System Center Data Protection Manager2007还原操作实例(下) V1.0
Microsoft System Center Configuration Manager的Dell

用于 Microsoft System Center Configuration Manager 的 Dell Server Deployment Pack 版本 2.0安装指南注、小心和警告备注: “注”表示可以帮助您更好地使用计算机的重要信息。
小心: “小心”表示可能会损坏硬件或导致数据丢失,并说明如何避免此类问题。
警告: “警告”表示可能会造成财产损失、人身伤害甚至死亡。
本出版物中的信息如有更改,恕不另行通知。
© 2012 Dell Inc. 版权所有,翻印必究。
未经Dell Inc. 书面许可,严禁以任何形式对这些材料进行复制。
本文中涉及的商标:Dell™、Dell 徽标、Dell Precision™、OptiPlex™、Latitude™、PowerEdge™、PowerVault™、PowerConnect™、OpenManage™、EqualLogic™、Compellent™、KACE™、FlexAddress™、Force10™及 Vostro ™是 Dell Inc. 的商标。
Intel®、Pentium®、Xeon®、Core®及 Celeron ®是 Intel Corporation 在美国和其他国家/地区的注册商标。
AMD®是注册商标,AMD Opteron™、AMD Phenom™及 AMD Sempron ™是 Advanced Micro Devices, Inc. 的商标。
Microsoft®、Windows®、Windows Server®、Internet Explorer®、MS-DOS ®、 Windows Vista ®及Active Directory®是 Microsoft Corporation 在美国和/或其他国家/地区的的商标或注册商标。
DPM(Data Protection Manager)各版本比较

DPM各版本详细对比一、DPM2006介绍1、软件需求安装DPM2006所需的组件2、硬件需求3、功能4、DPM2006的不足~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~二、DPM2007介绍1、功能介绍:System Center Data Protection Manager 2007 (以下简称DPM)是System Center 系列产品中的一部分,目前最新版本为DPM 2007,相比它的上一版本DPM2006,它继续向文件服务器、打印服务器以及分支机构提供稳定可靠的基于磁盘的保护,此外还提供了相应的管理工具来保护和恢复网络中计算机上的文件和应用程序数据,包括Microsoft Exchange Server、Microsoft SQL Server? 和Windows SharePoint Services,以及虚拟服务器Virtual Server和工作站。
在这篇文章中,我将为大家介绍如何安装配置使用这个强大的数据保护工具。
2、软件需求1. Windows PowerShell 1.02. Microsoft .NET Framework 2.03. Internet Information Services (IIS) 6.04. Microsoft SQL Server 2005 with SP2(注:DPM2007包含了一个SQL 2005标准版)5. Windows Server 2003 (R2)SP2或更高版本;WindowsStorage Server 2003 (R2)SP2或更高版本(注:DPM2007支持32位和64位,但是不支持IA64)6. 卷影复制服务VSS的一个补丁程序,详情查看/kb/940349/(注:该补丁程序在DPM服务器和DPM客户端均要安装)3、操作系统要求1、Windows Server 2003(带有Service Pack 2 (SP2) 或更高版本)2、Windows Server 2003 R2(带有 SP2)。
Microsoft System Center 2022 数据中心管理系统说明书
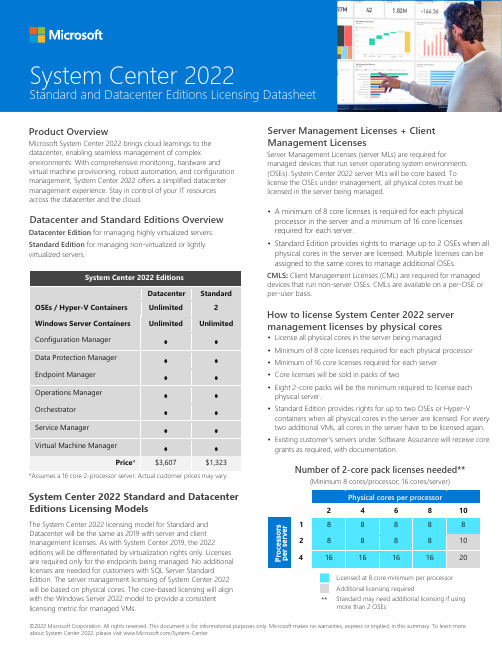
©2022 Microsoft Corporation. All rights reserved. This document is for informational purposes only. Microsoft makes no warranties, express or implied, in this summary. To learn more about System Center 2022, please visit /System-CenterProduct OverviewMicrosoft System Center 2022 brings cloud learnings to the datacenter, enabling seamless management of complexenvironments. With comprehensive monitoring, hardware and virtual machine provisioning, robust automation, and configuration management, System Center 2022 offers a simplified datacenter management experience. Stay in control of your IT resources across the datacenter and the cloud.Datacenter and Standard Editions OverviewDatacenter Edition for managing highly virtualized servers. Standard Edition for managing non-virtualized or lightly virtualized servers.System Center 2022 EditionsDatacenter StandardOSEs / Hyper-V Containers Unlimited 2 Windows Server Containers UnlimitedUnlimitedConfiguration Manager • • Data Protection Manager • • Endpoint Manager • • Operations Manager • • Orchestrator • • Service Manager • • Virtual Machine Manager••Price *$3,607$1,323*Assumes a 16 core 2-processor server. Actual customer prices may vary.System Center 2022 Standard and Datacenter Editions Licensing ModelsThe System Center 2022 licensing model for Standard and Datacenter will be the same as 2019 with server and client management licenses. As with System Center 2019, the 2022editions will be differentiated by virtualization rights only. Licenses are required only for the endpoints being managed. No additional licenses are needed for customers with SQL Server StandardEdition. The server management licensing of System Center 2022 will be based on physical cores. The core-based licensing will align with the Windows Server 2022 model to provide a consistent licensing metric for managed VMs.Server Management Licenses + Client Management LicensesServer Management Licenses (server MLs) are required formanaged devices that run server operating system environments (OSEs). System Center 2022 server MLs will be core based. To license the OSEs under management, all physical cores must be licensed in the server being managed.• A minimum of 8 core licenses is required for each physical processor in the server and a minimum of 16 core licenses required for each server.• Standard Edition provides rights to manage up to 2 OSEs when all physical cores in the server are licensed. Multiple licenses can be assigned to the same cores to manage additional OSEs.CMLS : Client Management Licenses (CML) are required for managed devices that run non-server OSEs. CMLs are available on a per-OSE or per-user basis.How to license System Center 2022 server management licenses by physical cores• License all physical cores in the server being managed • Minimum of 8 core licenses required for each physical processor• Minimum of 16 core licenses required for each server • Core licenses will be sold in packs of two• Eight 2-core packs will be the minimum required to license eachphysical server.• Standard Edition provides rights for up to two OSEs or Hyper-Vcontainers when all physical cores in the server are licensed. For every two additional VMs, all cores in the server have to be licensed again. • Existing customer’s servers under Software Assurance will receive coregrants as required, with documentation.Number of 2-core pack licenses needed**(Minimum 8 cores/processor; 16 cores/server)Physical cores per processor24 6 8 101 8 8 8 8 8 28 8 8 8 10 41616161620Licensed at 8 core minimum per processor Additional licensing required**System Center 2022Standard and Datacenter Editions Licensing DatasheetStandard may need additional licensing if using more than 2 OSEs。
Data_Protector安装参考手册
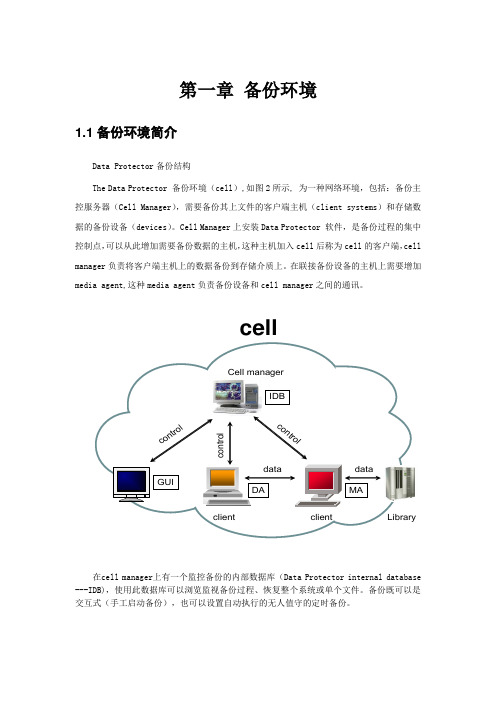
第一章 备份环境1.1备份环境简介Data Protector 备份结构The Data Protector 备份环境(cell ),如图2所示, 为一种网络环境,包括:备份主控服务器(Cell Manager ),需要备份其上文件的客户端主机(client systems )和存储数据的备份设备(devices )。
Cell Manager 上安装Data Protector 软件,是备份过程的集中控制点,可以从此增加需要备份数据的主机,这种主机加入cell 后称为cell 的客户端,cell manager 负责将客户端主机上的数据备份到存储介质上。
在联接备份设备的主机上需要增加media agent,这种media agent 负责备份设备和cell manager 之间的通讯。
Cell managerLibraryo n t r o l在cell manager 上有一个监控备份的内部数据库(Data Protector internal database ---IDB),使用此数据库可以浏览监视备份过程、恢复整个系统或单个文件。
备份既可以是交互式(手工启动备份),也可以设置自动执行的无人值守的定时备份。
第二章备份软件安装2.1 安装准备Cell Manager软件安装需求:PC Server (CPU P4,内存不小于512M)SCSI 卡(PCI LVD/SE接口)或光纤卡Windows 2000 server, Oracle 10g for windows,exchange,sqlserver 2000网络设置完毕:网卡配置完毕,网络连通,可以连接到服务器上(ping或telnet 到小型机执行成功)注意:由于备份软件的license和本地的IP地址相关联,所以安装之前最好确定本PC服务器的IP地址,以后不能随意更改,否则备份软件不能使用。
2.2安装过程:在备份PC服务器DL380光驱中插入DP 6.0 for windows光盘,安装程序自动启动选择Install Data Protector选择next选择I accept the terms in the license agreement选项,然后选择next输入口令(如果有口令)选择安装的路径,一般为默认路径安装;点击change,可以更改安装目录。
戴尔客户端管理包版本6.2用户指南说明书

