IPV6技术白皮书5
IPv6技术白皮书
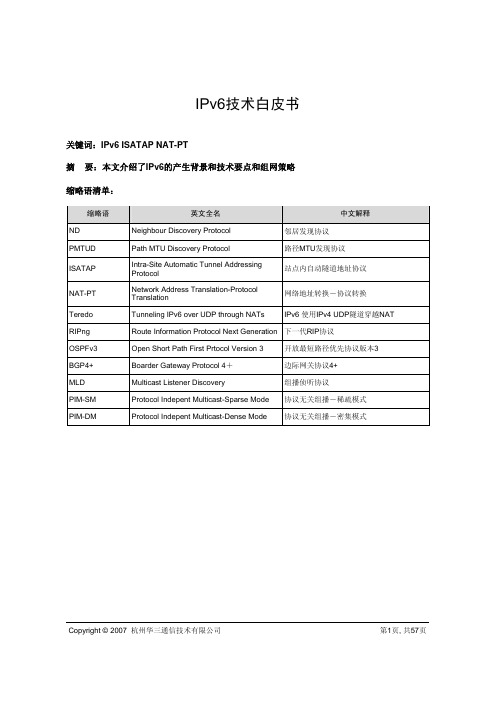
IPv6技术白皮书关键词:IPv6 ISATAP NAT-PT摘要:本文介绍了IPv6的产生背景和技术要点和组网策略缩略语清单:缩略语英文全名中文解释ND Neighbour Discovery Protocol 邻居发现协议PMTUD Path MTU Discovery Protocol 路径MTU发现协议ISATAP Intra-Site Automatic Tunnel AddressingProtocol站点内自动隧道地址协议NAT-PT Network Address Translation-ProtocolTranslation网络地址转换-协议转换Teredo Tunneling IPv6 over UDP through NATs IPv6 使用IPv4 UDP隧道穿越NATRIPng Route Information Protocol Next Generation下一代RIP协议OSPFv3 Open Short Path First Prtocol Version 3 开放最短路径优先协议版本3BGP4+ Boarder Gateway Protocol 4+边际网关协议4+MLD Multicast Listener Discovery 组播侦听协议PIM-SM Protocol Indepent Multicast-Sparse Mode 协议无关组播-稀疏模式PIM-DM Protocol Indepent Multicast-Dense Mode 协议无关组播-密集模式Copyright © 2007 杭州华三通信技术有限公司第1页, 共57页目录1 概述 (4)2 技术应用背景 (4)2.1 IPv6产生的背景 (4)2.2 技术优点 (6)3 特性介绍 (11)3.1 IPv6报文格式 (11)3.1.1 IPv6报文基本头格式 (11)3.1.2 IPv6报文扩展头格式 (13)3.1.3 IPv6 ICMP报文格式 (15)3.2 IPv6地址结构定义 (15)3.2.1 IPv6地址表示 (15)3.2.2 IPv6地址前缀表示 (16)3.2.3 IPv6地址分类 (16)3.2.4 IPv6单播地址 (17)3.2.5 IPv6泛播地址 (18)3.2.6 IPv6多播地址 (19)3.2.7 嵌入IPv4地址的IPv6地址 (21)3.2.8 IPv6中特殊的地址 (22)3.2.9 节点和路由器必须支持的IPv6地址 (22)3.3 IPv6地址分配 (23)3.3.1 全球单播地址空间分配 (23)3.3.2 IPv6实验网络地址分配(6BONE) (24)4 IPv6基本功能 (24)4.1 IPv6邻居发现协议 (24)4.1.1 邻居发现 (25)4.1.2 路由器发现 (26)4.1.3 IPv6无状态地址自动配置 (28)4.1.4 重定向 (28)4.2 IPv6路径MTU发现协议 (28)4.3 IPv6域名解析 (29)5 IPv4向IPv6过渡技术 (30)Copyright © 2007 杭州华三通信技术有限公司第2页, 共57页5.1 IPv6/IPv4双协议栈 (31)5.1.1 双栈 (31)5.1.2 DSTM (31)5.2 IPv6穿越IPv4隧道技术 (33)5.2.2 IPv6手工配置隧道 (34)5.2.3 IPv4兼容自动隧道 (34)5.2.4 6to4自动隧道 (35)5.2.5 ISATAP隧道 (37)5.2.6 IPv6 over IPv4 GRE隧道 (39)5.2.7 隧道代理 (39)5.2.8 6over4机制 (40)5.2.9 6PE (41)5.2.10 Teredo隧道 (42)5.3 IPv6与IPv4互通技术 (42)5.3.1 SIIT (43)5.3.2 NAT-PT (44)5.3.3 BIS (47)5.3.4 BIA (48)5.3.5 TRT (49)5.3.6 Socket IPv4/IPv6网关 (50)6 IPv6路由技术 (51)6.1 IPv6单播路由协议 (51)6.1.1 RIPng (51)6.1.2 OSPFv3 (51)6.1.3 ISISv6 (52)6.1.4 BGP4+ (52)6.2 IPv6多播路由协议 (53)6.2.1 MLDv1 Snooping (53)6.2.2 MLDv1 (53)6.2.3 PIM-SM (53)6.2.4 PIM-DM (53)7 IPv6部署策略 (53)8 相关协议标准 (55)Copyright © 2007 杭州华三通信技术有限公司第3页, 共57页1 概述IPv6(Internet Protocol Version 6,因特网协议版本6)是网络层协议的第二代标准协议,也被称为IPng(IP Next Generation,下一代因特网),它是IETF(Internet Engineering Task Force,Internet工程任务组)设计的一套规范,是IPv4的升级版本。
筑牢下一代互联网安全防线—IPv6网络安全白皮书().doc

筑牢下一代互联网安全防线—IPv6网络安全白皮书()筑牢筑牢下一代互联网安全防线下一代互联网安全防线——IPv6网络安全白皮书网络安全白皮书中国信息通信研究院中国信息通信研究院年9月月前前言言当前,网络信息技术加速引领新一轮科技革命,以前所未有的广度和深度引发经济社会多方位、全领域、深层次的技术创新和产业变革。
在5G、物联网、工业互联网等新兴领域蓬勃发展,人人互联加速向万物互联迈进的时代趋势下,网络空间传统IPv4地址资源紧缺等问题日益凸显,以IPv6为代表的下一代互联网技术应运而生。
IPv6凭借其海量地址空间、内嵌安全能力等技术优势,为泛在融合、大连接的新形势下网络信息技术的创新发展提供基础网络资源支撑,已成为促进生产生活数字化、网络化、智能化发展的核心要素,吸引世界发达国家的广泛关注和大力投入。
近年来,我国紧抓全球网络信息技术加速创新变革、信息基础设施快速演进升级的历史机遇,全力推进下一代互联网部署应用,为经济社会发展和网络强国建设提供有力支撑。
然而,IPv4向IPv6网络的升级演进是一个长期、持续的过程,现阶段已部署上线的IPv6业务仍相对有限,IPv6部署应用过程中的网络安全风险尚未完全显现。
此种客观情况对IPv6新环境下的网络安全防御工作而言是挑战也是机遇,与传统网络安全防御攻击方更为被动的形势相比,在IPv6环境中,攻防双方正处于同一起跑线上。
我们更应高度重视下一代互联网演进升级中存在的安全风险,加快提升IPv6网络安全防护能力,构建形成IPv6网络安全防护主动局面。
我院联合安天科技股份有限公司、北京蓝汛通信技术有限责任公司、北京天融信网络安全技术有限公司、北京知道创宇信息技术股份有限公司、北京神州绿盟信息安全科技股份有限公司、华为技术有限公司、杭州安恒信息技术股份有限公司、奇安信科技集团股份有限公司、上海观安信息技术股份有限公司、深信服科技股份有限公司、深圳市腾讯计算机系统有限公司、网宿科技股份有限公司、亚信科技(成都)有限公司、中国电信集团有限公司、中国联合网络通信集团有限公司、中国移动通信集团有限公司1共同推出《筑牢下一代互联网安全防线—IPv6网络安全白皮书》。
IPv6 Proxy技术白皮书

IPv6 Proxy技术白皮书文件编号文件类别技术白皮书编写周剡东日期2007年3月27日审核日期批准日期神州数码网络有限公司修改记录版本日期修改纪要修改人审核人发现问题1.0 2007-03-27 创建周剡东1.1 2007-03-30 修改部分专业术语修改3.4.2小节3.5节增加规避方法周剡东目录1.概述 (1)2.缩写和术语 (1)3.技术介绍 (1)3.1IP V6卡类型 (1)3.2应用环境 (2)3.3P ROXY配置 (2)3.4报文处理 (2)3.4.1二层IPv6报文 (2)3.4.2三层IPv6报文 (2)3.4.3IPv6协议报文 (3)3.5应用缺陷与规避方法 (4)3.5.1应用缺陷 (4)3.5.2规避方法 (4)4.典型应用指南 (4)4.1应用一 (4)4.2应用二 (5)5.参考资料 (6)1. 概述IPv6 Proxy指IPv6代理功能,用于分布式机架交换机,如7604和7608机架交换机。
IPv6 Proxy功能指在机架交换机中,仅支持IPv4硬件功能的线卡通过IPv6线卡的代理功能,实现IPv6的硬件转发。
IPv6 Proxy功能在实际应用中非常重要。
首先,早期的板卡仅支持IPv4硬件功能,不能转发IPv6报文,但机架交换机可以插入不同类型的板卡,可能出现一些板卡能转发IPv6报文,而一些板卡不能转发IPv6报文,引起不一致的问题;其次,支持IPv6硬件转发的板卡成本较高。
IPv6 Proxy功能很好的解决上面两个问题:第一,仅支持IPv4的板卡通过IPv6卡的IPv6 Proxy功能,也能实现IPv6的硬件功能,保持机架交换机的整体一致性;第二,机架交换机中只要插入一块IPv6卡,整个机架交换机既能支持IPv4硬件功能,也支持IPv6硬件功能,从而节约成本。
本文档将IPv6 Proxy功能主要特性和技术介绍合为一节,参看第3节。
本文档将介绍IPv6 Proxy功能的相关技术,适合网络公司售前技术工程师及相关人员。
互联网协议版本6 (IPv6) 白皮书

Table of ContentsIntroduction. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3 Why Internet Protocol Version 6? . . . . . . . . . . . . . . . . . . . . . . . . . 3 IPv6 History . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3 Differences between IPv4 and IPv6 . . . . . . . . . . . . . . . . . . . . . . . 4 Benefits of IPv6 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5 IPv6 Transition; Who Will Use it and Where?. . . . . . . . . . . . . . . . . . . . . . 6 Global Transition to IPv6. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6 IPv6 Transition Options. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6 Who Will Transition to IPv6?. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7 Where IPv6 is Used in the Network . . . . . . . . . . . . . . . . . . . . . . . 9 IPv6: The Technology. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10 Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10 Technical Changes from IPv4. . . . . . . . . . . . . . . . . . . . . . . . . . . . 10 An Introduction to the IPv6 Addressing Architecture. . . . . . . . 12Unicast Addresses. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13 Anycast Addresses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13Multicast Addressing. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14 Use of Unicast Addresses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16 Use of Anycast Addresses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16 Use of Multicast Addresses. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16 Impact of New Addressing Formats. . . . . . . . . . . . . . . . . . . . . . 17 Impact of IPv6 Address Auto-Configuration. . . . . . . . . . . . . . . . 18 Header Flow Labels and Header Extensions. . . . . . . . . . . . . . . 18 IPv6: The Security Perspective . . . . . . . . . . . . . . . . . . . . . . . . . . 19 IPv6 and Convergence. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21 Introduction. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21 IPv6 and Real-Time Applications . . . . . . . . . . . . . . . . . . . . . . . . 