GWO_finalVersion
Grandstream Networks, Inc. GWN7600LR 企业级 802.11ac

Grandstream Networks,Inc. GWN7600LR企业级802.11ac Wave-2室外型长距离WiFi接入点用户手册图4:GWN7600LR水平安装保修如果您购买自经销商,请直接联系经销商更换,维修或退货。
如果您直接购于潮流网络公司,请联系潮流技术支持团队,取得退货许可号码(RMA)后退货。
潮流网络科技公司保留在不做预先通知的情况下修改售后服务细则的权利。
图12:GWN7600Web页面登录页面访问Web页面:1.将电脑连到GWN7600LR所在的局域网中。
2.确保设备已经上电。
3.打开Web浏览器,并用“发现GWN7600LR”章节中介绍的方式输入设备MAC地址或以下形式输入Web页面 面 https://IP_Address。
4.输入管理员的账号和密码登录WEB配置页面,默认的管理员账号和密码均为“admin”。
Web页面语言当前GWN7600LR系列Web页面支持英语和简体中文。
用户可以在登录之前或之后在WEB用户登录界面的右上角选择显示的语言。
图8:GWN7600LR Web页面语言(登录页面)概览页面概览页面是成功登录GWN7600LR的Web界面后显示的第一页。
概览页面提供了以仪表板样式显示的GWN7600LR信息的总体视图,便于监控。
图10:概览页面用户可以点击进入接入显示连接的客户端的总数,击进入客户页面了解更多选项。
AP的客户端的数目或者组合上用户可以点击进入AP的客户端的数目或者组合上行和下行的数据使用来分类列表。
用户可以点击进入网络组页面以获得显示热门客户列表,击进入客户页面了解更多选项。
用户可以单击以弹出警报图11:应用修改应用修改,或点击图16:应用成功图14:登录页面在恢复出厂时,默认选中“以主接入点登录”,在输入管理员的用户名和密码后点击“登录”。
--------------------------------------------------------------------------------------------------------------------------------------------警告:“以主接入点登录”选项将禁止GWN7600LR接入点与其他主GWN76xx配对,并且只能作为主接入点控制器工作。
IPS-1000系列VoIP综合接入系统用户手册V1.05

IPS-1000系列VoIP综合接入系统用户手册版本:V1.05目录1.前言 (1)2.概述 (2)3.系统指标 (3)3.1功能、性能 (3)3.2工作条件 (3)3.3配置 (4)4.结构 (5)4.1VIP板面板图 (5)4.2面板 (5)4.3出线 (6)4.4系列结构标准 (6)5.安装和操作 (7)5.1IPS设置简介 (7)5.2产品安装和呼叫 (7)5.3呼叫 (7)5.4IPS系列编程 (7)6.VIP设置命令(Telnet 远程配置) (8)6.1操作系统登录命令Telnet (8)6.2帮助命令Help (8)6.3显示配置命令Show (9)6.4设置配置命令Set (10)6.5存盘命令Save (10)6.6恢复前次配置命令Load (10)6.7恢复初始配置命令LoadDefault (10)6.8系统重起动命令Reboot (10)6.9退出命令配置Quit (11)7.配置数据 (12)7.1NetWork部分 (12)7.1.1广域网IP (12)7.1.2广域网IP子网掩码 (12)7.1.3广域网MAC值 (12)7.1.4广域网口DHCP模式 (12)7.1.5局域网IP (13)7.1.6局域网IP子网掩码 (13)7.1.7局域网MAC值 (13)7.1.8DNS状态 (13)7.1.9DNS IP (13)7.1.10默认网关IP (14)7.1.11NAT功能 (14)7.1.12NAT端口映射表 (14)7.1.13PPPoE (14)7.1.14PPPoE 用户名 ......................................... 147.1.15PPPoE 用户密码. (15)7.2GateWay部分 (15)7.2.1网关别名 (15)7.2.2网关IP (15)7.2.3网关区号 (15)7.2.4呼入前缀匹配值 (15)7.2.5呼入前缀删除状态 (16)7.2.6设备最大允许话音通道数 (16)7.2.7启用快速呼叫功能 (16)7.2.8Q.931协议端口值 (16)7.2.9RTP起始端口值 (16)7.2.10TCP起始端口值 (17)7.2.11MCC通信定时器 (17)7.2.12网守定时器 (17)7.2.13TCP定时器 (17)7.2.14ALERTING定时器 (17)7.2.15CONNECING定时器 (17)7.2.16RAS重发次数 (18)7.2.17网守状态 (18)7.2.18网守IP (18)7.2.19TUNNEL状态 (18)7.2.20网关路由表 (18)7.3CDR IP部分 (19)7.3.1中央维护台的IP (19)7.3.2普通维护台IP (19)7.3.3设置SNMP 管理站IP (19)7.4GateKeeper部分 (19)7.4.1网守最大支持呼叫数基本属性 (19)7.4.2内部网守状态 (20)7.4.3IRR消息频率 (20)7.4.4RRQ消息频率 (20)7.4.5RRQ消息超时次数 (20)7.4.6IRR消息超时次数 (20)7.4.7GKID (20)7.4.8网守信息表 (21)7.4.9DSP状态 (21)7.4.10语音编码类型 (21)7.4.11传真模式 (21)7.4.12语音包允许延迟时长 (22)7.4.13回声抵消状态 (22)7.4.14静音检测状态 (22)7.5SYSTEM部分 (22)7.5.1系统软件版本 (22)7.5.2T35国家码 (22)7.5.3T35扩展码 (22)7.5.4终端类别 (23)7.5.5产品ID号 (23)7.5.6设备厂家号 (23)7.5.7H.323协议栈版本 (23)7.5.8H.225协议栈版本 (23)7.5.9H.245协议栈版本 (23)7.6Dialedlen部分 (23)7.7IP ECHO部分 (24)7.7.1IPECHO客户端 (24)7.7.2客户机定时发送消息时间 (24)7.7.3服务器所在地址 (24)7.7.4服务器所在端口 (25)7.7.5是否作为服务器 (25)8.关于配置文件的存取 (26)8.1下载VIP配置文件至PC (26)8.2上传PC的配置文件至VIP中: (26)8.3用TFTP升级VIP系统软件 (26)9.维护注意事项 (27)9.1VIP板RUN灯长亮 (27)9.2IPS电话无法呼出 (27)图图5-1面板指示图 (5)表表5-1面板LED定义 (5)1.前言●本手册详细地介绍了IPS-1000系列V oIP综合接入系统(IPS-1016/1160/1240)的结构、工程安装说明、软件设置等,您也可以根据目录及页眉的标题进行选择性地阅读此手册。
从PROFIBUS DP到PROFINET IO编程手册
从 PROFIBUS DP 到 PROFINET IO
编程手册, 10/2006, A5E00879152-01
3
前言
指南
本手册中涵盖的主题: • PROFIBUS DP 与 PROFINET IO 的比较: • 诊断和状态请求的数据记录 • 用户程序中的诊断实例 • 附录
词汇表解释了重要的术语。 索引中包含了重要的关键字,可以通过关键字快速访问相关的文 本段落。
5.2 5.2.1 5.2.2
PROFINET IO 的设备模型 ...........................................................................................................39 IO 设备的设备模型 .......................................................................................................................39 PROFINET IO 的诊断级别 ...........................................................................................................40
回收和处理
本文档中所说明的设备由于污染物少,可以进行回收。 为了环保可持续地回收和处理旧设 备,请联系有资质处理电子废弃物的公司。
相对于先前版本的变更 本手册说明了 SIMATIC 设备系列的新技术和增强功能。
读者群
本手册主要针对致力于使用 SIMATIC 产品的联网自动化解决方案的设计和工程的人群: • 决策者 • 计划人员 • 项目工程师
迈普3000_端口操作命令

第 5 章 LLDP 功能命令 ................................................. 21
5.1 lldp enable ....................................................................................... 21 5.2 lldp enable(端口) ......................................................................... 21 5.3 lldp mode ......................................................................................... 21 5.4 lldp tx-interval.................................................................................. 22 5.5 lldp msgTxHold ............................................................................... 22 5.6 lldp transmit delay .......................................................................... 23 5.7 lldp notification interval.................................................................. 23 5.8 lldp trap............................................................................................ 23 5.9 lldp transmit optional tlv................................................................. 24 5.10 lldp neighbors max-num............................................................... 24 5.11 lldp tooManyNeighbors................................................................. 24 5.12 show lldp........................................................................................ 25 2
英文论文写作与投稿经验

The simulation of cold expansion was carried out by changing the
position of mandrel on the 3 direction.
The simulation of cold expansion was carried out by the change of the
18
Reference的引用方式
用“作者+年份”表示
Hwang et al. (2005) indicated that…… It has been proven that……(Hwang et al., 2005). 最大优点是:有新的文献要插入时,不必重新编号
(Hwang, 2003), (Hwang & Lin, 2003), (Hwang et al. 2004) 建议在论文整理阶段采用此方式;大多SSCI/TSSCI 期刊采用这种格式
11
Abstract
内容:简介的浓缩版 字数:200-300字 包含
研究动机(motivation) 研究目的(问题的描述) 研究方法(概念性的描述) 研究成果(试验结果及贡献)
12
Introduction
内容:整篇文章的浓缩版 字数:500-1000字 包含
using countersunk bolt.
24
注意用词和语法Leabharlann 数值计算结果 × Numerical value calculation result Numerical result 焊接区,焊接件
Welding zone, welded part
GWBASIC使用手册