Dell Client Management Pack Version 6.2 for Microsoft System Center Operations Manager User’s GuideNotes, cautions, and warningsNOTE: A NOTE indicates important information that helps you make better use of your product.CAUTION: A CAUTION indicates either potential damage to hardware or loss of data and tells you how to avoid the problem.WARNING: A WARNING indicates a potential for property damage, personal injury, or death.© 2009 -2018 Dell Inc. or its subsidiaries. All rights reserved. Dell, EMC, and other trademarks are trademarks of Dell Inc. or its subsidiaries. Other trademarks may be trademarks of their respective owners.2018 - 10Rev. A001 Overview (4)What is new in this release (4)Key features of Dell Client Management Pack (4)About Dell Client Management Pack (5)Details of components modeled by Dell Client Management Pack (5)2 Dell Client Management Pack operations (7)Discovery and grouping (7)Discovering a Dell Client system (7)Dell hardware discovery and grouping (8)Objects discovered by Dell Client Management Pack (8)Monitoring (9)Health status indicators (9)Views (10)T asks (12)Client reboot and shutdown (12)Launching the remote desktop for a Dell client system (12)Accessing Reports (13)OpenManage Windows Event Log (13)Customizing the Dell Client Management Pack (13)Unit monitors (13)Object discoveries (15)Rules (15)Dell Command | Monitor or OMCI override properties (16)3 Related documentation and resources (17)Microsoft guidelines for performance and scalability for OpsMgr (17)Other documents you may need (17)Accessing documents from the Dell EMC support site (17)4 Troubleshooting (19)Contents3Overview This document describes the activities that you can perform with the Dell Client Management Pack version 6.2.The integration of Dell Client Management Pack version 6.2 with Microsoft System Center 2012 R2 Operations Manager, Microsoft System Center 2012 SP1 Operations Manager, Microsoft System Center 2012 Operations Manager, or Microsoft System Center Operations Manager 2007 R2 that enables you to manage and monitor the availability of Dell client systems.CAUTION: T o avoid data corruption, data loss, or both; perform the procedures in this document only if you have properknowledge and experience in using Microsoft Windows operating system and Microsoft System Center 2012 R2 Operations Manager, Microsoft System Center 2012 SP1 Operations Manager, Microsoft System Center 2012 Operations Manager, andMicrosoft System Center Operations Manager 2007 R2.NOTE: The term OpsMgr in this document refers to Microsoft System Center 2012 R2 Operations Manager, Microsoft System Center 2012 SP1 Operations Manager, Microsoft System Center 2012 Operations Manager, and Microsoft System Center Operations Manager 2007 R2, unless otherwise specified.See the Dell Client Management Pack’s Release Notes, which contain the latest information about software and management server requirements, and also information about known issues. The Release Notes is posted to the Systems Management documentation page on /support/home. The Release Notes is also packaged in the self-extracting executableDell_Client_Management_Pack_v6.2_Axx.exe (where xx is the Dell Client Management Pack release number).Topics:•What is new in this release•Key features of Dell Client Management Pack•About Dell Client Management PackWhat is new in this releaseThe release highlights of Dell Client Management Pack:•Support for Dell Command | Monitor version 10.1Key features of Dell Client Management PackT able 1. Features and functionality1 4OverviewAbout Dell Client Management PackT able 2. Management pack functionality and dependencies management packDetails of components modeled by Dell Client Management PackT able 3. Management pack details and components modeledOverview56OverviewDell Client Management Pack operationsThis chapter provides information about the various operations that you can perform on OpsMgr using the Dell Client Management Pack.The Dell Client Management Pack enables the following operations to manage Dell client systems:•Discovers and monitors Dell Venue Pro tablets, Dell Latitude, Dell Precision, and Dell OptiPlex systems running the supported Dell Command | Monitor or OMCI service and client Windows operating systems.•Groups Dell clients systems running without Dell Command | Monitor or OMCI service under the Dell UnManaged Clients group.NOTE:Dell Vostro systems are displayed under the Dell UnManaged Clients group.•Monitors the health status for client hardware components by polling at periodic intervals, and updates the state of each component in the Diagram View . A health status is a standardized description of the functional performance of a component, system, or service.•Performs client shutdown and reboot tasks.•Launches remote desktop for Dell client systems.•Generates reports on Dell Windows Event Log and Dell Command | Monitor or OMCI events from the Windows Event Log of the managed system.Topics:•Discovery and grouping •Monitoring •T asks•Accessing Reports•Customizing the Dell Client Management PackDiscovery and groupingDiscovering a Dell Client systemTo discover Dell client systems in a network, ensure that the devices appear in the Agent Managed view under the Administration section of the OpsMgr console. You can use overrides to increase or decrease the discovery and monitoring intervals for specific Dell hardware to meet the needs of your implementation.The client discovery process classifies a Dell system as Dell UnManaged Clients if:•Lower version than OMCI 8.1 is installed on the Dell client system.•Dell Command | Monitor or OMCI services are disabled or not running.•Client system is a Vostro system.Adding Dell client systemsTo add a Dell client system to the Agent Managed list:1 Log in to the system with an account that has the OpsMgr Administrator role for the OpsMgr management groups.2 In the OpsMgr console, click Administration .3At the bottom of the Administration pane, click Discovery Wizard .2Dell Client Management Pack operations 7The Computer and Device Management Wizard screen is displayed.4 Click Next after reading the instructions on the screen.5 To discover the Dell client systems, select the Advanced discovery option.6 In the Computer and Device Classes drop-down list, select Clients Only.7 Click Next.The Discovery Method screen is displayed.8 Select one of the two options given below:•Scan Active Directory — enables you to specify the selected objects from the Active Directory.1Click Configure to create a query to find the objects that you want to scan.2Select the domain where the objects that you want to discover reside, from the Domain drop-down list.•Browse for, or type-in computer names — enables you to browse for or type the names of the Dell client systems you want to discover. Click Browse to search for systems on the network or type the name of the system you want to discover.9 Click Next.The Administrator Account page is displayed.10 Specify the user account that has administrator rights on the computers that you want to scan using one of the two options:•Use selected Management Server Action Account - indicates that you can use the existing Management Server Action Account as the administrator account.•Other user account - indicates that you can specify any account other than the existing Management Server Action Account.Specify the User Name, Password, and the Domain in which the account is present.NOTE: If you select This is a local computer account, not a domain account and then you must specify the ComputerName instead of the Domain name.11 Click Discover.The Select Objects to Manage page displays the list of Dell client systems that you selected.12 Select the Dell client systems that you want to manage and click Next.13 Specify the path for Agent Installation Directory, specify the credentials for Agent Action Account, and click Finish.Dell hardware discovery and groupingThe following table lists the details of the hardware discovery and grouping by Dell Client Management Pack:T able 4. Dell hardware discovery and groupingObjects discovered by Dell Client Management PackThe following table lists the details of objects that are discovered by the Dell Client Management Pack:8Dell Client Management Pack operationsT able 5. Dell object discoveriesMonitoringThe Dell Client Management Pack enables you to monitor the discovered Dell client systems. The Health status indicators helps you to monitor the health of the Dell client systems on the network.Health status indicatorsThe following table lists the icons that indicate the health status of the discovered Dell client systems on the OpsMgr console. For more information about severity propagation, see State Views.T able 6. Icons and Severity levelsDell Client Management Pack operations9ViewsYou can monitor the Dell Client systems using the following views:•Alerts Views•Diagram Views•State ViewsAlerts viewsThe Alerts Views displays alerts for the events received from the supported Dell Command | Monitor or OMCI service running on the systems that you are monitoring. T o view the alerts for the systems you are monitoring:1 In the OpsMgr console, click Monitoring.2 In the Monitoring pane, navigate to the Dell folder and click the folder to display the different views.3 Click Alerts Views > Client Alerts.The OpsMgr console displays the alerts for all the Dell client systems that you are monitoring in the Client Alerts pane. You can see alerts that meet the criteria that you specified in the Authoring pane of the OpsMgr console, such as severity, resolution state, or alerts that are assigned to you.4 Select an alert to view the details in the Alert Details pane.Diagram viewsThe Diagram Views displays a hierarchical and graphical representation of all Dell clients on your network that OpsMgr manages. The Dell Windows Client Management Pack offers the following views:•Client Diagram•Complete Diagram ViewClient diagram viewFigure 1. Graphical representation of dell client systems managed by Opsmgr10Dell Client Management Pack operationsTo access the Client Diagram:1 In the OpsMgr console, click Monitoring.2 In the Monitoring pane, go to the Dell folder and click the folder to display the different views.3 Click Diagram Views > Client Diagram.The Client Diagram offers a graphical representation of all Dell client systems that OpsMgr manages. You can expand and verify the status of individual systems and their components in the diagram. The root node for this view is the Dell Windows Clients group. You can view details for Dell Clients with this view.4 Select a component in the diagram to view the details in the Detail View pane. You can view details of the Dell Command | Monitor orOMCI service and the following hardware components of Dell clients:•Memory•Processors•Sensors•StorageComplete diagram viewFigure 2. Graphical representation of all dell devicesTo access the Complete Diagram View:1 In the OpsMgr console, click Monitoring.2 In the Monitoring pane on the left side, navigate to the Dell folder and click the folder to display the different views.3 Click Diagram Views > Complete Diagram View.The Complete Diagram View offers a graphical representation of all Dell devices that OpsMgr manages. You can expand and verify the status of individual devices and their components in the diagram. You can view details for Dell Clients and Dell UnManaged with the Complete Diagram View.4 Select a component in the diagram to view the details in the Detail View pane.Viewing Dell client hardware health roll-upYou can view the Dell client hardware health rolled up to Windows computer health.Dell Client Management Pack operations11To view the Dell client hardware health roll-up:1 In the OpsMgr console, click My Workspace.2 Right-click Favorite Views and from the menu select New > Diagram Views.A Create Diagram View window is displayed.3 In the Name text box, provide the name.4 In the Description text area, provide the description.5 In the Choose T arget section, click Browse.The Select Object window is displayed.6 In the Select Object window, select Dell Windows Clients from the Look for drop-down list and then click Search.7 Click Add and then click OK.8 In the Choose from a template section, select Client Diagram from the drop-down list.9 Click Create.State viewsThe State Views displays the status of each Dell device managed by OpsMgr on your network. The Dell Client Management Pack provides a list of severity level indicators to help you monitor the health of the Dell client systems on the network.Accessing state viewsT o access the State Views:1 In the OpsMgr console, click Monitoring.2 In the Monitoring pane on the left side, select the Dell folder and click the folder to display the different views.3 Click State Views > Clients.The OpsMgr console displays the status of all the Dell client systems that you are monitoring on the right pane.4 Select a state to view the details in the Detail Views pane.TasksT asks are available in the Actions or T asks pane of the OpsMgr console. When you select a client system in the Diagram Views or the State Views, the relevant tasks are displayed in the Actions or T asks pane.Client reboot and shutdownT o reboot or shutdown a client:1 In the OpsMgr console, select either the State Views or Diagram Views.2 Select any discovered Dell client system.3 In the Actions or Tasks pane, click either Client Reboot or Client Shutdown.The Run Tasks screen is displayed.4 Click Run.Launching the remote desktop for a Dell client systemTo launch a remote desktop for the client system:1 In the OpsMgr console, navigate to either the Diagram Views or State Views.2 Select any discovered Dell client system.12Dell Client Management Pack operations3 Click Launch Remote Desktop under Dell Client Instance T asks in the Actions or T asks pane.The remote desktop for the client system is launched.Accessing ReportsT o access the reporting feature:1 Click Reporting on the OpsMgr console.2 Expand Reporting in the navigation pane.3 Click Dell Client.NOTE: You can also access Reporting from the Diagram Views by clicking on the client instance. The option Dell OpenManageWindows Event Log is located in the Actions or T asks pane under the Dell System instance reports along with the default Microsoft reports.OpenManage Windows Event LogThe event analysis report displays the event time, log record, and status (criticality) of Dell Command | Monitor or OMCI events for selected Dell Windows client systems.T o create a report for OpenManage Windows Event Log:1 Click Reporting on the OpsMgr console.2 Expand Reporting in the navigation pane.3 Click Dell Client for the OpenManage Windows Event Log.4 Click Open in the Actions or Tasks pane.5 Select the time period to generate the report.6 Click Add Object or Add Group.7 Click Search to search for an object or group.8 Select Add to add a single or multiple objects.The object is displayed in the selected object pane.9 Choose the event severity to generate a report.10 Click Run to generate the Windows Event Log report.Customizing the Dell Client Management PackYou can customize the following components of the Dell Client Management Pack by using overrides to increase or decrease the intervals to the specific Dell hardware management needs of the OpsMgr operator.•Monitors — Assesses various conditions that can occur in monitored objects. The result of this assessment determines the health state of a target and the alerts that are generated.•Object Discoveries — Discovers objects on a network that requires monitoring.•Rules — Collects data, such as events generated by managed objects.Unit monitorsThe following table provides information about the various Dell unit monitors and the applicable parameters for client systems:Dell Client Management Pack operations13T able 7. Dell unit monitors in Dell Client Management PackNOTE:•Monitoring for memory is available at the Group level only.Customizing unit monitorsYou can customize the following parameters of the Dell Client Management Pack unit monitors by using overrides:•Enabled - Enables you to enable or disable monitors. You can set the Override setting to True or False. The default setting is True.•Interval in Seconds - The frequency in seconds with which Dell Management Pack polls the Dell device to check the health of a component. The default is 3600 seconds (60 minutes).The unit monitors are triggered by a periodic poll that is configured as interval seconds.14Dell Client Management Pack operationsObject discoveriesT able 8. Dell discovery objectCustomizing object discoveriesUsing overrides, you can customize the following Dell Client Management Pack discovery parameters:•Enabled - Allows you to enable or disable discoveries. You can set the Override setting to True or False. The default setting is True.•Interval in Seconds - Specifies the frequency in seconds that the Dell Client Management Pack discovers the component instance andattributes of your Dell client system. The default value for this attribute is 86400 seconds (24 hours).RulesDell systems event processing rulesDell Client Management Pack processes rules from Dell Command | Monitor or OMCI. You can customize the rules by setting override parameters for the rules.To customize the rules:1 In the OpsMgr console, click Authoring.2 Select Rules under Management Packs Objects in the Authoring pane.3 In the Rules pane, expand Dell Client instance and select a rule.4 Right-click the rule and select Overrides.5 Select Disable the Rule and any of the suboptions to disable the rule.Dell Client Management Pack operations15OrSelect Override the Rule and any of the suboptions to set the override parameters for the rule.You can also change the Severity setting in the Override Properties window for the rule.6 Click OK to apply the override parameter to your rule or Cancel to cancel the changes.Dell Command | Monitor or OMCI override properties All warning and critical events for Dell Command | Monitor or OMCI have a corresponding event processing rule. Each of these rules is processed, based on the following criteria:•Source Name = Dell Command | Monitor or OpenManage Client Instrumentation•Event ID = Event ID of the Dell Command | Monitor or OMCI event•Severity = Severity of the Dell Command | Monitor or OMCI event•Data Provider = Windows System Event log16Dell Client Management Pack operationsRelated documentation and resourcesTopics:•Microsoft guidelines for performance and scalability for OpsMgr•Other documents you may need•Accessing documents from the Dell EMC support siteMicrosoft guidelines for performance and scalability for OpsMgrFor information about Microsoft’s recommendations for scalability, see the Microsoft website at .NOTE: Ensure that the Autogrow option is enabled in Operations Manager Data Warehouse or Database for improvedperformance.Other documents you may needBesides this User’s Guide, see the following guides available at /support/home.•The Dell Command | Monitor User’s Guide•The Dell OpenManage Client Instrumentation User’s Guide provides information about how the Dell OpenManage Client Instrumentation (OMCI) software enables remote management application programs to access client system information, monitor the client system status, or change the state of the client system.•The Dell Client Configuration T oolkit User's Guide describes the installation and use of the Client Configuration T oolkit (CCTK) to configure various BIOS features for Dell client computer platforms.•The client hardware's Owner’s Manual provides information about your system, installing the system components and troubleshooting your system.Accessing documents from the Dell EMC support site You can access the required documents using the following links:•For Dell EMC Enterprise Systems Management documents — /esmmanuals•For Dell EMC OpenManage documents — /openmanagemanuals•For Dell EMC Remote Enterprise Systems Management documents — /esmmanuals•For iDRAC and Dell Lifecycle Controller documents — /idracmanuals•For Dell EMC OpenManage Connections Enterprise Systems Management documents — /esmmanuals•For Dell EMC Serviceability T ools documents — /serviceabilitytools•a Go to /manuals.b Click Choose from all products.c From All products section, click Software & Security, and then click the required link from the following:–Enterprise Systems Management–Serviceability Tools3Related documentation and resources17–Dell Client Command Suite–Connections Client Systems Managementd T o view a document, click the required product version.•Using search engines:–Type the name and version of the document in the search box.18Related documentation and resources4Troubleshooting T able 9. Issues and resolutions applicable to OpsMgrTroubleshooting1920Troubleshooting。
Symantec Endpoint Protection版本升级向导