21 Conclusion. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22 Summary. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22 Technical References . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22 Other Web References . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23IntroductionIPv6 has been standardized for a number of years, although additional work is still ongoing in areas such as defining IPv6 versions of common applications and auxiliary protocols such as OSPF, IS-IS, Telnet, FTP and others. Additionally, the major issue IPv6 is expected to solve—the depletion of IPv4 addresses as the Internet grows—has failed to materialize as quickly as anticipated. This is due to the advent of technologies such as Network Address Translation (NAT) and Classless Inter Domain Routing (CIDR), which optimize IPv4 address usage and extend its life. Finally, since IPv4 addresses are disproportion-ately assigned to North American entities, the urgency in the largest market (the U.S.) has lagged behind the rest of the world where IPv4 addresses are more limited and technology adoption of new IP devices, such as 3g cellular, is more aggressive. All of these factors contributed to the market’s wait-and-see view of IPv6, and resulted in no real commitment to IPv6 by customers until recently.What has changed, and why IPv6 matters to all of us, is that major forces are beginning to push for the deployment of “IPv6-capable” networks. These forces include the United States federal government and its Global Information Grid (GIG) project. The federal government will spend some $35B annually on this new initiative and has committed that it will be “IPv6 capable.” Additionally, the governments of Japan and the European Union have mandated that in the near future, network devices must support IPv6. Given that the U.S. government is the single largest IT customer in the world and the EU and APACmarkets represent substantial portions of the IT market, the reality is that the customers exist for “IPv6 capable.”Why Internet Protocol Version 6?A great deal of industry press has been devoted to the “Next-Generation Internet Protocol, V ersion 6.” IPv6 has the potential to change the way we view computing and communications. IPv6 has been designed to facilitate pervasive mobile computing and information sharing on a worldwide scale. It is intended to allow almost every device that can be connected to a network to communicate. Because of this, there has been a great deal of excitement about this protocol.Based on the expected scalability of IPv6, many network operators and national governments around the world are embracing the enhanced Internet protocol. This is especially true in Asia and parts of Europe, where a lack of IP address space is viewed as a strategic national issue. Examples of the disparity in the distribution of current addresses can be seen in the fact that the country of China has the same number of official IP addresses as the Massachusetts Institute of Technology and that the single company formed by the merger of Digital Equipment, Compaq Computer and Hewlett Packard likely resulted in an organization with at least two Class A network address blocks.IPv6 HistoryThe Internet Protocol Next Generation (IPng) W orking Group of the Internet Engineering Task Force (IETF) was formed in the early 1990s to create a more scalable Internet protocol that would also address the issues with IPv4 addressing. When IPv4 was created, its creators felt that an address of 32 bits, which allows for a potential of 4 billion network hosts, would be more than enough to handle the computing needs of the U.S. government. In practical terms, though, the usable addresses are less than 4 billion. In the IETF RFC 3194, Internet scientists calculate that there are, at most, usable addresses for 250 millionhosts. By the end of 2002, there were 600 million Internet users, and that number was expected to grow to 950 million by the end of 2004. This growth will require a more expansive address space. To d a y, we use technologies such as Network Address Translation (NAT) to provide more IPv4 address scalability, but NAT inhibits host-to-host communications, which was the original design goal of the originators of the Internet. The IETF engineers that created IPv6 wanted a protocol that could scale to handle billions and billions of addresses; with an address of 128 bits, IPv6 can scale to 3.4 x 1038 addresses! Differences between IPv4 and IPv6IPv6 is very similar to IPv4, but it has been refined. Most applications that are compatible with IPv4 will also be compatible with IPv6. TCP, UDP, ICMP and IPSec are directly trans-portable by IPv6 just as they are with IPv4. The only applications that will have to be redesigned are the ones that encapsulate a work station’s IP address in the TCP or UDP payload, such as SQL and SNMP.IPv6 is more than just a large address space. IPv6 has been streamlined over its predecessor. IPv6 enforces geographic and regional addressing, where organizations will have common “prefixes” based on where they are located and the provider through whom they are connecting. This is similar to the way public phone networks operate, where companies in the state of Massachusetts, U.S., for instance, have a regional telephony area code of 978 or every company in Great Britain has a telephony country code of +44.IPv6 has also brought security to the forefront by requiring IPSec for host-level end-to-ends e c u r i t y. End-system addressing has been greatly simplified with the advent of address a u t o-d i s c o v e r y. Ty p i c a l l y, an end station will learn the IPv6 address for the local router, and then build its own address by combining the local “prefix” with its own MAC address. There is also an effort underway to develop a variant of Dynamic Host Configuration Protocol for version 6.The biggest technological change for IPv6 is the inability to broadcast packets to the network. IPv6 supports Unicast Addressing for one-to-one communications, Multicast Addressing for one-to-many communications