第1章 BASIC语言的特点及运行环境 (1)1.1 BASIC语官的发展与版本简介 (1)1.2 GWBASIC语言的特点 (1)1.3 GWBASIC的运行环境 (1)1.4 GWBASIC的启动 (2)1.5 BASIC的使用方式 (2)1.5.1 直接方式 (3)1.5.2 间接方式 (3)1.5.3 BASIC的退出 (3)第2章 BASIC的词法规则 (4)2.1 BASIC字符集 (4)2.2 BASIC保留字 (4)2.3 BASIC常数 (6)2.3.1 数值常数 (6)2.3.2 字符常数 (7)2.3.3 逻辑常数 (7)2.4 变量 (7)2.4.1 变量的类型 (7)2.4.2 变量的命名规则 (7)2.4.3 变量类型的说明 (7)2.5 下标变量 (8)2.5.1 数组 (8)2.5.2 下标变量 (9)2.5.3 下标变量的有关规定 (10)2.6 BASIC函数 (10)2.6.1 内部函数 (10)2.6.2 自定义函数 (15)2.7 运算符与表达式 (16)2.7.1 算术表达式 (16)2.7.2 关系表达式 (17)2.7.3 逻辑表达式 (17)2.7.4 复合逻辑表达式的运算顺序 (19)2.7.5 字符串表达式 (19)第3章 BASIC的程序结构 (21)3.1 BASIC语句和命令 (21)3.1.1 BASIC语句 (21)3.1.2 BASIC命令 (21)3.2 BASIC程序结构 (22)第4章 BASIC输入和输出 (23)4.1 输入数据的语句 (23)4.1.1 LET语句 (23)4.1.2 INPUT语句 (23)4.1.3 READ语句 (24)4.1.4 DATA语句 (24)4.1.5 RESTORE语句 (25)4.1.6 LINE INPUT语句 (25)4.1.7 SWAP语句 (26)4.2 输出语句 (26)4.2.1 PRINT语句 (26)4.2.2 PRINT USING语句 (27)4.2.3 LPRINT语句 (28)4.2.4 LPRINT USING语句 (28)4.3 输入、输出的辅助函数及变量 (29)4.3.1 TAB函数 (29)4.3.2 SPC函数 (29)4.3.3 LPOS函数 (29)4.3.4 INPUT$函数 (29)4.3.5 INKEY$变量 (30)4.4 提供系统日期和时间的语句和变量 (30)4.4.1 TIME$语句 (30)4.4.2 TIME$变量 (30)4.4.3 DATE$语句 (30)4.4.4 DATE$变量 (31)第5章 控制语句 (32)5.1 无条件控制转移语句 (32)5.1.1 GOTO语句 (32)5.1.2 GOSUB语句 (32)5.2 有条件转移语句 (33)5.2.1 IF语句 (33)5.2.2 ON n GOTO语句 (34)5.2.3 ON n GOSUB语句 (34)5.2.4 ON ERROR GOTO语句及相关变量 (34)5.2.5 ON KEY(n)GOSUB语句 (36)5.2.6 ON PLAY(n) GOSUB语句 (36)5.2.7 ON TIMER(n) GOSUB语句 (37)5.2.8 ON COM(n) GOSUB语句 (37)5.2.9 光笔控制语句与函数 (38)5.2.10 游戏杆操作的控制语句及函数 (38)5.3 循环控制 (39)5.3.1 FOR...NEXT语句 (39)5.3.2 WHILE...WEND语句. (41)第6章 数据文件及操作 (42)6.1 BASIC数据文件的有关概念 (42)6.1.1 数据文件的命名规则 (42)6.1.2 数据文件的分类 (43)6.2 顺序数据文件的建立和输入、输出 (43)6.2.1 顺序数据文件的打开和关闭 (43)6.2.2 顺序文件的输入和输出 (44)6.3 随机文件的建立和输入、输出 (46)6.3.1 随机文件的打开和关闭 (46)6.3.2 类型转换函数 (47)6.3.3 随机文件的输出有关语句 (48)6.3.4 随机文件的输入语句及转换函数 (48)第7章 BASIC绘图 (50)7.1 绘图环境的设置 (50)7.1.1 彩色图形显示器的工作模式 (50)7.1.2 显示器工作模式的选择语句 (51)7.1.3 绘图环境设置的其他语句 (53)7.2 绘图语句及相关函数 (54)7.2.1 画点、擦点语句 (54)7.2.2 画线语句 (55)7.2.3 画圆、圆弧及填充语句 (57)7.3 窗口与视口设置 (58)7.3.1 WINDOW语句 (58)7.3.2 VIEW语句 (59)7.4 动画设计语句及函数 (59)7.4.1 字符动画函数和变量 (59)7.4.2 图形模式下的动画设计语句和函数 (60)7.5 DXY-880A绘图仪BASIC命令 (61)7.5.1 DXY-880A绘图仪的联机方式 (61)7.5.2 DXY绘图命令 (62)第8章 GWBASIC的特殊语句及函数 (67)8.1 BASIC通信 (67)8.1.1 通信文件的打开与关闭 (67)8.1.2 通信文件的输入与输出 (68)8.2 机器级语句及函数 (68)8.2.1 机器级基本语句及函数 (68)8.2.2 机器语言子程序的调用 (71)8.3 其他语句 (71)8.3.1 CHAIN语句 (71)8.3.2 COMMON语句 (72)第9章 BASIC命令与键盘操作 (73)9.1 编辑命令 (73)9.1.1 AUTO命令 (73)9.1.2 RENUM命令 (73)9.1.3 DELETE命令 (73)9.1.4 EDIT命令 (74)9.1.5 LIST命令 (74)9.1.6 LLIST命令 (74)9.1.7 NEW命令 (74)9.2 文件的管理与操作命令 、 (75)9.2.1 FILES命令 (75)9.2.2 LOAD命令 (75)9.2.3 SAVE命令 (75)9.2.4 BSAVE命令 (75)9.2.5 BLOAD命令 (76)9.2.6 KILL命令 (76)9.2.7 NAME命令 (76)9.2.8 MERGE命令 (76)9.2.9 目录管理命令 (77)9.3 程序的执行命令 (77)9.3.1 RUN命令 (77)9.3.2 CLEAR命令 (78)9.3.3 RESET命令 (78)9.3.4 SYSTEM命令 (78)9.3.5 程序追踪命令 (78)9.3.6 CONT命令 (79)9.4 BASIC屏幕编辑键 (79)9.5 BASIC功能键的定义及使用 (80)9.5.1 命令功能键的定义及使用 (80)9.5.2 语句功能键 (80)第10章 编译BASIC (82)10.1 编译BASIC的构成 (82)10.2 编译BASIC的使用 (82)10.2.1 源程序编译 (82)10.2.2 目标程序的连接 (84)10.2.3 程序的执行 (84)10.3 编译BASIC与解释BASIC的主要区别 (84)10.3.1 操作命令的区别 (84)10.3.2 说明语句的区别 (85)附录A GWBASIC命令、语句和函数索引 (86)附录B ASCII字符代码表 (92)附录C GWBASIC错误信息 (97)附录D GWBASIC专用键 (103)第1章 BASIC语言的特点及运行环境1.1 BASIC语官的发展与版本简介BASIC语言是国际上通用的计算机语言之一,各种规模的计算机系统均配有BASlC语言。
Worldpay Payments Plug-in for Magento 2 安装指南说明书