Symantec Endpoint Protection版本升级向导一、为灾难恢复做准备必须在 Symantec Endpoint Protection Manager 安装期间及之后,收集文件和信息来为灾难恢复做准备。
例如,您必须记下安装时的加密密码。
您必须找到 Keystore文件并将其移至安全位置。
1 、定期备份您的数据库(最好每周),并将备份存储在异地。
数据库备份目录位于 \\Program Files\Symantec\SymantecEndpoint Protection Manager\data\backup。
2、找到您的 Keystore 文件和您的 server.xml 文件。
在安装期间,这些文件会备份到\\Program Files\Symantec\Symantec Endpoint ProtectionManager\Server Private Key Backup 目录中. 您也可以从管理服务器控制台中的“管理员”面板备份这些文件。
3、复制并粘贴sylink.xml 文件。
如果您只有一个域,请从\\ProgramFiles\Symantec\Symantec Endpoint ProtectionManager\data\outbox\agent\ 下的目录中查找并复制sylink.xml 文件。
然后,将该文件贴到\\ProgramFiles\Symantec\Symantec Endpoint ProtectionManager\Server Private Key Backup\。
4、记下在网络中安装第一个站点期间使用的加密密码、计算机的 IP 地址和主机名。
5、将这些文件复制到可移动介质,然后将此介质存放于安全位置。
二、安装 Symantec Endpoint Protection Manager 以进行复制嵌入式数据库和 Microsoft SQL Server 数据库都支持复制配置。
未雨绸缪,谈谈岛津工作站备份那些事