and Anycast Addressing for one-to-nearest communications. It is expected that applications that used to rely on IP broadcasting will move to multicasting. The routing protocols necessary to operate an IPv6 network are similar to the protocols needed to run an IPv4 network. RIP, OSPF, ISIS, BGP and PIM are all supported with IPv6. A network operating with both IPv4 and IPv6 workstations will run IPv4 and IPv6 versions of the routing protocol simultaneously; meaning that if today a network operates with OSPFv2 for IPv4, it will concurrently operate with OSPFv3 for IPv6.The IETF originally intended for IPv6 to replace IPv4, but the IETF has changed its position and indicated that IPv4 will be around for a long time. To d a y, it is envisioned that there will be a great number of dual-protocol networks running both IPv4 and IPv6 concurrently. The IETF has created a working group called NG-TRANS (Next-Generation Tr a n s i t i o n), which is developing technologies that will allow the protocols to share the same network and translate between the two protocols.Benefits of IPv6The primary benefits of IPv6 technology will be realized in the ability of an organization or enterprise to address every computing element within their organization directly, whether it is a mainframe, Linux/Windows workstation, wireless phone, PDA, security camera, soda machine, or home refrigerator. IPv6 will facilitate uninterrupted communi-cation between hosts without the limitations imposed by today’s NAT. IPv4 systems will be able to communicate directly with any system on the next-generation Internet. This will be of particular value to research and educational institutions. Operators of large campuses can incorporate all security systems into the campus network. Hospitals and medical organizations can incorporate medical telemetry and analysis systems with mobile communication systems carried by health care providers. IPv6 will facilitate a worldwide infrastructure to support public mobile computing, so users can utilize their mobile IP phones or laptops or PDAs anywhere in the world.For enterprise networks, there may not be a compelling case to move to IPv6 today, which may hinder the overall adoption of IPv6. For many enterprises, the lack of enterprise-specific applications and the administrative overhead of running dual-stack networks can override the benefits of IPv6. While HTTP6, FTP6 and Telnet6 are available today, there are few if any Enterprise Resource Planning (ERP), CRM or manufacturing automation applications that are supported by IPv6 today. Microsoft Exchange will operate over IPv6, but Microsoft SQL will not. That is potentially a major barrier since businesses run theirERP applications on SQL. Most enterprises finally arrived at an “IP (v4) only” network after years of being multiprotocol organizations with Novel IPX, SNA, DECnet, AppleTa l k,Banyan Vines and others. To d a y, there are only a few enterprises that need worldwide host-to-host connectivity, and in fact, many enterprises utilize NAT as a security mechanism, and will not likely change that any time soon.IPv6 Transition; Who Will Use it and Where?Global Transition to IPv6IPv6, the new emerging standard for communications on networks, is facing some interesting issues around its implementation. How IPv6 will be implemented globally, the geographies and organizations which will adopt IPv6, and which configurations are deployed, all will drive the transition to IPv6.In the world today, an area with a great drive to move toward IPv6 is Asia, followed by Europe. The reason for this is simple. Asia was late into the official assignment of IPv4 addresses, and because of this, there is a serious lack of address space in Asia, followed by almost the same shortage in Europe. Because Asia is one of the fastest areas of growth for networking, they are demanding more and more of a diminishing number of IPv4 addresses. Generally, organizations in Asia see IPv6 as the solution to this. There are an abundance of addresses in IPv6 that will solve this address space problem.After Asia, adoption of IPv6 will be most important in EMEA, Latin and South America, and finally North America. The reason that adoption will happen in this order is related to how adoption of IPv4 initially occurred. Regions that adopted IPv4 early managed to register enough address space so that they worry less about running out of address space in the short term. In addition, many organizations have adopted techniques to handle newaddresses inside their networks while maintaining the same original registered external addresses. As an example of this we can look at a typical enterprise. The company canhave registered a class “C” address domain. This gives the organization 255 registered Internet addresses. Conceivably every employee and every device inside the company could have their own Internet address, but only if there are less than 255 people and devices. If there are more people and devices, then they will need to create an address scheme based on private addresses. These addresses are not valid outside the organization. In order to communicate to the outside world, the traffic passes through a firewall and a NAPT (Network Address Port Translator) device at the edge of the internal network. This is a device that translates an address from the private side to an address on the public side. In this way very few of the registered addresses need to be used. Many organizations follow this same model, even when they have enough registered addresses. This technology makes the move to IPv6 less urgent to organizations that already have a significant number of IPv4 addresses registered and have a strategy in place for translation from private addresses to public addresses.IPv6 Transition OptionsOnce an organization has chosen to begin an IPv6 implementation, they must decide how to do the transition. In the same way that NAPT is used to move data between public and private address spaces, there will need to be a transition between IPv4 and IPv6 over time. There will probably be areas of IPv6 and IPv4 co-existing in organizations for years. In order to handle this gradual transition, different technologies and techniques are being developed. These various ways of transitioning are broadly divided between tunneling and translating.Tunneling Methods:•IPv6 IPv4 I P v6. Tunneling IPv6 through IPv4•IPv4 IPv6 I P v4. Tunneling IPv4 through IPv6Translating Methods:•Dual stacks. Each device and host that needs it has both IPv4 and IPv6 stacks. (Though not strictly a translation method, it has been included here.)