D. 1 to 2n6.The length of the address code is 32 bits, so addressing range (or the range of address) is ________________.A. 4GB.from –2G to 2GC.4G-1D. from 1 to 4G7.There are three kinds of BUSes. Which is not belong to them?A. address busB. system busC. data busD. control busQuestions1.Translate the following terms (Note: function)PC, MAR, MBR, IR, AC, bus, system bus, data bus , address bus , control bus , handler*, opcode, Bus arbitrate* , multiplexed bus* , interrupt, ISR, Instruction cycle , fetch cycle , execute cycle(带“*”为选做题)2.Page90 problems3.1What general categories of functions are specified by computer instruction?3. Describe simply the operations of PC and IR in an instruction cycle.4.Suppose the length of word is n-bit, describe simply operand(操作数) format and instruction format.5. Describe simply the procedure of the interruption6. Describe simply the types and functions of the BUS.一:选择题1.The computer memory system refers to _________A.RAMB.ROMC.Main memoryD.Register , main memory, cache, external memory2.If the word of memory is 16 bits, which the following answer is right ?A.The address width is 16 bitsB.The address width is related with 16 bitsC.The address width is not related with 16 bitsD.The address width is not less than 16 bits3.The characteristics of internal memory compared to external memoryA.Big capacity, high speed, low costB.Big capacity, low speed, high costC.small capacity, high speed, high costD.small capacity, high speed, low cost4.On address mapping of cache, any block of main memory can be mapped toany line of cache, it is ___________ .A) Associative Mapping B) Direct MappingC) Set Associative Mapping D) Random Mapping5. Cache’s write-through polity means write operation to main memory _______.A)as well as to cacheB)only when the cache is replacedC)when the difference between cache and main memory is foundD)only when direct mapping is used6.Cache’s write-back polity means write operation to main memory ______________.a)as well as to cacheb)only when the relative cache is replacedc)when the difference between cache and main memory is foundd)only when using direct mapping7. On address mapping of cache, the data in any block of main memory can be mapped to fixed line of cache, it is _________________.associative mapping B) direct mappingC)set associative mapping D) random mapping8.On address mapping of cache, the data in any block of main memory can be mapped to fixed set any line(way) of cache, it is _________________.associative mapping B) direct mappingD)set associative mapping D) random mapping二:计算题(from page 126)Problem 4.1 , Problem 4.3 , Problem 4.4 , Problem 4.5 , , Problem 4.7, Problem 4.10第五章作业1.which type of memory is volatile?A.ROMB. E2PROMC. RAMD. flash memory2.which type of memory has 6-transistor structure?A. DRAMB. SRAMC. ROMD. EPROMing hamming code, its purpose is of one-bit error.A. detecting and correctingB. detectingC. correctingD. none of all4.Flash memory is .A. read-only memoryB. read-mostly memoryC. read-write memoryD. volatile5.Which answer about internal memory is not true?A. RAM can be accessed at any time, but data would be lost when power down..B. When accessing RAM, access time is non-relation with storage location.C. In internal memory, data can’t be modified.D. Each addressable location has a unique address.Page161 Problems: 5.4 5.5 5.6 5.7 5.8第六章作业一、选择题1. RAID levels_________make use of an independent access technique.A. 2B. 3C. 4D. all2. In RAID 4, to calculate the new parity, involves _________reads.A. oneB. twoC. threeD.four3. During a read/write operation, the head is ___________A. movingB. stationaryC. rotatingD. above all4. On a movable head system, the time it takes to position the head at the track is know as______.A. seek timeB. rotational delayC. access timeD. transfer time5. RAID makes use of stored______information that enable the recovery of data lost due to a disk failure.A. parityB. user dataC. OSD. anyone6. Recording and retrieval via _________called a headA. conductive coilB. aluminiumC. glassD. Magnetic field7.In Winchester disk track format, _________is a unique identifier or address used to locate a particular sector.A. SYNCHB. GapC. ID fieldD. Data field8. Data are transferred to and from the disk in ________.A. trackB. sectorC. gapD. cylinder9. In _________, each logical strip is mapped to two separate physical disk.A. RAID 1B. RAID 2C. RAID 3D. RAID 410. With _________, the bits of an error correcting code are stored in the corresponding bit position on multiple parity disk.A. RAID 1B. RAID 2C. RAID 3D. RAID 411. The write-once read-many CD, known as ________.A. CD-ROMB. CD-RC. CD-R/WD. DVD二、How are data written onto a magnetic disk?