未雨绸缪,谈谈岛津工作站备份那些事1.目的为了避免电脑损坏、系统崩溃、工作站损坏等其他原因导致的数据丢失,按要求需定期做好数据备份。
因为一旦储存在工作站中的数据丢失,就会导致原始记录谱图无法追溯。
目前,工作站分为单机版和网络版,不同版本的工作站备份方式和时间大同小异。
2.备份方式LabSolutions工作站有两种备份方式,一种是手工备份(备份的是图谱数据及日志),另一种是系统备份,备份的是整个数据库(6.72版本以前为LSSBackupTool,6.81版本后为LSSSystemBackup。
本文主要简述手工备份流程。
3.备份流程1)具有备份权限的用户登录工作站,在“管理器”双击“备份”,进入备份界面。
2)选择备份对象,需要注意的是备份日志及项目不能同时备份,要分开操作,选择“日志”,在“备份理由”输入理由,点击“下一步”,进入“设置条件”界面,分别设置“备份位置”、“备份数据期间”、“备份数据密码”,设置完成点击“下一步”,然后点击“开始”,即可开始数据备份。
备份“项目”也是同法操作,备份项目时需一个个选中需要备份的项目,这是手工备份的一个缺点,没有设置全选,在项目较多时容易漏选。
4.备份验证要验证备份的数据文件能否正常查看,可以在“再解析”-“管理器”的菜单栏选择“工具”-“选择备份数据库”,加载备份出来的mdb格式文件即可。
要验证备份的日志文件能否正常查看,可以在“管理工具”-“日志浏览器”的下拉菜单内将“DB”改为“指定文件”,加载备份出来的mdb格式文件即可。
5.手工备份优点1)可直接查看数据如出现电脑崩溃、工作站无法打开时,可在另一台安装有工作站的电脑上查看数据,查看方式按上述“备份验证”操作。
2)可选择备份的时间区间在备份向导中可以选择任意时间段来执行这一时间段的备份。
并且任意时间段的备份都是独立的,可以独立打开任一时间段的数据。
随着时间推移,数据库项目日益增长,可以通过仅备份特定的时间段的数据来缩短备份时间。
I2 灾备软件用户使用手册

V4.0 2013-01-30
-------------------------------------------------------------------------------------------------------------
I2 控制机安装........................................................................................................................................... 15 a) b) Windows 安装................................................................................................................................. 15 Linux 安装......................................................................................................................................... 16
3.
I2 软件卸载............................................................................................................................................... 18
ii22nnooddee安安装装awindows安装awindows安装aawwiinnddoowwss安安装装双击安装程序包出现如下界面点击下一步勾上我接受输入用户名和公司名称选择全部则按程序默认方式安装选择定制可自定义安装目录安装完成后在桌面右下角点击服务管理图标确认复制服务rpc服务日志服务处于运行状态并确认版本号信息也可以通过任务管理器查看sdatadexerpcserverexesdatalogdexesrepdexerpcbaksvrexesdatabaklogdexe这些进程是否开启
system manager2.0

简单的设备管理
– 直观、基于 Web 浏览器 – 仪表板视图、图形报告 – 自动化工作流
Data ONTAP® 的强大功能
– 高效、安全存储 – 高可用性、复制 – 虚拟化、集群
平台
– – – –
NetApp 机密 — 使用受限
在 Windows® 或 Linux® 上运行 NetApp® 存储 Data ONTAP 7.2.3+ Data ONTAP 8.1 集群模式 VMware® ESX® 集成向导
OnCommand™
服务自动化 服务分析
OnCommand Insight
结合了 Akorri® BalancePoint® 和 SANscreen®
统一了 Provisioning Manager Protection Manager Operations Manager
• 服务自动化 • 基于策略的工作流 • SLA 服务目录
NetApp 机密 — 使用受限 3
当今的业务挑战和 IT 挑战以及数据激增
数据快速增长:到 2020 年,数据量将达到目前的 50 倍
– 企业数据一般以每年 50% 的速度增长 – 在增加的数据中,文件、电子邮件和视频预计将占到总量的 90%
存储系统的复杂性
– 不同的介质:SSD、缓存、SAS、SATA、光纤通道 – 高级服务:精简配置、重复数据删除、横向扩展 – 管理专业知识、脚本编写、多种工具
虚拟化支持 第三方集成 C 模式支持 可学习性 可用性 安装 许可
NetApp 机密 — 使用受限
15
System Manager 许可
购买了存储系统后,便可以使用该产品
System Center产品家族销售指南

System Center Configuration Manager 功能
Sys Ctr Config Mgr Svr
Sys Ctr Config Mgr Svr wSQL
Sys Ctr Config Mgr Svr Mgmt Lic Std
Sys Ctr Config Mgr Svr Mgmt Lic Ent
System Center产品家族 Center产品家族
销售指南
System Center (SCVMM) System Center (SCDPM) System Center (SCCM) System Center (SCOM) System Center
Virtual Machine Manager Data Protection Manager Configuration Manager Operations Manager Service Manager (SCSM)
重点产品
微软虚拟化管理平台
资源最大化
◦ 集中式虚拟机部署和管理 ◦ 虚拟机的智能布置 ◦ 快速可靠的P2V和V2V转换 ◦ 协同Operations Manager进行全面的服务级企业监控 增加灵活性 ◦ 利用模板和配置文件快速创建新虚拟机 ◦ 集中化的库文件服务器 ◦ 利用和扩展现有的存储基础架构 ◦ 允许对于虚拟机的委托管理 ◦ 熟悉的界面和公用基础库 ◦ 一个控制台中管理物理机和虚拟机 ◦ 全面支持PowerShell脚本
CMDB(Configuration Management Database)集成
◦ 通用的System Center模式 ◦ 易于建立和维护有意义的CMDB
事件和问题管理
◦ 通过惯例和知识库快速恢复服务 最小化生产环境的风险和中断
NVIDIA Datacenter GPU Manager 2.2说明书