•IPv4 N AT-PT (NAPT) I P v6. IPv4 to IPv6 network address translation and vice versa. Application Layer Gateways (ALG) will be necessary to support applications that will not work with NAT-P T.IPv6 Only:•I P v6. Complete replacement of IPv4 or only use IPv6 within network with no tunneling or translating to IPv4 environments.•Each of these methods can be used in different areas to accomplish different things. Who Will Transition to IPv6?Now that the methods have been identified, the next question for where IPv6 adoption will take place is: “What organizations will adopt IPv6?” The organizations and groups inwhich IPv6 will be adopted are the following:•U n i v e r s i t i e s•C a r r i e r s•G o v e r n m e n t s•Private enterprise•Home usersIPv6 has been closely followed and helped in its development by universities. This is not all that surprising since these are the same organizations that were the pioneers of the original Internet, and generally do primary academic research. Universities also see the value of an increased number addresses because they tend not to use NAT-PT between their internal network and the Internet. In general, they assign public addresses to all of their devices and make them accessible from the outside world.When universities begin to roll out IPv6, they will create islands of IPv6-capable devices. These will be servers and other devices with early IPv6 communications stacks either built into their operating systems or added to the devices. While these will be some of the first IPv6 implementations, from a network point of view these will be very small islands of disjointed activity. For the most part this has already begun to happen. In most cases these devices will need to be connected via existing networks to other islands of IPv6 devices. In order to accomplish this, routers at the edges of the network need to take the traffic from the IPv6 islands and tunnel it through the exiting IPv4 networks. In a few cases these pockets of activity will be directly connected to each other and will form pure IPv6 networks where no tunneling or translation will be necessary.Many carriers are also anxious to move to IPv6, especially as they move to 3G communi-cations devices. These devices in general are assigned an IPv6 address in order to com-municate. As these devices become more common, IPv6 will become more important forcarriers. Once adoption of IPv6 begins to occur in the carrier’s network, it will become nec-essary for organizations that have not yet adopted IPv6 to continue to link to other net-works. In this case there will be a requirement to deploy routers at the edge that tunnelIPv4 traffic through the IPv6 cloud.Once the carriers have provided an IPv6 infrastructure, universities will be able to connectusing this IPv6 backbone. A specific example of this linked IPv6 community is somethingcalled the 6bone. This is an IPv6 backbone set up to allow testing and collaboration on IPv6.Governments will have two reasons to move to IPv6: They have their own research depart-ments (including the military) that interact with universities, and they are themselves alarge consumer of Internet addresses. IPv6 gives them the capability to use as manyaddresses as they need to meet their needs. Governments will have the ability to use anyof the transition methods outlined above. In all likelihood, they will use several methods,depending on their specific needs in an area. As their adoption of IPv6 grows, they willwant those that they communicate with to also adopt IPv6.Private organizations will follow next. The barriers to private enterprises moving to IPv6 Array are many; cost, complexity and business value are a few. Businesses will move to IPv6when the business case for the implementation is more compelling than the cost of theimplementation. The cost of an IPv6 implementation can be considerable. It involves payingto replace any equipment that is not capable of doing IPv6. So what will drive privateorganizations to move to IPv6? Initially the organizations that deal with governments willbe encouraged to move to the new network. Organizations dealing with government can usethe IPv4-to-IPv6 translation devices. There are various ways to translate between IPv4 andIPv6. The first method involves having two communication stacks on each device: oneIPv4 and one IPv6. When the device (host or router) needs to communicate with anotherdevice, it sends requests on both stacks and sees which one responds. The stack that getsthe response is the one used for future communications. Another translation methodinvolves the use of network address translation and application layer gateways. In thismethod, a device (typically a router) sits at the edge of one of the networks and translatesthe conversation from IPv4 to IPv6. In some cases simply changing the addresses can dothis, and in other instances the application must be translated as well. In either case, thiscan be a complex undertaking and will probably be resisted by organizations because ofthe complexity. Over time however, as more organizations make the change, the remainingorganizations will begin to see the balance tip toward adoption of IPv6, at least at the edgesof their network.It is interesting to note that home users will probably adopt IPv6 as well. Home users willlikely begin to adopt IPv6 earlier than private enterprise. The reason for this is that it ishighly likely that they will purchase consumer electronics or operating systems, whichbegin to use IPv6 as their default. Since most consumers do not bother to change thedefault settings on their devices or software, this will signal the beginning of IPv6 adoptionfor this group. On the other hand, this adoption will likely take the longest to roll out. If aconsumer has an existing network, it will likely be IPv4. Any new equipment put into thisnetwork will likely have the option of supporting IPv4 or IPv6 and will do so for a while.The driver for the home user will be new devices that they want to take advantage of andthat default to IPv6. For current home networks, it will be a long time before home usersreplace their exiting IPv4 equipment with IPv6 equipment. They will demand co-existencebetween both protocols for some time to come.Page 8of 24 • WhitepaperWhere IPv6 is Used in the Network•Universities will create “islands” of IPv6 for testing and evaluation.