三、In the context of RAID, what is the distinction between parallel access and independent access?Homework in Chapter 71.“When the CPU issues a command to the I/O module, it must wait until the I/Ooperation is complete”. It is programmed I/O , the word “wait”means ___________________.a. the CPU stops and does nothingb. the CPU does something elsec. the CPU periodically reads & checks the status of I/O moduled. the CPU wait the Interrupt Request Signal2.See Figure 7.7. To save (PSW & PC) and remainder onto stack, why theoperations of restore them is reversed? Because the operations of stack are ________________.a. first in first outb. randomc. last in first outd. sequenceding stack to save PC and remainder, the reason is ____________________ .a.some information needed for resuming the current program at the point ofinterruptb.when interrupt occurs, the instruction is not executed over, so the instructionat the point of interrupt must be executed once againc.the stack must get some information for LIFOd.the start address of ISR must transfer by stack4.The signals of interrupt request and acknowledgement exchange between CPUand requesting I/O module. The reason of CPU’s acknowledgement is ________________a.to let the I/O module remove request signalb. to let CPU get the vectorfrom data busc.both a & bd. other aims5.In DMA , the DMA module takes over the operations of data transferring fromCPU, it means _________________________a.the DMA module can fetch and execute instructions like CPU doesb.the DMA module can control the bus to transfer data to or from memoryusing stealing cycle techniquec.the DMA module and CPU work together(co-operate) to transfer data into orfrom memoryd.when DMA module get ready, it issues interrupt request signal to CPU forgetting interrupt service6.Transfer data with I/O modules, 3 types of techniques can be used. Which one isnot belong them?a. Interrupt-driven I/Ob. programmed I/Oc. direct I/O accessd. DMA7.Think 2 types of different data transferring, to input a word from keyboard and tooutput a data block of some sectors to harddisk. The best choice is to use ___________.a. interrupt-driven I/O and DMAb. DMA and programmed I/O C. both interrupt-driven I/Os d. both DMAsparing with interrupt-driven I/O, DMA further raises the usage rate of CPUoperations, because __________a. it isn’t necessary for CPU to save & restore sceneb. it isn’t necessary for CPU to intervene the dada transferc. it isn’t necessary for CPU to read & check status repeatedlyd. both a and b9.Simply script the all actions when using Interrupt-driven I/O technique totransferring data with I/O module.(please insert the “vector “at step3 & step5)10.See Figure 7.7 & 7.8. Redraw figure 7.8, and mark the sequence numberaccording to Figure 7.7, to indicate the sequence of the information flowing.11. According to DMA technique, write all information of CPU sending to DMA module, and write at which time the DMA module issues interrupt request signal to CPU and why the INTR is issued ?.Chapter9 homework1.Suppose bit long of two’s complement is 5 bits, which arithmetic operation brings OVERFLOW?A. 5+8B. (-8)+(-8)C. 4-(-12)D.15-72.Overflow occurs sometime in ______arithmetic operation.A. addB. subtractC. add and subtractD. multiply3. In twos complement, two positive integers are added, when does overflow occurs?A. There is a carryB. Sign bit is 1C. There is a carry, and sign bit is 0D. Can’t determine4. An 8-bit twos complement 1001 0011 is changed to a 16-bit that equal to____.A.1000 0000 1001 0011B. 0000 0000 1001 0011C.1111 1111 1001 0011D.1111 1111 0110 1101 115. An 8-bit twos complement 0001 0011 is changed to a 16-bit that equal to____.A. 1000 0000 1001 0011B. 0000 0000 0001 0011C. 1111 1111 0001 0011D. 1111 1111 1110 11016.Booth’s algorithm is used for Twos complement ______.A. additionB. subtractionC. multiplicationD. division7. In floating-point arithmetic, addition can divide to 4 steps: ______.A. load first operand, add second operand, check overflow and store resultB. compare exponent, shift significand, add significands and normalizeC. fetch instruction, indirectly address operand, execute instruction and interruptD. process scheduling states: create, get ready, is running and is blocked8. In floating-point arithmetic, multiplication can divide to 4 steps: ______.A. load first operand, add second operand, check overflow and store resultB. fetch instruction, indirectly address operand, execute instruction and interruptC. process