Release NotesTABLE OF CONTENTS Changelog (iii)Patch Releases (iii)DCGM v2.2.9 (iii)DCGM v2.2.8 (iii)DCGM v2.2 GA (iv)New Features (iv)Improvements (iv)Bug Fixes (iv)Known Issues (v)This version of DCGM (v2.2) requires a minimum R418 driver that can be downloaded from NVIDIA Drivers. On NVSwitch based systems such as DGX A100 or HGX A100, a minimum of Linux R450 (>=450.80.02) driver is required. If using the new profiling metrics capabilities in DCGM, then a minimum of Linux R418 (>= 418.87.01) driver is required. It is recommended to install the latest datacenter driver from NVIDIA drivers downloads site for use with DCGM.Patch ReleasesDCGM v2.2.9DCGM v2.2.9 released in July 2021.Improvements‣Added support for the NVIDIA A100 80GB-PCIe product.‣Added support for the NVIDIA RTX A5000 product.‣The --plugin-path option is no longer supported by DCGM Diagnostics (dcgmi diag) and has been removed.Bug Fixes‣Fixed an issue where a DCGM exception (DcgmException) could result in a crash in some environments.DCGM v2.2.8DCGM v2.2.8 released in July 2021.Improvements‣DCGM now supports multiple indepdent clients (libdcgm.so) to connect and obtain GPU telemetry including profiling metrics.‣Added support to obtain GPU telemetry on systems that may have different GPU SKUs.‣Added support for the NVIDIA RTX A6000 product.‣Improved the error logging for dcgmproftester when run in incorrect configurations, such as non-administrator privileges when requesting profilingmetrics.Bug Fixes‣Fixed an issue where the DCGM packages did not include thedcgm_api_export.h header.Known Issues‣Profiling metrics are currently not supported on Arm64 server systems. This feature will be enabled in a future release of DCGM.DCGM v2.2 GADCGM v2.2.3 released in May 2021.New FeaturesGeneral‣Added support for NVIDIA A10 and A30 products.‣Added Python3 support in DCGM for the bindings.‣Profiling metrics are now supported on all NVIDIA datacenter/enterprise GPUs. Improvements‣Reduced the CPU overhead of Profiling metrics fields 1001-1012.‣Added --log-level and --log-filename parameters to dcgmproftester.‣DCGM installer packages no longer include libnvidia-nscq-dcgm.so.450.51.06 version of NSCQ. Customers are advised to install thelatest NSCQ packages from the CUDA network repository for use with DCGM.‣DCGM diagnostics now checks for row remapping failures on NVIDIA Ampere GPUs.‣DCGM libraries do not expose symbols other than dcgm* API. This should fix issues for users who link with DCGM and protobuf libraries at the same time.‣DCGM has reduced logging verbosity in some situations, resulting in a smaller log file size footprint.Bug Fixes‣Added better error message reporting when dcgmi diag cannot find the NVVS binary at the expected installed locations on the system.‣Fixed an issue where NVVS error reports would not include the GPU id.‣Fixed an issue with DCGM detecting GPU brands. DCGM has been updated to be consistent with new brand strings returned by NVML (e.g. "NVIDIA T4" vs."Tesla T4"). This issue may manifest as errors when trying to obtain profilingmetrics with the following message: Error setting watches. Result:Profiling is not supported for this group of GPUs or GPU‣Fixed an issue with the output of dcgmi discovery -v -i c where clocks were reported incorrectly.‣DCGM now reports an error when attempting to run diagnostics on a system with GPUs where some are in MIG mode.‣Fixed a bug in the DCGM Diagnostic where some valid parameters were being rejected as invalid when specified in the configuration file.Known Issues‣On DGX-2/HGX-2 systems, ensure that nv-hostengine and the Fabric Manager service are started before using dcgmproftester for testing the new profilingmetrics. See the Getting Started section in the DCGM User Guide for details oninstallation.‣On K80s, nvidia-smi may report hardware throttling(clocks_throttle_reasons.hw_slowdown = ACTIVE) during DCGMDiagnostics (Level 3). The stressful workload results in power transients thatengage the HW slowdown mechanism to ensure that the Tesla K80 productoperates within the power capping limit for both long term and short termtimescales. For Volta or later Tesla products, this reporting issue has been fixedand the workload transients are no longer flagged as "HW Slowdown". TheNVIDIA driver will accurately detect if the slowdown event is due to thermalthresholds being exceeded or external power brake event. It is recommended that customers ignore this failure mode on Tesla K80 if the GPU temperature is within specification.‣To report NVLINK bandwidth utilization DCGM programs counters in the HW to extract the desired information. It is currently possible for certain othertools a user might run, including nvprof, to change these settings after DCGMmonitoring begins. In such a situation DCGM may subsequently return errorsor invalid values for the NVLINK metrics. There is currently no way withinDCGM to prevent other tools from modifying this shared configuration. Oncethe interfering tool is done a user of DCGM can repair the reporting by runningnvidia-smi nvlink -sc 0bz; nvidia-smi nvlink -sc 1bz.NoticeTHE INFORMATION IN THIS GUIDE AND ALL OTHER INFORMATION CONTAINED IN NVIDIA DOCUMENTATION REFERENCED IN THIS GUIDE IS PROVIDED “AS IS.” NVIDIA MAKES NO WARRANTIES, EXPRESSED, IMPLIED, STATUTORY, OR OTHERWISE WITH RESPECT TO THE INFORMATION FOR THE PRODUCT, AND EXPRESSL Y DISCLAIMS ALL IMPLIED WARRANTIES OF NONINFRINGEMENT, MERCHANTABILITY, AND FITNESS FOR A PARTICULAR PURPOSE. Notwithstanding any damages that customer might incur for any reason whatsoever, NVIDIA’s aggregate and cumulative liability towards customer for the product described in this guide shall be limited in accordance with the NVIDIA terms and conditions of sale for the product.THE NVIDIA PRODUCT DESCRIBED IN THIS GUIDE IS NOT FAULT TOLERANT AND IS NOT DESIGNED, MANUFACTURED OR INTENDED FOR USE IN CONNECTION WITH THE DESIGN, CONSTRUCTION, MAINTENANCE, AND/OR OPERATION OF ANY SYSTEM WHERE THE USE OR A FAILURE OF SUCH SYSTEM COULD RESULT IN A SITUATION THAT THREATENS THE SAFETY OF HUMAN LIFE OR SEVERE PHYSICAL HARM OR PROPERTY DAMAGE (INCLUDING, FOR EXAMPLE, USE IN CONNECTION WITH ANY NUCLEAR, AVIONICS, LIFE SUPPORT OR OTHER LIFE CRITICAL APPLICATION). NVIDIA EXPRESSL Y DISCLAIMS ANY EXPRESS OR IMPLIED WARRANTY OF FITNESS FOR SUCH HIGH RISK USES. NVIDIA SHALL NOT BE LIABLE TO CUSTOMER OR ANY THIRD PARTY, IN WHOLE OR IN PART, FOR ANY CLAIMS OR DAMAGES ARISING FROM SUCH HIGH RISK USES.NVIDIA makes no representation or warranty that the product described in this guide will be suitable for any specified use without further testing or modification. T esting of all parameters of each product is not necessarily performed by NVIDIA. It is customer’s sole responsibility to ensure the product is suitable and fit for the application planned by customer and to do the necessary testing for the application in order to avoid a default of the application or the product. Weaknesses in customer’s product designs may affect the quality and reliability of the NVIDIA product and may result in additional or different conditions and/ or requirements beyond those contained in this guide. NVIDIA does not accept any liability related to any default, damage, costs or problem which may be based on or attributable to: (i) the use of the NVIDIA product in any manner that is contrary to this guide, or (ii) customer product designs.Other than the right for customer to use the information in this guide with the product, no other license, either expressed or implied, is hereby granted by NVIDIA under this guide. Reproduction of information in this guide is permissible only if reproduction is approved by NVIDIA in writing, is reproduced without alteration, and is accompanied by all associated conditions, limitations, and notices.TrademarksNVIDIA and the NVIDIA logo are trademarks and/or registered trademarks of NVIDIA Corporation in the Unites States and other countries. Other company and product names may be trademarks of the respective companies with which they are associated.Copyright© 2013-2021 NVIDIA Corporation. All rights reserved.。
SEP管理台升级流程