– IPv6 islands need to communicate to each other.– There are IPv4 networks in between; tunneling IPv6 inside IPv4 needs to be used. •Carriers will deploy IPv6 backbone networks.– Used to connect IPv6 “communication” devices—new cell phones and other devices—no tunneling required.– Expanded to allow organizations to communicate between IPv6 networks on these backbones—no tunneling required.– Eventually allow connection between IPv4 networks through these IPv6 backbones—tunneling IPv4 inside IPv6 needs to be used.•Government/carriers/universities will collaborate to create the initial sparks of an IPv6“Internet.”– This will begin as its own initiative (as did the Internet); eventually this will merge into a commercial IPv6 network.– Government will connect to the IPv6 carrier backbone and actively promote its use. – Organizations interacting with government will be encouraged to move to IPv6 tocommunicate with governments.•Home users will move once devices running IPv6 become the norm in the home.– By this point, many “home” devices will already have IPv6 deployed.–It will become a natural extension of home devices to communicate with each other and “universal” addressing is desired.•Many organizations will move slowly to IPv6 since there are few applications to drive them to IPv6. They will move when:– There is a business driver to move (like dealing with the government).–Implementing IPv6 becomes easier.–IPv6 connection between sites becomes the “norm.”– Complex translation or tunneling issues become easier to handle.IPv6: The TechnologyIntroductionIPv6 is an evolutionary change to the network from a user point of view. The network devices will attach to the LAN, W AN, wired and wireless phone network and just work. To d a y’s IPv4 networks are getting faster, more reliable, more mobile, more secure, and most importantly, more useful. This trend will continue. IPv6 will let it continue; better, fa s t e r, cheaper and importantly, for many more devices, with less burden to the IT departments. The magic of letting the regular user “be dumb” about the details of networking, yet more productive in using the global network, will continue.Behind the scenes of the attached devices will be the technical changes to let the productivity continue to grow. Most network devices will start to support not only the full complement of IPv4 features, but IPv6 features as well. Network attached devices will add IPv6 slowly, waiting for the critical application that forces its use without accepting any degradation of the current supported features of IPv4. As the use of IPv6 begins, the network infrastructure must support the coexistence of both protocols and also provide a smooth migration from one protocol to the other. There will be no “Y2K” day to dread or fear, no final day of switching to IPv6. As new applications and devices demand the newer, better IPv6 capabilities, the infrastructure will be upgraded to support it. In Asia, where the number of available IPv4 addresses is dwindling, governments are already mandating support.Those “islands of IPv6” will need to be “tunneled through” and “translated to” the rest of the Internet community.As IPv6 first rolls out, we are likely to see it just trying to “catch up” with the features, which IPv4 currently supports. Most would agree we’re not even to this stage yet. Most network users understand IPv6 is coming and should be coming, but still think we’re just ramping on the “plateau of production” for IPv4. Network Address Translation (NAT) has allowed everyone in the IT world to grow beyond the limitations of the existing address space. Hardware and NP (network processor) implementations, along with flow-based architectures, have allowed IP packet forwarding to exceed rates only dreamed of as the work on IPv6 began.IPv6 provides a bigger address space. But IPv6 has become much more than just IPv4 with a larger address field. Many of the functions provided by IPv4 will have another newer more efficient version for IPv6 or will be obsolete. Network functions like NAT will be engineered out of existence.Technical Changes from IPv4Address SpaceThe address space is a major step forward and the major driving factor for the technology. Nearly everyone understands that IPv6 has a bigger address. The 128-bit addresses used in IPv6 are four times larger than the 32-bit IPv4 addresses, providing for many billions more usable addresses.Page 1 1of 24 • Whitepaper Header Format Simplification The new fixed-length header (Figure 1) is twice as long as the IPv4 header without options (20 bytes) but that’s actually very good considering we quadrupled the two address fields in it. Addresses account for 32 of the 40 bytes in the header. The other fields contain version,p r i o r i t y, flow label, payload length, and hop limit, all expected and needed parts of the protocol.The only other field is the next header field; this field allows for the optional expansion of the packet to include other headers in a daisy-chained manner to any limit. The good news for implementers is a well-defined structure to the headers and fields and no header checksums.F i g u re 1. IPv6 Header No Hop-by-Hop Segmentation Routing will be simpler, but it forces the end devices to do Path MTU Discovery. Packet AlignmentWhile