ContentsHow to install the plugin (3)Install the plugin using Composer (3)Install the plugin from Packagist (recommended) (3)Install the plugin from GitHub (3)Install the plugin from GitHub branch (4)Install the plugin after manual download (5)Basic configuration (6)Troubleshooting (8)Contact Us (10)How to install the pluginThe Worldpay Payments Plugin for Magento 2 is hosted on GitHub and on Packagist.Install the plugin using ComposerPrerequisite: You must download Composer and install it on your machine.Install the plugin from Packagist (recommended)Check the version you need to install from Packagist.Run the following commandcomposer require sapient/module-worldpay: 2.4.5-p10123 to install this specific version. Please add the version number highlighted in yellow to download the exact required version.You will see the following as an output (Sample Screenshot):Install the plugin from GitHubWe recommend the Packagist installation, but if you have issues with that download the plugin from GitHub. Run following command to add the Worldpay GitHub repository to your composer.json file:composer config repositories.repo-name git https:///Worldpay/Worldpay-Magento2-CG.gitThe Worldpay GitHub repository is now added to your composer.json file:Run the following command to install the plugin, and include the version to be installed:composer require sapient/module-worldpay: 2.4.5-p10123You will see the following as an output (Sample Screenshot):Install the plugin from GitHub branchDo this if Worldpay has provided a patch. To install the plugin from Github branch, get the branch details from Worldpay. If the branch name is release-v2.4.5-p10123, run the following command: composer require sapient/module-worldpay:dev-release-v2.4.5-p10123In this case, the “dev” parameter informs Composer that you are trying to download the package from the GitHub branch. You will see the following as an output (Sample Screenshot):After you complete the installation, run the following command to refresh the Magento cache:php bin/magento setup:upgrade && php bin/magento setup:static-content:deploy -f && php bin/magento cache:flushInstall the plugin after manual downloadFor a manual installation, do the following:1. Download the extension from the Magento marketplace (recommended).2. If you have any issues with the Magento marketplace, download the extension from GitHub.3. Unzip the file in a temporary directory.4. You must create an app/code/Sapient/Worldpay directory to hold the unzipped Magento file structurementioned in step 3.5. After completing the steps above, run the following command to refresh the Magento cache:php bin/magento setup:upgrade && php bin/magento setup:static-content:deploy -f && php bin/magento cache:flushBasic configurationThe table below covers the basic configurations needed to test your first Worldpay payment:All fields marked (*) are mandatory.All fields marked (**) are mandatory for production mode.To find out more about features and configurations, see the Worldpay Payments Plugin User Guide. You can also find out more on the Worldpay Payment Gateway Guide.TroubleshootingHere are some basic ideas to help you identify and fix problems:•See the User Guide to verify the plugin’s configurations•You can also check the installation information at the Worldpay Troubleshooting, General Errors section •You can customize error messages. Find out more in the User Guide, under Worldpay Exception Codes•Make sure Worldpay module is enabled, the correct environment mode is set and the correct environment URL has been updated under Stores/Configuration/Sales/Worldpay/General ConfigurationSee the User Guide to find out more about various features.Note: For any issues not included in the table above, contact your Worldpay support representative with the following details to help them resolve the issue.•Screenshot of the issue•Screenshot of the particular admin configuration•Plugin-specific log•Worldpay.log•Version of the plugin and Magento you are usingContact UsContact your Worldpay Relationship Manager or other contact. If they’re not available, call our customer service team on 0800 096 3997.。
FACT-GOG-NTX_ENG_Final_Ver4_16Nov07

Below is a list of statements that other people with your illness have said are important . Please circle or mark one number per line to indicate your response as it applies to the past 7 days.PHYSICAL WELL-BEINGNot at all A little bit Some-what Quitea bit Very muchGP1I have a lack of energy.......................................................0 1 2 3 4 GP2I have nausea......................................................................0 1 2 3 4 GP3Because of my physical condition, I have troublemeeting the needs of my family......................................... 0 1 2 3 4 GP4I have pain..........................................................................0 1 2 3 4 GP5I am bothered by side effects of treatment.........................0 1 2 3 4 GP6I feel ill...............................................................................0 1 2 3 4 GP7I am forced to spend time in bed........................................1234SOCIAL/FAMILY WELL-BEINGNot at all A little bit Some-whatQuite a bitVery muchGS1I feel close to my friends....................................................0 1 2 3 4 GS2I get emotional support from my family............................0 1 2 3 4 GS3I get support from my friends.............................................0 1 2 3 4 GS4My family has accepted my illness....................................0 1 2 3 4 GS5I am satisfied with family communication about myillness.................................................................................. 0 1 2 3 4 GS6I feel close to my partner (or the person who is my main support)..............................................................................0 1234Q1Regardless of your current level of sexual activity, pleaseGS7I am satisfied with my sex life............................................0 1 2 3 4Please circle or mark one number per line to indicate your response as it applies to the past 7 days.EMOTIONAL WELL-BEING Notat all A littlebitSome-whatQuitea bitVerymuchGE1 I feel sad..............................................................................0 1 2 3 4 GE2 I am satisfied with how I am coping with my illness..........0 1 2 3 4 GE3 I am losing hope in the fight against my illness..................0 1 2 3 4 GE4 I feel nervous.......................................................................0 1 2 3 4 GE5 I worry about dying.............................................................0 1 2 3 4 GE6 I worry that my condition will get worse............................0 1 2 3 4FUNCTIONAL WELL-BEING Notat all A littlebitSome-whatQuitea bitVerymuchGF1 I am able to work (include work at home)..........................0 1 2 3 4 GF2 My work (include work at home) is fulfilling.....................0 1 2 3 4 GF3 I am able to enjoy life..........................................................0 1 2 3 4 GF4 I have accepted my illness...................................................0 1 2 3 4 GF5 I am sleeping well...............................................................0 1 2 3 4 GF6 I am enjoying the things I usually do for fun......................0 1 2 3 4 GF7 I am content with the quality of my life right now..............0 1 2 3 4Please circle or mark one number per line to indicate your response as it applies to the past 7 days.ADDITIONAL CONCERNS Not atall A littlebitSome-whatQuitea bitVerymuchNTX1I have numbness or tingling in my hands............................0 1 2 3 4NTX2I have numbness or tingling in my feet...............................0 1 2 3 4NTX3I feel discomfort in my hands..............................................0 1 2 3 4NTX4I feel discomfort in my feet.................................................0 1 2 3 4NTX5I have joint pain or muscle cramps.....................................0 1 2 3 4 HI12 I feel weak all over..............................................................0 1 2 3 4NTX6I have trouble hearing..........................................................0 1 2 3 4NTX7I get a ringing or buzzing in my ears...................................0 1 2 3 4NTX8I have trouble buttoning buttons.........................................0 1 2 3 4NTX 9 I have trouble feeling the shape of small objects whenthey are in my hand.............................................................0 1 2 3 4An6 I have trouble walking.........................................................0 1 2 3 4。
goctls 编译

goctls 编译英文回答:### GoCTLS Compilation Requirements.1. Go: Go version 1.18 or later is required.sh.go version.2. CGO: CGO must be enabled when building the Go binary. sh.go env CGO_ENABLED.3. OpenSSL: OpenSSL version 1.1.1 or later is required. sh.openssl version.4. BoringSSL: BoringSSL is an alternative to OpenSSL that is used by Go on some platforms. If you are using BoringSSL, version 1.1.1 or later is required.sh.boringssl version.5. Compiler: A C compiler is required to build the Go binary. The compiler must be compatible with your operating system and architecture.6. Make: Make is required to build the C code.sh.make --version.7. YACC: YACC is required to build the C code.sh.yacc --version.8. Bison: Bison is an alternative to YACC that is used by Go on some platforms. If you are using Bison, version3.0 or later is required.sh.bison --version.9. Flex: Flex is required to build the C code.sh.flex --version.10. libpcap: libpcap is required to build the Go binary. sh.pkg-config --modversion libpcap.11. libz: libz is required to build the Go binary.sh.pkg-config --modversion z.12. libffi: libffi is required to build the Go binary.sh.pkg-config --modversion libffi.13. libsodium: libsodium is required to build the Go binary.sh.pkg-config --modversion libsodium.中文回答:### GoCTLS 编译要求。
ue gworld 用法

ue gworld 用法GWorld是Unreal Engine(简称UE)中的一个核心概念,用于表示一个世界或一个游戏的实例。
在UE中,游戏的所有内容都在GWorld中管理和加载。
每个GWorld都包含了一个完整的游戏状态,包括所有的角色、物品、环境、关卡等。
以下是一些常见的GWorld用法的简要概述:1. 创建和初始化GWorld:在UE中,每个游戏或应用程序都需要一个GWorld实例。
你可以使用UE的宏宏`G`来创建和初始化GWorld。
例如,`GEngine->GameViewport->GWorld`表示当前的游戏世界。
2. 加载和卸载内容:GWorld提供了加载和卸载内容的功能。
你可以使用GWorld的`LoadContent`和`UnloadContent`方法来加载和卸载游戏内容。
例如,你可以在游戏开始时调用`LoadContent`来加载所有的游戏资源,然后在游戏结束时调用`UnloadContent`来卸载这些资源。
3. 管理游戏状态:GWorld包含了游戏的所有状态,包括角色的位置、状态、装备等。
你可以通过GWorld来获取和修改这些状态。
例如,你可以使用GWorld的`GetActor`方法来获取一个角色的实例,然后修改它的属性或调用它的方法。
4. 事件处理:GWorld提供了事件处理机制,你可以在GWorld中注册事件处理函数,以便在特定事件发生时执行相应的代码。
例如,你可以在GWorld中注册一个事件处理函数来处理角色的死亡事件,当角色死亡时执行相应的逻辑。
以上是GWorld的一些常见用法,具体使用方式可能会因项目需求而有所不同。
如果你需要更详细的信息或示例代码,可以查阅UE的官方文档或相关教程。
GWT开发教程范文