SEP管理台升级流程SEP(Symantec Endpoint Protection)管理台升级流程是指将旧版本的SEP管理台升级至最新版本的流程。
下面将详细介绍SEP管理台升级的步骤和注意事项。
步骤一:备份在进行任何升级前,首先需要备份SEP管理台的数据和配置文件。
备份的目的是为了防止升级过程中出现意外情况导致数据丢失或配置文件损坏。
备份可以使用SEP的内置备份功能,将数据和配置文件导出到一个安全的位置。
步骤三:停止SEP服务在升级之前,需要先停止SEP服务,以确保升级过程中不会有冲突或数据损坏。
可以通过在操作系统的服务管理器中停止SEP服务来实现。
步骤四:运行安装程序步骤五:检查升级状态升级过程中会出现一系列的进度条和提示信息,需要仔细观察和检查升级的状态。
确保没有出现错误或警告信息,升级过程顺利进行。
步骤六:测试和验证升级完成后,需要对SEP管理台进行测试和验证,确保升级后的功能正常运行。
可以使用一些典型的操作来测试SEP管理台的功能,比如添加和管理终端设备、查看日志等。
如果出现任何异常情况,需要及时反馈给厂商以进行修复。
步骤七:恢复配置和数据如果升级过程中备份了SEP管理台的配置和数据,可以通过SEP的内置还原功能来恢复配置和数据。
确保恢复后的配置和数据与升级前一致。
步骤八:启动SEP服务在确认升级无误并恢复了配置和数据后,可以启动SEP服务。
在操作系统的服务管理器中启动SEP服务。
步骤九:更新终端设备步骤十:数据迁移如果SEP管理台升级是在新的服务器上进行的,需要将原有服务器上的数据迁移到新的服务器上。
可以参考SEP的数据迁移文档和工具,将原有服务器上的数据导出并导入到新的服务器上。
注意事项:1.在升级之前,务必备份SEP管理台的数据和配置文件,以防止升级过程中数据丢失或配置文件损坏。
3.在升级之前,需要停止SEP服务,以防止升级过程中出现冲突或数据损坏。
4.升级过程中要仔细观察和检查升级的状态,确保没有出现错误或警告信息。
Dell PowerProtect DD Series Data Protection Storag

主要优势快速、安全和高效在单个机架中提供 1.5 PB 的可用容量* 基于戴尔内部测试和现场遥测数据,2022 年 3 月。
实际结果可能有所不同。
** 基于戴尔在 2022 年 3 月进行的内部测试,在测试中与上一代产品进行了比较。
实际结果可能有所不同。
***比较采用 Cloud Tier 的 DD9800 和采用 Cloud Tier 的 PowerProtect DD9900 上的 1 PB 数据。
实际结果可能有所不同。
2022 年 3 月。
**** 基于戴尔内部测试,在测试中将 DDVE 7.7 与 DDVE 7.1 进行了比较。
实际结果可能有所不同。
2022 年 3 月。
***** 在 DD9900 上使用 DDOS 7.7 及更高版本时。
基于戴尔内部测试。
实际结果可能有所不同。
2022 年 3 月© 2022 Dell Inc. 或其子公司。
适用于 PowerProtect 数据保护存储设备的 Smart Scale组织通常必须管理多个数据中心和云环境,添加、升级和淘汰保护存储基础架构,适应不断发展的新应用程序,以及优化容量和性能。
这不是一项轻松的任务,但戴尔正在利用 Smart Scale 来克服这一难题。
Smart Scale 允许您在统一命名空间下的单个系统池中管理多达 32 个 DD 系列数据保护专用存储设备,从而降低管理复杂性,同时提高存储效率。
Smart Scale 通过我们的单一管理控制台 PowerProtect DD Management Center 免费部署。
Smart Scale 在 DD9900、DD9400、DD6900 和 DD6400 上受支持。
关于软件集成,我们支持 Dell PowerProtect Data Manager、Dell NetWorker 和第三方备份应用程序。
Smart Scale 引入了移动存储单元,可在每个池中灵活地备份数据并以透明的方式移动备份数据。
思科数据中心网络管理器(DCNM)系统管理配置指南说明书

C H A P T E R S e n d d o c u m e n t c o m m e n t s t o n e x u s 7k -d o c f e e d b a ck @c i s c o.c o m 13-1Cisco DCNM System Management Configuration Guide, Release 5.xOL-23625-0113Working With Threshold RulesThis chapter describes how to configure threshold rules using Cisco Data Center Network Manager(DCNM).This chapter includes the following sections:•Information About Threshold Rules, page 13-1•Configuring Threshold Rules, page 13-4Information About Threshold RulesThis section includes the following topics:•Threshold Rules Overview, page 13-1•Threshold Rule Examples, page 13-2Threshold Rules OverviewCisco DCNM provides a feature that you use to specify rising or falling threshold rules for sample variablesin collected statistical data. Depending on the rule definition, a set of actions are performed by Cisco DCNM.You define the threshold rule on the Threshold Rules page, and you apply the threshold rule to the existingchart.This section includes the following topics:•Rising Threshold, page 13-1•Falling Threshold, page 13-2•Threshold Rule Properties, page 13-2•Threshold Rule Actions, page 13-2Rising ThresholdThe rising threshold is the upper threshold for a sample variable. When the current sampled variable isgreater than or equal to the specified threshold, a set of actions is performed.Chapter13 Working With Threshold Rules Information About Threshold RulesF I N A L D R A F TFalling ThresholdThe falling threshold is the lower threshold for a sample variable. When the current sampled variable islower than or equal to the specified threshold a set of actions is performed.Note You can specify only one rising threshold and one falling threshold for a single sampled variable.Threshold Rule PropertiesThreshold rule properties are as follows:•Name—Specifies the threshold rule name.•Frequency—Specifies the number of times the sampled variable must cross a threshold before triggering any actions.•Period—Specifies the interval of time the frequency is monitored.•Repeat—Prevents the timer from resetting after triggering an action within the period.•Trend—Specifies the rising or falling threshold.Threshold Rule ActionsThreshold rule actions are as follows:•Send an email or SMS to a mail server or mail to SMS gateway.•Run a script on the server.•Send an event to the current DCNM JMS channel.Threshold Rule ExamplesNote The granularity of a period is driven by the minimal interval of the collected data. Consequently, the period must be higher than that interval.This section includes the following topics:•Trigger an Action Each Time a Threshold is Crossed, page13-2•Trigger an Action Only Once in a Period When a Threshold is Crossed, page13-3•Trigger an Action Every Fourth Period When a Threshold is Crossed, page13-4Trigger an Action Each Time a Threshold is CrossedTo trigger an action each time a threshold is crossed, set properties as follows:•Frequency—1•Repeat—YesFigure13-1 shows the trigger action when you set rule properties to the preceding values.Cisco DCNM System Management Configuration Guide, Release 5.xOL-23625-01F I N A L D R A F T 13-3Cisco DCNM System Management Configuration Guide, Release 5.x OL-23625-01Chapter 13 Working With Threshold RulesInformation About Threshold RulesFigure 13-1T rigger an Action Each Time a Threshold is CrossedIf the sampled variable crosses the threshold, an action is taken the first time it crosses the threshold. As a result, an action is performed each time the threshold is crossed.Trigger an Action Only Once in a Period When a Threshold is CrossedTo trigger an action only once in a period when a threshold is crossed, set properties as follows:•Frequency—1•Period—300•Repeat—NoFigure 13-2 shows the trigger action when you set rule properties to the preceding values.Figure 13-2T rigger an Action Only Once When a Threshold is Crossed Within a PeriodIf the sampled variable crosses the threshold, an action is taken the first time it crosses the threshold. For the remaining 5 minutes, an action will not be taken. As a result, an action is performed only once during the specified period.F I N A L D R A F T Cisco DCNM System Management Configuration Guide, Release 5.x OL-23625-01Chapter 13 Working With Threshold RulesConfiguring Threshold Rules Trigger an Action Every Fourth Period When a Threshold is Crossed To trigger an action every fourth period when a threshold is crossed, set properties as follows:•Frequency—4•Period—300•Repeat—NoFigure 13-3 shows the trigger action when you set rule properties to the preceding values.Figure 13-3T rigger an Action Every Fourth Period When a Threshold is CrossedIf the sampled variable crosses the threshold, an action is taken the fourth time it crosses the threshold. For the remaining 5 minutes, an action is not taken. As a result, an action is performed only once during the specified period.Configuring Threshold RulesThis section includes the following topics:•Creating Threshold Rules, page 13-4•Deleting Threshold Rules, page 13-5•Editing Threshold Rules, page 13-6•Viewing Threshold Rules, page 13-6•Applying a Threshold Rule to a Chart, page 13-6Creating Threshold RulesYou can create threshold rules using Cisco DCNM.DETAILED STEPSStep 1From the Feature Selector pane, choose DCNM Server Administration > Threshold Rules .Chapter13 Working With Threshold RulesConfiguring Threshold RulesF I N A L D R A F TStep2From the toolbar, choose New, and then choose New Threshold Rule.The Details and Threshold Bindings tabs appear in the Details pane, with the Details tab open.Step3Create a threshold rule as follows:a.In the Name field, enter a name.b.In the Description field, enter a description of the threshold rule.After you have enter a description, the Rising Threshold check box is automatically checked and theThreshold field in the Settings area is outlined in red.Note A field outlined in red indicates that an entry is required. A field outlined in yellow indicatesthat the entry is satisfactory.c.In the Settings area, enter a value in the Threshold field.Once you have entered a value, the three options in the Action area are outlined in red.d.In the Action area, provide one of the following:–Enter email addresses (delimited with commas)–Select Sent Event to forward events to the DCNM Event Browser–Enter a script nameThe script receives all data regarding the crossed threshold. The script can be written in anyprogramming language and saved in one of the directories of the system PATH.Note Ensure that the Cisco DCNM server is configured for an SMTP server. For more informationabout configuring the Cisco DCNM server, see the Cisco DCNM Installation and LicensingGuide, Release 5.x.e.(Optional) In the corresponding Settings and Action areas, configure a Falling Threshold.f.(Optional) Click the Threshold Bindings tab to view bindings.g.Click Deploy.The rule is deployed.When you exit Cisco DCNM and Save Pending Changes is checked in the Warning dialog box, click Yesto save the rule.Deleting Threshold RulesYou can delete rules using Cisco DCNM.DETAILED STEPSStep1From the Feature Selector pane, choose DCNM Server Administration > Threshold Rules.The rules appear in the Summary pane.Step2From the Summary pane, right-click the appropriate rule.Cisco DCNM System Management Configuration Guide, Release 5.x OL-23625-01Chapter13 Working With Threshold Rules Configuring Threshold RulesF I N A L D R A F TStep3From the drop-down list, choose Delete Threshold Rule.A warning dialog box appears and displays “Are you sure you want to delete?”Step4Click Yes.The rule is deleted.Editing Threshold RulesYou can view threshold rules using Cisco DCNM.DETAILED STEPSStep1From the Feature Selector pane, choose DCNM Server Administration > Threshold Rules.The rules appear in the Summary pane.Step2Edit any appropriate areas.Note You cannot edit the Name field.Viewing Threshold RulesYou can view threshold rules using Cisco DCNM.DETAILED STEPSStep1From the Feature Selector pane, choose DCNM Server Administration > Threshold Rules.The rules appear in the Summary pane.Step2Click on a rule to view it.Applying a Threshold Rule to a ChartYou can apply threshold rules using Cisco DCNM.DETAILED STEPSStep1From the Feature Selector pane, choose the appropriate feature. For example, if you wanted to see statistics for an Ethernet port, choose Interfaces > Physical > Ethernet.The available devices appear in the Summary pane.Step2From the Summary pane, choose the appropriate device.Cisco DCNM System Management Configuration Guide, Release 5.xOL-23625-01Chapter13 Working With Threshold RulesConfiguring Threshold RulesF I N A L D R A F TStep3Click the Statistics tab.Step4In the toolbar, click New Chart and then from the drop-down list choose the chart that you want to view.For example, if you wanted to see statistics for traffic, choose Traffic Statistics Chart.Step5In the chart toolbar, click Launch Threshold Setting.Cisco DCNM System Management Configuration Guide, Release 5.xOL-23625-01Chapter13 Working With Threshold Rules Configuring Threshold RulesF I N A L D R A F TCisco DCNM System Management Configuration Guide, Release 5.xOL-23625-01。
System Center Operations Manager 2007 的定价和许可
System Center Operations Manager 2007 的定价和许可Operations Manager 2007 的许可Microsoft System Center Operations Manager 2007 需要为每台管理服务器购买服务器许可证,并为每台受管理的设备购买操作管理许可证(“OML”)。
提供企业和标准版的OML,以便进行服务器管理,并提供客户端版本的OML,以便对没有运行服务器操作系统的客户端的其他设备实施管理。
针对完整的应用系统和服务器管理,需要购买企业OML,而标准OML可被用于操作系统和基本的工作负载管理。
通过批量许可证计划购买标准OML 的另一种方式是购买Microsoft System Center 服务器管理许可证(“SML”) 组合。
标准SML 现已面市,并包括适用于Operations Manager 的标准OML,以及适用于Microsoft® Systems Management Server (SMS)和System Center Data Protection Manager (DPM)的标准管理许可证。
标准SML为针对您的Windows 文件服务器获得System Center 服务器管理的价值提供了一种简单、便捷和具成本效益的方式。
企业SML将于2007 年第四季度面市,它将包括OML 和Data Protection Manager Management 许可证的企业版、System Center Configuration Manager 2007服务器管理许可证、以及System Center Virtual Machine Manager 2007。
Operations Manager 2007 的定价说明:全部价格均为在美国国内购买的价格,并以美元结算。
所列的价格为估计的价格,并反映了批量许可计划中采用的起始价格;零售价可能有所不同。
Dell EMC 服务器部署包版本 4.1 安装指南说明书