the usersmay not care much about byte alignments, the engineers look to the details like 64-bit aligned packets to help improve efficiency and ease of implementation.This means faster and cheaper network devices in the long term. Security Security was built in from the start and IPSec is mandated. No Broadcast When would you really want EVERYONE to receive a packet anyway? IPv6 supports good Multicast capability, and we learned long ago that most broadcast techniques are horribly misused and a great source of pain to both the IT and network product engineers. Auto-Configuration Larger address numbers, more users, complex topologies, IPv4 migration, redundant paths,tunneling and translation: These all add up to a level of complexity in a large enterprise.IPv6, however, added features like Neighbor Discovery and local addressing to make IPv6more plug-and-play. Many in the IT community believe that the inherent auto configuration capabilities in IPv6 will make the network easier to operate and manage so that the migration will pay for itself in the long run.。
ipv6关键技术-iFIT逐流检测技术学习

IFIT随流测量技术详细白皮书IFIT(In-situ Flow Information Telemetry)是一种基于真实业务流的随流测量技术。
基于随流检测原理,IFIT提供真实业务流的端到端及逐跳SLA(丢包、流量、时延、抖动等)测量能力,可快速感知网络性能相关故障,并进行精准定界、排障。
相比传统检测技术如TW AMP、Y.1731等,IFIT在组网灵活性、SLA精准性、故障快速定界能力上具备更大优势,是未来5G移动承载网络运维的重要手段。
1.概述性能检测技术概述网络性能检测技术是互联网领域和电信领域的共同研究热点。
各种性能检测技术通过监控、测量、采集网络性能数据,对网络运行状态进行分析、评价、控制、调整,以提供长期稳定、可靠的网络服务,是网络运行的基础。
根据检测方式不同,检测技术可分为如下三大类(RFC 7799):主动检测:通过构造检测报文方式,对检测报文进行时延、丢包等SLA测量,间接获得网络质量。
如RFC 2544、TW AMP/OW AMP、Y.1564等均为主动检测技术。
由于测量的不是真实业务流量,主动检测的准确度与实际网络存在一定偏差。
被动测量:指直接对实际业务流进行测量的检测技术,如思科主导的in-situ OAM、Barefoot主导的INT、我司主导的IPFPM等技术。
被动测量基于实际业务流,测量精度高。
混合测量:介于主动测量与被动测量之间,通过构造少量辅助检测报文,对实际业务流进行SLA测量,例如Y.1731(CFM LM)、MPLS-TP OAM(LM)、RFC 6374等。
由于部分检测是基于实际业务流,其测量精度也较高。
以上检测技术各有优缺点,应用场景也各自不同:TWAMP主要用于端到端IP业务流级检测,但由于是测量构造的检测报文,检测精度较低,且无逐跳检测能力。
RFC 2544、Y.1564通常用于测量设备、网络的SLA能力,与实际业务流的SLA也存在一定差距。
Y.1731(CFM)仅用于L2业务,无法适用三层业务的检测;MPLS-TP OAM、RFC 6374仅支持MPLS管道级测试,且不支持乱序、负载分担、点到多点场景,如LAG、ECMP、双归等,同时也不支持逐跳测量。
IS-IS for IPv6技术白皮书
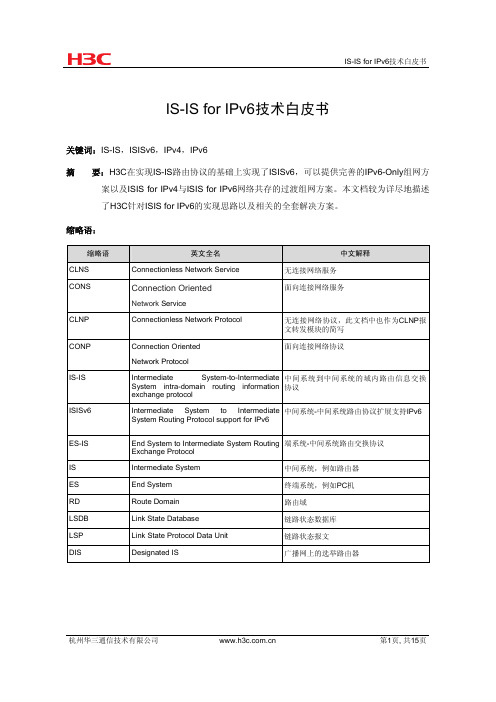
IS-IS for IPv6技术白皮书关键词:IS-IS ,ISISv6,IPv4,IPv6摘 要:H3C 在实现IS-IS 路由协议的基础上实现了ISISv6,可以提供完善的IPv6-Only 组网方案以及ISIS for IPv4与ISIS for IPv6网络共存的过渡组网方案。
本文档较为详尽地描述了H3C 针对ISIS for IPv6的实现思路以及相关的全套解决方案。
缩略语: 缩略语英文全名 中文解释 CLNSConnectionless Network Service 无连接网络服务 CONS Connection OrientedNetwork Service面向连接网络服务 CLNP Connectionless Network Protocol 无连接网络协议,此文档中也作为CLNP 报文转发模块的简写CONP Connection OrientedNetwork Protocol面向连接网络协议 IS-IS Intermediate System-to-Intermediate System intra-domain routing information exchange protocol中间系统到中间系统的域内路由信息交换协议 ISISv6 Intermediate System to Intermediate System Routing Protocol support for IPv6 中间系统-中间系统路由协议扩展支持IPv6ES-IS End System to Intermediate System Routing Exchange Protocol端系统-中间系统路由交换协议IS Intermediate System 中间系统,例如路由器ES End System 终端系统,例如PC 机RD Route Domain 路由域LSDB Link State Database 链路状态数据库LSP Link State Protocol Data Unit 链路状态报文DIS Designated IS广播网上的选举路由器目录1 概述 (3)1.1 技术应用背景 (3)1.2 技术优点 (3)2 特性介绍 (4)2.1 相关术语 (4)2.2 相关协议 (4)2.3 协议处理机制 (4)2.3.1 IS-IS工作机制概述 (4)2.3.2 ISISv6用到的TLV (6)2.3.3 ISISv6邻接关系 (8)2.3.4 LSP的维护 (9)2.3.5 路由计算 (10)3 典型组网案例 (10)3.1 IPv6-Only网络IS-IS典型组网举例 (10)3.2 IPv4/IPv6典型组网举例 (11)3.3 IPv6 ISIS实现IPv4/IPv6网络共存组网解决方案 (12)3.4 IS-IS for IPv6应用组网注意事项 (13)4 支持ISIS for IPv6技术的产品 (14)5 总结和展望 (14)6 参考文献 (14)1 概述对本文档介绍的技术进行概括性的描述,包括该技术的产生背景、技术优点等。
IPv6技术白皮书

IPv6技术白皮书摘要:随着Internet的发展,IPv4的局限越来越暴露出来,严重制约了IP技术的应用和未来网络的发展;IPv6作为下一代网络的基础以其鲜明的技术优势得到广泛的认可;本文从技术层面分析了IPv6的特点优势,同时就IPv4网络向IPv6网络部署的阶段,过渡技术以及方案做一个基本的介绍,并对IPv6的未来进行了展望关键字:IPv6、自动配置、扩展头、Mobile IPv6、过渡技术、双栈、隧道、6to4 、NAT-PT1.IPv4需要升级吗?计算机技术和通信技术的发展与融合使得Internet应用及规模飞速发展,其中Internet 中的核心技术IPv4功不可抹,IPv4技术以它的简结有效取得了巨大的成功,但IPv4协议是1973年制定的,它的早期设计者完全没有预料到IP网络会达到今天的发展速度和规模,到90 年代IPv4的缺陷和潜伏的危机逐渐暴露出来。
其中最大的问题是IP地址资源的紧缺。
据统计IPv4地址到96年已有80%的A类网络地址,50%的B类地址,10%的C类地址被分配,有专家估计到2010年左右IPv4地址可能面临耗尽的危险。
有人形象的把这个问题称为“网络泰坦尼克危机“。
IP地址被看作网络设备节点在互联网上的“身份号”,随着移动和宽带技术发展,IP地址需求将更大。
大量移动终端的IP接入需要更多IP地址,例如手机,PDA,甚至每个IC卡拥有一个IP地址。
目前宽带技术正在蓬勃发展,由于宽带业务模式与窄带业务模式不同,一般以对称和实时方式工作,要求用户时时在线,IP地址需求更大,如家电上网,IPCar等。
为了缓解IPv4地址的紧张,也出现了一些IPv4的补丁技术,如CIDR,NAT技术,混合地址等技术,但这些技术治标不治本。
以NAT技术为例,使用私有地址虽然可以缓解地址紧缺,但存在效率和应用层网关问题,而且NAT打破端到端的模式,限制了新应用的发展。
由于IP网络本身的特点,IP地址紧缺问题不像电话号码升位一样简单。
IPV6白皮书

IPv6技术介绍第一章引言 (3)第二章 IPv6基础知识 (5)2.1 IPv6 地址 (5)2.1.1 IPv6 地址结构定义 (5)2.1.2 IPv6 地址分类 (6)2.2 IPv6 报文格式 (9)2.2.1 IPv6 报文基本头格式 (10)2.2.2 IPv6 报文扩展头格式 (11)2.3 IPv6基本技术 (13)2.3.1 IPv6 邻居发现协议 (13)2.3.1.1 邻居发现 (13)2.3.1.2 路由器发现 (15)2.3.1.3 IPv6无状态地址自动配置 (16)2.3.1.4 重定向 (18)2.3.2 IPv6 路径MTU发现协议 (18)2.3.3动态主机配置协议(DHCPv6) (18)2.3.3.1 DHCPv6 概述 (18)2.3.3.2 DHCPv6地址/前缀分配过程 (19)2.3.3.3地址/前缀租约更新过程 (20)2.3.3.4 DHCPv6 无状态配置过程 (21)2.3.4 IPv6域名解析 (22)第三章 IPv6路由技术 (24)3.1 RIPng (24)3.2 OSPFv3 (24)3.3 IS-ISv6 (25)3.4 BGP4+ (26)第四章 IPv6 过渡技术 (27)4.1 IPv6/IPv4 双协议栈 (27)4.2 隧道技术 (28)4.3 IPv6与IPv4互通技术 (30)4.4 过渡技术比较 (33)第五章 IPv6 部署规划 (34)5.1 IPv6 地址规划 (34)5.2 IPv6路由规划 (34)5.2.1 域内路由协议 (35)5.2.2 域间路由协议 (35)5.3 网络管理 (36)第六章IPv6在中国 (37)第七章IP地址分配状况 (39)第八章IPv6网络新应用展望 (41)第一章引言目前IANA的IPv4地址已经全部分配完毕,亚太区(APNIC)的正常可分配的IPv4地址也于2011年4月宣告耗尽。
IPv6解决方案ND防攻击技术白皮书

IPv6解决方案ND防攻击技术白皮书关键词:ND,ARP,ND攻击,ARP攻击,交换机,IPV6摘 要:本文介绍了在IPv6网络中的ND攻击及防攻击的技术思路以及H3C公司的ND防攻击方案部署的典型方案以及技术特点。
缩略语清单:缩略语英文全名中文解释NDP Neighbor Discover邻居发现协议ProtocolARP Address Resolution地址解析协议ProtocolIPv6Internet Protocol因特网协议第六版Version 61ND攻击概述邻居发现协议(Neighbor Discovery Protocol,以下称ND协议)是IPv6的一个关键协议,可以说,ND协议是IPv4某些协议在IPv6中综合起来的升级和改进,如ARP、ICMP路由器发现和ICMP重定向等协议。
当然,作为IPv6的基础性协议,ND还提供了其他功能,如前缀发现、邻居不可达检测、重复地址检测、地址自动配置等。
在IPv4网络中,ARP攻击问题已经为广大的网络管理者,设备厂商所认识,ARP攻击能够造成大面积网络不能正常访问外网,使得正常用户深受其害。
针对ARP攻击,大部分的网络设备厂商都推出了自己的ARP防攻击解决方案,在很大程度上解决了ARP攻击的问题。
而伴随着IPv6网络的建设,在IPv6协议族中的NDP协议越来越被重视,而在ND协议的设计与ARP协议一样并未提供认证机制,导致网络中的主机是不可信的,从而使得针对ND协议的攻击非常容易。
2ND协议介绍2.1ND报文类型ND协议定义的报文使用ICMP承载,其类型包括:路由器请求报文、路由器通告报文、邻居请求报文、邻居通告报文和重定向报文。
由于ND报文中的可选字段及代码类型较多,下面描述的ND报文中的各个字段并不完全,主要描述了涉及到ND防攻击技术的选项。
2.1.1路由器请求报文RS Router Solicitation Message主机启动后,通过RS消息向路由器发出请求,期望路由器立即发送RA消息响应。
(完整版)锐捷IPv6-过渡技术白皮书

Manually Configured Tunnel
手动配置隧道
LDP
Lable Distribution Protocol
标签分发协议
BGP
Border Gateway Protocol
边界网关协议
GRE
Generic Routing Encapsulation
通用路由封装