scheduling states: create, get ready, is running and is blockedD. check for zero, add exponents, multiply significands, normalize, and round.9.The main functions of ALU are?A. LogicB. ArithmeticC. Logic and arithmeticD. Only addition10. Which is true?A. Subtraction can not be finished by adder and complement circuits in ALUB. Carry and overflow are not sameC.In twos complement, the negation of an integer can be formed with thefollowing rules: bitwise not (excluding the sign bit), and add 1.D. In twos complement, addition is normal binary addition, but monitor sign bit foroverflowPage326:9.4, 9.5 and 9.7(其中9.4选作)To prove: in twos complement, sign-extension rule (converting between different bit length) and negation rule ( (-X)补= X补+ 1).Chapter 10 and Chapter 111: In instruction, the number of addresses is 0, the operand(s)’address is implied, which is(are) in_______.A. accumulatorB. program counterC. top of stackD. any register2: Which the following addressing mode can achieve the target of branch in program?A.Direct addressing modeB.Register addressing modeC.Base-register addressing modeD.Relative addressing mode (有问题)3: In index-register addressing mode , the address of operand is equal toA.The content of base-register plus displacementB.The content of index-register plus displacementC.The content of program counter plus displacementD.The content of AC plus displacement4: The address of operand is in the instruction, it is_________ ?A.Direct addressing modeB.Register indirect addressing modeC.Stack addressing modeD.Displacement addressing mode5: Which the following is not the area that the source and result operands can be stored in ?A.Main or virtual memoryB.CPU registerC.I/O deviceD.Instruction6: Compared with indirect addressing mode , the advantage of register indirect addressing mode isrge address spaceB.Multiple memory referenceC.Limit address spaceD.Less memory access7:With base-register ADDRESSING , the ______________ register can be used.A. BASEB. INDEXC. PCD. ANY8:The disadvantage of INDIRECT ADDRESSING is ____________.A. large addressing rangeB. no memory accessC. more memory accessD. large value range9:Which is not an advantage with REGISTER INDIRECT?A. just one times of operand’s accessB. large memory spaceC. large value rangeD. no memory reference10:The REGISTER ADDRESSING is very fast, but it has _________________.A. very less value rangeB. very less address spaceC. more memory accessD. very complex address’ calculating11:The disadvantage of IMMEDIATE ADDRESSING is ___________.A. limited address rangeB. more memory accessC. limit value rangeD. less memory access12:In instruction, the number of addresses is 2, one address does double duty both _______________.A. a result and the address of next instructionB.an operand and a resultC.an operand and the address of next instructionD.two closed operands13.In instruction, the number of addresses is 3, which are _______________.A. two operands and one resultB. two operands and an address of next instructionC. one operand, one result and an address of next instructionD. two operands and an address of next instruction14.The address is known as a type of data, because it is represented by __________.A. a number of floating pointB. a signed integerC. an unsigned integerD. a number of hexadecimal15.Which is not a feature of Pentium .A. complex and flex addressingB. abundant instruction setC. simple format and fixed instruction lengthD. strong support to high language16. Which is not a feature of Power PC .A. less and simple addressing modeB. basic and simple instruction setC. variable instruction length and complex formatD. strong support to high languageChapter 12 and Chapter 181. After the information flow of fetch subcycle, the content of MBR is_____________.A.oprandB.address of instructionC. instructionD. address of operand2. After the information flow of instruction subcycle, the content of MBR is_____________.A.oprandB.address of instructionC. instructionD. address of operand3. The worse factor that limits the performance of instruction pipeline is _________________.A.conditional branch delaying the operation of target addressB. the stage number of pipeline c an’t exceed 6C. two’s complement arithmetic too complexD. general purpose registers too few4.The most factor to affect instruction pipeline effectiveness is __________.A. The number of stagesB. the number of instructionC. the conditional branch instructionD. the number of pipelines5. RISC rejects ______.A. few, simple addressing modesB. a limited and simple instruction setC. few, simple instruction