用于 Microsoft System Center Configuration Manager 的 Dell EMC Server Deployment Pack 版本 4.1安装指南8 2021注意、小心和警告:“注意”表示帮助您更好地使用该产品的重要信息。
:“小心”表示可能会损坏硬件或导致数据丢失,并告诉您如何避免此类问题。
:“警告”表示可能会导致财产损失、人身伤害甚至死亡。
© 2019 - 2021 年 Dell Inc. 或其子公司。
保留所有权利。
Dell、EMC 和其他商标是 Dell Inc. 或其附属机构的商标。
其他商标可能是其各自所有者的商标。
章 1: 概览 (4)此版本中的新功能 (4)前提条件与要求 (5)支持的系统 (6)用于 Dell EMC Server Deployment Pack 的 Configuration Manager、操作系统、AIK/ADK 支持值表 (6)安装 Dell EMC Server Deployment Pack (8)首次在系统上安装 Dell EMC Server Deployment Pack (8)升级 Dell EMC Server Deployment Pack (9)迁移至 Microsoft System Center Configuration Manager (9)使用 GUI 卸载 Dell EMC Server Deployment Pack (10)使用命令行安装、升级和卸载 Dell EMC Server Deployment Pack (10)安装 Dell EMC Server Deployment Pack (10)卸载 Dell EMC Server Deployment Pack (10)升级 Dell EMC Server Deployment Pack (11)使用 Configuration Manager Admin Console (11)故障排除 (12)PCI 设备驱动程序的运行状况显示为“严重” (12)使用控制面板卸载 Dell EMC Server Deployment Pack (12)在一个或多个 SMS 提供程序关闭时安装 Dell EMC Server Deployment Pack (12)使用 WinPE 3.0 在第 13 代 PowerEdge 平台上部署操作系统 (12)可能需要的其他 Dell 说明文件 (12)联系 Dell (13)访问 Dell EMC 支持网站上的支持内容 (13)目录3概览本指南提供了有关安装和卸载用于 Microsoft System Center Configuration Manager (SCCM) 或 Microsoft Endpoint Configuration Manager(MECM) 的 Dell EMC Server Deployment Pack (DSDP) 的软件前提条件和要求的信息。
dell powervault 数据保护解决方案快速参考指南说明书

Dell™ PowerVault™ 数据保护解决方案快速参考指南概览本说明文件旨在帮助您快速找到有关 Dell™ PowerVault™数据保护解决方案的信息。
本说明文件分为下列几个部分:•快速参考部分—根据您要执行的功能,帮助您找到所需的特定说明文件•PowerVault 数据保护解决方案软件说明文件—列出 Dell 和Microsoft™软件说明文件及其位置•PowerVault 数据保护解决方案硬件说明文件—列出 Dell 硬件说明文件及其位置•系统管理说明文件—列出 Dell 和 Microsoft 系统管理说明文件及其位置•Dell PowerVault 数据保护解决方案介质—列出恢复磁盘和系统附带的其它介质表 1-1.说明文件的组织快速参考说明文件表 1-2.“PowerVault 数据保护解决方案规划和部署”表 1-3.“操作 PowerVault 数据保护解决方案”表 1-4.““故障排除”和“获得帮助””PowerVault 数据保护解决方案软件说明文件表 1-5.“PowerVault 数据保护解决方案软件说明文件”表 1-6.“Microsoft System Center Data Protection Manager 2007 说明文件”PowerVault 数据保护解决方案硬件说明文件表 1-7.“PowerVault 数据保护解决方案硬件说明文件”系统管理说明文件表 1-8.“系统管理说明文件”PowerVault 数据保护解决方案介质表 1-9.“PowerVault 数据保护解决方案 CD/DVD 介质”快速参考部分表 1-2.PowerVault 数据保护解决方案规划和部署您要做什么™在何处查找信息:了解 DPM 2007有关 DPM 2007 的简介,请参阅规划 DPM 2007 部署中的“DPM 2007 简介”。
有关 DPM 2007 的详细信息,另请参阅System Center Data Protection Manager 2007 使用入门指南。
IBM Endpoint Manager for Core Protection Data Prot