ISATAP
Intra-Site Automatic Tunnel Addressing Protocol
图2.1 IPv4/IPv6双协议栈结构
双协议栈的工作机制大致过程如下:
1.链路层解析出接收到的数据包的数据段,拆开并检查报头。
2.如果IP包的版本号是4,该包就由IPv4的协议栈来处理;如果版本是6,则由IPv6的协议栈处理。
IPv4/IPv6双协议栈的工作过程如图2.2所示。
图2.2支持IPv4和IPv6的双协议栈应用
站点内自动隧道寻址协议
NAT-PT
Network Address Translation – Protocol Translation
网络地址转换-协议转换
6PE
IPv6 Provider Edge Router
IPv6运营商边缘路由器
OSPF
Open Shortest Path First
开放最短路径优先
EoMPLS
Ethernet-over-MPLS
MPLS之上的以太网
VPLS
Virtual Private LAN Service
虚拟专用LAN服务
NBMA
NonBroadcastMultiaccess
非广播多路访问网络
DSTM
IPV6技术白皮书

IPV6技术白皮书摘要Ipv6是Internet在网络层之上的一个新的标准协议族。
Ipv6是未来的网络互联协议,它的设计目的在于解决现有IPV4版本所具有的各种问题,包括地址的数量限制、安全性、自动配置、可扩展性以及其它许多问题。
它的使用将扩展Internet的功能,为许多有价值的应用构想提供进一步的支持,其中包括点对点应用和移动应用。
本文的目的就是在技术层面上分析IPV6的特点和优势,同时结合目前网络状况对IPV6的部署以及相关的过渡技术进行介绍。
关键字:IPV6、扩展头、自动配置、邻机发现、路径MTU发现、移动IPV6、过渡技术、双栈、DSTM、NAT-PT、DNS、TELNET6、ALG(应用层网关)、手工隧道、半手工隧道GRE、隧道代理(Tunnel Broker)、自动6To4隧道、ISATAP、6PE、RIPng、OSPFv3、IS_ISv6、BGP4+、SNMP。
回顾Ipv4,展望IPV6大量增加的上网设备使得互联网的规模不断扩大,基于32位地址的IPv4协议逐渐显得力不从心。
尽管出现了诸如NAT,CIDR以及混合地址等技术,在一定程度上缓解了IPV4地址短缺的压力,但是同时也带来了许多负面作用(如破坏了网络层的端到端构架等)。
相对于IPv4,新的IPv6协议的显著特点就是地址充足,报头简单,易于扩展,层次区划,实现安全,组播完善,QOS有保证,即插即用,移动便捷。
这些特点主要来自于128位的地址;简化了固定报头,取消了IP头校验和域,IPv6对报文进行必要的分片完全依靠报文的发送方进行,并在接收端进行重组,取消了路由器对报文的分片功能,提高了IPv6路由器的转发效率并且提高了处理效率;取消了原先IPV4报头中的选项域而取代为灵活的扩展报头,使得协议易于扩展;地址结构有层次性,利于路由的快速查找并且便于路由聚合,有效缩减IPV6路由表的尺寸;将IPSec作为IPV6的标准扩展头实现,在网络层实现IPSec 的加密与认证,实现端到端的安全;支持IP地址的无状态自动配置和重配置,实现IP地址的自动更新,易于管理;在IPV6报头中增加Flow Label域,增强了IP Qos的特性;IPv6使用了更多的组播地址,同时对组播域进行了划分,取消了IPv4当中的广播,可以更加有效地利用网络带宽,避免广播风暴;Mobile Ipv6更好的解决了IP的移动性,相比Mobile Ipv4有较大改进。
IPv6 Proxy技术白皮书

IPv6 Proxy技术白皮书神州数码网络有限公司修改记录目录1.概述 (1)2.缩写和术语 (1)3.技术介绍 (1)3.1IP V6卡类型 (1)3.2应用环境 (2)3.3P ROXY配置 (2)3.4报文处理 (2)3.4.1二层IPv6报文 (2)3.4.2三层IPv6报文 (2)3.4.3IPv6协议报文 (3)3.5应用缺陷与规避方法 (4)3.5.1应用缺陷 (4)3.5.2规避方法 (4)4.典型应用指南 (4)4.1应用一 (4)4.2应用二 (5)5.参考资料 (6)1. 概述IPv6 Proxy指IPv6代理功能,用于分布式机架交换机,如7604和7608机架交换机。
IPv6 Proxy功能指在机架交换机中,仅支持IPv4硬件功能的线卡通过IPv6线卡的代理功能,实现IPv6的硬件转发。
IPv6 Proxy功能在实际应用中非常重要。
首先,早期的板卡仅支持IPv4硬件功能,不能转发IPv6报文,但机架交换机可以插入不同类型的板卡,可能出现一些板卡能转发IPv6报文,而一些板卡不能转发IPv6报文,引起不一致的问题;其次,支持IPv6硬件转发的板卡成本较高。
IPv6 Proxy功能很好的解决上面两个问题:第一,仅支持IPv4的板卡通过IPv6卡的IPv6 Proxy功能,也能实现IPv6的硬件功能,保持机架交换机的整体一致性;第二,机架交换机中只要插入一块IPv6卡,整个机架交换机既能支持IPv4硬件功能,也支持IPv6硬件功能,从而节约成本。
本文档将IPv6 Proxy功能主要特性和技术介绍合为一节,参看第3节。
本文档将介绍IPv6 Proxy功能的相关技术,适合网络公司售前技术工程师及相关人员。
2. 缩写和术语IPv6卡:支持IPv4和IPv6硬件功能的卡,又称为双栈卡。
IPv4卡:仅支持IPv4硬件功能的卡。
IPv6 Proxy功能:IPv6代理功能,指IPv4卡通过IPv6卡的代理实现IPv6硬件转发功能。
IPv6解决方案可控组播技术白皮书(2021)

IPv6解决方案可控组播技术白皮书(2021)IPv6解决方案可控组播技术白皮书关键词:组播,可控组播,IPV6摘要:IP组播技术的出现使得对特定数据的分发能够大大的节约带宽。
但使用组播技术的同时,如何进行有效的安全控制也是目前组播技术研究的一个方向。
本文描述了在IPv6环境下的一种可控组播的技术及其部署方案。
缩略语清单:缩略语 PIM PIM DM PIM SM MLD MLD Snooping 英文全名 Protocol Independent Multicast Protocol Independent Multicast Dense Mode Protocol Independent Multicast Sparse Mode Multicast Listener Discovery Multicast Listener Discovery Snooping 中文解释协议无关组播协议无关组播―密集模式协议无关组播―稀疏模式组播侦听者发现协议组播侦听者发现协议窥探Copyright ? 2021 杭州华三通信技术有限公司第1页, 共15页IPv6解决方案可控组播技术白皮书公开目录1 2组播技术概述 ........................................................................... ........................................ 3 IPv6组播技术介绍 ........................................................................... ................................ 3 2.1 2.2 2.3 2.4 2.5 3IPv6组播地址 ........................................................................... ............................ 3 IPv6组播MAC地址 ........................................................................... ................... 4 组播组管理协议 ........................................................................... ........................ 5 MLD Snooping技术............................................................................ .................. 8 组播路由协议与组播转发 ........................................................................... (11)H3C可控组播技术 ........................................................................... .............................. 12 3.1 3.2 3.3 3.4组播源控制 ........................................................................... .............................. 12 组播接收者控制 ........................................................................... ...................... 13 用户组播权限部署及计费 ........................................................................... ...... 14 典型应用场景 ........................................................................... .. (15)4 总结 ........................................................................... (15)2021-5-7第2页, 共15页IPv6解决方案可控组播技术白皮书公开1 组播技术概述组播是指在IP网络中将数据包以尽力传送的形式发送到某个确定的节点集合(即组播组),其基本思想是:源主机(即组播源)只发送一份数据,其目的地址为组播组地址;组播组中的所有接收者都可收到同样的数据拷贝,并且只有组播组内的主机可以接收该数据,而其它主机则不能收到。
《中国IPv6发展状况》白皮书().doc

《中国IPv6发展状况》白皮书()中国中国IPv6发展发展状况状况推进IPv6规模部署专家委员会7月前言11月,中共中央办公厅、国务院办公厅印发了《推进互联网协议第六版(IPv6)规模部署行动计划》(以下简称《行动计划》),明确提出了未来五到十年我国基于IPv6的下一代互联网发展的总体目标、路线图、时间表和重点任务,是加快推进我国IPv6规模部署、促进互联网演进升级和健康创新发展的行动指南。
《行动计划》发布以来,政府部门、中央企业、基础电信企业、互联网企业、通信设备制造企业、科研机构等积极响应,纷纷制定具体的落地实施方案和工作计划,加快IPv6升级改造,我国IPv6规模部署工作呈现加速发展态势。
为及时、准确、全面地掌握我国IPv6发展情况,按照《行动计划》中“全面监测和深入分析互联网网络、应用、终端、用户、流量等IPv6发展情况”和“定期开展企业、行业、区域应用情况评测”的具体要求,推进IPv6规模部署专家委员会组织相关各方,研究制定了我国IPv6发展情况的监测指标和监测方法,初步构建了国家IPv6发展监测平台。
经过8个多月的试行监测和统计,逐步完善并形成了比较成熟的IPv6发展监测体系和监测报告。
本白皮书主要从用户数、流量、基础资源、云端、网络、终端、应用等7个维度对我国IPv6发展情况进行综合分析,力求全面、准确反映我国IPv6发展状况,为持续有效推进IPv6规模部署工作提供必要的信息支撑。
本白皮书在调查研究、数据采集、统计分析、编制发布过程中,得到了中央网络安全和信息化委员会办公室、工业和信息化部等部门的大力指导,得到了产学研用各方的大力支持,在此对给予指导和支持的部门及相关各方表示衷心的感谢!推进IPv6规模部署专家委员会7月目录摘摘要要1第一章第一章IPv6用户数用户数.3第二章第二章IPv6流量流量.6第三章第三章IPv6基础资源基础资源.7第四章第四章云端就绪度云端就绪度9第五章第五章网络就绪度网络就绪度.11第六章第六章终端就绪度终端就绪度13第七章第七章应用可用度应用可用度16附附录录IPv6监测指标体系监测指标体系.191摘要《行动计划》发布以来,我国IPv6规模部署工作呈现加速发展态势,取得了积极进展。
IPv6邻居发现攻击防护解决方案技术白皮书

Hillstone IPv6邻居发现攻击防护解决方案技术白皮书关键词:IPv6,邻居发现(ND),安全网关,NS/NA,RS/RA摘要:本文介绍了IPv6邻居发现协议的基本原理、攻击种类、Hillstone安全网关防护方法,以及典型实际环境中的应用。
缩略语:1.IPv6邻居发现协议简介IPv6的邻节点发现(ND)协议,是用一系列的报文和步骤来确定邻节点之间关系的过程。
ND取代了IPv4中使用的ARP、ICMP路由器发现和ICMP重定向报文。
●ND协议定义功能:●ND协议报文格式:邻节点发现报文使用ICMPv6的报文格式,及ICMPv6的从133到137的报文类型。
●ND协议报文类型:2.IPv6邻居发现攻击介绍在IPv4网络中,ARP攻击问题已经为广大的网络管理者、设备厂商所认识,ARP攻击能够造成大面积网络不能正常访问外网,使得正常用户深受其害。
针对ARP攻击,大部分的网络设备厂商都推出了自己的ARP攻击解决方案,在很大程度上解决了ARP攻击的问题。
而伴随着IPv6网络的建设,在IPv6协议族中的ND协议越来越被重视,而ND协议在设计上与ARP协议一样并未提供认证机制,导致网络中的主机是不可信的,从而使得针对ND协议的攻击非常容易。
ND攻击类型总结如下:●地址欺骗攻击攻击者利用NS/NA/RA报文来修改受害主机或网关上的MAC地址,造成受害主机无法与网络进行正常的通信,甚至形成中间人攻击。