formatsD. a few number of general purpose registers6. RISC rejects ______.A.a large number of general-purpose registersB. indirect addressingC. a single instruction sizeD. a small number of addressing mode7. Which is NOT a characteristic of RISC processor.A. a highly optimized pipeline.B. Register to registeroperationsC. a large number of general-purpose registersD. a complexed instructionformat8.Control unit use some input signals to produce control signals that open the gatesof information paths and let the micro-operations implement. Which is NOT the input signals of control unit/A.clock and flagsB.instruction registerC.interrupt request signalD.memory read or write9.Control unit use some output signals to cause some operations. Which is notincluded in the output signals?A.signals that cause data movementB.signals that a ctivate specific functions(e.g. add/sub/…)C.flagsD.read or write or acknowledgement10. Symmetric Multi-Processor (SMP) system is tightly coupled by _______.A. high-speed data-link and distributed memoryB. shared RAIDs and high-speed data-linkC. distributed caches and shared memoryD. interconnect network and distributed memory11. The SMP means __________.A.Sharing Memory ProcessesB.Split Memory to PartsD.Stack and Memory Pointer D.Symmetric Multi-Processo r12.The “MESI” means states of ____________ .A.Modified, Exclusive, Stored and InclusiveB.Modified, Expected, Shared and InterruptedC.Modified, Exclusive, Shared and InvalidD.Moved, Exchanged, Shared and Invalid13.The protocol “MESI” is also called __________.A. write back policyB. write-update protocolC. write-invalidate protocolD. write through policyChapter 121.Which register is user –visible but is not directly operated in 8086 ?A. DSB. SPC. IPD. BP2.The indirect sub-cycle is occurred _____________ ?A. before fetch sub-cycleB. after execute sub-cycleC. after interrupt sub-cycleD. after fetch sub-cycle and before execute sub-cycle3.Within indirect sub-cycle , the thing the CPU must do is ______________?A. fetch operand or store resultB. fetch operand’s address from memoryC. fetch next instruction from memoryD. nothing4.In general, which register is used for relative addressing ---- the content inthis register plus the A supplied by instruction to make a target address in branch or loop instructions.A. SPB. IRC. BRD. PC5.The Memory Address Register connects to ____________ BUS .A. systemB. addressC. dataD. control6.The Memory Buffer Register links to ________ BUS.A. systemB. addressC. dataD. control7.After Indirect cycle , there is a ______________ cycle .A. FetchB. IndirectC. ExecuteD. Interrupt8.The Interrupt cycle is __________ ______ Execute cycle .A. always afterB. never afterC. sometime afterD. maybe before9.The correct cycle sequence is _________________ .A. Fetch , Indirect , Execute and InterruptB. Fetch , Execute , Indirect and InterruptC. Fetch , Indirect , Interrupt and ExecuteD. Indirect , Fetch , Execute and Interrup10.The aim of the indirect cycle is to get __________________.A. an operandB. an instructionC. an address of an instructionD. an address of an operand11.Which is not in the ALU ?A. shifterB. adderC. complementerD. accumulator12.The registers in the CPU is divided _____registers and ________registers .A. general purpose , user-visibleB. user-visible , control and statusC. data , addressD. general purpose , control and status13.The Base register is a(n) __________ register in 8086.A. general purposeB. dataC. addressD. control14.The Instruction Pointer is a(n) __________ register in 8086.A. general purposeB. dataC. addressD. control15.The Index register is a(n) __________ register in 8086.A. general purposeB. dataC. addressD. control16.The Stack Pointer is a(n) __________ register in 8086.A. general purposeB. dataC. addressD. control17.The Accumulator is a(n) __________ register in 8086.A. general purposeB. dataC. addressD. control18.The Programming Status W ord is a(n) __________ register .A. general purposeB. dataC. addressD. controlShow all the micro-operations and control signals for the following instruction:1. ADD AX, X; —The contents of AC adds the contents of location X, result is stored to AC.2. MOV AX, [X];—Operand pointed by the content of location X is moved to AX, that means ((X))->AX—[ ] means indirect addressing.3. ADD AX, [BX];—Operand pointed by the content of Register BX is added to AX, that means (AX)+((BX))->AX—[ ] means register indirect addressing.4. JZ NEXT1; —If (ZF)=0,then jump to (PC)+ NEXT1.5. CALL X; —Call x function, save return address on the top of stack.6. RETURN; —From top of stack return to PC.。