IBM Endpoint Manager for Core Protection DataProtection Add-onVersion 9.2.0Quick Start GuideThis guide describes a quick and easy way to install the product.National Language Version:To obtain the Quick Start Guide in other languages, print the language-specific PDF from the installation media.Product overviewIBM ®Endpoint Manager, built on BigFix ®technology, delivers endpoint lifecycle and security management through a single,lightweight, extensible infrastructure. This solution enables organizations to proactively manage their servers, desktops, andlaptops. IBM Endpoint Manager provides a clear path for improving control and compliance with clear, accurate reporting, and easy integrations with adjacent management infrastructures. For details about IBM Endpoint Manager, see Getting Started.Version 9.2.0includes significant improvements to the capabilities in the individual applications built on the IBM Endpoint Manager platform:vNew role-based access controls to allow IBM Endpoint Manager administrators greater control over operator permissions.v Expanded agent coverage for heterogeneous platform support. New platforms on UNIX and Linux include Red Hat Enterprise Linux (RHEL) 7, Power Linux (RHEL, big endian), and Ubuntu 14.IBM Endpoint Manager for Core Protection Data Protection Add-on is optional and can be deployed and managed through the IBM Endpoint Manager infrastructure. The module also helps improve data protection capabilities while helping to control operational costs.IBM Endpoint Manager for Core Protection Data Protection Add-on offers a robust data loss prevention and device control solution that integrates into the anti-virus and anti-malware capabilities provided by the Core Protection solution and can:v Secure data (sensitive or not) on devices that leave the business premisesv Enforce security policies such that users can access sensitive data for their jobs, but not misuse or lose that data v Comply with the growing number of data privacy laws that affect the industry or company.IBM Endpoint Manager for Core Protection V9.2.0adds improvements on Microsoft Windows and Mac OS X to protect managed computers from security risks by scanning files and performing a specific action on each security risk detected. For detailed information about this product, see IBM Endpoint Manager for Core Protection on IBM Knowledge Center.The IBM Endpoint Manager package includes the following product DVD:v IBM Endpoint Manager Core Protection - Data Protection Add-on for WindowsFor complete documentation, see /support/knowledgecenter/SS2TKN/welcome.For information about using the IBM Endpoint Manager for Core Protection Data Protection Add-on, see the Core Protection Module 10.6 SP1 Administrator's Guide.3Step 3: Get started and install IBM Endpoint ManagerA complete IBM Endpoint Manager installation is composed of installation and registration of the platform, followed by the configuration of the applications:1.For an introduction to the product platform and applications, see Getting Started2.To learn about the installation of the platform and the product components, see Installation Guide.IBM®More informationFor more information, see the following resources:v IBM Endpoint Manager Support Site at: /support/entry/portal/Overview/Software/Tivoli/Tivoli_Endpoint_Managerv IBM Endpoint Manager wiki at: https:///developerworks/mydeveloperworks/wikis/home?lang=en#/wiki/ Tivoli Endpoint Manager/page/Homev Knowledge Base at: /support/docview.wss?uid=swg21584549v Forums and Communities at: /developerworks/forums/category.jspa?categoryID=506IBM Endpoint Manager Version 9.2.0 Licensed Materials - Property of IBM. © Copyright IBM Corp. 2013, 2014. U.S. Government Users Restricted Rights - Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp.IBM, the IBM logo, and ®are trademarks or registered trademarks of International Business Machines Corp., registered in many jurisdictions worldwide. Other product and service names might be trademarks of IBM or other companies. A current list of IBM trademarks is available on the Web at “Copyright and trademark information” (/legal/copytrade.shtml).Printed in Ireland。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
System Center Data Protection Manager2007还原操作实例(下)
V1.0
Charli-wei
Charli_wei@
目录
1.数据恢复 (3)
1.1测试环境: (3)
1.2系统状态恢复 (3)
1.3文件还原 (28)
1.4数据库还原 (45)
2.备份还原分析 (65)
2.1备份媒体(不包含创建副本所需的时间) (65)
2.2还原媒体 (66)
2.3备份数据类型对比 (66)
2.4还原数据类型对比 (66)
1.数据恢复
1.1测试环境:
测试机TDPM
IP:192.168.108.89
测试系统状态用帐户:DPMTEST
测试文件:E:\DMPTEST
测试数据库:TDB01,TDPM
1.2系统状态恢复
1)TDPM上已新建一个DPMTEST用户,并已创建恢复点
2)显删除改新建帐户模拟数据丢失
3)打开恢复页,在左工具栏浏览中找到需要恢复的计算机
4)选择并所选择计算机的SystemState子项,右键选择“显示所有恢复点”
5)可以查看到所有的可恢复版本
6)选择所需要的恢复点,并点击恢复
7)恢复向导中复查恢复选择,确定无误,点击下一步
8)如果恢复源来自磁带则如下图:
数有限,所有不推荐选择复制到磁带。
10)如选择复制到网络文件夹则进入指定目标页,点击浏览
11)选择数据恢复到的位置,点击确定
12)确定目标这里选择的目标机的E盘,并点击下一步
13)如选择复制到磁带则,选择压缩,并点击下一步
收件人的邮箱地址
15)在网络带宽使用限制文件框中点击修改,可以限制网络带宽
16)这里我们只设置了通知邮箱,完成设置点击下一步
17)摘要页检查信息是否正确,然后点击恢复
18)下面是从磁盘复制到磁带的摘要
19)等待完成。
20)在监视页面作业选项卡中可查看相关信息。
21)如果之前选择了复制到网络文件夹则在你指定的网络路径中将生成一个文件
夹
22)在该文件夹内可以找到对应的*.bkf备份文件
23)如果之前选择了复制到磁带则可以在管理页面的库选项卡中要到对应的磁带
项,它将在磁带标签处进行详细的描述。
24)需要从磁带中恢复数据需要先将数据复制至网络文件夹。
在对应的磁带上右键
选择查看磁带内容
25)这时会弹出需要进行重新编录的警告,点击确定,并等待完成
据,并点击复制
27)在请指定其他恢复目录的对话框中,选择你打算恢复的目标,这里选择目标机
的D盘,并点击确定
28)弹出对话框点击确定,等待作业完成
29)在当前管理页的库选项卡中可以看到磁带的操作情况
30)在监视页的作业选项卡中可以查看进度信息
31)然后在目标机D盘可以找到备份文件的文件夹
32)使用备份文件还原系统状态
33)双击备份文件,弹出备份或还原向导,默认点击下一步
34)在备份或还原页选择还原文件和设置,并点击下一步
35)还原项目页展开要还原的项目目录树,勾选System State项,并点击浏览
36)选择备份文件所在的目录,并点击确定,然后在还原项目页点击下一步
37)等待还原完成
38)点击报告可以查看,还原日志。
39)系统状态还原需要重启之后才能生效。
重启后可以查看用户已还原成功。
1)这里在备份之后在一个日志文件中插入当前时间模拟数据变更
2)打开恢复页面在左边工具栏中找到需要恢复的计算机
3)展开该节点,在所需要恢复的路径上右键选择显示所有恢复点
4)弹出所有版本对话框,选择所需要恢复的版本,并点恢复
5)如果选择恢复的媒体为磁盘则
6)如果选择恢复的媒体为磁带则
一步
8)在指定恢复选项页,可以选择现有版本恢复行为:
●创建副本为创建现有版本的副本,对目标机上的文件不进行任何修改;
●跳过为有同名文件则跳过;
●覆盖为覆盖同名文件;
同时也可以修改网络带宽限制和通知设置,这里同系统状态恢复中设置。
9)在选择恢复类型页,如果选择恢复到其他位置则需要点击浏览指定恢复目标,
其后页面同恢复到原位置
10)在选择恢复类型页,如果选择恢复到磁带,点击下一步
11)指定库页这里在磁带选项中选择压缩,然后点击下一步
12)在指定恢复选项页仅有SAN恢复和通知,其后页面同恢复到原位置
13)摘要页确认信息点击恢复
14)这里选择覆盖为测试用例,所在查看目标机上的文件已经还原为原文件,无插
入时间信息。
还原成功。
15)如选择复制到磁带则需要进行同系统状态恢复时复制到磁带相同的查看磁带
操作,流程如下
在管路页库选项卡找到对应磁带
选择磁带在其上右键选择查看磁带内容
弹出磁带需要重新编录对话框,点击是
等待完成编录
再次右键选择查看磁带内容
在查看磁带内容对话框勾选需要恢复的数据,点击恢复
在请指定其他恢复目标对话框,选择恢复目标,并点击确定
弹出信息对话框,点击确定,等待完成
完成之后将在目标位置发现还原文件
1)在TDB上新建TDPM数据库,并新建表User_Name,填充数据如下图
2)数据库已创建还原点。
现在插入一行数据模拟数据库修改或破坏
3)在恢复页左边工具栏展开找到需要恢复的数据库
4)在其上右键选择显示所有恢复点
5)在所有版本弹出对话框中选择需要恢复的版本,点击恢复
6)弹出恢复向导,复查恢复选择页,确认无误点击下一步
库),点击下一步
8)指定数据库状态页,默认选择使数据库保持可操作状态,点击下一步。