●路由通告欺骗攻击RA报文能够携带很多网络配置信息,包括默认路由器,网络前缀列表,是否进行有状态地址分配等网络配置的关键信息。
如果受害者接收了虚假的RA信息,会造成网络配置错误,从而引发欺骗攻击。
●针对网关的泛洪攻击通过发送大量的NS/RS报文,造成网关的ND表项溢出。
3.Hillstone IPv6邻居发现攻击防护方法通过对上文ND攻击类型的介绍,我们可以看出发现当前ND攻击防御的关键所在:如何获取到合法用户和网关的IPv6地址和MAC地址的对应关系,并如何利用该对应关系对ND报文进行检查,过滤掉非法ND报文。
IPv6组播技术白皮书
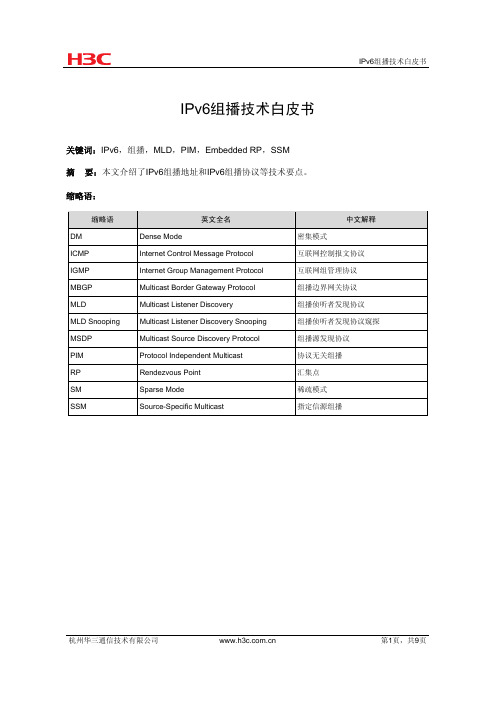
IPv6组播技术白皮书关键词:IPv6,组播,MLD,PIM,Embedded RP,SSM摘要:本文介绍了IPv6组播地址和IPv6组播协议等技术要点。
缩略语:缩略语英文全名中文解释DM DenseMode 密集模式ICMP Internet Control Message Protocol 互联网控制报文协议IGMP Internet Group Management Protocol 互联网组管理协议MBGP Multicast Border Gateway Protocol 组播边界网关协议MLD Multicast Listener Discovery 组播侦听者发现协议MLD Snooping Multicast Listener Discovery Snooping 组播侦听者发现协议窥探MSDP Multicast Source Discovery Protocol 组播源发现协议PIM Protocol Independent Multicast 协议无关组播Point 汇集点RP RendezvousSM SparseMode 稀疏模式Multicast 指定信源组播SSM Source-Specific目录1 概述 (3)2 IPv6组播技术实现 (3)2.1 IPv6组播地址 (3)2.1.1 IPv6组播地址格式 (3)2.1.2 永久分配的IPv6组播地址 (4)2.1.3 基于单播前缀的IPv6组播地址 (5)2.1.4 内嵌RP地址的IPv6组播地址 (6)2.1.5 IPv6 SSM组播地址 (7)2.1.6 IPv6组播MAC地址 (7)2.2 IPv6组播协议 (8)2.2.1 组播组管理协议 (8)2.2.2 组播路由协议 (8)3 参考文献 (9)1 概述作为IPv4协议的替代,IPv6协议使用128位的地址结构解决了IP地址不足的问题,同时对一些特性进行了优化处理。
H3C公司IPV6网络WLAN接入服务技术白皮书 v2.00
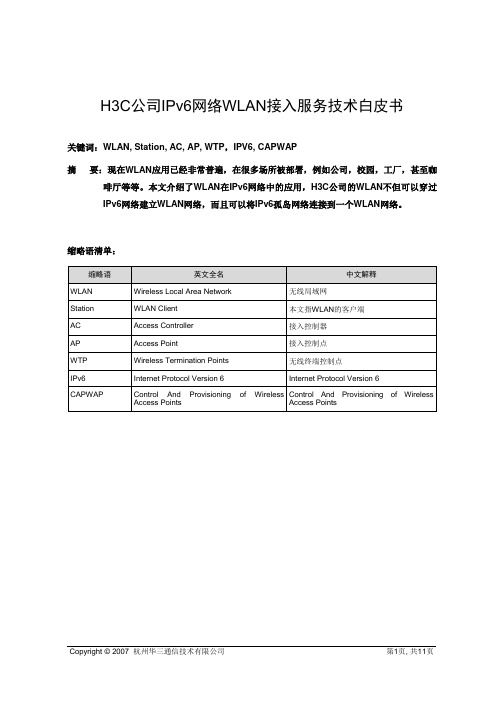
H3C公司IPv6网络WLAN接入服务技术白皮书关键词:WLAN, Station, AC, AP, WTP,IPV6, CAPWAP摘要:现在WLAN应用已经非常普遍,在很多场所被部署,例如公司,校园,工厂,甚至咖啡厅等等。
本文介绍了WLAN在IPv6网络中的应用,H3C公司的WLAN不但可以穿过IPv6网络建立WLAN网络,而且可以将IPv6孤岛网络连接到一个WLAN网络。
缩略语清单:目录1 概述 (3)2 技术应用背景 (3)3 特性介绍 (5)4 H3C公司集中管理WLAN实现的技术特色 (6)5 典型组网案例 (7)6 支持组建IPv6 WLAN网络技术的产品(或单板) (10)7 总结和展望 (10)8 参考文献 (11)9 附录 (11)1 概述WLAN,全称Wireless Local Area Network,即无线局域网,和传统的有线接入方式相比无线局域网让网络使用更自由:1. 无线局域网彻底摆脱了线缆和端口位置的束缚,用户不在为四处寻找有线端口和网线而苦恼,接入网络如喝咖啡般轻松和惬意。
2. 无线局域网具有便于携带,易于移动的优点,无论是在办公大楼、机场候机大厅、酒店,用户都可以随时随地自由接入网络办公、娱乐。
另外,WLAN最大的优势就是免去或减少了繁杂的网络布线,一般只要在安放一个或多个接入点(Access Point)设备就可建立覆盖整个建筑或地区的局域网络。
另外对于地铁、公路交通监控等难于布线的场所,无线局域网的应用越来越广泛。
和有线相比,无线局域网的启动和实施相对简单,后期维护容易,整个建网和维护的成本更低廉。
随着以IPv4为核心技术的Internet获得巨大成功,促使IP技术广泛应用,从而产生对IP地址的巨大需求,但IPv4地址资源紧张直接限制了IP技术应用的进一步发展。
IETF在20世纪90年代提出下一代互联网协议-IPv6被公认的IPv4未来的升级版本。
IPv6将地址长度由32为增加到128位,从本质上改进了地址资源紧缺问题――几乎达到了无限的地址空间。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
IPv6应用和过渡1 如何推动IPv6实用化?市场、成本与政策是推动IPv6实用化的关键。
市场需求驱动IPv6IPv6从趋势变成现实,在技术上得以保障的前提下,业务和市场是真正使IPv6得以广泛应用的条件。
未来的电信网将是基于IP技术的网络,电信级的IP网和GPRS、3G移动上网成为了公认的两个“杀手”性应用,推动了IPv6的发展。
降低门槛启动IPv6IPv6虽然是发展趋势,也比较成熟,但仍存在一些需要解决的问题。
逐步将IPv4向IPv6迁移,是业界的共识。
目前数量巨大的IPv4协议网络中的设备和装置仍然需要得到IPv6的支持。
因此,在IPv4环境下,降低IPv6的启动门槛,成为铺开IPv6的重要条件。
降低门槛的一个办法是提供硬件支持IPv6的产品,以节省用于升级的成本。
降低门槛的另一个办法是通过软件升级的方法,可以用在一些要求不太高的环境。
政策规划推动IPv6IPv6推动最快的是日本。
日本采取了模型证实实验,由地方政府、企业用户、家庭用户组成一个模型地区,进行从IPv4方式过渡到IPv6方式的试验,来制定合适的过渡模型。
为了促进IPv6产业发展,日本制定了一系列的优惠、低利息、无利息贷款等各种支持。
目前,日本已经形成了IPv6运营商、IPv6设备提供商、IPv6终端提供商、IPv6用户这样一个完整的产业链,使得日本的IPv6走在了世界的前面。
除了日本,还有与我们紧邻的韩国政府也采取了有力的推动措施。
同样积极的还有欧洲国家。
我国的IPv6发展已经得到了政府的高度重视。
中国应尽快制定IPv6的发展措施,制定推动IPv6的时间表,以有利于国内信息通信业的发展。
2 现有网络转换为IPv6网络存在哪些困难?从IPv4过渡到IPv6并不是一件容易的事情,因为从IPv4升级到IPv6涉及到很多技术问题和商业问题,甚至还有政治问题。
最明显的当然是技术更换的策略,以及基础设施的升级和建设。
IPv4的可靠性和普遍应用是IPv6发展中主要的减速因素。
具体来说,现有网络向IPv6网络的转化存在下述几个方面的困难:(1) 现有的IPv4网络运行十分稳定,设备制造商(包括芯片设计与生产商)、网络运营商、网络连接提供商等正从IPv4上获得稳定的收益,在目前他们还不想转到IPv6上,因为那意味着淘汰现有设施,构建新的通信网络,新的IPv6网络的成本需要相当长的时间才能收回;(2) 网络管理员惧怕任何需要对大量基础设施进行升级的操作。
浏览器、IP电话、网络游戏、Web商业应用等每一个使用IPv6网络的应用都必须进行修改;(3) 人们在IPv4基础设施及应用开发上的投资十分巨大,由于IPv6与IPv4的不同,现有网络仅靠简单的软件升级是无法很好的支持通信服务性能的,要想提升IPv6网络性能,必须在芯片一级上按IPv6的特性进行设计才行,这是一项相当大的开销,因此人们在还能容忍现有IPv4网络的情况下,不会轻易进行IPv6改造;(3) 当前人们开发网络应用时都还基于IPv4网络,因此IPv6网络提供给用户的应用还十分少。
只要现有的IPv4网络还能够十分经济的解决人们各个方面的应用需求,IPv6就无法得到长足的发展和大面积推广。
数据业务是驱动IPv6技术实现的一个最重要的动力源。
如果没有足够的需求必须要采用独立的合法IP地址,那么运营商也就不会热衷于升级设备或扩建基础设施;(4) 操作系统对IPv6的支持还不充分。
目前作为终端用户最常用的操作系统之一的Windows不能提供对IPv6的完全支持,使得设备开发商无法及时推出支持IPv6的应用设备,特别是IPv6终端设备。
这使得用户也无法很好的熟悉并使用IPv6网络;(5) 缺乏IPv6的网管和安全产品。
在IPv6中,原则上所有的终端都拥有全局IP地址。
因此,存在着能够从Internet访问内部网中所有终端的危险性,安全成为IPv6连接的最大问题。
目前,适配IPv6的防火墙产品的开发还很落后,可以说导入IPv6的时间受到IPv6防火墙产品性能的限制;美国政府和IETF似乎也未做好向IPv6过渡的准备。
由于美国长期在信息技术领域处于国际领先地位,且拥有大量地址,因此不急于向IPv6过渡。
但是随着手持设备的大量使用,在两三年内,美国乃至全球都会感到IP地址的缺乏。
IETF当然是IPv6技术获得推进的关键性组织,但它的思路似乎是等到技术细节完全确定后,才在全球范围内推广使用IPv6。
但我国以及亚太的一些国家,如韩国、日本等,已经不可能再等待了。
对中国而言,电信业和网络市场其实是全球新技术和新设备的温床,IPv6应当在这里获得第一推动性的发展。
3 当前IPv6试验网上的典型应用有那些?目前,国际上进行的IPv6实验主要集中在以下几个关键技术上:(1) IPv6基本功能的实现:地址和路由机制、ICMPv6、主机自动配置、各种平台的IPv6代码和应用程序接口(API)已经实现,Cisco和Bay已经制造出支持IPv6的路由器,主要应用向支持IPv6的升级也正在进行;(2) 从IPv4向IPv6过渡的技术:IPv6和IPv4必然有一段较长的共存时间,在此期间,IPv4和IPv6的互通主要采用以下技术:双协议栈,隧道(Tunnel)及隧道代理(Tunnel Broker),NAT-PT,无状态IPv4-IPv6翻译(Stateless IPv4-IPv6 Translator,SIIT),其中隧道技术和双协议栈技术已经得到广泛的使用;(3) IPv6的安全性:不少研究开发项目是将IPv6同IPSec(IP Security)结合起来的,典型的,如KAME和NRL开发的IPv6协议栈,都包含IPSec的代码;(4) IPv6对服务质量(Quality of Service,QoS)的支持:包括对“综合服务”(InteServ)特别是“区分服务”(DiffServ)的支持;(5) IPv6支持移动性的能力:这一方面的研究同IPv4移动性的研究并列进行。
然而,初步的研究和实践倾向于选择IPv6作为支撑移动计算的平台;移动性的实现同安全、服务质量等方面的技术密切相关。
4 未来的IPv6网络上可能会出现什么应用?IPv6通过自动识别机能、无限多的地址、网络安全设置,能对每个终端(包括无线终端)、每个家电、每个生产流程、每个感应器,都进行IP全球化管理。
可以说,在以IPv6为核心技术的下一代网络上,可以实现现有IPv4网络所提供的全部通信业务。
更重要的是,IPv6所提供的巨大的地址空间以及所具有的诸多优势和功能,使其提供语音、数据、视频融合的高品质、多样化通信服务的下一代网络的实现成为可能。
那时,从移动终端、汽车到自动售货机、报警系统、照相机乃至钥匙环和其他各种各样的产品都可以实时在线,一个个信息孤岛最终将连成强大的网络,人们也将在以下三方面获得全新的通信服务体验:端到端实时通信端到端实时通信是通信业务的基本特征,同时也是下一代网络的本质特征和发展方向。
将来,所有的电信服务和信息服务都会使用下一代网络。
下一代网络将逐渐取代电路交换网络和构成现有互联网的IP网,除了提供原来在这些网上提供的服务之外,运营商还将利用下一代网络的多业务能力,提供新的服务,创造新的收入增长点。
这类通信服务主要包括应用服务提供与综合话音和数据业务,其中应用服务提供主要有应用软件的递送和支持、电子商务服务两种;综合话音和数据业务是指下一代网络具有把话音和数据综合在一起的能力,包括web使能的呼叫中心、统一消息和多媒体会议。
移动互联IPv6与移动通信的结合将为目前的互联网开拓一个全新的领域——移动互联网,无线将成为IPv6的第一个“杀手级”应用。
移动互联网上有许多新型而精彩的服务,IPv6将是实现这些服务的关键。
通过移动互联网,人们能够随时随地以在线方式选购商品或服务并为之付款;也可以使用移动设备查询飞机的航班、风景点的简要情况,查找地图以及要参观的地方;人们还能够找到距离最近的餐馆;如果是平时驾车外出,安装在汽车里的无线设施将提供实时定位技术,同时也起到导航和安全保护的作用。
此外,在不远的未来,家电厂商们将开发出新一代的信息家电,除了计算机之外,还可给电视机、冰箱、微波炉、空调、洗衣机等家用电器分配IP地址,以利于它们与Internet的连接。
当信息家电与Internet连接后,人们不在家也可以操作家中的空调、冰箱等。
宽带网络实行IPv6协议可以从根本上优化路由器传输效率,使得目前的各种宽带传输技术迈上一个新的台阶。
到那时,困扰中国网民很久的网络速度问题将得到彻底解决,人们可以舒舒服服地呆在家里,享受超高速网络所带来的欢乐。
信息家电连上光纤后,更可直接以交互方式收看电影、听音乐和广播。
股民即使在家中,也能通过光纤网络和证券公司等金融机构的业务员在电视上交谈,同时进行交易。
应用是没有止境的。
在以IPv6为核心的下一代网络的服务平台上开发多种多样的应用,可以带来更多的商机、更大的市场,许多今天还无法想象的服务将带给人们更大的灵活性,更多的方便和自由。
5 IPv6带来的新的应用与服务有什么特征?在市场需求的牵引下,IPv6的优势将在具体应用中得到越来越突出的显现。
IPv6所带来的创新应用与服务将具有如下特征:·需要大量公有地址,如信息家电、移动终端、工业传感器、自动售货机、汽车等对地址的需求;·对服务质量和安全高度敏感的端到端实时语音及视频应用;·无处不在(Ubiquitous)的信息与通信服务方式。