GWT开发教程范文GWT(Google Web Toolkit)是一个由Google开发的Java框架,用于开发基于Web的应用程序。
它通过将Java代码转化为浏览器可执行的JavaScript代码,使开发者能够使用Java语言来开发Web应用程序,而不需要直接编写JavaScript代码。
GWT框架具有良好的兼容性,支持所有主流的浏览器,并提供了丰富的工具和库,使开发者能够更加高效地构建功能强大、响应迅速的Web应用程序。
GWT的核心概念是模块(module)。
模块是应用程序的组件,定义了应用程序的入口点、所需的资源以及需要与服务器进行通信的服务。
创建一个模块时,需要定义模块的名称和入口点。
入口点是应用程序的入口,用于初始化应用程序并将其与浏览器的DOM进行绑定。
在入口点中,可以添加事件处理程序、添加用户界面组件以及执行其他必要的初始化操作。
在GWT中,与服务器通信是非常重要的一部分。
GWT提供了两种方式来实现与服务器的通信:RPC(Remote Procedure Call)和RESTful服务。
RPC是一种基于方法调用的通信方式,可以远程调用在服务器上定义的方法。
通过RPC,可以在客户端和服务器之间传输Java对象,使得服务器和客户端能够共享数据和状态。
RESTful服务是一种基于HTTP协议的通信方式,可以通过发送HTTP请求来与服务器进行交互。
GWT提供了相应的类和方法来封装HTTP请求和响应,使得与服务器的通信变得更加简单和方便。
在开发GWT应用程序时,还需要考虑到应用程序的可维护性和扩展性。
为了提高代码的可维护性,可以使用模块化的开发方法,将相关的代码组织成模块,使得每个模块都具有清晰的责任和功能。
另外,还可以使用设计模式和面向对象的编程思想,使代码具有良好的结构和可理解性。
为了提高代码的扩展性,可以使用依赖注入、模板模式等设计技术,使得应用程序的功能可以灵活地扩展和修改。
总的来说,GWT是一个功能强大、易用且高效的Java开发框架,可以大大简化Web应用程序的开发过程。
gowsdl 用法 -回复

gowsdl 用法 -回复如何使用gowsdl工具。
一、简介gowsdl是一个用于生成Go语言客户端代码的工具,它可以根据WSDL(Web服务描述语言)文件生成对应的API调用代码。
WSDL是一种用于描述Web服务的XML语言,通过使用W SD L,我们可以很方便地定义和描述Web服务的接口、方法、参数等信息。
二、安装gowsdl使用gowsdl之前,我们需要先安装它。
在命令行中执行以下命令可以安装最新版本的gowsdl:go get -u github/hooklift/gowsdl三、生成Go代码在安装完gowsdl之后,我们可以通过以下方法来生成Go代码:1. 打开命令行,进入到包含WSDL文件的目录中。
2. 执行以下命令:gowsdl -o [输出目录] [WSDL文件路径]其中,[输出目录]为生成的Go代码的输出目录,[WSDL文件路径]为需要生成代码的WSDL 文件的路径。
例如,我们有一个名为"example.wsdl"的WSDL文件,我们可以执行以下命令来生成Go 代码:gowsdl -o ./output ./example.wsdl生成的Go代码将会保存在"./output"目录中。
四、使用生成的Go代码生成的Go代码包含了对应的API调用代码,我们可以在自己的项目中引入这些代码,并使用它们来调用对应的Web服务接口。
以"example.wsdl"为例,假设其中定义了一个名为"ExampleService"的服务,并包含一个名为"ExampleMethod"的方法。
我们可以在我们的Go代码中引入生成的代码,并使用它们来调用"ExampleMethod"方法:import ("fmt""github/user/project/output")func main() {创建ExampleService的实例service :=&output.ExampleService{}调用ExampleMethod方法response, err :=service.ExampleMethod("参数1", "参数2") if err != nil {fmt.Println("调用ExampleMethod方法失败:", err)return}处理返回结果fmt.Println("ExampleMethod方法返回结果:", response)}这样,我们就可以使用生成的代码来调用Web服务的接口了。
ffmpeg libavcodec 版本号命名规则

一、概述FFmpeg是一个开源的音视瓶处理工具,其在多个领域有广泛的应用,尤其在音视瓶编解码上具有较高的知名度。
本文主要介绍FFmpeg的libavcodec版本号命名规则,以帮助读者更好地理解和使用FFmpeg 库。
二、FFmpeg libavcodec版本号命名规则1. FFmpeg版本号命名规则FFmpeg采用的版本号命名规则是主版本号.次版本号.发布号的形式。
3.4.6表示主版本号为3,次版本号为4,发布号为6。
其中,主版本号的变化通常与较大的功能更新和兼容性修改相关,次版本号的变化通常与较小的功能更新和接口修改相关,发布号则表示针对特定主次版本的错误修复或小幅更新。
2. libavcodec版本号libavcodec是FFmpeg中负责音视瓶编解码的核心库之一,其版本号遵循与FFmpeg整体版本号相同的命名规则。
libavcodec的版本号与FFmpeg的版本号是一致的,两者共享相同的主次版本号,并且在特定版本的FFmpeg中,其使用的libavcodec版本是固定的,不能自行更改。
3. libavcodec版本号命名规则的变化随着FFmpeg整体版本的更新,libavcodec的版本号也会随之变化。
一般来说,新版本的libavcodec会包含对新的音视瓶编码标准的支持、对现有编码器的性能优化和bug修复等内容。
当使用新版本的FFmpeg时,建议使用相应版本的libavcodec以获得更好的编解码效果和稳定性。
4. 如何查看libavcodec版本号在使用FFmpeg时,可以通过命令行工具或者编程接口查询当前使用的libavcodec版本号。
在命令行中执行以下命令可以查看libavcodec的版本信息:```shellffmpeg -hide_banner```该命令会输出当前FFmpeg的版本号以及与之对应的libavcodec版本号。
另外,如果使用FFmpeg的编程接口进行开发,也可以通过相应的API函数获取libavcodec版本号信息。
ginkgo参数

ginkgo参数Ginkgo 是一个用于 Go 语言的 BDD(行为驱动开发)测试框架。
以下是Ginkgo 的一些常用参数:`-v`:打印详细的测试例执行信息。
`--process`:当使用 `^C` 终止运行后,会打印出执行步骤信息,如BeforeEach 和 JustBefore 中执行到第几步等。
`--noisyPendings=false`:默认值是 true,设置是否打印 Pending 的测试例的信息。
`--failOnPending`:将 Pending 的测试例视为失败。
`--noisySkippings=false`:默认值是 true,设置是否打印 Skip 掉的测试例的信息。
`--skip=REGEXP`:跳过符合正则的测试例,用测试例 It 第一个参数 text 的值做判断。
`--focus=REGEXP`:执行符合正则的测试例,用测试例 It 第一个参数 text 的值做判断。
`-r`:递归执行文件夹内的所有测试用例,用于有多层文件夹的情形。
`--procs=N`:并行运行的进程数。
`--compilers=N`:使用的编译器数量。
`--randomize-all`:随机化所有测试用例的执行顺序。
`--randomize-suites`:随机化测试套件(目录)的执行顺序。
`--fail-on-pending`:将 Pending 的测试用例视为失败。
`--keep-going`:在某个测试用例失败时继续执行其他测试用例。
`--cover`:启用代码覆盖率报告。
`--coverprofile=`:覆盖率报告的文件路径。
`--race`:启用数据竞态检测。
`--trace`:启用调用追踪。
`--json-report=`:JSON 格式的测试报告文件路径。
`--timeout=TIMEOUT`:设置超时时间。
`--poll-progress-after=Xs`:每隔 X 秒打印一次进度信息。
monolog参数

monolog参数英文回答:Monolog is a popular logging library in PHP that allows developers to easily log messages to different channels such as files, databases, email, and more. It provides a simple and flexible way to manage logs in your application.One of the key features of Monolog is its ability to configure different loggers with different handlers and formatters. This allows you to customize how your logs are stored and formatted based on your specific needs. For example, you can create a logger that writes error messages to a file with a specific format, while another logger writes debug messages to a database.Monolog also supports logging levels, which allow you to categorize your log messages based on their severity. This can help you filter out unnecessary information and focus on the most important messages. For instance, you canset different handlers for different log levels, so that critical errors are sent to your email while informational messages are stored in a file.In addition, Monolog provides a variety of built-in handlers and formatters, making it easy to get started with logging in your application. You can also create custom handlers and formatters to suit your specific requirements. This flexibility makes Monolog a powerful tool for managing logs in PHP applications.Overall, Monolog is a versatile and powerful logging library that can help you effectively manage and analyze logs in your PHP applications. Whether you're debugging an issue or monitoring performance, Monolog has the features you need to handle logging in a flexible and efficient way.中文回答:Monolog是PHP中一款流行的日志记录库,允许开发人员轻松地将消息记录到不同的渠道,比如文件、数据库、电子邮件等。
ViggorAPP 990000 Concurrent Dual Band APP 快速入门指南说明

V i g o r A P900C o n c u r r e n tD u a l B a n d A PQuick Start GuideVersion: 1.0Date: 25/07/2013WarrantyWe warrant to the original end user (purchaser) that the router will be free from any defects in workmanship or materials for a period of one (1) year from the date of purchase from the dealer. Please keep your purchase receipt in a safe place as it serves as proof of date of purchase. During the warranty period, and upon proof of purchase, should the product have indications of failure due to faulty workmanship and/or materials, we will, at our discretion, repair or replace the defective products or components, without charge for either parts or labor, to whatever extent we deem necessary tore-store the product to proper operating condition. Any replacement will consist of a new or re-manufactured functionally equivalent product of equal value, and will be offered solely at our discretion. This warranty will not apply if the product is modified, misused, tampered with, damaged by an act of God, or subjected to abnormal working conditions. The warranty does not cover the bundled or licensed software of other vendors. Defects which do not significantly affect the usability of the product will not be covered by the warranty. We reserve the right to revise the manual and online documentation and to make changes from time to time in the contents hereof without obligation to notify any person of such revision or changes.European Community DeclarationsManufacturer: DrayTek Corp.Address: No. 26, Fu Shing Road, HuKou Township, HsinChu Industrial Park, Hsin-Chu, Taiwan 303Product: VigorAP 900DrayTek Corp. declares that VigorAP 900 is in compliance with the following essential requirements and other relevant provisions of R&TTE Directive 1999/5/EEC, ErP 2009/125/EC and RoHS 2011/65/EU.The product conforms to the requirements of Electro-Magnetic Compatibility (EMC) Directive 2004/108/EC by complying with the requirements set forth in EN55022/Class B and EN55024/Class B.The product conforms to the requirements of Low Voltage (LVD) Directive 2006/95/EC by complying with the requirements set forth in EN60950-1.Federal Communication Commission Interference StatementThis equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses and can radiate radio frequency energy and, if not installed and used in accordance with the instructions, may cause harmful interference to radio communications. However, there is no guarantee that interference will not occur in a particular installation. If this equipment does cause harmful interference to radio or television reception, which can be determined by turning the equipment off and on, the user is encouraged to try to correct the interference by one of the following measures:z Reorient or relocate the receiving antenna.z Increase the separation between the equipment and receiver.z Connect the equipment into an outlet on a circuit different from that to which the receiver is connected.z Consult the dealer or an experienced radio/TV technician for help.This device complies with Part 15 of the FCC Rules. Operation is subject to the following two conditions:(1) This device may not cause harmful interference, and(2) This device may accept any interference received, including interference that may cause undesired operation.This product is designed for 2.4GHz/5GHz WLAN network throughout the EC region and Switzerland with restrictions in France.Package ContentQuick Start GuideCDRJ-45 Cable (Ethernet) AntennaThe type of the power adapter depends on the country that the router will be installed:UK-type power adapterEU-type power adapterUSA/Taiwan-type power adapter AU/NZ-type Power AdapterDescriptions of ComponentsLED Status ExplanationOff The system is not ready or is failed.ACTBlinking The system is ready and can work normally.On A USB device is connected and active.USBBlinking The data is transmitting.On Wireless function is ready.Off Wireless function is not ready.2.4GBlinking Data is transmitting (sending/receiving).On Wireless function is ready.Off Wireless function is not ready.5GBlinking Data is transmitting (sending/receiving).On A normal connection (rate with 100M/1000M) isthrough its corresponding port.Off LAN is disconnected.LAN A1 - A4Blinking Data is transmitting (sending/receiving).On A normal connection (rate with 100M/1000M) isthrough its corresponding port.Off LAN is disconnected.LAN BBlinking Data is transmitting (sending/receiving).InterfaceDescriptionWPS Button Press this button for 2 seconds to wait for client device making network connection through WPS. When the orange LED lights up, the WPS will beon.Restore the default settings. Usage: Turn on the router. Press the button and keep for more than 10 seconds. Then the router will restart with the factory default configuration. LAN BConnecter for xDSL / Cable modem (Giga level) or router.LAN A1 (PoE) - A4Connecter for xDSL / Cable modem (Giga level) / computer or router.PWR: Connecter for a power adapter. USBConnector for a printer.ON/OFF: Power switch.Installing Your RouterThis section will guide you to install the AP through hardware connection and configure the settings through web browser.Before starting to configure the router, you have to connect your devices correctly.1.Connect VigorAP 900 to ADSL modem, router, or switch/hub in yournetwork through the LAN A port of the access point by Ethernet cable.Note: You can also connect VigorAP 900 to a Vigor router via wireless connection. For detailed information, refer to VigorAP 900 User’sGuide.2.Connect a computer to other available LAN A port. Make sure thesubnet IP address of the PC is the same as VigorAP 900 management IP,e.g., 192.168.1.X.3.Connect the A/C power adapter to the wall socket, and then connect it tothe PWR connector of the access point.4.Power on VigorAP 900.5.Check all LEDs on the front panel. ACT LED should be steadily on,LAN LEDs should be on if the access point is correctly connected to the ADSL modem, router or switch/hub.Configuring Web PagesThe Operation Mode is designed for you to easily set up your router for Internet access.1.Make sure your PC connects to the router correctly.2.Open a web browser on your PC and type http://192.168.1.2. A pop-upwindow will open to ask for username and password. Pease type“admin/admin” on Username/Password and click Login.3.The Main Screen will pop up. Click Quick Start Wizard.4.The first page is set for 2.4G wireless connection. There are five operationmodes for you to choose. Simply click any one of modes. In this example, choose AP and click Next.5.For the SSID configuration, choose the mode you want and type relatedinformation for client authentication. Then, click Next.6.Next, the following page is set for 5G wireless connection. There are threewireless modes for you to choose. The default is Mixed(11a+11n). Change the information listed in this page according to the data offered by your ISP.Then click Next.7.For the SSID configuration, choose the mode you want and type relatedinformation for client authentication. Then, click Next.8.In the next page, click Finish. The system will make a connectionautomatically. Open Online Status to see the result of network connection.Now, VigorAP 900 is ready for any station to connect for accessing Internet. Contacting Your DealerIf the router still cannot work correctly after trying many efforts, please contact your dealer for further help right away. For any questions, please feel free to *******************************.。
GWT(GoogleWebToolkit)有哪些主要的原件组成?

GWT(GoogleWebToolkit)有哪些主要的原件组成?gwt(googlewebtoolkit)有四个主要的原件组成,他们是:1.一个java到javascript的编译器,用来把gwt应用编译成javascript,这样应用就可以部署到一个web容器中。
2.一个”hosted”的浏览器hosted浏览器可以让你在jvm中执行java那样执行你的gwt应用而不用先编译成javascript。
3.jre模拟类库jre模拟类库包含了大部分常用的ng和java.util包里的类的javascript实现,jdk里面的所有其他包里面的类都不在这个模拟类库中。
在客户端的gwt项目中,只能用jre模拟类库里面的这些类来实现。
4.gwtwebui类库这个类库提供了一些定制的用户接口和类是你能创建多种widgets如buton,textbox,image,gwt附带有几乎所有的在webapplication中最常用的widgets.拓展:有了gwt可以使用java编程语言编写ajax前端,然后gwt会交叉编译到优化的javascript中,而javascript可以自动在所有主要浏览器上运行。
gwt允许开发人员使用java编程语言快速构建和维护复杂但*能高的javascript前端应用程序,从而降低了开发难度,尤其是与eclipsegoogle*件结合使用时,优势更明显。
如今,编写网络应用程序是一个单调乏味且易于出错的过程。
开发人员可能要花费90%的时间来处理浏览器行话。
此外,构建、重复使用以及维护大量javascript代码库和ajax组件可能困难且不可靠。
googleweb工具包(gwt)通过允许开发人员用java编程语言快速构建和维护复杂但高*能的javascript前端应用程序来减轻该负担。
有了googleweb工具包(gwt),可以使用java编程语言编写ajax前端,然后gwt会交叉编译到优化的javascript中,而javascript可以自动在所有主要浏览器上运行。
Linux使用LGOGDownloader怎么下载GOG游戏

Linux使用LGOGDownloader怎么下载GOG游戏GOG是国外热么的游戏销售网站,我们可以在上面购买下载热门游戏,但GOG只有Windows客户端,Linux系统想要下载GOG游戏要怎么办呢?那就需要使用到LGOGDownloader了,下面店铺就给大家介绍下Linux命令行下载GOG游戏的方法,一起来了解下吧。
虽然Windows上的GOG客户端已经存在了很长的时间,但是官方的Linux版本客户端却是无处可见。
因此,如果你不想等待官方的正式版本,一个名为LGOGDownloader非官方的开放源码计划能让你在命令行中访问你的库。
在Linux中安装 LGOGDownloader对于Ubuntu用户来说,其官方页面建议您下载源代码并执行:$ sudo apt-get install build-essential libcurl4-openssl-dev liboauth-dev libjsoncpp-dev libhtmlcxx-dev libboost-system-dev libboost-filesystem-dev libboost-regex-dev libboost-program-options-dev libboost-date-time-dev libtinyxml-dev librhash-dev help2man$ tar -xvzf lgogdownloader-2.17.tar.gz$ cd lgogdownloader-2.17$ make release$ sudo make install如果你是ArchLinux用户。
有一个AUR 包等着你:LGOGDownloader 的使用一旦安装了该程序,你需要用下面的命令登录:$ lgogdownloader --login如果你需要配置文件,那它在这里:~/.config/lgogdownloader/config.cfg验证通过后,你可以列出你库中所有的游戏:$ lgogdownloader --list用下面的命令下载游戏:$ lgogdownloader --download --game [game name]你可以注意到lgogdownloader允许你恢复之前中断的下载,这当下载的游戏并不小时是很有用的。
NVIDIA Shader Debugger for FX Composer June 2008 1
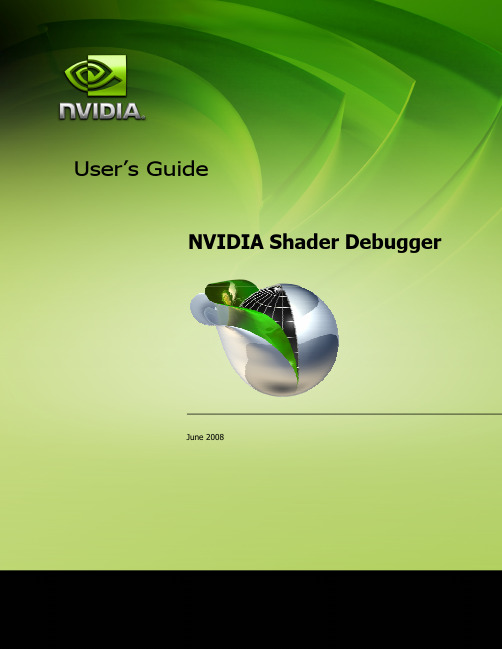
2. Shader/Technique & Function Selector for Editor. On the left, provides a summary of all the techniques and their respective passes for the current effect. On the right, provides a dropdown of all functions in the current shader file.
Makes it easy to understand shader algorithms and control logic Improving productivity by removing the need to embed additional debugging
functionality into shaders Quickly understanding shaders written by other artists, developers, or shader
Feature List
The NVIDIA Shader Debugger contains several features to debug and understand shaders. These features include:
1. Debugger Toolbar. This toolbar contains several convenient buttons:
Features ............................................................................................................. 2 Overview ......................................................................................................................... 2 Feature List...................................................................................................................... 2
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Grey Wolf Optimizer1 Seyedali Mirjalili,2 Seyed Mohammad Mirjalili, 1 Andrew Lewis1 School of Information and Communication Technology, Griffith University, Nathan, Brisbane, QLD 4111,Australia2 Department of Electrical Engineering, Faculty of Electrical and Computer Engineering, Shahid BeheshtiUniversity, G. C. 1983963113, Tehran, Iranseyedali.mirjalili@.au, mohammad.smm@, a.lewis@.auAbstract: This work proposes a new meta-heuristic called Grey Wolf Optimizer (GWO) inspired by grey wolves (Canis lupus). The GWO algorithm mimics the leadership hierarchy and hunting mechanism of grey wolves in nature. Four types of grey wolves such as alpha, beta, delta, and omega are employed for simulating the leadership hierarchy. In addition, the three main steps of hunting, searching for prey, encircling prey, and attacking prey, are implemented. The algorithm is then benchmarked on 29 well-known test functions, and the results are verified by a comparative study with Particle Swarm Optimization (PSO), Gravitational Search Algorithm (GSA), Differential Evolution (DE), Evolutionary Programming (EP), and Evolution Strategy (ES). The results show that the GWO algorithm is able to provide very competitive results compared to these well-known meta-heuristics. The paper also considers solving three classical engineering design problems (tension/compression spring, welded beam, and pressure vessel designs) and presents a real application of the proposed method in the field of optical engineering. The results of the classical engineering design problems and real application prove that the proposed algorithm is applicable to challenging problems with unknown search spaces.Keywords: Optimization, optimization techniques, heuristic algorithm, Metaheuristics, Constrained Optimization, GWO1. IntroductionMeta-heuristic optimization techniques have become very popular over the last two decades. Surprisingly, some of them such as Genetic Algorithm (GA) [1], Ant Colony Optimization (ACO) [2], and Particle Swarm Optimization (PSO) [3] are fairly well-known among not only computer scientists but also scientists from different fields. In addition to the huge number of theoretical works, such optimization techniques have been applied in various fields of study. There is a question here as to why meta-heuristics have become remarkably common. The answer to this question can be summarized into four main reasons: simplicity, flexibility, derivation-free mechanism, and local optima avoidance.First, meta-heuristics are fairly simple. They have been mostly inspired by very simple concepts. The inspirations are typically related to physical phenomena, animals’ behaviors, or evolutionary concepts. The simplicity allows computer scientists to simulate different natural concepts, propose new meta-heuristics, hybridize two or more meta-heuristics, or improve the current meta-heuristics. Moreover, the simplicity assists other scientists to learn meta-heuristics quickly and apply them to their problems.Second, flexibility refers to the applicability of meta-heuristics to different problems without any special changes in the structure of the algorithm. Meta-heuristics are readily applicable to different problems since they mostly assume problems as black boxes. In other words, only the input(s) and output(s) of a system are important for a meta-heuristic. So, all a designer needs is to know how to represent his/her problem for meta-heuristics.Third, the majority of meta-heuristics have derivation-free mechanisms. In contrast to gradient-based optimization approaches, meta-heuristics optimize problems stochastically. The optimization process starts with random solution(s), and there is no need to calculate the derivative of search spaces to find the optimum. This makes meta-heuristics highly suitable for real problems with expensive or unknown derivative information.Finally, meta-heuristics have superior abilities to avoid local optima compared to conventional optimization techniques. This is due to the stochastic nature of meta-heuristics which allow them to avoid stagnation in local solutions and search the entire search space extensively. The search space of real problems is usually unknown and very complex with a massive number of local optima, so meta-heuristics are good options for optimizing these challenging real problems.The No Free Lunch (NFL) theorem [4] is worth mentioning here. This theorem has logically proved that there is no meta-heuristic best suited for solving all optimization problems. In other words, a particular meta-heuristic may show very promising results on a set of problems, but the same algorithm may show poor performance on a different set of problems. Obviously, NFL makes this field of study highly active which results in enhancing current approaches and proposing new meta-heuristics every year. This also motivates our attempts to develop a new meta-heuristic with inspiration from grey wolves.Generally speaking, meta-heuristics can be divided into two main classes: single-solution-based and population-based. In the former class (Simulated Annealing [5] for instance) the search process starts with one candidate solution. This single candidate solution is then improved over the course of iterations. Population-based meta-heuristics, however, perform the optimization using a set of solutions (population). In this case the search process starts with a random initial population (multiple solutions), and this population is enhanced over the course of iterations. Population-based meta-heuristics have some advantages compared to single solution-based algorithms:∙Multiple candidate solutions share information about the search space which results in sudden jumps toward the promising part of search space∙Multiple candidate solutions assist each other to avoid locally optimal solutions∙Population-based meta-heuristics generally have greater exploration compared to single solution-based algorithmsOne of the interesting branches of the population-based meta-heuristics is Swarm Intelligence (SI). The concepts of SI was first proposed in 1993 [6]. According to Bonabeau et al. [1], SI is “The emergent collective intelligence of groups of simple agents”. The inspirations of SI techniques originate mostly from natural colonies, flock, herds, and schools. Some of the most popular SI techniques are ACO [2], PSO [3], and Artificial Bee Colony (ABC) [7]. A comprehensive literature review of the SI algorithms is provided in the next section. Some of the advantages of SI algorithms are:∙SI algorithms preserve information about the search space over the course of iteration, whereas Evolutionary Algorithms (EA) discard the information of the previous generations ∙SI algorithms often utilize memory to save the best solution obtained so far∙SI algorithms usually have fewer parameters to adjust∙SI algorithms have less operators compared to evolutionary approaches (crossover, mutation, elitism, and so on)∙SI algorithms are easy to implementRegardless of the differences between the meta-heuristics, a common feature is the division of the search process into two phases: exploration and exploitation [8-12]. The exploration phase refers to the process of investigating the promising area(s) of the search space as broadly as possible. An algorithm needs to have stochastic operators to randomly and globally search the search space in order to support this phase. However, exploitation refers to the local search capability around the promising regions obtained in the exploration phase. Finding a proper balance between these two phases is considered a challenging task due to the stochastic nature of meta-heuristics. This work proposes a new SI technique with inspiration from the social hierarchy and hunting behavior of grey wolf packs. The rest of the paper is organized as follows:Section 2 presents a literature review of SI techniques. Section 3 outlines the proposed GWO algorithm. The results and discussion of benchmark functions, semi-real problems, and a real application are presented in Section 4, Section 5, and Section 6, respectively. Finally, Section 7 concludes the work and suggests some directions for future studies.2.Literature reviewMeta-heuristics may be classified into three main classes: evolutionary, physics-based, and SI algorithms. EAs are usually inspired by the concepts of evolution in nature. The most popular algorithm in this branch is GA. This algorithm was proposed by Holland in 1992 [13] and simulates Darwnian evolution concepts. The engineering applications of GA were extensively investigated by Goldberg [14]. Generally speaking, the optimization is done by evolving an initial random solution in EAs. Each new population is created by the combination and mutation of the individuals in the previous generation. Since the best individuals have higher probability of participating in generating the new population, the new population is likely to be better than the previous generation(s). This can guarantee that the initial random population is optimized over the course of generations. Some of the EAs are Differential Evolution (DE) [15], Evolutionary Programing (EP) [16, 17], andEvolution Strategy (ES) [18, 19], Probability-Based Incremental Learning (PBIL), Genetic Programming (GP) [20], and Biogeography-Based Optimizer (BBO) [21].As an example, the BBO algorithm was first proposed by Simon in 2008 [21]. The basic idea of this algorithm has been inspired by biogeography which refers to the study of biological organisms in terms of geographical distribution (over time and space). The case studies might include different islands, lands, or even continents over decades, centuries, or millennia. In this field of study different ecosystems (habitats or territories) are investigated for finding the relations between different species (habitants) in terms of immigration, emigration, and mutation. The evolution of ecosystems (considering different kinds of species such as predator and prey) over migration and mutation to reach a stable situation was the main inspiration of the BBO algorithm.The second main branch of meta-heuristics is physics-based techniques. Such optimization algorithms typically mimic physical rules. Some of the most popular algorithms are Gravitational Local Search (GLSA) [22], Big-Bang Big-Crunch (BBBC) [23], Gravitational Search Algorithm (GSA) [24], Charged System Search (CSS) [25], Central Force Optimization (CFO) [26], Artificial Chemical Reaction Optimization Algorithm (ACROA) [27], Black Hole (BH) [28] algorithm, Ray Optimization (RO) [29] algorithm, Small-World Optimization Algorithm (SWOA) [30], Galaxy-based Search Algorithm (GbSA) [31], and Curved Space Optimization (CSO) [32]. The mechanism of these algorithms is different from EAs, in that a random set of search agents communicate and move throughout search space according to physical rules. This movement is implemented, for example, using gravitational force, ray casting, electromagnetic force, inertia force, weights, and so on.For example, the BBBC algorithm was inspired by the big bang and big crunch theories. The search agents of BBBC are scattered from a point in random directions in a search space according to the principles of the big bang theory. They search randomly and then gather in a final point (the best point obtained so far) according to the principles of the big crunch theory. GSA is another physics-based algorithm. The basic physical theory from which GSA is inspired is Newton’s law of universal gravitation. The GSA algorithm performs search by employing a collection of agents that have masses proportional to the value of a fitness function. During iteration, the masses are attracted to each other by the gravitational forces between them. The heavier the mass, the bigger the attractive force. Therefore, the heaviest mass, which is possibly close to the global optimum, attracts the other masses in proportion to their distances.The third subclass of meta-heuristics is the SI methods. These algorithms mostly mimic the social behavior of swarms, herds, flocks, or schools of creatures in nature. The mechanism is almost similar to physics-based algorithm, but the search agents navigate using the simulated collective and social intelligence of creatures. The most popular SI technique is PSO. The PSO algorithm was proposed by Kennedy and Eberhart [3] and inspired from the social behavior of birds flocking. The PSO algorithm employs multiple particles that chase the position of the best particle and their own best positions obtained so far. In other words, a particle is moved considering its own best solution as well as the best solution the swarm has obtained.Another popular SI algorithm is ACO, proposed by Dorigo et al. in 2006 [2]. This algorithm was inspired by the social behavior of ants in an ant colony. In fact, the social intelligence of ants in finding the shortest path between the nest and a source of food is the main inspiration of ACO. A pheromone matrix is evolved over the course of iteration by the candidate solutions. The ABC is another popular algorithm, mimicking the collective behavior of bees in finding food sources. There are three types of bees in ABS: scout, onlooker, and employed bees. The scout bees are responsible for exploring the search space, whereas onlooker and employed bees exploit the promising solutions found by scout bees. Finally, the Bat-inspired Algorithm (BA), inspired by the echolocation behavior of bats, has been proposed recently [33]. There are many types of bats in the nature. They are different in terms of size and weight, but they all have quite similar behaviors when navigating and hunting. Bats utilize natural sonar in order to do this. The two main characteristics of bats when finding prey have been adopted in designing the BA algorithm. Bats tend to decrease the loudness and increase the rate of emitted ultrasonic sound when they chase prey. This behavior has been mathematically modeled for the BA algorithm. The rest of the SI techniques proposed so far are as follows:∙Marriage in Honey Bees Optimization Algorithm (MBO) in 2001 [34]∙Artificial Fish-Swarm Algorithm (AFSA) in 2003 [35]∙Termite Algorithm in 2005 [36]∙Wasp Swarm Algorithm in 2007 [37]∙Monkey Search in 2007 [38]∙Bee Collecting Pollen Algorithm (BCPA) in 2008 [39]∙Cuckoo Search (CS) in 2009 [40]∙Dolphin Partner Optimization (DPO) in 2009 [41]∙Firefly Algorithm (FA) in 2010 [42]∙Bird Mating Optimizer (BMO) in 2012 [43]∙Krill Herd (KH) in 2012 [44]∙Fruit fly Optimization Algorithm (FOA) in 2012 [45]This list shows that there are many SI techniques proposed so far, many of them inspired by hunting and search behaviors. To the best of our knowledge, however, there is no SI technique in the literature mimicking the leadership hierarchy of grey wolves, well known for their pack hunting. This motivated our attempt to mathematically model the social behavior of grey wolves, propose a new SI algorithm inspired by grey wolves, and investigate its abilities in solving benchmark and real problems.3.Grey Wolf Optimizer (GWO)In this section the inspiration of the proposed method is first discussed. Then, the mathematical model is provided.3.1. InspirationGrey wolf (Canis lupus) belongs to Canidae family. Grey wolves are considered as apex predators, meaning that they are at the top of the food chain. Grey wolves mostly prefer to live in a pack. The group size is 5-12 on average. Of particular interest is that they have a very strict social dominant hierarchy as shown in Fig. 1.Fig. 1. Hierarchy of grey wolf (dominance decreases from top down)The leaders are a male and a female, called alphas. The alpha is mostly responsible for making decisions about hunting, sleeping place, time to wake, and so on. The a lpha’s decisions are dictated to the pack. However, some kind of democratic behavior has also been observed, in which an alpha follows the other wolves in the pack. In gatherings, the entire pack acknowledges the alpha by holding their tails down. The alpha wolf is also called the dominant wolf since his/her orders should be followed by the pack [46]. The alpha wolves are only allowed to mate in the pack. Interestingly, the alpha is not necessarily the strongest member of the pack but the best in terms of managing the pack. This shows that the organization and discipline of a pack is much more important than its strength.The second level in the hierarchy of grey wolves is beta. The betas are subordinate wolves that help the alpha in decision-making or other pack activities. The beta wolf can be either male or female, and he/she is probably the best candidate to be the alpha in case one of the alpha wolves passes away or becomes very old. The beta wolf should respect the alpha, but commands the other lower-level wolves as well. It plays the role of an advisor to the alpha and discipliner for the pack. The beta reinforces the alpha's commands throughout the pack and gives feedback to the alpha.The lowest ranking grey wolf is omega. The omega plays the role of scapegoat. Omega wolves always have to submit to all the other dominant wolves. They are the last wolves that are allowed to eat. It may seem the omega is not an important individual in the pack, but it has been observed that the whole pack face internal fighting and problems in case of losing the omega. This is due to the venting of violence and frustration of all wolves by the omega(s). This assists satisfying the entire pack and maintaining the dominance structure. In some cases the omega is also the babysitters in the pack.If a wolf is not an alpha, beta, or omega, he/she is called subordinate (or delta in some references). Delta wolves have to submit to alphas and betas, but they dominate the omega. Scouts, sentinels, elders, hunters, andcaretakers belong to this category. Scouts are responsible for watching the boundaries of the territory and warning the pack in case of any danger. Sentinels protect and guarantee the safety of the pack. Elders are the experienced wolves who used to be alpha or beta. Hunters help the alphas and betas when hunting prey and providing food for the pack. Finally, the caretakers are responsible for caring for the weak, ill, and wounded wolves in the pack.In addition to the social hierarchy of wolves, group hunting is another interesting social behavior of grey wolves. According to Muro et al. [47] the main phases of grey wolf hunting are as follows: ∙Tracking, chasing, and approaching the prey∙Pursuing, encircling, and harassing the prey until it stops moving∙Attack towards the preyThese steps are shown in Fig. 2.Fig. 2. Hunting behaviour of grey wolves: (A) chasing, approaching, and tracking prey (B-D) pursuiting, harassing, and encircling(E) stationary situation and attack [47]In this work this hunting technique and the social hierarchy of grey wolves are mathematically modeled in order to design GWO and perform optimization.3.2. Mathematical model and algorithmIn this subsection the mathematical models of the social hierarchy, tracking, encircling, and attacking prey are provided. Then the GWO algorithm is outlined.3.2.1. Social hierarchy:In order to mathematically model the social hierarchy of wolves when designing GWO, we consider the fittest solution as the alpha (). Consequently, the second and third best solutions are named beta () and delta () respectively. The rest of the candidate solutions are assumed to be omega (). In the GWO algorithm the hunting (optimization) is guided by , , and . The wolves follow these three wolves.3.2.2. Encircling prey:As mentioned above, grey wolves encircle prey during the hunt. In order to mathematically model encircling behavior the following equations are proposed:⃗ ⃗⃗⃗⃗(3.1)⃗⃗⃗⃗ ⃗(3.2)where t indicates the current iteration, and are coefficient vectors , ⃗⃗⃗⃗ is the position vector of the prey,andindicates the position vector of a grey wolf. The vectors and are calculated as follows: = 2 . ⃗⃗⃗ - (3.3) ⃗⃗⃗(3.4)where components of are linearly decreased from 2 to 0 over the course of iterations and , are random vectors in [0,1].To see the effects of equations (3.1) and (3.2), a two-dimensional position vector and some of the possible neighbors are illustrated in Fig. 3 (a). As can be seen in this figure, a grey wolf in the position of (X,Y ) can update its position according to the position of the prey (X*,Y*). Different places around the best agent can bereached with respect to the current position by adjusting the value ofand vectors. For instance, (X*-X,Y*) can be reached by settingand . The possible updated positions of a grey wolf in 3D space are depicted in Fig. 3 (b). Note that the random vectors and allow wolves to reach any position between the points illustrated in Fig. 3. So a grey wolf can update its position inside the space around the prey in any random location by using equations (3.1) and (3.2).(X*,Y*)(X*,Y)(X,Y*)(X,Y*-Y)(X*-X,Y)(X*,Y*-Y)(X*-X,Y*-Y)(X*-X,Y*)(X*,Y*,Z*)(X,Y*-Y,Z*-Z)(X*-X,Y,Z*-Z)(X*,Y*-Y,Z*-Z)(X*-X,Y*-Y,Z-Z*)(X*-X,Y*,Z*-Z)(X,Y*,Z)(X,Y*-Y,Z)(X,Y*,Z*)(X,Y,Z*)(X*,Y*,Z*-Z)(X,Y*,Z*-Z)(X*,Y,Z*-Z)(X,Y,Z*-Z)(X*-X,Y,Z*)(X,Y,Z*)(X*,Y,Z*)(b)Fig. 3.2D and 3D position vectors and their possible next locationsThe same concept can be extended to a search space with n dimensions, and the grey wolves will move in hyper-cubes (or hyper-spheres) around the best solution obtained so far.3.2.3. Hunting:Grey wolves have the ability to recognize the location of prey and encircle them. The hunt is usually guided by the alpha. The beta and delta might also participate in hunting occasionally. However, in an abstract search space we have no idea about the location of the optimum (prey). In order to mathematically simulate the hunting behavior of grey wolves, we suppose that the alpha (best candidate solution) beta, and delta have better knowledge about the potential location of prey. Therefore, we save the first three best solutions obtained so far and oblige the other search agents (including the omegas) to update their positions according to the position of the best search agent. The following formulas are proposed in this regard.⃗⃗⃗⃗⃗ ⃗⃗⃗⃗ , ⃗⃗⃗⃗ ⃗⃗⃗⃗ , ⃗⃗⃗⃗ ⃗⃗⃗⃗ ⃗⃗⃗⃗ (3.5)⃗⃗⃗⃗ ⃗⃗⃗⃗ ( ⃗⃗⃗⃗⃗ ), ⃗⃗⃗⃗ ⃗⃗⃗⃗ ⃗⃗⃗⃗ ( ⃗⃗⃗⃗ ), ⃗⃗⃗⃗ ⃗⃗⃗⃗ ⃗⃗⃗⃗ ( ⃗⃗⃗⃗ )(3.6)⃗⃗⃗⃗ ⃗⃗⃗⃗ ⃗⃗⃗⃗(3.7)Fig. 4 shows how a search agent updates its position according to alpha, beta, and delta in a 2D search space. It can be observed that the final position would be in a random place within a circle which is defined by the positions of alpha, beta, and delta in the search space. In other words alpha, beta, and delta estimate the position of the prey, and other wolves updates their positions randomly around the prey.Fig. 4. Position updading in GWO3.2.4. Attacking prey (exploitation):As mentioned above the grey wolves finish the hunt by attacking the prey when it stops moving. In order to mathematically model approaching the prey we decrease the value of . Note that the fluctuation range of is also decreased by . In other words is a random value in the interval [-a,a] where a is decreased from 2 to 0 over the course of iterations. When random values of are in [-1,1], the next position of a search agent can be in any position between its current position and the position of the prey. Fig. 5 (a) shows that |A|<1 forces the wolves to attack towards the prey.(a) (b)Fig. 5. Attacking prey versus searching for preyWith the operators proposed so far, the GWO algorithm allows its search agents to update their position based on the location of the alpha, beta, and delta; and attack towards the prey. However, the GWO algorithm is prone to stagnation in local solutions with these operators. It is true that the encircling mechanism proposed shows exploration to some extent, but GWO needs more operators to emphasize exploration.3.2.5. Search for prey (exploration):Grey wolves mostly search according to the position of the alpha, beta, and delta. They diverge from each other to search for prey and converge to attack prey. In order to mathematically model divergence, we utilize with random values greater than 1 or less than -1 to oblige the search agent to diverge from the prey. This emphasizes exploration and allows the GWO algorithm to search globally. Fig. 5(b) also shows that |A|>1 forces the grey wolves to diverge from the prey to hopefully find a fitter prey. Another component of GWO that favors exploration is . As may be seen in Equation (3.4), the vector contains random values in [0, 2]. This component provides random weights for prey in order to stochastically emphasize (C>1) or deemphasize (C<1) the effect of prey in defining the distance in Equation (3.1). This assists GWO to show a more random behavior throughout optimization, favoring exploration and local optima avoidance. It is worth mentioning here that C is not linearly decreased in contrast to A. We deliberately require C to provide random values at all times in order to emphasize exploration not only during initial iterations but also final iterations. This component is very helpful in case of local optima stagnation, especially in the final iterations.The C vector can be also considered as the effect of obstacles to approaching prey in nature. Generally speaking, the obstacles in nature appear in the hunting paths of wolves and in fact prevent them from quickly and conveniently approaching prey. This is exactly what the vector C does. Depending on the position of a wolf, it can randomly give the prey a weight and make it harder and farther to reach for wolves, or vice versa.To sum up, the search process starts with creating a random population of grey wolves (candidate solutions) in the GWO algorithm. Over the course of iterations, alpha, beta, and delta wolves estimate the probable position of the prey. Each candidate solution updates its distance from the prey. The parameter a is decreased from 2 to 0 in order to emphasize exploration and exploitation, respectively. Candidate solutions tend to diverge from the prey when ||>1 and converge towards the prey when ||<1. Finally, the GWO algorithm is terminated by the satisfaction of an end criterion.The pseudo code of the GWO algorithm is presented in Fig. 6.Fig. 6. Pseudo code of the GWO algorithmTo see how GWO is theoretically able to solve optimization problems, some points may be noted: ∙The proposed social hierarchy assists GWO to save the best solutions obtained so far over the course of iteration∙The proposed encircling mechanism defines a circle-shaped neighborhood around the solutions which can be extended to higher dimensions as a hyper-sphere∙The random parameters A and C assist candidate solutions to have hyper-spheres with different random radii∙The proposed hunting method allows candidate solutions to locate the probable position of the prey ∙Exploration and exploitation are guaranteed by the adaptive values of a and A∙The adaptive values of parameters a and A allow GWO to smoothly transition between exploration and exploitation∙With decreasing A, half of the iterations are devoted to exploration (|A|≥1) and the other half are dedicated to exploitation (|A|<1)∙The GWO has only two main parameters to be adjusted (a and C)There are possibilities to integrate mutation and other evolutionary operators to mimic the whole life cycle of grey wolves. However, we have kept the GWO algorithm as simple as possible with the fewest operators to be adjusted. Such mechanisms are recommended for future work. The source codes of this algorithm can be found in /GWO.html and .au/matlabcentral/fileexchange/44974.4.Results and discussionIn this section the GWO algorithm is benchmarked on 29 benchmark functions. The first 23 benchmark functions are the classical functions utilized by many researchers [16, 48-51]. Despite the simplicity, we have chosen these test functions to be able to compare our results to those of the current meta-heuristics. These benchmark functions are listed in Table 1, Table 2, and Table 3 where Dim indicates dimension of the function, Range is the boundary of the function’s search space, and f min is the optimum. The other test beds that we have chosen are six composite benchmark functions from a CEC 2005 special session [52]. These benchmark functions are the shifted, rotated, expanded, and combined variants of the classical functions which offer the greatest complexity among the current benchmark functions [53]. Tables 4 lists the CEC 2005 test functions, where Dim indicates dimension of the function, Range is the boundary of the function’s search space, and f min is the optimum. Fig. 7, Fig. 8, Fig. 9, and Fig. 10 illustrate the 2D versions of the benchmark functions used.Generally speaking, the benchmark functions used are minimization functions and can be divided into four groups: unimodal, multimodal, fixed-dimension multimodal, and composite functions. Note that a detailed descriptions of the composite benchmark functions are available in the CEC 2005 technical report [52].。
